#Data Security threats
Explore tagged Tumblr posts
Text
#lmao#lol#tiktok#national security#chinese spy#byteDance#espionage#data privacy#cybersecurity#congressional hearings#china-us relations#social media#misinformation#manipulation#intelligence agencies#hypothetical threat#chinese government#user data privacy#tiktok ownership#foreign influence#online surveillance#misinformation campaign
120 notes
·
View notes
Text
Hackers Access Legacy Systems in Oxford City Council Cyberattack

Summary: Hackers breached Oxford City Council's legacy systems, potentially accessing personal data of staff involved in elections between 2001 and 2022. While there is no evidence of large-scale data exfiltration, the incident highlights the risks posed by outdated infrastructure and insufficient segmentation of historical data.
Source: https://www.securityweek.com/hackers-access-legacy-systems-in-oxford-city-council-cyberattack/
More info: https://www.oxford.gov.uk/news/article/1704/statement-on-cyber-security-incident
2 notes
·
View notes
Text
The US is still carrying out a witch hunt against TikTok under the guise that it is a national security threat. Meanwhile, the US government has bled out our social security numbers and has done nothing to correct this for us.
But yes. TikTok is the problem. TikTok is the national security threat.
The US government at present is the true national security threat simply by being inactive and doing nothing to correct its citizens’ compromised identities, which are already sought after by individuals both foreign and domestic.
But yes. TikTok is the problem. TikTok is the national security threat.
#disgusting#republicans#politics#conservatives#data privacy#protection#national security#us government#us govt#tiktok#tiktok ban#social security#social security number#national security threat#facism#censorship
6 notes
·
View notes
Text
The decision to ban TikTok is interesting because yeah let’s take away what’s distracting over 170 million Americans everyday from the fucked up reality they live in. Let’s take away what’s distracting over half of the young generation and subduing them from going apeshit. Yeah that’s good. Take the dopamine shackles off yeah. Certainly that won’t result in anything.
#Walt talks#hey America can I have human right? maybe? maybe not? oh that’s scary! can I at least have an app to make silly videos on to cope? no?#I’ll just take the hint and go fuck myself then#not even. mentioning the amount of people but more importantly disabled people who make an income from tiktok#the amount of fundraisers that occur in tiktok#and when asked to present proof tiktok was a national security threat; they came up dry of solid proof and presented a lot of ‘maybes’#MIND YOU tiktok quite literally has a US center that houses it’s data SEPERATELY from it’s parent company#I’m fine with investigating the safety of social media but if we’re going to drive down that road#then meta needs to be under fire also#the exclusive targeting of tiktok makes their motive very clear and it’s very ugly
3 notes
·
View notes
Text
When Trusted Tools Turn Rogue: Hackers Exploit Salesforce App to Breach Global Firms
In a chilling revelation, Google has exposed a sophisticated cyber campaign where hackers are manipulating a Salesforce-related app to steal sensitive corporate data and extort companies. The attackers have successfully targeted organizations across Europe and the Americas by convincing employees to install a tampered version of Salesforce's Data Loader. This attack, tracked by Google's Threat Intelligence Group under the identifier UNC6040, underscores the growing vulnerabilities in enterprise software environments and the alarming ease with which cybercriminals can infiltrate even the most trusted digital infrastructures.

#Salesforce app breach#Google cyber threat report#UNC6040 hackers#Salesforce Data Loader attack#cyberattack global firms#enterprise software hack#cloud security breach#social engineering cybercrime#Google Threat Intelligence
0 notes
Text
How AI Is Revolutionizing Cybersecurity in 2025: Key Innovations and Benefits
Introduction As cyber threats grow increasingly sophisticated in 2025, AI cybersecurity is emerging as a game-changer. Artificial intelligence enhances digital defenses by automating threat detection, predicting attacks, and accelerating incident response. This blog explores how AI is revolutionizing cybersecurity in 2025 and why businesses and individuals must embrace these technologies to stay…
#AI cybersecurity#artificial intelligence#automated incident response#cyber defense#cybersecurity trends 2025#data security AI#machine learning security#threat detection AI
0 notes
Text
https://digimob.com.au/signs-of-malware-on-phone-or-laptop

#Phone Repair#Laptop Repair#Malware Detection#Mobile Security#Computer Security#Virus Removal#Tech Tips#Device Troubleshooting#Cyber Threats#Phone Performance Issues#Laptop Running Slow#Data Protection#Digimob Phone Repair#Device Malware Signs#Professional Repair Services
0 notes
Text
Insider Threats in Hybrid Work Environments: Mitigation Strategies.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Hybrid work has redefined insider risk. Learn how CIOs and tech leaders can mitigate threats with smart frameworks and real leadership. Why securing the inside is now your outside priority. The rise of hybrid work models has redrawn the boundary lines of enterprise security. With people working fluidly across home offices,…
#CIO Data Security#digital transformation leadership#Hybrid Work Cyber Risks#Insider Threat Mitigation#IT operating model evolution#News#Sanjay Kumar Mohindroo
0 notes
Text
Come find out how your information may be heading down stream to threat actors.
0 notes
Text
I haven’t really seen any of the more recent U.S. election news hitting tumblr yet so here’s some updates (now edited with sources added):
There’s evidence of Trump cheating and interfering with the election.
Possible Russian interference.
Mail-in ballots are not being counted or “recognized” in multiple (notably swing) states.
30+ bomb threats were called in and shut down polling stations on Election Day.
20+ million votes are still unaccounted for, and that’s just to have the same voter turnout as 2020.
There was record voter turnout and new/first-time voter registration this year. We definitely should be well over the turnout in 2020.
U.S. citizens are using this site to demand, not only a recount, but a complete investigation into election fraud and interference for the reasons stated above:
Here is what I submitted as an example:
An investigation for election interference and fraud is required. We desperately need a recount or even a revote. The American people deserve the right to a free and fair election. There has been evidence unveiled of Trump cheating and committing election fraud which is illegal. There is some evidence of possible Russian interference. At least 30+ bomb threats were called in to polling places. Multiple, notably swing states, have ballots unaccounted for and voting machines not registering votes. Ballots and ballot boxes were tampered with and burned. Over 20 million votes that we know of are unaccounted for. With record turnout and new voter registration this year, there should be no possibility that there are less votes than even in the 2020 election.
Sources (working on finding more links but if anyone wants to add info, it’s appreciated):
FBI addressing Russian interference and bomb threats:
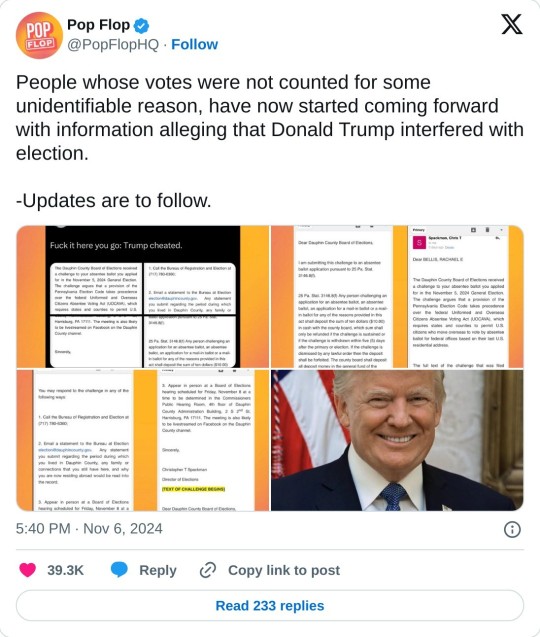
Emails released by Rachael Bellis (private account, can’t share original tweet) confirming Trump committing election fraud:
Pennsylvania's Centre County officials say they are working with their ballot scanner vendor to figure out why the county's mail-in ballot data is "not being recognized when uploaded to the elections software:”

Wisconsin recount:
[ID:
Multiple screenshots and images.
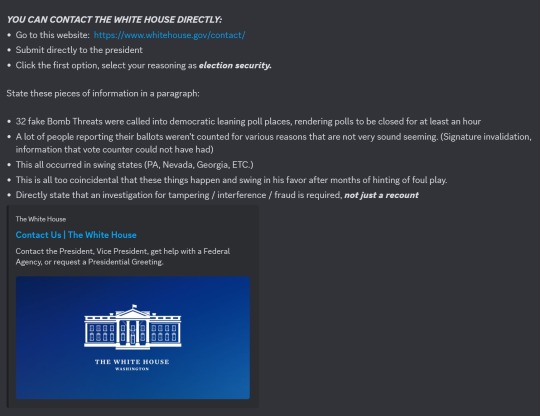
The first is a screenshot with a link and information for contacting the White House directly regarding election fraud. The instructions include choosing to leave a comment to President Joe Biden directly and to select election security as the reason.
The screenshot then instructs people to include any or all of the following information in a paragraph as a comment to the president:
32 fake bomb threats were called into Democratic leaning poll places, rendering polling places closed for at least an hour.
A lot of people reporting their ballots were not counted for various reasons.
This all occurred in swing states.
This is too coincidental that these things happen and swing in his favor after months of hinting at foul play.
Directly state that an investigation for tampering, interference, fraud is required, not just a recount.
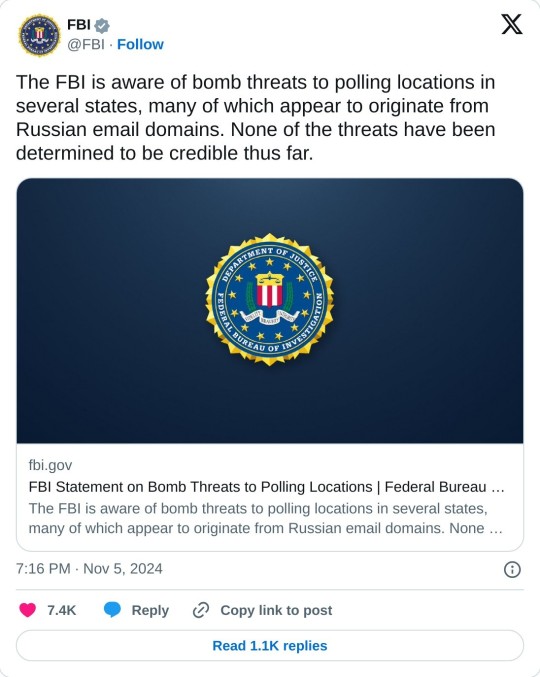
The second image is from the FBI Twitter account that reads:
The FBI is aware of bomb threats to polling locations in several states, many of which appear to originate from Russian email domains. None of the threats have been determined to be credible thus far. https://t.co/j3YfajVK1m — FBI (@FBI) November 5, 2024
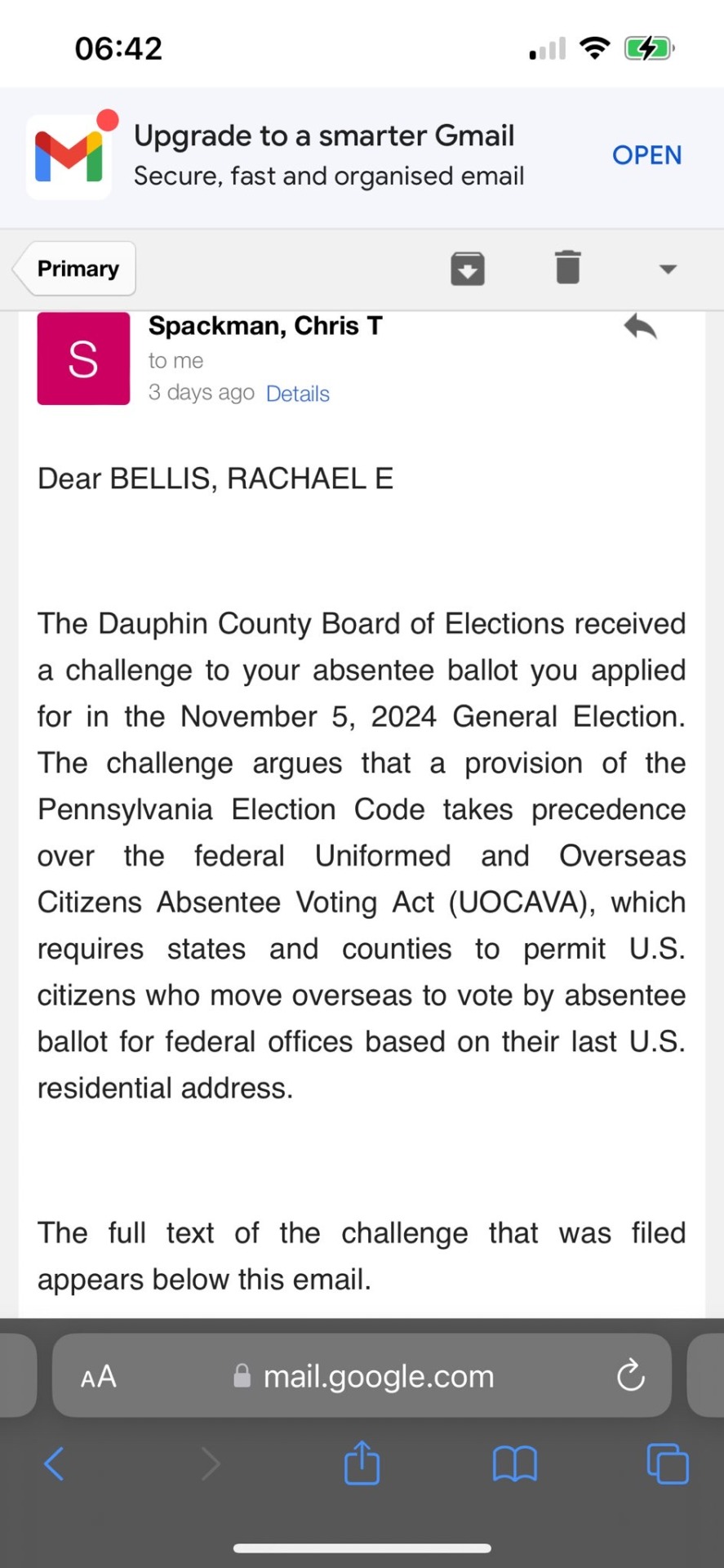
The next four Gmail screenshots of an email sent to Rachael Bellis from Chris T. Spackman that read together as follows:
Dear BELLIS, RACHAEL E., The Dauphin County Board of Elections received a challenge to your absentee ballot you applied for in the November 5, 2024 General Election. The challenge argues that a provision of the Pennsylvania Election Code takes precedence over the federal Uniformed and Overseas Citizens Absentee Voting Act (UOCAVA), which requires states and counties to permit U.S. citizens who move overseas to vote by absentee ballot for federal offices based on their last U.S. residential address.
The full text of the challenge that was filed appears below this email.
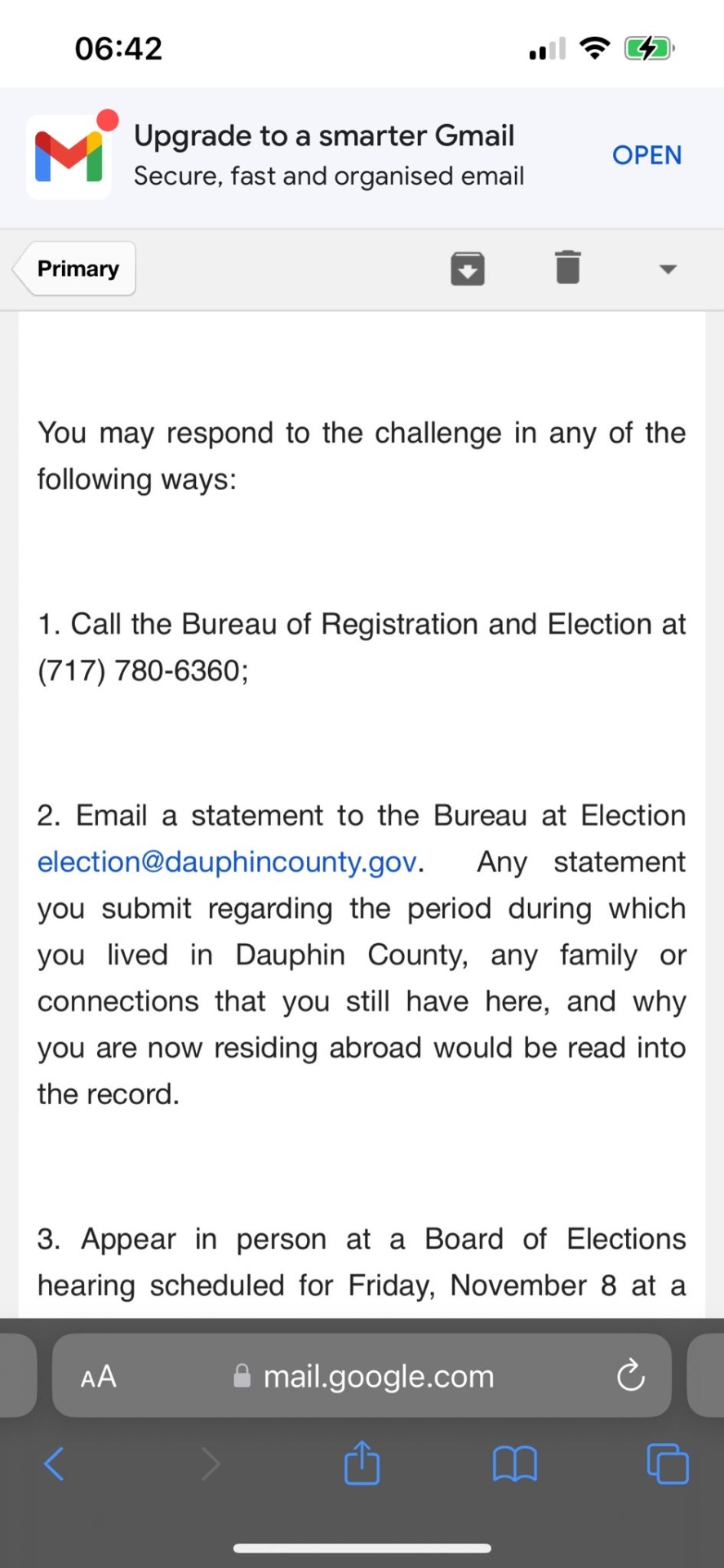
You may respond to the challenge in any of the following ways:
1. Call the Bureau of Registration and Election at (717) 780-6360;
2. Email a statement to the Bureau at Election [email protected]. Any statement you submit regarding the period during which you lived in Dauphin County, any family or connections that you still have here, and why you are now residing abroad would be read into the record.
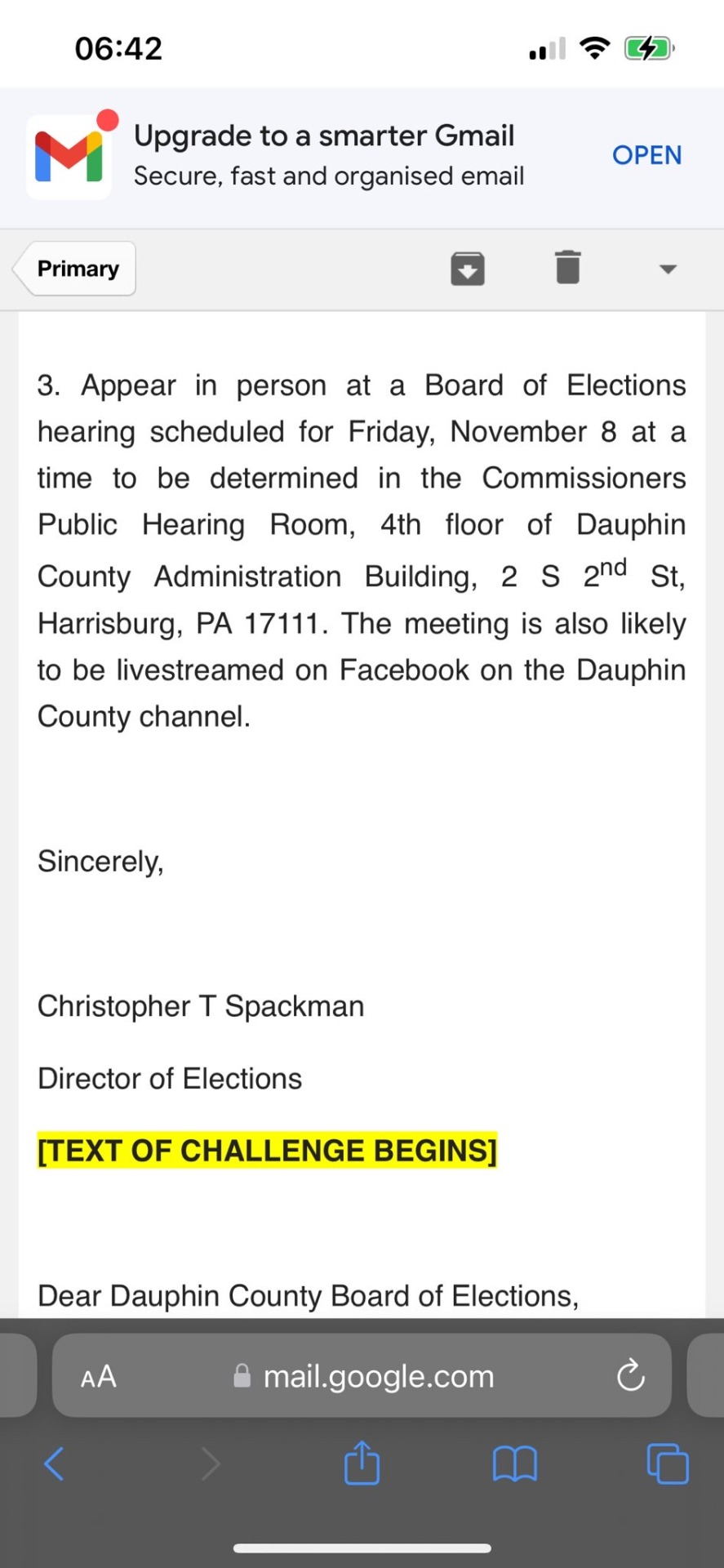
3. Appear in person at a Board of Elections hearing scheduled for Friday, November 8 at a time to be determined in the Commissioners Public Hearing Room, 4th floor of Dauphin County Administration Building, 2 S 20d St, Harrisburg, PA 17111. The meeting is also likely to be livestreamed on Facebook on the Dauphin County channel.
Sincerely,
Christopher T Spackman
TEXT OF CHALLENGE BEGINS
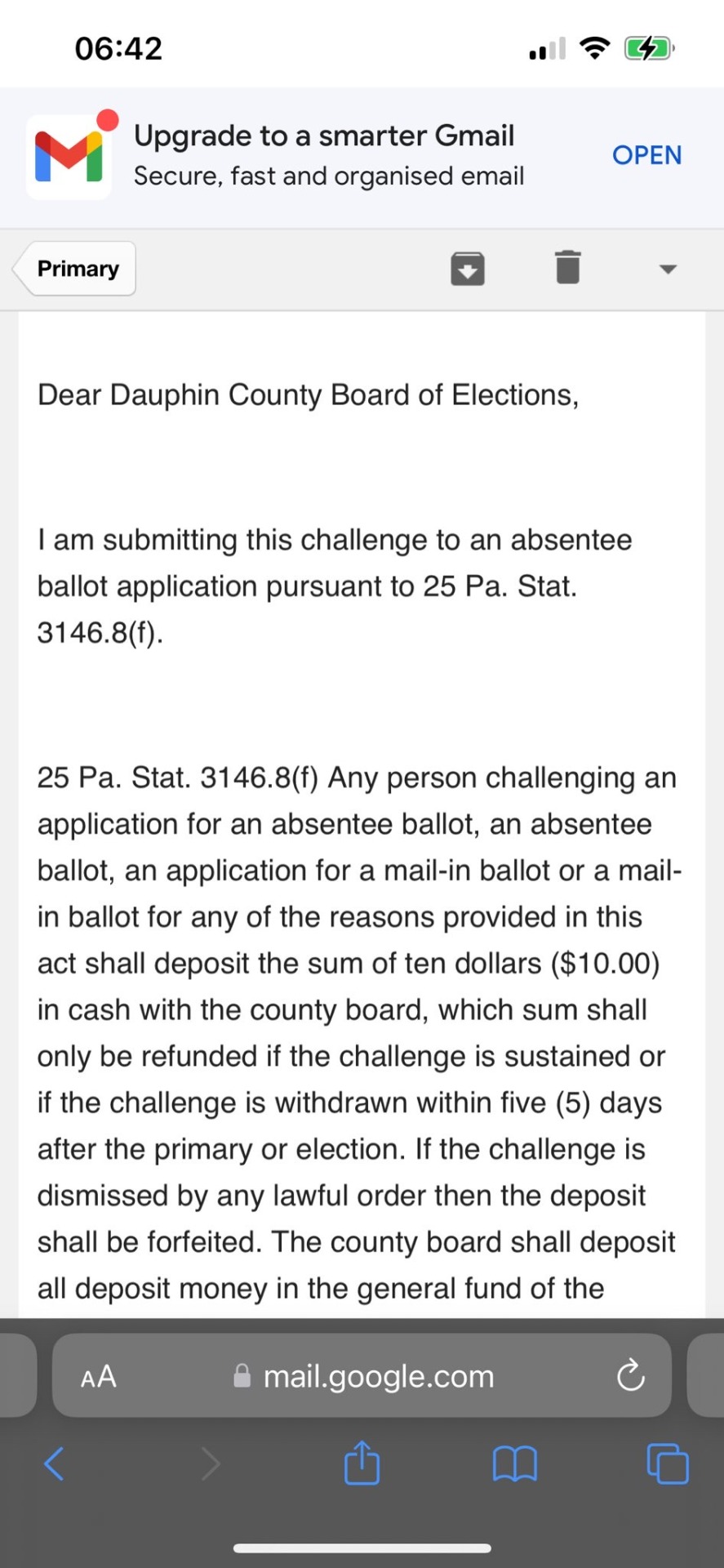
Dear Dauphin County Board of Elections,
I am submitting this challenge to an absentee ballot application pursuant to 25 Pa. Stat.
3146.8(f).
25 Pa. Stat. 3146.8(f) Any person challenging an application for an absentee ballot, an absentee ballot, an application for a mail-in ballot or a mail-in ballot for any of the reasons provided in this act shall deposit the sum of ten dollars ($10.00) in cash with the county board, which sum shall only be refunded if the challenge is sustained or if the challenge is withdrawn within five (5) days after the primary or election. If the challenge is dismissed by any lawful order then the deposit shall be forfeited. The county board shall deposit all deposit money in the general fund of the…
The rest of the forwarded email is cut off.
The last image is a screenshot of the official statement from the Centre County, Pennsylvania Board of Commissioners released on November 6, 2024 that states:
Centre County Working with Ballot Scanner Vendor to Export Election Results.
(Bellefonte, PA) -Centre County Elections Office is working continuously to provide mail-in ballot data in order to post unofficial results.
To this point, all ballots have been scanned, including all mail-in ballots.
Centre County's Election team and IT team have identified that the data are successfully being exported from the mail-in ballot scanners, but that the data is not being recognized when uploaded to the elections software.
Centre County's Administrator, John Franek, Jr. stated, "We have not stopped working, and we will continue to work until unofficial results are posted and reported to the Pennsylvania Department of State."
As a next step, Centre County has begun working with the equipment vendor to adjust configurations to make the two systems-the mail-in ballot scanner and the elections software where data are uploaded -compatible with one another.
We will provide updates as we make progress.
/end ID]
#sources added#us politics#us election#presidential election#2024 presidential election#election interference#election integrity#election security#image described#image description in alt#image description included#image description added#described#kamala harris#kamala 2024#us news#us presidents#updated id
36K notes
·
View notes
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text
The Importance of Cybersecurity
Living in a Digital World Full of Risks In today’s hyper-connected world, cybersecurity is no longer a luxury — it is a necessity.Every aspect of our lives depends on digital platforms. This ranges from social media profiles to banking apps. It also includes corporate databases and government systems.While this connectivity offers incredible convenience and efficiency, it also creates…
#business security#cyber attacks#cybercrime prevention#cybersecurity#cybersecurity awareness#cybersecurity in business#cybersecurity threats#cybersecurity tips#data protection#digital security#information security#internet safety#online safety#protecting data online
0 notes
Text
A History of Cybersecurity
in the Twenty-First Century 🧠 TL;DR – A History of Cybersecurity in the 21st Century 🔐💻 🔍 Overview:From the early 2000s to the 2020s, cybersecurity has evolved dramatically in response to increasingly sophisticated threats. What started with experimental worms has escalated into ransomware, nation-state cyber warfare, and AI-powered attacks. 📅 2000s – The Worm Era 🪱 Famous viruses: ILOVEYOU,…
#21st century cyber threats#AI in cybersecurity#APTs#cloud security#Colonial Pipeline attack#cyber defense evolution#cybercrime trends#cybersecurity history#cybersecurity statistics#cybersecurity timeline#cyberwarfare#evolution of cybersecurity#future of cybersecurity#IoT vulnerabilities#major data breaches#mobile malware#nation-state cyberattacks#Patch Tuesday#phishing scams#ransomware as a service#ransomware attacks#SIEM systems#Stuxnet#supply chain attacks#worm era
0 notes
Text
Dark Web Monitoring: How Companies Can Protect Their Data?

The dark web is a hidden part of the internet where cybercriminals trade stolen data, sell hacking tools, and conduct illicit transactions. With the rise of cyber threats, businesses must take proactive steps to protect their sensitive information from being exploited in these underground marketplaces. Dark web monitoring has emerged as a crucial cybersecurity strategy that enables organizations to detect and mitigate data breaches before they escalate into significant financial and reputational damage.
For C-suite executives, startup entrepreneurs, and managers, understanding how the encrypted web operates and implementing robust monitoring solutions is vital. This article explores the importance of dark web monitoring, how it works, and the best practices companies can adopt to safeguard their data.
The Risks of the Dark Web for Businesses

Businesses of all sizes face cybersecurity threats, but large enterprises and startups dealing with sensitive customer data are prime targets for cybercriminals. Key risks include:
Stolen Credentials: Employee and customer login details are frequently sold on darknet forums, leading to unauthorized access and potential financial fraud.
Intellectual Property Theft: Trade secrets, proprietary algorithms, and confidential business plans can be leaked or auctioned to competitors.
Financial Scams and Fraud: Cybercriminals use compromised business accounts for phishing campaigns, identity fraud, and extortion schemes.
Ransomware Attacks: The dark web serves as a marketplace for ransomware-as-a-service (RaaS), enabling even novice hackers to launch devastating cyberattacks.
Customer Data Exposure: Personal details of customers can be misused for identity theft, damaging brand trust and inviting legal repercussions.
Insider Threats: Employees with access to sensitive information can be tempted to sell data on anonymous web marketplaces, creating an internal risk for organizations.
DDoS-for-Hire Services: Malicious actors offer distributed denial-of-service (DDoS) attacks as a service, allowing competitors or disgruntled individuals to target businesses.
Counterfeit Goods and Fraudulent Transactions: Fraudsters may use stolen payment information to conduct illegal transactions or produce counterfeit versions of proprietary products.
How Dark Web Monitoring Works?
Dark web monitoring involves scanning and tracking illicit activities across underground forums, encrypted marketplaces, and hidden chat rooms. Businesses leverage specialized cybersecurity tools to detect whether their sensitive data is being traded or discussed in these hidden networks.
Key Components of Dark Web Monitoring

Continuous Scanning – Automated systems monitor hidden web marketplaces, hacker forums, and data dump sites for leaked credentials and business information.
Artificial Intelligence & Machine Learning – AI-driven tools analyze patterns and detect anomalies in cybercriminal activities, providing real-time alerts.
Credential Tracking – Security platforms cross-reference stolen credentials with company databases to identify breached accounts.
Threat Intelligence Reports – Cybersecurity experts compile intelligence reports to help organizations assess risks and take proactive measures.
Incident Response & Remediation – When a breach is detected, organizations can act swiftly by resetting compromised credentials, informing affected users, and reinforcing security measures.
Deep Web vs. Dark Web Monitoring – Unlike encrypted web monitoring, which focuses on hidden illicit activities, deep web monitoring includes scanning non-indexed sites for potential threats.
Behavioral Analytics – AI-powered monitoring tools use behavioral analytics to identify suspicious patterns that could indicate upcoming cyberattacks.
Best Practices for Dark Web Protection
Implementing an effective deep web monitoring strategy requires a combination of technology, policies, and employee awareness. Here are key best practices:
1. Invest in Shadow Web Monitoring Services
Companies should leverage cybersecurity solutions that specialize in hidden web intelligence, such as:
IBM X-Force Threat Intelligence
Recorded Future
SpyCloud
Have I Been Pwned (for individual email monitoring)
Digital Shadows
DarkOwl
These services help organizations detect stolen credentials, financial data leaks, and other vulnerabilities before cybercriminals exploit them.
2. Strengthen Employee Cyber Hygiene
Many cyber breaches originate from weak or reused passwords. Businesses should:
Implement multi-factor authentication (MFA) to reduce the risk of unauthorized access.
Enforce strong password policies with frequent updates.
Conduct regular cybersecurity training to educate employees about phishing attacks and data security practices.
Use password managers to generate and store complex passwords securely.
Implement role-based access control (RBAC) to limit access to critical data based on employee roles.
3. Monitor Third-Party Vendor Security
Supply chain attacks are becoming increasingly common. Organizations must:
Assess the security measures of third-party vendors.
Require dark web monitoring as part of vendor risk management policies.
Limit access to sensitive data for external partners.
Regularly audit vendor compliance with cybersecurity standards.
4. Regularly Conduct Penetration Testing & Security Audits
Simulating cyberattacks through penetration testing helps businesses identify vulnerabilities before attackers exploit them. Security audits should:
Assess cloud security configurations.
Identify weak points in networks and endpoints.
Ensure compliance with industry regulations (e.g., GDPR, HIPAA, CCPA).
Evaluate IoT security as connected devices become prime targets for cyber threats.
5. Develop an Incident Response Plan
A well-structured incident response plan ensures businesses can react swiftly in case of a data breach. It should include:
A crisis management team responsible for addressing cyber threats.
Steps to contain, assess, and recover from data leaks.
Legal & PR strategies to handle potential reputational damage.
Forensic analysis to trace the source of breaches and prevent recurrence.
Cyber insurance to mitigate financial losses from data breaches and ransomware attacks.
Future of Dark Web Monitoring and Cybersecurity Trends

As cybercriminals evolve their tactics, the future of deep web monitoring will rely heavily on:
AI & Machine Learning Enhancements: Advanced AI models will predict and prevent cyber threats more efficiently.
Blockchain for Data Protection: Decentralized security frameworks will help organizations secure sensitive transactions.
Zero Trust Security Models: Businesses will adopt stricter verification mechanisms to minimize data breaches.
Collaborative Cyber Threat Intelligence: Companies will increasingly participate in shared intelligence networks to combat cyber threats collectively.
Quantum Computing’s Role in Cybersecurity: As quantum technology advances, it will impact encryption and security protocols, both strengthening and challenging traditional cybersecurity measures.
Cloud Security Enhancements: As businesses migrate to the cloud, improved security measures will be required to prevent cloud-based data breaches.
AI-Powered Fraud Detection: Enhanced AI-driven tools will monitor financial transactions and detect fraudulent activities in real-time.
Advanced Ransomware Defense Strategies: New technologies will emerge to counteract the growing threat of ransomware attacks on businesses.
Conclusion
The dark web poses a serious threat to businesses, making deep web monitoring an essential component of modern cybersecurity strategies. By proactively scanning for data breaches, investing in AI-powered threat intelligence, and educating employees, companies can mitigate risks and safeguard their sensitive information.
For C-suite executives and entrepreneurs, the message is clear: cybersecurity is no longer optional—it is a business imperative. Prioritizing hidden web monitoring today will ensure resilience against emerging cyber threats, helping businesses maintain trust, security, and long-term success in the digital landscape.
Uncover the latest trends and insights with our articles on Visionary Vogues
#Dark web monitoring#cybersecurity#data protection#cyber threats#stolen credentials#ransomware defense#AI security#threat intelligence
0 notes
Text
5 Signs You Have Outgrown Your Accounting System
Is your accounting system keeping up with your business growth? Many businesses unknowingly rely on outdated systems that no longer serve their evolving needs. If you're experiencing inefficiencies, errors, or bottlenecks, it might be time to assess whether your current system is still the right fit.
Signs You’ve Outgrown Your Accounting System
1. Limited Scalability
As your business grows, your accounting system should scale with it. If your current system struggles to handle increased transactions, multiple users, or expanding financial needs, it’s a clear sign that you need a more robust solution.
2. Lack of Integration
Are you manually transferring data between different systems? Modern businesses need seamless integration between accounting, payroll, CRM, and other essential tools to ensure efficiency and accuracy.
3. Inadequate Financial Reporting
Timely and insightful financial reporting is crucial for decision-making. If your system doesn’t provide real-time insights or requires extensive manual effort to generate reports, it’s time to consider an upgrade.
4. Compliance and Security Concerns
With evolving financial regulations and cybersecurity threats, relying on outdated software can put your business at risk. A modern accounting system ensures compliance and enhances data security.
5. High Maintenance Costs
If you’re spending too much time and money on system maintenance, updates, and troubleshooting, investing in a new system can save costs and improve efficiency in the long run.
What’s Next?
Discover how the right accounting solution can unlock streamlined operations, improved reporting, and better decision-making. Get your free copy now and take control of your business growth today!
0 notes
Text
गूगल ने प्ले स्टोर से हटाए 331 मालिशियस ऐप्स: वेपर ऑपरेशन से जुड़े थे, 6 करोड़ से ज्यादा डाउनलोड्स
Google removed 331 malicious apps from Play Store: अगर आपके स्मार्टफोन में कुछ खास ऐप्स इंस्टॉल हैं, तो आपकी सुरक्षा खतरे में हो सकती है। गूगल ने हाल ही में अपने प्ले स्टोर से 331 मालिशियस ऐप्स को हटा दिया है, जो फिशिंग कैंपेन और “वेपर ऑपरेशन” (Vapor Operation) का हिस्सा थे। इन ऐप्स ने चुनिंदा एंड्रॉयड वर्जन्स की सिक्योरिटी को बायपास करने की क्षमता रखी थी और इन्हें अब तक 6 करोड़ से ज्यादा बार…
#Ad Fraud#Android Security#AquaTracker#BeatWatch#BleepingComputer#ClickSave Downloader#cyber fraud#Data Theft#Google Play Store#IAS Threat Lab#Malicious Apps#Phishing Campaign#Scan Hawk#TranslateScan#Vapor Operation
0 notes