#Database Backups
Explore tagged Tumblr posts
Text
Video to Backup and Restore your WordPress Files and Database
Backup and Restore your WordPress Files and Database
youtube
View On WordPress
#Database Backups#File Backup#Wordpress#WordPress Backup#WordPress Data Protection#WordPress Restore#Youtube
0 notes
Text
i was gonna spend my whole day in bed (productively) but i did do last minute coding

it doesnt look like much but i managed to figure out fetching from the database so its actually something!
this is just a temp photo btw lol
#and i did it sever side#which is great cause i was worried about having to write to the database from the client side for like other stuff im gonna do#doing it server side is supposed to avoid what i was worried about (someone figuring out how to manually edit affection lvls)#but we will see#i read a lot of stuff today#about database security so im trying to be careful#but also its a lot so sometimes info doesnt click until days later and im not confident enough to say no mistakes will happen#dont worry tho! im gonna get ppl in here at some point to test the site and make sure to backup often just in case something does happen#its early days so losing data isnt as scary#i prefer to avoid it all together tho but yea#codeblr#webdev
2 notes
·
View notes
Link
#Automation#backup#cloudstorage#collaboration#dataprivacy#database#Docker#filesharing#HTTPS#Install#Linux#networking#Nextcloud#Nextcloudsetup#open-source#reverseproxy#Security#self-hosted#Server#systemadministration
0 notes
Text
How to Protect Your WordPress Database from Cyber Threats
Introduction Your WordPress database is the backbone of your website, storing critical data such as user information, posts, pages, comments, and settings. If compromised, your site could suffer data breaches, downtime, or even total loss of content. Cyber threats like SQL injections, brute force attacks, malware infections, and unauthorized access can put your database at serious…
#brute force attack protection#database backup#database security#limit login attempts#malware scanning#optimize wordpress database#secure wp-config#SQL injection prevention#two-factor authentication#web application firewall#wordpress cybersecurity#wordpress database protection#wordpress firewall#wordpress security
0 notes
Text
why can't sideloading to kobo with calibre be simple and easy an perfect all the time
#oriole text#i love sideloading bc my library is so so so secure and accessible and i can fix formatting issues in the ebook editor#and upload ao3 + adobe digital editions files to the same library as all my other books#but i just lost all of my annotations for metal from heaven#because i had to factory-reset my kobo for the 3rd time since i started using calibre#and for some reason the automatic backup it made yesterday night didn't have any reading progress after jan 28??#was the database already corrupted at that point? it's let me sideload since then so i don't think so?#annotating is more fun and reliable in paperbacks anyways :')#i wish there were windows ereaders so i wouldn't have to guess and choose what's going on under the hood of the kobo#tho i really love my kobo 90% of the time#time to go angrily eat a delicious chocolate chip muffin
0 notes
Text







#DidYouKnow These About Oracle Database Management Services?
Swipe left to explore!
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#didyouknowfacts#knowledgedrop#interestingfacts#factoftheday#learnsomethingneweveryday#mindblown#oracle#database#oracledatabase#databasemanagement#speed#query#flashcache#orackeflashcache#rman#backup#application#applicationservice#didyouknowthat#triviatime#makingitsimple#learnsomethingnew#simplelogicit#simplelogic#makeitsimple
0 notes
Text

Alarm Management Software
#Alarm Management Application#Alarm Management Software#Industrial Alarm Management Application#Industrial Alarm by SMS#OPC Alarm by SMS#OPC alarm notification software#MSSQL Backup Utility#SQL Server Backup#SQL Backup and Restore Utility#MSSQL Data Truncate#Data Backup and Restore#Database Backup#Database Backup and Restore Utility#opc alarms by SMS applications Alarms by SMS#sql alarms by SMS application#Digital Alarms by SMS#digital alarms by SMS application#Analog Alarms by SMS#analog alarms by SMS application#SMS Alarm SCADA#SMS Alarm SCADA system
0 notes
Text
Ransomware: Un rischio in crescita per l'economia globale. Entro il 2031, danni stimati per 265 miliardi di dollari e l'ultimo caso di InfoCert
Un panorama in espansione per i cyberattacchi I danni globali causati dai ransomware potrebbero raggiungere la cifra impressionante di 265 miliardi di dollari entro il 2031, con un impatto economico e sociale senza precedenti.
Un panorama in espansione per i cyberattacchi I danni globali causati dai ransomware potrebbero raggiungere la cifra impressionante di 265 miliardi di dollari entro il 2031, con un impatto economico e sociale senza precedenti. La diffusione di questo tipo di attacco informatico, che compromette i dati di aziende e istituzioni richiedendo riscatti milionari, rappresenta una delle minacce più…
#Alessandria today#attacchi hacker#attacco informatico#attacco ransomware#aziende#backup#costi cybercrime#crittografia#cybercrime#cybersecurity#Danni economici#database clienti#dati compromessi#difesa informatica#economia globale#Formazione personale#Google News#hacking#incidenti di sicurezza#industria digitale#InfoCert#infrastrutture critiche#Investimenti#italianewsmedia.com#minaccia informatica#pagamenti illeciti#perdite operative.#phishing#Pier Carlo Lava#Prevenzione
0 notes
Video
youtube
You Won't Believe How Easy Amazon RDS Backup and Restore Can Be
#youtube#AmazonRDS DataBackup DataRecovery RDSBackup AWSDataProtection CloudRecovery RestoreData DatabaseBackup AWSCloud RDSRestore DataSecurity AWSH#How to Work Automated Backups & Restore Database?How to Database Restore Pint in Time First Way?How to Manage Cross-Region Replication?How t
1 note
·
View note
Text
fibrecrafts: ooh, strings
programming: ugh, strings
#my real life#programming#brought to you by trying to parse a txt database backup into a different format
1 note
·
View note
Text
Deep Dive into Protecting AWS EC2, RDS Instances and VPC
Veeam Backup for Amazon Web Services (Veeam Backup for AWS or VBAWS) protects and facilitates disaster recovery for Amazon Elastic Compute Cloud (EC2), Amazon Relational Database Service (RDS), Amazon DynamoDB, and Amazon Elastic File System (EFS) environments. In this article, we shall deep dive into Protecting AWS EC2 and RDS Instances and VPC (Amazon Virtual Private Cloud) configurations as…

View On WordPress
#Amazon S3 Object Storage#AWS RDS Backups with Veeam#Database Backups#Protecting AWS EC2 and RDS#RDS Automated Backup#Veeam#Veeam Backup and Replication#Veeam Backup for AWS
0 notes
Text
Postgresql database backup
Upback! The effortless database backup and recovery solution. We make it simple and secure to safeguard your data, focusing on essential database backup processes for MySQL, MariaDB, and PostgreSQL. Our easy-to-use management console allows you to perform scheduled database backups without the fuss and all the functionalities!
0 notes
Text
Preventing Ransomware Attacks: Proactive Measures to Shield Your Business
New Post has been published on https://thedigitalinsider.com/preventing-ransomware-attacks-proactive-measures-to-shield-your-business/
Preventing Ransomware Attacks: Proactive Measures to Shield Your Business


All forms of cyber attacks are dangerous to organizations in one way or another. Even small data breaches can lead to time-consuming and expensive disruptions to day-to-day operations.
One of the most destructive forms of cybercrime businesses face is ransomware. These types of attacks are highly sophisticated both in their design and in the way they’re delivered. Even just visiting a website or downloading a compromised file can bring an entire organization to a complete standstill.
Mounting a strong defense against ransomware attacks requires careful planning and a disciplined approach to cyber readiness.
Strong Endpoint Security
Any device that’s used to access your business network or adjacent systems is known as an “endpoint.” While all businesses have multiple endpoints they need to be mindful of, organizations with decentralized teams tend to have significantly more they need to track and protect. This is typically due to remote working employees accessing company assets from personal laptops and mobile devices.
The more endpoints a business needs to manage, the higher the chances that attackers can find hackable points of entry. To mitigate these risks effectively, it’s essential to first identify all the potential access points a business has. Businesses can then use a combination of EDR (Endpoint Detection and Response) solutions and access controls to help reduce the risk of unauthorized individuals posing as legitimate employees.
Having an updated BYOD (Bring Your Own Device) policy in place is also important when improving cybersecurity. These policies outline specific best practices for employees when using their own devices for business-related purposes – whether they’re in the office or working remotely. This can include avoiding the use of public Wi-Fi networks, keeping devices locked when not in use, and keeping security software up-to-date.
Better Password Policies and Multi-Factor Authentication
Whether they know it or not, your employees are the first line of defense when it comes to avoiding ransomware attacks. Poorly configured user credentials and bad password management habits can easily contribute to an employee inadvertently putting an organization at more risk of a security breach than necessary.
While most people like having a fair amount of flexibility when creating a password they can easily remember, it’s important as a business to establish certain best practices that need to be followed. This includes ensuring employees are creating longer and more unique passwords, leveraging MFA (multi-factor authentication) security features, and refreshing their credentials at regular intervals throughout the year.
Data Backup and Recovery
Having regular backups of your databases and systems is one way to increase your operational resilience in the wake of a major cyberattack. In the event your organization is hit with ransomware and your critical data becomes inaccessible, you’ll be able to rely on your backups to help recover your systems. While this process can take some time, it’s a much more reliable alternative to paying a ransom amount.
When planning your backups, there is a 3-2-1 rule you should follow. This rule stipulates that you should:
Have three up-to-date copies of your database
Use two different data storage formats (internal, external, etc.)
Keep at least one copy stored off premises
Following this best practice lowers the likelihood that “all” your backups become compromised and gives you the best chance for recovering your systems successfully.
Network Segmentation and Access Control
One of the most challenging things about ransomware is its ability to spread rapidly to other connected systems. A viable strategy for limiting this ability is to segment your networks, breaking them up into smaller, isolated strings of a wider network.
Network segmentation makes it so that if one system becomes compromised, attackers still won’t have open access to a system. This makes it much harder for malware to spread.
Maintaining strict access control policies is another way you can reduce your attack surface. Access control systems limit the amount of free access that users have in a system at any given time. In these types of systems, the best practice is to ensure that regardless of who someone is, they should still only ever have just enough permissions in place to access the information they need to accomplish their tasks – nothing more, nothing less.
Vulnerability Management and Penetration Testing
To create a safer digital environment for your business, it’s important to regularly scan systems for new vulnerabilities that may have surfaced. While businesses may spend a lot of time putting various security initiatives into place, as the organization grows, these initiatives may not be as effective as they used to be.
However, identifying security gaps across business infrastructures can be incredibly time-consuming for many organizations. Working with penetration testing partners is a great way to fill this gap.
Pentesting services can be invaluable when helping businesses pinpoint precisely where their security systems are failing. By using simulated real-world attacks, penetration testers can help businesses see where their most significant security weaknesses are and prioritize the adjustments that will bring the most value when protecting against ransomware attacks.
Data Security Compliance and Ethical AI Practices
There are various considerations you want to make when implementing new security protocols for your business. Ransomware attacks can do much more than disrupt day-to-day operations. They can also lead to data security compliance issues that can lead to a long list of legal headaches and do irreparable damage to your reputation.
Because of this, it’s important to ensure all critical business data uses active encryption protocols. This essentially makes data inaccessible to anyone not authorized to view it. While this in itself won’t necessarily stop cybercriminals from accessing stolen data, it can help to protect the information from being sold to unauthorized parties. Leveraging data encryption may also already be a requirement for your business depending on the regulatory bodies that govern your industry.
Another thing to consider is that while AI-enabled security solutions are becoming more widely used, there are certain compliance standards that need to be followed when implementing them. Understanding any implications associated with leveraging data-driven technologies will help ensure you’re able to get maximum benefit out of using them without inadvertently breaching data privacy rights.
Keep Your Business Better Protected
Protecting your business from ransomware attacks requires a proactive approach to risk management and prevention. By following the strategies discussed, you’ll be able to lower your susceptibility to an attack while having the right protocols in place if and when you need them.
#access control#ai#approach#assets#Attack surface#attackers#authentication#backup#backups#breach#Business#BYOD#compliance#control systems#credentials#cyber#cyber attacks#cyber readiness#cyberattack#cybercrime#cybercriminals#cybersecurity#data#data backup#Data Breaches#data privacy#data security#data storage#data-driven#databases
0 notes
Text
Azure Backup vs SQL Backup for Large Azure SQL Server VMs
Introduction If you’re running SQL Server on an Azure VM with multi-terabyte databases, choosing the right backup strategy is critical. Should you use Azure Backup or native SQL Server backups? As a data platform consultant, I’ve helped many clients navigate this decision. In this article, I’ll share the key pros and cons of each approach to help you make the best choice for your scenario. By…
View On WordPress
0 notes
Text
7 Benefits Of Using Azure Data Lake ?
Azure Data Lake offers a range of benefits that empower businesses to manage, analyze, and derive insights from large volumes of data. Here are seven key benefits of using Azure Data Lake:
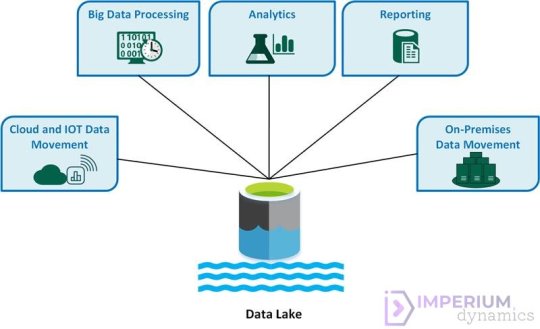
Scalability: Azure Data Lake provides virtually unlimited storage capacity, allowing businesses to store and process massive volumes of structured and unstructured data. With its scalable architecture, Azure Data Lake can accommodate growing data volumes and handle processing demands with ease.
Cost-Effectiveness: Azure Data Lake offers a cost-effective storage solution, enabling businesses to pay only for the storage and processing resources they use. By leveraging features such as pay-as-you-go pricing and storage tiering, businesses can optimize costs and achieve better cost efficiency.
Flexibility: Azure Data Lake supports a wide range of data types, including structured data, semi-structured data, and unstructured data. This flexibility enables businesses to ingest, store, and analyze diverse data sources, including text, images, videos, and IoT data, without the need for data transformation or preprocessing.
Unified Data Platform: Azure Data Lake integrates seamlessly with other Azure services and tools, such as Azure Synapse Analytics, Azure Databricks, and Power BI, creating a unified data platform for end-to-end data analytics and insights. This integration enables businesses to streamline data workflows, improve collaboration, and derive more value from their data assets.
Advanced Analytics: Azure Data Lake provides built-in support for advanced analytics and machine learning, enabling businesses to derive insights and make data-driven decisions. With features such as Azure Data Lake Analytics and Azure Machine Learning, businesses can perform complex data processing, predictive analytics, and AI modeling at scale.
Security and Compliance: Azure Data Lake offers robust security and compliance features to protect sensitive data and ensure regulatory compliance. With features such as encryption, access controls, auditing, and compliance certifications (e.g., GDPR, HIPAA, SOC), businesses can maintain data privacy, integrity, and security across the data lifecycle.
Real-Time Insights: Azure Data Lake supports real-time data processing and analysis, enabling businesses to derive insights and take action on data in near-real-time. By leveraging streaming data processing capabilities with services like Azure Stream Analytics and Azure Event Hubs, businesses can monitor, analyze, and respond to events and trends as they occur.
#marketing#microsoft#machine learning#business#commercial#technology#success#artificial intelligence#crm software#data lake#database#backup#databackup
0 notes
Text
Understanding Data Encryption and Classification for Effective Data Rights Management
Introduction:
Nowadays, data security has become a top priority. As the data is generated and shared more exponentially, the safeguarding of sensitive information has become more challenging while being crucial. Data encryption and classification are the two major aspects of data rights, and they play a leading part in protecting information from involuntary or Best geofence storage service and in compliance with privacy laws.

What is Data Encryption?
Data encryption is like putting your information in a safe, but it is a digital safe. This process entails encoding the plain text into an illegible text referred to as ciphertext with a specific algorithm and key. This procedure makes sure that even if somebody who's not authorized is granted access to the data, they will still not be able to decrypt it without the corresponding decryption key.
Imagine that you want to send a secret message to your friend. Instead of writing the message clearly, you mix it up using some secret code that only you and your friend know. Without the key, any interposition would only yield nonsensical letters.
What is Data Classification?
Data classification is grouping the data according to its level of sensitivity and significance. It also allows organizations to categorize their data holdings and decide which data needs to be protected at what level. Classification is usually done by tagging data with a label that identifies its security requirements or handling process.
Data classification is like putting your stuff into different boxes. All your important documents might go into a folder, another for pictures and one for miscellaneous notes. Every folder is labelled to indicate what paperwork is inside of it and how you should handle it.
Effective Data Rights Management
Encrypting and classifying data are crucial in the context of the formulation of advice on the management of data rights with the objective of attaining maximum data protection and regulatory compliance. Here's how they work together, Here's how they work together:
Data Identification:
This high classification facilitates to define the sensitive data that needs to be encrypted conveniently. By splitting the data into groups according to the application of encryption technologies, information systems can address the shortage of encryption means and distribute the resources in a reasonable way.
Access Control:
Encryption is a safeguard against unpermitted access, and people with classification rights choose who to give access to encoded information. The access controls can build on data classification labels so that only the laid-out clearance users, possessing the proper clearance can unscramble the cipher and access sensitive information.

Conclusion:
The use of data encryption and classification forms part of comprehensive data rights management plans. Encryption works to make Best Database Backup Services only accessible to authorized people. While at the same time, sensitivity labels can be used to classify easy-to-reach data from data that requires more protection. Organizations can provide an appropriate environment for data if they combine these approaches. They can take care of risks, protect confidential information, and be consistent with data privacy regulations.
#Best object storage software#Best Database backup Services#IT Security services#Cyber security company
0 notes