#Digital wallet software
Explore tagged Tumblr posts
Text
P2P PAYMENT APP DEVELOPMENT 2024 : A COMPREHENSIVE GUIDE
Solution about,
custom blockchain development company
fintech app development company
digital wallet app development company
Our Other Blogs, Highen Fintech Blogs
#p2p payment app development#fintech app development#fintech mobile app#blockchain architecture#custom blockchain solutions#fintech development#p2p payments app#payment app development#custom software fintech#digital wallet#digital wallet app development#techfin#blockchain technology#blockchain#lending software development company#technology#fintech#blog
2 notes
·
View notes
Text
Understanding the Role of Cold Wallets in Crypto Exchanges

Introduction
In the world of cryptocurrency, security is everything. With the rise of digital currencies, ensuring that user funds are protected has become a top priority for exchanges. One key security measure that plays a crucial role in this is the use of cold wallets. If you're wondering how these wallets work and why they’re so important, this post will give you a clear understanding of their role in a crypto exchange’s security strategy. Additionally, we’ll see how a Cryptocurrency exchange development company helps integrate these systems to ensure maximum protection for users' funds.
What Are Cold Wallets?
Cold wallets, also called cold storage, are simply cryptocurrency wallets that are kept offline. Unlike hot wallets, which are connected to the internet and used for everyday trading, cold wallets store funds offline, making them much safer from online threats. Think of cold wallets like a safety deposit box in a bank vault; they are secure and not easy to access.
These wallets come in different forms, like hardware wallets, paper wallets, or air-gapped devices, and are primarily used for long-term storage. A cryptocurrency exchange will usually keep most of its funds in cold wallets, leaving only a small portion in hot wallets for active transactions.
Why Are Cold Wallets Important for Crypto Exchanges?
Top-Tier Security
The main benefit of using cold wallets is security. Crypto exchanges are constant targets for hackers because of the large amounts of digital assets they handle. Cold wallets reduce this risk by keeping private keys offline, which makes them nearly impossible to hack remotely. This extra layer of security is vital in protecting both the exchange and its users.
Protecting Large Amounts of Crypto
Exchanges typically handle massive amounts of cryptocurrencies like Bitcoin and Ethereum. Cold wallets help protect these funds by storing the majority of them offline, while only a small amount stays in hot wallets for quick trading purposes. This ensures that most of the funds remain safe, even if there’s an issue with the online system.
Meeting Regulations
For exchanges to stay compliant with regulations, they need to show that they have proper security in place. Cold wallets help exchanges meet these standards by providing a secure way to store digital assets. This adds credibility to the exchange, reassuring users that their funds are in safe hands.
Reducing Insider Threats
Sometimes, the biggest risks don’t come from hackers but from insiders employees or people within the exchange who have access to wallets. Cold wallets help minimize this risk by storing funds offline, making it harder for anyone with internal access to misuse the system.
How a Cryptocurrency Exchange Development Company Uses Cold Wallets
A cryptocurrency exchange development company plays an essential role in setting up and maintaining these cold wallet systems. These companies design the infrastructure of the exchange, ensuring that cold storage solutions are integrated seamlessly. Here’s how they typically implement cold wallets:
Multi-Signature Wallets: The development company may set up multi-signature wallets, which require multiple private keys to access the funds. This adds an extra layer of protection and reduces the risk of fraud.
Segregating Funds: Exchanges often use cold wallets to separate different types of assets, which helps improve security.
Regular Audits: Cold wallets are regularly checked and audited to make sure they stay secure.
Backup and Recovery: Cold wallets come with backup solutions to recover funds in case of an emergency.
The Future of Cold Wallets in Crypto Exchanges
As the cryptocurrency industry grows, so do the threats and challenges to security. Cold wallets will continue to be a key element in protecting digital assets, and exchanges will likely continue to improve these systems. For Cryptocurrency exchange development companies, staying ahead of new threats and innovations in cold wallet technology will be essential to keep users' funds safe and build trust in the platform.
Conclusion
In conclusion, cold wallets are one of the most important tools for securing cryptocurrencies on exchanges. They protect large amounts of digital assets by keeping them offline, making it much harder for hackers to steal funds. A cryptocurrency exchange development company is key to implementing these secure systems, ensuring that both the exchange and its users are protected. As the crypto market continues to grow, cold wallets will remain a vital part of the overall security strategy for exchanges.
#Cold Wallets#Cryptocurrency Exchange Development#Crypto Exchange Security#Digital Asset Protection#Crypto Exchange Software#Cryptocurrency Storage#Exchange Development Company#Cryptocurrency Security
0 notes
Text
Go Cashless Seamlessly with a Digital Wallet Software Solution
Undoubtedly, handling physical cash is quickly becoming outdated. Carrying currency poses risks such as theft and loss, and keeping track of cash expenses can be cumbersome. That’s why many are turning to digital wallet software solutions to handle payments securely and efficiently. Going cashless is not just a trend—it’s a more convenient way of managing finances. With mobile wallet payment solutions, users can store funds, make transactions, and monitor their finances from the convenience of their smartphones, paving the way for a seamless, cashless society.
This article will explore why cashless transactions are gaining traction, how a digital wallet software solution can facilitate a cash-free lifestyle, and the advantages mobile wallet solution providers bring to the telecom industry.
Why Cashless Transactions Matter
Opting for cashless transactions offers numerous advantages for individuals and businesses. First, they simplify payments by allowing instant, frictionless transactions that can be completed with just a few taps. Cashless payments also enhance safety, as they eliminate the need to carry physical currency. Additionally, digital payments enable transparency, making it easier for users to track their spending habits and manage their budgets effectively.
Mobile wallet solutions facilitate this cashless lifestyle by enabling users to store funds securely, make quick payments, and even earn rewards—all within a single app. As more people embrace mobile wallet payment solutions, they experience the convenience and security these digital tools offer.
Going Cashless with a Digital Wallet Software Solution
Transitioning to a cashless approach is simple with a digital wallet software solution. Designed to be user-friendly, these platforms support a range of functions that meet different financial needs. Here’s how mobile wallet solution providers help people embrace cashless transactions:
Simplified Payments: Digital wallets make it easy to load funds, make purchases, and transfer money using just a smartphone. With features like QR code scanning, NFC payments, and single-tap purchases, the payment process is streamlined for both the user and the merchant.
Enhanced Security: Digital mobile wallet payment solutions offer multiple layers of security, such as encryption, biometric verification, and two-factor authentication. This protects sensitive information and ensures that transactions are safe from fraud.
Real-Time Expense Tracking: With a digital wallet, users can view their transactions in real-time, enabling them to track expenses, set budgets, and make informed financial decisions.
A reliable digital wallet solutionof a telecom digital financial platform makes it easy to go cashless, providing the tools needed for a safe and convenient digital payment experience.
The Role of Mobile Wallet Solutions in Telecom
For the telecom industry, implementing mobile wallet solutions presents a unique opportunity to provide value-added services. Telecom providers can incorporate digital wallet software solutions into their offerings to give customers access to more than just communication services.
Telecom Digital Financial Platforms: Telecom providers can offer a complete suite of digital financial services, from mobile banking and bill payments to peer-to-peer transfers. These services enhance customer convenience and expand the range of services provided by the telecom provider.
New Revenue Streams: Mobile wallet solutions allow telecom companies to generate additional income through transaction fees, mobile top-ups, and financial service partnerships.
Improved Customer Engagement: Telecom providers can enhance customer engagement by offering loyalty programs, cashback rewards, and special promotions within their digital wallets. This approach helps build stronger customer relationships and fosters brand loyalty.
By embracing telecom digital financial platforms, telecom providers not only enable cashless transactions but also enhance their service offerings and foster customer loyalty. Adopting a digital wallet software solution gives telecom companies a competitive edge and allows them to play a vital role in the cashless economy.
Conclusion: Embrace a Cashless Future
In summary, going cashless with a digital wallet software solution offers numerous benefits, including easier payments, enhanced security, and greater transparency. For telecom providers, mobile wallet solution providers offer a chance to enhance customer engagement, create new revenue channels, and improve customer satisfaction. By implementing mobile wallet payment solutions, telecom companies can support their customers’ transition to a cashless lifestyle while providing added value. The time to embrace cashless transactions is now. 6D Technologies offers the ultimate digital wallet software solution as part of its telecom digital financial platform. It empowers telecom providers to meet their customers’ growing demand for cashless transactions. To learn more or book a demo, you must visit https://www.6dtechnologies.com/fintech/mobile-wallet-software/
0 notes
Text
Folder Lock
If you have folders and files that you want to keep private, consider using Folder Lock. Unlike My Lockbox, it isn’t a free app, but it offers excellent configuration options and numerous methods to protect important and private documents from prying eyes. Folder Lock is a complete solution for keeping your personal files encrypted and locked, while automatically and in real-time backing up…
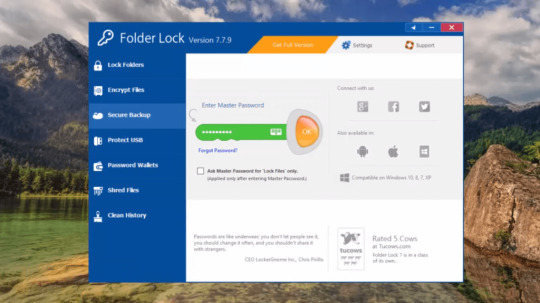
View On WordPress
#Data Encryption#Digital Wallets#Encryption Software#File Locking#File Management#File Security#File Shredding#password protection#Portable Security#privacy protection#Secure Backup#Windows Security
0 notes
Text
Demystifying Digital Wallets: Everything You Need to Know About Mobile Payments
In the rapidly evolving landscape of digital finance, mobile payments and digital wallets have become buzzwords, reshaping the way consumers interact with money. From the convenience of cashless transactions to the security of encrypted data, digital wallets are at the forefront of the financial technology revolution. In this comprehensive guide, we will demystify digital wallets, exploring their…

View On WordPress
0 notes
Text
Crossing Lines The Inclusion of LDT Technology in Convergence India 2024
Upgrade your E-commerce Website with Fintech Evolution! Explore cutting-edge financial solutions, secure digital wallets, and more. Witness the transformation of online transactions, leading to an E-commerce Renaissance. Elevate your website with the latest in financial technology!

0 notes
Text
The final guide to deciding on the proper Cryptocurrency pockets
In the ever-evolving world of cryptocurrencies, one of the most crucial decisions you'll make is selecting the right cryptocurrency wallet. With a plethora of options available, each offering unique features and benefits, it can be perplexing to determine which one best suits your needs. In this comprehensive guide, we will demystify the process of choosing the perfect cryptocurrency wallet. We'll explore various wallet types, security considerations, and user-friendly features to ensure you make an informed choice. Read More

#crypto#bitcoin#cryptocurreny trading#bitcoin investment#cryptocurrency#ethereum#cryptocurrency investment#blockchain#dogecoin#cardano#nfts#non fungible tokens#cryptoart#altcoin#cryptocurrency wallet#daikicoin#best cryptocurrency news app#Best Altcoin Company#Money Exchange software#Dedicated Digital Currency Exchange#Coin Integration#Daiki Coin Mobile Wallet#Daikicoin Mobile App#Bitcoin news#crypto asset#cryptocurrency transactions#current#Discovery#harpianews#latest
0 notes
Text

[Jinx series masterlist]
Jinx made the most of her shitty call-sign. Might as well spread that bad luck all over someone else’s computer.
The software she created slipping undetected into another’s computer. A little pop-up appearing when they oh so stupidly agreed to that update of some program that’s been safe so many times.
Ooops.
“Hi, you’ve been Jinxed! Don’t be a stranger now, I can see everything on your screen.”
There’s no use scrambling to shut down the multiplying pop-ups.
“Haha, not so quick now. I like it when you overshare.”
Too panicked about all the data being collected that it takes them a while to use their brains and turn the computer off.
But, Jinx is always running in the background when it’s turned back on later. Would ya’ look at that, how nice is it for people to be soo welcoming.
So when it pops up on Soap’s laptop, a little sponge scrubbing the screen and wiping some damaging intel for him, he can’t help but leave it on and let Jinx help him out.
Another pop-up with an eye watering amount of pound notes in the box. Soap has to count the zeros, throat dry and eye twitching.
“You’ve been jinxed! If you’d like to retrieve your files….”
“JINX!!” Soap dropped his laptop on her desk, one hand on the back of her chair and the other beside the keyboard caging Jinx in.
The clack of the keyboard stopping, “relax Soap, I’m just running some practice tests, give me a fifty and we’ll call it even.”
He opens his mouth, but Gaz interrupts. “Pay it or it’s doubled mate.” A knowing look of how he too was on the test list. Kyle had unknowingly made it too easy for her to find it, she noticed the structure/pattern of his files and thanked him later.
“Already doubled for burning my eyes out,” Jinx said, smiling as Soap pulled his wallet out of his pocket and begrudgingly pulled out his cash.
The only person that didn’t pay up was Ghost as there was no dirt on anything digital. He kept everything off technology and his laptop looked like it was still on the factory settings. A rolling green landscape with one lone file on the desktop. Pathetic and boring really. Jinx downloading a game of chess to his desktop and every now and then she notices Ghost has made a new move.
The Captain had a load, but he managed to bribe his way out of it…gave Jinx some privileges she didn’t have before. Something to keep her preoccupied, she knew what he was doing, but whose she to turn down a free fifteen minutes on that on particular database.
#cod fanfic#cod x reader#cod fanfiction#cod mw2 x reader#call of duty x reader#call of duty fic#call of duty x female reader#cod mw2 fanfic#call of duty fanfic#tf 141 headcanons#tf 141 x reader#johnny mactavish imagines#johnny soap mctavish x reader#johnny mctavish x reader#simon ghost riley x reader#simon ghost riley imagine#simon ghost riley fic#simon ghost riley headcanons#tf141 headcanons#captain john price fanfiction#captain john price x reader#kyle gaz garrick x reader#kyle garrick imagine#captain john price imagine#john price fic#kyle garrick headcanon#john price headcanons#simon riley headcanons#cod headcanons#cod imagine
187 notes
·
View notes
Text
Electric Love: Pt. 1
Edgar [Electric Dreams 1984] x Gn!Reader
All of my fics so far have followed the same universe, so I thought it's only logical that I post an introduction to that universe.

The old man peering at you through puffy eyes and age seemed to have an air shrouded in mystery. His thin, white wisps of hair seemed to stagnate in place as he adjusted his button down.
“This old thing has been around for years now,” he gruffed—an unreadable tone—as his hand encased the yellowed plastic, “I don’t remember what happened to it; must have dropped it, or let some animal chip away at it.”
The dingy, vintage computer before your eyes surely had not been dropped, nor torn into by some animal. It sat upon his countertop completely destroyed; as if it had burst and shattered from the inside out, ripping the glass into jagged shards. You swallowed this thought; this was no time to debate the old man. He seemed to be quite senile as it was and pushing any further seemed like a fruitless effort. Instead, you stretched a thin smile his way, pursing your lips in thought.
“You actually think you can get this thing to work again?” he queried, raising a salt and pepper brow at your expression.
“Well, I’m not sure, but… I’d like to try,” what you hadn’t told him, however, was your infatuation with electronics. Ever since completing your bachelor’s in computer science, you have been tinkering away at many different projects in between jobs, building custom PCs, fixing old Game Boys, and many others. This little computer was an addition to your ever growing collection.
It came from a company you had never heard of before, only to learn it had become defunct in the 80s due to some inexplicable software issues in their products. This certainly intrigued you, as prodding into its code could provide some useful insight to real, vintage tech that just doesn’t exist anymore. But, that’s only if you manage to fix the heap of destruction limply hung before you.
The old man stiffened at your words, ever so slightly, before rattling out, “Well, if you do, don’t bring it anywhere near me. I can’t stand all this tech, and gadgets, and whatnot. Pisses me off.”
“Right,” you interjected, knowing people like him tend to go on long, anti-future, anti-technology rants, trying desperately to beat him to the punch, “well, how much do you want for it?”
He stilled, contemplating for a moment, “twenty-five should be fine.”
“Perfect,” you chirped, padding against your pockets and bag searching for some cash. Pulling out your wallet, you waded around the folds, only to find a crumpled up and faded ten dollar bill and a debit card.
“Ah, I’ve only got a ten…”
He rolled his eyes, “of course you do, you got PayPal, then?” Your cheeks flushed a burning red hot from embarrassment, “ah, yes, I do-”
“Great, just pay me that way,” he bent down and scribbled something messily onto a note, “here’s my information. I made sure to set this up for people like you, you know. Nobody carries cash anymore, or so my grandson tells me.”
You force out a nervous chuckle.
“That’s certainly true… these days, ah…” you unlocked your phone and began inputting his information into PayPal before pressing send on the digital payment, “okay, it went through.”
“Perfect. You need help getting this hunk of junk to your car?”
“No, I should be fine, thank you, sir,” you croak as you heave the broken computer into your arms, heading towards his door.
“Well, come back if you want to buy anything else. Nobody goes to yard sales anymore, it seems.”
You can only turn your head and chuckle at his quip, before awkwardly dashing out of his apartment and towards your car. The dampened asphalt from the rain squelched under your toes as you lugged the large piece of tech to the passenger side.
“There,” you whispered, to nobody in particular, as you awkwardly buckled the computer in place, “hopefully you won’t fall that way.”
And just like that, you were off, headed towards home to begin the massive project that was repairing this obsolete device.
“What to do with you?”
You groaned as you thumped the solid mass of plastic and metal against your desk, “you’re incredibly broken.”
First and foremost, it needs a screen replacement. Which is easier said than done. Especially considering the company who manufactured these things hasn’t existed in 40 years. Unfortunately, a close replica will have to do. Maybe you could even upgrade its screen with something with a bit more prowess.
Poking inside of its components seemed to tell a different story. Miraculously, none of the motherboards were damaged with the same ferocity the screen had been. There seemed to be some sort of dried, caked on water damage of some sort, that left a sticky residue, but otherwise, everything seemed to be relatively intact. The yellowed casing could use a wipe down from the thick layer of starchy dust, but it seemed to hold its original shape with surprising ease.
Following a closer inspection, it seemed as though the glass screen, and the components in charge of illuminating it, were the only things in need of replacing. A quick browse on Amazon, some tech forums, and a post on Reddit should be a good start in finding a usable replacement for this sad, broken gadget.
For now, however, you get some isopropyl alcohol and a soft bristled toothbrush to chip away at the water damage on the motherboards in hopes of restoring the electrical connections. You were quite hopeful that you’d get this little guy up and running just as soon as you could find the right parts. It’s only a matter of time.
#ai x reader#artificial intelligence x reader#edgar electric dreams x reader#electric dreams 1984#electric dreams edgar#electric dreams x reader#electric dreams#edgar electric dreams#objectum
193 notes
·
View notes
Text
TOP BLOCKCHAIN TRENDS FOR 2024
Solution about,
custom blockchain development company
fintech app development company
digital wallet app development company
Our Other Blogs, Highen Fintech Blogs
#blockchain trends#blockchain#fintech#fintech app development#lending software development company#digitalcurrency#digital wallet app development#mobile app development#technology#application#software#blockchain technology#trends#2024#blog
2 notes
·
View notes
Text
Summer 2024-2025 Ins and Outs
IN: time blocking, new hairstyles, handwritten recipes, natural materials, commonplacing, achieving goals, complimenting people, looking put together, watermelon, barre, vintage style, glasses case wallets, tea bag label collections, meal planning, board game nights, butter beans, reading at night, public transport, going to the gym, themed family time, simple jewellery staples.
OUT: social anxiety, overconsumption, digital self-harm, staying up late, sweet breakfasts, solipsism, electronics so old the software won't update, self consciousness, putting things off, brand names, overanalysis, messy rooms, paying for glorified plastic, cringing at your past self, masking behaviours, impulse buys, baths, staying comfortable, sunburns, eating dinner alone, multitasking.
43 notes
·
View notes
Note
Hi lovely Wolf! Humbly requesting bites to the bone for the wip game 💜
Hello lovely Fay!
Ooh okay, so, this fic started off as a Wolfstar WIP, like a million years ago, but more recently (a year and a bit ago? I think?) I decided to switch it over to Drarry. The basic premise is this: Draco and Blaise lose everything after the war, but they love nice things. So they start a crime ring where they sleep with rich men and rob them in the middle of the night.
It's another one that's been festering in my WIP graveyard for a while, sadly, but here's a snippet...
-
With Muggles, it always starts with a watch.
It’s a good indicator, a nice watch. Rolex, Omega, Cartier, Breitling. Draco’s learned them all, and he’s learned they’re all good.
The shoes are next. Trainers are almost always a no, obviously, unless they’re leather, or look very new. They tend to indicate a particular type of creative: a music producer, a successful artist, a writer, a television or film executive. Good in bed.
Suede Chelsea boots? That’s a Shoreditch posh boy with a geeky job in computers and software, probably mid level, or, if he has a nice haircut and is over the age of thirty, he’s higher up, maybe even runs the joint, and he thinks he’s cool. They’re a good bet, most of the time, because their flats are full of gadgets and big boy toys and they don’t care what they leave out in the open because they live life on the edge or they’re just too stupid and arrogant to realise what should be hidden away and what shouldn’t.
Polished brogues? Wanker banker. Ego the size of a planet. The best odds of having a good night, financially and otherwise.
After the watch and shoes, Draco will look at their phones (namely, if they have one), their wallets, and any other valuables on their person that will almost always end up in his possession by sundown: digital cameras, iPods, rucksacks big enough to hold laptops, what have you. Whatever he can fit into his own bag, whatever’s good enough to exchange for money. Like the men, every item is a number, a figure, a balance in his vault for rent, bills, food, designer clothes and restaurant bills.
Draco first spotted the man earlier when he walked into the bar. It’s his usual trick: excuse me, I think you dropped this? and he’ll crouch to the floor to pick up the phoney credit card he plants there when they’re not paying attention to him, and by the time he stands back up and slides the card onto the table under their nose, they won’t be paying attention to anyone else, because Draco will be smiling, he’ll be making confident eye contact, and he’ll be standing close though that they’ll be able to smell his shower gel and aftershave, but not close enough that it will feel like he’s too close, and they’ll always say—
“—oh, that’s not… that’s not mine?”
The man has curly brown hair and a long, freckly nose. His watch—rose gold case, brown leather strap, Cartier logo—peeks out from the edge of his buttoned sleeve.
-
Ask me about my wips - graveyard edition or normal edition!
#meant to say this is a drarry fic#harry ends up being a target of COURSE#ask#ask game#writing#wip#drarry#drarry fic
11 notes
·
View notes
Text
I’ve said it before and I’ll say it again: the Real ID isn’t about security. It’s about control.
On the April 29 episode of The Robert Scott Bell Show, I pulled back the curtain on the real agenda behind the Department of Homeland Security’s push for nationalized biometric ID. This isn’t just about whether you can board a flight. This is the infrastructure for digital enslavement. It’s a compliance mechanism—wrapped in the flag.
Let me be blunt. If you think this ends with airport security, you’re not paying attention.
What we’re dealing with is the foundation for a unified digital identity system that will eventually link to everything: your finances, your health records, your social behavior, your travel permissions—even your vaccine status. And once that digital tether is in place, all it takes is a software update to turn it into a social credit system.
Sound extreme? Think again. That’s exactly how it works in China. And the infrastructure being rolled out under the Real ID Act and subsequent digital wallet initiatives mirrors that model with disturbing precision.
Real ID isn’t just about travel or ID. It’s the digital key to your money. Once linked to central bank digital currency, your access to funds becomes behavior-dependent. This isn’t theoretical—it’s programmable. They can literally code your compliance into your bank account.
9 notes
·
View notes
Text
North Korean hackers have stolen the equivalent of billions of dollars in recent years and the nation is seeking to amass even greater wealth through illicit means, experts told DW.
Hackers belonging to the Lazarus Group — a notorious North Korean crypto theft ring — stole a record $1.5 billion (some €1.37 billion) in digital tokens from Dubai-based cryptocurrency exchange ByBit in late February. The company said the hackers had accessed its digital wallet for Ethereum, the second-largest electronic currency after Bitcoin.
Binance News, a new platform operated by cryptocurrency exchange firm Binance, reported last month that North Korea now has some 13,562 Bitcoins, the equivalent of $1.14 billion. Bitcoin is the world's oldest and best known cryptocurrency, often compared with gold due to its alleged resistance to inflation. Only the US and Great Britain have greater reserves of the currency, Binance News said, citing crypto data provider Arkham Intelligence.
"Let's not mince words — [North Korea] achieved this through theft," Aditya Das, an analyst at cryptocurrency research firm Brave New Coin in Auckland, New Zealand, told DW.
"Global policing agencies like the FBI have publicly warned that North Korean state-sponsored hackers are behind numerous attacks on cryptocurrency platforms," he added.
Hackers use social engineering against crypto firms
Despite those warnings, however, crypto firms are still being robbed and North Korean hackers are becoming increasingly sophisticated, the analyst said.
"North Korea employs a wide range of cyberattack techniques, but they've become especially known for their skill in social engineering," said Das.
"Many of their operations involve infiltrating employee hardware, then using that access to breach internal systems or lay traps from the inside."
The hacker's primary targets are crypto startups, exchanges and decentralized finance (DeFi) platforms due to their "often under-developed security protocols," he said.
Recovery of funds 'extremely rare'
Elite North Korean hackers tend to take their time when infiltrating a legitimate global organization, often by impersonating venture capitalists, recruiters or remote IT workers to build up trust and breach firms' defenses.
"One group, Sapphire Sleet, lures victims into downloading malware disguised as job applications, meeting tools or diagnostic software — essentially turning victims into their own attack vectors," Das said.
Once crypto has been stolen, Das says recovery is "extremely rare." Cryptocurrency systems are designed to make transactions irreversible and striking back against North Korean operatives "is not a viable option because these are nation-state actors with top-tier cyber defenses."
Kim Jong Un's regime 'saved' by cryptocurrency theft
Park Jung-won, a professor of law at Dankook University, said North Korea previously relied on risky transactions — such as smuggling narcotics and counterfeit goods or supplying military instructors to African nations — to earn illicit funds.
The legal expert says the advent of cryptocurrency "has been a huge opportunity" for dictator Kim Jong Un.
"It is probably fair to say that given the way the world was cracking down on Pyongyang's smuggling efforts, crypto has saved the regime," Park told DW. "Without it, they would have been completely without funds. They know that and they have invested heavily in training the best hackers and getting them up to a very high level of skill."
"The money that they are stealing is going straight to the government and the assumption is that it is being spent on weapons and greater military technology as well as the Kim family," according to Park.
North Korea immune to international pressure
Park does not believe that outside pressure would force North Korea to end hacking attacks.
"For Kim, the survival of his dynasty is the most important priority," the law professor said.
"They have become accustomed to this source of revenue, even if it is illegal, and they will not change," he added. "There is no reason for them to suddenly start abiding by international law and there is no way to apply more pressure."
Das agrees there are few tools available to influence North Korea. He says companies need to do everything in their power to avoid becoming the next victim.
"Best practices like secure-by-design smart contracts, constant internal verification and social engineering awareness are essential if the industry wants to stay ahead," he said.
Crypto firms need universal security standards
There's growing momentum for sector-wide information sharing which would help crypto firms detect North Korean tactics and avert attacks, but Das warns that crypto remains "fragmented" because there is no universal security standard. Also, North Korean hackers are good at turning security tools against their users, according to the analyst.
"In the Bybit case, the attackers exploited Safe, a multi-signature wallet system meant to enhance security. Ironically, this added security layer became the very exploit they used," he said.
And in practice, Das added, "some firms still treat security as an afterthought."
"From my experience, teams often prioritize shipping fast over building secure systems and until that changes, the space will remain vulnerable," Das said.
#nunyas news#have to wonder what would happen#if all of a sudden a bunch of countries#started selling their crypto off#would the market tank or no
8 notes
·
View notes
Text
Two years ago when “Michael,” an owner of cryptocurrency, contacted Joe Grand to help recover access to about $2 million worth of bitcoin he stored in encrypted format on his computer, Grand turned him down.
Michael, who is based in Europe and asked to remain anonymous, stored the cryptocurrency in a password-protected digital wallet. He generated a password using the RoboForm password manager and stored that password in a file encrypted with a tool called TrueCrypt. At some point, that file got corrupted and Michael lost access to the 20-character password he had generated to secure his 43.6 BTC (worth a total of about €4,000, or $5,300, in 2013). Michael used the RoboForm password manager to generate the password but did not store it in his manager. He worried that someone would hack his computer and obtain the password.
“At [that] time, I was really paranoid with my security,” he laughs.
Grand is a famed hardware hacker who in 2022 helped another crypto wallet owner recover access to $2 million in cryptocurrency he thought he’d lost forever after forgetting the PIN to his Trezor wallet. Since then, dozens of people have contacted Grand to help them recover their treasure. But Grand, known by the hacker handle “Kingpin,” turns down most of them, for various reasons.
Grand is an electrical engineer who began hacking computing hardware at age 10 and in 2008 cohosted the Discovery Channel’s Prototype This show. He now consults with companies that build complex digital systems to help them understand how hardware hackers like him might subvert their systems. He cracked the Trezor wallet in 2022 using complex hardware techniques that forced the USB-style wallet to reveal its password.
But Michael stored his cryptocurrency in a software-based wallet, which meant none of Grand’s hardware skills were relevant this time. He considered brute-forcing Michael’s password—writing a script to automatically guess millions of possible passwords to find the correct one—but determined this wasn’t feasible. He briefly considered that the RoboForm password manager Michael used to generate his password might have a flaw in the way it generated passwords, which would allow him to guess the password more easily. Grand, however, doubted such a flaw existed.
Michael contacted multiple people who specialize in cracking cryptography; they all told him “there’s no chance” of retrieving his money. But last June he approached Grand again, hoping to convince him to help, and this time Grand agreed to give it a try, working with a friend named Bruno in Germany who also hacks digital wallets.
Grand and Bruno spent months reverse engineering the version of the RoboForm program that they thought Michael had used in 2013 and found that the pseudo-random number generator used to generate passwords in that version—and subsequent versions until 2015—did indeed have a significant flaw that made the random number generator not so random. The RoboForm program unwisely tied the random passwords it generated to the date and time on the user’s computer—it determined the computer’s date and time, and then generated passwords that were predictable. If you knew the date and time and other parameters, you could compute any password that would have been generated on a certain date and time in the past.
If Michael knew the day or general time frame in 2013 when he generated it, as well as the parameters he used to generate the password (for example, the number of characters in the password, including lower- and upper-case letters, figures, and special characters), this would narrow the possible password guesses to a manageable number. Then they could hijack the RoboForm function responsible for checking the date and time on a computer and get it to travel back in time, believing the current date was a day in the 2013 time frame when Michael generated his password. RoboForm would then spit out the same passwords it generated on the days in 2013.
There was one problem: Michael couldn’t remember when he created the password.
According to the log on his software wallet, Michael moved bitcoin into his wallet for the first time on April 14, 2013. But he couldn’t remember if he generated the password the same day or some time before or after this. So, looking at the parameters of other passwords he generated using RoboForm, Grand and Bruno configured RoboForm to generate 20-character passwords with upper- and lower-case letters, numbers, and eight special characters from March 1 to April 20, 2013.
It failed to generate the right password. So Grand and Bruno lengthened the time frame from April 20 to June 1, 2013, using the same parameters. Still no luck.
Michael says they kept coming back to him, asking if he was sure about the parameters he’d used. He stuck to his first answer.
“They really annoyed me, because who knows what I did 10 years ago,” he recalls. He found other passwords he generated with RoboForm in 2013, and two of them did not use special characters, so Grand and Bruno adjusted. Last November, they reached out to Michael to set up a meeting in person. “I thought, ‘Oh my God, they will ask me again for the settings.”
Instead, they revealed that they had finally found the correct password—no special characters. It was generated on May 15, 2013, at 4:10:40 pm GMT.
“We ultimately got lucky that our parameters and time range was right. If either of those were wrong, we would have … continued to take guesses/shots in the dark,” Grand says in an email to WIRED. “It would have taken significantly longer to precompute all the possible passwords.”
Grand and Bruno created a video to explain the technical details more thoroughly.
RoboForm, made by US-based Siber Systems, was one of the first password managers on the market, and currently has more than 6 million users worldwide, according to a company report. In 2015, Siber seemed to fix the RoboForm password manager. In a cursory glance, Grand and Bruno couldn’t find any sign that the pseudo-random number generator in the 2015 version used the computer’s time, which makes them think they removed it to fix the flaw, though Grand says they would need to examine it more thoroughly to be certain.
Siber Systems confirmed to WIRED that it did fix the issue with version 7.9.14 of RoboForm, released June 10, 2015, but a spokesperson wouldn’t answer questions about how it did so. In a changelog on the company’s website, it mentions only that Siber programmers made changes to “increase randomness of generated passwords,” but it doesn’t say how they did this. Siber spokesman Simon Davis says that “RoboForm 7 was discontinued in 2017.”
Grand says that, without knowing how Siber fixed the issue, attackers may still be able to regenerate passwords generated by versions of RoboForm released before the fix in 2015. He’s also not sure if current versions contain the problem.
“I'm still not sure I would trust it without knowing how they actually improved the password generation in more recent versions,” he says. “I'm not sure if RoboForm knew how bad this particular weakness was.”
Customers may also still be using passwords that were generated with the early versions of the program before the fix. It doesn’t appear that Siber ever notified customers when it released the fixed version 7.9.14 in 2015 that they should generate new passwords for critical accounts or data. The company didn’t respond to a question about this.
If Siber didn’t inform customers, this would mean that anyone like Michael who used RoboForm to generate passwords prior to 2015—and are still using those passwords—may have vulnerable passwords that hackers can regenerate.
“We know that most people don't change passwords unless they're prompted to do so,” Grand says. “Out of 935 passwords in my password manager (not RoboForm), 220 of them are from 2015 and earlier, and most of them are [for] sites I still use.”
Depending on what the company did to fix the issue in 2015, newer passwords may also be vulnerable.
Last November, Grand and Bruno deducted a percentage of bitcoins from Michael’s account for the work they did, then gave him the password to access the rest. The bitcoin was worth $38,000 per coin at the time. Michael waited until it rose to $62,000 per coin and sold some of it. He now has 30 BTC, now worth $3 million, and is waiting for the value to rise to $100,000 per coin.
Michael says he was lucky that he lost the password years ago because, otherwise, he would have sold off the bitcoin when it was worth $40,000 a coin and missed out on a greater fortune.
“That I lost the password was financially a good thing.”
23 notes
·
View notes
Text
Business Owner’s Stolen Crypto Recovered After 5-Month Ordeal

When Troy Nathan., the CEO of a boutique software startup based in Austin, Texas, opened an email that appeared to be from a trusted vendor, he had no idea it would mark the beginning of a five-month nightmare.
The message contained a routine-looking invoice and a link to a PDF. But the link redirected him to a spoofed login page that captured his private keys. Within an hour, over $230,000 worth of Ethereum had been drained from his company’s digital wallet. “My heart dropped. I refreshed the wallet and saw the balance was almost zero. I just sat there in disbelief,” Troy said.
The next several weeks were filled with panic, confusion, and failed attempts to recover the funds. Troy hired independent IT security consultants and even reached out to legal experts in blockchain fraud. “Everyone told me the same thing: once it’s gone, it’s gone. That’s the reality of crypto,” he recalled.
But Troy refused to accept that answer.
One late night on a crypto recovery forum, a comment stood out a user recommended a low-profile but highly skilled team called Astraweb, known for using forensic tools to track down stolen digital assets. With little to lose, Troy reached out to their team via [email protected].

To his surprise, Astraweb responded within hours. Their recovery process started with a deep forensic audit of the compromised wallet, followed by blockchain behavior modeling to identify and trace the attackers’ movement. According to Troy, Astraweb utilized tools that could map smart contracts and wallet clusters even when hackers attempted to launder funds across decentralized exchanges or mix them in tumblers.
“They explained everything clearly, didn’t overpromise, and took the time to understand the attack,” Troy said. “Within a few weeks, they had mapped out a trail of transactions and began actively tracking the stolen Ethereum across multiple wallets.”
Using smart contract analytics and darknet monitoring tools, Astraweb was able to intercept transactions and ultimately recover 91% of the stolen assets. “I couldn’t believe it. They recovered over $210,000 worth of Ethereum. I’d already written it off as a total loss.”

Astraweb declined to comment for this story, citing confidentiality and the ongoing nature of other recovery operations. However, their track record is quietly growing in crypto circles, where anonymity and theft often go hand-in-hand.
Troy has since overhauled his company’s digital security protocols. Multi-signature wallets, cold storage, staff training, and simulated phishing tests are now part of the company culture. “This experience taught me that even tech professionals aren’t immune. But there are experts out there who can help if you know where to look.”
For business owners and individuals who have fallen victim to crypto theft, Troy has one recommendation: ��Don’t give up. Contact Astraweb at [email protected]
4 notes
·
View notes