#used a mix of ai photos and regular photos for this one
Text


Video game I saw in a dream. It was in this low poly style like an older video game. You play as this character I think was meant to be a lamb, or maybe a weird mix of a lamb a mouse and a rabbit, (while not really looking like any of those things) and you’re running away from a wolf. Your objective is to last as long as possible before the wolf catches and eats you.
The house you’re running in is endless and bizarrely put together like most building interiors in dreams are (like the infinite toilet dream dimension on Reddit lol) the layout of the house is pretty detailed, you can stop and hide in places like closets or bins while the wolf looks for you, you can go up and down stairs and into rooms etc.
You never actually know where the wolf is or how close it is to you until it appears in your line of sight, it makes no noise and the game gives you no way of knowing where it is, and it’s pretty unpredictable it doesnt move at a consistent pace. When the wolf catches you there’s an animation showing it eating your character
#the actual animation of the wolf eating your character wasnt scary he kind of just cartoonishly swallows the character whole lol#the scary part is being pursued by him and never knowing how close he is#i remember being surprised when i first saw the game bc it was presented to me as#a fun addictive sort of game kinda like a mobile app game#and then i see it and its a horror game and the creators are just completely oblivious to it lmao#dream art#<- thats my tag for all my dream-inspired art#art#gif#photomanipulation#digital art#liminal#weirdcore#used a mix of ai photos and regular photos for this one#the ai stuff is sooooo good for recreating what a dream looks and feels like#but i didnt use it too much bc i wasnt able to get the specific photos i wanted :/#hmmmm this is vore isn’t it
21K notes
·
View notes
Note
Hello! Not a kuro related ask but can i ask how can u tell if someone is a bot or not on tumblr? Also can they do any harm to your account?
⚠️ I originally expected to give a short answer, but there's actually a lot I can say about this, having become a regular target of bots. My blocked list has quite the collection! So it's kind of a long post.
How to spot bots and why they are bad
Some bots are easy to spot while others are not. And they are getting harder to spot, as whoever programs the bot generators is learning how to make them less noticeable. Or an AI that's been made is learning. 😳
Blog name patterns
You might have noticed how default blog urls here have four random words stuck together, and early bots used a similar pattern. But it has evolved. I recall seeing names that were two or three random words and a two digit number, typically from 20 to 50, presumably meant to be seen as a person's age. Like these:

Then a different pattern was used, like two or three words then a hyphen then a number. Then another, like a first name mixed in with random words, etc. Now, it's harder to see a pattern, so some bot names now look more (or less) random... more like real blogs. If you see a new follower with a random name, it doesn't mean much, but if you see more and more followers with names that seem to fit a pattern (and it's not simply the tumblr default username pattern), then chances are, they are bots created with the same or a similar program. Here's an example of getting new followers where the names seem too random to be real but you don't really notice until you get a bunch in a row, and the randomness is itself a pattern:
Profile pics that real tumblrs wouldn't choose
Often they used to have closeups of female faces. Now they still tend to have pictures of women, but not so zoomed in, and some even feature two women. Like here:
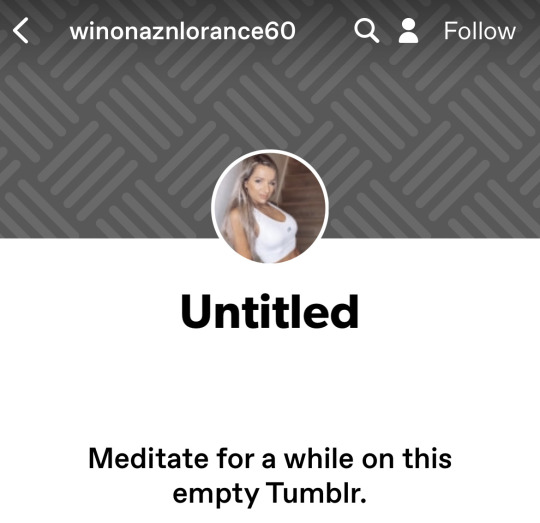
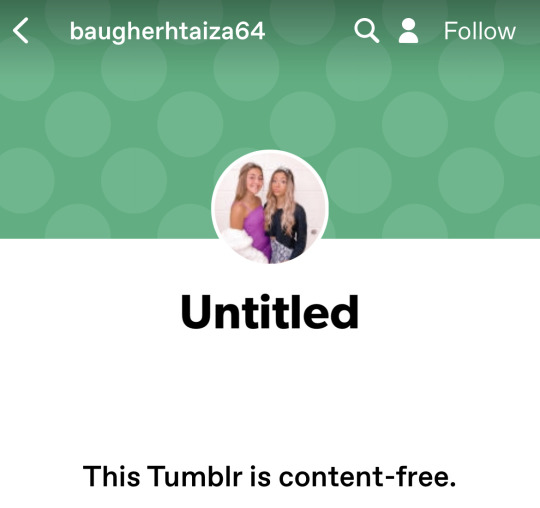

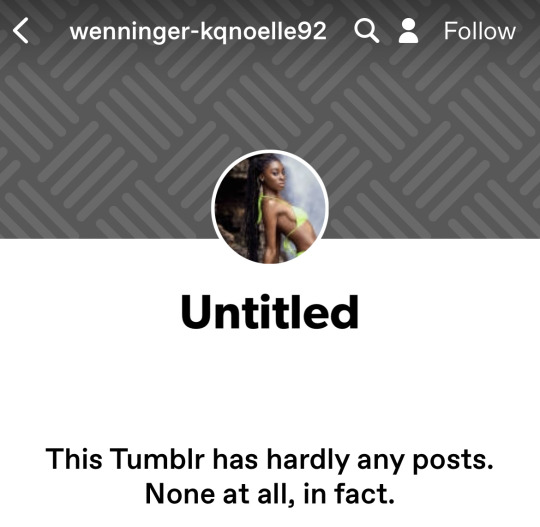
Notice that three of the above examples follow a naming pattern of what could be actual people names and a number. The fourth is like that, too, but with a hyphen tossed in.
And bots sometimes have default profile pics that may or may not be changed later, so watch out for default pfp's that later get replaced with pics of random women. Usually young and somewhat attractive. Most of the bots are geared towards attracting hetero men, hence the female pfp's of generally attractive women. The hope is we see one of these pics and think that's actually what the blogger looks like.
Truth is, Tumblrs rarely choose pfp's like that. This isn't the kind of social media platform where we typically show our faces (unless it's a personal fashion or cosplay blog, and then we are probably wearing makeup and costumes). We choose pics of plants and animals, fictional characters, historical figures, celebrities, artwork, etc. It's unusual for us to market ourselves based on personal appearance. So, when you see a blog with a pfp that looks like it's from Instagram or LinkedIn... or from a dating profile... it's probably fake. They are just random pics found online and essentially stolen from whoever originally uploaded them.
Default header images or more random women
Usually, bots have blank or default blog header images (see the examples above). I used to see a lot of bot blogs where the pic used for the header is the same as the pfp; those usually have descriptions where it's just a name and a suggestive emoji or a name and a plug for dirty pictures. Like:


More recently, they've started using images that show women who match or at least look like the women in their pfp's, but they aren't the same photos. Just like those pfp's, the header images are likely stolen from profiles elsewhere or random pics online. The ones that have header images that "work" with the pfp's also have a tendency to include links in their blog descriptions.
Sus blog descriptions or none at all
Most bot blogs lack blog descriptions entirely or just have a name or something about photos, like those examples above. But lately I've been seeing ones where there's a short description. In those cases, it's usually a link to who knows where, and it's best not to even find out. The text, whether there's a link or not, is usually an age (assume that's fake), something about the person's identity or preferences (often of a sexual nature), sometimes a reference to ranking on OnlyFans (it wants you to think any link there might take you to that sort of content), and a collection of oddly chosen emojis mixed into it.
Zero posts or sus posts and reblogs
A lot of legit blogs are created for the sole purpose of following content they want... and maybe asking questions, usually as anons. Those "don't follow me, I'm just lurking" type blogs rarely post or even reblog anything. Most bots also take this approach.
But some reblog sexually suggestive posts and some reblog more explicit content -- even links advertised as naughty games -- but the most realistic looking ones reblog a mix of sexual and innocuous, even innocent-looking content. As you scroll down through images of puppies, mysteriously inviting landscapes, and teacups next to open books... you eventually find images and even sometimes gifs of very mature content. Often with suggestive emojis and links that should be avoided at all costs. Some even just make one or two posts with links and leave the blogs untouched for years. Like this one:
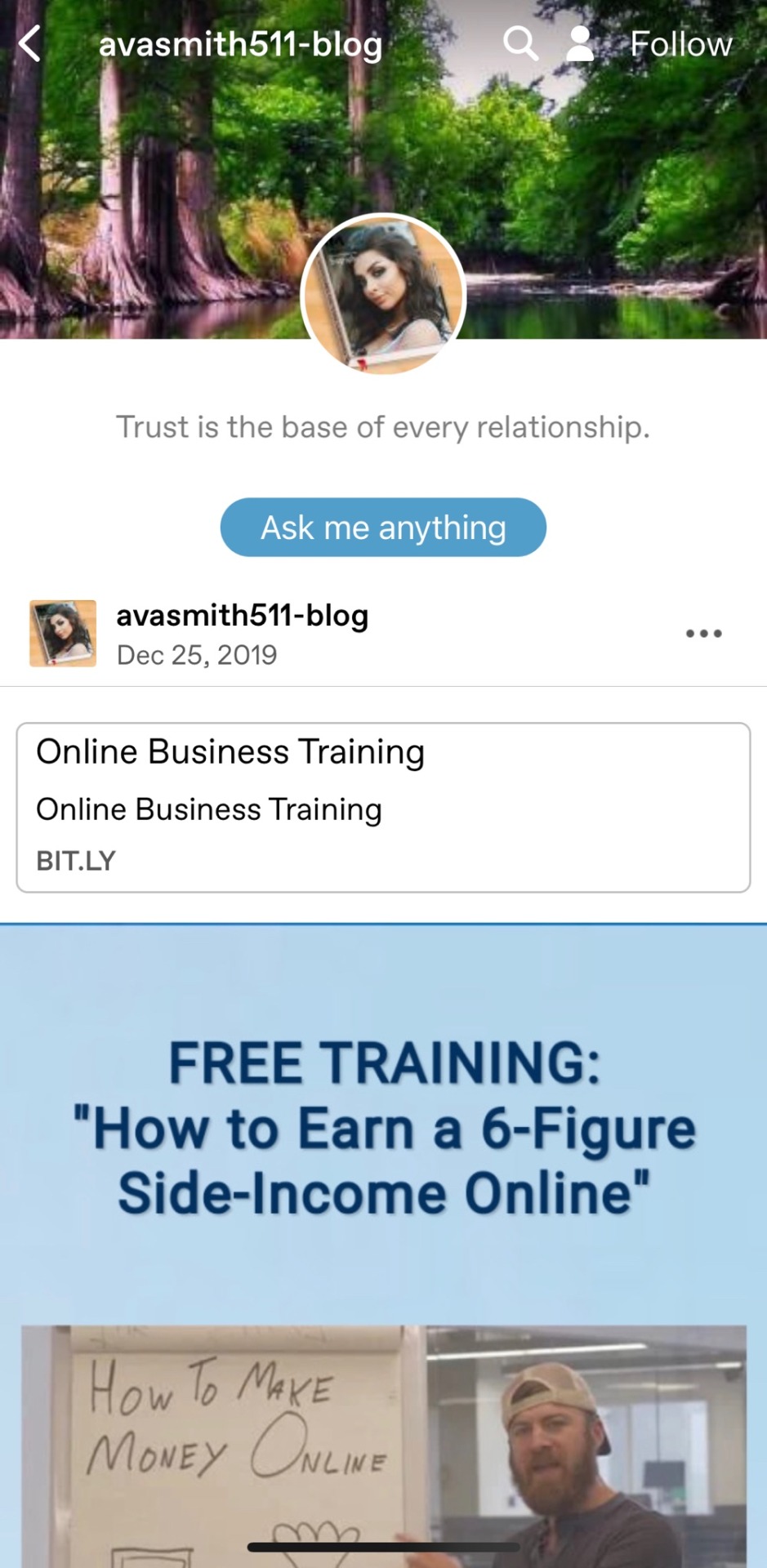

This blog only has one post, and it's from 2019. Claims about some free training program that'll earn you large incomes. Notice the tags on it are kind of generic, and some don't fit, like #home #decor #gardening. But it's a link to... something.
They might try to chat, but what they say is sus
It's very rare, in my experience, but I will occasionally get a dm from a random blog that just doesn't sit right.
Sure, sometimes a new follower will contact me to let me know they found my blog and enjoy it. Even longtime, mostly silent readers/followers will occasionally decide to reach out and privately tell me they were a particular anon in an ask... or simply that they finally found the nerve to say hi. That's all fine and dandy.
But when a new follower (who doesn't seem to share interests with you or has interests that don't match your blog topic) or a random content blog that doesn't even follow you just dms with "hi" or "how are you?", I get very suspicious it's just a bot. Their blog might look default or not but lacks content. It might be full of content that simply has nothing to do with your content. And they send a random starter message, completely open to your response. You can test them by asking if they are a bot. If they ignore that and respond with something like "I'm lonely" or "what are you doing tonight?", they are definitely a bot. If they say "no I'm not a bot" (or something like that) then ask leading questions like the "what are you doing" one, they might not be a bot, but they are likely just phishing/scamming.
One of the best tests is to ask them what they think about your own blog posts. If they ignore that and act like they might be following a script? Bot. If they say something very generic, like "I like it a lot" but immediately change the subject back to personal questions or something phishy (might also be a bit scripted)? Scammer. Either way, best to report the chat as spam, which will also remove the conversation from your view.
It's often not one thing but a combination
If you get followed by a blog that looks completely default, the best thing to do is maybe dm them to ask if it's a real person/legit blog. If they don't respond within a decent timeframe, they might just be too shy, but chances are they are a bot. If they respond with something that feels too general or scripted, probably either a bot or a scammer -- some are sleepers that wait for you to contact them. But a blog just being default doesn't mean it's bad; it could be a shy lurker or it could be someone new to tumblr who hasn't chosen pics, themes, etc. yet.
However, if you see a follower pop up (either new or their blog has changed since they started following), and the blog has some combo of the traits mentioned above, chances are super high it's a bot.
What bots do
I'm not entirely certain about all the different things they can do, and some of the things are likely more harmful than others.
I've gleaned a few ideas from posts I've read about the bots, though, including a good one I saw that had been reblogged by Neil Gaiman. I reblogged it from him, though I might have moved it to @aby-off-topic.
My understanding is that the same creator (person or program) makes a whole bunch of them. And there are probably many different individual creators, each making large groupings of them. Some of the bot blogs have content, usually of a sexual nature but occasionally not, like cryptocurrency or some random-sounding business venture. Those will have links to other sites, though some might actually link to other, related blogs in the same grouping. The content blogs also tend to be full of various tags, typically reusing key tags copied from the posts they reblog. If they have "original" posts, those will probably have the same key tags. The grouped content blogs boost each other and make their suspicious content become more noticeable to users who follow certain tags. It mostly clutters those tags with useless content, annoying those tag followers. But the point of them is to lure in the occasional individual who doesn't know any better; once they click a link, they could fall victim to stuff like:
Automatic exposure to malware
Mature content that requires payment (and might steal personal and financial information at the same time)
Phishing attacks of various kinds
Cryptocurrency and/or NFT scams
Companies that sell fake products (like cheap knockoffs, items that just don't work as promised, and items that are never shipped and might not even exist in stock/inventory)
People who try to recruit for MLM (multi level marketing), pyramid schemes, and similar money pits. These days it could still include wasteful timeshare programs, but now there are AirBnB scams and all sorts of things. Something that requires a time and money commitment and promises profit or some other benefit, but it just drains your energy and funds. Someone profits, but it's not you.
The bots that have no content except links in their descriptions are just hoping someone clicks. Then the unwitting person might fall prey to the same things listed above.
Bots that just follow but have zero content? Well, that's possible but not always true. The ones that truly have zero content might want you to interact with them in messages. Other bots don't have any posts or reblogs, but they might allow you to see the posts they've ❤️'d and/or the blogs they follow. You have to check out their Likes and Follow tabs to get this information, so it makes the blogs seem kind of legit and innocent. You are snooping around their blog, after all, right? But some of the posts they "like" and some of the blogs they follow will send unsuspecting individuals down a rabbit hole that might quickly lead to content blogs with those same suspicious links and too-good-to-be-true schemes.
Harming your blog
Ultimately, their main goals are to part people from their money and steal information. But they can cause problems for your blog, too. Like:
Decreased exposure 1: By making your posts disappear in a sea of junk posts with the same tags, it might be harder for new readers to find your content that matches their interests.
Decreased exposure 2: Similarly, people who follow certain tags and typically read your content that way might stop following those tags. They might choose to follow you directly, but they might not. They might unfollow a tag and then realize they don't recall your blog name. Some will be interested enough to figure it out and others won't.
Damaging your reputation: It's not common now, and changes to the website/app might have actually helped to stop this, but some blogs used to reblog others' posts with one or more images, remove the original text, then add their own links and tags. This happened to several of my old posts, too, and the alterations made it look like I'd posted manga panels or whatever with a link to a porn site or something. I had to report the reblogs and also assure readers that my original posts didn't contain these potentially harmful links. To get this remedied, I think I had to use a special reporting method that allowed me to give the Tumblr reps specific information about what the blogs were doing to my post content. I also explained that those blogs were doing the same thing to posts from other bloggers. Were they truly bots? Idk, but possibly.
Simply put, they can decrease your exposure to readers, make the tagging feature less useful for everyone, and even cause a PR nightmare for your blog. All in the name of trying to scam the occasional person who falls into their traps.
When you decide a blog must be a bot, please report them as SPAM (more likely to get it removed) and block it.
#off topic#but important#tumblr bots#stop the bots#how to spot them#why they are bad#anon asks#i answer#answered asks#this has been a psa#feb 25 2023#long reads#long post
100 notes
·
View notes
Text
Ahsoka spoilers/leaks
Ahsoka leaks compilation
Previous posts: TBOBF post-series | Kenobi (pre-trailer, post-series) | Andor (pre-series, post) | Mando S3 (pre-season, pre-finale, post)
Cast
There is another young actor playing Ahsoka (MSW). Very questioable sources (Nerdgasm) said she's played by Savannah Steyn.
Hayden Christensen (THR).
Darth Vader team (MSW, Bespin Bulletin), voiced by James Earl Jones AI. Fully suited Darth Vader will exclusively be played by Tom O’Connel. Tom O’Connel is being fitted for a new Darth Vader suit (different than the one used for Obi-Wan Kenobi last year). MSW
Ezra played by Eman Esfandi (Jordan Maison, THR). There were false reports of him being Mena Massoud.
"Riz" codename (The Illuminerdi) - a man in his 20s, described as a bit of a lone wolf, world-wise despite his young age and able to handle anything life throws his way. This character is listed as a series regular with options. [Most likely Ezra]
Sabine played by Natasha Liu Bordizzo (Deadline). There were false reports about frontrunners.
Hera (MSW), Mary Elizabeth Winstead (THR), Hera played by MEW (Bespin Bulletin)
Ivanna Sakhno (Deadline) plays Shin. According to The Illuminerdi, the character is codenamed “Astrid”, and is described as striking and ferocious. A formidable mercenary who must now decide between two paths. Astrid can either follow the path of her unit or take hold of her own aspiration in service of her own glory.
Ray Stevenson plays Baylan, previously thought as "Admiral" (THR). Loyal to Thrawn. He has a droid and an assassin by his side. Has a lot of screentime. (MSW)
Thrawn played by Lars Mikkelsen (guesses, KRT, Christopher Marc, MSW). There were contradicting reports by Jordan Maison.
Commander Rex (Christopher Marc) played by Temuera Morrison (BSL)
Captain Enoch (MSW) played by Wes Chatham (Deadline), Thrawn's bodyguard [Note: the article doesn't say he's Enoch, but it's hidden in the metadata of the article, viewable in view page source]
A new cyborg/droid character named Carnast who serves Thrawn and Baylan. Might be a Dark Trooper. (MSW)
Morgan Elsbeth (MSW)
Unknown character played by Matthew Law (DanielRPK)
Unknown character played by Shakira Barrera (DanielRPK, Jordan Maison, Charles Murphy)
David Tennant is back (reddit user PlayThenPause) as Hyuang
Mon Mothma (MSW)
Jacen Syndulla, has black hair (Lego set)
Barriss Offee (The illuminerdi). Most likely wrong and mixed with the "Barriss" codename which was actually for Sabine.
Officially revealed minor characters
Senators - Senator Mawood (Maurice Irvin), Senator Rodrigo (Jacqueline Antaramian), Chancellor Mon Mothma (Genevieve O'Reilly), Senator Xiono (Nelson Lee) and Gran Senator (Erica Duke)
Mark Rolston plays Captain Hale - Source
Hawkins, first officer in the New Republic, played by Nican Robinson (Lego set)
Beyta, a Mon Calamari lieutenant pilot in the New Republic (Lego set)
Porter, a New Republic captain pilot (Lego set)
Crew
All epsiodes were written by Dave Filoni.
Directors: Dave Filoni, Steph Green, Peter Ramsey (first reported by THR), Jennifer Getzinger, Geeta Vasant Patel (first reported by MSW) and Rick Famuyiwa.
Eric Steelberg and Quyen Tran are the Cinematographers - Source
Databank entries & officially released photos
Marrok (Inquisitor): Once an Inquisitor hunting Jedi for the Empire, the mysterious Marrok now works as a mercenary hired by Morgan Elsbeth to carry out dark deeds. Fully encased in battered battle armor, the warrior still carries a red double-bladed saber with a circular hilt.
Shin Hati: The eager apprentice of Baylan Skoll, Shin Hati is adept at lightsaber combat, a skill she uses in their work as mercenaries allied to Morgan Elsbeth, the former Magistrate of Calodan.
[Note: The Illuminerdi said Ivanna plays "Astrid" - "A formidable mercenary who must now decide between two paths. Astrid can either follow the path of her unit or take hold of her own aspiration in service of her own glory". This implies Shin will have to decide between following Baylan or betraying him].
Baylan Skoll: Baylan Skoll is lightsaber-wielding mercenary for hire overseeing his apprentice Shin Hati. But make no mistake: although there was a time when Skoll knew the acclaimed Jedi Knight Anakin Skywalker, Baylan is no Jedi. Now allied to Morgan Elsbeth, the former Magistrate of Calodan, after the fall of the Jedi and the Empire, Skoll remains a shrewd fighter in search of power who believes that another war is inevitable.
Magistrate Morgan Elsbeth: The coldhearted former Magistrate of Calodan, Morgan Elsbeth is an ally of Grand Admiral Thrawn and an enemy of the New Republic. A formidable fighter with a mysterious past, Elsbeth once hunted Ahsoka Tano on the world of Corvus before she was bested in battle and arrested for acting as an Imperial sympathizer.
Officially released 10 photos and their source episode - link. Sabine has short hair in episode 2.
Officially released concept art
Plot
Structure (MSW)
Ahsoka will have a midseason time-jump. The Rebels epilogue takes place in the middle of the season, and the season is like 2 different parts (four episodes each).
The first part of Ahsoka has New Republic centric-content which will feature Mothma. The first half of Ahsoka is a story about a failing New Republic, Ahsoka's warnings are ignored, and about Sabine.
The second part is finding Ezra and Thrawn. (MSW)
The "New Beyond" & Skeleton Crew
The Ahsoka show is gonna introduce concepts that are gonna be explored in Skeleton Crew. (MSW)
After Rebels, Thrawn and Ezra end up in a completely new and unexplored area of the universe, of which he calls ''The New Beyond” or “New Space'' until an official name is revealed. This region views and uses the Force differently, and magic users in the Star Wars universe we have seen before (like the nightsisters), originate from this place, and we have seen outcasts from there in past SW stories. (MSW)
Both Ivanna Sakhno and Diana Lee Inosanto's (Morgan Elsbeth) characters have a connection to this place. (MSW)
Skeleton Crew kids end up in this unexplored part of space too. (MSW)
World Between Worlds, Vader battle & different Ahsokas
The World Between Worlds is in Ahsoka too. (MSW)
We will get glimpses of Tano in other times and eras via The World Between Worlds. There is a version of Ahsoka in her late teens, one for another undisclosed time (might be present day Ahsoka in terms of the narrative itself), and finally for the version we saw in the final moment of Rebels in her white robes. (MSW)
Ahsoka will fight “Darth Vader” (Vader being dark side Anakin, not necessarily in the Vader suit) in more than one way and Hayden Christensen required some training for a sequence in the series because we will see his face again on screen, wearing the same costume he wore on Mustafar in Revenge of the Sith. (MSW)
We will see many possible outcomes for Ahsoka’s life and how in essence, no matter what, they all lead to a particular moment in her story. If Ahsoka had returned to the Jedi Order, she would be the one fighting Darth Vader on Mustafar having the high ground, not Obi-Wan Kenobi, because what happened had to happen, to get Tano to where she and the Skywalkers needed to be. Hayden Christensen filmed fight scenes with Clone Wars Ahsoka in this scenario. (MSW)
Through the World Between Worlds, it seems present day Ahsoka will learn that Anakin Skywalker was destined to take the path he did and we the audience will see aspects of those outcomes and in some of them we see live action Clone Wars era Ahsoka Tano played by a new actor in a duel with her former Jedi Master, taking the place of Obi-Wan Kenobi in this reality that never was. To be clear, these are glimpses or small sequences and Dawson will play Ahsoka during the majority of the story. (MSW)
Ahsoka will also see other visions in these sequences. Had Ahsoka killed Thrawn and Ezra Bridger did not need to use the Purrgil, Ahsoka’s destiny remained the same. The lesson for Tano appears to be that she cannot change her destiny and instead she must embrace it. (MSW)
There was an Obi-Wan corpse made. (MSW)
Ezra & Sabine
Ezra and Sabine have action scenes together (MSW).
MSW heard about a sequence in Ahsoka where Ezra uses the Force in a way compared to Luke Skywalker shattering the Beehive Hut on Ahch-To when he catches Rey talking with Kylo. However, the difference is one source saying and others confirming Ezra “hadoukens” with the Force. (MSW)
Sabine Wren uses Ezra's lightsaber. There are sequences with Sabine using the lightsaber with Ezra Bridger. It is not clear if Ezra gets another laser sword at some point or just finally takes his lightsaber back from her but she’s usually using it. (MSW)
Ezra developed his own martial arts based Force powers, not unlike Teras Kasi, but his own style. This martial arts style coupled with his connection to animals makes him an interesting take on a Force user on screen as he uses his hands, feet, the Force and nature to beat up undead Stormtroopers. (MSW)
Most of the scenes: Ezra doing Force Karate while Sabine swings the lightsaber around (MSW)
This series has more lightsaber fighting than probably anything we have seen on Disney+ (MSW)
We will have sequences where Baylon, Shin, have red sabers, Morgan Elsbeth and the witches standing off against Ahsoka with her two white lightsabers, Sabine with the green saber, and Ezra doing Force karate. (MSW)
Sabine will duel Shin with her red rapier laser sword while Ashoka Tano will fight Baylon’s red claymore lightsaber. The duel happens concurrently while Ezra fights Stromtroopers with his force Karate in the Nodian Highlands.
Thrawn and his minions
Will have an army “resurrected by dark side shadow magicks.” (MSW)
Zabrak troopers in white and burgundy uniforms (Christopher Marc)
Thrawn’s command ship, Chimera, is in the series. (MSW)
A survivor of Order 66, a Jedi named Babylon, fled to this unknown region of the galaxy for safety. Sources think Babylon wanted to maintain the Jedi way but was corrupted over time, maybe from the influence of life with the Nightsisters. (MSW)
"Nightsister" Morgan Elsbeth has a plan that the New Republic cannot respond to. "Nightsister" Morgan Elsbeh is searching for Thrawn, like Sabine and Ahsoka for Ezra. (MSW)
Elsbeth was extracting resources from the planet to build a ship capable of bringing Grand Admiral Thrawn back to the core worlds (ship or TIE fighters - some project to bring back Thrawn)
Baylon and Shin are in the core worlds initially and allied with Elsbeth. They are in both parts of the series. Baylon is dedicated to the mission to extract Thrawn and bring him home.
Thrawn has a new bodyguard named Enoch - MSW says looks like a "golden Destro from G.I. Joe with Samurai influences". They also have a new cyborg/droid character named Carnast.
Ahsoka and Sabine follow the Nightsister and her allies to Thrawn
A large fight will take place in a location that could be called "The Nodian Highlands." (MSW)
Kintsugi (MSW)
*In Episode IX, Kylo Ren visits an ape named Albrekh who fixes his armor (also an old MSW scroop). The mask is repaired using “Sarrassian iron.” The red iron is used to weld the red cracks of his armor together giving it that red veiny aesthetic.
*Ahsoka will riff on this aesthetic. Most of the Stormtroopers have been destroyed, their armor obliterated, much like Kylo’s helmet. However, instead of the red veins running through the rebuilt armor, these troopers have what has been described as “golden cracks” or “yellow veins” running through their exterior.
*The visual used in Episode IX is based on Kintsugi, a Japanese art which translates to “golden joinery.” Broken valuables use gold or silver to mend and join the broken pieces of antique or art. The process sees the breaks as part of the history of the object.
*MSW doubts it's “Sarrassian” as these troopers were “reforged” by The Nightsisters. MSW says: "In The Clone Wars, the Nightsisters of Dathomir had a green magic, but these are different Nightsisters from a new place and perhaps their magic is golden instead of green to match the Kintsugi look?"
*These troopers will be on the hunt, serving Thrawn, under the command of Baylon, but led into battle by the red sabered user named Shin. They will be tracking the reunited Ezra, Sabine, and Ahsoka.
*When the trio is finally reunited, they will face off against this new take on the Imperial Stormtrooper.
*Visually it will be a new evil Force user (Shin), red saber ignited and an armor with a battalion of reforged Stormtroopers with golden veins through their armor. Ahsoka, Sabine, and Ezra fleeing from them before being forced to fight.
The ending (MSW)
Ahsoka is basically The Empire Strikes Back of the “Mando Era”. The good guys fail in the end.
Ahsoka and Sabine inherit a secondary mission to stop Grand Admiral Thrawn and his cronies from returning to the core of the galaxy.
Thrawn returns to the main galaxy at the climax of the 8th and final episode of the season, with his forces all laid out before him. Thrawn revels in the moment, promising a reckoning is coming and ready to take on a faltering New Republic and take back the galaxy.
Most likely, the allies who sprung him from the far reaches of space have been a part of a power play he has had cooking for years.
The general consensus from those working on the show is that Ahsoka will have multiple seasons.
The story/cliffhanger will likely pick up in the second season of the series.
Looking at the grand scheme of things and the information MSW has been given, it’s likely that this attack/war is what will really allow the first order to rise.
Misc
Temple Ruins set photos (Bespin Bulletin)
MSW said that a woman seemed to want to be let in to what in the photo. He thinks the woman might have been Ahsoka, but he's not sure.
Ahsoka with white cloak will ride a loth-wolf (horse) nicknamed DOOM (MSW)
Ahsoka episode 1 is 54 minutes and 21 seconds long (credits at 51:06). Episode 2 is 42 minutes and 15 seconds long (credits at 38:33) (Cryptic HD)
---
Rosario's favorite episode is 5, Natasha's 1, Ivanna's 6.
---
"Sources" that are not included: Mike Zeroh, Doomcock, Hashtag Show, InsideTheMagic, Nick Santos, Giant Freaking Robot, fake "leaks" twitter accounts, 4chan, new accounts in wild rumors thread, etc.
#wooloo-writes#wooloo writes#star wars#sw#ahsoka#ahsoka series#ahsoka show#ahsoka spoilers#star wars ahsoka#ahsoka leaks#sw spoilers#star wars spoilers#ahsoka tano#sabine wren#ezra bridger#grand admiral thrawn#baylan skoll
31 notes
·
View notes
Text
US Major Step In Fight Between AI vs. Artists
So, we all know that a bunch of the creator strikes in America and a multitude of other countries associated with WGA and AFTRA have been for a multitude of different reasons. These are money, treatment, being taken advantage of by powerful companies and corporations. However, one big reason, specifically for the WGA Strike, is the use of AI. Companies and show creators in the industries refused to agree to not use AI prior to the strike, and this became one of the listed reasons the WGA Strike started.
Those of us who are content creators, artists of any media, and consumers of that media who spend time in those communities know that there are a lot of problems with this. For one thing, AI steals from works that have already been created. It also isn't actually AI, just machine learning. These co-exist to mean that if someone creates work with AI, there is no argument without rebuttal to be made that they aren't stealing or committing plagiarism. Another issue with AI is that it is extremely biased and is both socially and culturally harmful.

This is a photo created by a man named Matthew Allen using Midjourney AI and editing tools.
The photo above was AI generated. However, it still won an art contest at the Colorado State Fair. This is despicable in its own right but that's a whole different thing that we don't have time for right now. Matthew Allen was denied to have his work allowed Copyright protection because it was AI generated.

This is an image generated by a man named Stephen Phaler that was also denied copy rights.
This was made by Stephen Phaler, who also tried to make the case that his work was copyrightable. The court ruled against him, another promising sign for the creator community. This means that despite making his own AI Art system, he's works with it are still not protected. The software is his, but the art is not.
This is a major step in taking action against AI in courts. We need laws against AI to protect creators, because many of these efforts to do so have so far been unsuccessful through strikes and protests. All in good time, but for this is beacon of hope for us.
Not only have regular people who are unaware or refuse to acknowledge the harm of AI been using it, but people in academics have also used AI to do their work or assignments for them. Artists, writers, and musicians have been more hesitant to post their work because of AI algorithms stealing from them. If you look on AO3, any fandom, any type of work, you'll notice a large spike in restricted fics. This is because it's harder for AI to steal when only users with registered accounts can view many of the sites works due to restricted access.
The refusal of a federal judge in the U.S against AI is so undeniably important because not only will it hopefully prevent future AI users from making money off other people's work, but it's also a better way to spread words. Not everyone had Tumblr, or Twitter, or Reddit, or Facebook where you might hear about the dangers of AI and the algorithm only feeds you certain posts and things it thinks you want to see. Actually taking a legal stance against AI use and forcing restrictions is an excellent way to draw attention to the dangers of AI.
You'll also note there's various signs that a piece of artwork or writing was made with AI, for it lacks humanity. There's a post that said something alone the likes of, "Calling yourself an artist when you use AI Art is like buying box mix brownies and calling yourself a chef". This is one of the best examples of how ridiculous the use of AI art in genuine creative processes' are. It's not modernizing, it's theft and it's dishonest and lazy. You're not doing the work yourself, you're typing words and descriptions into a computer so it can do all the heavy lifting. That is horrible and dishonest.
Ultimately this post is about how we need more of this. We need it in other counties, we need to support our WGA and AFTRA strikes, we need to protect online and local creators who may not have as much voice when speaking out against AI. This includes famous, big names as well. This is all a positive step forward, and I encourage everyone to spread the word. Thank you for reading.
Tagging some mutuals who might be interested, but no pressure to reblog guys <3: @iammadeofmemoriesforlife @justanormaldemon @violets-and-books @rinadragomir @laylax13s @all-this-panic-still-no-disco @wesperbrekkered @grace-lightwoodd
#wga strike#wga strong#support the wga#sag aftra strike#sag aftra#aftra strike#sag strike#sag strong#support content creators#support artists#support musicians#support writers#writblr#artblr#musicblr#anti ai#ai artwork#ai art#ai image#ai pictures#fight ai#no ai art#no ai writing#ai is theft#ai is not art#ai is a plague#ai issues#united states#federal judge#important lore
13 notes
·
View notes
Note
Tom has been gay men's obsession since day one as an adult actor. I follow some gay male professional in the industry like writers and critics who used to talk about him in the grossest ways and even posted those fakes, which is super unprofessional IMO. But I guess talking about men in the way people used to openly talk about women is still okay. They do it with Timmy too, but the biggest obsessions for a decade are Bieber, Shawn Mendes, Tom, and the Chrises.
I'm surprised that the only people I've seen make a huge deal about the AI stuff is Taylor Swift and a couple of very young female celebs. it's a huge problem for all ages and genders, and not just sexual images. And I've seen a few regular people say they've found fakes of themselves made. Maybe the idea is that speaking out will draw more attention to it, but it's out of control. There was a point where I couldn't even click on a trending topic on Twitter without seeing the stuff mixed in or being joked about.
Thanks Anon.
Ugh, that is so unprofessional indeed. 🙄😔
Like you said, people shouldn't be talking about women in this way, or making sexualized AI images of them, and they shouldn't be doing it to men either.
If they were to put themselves in these men's shoes, they should ask themselves: How would I like it if strangers online were making fake manips of using my likeness and putting my face on a fake body, with sexualized imagery, making photos of me do all kinds of graphic sexual acts or poses? 🥴
🤔
5 notes
·
View notes
Text
How to find the business value in AI & ML

There are numerous approaches to determining the business value of AI and ML, and the most effective method will depend on the particular use case and sector. Typical techniques for determining business value include:
Automating repetitive tasks: AI and ML can speed up and lower the risk of errors in repetitive tasks like data entry and analysis.
Decision-making can be improved by using AI and ML to evaluate massive volumes of data and find patterns that help guide decisions. A retail business might, for instance, utilise ML to examine sales data and determine which products are most popular across various client segments.
Personalization: The consumer experience may be made more tailored with the use of AI and ML. A business might, for instance, utilise AI to suggest pro: AI and ML can be used to improve production, logistics, and supply chain management. A manufacturing organisation, for instance, could utilise ML to streamline its production process and cut waste.
Predictive maintenance: AI and ML are tools that can be used to foresee possible mechanical problems and downtime, reducing both downtime and maintenance costs.
Fraud detection: AI and ML can be used to identify and stop fraud, saving a business a lot of money.
Incttacks.
It's crucial to remember that determining the commercial value of AI and ML is a continuous process that calls for ongoing experimentation and testing, learning from the results of the deployment, and reacting to the feedback received. Additionally, it is important to take into account the solution's cost and scalability, which must be balanced with the advantages they offer.
READ MORE: JOIN THE BEST MACHINE LEARNING COURSE IN BANGLORE.
Meeting the potential of ML and AI
It is crucial to have access to a wide-ranging and sizable dataset, as well as computational resources to train ML models, in order to fully utilise the potential of machine learning (ML) and artificial intelligence (AI). In order to ensure that the models are trained on pertinent and high-quality data and can be used effectively to solve real-world problems, it is also crucial to have a team with a wide mix of expertise, including machine learning professionals and domain experts. Furthermore, it is crucial to develop and implement AI systems responsibly and openly, as well as to comprehend the ethical and societal ramifications of AI. Finally, in order to maximise the performance of ML and AI systems, it is critical to keep up with the most recent research and advances in the field.
Manual and ML and don’t mix
While there are undoubtedly scenarios in which combining human procedures with machine learning (ML) may not be the best course of action, they frequently complement one another and can be effective.
For instance, cleaning and preparing data for ML models might be done manually. This can take a lot of time and effort, but it is frequently important to make sure the data is reliable and that it can be utilized to train ML models.
ML models can be developed and utilised to automate specific operations or generate predictions after the data has been cleansed and prepared. To make sure the models are still effective and are not producing any blatantly wrong forecasts, it could be important to examine and update them on a regular basis.
In order to complete some activities with the needed level of accuracy and effectiveness, it may be necessary to combine manual and ML-based methods. In medical imaging, for instance, a radiologist might utilize ML-based algorithms to spot probable problems in a scan before manually going over the photos to determine the results.
In conclusion, it's true that manual and ML-based approaches can occasionally be challenging to integrate, but there are many circumstances where they can operate effectively together to accomplish a similar objective and enhance overall performance.
READ MORE: JOIN BANGLORE BEST JAVA FULL STACK COURSE ONLINE
0 notes
Text
Project Zero 2: Wii Edition and the Remake Dilemma

I’m a firm believer that remakes are typically losing propositions. There are cases that buck this trend as there always are (Resident Evil comes to mind), but when it comes to games that can be considered landmark titles in their respective genres, or just superbly made games, the benefit of a remake is limited to its availability on new platforms. This is something a port could accomplish with significantly less risk of messing with the integrity and intent of the original creation. Sometimes, though, games are completely overhauled for one reason or another. Project Zero 2: Wii Edition falls into this category.
A remake of the 2003 PlayStation 2 and Xbox release, known in the US as Fatal Frame II: Crimson Butterfly, Project Zero 2: Wii Edition uses two basic templates from which it forms its mold. The first is the original game. Fatal Frame II was a pretty big step forward from its predecessor. It maintained the basic underpinnings of exploring haunted old buildings and fighting ghosts by taking pictures of them with a magic camera, but it added some significant and interesting changes. In Crimson Butterfly you don’t go through the whole house of horrors alone. Your twin sister often tags along as your AI companion. This means she can alert you to the location of ghosts, and can also become the target of their attacks. The mechanics of camera combat are tweaked as well, where your proximity to ghosts is used to scale your damage up more than the time multiplier used in the first game. Because of this, ghosts often have jittery animations that make getting close to them risky and capturing them with combo inducing fatal frames difficult. The explorable area is also expanded out to several sometimes connected buildings and the space between those buildings in a small village compared to the single mansion that made up the first game.
Wii Edition borrows Crimson Butterfly’s structural framework practically wholesale. The level design in almost unchanged, the combat parameters are pretty much the same, and your AI sister manages to get in your way just about as often. What’s different is everything else. Shedding the fixed camera angles so common in survival horror games, Project Zero 2 takes its presentation from its console release cousin, Zero: Tsukihami no Kamen. Released four years earlier in 2008, Tsukihami no Kamen completely shifted how the Fatal Frame games were presented to players and how players interacted with them. The camera went from fixed and set tracking to being pulled in over the player character’s shoulder. It became dynamic, the player could direct it with a certain amount of freedom to focus on what they wanted to in the environment. Motion control was also introduced to more accurately convey the feeling of aiming a flashlight and camera around. It was a complete break from what the series had been doing up until that point, and Project Zero 2: Wii Edition fully embraces these changes.
The mix of classic Fatal Frame level design with modern Fatal Frame camera angles and control schemes produces mixed results. For lack of a better term, the game is clumsy. This manifests itself in some interesting ways. First is the unoptimized menu navigation. As you explore the Lost Village, you come across a variety of objects that reveal lore. Most of these are paper documents of various types. Picking one up will open the article so you can read it. To close it, you first press B on the Wii remote to stop reading, then press A to close the text. This might not sound so bad, not adjusting the purpose of a single button to match player intent in context-sensitive ways makes quickly navigating the menu both confusing to learn and quite difficult to do quickly. While the backstory to the Fatal Frame games is interesting and worth taking the time to investigate, repeat playthroughs don’t always require that you read a seven-page journal entry again. The menu system actively works against playing quickly or efficiently. Considering how much time players have to spend in menus, missteps here can add up to some significant time loss.
Time lost to players doesn’t seem to have been a concern for Koei Tecmo when developing this game as it also features unskippable cutscenes. Wii Edition is not a game that is overwhelmed by its pre-rendered scenes, but they are frequent enough that they disrupt play in regular intervals. For first time players, they probably aren’t something you’d want to gloss over as they provide guidance on what to do next but they are far, far less important for those who have played the game before. Not being able to skip these scenes is especially odd considering the odds that many people playing the remake of Crimson Butterfly also played the original and are familiar with the story already. Forcing players to watch cutscenes always ends up feeling like the player is having control taken away from them, and it’s especially painful here due to the more general issues with player control.
Perhaps the easiest target with regard to player control is how it feels to move the player character around. Unfortunately, Mio and Mayu feel very slow. Slow movement on its own is not a problem, but the game does not feel balanced around the movement speed. A prime example is the sluggishness of the quick turn. What was a snappy animation that turned you around 180 degrees in Tsukihami no Kamen became a set piece of animation reorienting the character that feels as if it’s playing back in slow motion. The animation itself isn’t even particularly slow, but the built-in delay to the starting of that animation makes the whole thing feel unnaturally labored. It’s a much less useful technique because of this. Timing it right during combat becomes more a test of how well you anticipate a ghost’s actions rather than how quickly you can react, which is unfair to ask of players when ghosts spend so much of their time hidden from player view.
The slow movement might have been the result of the game taking place in such tight quarters, a problem created when spaces aren’t redesigned to match the other changes. The slow animations feel like a safeguard against players running themselves into walls constantly or rushing past something they were supposed to pay attention to. This is taken to an extreme in one particular room where the player can walk through a pair of hanging curtains. Going through them triggers an especially aggravating animation of Mio nervously pushing the curtain back before stepping forward. These animations are triggered by proximity to the curtain rather than the on-screen prompt to press A like in nearly every other interaction in the game. It’s a particularly bad moment. If you just to happen to be ambushed by a ghost while doing this, suddenly you can rush through the curtains at full running speed with no issue, demonstrating the arbitrary nature of Mio’s movement limitations. Unfortunately, the forced pace feels like it creates more problems than it solves. Players just have to suffer through everything taking a bit longer than it probably should, with backtracking or getting temporarily lost compounding the problem.

Getting ambushed here is about as dirty a trick as the game can play.
Combat also suffers some unexpected clunkiness. All Fatal Frame games are a bit clunky when it comes to wielding the Camera Obscura, though this has the express purpose of making the game both challenging and tapping into the fear of the player, who might perform the wrong action due to a panicked state. In Zero: Tsukihami no Kamen, the imprecise motion controls of the Wii were mitigated by the lock on mechanic. One could argue this made the game a bit too easy, but Project Zero 2 for Wii goes very far in the other direction. The lock on keeps your camera in the vicinity of your nearest target, and the player must adjust their aim within the lock by rolling the Wii remote to either side or pointing it up or down. Locking on happens quickly and is accompanied by a satisfying shink sound that provides the player with positive feedback. Hearing it, you get the sense that the hard part is over and now it’s just a matter of waiting for a fatal frame chance.
Really, your photo album efforts are just beginning as the ghosts can easily disappear out of your lock on, reducing your spirit energy levels back to nothing. What you’re supposed to do is lock on, then diligently follow along, making minute adjustments to the position of the Wii remote in order to keep the ghost centered in the viewfinder. This is no easy feat, especially if your Wii remote calibration is off or you have a less than ideal location for the sensor bar. The semi-automated lock on and precision aiming feel at odds with one another. Adding in the analog stick of the nunchuck on top of that for turning your character around and you have three methods of controlling the aim of the Camera Obscura, all of which just get in each other’s way. Its lack of complementary components is all the more surprising since it had worked so much better in the previous Wii effort. While Tsukihami no Kamen’s combat could certainly have used some fine tuning, Wii Edition reduced that complete package back down to its individual pieces without remembering how they were supposed to fit back together.
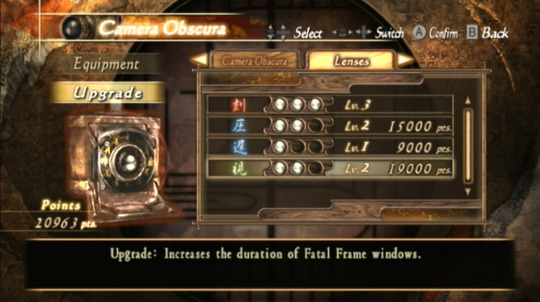
The game really forces you to upgrade as much as possible since your basic film does very little damage and getting fatal frame combos is quite difficult compared to the other games in the series.
A quirkier addition for combat scenarios is the blacking out of the screen during certain encounters. There you are, tracking a ghost as it glides around the room while you charge your spirit meter, when suddenly the room goes completely dark. You lose the ability of your filament to point you toward the ghost’s position right along with the ability to see anything. It’s supposed to add tension, maybe even give you a fright. The first time it happens, it gets close to accomplishing that. At the very least you’ll be surprised. That raising of the stakes fails to deliver once you figure out that the underhanded tactic of your spectral enemy goes away after a few seconds and in the meantime, you can just run around to avoid getting caught unaware. It’s a fun new trick to see once, but it doesn’t force the player to reassess their predicament or use new strategies to deal damage to ghosts. The same exact methods of evasion work just as well, you simply have to wait until the lights come back on to hurt your foe.
Since the game was released in PAL regions, it did receive localized voice acting in English. What might be a surprise to those of us in North America is that the dub was done with English voice actors, meaning it differs wildly from the original English language dub that was produced for North America and PAL regions. For those familiar with the original game, it’s quite off-putting to hear these new voices. For a game so rooted in being Japanese, non-Japanese voice acting always felt a little strange. To their credit, the actors who worked on Project Zero: Wii Edition did a fantastic job, and once you’ve become accustomed to it, I find that it often outshines the original English dub. Sadly, the English dub is the only one you can choose from despite its release in multiple European countries and featuring several language options for the subtitles and menus (I played the Italian release, complete with box art and manual, printed in Italian). The Japanese audio isn’t even available, which is a real shame, as it would have been nice to give the characters their presumed native language to give it that much more coherency. Of course, multi-language tracks were still uncommon in 2012, so you take what you can get.
Aside from getting an English dub, the greatest thing about the PAL release of Wii Edition is that it made the game available to a wider audience. If you only happen to have a North American Wii, however, you face the same kinds of problems trying to play this game as you do trying to play the fourth game. Without a PAL or Japanese console, you can’t simply pop a disc in and start playing. If you don’t want to invest in another console for a single game, then the easy answer is emulation. Wii emulation is in a very good state, so the game is easily playable on PC, though you are likely to get some audio stuttering and maybe a bit of slowdown. You can even get a USB sensor bar and pair your Wii remote with your computer to replicate the control scheme exactly. If you want to play on your North American console, you can also do that thanks to the robust homebrew community for the console. Bypassing the region lockout using sideloaded applications means you can play the game on actual hardware exactly as one would expect, and it works flawlessly. If you really want to, you can also track down an undubbed version of the game which features the original Japanese audio with the texts of the various PAL region languages.
With so many available options to play it, the question really becomes whether or not it’s worth playing. For anyone who loves Fatal Frame, the answer is easy enough. Yes. It’s interesting to see the game redesigned for a completely different perspective. It’s fun to hear the extremely different voice acting, and at its core, it’s very much the same type of game that all the games in the series are. You can’t really go wrong with it in that regard. For those who might be coming late to the series, I’d have to recommend the original over this version. Crimson Butterfly is readily available, can be played digitally in HD via the PlayStation 3, and simply holds up better as an overall package. If you love motion controls but only have room in your life for one Fatal Frame game to try, then you’re better off going with Zero: Tsukihami no Kamen. It’s more responsive animations, more appropriately designed locales, and tighter Camera Obscura mechanics make it the obvious choice. It also incorporates the Wii’s motion control gimmicks in interesting and surprising ways that truly enhance the experience, something Project Zero 2: Wii Edition curiously omits. For a remake, Wii Edition doesn’t make much of a case for itself being the definitive version. It acts more as a companion piece to the original, a super new game plus, almost. It’s one to come back to only once you’ve made your way through the rest of the series and still want more
3 notes
·
View notes
Text
Is spray paint cheaper than paint?
We know that the cost of paint is relatively high. So, it makes sense to use spray paints instead of painting. In addition, spray paints are environmentally friendly and can be used on all kinds of surfaces such as windows, walls, and doors. The only downside is that they are not as durable as regular paints.
Spray paint will leave a lasting impression on any surface it is used on, but it is important to remember that spray paints can be hazardous. Paint should always be applied sparingly and gently so as not to stain or damage the surface.
Spray Paints Are Cheaper Than Paint?
Spray paints are cheaper than paint, but there are still a lot of people who don't know about spray paints. The average person has no idea that the paint is cheaper than the spray paint.

Spray paints have been around for a long time and have been used by many professional artists, architects, and construction workers for over 100 years. But most people don't know about them because they are not very popular in the market and there isn't any brand name for them. In Painter Sprayer blog site proper guide you which will better for you.
One of the reasons why spray paints are not as popular as the paint is that they come in different colors so there is no brand name to identify it. Even though you can buy paint from any hardware store or even online, you will never be able to identify what kind of color you have bought because it will always be in shades
Spray Paint Prices Why Spray Paint Is More Expensive Than Regular
I am going to give you a brief overview of what is spray paint and why it is more expensive than regular house painting.
Spray painting is a method of applying paint that uses a machine to apply the paint directly to the surface, without the use of brushes or rollers.
It's very easy to use and it's fast, but it can be expensive. Spray paints are available in different colors and can be applied in various ways: by hand, with brushes, with a roller, or even by machines.
How to Choose Which Spray Paint is Best?
In this article, we will discuss the pros and cons of different spray paint brands. We will also discuss how to choose which brand is best for you.
We know that our breath can be a problem for other people. Therefore, we don't want our breath to smell bad. The choice of your spray paint brand is very important since you will have to use it on various surfaces such as walls, wall decorations, windows, and doors. So, we will discuss the pros and cons of different types of spray paint brands
Undercover Spray Paints' Secretive Prices & Benefits
Spray paint is a very popular product that can be bought in almost every household. It is used to decorate the interior of your home and also on the exterior of your home. But not everyone knows that there are some brands of spray paints that are very expensive, which means they are not worth buying.
This article will give you some tips on how to spot a fake spray paint brand and how you can get the best deal for your money.
Section topic: The Future of AI Writing Tools & Automated Writers' Tools (AI Writing Assistants)
Section keywords: Artificial Intelligence, AI writing tools, automation writers' tools, automated writers' tools, text-to-speech (TTS) software, speech recognition software
Good Reasons to Choose a Cheap Price over the Competition?
We should not think of these spray painting tips for beginners as a replacement for traditional spray painting. It is more like a "cheap" alternative to paint. It is just a tool to get the job done, but not an actual product that you can buy and use yourself.

Spray painting is a fun hobby for many people but it is hard to learn how to do spray painting. Spray painting is not like traditional painting where one can just spray a color, use a brush and then add water. to get the pigment in the paint. In fact, it is more like a photo editing and painting software. You need to be familiar with all aspects of paint technology, know how to mix colors, and have a good technique for applying these colors on painted surfaces.
Conclusion
In this article, we will show you how to apply graffiti-style effects using spray cans and brushes.
When you want to create a unique style for your website, you need to be creative and have good skills. Using these techniques will allow you to create unique designs that will make your site stand out from the rest.
1 note
·
View note
Text
Macbook Offline Netflix
Macbook Offline Netflix Review
Netflix Offline On Macbook
Inspire your students with thousands of free teaching resources including videos, lesson plans, and games aligned to state and national standards. Netflix is a video on demand we site which was put up on August 29, 1997, by Marc Randolph and Reed Hastings in California. Netflix is pretty much the online version of a local theater. People go there to watch movies, anime all over again, without having any restrictions on snacks not being allowed and chill.
Macbook Offline Netflix Review
Best apps live in Setapp
Replace Mac defaults and discover new gems in one suite.
If you use a MacBook, MacBook Air, or MacBook Pro for work, you’ve certainly thought about getting an external monitor at some point. Which is a 100% correct idea. Spending eight-plus hours every day hunched over the laptop on your desk won’t do your health any good long term. So a high-quality monitor is a must.
Naturally, the first thing that comes to mind here is the iconic Apple Cinema Display, which embellished the desks of most creatives for nearly over a decade. This Mac monitor was, however, updated in 2011 with the now ubiquitous Apple Thunderbolt Display.
Apple’s first Thunderbolt monitor was a beautiful and sturdy 27-inch LED screen. But after a few weak updates, it too, unfortunately, got discontinued in 2016 without any immediate successor. Although it’s possible to buy an Apple Thunderbolt Display secondhand today, it’s not a really good idea, since its specifications are quite outdated. Finally, in 2019, Apple released its brand new Thunderbolt 3 monitor — Apple Pro Display XDR.
Enhance your design with Setapp
Installing PIP on Linux Operating system is a bit different as compared to Mac and Windows. You need to check first if the Python is already installed or not. But if your Linux distro came with Python already installed, you should be able to install PIP using your system’s package manager. Before we start with how to install pip for Python on macOS, let’s first go through the basic introduction to Python. Python is a widely-used general-purpose, high-level programming language. Python is a programming language that lets you work quickly and integrate systems more efficiently. Modern Mac systems come with Python and PIP already installed. However, this version of Python tends to be outdated and not the best choice for serious Python development. It's highly recommended that you install a more current version of Python and PIP. Follow the instructions on the page and then after successfully downloading Pip3, run python3 get-pip.py in your terminal This will install pip3 into your laptop and then you can check the. Install python and pip mac.
Install a bunch of best design apps — all in one. Setapp will help you create, edit, and share visuals at little cost.
What’s Good And Bad About Apple Pro Display XDR
Unlike all previous Apple monitors, Apple Pro Display XDR is positioned as the ultimate creative machine in the top price bracket, starting at $4,999 for the base model. Wow.
What do you get for that price? The specs are truly outstanding. Let’s start with the 32-inch Retina 6K display, delivering up to 1600 nits of brightness (compared to about 300 in regular monitors), a 1,000,000:1 contrast ratio, and close to a billion colors. The dynamic range of this Apple screen is so broad that it far surpasses HDR (high dynamic range) and reaches XDR (extreme dynamic range).
Overall, Apple Pro Display XDR is stunning and can not only be used for Mac Pro but also be a great companion MacBook Pro display or even an extra iMac external monitor. The only downside is, of course, the price. While, $4,999 is what you start with, you could pay $5,999 for a model with nano-textured glass and $999 more for a Pro stand.
The top-tier cost of the Apple monitor 2019 model makes sense for professionals who rely on accurate color representation in their daily work, but seems to be overkill for almost everyone else. Luckily, there are lots of non-Apple displays on the market today as well. Why not explore some more options?
Close competitor: Dell UltraSharp 32-inch 8K Monitor
Those who really like Apple Display Pro but wished for a higher resolution at just a bit of a lower price would really love Dell’s 8K monitor. The same 32 inches here deliver a breathtaking 7,680 x 4,320 resolution. Although the contrast ratio is only 1,300:1 compared to Mac display’s 1,000,000:1.
While MSRP on Dell’s monitor is set at $4,999, most retailers sell them for somewhere between $3,499 and $3,899. Thus the screen fits in the niche between Apple 5K monitor that iMac has and Apple Display Pro XDR, and is also targeted at creative professionals.
Ultrawide: LG 34-inch 5K Nano LED Monitor
Free tetris for mac downloads. If you don’t need an 8K monitor (there’s in fact not much content yet made for 8K) and really enjoy having lots of screen real estate, why not take a look at LG’s 34-inch UltraWide 5K display.
This Thunderbolt 3 monitor features two HDMI, two USB-As, and one DisplayPort ports, as well as a headphone jack to make a perfect MacBook Pro display. The screen has an impressive 60 Hz refresh rate and 600 nits of brightness. All in all, a good investment at $1,499 MSRP.
Workhorse: LG 24-inch UltraFine 4K Monitor
Download word 2019 cracked. When you just need a monitor that does its job really well, look no further than LG’s 24” UltraFine 4K.
Besides giving you a beautiful 4K picture, this screen features three USB-C ports for all your external devices and 85 W power supply to become the perfect Mac display for any need. The price is reasonable too, somewhere around $700–800.
On budget: BenQ 27-inch GW Series Monitor
Some of you will see the prices above and go into shock mode — after all, you just wanted something simple to get the job done, not spend a laptop-worthy sum on a Mac monitor.
In this case, what you need is a BenQ GW Series display. Its 27-inch LED screen has a 2560 x 1440 resolution that gives you 77% more working space than regular HD monitors — certainly good enough for all everyday needs. The most impressive part, however, is the price. BenQ GW Series is one of the most affordable Mac displays and retails for just about $280.
So, here you go, the choice is yours, whether you’re ready to go all in with the Apple screen, take it down a notch with Dell, embrace the UltraWide with 34-inch LG, get to work with UltraFine 24-inch LG, or save some money and settle for 27-inch BenQ.
But since you’re interested in great Apple displays intended mostly for designers and creative professionals, it might be that you could benefit from a few essential apps that any designer would go crazy about.

Essential creative apps for every designer
It’s no secret that all designers cherish the typography on their Macs. Sadly, the built-in Font Book utility comes up short a lot. The absence of a customizable display of fonts and live comparisons make it hard to choose the perfect font. That’s where designers should try Typeface.
Typeface is a simple app that does a lot — giving you full control over how your collection of fonts is displayed. Mix system and custom fonts together, write any phrase to test the one you need, and group the best ones to use in a client project, all with ease.
Netflix Offline On Macbook
Aquarelo is another tool every designer needs, but not every designer knows exist. When beginning work on any project, it’s not too hard to come up with two primary colors. What’s much more difficult is to create a full palette out of them. Aquarelo does exactly that, giving you an easy way to generate up to 15 gradations between any colors, which you can input directly with HEX codes or using a color picker.
Goldie App is a must for those obsessed with grids. This tiny menu bar utility lets you create designs that follow the most perfect golden ratio. You can use presets or calculate your own grids in seconds, and Goldie always remains just a click away.
Luminar Flex helps those who would like to spend less time fine-tuning every photo in Photoshop or Apple Photos. It’s an essential plugin that leverages the power of AI to make perfect edits, beautiful filters, and automated workflows. Just a few quick steps and your whole day of shooting is perfectly corrected for exposure, contrast, and color.
Finally, Folio is the cornerstone of every design process — offering detailed version control in one place. No more multiple files saved on different Macs across the whole team. With Folio, everyone knows the exact workflow, can resolve conflicts quickly, and save the precious files that would otherwise be lost.
Simply keeping these five apps on your Mac will considerably simplify your working life: fonts in one place, grid tools handy, colors made for you, photographs edited, and everything version controlled.
Best of all, you can try Typeface, Goldie App, Aquarelo, Luminar Flex, and Folio absolutely free for seven days via Setapp, a platform with more than 200 apps that every Mac user would find incredibly helpful, whether it’s related to design, writing, managing, or even optimizing your own Mac. Just visit Setapp’s website and see for yourself!
Setapp lives on Mac and iOS. Please come back from another device.
Meantime, prepare for all the awesome things you can do with Setapp.
Read on
Sign Up
Setapp uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy.

0 notes
Text
June Small Wins
1 - ecmocard meeting with ppl from aussie to learn to sort out data. Felt better after the meeting cause i didnt feel like doing anything before. Got two season deli box cake from dapur cokelat for nessa. Videocalled w her and ren.
2 - dr eva chatted and gave things to do. I also need to make intern log for dr retha. I just cant bring myself to start. Finally mustered the courage. Im not the type of person for wfh. At least in this house. Finished reading love or hate. I rly felt like shit at night.
3 - started reading positively yours. Had no will to do anything
4 - some more sending spss work for dr eva. weekdays with no “outside work” rly render me useless in functioning. a vegetable
5 - iluni webinar. Lost my attention during electrolyte and fluid stuff. tried to cook ribeye steak lmao (meat from @/fridaymeatshop). Its too chewy and leathery. But its not too welldone. And at least it tastes good. Went to depok by krl. its quite quick since krl arrived just after im at poris and duri. went ahead of silvi devi. satpam on the lobby wont open the access hhhh (i dont have one. i dunno why. mom said she cant find it although we supposedly have 2). but my mood improved once im upstairs. we prepped a bit of deco. conversed in the dark so not to make racheel suspicious. surprisee. had truffle belly chicken cheese for dinner. the cheese was not to cheesy, its more of a gentle taste. mushroom tastes better. we watched sweet and sour from my mobile data. surprisingly, its not that much of data. slept at like 12-1ish
6 - the electric token went out in the morning. we went for a walk in ui. the PLK man across of st ui forbade us from going in. ugh. but it was rly empty. so we went from barel. its empty on the library. there was a dog that walked along with us. talked a bit in front of the lake. went back. i got 2 moon chicken (the basic flavor and not the wings) and spicy jumeokbap. the jumeokbap was nothing like what i had in korea. like the seaweed’s taste doesnt come out that much, and its not that flavorful/savory. the one in korea its good even by itself. went back to jkt nebeng reza silvi with devi. originally planned to go to flavola, but my head kinda hurts, so i finished my moon chicken at the mushola and asked juan to pick me up. still feel healthy and normal after going and staying out, so i started reading a book abt handwriting analysis lmaoo. fell asleep. tried several attempts to figure out my bpjs number and turns out the best there is to respond is BPJS’ twitter. the problem was solved under 5 mins.
7 - woke up, fell asleep again. Adita told me that i might be interviewed today for the ipd intern but theres no info. Did the registration stuff for my bpjs. Registered for npwp. Watched bts x na pd
8 - off to RSF. its audit day today. hiks to phonecall follow up work. i did not do anything inaco related, i just sat there and did dr dafsah’s excel. dr vera bought me pecel ayam hehe yay. went to como park to meet up with indah regen. tried ricotta pizza from pizza place (33k). the cheese is cheese but not that typical cheesy (?) coupled with mushroom. i had to add sauce to withstand the last bites (still kinda full). tried other’s as well, pesto and mushroom. pesto had the most taste. while waiting for doggo to arrive, we bought gelato (S: 35k). apparently their special flavor was ricotta lmao. tried green tea (bitter, which i like) and peanut butter + caramel, which makes you feel thirsty. watched the doggos from the sidelines. after maghrib we went to 1/15. ordered ice mocha (50k). the chocolate taste stood out more. not gonna order again lol. the staff initially recommended pandan flavor. took grab to gbk station to go home.
9 - rsf. second audit day. i hate it here lmao. im not even paid for my time here. excused myself to eat. turns out mbak Ai bought hokben. i almost forgot thanking her since i felt hungry with a bit of headache. talked a bit with dr retha regarding changes of assistant (since internship is soon). went back and immediately laid down in bed. mom bought pizza so thats what i ate for dinner. fell asleep (i can feel it. my face will get consequences)
10 - cant bring myself to do anything. i reread painter of the night lmao. seungho is a prick. inhun is also a prick (a greedy one). ate arirang bone marrow. put the egg-seasoning mixture to the pan since im not confident enough to just pour boiling water into the bowl. felt surprisingly full. went to sbux. green tea latte as usual. but turns out tumblr 50% promo only applies to sbux member. so i had to pay 40k for my green tea latte. at least i got to feel good from outside vibes. did some follow up for INACO patients.
11 - went to rm rsf. Took lots of photos of RM. I was given rujak by the rm staff lmaoo so cute. Didnt do any entry afterwards lmao i just laid down
12 - breakfast is paldo jjajangmen and egg. It tasted like soy. Its good but not in a micin way. Its quite fulfilling. Had some of the beef slices by putting it in a buttered pan (is it pan fried? Grilled? Idk). Had banana and brownies together (makes it rly good). Did a bit of clires work. I drank sbux's caramel macchiato but yall my stomach cant handle it lmao. It hurts so much that i even got a headache. So i just laid down in bed
13 - had arirang again loll. Inserted the egg to the pan still, but quicker this time. Its too salty today. Maybe its not enough water. I was eating it while googling how to remove excess sodium. Ate the rest of beef slices (shared with bros ofc) and mixed some with moms fried rice. Ate banana brownies again. Felt soooo full. Did some clires work accompanied by sbux matcha
14 - i felt like shit this morning. Watched leahs vid. Listened to her podcast while having bfast. I walked from moms car to bougenville while still feeling like shit. It slowly gets better afterwards, thankfully. Did some clires and follow up. Went to gandy steak in dr retha's car (which had anesthesiology textbook inside). Tried aus sirloin steak. The bread tasted ok. The garlic bread also ok. The mashed potato was so so (the one in depok was more creamy and smooth). The steak was good, especially the fat part, the sauce so so. Honestly that depok steak had more value for money compared to this, i think. Nebeng dr rara and husband to busway station. Arrived in ar and i immediately showered, such wow 👏👏
15 - today is no rsf day aka self made wfh day. Moms getting vaccinated today. I just lazed. And read kanej fics
16 - off to rsf. Took care of rm stuff. Tried social affair's croffle since i was so curious (60k [10k tip]). The nutella and cinnamon sugar one. Its crunchy and a bit crumbly inside, but not as fragile as croissant. Its quite fulfilling too. But its basically flour batter variations. (thats what mom would say). randomly chatted racheel and we ended up taking a walk and a bit of jog citra 6 (with my sneakon regular shoes). My left tendon was screaming lol. Picked up by juan who surprisingly effortlessly found the address at night.
17 - mbak aan chatted me today to go to rscm. Met prof murdani at pesc and he gave me ppt assigment for 13:30 THAT DAY. Finished it unsatisfyingly (i wish i couldve done more). Lunch was free bebek bkb yay thankyou Prof c: (he even asked what did i ate) took care of legalisir stuff. Went home by tj. Drank matcha w vsoy and i somehow was not sleepy after maghrib. I also changed my desj layout. Maybe it kinda works to separate my spaces
18 - arrived at rscm at 8-ish. sent updated thibbun nabawi ppt. literature search. and then somehow its 14:30. went to SCI w ara wani rasyid. tried bandeng nyonya, oyster, salmon, cumi lada garam (its crazy good among all the good tasting food wtff), shrimp and pocai telor (veggie stuff). dessert was thailand cassava. spent about 190k. went back by TJ. had wudu at pulomas and prayed ashar on the bus lol. i passed out after playing w my phone lmaoo
19 - spent almost the whole day just sleeping and eating. finally showered in the afternoon. had matcha vsoy latte after maghrib and with enough day sleeping, i did presentation outline. at like 1/2 am i initially planned to sleep but my eyes still have plenty of watts. so i read hold me tight. slept at like 4/5 am
20 - woke up at 9. off to om dokter’s house to ask for healthy letter. we talked almost the entire time im there lol. before u know it mom and dad’s done talking with grandma. om dokter shared some of his experiences in the past. and he said something about making your choice and living with it, and it will all have a meaning even if you might initially agonize about it. girl i was holding back tears. here he was talking about choices, something i never rly talk about at my house. im getting teary just typing this. he talked about it in a way that sounds simple, even though i agonized abt internship choices and sometimes avoid thinking about it. it rly rly was a new experience. i dont rly talk about “choices” with my parents. so hearing how to go through options in life from a person i can relate to regarding this med stuff is. i feel like i would have loved it if i can hear his wisdom earlier. i dont talk with him much if my parents are around bcs they will just meddle and say stuff that wreck my peace. they dont rly know what im going through but can be very opinionated. this peaceful one on one talk rly made me feel relieved and reassured. and i was today years old when i found out he initially wanted to be a psychiatrist. he would have been a great psychiatrist. i feel like we have some understanding thats left unsaid. like he knows how my parents are like. he would probably understand why i dont talk with him much at AR. after what feels super quick, we went back to AR. registered for STR. searched some literature for the topics that Prof is the moderator of. powered by matcha energy
21 - rscm as usual. the Prof did not come. lunch was bread i brought from home. waited for mom to pick me up at kfc so i bought pukis kfc. its like properly made pukis and not the street seller made ones. the chocolate one was good since the toppings generous. felt a bit feverish? like my body felt warm. fell asleep and then suddenly its 6 am in the morning.
22 - Prof still did not came. had amart’s ayam penyet jamur for lunch. turns out juan bought ayam geprek gendut for dinner. night time is diarrhea time lmaooooo. did not feel sleepy at AR but i skipped shower again lmao,,,,,,,, and then suddenly its morning again
23 - jajan from sisterfield today. tried their carrot cake and kopi susu gula aren. the carrot cake has that carrot texture. its different. the icing was fresh cream cheese that made the cake taste good. the coffee made my stomach ache a bit. it has that subtle chocolatey taste. fell asleep again. third time’s the charm (of 1x/day face wash). woke up at 3 am planning to sleep but i ended up washing my face. turns out atikah was still awake due to AZ fever.
24 - this is the bestest sleep i had in this week (?) had a dream about going to bandung and the car falling to water. forgot my headset today. can finally meet prof Mur. talked abt inaco stuff w agassi. reread komugi meruem lmaoo. felll asleep. somehow had the misfortune of hearing dad’s hurtful words to mom. i want to fall asleep again but its difficuly. i went through stages of pent up anger, some sort of selfishness (i will go out from jakarta for internship), amazement to mom, and... (continue 2moro)
25 - lunch was dori rice from kanprim thanks to rasyid’s jastip. watched bts’ butter norebang lolll :(((. arrived at AR the fastest ive been. mom came to me right before maghrib and summed some stuff dad said yesterday. she handled it in a trivial way. like she was unaffected. and that somehow helped me too. stuck around in the dining room for a while after maghrib. talked about internship w mom. i left some chance for dad to yap yap abt whatever related to internship (thankfully songs were full volume through my wireless headset) while im inhaling through my matcha latte. i wont write what he said bcs its lowkey super embarrassing. thank the gods for wireless speakers.
26 - did not do anything productive today. Had arirang salted egg for bfast (wont repurchase). Had the meat cubes i bought online and its rly good. Ran with racil at citra 6. The tendon in my left feet hurt lol. Gmeet with ara et al to discuss internship review
27 - lazed. Wanted to start my day early but couldnt bring myself to. Binge watched twoset videos. Did clires stuff. 1 more RM to wait from IRMIK. No gastro intern work this weekend aaaa im starting to panic.
28 - juan came along otw to rscm. Talked about iship otw. brought tons of stuff to eat, including matcha latte, but i was unable to finish it lol. Discussed research budgeting w Prof. Didnt do anything in home. Starting to panic with my ppt progress.
29 - discussed budgeting revision. Prof thought abt little details i didnt even consider. Didnt do anything while at ar anjengggg
30 - prof did not come to dept today. Listemed to agassi rambling abt intern stuff. Immediately opened my laptop in ar. Watched two set. Played marapets lmaooo i finally managed to gather 3 au for shop pricer. But still didnot wash my face 👁️👄🤦♀️ maybe bcs i hate doing what people tells me to do (re: shower due to covid scare). Had a nightmare abt being in a car ride alone w dad and it was rly rly awkward
0 notes
Text
Automotive And Car Design Software Program
Some cookies are required for safe log-ins but others are optionally available for useful actions. We recommend you accept our cookies to make sure you’re receiving the best performance and functionality our site can present. The C2B transmission format was chosen to provide maximum robustness for this automotive use case. The signaling scheme provides a ten× reduction in cable bandwidth requirements over other solutions.
Fully electrical automobiles have considerably fewer shifting elements and do not require engine oil.
Find out the way to accelerate automotive SoC design whilst minimizing the danger of systematic faults and constructing robust processes.
The lifetime of a car built in the 2020s is expected to be about 16 years, or about 2 million kilometres (1.2 million miles) if pushed lots.
As linked automobiles turn into mainstream, web connectivity will start to be perceived as some of the very important trendy car techniques, equally necessary because the engine and the steering system. While self-driving cars are still Car & Automotive far from becoming omnipresent, a totally linked car is already a new regular. Ultimately, one of many ways related vehicles will rework our lives will lie in increased value-effectiveness.
Andre Carrel Receives Five
Faced with the prospect of long term decline, OEMs who enter new layers of the worth chain (software and/or purposes) will proceed to be relevant in the trade of tomorrow. More vital is the truth that these software and utility focused Automotive layers are also greater margin businesses. A research by Strategy& discovered that whereas income share for hardware suppliers will decline, their share of trade earnings will decline way more considerably .

SEMICOLON GIVEAWAY: MINGYU DIGIPACK UNSEALED

By: @_cnehlezen @dokiwonu
Mechanics can be found in the picture:
– RT and LIKE this tweet
– must be following @dokiwonu @_cnehlezen
– You can do this daily with the ff tags @pledis_17 #SEVENTEEN#SEVENTEEN_BBMAs pic.twitter.com/xqhlMlpJlC
— car ♡ wonu au

(@dokiwonu) May 11, 2021
Plycar is ready to transport your automobile for you so you can relaxation simple understanding that your car is in secure palms. Wherever and whenever you need, you’ll be able to belief us to ship your vehicles securely. Ceramic substrates and particulate filters kind the core of world-class pollution control techniques in vehicles. Corning’s automotive products leverage some of our three best-in-the-world core applied sciences and four skilled manufacturing processes. To invent and make our products, we mix our deep knowledge of glass and ceramic science with professional capabilities in fusion, extrusion, and precision forming. The born-digital model Lynk & Co uses Connected Vehicle Cloud to supply an at all times connected expertise.
Engines
There continues to be an increased danger that world passenger automobile demand could drop to 70m or beneath if the present financial recession turns into additional entrenched or a second important wave of the virus happens post-lockdown. Adhering to new security norms, i.e. frequent plant sanitization, carrying of face masks, and temperature checks upon entry – Daimler and Hyundai have resumed production at their Alabama crops within the final week of April. The UAW union has additionally given a go-forward for its members of the Detroit 3 Car to return to work. Other automakers plan to observe similar protocols, including modifying layouts and floor plans of manufacturing websites to have fewer workers at each work station. All these further safety measures will limit the pace of ramp-up and eventual production line rates. Even earlier than the pandemic, the trade was careworn financially from increased emissions-related upgrade prices and elevated R&D investments in rising technologies.
What’s The Most Unreliable Car You’ve Ever Owned? – Jalopnik
What’s The Most Unreliable Car You’ve Ever Owned?.
Posted: Mon, 10 May 2021 12:31:00 GMT [source]
With over 70 million cars produced final 12 months, it’s no surprise producers are in search of out equipment and ways to reinforce manufacturing. Similar to present transportation services like Uber or Lyft, a person would summon a Zoox automobile for a journey by way of an app on their smartphone. With over eight million autonomous miles pushed thus far, Waymo’s 360-diploma perception technology detects pedestrians, other automobiles, cyclists, highway work and different obstacles from as much as 300 yards away. Whether their expertise is for use in public transportation, journey sharing or personal wants, the following firms are at the forefront of autonomous car technology. Though many imagine personal, autonomous automobiles are the future, there are multiple ways in which AI and machine learning are being applied in how vehicles are built and how they function on the highway.
Welcome To Brown’s Car Stores
Expert automotive software program improvement services should enhance performance and reduce the complexity of a contemporary car, which, in fact, is a heterogeneous system of embedded computer systems. While a vehicle requires an enormous information processing capacity, features like automation, connectivity, and electrification type an underlying kernel of automotive software program growth. On the one hand, it’s the delivery of sophisticated automotive software options as the result of our automotive development providers. On the opposite hand, it’s a important need to ensure a high degree of software program efficiency. In 1879, Benz was granted a patent for his first engine, which had been designed in 1878. Many of his different inventions made the use of the inner combustion engine feasible for powering a automobile.

We need clients to come again repeatedly – however never for a similar issue. Lightyear One is an extended range photo voltaic electric vehicle designed to be grid independent and to drive anyplace. Its unique car structure and expertise have been developed with excessive efficiency in thoughts, allowing Lightyear One to devour only eighty three Wh/km — two to three instances much less energy than some other electrical car on the market right now. This ends in an exceptional range of 725 km with the bottom emissions, the lowest charging frequency and 7,000 to 20,000 kilometres of free, effortless and clear photo voltaic range every year. With Spain and France having gone into lockdown in mid-March, new automobile sales fell by nearly 70% in each market. Sales in Germany, the most important market within the region, dropped by practically forty%.
The post Automotive And Car Design Software Program appeared first on dansealsforcongress.
from WordPress https://ift.tt/33FeFrG
via IFTTT
0 notes
Text
Privacy Protection through Biometric Data Protection
Misuse of Biometrics Infringes on Privacy
Biometrics are becoming commonplace in today’s cybersecurity practices, especially in authentication. Companies are collecting various types of databases filled with employee and customer biometric data ranging from a person’s walking gait to their voice patterns, retina scans, facial data, fingerprints, and even DNA. These databases can be used for single purposes, like authenticating access, or for large-scale surveillance, like in China (Ng, 2020). Misuse of biometric data can severely threaten human privacy, even if it wasn’t stolen. For example, the Chinese government log over 6.8 million records of people over the age of 8 in their country. They actively use their facial recognition technology and data to find, detain, and watch Uyghur Muslims in and after re-education concentration camps (Ng, 2020).
Stolen biometrics are just as concerning, especially if the data is posted publicly. In August, 2019, one of the largest biometric companies in the world, Biostar2, was breached (Ikeda, 2019). About 28 million biometric records were posted, unencrypted, on a public website. These included facial recognition profiles, fingerprint scans, and log in credentials (Ikeda, 2019). Anyone could use these to enter a building, unlock a phone, or make a fake ID, and they still can because a person can’t change their face or fingerprint like they would a password. Once a person’s biometric data is available to the public, it will always be public. This makes biometric data one of the most sensitive and critical to keep secure. Concerned System Administrators are justified in finding advanced protective techniques to keep biometric data safe from people who would misuse it.
Techniques to Protect Biometric Data
The best defense is to use multiple layers of the newest technology and algorithms. The following techniques are ones currently in practice, but it should be noted that none are used alone. For example, a biometric database that uses blockchain, a virtual machine monitoring system, and a correct RFID scan before giving a user access is much safer than one using just a single method.
Merkle Tree Blockchain
Blockchain, a type of Distributed Ledger Technology (DLT), is the technique of having devices in a connection share a new encrypted key between each link, as if in a chain (Alruwaili, 2020). These keys act as a device, and user’s, authentication for the duration of their session, which is inevitably closed. When the connection is severed, the session keys are discarded. The devices in the link can act as a record for transactions, which helps with auditing. This technique also allows for privacy because only the end device needs to know the Personal Identification Information (PII) for authentication, while all other devices in the chain only need to trust its neighbors, so the PII isn’t handed off through devices. Furthermore, if any of the keys are altered, like in a (wo)man-in-the-middle attack, the chain is broken.
Blockchain works best in what’s called a “Merkle Tree”, which is simply setting up a network’s logical connection in a hierarchical map (Kou, He, Xiong, & Lv, 2020). Privileged and Administrative users are at the top of the “tree” and are fewer in number. Lower down, the structure fans out as different and separate sections are connected, containing department heads and regular users. Combining Blockchain with the Merkle Tree model lets networks grant access based on roles and levels. The higher a system is on a tree, the more permissions it has (Kou, He, Xiong, & Lv, 2020). This would, for example, grant access downward, but not upward, as a System Administrator would need encrypted connection to a user, but a regular user shouldn’t have privileged access to a network server or database.
Multifactor Authentication
At an “end point”, the last device between a connection and a user, final authentication methods need to assure the correct human is asking to connect (Shalaby, Gad, Hemdan, & El-Fishawy, 2021). Physical barriers also need to be able to know whether to unlock or let someone through. Giving the wrong person access to a device or building can wreak catastrophic results. “Multifactor Authentication” simply means testing a person’s legitimacy and identity in more ways than one. It can be something someone has, something they know, something they are, or somewhere they are. Biometrics obviously cover what a person is, and something a person knows is usually a password (Shalaby, Gad, Hemdan, & El-Fishawy, 2021).
Two of the most current popular Multifactor Authentication methods are phone applications and RFID, or Radio Frequency Identification. A phone application can act as something someone has, where they are, and what they know, because the users phone is a unique item only they should have, the geolocation of the device in use should match where the user should be, and to unlock and approve the push notification, the user needs to know their pin to unlock the phone, and then the pin to approve the notification. A bank, for example, can approve authentication through the banks mobile app on the user’s phone as well as iris recognition software at ATM locations, before letting them access an account or withdraw money (Shalaby, Gad, Hemdan, & El-Fishawy, 2021).
RFID badges are usually given to employees as cards on lanyards and, while they can be stolen, work well as an extra step in the authentication process. These cards usually come with a photo ID and microchip with user data that fills into access logs and checks certain constraints (Fu, 2020). For example, a person may look like an employee, have stolen their RFID badge, and gotten through the front door, but if it’s after 6PM, the turnstile might reject admission because that employee is only allowed to enter during work hours.
Artificial Intelligence
Artificial Intelligence is a program given networking power based off decision trees and real-time data (Alruwaili, 2020). This means that the running software will work its way through “if-then” scenarios to reach choices depending on what information it’s given. These decision routes can be set in a way that covers future scenarios that make the program appear to “adapt” in a way to new situations. This can be used to make sure an employee is entering at the correct time of day, as mentioned before, or even to determine whether a digital certificate should be issued, as with Blockchain (Alruwaili, 2020).
Another highlight is creating a decentralized governance in a network by making several of these programs which only allow data or a user through to the next AI if certain conditions are met (Alruwaili, 2020). This way, an attacker wanting Facebook’s facial recognition technology, used to automatically suggest tagging friends, can’t simply fool one program to gain access. This technique is one of the best options because code can be obfuscated and as many separate layers as wanted can be set up in defense. This can be further extended by putting each AI on a different device in a logical network (Alruwaili, 2020). Other variants of this technique are Virtual Machine Monitoring and Fog Computing. Virtual Machines are separated systems that can take and compare snapshots of devices in a network, keeping an eye out for intruders (Nirmala, & Muthurajkumar, 2020). Fog Computing is the strengthening of authentication techniques in nodes, which are devices between endpoint devices and cloud systems, or internet spanning networks (Fog Computing vs. Cloud Computing: Key Differences | SaM Solutions, 2019).
Doubling Down on Biometrics
If a company has one type of biometric for their customers, they may consider using another type of biometric for their employees. That way, they have a smaller database to keep from imposters, and a separate kind of data to protect from cyber intrusions. For example, an employee might have to pass a fingerprint and iris scan, along with one or two of the previously mentioned layers of protection, in order to have access to a facial recognition database. This way, employee records aren’t saved with customer records, and certainly aren’t protected in the same way. The redundancy of using the same biometric to access biometrics is best explained with the Multifactor Authentication theory (Shalaby, Gad, Hemdan, & El-Fishawy, 2021). For example, it’s unsafe to unlock something someone knows using something someone knows, like being given a password in exchange for just a person’s date of birth and nothing else.
As with every technique given, biometrics, even to protect other biometrics, work best mixed and diversified with other practices. For example, biometrics can be used to produce a session key, which cannot be stolen or reproduced because the same biometric is required to open the session again (Kim, Wang, & Seo, 2020). Paired with Post-Quantum Cryptography, cryptography created to be resistant to quantum algorithms, this kind of authentication is fast and secure.
Conclusion
Whether it’s systemic abuse of biometric data, thieves impersonating victims of breaches, or a government employee’s fingerprints being posted online, the misuse of biometric data is an unacceptable consequence of a vulnerable network. Several layers of the newest techniques, technology, and algorithms are the backbone of a network’s defense and offense. This data can be abused and reused because a person can’t change their biometrics. So as the use of biometrics grows, the concern for privacy should as well.
References
Alruwaili, F. F. (2020). Artificial intelligence and multi agent based distributed ledger system for better privacy and security of electronic healthcare records. PeerJ Computer Science, 6, e323. https://link.gale.com/apps/doc/A643261296/CDB?u=lirn55593&sid=CDB&xid=724e67b2
Fog Computing vs. Cloud Computing: Key Differences | SaM Solutions. (2019, September 10). Www.sam-Solutions.com. https://www.sam-solutions.com/blog/fog-computing-vs-cloud-computing-for-iot-projects/
Fu, M.-H. (2020). Integrated Technologies of Blockchain and Biometrics Based on Wireless Sensor Network for Library Management. Information Technology and Libraries, 39(3), NA. https://link.gale.com/apps/doc/A654984075/CDB?u=lirn55593&sid=CDB&xid=2ea47813
Ikeda, S. (2019, August 27). Breach of Biometrics Database Exposes 28 Million Records Containing Fingerprint and Facial Recognition Data. CPO Magazine. https://www.cpomagazine.com/cyber-security/breach-of-biometrics-database-exposes-28-million-records-containing-fingerprint-and-facial-recognition-data/
Kim, A., Wang, C., & Seo, S.-H. (2020). PCA-CIA Ensemble-based Feature Extraction for Bio-Key Generation. KSII Transactions on Internet and Information Systems, 14(7), 2919+. https://link.gale.com/apps/doc/A635538097/CDB?u=lirn55593&sid=CDB&xid=e3c7efe0
Kou, J., He, M., Xiong, L., & Lv, Z. (2020). Efficient Hierarchical Authentication Protocol for Multiserver Architecture. Security and Communication Networks, 2020, NA. https://link.gale.com/apps/doc/A624417181/CDB?u=lirn55593&sid=CDB&xid=ba67d327
Ng, A. (2020, August 11). China tightens control with facial recognition, public shaming. CNET. https://www.cnet.com/news/in-china-facial-recognition-public-shaming-and-control-go-hand-in-hand/
Nirmala, E., & Muthurajkumar, S. (2020). A Four-Layer Robust Storage in Cloud using Privacy Preserving Technique with Reliable Computational Intelligence in Fog-Edge. KSII Transactions on Internet and Information Systems, 14(9), 3870+. https://link.gale.com/apps/doc/A643530219/CDB?u=lirn55593&sid=CDB&xid=2cb269cf
Shalaby, A., Gad, R., Hemdan, E. E.-D., & El-Fishawy, N. (2021). An efficient multi-factor authentication scheme based CNNs for securing ATMs over cognitive-IoT. PeerJ Computer Science, 7, e381. https://link.gale.com/apps/doc/A653504894/CDB?u=lirn55593&sid=CDB&xid=074b20a2
0 notes