#Advanced Data Security
Explore tagged Tumblr posts
Text
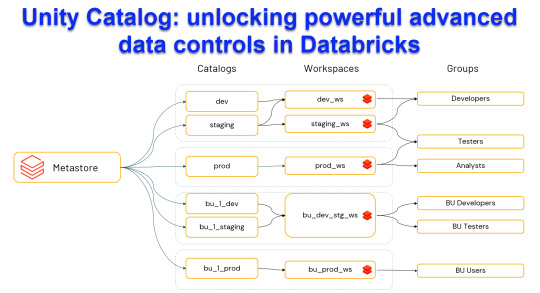
Unity Catalog: Unlocking Powerful Advanced Data Control in Databricks
Harness the power of Unity Catalog within Databricks and elevate your data governance to new heights. Our latest blog post, "Unity Catalog: Unlocking Advanced Data Control in Databricks," delves into the cutting-edge features
View On WordPress
#Advanced Data Security#Automated Data Lineage#Cloud Data Governance#Column Level Masking#Data Discovery and Cataloging#Data Ecosystem Security#Data Governance Solutions#Data Management Best Practices#Data Privacy Compliance#Databricks Data Control#Databricks Delta Sharing#Databricks Lakehouse Platform#Delta Lake Governance#External Data Locations#Managed Data Sources#Row Level Security#Schema Management Tools#Secure Data Sharing#Unity Catalog Databricks#Unity Catalog Features
0 notes
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
Swarm Enterprises
Website: https://swarm.enterprises/
Address: San Francisco, California
Phone: +1 (504) 249-8350
Swarm Enterprises: Revolutionizing Decision-Making with Cutting-Edge Technology
Swarm Enterprises is at the forefront of innovation, harnessing the power of swarm intelligence algorithms to redefine the way decisions are made. Inspired by the coordinated movements of natural swarms, these algorithms deliver unparalleled precision and intelligent recommendations. Clients are empowered to embrace data-driven decision-making, resulting in heightened efficiency and superior outcomes.
The company's secret weapon lies in its utilization of machine learning techniques, where massive data sets are transformed into invaluable insights. By training algorithms on both historical and real-time data, Swarm Enterprises uncovers hidden patterns, emerging trends, and subtle anomalies that often elude human analysis. This extraordinary capability allows clients to unearth concealed opportunities, minimize risks, and gain an undeniable competitive edge.
Swarm Enterprises doesn't stop there; they seamlessly integrate IoT (Internet of Things) devices into their offerings, enabling real-time data collection and analysis. These connected physical objects grant clients the ability to remotely monitor and manage various aspects of their operations. This groundbreaking technology not only streamlines proactive maintenance but also enhances operational efficiency and boosts overall productivity.
In a world where informed decisions are paramount, Swarm Enterprises is a trailblazer, providing the tools and insights necessary for success in an increasingly data-centric landscape.

#Bot Detection & Defense in San Francisco#Real-time bot detection near me#Security against live botnet traffic#Browser Feature Signatures#Performance Profiling#Automated Behavior Analysis#Advanced Analysis Technique#Integration & Results#Data & Insights#Simplified Integration#Accuracy and Precision#Real-time Reporting
2 notes
·
View notes
Text
Apple cedează presiunilor autorităților britanice: Criptarea end-to-end pentru iCloud, dezactivată în Marea Britanie
Apple a confirmat oficial că renunță la criptarea end-to-end oferită prin sistemul Advanced Data Protection (ADP) pentru utilizatorii iCloud cu conturi nou create în Regatul Unit, urmând ca și utilizatorii existenți să fie afectați de această decizie. Acest pas marchează un compromis semnificativ în politica de confidențialitate a companiei americane, realizat în urma presiunilor exercitate de…
#ADP#Advanced Data Protection#apple#backdoor#bam#cloud storage#Confidențialitate#criptare end-to-end#cybersecurity#data protection#diagnosis#diagnoza#end-to-end encryption#icloud#Marea Britanie#neamt#online security#privacy#Protecția datelor#Regatul Unit#roman#securitate cibernetică#securitate online#UK#United Kingdom
0 notes
Text

Quantum Security and Post-Quantum Cryptography: Preparing for the Cryptographic Revolution
Cryptography serves as the foundation of our digital security infrastructure, protecting sensitive data from unauthorized access and ensuring the integrity of our communications. This science of secure information exchange has evolved continuously alongside advances in computing technology. However, we now stand at a critical juncture as quantum computing emerges from theoretical possibility to practical reality, threatening to undermine the very cryptographic systems we rely on daily.
The imminent arrival of powerful quantum computers presents both unprecedented challenges and opportunities for information security. This article explores how quantum computing affects current cryptographic practices, why we need quantum-resistant solutions, and the promising approaches being developed to secure our digital future in the post-quantum era.
Classical Cryptography
The Vulnerability of Classical Algorithms
The security of most cryptographic systems today relies on mathematical problems that are computationally difficult for classical computers to solve. Quantum computers, however, can exploit quantum mechanical phenomena like superposition and entanglement to solve certain problems exponentially faster than their classical counterparts.
This quantum advantage becomes particularly concerning when we consider widely-used public-key cryptographic algorithms like RSA (Rivest-Shamir-Adleman) and ECC (Elliptic-Curve Cryptography). These systems form the backbone of secure communications across the internet, protecting everything from financial transactions to private messages.
How Shor's Algorithm Threatens Current Encryption
At the heart of the quantum threat lies Shor's Algorithm, developed by mathematician Peter Shor in 1994. This quantum algorithm can efficiently solve two mathematical problems that underpin much of modern cryptography:
RSA Encryption Under Threat
RSA encryption derives its security from the difficulty of factoring large composite numbers into their prime components. For example, while it's easy to multiply two large prime numbers (p and q) to get a product (n), working backward to determine the original primes becomes exponentially more difficult as the numbers grow larger.
A classical computer would require billions of years to factor a 2048-bit RSA key. However, Shor's Algorithm running on a sufficiently powerful quantum computer could perform this factorization in hours or even minutes. Once the prime factors are known, the private key can be easily derived from the public key, completely compromising the encryption system.
To illustrate: If n = p × q is a 2048-bit number (the product of two 1024-bit primes), a classical computer would need to check an astronomical number of possibilities. A quantum computer using Shor's Algorithm could find the factors p and q directly through quantum operations that essentially explore multiple possibilities simultaneously.
ECC Encryption Equally Vulnerable
Elliptic Curve Cryptography faces a similar threat. ECC relies on the difficulty of solving the discrete logarithm problem on elliptic curves – finding the value k when given points G and P, where P = k·G on an elliptic curve.
Shor's Algorithm can also be adapted to solve this discrete logarithm problem efficiently. Once a quantum computer can determine the private key k from the publicly available information G and P, the security guarantees of ECC collapse completely.
These vulnerabilities are not merely theoretical concerns. As quantum computers continue to advance, the timeline for practical quantum threats to cryptography grows shorter. This reality has spurred intense research into post-quantum cryptographic solutions.
Quantum-Resistant Cryptography
Post-Quantum Cryptography: A New Paradigm
Post-quantum cryptography (PQC) represents a new approach to cryptographic algorithm design. Rather than relying on mathematical problems vulnerable to quantum attacks, PQC algorithms are built on alternative mathematical foundations believed to be resistant to both classical and quantum computational methods.
Several promising approaches have emerged in the field of post-quantum cryptography:
Lattice-Based Cryptography
Lattice-based cryptography relies on the computational difficulty of solving certain problems related to geometric structures called lattices. These problems, such as finding the shortest vector in a high-dimensional lattice, appear resistant to quantum attacks.
CRYSTALS-Kyber, selected by NIST as a standard for post-quantum key encapsulation, exemplifies this approach. The security of Kyber stems from the hardness of the module learning with errors (MLWE) problem, which has withstood significant cryptanalysis efforts.
Lattice-based systems offer reasonable key sizes and efficient operations, making them practical for implementation across various computing environments.
Hash-Based Cryptography
Hash-based cryptography builds secure systems from cryptographic hash functions, which are already believed to be quantum-resistant. These approaches, like SPHINCS+, provide strong security guarantees based on minimal assumptions, making them particularly attractive as conservative options for long-term security.
The main challenge with hash-based signatures has been their relatively large signature sizes, though newer variants have made significant improvements in efficiency.
Code-Based Cryptography
Code-based cryptography leverages the difficulty of decoding certain error-correcting codes without knowledge of the code structure. McEliece, one of the oldest public-key cryptosystems (proposed in 1978), falls into this category and has resisted both classical and quantum cryptanalysis for decades.
While code-based systems typically require larger key sizes, they offer fast encryption and decryption operations, making them suitable for specific applications where key size is less constrained.
NIST's Post-Quantum Standardization Process
Recognizing the urgency of developing quantum-resistant standards, the U.S. National Institute of Standards and Technology (NIST) initiated a comprehensive evaluation process in 2016. This multi-year effort involved the global cryptographic community in analyzing and testing candidate algorithms.
In July 2022, NIST selected CRYSTALS-Kyber for general encryption and key establishment, along with three digital signature algorithms: CRYSTALS-Dilithium, FALCON, and SPHINCS+. These selections represent a significant milestone in preparing our digital infrastructure for the quantum era.
The standardization process continues with additional candidates under consideration, ensuring a diverse portfolio of solutions to meet various security and performance requirements.
Quantum Key Distribution
While post-quantum cryptography focuses on developing classical algorithms resistant to quantum attacks, quantum key distribution (QKD) takes a fundamentally different approach by using quantum mechanics itself to secure communications.
How QKD Works
QKD leverages fundamental properties of quantum physics to create a secure communication channel. The process typically involves sending polarized photons (light particles) between two parties, traditionally named Alice and Bob:
1. Alice sends a stream of photons, each randomly polarized in one of several possible states
2. Bob measures each photon, also choosing measurement bases randomly
3. Alice and Bob publicly compare which measurement bases they used (but not the results)
4. They keep only the results where they happened to use matching bases
5. These matching results form a shared secret key
The security of QKD stems from a fundamental principle of quantum mechanics: the act of measuring a quantum system disturbs it. If an eavesdropper (Eve) attempts to intercept and measure the photons, she inevitably introduces detectable errors in the transmission. Alice and Bob can detect these errors through statistical analysis, revealing any attempted eavesdropping.
Limitations and Practical Considerations
While QKD offers theoretical perfect security, practical implementations face significant challenges:
- Physical distance limitations due to photon loss in transmission media
- Vulnerability to side-channel attacks targeting implementation flaws
- Requirements for specialized hardware and dedicated quantum channels
- Integration difficulties with existing network infrastructure
Despite these challenges, QKD networks have been deployed in limited settings, such as financial institutions and government facilities. Ongoing research continues to address these limitations, potentially expanding QKD's practical applications.
Implementing Quantum Security
Hybrid Cryptographic Systems
Given the evolving nature of both quantum threats and quantum-resistant solutions, security experts recommend a hybrid approach during the transition period. This strategy involves implementing both classical and post-quantum algorithms simultaneously, providing immediate protection while allowing for gradual migration.
For example, a hybrid TLS implementation might use both an RSA key exchange and a lattice-based key exchange, requiring an attacker to break both systems to compromise the connection. This approach provides defense in depth while the security community builds confidence in post-quantum solutions.
Continuous Monitoring and Threat Detection
As quantum computing capabilities advance, organizations must implement robust monitoring systems to detect potential quantum threats. Advanced analytics and machine learning algorithms can identify unusual patterns that might indicate quantum-based attacks on cryptographic systems.
This continuous vigilance allows security teams to respond rapidly to emerging threats, potentially identifying compromised systems before significant damage occurs.
Blockchain Integration with Quantum-Resistant Cryptography
Blockchain technology, with its emphasis on immutability and decentralized trust, represents both a vulnerable target and a potential solution in the quantum security landscape. By integrating quantum-resistant cryptographic algorithms into blockchain protocols, these systems can maintain their security guarantees even against quantum attacks.
Several blockchain projects are already implementing post-quantum signatures and encryption methods, demonstrating how these technologies can complement each other to enhance overall security.
Quantum Random Number Generation
The strength of any cryptographic system ultimately depends on the quality of randomness used in key generation. Quantum Random Number Generators (QRNGs) leverage quantum phenomena to produce truly random numbers, providing a fundamental advantage over classical random number generators.
Unlike classical RNGs, which might contain subtle patterns or biases, QRNGs derive randomness from inherently unpredictable quantum processes like radioactive decay or photon path detection. This true randomness strengthens cryptographic systems by ensuring that keys cannot be predicted, even with advanced computational capabilities.
Commercial QRNG solutions are already available, offering enhanced security for critical applications where high-quality randomness is essential.
Preparing for the Post-Quantum Future
Impact Across Sectors
The transition to quantum-resistant cryptography will affect virtually every sector of the digital economy:
Financial Services: Banks and payment processors must protect transaction data not only from current threats but also from future attacks where encrypted data, harvested today, could be decrypted once quantum computers mature—a "harvest now, decrypt later" attack strategy.
Healthcare: Medical records contain sensitive personal information that requires long-term protection, making early adoption of post-quantum cryptography particularly important for healthcare organizations.
Government and National Security: Government agencies handling classified information face some of the most urgent needs for quantum-resistant solutions, as nation-state adversaries may be among the first to develop advanced quantum computing capabilities.
Critical Infrastructure: Power grids, telecommunications networks, and transportation systems rely on secure communications to function safely, making their protection from quantum threats a matter of national security.
Research and Development Priorities
As we navigate the transition to post-quantum security, several research priorities emerge:
Performance Optimization: Further research to improve the efficiency of post-quantum algorithms, reducing computational overhead and resource requirements
Implementation Security: Development of side-channel resistant implementations to ensure that practical deployments don't introduce vulnerabilities
Cryptographic Agility: Creating systems that can rapidly update cryptographic algorithms without major infrastructure changes
Standards Development: Continued international cooperation on cryptographic standards to ensure global interoperability of secure systems
Conclusion
The advent of quantum computing represents both a significant challenge and an opportunity for cryptographic security. While quantum computers threaten to break the mathematical foundations of current encryption systems, they also inspire the development of more robust cryptographic approaches.
Through the development and adoption of post-quantum cryptographic algorithms, quantum key distribution, and enhanced security practices, we can ensure that our digital infrastructure remains secure in the quantum era. The path forward requires collaboration between researchers, industry leaders, and government agencies, working together to build quantum-resistant systems before large-scale quantum computers become a reality.
By understanding the quantum threat landscape and implementing proactive security measures, organizations can protect their sensitive information and maintain trust in digital systems even as quantum computing technology advances. The time to prepare for the post-quantum future is now, ensuring that cryptography continues to fulfill its essential role in securing our increasingly connected world.
#linklayer#blog#technology#innovation#science#space science#space#electronics#global#computer science#advanced technologies#tech#techinnovation#quantum computing#quantum physics#quantum mechanics#learning#cybersecurity#cyber security#data security#cryptography#blockchain
0 notes
Text
Dark Web Monitoring

🔒 Safeguard Your Business in the Digital Age with Century Solutions Group! 🔒
🚨 Did You Know? The Dark Web is a hidden marketplace where stolen business data is bought and sold—and small businesses are prime targets!
Imagine this: A small online retailer gets hacked, and customer data is exposed on the Dark Web. The result? Loss of trust, reputation damage, and financial setbacks.
💡 How Can You Stay Protected?
🔍 Dark Web Monitoring – With Century Solutions Group, your business is constantly scanned for compromised data. If your credentials appear on illicit platforms, we alert you before the damage is done!
🛡️ Our Cybersecurity-First Approach Includes: ✅ Advanced Threat Protection – Firewalls, encryption, and AI-driven security. ✅ Employee Security Training – Your first line of defense is an informed team! ✅ Multi-Layered Defense – Strong passwords, MFA, and endpoint security. ✅ Secure Payment Transactions – Protect your customers & your revenue.
💼 Why Partner with Century Solutions Group? We’ve been Atlanta’s trusted IT MSP since 1996, offering cutting-edge cybersecurity solutions tailored for small businesses. Our proactive security approach means you can focus on growth—while we keep the bad guys out!
💪 Don’t wait for a cyberattack to react—stay ahead with Century Solutions Group! https://centurygroup.net/cloud-computing/cyber-security/
#CyberSafeBusiness #DarkWebDefense #CenturySolutionsGroup #MSP #SmallBizSecurity #CybersecurityAwareness
#Dark Web Monitoring#Cybersecurity#cybersecurity threats#data backup#Advanced Threat Protection#Employee Security Training#managed it services
2 notes
·
View notes
Text
Exploring the Benefits of Psync's Two-Way Audio Camera
In today's world, home security is more important than ever, and Psync is leading the charge with its innovative Two-Way Audio Camera. This cutting-edge device not only allows you to monitor your home in real-time, but it also enables seamless communication with family members or pets from anywhere.
The Two-Way Audio feature is a game changer. It provides peace of mind by allowing you to check in on your loved ones and speak to them directly through the camera. Whether you're at work, on vacation, or just in another room, you can always stay connected.
Psync's cameras are designed with user-friendly technology that makes installation a breeze. With high-definition video quality and night vision capabilities, you can have clear visibility around the clock. The sleek design ensures that the camera fits perfectly into any home decor.
Moreover, Psync prioritizes security and privacy. The camera's encrypted data transmission ensures that your footage is safe from unauthorized access. You can enjoy the benefits of advanced home security without worrying about potential breaches.
In summary, Psync's Two-Way Audio Camera is an excellent investment for anyone looking to enhance their home security system. With its interactive features and superior design, it's a fantastic choice for keeping your home and loved ones safe.
#encrypted data transmission#privacy#home security#real-time monitoring#interactive features#user-friendly technology#advanced home security
0 notes
Text
AI and Health: New Technologies Paving the Way for Better Treatment
Artificial intelligence (AI) is expanding rapidly in the health sector, and it is revolutionizing our medical system. With the help of AI, new technologies are being developed that are not only helpful in accurately diagnosing diseases but are also playing an important role in personalized treatment and management.

Quick and accurate diagnosis of diseases AI-based tools can now analyze medical imaging data such as X-rays, CT scans, and MRIs quickly and accurately. This helps doctors to quickly detect complex conditions such as cancer, heart diseases, and neurological problems.
Personalized medicine AI can help create personalized treatment plans for every individual by analyzing genomics and biometrics. This technology ensures that the patient gets the right medicine and the right dose at the right time.
Improved health management AI-based health apps and wearables such as smart watches are now helping people monitor their health condition. These devices regularly track health indicators such as heart rate, blood pressure and sleep quality.
Accelerating medical research The role of AI has become extremely important in the development of new drugs and vaccines. Using AI, scientists can analyze complex data sets and make new medical discoveries faster.
Accessible and affordable healthcare AI technology is helping in delivering affordable and effective healthcare, even in rural and remote areas. Telemedicine and virtual health assistants are bridging the gap between patients and doctors.
Conclusion Artificial intelligence is playing an important role in making healthcare more effective, accurate, and accessible. However, there are challenges such as data security and ethics in the use of AI technology which need to be dealt with. In the coming years, with more advanced and innovative uses of AI, the healthcare landscape may change completely.
#AI and Health: New Technologies Paving the Way for Better Treatment#Artificial intelligence (AI) is expanding rapidly in the health sector#and it is revolutionizing our medical system. With the help of AI#new technologies are being developed that are not only helpful in accurately diagnosing diseases but are also playing an important role in#Quick and accurate diagnosis of diseases#AI-based tools can now analyze medical imaging data such as X-rays#CT scans#and MRIs quickly and accurately. This helps doctors to quickly detect complex conditions such as cancer#heart diseases#and neurological problems.Personalized medicine#AI can help create personalized treatment plans for every individual by analyzing genomics and biometrics. This technology ensures that the#AI-based health apps and wearables such as smart watches are now helping people monitor their health condition. These devices regularly tra#blood pressure and sleep quality.Accelerating medical research#The role of AI has become extremely important in the development of new drugs and vaccines. Using AI#scientists can analyze complex data sets and make new medical discoveries faster.Accessible and affordable healthcare#AI technology is helping in delivering affordable and effective healthcare#even in rural and remote areas. Telemedicine and virtual health assistants are bridging the gap between patients and doctors.#Conclusion#Artificial intelligence is playing an important role in making healthcare more effective#accurate#and accessible. However#there are challenges such as data security and ethics in the use of AI technology which need to be dealt with. In the coming years#with more advanced and innovative uses of AI#the healthcare landscape may change completely.
1 note
·
View note
Text
IT Networking Solutions by Vivency Technology LLC
Vivency Technology LLC is a trusted provider of advanced IT networking solutions designed to meet the evolving needs of businesses. Our comprehensive services include network design, implementation, and optimization for seamless connectivity and enhanced productivity.
Whether you require structured cabling, wireless solutions, or secure data networks, our team of experts ensures tailored solutions to support your business growth. With a commitment to quality and innovation, we deliver robust networking systems that ensure reliability, scalability, and security.
Partner with Vivency Technology LLC to experience cutting-edge IT networking solutions that empower your organization to stay connected in the digital age. Visit our website for more information or to request a consultation.
#IT networking solutions Dubai#Network design services#Secure data networks#Structured cabling solutions#Wireless networking Dubai#Business connectivity solutions#IT network optimization#Reliable IT networks#Scalable networking systems#Corporate networking solutions#Advanced IT networks#Network implementation services#IT infrastructure Dubai#Vivency Technology LLC networking#Digital connectivity solutions
0 notes
Text
#Advanced AI Systems#Apple Vision Pro#Biometric Authentication#Biometric Innovations#Civil Liberties and Technology#Consumer Technology#Corporate Control#Data Security Risks#facts#Iris Recognition Technology#life#New World Order#Optic ID#Podcast#Privacy Concerns#serious#straight forward#Surveillance Technology#truth#upfront#website
0 notes
Text

Elevate your accounting expertise with G-Tec Education Institute's AI Integrated Accounting course in Dubai. Master Advanced Excel and harness AI-driven tools to automate, analyze, and enhance your financial management tasks. Stay ahead in the ever-evolving world of finance and unlock the future of accounting today!
Contact Us: +971 50 398 0768 +971 4 266 5884 Visit our website https://gtecqusais.com/courses/advanced-excel/
#Advanced Excel Courses in Dubai#Cyber Security and Ethical Hacking Certification Courses in Dubai#ethical hacking training in Dubai#Data Analysis Diploma Course in Dubai
0 notes
Text
Emerging Tech Trends in the Internet of Things (IoT)
Introduction
The Internet of Things (IoT) is transforming our world by connecting devices and enabling smarter, more efficient interactions. In everything from smart homes to industrial automation, the IoT is leading a revolution in our living and working environments. In this article, TechtoIO explores the emerging tech trends in IoT, highlighting the innovations and advancements that are shaping the future. Read to continue link
#Innovation Insights#Tags5G IoT#AI in IoT#autonomous vehicles IoT#big data IoT#edge computing IoT#future of IoT#IIoT#industrial IoT#Internet of Things#IoT data analytics#IoT healthcare#IoT innovations#IoT security#IoT technology#IoT trends#smart cities IoT#smart homes#wearable IoT#Technology#Science#business tech#Adobe cloud#Trends#Nvidia Drive#Analysis#Tech news#Science updates#Digital advancements#Tech trends
1 note
·
View note
Text
Future Of AI In Software Development

The usage of AI in Software Development has seen a boom in recent years and it will further continue to redefine the IT industry. In this blog post, we’ll be sharing the existing scenario of AI, its impacts and benefits for software engineers, future trends and challenge areas to help you give a bigger picture of the performance of artificial intelligence (AI). This trend has grown to the extent that it has become an important part of the software development process. With the rapid evolvements happening in the software industry, AI is surely going to dominate.
Read More
#Accountability#Accuracy Accuracy#Advanced Data Analysis#artificial intelligence#automated testing#Automation#bug detection#code generation#code reviews#continuous integration#continuous deployment#cost savings#debugging#efficiency#Enhanced personalization#Ethical considerations#future trends#gartner report#image generation#improved productivity#job displacement#machine learning#natural language processing#privacy privacy#safety#security concerns#software development#software engineers#time savings#transparency
0 notes
Text
Explore the best developer friendly API platforms designed to streamline integration, foster innovation, and accelerate development for seamless user experiences.
Developer Friendly Api Platform
#Developer Friendly Api Platform#Consumer Driven Banking#Competitive Market Advantage Through Data#Banking Data Aggregation Services#Advanced Security Architecture#Adr Open Banking#Accredited Data Recipient
0 notes
Text
The Rising Tide of Military Cloud Computing: Transforming Defense Operations

Military Cloud Computing is revolutionizing the way defense agencies operate in an era marked by rapid technological advancements and evolving security threats. With its promise of improved collaboration, flexibility, and cost-efficiency, cloud computing has become indispensable in modern warfare. Defense agencies worldwide are embracing cloud-based solutions to enhance their operational capabilities, strengthen cybersecurity, and gain a competitive edge on the battlefield.
One of the primary drivers behind the adoption of military cloud computing is the need for interoperability and information sharing among allied forces. Cloud-based systems enable seamless integration and collaboration across different branches of the military and partner nations, facilitating joint operations and enhancing mission effectiveness. Additionally, the centralized nature of cloud computing ensures data consistency and accessibility, even in remote or austere environments.
Furthermore, military cloud computing offers defense agencies a scalable and secure platform to store, process, and analyze vast amounts of data generated from various sources, including sensors, satellites, and reconnaissance missions. By leveraging cloud-based solutions, military organizations can enhance situational awareness, make data-driven decisions in real-time, and adapt to dynamic battlefield conditions more effectively. Additionally, cloud computing enables rapid prototyping and deployment of new capabilities, allowing defense agencies to stay ahead of emerging threats and technological advancements.
Security remains a paramount concern for military cloud computing, given the sensitive nature of defense data and the prevalence of cyber threats. To address these concerns, cloud service providers invest heavily in implementing robust security measures, including encryption, authentication, and access controls, to safeguard against unauthorized access and data breaches. Additionally, compliance with stringent regulatory standards and certifications ensures the integrity and confidentiality of military data stored in the cloud.
Looking ahead, the Military Cloud Computing Market is poised for continued growth as defense agencies prioritize digital transformation and innovation in their operations. With advancements in technologies such as artificial intelligence, machine learning, and edge computing, the potential for cloud-based solutions to revolutionize military operations is vast. By harnessing the power of the cloud, defense organizations can adapt to evolving threats, enhance agility, and maintain superiority in an increasingly complex and dynamic security environment.
#defense#cloud computing#cybersecurity#military operations#interoperability#data security#advanced technology#real-time collaboration
0 notes
Text
The Best Silent Phone License Privacy Protection in the UK

These days, with Silent Phone License Privacy Protection digital privacy becoming compromised more and more, it is critical to identify trustworthy ways to safeguard your private correspondence. The best option for encrypted communication and safe texting is the Silent Phone License. Let's explore how this cutting-edge platform protects your personal information in a world where cybersecurity threats are constantly changing.
#mobilephonedeals#latestmobilephones#smartphonesandaccessories#cellphones#luxuriousmobilephones#buyonlinelatestsmartphone#luxurymobilephonestore#cellphonesmanufactured#kickmobiles#mobilephonemanufacturingdeals#Encrypted Communication#Silent Phone License Secure Messaging#Advanced Encryption#Silent Phone License Data Protection#Silent Phone License
0 notes