#Backend Proxy
Explore tagged Tumblr posts
Text
Purecode | Backend Proxy
Consider making API requests through a backend server where your API key is stored and not exposed to the frontend. This way, the API key is kept hidden from the client-side, reducing the potential for unauthorized access.
#Backend Proxy#Consider making API requests#API key is kept hidden#potential for unauthorized access.#purecode#purecode ai company reviews#purecode ai reviews#purecode company#purecode software reviews#purecode reviews
0 notes
Text
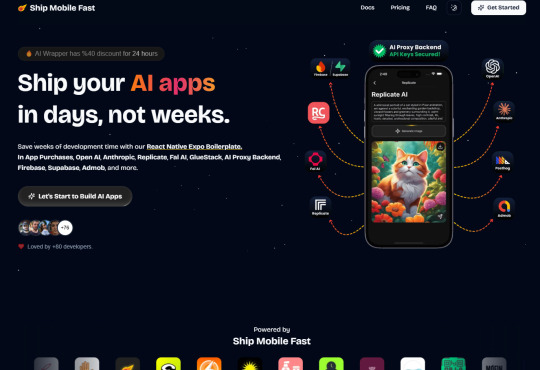
Ship Mobile Fast
Ship your AI apps in days, not weeks.
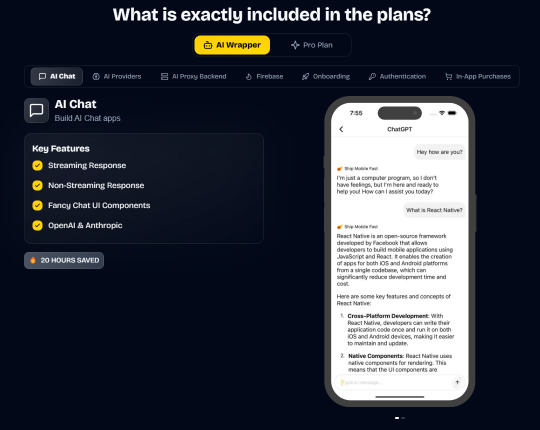
Save weeks of development time with our React Native Expo Boilerplate. In App Purchases, Open AI, Anthropic, Replicate, Fal AI, GlueStack, AI Proxy Backend, Firebase, Supabase, Admob, and more.
Ship Mobile Fast AI Wrapper is Live!🔥
For those who want to build AI applications…
Now, you can create the apps you envision in just 1-2 days.😎
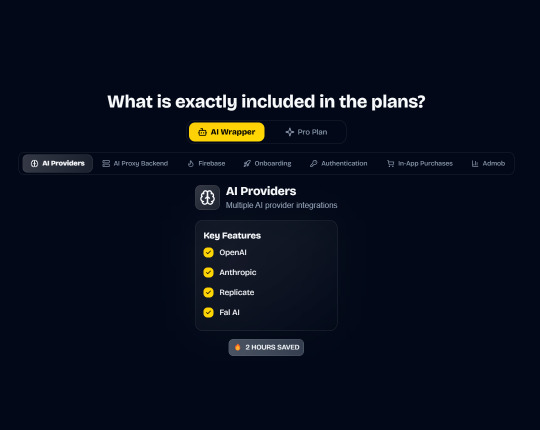
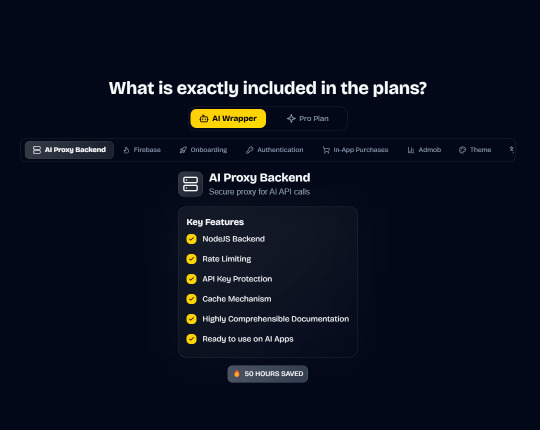
Integrations with OpenAI, Anthropic, Replicate, and Fal AI. Protect your API keys from being stolen with AI Proxy Backend.
*
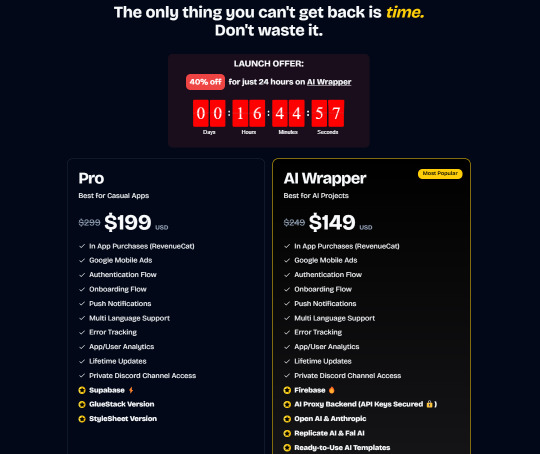
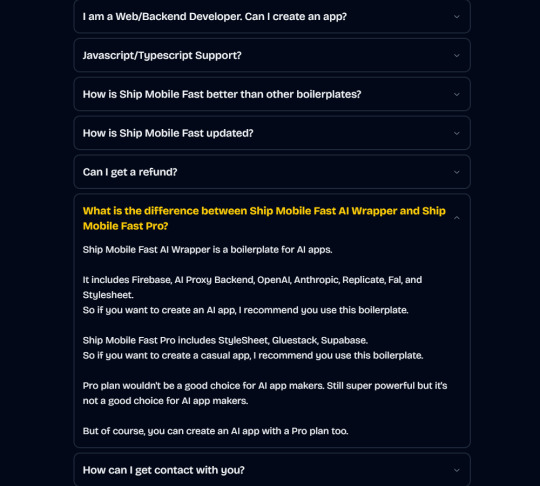
Pro (Best for Casual Apps):
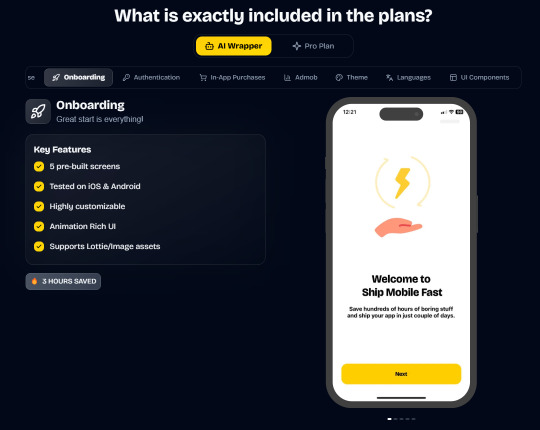
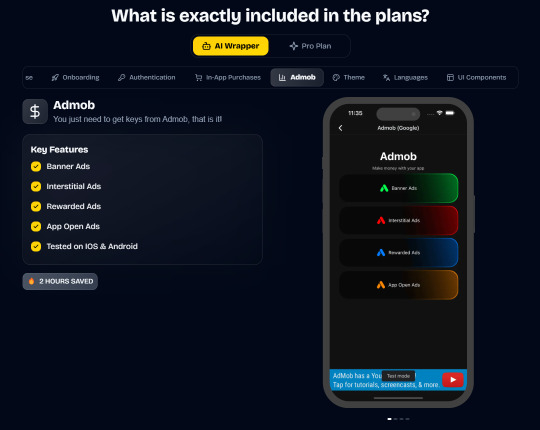
In App Purchases (RevenueCat) Google Mobile Ads Authentication Flow Onboarding Flow Push Notifications Multi Language Support Error Tracking App/User Analytics Lifetime Updates Private Discord Channel Access Supabase⚡️ GlueStack Version StyleSheet Version
*
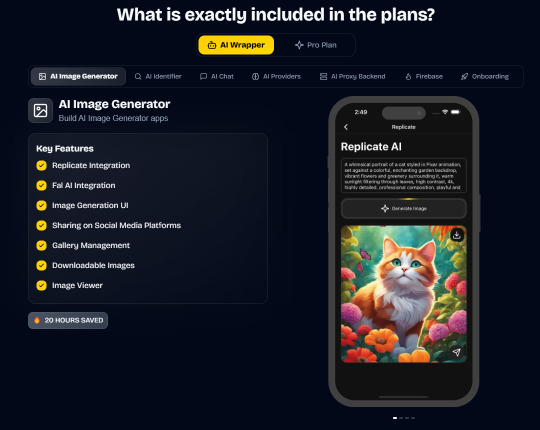
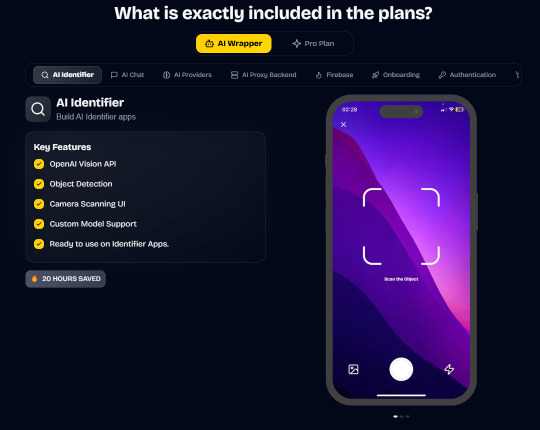
AI Wrapper (Best for AI Projects):
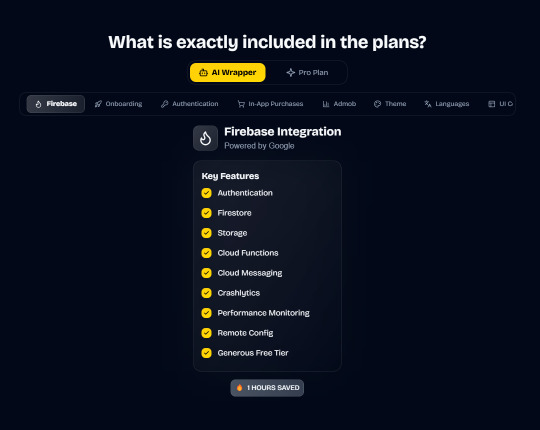
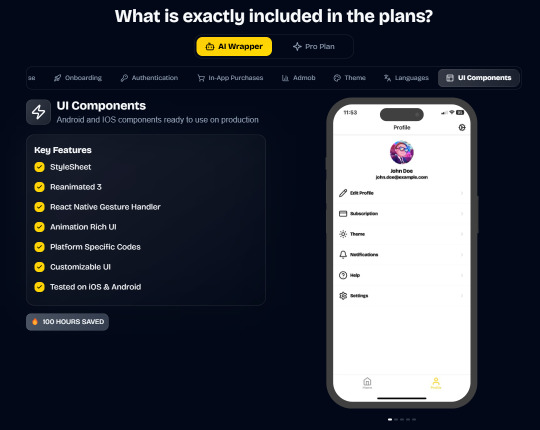
In App Purchases (RevenueCat) Google Mobile Ads Authentication Flow Onboarding Flow Push Notifications Multi Language Support Error Tracking App/User Analytics Lifetime Updates Private Discord Channel Access Firebase🔥 AI Proxy Backend (API Keys Secured🔒) Open AI & Anthropic Replicate AI & Fal AI Ready-to-Use AI Templates
*
Ship Mobile Fast: https://shipmobilefast.com/?aff=1nLNm
Telegram: ahmetmertugrul


#ai#app#ship#mobile#fast#openai#claude#deepseek#proxy#api#admob#ads#firebase#supabase#falai#backend#ui#ux#replicate#revenuecat#google#expo#boilerplate#template#wrapper
2 notes
·
View notes
Text
Okay, I've applied a few patches to y232* including using a different backend for yt videos, I'm seeing big speed improvements but I did have to retry so its definitely not immediately solving the problem but we'll see how it pans out, I think tomorrow I'll write a proxy pausing algorithm for when the dreaded error pops up so hopefully that'll solve a little more of the issue
y232 is an ad free tracking free you/tube downloader that you can host for yourself (though the new code hasn't been upstreamed just yet)
76 notes
·
View notes
Text
pangi keeps telling pili how proud he is of him and its actually too sweet i wish it wasnt backended by bad hearing about pili making a potion room and focusing on how its Beneficial and reminding me how he told pili he should get strong in alchemy because itd make him less likely to betray him (and by proxy, leave pangi to die one day)
32 notes
·
View notes
Text
Brave Software launched Cookiecrumbler, an open-source tool (April 2025) that detects and neutralizes deceptive cookie consent pop-ups using AI, preserving privacy while maintaining site functionality.
The tool scans websites via proxies, uses open-source LLMs to classify cookie banners, and suggests precise blocking rules—avoiding invasive tracking or site breakage.
Detected pop-ups undergo human review to minimize errors, with findings published on GitHub for collaborative refinement by developers and ad-blockers.
Unlike traditional blockers (which risk breaking sites), Cookiecrumbler tailors rules per website and processes data on Brave’s backend—never on users’ devices.
The tool exposes the failure of GDPR-like regulations to enforce true consent, offering a stopgap until stronger legal accountability emerges. It signifies a shift toward usable privacy.
7 notes
·
View notes
Text
closed for @blackbcxwarning ( for arielle )
Sienna hesitated outside the office for a full thirty seconds before walking in. She didn’t usually do this—the whole pitching stories to journalists thing—but this wasn’t just a hunch. It was a pattern. A troubling one. She made her way past the bullpen and knocked lightly on Arielle’s open door, her tablet tucked under one arm, a thumb drive in the other. “Hey. Got a minute?”
She stepped inside, brushing a strand of hair behind her ear. “This isn’t exactly my usual territory, but I think I’ve come across something that might be worth printing. Or at least… worth looking into.” Sienna handed over the thumb drive first. “I was tracing backend vulnerabilities for a freelance cybersecurity audit—routine stuff—and I found fragments of a shadow network piggybacking off municipal Wi-Fi zones. Whoever’s behind it has been discreetly scraping user data and rerouting it through a proxy that disappears every 72 hours. It’s not just public browsing data either—there are traces of keystroke logs. Someone’s getting bold.”
She met Arielle’s gaze evenly. “Most people wouldn’t notice. But if you connect this with those data breach rumours floating around city offices? Someone’s fishing. Quietly. And if this is linked to a third-party contractor or a public-private deal no one vetted properly…” She gave a soft breath, the weight of it settling. “I don’t want to cry conspiracy, but you’re the one person in town who doesn’t look away when something smells off. So I thought I’d bring it to you first.” A small, self-aware smile tugged at the edge of her lips. “Besides, a digital paper trail is still a paper trail. Just a little more encrypted.”

#interactions | sienna#interactions#arielle | 001#( i hope this is okay let me know if it needs changing! )
4 notes
·
View notes
Text
Load Balancing Web Sockets with K8s/Istio
When load balancing WebSockets in a Kubernetes (K8s) environment with Istio, there are several considerations to ensure persistent, low-latency connections. WebSockets require special handling because they are long-lived, bidirectional connections, which are different from standard HTTP request-response communication. Here’s a guide to implementing load balancing for WebSockets using Istio.
1. Enable WebSocket Support in Istio
By default, Istio supports WebSocket connections, but certain configurations may need tweaking. You should ensure that:
Destination rules and VirtualServices are configured appropriately to allow WebSocket traffic.
Example VirtualService Configuration.
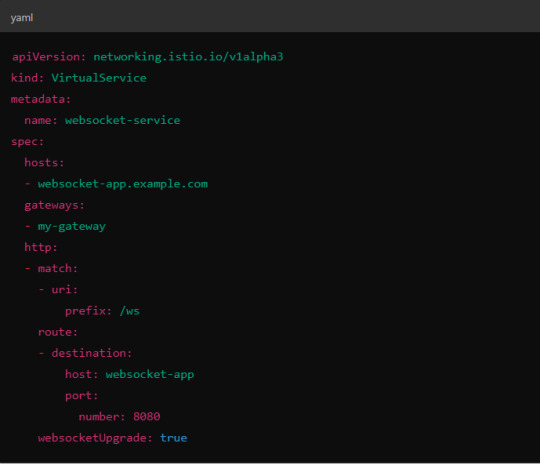
Here, websocketUpgrade: true explicitly allows WebSocket traffic and ensures that Istio won’t downgrade the WebSocket connection to HTTP.
2. Session Affinity (Sticky Sessions)
In WebSocket applications, sticky sessions or session affinity is often necessary to keep long-running WebSocket connections tied to the same backend pod. Without session affinity, WebSocket connections can be terminated if the load balancer routes the traffic to a different pod.
Implementing Session Affinity in Istio.
Session affinity is typically achieved by setting the sessionAffinity field to ClientIP at the Kubernetes service level.
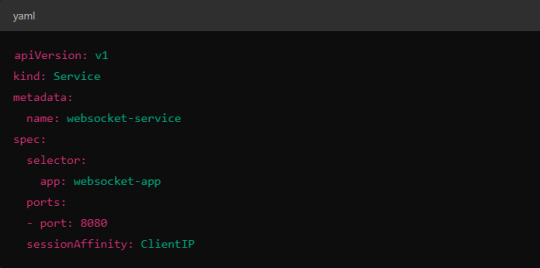
In Istio, you might also control affinity using headers. For example, Istio can route traffic based on headers by configuring a VirtualService to ensure connections stay on the same backend.
3. Load Balancing Strategy
Since WebSocket connections are long-lived, round-robin or random load balancing strategies can lead to unbalanced workloads across pods. To address this, you may consider using least connection or consistent hashing algorithms to ensure that existing connections are efficiently distributed.
Load Balancer Configuration in Istio.
Istio allows you to specify different load balancing strategies in the DestinationRule for your services. For WebSockets, the LEAST_CONN strategy may be more appropriate.
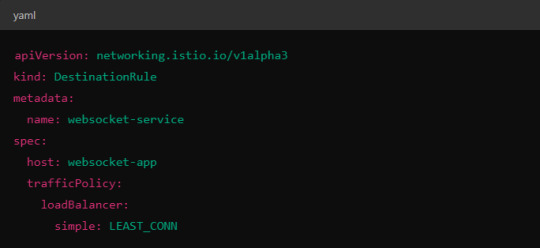
Alternatively, you could use consistent hashing for a more sticky routing based on connection properties like the user session ID.
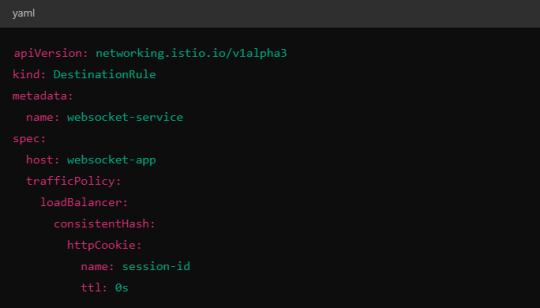
This configuration ensures that connections with the same session ID go to the same pod.
4. Scaling Considerations
WebSocket applications can handle a large number of concurrent connections, so you’ll need to ensure that your Kubernetes cluster can scale appropriately.
Horizontal Pod Autoscaler (HPA): Use an HPA to automatically scale your pods based on metrics like CPU, memory, or custom metrics such as open WebSocket connections.
Istio Autoscaler: You may also scale Istio itself to handle the increased load on the control plane as WebSocket connections increase.
5. Connection Timeouts and Keep-Alive
Ensure that both your WebSocket clients and the Istio proxy (Envoy) are configured for long-lived connections. Some settings that need attention:
Timeouts: In VirtualService, make sure there are no aggressive timeout settings that would prematurely close WebSocket connections.
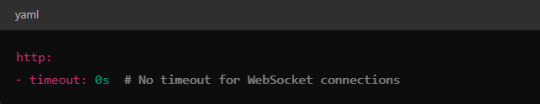
Keep-Alive Settings: You can also adjust the keep-alive settings at the Envoy level if necessary. Envoy, the proxy used by Istio, supports long-lived WebSocket connections out-of-the-box, but custom keep-alive policies can be configured.
6. Ingress Gateway Configuration
If you're using an Istio Ingress Gateway, ensure that it is configured to handle WebSocket traffic. The gateway should allow for WebSocket connections on the relevant port.
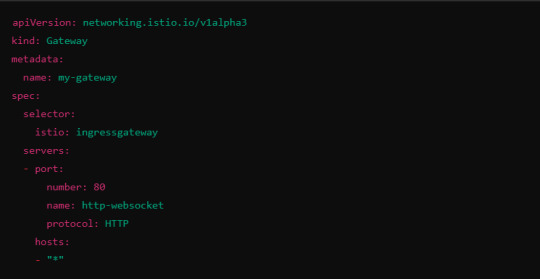
This configuration ensures that the Ingress Gateway can handle WebSocket upgrades and correctly route them to the backend service.
Summary of Key Steps
Enable WebSocket support in Istio’s VirtualService.
Use session affinity to tie WebSocket connections to the same backend pod.
Choose an appropriate load balancing strategy, such as least connection or consistent hashing.
Set timeouts and keep-alive policies to ensure long-lived WebSocket connections.
Configure the Ingress Gateway to handle WebSocket traffic.
By properly configuring Istio, Kubernetes, and your WebSocket service, you can efficiently load balance WebSocket connections in a microservices architecture.
#kubernetes#websockets#Load Balancing#devops#linux#coding#programming#Istio#virtualservices#Load Balancer#Kubernetes cluster#gateway#python#devlog#github#ansible
5 notes
·
View notes
Text
Boost Your Website with Nginx Reverse Proxy
Hi there, enthusiasts of the web! 🌐
Have you ever wondered how to speed up and protect your website? Allow me to provide to you a little tip known as Nginx reverse proxy. I promise it will revolutionise the game!

What’s a Reverse Proxy Anyway?
Consider a reverse proxy as the security guard for your website. It manages all incoming traffic and ensures seamless operation by standing between your users and your server. Do you want to go further? Take a look at this fantastic article for configuring the Nginx reverse proxy.
Why You’ll Love Nginx Reverse Proxy
Load Balancing: Keep your site running smoothly by spreading traffic across multiple servers.
Extra Security: Protect your backend servers by hiding their IP addresses.
SSL Termination: Speed up your site by handling SSL decryption on the proxy.
Caching: Save time and resources by storing copies of frequently accessed content.
Setting Up Nginx Reverse Proxy
It's really not as hard to set up as you may imagine! On your server, you must first install Nginx. The configuration file may then be adjusted to refer to your backend servers. Want a detailed how-to guide? You just need to look at our comprehensive guide on setting up a reverse proxy on Nginx.
When to Use Nginx Reverse Proxy
Scaling Your Web App: Perfect for managing traffic on large websites.
Microservices: Ideal for routing requests in a microservices architecture.
CDNs: Enhance your content delivery by caching static content.
The End
It's like giving your website superpowers when you add a Nginx reverse proxy to your web configuration. This is essential knowledge to have if you're serious about moving your website up the ladder. Visit our article on configuring Nginx reverse proxy for all the specifics.
Hope this helps! Happy coding! 💻✨
2 notes
·
View notes
Text
Youtube has now started disabling the video player if you use an adblock, anyone got a workaround or effective proxy/backend to make it work? I am on Firefox btw, for a long time Firefox could avoid their adblock detection but now it is no longer effective.
11 notes
·
View notes
Text
Introduction 自我介紹
DID SYSTEM OVER HERE 本人為人格分裂/解離症/DID患者
SYSTEM NAME 人格分裂系統名稱
Mmm... I can't think of one yet, but for everyones convenience I put a J there in my UN so call us J or call the host/whoever fronting as J.
我還沒有想好一個系統名稱呢! 不過為方便大家稱呼本系統, 我在用戶名稱裡放上J字, 叫我們J就好. 或者稱呼我們的身體主控部分為J就好.
ABOUT US 關於我們
我是一個自閉譜系的解離性身份障礙(DID, 又俗稱人格分裂)華人患者. 我在中國出世並在出世地區長大和定居. 我在失業前是一名���序員. 被解僱原因則是由長期創傷造成的影響(身心症/轉化症/情緒問題/人格部分的爭吵困擾等等)導致工作表現極不理想, 因此我沒有怪責我的公司/上司, 而目前只好靜心休養.
I'm an autistic DID system who is a Chinese living in my hometown. I was a IT programmer before getting fired for the cap of all the traumatic effect (somatic/emotions/alter disputes etc.) affecting my performamce, which I think is pretty fair enough so I don't blame them. So now I'm unemployed and I'm trying to rest for a bit and hoping to get healed.
系統綜合適用第二人稱
你/妳
COLLECTIVE PRONOUN 系統綜合適用第三人稱
她/他(們)/佢(地)
She/They. Unless someone here tells you otherwise. Some of them seems more like a "he" but not quite seems to care about gender. We seem pretty ok with body = cis female so that's it. But this body is a cis female and I've been relating myself to female for so long, so your best choice is to call us she/they.
ALTERS 人格部分
Uh... We're kind of like PDID in ICD 11, and recently I suspect we're polyfrag so things get pretty confusing over here. Afaik we're always cocon and even cofront but mainly it's me hosting. And we hardly have our own names. But I can still try my best to tell you some basic stuff about us.
HOST/SHELL 主控/外殼部份
直接叫我J吧. 如果你想指定稱呼主控部份, 那就說類似"J的主控部分"的話吧.
It's me. Chara. ... No, call us J or if you wish to be very specific about this host, then call us the host of J or something like that. I'm always here, even when I full switched (I know some of you might dislike this term but I think it describes my experience fairly good, so please excuse me) twice in life. The first time it was I got yoinked back to somewhere backend of the frontend (I told you I'm a programmer *cough*) and watched a proxy of demon or something alter to control the body, fully in charge of frontend thoughts, even teases me, while I went numb and lost sense of self, despite watching through body's eyes (but one step backward inside somewhere in brain) and feeling everything happened. That has to be way more than just a depersonalization.
THE INNOCENT CHILD
When I first aware of her existence (or re-existence), I could imediately tell she's the child version of me. It was when I had my second full switch. I forgot what exactly was the strong feeling that made me felt like rolling back to before I forced myself to become this personality during the days where the last straw of the traumas explicitly ruined me. (And yes, I remember quite a lot of the said trauma, and many other traumas) And suddenly, I feel like I'm gonna rollback, then I went back to the backend of the frontend again. Despite this time iirc I still kind of feel my sense of self, it's a lot more comfortable than the previous full switch. I forgot about the exact time line but I did feel like "oh, so she's still here and that's how she feels over all these years", after realizing her depression and guilt on what she has done over all these years by "summoning" us, me and the "demon". I feel sorry for her. But I refuse to give up my part and living like her and rollback, for self/system protection or selfish sake. I mean if living like her was feasible, I wouldn't be here and hosting for years.
DNI
As long as you're not a freak or troll or Nazis or some sort of that, I'm good with it. And of course, do NOT fakeclaim or diminish anyone's trauma.
完整介紹及中文版即將推出
TBC
11 notes
·
View notes
Text
Fix Crawl Errors in Google Search Console Step‑by‑Step

If you’ve ever been frustrated by crawl errors in Google Search Console, you aren’t alone. These little issues can quietly wreck your SEO and drag down your rankings. I’ve had my fair share of nights checking for missing pages, 5xx errors, and DNS troubles. But today things are different. Let me take you through a simple, human‑friendly way to fix crawl errors, using the newest tools Google just rolled out after announcing big updates like Gemini 2.5, AI Mode in Google Search, and Agent Mode at Google I/O 2025.
Why crawl errors matter for SEO marketing
When Googlebot tries to read your site and hits a wall, it logs a crawl error. That might be a page not found, a server failing, or your DNS acting up. In SEO marketing every page counts, and if Google can’t crawl your pages, they can’t rank. Crawl errors are like hidden leaks in a ship—you don’t know they’re sinking you until it’s too late. Fixing them keeps your content visible and avoids sudden drops in traffic.
The new era after Google I/O 2025
You might be wondering, when is Google I/O 2025 happening? It took place on May 20 and 21, and Google used that stage to drop some big announcements. The star of the show for Search Console was AI Mode in Google Search, powered by Gemini 2.5 under the hood, and an enhanced Agent Mode to help us webmasters fix issues faster. These updates have transformed a manual, frustrating process into something more intelligent and efficient.
How to see crawl errors in Search Console
First thing’s first: open Google Search Console and click on Coverage followed by the Errors tab. Instead of a raw list of URLs, you’ll now see AI‑powered suggestions if you’ve enabled AI Mode. These suggestions might flag groups of 404 errors, server issues, or DNS blips. Even if the list is long, the AI groups related errors together, saving you time and giving you a clear view of what needs fixing.
Understanding each error type
Each category of crawl errors requires a different approach, so it helps to understand why they happen. DNS errors usually mean your domain couldn’t be resolved, often tied to hosting or DNS provider problems. Server errors, the dreaded 5xx family, point to issues on your web server—maybe it crashed or your scripts got overwhelmed. The classic 404 means the page is missing, often from deleted content or wrong internal links. Soft 404s are sneaky; they return a 200 status but have little or no real content, causing Google to treat them as “page missing.” Recognizing these differences helps you tackle them correctly.
Fixing DNS and server errors step by step
When you spot a DNS error, log into your DNS provider or hosting dashboard. See if your A, CNAME, or NS records are intact. If you recently switched providers or used Cloudflare, check for any misconfigurations. You might even temporarily pause Cloudflare’s proxy to make sure it’s not blocking Googlebot. Once the records fix, go back to Search Console and hit Validate Fix. It tells Google to recrawl those URLs.
Server errors can be trickier. Log into your server or hosting control panel and check for error logs around the time Googlebot hit your site. It might be overloaded PHP scripts or a misbehaving plugin. Maybe a sudden spike in traffic caused timeouts. With AI Mode and Agent Mode, Search Console sometimes gives hints like “slow response time” or “resource limit reached.” If you’re using managed hosting, reach out to support. Once you’ve fixed the backend, go back and ask Google to validate.
Repairing 404 and soft 404 pages
When Google bumps into a 404, think about why that page is missing. If the content is gone for good, send a hard 410 Gone status—it tells Google you meant to remove that page. If you’ve moved the content somewhere else, a 301 redirect to the new URL is the right move. Soft 404s are a little trickier. They happen when pages return 200 but have no substance—maybe a thin “this page doesn’t exist” message. Beef up those pages, add real content, or turn them into redirects. After updating, hit Validate Fix again in Search Console.
The lasting benefit to SEO marketing
Every crawl error you fix is a step toward better SEO marketing performance. Google sees a healthy, well‑structured site as easier to trust. Combine that with optimized content, mobile speed, and user‑friendly layouts, and you’ve built a strong foundation that gets rewarded in rankings. The enhancements from Google I/O 2025 — Gemini 2.5, AI Mode, and Agent Mode — just speed up the process. You’re not chasing errors, you’re preventing problems before they happen.
Putting it into practice
Let me walk you through a typical week. On Monday, I log into Search Console and check the Coverage Errors tab. The new interface shows AI Mode suggestions up front. If I see a few new 5xx or DNS errors, I log into my hosting dashboard, look at logs, make tweaks, and hit Validate Fix. Mid‑week, I review soft 404s or broken links, fix any thin pages or add 301s, and re‑validate. On Friday I glance at performance metrics—any dips? Did click impressions bounce back? If yes, job done. If not, I dig deeper. You can do the same, and now you’ve got Google’s own AI tools to help.
Using Google Translate for multilingual sites
If your site targets different languages, this step is crucial. After enabling AI Mode and Agent Mode, use Google Translate to scan your international content. Gemini 2.5 helps report crawl errors by language path, and you can fix errors in each version separately. No guessing. If your French pages are missing metadata or serve soft 404s, you’ll know exactly which URLs need attention.
Final thoughts
Crawl errors are like mosquitoes—tiny but irritating, and if you ignore too many, they can ruin your day. When Google I/O 2025 introduced AI Mode, Gemini 2.5, and Agent Mode, they gave us more powerful tools to wipe those bugs out fast. I’ve distilled everything here into a real, step‑by‑step approach you can follow now. Start with the Coverage tab, let AI group errors, dive into server, DNS, or content issues, fix them, validate, and repeat. Keep monitoring performance and stay on top of any new crawl issues.
#WebsiteRankingChecker#SEO2025#SearchEngineOptimization#SEOTool#DigitalMarketingTools#WebsitePerformance#RankTracking#KeywordTracking
0 notes
Link
[ad_1] From zero-day exploits to large-scale bot attacks — the demand for a powerful, self-hosted, and user-friendly web application security solution has never been greater. SafeLine is currently the most starred open-source Web Application Firewall (WAF) on GitHub, with over 16.4K stars and a rapidly growing global user base. This walkthrough covers what SafeLine is, how it works, and why it's becoming the go-to solution over cloud-based WAFs. What is SafeLine WAF? SafeLine is a self-hosted web application firewall that acts as a reverse proxy, filtering and monitoring HTTP/HTTPS traffic to block malicious requests before they reach your backend web applications. Unlike cloud-based WAFs, SafeLine runs entirely on your own servers—giving you unmatched visibility and data sovereignty. Key Features of SafeLine WAF Comprehensive Attack Prevention SafeLine effectively blocks a wide range of common and advanced web attacks, including SQL injection(SQLi), cross-site scripting (XSS), OS command injection, CRLF injection, XML External Entity (XXE) attacks, Server Side Request Forgery (SSRF), and directory traversal, etc. Zero-Day Detection via Semantic Analysis Unlike traditional signature-based WAFs, SafeLine uses a patented semantic analysis engine that deeply parses HTTP traffic semantics. This approach enables it to detect complex and zero-day attacks with high accuracy, resulting in an industry-leading detection rate of 99.45% and an ultra-low false positive rate of 0.07%. (The chart below compares SafeLine with the two versions of a globally recognized open-source WAF.) Robust Bot Protection SafeLine delivers comprehensive, multi-layered defenses against automated bot attacks, a growing threat vector responsible for credential stuffing, malicious scraping, inventory hoarding, and vulnerability scanning. It combines several out-of-box powerful mechanisms: CAPTCHA Challenges: Dynamically issued to distinguish human users from automated clients, especially in suspicious or high-risk traffic scenarios. Dynamic Protection: Randomly encrypts and obfuscates frontend code, such as HTML and JavaScript, before delivering it to the client. This prevents bots from reliably parsing page structures or interacting with DOM elements, rendering automated scripts ineffective. Anti-Replay Mechanisms: Detect and block reuse of tokens, headers, or payloads often leveraged in scripted attacks or credential stuffing campaigns. HTTP Flood DDoS Mitigation HTTP flood DDoS attacks attempt to overwhelm servers by sending massive volumes of HTTP requests in a short period of time. These attacks can exhaust server resources, degrade performance, or take applications offline entirely. To counter this, SafeLine implements rate limiting to cap request frequency and mitigate abuse. These measures are highly configurable, allowing defenders to tailor thresholds based on real-world traffic patterns. For sudden traffic spikes—whether legitimate or malicious—SafeLine provides a virtual waiting room mechanism. This ensures service availability by queuing excess users and releasing them gradually, preventing backend overload while maintaining a fair and orderly access experience. Authentication Challenges SafeLine is also designed with Zero Trust principles in mind—never trust, always verify. It offers configurable visitor authentication to secure access to protected applications, enhancing security through enforced identity checks. As a built-in identity gateway, it supports modern authentication protocols such as OIDC and integrates seamlessly with identity providers like GitHub and others. SafeLine also supports Single Sign-On (SSO) to streamline user authentication and simplify login experience in the meantime. Best of all, these enterprise-grade identity features are included for free. Simple Deployment in Minutes SafeLine is designed for quick setup and easy management. It requires the following environment to be installed and run: Operating System: Linux (x86_64 or arm64) Dependencies: Docker (version 20.10.14 or higher) and Docker Compose (version 2.0.0 or higher) Minimum System Requirements: 1 CPU core, 1 GB of RAM, and 5 GB of available disk space Once the environment is ready, installation takes just a few minutes with a single command. bash -c "$(curl -fsSLk -- --en A user-friendly, wizard-based interface guides you through configuration. Full documentation is available here. Why Choose SafeLine Over Cloud-Based WAFs? Unlike traditional cloud-based WAFs that route your traffic through third-party infrastructure, SafeLine offers complete deployment autonomy. Here are the advantages: Full Data Control: Sensitive traffic and logs remain on-premises, reducing exposure to third-party cloud risks. Cost Efficiency: Avoids recurring subscription fees common with cloud WAFs, especially beneficial for high-traffic environments. Free and Out-of-Box Enterprise Features: Advanced threat detection, bot protection, identity authentication, and more—typically gated behind "premium" tiers elsewhere—are out-of-box and included for free. Get SafeLine — free forever for personal use, with optional 7-day Pro trial. Use Cases Ideal for SafeLine SafeLine is a versatile solution built for a wide range of web application security needs. It's particularly well-suited for: Organizations with strict data privacy or regulatory compliance requirements Teams Targeted by Sophisticated Bots and Automated Threats Small and medium-sized businesses seeking affordable, enterprise-grade protection DevOps and Security Teams Requiring Full Deployment Control and Customization Projects requiring rapid deployment and easy maintenance Final Words SafeLine stands out as a powerful, open-source alternative to traditional cloud-based WAFs. With cutting-edge zero-day detection, robust bot mitigation, and zero trust–aligned identity features—all bundled into a self-hosted, easy-to-deploy package—SafeLine empowers developers, security teams, and organizations of all sizes to take control of their web security. Get SafeLine — free forever for personal use, with optional 7-day Pro trial. Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Twitter and LinkedIn to read more exclusive content we post. [ad_2] Source link
0 notes
Text
How Imginn Lets You Watch Instagram Stories Without Being Seen
Instagram Stories are a great way to share fleeting moments, but what if you want to view them without leaving a trace? Whether you're conducting competitive research, keeping tabs discreetly, or just want to maintain your privacy, tools like Imginn offer a solution. But how exactly does Imginn keep you anonymous while watching Instagram Stories ( You can see more detail via imginnig.com)? Let’s show what it is, how it works, and the privacy implications.
What Is Imginn?
Imginn is a third-party web tool designed to let users view Instagram content particularly Stories, reels, and posts without logging in to Instagram. Unlike the Instagram app or website, which notifies users when someone views their Stories, Imginn allows you to bypass these notifications entirely.
It's especially popular among users who want to:
View Stories without being seen.
Browse public Instagram profiles anonymously.
Download content for offline access.
How Imginn Works
The platform functions by accessing Instagram’s public data endpoints. Here’s a simplified breakdown of the process:
Public Data Scraping: Imginn scrapes data from public Instagram profiles. If a user has a public account, their Stories and posts can be accessed without login credentials.
Proxy Browsing: Imginn acts as a middle layer between you and Instagram’s servers. When you search for a profile or Story, Imginn retrieves the data for you and displays it on its platform Instagram never sees your IP address or that you accessed the content.
No Login Required: Because you’re not logged in, your Instagram identity remains completely hidden. This eliminates the digital footprint that traditional Instagram views would leave behind.
Key Features That Enhance Anonymity
No Account Needed: You don’t need to create an Imginn account or provide personal information.
No App Installation: Since it's a web-based service, you don’t risk downloading any potentially invasive apps.
Minimal Tracking: Imginn claims not to store viewing history, and because you’re not logged into Instagram, there’s no direct way for your activity to be linked back to you.
Limitations to Be Aware Of
While Imginn can be a useful tool, it's important to understand its limitations:
Only Works for Public Accounts: If a profile is set to private, Imginn cannot access it.
Third-Party Risk: As with any third-party tool, you should be cautious about the privacy policies and data practices of Imginn itself.
Legal & Ethical Boundaries: Viewing someone’s content anonymously may cross ethical lines, especially if used to invade someone’s digital privacy.
Why Anonymity Matters
The desire for anonymity online is more prevalent than ever. Whether for personal reasons, professional discretion, or just curiosity, tools like Imginn give users control over how they interact with social media platforms. While Instagram is designed to be social and transparent, anonymity tools offer an alternative that prioritizes user privacy.
Conclusion
Imginn offers a compelling solution for anonymous Instagram browsing, particularly when it comes to Stories. It leverages publicly available data and clever backend processes to ensure you can watch without being watched. However, it’s always wise to use such tools responsibly and respect others' online privacy.
1 note
·
View note
Text
Chapter 10: Lightmap UV seams

Figure 20. Lightmap UV split visible across the hand after baking (left). Unity fixes seams after enabling the Stitch Seams option and baking again (right).
10.1 Why does this happen?
By default, GPUs cannot blend color values between separate UV shells. Without the extra post processing step, this limitation can cause visible seams to appear in a lightmap. Aggressive filtering and low lightmap resolution can exacerbate this problem by bleeding texel color values into neighboring UV shells.
10.2 How to fix it
Disclaimer: fixing lightmap seams in a single object can be trivial. It is more difficult to address this problem when working with modular meshes. This is a common issue that most lightmapping backends face, and it is a hard problem to solve.
10.2.1 Enable Stitch Seams option
Stitch Seams option is available in the Mesh Renderer component, under the Lightmapping header. By enabling it, Unity will attempt to fix seams by blending color values between UV shells that share a stitchable common edge in the model.
Note that this option only works with single GameObjects. Multiple GameObjects are not supported.
10.2.2 Combine meshes in a DCC tool

Figure 21. Cornell Box scene assembled using modular meshes with visible seams after lightmap baking (left). Meshes combined in a DCC tool prior to exporting with no lightmap seams visible (right). You can achieve the result on the right by disabling filtering and baking with high sample counts.
The easiest way to mitigate seams is to combine meshes in a 3D modeling package. Make sure to weld overlapping vertices before exporting. Or, you can weld vertices in in the Model Import Settings window. Skipping this step might impede automatic lightmap unwrapping in Unity.
10.2.3 Combine meshes via an API
Mesh.CombineMeshes method combines meshes into one, achieving the same result as merging them in a DCC package.
10.2.4 Combine meshes using ProBuilder
When working with ProBuilder meshes it is possible to merge multiple objects by using the Merge Objects option.
You can make this option available for regular meshes by converting them into ProBuilder meshes using the ProBuilderize option.
10.2.5 Disable filtering and denoising
By disabling filtering, it is possible to avoid blurring and dilation issues described earlier. The main drawback of this approach is long bake times, as you would need to increase the number of samples to achieve clean results.
10.2.6 Increase lightmap padding
If disabling filtering does not solve the issue, try increasing Lightmap Padding value. When working with modular meshes, each mesh has its own UV atlas. Lightmap Padding property allows you to change the distance between UV atlases – but not between UV shells within the atlas - to prevent leaking.
10.2.7 Use light probes
Light probes are often used to provide indirect illumination for dynamic objects. Consider utilizing light probes for difficult to lightmap objects.
It is worth mentioning that probe-lit objects receive lighting information from a single probe. It can be detrimental when illuminating large objects. Light Probe Proxy Volume (LPPV) component can mitigate this problem, by creating a grid of light probes within a bounding volume. As a result, probe-lit objects that make use of LPPVs have a spatial gradient improving their look.
Adaptive probe volumes allow for per-pixel lighting and streamlined placement when compared to light probe groups, and LPPVs.
10.2.8 Hide seams using meshes or textures
If the art direction allows for it, try using trim meshes to hide seams between objects. This is a commonly used technique in game development.
0 notes
Text
The Rise of Touchless Biometric Attendance with Mobile Features in 2025
As we move deeper into a world shaped by digital transformation, organizations are shifting how they manage people, spaces, and security. One of the most notable evolutions is the rise of biometrics attendance systems—particularly touchless solutions integrated with mobile capabilities. In 2025, these systems are no longer futuristic concepts but practical tools that are redefining how attendance is tracked and managed across diverse workplaces.

Let’s explore how the synergy between biometric technology and mobile-first experiences is setting a new standard for attendance management, security, and employee satisfaction.
What Is a Biometrics Attendance System?
A biometrics attendance system uses an individual’s unique physiological or behavioral traits—such as fingerprints, facial features, or iris scans—to record time entries and exits. Unlike traditional systems that rely on punch cards, PINs, or swipe cards, biometric systems significantly reduce the chances of proxy attendance (also known as "buddy punching") and eliminate the hassle of forgotten credentials.
The newer generation of biometric systems leverages touchless identification and integrates seamlessly with smartphones. This offers a convenient, hygienic, and highly secure alternative, especially in today’s post-pandemic workplace, where touch-free interactions are in high demand.
Why Touchless Technology Matters in 2025
Touchless biometric systems gained prominence during the COVID-19 pandemic due to the heightened emphasis on hygiene. But even as the world moved beyond the crisis, businesses realized that contactless attendance solutions were more than a temporary fix—they offered long-term advantages.
Here’s why touchless biometrics are becoming the norm:
Improved Hygiene and Safety: Eliminating shared surfaces reduces the spread of germs.
Faster Authentication: Facial recognition and mobile-based systems cut down wait times.
Convenience: No physical contact means quicker, seamless check-ins.
Scalability: Cloud-based backends allow centralized control for multiple office locations.
In 2025, with health and efficiency top of mind, these systems offer the perfect intersection of security, innovation, and user comfort.
Mobile-Enabled Biometrics: A Game-Changer
Imagine walking into your office and checking in through your smartphone using facial recognition or a quick Bluetooth handshake. That’s what mobile-first biometric systems are making possible today. These systems eliminate the need for dedicated terminals while delivering a personalized and secure experience.
The integration of mobile capabilities into biometric attendance systems brings several benefits:
Geofencing and GPS Integration: Ensures employees are marking attendance from authorized locations.
Self-Service Features: Employees can view attendance logs, request time-off, and manage shift schedules directly from their mobile app.
Real-Time Syncing: Data is uploaded to the cloud instantly, giving HR and operations teams live insights into attendance metrics.
Remote Workforce Compatibility: Perfect for hybrid teams or staff working on the go.
Solutions like these empower businesses with flexibility while keeping security airtight—something that modern organizations are prioritizing more than ever.
The Role of Cloud-Based Infrastructure
Modern biometric attendance solutions are not standalone devices; they are part of an intelligent, cloud-driven ecosystem. By integrating mobile, biometric, and cloud technologies, companies can manage attendance across multiple sites, sync data in real-time, and automate reporting.
This cloud-based infrastructure also enables:
Automatic backups and updates
Remote troubleshooting and system access
Integration with payroll and HR management tools
Data security through encryption and access controls
Such systems are especially useful for enterprises that operate across cities or even countries. Centralized dashboards and analytics allow decision-makers to get a unified view of workforce attendance—anytime, anywhere.
Benefits of Biometric Attendance in 2025
The adoption of biometric attendance systems in 2025 is being driven by a clear set of benefits:
Accuracy: Eliminates manual errors and time theft.
Accountability: Creates a transparent log of employee movement.
Efficiency: Reduces administrative workload for HR and operations teams.
Security: Minimizes the risk of impersonation and unauthorized access.
User Experience: Offers a seamless, non-intrusive method of tracking time.
These advantages contribute not just to improved attendance tracking, but also to better workforce management and productivity.
Use Cases Across Industries
Biometric and mobile attendance systems are finding application across a range of sectors:
Corporate Offices: For managing hybrid teams and enabling flexible check-ins.
Manufacturing Plants: Where shifts run 24/7 and tracking needs to be robust and tamper-proof.
Healthcare Facilities: For regulating staff attendance across multiple departments.
Educational Institutions: To monitor staff and student attendance without disrupting daily schedules.
Co-working Spaces: Where visitors, freelancers, and rotating teams need smooth, secure entry.
Every industry has unique requirements, but the core advantage remains the same—reliable, real-time attendance data delivered effortlessly.
Indirect Suggestion: Future-Ready Solutions
For businesses planning to implement these technologies, choosing the right partner is crucial. It's worth exploring platforms that offer mobile integration, biometric accuracy, and cloud-based scalability in one seamless solution. Companies that are at the forefront of this transformation are already providing such forward-thinking systems that empower organizations to modernize their attendance tracking infrastructure.
While many providers offer parts of the solution, few deliver the full package—combining innovation with usability. Organizations evaluating new-age biometric systems should consider solutions that are trusted by leading businesses, known for enabling secure, connected, and smart workplaces.
Conclusion
As organizations continue to adapt to a more mobile and digitally connected world, the need for smart, secure, and seamless attendance solutions is more evident than ever. Touchless biometric attendance systems with mobile features offer a future-ready approach—one that improves accuracy, safeguards employee health, and enhances overall efficiency.
Companies looking to modernize their operations should consider solutions that not only meet today’s needs but are scalable for tomorrow’s challenges. This is where innovators like Spintly are making an impact. By reimagining traditional attendance tracking with wireless, cloud-based, and mobile-integrated technology, Spintly is helping businesses transform their workplace experience without compromising on security or user convenience.
For organizations ready to embrace the next generation of attendance systems, exploring what platforms like Spintly have to offer could be a decisive step toward smarter workforce management.
#biometrics#biometric attendance#visitor management system#spintly#smartacess#accesscontrol#access control system#access control solutions#smartbuilding#mobile access
0 notes
Text

Introduction
Nginx is a high-performance web server that also functions as a reverse proxy, load balancer, and caching server. It is widely used in cloud and edge computing environments due to its lightweight architecture and efficient handling of concurrent connections. By deploying Nginx on ARMxy Edge IoT Gateway, users can optimize data flow, enhance security, and efficiently manage industrial network traffic.
Why Use Nginx on ARMxy?
1. Reverse Proxying – Nginx acts as an intermediary, forwarding client requests to backend services running on ARMxy.
2. Load Balancing – Distributes traffic across multiple devices to prevent overload.
3. Security Hardening – Hides backend services and implements SSL encryption for secure communication.
4. Performance Optimization – Caching frequently accessed data reduces latency.
Setting Up Nginx as a Reverse Proxy on ARMxy
1. Install Nginx
On ARMxy’s Linux-based OS, update the package list and install Nginx:
sudo apt update sudo apt install nginx -y
Start and enable Nginx on boot:
sudo systemctl start nginx sudo systemctl enable nginx
2. Configure Nginx as a Reverse Proxy
Modify the default Nginx configuration to route incoming traffic to an internal service, such as a Node-RED dashboard running on port 1880:
sudo nano /etc/nginx/sites-available/default
Replace the default configuration with the following:
server { listen 80; server_name your_armxy_ip;
location / {
proxy_pass http://localhost:1880/;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
Save the file and restart Nginx:
sudo systemctl restart nginx
3. Enable SSL for Secure Communication
To secure the reverse proxy with HTTPS, install Certbot and configure SSL:
sudo apt install certbot python3-certbot-nginx -y sudo certbot --nginx -d your_domain
Follow the prompts to automatically configure SSL for your ARMxy gateway.
Use Case: Secure Edge Data Flow
In an industrial IoT setup, ARMxy collects data from field devices via Modbus, MQTT, or OPC UA, processes it locally using Node-RED or Dockerized applications, and sends it to cloud platforms. With Nginx, you can:
· Secure data transmission with HTTPS encryption.
· Optimize API requests by caching responses.
· Balance traffic when multiple ARMxy devices are used in parallel.
Conclusion
Deploying Nginx as a reverse proxy on ARMxy enhances security, optimizes data handling, and ensures efficient communication between edge devices and cloud platforms. This setup is ideal for industrial automation, smart city applications, and IIoT networks requiring low latency, high availability, and secure remote access.
0 notes