#Data Tracking
Explore tagged Tumblr posts
Text









217 notes
·
View notes
Text
Bit concerned about AO3’s new TOS, to be honest.
I’m sure I’m just being paranoid but I have this mental image of some random AO3 employee in America looking at what I read and then going through the images on my phone.
13 notes
·
View notes
Text
The first attempt to transfer memories between the brain and an 8-bit computer.
#vaporwave#80s aesthetic#synthwave#retrowave#retrofuture#glitch#glitch gif#gif#glitchart#glitch art#art#abstract#abstract art#corrupted data#computer art#computing#data transfer#data transmission#data tracking#trippy gif
23 notes
·
View notes
Video
youtube
Your Android Phone Tracking You and Listening. TURN THIS OFF by Useful Things
4 notes
·
View notes
Text

5 notes
·
View notes
Text
Essential Toolkit for Outbound Lead Generation
To succeed in outbound lead generation, you need the right mix of tools and tactics. LinkedIn is a great place to start. Personalize your connection requests and engage with your prospects’ posts to build trust before making a pitch. This human touch can make your outreach more effective.
Email automation tools are also essential,they help you send follow-ups consistently without the manual work.This keeps your pipeline active and efficient.
Next, track your progress. Pay attention to key metrics like open rates, response rates, and qualified leads. These KPIs show what’s working and what needs improvement.
Finally, don’t be afraid to test different messages. A/B testing your emails or call scripts helps you find the most effective way to connect with your audience.
With this toolkit,LinkedIn, email automation, data tracking, and testing,you’ll be well equipped to grow your leads and boost sales.
#outbound#Outbound lead generation#leadgeneration#outbound generation#A/B testing#kpi#linkedin#toolkit#email automation#data tracking
0 notes
Text
Jade Ann Byrne 🩸 Blood Pressure Chronicles: What 92/45 and 96/57 Say About My Post Home Alone Midnight Journey
Jade Ann Byrne 🩸 Blood Pressure Chronicles: What 92/45 and 96/57 Say About My Post Home Alone Midnight Journey Life is measured in moments, and health is written in numbers. Today’s check-in? A rollercoaster of 92/45 mmHg followed by a slight rebound to 96/57 mmHg, with a steady pulse of 85 bpm. Let’s break it down and see what the body is whispering. 📊 Breaking It Down: 🔹 Systolic (92 → 96…
#adrenaline and BP correlation#AI-driven BP tracking#ambulatory blood pressure#arm circumference BP adjustments#arterial stiffness index#automated BP cuff#autonomic dysfunction#baroreflex#blood circulation#blood pressure#blood pressure monitor#blood pressure variability#blood volume pulse#BP accuracy factors#BP artifacts#BP cuff calibration#BP logging#BP rebound effect#BP telemetry#BP trends analysis#caffeine effects on BP#capillary refill time#cardiovascular health#chronic illness#circulatory efficiency#cuff inflation technology#cuff positioning#daily vitals#data tracking#diastolic pressure
0 notes
Text
UHF Reader Based on Pico W & ESP32 with 50 Tags/Second Reading within 1.5 Meter Range

A UHF Reader (Ultra High Frequency Reader) is a device that is used to read and write data from UHF RFID tags within the 860MHz-960MHz frequency range. It is a multi tags 50 tags/second reading/writing device within 1-1.5 meter range designed with cutting edge UHF technology. It is a compact, portable and easy to use device.
The UHF reader has 2 variants: one is UHF Reader by Pico W and another is UHF Reader by ESP32. The Pico W variant comes with RP2040 microcontroller with Wi-Fi and BLE support. It is compatible with MicroPython, CircuitPython and Arduino for programming. ESP32 variant comes with ESP32 S3 series microcontroller and has 2.4GHz & Bluetooth 5 (LE) support. It is compatible with Arduino and Espressif IDE for programming.
Key Features and Specifications:
UHF Reader Pico Variant:

Powered by Raspberry Pi Pico W
RP2040 microcontroller dual-core Arm Cortex M0+ microprocessor with 264kB RAM
Supports Wi-Fi and BLE
1.14” TFT display for better visualization
Multi-tone buzzer for audio alerts
Micro USB Support for programming & Type C support for power
3 programmable buttons and Reset button
SD card slot for data storage/transfer
LED Status for power and battery charging
Multipurpose GPIOs breakout for interfacing external peripherals
SWD pins breakout for serial debugging
Supports MicroPython, CircuitPython, and Arduino for programming
UHF Reader ESP32 Variant:

Powered by ESP32 S3 WROOM-1
Dual-core 32 bit LX7 microprocessor with Up to 8 MB PSRAM and up to 16 MB flash memory
Supports 2.4GHz (802.11b/g/n) Wi-Fi and Bluetooth 5 (LE)
1.14” TFT display with ST7789 display driver
Comes with a Read and Write UHF module.
Frequency range of 865.1MHz-867.9MHz (for EU/UK) and 902.25MHz-927.75MHz (for US)
Can Identify 50 tags/second up to the 1.5-meter range.
TTL UART communication interface and communication baud rates 115200bps-38400bps
output power 18-26dBm and output power accuracy +/- 1dB
operation current 180mA at 3.5V (26 dBm Output), 110mA at 3.5V (18 dBm Output)
Multi-tone buzzer for audio alerts
2 user programmable buttons, Boot and Reset buttons
For power and programming support, the Type C Interface
SD Card slot for data transfer/storage
LED status for power and charging
Multipurpose GPIOs breakout for interfacing external peripherals
Supports Arduino and Espressif IDE for programming
By using ESP32 and RP2040, you can build a UHF RFID reader for scan tags and data tracking. This UHF Reader with ESP32 and Pico by SB Components is suitable for applications like warehouses, retail stores, and many other applications where you want to track your inventory data accurately.
#technology#innovation#tech#iot#rfid#uhf#uhf reader#arduino#espressif#iot applications#raspberry pi#rp2040#esp32#projects#programming#ultra high frequency reader#rfid tags#data tracking#electronics
1 note
·
View note
Text
Online Privacy: How Much Information Are You Sharing Without Realizing It?

The internet offers a treasure trove of information and connectivity. From social media interactions to online shopping experiences, we constantly share data in exchange for convenience and entertainment. However, in this ever-connected world, the lines between convenience and privacy can easily become blurred.
This blog delves into the concept of online privacy, exploring the different ways we share information online, often without even realizing it. Whether you're a seasoned internet user or just starting to navigate the digital landscape, this guide will raise your awareness about your online footprint and empower you to make informed decisions about your privacy.
The Ever-Expanding Online Footprint: How We Share Data
Our online footprint refers to the trail of data we leave behind as we navigate the internet. This data can include:
Personal Information: Names, addresses, phone numbers, email addresses, and even birthdays are often shared willingly when creating online accounts or registering for services.
Browsing History: Websites you visit, search queries you enter, and links you click on all contribute to a detailed record of your online interests and activities.
Social Media Activity: Posts, comments, photos, and even "likes" on social media platforms paint a picture of your preferences, relationships, and even location.
Device Data: Smartphones and other connected devices collect information about your location, app usage, and even browsing habits.
Cookies and Tracking Pixels: These small pieces of code embedded in websites track your online activity across different platforms, building a comprehensive profile of your digital behavior.
The Hidden Costs of Oversharing: Why Online Privacy Matters
While sharing information online can be convenient, there are potential consequences to consider:
Targeted Advertising: Companies use your online footprint to create targeted advertising profiles, bombarding you with ads based on your browsing habits and interests.
Identity Theft: Excessive personal information shared online can make you vulnerable to identity theft, where criminals use your data to commit financial fraud or impersonate you.
Social Engineering Attacks: Cybercriminals can exploit information gleaned from your online footprint to launch social engineering attacks, tricking you into revealing sensitive data or taking actions that compromise your security.
Limited Job Opportunities: Some employers might screen potential candidates' online profiles, and oversharing personal information or unprofessional content could negatively impact your job prospects.
Loss of Control: Once information is shared online, it can be difficult to control who sees it or how it's used. Oversharing can also lead to a sense of loss of control over your own privacy.
Empowering Yourself: Taking Control of Your Online Privacy
Here are some actionable steps you can take to manage your online privacy and minimize the amount of data you share unknowingly:
Review Your Privacy Settings: Most social media platforms and online services offer granular privacy settings. Take time to understand these settings and restrict data sharing according to your comfort level.
Limit App Permissions: Be mindful of the permissions you grant to apps on your phone or other devices. Only allow access to features necessary for the app's functionality.
Think Before You Share: Before posting anything online, consider who might see it and the potential consequences. Is it something you would be comfortable sharing with the world?
Use Strong Passwords and Multi-Factor Authentication: Implement strong, unique passwords for your online accounts and enable multi-factor authentication for an extra layer of security.
Consider a Privacy-Focused Browser: Some web browsers offer enhanced privacy features like blocking tracking cookies and preventing websites from collecting your data.
Educate Yourself: Knowledge is power. Invest in a comprehensive Cyber Security Course to gain a deeper understanding of online privacy threats and learn advanced techniques to protect your data.
Investing in Knowledge: Cyber Security Courses
A Cyber Security Course can equip you with the tools and knowledge you need to navigate the online world with confidence and protect your privacy. Here's how these courses can benefit you:
Understanding Data Privacy Regulations: Cyber Security Courses cover regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act), empowering you to understand your rights and take control of your data.
Learning Data Security Best Practices: These courses delve into best practices for data security, including secure data storage, encryption techniques, and responsible data sharing practices.
Developing Online Privacy Strategies: Cyber Security Courses equip you with the knowledge to create personalized online privacy strategies tailored to your individual needs and risk tolerance.
Identifying Privacy Threats: These courses explore the various threats to online privacy, including malware, phishing scams, and data breaches. They equip you with the skills to identify these threats and avoid falling victim.
Staying Up-to-Date on Emerging Threats: The cyber threat landscape is constantly evolving. Cyber Security Courses help you stay informed about the latest privacy threats and equip you with the knowledge to adapt your privacy strategies accordingly.
Cyber Security Courses: Options for All Levels
Here's a breakdown of the various Cyber Security Courses available, catering to different learning styles and experience levels:
Cyber Security Course Beginner: These introductory courses provide a foundational understanding of online privacy concepts, common data collection practices, and essential strategies for protecting your digital footprint. They are ideal for individuals new to the online world or those seeking to enhance their basic privacy awareness.
Cyber Security Course Intermediate: These courses delve deeper into online privacy regulations, data security best practices, and explore advanced privacy-enhancing technologies like anonymization and encryption. They are suitable for individuals with some understanding of online privacy who want to refine their strategies and learn how to mitigate more sophisticated data collection techniques.
Cyber Security Course Advanced : These specialized courses cover intricate topics like digital forensics and online reputation management. They are geared towards experienced IT professionals and security enthusiasts seeking to delve deeper into protecting their own privacy and potentially helping others do the same.
Building a Culture of Online Privacy Awareness
Online privacy is not a one-time fix; it's an ongoing process of awareness and informed decision-making. By understanding how your data is collected and taking proactive steps to minimize unnecessary information sharing, you can significantly enhance your online privacy and protect yourself from potential threats.
Investing in a comprehensive Cyber Security Course empowers you to navigate the online world with confidence, control your digital footprint, and create a more secure and private online experience for yourself. Remember, knowledge is your greatest weapon in the fight for online privacy. Don't wait until your data falls into the wrong hands – take charge of your online privacy today!
#cyber security course#cyber security#cybersecurity#techcore#cyber attack#data security#social security#data privacy#online privacy#internet privacy#data theft#data tracking#data storage#hacking#awareness#cyber awareness
1 note
·
View note
Text
Entry 9:
Unraveling the Web: How Facebook Collects Your Data
In the interconnected world of social media, Facebook stands as a giant. With over 2.8 billion monthly active users, it’s a treasure trove of data. But have you ever wondered how Facebook collects your data? Let’s delve into it.
What Data Does Facebook Collect?
Facebook collects a wide array of information. This includes the information you provide directly like your name, email, birthday, and location. It also includes the content you post, your friends list, the pages and hashtags you interact with, and even the type of device you’re using.
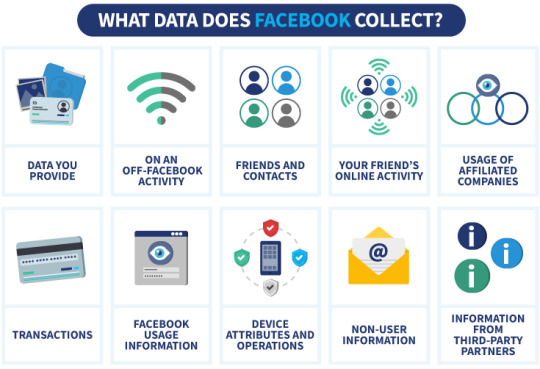
How Does Facebook Collect Data?
Directly from the Users: The most straightforward way Facebook collects data is directly from its users. When you sign up, you provide personal details. Every time you post a status, like a page, or start a chat, Facebook collects that information.
Through Your Actions: Facebook tracks your interactions. This includes the posts you like, the pages you follow, and the friends you have. This helps Facebook understand your preferences and tailor your News Feed.
Through Third-Party Apps and Websites: When you use your Facebook account to log into other apps or websites, Facebook receives data from these sites. This can include information about your activities and purchases.
Through Cookies: Like many websites, Facebook uses ‘cookies’ to collect data. These small pieces of data are stored on your browser and let Facebook track your activity both on and off the platform.
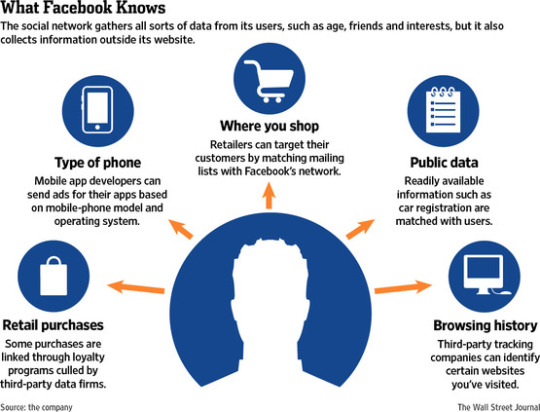
Why Does Facebook Collect Data?
Facebook collects data primarily to personalize your experience. By understanding your preferences, Facebook can show you relevant content, suggest new friends, and even target advertisements.
However, this extensive data collection has raised privacy concerns. It’s essential to regularly review your privacy settings and be mindful of the information you share.

Remember, in the digital world, knowledge is power. Understanding how platforms like Facebook collect and use your data is the first step towards protecting your online privacy.
#college#data#data privacy#university#data security#the philippines#Facebook#social media#data tracking#data collection
0 notes
Text
🌟 Revolutionize school management with Schezy!
Explore Schezy, the revolutionary school management system transforming education in India. Designed to streamline administrative tasks, Schezy offers a user-friendly interface, centralized database management, and tailored modules for attendance, fees, exams, and more.

This all-in-one solution enhances communication, saves time, and ensures data security. From efficient information updates to online fee payments and real-time notifications, Schezy redefines school management for administrators, teachers, parents, and staff. Embrace the future of education with Schezy's innovative features and comprehensive benefits. Read more about Schezy in detail here.
Ready to revolutionize your school's management? Register today!

Join the Schezy revolution today and unlock the future of school management! #Schezy #EducationTech #SchoolManagement #SchezyRevolution
Read more Agami blogsStart Your Agami Journey: Schedule Today!
#School Management Software#Educational Technology#Student Information System#Administration Software#Data Tracking#Attendance Management#Fee Management#Hostel Management#Cloud-based School Software#Education Administration#School ERP
0 notes
Text
But according to the FTC, from 2014 to 2020, guess who was tracking consumers’ browser information and then selling it to more than 100 other companies through an affiliate called Jumpshot? Ironically enough, Avast Limited.
0 notes
Video
youtube
How Big Tech Steals Our Livesby Andrewism
1 note
·
View note
Text
Level Up Your Affiliate Game: Micro-Conversions are the Mighty Mushrooms of Success
Cultivate affiliate success with micro-conversions: Nurture leads and watch your revenue blossom! Forget gold rushes and diamond mines, fellow hackers! The real affiliate treasure lies in the hidden valleys of micro-conversions. These seemingly insignificant steps – email signups, free ebook downloads, quiz participations – might not look like much, but string them together, and you’ve got…

View On WordPress
#affiliate marketing tips#automation#challenges and quizzes#data tracking#email marketing strategies#interactive content#lead nurturing#micro-conversions#optimization
0 notes
Text
"After the fall of Roe on Friday—the 1973 decision that legalized abortion in the United States—people online started urging others to delete their period tracking apps."
#periods#roe v wade#abortion#data tracking#data#period tracking apps#reproductive rights#human rights#delete your period tracking apps
1 note
·
View note