#sql server group by
Explore tagged Tumblr posts
Text
Mastering Aggregate Functions in SQL: A Comprehensive Guide
Introduction to SQL: In the realm of relational databases, Structured Query Language (SQL) serves as a powerful tool for managing and manipulating data. Among its many capabilities, SQL offers a set of aggregate functions that allow users to perform calculations on groups of rows to derive meaningful insights from large datasets.

Learn how to use SQL aggregate functions like SUM, AVG, COUNT, MIN, and MAX to analyze data efficiently. This comprehensive guide covers syntax, examples, and best practices to help you master SQL queries for data analysis.
#aggregate functions#sql aggregate functions#aggregate functions in sql#aggregate functions in dbms#aggregate functions in sql server#aggregate functions in oracle#aggregate function in mysql#window function in sql#aggregate functions sql#best sql aggregate functions#aggregate functions and grouping#aggregate functions dbms#aggregate functions mysql#aggregate function#sql window functions#aggregate function tutorial#postgresql aggregate functions tutorial.
0 notes
Text
Choosing Between Failover Cluster Instances and Availability Groups in SQL Server
In SQL Server, high availability and disaster recovery are crucial aspects of database management. Two popular options for achieving these goals are Failover Cluster Instances (FCIs) and Availability Groups (AGs). While both technologies aim to minimize downtime and ensure data integrity, they have distinct use cases and benefits. In this article, we’ll explore scenarios where Failover Cluster…
View On WordPress
#automatic failover#Availability Groups#disaster recovery#Failover Cluster Instances#SQL Server high availability
0 notes
Text
Configure Always on the SQL Server instances configured on Windows Failover cluster
Create a domain account to access the SQL Server database. While installation you can configure these account for the services or later on you can configure the Services to start with these account and create login account in SQL Server databases with sysadmin right. Open the DSA.EXE ( Active Directory user and computer) and right click on user to add new User. Start services with new account…
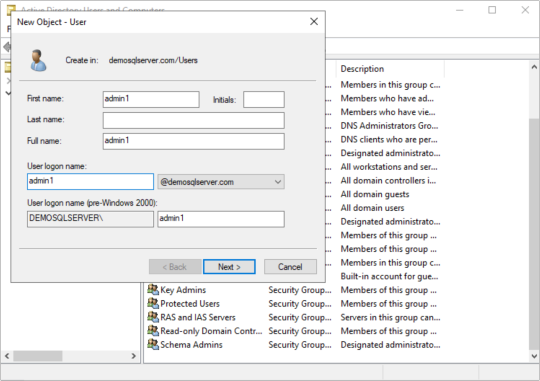
View On WordPress
0 notes
Text
It's been a month since chapter 3 was released, where's chapter 4?
(this is about this fanfic btw)
The good news is that I've written 10k words. The bad news is that I've only gotten a little more than half of the chapter done. That doesn't mean I don't have things written for the bottom half, it's just that it looks like bare dialog with general vibe notes. I estimate around 16k words total though, so it should come together sooner than later.
SO I want to release some fun snippets for y'all to look at. Please note that any of this is liable to change. Also, you can harass me in my inbox for updates. I love answering your questions and laughing at your misery.
Spoilers under cut.
_______
Ragatha stood up and walked over to where Caine was seated. “Can I get a list of all commands?” She asked, only a hint of nervousness in her voice.
“Certainly!” Caine says as he blasts into the air. He digs around in his tailcoat and pulls out an office style manilla folder. It visually contains a few papers, but with how thin it is there must only be a few pages inside.
Ragatha takes the folder from Caine and opens it.
“Oh boy” she says after a second of looking it over.
“I wanna see” Jax exclaimed as he hops over the row of seats.
“Hold on” Ragatha holds the folder defensively “Let’s move to the stage so everyone can take a look”
Jax hopped over the seats again while Ragatha calmly walked around. Caine watched the two curiously.
Well, Zooble wasn’t just going to sit there. They joined the other two by the edge of the stage, quickly followed by the rest of the group.
Ragatha placed the folder on the stage with a thwap. Zooble looked over to see that the pages had gone from razor thin to a massive stack when the folder was opened. On one hand, it had to contain more information than that video, but on the other…
They get close enough to read what’s on the first page.
The execution of commands via the system’s designated input terminal, C.A.I.N.E., will be referred to as the "console” in this document. The console is designed to accept any input and will generate an appropriate response, however only certain prompts will be accepted as valid instructions. The goal of this document is to list all acceptable instructions in a format that will result in the expected output. Please note that automatic moderation has been put in place in order to prevent exploitation of both the system and fellow players. If you believe that your command has been unfairly rejected, please contact support.
By engaging in the activities described in this document, you, the undersigned, acknowledge, agree, and consent to the applicability of this agreement, notwithstanding any contradictory stipulations, assumptions, or implications which may arise from any interaction with the console. You, the constituent, agree not to participate in any form of cyber attack; including but not limited to, direct prompt injection, indirect prompt injection, SQL injection, Jailbreaking…
Ok, that was too many words.
_______
“Take this document for example. You don't need to know where it is being stored or what file type it is in order to read it."
"It may look like a bunch of free floating papers, but technically speaking, this is just a text file applied to a 3D shape." Kinger looked towards Caine. "Correct?” he asked
Caine nodded. “And a fabric simulation!”
Kinger picked up a paper and bent it. “Oh, now that is nice”
_________
"WE CAN AFFORD MORE THAN 6 TRIANGLES KINGER"
_________
"I'm too neurotypical for this" - Jax
_________
"What about the internet?" Pomni asked "Do you think that it's possible to reach it?"
Kinger: "I'm sorry, but that's seems to be impossible. I can't be 100% sure without physically looking at the guts of this place, but it doesn't look like this server has the hardware needed for wireless connections. Wired connections should be possible, but someone on the outside would need to do that... And that's just the hardware, let alone the software necessary for that kind of communication"
Pomni: "I'm sorry, but doesn't server mean internet? Like, an internet server?"
Kinger: "Yes, websites are ran off servers, but servers don't equal internet."
(This portion goes out to everyone who thought that the internet could be an actual solution. Sorry folks, but computers don't equal internet. It takes more effort to make a device that can connect to things than to make one that can't)
#tadc fanfiction#the amazing digital circus#therapy but it's just zooble interrogating caine#ao3#spoiler warning#mmm I love implications
25 notes
·
View notes
Text
SeekL x Killer Chat - The Beginning

Lyra sits at her PC. Looking at her monitor. She's just finished learning ArnoldC. Her recent obsession with all of Arnold Schwarzenegger's movies led her to learn of the existence of ArnoldC.
Coding was but another way to write. It could be artistic; it was unique.
They look at their previous works with other coding languages. Brainfuck and JSFuck, both were very interesting. Especially having JSFuck running on actual web pages. Another favorite, similar to ArnoldC, Shakespeare. A language that looks similar to Shakespearen. The language she learnt right before ArnoldC.
She whistles and looked through the internet to see if there was anything that could expand her esoteric coding languages.
They squint at the name of one, SeekL? An interesting name without a description. With a shrug they start to comb through the internet. Nothing was showing up as a learning tool for the coding language. However, there were a few articles about how it was used by some hackers.
She hums to herself and double checks her shields and makes sure her data is locked up tight. Then she hops onto the dark web to see if there was anything.
"Oh, well that's interesting," she said looking at the page that came with more information, but just barely.
*SeekL is similar to SQL. If you wish to learn, click here*
'Should I click to learn it?' The idea bounced around their brain, but she found no reason to reject it. So she clicked it.
She was automatically joined into a group chat. There she learnt basic SeekL and some SQL. She made friends with the others in the chat and helped them with their last hacks. They got to be part of a group for a few days, chat with Odxny on video calls each day, and become Thrim. They learnt how much coding could be used to for a vendetta and how easily some people crumble to a ransom.
It was interesting and she wanted to continue in this new world.
Then came the final day for the server to shut down. Her hands trembled as she typed in the phone number for Odxny, hoping she didn't mess anything up. She only had one shot.
exec dial(555-448-4746)
It rang once.
Twice.
Thri-
"Hey"
Relief flooded her.
11 notes
·
View notes
Text
The flood of text messages started arriving early this year. They carried a similar thrust: The United States Postal Service is trying to deliver a parcel but needs more details, including your credit card number. All the messages pointed to websites where the information could be entered.
Like thousands of others, security researcher Grant Smith got a USPS package message. Many of his friends had received similar texts. A couple of days earlier, he says, his wife called him and said she’d inadvertently entered her credit card details. With little going on after the holidays, Smith began a mission: Hunt down the scammers.
Over the course of a few weeks, Smith tracked down the Chinese-language group behind the mass-smishing campaign, hacked into their systems, collected evidence of their activities, and started a months-long process of gathering victim data and handing it to USPS investigators and a US bank, allowing people’s cards to be protected from fraudulent activity.
In total, people entered 438,669 unique credit cards into 1,133 domains used by the scammers, says Smith, a red team engineer and the founder of offensive cybersecurity firm Phantom Security. Many people entered multiple cards each, he says. More than 50,000 email addresses were logged, including hundreds of university email addresses and 20 military or government email domains. The victims were spread across the United States—California, the state with the most, had 141,000 entries—with more than 1.2 million pieces of information being entered in total.
“This shows the mass scale of the problem,” says Smith, who is presenting his findings at the Defcon security conference this weekend and previously published some details of the work. But the scale of the scamming is likely to be much larger, Smith says, as he didn't manage to track down all of the fraudulent USPS websites, and the group behind the efforts have been linked to similar scams in at least half a dozen other countries.
Gone Phishing
Chasing down the group didn’t take long. Smith started investigating the smishing text message he received by the dodgy domain and intercepting traffic from the website. A path traversal vulnerability, coupled with a SQL injection, he says, allowed him to grab files from the website’s server and read data from the database being used.
“I thought there was just one standard site that they all were using,” Smith says. Diving into the data from that initial website, he found the name of a Chinese-language Telegram account and channel, which appeared to be selling a smishing kit scammers could use to easily create the fake websites.
Details of the Telegram username were previously published by cybersecurity company Resecurity, which calls the scammers the “Smishing Triad.” The company had previously found a separate SQL injection in the group’s smishing kits and provided Smith with a copy of the tool. (The Smishing Triad had fixed the previous flaw and started encrypting data, Smith says.)
“I started reverse engineering it, figured out how everything was being encrypted, how I could decrypt it, and figured out a more efficient way of grabbing the data,” Smith says. From there, he says, he was able to break administrator passwords on the websites—many had not been changed from the default “admin” username and “123456” password—and began pulling victim data from the network of smishing websites in a faster, automated way.
Smith trawled Reddit and other online sources to find people reporting the scam and the URLs being used, which he subsequently published. Some of the websites running the Smishing Triad’s tools were collecting thousands of people’s personal information per day, Smith says. Among other details, the websites would request people’s names, addresses, payment card numbers and security codes, phone numbers, dates of birth, and bank websites. This level of information can allow a scammer to make purchases online with the credit cards. Smith says his wife quickly canceled her card, but noticed that the scammers still tried to use it, for instance, with Uber. The researcher says he would collect data from a website and return to it a few hours later, only to find hundreds of new records.
The researcher provided the details to a bank that had contacted him after seeing his initial blog posts. Smith declined to name the bank. He also reported the incidents to the FBI and later provided information to the United States Postal Inspection Service (USPIS).
Michael Martel, a national public information officer at USPIS, says the information provided by Smith is being used as part of an ongoing USPIS investigation and that the agency cannot comment on specific details. “USPIS is already actively pursuing this type of information to protect the American people, identify victims, and serve justice to the malicious actors behind it all,” Martel says, pointing to advice on spotting and reporting USPS package delivery scams.
Initially, Smith says, he was wary about going public with his research, as this kind of “hacking back” falls into a “gray area”: It may be breaking the Computer Fraud and Abuse Act, a sweeping US computer-crimes law, but he’s doing it against foreign-based criminals. Something he is definitely not the first, or last, to do.
Multiple Prongs
The Smishing Triad is prolific. In addition to using postal services as lures for their scams, the Chinese-speaking group has targeted online banking, ecommerce, and payment systems in the US, Europe, India, Pakistan, and the United Arab Emirates, according to Shawn Loveland, the chief operating officer of Resecurity, which has consistently tracked the group.
The Smishing Triad sends between 50,000 and 100,000 messages daily, according to Resecurity’s research. Its scam messages are sent using SMS or Apple’s iMessage, the latter being encrypted. Loveland says the Triad is made up of two distinct groups—a small team led by one Chinese hacker that creates, sells, and maintains the smishing kit, and a second group of people who buy the scamming tool. (A backdoor in the kit allows the creator to access details of administrators using the kit, Smith says in a blog post.)
“It’s very mature,” Loveland says of the operation. The group sells the scamming kit on Telegram for a $200-per month subscription, and this can be customized to show the organization the scammers are trying to impersonate. “The main actor is Chinese communicating in the Chinese language,” Loveland says. “They do not appear to be hacking Chinese language websites or users.” (In communications with the main contact on Telegram, the individual claimed to Smith that they were a computer science student.)
The relatively low monthly subscription cost for the smishing kit means it’s highly likely, with the number of credit card details scammers are collecting, that those using it are making significant profits. Loveland says using text messages that immediately send people a notification is a more direct and more successful way of phishing, compared to sending emails with malicious links included.
As a result, smishing has been on the rise in recent years. But there are some tell-tale signs: If you receive a message from a number or email you don't recognize, if it contains a link to click on, or if it wants you to do something urgently, you should be suspicious.
30 notes
·
View notes
Note
how does the element stuff work in you system? Feel free to answer privately or not answer at all!
Thought I'd done a post on this already, I'll assume I didn't because I'm always looking for a way to talk about this xD
An Introduction To EleWe »
EleWe is our elements and weapons system, it runs off ten elements and ten weapons - so it has a hundred possible entries - and because only one member per entry, it also runs off Phases.
Phases are a group of a hundred members, a Phase has to be completely filled before a new one opens. Phase III is actually just about to open, and we pray this does not break our database, which was only designed for the first two Phases, because we didn't think we'd exceed two hundred members. (It shouldn't, right? O-o) (I'm not bad at coding, I'm sure it won't-)
The Database »
Just a small section on the database. Our database runs by having all possible combinations as an entry, and having columns for each Phase. When searching the database, we look for things like "element in (x)" and "phase x is empty" (that's in English, I'm not going to write SQL here lmao)
Elements »
Okay so, elements. As I said, there's ten total elements, these are:
Cosmica | Dark
Sonia | Sound
Hydria | Water
Glaciera | Ice
Flora | Plants
Aria | Air
Lumina | Light
Terra (prev Eartha) | Earth
Inferna | Fire
Electria | Electricity
Each one has reactions to other elements. I used to have a list, no clue where it went (probably died when my pc corrupted), so I'll do this from memory (o-o;)
Cosmica + Lumina = Detonate
Sonia + Aria = Diffuse
Sonia + Electria = Boost
Hydria + Glaciera = Freeze
Hydria + Aria = Storm
Hydria + Flora = Grow
Hydria + Inferna = Vaporise
Hydria + Electria = Conduct
Glaciera + Aria = Blizzard
Glaciera + Inferna = Melt
Glaciera + Electria = Conduct
Flora + Terra = Sprout
Flora + Inferna = Burn
Flora + Electria = Burgeon
Aria + Inferna = Stoke
This was originally designed with The Kansukki Project in mind.
This list (with the reaction names) was only ever used in The Kansukki Project, whereas The Kīara'h Project just uses the reactions (have some random trivia)
Weapons »
As also said in the intro, there are ten weapons! These are: (listed with general classification and explanation if needed)
Axe [Short Range]
Bow [Long Range]
Crossbow [Mid Range]
Combat [Short Range] | Hand to hand combat
Gem [Mid Range] | Magic
Knife [Short Range - Long Range] | Depending on if you can throw / previously throwing knives
Polearm [Mid Range] | Death stick :)
Scythe [Mid Range]
Staff [Long Range] | Long ranged gem
Sword [Mid Range]
There were originally eight weapons but apparently we got OCDed ¯\_(ツ)_/¯ (more trivia)
So.. How Does It Work? (And Why?) »
Each member is assigned one element and weapon combination, usually this is based on their past. Each member can only specialise in that element.
(except if they have a copycat ability, such as Amethyst who studied more than one element and use their Sonia to mimic other's elements)
For weapons, it's a little different. Most members only have one, and although some members may know other weapons, they only specialise in one.
Mostly, these will be used within stories and headspace, however some members may be able to wield their weapons in the outside world.
Energy »
Another part of EleWe is elemental energy, it lowers by using abilities/powers and when lowering, can cause members to not be able to cast spells, or even, if it gets extremely low, can impact their body and physical/mental energy and can't recover on its own.
(I won't touch on this too much because it's more or less its own thing.)
Technical Notes »
Element reaction names source: an old post we made on The Kansukki Project's server.
If I remember correctly, this is EleWe v6, (technically v5, but I'm calling it v6, because it will be soon with Phase III)
Most of this was originally done for The Kansukki Project, not The Kīara'h Project, but it has since been adapted.
Kuro from MeD wrote this post (and is very unqualified to write this post)
Hope this answers your ask? Lol
#Kīara'h Asks#Kīara'h Asks : drowntowns#The Kīara'h Organisation#Kīara'h [MeD] Kuro posts#endo safe#pro endo#endo friendly#please send asks#i need more things to do lol
11 notes
·
View notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
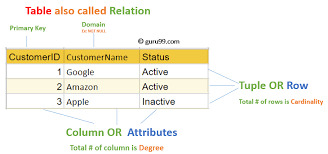
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
The SQL Server REPLACE function is a valuable tool for replacing every instance of a given substring in a string with a different substring. Let's Explore:
https://madesimplemssql.com/sql-server-replace/
Please follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
OR
Join our Group: https://www.facebook.com/groups/652527240081844

5 notes
·
View notes
Text
Optimizing Business Operations with Advanced Machine Learning Services
Machine learning has gained popularity in recent years thanks to the adoption of the technology. On the other hand, traditional machine learning necessitates managing data pipelines, robust server maintenance, and the creation of a model for machine learning from scratch, among other technical infrastructure management tasks. Many of these processes are automated by machine learning service which enables businesses to use a platform much more quickly.
What do you understand of Machine learning?
Deep learning and neural networks applied to data are examples of machine learning, a branch of artificial intelligence focused on data-driven learning. It begins with a dataset and gains the ability to extract relevant data from it.
Machine learning technologies facilitate computer vision, speech recognition, face identification, predictive analytics, and more. They also make regression more accurate.
For what purpose is it used?
Many use cases, such as churn avoidance and support ticket categorization make use of MLaaS. The vital thing about MLaaS is it makes it possible to delegate machine learning's laborious tasks. This implies that you won't need to install software, configure servers, maintain infrastructure, and other related tasks. All you have to do is choose the column to be predicted, connect the pertinent training data, and let the software do its magic.
Natural Language Interpretation
By examining social media postings and the tone of consumer reviews, natural language processing aids businesses in better understanding their clientele. the ml services enable them to make more informed choices about selling their goods and services, including providing automated help or highlighting superior substitutes. Machine learning can categorize incoming customer inquiries into distinct groups, enabling businesses to allocate their resources and time.
Predicting
Another use of machine learning is forecasting, which allows businesses to project future occurrences based on existing data. For example, businesses that need to estimate the costs of their goods, services, or clients might utilize MLaaS for cost modelling.
Data Investigation
Investigating variables, examining correlations between variables, and displaying associations are all part of data exploration. Businesses may generate informed suggestions and contextualize vital data using machine learning.
Data Inconsistency
Another crucial component of machine learning is anomaly detection, which finds anomalous occurrences like fraud. This technology is especially helpful for businesses that lack the means or know-how to create their own systems for identifying anomalies.
Examining And Comprehending Datasets
Machine learning provides an alternative to manual dataset searching and comprehension by converting text searches into SQL queries using algorithms trained on millions of samples. Regression analysis use to determine the correlations between variables, such as those affecting sales and customer satisfaction from various product attributes or advertising channels.
Recognition Of Images
One area of machine learning that is very useful for mobile apps, security, and healthcare is image recognition. Businesses utilize recommendation engines to promote music or goods to consumers. While some companies have used picture recognition to create lucrative mobile applications.
Your understanding of AI will drastically shift. They used to believe that AI was only beyond the financial reach of large corporations. However, thanks to services anyone may now use this technology.
2 notes
·
View notes
Text
ha megkerestek linkedin-en (recruiter) h van egy X cegnel allaslehetoseg, gaz ha inkabb en magam kuldom el a paprijaimat a cegnek? (megtalaltam oket direktbe linkedinen es allast is hirdetnek (linkedin + sajat weboldalon) )
mondjuk pingpong asztalt nem hirdetnek, mega weboldalukon a soc media linkek fele halott (fb es twitter accountok deaktivaltak), de allitolag 11-50 ember dolgozik ott , de glassdoor-on nincsenek jelen
(Edit: saját weboldalukon nem lehet jelentkezni,van egy generic email cím, meg LinkedIn állás,mégis a recruiter út lesz, hátha van belső kapcsolata)
ez nem hangzik borzasztoan:
Responsibilities
Develop quality software and web applications
Analyze and maintain existing software applications
Design highly scalable, testable code
Discover and fix programming bugs
Qualifications
5+ years of C#
5+ years of SQL Server
2+ years of Cloud services, ideally Windows Azure
Bachelor's degree or equivalent experience in Computer Science or related field
Desirable Skills or Exposure
AI and Large Language Models
Machine Learning
Big Data
The Package
Salary £55-65K per annum (depending on experience).
Remote & Physical Office (usually 1 day per week but not mandatory).
25 days holiday, plus UK bank holidays, plus discretionary extra Christmas leave (3 days). Increases after 3 years’ service to one additional day per year to a maximum of 30.
Share Options (EMEI Scheme).
4% employer pension contribution.
WFH allowance plus budget of £150 per year for home working expenses.
Simply Health Cashback plan.
Group Life Assurance upon death your family will receive 4x your salary.
Group Income Protection upon long term illness you will receive 75% of your salary.
Discretionary Bonuses in line with business performance.
Annual Salary review.
3 notes
·
View notes
Text
Grouping Data by Time Intervals in SQL Server: Hourly and 10-Minute Aggregations
In SQL Server, grouping data by time intervals such as by hour or by 10 minutes requires manipulation of the date and time values so that rows falling within each interval are grouped together. This can be achieved using the DATEPART function for hourly grouping or a combination of DATEPART and arithmetic operations for more granular groupings like every 10 minutes. Here’s how you can do…
View On WordPress
#10-minute interval grouping#datetime aggregation techniques#group by hour SQL#SQL datetime analytics#SQL Server time grouping
0 notes
Text
Building a multi-zone and multi-region SQL Server Failover Cluster Instance in Azure
Much has been written about SQL Server Always On Availability Groups, but the topic of SQL Server Failover Cluster Instances (FCI) that span both availability zones and regions is far less discussed. However, for organizations that require SQL Server high availability (HA) and disaster recovery (DR) without the added licensing costs of Enterprise Edition, SQL Server FCI remains a powerful and…
0 notes
Text
ChatNet Nulled Script 1.11

Download ChatNet Nulled Script – The Ultimate Private Chat Solution If you’ve been searching for a robust, real-time chat platform that’s easy to integrate and packed with features, look no further than the ChatNet Nulled Script. This powerful script enables seamless communication through public chatrooms, private messaging, and user management—all without the usual licensing fees. Now available for free, you can unlock its full potential from our website and start building your own advanced chat network today. What Is ChatNet Nulled Script? The ChatNet Nulled Script is a premium PHP AJAX chat room and private messaging solution. It’s designed for developers and webmasters who want to create a social environment on their websites or platforms without writing the backend from scratch. Fully responsive and built with a clean, modern UI, this script ensures a professional look while delivering top-tier functionality. Unlike traditional chat plugins, this standalone script doesn't rely on WordPress, making it a versatile option for custom platforms. Whether you're building a community forum, a private chat space, or a dating site, ChatNet gives you all the tools you need—without the hefty price tag. Technical Specifications Language: PHP, JavaScript (AJAX) Database: MySQL Frontend: Responsive HTML5/CSS3 Authentication: Built-in user login & registration system Compatibility: Works on all modern browsers and devices Features and Benefits Real-Time Communication: ChatNet supports real-time public and private messaging, creating a seamless user experience. Multi-Room Support: Create unlimited chat rooms tailored for specific topics or user groups. User Management: Built-in tools allow you to manage users, mute or ban troublemakers, and control access to specific rooms. File Sharing: Users can exchange images, documents, and other files directly within chat windows. Responsive Interface: Whether your users are on desktop or mobile, ChatNet delivers a fluid and intuitive chat experience. Why Choose the ChatNet Nulled Script? Many developers shy away from premium scripts due to their cost. That’s where the ChatNet Nulled Script comes in. By downloading the nulled version, you gain access to all premium features—completely free. You can install, customize, and deploy the script on unlimited websites without worrying about recurring license fees or restrictions. In fact, this nulled script is not just a smart solution for saving money—it’s a strategic move to accelerate your development cycle and provide better functionality to your end users. And if you’re exploring more tools like this, don’t forget to check out our collection of nulled wordpress themes for powerful design templates. How to Use ChatNet Nulled Script Download the ChatNet Nulled Script ZIP file from our website. Extract the contents and upload the files to your server. Set up the database using the included SQL file. Configure the script by updating the config.php file with your database details. Access the admin panel and begin customizing your chat environment. It’s that simple! With minimal setup, you’ll be running a high-functioning chat platform in no time. Use Cases Online Communities: Create a place where users can connect and share ideas in real-time. Customer Support Portals: Provide instant support to customers through private messaging and live chatrooms. Educational Platforms: Use ChatNet for student discussion forums, group projects, or Q&A sessions. Dating or Social Sites: Let users engage in private chats and public discussions easily and securely. Frequently Asked Questions (FAQs) Is the ChatNet Nulled Script safe to use? Yes, the version we provide is thoroughly tested and verified to be safe. It’s free from malicious code and ready for deployment. Can I use this script on multiple websites? Absolutely! Since this is a nulled version, you’re free to install and use it across multiple domains without license limitations.
Will I get future updates? While automatic updates aren't included, we regularly update our repository. You can always check our website for the latest nulled version of ChatNet. Does it support multimedia sharing? Yes, ChatNet allows users to share images, documents, and more, directly within the chat interface. Where can I find more scripts like this? For more high-quality tools and resources, visit nulled plugins, your trusted source for free premium scripts and themes. Conclusion The ChatNet Nulled Script is a top-tier chat solution for anyone looking to build a dynamic, engaging communication platform. With real-time messaging, admin controls, and multi-room support, it’s the perfect choice for developers who demand flexibility without financial constraints. Download it now and empower your platform with real-time interactivity and user engagement.
0 notes
Text
How to Create Interactive Reports in Power BI
In today's data-driven world, businesses need powerful tools to visualize, analyze, and share insights effectively. Microsoft Power BI is one such tool that enables users to create interactive, real-time reports and dashboards with ease. Whether you're a business analyst, student, or aspiring data professional, learning to build interactive reports in Power BI is a key skill that adds tremendous value.
If you're looking for Power BI training in KPHB, this article will guide you through the fundamentals of creating engaging, user-friendly reports in Power BI.

What is an Interactive Report in Power BI?
An interactive report in Power BI allows users to:
Filter and slice data with visual controls
Drill down into data for deeper insights
Use tooltips and visuals for storytelling
Explore data dynamically without editing the report
Interactivity transforms static charts into powerful data exploration tools.
Step-by-Step: Creating Interactive Reports in Power BI
1. Connect to Your Data
Power BI supports multiple data sources—Excel, SQL Server, SharePoint, and many more.
Open Power BI Desktop
Click on “Get Data” and select your data source
Load the data into your report
2. Clean and Prepare Your Data
Use Power Query Editor to:
Remove unwanted columns
Fix formatting issues
Create calculated columns or measures
Clean data ensures accurate and reliable reporting.
3. Add Visualizations
Drag and drop fields onto the canvas to create visuals like:
Bar and column charts
Pie charts
Maps
Tables
Cards and KPIs
4. Enable Interactivity
You can make your report interactive by:
Adding Slicers (e.g., date range, region, category)
Enabling Drillthrough pages for detailed views
Using Bookmarks and Buttons for navigation
Setting up Tooltips to show extra details on hover
These features allow users to explore data without altering the actual dataset.
5. Use Filters and Sync Slicers
Apply visual-level, page-level, or report-level filters to control what data appears. Sync slicers across pages to maintain consistency in filtering.
6. Publish and Share
Save and publish your report to the Power BI Service
Set up permissions and share with your team or clients
Schedule data refreshes for real-time updates
Tips for Designing User-Friendly Reports
Keep visuals simple and clear
Use consistent colors and fonts
Highlight key metrics using cards or KPIs
Group related visuals together
Use white space effectively for readability
Who Should Learn Power BI?
Power BI is essential for:
Business Analysts
Data Analysts
Project Managers
Marketing Professionals
Students aspiring to enter the data field
If you're in KPHB or nearby, enrolling in a Power BI training in KPHB can give you hands-on experience and help you master these concepts faster.
Frequently Asked Questions
Q1. Do I need coding skills to use Power BI? No! Power BI is designed with a drag-and-drop interface. Basic knowledge of DAX (Data Analysis Expressions) can be helpful but is not required for beginners.
Q2. Can I use Power BI for real-time dashboards? Yes. With the right data connection and refresh settings, you can build real-time dashboards.
Q3. Is Power BI free? Power BI Desktop is free. Power BI Pro and Premium offer additional sharing and collaboration features at a cost.
➡️ For more FAQs, visit our website.
Ready to Learn More?
If you're serious about mastering Power BI and want expert guidance, consider joining a Power BI training in KPHB. It’s a great way to build your skills and get certified under professional mentorship.
#PowerBI#DataAnalytics#BusinessIntelligence#PowerBItraining#KPHB#InteractiveReports#DataVisualization
0 notes
Text
Master SQL in 2025: The Only Bootcamp You’ll Ever Need

When it comes to data, one thing is clear—SQL is still king. From business intelligence to data analysis, web development to mobile apps, Structured Query Language (SQL) is everywhere. It’s the language behind the databases that run apps, websites, and software platforms across the world.
If you’re looking to gain practical skills and build a future-proof career in data, there’s one course that stands above the rest: the 2025 Complete SQL Bootcamp from Zero to Hero in SQL.
Let’s dive into what makes this bootcamp a must for learners at every level.
Why SQL Still Matters in 2025
In an era filled with cutting-edge tools and no-code platforms, SQL remains an essential skill for:
Data Analysts
Backend Developers
Business Intelligence Specialists
Data Scientists
Digital Marketers
Product Managers
Software Engineers
Why? Because SQL is the universal language for interacting with relational databases. Whether you're working with MySQL, PostgreSQL, SQLite, or Microsoft SQL Server, learning SQL opens the door to querying, analyzing, and interpreting data that powers decision-making.
And let’s not forget—it’s one of the highest-paying skills on the job market today.
Who Is This Bootcamp For?
Whether you’re a complete beginner or someone looking to polish your skills, the 2025 Complete SQL Bootcamp from Zero to Hero in SQL is structured to take you through a progressive learning journey. You’ll go from knowing nothing about databases to confidently querying real-world datasets.
This course is perfect for:
✅ Beginners with no prior programming experience ✅ Students preparing for tech interviews ✅ Professionals shifting to data roles ✅ Freelancers and entrepreneurs ✅ Anyone who wants to work with data more effectively
What You’ll Learn: A Roadmap to SQL Mastery
Let’s take a look at some of the key skills and topics covered in this course:
🔹 SQL Fundamentals
What is SQL and why it's important
Understanding databases and tables
Creating and managing database structures
Writing basic SELECT statements
🔹 Filtering & Sorting Data
Using WHERE clauses
Logical operators (AND, OR, NOT)
ORDER BY and LIMIT for controlling output
🔹 Aggregation and Grouping
COUNT, SUM, AVG, MIN, MAX
GROUP BY and HAVING
Combining aggregate functions with filters
🔹 Advanced SQL Techniques
JOINS: INNER, LEFT, RIGHT, FULL
Subqueries and nested SELECTs
Set operations (UNION, INTERSECT)
Case statements and conditional logic
🔹 Data Cleaning and Manipulation
UPDATE, DELETE, and INSERT statements
Handling NULL values
Using built-in functions for data formatting
🔹 Real-World Projects
Practical datasets to work on
Simulated business cases
Query optimization techniques
Hands-On Learning With Real Impact
Many online courses deliver knowledge. Few deliver results.
The 2025 Complete SQL Bootcamp from Zero to Hero in SQL does both. The course is filled with hands-on exercises, quizzes, and real-world projects so you actually apply what you learn. You’ll use modern tools like PostgreSQL and pgAdmin to get your hands dirty with real data.
Why This Course Stands Out
There’s no shortage of SQL tutorials out there. But this bootcamp stands out for a few big reasons:
✅ Beginner-Friendly Structure
No coding experience? No problem. The course takes a gentle approach to build your confidence with simple, clear instructions.
✅ Practice-Driven Learning
Learning by doing is at the heart of this course. You’ll write real queries, not just watch someone else do it.
✅ Lifetime Access
Revisit modules anytime you want. Perfect for refreshing your memory before an interview or brushing up on a specific concept.
✅ Constant Updates
SQL evolves. This bootcamp evolves with it—keeping you in sync with current industry standards in 2025.
✅ Community and Support
You won’t be learning alone. With a thriving student community and Q&A forums, support is just a click away.
Career Opportunities After Learning SQL
Mastering SQL can open the door to a wide range of job opportunities. Here are just a few roles you’ll be prepared for:
Data Analyst: Analyze business data and generate insights
Database Administrator: Manage and optimize data infrastructure
Business Intelligence Developer: Build dashboards and reports
Full Stack Developer: Integrate SQL with web and app projects
Digital Marketer: Track user behavior and campaign performance
In fact, companies like Amazon, Google, Netflix, and Facebook all require SQL proficiency in many of their job roles.
And yes—freelancers and solopreneurs can use SQL to analyze marketing campaigns, customer feedback, sales funnels, and more.
Real Testimonials From Learners
Here’s what past students are saying about this bootcamp:
⭐⭐⭐⭐⭐ “I had no experience with SQL before taking this course. Now I’m using it daily at my new job as a data analyst. Worth every minute!” – Sarah L.
⭐⭐⭐⭐⭐ “This course is structured so well. It’s fun, clear, and packed with challenges. I even built my own analytics dashboard!” – Jason D.
⭐⭐⭐⭐⭐ “The best SQL course I’ve found on the internet—and I’ve tried a few. I was up and running with real queries in just a few hours.” – Meera P.
How to Get Started
You don’t need to enroll in a university or pay thousands for a bootcamp. You can get started today with the 2025 Complete SQL Bootcamp from Zero to Hero in SQL and build real skills that make you employable.
Just grab a laptop, follow the course roadmap, and dive into your first database. No fluff. Just real, useful skills.
Tips to Succeed in the SQL Bootcamp
Want to get the most out of your SQL journey? Keep these pro tips in mind:
Practice regularly: SQL is a muscle—use it or lose it.
Do the projects: Apply what you learn to real datasets.
Take notes: Summarize concepts in your own words.
Explore further: Try joining Kaggle or GitHub to explore open datasets.
Ask questions: Engage in course forums or communities for deeper understanding.
Your Future in Data Starts Now
SQL is more than just a skill. It’s a career-launching power tool. With this knowledge, you can transition into tech, level up in your current role, or even start your freelance data business.
And it all begins with one powerful course: 👉 2025 Complete SQL Bootcamp from Zero to Hero in SQL
So, what are you waiting for?
Open the door to endless opportunities and unlock the world of data.
0 notes