#POS System Implementation
Explore tagged Tumblr posts
Text
POS Implementation
POS Implementation: A Comprehensive Guide
In today’s fast-paced retail and service environments, implementing a Point of Sale (POS) system can significantly streamline operations, enhance customer experience, and improve overall efficiency. Whether you’re upgrading from a traditional cash register or installing your first POS system, proper implementation is crucial to maximizing its benefits. This guide will walk you through the essential steps of POS implementation.
Step 1: Identify Business Needs
Before selecting a POS system, assessing your business requirements is important. Consider the following:
The size and type of your business.
Specific features you need (e.g., inventory tracking, customer loyalty programs).
Budget constraints.
Integration requirements with existing software and hardware.
Step 2: Choose the Right POS System
Not all POS systems are created equal. Here’s how to select one that fits your needs:
Research and compare various providers.
Look for scalability to accommodate future growth.
Ensure it supports multiple payment methods.
Check reviews and testimonials from similar businesses.
Step 3: Hardware and Software Setup
A POS system consists of hardware (like barcode scanners, receipt printers, and card readers) and software. Ensure you:
Acquire hardware compatible with your chosen POS software.
Install and configure the software according to your operational needs.
Test all components to ensure they work seamlessly together.
Step 4: Data Migration
If you’re transitioning from an older system, data migration is a critical step:
Back up your existing data.
Transfer inventory, sales history, and customer information to the new system.
Verify the accuracy of migrated data.
Step 5: Employee Training
Proper training ensures your team can effectively use the POS system:
Organize hands-on training sessions.
Provide user manuals and support materials.
Address common troubleshooting scenarios.
Step 6: Pilot Testing
Before full-scale implementation, conduct a pilot test:
Use the system in a controlled environment.
Monitor for any issues or inefficiencies.
Gather feedback from staff and customers.
Step 7: Go Live
Once testing is complete, it’s time to roll out the system:
Schedule the launch during a low-traffic period to minimize disruptions.
Ensure on-site support is available for the initial days.
Communicate the change to your team and customers.
Step 8: Monitor and Optimize
Implementation doesn’t end with the launch. Regular monitoring is essential:
Analyze performance metrics (e.g., transaction times, error rates).
Update the system as needed to fix bugs and improve features.
Seek ongoing feedback from employees and customers.
Conclusion
Implementing a POS system is an investment in your business's future. With proper planning and execution, it can simplify daily operations, enhance customer satisfaction, and drive growth. By following the steps outlined above, you can ensure a smooth and successful implementation.
#POS System Implementation#Point of Sale Guide#Retail Technology#Business Efficiency#POS Hardware and Software#Data Migration Tips#Employee Training for POS#Pilot Testing POS#POS System Optimization#Small Business Solutions#Inventory Management#Customer Loyalty Programs#Payment Integration#Retail Operations#Streamlining Business Processes
0 notes
Text
Why Kuwaiti Businesses Are Choosing Odoo for Their ERP Needs

Kuwait’s economy is thriving, with businesses across industries like oil and gas, retail, logistics, and finance embracing digital transformation to stay competitive. In this fast-paced landscape, Enterprise Resource Planning (ERP) systems have become indispensable tools for growth. Among the solutions gaining traction, Odoo ERP is a favorite for Kuwaiti businesses.
But why? At Centrix Plus, Kuwait’s trusted partner for Odoo implementation and customization, we’ve witnessed firsthand how this open-source platform is revolutionizing local operations. Here’s why Kuwaiti companies are making the switch to Odoo.
1. Cost-Effective Flexibility for Growing Businesses
Kuwaiti SMEs and large enterprises alike prioritize solutions that deliver value without breaking the bank. Odoo’s modular structure allows businesses to start with essential apps (like accounting, inventory, or CRM) and scale up as needed. Unlike rigid, pre-packaged ERP systems, Odoo’s pay-as-you-grow model aligns perfectly with Kuwait’s dynamic market, where agility is key.
Centrix Plus Insight:We’ve helped Kuwaiti startups and conglomerates customize Odoo modules to fit their budgets, eliminating the need for costly overhauls down the line.
2. Local Compliance Made Simple
Kuwait’s regulatory environment demands precision, including VAT and financial reporting standards. Odoo’s localization features for the Middle East ensure compliance with Kuwaiti laws, from Arabic-language interfaces to automated tax calculations.
Did You Know?Centrix Plus offers Kuwait-specific Odoo customizations, such as Zakat reporting and integration with local banking systems, ensuring seamless adherence to regional requirements.
3. Scalability to Match Kuwait’s Ambitions
With Kuwait Vision 2035 driving economic diversification, businesses need ERP systems that grow with their goals. Odoo’s cloud-based infrastructure supports scalability, whether a company is expanding its warehouse in Shuwaikh or launching an e-commerce platform across the GCC.
Real-World Example:A Kuwaiti logistics firm partnered with Centrix Plus to implement Odoo’s fleet management and route optimization modules. Within months, they reduced delivery times by 30% and scaled operations to serve Saudi Arabia and the UAE.
4. Seamless Integration with Existing Tools
Many Kuwaiti businesses rely on legacy software or niche tools for industry-specific tasks. Odoo’s open-source API allows effortless integration with third-party systems, from government portals to custom POS setups in Kuwaiti retail stores.
Centrix Plus Advantage:Our developers specialize in bridging Odoo with Kuwait’s most-used platforms, ensuring minimal disruption during implementation.
5. Unmatched Customization for Kuwait’s Unique Needs
Kuwait’s market has distinct challenges, from managing seasonal demand during Ramadan to handling complex supply chains. Odoo’s flexible framework lets businesses tailor workflows to their exact needs.
Case in Point:A Kuwaiti construction company used Centrix Plus to build a custom Odoo module for project cost tracking, slashing budget overruns by 22% and improving stakeholder transparency.
Why Centrix Plus is Kuwait’s Go-To Odoo Partner
While Odoo’s benefits are clear, successful implementation requires local expertise. Here’s how Centrix Plus empowers Kuwaiti businesses:
In-Depth Regional Knowledge: We understand Kuwait’s business culture, regulations, and pain points.
24/7 Arabic/English Support: From Salmiya to Jahra, our team provides round-the-clock assistance.
Industry-Specific Solutions: Tailored Odoo setups for healthcare, trading, manufacturing, and more.
Post-Implementation Training: We ensure your team maximizes Odoo’s potential.
The Future of ERP in Kuwait Starts with Odoo
Kuwait’s businesses are no longer settling for one-size-fits-all ERP systems. With Odoo’s adaptability, cost efficiency, and localization strengths—paired with Centrix Plus’s expertise—companies are future-proofing their operations while staying rooted in Kuwait’s unique market demands.
Ready to Join the Odoo Revolution?
Contact Centrix Plus today to schedule a free consultation. Let us show you how Odoo can streamline your workflows, boost profitability, and position your business as a leader in Kuwait’s digital economy.
#Odoo ERP Kuwait#Best ERP Software Kuwait#Odoo Implementation Services Kuwait#Affordable ERP Solutions Kuwait#Top Odoo Partner Kuwait#Custom Odoo Development Kuwait#Odoo Accounting Software Kuwait#Odoo Inventory Management Kuwait#Kuwait VAT Compliance Odoo#Odoo Cloud Hosting Kuwait#Odoo Training and Support Kuwait#Arabic Odoo ERP Kuwait#Odoo for SMEs in Kuwait#Odoo POS System Kuwait#Odoo HR Module Kuwait
0 notes
Text
i think i'm too tired to work much on my image viewer build tonight but i'll try in the morning
#have been so slow#thought i'd finish this in 24hrs#need to quickly implement the json formatting/bounding box display and user interactions with file update#and i think that's mostly it? outside of multiple select and maybe some color based speaker display system#then of course need to write the whole ocr backend lol#which is coming out to maybe be training-own-model extent of nightmare#depending on how nicely it plays with furigana#and if it does play nicely with furigana then i need to implement a whole second stage of string analysis#doing some 2d math to combine bounding boxes to display nicely for the viewer i guess#and associating the relevant furiganas#which in json i guess i can just store as an array of kanji char pos len and associated furigana in the recognized line
0 notes
Text

Boosting Customer Satisfaction - Intelligent ERP for Retail Industry :
Gainz Retail ERP Software – A Feature Rich Solutions
B2B and B2C ERP Solution for Retail Industry
Integrated Omnichannel Business Solution
In Store Point of Sale (POS) and MPOS
Secure Integrated E-Commerce with Payment Gateway
Responsive Website built with Bootstrap 5 and ASP.NET
CRM and Digital Marketing Tools.
Real-time Order and Inventory
Multi-Warehousing and 3PL Fulfillment
HR & Payroll
Integrated Accurate Accounting
Cost-effective and Flexible Pay-As-You-Go SaaS Model
Resilient Offline Capability and Intelligent Data Synchronization
#cloud erp#erp for small business#erp implementation#erp software#erp#erpcompany#erpdevelopment#erpsolutions#canada#sap erp#retail pos solutions#retail pos system software#cloud retail erp software#retail#retail pos software#retail business#retail erp software#retail store#retail sales#retail industry
1 note
·
View note
Text
Employees at the Social Security Administration (SSA) were informed on Thursday morning that new rules forbid them from accessing “general news” websites, including those that have been at the forefront of the reporting on Elon Musk’s so-called Department of Government Efficiency (DOGE) effort.
In an email reviewed by WIRED and addressed to “all SSA employees” from a mailing list called “internal communications,” the agency informed employees that it was “implementing additional restrictions to the categories of websites prohibited from government-furnished equipment. Effective today, March 6, 2025, the categories include: Online shopping; General News; and Sports.” The headline read “Internet Browsing from Government Equipment.”
The email did not specify which websites in particular were to be blocked. However, WIRED has confirmed with two sources inside the SSA that Wired.com is no longer accessible today, though it was accessible previously.
The sources also confirmed that the websites of The Washington Post, The New York Times, and MSNBC were inaccessible. However, the sources were able to access other news websites including Politico and Axios.
“Local news blocked,” says one source at SSA, who was granted anonymity over fears of retribution. “So if there was a local shooting or something, I wouldn’t be able to see.”
It’s unclear who has implemented the block list or what criteria were used to populate it, but it appears not to be based on ideological grounds, as Fox News and Breitbart are also blocked.
On Friday, weeks after DOGE engineers were installed at SSA, the agency announced plans to cut 7,000 employees. Many of the agency’s most senior staff have resigned. This includes former SSA commissioner Michelle King, who has decades of experience within the agency. She was replaced by acting commissioner Leland Dudek, a mid-level staffer who claimed in a LinkedIn post, reviewed by WIRED, that he had been punished by King for helping DOGE engineers when they first arrived. Musk and Donald Trump have also continued to push the conspiracy theory that millions of dead people are continuing to collect social security benefits, despite the fact those claims have been debunked.
In the hours after the initial email was sent about blocking news sites, some employees received another email from their managers providing instructions on how to disable news showing up on the Edge landing page. This was not a requirement but a recommendation to help employees resist the temptation to click on news links, a source who had received the email told WIRED.
Those trying to visit Wired.com were greeted with a page replicating much of what was in the initial email. It also listed a “URL Reputiation” score, though it was unclear where that score was being sourced from, or if it has a bearing on site access. Different blocked news websites were given different scores, according to screenshots viewed by WIRED.
SSA employees typically use computers with Microsoft’s Edge installed as the internet browser. The default landing page on that browser is set to show news headlines, according to several sources at SSA.
“Employees with a legitimate business [sic] should submit an exception SAM request for their supervisor's review,” the email continued. “These additional restrictions will help reduce risk and better protect the sensitive information entrusted to us in our many systems.”
On Reddit, multiple members of the FedNews subreddit who said they worked at the SSA claimed that accessing news in a timely manner was an essential part of their job. Others pointed out that being able to make purchases online was a core component of their work.
After this article was published, an SSA spokesperson told WIRED that it implemented the restrictions because “employees should be focused on mission-critical work and serving the American people.”
It did not respond to requests for comment on why some news websites were blocked and others were not.
Employees at several other US government agencies contacted by WIRED said similar blocks on news pages had not been implemented on their networks.
43 notes
·
View notes
Text

We have been debating tirelessly on different ways to abolish caste and other social evils which permeate the society that we have today. Raising voices against oppression, forming political parties and contesting in elections and also trying to force the government to form and implement policies which will give the Bahujans their fundamental rights. We have come a long way through decades of struggle in gaining rights, but the present political scenario of the country is not looking hopeful to the Bahujan aspirations for breaking away the shackles of caste.
With the diluting of labour laws and enabling state sanctioned exploitation of Bahujan labour, implementation of NEP which further marginalize the Bahujan children and extinguish their hopes of upward social and economic mobility, a proposed EIA which will rob the Bahujans and Adivasis of their land and livelihood, implementation of CAA and NRC to deprive the status of citizenship, privatization of key public utilities and destroying the already weakened public healthcare system, the government is openly showing its motives as a corporate stooge which dances to the whims of Adani, Ambani and other Brahmin Bania masters.
Armed with a grass roots organization like RSS and corporate funded media outlets, they have complete dominance in creating narratives they want the public to believe and they also have a well-oiled IT cell to spread fake news against any dissenters who dare to raise voice against them. Even though there are voices in the society which are raising against these government policies, there is a lack of grass root organization and common vision is sometimes lacking. This doesn’t mean that all the opposing forces against the fascist regime, which is murdering our democracy, should be centralized under one political entity. Instead it is time to think about exactly the opposite, the expansion of the idea of democracy from merely being a political tool used while casting vote once every 5 years to inculcating an idea of democracy in all aspects of life — political, social and economical and decentralization of all aspects of society.
Anarchism is a political philosophy which rejects all coercive and oppressive forms of hierarchy, be it caste, class, color, creed, clan, gender, age, orientation or country. It says that every system of power hierarchy should be scrutinized and made to justify its existence, and any system which fails to justify itself and is trampling the freedom of the individual will have to be abolished. The idea of questioning oppressive power structures is inherent to the idea of anarchism. It prohibits a system where even a party or a few leaders decide on how the society will function. Instead it focuses on decentralizing power to local bodies and communities so that decisions are made at the lowest level possible, thus eliminating the concentration of power into a few hands. It also shares the view that people who are most impacted by policies and decisions are the ones who are most capable of making them.
Historically, humans have developed to live in societies which didn’t have the kind of huge inequalities as it exists today. There is an intrinsic instinct to cooperate and help each other which is visible when a disaster strikes or the self-organization that appears out of nowhere in organic movements against oppression. Solidarity and mutual aid are the foundations of an anarchist society. The “right to well-being” of all human beings, meaning “the possibility of living like human beings, and of bringing up children to be members of a society better than ours” (Kropotkin, 1892). Two of the examples of societies which function close to anarchist principles today are Zapatistas of Mexico (Nacional, 2002) and Rojava in Syria (Democracy, 2018). Extreme corruption, colonization and environmental exploitation forced the indigenous people of Mexico to form an autonomous region where people directly form communities and decide the policies. Similarly, the people of Rojava, battered by the civil war, have formed an autonomous region with direct democratic ambitions based on an anarchist and libertarian socialist ideology promoting decentralization, gender equality, environmental sustainability and pluralistic tolerance for religious, cultural and political diversity based on democratic confederalism. One of the principles of direct democracy is that there are no elected representatives for a fixed term, any member who is elected will just be a spokesperson of the community and can be withdrawn immediately if he goes against the decision taken by discussion and deliberations. The means of production will be owned by workers and run by worker councils. Conflict resolution mechanism and alternative systems of judiciary exists within the community run by the members. There won’t be police or other systems which grant power to one person or group to take away the life and liberty of an individual, rather power will be distributed equally or rotationally which is controlled by the community. During the current times of BLM protests all over the world, it is clear that the police institution is just a tool employed by the ruling and propertied class to control the lower class and there is mass class for defunding the police and transferring the resources to community welfare projects.
We need to look at how these communities organize themselves in the face of an oppressive regime and come up with innovative ways to decentralize and create institutions which we are brainwashed to assume will work only if they are centralized. Decentralized community gardens provide food for the community which is maintained by them. Systems of education, community defense, criminal justice systems, industry and healthcare can be decentralized and we need to focus our efforts in building such grassroot level communities which function along the principles solidarity and mutual aid. We already have systems of mutual aid in our communities, all we need to do is to transfer these tendencies to all the systems we live by.
The Indian social mentality of following a leader or waiting for a savior needs to change. Any system which can consolidate power in the hands of the few can change into authoritarianism. Even if the leaders are benevolent and have the will to serve the people, there are systems of coercion which exist in our society, where economic, political and social power resides in the hands of the few, that they will bind the leaders from doing their duty to the Bahujans. The leaders and parties we look up to keep failing and disappointing us time and again. Now, action needs to be taken directly at grass root level by the Bahujans by creating communities and networks of solidarity and mutual aid and practicing decision making and direct participatory democracy. The culture of outsourcing decision making to politicians or other ruling class needs to stop. This has to start at all sectors of industry, agriculture and services too, and also within family.
We can’t turn to the state for protection anymore as it the state apparatus which is being systematically abused by the ruling castes to exploit Bahujan labour to create their wealth. Along with the efforts to educate Bahujans through social media and other means to sensitize them of their exploitation, effort needs to be focused at the bottom most level to inculcate the habit of participatory democracy at individual, family and community levels, respecting the liberty of the individual. The fight for annihilation of caste cannot be won, unless all unjust power structures in the society cease to exist and power is decentralized and distributed to the people directly, where individuals themselves can organize and make decisions about their life without being coerced or exploited to create wealth for others.
References
Democracy, N. (2018, July 6 ). The Communes of Rojava: A Model In Societal Self Direction. Retrieved from YouTube: https://www.youtube.com/watch?v=cDnenjIdnnE
Kropotkin, P. (1892). The Conquest of Bread. Paris.
Nacional, E. Z. ( 2002). A Zapatista Response to “The EZLN Is NOT Anarchist”. Retrieved from The Anarchist Library: https://theanarchistlibrary.org/library/ejercito-zapatista-de-liberacion-nacional-a-zapatista-response-to-the-ezln-is-not-anarchist
#desiblr#india#hinduism#caste#varna#caste system#dalit#dalit rights#desi#desi tumblr#indian#organization#revolution#anarchism#daily posts#communism#anti capitalist#anti capitalism#late stage capitalism#anarchy#anarchists#libraries#leftism#social issues#economy#economics#climate change#anarchy works#environmentalism#environment
20 notes
·
View notes
Text
Strategies for Reducing Food Waste in Restaurants
Food waste reduction is a real pressing issue that affects our planet and leads to substantial financial loss for companies, especially the restaurant sector. Around one-third of the food meant for human consumption produced globally every year goes to waste — approximately 1.3 billion tons, according to the Food and Agriculture Organization (FAO). For restaurants, this is both a challenge and an opportunity. Palate cleanser: It is possible for restaurants to save money while boosting their sustainability and appealing to eco-conscious consumers by implementing waste reduction strategies.
Understanding the Scope of Food Waste in Restaurants
Before we get into strategies, it’s crucial to understand where restaurants waste food and its impact. Food waste can be categorized into various stages in a restaurant’s operations:
Purchasing and Inventory Management:
Over-ordering of ingredients, imprecise forecasting, and poor storage practices are some of the main reasons behind spoilage and waste.
Food Preparation:
This phase encompasses waste generated during cutting, peeling and preparing food. Not every food scrap is usable, but most can serve a second life in stocks, sauces or composting.
Serving and Portioning:
Large portion sizes, failure to communicate menu items with customers, or simply not customizing portions to the customer’s taste can leave food on plates untouched.
Customer Waste:
Customers may waste food at the point of consumption. This is true, for example, in buffet- or family-style servings in which customers tend to get more than is actually necessary.
Post-consumption:
When food is left after consumption and is not given away or recycled, it is often thrown away.
The problem for the restaurants is how to deal with food waste minimization and at the same time accomplish the desired food quality and the satisfaction of the customers. It follows that devising and using sound approaches to food waste minimization is not only ecologically sound but makes business sense.
1. Improve Inventory Management
Efficient management of items in include Field Normalized Items Helped Level(s) – Include Level(s)/An Item Management for Efficient Use Minimization of Spaces (Etalons Inventory) – Allocate Appropriate Time Together with all Frequently Added by Users Items Ordered As The Components Eg Groceries Such Plus Da Foods or Beverages Such or Canned Soup
Best Practices for Inventory Management:
Use Data and Predictive Tools:
Identify historical surveys on targets in terms of demand Guess at the future need of a particular item with the support of the mandated technology. Consumption Pattern for A Particular Item And Its Successive Application to Estimate Future Requirement Minimum Order Quantity for Presales To Minimize Holding Cost of Revision Points of Sale POS Forecasts Data Driven Needs Analysis And Application.
First İn First Out (FIFO) System:
Ensure all older stocks are consumed before newer stock in circulation to achieve his or her aim of improving customer satisfaction that is through minimizing stock tremendous losses. Protect storage and telling peri with raw materials's less risk of spoilage such as.
Regular Stock Checks:
Undertake inventory management to avoid overordering of stock and establish how soon certain items can become obsolete and should be consumed. Maintaining ideal conditions of storage as well can help improve shelf life.
Optimize Supplier Relationships
Collaborate with suppliers to ensure that stock inventories are not rigid and changes can be made to meet market needs. Even some suppliers would also be willing to accept back some excess stock for the future use.
Designing the Menu with Portion and Food Control
In relation to food preparation and consumption, menu design is crucial as it creates an impact in food wastage minimization.
Designing a restaurant menu in particular should include the following strategies:
Flexible Portions:
Incentivise clients to self-determine the size of their portions, for instance the option to have a smaller portion, opt for a ‘half-plate’ and such. That effectively reduces the chances of food being returned to the kitchen uneaten by customers.
Prepare Leftovers:
Create a menu containing ingredients that are useful in the preparation of more than one dish. This way all the excess stock will not go to waste since it will be put to use in preparing other meals, thereby reducing wastage.
Create Specials Out of Wasted Ingredients:
Whenever you are in possession of perishable ingredients which are close to expiry, create specials featuring the ingredients instead. That way there is a reduction in wastage and at the same time there is possible use of the ingredients in making appealing dishes that are out of the ordinary.
Creative Use of Leftover Scraps:
With regards to carrot tops and beet, these can be used in salads or pestos, while bread ends can be made into croutons. There are also other ways to make use of food scraps by incorporating them into other food items for example, using vegetable peels.
Portion Control Techniques:
Use Standardized Recipes:
By setting a group of standardized recipes on how things should be done or sizes of food, more food wastes are controlled since food quality and portion control are ensured.
Train Staff in Proper Portioning:
Explain what are the reasons behind these measurements to the cooks and order them to implement such measures. When a portion is too big, it wastage occurs, even on a customer’s plate and inside the kitchen.
Offer Takeaway Options:
Retrieve food that could have been wasted. Rather than using an excuse of having no containers for takeout, truly make them offer. Tell your workers to explain the option of take out whenever people leave food on the table, which should not be the case at all.
3. Reduce Food Waste Through Repurposing and Recycling
This can easily be accomplished by using leftover food for example. If you have roast chicken from last night, there is absolutely no need to throw it out as it can be used to bake stocks. There are many ways to do this.
Repurposing Strategies:
Make Stocks and Sauces:
These are edibles which are deemed nay useless by quite a number of restaurants. Instead of discarding, leftovers should be combined with vegetable scraps and created behind to be used in gravies, sauces, which will reduce the amount of food waste by a considerable amount.
Composting:
Organic waste is often abused and thrown in the garbage, which shouldn’t be practiced. There is unused food which includes coffee grounds or fruit cores which can be composted, increasing its usage.
Food Donation:
Finding a local shelter, food bank or charity can be relied on which one can serve food beyond what one has to eat themselves, which is a positive way to nourish oneself while decreasing food waste.
Repurpose Day-Old Bread:
One of the most ideal ways to ensure food being wasted decreases is repurpose day old bread. Croutons, breadcrumbs, or even desserts like bread pudding can be made, which is a perfect way to ensure food which would have otherwise been thrown away.
5. Educate and Train Staff
Proper training and education are essential for any strategy to be effective in reducing food waste. Staff members should understand the importance of minimizing waste and be equipped with the knowledge to make changes in their daily routines.
Staff Training Tips:
Training Programs on Waste Reduction:
Organize regular training sessions focused on food waste awareness. Train staff on portion sizes, how to properly store food, and the importance of using food scraps creatively.
Encourage Communication:
Foster a culture where staff members feel comfortable discussing food waste with management. Encourage them to share ideas for reducing waste, as they often have valuable insights from the ground level.
Incentivize Waste Reduction:
Consider creating an incentive program that rewards staff for coming up with waste-reduction ideas or achieving certain waste-reduction goals.
6. Engage Customers in the Effort
Customers also play an integral role in reducing food waste. Engaging them in the process can not only help minimize waste but can also enhance their dining experience.
Customer Engagement Strategies:
Educate Customers on Food Waste:
Use your menu or signage in the restaurant to educate diners on the importance of food waste reduction. This could include messages about sourcing, composting efforts, or the benefits of ordering the right portion sizes.
Offer Leftover Boxes:
Encourage customers to take home leftovers by offering them the option of takeaway containers, particularly for large portions that may not be finished in one sitting.
Promote Sustainable Practices:
Offer discounts or incentives for customers who choose sustainable options, such as smaller portion sizes or plant-based meals, which generally have a lower environmental impact.
Showcase Waste-Reducing Practices:
Make your waste-reduction efforts a part of your brand identity. Let customers know about your sustainability initiatives, such as food donations or composting, which can enhance your restaurant’s appeal to eco-conscious diners.
Conclusion
Reducing food waste in restaurants requires a comprehensive and multi-disciplinary approach. This includes effective inventory management. Creating a thoughtful menu Creative use of ingredients use of technology Engaging employees and customers in waste reduction efforts To apply these strategies Restaurants not only have an impact on the environment... It also reduces, but the ability to make profits grows. Increase operational efficiency and strengthen your brand's reputation... The financial savings and sustainability benefits of reducing food waste are undeniable. And as consumers increasingly value environmental responsibility. Implementing these strategies can help restaurants stay competitive in an ever-evolving market. Ultimately, reducing food waste isn't just good for business, it's good for the planet.
3 notes
·
View notes
Note
Happy STS!! Can I request an infodump of Thiruneah? She sounds cool!
(also how do you track all your characters? Is it a spreadsheet or something?)
Yessss! Thank you! Thiruneah is probably one of my lore characters that even I still feel curious about!
As one of the three goddesses tgat emerged from The Might (the primordial force that made up the all of Existence) in the very beginning. She was the second of the three "sisters" to come into existence, after Eliltta (the goddess of life and creation) and before Nihynia (goddess of space, worlds, and dimensions.
Thiruneah is the goddess po time, and the one pillar of the Triple Balance that is always standing. The ever-flowing threads of time are conjured,c ontrolled, and protected by her.
Unlike her sisters who often went around to maintain life or the universes they've created, Thiruneah would basically never leave her domain at the center of Existence. She was the one who made sure time flowed as it was supposed to for every universe, world, person, etc.
Basically, she was one of the key reasons there's any order at all in Existence.
Of course, such a responsibility could cause someone to grow very strict and rigid, as Thiruneah is known to be the least lenient of all ten of the deities with crystald, as well as the kast to volunteer.
In that sense, Thiruneah is probably the epitome of a l"awful neutral" character, as she has a very strict moral code centeering around keeping tge balance abd order of the Existence togather, but also being unwilling to break those codes even if it means any hero or villain asks for help from her. She's a stable force of nature, strong and seemingly unchanging.
The most well-known myth about her in Interdimensional, is about her punishment of Arfene (goddess of magic) for implementing time as an element for some of her magic systems without asking for Thiruneah's permission. It's believed that Arfene had lived ten thousand years of mortal lives, reincarnating in a different world of Thiruneah's choosing every time she died.
She's also the deity who (albeit reluctantly) gave power for the Crystal Of Time, which Kent has in the main series, and later Alondra finds one of the missing pieces of. Time as a spellcasting element is banned by both BSA and Dark Crystal, which only three people at max are even permitted by Thiruneah to have the access to it in the first place (that being Kent, Wilfrid and in incredibly minor ways, Alondra), as it's considered one of the most dangerous elements a person can wield. Both that and everyone knows what the fact that happened when even a deity tried to use time nagic.
We will also see Thiruneah in both the Divine Trials Arc and the Time Travel Arc, which happen in and after year 8 respectively. However unlike Eliltta and Nihynia, Thiruneah doesn't have as large of an impact on the Legendaries, not because she can't, but because she chooses not to. Remember, what she watches over is far more than just the timeline of Eight Alters. She still does what's necessary for her to do but doesn't go further thsn that.
Lastly, in one of my side stories that I co-write with a friend (where we put our single characters through a fun matchmaking event, and trust me there are over three hundred of those characters-), Thiruneah is matched with an immortal fire elemental named Ignacius, who's among the most prominent vessels Lorkness (Beislar), making him one of the main antagonists in the series. I do know they will interact at least once in the main series too, but I'm not sure how it'll happen or how it'll go.
I hope this was enough infodumping about our lovely Lady Time. :)
As for how I keep track of my characters... I'm not 100% sure either. I do have three separate lists (one on my Notes app, one on my Character Story Planner, and one on Quotev), but none of the lists are complete, the one in my Notes app in particular having outdated names for many of the earlier characters I made. And none of the lists sp far include some of the important characters such as Iluthmil siblings, Keegan family members, Francis, Beatrice, Jarek, Roimata, Cassandra, or Aphelion.
Turns out I mostly keep them in my head and remember through their roles (as I used to always forget that Dark Crystal's main tech guy was a dwarf man named Gwydion with a grumpy grudge against Frank, until I gave him a proper role in the first Meras arc). But having an organized list does help, which I'm working on. I promise.😅
#writing#writeblr#creative writing#writers on tumblr#writer#my writing#my characters#original characters#time#writing community#writerscommunity#interdimensional series#gods and goddesses#time god#Thiruneah the goddess of time
2 notes
·
View notes
Text
Exploring Kerberos and its related attacks
Introduction
In the world of cybersecurity, authentication is the linchpin upon which secure communications and data access rely. Kerberos, a network authentication protocol developed by MIT, has played a pivotal role in securing networks, particularly in Microsoft Windows environments. In this in-depth exploration of Kerberos, we'll delve into its technical intricacies, vulnerabilities, and the countermeasures that can help organizations safeguard their systems.
Understanding Kerberos: The Fundamentals
At its core, Kerberos is designed to provide secure authentication for users and services over a non-secure network, such as the internet. It operates on the principle of "need-to-know," ensuring that only authenticated users can access specific resources. To grasp its inner workings, let's break down Kerberos into its key components:
1. Authentication Server (AS)
The AS is the initial point of contact for authentication. When a user requests access to a service, the AS verifies their identity and issues a Ticket Granting Ticket (TGT) if authentication is successful.
2. Ticket Granting Server (TGS)
Once a user has a TGT, they can request access to various services without re-entering their credentials. The TGS validates the TGT and issues a service ticket for the requested resource.
3. Realm
A realm in Kerberos represents a security domain. It defines a specific set of users, services, and authentication servers that share a common Kerberos database.
4. Service Principal
A service principal represents a network service (e.g., a file server or email server) within the realm. Each service principal has a unique encryption key.
Vulnerabilities in Kerberos
While Kerberos is a robust authentication protocol, it is not immune to vulnerabilities and attacks. Understanding these vulnerabilities is crucial for securing a network environment that relies on Kerberos for authentication.
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak user account settings. When a user's pre-authentication is disabled, an attacker can request a TGT for that user without presenting a password. They can then brute-force the TGT offline to obtain the user's plaintext password.
2. Pass-the-Ticket Attacks
In a Pass-the-Ticket attack, an attacker steals a TGT or service ticket and uses it to impersonate a legitimate user or service. This attack can lead to unauthorized access and privilege escalation.
3. Golden Ticket Attacks
A Golden Ticket attack allows an attacker to forge TGTs, granting them unrestricted access to the domain. To execute this attack, the attacker needs to compromise the Key Distribution Center (KDC) long-term secret key.
4. Silver Ticket Attacks
Silver Ticket attacks target specific services or resources. Attackers create forged service tickets to access a particular resource without having the user's password.
Technical Aspects and Formulas
To gain a deeper understanding of Kerberos and its related attacks, let's delve into some of the technical aspects and cryptographic formulas that underpin the protocol:
1. Kerberos Authentication Flow
The Kerberos authentication process involves several steps, including ticket requests, encryption, and decryption. It relies on various cryptographic algorithms, such as DES, AES, and HMAC.
2. Ticket Granting Ticket (TGT) Structure
A TGT typically consists of a user's identity, the requested service, a timestamp, and other information encrypted with the TGS's secret key. The TGT structure can be expressed as:
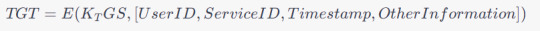
3. Encryption Keys
Kerberos relies on encryption keys generated during the authentication process. The user's password is typically used to derive these keys. The process involves key generation and hashing formulas.
Mitigating Kerberos Vulnerabilities
To protect against Kerberos-related vulnerabilities and attacks, organizations can implement several strategies and countermeasures:
1. Enforce Strong Password Policies
Strong password policies can mitigate attacks like AS-REP Roasting. Ensure that users create complex, difficult-to-guess passwords and consider enabling pre-authentication.
2. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This can thwart various Kerberos attacks.
3. Regularly Rotate Encryption Keys
Frequent rotation of encryption keys can limit an attacker's ability to use stolen tickets. Implement a key rotation policy and ensure it aligns with best practices.
4. Monitor and Audit Kerberos Traffic
Continuous monitoring and auditing of Kerberos traffic can help detect and respond to suspicious activities. Utilize security information and event management (SIEM) tools for this purpose.
5. Segment and Isolate Critical Systems
Isolating sensitive systems from less-trusted parts of the network can reduce the risk of lateral movement by attackers who compromise one system.
6. Patch and Update
Regularly update and patch your Kerberos implementation to mitigate known vulnerabilities and stay ahead of emerging threats.
4. Kerberos Encryption Algorithms
Kerberos employs various encryption algorithms to protect data during authentication and ticket issuance. Common cryptographic algorithms include:
DES (Data Encryption Standard): Historically used, but now considered weak due to its susceptibility to brute-force attacks.
3DES (Triple DES): An improvement over DES, it applies the DES encryption algorithm three times to enhance security.
AES (Advanced Encryption Standard): A strong symmetric encryption algorithm, widely used in modern Kerberos implementations for better security.
HMAC (Hash-based Message Authentication Code): Used for message integrity, HMAC ensures that messages have not been tampered with during transmission.
5. Key Distribution Center (KDC)
The KDC is the heart of the Kerberos authentication system. It consists of two components: the Authentication Server (AS) and the Ticket Granting Server (TGS). The AS handles initial authentication requests and issues TGTs, while the TGS validates these TGTs and issues service tickets. This separation of functions enhances security by minimizing exposure to attack vectors.
6. Salting and Nonces
To thwart replay attacks, Kerberos employs salting and nonces (random numbers). Salting involves appending a random value to a user's password before hashing, making it more resistant to dictionary attacks. Nonces are unique values generated for each authentication request to prevent replay attacks.
Now, let's delve into further Kerberos vulnerabilities and their technical aspects:
7. Ticket-Granting Ticket (TGT) Expiry Time
By default, TGTs have a relatively long expiry time, which can be exploited by attackers if they can intercept and reuse them. Administrators should consider reducing TGT lifetimes to mitigate this risk.
8. Ticket Granting Ticket Renewal
Kerberos allows TGT renewal without re-entering the password. While convenient, this feature can be abused by attackers if they manage to capture a TGT. Limiting the number of renewals or implementing MFA for renewals can help mitigate this risk.
9. Service Principal Name (SPN) Abuse
Attackers may exploit misconfigured SPNs to impersonate legitimate services. Regularly review and audit SPNs to ensure they are correctly associated with the intended services.
10. Kerberoasting
Kerberoasting is an attack where attackers target service accounts to obtain service tickets and attempt offline brute-force attacks to recover plaintext passwords. Robust password policies and regular rotation of service account passwords can help mitigate this risk.
11. Silver Ticket and Golden Ticket Attacks
To defend against Silver and Golden Ticket attacks, it's essential to implement strong password policies, limit privileges of service accounts, and monitor for suspicious behavior, such as unusual access patterns.
12. Kerberos Constrained Delegation
Kerberos Constrained Delegation allows a service to impersonate a user to access other services. Misconfigurations can lead to security vulnerabilities, so careful planning and configuration are essential.
Mitigation strategies to counter these vulnerabilities include:
13. Shorter Ticket Lifetimes
Reducing the lifespan of TGTs and service tickets limits the window of opportunity for attackers to misuse captured tickets.
14. Regular Password Changes
Frequent password changes for service accounts and users can thwart offline attacks and reduce the impact of credential compromise.
15. Least Privilege Principle
Implement the principle of least privilege for service accounts, limiting their access only to the resources they need, and monitor for unusual access patterns.
16. Logging and Monitoring
Comprehensive logging and real-time monitoring of Kerberos traffic can help identify and respond to suspicious activities, including repeated failed authentication attempts.
Kerberos Delegation: A Technical Deep Dive
1. Understanding Delegation in Kerberos
Kerberos delegation allows a service to act on behalf of a user to access other services without requiring the user to reauthenticate for each service. This capability enhances the efficiency and usability of networked applications, particularly in complex environments where multiple services need to interact on behalf of a user.
2. Types of Kerberos Delegation
Kerberos delegation can be categorized into two main types:
Constrained Delegation: This type of delegation restricts the services a service can access on behalf of a user. It allows administrators to specify which services a given service can impersonate for the user.
Unconstrained Delegation: In contrast, unconstrained delegation grants the service full delegation rights, enabling it to access any service on behalf of the user without restrictions. Unconstrained delegation poses higher security risks and is generally discouraged.
3. How Delegation Works
Here's a step-by-step breakdown of how delegation occurs within the Kerberos authentication process:
Initial Authentication: The user logs in and obtains a Ticket Granting Ticket (TGT) from the Authentication Server (AS).
Request to Access a Delegated Service: The user requests access to a service that supports delegation.
Service Ticket Request: The user's client requests a service ticket from the Ticket Granting Server (TGS) to access the delegated service. The TGS issues a service ticket for the delegated service and includes the user's TGT encrypted with the service's secret key.
Service Access: The user presents the service ticket to the delegated service. The service decrypts the ticket using its secret key and obtains the user's TGT.
Secondary Authentication: The delegated service can then use the user's TGT to authenticate to other services on behalf of the user without the user's direct involvement. This secondary authentication occurs transparently to the user.
4. Delegation and Impersonation
Kerberos delegation can be seen as a form of impersonation. The delegated service effectively impersonates the user to access other services. This impersonation is secure because the delegated service needs to present both the user's TGT and the service ticket for the delegated service, proving it has the user's explicit permission.
5. Delegation in Multi-Tier Applications
Kerberos delegation is particularly useful in multi-tier applications, where multiple services are involved in processing a user's request. It allows a front-end service to securely delegate authentication to a back-end service on behalf of the user.
6. Protocol Extensions for Delegation
Kerberos extensions, such as Service-for-User (S4U) extensions, enable a service to request service tickets on behalf of a user without needing the user's TGT. These extensions are valuable for cases where the delegated service cannot obtain the user's TGT directly.
7. Benefits of Kerberos Delegation
Efficiency: Delegation eliminates the need for the user to repeatedly authenticate to access multiple services, improving the user experience.
Security: Delegation is secure because it relies on Kerberos authentication and requires proper configuration to work effectively.
Scalability: Delegation is well-suited for complex environments with multiple services and tiers, enhancing scalability.
In this comprehensive exploration of Kerberos, we've covered a wide array of topics, from the fundamentals of its authentication process to advanced concepts like delegation.
Kerberos, as a network authentication protocol, forms the backbone of secure communication within organizations. Its core principles include the use of tickets, encryption, and a trusted third-party Authentication Server (AS) to ensure secure client-service interactions.
Security is a paramount concern in Kerberos. The protocol employs encryption, timestamps, and mutual authentication to guarantee that only authorized users gain access to network resources. Understanding these security mechanisms is vital for maintaining robust network security.
Despite its robustness, Kerberos is not impervious to vulnerabilities. Attacks like AS-REP Roasting, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks can compromise security. Organizations must be aware of these vulnerabilities to take appropriate countermeasures.
Implementing best practices is essential for securing Kerberos-based authentication systems. These practices include enforcing strong password policies, regular key rotation, continuous monitoring, and employee training.
Delving into advanced Kerberos concepts, we explored delegation – both constrained and unconstrained. Delegation allows services to act on behalf of users, enhancing usability and efficiency in complex, multi-tiered applications. Understanding delegation and its security implications is crucial in such scenarios.
Advanced Kerberos concepts introduce additional security considerations. These include implementing fine-grained access controls, monitoring for unusual activities, and regularly analyzing logs to detect and respond to security incidents.
So to conclude, Kerberos stands as a foundational authentication protocol that plays a pivotal role in securing networked environments. It offers robust security mechanisms and advanced features like delegation to enhance usability. Staying informed about Kerberos' complexities, vulnerabilities, and best practices is essential to maintain a strong security posture in the ever-evolving landscape of cybersecurity.
12 notes
·
View notes
Text
The Ultimate Guide to Running Multiple Restaurants
There are times when managing a single restaurant might face a challenge. Increasing foot traffic helps a restaurant to grow, but it can also be an issue if not handled properly. With the growing popularity of dining culture on weekends, restaurant businesses are increasing at a remarkable pace. However, many restaurant owners struggle with the question of how to manage multiple restaurants.
There are many things to look into while running a successful restaurant business. You ought to make quick decisions regarding the management of your restaurant. Your restaurant should be capable of catering to any situation at any time.
This blog will provide you with an ultimate guide to multi-unit restaurant management.
Challenges Faced While Running Multiple Restaurants
Before we explore how to manage multiple restaurants, let us first dive into the challenges restaurant owners face while running various restaurants.
Meeting the Demands
With more options in the market, people look for more every time they visit a restaurant. It is not just about the food but also customer satisfaction that matters the most. Building a trustworthy relationship with your customers is necessary.
This is doable with social media for a single restaurant, where you can communicate with the customers. However, for multiple restaurants, a robust automation system is necessary.
Maintaining Control
Maintaining control over the operations of more than one restaurant becomes challenging. The restaurant business requires continuous monitoring, which is achievable if the owner looks over the operations in person. However, with multi-unit restaurant management, the owner can find it overwhelming to oversee the operations simultaneously.
Maintaining Quality
Maintaining consistent quality with different chefs and staff at various locations becomes challenging. Training the staff is essential to maintain consistency across all the restaurants.
Documenting and adhering to recipes is crucial so that they are easily accessible to the staff. Maintaining a consistent ambience across all restaurants is essential for ensuring a cohesive environment.
New Customer Acquisition
Establishing connections with existing customers and understanding their preferences is valuable. However, transitioning to a new location presents challenges as you must rebuild these relationships.
When expanding to a new area, it's crucial to prioritise customer engagement, considering the shifts in preferences influenced by geographical differences.
Tips for Running Multiple Restaurants Successfully
Delegate Responsibility
Managing all the restaurants at once is challenging; however, this can be achieved by delegating responsibilities. Building a team of trusted managers to allocate responsibility will help to achieve success.
Entrust Managers with Proper Tools
Understanding how each unit performs is imperative to improve guest experiences, margins, and profits consistently. An all-in-one system integrated with your POS and other vendors helps you understand each unit’s performance.
Maintain Consistency
Your restaurant’s reputation is determined by its consistency, contributing to its success. The customer experience begins as soon as they step into the restaurant. Maintaining the right ambience consistently throughout all the restaurants is necessary to ensure greater satisfaction.
Centralise the Process
Centralising data from all locations is necessary to streamline operations across multiple restaurants. This consolidated approach enables owners to monitor all outlets from a single platform, facilitating informed decision-making. Centralising data also solves the issue of how to manage multiple restaurants.
Conclusion
Although there are many challenges faced by restaurant owners to maintain efficiency in terms of multi-unit restaurant management, these can be met with a proper system. Implement a robust system that lets the owner delegate the responsibilities and centralise and optimise the restaurant processes.
QPOS software can help provide all the solutions to ensure the restaurants run smoothly at all locations. With QPOS, all the other systems can be integrated to ensure that all the locations perform up to the mark.
3 notes
·
View notes
Text
"Streamlining Online Ordering and Restaurant Technology"

Delivery and off-premises dining has become the standard, with customers now expecting the convenience of ordering on their terms. According to Hospitality Technology, 54% of people consider off-premises dining an essential part of their lives. For small businesses, enhancing daily operations to incorporate off-premises options requires careful decision-making and the implementation of a POS system tailored to their specific requirements.
Below is a summary of steps to effectively handle the growing demand for online ordering in small businesses by utilizing a POS system. These steps include scaling operations, simplifying processes, and ensuring accommodation for the increasing online orders.
Offer direct online order options
According to our latest restaurant trends report, the majority of consumers prefer ordering directly from a restaurant rather than using third-party platforms. This preference is excellent news for independent restaurateurs as it allows them to have control over both customer acquisition costs and profit margins, which are vital for long-term success.
However, implementing an online ordering system for restaurants can be daunting for most restaurant operators, as they are not web developers and the associated expenses may seem overwhelming.
Fortunately, Foodesoft offers an advanced online ordering system designed specifically for small restaurant businesses. With Foodesoft, restaurants can quickly set up a functional website and start accepting orders in a matter of hours. The advantage of managing orders directly is that it gives restaurants control over guest data, enabling them to create personalized offers based on purchase history, a feature appreciated by 55% of consumers.
By utilizing Foodesoft’s platform, independent restaurants can meet customer preferences for direct ordering, optimize their financial performance, and build stronger customer relationships through tailored offers.
Curate your menu and the carryout experience
When implementing online ordering, it is essential to optimize your menu with three key considerations: focus on dishes that travel well, accommodate dietary restrictions, and appeal to families. Prioritize meals that are emotionally and nutritionally satisfying while also offering suitable options for patrons with dietary limitations. Additionally, be mindful of environmentally conscious consumers by exploring biodegradable or recyclable packaging solutions to enhance sustainability and attract eco-conscious diners. Testing various packaging options can help strike a balance between food quality, cost-effectiveness, and environmental responsibility.
Think carefully about inventory management
Building upon the above: The choices you make regarding your menu will significantly affect the long-term sustainability of your business. After finalizing an online ordering menu that is attractive and suitable for takeout or pickup, analyze it from a financial perspective. Conduct thorough reports on the previous year's performance to identify the optimal configuration that caters to both your customers' preferences and your bottom line.
A payment processor that works for you and your customers
The growing demand for off-premises and in-person dining necessitates a greater reliance on various payment methods. However, many payment processors come with hidden fees, fixed contracts, and expensive processing charges based on the payment type. To address this, opt for an end-to-end payment processor solution that offers a fixed fee rate, flexible month-to-month terms, and transparency with no hidden charges. Your customers should have the freedom to pay using their preferred methods, such as debit cards, credit cards, Apple Pay, Samsung Pay, and Google Pay, without incurring additional costs on your end.
Get Started Now!
With Foodesoft online ordering, restaurant owners can conveniently accept online orders for pickup, delivery, and tableside service through a user-friendly mobile app. The platform offers operators the flexibility to update menus and pricing, access sales reports, and execute marketing campaigns for multiple restaurant locations via an intuitive restaurant dashboard accessible from any web browser. The best part is that it comes at no cost, and the system can be set up quickly, ensuring a smooth and efficient process for businesses.
Using Foodesoft restaurant technology, restaurants can put online ordering transaction data into motion. The reporting dashboard measures performance at every step of the customer journey, from advertising performance to repeat order frequency. It provides:
Promotion statistics
Google rankings
Website visits and funnels
Orders, table reservations, and sales
Delivery heatmaps
Customer details
The restaurant ordering system takes minutes to set up and integrates with Essentials for customers around the globe...
2 notes
·
View notes
Text
How Restaurant Management Software Streamlines Operations and Boosts Efficiency
The restaurant industry is highly competitive, and efficient operations play a crucial role in the success of any establishment. In today's digital age, restaurant management software has emerged as a powerful tool to streamline operations and boost efficiency. This blog post explores the various ways in which restaurant management software revolutionizes the way restaurants operate, enabling them to deliver exceptional customer experiences while optimizing their backend processes.
The Role of Restaurant Management Software:
Online eMenu Restaurant management software is a comprehensive solution designed to handle the diverse aspects of running a restaurant. It encompasses a wide range of features and functionalities that simplify day-to-day operations, enhance productivity, and improve overall efficiency. From Restaurant tasks to Restaurant operations, the software offers a centralized platform to manage and streamline various processes.
Streamlining Restaurant Operations:
In the bustling environment of a restaurant, managing Restaurant operations efficiently is essential. Online eMenu Restaurant management software offers tools for reservation and table management software, allowing customers to book tables online and providing staff with real-time updates on reservations. This helps optimize table turnover and maximize seating capacity, leading to better customer service and increased revenue. Additionally, the software integrates with the point-of-sale (POS) system, enabling seamless order taking and processing.
Enhancing Restaurant Efficiency:
Efficiency in the Restaurant operations is equally important for smooth restaurant functioning. With restaurant management software, staff scheduling and labor management become hassle-free. The software automates scheduling, taking into account factors such as staff availability and workload, resulting in optimized staff allocation and improved productivity. It also tracks labor costs and performance metrics, providing valuable insights for effective decision-making.
Supplier and procurement management is another critical aspect that software addresses. By streamlining the ordering process and managing suppliers, restaurants can ensure timely and accurate deliveries. The software facilitates inventory forecasting, minimizing wastage and optimizing stock levels. Real-time reporting and analytics capabilities empower restaurant owners and managers to monitor sales, expenses, and performance, enabling data-driven decision-making.
Customer Relationship Management (CRM):
Building strong customer relationships is vital for the success of any restaurant. Restaurant management software Customer Relationship Management (CRM) helps in creating and maintaining customer profiles, capturing preferences, and analyzing data to deliver personalized experiences. Additionally, the software facilitates the implementation of loyalty programs and targeted marketing campaigns, allowing restaurants to engage with customers effectively and increase customer retention.
Ensuring Data Security and Accessibility:
Data security is a paramount concern in today's digital landscape. Restaurant management software offers robust security measures to protect sensitive customer information and business data. Cloud-based solutions provide data backup and ensure accessibility from anywhere, anytime, allowing owners and managers to monitor and manage their restaurant's operations remotely. User access control features further enhance data privacy and confidentiality.
Case Studies: Success Stories of Restaurant Management Software Implementation
Real-life examples of restaurants that have implemented restaurant management software can provide valuable insights into its effectiveness. Case studies highlighting specific improvements and outcomes achieved through the software demonstrate how it has helped restaurants streamline their operations, enhance efficiency, and deliver exceptional dining experiences.
Challenges and Considerations:
While restaurant management software offers numerous benefits, it's essential to consider potential challenges and factors when selecting the right software. Factors such as cost, scalability, user-friendliness, and integration capabilities with existing systems should be evaluated before making a decision. Addressing these considerations ensures a successful implementation and maximizes the software's potential.
Conclusion:
Restaurant Management software has become a game-changer in the industry, revolutionizing the way restaurants operate. By streamlining operations, enhancing efficiency, and optimizing processes, this software empowers restaurants to deliver exceptional customer experiences while driving profitability. As technology continues to shape the future of the restaurant industry, embracing restaurant management software becomes essential for those seeking.
#restaurant management software#contactless menu system#qr code#restaurant management system#restaurant pos system#contactless menu#contactless qr code menu#contactless ordering app#point-of-sale (POS) system#point-of-sale system#pos billing software#restaurant pos software#pos system#pos software#restaurant software#restaurant sales#restaurant#qrcodemenu#qr code menu#cloud based pos billing system#cloud based pos billing software#crm software#crmintegration#restaurant crm#restaurant crm software#crm development#online food ordering software#online food ordering system#food ordering system online#Restaurant Table Booking
4 notes
·
View notes
Text
How to Run a Restaurant Business Successfully in India: Essential Tips and Strategies
A thorough understanding of the Indian food sector, effective administration, and careful planning are all necessary for operating a successful restaurant. With the ever-increasing competition and evolving customer preferences, restaurant owners must stay ahead of the game to thrive in this dynamic market. In this article, we will explore essential tips and strategies for running a restaurant business successfully in India, with a particular focus on leveraging restaurant system management and software for efficient operations.
Embrace Technology: Restaurant Point of Sale (POS) Systems-
One of the most crucial aspects of running a successful restaurant business is adopting modern technology to streamline operations. A robust restaurant Point of sales system is an invaluable tool that can revolutionize your restaurant's efficiency and profitability. A restaurant POS system automates various tasks such as order management, inventory tracking, billing, and reporting.
Investing in reliable software for restaurant POS in India can enhance the overall dining experience for your customers. With a feature-rich POS system, you can expedite order processing, reduce errors, and improve table turnover. Furthermore, advanced POS software allows you to manage multiple aspects of your restaurant, including online orders, delivery, and reservations.
Optimize Restaurant System Management
Efficient management of your restaurant system is crucial for smooth day-to-day operations. Here are some essential tips to consider:
a) Staff Training: Invest in comprehensive training programs to ensure your staff is well-equipped to handle various responsibilities. Properly trained employees can provide better customer service, handle busy periods efficiently, and effectively utilize the restaurant POS system.
b) Inventory Management: Implement a robust inventory management system to track ingredients, supplies, and equipment. Regularly monitor stock levels, streamline procurement processes, and reduce wastage to minimize costs.
c) Menu Engineering: Analyze your menu and identify the most popular dishes, as well as the least profitable ones. Optimize your menu by highlighting high-margin items and removing underperforming dishes. This strategic approach can significantly impact your revenue and customer satisfaction.
d) Streamline Operations: Look for areas where you can automate or streamline operations further. This could include implementing self-service kiosks for order placement, online reservation systems, or integrating your POS system with third-party delivery platforms.
Focus on Customer Experience
In the highly competitive restaurant industry, providing an exceptional customer experience is paramount. Happy customers become loyal patrons and often spread positive word-of-mouth, which is invaluable for your business. Here are some tips to enhance the customer experience:
a) Personalized Service: Train your staff to provide personalized attention to customers. Encourage them to engage in friendly conversations, remember regular customers' preferences, and offer recommendations based on individual tastes.
b) Speed and Efficiency: With the help of a restaurant POS system, streamline your order management process to ensure quick and accurate service. Reduce waiting times, expedite food preparation, and optimize the billing process to leave a lasting positive impression.
c) Online Presence: Leverage the power of digital platforms to connect with your customers. Maintain an informative and user-friendly website, regularly update your social media accounts, and actively engage with customer reviews and feedback.
d) Loyalty Programs: Implement a customer loyalty program to incentivize repeat visits. Offer discounts, freebies, or exclusive benefits to encourage customers to choose your restaurant over competitors.
Maintain Quality and Consistency
Consistency is key to building a strong brand reputation and earning customer loyalty. To maintain high-quality standards:
a) Ingredients and Sourcing: Source fresh and high-quality ingredients from reliable suppliers. Ensure your kitchen staff follows strict guidelines for food preparation and storage.
b) Menu Testing: Regularly evaluate and test new dishes or menu updates to maintain consistency in taste, presentation, and portion sizes.
c) Hygiene and Cleanliness: Ensure that your restaurant maintains impeccable hygiene standards. Regularly clean and sanitize all areas, including the dining area, kitchen, restrooms, and storage spaces. Train your staff on proper food handling and safety practices to prevent any health hazards.
d) Feedback and Improvement: Encourage customer feedback and take it seriously. Address any concerns or complaints promptly and take necessary measures to rectify them. Use feedback as an opportunity for continuous improvement and to meet and exceed customer expectations.
Effective Marketing and Promotion
Implementing effective marketing and promotional strategies can help increase your restaurant's visibility and attract new customers. Consider the following tips:
a) Online Presence: Develop a strong online presence through a well-designed website, active social media profiles, and online review platforms. Regularly update your online platforms with enticing content, attractive food photography, and engaging promotions.
b) Local Partnerships: Collaborate with local influencers, food bloggers, and organizations to reach a wider audience. Offer special deals or partnerships to enhance visibility and credibility.
c) Special Events and Offers: Organize special events, themed nights, or seasonal promotions to create excitement and attract customers. Offer discounts, happy hour specials, or loyalty program incentives to entice new and repeat visitors.
d) Customer Referrals: Implement a referral program that rewards customers for bringing in new patrons. Word-of-mouth referrals can be highly effective in attracting new business.
Financial Management and Cost Control
To run a successful restaurant business, effective financial management is crucial. Consider these tips for better cost control:
a) Budgeting: Develop a comprehensive budget that includes all aspects of your restaurant's expenses, including food costs, staff salaries, rent, utilities, and marketing. Regularly review and analyze your budget to identify areas where costs can be reduced without compromising quality.
b) Menu Pricing: Set prices strategically by considering ingredient costs, competition, and customer perception. Ensure that your menu pricing allows for a healthy profit margin without alienating customers.
c) Vendor Negotiations: Build strong relationships with your suppliers and negotiate favorable terms to secure competitive pricing for ingredients and supplies. Regularly compare prices from different vendors to ensure you're getting the best deals.
d) Waste Reduction: Implement measures to minimize food waste and optimize portion sizes. Train your staff on portion control techniques and consider donating excess food to local charities or food banks.
Conclusion Running a successful restaurant business in India requires a combination of effective management strategies, embracing technology, providing exceptional customer experiences, and implementing smart marketing techniques. By utilizing restaurant system management and leveraging pos restaurant software in India, you can streamline operations, enhance efficiency, and improve overall profitability. Additionally, focusing on customer satisfaction, maintaining quality standards, and controlling costs are essential elements of a thriving restaurant business. With dedication, continuous improvement, and the implementation of these essential tips and strategies, you can position your restaurant for success in the dynamic Indian food industry.

2 notes
·
View notes
Text
In April 2018, I was invited by the American ambassador to a meeting at the embassy in Tbilisi, Georgia. The ambassador had assembled a group of nongovernmental organization (NGO) leaders in the field of disinformation to meet with a senior Trump administration official from the State Department. He asked us to describe the main narratives of Kremlin disinformation. As the director of a large international democracy organization, I highlighted Russia’s manipulation of gender and LGBTQ issues to sway Georgians away from the perceived “cultural decadence” of the European Union. The official’s frustration was palpable. His response, tinged with irritation, was telling: “Is that all you people can talk about? The gays?”
A year before, several international organizations partnered with Georgian parliamentarians on a gender equality assessment, supported by several government donors. This collaboration led to an internal conflict. The United States Agency for International Development (USAID) wanted to scrub the original report, as it covered abortion, notably legal in Georgia, while the Swedish government and other stakeholders wanted the complete assessment. As a result, at the time of its release, two distinct reports had to be printed, one with references to abortion and one without.
Former U.S. President Donald Trump emerged victorious from last week’s New Hampshire primary and is likely to be the Republican Party’s presidential nominee. His closing statement in New Hampshire praised Hungarian leader Viktor Orban, who embraces the oxymoronic term “illiberal democracy” while suppressing independent media, civil society, and courts. He has repeatedly emphasized the glory of strongmen like Orban. His foreign policy has been clear: stopping support for Ukraine, NATO, and our European allies.
But while there has been plenty of analysis of Trump’s America First impact on foreign policy and security, less covered is how it will also completely redefine foreign aid as well as the liberal democracy agenda. My experience with the first Trump administration as a senior leader in democracy organizations receiving funding from USAID provides some insight into the foreign-aid agenda of a second, but likely only scratches the surface of what is to come.
The Heritage Foundation’s Project 2025, established in 2022, offers a detailed roadmap for revamping USAID under Trump—one that will undermine, eliminate, and censor the critical work of thousands of people and organizations committed to building more just societies. The Heritage Foundation has been staffing and providing a pipeline of ideas to Republican administrations since President Ronald Reagan. Project 2025 is a plan to shape the next Republican administration, and its funders have close ties to Trump. The project’s objective is to replace “deep state” employees with conservative thought leaders to carry out an executive-driven agenda.
In the overview, the project articulates its goal to end what it calls USAID’s “divisive political and cultural agenda that promotes abortion, climate extremism, gender radicalism, and interventions against perceived systemic racism.” A key component of the illiberal playbook is to attack gender and marginalized communities, an early warning sign of democratic backsliding. Illiberal strongmen, such as Turkey’s Recep Tayyip Erdogan and Russia’s Vladimir Putin, exploit traditional hierarchies to divide society and create pecking orders of power. Russia refused to sign, and Turkey withdrew from, the Istanbul Convention, a commitment to protect women from domestic violence. The Narendra Modi administration in India filed an affidavit in the Supreme Court against criminalizing marital rape, arguing it would destabilize marriage. Hungary and Poland lobbied to ban the term “gender equality” in international agreements and implemented anti-LGBTQ policies, including local municipalities adopting “LGBT-free” zones as part of a government-supported “Family Charter” in Poland.
As a first step, Trump’s USAID will “dismantle” all diversity, equity, and inclusion (DEI) initiatives, which Project 2025 calls “discriminatory.” This mandate includes firing the chief diversity officer and all advisors and committees. In 2016, the Obama administration issued a DEI presidential memorandum to ensure USAID, among other agencies, had a diverse and representative workforce. Trump scaled back these efforts. On Jan. 20, 2021, Biden’s first day in office, he signed an executive order that demanded that government agencies devise strategies to tackle DEI issues. Pursuant to this, USAID Administrator Samantha Power signed USAID’s DEI strategy on her first day in May 2021. Project 2025 would reverse this strategy, requiring USAID to “cease promotion of the DEI agenda, including the bullying LGBTQ+ agenda,” which entails support for organizations overseas that work on these issues.
According to Project 2025, Trump’s new USAID will also eliminate the word “gender” full stop, arguing that “Democrat Administrations have nearly erased what females are.” This is bizarre, as I have decades of experience receiving USAID funding for numerous programs to advance women in political life and support women’s organizations. Working for democracy organizations across Asia and the former Soviet Union, I saw USAID provide critical support to expand women’s wings of political parties; recruit women election officials, observers, and administrators; train women’s advocacy and rights organizations; and build women’s committees in parliaments.
The Heritage Foundation report also accuses USAID of “outright bias against men,” an equally strange claim; in fact, gender realignment was needed and implemented. A Trump USAID will fire more than 180 gender advisors and points of contact, who work alongside USAID colleagues “to integrate gender and advance gender equality objectives in USAID’s work worldwide,” and scrub the words “gender,” “gender equality,” and “gender equity” from all documents. This would require a massive purge of decades of USAID materials and websites.
USAID has spent years incorporating gender into all aspects of its programming to ensure the agency addresses the needs of women, including unique development obstacles they face. Removing a gender lens would take us back in time to programming that often harmed women, inadvertently, by failing to analyze the varying effects of programming based on gender and power dynamics in different environments. To erase all of USAID’s tools, learning, and research on how to ensure best practice would have dangerous consequences. For example, when I worked for USAID in Cambodia in the 1990s, the agency supported micro-lending for small community projects, in which most of the loans went to women. This resulted in increased domestic violence, as men were angry about the financial imbalance in the home. Today, USAID has gender analysis and research on risk factors to mitigate against such outcomes.
Relatedly, a Trump USAID will make anti-choice “core” to its mission, removing all “references to ‘abortion,’ ‘reproductive health,’ and ‘sexual and reproductive rights.’” Project 2025’s blueprint singles out specific organizations and U.N. agencies to target and defund. Further, the president himself would have the ability to oversee programming directly: “Current law in the Foreign Assistance Act gives the President broad authority to set ‘such terms and conditions as he may determine’ on foreign assistance, which legally empowers the next conservative President to expand this pro-life policy.” Previous administrations have restricted funding to organizations that provide abortions (the “Mexico City Policy”), which resulted in an increase in maternal and child mortality and unsafe abortions—exactly what the policy claimed to want to prevent. In sub-Saharan Africa, data shows the policy increased abortions by defunding clinics that provided family-planning services. The first Trump administration expanded restrictions further, impacting speech and service delivery around the world.
A Trump USAID would not only stop funding local partner organizations that support gender, LGBTQ, and rights agendas but redirect that money to religious organizations. In fact, it would mandate training and indoctrination for all USAID staff on the link between religion and development. USAID would also ensure conservative oversight of all grantmaking to ensure against “progressive policies” and a “radical agenda.” USAID already engages with faith-based partnerships, alongside secular NGOs, but Project 2025 would like to shift the balance, creating a “New Partnership Initiative” that would help prioritize religious groups.
A stated “key outcome of the transformation of USAID” under Trump will be a complete revamp of the Bureau for Democracy, Development, and Innovation, shifting its focus to trade, the private sector, and religious communities, and purging staff. Importantly, all directors of each center—not just the assistant administrator—will have political leadership, not career experts. In addition, Trump’s USAID will rewrite all policy “as soon as possible” to ensure a conservative agenda.
During the first Trump administration, I felt the impact in my work overseas. I worked closely with the LGBTQ community in Georgia, which faced horrific obstacles—ostracization, violence, homelessness—and which was targeted relentlessly by Kremlin information operations. USAID has long been a defender of human rights and funded projects on these issues. There was a shift under Trump, though I applaud individual USAID employees for creatively trying to find workarounds and continue support—like slight renaming of initiatives or cleverly filing them under more favorable, broader categories like “human rights.” They no doubt prevented damaging cuts to our important work.
I am far more worried about the impact of a second administration. Back then, there was no concrete, detailed roadmap like Project 2025 and no massive replacement of foreign aid professionals with conservative political operatives. Under a second administration, under Schedule F, Trump has planned a sweeping political takeover of our civil service, stripping civil servants of protection, forcing them to implement his political policy agenda, and giving the president unilateral power to fire employees at will.
The organization I now work for, the German Marshall Fund, supports hundreds of civil society organizations across the Balkans, Black Sea region, Ukraine, and Central Europe—thanks to more than a decade of USAID support. USAID has encouraged our goals of promoting democracy; bolstering the rights of women, LGBTQ, and other marginalized communities; and deterring illiberalism through independent media, watchdog organizations, and information integrity efforts. We do this through grantmaking, capacity-building and technical assistance, leadership programs, and policy dialogues.
With democracy in global decline and illiberal strongmen on the rise, we need these efforts more than ever. Backsliding elsewhere affects democracy everywhere. America benefits from strong, free, liberal societies—it is in our national interest and key to our global security and order. While few voters go to the polls with foreign aid on their minds, the consequences for millions of people worldwide are on the ballot this November.
34 notes
·
View notes
Text

https://www.romiotech.com/fine-dine-restaurant-billing.html
Romio Restaurant POS is a billing system that caters to the Fine Dine Restaurant. Its graphics based interface make it easy to use and fast to implement hence reducing the training time.
2 notes
·
View notes
Text
This Week in Rust 510
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.72.0
Change in Guidance on Committing Lockfiles
Cargo changes how arrays in config are merged
Seeking help for initial Leadership Council initiatives
Leadership Council Membership Changes
Newsletters
This Week in Ars Militaris VIII
Project/Tooling Updates
rust-analyzer changelog #196
The First Stable Release of a Memory Safe sudo Implementation
We're open-sourcing the library that powers 1Password's ability to log in with a passkey
ratatui 0.23.0 is released! (official successor of tui-rs)
Zellij 0.38.0: session-manager, plugin infra, and no more offensive session names
Observations/Thoughts
The fastest WebSocket implementation
Rust Malware Staged on Crates.io
ESP32 Standard Library Embedded Rust: SPI with the MAX7219 LED Dot Matrix
A JVM in Rust part 5 - Executing instructions
Compiling Rust for .NET, using only tea and stubbornness!
Ad-hoc polymorphism erodes type-safety
How to speed up the Rust compiler in August 2023
This isn't the way to speed up Rust compile times
Rust Cryptography Should be Written in Rust
Dependency injection in Axum handlers. A quick tour
Best Rust Web Frameworks to Use in 2023
From tui-rs to Ratatui: 6 Months of Cooking Up Rust TUIs
[video] Rust 1.72.0
[video] Rust 1.72 Release Train
Rust Walkthroughs
[series] Distributed Tracing in Rust, Episode 3: tracing basics
Use Rust in shell scripts
A Simple CRUD API in Rust with Cloudflare Workers, Cloudflare KV, and the Rust Router
[video] base64 crate: code walkthrough
Miscellaneous
Interview with Rust and operating system Developer Andy Python
Leveraging Rust in our high-performance Java database
Rust error message to fix a typo
[video] The Builder Pattern and Typestate Programming - Stefan Baumgartner - Rust Linz January 2023
[video] CI with Rust and Gitlab Selfhosting - Stefan Schindler - Rust Linz July 2023
Crate of the Week
This week's crate is dprint, a fast code formatter that formats Markdown, TypeScript, JavaScript, JSON, TOML and many other types natively via Wasm plugins.
Thanks to Martin Geisler for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
Hyperswitch - add domain type for client secret
Hyperswitch - deserialization error exposes sensitive values in the logs
Hyperswitch - move redis key creation to a common module
mdbook-i18n-helpers - Write tool which can convert translated files back to PO
mdbook-i18n-helpers - Package a language selector
mdbook-i18n-helpers - Add links between translations
Comprehensive Rust - Link to correct line when editing a translation
Comprehensive Rust - Track the number of times the redirect pages are visited
RustQuant - Jacobian and Hessian matrices support.
RustQuant - improve Graphviz plotting of autodiff computational graphs.
RustQuant - bond pricing implementation.
RustQuant - implement cap/floor pricers.
RustQuant - Implement Asian option pricers.
RustQuant - Implement American option pricers.
release-plz - add ability to mark Gitea/GitHub release as draft
zerocopy - CI step "Set toolchain version" is flaky due to network timeouts
zerocopy - Implement traits for tuple types (and maybe other container types?)
zerocopy - Prevent panics statically
zerocopy - Add positive and negative trait impl tests for SIMD types
zerocopy - Inline many trait methods (in zerocopy and in derive-generated code)
datatest-stable - Fix quadratic performance with nextest
Ockam - Use a user-friendly name for the shared services to show it in the tray menu
Ockam - Rename the Port to Address and support such format
Ockam - Ockam CLI should gracefully handle invalid state when initializing
css-inline - Update cssparser & selectors
css-inline - Non-blocking stylesheet resolving
css-inline - Optionally remove all class attributes
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
366 pull requests were merged in the last week
reassign sparc-unknown-none-elf to tier 3
wasi: round up the size for aligned_alloc
allow MaybeUninit in input and output of inline assembly
allow explicit #[repr(Rust)]
fix CFI: f32 and f64 are encoded incorrectly for cross-language CFI
add suggestion for some #[deprecated] items
add an (perma-)unstable option to disable vtable vptr
add comment to the push_trailing function
add note when matching on tuples/ADTs containing non-exhaustive types
add support for ptr::writes for the invalid_reference_casting lint
allow overwriting ExpnId for concurrent decoding
avoid duplicate large_assignments lints
contents of reachable statics is reachable
do not emit invalid suggestion in E0191 when spans overlap
do not forget to pass DWARF fragment information to LLVM
ensure that THIR unsafety check is done before stealing it
emit a proper diagnostic message for unstable lints passed from CLI
fix races conditions with SyntaxContext decoding
fix waiting on a query that panicked
improve note for the invalid_reference_casting lint
include compiler flags when you break rust;
load include_bytes! directly into an Lrc
make Sharded an enum and specialize it for the single thread case
make rustc_on_unimplemented std-agnostic for alloc::rc
more precisely detect cycle errors from type_of on opaque
point at type parameter that introduced unmet bound instead of full HIR node
record allocation spans inside force_allocation
suggest mutable borrow on read only for-loop that should be mutable
tweak output of to_pretty_impl_header involving only anon lifetimes
use the same DISubprogram for each instance of the same inlined function within a caller
walk through full path in point_at_path_if_possible
warn on elided lifetimes in associated constants (ELIDED_LIFETIMES_IN_ASSOCIATED_CONSTANT)
make RPITITs capture all in-scope lifetimes
add stable for Constant in smir
add generics_of to smir
add smir predicates_of
treat StatementKind::Coverage as completely opaque for SMIR purposes
do not convert copies of packed projections to moves
don't do intra-pass validation on MIR shims
MIR validation: reject in-place argument/return for packed fields
disable MIR SROA optimization by default
miri: automatically start and stop josh in rustc-pull/push
miri: fix some bad regex capture group references in test normalization
stop emitting non-power-of-two vectors in (non-portable-SIMD) codegen
resolve: stop creating NameBindings on every use, create them once per definition instead
fix a pthread_t handle leak
when terminating during unwinding, show the reason why
avoid triple-backtrace due to panic-during-cleanup
add additional float constants
add ability to spawn Windows process with Proc Thread Attributes | Take 2
fix implementation of Duration::checked_div
hashbrown: allow serializing HashMaps that use a custom allocator
hashbrown: change & to &mut where applicable
hashbrown: simplify Clone by removing redundant guards
regex-automata: fix incorrect use of Aho-Corasick's "standard" semantics
cargo: Very preliminary MSRV resolver support
cargo: Use a more compact relative-time format
cargo: Improve TOML parse errors
cargo: add support for target.'cfg(..)'.linker
cargo: config: merge lists in precedence order
cargo: create dedicated unstable flag for asymmetric-token
cargo: set MSRV for internal packages
cargo: improve deserialization errors of untagged enums
cargo: improve resolver version mismatch warning
cargo: stabilize --keep-going
cargo: support dependencies from registries for artifact dependencies, take 2
cargo: use AND search when having multiple terms
rustdoc: add unstable --no-html-source flag
rustdoc: rename typedef to type alias
rustdoc: use unicode-aware checks for redundant explicit link fastpath
clippy: new lint: implied_bounds_in_impls
clippy: new lint: reserve_after_initialization
clippy: arithmetic_side_effects: detect division by zero for Wrapping and Saturating
clippy: if_then_some_else_none: look into local initializers for early returns
clippy: iter_overeager_cloned: detect .cloned().all() and .cloned().any()
clippy: unnecessary_unwrap: lint on .as_ref().unwrap()
clippy: allow trait alias DefIds in implements_trait_with_env_from_iter
clippy: fix "derivable_impls: attributes are ignored"
clippy: fix tuple_array_conversions lint on nightly
clippy: skip float_cmp check if lhs is a custom type
rust-analyzer: diagnostics for 'while let' loop with label in condition
rust-analyzer: respect #[allow(unused_braces)]
Rust Compiler Performance Triage
A fairly quiet week, with improvements exceeding a small scattering of regressions. Memory usage and artifact size held fairly steady across the week, with no regressions or improvements.
Triage done by @simulacrum. Revision range: d4a881e..cedbe5c
2 Regressions, 3 Improvements, 2 Mixed; 0 of them in rollups 108 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Create a Testing sub-team
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] Stabilize PATH option for --print KIND=PATH
[disposition: merge] Add alignment to the NPO guarantee
New and Updated RFCs
[new] Special-cased performance improvement for Iterator::sum on Range<u*> and RangeInclusive<u*>
[new] Cargo Check T-lang Policy
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-08-30 - 2023-09-27 🦀
Virtual
2023-09-05 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-09-05 | Virtual (Munich, DE) | Rust Munich
Rust Munich 2023 / 4 - hybrid
2023-09-06 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-09-12 - 2023-09-15 | Virtual (Albuquerque, NM, US) | RustConf
RustConf 2023
2023-09-12 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2023-09-13 | Virtual (Boulder, CO, US) | Boulder Elixir and Rust
Monthly Meetup
2023-09-13 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
The unreasonable power of combinator APIs
2023-09-14 | Virtual (Nuremberg, DE) | Rust Nuremberg
Rust Nürnberg online
2023-09-20 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2023-09-21 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-09-21 | Lehi, UT, US | Utah Rust
Real Time Multiplayer Game Server in Rust
2023-09-21 | Virtual (Linz, AT) | Rust Linz
Rust Meetup Linz - 33rd Edition
2023-09-25 | Virtual (Dublin, IE) | Rust Dublin
How we built the SurrealDB Python client in Rust.
Asia
2023-09-06 | Tel Aviv, IL | Rust TLV
RustTLV @ Final - September Edition
Europe
2023-08-30 | Copenhagen, DK | Copenhagen Rust Community
Rust metup #39 sponsored by Fermyon
2023-08-31 | Augsburg, DE | Rust Meetup Augsburg
Augsburg Rust Meetup #2
2023-09-05 | Munich, DE + Virtual | Rust Munich
Rust Munich 2023 / 4 - hybrid
2023-09-14 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2023-09-19 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
Logging and tracing in Rust
2023-09-20 | Aarhus, DK | Rust Aarhus
Rust Aarhus - Rust and Talk at Concordium
2023-09-21 | Bern, CH | Rust Bern
Third Rust Bern Meetup
North America
2023-09-05 | Chicago, IL, US | Deep Dish Rust
Rust Happy Hour
2023-09-06 | Bellevue, WA, US | The Linux Foundation
Rust Global
2023-09-12 - 2023-09-15 | Albuquerque, NM, US + Virtual | RustConf
RustConf 2023
2023-09-12 | New York, NY, US | Rust NYC
A Panel Discussion on Thriving in a Rust-Driven Workplace
2023-09-12 | Minneapolis, MN, US | Minneapolis Rust Meetup
Minneapolis Rust Meetup Happy Hour
2023-09-14 | Seattle, WA, US | Seattle Rust User Group Meetup
Seattle Rust User Group - August Meetup
2023-09-19 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2023-09-21 | Nashville, TN, US | Music City Rust Developers
Rust on the web! Get started with Leptos
2023-09-26 | Pasadena, CA, US | Pasadena Thursday Go/Rust
Monthly Rust group
2023-09-27 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
Oceania
2023-09-13 | Perth, WA, AU | Rust Perth
Rust Meetup 2: Lunch & Learn
2023-09-19 | Christchurch, NZ | Christchurch Rust Meetup Group
Christchurch Rust meetup meeting
2023-09-26 | Canberra, ACT, AU | Rust Canberra
September Meetup
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
In [other languages], I could end up chasing silly bugs and waste time debugging and tracing to find that I made a typo or ran into a language quirk that gave me an unexpected nil pointer. That situation is almost non-existent in Rust, it's just me and the problem. Rust is honest and upfront about its quirks and will yell at you about it before you have a hard to find bug in production.
– dannersy on Hacker News
Thanks to Kyle Strand for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
0 notes