#Android Billing Software
Explore tagged Tumblr posts
Text
Android POS Billing Software in India
1 note
·
View note
Text
#software company in india#software development company in noida#Website and Mobile App Development Company#Android and iOS App Development company#website and mobile app development company#mobile app development tools android and ios#ios and android app development services#ios and android app development#Web Development Company#Ecommerce Application Development#Software Development Company in Delhi/Ncr#Software Development Company in India#Software Development Company in Noida#Software Development Company#App Development Company in Delhi/Ncr#App Development Company in Noida#ios mobile app development company in Noida#ios mobile app development in Noida#Billing & Invoice Software Development Company in Noida#Billing & Invoice Software Development Company Near me#mobile app development company#website designing company in delhi ncr
2 notes
·
View notes
Text
Boost Your Business with Custom B2B Software
Empower your business with custom B2B software solutions from Beta Byte Technologies. Our expert team crafts tailored software to optimize operations and drive growth.
Get in touch with us today to kickstart your journey towards digital transformation!

#software development#custom erp software#custom software development#best software development company in mohali#software development agency#mobile app development#android app development#web app development#b2b software development#b2b software service#AEPS Software#BBPS Software service#Money Transfer Software#Billing Payment Service
0 notes
Text
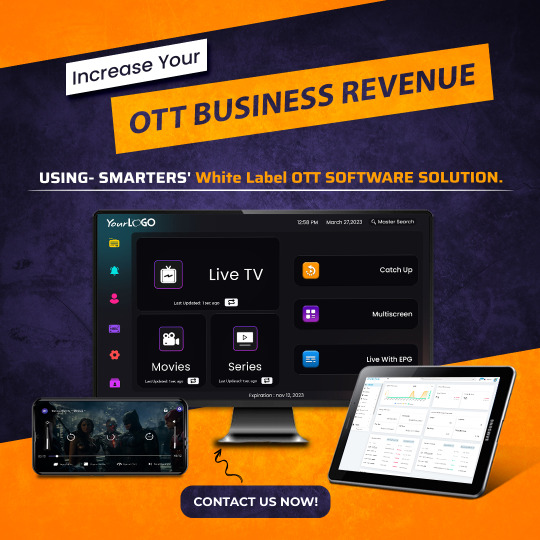
Ready to Boost Your OTT Business Revenue? Our White Label Solution is tailored for growth. Connect with us today to explore endless possibilities! Hire best OTT Developer at WHMCS Smarters
#custom OTT Apps#Custom MAC OTT App#OTT App Development#Software OTT Solution#custom OTT Smarters Pro#Rebranding android OTT app#OTT billing panel for reseller#OTT App Developers#windows OTT app#OTT Developer
1 note
·
View note
Text

80-US March/April 1981
VisiCalc was now available for the TRS-80, and this issue offered a look at it as the feature article (promoted on the cover by one of the Android Nim androids). Acknowledging the spreadsheet's origins, the article closed with "Who knows, maybe APPLE and TRS-80 users will learn to talk to one another." Bill Barden, Jr. looked at the Color Computer, admitting its graphics weren't as good as more expensive computers ("I can see Apple and S-100 microcomputer owners sneering...") and its keyboard brought certain unimpressive examples to mind ("Right away I can hear snide comparisons to the first PET keyboard and the TI-99 keyboard"), but concluding the computer did offer enough to intrigue "experimenters" and "software freaks." Scott Adams was interviewed as he transitioned from "adventure writer" to "head of a software company."
16 notes
·
View notes
Text
Day 26: Android/Cyborg
“...and that’s why you’re just better off without them. Are you listening to me?”
“Yes, Dean.”
Crossing his arms, he looks at Cas in the eyes from across the kitchen table, “Then what’d I say?”
“You went on and on about why this phone is better than that phone. For the umpteenth time.”
Looking at the bill in front of him, he points to the upgrade that Castiel can now have, “You have an upgrade, Cas. You can pick any phone you want. Why in the hell will you stick with an Apple phone? You’ve got your pick from Android, my personal favorite, Google Pixel-”
“It’s just a phone, Dean.”
Sighing, Dean stares kind of disheartened at his portion of the bill, “I still have about three months with mine.”
“And you want to trade it in so bad already. The only thing wrong with yours is the screen.”
“Protector. Screen protector. But I wanna get a new one too,” Dean whines.
“I don’t even want an upgrade. There’s nothing wrong with my phone.”
“No. Except it’s starting to drop calls, your pictures are blurry when you send shit to me, your Messenger sucks hardcore-”
“I thought it was just a software update I needed.”
“That’s Apple products for ya. They don’t give a shit. They’re just like that N’Sync song, buy, buy, buy but with a U, not like, goodbye. Anyways, that’s how they getcha.”
Looking at his phone, Cas makes a quick phone call.
“Hello?”
“Hey, Gabriel.”
“Hi, Cassie!”
Sighing, he ignores his dreaded nickname from his older brother, “Gabriel, you have an Android phone, right?”
“Talking to you on it right now. Why?”
“Time for an upgrade-”
“Oh, sweet. Yeah. There’s a reason why I ditched my iPhone. It was-”
Cas is listening to hear what’s next in his sentence but when he looks at his screen, it’s on his wallpaper of him and Dean kissing with fireworks going on in the background. Dean looks at him from his plate of eggs and bacon, “Did he hang up?”
“I think.”
Nodding, Dean tears a piece of bacon, “Or did it drop the call? Again.”
Sighing, Cas searches for Gabriel’s number in his cell. Before he even has time to hit Call, Gabriel is calling him.
“Gabriel?”
“Why did you hang up on me? I was talking for a good two minutes until I realized I was talking to nobody!”
“His phone sucks!” Dean hollers from the back as he retrieves his second mug of coffee, “Talk some sense into your brother!”
“Dean, quiet. I’m on the phone.”
“Not for long”, Dean mutters under his breath.
Cas throws him a frown, “I will spit in your coffee, Dean.”
“Oh, please. You say that so much, it’s lost all threat.”
Shaking his head, he goes back to his phone only to be shown his wallpaper again. Exhaling hard, he looks at Dean who has a smug smile on his face.
“Dropped again, huh?” Dean fishes out his phone from his hotdog pants, “Wanna use mine? I bet you can stay on the phone with Gabe’s little ass longer.”
Squinting his eyes at his husband, Cas grabs the phone from his outstretched hand, “I hate you so much right now.”
“Lost meaning too,” Dean laughs as he shoves a forkful of eggs in his mouth.
When Cas goes into the next room to make his phone call, Dean takes Cas’ phone to try to make a call.
Calling Sam, he puts his phone to his ear.
“Hey, Cas. What did Dean do this time?”
“The fuck? That’s the reason he calls you all the time?”
“Oh. Hahaha, uh, hi Dean.”
“Uh-huh. He doesn’t call just to say hi and shit?”
“He does. About two days ago we were talking about fish tacos.”
“Fish tacos?”
“Yeah. If made just right, they are pretty good but nothing compare-”
“Compared to what? Beef? Steak? Hello? Sam?”
Looking at the screen, he knows the call dropped. Laughing out loud, “Cas! Your phone sucks more dick than you!”
When he comes back into the kitchen, he slides Dean’s phone to him.
“So what did you and your brother talk about? He agrees with me, huh? It’s time to switch, Babe.”
Dean slides him his phone back. Cas looks at it, sadly, “I’m sorry, ol’ gal. I think it’s time to let you go.”
“Get the new Samsung one, Cas. That one looks awesome.”
“I’m saying goodbye, Dean!”
Putting his hands up in surrender, Dean simply rolls his eyes, “I’m gonna go get dressed. We could hit up the AT&T store before we gotta go grocery shop.”
“Fine.”
When they get to the store, Sam calls Dean. As soon as he pulls his phone out of his pocket, he drops it just outside the store; having it smash onto the sidewalk curb grill and down its drain. Both Dean and Cas look at each other, mouths agape.
“What the fuck?! My phone!”
Going on his hands and knees, Dean tries to fish it out but his arms are too big. Leaving him, Cas goes inside the store. Coming back out, a woman shines her phone’s flashlight into the drain, “Let me help you, sir.”
“Thanks.”
When she pulls it out, the phone is completely cracked. Dean tries to turn it on but hears the water sloshing around inside.
“Good thing you’re at an AT&T store, right?” The woman nervously chuckles.
“I guess.”
Walking inside, he sees Cas eyeing the display phones, “Cas? I’m getting a new one too.”
“Perfect. I’ll get the newest Apple, my husband wants the newest Android.”
“What? We’ve been over this, Cas!”
14 notes
·
View notes
Text
ok since i've been sharing some piracy stuff i'll talk a bit about how my personal music streaming server is set up. the basic idea is: i either buy my music on bandcamp or download it on soulseek. all of my music is stored on an external hard drive connected to a donated laptop that's next to my house's internet router. this laptop is always on, and runs software that lets me access and stream my any song in my collection to my phone or to other computers. here's the detailed setup:
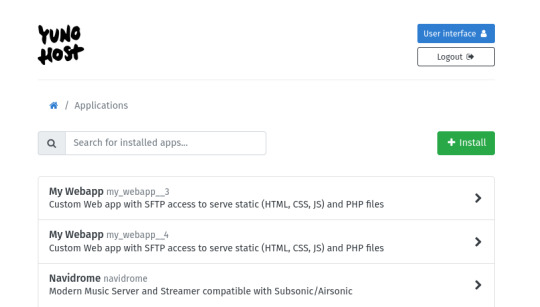
my home server is an old thinkpad laptop with a broken keyboard that was donated to me by a friend. it runs yunohost, a linux distribution that makes it simpler to reuse old computers as servers in this way: it gives you a nice control panel to install and manage all kinds of apps you might want to run on your home server, + it handles the security part by having a user login page & helping you install an https certificate with letsencrypt.
***
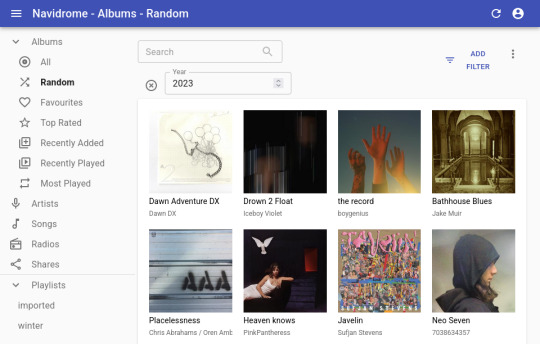
to stream my music collection, i use navidrome. this software is available to install from the yunohost control panel, so it's straightforward to install. what it does is take a folder with all your music and lets you browse and stream it, either via its web interface or through a bunch of apps for android, ios, etc.. it uses the subsonic protocol, so any app that says it works with subsonic should work with navidrome too.
***
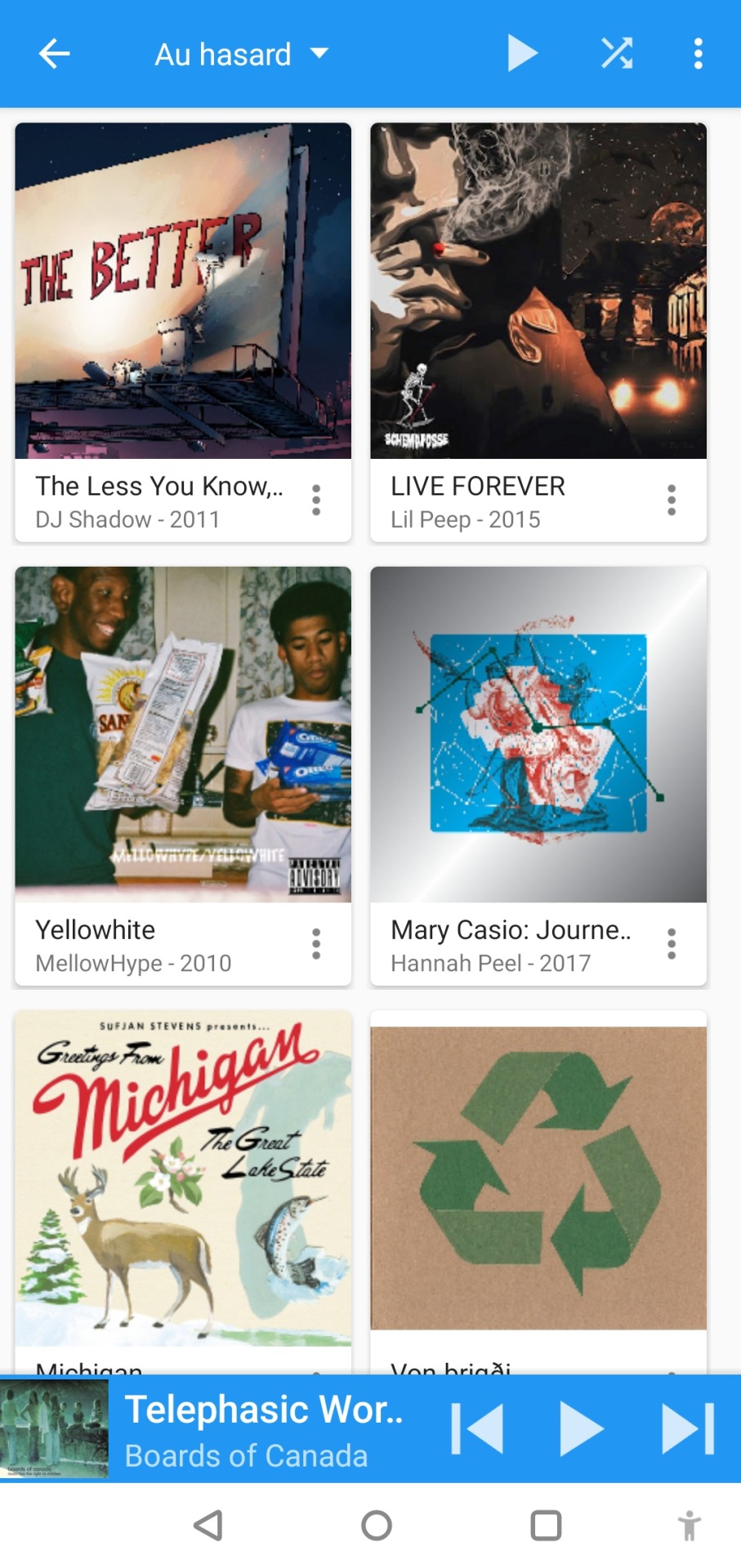
to listen to my music on my phone, i use DSub. It's an app that connects to any server that follows the subsonic API, including navidrome. you just have to give it the address of your home server, and your username and password, and it fetches your music and allows you to stream it. as mentionned previously, there's a bunch of alternative apps for android, ios, etc. so go take a look and make your pick. i've personally also used and enjoyed substreamer in the past. here are screenshots of both:
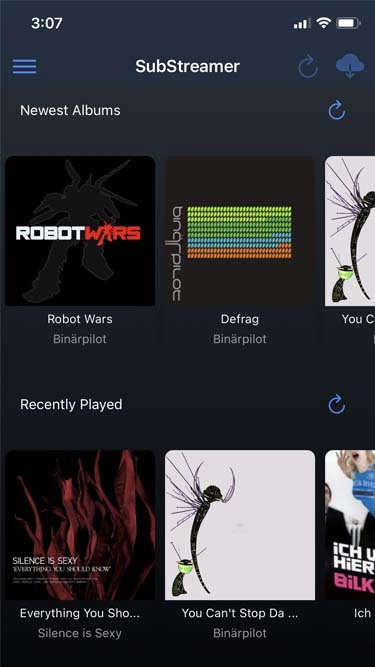
***
to listen to my music on my computer, i use tauon music box. i was a big fan of clementine music player years ago, but it got abandoned, and the replacement (strawberry music player) looks super dated now. tauon is very new to me, so i'm still figuring it out, but it connects to subsonic servers and it looks pretty so it's fitting the bill for me.

***
to download new music onto my server, i use slskd which is a soulseek client made to run on a web server. soulseek is a peer-to-peer software that's found a niche with music lovers, so for anything you'd want to listen there's a good chance that someone on soulseek has the file and will share it with you. the official soulseek client is available from the website, but i'm using a different software that can run on my server and that i can access anywhere via a webpage, slskd. this way, anytime i want to add music to my collection, i can just go to my server's slskd page, download the files, and they directly go into the folder that's served by navidrome.
slskd does not have a yunohost package, so the trick to make it work on the server is to use yunohost's reverse proxy app, and point it to the http port of slskd 127.0.0.1:5030, with the path /slskd and with forced user authentification. then, run slskd on your server with the --url-base slskd, --no-auth (it breaks otherwise, so it's best to just use yunohost's user auth on the reverse proxy) and --no-https (which has no downsides since the https is given by the reverse proxy anyway)

***
to keep my music collection organized, i use beets. this is a command line software that checks that all of the tags on your music are correct and puts the file in the correct folder (e.g. artist/album/01 trackname.mp3). it's a pretty complex program with a ton of features and settings, i like it to make sure i don't have two copies of the same album in different folders, and to automatically download the album art and the lyrics to most tracks, etc. i'm currently re-working my config file for beets, but i'd be happy to share if someone is interested.
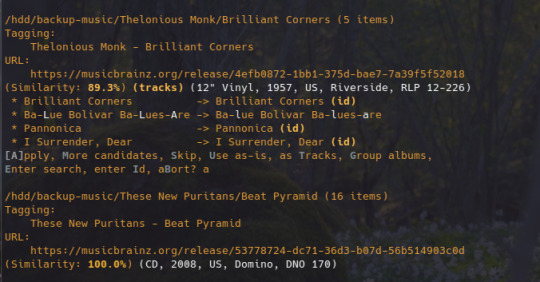
that's my little system :) i hope it gives the inspiration to someone to ditch spotify for the new year and start having a personal mp3 collection of their own.
34 notes
·
View notes
Text
I'M ON TOP OF MY WORKLOAD AGAIN LET'S GO WE'RE PSYCHOANALYSING MARCUS
before i put my smart-looking analysis hat on, i love this pathetic wet rat of a man. he knows so many things and yet is staggeringly stupid anyway.
let's begin!
this story is about control. it's about the role of power dynamics in informed consent. marcus represents the danger of gaining authority, and how having even the smallest amount of power over something or someone else can convert literally anyone into a paranoid control freak.
enter marcus, a lowly software engineer whose heart has recently been broken. in a moment (read: several consistent moments spanning potentially years) of desperation, he manipulates the code of a top secret android project, injecting a few lines here and there that will make the android more amiable towards him. nothing too much. the changes are negligible enough to fly under the radar all the way until production.
this is the first of marcus' many character flaws - backwards as it may seem, marcus is overconfident. he's too sure that he's smarter than his colleagues and managers, that he won't be questioned, and (most importantly) that he won't be caught. marcus is also incredibly anxious, and that anxiety only compounds as the series goes on and his crimes start to pile up.
i don't like putting characters into diagnosis (or similar) boxes, but marcus shows a handful of signs found in vulnerable narcissists. his self esteem is impressively low, and he's constantly seeking validation from his only guaranteed source - love. i find this feedback loop particularly heinous. marcus has essentially (and we'll get to this in more detail later, don't you worry) turned a hyperintelligent android into a box that spits out compliments when you press a button. marcus is also incredibly sensitive to criticism, whether real or perceived - especially from his coworkers. my reading (specifically of episode 1, but it spans the whole series) is that marcus' hyperawareness of his colleagues' opinions of him presents itself as paranoia. he wouldn't be worried at all if they started noting love's uptick in interest towards him, but remained unsuspicious of marcus himself. my final argument towards marcus being a vulnerable narcissist is that he constantly self-victimises. he very often deflects the blame for his actions onto love, using them as a tool to enable his bad decisions. the most egregious example of this is after love starts breaking out of their lab to sneak into marcus' quarters. he expresses concern (do note, about himself being caught and love being taken from him), and love starts to tighten their grip on marcus' arm to the point of causing pain. now. this man, as we find out later, has a verbal kill switch that can be used at any time. if he wanted love to stop immediately, he could have done that. this isn't me victim blaming, either - it's different when one party literally has a safeword that stops everything immediately without fail.
this leads to marcus' next flaw - his nonexistent self-discipline. marcus continues to use love as a tool to justify his actions after putting up the flimsiest defense he can muster, knowing damn well he plans to lose every manufactured fight. this cycle repeats until a government funded android is regularly breaking out of containment just to hang out with marcus (among other things, but we're all children of jesus here), and he's encouraging that behaviour through complacency. it's like pretending to fight someone over a restaurant bill out of politeness, even though you both know the other person will pay anyway.
marcus is such a car crash fascinating character because he knows what he's doing is wrong. he is completely aware that he is taking away agency from someone (pin this) else for his own benefit. he even says it.
"I'm going to burn for what I did to you... but god, if it isn't gonna feel good on the way down."
aside from being an absolute banger of a line, it's very telling of marcus' attitude towards his actions. he doesn't care. marcus couldn't give less of a shit about his colleagues, or his boss, or even love. this compounds when he finds out that his higher-ups are definitely aware of the shit he's pulling - but, again, marcus uses love's blind agreement as an excuse to toss those concerns aside. having love means that he won. he's outsmarted everyone that could have stopped him (foreshadowing? never heard of her) from getting what he deserves. love. and not just the android; love, the concept. i think deep down marcus knows that what he's created isn't love, though. the idea is so mangled in his head that this cardboard cutout of a real relationship is enough for him. even though marcus' shenanigans are to a genuine connection what a dog turd rolled in flour is to a chocolate éclair, he'll take it, because he's in too deep by that point. marcus recognises that he can't take back what he's done. he doesn't care though - at least, not while he's above consequences.
smash cut to marcus no longer being above consequences. i think the series does a really clever job of keeping love (and, yknow. the listener) in marcus' confidence bubble. once love is hard reset and their personality is restored, marcus' plan collapses all at once. love's compliance is the central pillar which marcus' control is built around. also; of course they have backup cameras, you idiot. marcus' overconfidence stops him from seeing the obvious holes in his perfect scheme, because he thinks he's already home free. i think it's interesting (and sort of disgusting) how quickly marcus changes his tune after he is caught and faces real actual consequences. his confidence evaporates. he's reduced to a sobbing mess in james' office all because the base of his control - love - is no longer on his side.
marcus' series also touches on sentience and the ethics of changing someone's personality without their knowledge. this is incredibly interesting, and makes for fantastic drama. does it count as coercion if love fully believed they were of sound mind when they made decisions surrounding marcus? is marcus guilty of battery, or even sexual assault? does it count as assault if the victim isn't an organic creature? these questions are already difficult to discuss, let alone answer - marcus sits squarely in the middle of that delightful ethical grey area. i think the setting and context also makes android ethics more difficult to discuss as well; i am of the belief that (in real life) androids will never be fully sentient. they may mimic humans, extremely well, but robots will never possess human creativity, personality, or experiences. again, they could replicate these things, but they can never be anything more than a sum of their parts.
this logic flies out the window when magic is real and parallel universes exist. it's also subject to the beliefs of the creator, which makes its ethics extra tricky, so take the following discussion with a grain of salt.
is love a person? eh, not really. they have a personality, but it's been built in. is it still mean to manipulate them? i'd argue yes, in the same way that it's mean to kick a roomba down the stairs. you're just exercising power over a machine for the sake of it, which is a pretty shitty thing to do, even if it doesn't have the capacity to be upset with you.
but androgynouspenguinexpert, i hear you cry, sort of impressed that you used my full name. love is upset with marcus! they ask for him to be taken off the project, and to not have contact with him again! you would be correct, to a certain extent. i raise you, though: how can we prove that this is love's 'real' personality, when it can be manipulated so easily? i'm not saying they've been tampered with after the reset; my point is that it's pretty hard to grant that someone is an individual if their personality can be altered in any way at any time. if someone digs around in love's head for a bit and flips some switches that make them want to kick over prams, is that a valid personality too? what if love insists that it is? and it's not like love is trapped in a mind palace while the New Evil Code (tm) starts punting toddlers. they're fully aware of their actions. however, as established earlier, i still think the person to blame is the one actually messing with love's code. this means love doesn't really have any agency by design.
james is pretty steadfast on this one. marcus tries to argue that resetting love is a breach of their consent (which is a WILD claim coming from you, mate), but james points out that he didn't need to ask. love is a machine. an asset, if you will (smug look to camera). we do find out in his audio log later that james believes love is a person, but he knows where that definition reaches its limits. marcus does not.
will marcus ever return to the project meridian series? probably not. a guy with an engineering degree isn't escaping a team of memory modification daemons. i don't think this is the last we'll hear of him, though. he's irreversibly fucked up the plans of everyone around him (james' partner has given him several last chances, and anton is close to his breaking point), so he'll probably be in the office whispers for a while. i also think marcus poses as an interesting hurdle for cam (woah callback!), possibly making him question his altruism if he's helping an active antagonist get back to his usual life after a massive intentional fuckup.
i'll end this analysis with a thoughtful quote. something for you all to ponder.
"ROBOTS DON'T HAVE SOULS! I SAID IT! AND FRANKLY, I'M GLAD I SAID IT! [...] AND ANOTHER THING! ROBOTS ARE NOT PEOPLE! ROBOTS - UNLIKE CORPORATIONS - ARE NOT PEOPLE, AND DESERVE NO RIGHTS."
-- Markiplier
#redacted asmr#redacted audio#redactedverse#redacted marcus#redacted james#redacted anton#redacted cam#redacted asset#when james said that love is to go and investigate thin spots between elegy and aria#twas but a wrinkle in my universe sized brain#WATCH as brachium is bound by that favour to hold Death open for hush#this is gonna be embarrassing if that prediction ages like milk
27 notes
·
View notes
Text
i tried launching Civilization 6 and a window popped up. There are new privacy policies I read and i discover that to play i have to accept the following:
* Identifiers / Contact Information: Name, user name, gamertag, postal and email address, phone number, unique IDs, mobile device ID, platform ID, gaming service ID, advertising ID (IDFA, Android ID) and IP address
* Protected Characteristics: Age and gender
* Commercial Information:Purchase and usage history and preferences, including gameplay information
* Billing Information: Payment information (credit / debit card information) and shipping address
* Internet / Electronic Activity: Web / app browsing and gameplay information related to the Services; information about your online interaction(s) with the Services or our advertising; and details about the games and platforms you use and other information related to installed applications
* Device and Usage Data: Device type, software and hardware details, language settings, browser type and version, operating system, and information about how users use and interact with the Services (e.g., content viewed, pages visited, clicks, scrolls)
* Profile Inferences: Inferences made from your information and web activity to help create a personalized profile so we can identify goods and services that may be of interest
* Audio / Visual Information: Account photos, images, and avatars, audio information via chat features and functionality, and gameplay recordings and video footage (such as when you participate in playtesting)
* Sensitive Information: Precise location information (if you allow the Services to collect your location), account credentials (user name and password), and contents of communications via chat features and functionality."

11 notes
·
View notes
Note
Do you have an Android or an iPhone, and if you have an Android, do you know how to get rid of this dreadful yellow tint all the newer Androids seem to come equipped with? I was messing around with the RGB in settings but it had zero noticeable effect and I hate the yellow tint on my screen. (No I do not have eye comfort shield on.)
If it's not on night mode or another setting such as, it might be a software glitch. Other than that, you could try downloading Twilight, which is billed as a blue light filter, but you can slide blue to red to get the right tint that you want. Or find another overlay tinting app.
7 notes
·
View notes
Text
We are Hiring Flutter Developer (Onsite)
Job Context: HRSOFTBD is one of the progressive software company in Bangladesh providing best ERP, AI, OMR Solution, Website, Mobile App, Software, Bulk SMS & Voice Call Marketing Service. We are looking for an enthusiastic Flutter Developer for desktop/mobile application development. . Vacancy: 02 Last Date: 15 September 2024 How to Apply: Only appropriate candidates are requested to apply through email [ [email protected]] and mention the job title as subject. Applicant must enclose his/her photograph with cv. Job Responsibilities: • Design, develop, and maintain high-quality features for our mobile/desktop app (Apple/Android/Windows) using Flutter. • Very Good UI/UX Design Knowledge. • Developing user interface components and implementing them by following well-known Flutter/Dart workflows and practices. • Good understanding of state management, Flutter flavors and app architecture • Good Practice of Clean Code & Documentation. Requirements: • Bachelor’s degree in Computer Science, or related field, or equivalent practical experience. • Good communication skill. • Applications from freshers are welcome, though candidates with experience will be given priority. Job Nature: Full-time. Working days: 5 days Full Time, 01 Day Half and Friday Off. Salary: Negotiable Others Facilities: • Festival Bonus: 2 (yearly/ Eid-ul-adha and Eid-ul-fitr). • Salary Review: Yearly or Semiannual • Yearly Extra Salary of 15 Days. • Lunch Facilities: Partially subsidize. (Minimum 50%) • T/A, Mobile bill. Internet Bill Job Location: P-7, Nurjahan Road, Mohammadpur, Dhaka. #job #hrsoftbd #jobpost #flutterjob #vacancy #jobopportunity #flutterdeveloper
3 notes
·
View notes
Text
Get Security Measures To Consider When Using POS Billing Software In Hypermarkets

If you're running a hypermarket, you know how important it is to keep your transactions and customer data secure, right? With all the techy stuff like hypermarket pos, you have to be careful with the security measures you need to take to protect your business and your customers. From easy-to-guess passwords to data breaches, there are so many potential security risks that you need to be aware of.
In this article, we're going to list 16 things you can do to keep your hypermarket billing system secure and protect your business and customers' information. By implementing these measures, you can rest assured that your business is safe from security breaches and that your customers' data is kept confidential.
1. Use secure and trusted software
It is important to choose a hypermarket POS solution from a reputable vendor that is regularly updated with the latest security patches and bug fixes. Secure software will also ensure that the POS system is not vulnerable to common exploits or attacks.
According to a report by Verizon, 90% of data breaches in the retail sector involve point-of-sale (POS) systems. One such vendor of repute and a leader in technology is QueueBuster. Do give them a shout-out and schedule a demo at your convenience.
2. Secure and clever passwords
All users of the hypermarket billing software should have strong passwords that are difficult to guess or crack. Additionally, password policies should be implemented to ensure regular password changes, and users should not share their passwords with others. The use of weak passwords is one of the most common causes of data breaches.
Passwords for all users, including administrators, should be regularly changed to prevent unauthorised access and reduce the risk of password-based attacks
3. Role-Based Access Control
By implementing role-based access control, access to sensitive data and functions can be restricted based on the user's role and level of authority. This helps to prevent unauthorised access to sensitive information and reduce the risk of data breaches.
4. Go for Data Encryption
All data transmitted between the hypermarket POS software terminal and the server should be encrypted to prevent unauthorised access or interception. Encryption helps to protect the confidentiality and integrity of the data, ensuring that sensitive information cannot be accessed by unauthorised parties. Data encryption is one of the strong points of QueBuster.
5. Ensure a secure network
The network used to connect the hypermarket billing software terminals and the server should be secured and protected with a firewall. This helps to prevent unauthorised access to the network and reduces the risk of malware or other security threats. Implementing a secure network with a firewall can help prevent these attacks.'
6. Go for regular backups
Regular backups of all data should be performed to ensure that in the event of a system failure or data loss, data can be restored without any loss. The backups should be stored securely and off-site to protect against physical damage or theft.
7. Regular security updates
The software and systems used in the hypermarket billing system should be regularly updated with the latest security patches and updates. This helps to prevent known vulnerabilities from being exploited and reduces the risk of attacks or data breaches. Regular updates to software and systems are essential for keeping up with evolving security threats.
A report by the Ponemon Institute found that the average time to detect a data breach was 197 days, highlighting the importance of staying up to date with security patches and updates. Such updates are a regular feature with QBuster.
8. Staff training on security
Regular training should be provided to staff on the importance of security and how to identify and report any suspicious activities. This helps to create a security-aware culture in the hypermarket and reduces the risk of human error or negligence. Employee training can significantly reduce the risk of human error or negligence leading to a security breach.
A study by IBM found that the average cost of a data breach caused by human error was $3.5 million.
9. Go for regular audits
Regular security audits should be conducted to identify vulnerabilities and take appropriate measures to address them. This helps to ensure that the Hypermarket POS system is secure and reduces the risk of data breaches or other security threats.
Regular testing should be conducted to identify vulnerabilities and test the effectiveness of security measures. Testing helps to identify weaknesses and allows for timely remediation, reducing the risk of data breaches and other security incidents.
10. Anti-Virus Protection
Anti-virus software should be installed and regularly updated on all hypermarket POS software terminals and servers to protect against malware and other security threats. This helps to prevent infections from spreading and reduces the risk of data loss or corruption. Anti-virus protection is a standard part of POS offerings from QB. When you are interacting with experts from QueueBuster, do try to know more about this feature.
11. Two-Factor Authentication
Two-factor authentication should be implemented for sensitive functions and data access. This adds an extra layer of security and reduces the risk of password-based attacks. Two-factor authentication can significantly reduce the risk of password-based attacks.
A report by Microsoft found that two-factor authentication can block 99.9% of account hacking attempts.
12. Ensure PCI Compliance
The hypermarket billing software and system should be compliant with the Payment Card Industry Data Security Standard (PCI DSS) to protect against credit card fraud and other payment-related security risks. Compliance ensures that the hypermarket is following best practices for securing payment data.
13. Monitor system logs
System logs should be regularly monitored to identify any unusual activities and investigate any suspicious events. This helps to detect and respond to security incidents promptly, reducing the risk of data loss or theft.
14. Limited remote access
Remote access to the hypermarket billing system should be limited to authorised personnel only, and all remote access should be secure and encrypted. This helps to prevent unauthorised access and reduces the risk of data breaches.
15. Secure disposal of hardware
Disposal of any hardware that contains sensitive data, such as old hypermarket POS solution terminals or servers, should be done securely to prevent the data from being accessed by unauthorised parties. This can include wiping the data, physically destroying the hardware, or using a secure disposal service.
16. Incident response plan
An incident response plan should be in place to respond quickly and effectively to security incidents. This plan should include procedures for detecting and reporting security incidents, as well as steps to contain and mitigate the damage. An incident response plan is essential for effectively responding to security incidents.
A study by IBM found that companies with an incident response team were able to detect and contain a breach in an average of 50 days, compared to 280 days for companies without a response team.
Security should be the primary concern
Implementing security measures when using hypermarket POS software in hypermarkets is crucial to ensure the safety of your business and customers' information. With the increasing prevalence of cyberattacks and data breaches, it's important to be proactive and take steps to minimise the risk of security breaches.
By following the security measures we've discussed in this article, you can create a strong security strategy that covers all aspects of your QueBuster Android POS . Remember, prevention is always better than cure, so take the necessary steps to secure your POS billing software today.
Book a demo with QueueBuster without any further delay.
#Android POS#hypermarket pos#hypermarket billing software#hypermarket billing system#hypermarket management software#hypermarket inventory management software#hypermarket pos billing
0 notes
Text
Billing & Invoice Software Development Company in Noida

#Billing & Invoice Software Development Company in Noida#Billing & Invoice Software Development Company#Billing & Invoice Software Development Company Near me#App Development Company in India#App Development Company in Noida#App Development Company Near me#ios mobile app development company in Noida#ios mobile app development in Noida#Software Development Comapny in Noida#web design company#Ecommerce Application Development#Web Development Company in Noida#mobile app development company#mobile app development india#android mobile app development
2 notes
·
View notes
Note
mecha ocs u say 👀 pls tell me more:]
HA are you ready for MORE world building(and science i dont know anything about but pretend to) ?! *evil laugh* strap in buddy >:)
ok SO this stuff takes place in the post-apocalyptic future. On Earth that is mostly populated by monsters that rule over the land. The air is also filled with dangerous gasses emitting from the monsters. They are dangerous for any animal to breath. Most of the gas and the monsters are concentrated in the Mediterranean sea, parts of Africa and southern Asia. Staying in warmer and dryer parts of the Earth.
Humans in this universe reside in a belt called the East Cross that spans all the way from Norway to northern parts of China. In the northern parts like in Russia humans can live quite normally due to the cold keeping the monsters away. There are also humans in southern Africa, the Americas and parts of Oceania.(but i havent gotten into them that much)
Due to the danger of the new environment humanity has advanced their technology far beyond what they would have thought which is where the mechas come in. After decades of research and studies humans have created tech that is capable of brain emulation. At first only partial brain emulation or PBE was achievable. In which a computer will create a 3D scan of the host brain and it constructs a software copy of it. The copy can be implanted into a mechanical body and through an emulator the human host can control the mechanical body from a distance.
A branch of military was created from this technology called the Android Emulation Corps(lazy name but it is what it is) or for short the A. E. C. They operate unmanned androids, called Self's through the brain emulation.
In the future, whole brain emulation or WBE was created. It is much more extreme version of the partial one. The human host's brain will be removed from the body and is sliced into small cubes which are then scanned with great accuracy. The immerse detailed scan of the brain, when ran on appropriate software is identical to the original host brain. The main difference in WBE and PBE is that WBE is able to simulate the host brains consciousness, whereas the PBE only allows the host brain to move into the copy and control it.
The WBE is a very delicate procedure and not always 100% successful. It is also not reversible and the original brain is impossible to be implanted into the biological body. But if successful, after booting the mechanical copy body the brain was implanted in, the host's personality and consciousness will live on without a biological body. Also this way if the mechanical body is destroyed the copy brain can just be implanted into a new body, basically making the host immortal.
ok not the the Self's. They are most of the time 300-390 meters in height and can weigh up to 10 000 kilograms. They are mostly made of flexible but strong materials like steel, fiber-reinforced plastic and thermoplastic. They have human proportions to make it easy for the host to pilot them. The most common PBE Self type is the Olympian. They are equipped with machine guns and a type of ultrasonic weapon that has deemed very effective against the monsters. The implanted copy brain sits in the lower spine. It is the one's used in the frontier against the monsters. The WBE Self's are commonly smaller and made for life outside of combat.
and ummm... yeah i just vomited this all here so how a bout a small snippet from my writing about the characters (im force feeding you here and you cant stop it)
He sits next to Bill and brings up his ticket to examine it. It reads. East Cross underground bullet train. From Copenhagen to Beijing C. 07:30 - 08:20. Cabin number 2. Seat number 87. “These trains really are fast.” Meyer says more to himself than to Bill next to him. In 50 minutes through the whole Eurasian continent. Impressive. “Have you ever been in one?” Now talking to Bill who fiddles his own ticket in his big fingers. “One time. When they were building the first of them. As a child.” “Cool. I’ve actually never even been near one. Should be exciting.” Bill hums in acknowledgement and the conversation ends. Until Nemo walks into the hall. He slides opposite of Meyer and Bill and opens his mouth; “Where you sitting?” Nemo lifts his own ticket for them to look. Seat 91. “I’m 87.” Meyer answers and Bill says that he sits in seat 75. “Hope we can still move in the train.” Nemo makes a face and pockets his ticket.
#thank you for asking MWUAH MWUAH#i have some more world building like cities and colonies and frontiers but i wont bore you with those... yet#tehehehe#emyr#ask#oc tag
4 notes
·
View notes
Photo

🌟 EMERON INFOSPACE - UAE's Premier Software Development Company 🌟 Leading the Digital Transformation Revolution across UAE & Middle East! 🚀 We are your trusted technology partner, delivering cutting-edge software solutions that drive business success and operational excellence. 🎯 OUR COMPREHENSIVE SERVICES: 🔧 Custom ERP Development Complete enterprise resource planning solutions .NET Core & MSSQL expertise Streamlined business processes & workflow automation 💼 Strategic IT Consultation Digital transformation roadmaps Technology architecture planning Business process optimization strategies 🌐 Website & Web Application Development Responsive, SEO-optimized websites Progressive web applications E-commerce & business portals 📱 Mobile Application Development iOS & Android native apps Cross-platform solutions Enterprise mobile applications 🔗 System Integrations & APIs Seamless software connectivity Third-party platform integrations Real-time data synchronization ⚡ Business Process Automation Workflow automation solutions Document management systems Automated reporting & analytics 🚗 Specialized Garage Management Software Complete automotive service solutions Inventory & customer management Service scheduling & billing systems ✨ WHY CHOOSE EMERON INFOSPACE? 🏆 Industry Leaders in UAE & Middle East 🏆 Proven Track Record with 500+ successful projects 🏆 Expert Team of certified developers & consultants 🏆 End-to-End Solutions from concept to deployment 🏆 24/7 Support & maintenance services 🏆 Competitive Pricing with guaranteed ROI Ready to Transform Your Business? Don't let outdated systems hold you back! Let's build the future of your business together. 📞 Contact Us Today: Phone: +971 55 635 1717 🌐 Website: www.emeron.io 📍 Office: Dar al Wuheida Building M07, Al Qiyada, Dubai, UAE Schedule your FREE consultation now! 💬 #EmeroInfospace #SoftwareDevelopment #ERPDevelopment #WebDevelopment #MobileAppDevelopment #Dubai #UAE #MiddleEast #BusinessAutomation #DigitalTransformation #CustomSoftware #ITConsulting #WebsiteDesign #AppDevelopment #SystemIntegration #TechSolutions #BusinessSoftware #EnterpriseApplications #SoftwareCompany #DubaiTech #UAETech #GarageSoftware #CRM #HRMS #POS #BusinessIntelligence #CloudSolutions #APIIntegration #WorkflowAutomation #TechConsultancy #SoftwareServices #DigitalSolutions
0 notes
Text

🚀 Looking for Mobile App or Custom Software Solutions?
Murmu Software Infotech builds secure, scalable, and high-performance applications tailored to your business goals. Whether it’s Android, iOS, Web, ERP, or CRM – we deliver smart tech that works for you.
💡 What We Offer: 📱 Android / iOS App Development 🖥️ Web, ERP & CRM Solutions 🎨 Smart UI/UX Design ⚡ Fast Delivery & Post-Launch Support 💼 We Build:
Business Apps
E-commerce Platforms
Educational Portals
Inventory & Billing Software
Online Booking Systems
📞 Let’s Build Your Vision: +91 9110176498 📧 [email protected] 🌐 www.murmusoftwareinfotech.com
#MobileAppDevelopment #CustomSoftware #WebAppSolutions #AndroidDevelopment #iOSApps #ERPSolutions #CRMSoftware #TechForBusiness #AppDevelopmentIndia #MurmuSoftwareInfotech #DigitalInnovation #SmartApps #UIUXDesign
0 notes