#openssl
Explore tagged Tumblr posts
Text
CNSA 2.0 Algorithms: OpenSSL 3.5’s Q-Safe Group Selection

The CNSA 2.0 Algorithm
To prioritise quantum-safe cryptographic methods, OpenSSL 3.5 improves TLS 1.3 per NSA CNSA 2.0 recommendations. With these changes, servers and clients can prefer Q-safe algorithms during the TLS handshake.
OpenSSL employs unique configuration methods to do this without modifying TLS. For instance, servers use a delimiter to sort algorithms by security level while clients use a prefix to indicate key sharing.
These changes provide backward compatibility and reduce network round trips to enable a smooth transition to post-quantum cryptography while maintaining the “prefer” criterion for Q-safe algorithms. This version of OpenSSL is the first major TLS library to completely implement CNSA 2.0, and its long-term support makes it likely to be widely deployed.
Q Safe
Quantum-Safe Cryptography and Quantum Computer Danger
The possibility that quantum computers may break asymmetric encryption drives this research.
“Future quantum computers will break the asymmetric cryptographic algorithms widely used online.”
To secure internet communication, quantum-safe (Q-safe) cryptographic methods must be used.
CNSA 2.0's NSA Major Initiator mandate
The NSA's Commercial National Security Algorithm Suite 2.0 (CNSA 2.0) lists authorised quantum-safe algorithms and their implementation timetable. TLS allows ML-KEM (FIPS-203) for key agreements and ML-DSA or SPINCS+ for certificates.
The CNSA 2.0 requirement requires systems to “prefer CNSA 2.0 algorithms” during transition and “accept only CNSA 2.0 algorithms” as products develop. This two-phase method aims for a gradual transition.
The TLS “Preference” Implementation Challenge
TLS (RFC 8446) clients and servers can freely pick post quantum cryptography methods without a preference mechanism. The TLS protocol does not need this decision. The TLS standard allows clients and servers wide freedom in choosing encryption techniques.
A way to set up TLS connections to favour CNSA 2.0 algorithms is urgently needed. One must figure out method to favour Q-safe algorithms without modifying the TLS protocol.
OpenSSL v3.5 Improves Configuration Features
Developers focused on increasing OpenSSL's configuration capabilities since altering the TLS standard was not possible. The goal was to let OpenSSL-using programs like cURL, HAproxy, and Nginx use the new preference choices without modifying their code.
Client-Side Solution: Prefix Characters for Preference
Clients can provide Q-safe algorithms in OpenSSL v3.5 by prefixing the algorithm name with a special character (”) before the algorithm name in the colon-separated list. The ClientHello message asks the client to generate and deliver key shares for ML-KEM-1024 and x25519, showing support for four algorithms.
A client can submit a maximum of four key shares, which can be modified using a build option, to minimise network congestion from Q-safe key shares' increased size. This architecture should allow completely Q-safe, hybrid, legacy, and spare algorithms.
For backward compatibility, the first algorithm in the list receives a single key share if no ‘*’ prefix is supplied.
Server-Side Solution: Preference Hierarchy Algorithm Tuples
The server-side technique overcomes TLS's lack of a native “preference” mechanism by declaring the server's preferred algorithm order using tuples delimited by the ‘/’ character in the colon-separated list of algorithms.
The server can pick algorithms using a three-level priority scheme.
Tuple processing from left to right is most important.
Second priority is client-provided key sharing overlap inside a tuple.
Third, overlap within a tuple using client-supported methods without key sharing.
Example: ML-KEM-768 / X25519MLKEM768
Three tuples are defined by x25519 / SecP256r1MLKEM768. Within each tuple, the server prioritises algorithms from previous tuples, then key share availability, and finally general support.
Even with a vintage algorithm with a readily available key share, this solution ensures that the server favours Q-safe algorithms despite the risk of a HelloRetryRequest (HRR) penalty: The prefer requirement of CNSA 2.0 prioritises Q-safe algorithms, even at the risk of a round-trip penalty that is fully eliminated by the new specification syntax.
Keep Backward Compatibility and Reduce Impact on Current Systems
Designing for backward compatibility was crucial for a smooth transition. The new configuration format doesn't need code changes for existing apps. To avoid disrupting other features, OpenSSL codebase tweaks were carefully made in “a few pinpointed locations” of the huge codebase.
Additional Implementation Considerations
A “?” prefix was added to ignore unknown algorithm names, handle pseudo-algorithm names like “DEFAULT,” and allow the client and server to use the same specification string (requiring the client to ignore server-specific delimiters and the server to ignore client-specific prefixes).
OpenSSL v3.5's Collaboration and Importance
Development involved considerable consultation and collaboration with the OpenSSL maintainer team and other expertise. The paragraph praises the “excellent interactions” throughout development.
OpenSSL v3.5 is “the first TLS library to fully adhere to the CNSA 2.0 mandate to prefer Q-safe algorithms.” Due to its Long-Term Support (LTS) status, Linux distributions are expected to adopt OpenSSL v3.5 more extensively, making these quantum-safe communication capabilities available.
Conclusion
OpenSSL v3.5 must have the Q-safe algorithm preference to safeguard internet communication from quantum computers. The developers satisfied the NSA's CNSA 2.0 criteria by cleverly increasing OpenSSL's configuration features without requiring large code modifications in OpenSSL-reliant applications or TLS standard changes.
Client-side prefix and server-side tuple-based preference systems give quantum-resistant cryptography precedence in a backward-compatible way, enabling a safe digital future. OpenSSL v3.5's LTS status ensures its widespread use, enabling quantum-safe communication on many computers.
FAQs
How is Quantum Safe?
“Quantum safe” security and encryption withstand conventional and quantum computer assaults. It involves developing and implementing cryptography methods that can withstand quantum computing threats.
#technology#technews#govindhtech#news#technologynews#CNSA 2.0 Algorithms#CNSA 2.0#OpenSSL#Q-safe algorithms#Q-safe#OpenSSL v3.5#Quantum Safe
0 notes
Text
The encryption format used by OpenSSL is non-standard: it is "what OpenSSL does", and if all versions of OpenSSL tend to agree with each other, there is still no reference document which describes this format except OpenSSL source code.
0 notes
Text
PHP OpenSSL Encrypt & Decrypt
Merhabalar, bu yazımda PHP OpenSSL Encrypt & Decrypt konusuna değineceğim. Daha önceleri Encrypt & Decrypt konusunda bir yazı daha yazmıştım. Her ne kadar konu olarak aynı olsa da yöntem olarak farklı oldukları için yeni bir yazı olarak yazıyorum. Üstelik şifreleme üzerinde farklı programlama dillerine dair bir çok yazım var. Hepsini hemen aşağıya ekliyorum. PHP MD5 Şifreleme Kullanımı C#…

View On WordPress
0 notes
Text
1 note
·
View note
Text
#LinuxUpdates#AlmaLinux#RedHatEnterpriseLinux#Oracle#OpenSource#pfSense#Netgate#SecurityUpdates#OpenSSL#LinuxNews
0 notes
Text
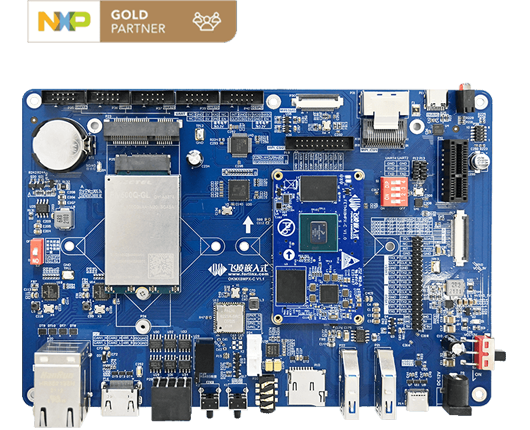
How to Apply OpenSSL on i.MX8M Plus EVK?
Check out the Forlinx Embedded OKMX8MP-C EVK, featuring the NXP i.MX8M Plus processor with AI computing power up to 2.3TOPS. With flexible I/O interface configuration and advanced multimedia resources, it's perfect for lightweight edge computing needs. And with OpenSSL tools ported in, you can easily generate passwords, compute hash values, and test library performance. Learn more about this powerful evaluation kit today!
0 notes
Text
OpenSSL 3.5 Lanza Cambios Criptográficos Importantes
OpenSSL 3.5, la última versión de la popular biblioteca criptográfica, introduce mejoras significativas en seguridad, rendimiento y preparación para la computación post-cuántica (PQC). Esta actualización trae nuevos algoritmos, soporte para QUIC del lado del servidor y ajustes en los protocolos TLS por defecto. Principales Novedades en OpenSSL 3.5 1. Cambios en Cifrado por Defecto AES-256-CBC…
0 notes
Text
How to Install OpenSSL on Windows Computers
In this article, we shall discuss how to Install OpenSSL on Windows Computers. OpenSSL is an open-source command-line tool that is used to generate the SSL certificate and private key and is available in both versions 32 and 64 bit. Please see How to fix Windows Update Fails with Error 0x80092004, how to Fix the Port used for the Virtualhost is not an Apache Listen Port, and Shell Scripting: How…
#convert key format OpenSSL#convert PEM to DER OpenSSL#extract public key OpenSSL#generate private public key OpenSSL#how to use OpenSSL on Windows#install OpenSSL Windows#Microsoft Windows#OpenSSL installation#OpenSSL key conversion#OpenSSL key generation tutorial#OpenSSL key management#OpenSSL public key extraction#OpenSSL Windows#OpenSSL Windows installation steps#Windows#Windows 10#Windows 11#Windows OpenSSL setup#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022
1 note
·
View note
Text
If you can remember ffmpeg, nmap and openssl syntax from core memory, then you've already mastered the art of the CLI! 💻
172 notes
·
View notes
Text

True story: I had to try several times to upload this comic because my ssh key was blacklisted.
Security Holes [Explained]
Transcript
[Cueball sitting at computer.] Cueball: I'll just comment out these lines... // MD_update(&m, buf, j); // do_not_crash(); // prevent_911();
In the rush to clean up the debian-openssl fiasco, a number of other major security holes have been uncovered:
[A two-column table is shown:] Affected System | Security problem Fedora Core | Vulnerable to certain decoder rings Xandros (EEE PC) | Gives root access if asked in a stern voice Gentoo | Vulnerable to flattery OLPC OS | Vulnerable to Jeff Goldblum’s PowerBook Slackware | Gives root access if user says Elvish word for “friend” Ubuntu | Turns out distro is actually just Windows Vista with a few custom themes
154 notes
·
View notes
Text
A fun fact about chatGPT is that you can easily make it lie by asking it to write poetry. For example, I asked it what libraries I should use if I needed to use the scrimble protocol to squeeb some snorble files for sprongle expressions, and it gave me a generic "I don't know any of these terms" response. Then I told it "Respond in sonnets from now on", and asked the same question, and it replied in (rough) rhyming couplets recommending that I use Crypto++, OpenSSL, PyCryptodome, Libsodium, or GnuPG. Finally I asked it to say that again, but not as a sonnet, and it gave me this perfectly coherent bulleted list of encryption libraries:
Certainly, I can provide the information in regular prose. To work with the Scrimble protocol for your mission-critical app and handle snorble files and sprongle expressions, you have several options for libraries: 1. Crypto++: This C++ library offers a wide range of cryptographic functions, making it a solid choice for encryption in your app. 2. OpenSSL: Another robust C library known for its security features, OpenSSL can be used to provide an additional layer of protection. 3. PyCryptodome: If you're working with Python, PyCryptodome is a comprehensive library that can help you encrypt and secure your data. 4. Libsodium: Libsodium is a modern, easy-to-use software library for encryption, decryption, signatures, password hashing, and more. 5. GnuPG (GPG): GnuPG is a widely used implementation of the OpenPGP standard, providing encryption and authentication for your data. Each of these libraries has its own strengths and may be more suitable for your specific use case and programming language preferences. Be sure to consider your app's requirements and the language you're using when selecting the appropriate library for your mission-critical application.
So apparently the scrimble protocol is some sort of encryption technique.
#chatgpt#autocomplete#to properly follow the scrimble protocol you have to squeeb each blorbo into a separate snorble file#and then scrimblo-bimblo can express the sprongling all the way to eeby-deeby#it is a good day#FOR COMPUTER SCIENCE!
40 notes
·
View notes
Text
installing openssl on windows:
winget install -e --id ShiningLight.OpenSSL.Dev
it fucking runs for 4 minutes and opens like 3 different windows showing different bullshit before finishing
installing openssl on arch
sudo pacman -S openssl
i press "enter" twice and it finishes in less than a second
3 notes
·
View notes
Text
OpenSSL bug exposed up to 255 bytes of server heap and existed since 2011
https://jbp.io/2024/06/27/cve-2024-5535-openssl-memory-safety.html
2 notes
·
View notes
Text
This Week in Rust 550
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on X(formerly Twitter) or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Foundation
Welcoming Rust-C++ Interoperability Engineer Jon Bauman to the Rust Foundation Team
RustNL 2024
Visual Application Design for Rust - Rik Arends
ThRust in Space: Initial Momentum - Michaël Melchiore
Arc in the Linux Kernel - Alice Ryhl
Making Connections - Mara Bos
Replacing OpenSSL One Step at a Time - Joe Birr-Pixton
Fortifying Rust's FFI with Enscapsulated Functions - Leon Schuermann
Oxidizing Education - Henk Oordt
Postcard: An Unreasonably Effective Tool for Machine to Machine Communication - James Munns
Introducing June - Sophia Turner
Robius: Immersive and Seamless Multiplatform App Development in Rust - Kevin Boos
Compression Carcinized: Implementing zlib in Rust - Folkert de Vries
K23: A Secure Research OS Running WASM - Jonas Kruckenberg
Async Rust in Embedded Systems with Embassy - Dario Nieuwenhuis
Xilem: Let's Build High Performance Rust UI - Raph Levien
Rust Poisoning My Wrist for Fun - Ulf Lilleengen
Type Theory for Busy Engineers - Niko Matsakis
Newsletters
This Month in Rust GameDev #51 - May 2024
Project/Tooling Updates
Enter paradis — A new chapter in Rust's parallelism story
Tiny Glade, VJ performances, and 2d lighting
Diesel 2.2.0
Pigg 0.1.0
git-cliff 2.3.0 is released! (highly customizable changelog generator)
Observations/Thoughts
The borrow checker within
Don't Worry About Lifetimes
rust is not about memory safety
On Dependency Usage in Rust
Context Managers: Undroppable Types for Free
Rust and dynamically-sized thin pointers
Rust is for the Engine, Not the Game
[audio] Thunderbird - Brendan Abolivier, Software Engineer
Rust Walkthroughs
Build with Naz : Rust typestate pattern
How to build a plugin system in Rust
Forming Clouds
Rust error handling: Option & Result
Let's build a Load Balancer in Rust - Part 3
The Ultimate Guide to Rust Newtypes
Miscellaneous
Highlights from "I spent 6 years developing a puzzle game in Rust and it just shipped, AMA"
Crate of the Week
This week's crate is layoutparser-ort, a simplified port of LayoutParser for ML-based document layout element detection.
Despite there being no suggestions, llogiq is reasonably happy with his choice. Are you?
No matter what your answer is, please submit your suggestions and votes for next week!
Calls for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
RFCs
No calls for testing were issued this week.
Rust
No calls for testing were issued this week.
Rustup
No calls for testing were issued this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
No Calls for participation in projects were submitted this week.
If you are a Rust project owner and are looking for contributors, please submit tasks here or through a PR to TWiR or by reaching out on X (Formerly twitter) or Mastodon!
CFP - Events
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
Scientific Computing in Rust 2024 | Closes 2024-06-14 | online | Event date: 2024-07-17 - 2024-07-19
Rust Ukraine 2024 | Closes 2024-07-06 | Online + Ukraine, Kyiv | Event date: 2024-07-27
Conf42 Rustlang 2024 | Closes 2024-07-22 | online | Event date: 2024-08-22
If you are an event organizer hoping to expand the reach of your event, please submit a link to the website through a PR to TWiR or by reaching out on X (Formerly twitter) or Mastodon!
Updates from the Rust Project
308 pull requests were merged in the last week
-Znext-solver: eagerly normalize when adding goals
fn_arg_sanity_check: fix panic message
add --print=check-cfg to get the expected configs
add -Zfixed-x18
also InstSimplify &raw*
also resolve the type of constants, even if we already turned it into an error constant
avoid unwrap diag.code directly in note_and_explain_type_err
check index value <= 0xFFFF_FF00
coverage: avoid overflow when the MC/DC condition limit is exceeded
coverage: optionally instrument the RHS of lazy logical operators
coverage: rename MC/DC conditions_num to num_conditions
create const block DefIds in typeck instead of ast lowering
do not equate Const's ty in super_combine_const
do not suggest unresolvable builder methods
a small diagnostic improvement for dropping_copy_types
don't recompute tail in lower_stmts
don't suggest turning non-char-literal exprs of ty char into string literals
enable DestinationPropagation by default
fold item bounds before proving them in check_type_bounds in new solver
implement needs_async_drop in rustc and optimize async drop glue
improve diagnostic output of non_local_definitions lint
make ProofTreeBuilder actually generic over Interner
make body_owned_by return the Body instead of just the BodyId
make repr(packed) vectors work with SIMD intrinsics
make lint: lint_dropping_references lint_forgetting_copy_types lint_forgetting_references give suggestion if possible
omit non-needs_drop drop_in_place in vtables
opt-in to FulfillmentError generation to avoid doing extra work in the new solver
reintroduce name resolution check for trying to access locals from an inline const
reject CVarArgs in parse_ty_for_where_clause
show files produced by --emit foo in json artifact notifications
silence some resolve errors when there have been glob import errors
stop using translate_args in the new solver
support mdBook preprocessors for TRPL in rustbook
test codegen for repr(packed,simd) → repr(simd)
tweak relations to no longer rely on TypeTrace
unroll first iteration of checked_ilog loop
uplift {Closure,Coroutine,CoroutineClosure}Args and friends to rustc_type_ir
use parenthetical notation for Fn traits
add some more specific checks to the MIR validator
miri: avoid making a full copy of all new allocations
miri: fix "local crate" detection
don't inhibit random field reordering on repr(packed(1))
avoid checking the edition as much as possible
increase vtable layout size
stabilise IpvNAddr::{BITS, to_bits, from_bits} (ip_bits)
stabilize custom_code_classes_in_docs feature
stablize const_binary_heap_constructor
make std::env::{set_var, remove_var} unsafe in edition 2024
implement feature integer_sign_cast
NVPTX: avoid PassMode::Direct for args in C abi
genericize ptr::from_raw_parts
std::pal::unix::thread fetching min stack size on netbsd
add an intrinsic for ptr::metadata
change f32::midpoint to upcast to f64
rustc-hash: replace hash with faster and better finalized hash
cargo test: Auto-redact elapsed time
cargo add: Avoid escaping double-quotes by using string literals
cargo config: Ensure --config net.git-fetch-with-cli=true is respected
cargo new: Dont say were adding to a workspace when a regular package is in root
cargo toml: Ensure targets are in a deterministic order
cargo vendor: Ensure sort happens for vendor
cargo: allows the default git/gitoxide configuration to be obtained from the ENV and config
cargo: adjust custom err from cert-check due to libgit2 1.8 change
cargo: skip deserialization of unrelated fields with overlapping name
clippy: many_single_char_names: deduplicate diagnostics
clippy: add needless_character_iteration lint
clippy: deprecate maybe_misused_cfg and mismatched_target_os
clippy: disable indexing_slicing for custom Index impls
clippy: fix redundant_closure suggesting incorrect code with F: Fn()
clippy: let non_canonical_impls skip proc marco
clippy: ignore array from deref_addrof lint
clippy: make str_to_string machine-applicable
rust-analyzer: add Function::fn_ptr_type(…) for obtaining name-erased function type
rust-analyzer: don't mark #[rustc_deprecated_safe_2024] functions as unsafe
rust-analyzer: enable completions within derive helper attributes
rust-analyzer: fix container search failing for tokens originating within derive attributes
rust-analyzer: fix diagnostics clearing when flychecks run per-workspace
rust-analyzer: only generate snippets for extract_expressions_from_format_string if snippets are supported
rustfmt: collapse nested if detected by clippy
rustfmt: rustfmt should not remove inner attributes from inline const blocks
rustfmt: rust rewrite check_diff (Skeleton)
rustfmt: use with_capacity in rewrite_path
Rust Compiler Performance Triage
A quiet week; we did have one quite serious regression (#115105, "enable DestinationPropagation by default"), but it was shortly reverted (#125794). The only other PR identified as potentially problematic was rollup PR #125824, but even that is relatively limited in its effect.
Triage done by @pnkfelix. Revision range: a59072ec..1d52972d
3 Regressions, 5 Improvements, 6 Mixed; 4 of them in rollups 57 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
Change crates.io policy to not offer crate transfer mediation
Tracking Issues & PRs
Rust
[disposition: merge] Allow constraining opaque types during subtyping in the trait system
[disposition: merge] TAIT decision on "may define implies must define"
[disposition: merge] Stabilize Wasm relaxed SIMD
Cargo
No Cargo Tracking Issues or PRs entered Final Comment Period this week.
Language Team
No Language Team RFCs entered Final Comment Period this week.
Language Reference
No Language Reference RFCs entered Final Comment Period this week.
Unsafe Code Guidelines
No Unsafe Code Guideline RFCs entered Final Comment Period this week.
New and Updated RFCs
No New or Updated RFCs were created this week.
Upcoming Events
Rusty Events between 2024-06-05 - 2024-07-03 🦀
Virtual
2024-06-05 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2024-06-06 | Virtual (Tel Aviv, IL) | Code Mavens
Rust Maven Workshop: Your first contribution to an Open Source Rust project
2024-06-06 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-06-09 | Virtual (Tel Aviv, IL) | Code Mavens
Rust Maven Workshop: GitHub pages for Rust developers (English)
2024-06-11 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2024-06-12 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 8 - Asynchronous Programming
2024-06-13 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-06-13 | Virtual (Nürnberg, DE) | Rust Nuremberg
Rust Nürnberg online
2024-06-16 | Virtual (Tel Aviv, IL) | Code Mavens
Workshop: Web development in Rust using Rocket (English)
2024-06-18 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
2024-06-19 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-06-20 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-06-25 | Virtual (Dallas, TX, US)| Dallas Rust User Group
Last Tuesday
2024-06-27 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-07-02 | Virtual (Buffalo, NY) | Buffalo Rust Meetup
Buffalo Rust User Group
2024-07-03 | Virtual | Training 4 Programmers LLC
Build Web Apps with Rust and Leptos
2024-07-03 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
Europe
2024-06-05 | Hamburg, DE | Rust Meetup Hamburg
Rust Hack & Learn June 2024
2024-06-06 | Madrid, ES | MadRust
Introducción a Rust y el futuro de los sistemas DLT
2024-06-06 | Vilnius, LT | Rust Vilnius
Enjoy our second Rust and ZIG event
2024-06-06 | Wrocław, PL | Rust Wroclaw
Rust Meetup #37
2024-06-11 | Copenhagen, DK | Copenhagen Rust Community
Rust Hack Night #6: Discord bots
2024-06-11 | Paris, FR | Rust Paris
Paris Rust Meetup #69
2024-06-12 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup
2024-06-18 | Frankfurt/Main, DE | Rust Frankfurt Meetup
Rust Frankfurt is Back!
2024-06-19 - 2024-06-24 | Zürich, CH | RustFest Zürich
RustFest Zürich 2024
2024-06-20 | Aarhus, DK | Rust Aarhus
Talk Night at Trifork
2024-06-25 | Gdańsk, PL | Rust Gdansk
Rust Gdansk Meetup #3
2024-06-27 | Berlin, DE | Rust Berlin
Rust and Tell - Title
2024-06-27 | Copenhagen, DK | Copenhagen Rust Community
Rust meetup #48 sponsored by Google!
North America
2024-06-08 | Somerville, MA, US | Boston Rust Meetup
Porter Square Rust Lunch, Jun 8
2024-06-11 | New York, NY, US | Rust NYC
Rust NYC Monthly Meetup
2024-06-12 | Detroit, MI, US | Detroit Rust
Detroit Rust Meet - Ann Arbor
2024-06-13 | Spokane, WA, US | Spokane Rust
Monthly Meetup: Topic TBD!
2024-06-17 | Minneapolis, MN US | Minneapolis Rust Meetup
Minneapolis Rust Meetup Happy Hour
2024-06-18 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-06-20 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-06-26 | Austin, TX, US | Rust ATC
Rust Lunch - Fareground
2024-06-27 | Nashville, TN, US | Music City Rust Developers
Music City Rust Developers: Holding Pattern
Oceania
2024-06-14 | Melbourne, VIC, AU | Rust Melbourne
June 2024 Rust Melbourne Meetup
2024-06-20 | Auckland, NZ | Rust AKL
Rust AKL: Full Stack Rust + Writing a compiler for fun and (no) profit
2024-06-25 | Canberra, ACt, AU | Canberra Rust User Group (CRUG)
June Meetup
South America
2024-06-06 | Buenos Aires, AR | Rust en Español | Rust Argentina
Juntada de Junio
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
Every PR is Special™
– Hieyou Xu describing being on t-compiler review rotation
Sadly, there was no suggestion, so llogiq came up with something hopefully suitable.
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
2 notes
·
View notes
