#software integration tips
Explore tagged Tumblr posts
Text
Integrating New Software: Tips for a Smooth Transition
Introduction
In today’s fast-paced technological landscape, businesses often find themselves integrating new software to stay competitive and efficient. However, the process can be daunting, fraught with potential disruptions and challenges. At TechtoIO, we understand the importance of a smooth transition when implementing new software. This guide provides essential tips to help you integrate new software seamlessly, minimizing downtime and maximizing productivity. Read to Continue
#addressing software resistance#business software implementation#continuous software improvement#data migration tools#effective software rollout#ensuring data integrity#Integrating new software#minimizing downtime in software integration#new software adoption#performance metrics for software integration#post-implementation software review#selecting new business software#smooth software transition#software compatibility considerations#software implementation roadmap#software integration tips#software migration strategies#software vendor selection#successful software integration#training for software integration#software solutions
1 note
·
View note
Text
How to Use n8n and AI to Build an Automation System
Automation is changing how we work every day. It helps save time, reduce mistakes, and get more done with less effort. If you want to automate your tasks but don’t know where to start, this guide is for you. In this post, you will learn how to use n8n — a free, open-source automation tool — combined with AI to build smart workflows that do work for you. What Is n8n? n8n (pronounced…
#AI automation#AI integration#AI workflow#AI-powered workflows#API integration#artificial intelligence tools#automate emails#automate tasks#automation platform#automation software#automation system#automation tips#business automation#chatbot automation#data processing automation#email automation#intelligent automation#low-code automation#n8n automation#no-code automation#open source automation#productivity tools#smart automation#time-saving tools#workflow automation#workflow builder
0 notes
Text
POS Implementation
POS Implementation: A Comprehensive Guide
In today’s fast-paced retail and service environments, implementing a Point of Sale (POS) system can significantly streamline operations, enhance customer experience, and improve overall efficiency. Whether you’re upgrading from a traditional cash register or installing your first POS system, proper implementation is crucial to maximizing its benefits. This guide will walk you through the essential steps of POS implementation.
Step 1: Identify Business Needs
Before selecting a POS system, assessing your business requirements is important. Consider the following:
The size and type of your business.
Specific features you need (e.g., inventory tracking, customer loyalty programs).
Budget constraints.
Integration requirements with existing software and hardware.
Step 2: Choose the Right POS System
Not all POS systems are created equal. Here’s how to select one that fits your needs:
Research and compare various providers.
Look for scalability to accommodate future growth.
Ensure it supports multiple payment methods.
Check reviews and testimonials from similar businesses.
Step 3: Hardware and Software Setup
A POS system consists of hardware (like barcode scanners, receipt printers, and card readers) and software. Ensure you:
Acquire hardware compatible with your chosen POS software.
Install and configure the software according to your operational needs.
Test all components to ensure they work seamlessly together.
Step 4: Data Migration
If you’re transitioning from an older system, data migration is a critical step:
Back up your existing data.
Transfer inventory, sales history, and customer information to the new system.
Verify the accuracy of migrated data.
Step 5: Employee Training
Proper training ensures your team can effectively use the POS system:
Organize hands-on training sessions.
Provide user manuals and support materials.
Address common troubleshooting scenarios.
Step 6: Pilot Testing
Before full-scale implementation, conduct a pilot test:
Use the system in a controlled environment.
Monitor for any issues or inefficiencies.
Gather feedback from staff and customers.
Step 7: Go Live
Once testing is complete, it’s time to roll out the system:
Schedule the launch during a low-traffic period to minimize disruptions.
Ensure on-site support is available for the initial days.
Communicate the change to your team and customers.
Step 8: Monitor and Optimize
Implementation doesn’t end with the launch. Regular monitoring is essential:
Analyze performance metrics (e.g., transaction times, error rates).
Update the system as needed to fix bugs and improve features.
Seek ongoing feedback from employees and customers.
Conclusion
Implementing a POS system is an investment in your business's future. With proper planning and execution, it can simplify daily operations, enhance customer satisfaction, and drive growth. By following the steps outlined above, you can ensure a smooth and successful implementation.
#POS System Implementation#Point of Sale Guide#Retail Technology#Business Efficiency#POS Hardware and Software#Data Migration Tips#Employee Training for POS#Pilot Testing POS#POS System Optimization#Small Business Solutions#Inventory Management#Customer Loyalty Programs#Payment Integration#Retail Operations#Streamlining Business Processes
0 notes
Text
Boost Your Productivity with These Tools
Boost your business productivity with these 10 must-have tools! From Trello to Slack, learn how to streamline your operations and save time with the best apps.
Boost Your Productivity with These Tools Written By: that Hannah Jones Time to Read: 7 minutes Running a business or managing a team is no small feat, especially when juggling multiple tasks, projects, and deadlines. With so much to manage, productivity tools are no longer just “nice-to-haves”—they’re essential for keeping your operations streamlined and efficient. Whether you’re looking to…
#app integration tools#Asana project management#automation tools for business#best productivity apps#best tools for entrepreneurs#business apps for entrepreneurs#business efficiency tools#business growth tools#business workflow tools#digital productivity apps#Evernote for note-taking#Google Workspace tips#improving business efficiency#Monday.com workflows#Notion for knowledge sharing#productivity hacks#productivity strategies#productivity tools for business#project planning tools#RescueTime focus app#Slack for communication#small business tools#task management apps#team collaboration apps#time management software#time tracking tools#tools for entrepreneurs#tools for remote teams#Trello for project management#Zapier automation
0 notes
Text
youtube
Elevate Your Podcast with Riverside's Game-Changing Features!
Discover how Riverside can transform our podcasting journey with its top 10 game-changing features. From studio-quality recording that ensures uncompressed audio and video to local recording capabilities, we’ll explore how this platform keeps our content professional even during shaky internet connections. Riverside also offers separate track recording for ultimate editing control, live streaming options to engage audiences in real-time, and easy remote guest invitations. With automatic transcriptions, integrated editing tools, secure cloud storage, and custom branding options, Riverside is perfect for both beginners and seasoned pros looking to elevate their podcasts.

#Podcasting #Riverside
#Youtube#Riverside platform#Neturbiz#podcasting tools#podcast recording#studio quality audio#high resolution video#local#remote#recording#separate track recording#live streaming podcasts#screen sharing#remote guest invitations#automatic transcriptions#integrated tools#cloud storage#custom branding#podcast production#improve podcast quality#podcasting#for beginners#software#strategies#tips#features#video podcasting#audio podcasting#podcast#editing
1 note
·
View note
Text
AI Automation Workflow-Productivity
AI workflow automation is transforming the way businesses operate. By integrating artificial intelligence into your workflows, you can automate repetitive tasks, enhance efficiency, and free up your team to focus on strategic priorities. Benefits of AI Workflow AutomationImplementing AI Workflow Automation: Expert TipsStart Small and ScaleFocus on User AdoptionPrioritize Data QualityExamples of…
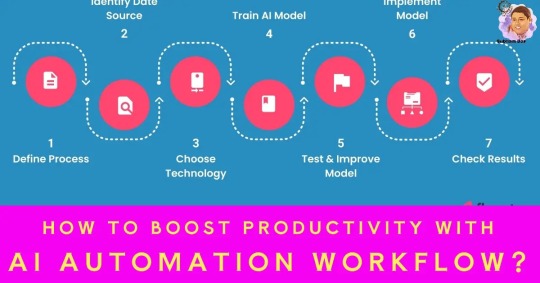
View On WordPress
#artificial intelligence#automation#productivity#AI automation#workflow automation#productivity hacks#automation tools#productivity tips#AI tools#workflow efficiency#business automation#time management#productivity strategies#AI in business#automation trends#AI productivity#tech automation#AI software#productivity apps#digital transformation#automation benefits#work smarter#AI integration#efficiency tips#automation solutions#AI workflows#AI trends#business productivity#tech productivity#AI optimization
0 notes
Note
Hi i love your art!! I really like how you integrate 3d in illustrations, which tips would you tonnato someone who wants to learn 3d art / how do you approach it?
thanks in advance!
i never took a proper class for it, but youtube tutorials do a pretty dang good job for this! and messing around by yourself!
first things first, is to choose the software to use i use blender, it's free and very powerful for 3d and animation
starting out, follow some tutorials for basic functionality perhaps a stick figure-esque rigged model
after that, you can experiment yourself with what you want to make and look up specific things as you go along
Here are some links, it's been awhile since I've started so idk how helpful they are but hope they help!
Beginner Tutorial Playlist
Rigged Character Playlist
UV Transparency
Shape Keys
69 notes
·
View notes
Text
Centibillionaire Elon Musk’s takeover of the former US Digital Service—now the United States DOGE Service—has been widely publicized and sanctioned by one of President Donald Trump’s many executive orders. But WIRED reporting shows that Musk’s influence extends even further, and into an even more consequential government agency.
Sources within the federal government tell WIRED that the highest ranks of the Office of Personnel Management (OPM)—essentially the human resources function for the entire federal government—are now controlled by people with connections to Musk and to the tech industry. Among them is a person who, according to an online résumé, was set to start college last fall.
Scott Kupor, a managing partner at the powerful investment firm Andreessen Horowitz, stands as Trump’s nominee to run the OPM. But already in place, according to sources, are a variety of people who seem ready to carry out Musk’s mission of cutting staff and disrupting the government.
Amanda Scales is, as has been reported, the new chief of staff at the OPM. She formerly worked in talent for xAI, Musk’s artificial intelligence company, according to her LinkedIn. Before that, she was part of the talent and operations team at Human Capital, a venture firm with investments in the defense tech startup Anduril and the political betting platform Kalshi; before that, she worked for years at Uber. Her placement in this key role, experts believe, seems part of a broader pattern of the traditionally apolitical OPM being converted to use as a political tool.
“I don't think it's alarmist to say there's a much more sophisticated plan to monitor and enforce loyalty than there was in the first term,” says Don Moynihan, a professor of public policy at the University of Michigan.
Got a Tip?
Are you a current or former employee with the Office of Personnel Management or another government agency impacted by Elon Musk? We’d like to hear from you. Using a nonwork phone or computer, contact Vittoria Elliott at [email protected] or securely at velliott88.18 on Signal.
Sources say that Riccardo Biasini, formerly an engineer at Tesla and most recently director of operations for the Las Vegas Loop at the Boring Company, Musk’s tunnel-building operation, is also at the OPM as a senior adviser to the director. (Steve Davis, the CEO of the Boring Company, is rumored to be advising Musk on cuts to be made via DOGE and was integral in Musk’s gutting of Twitter, now X, after his takeover of the company in 2022.)
According to the same sources, other people at the top of the new OPM food chain include two people with apparent software engineering backgrounds, whom WIRED is not naming because of their ages. One, a senior adviser to the director, is a 21-year-old whose online résumé touts his work for Palantir, the government contractor and analytics firm cofounded by billionaire Peter Thiel, who is its chair. (The former CEO of PayPal and a longtime Musk associate, Thiel is a Trump supporter who helped bankroll the 2022 Senate campaign of his protégé, Vice President JD Vance.) The other, who reports directly to Scales, graduated from high school in 2024, according to a mirrored copy of an online résumé and his high school’s student magazine; he lists jobs as a camp counselor and a bicycle mechanic among his professional experiences, as well as a summer role at Neuralink, Musk’s brain-computer interface company.
Among the new highers-up at the OPM is Noah Peters, an attorney whose LinkedIn boasts of his work in litigation representing the National Rifle Association and who has written for right-wing outlets like the Daily Caller and the Federalist; he is also now a senior adviser to the director. According to metadata associated with a file on the OPM website, Peters authored a January 27 memo that went out under acting OPM director Charles Ezell’s name describing how the department would be implementing one of Trump’s executive orders, “Restoring Accountability to Policy-Influencing Positions Within the Federal Workforce.” This has to do with what’s sometimes known as Schedule F—a plan to recategorize many civil service jobs as political appointees, meaning they would be tied to the specific agenda of an administration rather than viewed as career government workers. The order would essentially allow for certain career civil servants to be removed in favor of Trump loyalists by classifying them as political appointees, a key part of the Project 2025 plan for remaking the government.
“I think on the tech side, the concern is potentially the use of AI to try and engage in large-scale searches of people's job descriptions to try and identify who would be identified for Schedule F reclassification,” says Moynihan.
Other top political appointees include McLaurine Pinover, a former communications director for Republican congressman Joe Wilson and deputy communications director for Republican congressman Michael McCaul, and Joanna Wischer, a Trump campaign speechwriter.
“OPM is not a very politicized organization,” says Steven Kelman, a professor emeritus at Harvard’s John F. Kennedy School of Government. “My guess is that typically, in the past, there have been only one or maybe two political appointees in all of OPM. All the rest are career. So this seems like a very political heavy presence in an organization that is not very political.”
Another OPM memo, concerning the government’s new return-to-office mandate, appears, according to metadata, also to have been authored by someone other than Ezell: James Sherk, previously at the America First Policy Institute and author of an op-ed advocating for the president to be able to fire bureaucrats. Formerly a special assistant to the president during Trump’s first term, he is now a part of the White House Domestic Policy Council.
The return-to-office policy, according to the November Wall Street Journal op-ed authored by Musk and Vivek Ramaswamy, is explicitly geared toward forcing the attrition of federal employees.
Last week, many federal workers received test emails from the email address [email protected]. In a lawsuit filed last night, plaintiffs allege that a new email list started by the Trump administration may be compromising the data of federal employees.
“At a broadest level, the concern is that technologists are playing a role to monitor employees and to target those who will be downsized,” says Moynihan. “It is difficult in the federal government to actually evaluate who is performing well or performing poorly. So doing it on some sort of mass automated scale where you think using some sort of data analysis or AI would automate that process, I think, is an invitation to make errors.”
Last week, federal employees across the government received emails encouraging them to turn in colleagues who they believed to be working on diversity, equity, inclusion, and access initiatives (DEIA) to the OPM via the email address [email protected].
“This reminded me,” says Kelman, “of the Soviet Stalinism of turning in your friends to the government.”
The OPM did not immediately respond to a request for comment, nor did the people whom sources say now sit atop the bureaucracy.
“I am not an alarmist person,” says Kelman. “I do think that some of the things being described here are very troubling.”
69 notes
·
View notes
Note
how do you feel about number 5. "Wait a Minute. Are you Jealous?" with Hank/Connor please?
Connor is buzzing.
He does not like this sensation, whatever it is. It sits uncomfortably tight in his chassis, humming hotly along his wires. He's searching through his programming in an attempt to identify it, but he seems to be ...lagging because of it.
Hank is standing with Captain Fowler and a woman Connor's scans tell him is from DPD Accounting. They appear to be old friends. Hank's head is tipped back as he laughs, loud and deep and not giving a single fuck.
The way he laughs when Connor gets a joke right. The way Hank laughs for Connor, sometimes.
"Wait a minute," someone says, and Connor is severely lagging if Gavin Reed has gotten this close without notification. "Your blinker's basically spinning green."
Connor does not want to take his eyes off of Hank.
"It's okay, tin can," Reed adds, with that awful gesture he calls a wink. "She's married."
Connor -- frowns. What is Reed talking about? Why would marital status be any kind of relevant issue? Hank is laughing again and there is another hot flare of emotion fizzing through his software.
"I don't believe you're jealous," Reed tosses out as he walks away. "Guess you can't program taste."
Jealous?
The search through his emotional integration software ends with an abrupt ping, and -- a number of things suddenly make sense to Connor that he hadn't realized before.
11 notes
·
View notes
Text
Impact Event | chapter 5 sneak peek #3
(In their shared mindscape. Sunrise is the OG Sun, and Sunny is Solar's brother. Currently inhabiting the same shell under duress.)
Sunny sighed, the fight leaving him in a slump of shoulders and spine, “I’m so sorry, Sunrise.”
“No, don't be,” said Sunrise, reaching out to tip Sunny’s chin up, “You didn’t do anything wrong.”
“I didn’t know what my Moon was capable of,” mumbled Sunny miserably, “I… no, that’s not true. I did know. Or I suspected, at least. But I never thought he’d actually hurt my Eclipse, not when he knew I thought of him as family too. I should've known. God, I let Eclipse down so badly.”
“That genius moron loves you to the ends of the earth,” insisted Sun, smothering the urge to wince as pressure tugged at the edges of his AI. He felt spread thin, somehow, pulled and stretched in too many directions. “He—nngh—misses you so much. He blames himself for what happened to you.”
“It wasn’t his fault, it was an accident!” cried Sunny, before his face creased into a reluctant, rueful smile, “But blaming himself sounds just like him." He scrubbed a few more oily tears from his cheeks. "I’m not complaining, but how are you even talking to me? Shouldn’t maintenance mode have shut you down?”
It was Sun’s turn to huff a weary grin. “Yeah, your Moon definitely meant for you to never find out. But it's not my first rodeo, I’m an expert in fighting for control. My Eclipse and I didn’t get on. Not that it’s easy, it feEEEEEE—"
The pressure turned to pain and then panic. Sunrise's outline glitched and errored out, warping to impossible neon colour and flashing, ceasing, then re-solidifying to gold and metal edges.
“Sunrise!” called Sunny frantically, “What’s wrong? What’s—what’s happening?”
WARNING. WARNING. WARNING.
HIGH CPU USAGE. BATTERY DISCHARGE. OVERHEAT RISK. SOFTWARE INTEGRITY COMPROMISED. STUTTER/CRASH RISK HIGH.
WARNING. WARNING. WARNING.
RECOMMENDATIONS: NOTIFY PARTS & SERVICES. EMERGENCY SHUTDOWN.
YES/NO?
Frantically, Sunny pushed an adamant NO through their systems, helpless to do anything except cling to Sunrise as his glitching form settled and slumped, coughing and sucking air he didn’t need. “Sunrise? Sunrise, talk to me, I'm here, I've got you. What’s wrong? What can I do?”
Patting himself down, confirming he was still here and still whole, Sunrise blew out a phantom breath. “I... wow, that sucked. I’m okay. I think.”
“Good. Are you in pain?”
“No.”
“Fibber.”
“Maybe a bit.”
Sunny shook his head on huffing, helpless chitter. "That was scary. What was that? What happened to you?"
Sitting up slowly, Sunrise fixed Sunny with a heavy stare.
“I can’t be sure, but... I think both our AIs running at the same time is maxing us out. And you’re still pretty broken. I'm literally holding our systems together, and I’m not going to be able to do it forever. I, uh… I actually think we’re working with a whole lot less time than we thought. We need to figure out how to get out of this dimension and get help, right now. Before... before something breaks permanently.”
(Impact Event on AO3 here.)
#tsams celestial phenomena#tsams impact event#tsams solar#tsams sun#tsams sun x solar#tsams solar x sun#fic sneak peek#sun and moon show#the sun and moon show#tsams#tsams solar's moon#tsams styx#tsams solar's sun#tsams sunny#happy ending incoming but it has to be earned
26 notes
·
View notes
Text
Four years ago, I asserted that we can “never again” allow an election like 2020 to happen. I’m back to say that despite Trump’s near landslide, America’s election system is still broken.
And the time to fix it is immediately, while President Trump has the wind at his back with a Republican Congress and the public on his side.
You most clearly see a broken election system when the margins are extremely tight. We saw it in 2020 when approximately 40,000 votes in key states tipped the election, and not so much in 2024. But rest assured, the public still lacks confidence in the integrity of our elections, and rightly so. They are only partially transparent. The tools to cheat are still on the table and able to be used. This is a ticking time bomb that could throw America into chaos in a future close election.
The main problems are ridiculously extended voting periods, mass absentee ballots, lack of voter ID, flimsy signature verification, unsecured drop boxes, voting machines with opaque software and connectivity to the internet, and sloppy, inaccurate voter rolls. We wouldn’t accept any of these third-world standards in our personal banking or accounting practices — why are we OK applying them to our precious votes?
16 notes
·
View notes
Text
The Importance of Event Photography: Capturing Moments That Matter

Event photography plays a crucial role in documenting significant occasions, from corporate gatherings to weddings and birthday celebrations. A skilled event photographer not only captures the highlights but also preserves the emotions and atmosphere of the day, creating lasting memories for clients. In this blog, we will delve into what event photography entails, the benefits of hiring a professional, tips for selecting the right photographer, and frequently asked questions.
What is Event Photography?
Event photography refers to the practice of capturing images during events, whether they are personal celebrations like birthdays and weddings or corporate functions such as product launches and conferences. This type of photography requires a blend of technical skill and an artistic eye to document candid moments, posed portraits, and the overall ambiance of the occasion.
Key Features of Event Photography
Candid Shots: One of the hallmarks of event photography is the ability to capture spontaneous moments. A good photographer will blend into the background, allowing guests to interact naturally, which results in genuine expressions and emotions.
Formal Portraits: In addition to candid shots, many events require posed photographs. Whether it’s a couple at their wedding or a team at a corporate gathering, formal portraits play a significant role in preserving memories.
Details and Decor: Professional event photographers pay attention to the little details that make an event special. This includes decorations, table settings, and other elements that contribute to the overall theme and atmosphere.
Why Hire a Professional Event Photographer?
While it might be tempting to ask a friend or family member to take pictures during an event, hiring a professional comes with numerous benefits:
Expertise and Experience
Professional photographers have extensive experience in capturing various types of events. They understand how to manage lighting, composition, and angles to ensure the best possible shots. With their expertise, you can trust that they will deliver high-quality images that meet your expectations.
High-Quality Equipment
Professionals invest in top-of-the-line cameras and lenses to achieve superior image quality. This equipment is essential for capturing moments in different lighting conditions, ensuring that every photograph is sharp and vibrant.
Post-Processing Skills
Editing is an integral part of photography. Professionals have the skills and software necessary to enhance images, ensuring they look polished and visually appealing. This can include color correction, retouching, and creating a cohesive style that reflects your event.
Time-Saving
Hiring a photographer allows you to focus on enjoying the event rather than worrying about capturing it. A skilled photographer knows what to look for and can document moments without interrupting the flow of the event.
How to Choose the Right Event Photographer
Selecting the right event photographer can make a significant difference in the outcome of your photos. Here are some tips to consider:
Review Portfolios
Before hiring a photographer, review their portfolio to assess their style and expertise. Look for consistency in their work and ensure that their style aligns with your vision for the event.
Read Reviews and Testimonials
Client reviews can provide valuable insights into a photographer’s professionalism, reliability, and ability to deliver quality work. Check their website and social media for testimonials from previous clients.
Discuss Your Vision
Schedule a consultation with potential photographers to discuss your vision for the event. Be clear about your expectations, preferred styles, and any specific moments you want to capture. This will help the photographer understand your needs and deliver results that align with your vision.
Understand Pricing and Packages
Different photographers offer various pricing structures and packages. Ensure you understand what’s included, such as the number of hours of coverage, the number of edited images, and whether prints are available. Compare different options to find the best fit for your budget.
The Role of JAGstudios as an Event Photographer
At JAGstudios, we take pride in being a leading photographer for events. We recognize the significance of every moment and strive to capture each detail beautifully. Our approach seamlessly blends professionalism with a personal touch, ensuring that your event is not only memorable in your mind but also immortalized in stunning photographs. As a dedicated JAGstudios photographer for events, we cater to various occasions, whether it’s a wedding, corporate gathering, or milestone celebration. Our commitment is to provide exceptional photography services that go above and beyond your expectations.
Conclusion
Event photography is a vital aspect of commemorating life’s special moments. By hiring a professional photographer, you can ensure that every detail, emotion, and memory is preserved in stunning images. Whether you’re planning a wedding, corporate event, or family gathering, the right photographer can make all the difference. For those seeking high-quality event photography, consider JAGstudios for your next occasion. Our commitment to excellence will help you cherish your memories for years to come.
Frequently Asked Questions
What types of events can a photographer cover?
A professional event photographer can cover a wide range of events, including weddings, corporate functions, birthday parties, family reunions, and more.
How much should I expect to pay for event photography?
Pricing can vary significantly depending on the photographer's experience, location, and the complexity of the event. It’s essential to discuss your budget and understand what services are included in the package.
How long will it take to receive my photos?
Typically, photographers take anywhere from a few days to several weeks to deliver edited images. This timeline can vary based on the photographer’s workload and the number of photos taken.
Can I request specific shots?
Yes! Most photographers welcome input from clients and will work with you to ensure that specific moments or details are captured during the event.
Why should I hire JAGstudios for my event photography?
At JAGstudios, we specialize in capturing the essence of your events with our unique style and professional approach. Our experienced team is dedicated to providing stunning images that you'll treasure for years to come.
7 notes
·
View notes
Text
Leveraging XML Data Interface for IPTV EPG
This blog explores the significance of optimizing the XML Data Interface and XMLTV schedule EPG for IPTV. It emphasizes the importance of EPG in IPTV, preparation steps, installation, configuration, file updates, customization, error handling, and advanced tips.
The focus is on enhancing user experience, content delivery, and securing IPTV setups. The comprehensive guide aims to empower IPTV providers and tech enthusiasts to leverage the full potential of XMLTV and EPG technologies.
1. Overview of the Context:
The context focuses on the significance of optimizing the XML Data Interface and leveraging the latest XMLTV schedule EPG (Electronic Program Guide) for IPTV (Internet Protocol Television) providers. L&E Solutions emphasizes the importance of enhancing user experience and content delivery by effectively managing and distributing EPG information.
This guide delves into detailed steps on installing and configuring XMLTV to work with IPTV, automating XMLTV file updates, customizing EPG data, resolving common errors, and deploying advanced tips and tricks to maximize the utility of the system.
2. Key Themes and Details:
The Importance of EPG in IPTV: The EPG plays a vital role in enhancing viewer experience by providing a comprehensive overview of available content and facilitating easy navigation through channels and programs. It allows users to plan their viewing by showing detailed schedules of upcoming shows, episode descriptions, and broadcasting times.
Preparation: Gathering Necessary Resources: The article highlights the importance of gathering required software and hardware, such as XMLTV software, EPG management tools, reliable computer, internet connection, and additional utilities to ensure smooth setup and operation of XMLTV for IPTV.
Installing XMLTV: Detailed step-by-step instructions are provided for installing XMLTV on different operating systems, including Windows, Mac OS X, and Linux (Debian-based systems), ensuring efficient management and utilization of TV listings for IPTV setups.
Configuring XMLTV to Work with IPTV: The article emphasizes the correct configuration of M3U links and EPG URLs to seamlessly integrate XMLTV with IPTV systems, providing accurate and timely broadcasting information.
3. Customization and Automation:
Automating XMLTV File Updates: The importance of automating XMLTV file updates for maintaining an updated EPG is highlighted, with detailed instructions on using cron jobs and scheduled tasks.
Customizing Your EPG Data: The article explores advanced XMLTV configuration options and leveraging third-party services for enhanced EPG data to improve the viewer's experience.
Handling and Resolving Errors: Common issues related to XMLTV and IPTV systems are discussed, along with their solutions, and methods for debugging XMLTV output are outlined.
Advanced Tips and Tricks: The article provides advanced tips and tricks for optimizing EPG performance and securing IPTV setups, such as leveraging caching mechanisms, utilizing efficient data parsing tools, and securing authentication methods.
The conclusion emphasizes the pivotal enhancement of IPTV services through the synergy between the XML Data Interface and XMLTV Guide EPG, offering a robust framework for delivering engaging and easily accessible content. It also encourages continual enrichment of knowledge and utilization of innovative tools to stay at the forefront of IPTV technology.
3. Language and Structure:
The article is written in English and follows a structured approach, providing detailed explanations, step-by-step instructions, and actionable insights to guide IPTV providers, developers, and tech enthusiasts in leveraging the full potential of XMLTV and EPG technologies.
The conclusion emphasizes the pivotal role of the XML Data Interface and XMLTV Guide EPG in enhancing IPTV services to find more information and innovative tools. It serves as a call to action for IPTV providers, developers, and enthusiasts to explore the sophisticated capabilities of XMLTV and EPG technologies for delivering unparalleled content viewing experiences.
youtube
7 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text

Effective XMLTV EPG Solutions for VR & CGI Use
Effective XMLTV EPG Guide Solutions and Techniques for VR and CGI Adoption. In today’s fast-paced digital landscape, effective xml data epg guide solutions are essential for enhancing user experiences in virtual reality (VR) and computer-generated imagery (CGI).
Understanding how to implement these solutions not only improves content delivery but also boosts viewer engagement.
This post will explore practical techniques and strategies to optimize XMLTV EPG guides, making them more compatible with VR and CGI technologies.
Proven XMLTV EPG Strategies for VR and CGI Success
Several other organizations have successfully integrated VR CGI into their training and operational processes.
For example, Vodafone has recreated their UK Pavilion in VR to enhance employee training on presentation skills, complete with AI-powered feedback and progress tracking.
Similarly, Johnson & Johnson has developed VR simulations for training surgeons on complex medical procedures, significantly improving learning outcomes compared to traditional methods. These instances highlight the scalability and effectiveness of VR CGI in creating detailed, interactive training environments across different industries.
Challenges and Solutions in Adopting VR CGI Technology
Adopting Virtual Reality (VR) and Computer-Generated Imagery (CGI) technologies presents a set of unique challenges that can impede their integration into XMLTV technology blogs.
One of the primary barriers is the significant upfront cost associated with 3D content creation. Capturing real-world objects and converting them into detailed 3D models requires substantial investment, which can be prohibitive for many content creators.
Additionally, the complexity of developing VR and AR software involves specialized skills and resources, further escalating the costs and complicating the deployment process.
Hardware Dependencies and User Experience Issues
Most AR/VR experiences hinge heavily on the capabilities of the hardware used. Current devices often have a limited field of view, typically around 90 degrees, which can detract from the immersive experience that is central to VR's appeal.
Moreover, these devices, including the most popular VR headsets, are frequently tethered, restricting user movement and impacting the natural flow of interaction.
Usability issues such as bulky, uncomfortable headsets and the high-power consumption of AR/VR devices add layers of complexity to user adoption.
For many first-time users, the initial experience can be daunting, with motion sickness and headaches being common complaints. These factors collectively pose significant hurdles to the widespread acceptance and enjoyment of VR and AR technologies.

Solutions and Forward-Looking Strategies
Despite these hurdles, there are effective solutions and techniques for overcoming many of the barriers to VR and CGI adoption.
Companies such as VPL Research is one of the first pioneer in the creation of developed and sold virtual reality products.
For example, improving the design and aesthetics of VR technology may boost their attractiveness and comfort, increasing user engagement.
Furthermore, technological developments are likely to cut costs over time, making VR and AR more accessible.
Strategic relationships with tech titans like Apple, Google, Facebook, and Microsoft, which are always inventing in AR, can help to improve xmltv guide epg for iptv blog experiences.
Virtual Reality (VR) and Computer-Generated Imagery (CGI) hold incredible potential for various industries, but many face challenges in adopting these technologies.
Understanding the effective solutions and techniques for overcoming barriers to VR and CGI adoption is crucial for companies looking to innovate.
Practical Tips for Content Creators
To optimize the integration of VR and CGI technologies in xmltv epg blogs, content creators should consider the following practical tips:
Performance Analysis
Profiling Tools: Utilize tools like Unity Editor's Profiler and Oculus' Performance Head Hub Display to monitor VR application performance. These tools help in identifying and addressing performance bottlenecks.
Custom FPS Scripts: Implement custom scripts to track frames per second in real-time, allowing for immediate adjustments and optimization.
Optimization Techniques
3D Model Optimization: Reduce the triangle count and use similar materials across models to decrease rendering time.
Lighting and Shadows: Convert real-time lights to baked or mixed and utilize Reflection and Light Probes to enhance visual quality without compromising performance.
Camera Settings: Optimize camera settings by adjusting the far plane distance and enabling features like Frustum and Occlusion Culling.
Building and Testing
Platform-Specific Builds: Ensure that the VR application is built and tested on intended platforms, such as desktop or Android, to guarantee optimal performance across different devices.
Iterative Testing: Regularly test new builds to identify any issues early in the development process, allowing for smoother final deployments.
By adhering to these guidelines, creators can enhance the immersive experience of their XMLTV blogs, making them more engaging and effective in delivering content.
Want to learn more? You can hop over to this website to have a clear insights into how to elevate your multimedia projects and provide seamless access to EPG channels.
youtube
7 notes
·
View notes
Text
the youtube ad: may i interest you in the latest of business ventures? broaden your viewpoint and invest in profit margins: we are revolutionizing the sector with turn-of-the-century research at the tip of your fingers thanks to cloud-based AI-powered large-scale decentralized databases! purchase our premium software with priority service level agreements and around-the-clock support, long term service upgrades and pay-what-you-want, freemium alternatives all integrated in our ecosystem to maximize productivity and interconnectivity and make use of our versioning and bundling offers! better yet - let us tailor our services to your needs with our elite golden platinum diamond upgrade, or make use of our enterprise solution!
me, who took off their headphones and was playing clash royale on the phone: yurr. evo mortar
2 notes
·
View notes