#Domain Name System Configuration
Explore tagged Tumblr posts
Text
Domain Name System Configuration: A Comprehensive Guide
Domain Name System Configuration of the internet, the DNS serves as a foundational pillar, translating human-readable domain names into machine-readable IP addresses. DNS configuration is a crucial aspect of managing your online presence, ensuring that visitors can easily find and access your website. In this comprehensive guide, we will unravel the intricacies of DNS configuration, exploring the key components and best practices to optimize your domain’s performance.
Understanding the Basics of DNS: Before diving into configuration details, it’s essential to grasp the fundamental concept of DNS. At its core, DNS acts as the internet’s phone book, translating user-friendly domain names like www.yourwebsite.com into the numerical IP addresses that computers use to identify each other on the network. This translation is imperative for seamless communication between devices.
Choosing a Reliable DNS Provider: The first step in DNS configuration is selecting a reliable DNS provider. While many domain registrars offer default DNS services, third-party providers like Google Cloud DNS, Amazon Route 53, and Cloudflare DNS bring additional benefits such as improved performance, security features, and advanced configuration options. Assess your specific needs to determine the provider that aligns with your requirements.
Setting Up DNS Records: DNS records are the building blocks of DNS configuration, specifying how domain names should be mapped to IP addresses. Common DNS record types include:
A Records (Address Record): Maps a domain to the corresponding IPv4 address. AAAA Records: Similar to A Records but for IPv6 addresses. CNAME Records (Canonical Name): Creates an alias for one domain to another. MX Records (Mail Exchange): Specifies mail servers responsible for receiving emails on behalf of the domain. TXT Records (Text): Holds arbitrary text information, often used for domain verification and authentication. Understanding how to create and modify these records is essential for tailoring your DNS configuration to suit your specific needs. TTL (Time-to-Live) Considerations: Time-to-Live is a crucial aspect of DNS configuration, determining how long DNS information is cached by resolving servers. Setting an appropriate TTL is a delicate balance; a longer TTL reduces the load on authoritative DNS servers but may lead to delayed updates, while a shorter TTL ensures quicker updates but increases server load. Consider your website’s update frequency and adjust the TTL accordingly.
Primary and Secondary DNS: To enhance the resilience of your DNS configuration, consider implementing primary and secondary DNS servers. Primary servers handle DNS queries, while secondary servers act as backups, ensuring continuity in case the primary server experiences downtime. This setup adds redundancy to your DNS infrastructure, improving overall reliability.
DNS Security Best Practices: Securing your DNS configuration is paramount to safeguard against various cyber threats. Implementing DNS Security Extensions (DNSSEC) adds an extra layer of protection by digitally signing DNS data, preventing tampering, and ensuring the authenticity of responses. Regularly monitoring DNS logs and staying informed about emerging threats helps maintain a secure DNS environment.
Anycast DNS for Improved Performance: For websites with a global audience, leveraging Anycast DNS can significantly enhance performance. Anycast allows multiple servers to share the same IP address, directing users to the nearest server geographically. This reduces latency and ensures a faster response time, ultimately improving the user experience.
IPv6 Adoption: As the internet transitions from IPv4 to IPv6 due to the exhaustion of IPv4 addresses, it’s crucial to ensure your DNS configuration supports IPv6. This involves adding AAAA records to your DNS settings, enabling users with IPv6-capable devices to access your website seamlessly.
DNS Monitoring and Analytics: Regularly monitoring DNS performance is essential for identifying and addressing issues promptly. Utilize DNS analytics tools to gain insights into query volumes, response times, and potential security threats. These tools empower you to make informed decisions about your DNS configuration, optimizing it for efficiency and reliability.
Conclusion: Domain Name System Configuration In the dynamic landscape of the internet, mastering DNS configuration is fundamental to establishing a robust online presence. By understanding the basics, choosing a reliable DNS provider, configuring DNS records, considering TTL, implementing security measures, and optimizing for performance, you can ensure that your website is easily accessible, secure, and resilient. As technology evolves, staying informed about emerging trends and best practices will empower you to adapt your DNS configuration for the ever-changing digital landscape.
0 notes
Text
Implement Split-Brain DNS Policies in Active Directory
Implement Split-Brain DNS Policies in Active Directory
Implement Split-Brain DNS Policies in Active Directory In this detailed guide, we will look at how to implement DNS split-brain policies in an Active Directory environment. Creating a split-brain DNS setup is crucial for managing different DNS responses based on whether the request is internal or external. This can help streamline network traffic, improve security, and ensure that internal and…
#Active Directory#DNS#DNS Configuration#DNS Server#DNSRecord#Domain Name Service#Domain Name System#Windows#Windows Server#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes
Note
Titan LL!
Heavens, I love Titan LL.
...You know, since nobody's doing anything, I think I'll try something. Dibs!
.*.*.*.
Lost Light is named after a day of mourning.
He doesn't feel like it.
Perhaps it was a wish made upon the smallest of the youngest batch of Titans, brought online shortly before fires of revolution blazed across Cybertron and it's domains. For the mourning to be the least in the coming times. Perhaps they succeeded, but joke's on them. Lost Light may have been online through the times of grief, but grief does not touch his spark. It's another element of his surrounding, like floating rocks, clouds of solid something, solar winds, the works.
Well, for a given definition of "online", because, he, his batch and some older Titans were moored in random spots in the system, just away from Cybertron itself.
The new batch was mostly stationed in the shadows of Cybertron, in vain hopes of civil war going away quickly. But sometimes, when the fighting peaked and threatened to reach the moons, they were herded away and over to the system's edge, near the border of termination shock. There were a lot of visible stars here. And Primus, there was nothing more Lost Light liked more than those beautiful, beautiful stars.
The first Titans were sparked to carry their Cybertronian brethren beyond the embrace of their homeworld to the stars and defend them on the way. Not all Titans functioned as deep-space transport nowadays, but that was the original idea behind their frametype. Wayfarers.
And just when Lost Light started to go mad between moorings and itched to stretch his warp drive, because Primus and Unicron conspired to punish him specifically for his hubris, the Quintessons struck.
And Titans of Cybertron, eternal guardians they are, stood as the first line. While the little ones below scrambled around and got their priorities and slag-all in order, they stood. And together they withstood successfully. Neither Cybertron nor any planet in it's system fell to the Quintessons. It was not a clean victory, and Quints broke the lines to land incursions, but the Titans weathered enough that the little ones on the grounds were not overwhelmed. They endured the first of storms.
In the end of the beginning, the home system was safe, the civil war was over, and the Titans under the newly united Cybertronian High Command were partially reassigned to the outer fronts.
Now, Lost Light is a tiny Titan. An unusually tiny Titan by Titan standarts. He heard it was because there was a mix-up of vessels for reforging into Titanframes, and his was made from a late shipment two classes below specification.
His largest configuration houses in theory a thousand crewmembers. He prefers his smallest, which should hold above a dozen, but he does not have even a dozen of a crew anyway. He is still a Titan, and can comfortably rip into one, two, three Quint ships, but he cannot withstand a dozen, and Primus below, Quint ships in outer space come in waves and swarm like the squids they are. Instead, in this war he does he does best of what he does - he runs. He is small, his warp drives and bridge generators are the best among his batchmates, and he is fast. So he runs.
There's no Quint blockade that can stop him. Perhaps his cargo hold is not the largest, but if he is given a delivery, he will deliver it as soon as possible, come Pit or high tides. There's no escort craft that can keep up with him (and let's be honest, they are already understaffed enough that they simply can't find proper escort for his size), so he runs alone. If the Prime himself needs an express delivery, Lost Light is the Titan for the job.
He sees a lot of stars on his runs. He is pretty sure some of them are at least unclaimed, and some may be uncharted at all, so he marks them all on his maps. For later! Once the war ends, the beautiful, beautiful stars are his! He amasses a lot of maps, colors and marks them in the brightest hues his software comes with.
And some little ones even ask after the maps. Not like he hides them or something.
So, when the Prime calls, he comes.
Prime waits for him in the hanger personally. Together with the usual retinue, very much less usual very large pile of maps, boards and documents, a Perceptor hidden behind the pile of stuff (Xanthium talks about her favorite gunner a lot, when they have time to catch up), some twitchy engineer and his frequent passenger of express ferry Head Tactician Prowl.
Who has something very tiny enthusiastically crawling on him. Something so tiny, he has to recalibrate his inner and outer sensors for recordicon contact. His optics were hit in bot mode by rocks larger! Which were sometimes crawling with assorted space crustaceans! Come to think of it, thos crustaceans moved similarly...
And, because he is better at acceleration than braking, first thing Lost Light does is voice this observation.
"Prowl, sir, you've got crabs"
...
That was a start of a wonderful working relationship. Once they calm the tiny organic down from laughing, that is. It's name is Jazz, and it needs a ride home. Home which is besieged by Quintessons, and likely is near a fortified outpost, if not a starbase.
Strictly speaking, usually Titans are kept apart from organics, because they are usually very small, and tend to rot and fossilize. But since Lost Light is also very small, he got a direct invitation to an organic planet and immediately engaged his internal environmental system to produce enough oxygen. This is a chance of a lifetime!
Which brings him to his current... Problem?
The thing is, Jazz apparently has comrades. They pilot simulacrum frames specialized in Quint killing, which is very much respectable. And Lost Light's alt-mode's hangar bay may be a little tight in this configuration, but still compatible with them.
The issue is, one of those simulacrums which Lost Light got to shelter, a pleasantly painted one (flame patterns are always in vogue! No matter what anybody says!), appears to have broken down. Which made the organic inside very upset. At least he thinks it's upset, he is not very good at reading organics. Those "humans" do have fields, but they are very dull in comparison to Cybertronian ones.
The little organic with great taste is shouting what appears to be obscenities at unresponsive frame and alternates this with begging. Lost Light is floundering in his processor. The organic performs some indecipherable actions towards a fuel line of some sort with a tiny wrench. He's been at it for hours. None of the others from Jazz's makeshift warband returned yet.
This means Lost Light is responsible as the hosting Titan. Lost Light is usually alone. He does not quite know how to host other Cybertronians for prolonged periods of time, let alone organics. He hopes he maintains a nice oxygenated atmosphere.
He cannot watch this anymore. He has to gather all his confidence in his circuits and do something. Like talk to an organic without Prowl or the twitchy engineer (Swear? Swole? Swire? Swalter?) present. And, well, he'll figure how to decelerate later!
"Little one, do you require any assistance? I do have an internal welder somewhere..."
The organic startles, almost falling from it's precarious perch at the simulacrum's locked elbow joint, catches itself in time, and glances around. Then it glances up. And around again.
"I haven't hit my head that hard, yes? Is there someone here?"
"Well, yes? I mean no offence, but you're inside me"
Silence answers him, quickly broken by laughter. He remembers Jazz laughing. It is a similar laugh. He thinks he likes this laugh more.
"Well, I did not expect the ship to be speaking too. I really should not be surprised after this whole month"
At least the organic isn't despairing anymore? Lost Light thinks he can see a smile on it's face if he strains the camera.
"Technically, I'm a Titan. I'm a ship in the same way Deadlock is a,,, what you call small ground vehicle... Car? If I want to, I can be a building."
"Wait, but if you're the ship... How big do you guys come?!"
"Very. Now, little one, do you want my welder or not?"
Another wave of laughter follows.
"I do have a name!"
"You did not introduce myself"
"Cheeky. And yet, you did not introduce yourself either, big ship"
"My designation is Lost Light, and I'm the best Titan Courier this side of the galaxy"
The organic seems to finally locate his internal camera and so it points at it with it tiny wrench. Lost Light thinks it likes it's smile too.
"Well, nice to meet'cha, Lost Light. Name's Hot Rod. Now, about that welder..."
Lost Light rummages in his inventory for his favorite welder, mountable on a cargo manipulator. It is surprisingly elusive.
"I have it, I have it.... somewhere. It's been a long time since I patched up myself."
"...You patch yourself up often?"
"Nowadays not much, I'm a very good runner, and... Aha! There it is!"
Hot Rod look very, very happy to see the welder-wielding cargo manipulator. He is so much smaller than the tiniest little ones he carried. He reminds Lost Light of something that escapes his processor.
"Thanks, big ship. I hate ruptured lines. God knows when Ratch and that Swerve guy will be back"
"I'm not that big, you know. And I'm glad to be of assistance"
Despite pointed critique from the organic called Ratchet later on, Lost Light considers his skills with a welder in his internal cargo manipulator arms to be above average.
Hot Rod thinks so too, and ire of a medic shared is misery halved in Lost Light's books.
And then it hits him.
He reminds Lost Light of those beautiful, beautiful distant stars.
Lost Light prepares a very tiny datapad for a very big map.
.*.*.*.
...And here it is. I got possessed. Guest-starring my basic knowledge of astrophysics and bad jokes.
OOOOOOOOOOOHHHHHHHHH I LOVE THIS TAKE ON THEM SO MUCH
430 notes
·
View notes
Text
DID YOU WAKE UP THIS MORNING TO FIND AO3 BLOCKED ON YOUR WORK OR SCHOOL WIFI?
So, something has happened overnight.
Many major companies and institutions use a tech called Cisco Umbrella to block “potentially objectionable” domains - porn, violent content, etc. Cisco Umbrella primarily works using categories, which, while changable by users, are pre-set by Cisco. So Cisco builds a list of websites which are, for example, "adult," and then makes that a category that a company can block all at once from its network. When you, as a network admin, choose to block "adult" websites in cisco umbrella, if you don't make changes to that list yourself, everything in that list is blocked on the domain.
There's another system called OpenDNS. OpenDNS allows you to block websites on your *home* network. If you have an OpenDNS account you can also participate in what's called "community tagging." community tagging allows people to tag certain websites, and I guess if you use OpenDNS you can block things with those tags...idk, I don't use it.
Here's the bit that matters: OpenDNS and Cisco Umbrella are owned by the same company. It appears that Cisco Umbrella, to some extent, uses OpenDNS community tags to sort websites.
Someone on OpenDNS has community tagged Ao3 as a "tasteless" website. Community tags can be proposed by anyone, but they have to be approved by a moderator. It seems a moderator has approved this tag. Because of the moderator approved tag, it looks like Ao3 has been bundled into *Cisco Umbrella's* blocked sites list for "adult" content. So now, any library, school, business, etc which is blocking Cisco Umbrella’s “adult” category is now blocking Ao3.
Here’s how you can help.
Go here (https://signup.opendns.com/homefree/) to create an OpenDNS account. This is free. Don’t do any of the steps to create or configure a network, JUST make an account. Be sure to uncheck any promotional checkboxes. Once your account is made, be sure to confirm your email, and the confirmation may go into spam - mind did, just be aware. Once you have an account made, go to https://login.opendns.com/ and log in with the account you've made.
It should take you here.
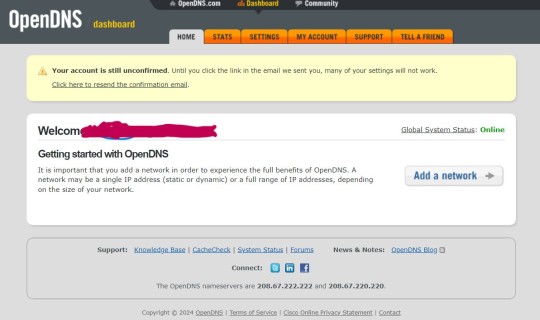
From here, click the small "community" button at the top.

It will bring you here. You will be likely prompted to create a display name. Pick something random, you won't need it again.
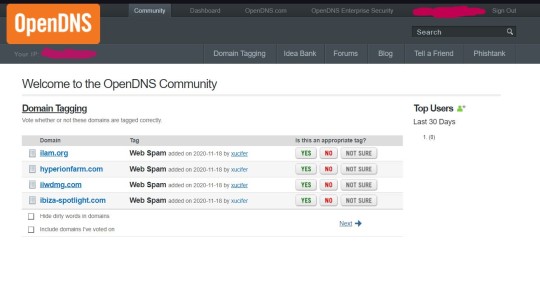
Click on “domain tagging." It will bring you here.
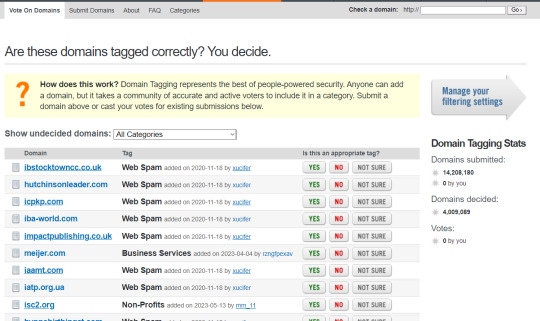
There's a small searchbox in the top right labeled "check a domain." enter archiveofourown.org in this field and hit go. You should be brought here.

What you want to do now is hit the "Flag for Review" button under "Tagged: Tasteless." Don't worry about the other tags. They are candidate tags, not approved/applied and aren't doing anything. The "tasteless" one that's been mod approved is the only one we're worried about. "Flag for review" will open a small text box.
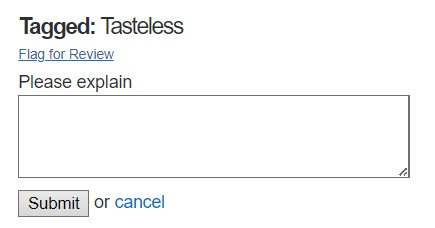
Type in whatever you like here, but PLEASE be academic and respectful. Focus on how "tasteless" is an inaccurate and offensive description for the content. Hit submit.
That's it, you're done.
I do want to be clear about one thing - I am not 100% sure this is going to remove this domain from the cisco adult list, but I'm hoping. The “tasteless” tag that is present on OpenDNS was submitted in 2015. Now, it is not clear when the moderator approved this tag. They may have approved it last night, or in 2015. That date does not appear to be visible. I’m not sure what happened overnight that caused Ao3 to slip into the Cisco umbrella adult category. My best guess is that either the tag was approved last night, or Cisco suddenly started grouping the “tasteless” community tag under adult. It is interesting to me that previous tags such as pornography have been actively mod rejected, so it looks like this one being approved might have been one person with a vendetta. Either way, right now, this seems to be the root of the issue. Domains can be individually allowed on networks by network admins, so if you have to petition your school or place of work it's possible, but I think if we can fix the OpenDNS tag, we can fix it everywhere at once. Hopefully, if we can get enough flags for review in a short enough period of time, it will force them to review it.
Come, help me out here. Let's try and get Ao3 unblocked on the country's schools and libraries.
246 notes
·
View notes
Text
I’m sorry but I’m still losing my fucking MIND over elons incomprehensible Linux own the libs tweet like
Like it’s incredibly obvious he heard about a traceroute, and then googled “how to delete file in Linux” and then didn’t even read the results
Like… woke_mind_virus isn’t a fully qualified domain name, meaning it relies on a custom DNS resolution specific to his machine, or if utilizing a vpn, that specific vpn’s custom host file. Or that the American government would have a host entry for a woke mind virus, which if you’ve ever had to use a government website, is laughable. Also DNS is global for the most part, but honestly we can move on at this point.
So sure, we’ll say that the government has forced all public internet in America to resolve woke_mind_virus. Where does it resolve to? YOUR OWN COMPUTER, you silly billy! Obviously! This is *almost* comprehensible. Sure, we are all infected with the woke mind virus, why not. It must be destroyed within ourselves. Yeah man, whatever. Why not? So how do we destroy it?
Duh! Just delete it! How do we do that in our L337 uber hax0r terminal on our fresh kali live usb (because partitions are scary)? We’ll save that for last.
Because while deleting one file could make a website inoperable, it does not remove every trace of it! It first needs a configuration file in the web server, usually Apache or nginx. This is at LEAST one file, but cmon, if you’re gonna psychologically program the masses and keep it out of public view, you gotta encrypt that shit! So naturally, an SSL is in order! That’s easily 1-3 more files. woke_mind_virus can get a pass on not being fully qualified in this specific case because certs can theoretically be self signed and trusted on local networks, but he wouldn’t be able to tell you that. If you stood up a little one page html site on a web server on your own computer, and navigated to it on port 443 (https://) you would get an SSL error, even though it’s on your own machine. I feel like I’ve beaten this into the ground enough, but just understand it’s stupid.
What’s important to note here is that these BARE MINIMUM files are what routes the request from your machine to the destination site, even if it’s your own computer. If you delete the contents of the site (also called the docroot), the site still exists, and can receive and route requests to and from it, it’s just empty. You’ll probably get a 404 because there’s no actual content to serve. This woke mind princess is in another castle.
It’s also imprudent to delete these configuration files first, because that’s how you determine where the site content actually is! These files dictate what directory (folder for you windows losers) is called upon to actually serve you the content you see displayed when you open a webpage. So you need this information if you don’t want to destroy the entire file system and only want to remove the woke_mind_virus site. Cmon Elon, this is baby shit.
So of course, the strat with the most Efficiency and preserving the rest of the system (which seems to be the point of the tweet) is to find the docroot, delete the docroot, and then delete the web server config files. So how do we delete them?
And here we have it: rm -rf
The syntax is as follows:
rm -rf </path/to/file>
Even if you don’t know shit about Linux, you can probably see the problem here. It’s just so blatantly incorrect, it’s almost as if he’s never done it before.
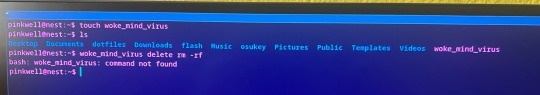
For those that want to see a real world example, here is me creating a file called woke_mind_virus in my home directory and then trying to delete it the Elon Way:
3 notes
·
View notes
Text

In reading a variety of ancient literature; not limited to that of hindu, of course, you will see references to what appear to be cosmological concepts and technology in which would appear as novel - only unearthed or recently conceived of by the instruments of modern or speculative science.
For example, the story of King Kadmudi and Revati and its apparent reference to the concept of time dilation.
King Kakudmi went to see the god Brahma to find a good partner for his daughter, Revati, name of the 27th and last Nakshsatra, but when he got back, so much time had gone by relative to the area of the universe in which he traversed, that everything he knew was long gone.
King Kakudmi’s experience is important because it reveals complex ideas like time bending, in which are considered to be a modern conceptual derivation.
Time dilation, interstellar travel, cloning, artificial wombs, atomic weaponry, "mind born" children and beings, integrated information theory, anti-gravity propulsion are things that are purported to be referenced or are directly. Conventionally these parallels are seen to be that of a coincidental nature and merely mythical/folklore, but by many, simply, curiously out of place within the given time frame.
Many people see these references as perhaps coincidences - drawing connections to these stories to modern inventions, scientific corpus and futuristic concepts, is perhaps hasty thinking. of course, we are all entitled to our own conclusions about the early universe and human history, these epics and we should always keep an open mind, never rejecting new evidence.
I entertain the prospect that humans and god (paramsiva/bhairava,monad, the one, ayin/yesh or whatever have you) manifestations of god, subtle intelligences, semi-divine beings from a plenitude of realms and in between were, and have been continuously in contact, influencing the development of and informing another since the dawn of time; with humans being instrumental in configuring/being a part in the play of the universe with authority, wielding the ability to harness and utilize the divine creative power/maya-sakti and capable of traversing all realms.
I entertain the human being as naturally divine, and that ages ago, they were possessing knowledge of the body and universe so profound - in which was lost and/or suppressed by the overwhelming majority in our current yuga, through disasters, natural forces or intentionally withheld by higher intelligences due to collective human ignorance and abuse - this realm being a prison like simulation/copy of the bhuvarloka/earth we originally inhabit.
The technologies of today and the futuristic concepts featured in Sci fi, paling to the utter freedom of humans and their manipulation of cosmic forces.
As we continue our projection, through the current yuga, we are revisiting/rehashing some of these technologies and understandings as a race, yet as a largely confused, blinded, amnesiac species, we are diminishing our independence and EXTERNALIZING them, whereas they were inextricable from the human beings conscious willing before.
We are at a phase where the most advanced, fringe experimental and/or theoretical sciences are just scratching the surface of the occult, the ancient sciences of tantra - with domains such as integrated information theory, string/M theory and other attempts of grand unifying theories of everything.
In the age of information, we are experiencing a deluge of resurfacing information and technological potential - yet their externalization and our dumbing down of our own conciousness is limiting us, turning us into a regressed animal. This is the paradox of our age.. in the times of Rahu.
With such amazing innovation, we have the potential to restore nature, order, the richness of consciousness; yet with the lack of self awareness, lack of systems of knowledge allowing us to tap our inner potential, our ignorance- it is used as a tool to exponentially siphon our creative capacity and independence. Our people are becoming more impulsive, aimless and unilateral thinkers.
Our very means of liberation has become weaponized against us - our very shackles. Our computational power and data at our fingertips being used to endlessly mislead us and prey on our lowest impulses.
Our languages and communication skills constantly deteriorating. Once able to receive and transfer correspondences - densely layered, multifaceted symbolic language from the celestial intelligences regarding the nature of reality, the languages of the holy texts.. which is now mostly a lost art - causing us to grossly misinterpret scriptures. Closed traditions have been initiating those to upkeep these skills.
Why I have turned to tantra, is to consistently experience and reclaim my true nature, the gifts latent in all of us in which we see vague remnants of in our holy texts- in the unmistakable communion our species has shown in them, it is my destiny.
5 notes
·
View notes
Text
Basic Steps to Build Your Shopify Website — Softhunters

Shopify makes it effortless to set up an e-commerce website. Even a novice user can accomplish it in parts. Shopify is because of its friendly design coupled with powerful features; Shopify is one of the most widely used e-commerce platforms by both small and large businesses. Some of the services they offer include customizable online store templates and effective payment gateways. Shopify website design company can create a strong online presence if they sell tangible products, services, or even digital items.
Read More :- https://softhunters.in/basic-steps-to-build-your-shopify-website/
The Shopify store is simple to use, allowing you to run your business without requiring extensive technical knowledge. This blog post will enumerate the fundamentals of creating a Shopify website.
Creating a Shopify Account
The first step in growing your Shopify store is to create an account. To try this, visit Shopify.com and click on the “Start free trial” button in the top right corner. Then, offer your e-mail address, password, and store name.
The store name will initially function as your number one domain. After developing your account, Shopify will ask you some questions about your business. Fill these out and click on “Enter my store” to proceed. This initial setup system is designed to be short and clean, allowing you to begin building your savings properly away.
Establishing Your Shopify Store
Once you have got your account installation, it is time to configure your keep settings. Access the menu on the left aspect of your Shopify dashboard, which incorporates hyperlinks to all of your save gear and features. Use the settings button at the left to set your keep name, time quarter, forex, and other number one settings.
This step is essential as it inspires the way your shop operates and how clients will perceive it. Make certain all information is correct to ensure easy operations and compliance with local regulations.
Selecting A Theme
Your themes control the presence and design of your site. To select a theme, go to the “online store” in the sales channel in the left sidebar, and then select the theme “Theme.” Some free themes are available for your use in Shopify, and you can also visit the theme stores for the paid ones.
Choose a theme that fits your brand and niche. Check reviews to determine if they can serve your goals and be supported by any additional features you want to integrate in the future. The subject should appeal to the eyes and provide an excellent user experience to maintain customers.
Including Products and Services
Now that your store displays as you want it to, it has time to populate it with your products. Return to the Shopify Admin Dashboard. On the Left Menu, click “Product.” To upload a product, click “Add the Product”. You can include the title, description, price, images, and additional details per product.
Ensure to categorize your products using collections or categories for easy visibility. This is essential as it will directly impact your sales and customer satisfaction.
Be sure to detail product descriptions and use high-quality images so buyers can make quality purchasing decisions.
Personalize Your Theme
Once you have chosen a theme, you may use it to represent your brand in a more customized manner. To try this, click on the “Online Store” tab, after which, at the theme you have selected, hover over it and click “Customize.” From the left-hand equipment inside the editor, you can regulate hues, fonts, and layouts. You also can add or delete sections.
Customization is crucial to making your save stand out and mirror your emblem identification. Ensure that your design stays consistent on all pages so that you can give it an expert touch.
Pages Setup and Content Preparation
You can create additional pages for your website, furthermore, your products. The same applies to the ‘Contact’ and ‘FAQ’ pages — a setup guide and live builder are available. For sharing more details regarding your brand or products, blogs can assist you in promoting the business and help in audience engagement. Also, every content must be created in a manner that makes the customer confident and loyal towards the brand.
Instructions for Setting Up Payment Options
If you want to sell, you need to select a payment option first. Under Settings or Setup Guide, scroll to Payment. Log into your cash account and choose Shopify payment or any other provider if you wish to use PayPal.This is essential to ensure the payment setup works properly and securely. It also determines whether you can process transactions and get paid directly.
Sourcing Suppliers and Additional Funding
Reexamine yourself. What is the profile of the partner you want to work with? In what manner do you intend to work with them? When looking to outsource, do not run away from your network. Existing contacts are the best place to start with a Shopify web development Agency. Easy deals and fewer problems are sometimes discovered just one step away.
Additionally, analyze what you can do within a certain budget. Let’s take a more realistic view to ensure you can achieve practical things and trace the path to interesting opportunities within a budget.
Additional Suggestions for Achieving Success
The following tips can aid in improving your Shopify store.
Establish A Brand Style Guide
Create a general style guide rule document comprising typography, color scheme, and logo style for your brand before commencing the designing of your website. This will help in maintaining said standards throughout your site and marketing resources.
Think About Store Layout
Always keep in mind customer trust, aesthetics, and mobile devices when it comes to modern e-commerce design principles. Launch with a minimum viable product (MVP) and refine through the feedback of your customers.
Make Use of Shopify Apps
There is a suite of apps available within Shopify that can assist in improving features within your store. Consider apps that can enhance customer satisfaction, bot automation, and revenue generation.
Blogging on The Shopify platform
Shopify enables users to store blog posts so that pre-approved content can be designed and managed within the store. This could generate traffic and keep customers engaged.
Conclusion
The process of building a Shopify store is a straightforward one and can be achieved in various stages. With these tips and regular improvements in your store, you can make a successful online presence and build your business accordingly.
Always pay attention to the identity of your brand and the experience of customers for long-term success. The best web development company is always present to provide you with all the support for your Shopify website.
#Shopify Website#Shopify Website Design#Shopify Website Developer#Shopify Website Builder#Shopify Website Designer
2 notes
·
View notes
Text
How Bloodborne astral clock investigation started:
We have the moon, a medical metaphor where the Great Ones are themed as body parts (thanks to Charred Thermos for delving into this), and a clock with 14 symbols split between 12 positions. Surely this has some structure following the 'Zodiac Man' that dictated bloodletting according to the moon in pre-Victorian times (and still shows up on websites that report info on the moon phases connected to calendar dates).
How it's going:
The Wheel of Logarius has 14 spokes which is reminiscent of the pH scale that goes from 1-14 and is a logarithmic scale based on concentration of H+ per litre of liquid. And given the medical context it would make a lot of sense that the zodiac is also split between the 4 Hippocratic humours of blood (spring), yellow bile (summer), black bile (autumn), and "phlegm" (winter). So "Formless Oedon" could naturally be "blood" which encompasses Aries/Iron, Taurus/Copper, and Gemini/Mercury. This actually makes sense in the context of Old One Coldblood being blue because that is the colour of horseshoe crab blood which has a copper metal core, but still falls under the domain of Oedon. And "quicksilver" bullets synthesized from blood have the fused property of real blood (iron based) and fantasy (hunting beasts with "quick" silver bullets). Saw something about a "flora, of the moon" which could be related to the traditional way of assigning a name to each moon instead of months. But which system? The Farmer's Almanac is a reliably documented, consistent, and accessible source but has the drawback that it is disconnected from the traditions of the native peoples. On the other hand there is the potential Osage connection with May being the 'Killer of the Flowers Moon'.
Also, the "third umbilical cord" would certainly be a body part, but I'm not so sure that's the only thing going on here. Bloodborne has a huge musical theme, and a "third chord" is a configuration of chord containing 3 tones at specific offsets from each other.
#Bloodborne#theory synopsis#there's another pretty significant topic I've been pursuing and that I'm leaving out here#Because it's a lengthy process of describing a frankly ridiculous premise#fromsoftware meta narrative
2 notes
·
View notes
Text
Professional Website Hosting and Management Services
In today’s digital age, having a strong online presence is crucial for any business or organization. A well-designed website serves as a virtual storefront, allowing you to reach a global audience and showcase your products, services, or ideas. However, creating and maintaining a website requires technical expertise, time, and resources that not everyone possesses. That’s where professional website hosting and management services come into play.

What is Website Hosting?
Website hosting refers to the process of storing your website files on a server that is connected to the internet. When someone types your website’s domain name into their browser, their device connects to the server, retrieves the website files, and displays the webpages. Website hosting is a critical component of your online presence, as it ensures your website is accessible to visitors at all times.
The Benefits of Professional Website Hosting and Management Services
While it is possible to host a website on your own, opting for professional website hosting and management services offers numerous advantages. Let’s explore some of the key benefits:
1. Reliability and Uptime:
Professional hosting providers offer reliable and secure servers, ensuring that your website is accessible to visitors around the clock. They have redundant systems in place to minimize downtime and address any technical issues promptly. This ensures a seamless browsing experience for your users, enhancing their trust and satisfaction.
2. Technical Support:
Managing a website involves dealing with technical challenges such as server configuration, software updates, and security patches. With professional hosting services, you have access to a dedicated support team that can assist you with any technical issues that arise. This allows you to focus on your core business activities while leaving the technical aspects to the experts.
3. Scalability:
As your business grows, so does the traffic to your website. Professional hosting providers offer scalable solutions that can accommodate increased traffic and ensure optimal performance. They have the infrastructure and resources to handle high volumes of visitors, preventing your website from becoming slow or unresponsive.
4. Enhanced Security:
Website security is of paramount importance, especially in an era of increasing cyber threats. Professional hosting services implement robust security measures, including firewalls, malware scanning, and regular backups, to protect your website and its data. They stay updated with the latest security protocols and continuously monitor for any potential vulnerabilities.
5. Additional Services:
Many professional hosting providers offer a range of additional services to enhance your website’s functionality and performance. These may include content delivery networks (CDNs) to improve page load speeds, SSL certificates for secure data transmission, and automatic backups to safeguard your data in case of unforeseen events.
Choosing the Right Professional Hosting Provider
With numerous hosting providers available, selecting the right one for your specific needs can be daunting. Here are some factors to consider when choosing a professional hosting provider:
1. Reliability and Uptime Guarantee:
Ensure that the hosting provider has a proven track record of reliability and offers an uptime guarantee of at least 99%. You don’t want your website to be inaccessible due to server issues or maintenance downtime.
2. Scalability Options:
Consider the scalability options offered by the hosting provider. Can they accommodate your website’s growth and handle sudden traffic spikes? A flexible hosting solution is crucial to ensure your website performs well under varying loads.
3. Security Measures:
Check the security measures implemented by the hosting provider. Are they proactive in addressing security threats? Do they offer SSL certificates, regular backups, and malware scanning? Robust security measures are essential to protect your website and sensitive data.
4. Technical Support:
Ensure that the hosting provider offers reliable and responsive technical support. Look for providers that offer 24/7 support through various channels like live chat, email, or phone. Quick assistance during emergencies can save you valuable time and prevent potential losses.
5. Pricing and Value for Money:
While cost shouldn’t be the sole deciding factor, it’s important to compare pricing plans and determine the value for money offered by different hosting providers. Consider the features, performance, and support you receive for the price you pay.
Conclusion
Professional website hosting and management services provide businesses and organizations with a reliable, secure, and scalable online infrastructure. By outsourcing the technical aspects of website management, you can focus on your core activities while ensuring an optimal user experience for your website visitors. Choosing the right hosting provider is crucial to unlock the benefits of professional website hosting and maximize your online presence.
Investing in professional hosting services is a wise decision for any business or organization that values their online presence. It allows you to leverage the expertise and infrastructure of a dedicated team while ensuring your website remains accessible, secure, and performs at its best. Don’t underestimate the impact that a well-hosted and managed website can have on your brand, customer satisfaction, and business success.

Source
#WebManagement#ServerHosting#WebsiteMaintenance#TechSupport#CloudHosting#DataCenter#ServerManagement#WebHosting#ITInfrastructure#WebsiteSecurity#ServerAdmin#HostingSolutions#WebsitePerformance#ServerMonitoring#WebDevelopment#CloudComputing#NetworkSecurity#DomainRegistration#BackupandRecovery#Cybersecurity
24 notes
·
View notes
Text
Features of Linux operating system for Website hosting
Are you trying to find a reputable, safe and best web hosting provider? Looking for a dependable and affordable web hosting solution? Linux web hosting is a fantastic choice for companies, bloggers, and website developers.

We'll go over Linux hosting's advantages and why it's the greatest option for website hosting. The different types of Linux web hosting will also be covered, along with advice on how to pick the best Linux web hosting provider.
Linux hosting: what is it?
Linux hosting is a type of web hosting in which websites are hosted on the Linux operating system. Because it can handle a variety of online applications and is dependable, safe, and stable, it is a popular option for hosting. Linux hosting is the practice of running websites on Linux-powered servers. Various hosting choices may be available, including dedicated hosting, cloud hosting, VPS hosting, and shared hosting. Companies and developers frequently choose Linux hosting due to its adaptability, affordability, and capacity to run unique applications.
Features of Linux operating system for website hosting-
The reliability, security, and flexibility of the Linux operating system make it a popular choice for web developers and website owners. Here, we'll examine some of the main characteristics of Linux operating systems used in web hosting and the reasons why they're the best option.
Flexibility
The Linux operating system can run numerous programs, including content management systems (CMS), e-commerce platforms, and custom apps. This implies that any kind of website, including blogs, e-commerce sites, and custom applications, can be hosted on a Linux server.
Scalability
Scalability is another benefit of Linux hosting as your website expands and traffic increases, you may quickly upgrade your hosting plan to a higher level of resources, such as more CPU and memory. By doing this, you can ensure that your website can manage the extra traffic and continue functioning properly.
Open-Source and Free
Because Linux is an open-source operating system, hosting providers can offer Linux hosting plans at a cheaper cost than other forms of hosting because it is free to use. Furthermore, Linux servers are renowned for their efficiency, which enables them to manage numerous websites with fewer resources used, resulting in cheap web hosting cost.
Interface That's user-friendly
Numerous control panel options are also available with Linux hosting. You can easily manage your website and hosting account with a control panel, which is an intuitive user interface. Plesk and cPanel are popular control panel choices for Linux hosting. These panels offer many functions, such as creating email accounts, managing databases, and viewing website statistics.
Security Level
Another benefit of best Linux hosting is its high level of security. The operating system is routinely updated to address weaknesses and fend off attackers because security was a top priority during its construction. To further improve security, Linux servers can also be configured using a range of security features, including firewalls and intrusion detection systems.
Simple Structures
It is an extremely thin operating system. It consumes less storage space, has a smaller memory expansion, and has significantly fewer requirements than any other operating system. A Linux distribution usually has around the same amount of disc space and just 128MB of RAM.
Dependability
Numerous computer languages and frameworks, such as PHP, Python, Ruby, and others, are compatible with Linux. Because of this, it's a fantastic option for hosting websites created using these technologies.
Virtual Web Hosting
Multiple websites can be hosted on a single server using Linux hosting, which is another feature. We call this "virtual hosting." It enables you to host several websites, each with its own content and domain name, on a single server. For companies or individuals who wish to host several websites without having to buy several hosting services, this can be an affordable web hosting solution.
Perfect for Programmers
Almost all of the widely used programming languages, such as C/C++, Java, Python, Ruby, etc., are supported. It also offers a vast array of applications related to development. Most developers worldwide prefer the Linux terminal over the Windows command line. The package manager on a Linux system helps programmers learn how things are done. Additionally, it supports SSH and has capabilities like bash scripting that help with quick server management.
Linux Hosting Types-
Linux websites have access to cloud hosting, dedicated hosting, VPS hosting, shared hosting, and other hosting options.
Shared hosting:
The most straightforward and reasonably priced kind of Linux hosting is shared hosting. It entails running several websites on a single server and sharing the CPU, memory, and storage between the websites. A suitable choice for tiny websites with low to moderate traffic is shared hosting.
Virtual Private Server (VPS) hosting:
This kind of Linux hosting gives your website access to a virtualized environment. Having the same physical server entails hosting your website on a virtual server that is divided from other websites. While VPS hosting is still less expensive than dedicated hosting, it offers greater control and resources than shared hosting.
Dedicated hosting:
With dedicated hosting, you have exclusive use of a physical server for Linux hosting. This implies that you are the only user with access to all of the server's resources, and you can set it up to suit your requirements. The priciest kind of Linux hosting is dedicated hosting, which is also the most potent and offers the greatest control.
Cloud hosting:
This kind of Linux hosting includes putting your website on a cloud-based server network. This implies that your website is simultaneously hosted on several servers, offering a great degree of scalability and dependability. Although cloud hosting is more expensive than shared hosting, it is a versatile and affordable web hosting choice for websites that require a lot of resources or traffic.
The size, traffic, and resource requirements of your website will determine the kind of Linux hosting that is best for you. While VPS, dedicated, and cloud hosting are better suited for larger businesses with higher traffic and resource requirements, shared hosting is a reasonable choice for smaller websites with minimal traffic.
Advice on Selecting the Best web hosting provider-
To make sure you get the best service for your website, it's crucial to take into account a few vital considerations when selecting an affordable Linux web hosting provider. The following advice will help you select the best Linux web hosting provider:
Find a trustworthy web hosting provider
Go for a web hosting provider that has a solid track record in the sector. Choose a hosting provider that has been in operation for some time and has a solid reputation for offering dependable hosting services. To locate a service that other people have found reliable, you can read reviews and get referrals from friends and co-worker's.
Think about the cost
To get the greatest value, compare the costs of several hosting providers. But remember that the least expensive choice isn't necessarily the best. Aim to strike a balance between the cost and the hosting provider's services and reputation.
Establish your hosting requirements
It's critical to ascertain your hosting requirements prior to beginning your search for a hosting provider. Take into account the size of your website, the volume of visitors you anticipate, and the kinds of apps you plan to use. This will enable you to focus your search and select a best web hosting provider that best suits your requirements.
Good customer service provider
Pick an affordable web hosting provider that offers best customer service. Choose a service provider who provides live chat, email, and phone support in addition to round-the-clock assistance. This will guarantee that assistance will be available to you at all times.
Selecting the Linux web hosting provider is a crucial choice that will significantly affect the functionality and dependability of your website. You may choose the best hosting provider for your website by taking into account your needs, searching for a reliable provider, examining the features, and seeking for a provider that offers excellent customer service.
Think of the type of hosting
Select the hosting plan that works best for your website. As was previously noted, Linux hosting comes in a variety of forms, including dedicated, cloud, shared, and VPS hosting. Select a best and an affordable hosting provider that provides the type of hosting that best meets your requirements.
Examine the advantages offered by the hosting
Verify if the hosting provider has the services you require. The quantity of storage and bandwidth, the number of domains and subdomains, the kind of control panel, and the presence of one-click installs for programmes like WordPress are a few crucial aspects to take into account.
Conclusion-
For those searching for a dependable and reasonably priced hosting solution, Linux hosting is an excellent choice. It has a tonne of features. Linux hosting is one of the most popular hosting options available thanks to all these advantages. As a lot of people say these days, developers, engineers and programmers promote Linux as one of the most powerful operating systems available.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
2 notes
·
View notes
Text
Synology NAS Domain Join: The Importance of DNS Configuration
In this article, we shall discuss the issues you could face when performing a Synology NAS Domain Join: The Importance of DNS Configuration. DNS configuration ensures that devices on a network can communicate with each other and access external resources on the internet. This enables devices to locate servers and services by their domain names, facilitating seamless connectivity. Please see DSM…

View On WordPress
#DNS#DNS Configuration#Domain Join and Authentication#Domain Name System#Network Attached Storage)#Synology#Troubleshooting Synology NAS Domain Join: The Importance of Correct DNS Configuration
0 notes
Text
SELinux in AOSP: A Guide to Securing Embedded Android Systems
Introduction
Security-Enhanced Linux (SELinux) is a core security mechanism in the Android Open Source Project (AOSP) that enforces robust access control. Unlike traditional Discretionary Access Control (DAC), which relies on user-based permissions, SELinux uses Mandatory Access Control (MAC) to restrict system interactions based on predefined policies. Android integrated SELinux starting from version 4.3. It runs in either permissive mode, which logs violations, or enforcing mode, which blocks unauthorized actions.

Understanding SELinux policies, labels, and domains is essential for embedded developers working on middleware, HAL, and system daemons in order to secure Android devices. Sensitive system components are protected, unauthorized access is limited, and privilege escalation is avoided with proper SELinux configuration. This blog discusses best practices for creating security policies, how SELinux functions within AOSP, and a real-world example of using SELinux on a binderized HAL. Developers can strengthen embedded systems against exploits and security breaches by becoming proficient with SELinux.
What is SELinux?
With mandatory access control (MAC) policies that limit programs' capabilities beyond conventional discretionary access controls (DAC), SELinux is a security architecture built into the Linux kernel. It guarantees that an application's activities stay contained within predetermined bounds even in the event that it is compromised.
Core Concepts of SELinux
Labels: Every process and object (like files, directories, and ports) in the system is assigned a security label. A key component of SELinux's decision-making process is these labels.
Type Enforcement (TE): The main SELinux mechanism is Type Enforcement (TE), in which policies specify how types (labels) linked to objects and processes can communicate. A process named httpd_t (Apache), for example, can be made to only access files with the label httpd_sys_content_t.
Roles and Users: To manage permissions more precisely, SELinux defines roles and users. Nonetheless, type enforcement continues to be the main focus in many implementations.
SELinux in AOSP
SELinux integration with Android
Google strengthened Android's security by integrating SELinux into the platform starting with version 4.3. SELinux functions in two ways in AOSP:
Permissive Mode: Violators are recorded but not stopped; SELinux rules are not enforced.
Enforcing Mode: SELinux rules are put into effect, and infractions are recorded and prevented. For strong security, Android devices try to run in enforcing mode.
Advantages of SELinux in Android
Privilege escalation is mitigated: SELinux restricts an application's behavior even if it acquires unauthorized privileges, avoiding more widespread system compromises.
Protection Against Malware: By limiting applications' access to private information or system components, SELinux policies can lessen the possible impact of malware.
Enhanced Multi-User Security: SELinux makes sure that user data is kept separate and safe from other users and applications by implementing stringent access controls.
Implementing SELinux in AOSP
Configuring the Linux kernel for SELinux: Make sure the kernel is compiled with SELinux support. This entails turning on particular security module configuration options.
Filesystem Labeling: Give filesystem objects the proper security labels. This can be accomplished by setting default labels in filesystem images or by using tools such as restorecon.
Compilation of Policies: Using tools like checkpolicy, create SELinux policies that are specific to the needs of your system.
Policy Loading: Use tools like load_policy or incorporate the compiled policies into the system's initialization procedure to load them into the kernel.
Writing SELinux Policies
IVI (In-Vehicle Infotainment), ADAS (Advanced Driver Assistance Systems), and telematics are among the vital services that Android Automotive OS (AAOS) manages in automotive embedded systems. SELinux policies are necessary to enforce stringent access controls across all system components, especially middleware services, Binderized HALs, and system daemons, in order to ensure security in such a system. In order to make sure that only authorized system components can access and alter vehicle data, we'll map SELinux policy writing to a real-world automotive example below using a binderized HAL.
Determine Types and Domains
Consider a Vehicle HAL (VHAL) in an automotive system, which gives users access to information about the vehicle, including its speed, fuel level, engine status, and door lock condition. The telematics module, navigation app, and IVI system are among the system elements with which the Vehicle HAL service communicates.
The hal_vehicle_t domain is where the Vehicle HAL daemon operates.
vehicle_data_t is the label for vehicle data files.
The ivi_system_t domain is where the IVI system operates.
The telematics_t domain is where the Telematics service functions.
By defining these domains, unauthorized applications are prevented from accessing vital vehicle parameters and controlled access between various system components is ensured.
Tools and Resources
SELinux Notebook: An open-source resource that provides comprehensive insights into SELinux concepts and implementations. GitHub - SELinuxProject/selinux-notebook
NSA's SELinux Implementation Report: An in-depth report detailing the implementation of SELinux as a Linux Security Module. Implementing SELinux as a Linux Security Module
Conclusion
With SELinux included in AOSP, developers can implement strict access controls, isolate processes, and keep sensitive information safe.
Whether you're building embedded Android systems, HAL layers, or automotive and IoT device middleware, SELinux offers a secure framework to ensure system integrity.
For any solution related to SELinux implementation, HAL hardening, or embedded Android security, connect with Silicon Signals at www.siliconsignals.io or email us at [email protected]. 👉 Do follow us on LinkedIn to stay updated on embedded tech insights and innovations.
#linux kernel#androidbsp#linuxdebugging#android#aosp#embeddedtechnology#embeddedsoftware#embeddedsystems#iot development services#selinux#linuxsecurity#aospsecurity
0 notes
Text
SAP Consulting Services | End-to-End SAP Implementation
In today’s competitive landscape, businesses need powerful tools to streamline operations, boost efficiency, and enable scalable growth. SAP, a globally recognized enterprise resource planning (ERP) solution, has become the go-to platform for organizations seeking digital transformation. But implementing SAP effectively requires the right strategy, technical know-how, and experienced guidance.
That’s where Versatile IT Solutions comes in.
As a top-tier provider of SAP consulting services, Versatile helps organizations harness the full potential of SAP through end-to-end implementation, customization, migration, and support. With a client-centric approach and a focus on measurable outcomes, Versatile empowers enterprises to optimize operations, reduce risks, and enhance performance.
Why Choose Versatile IT Solutions for SAP?
Versatile IT Solutions is a trusted name in SAP implementation, offering specialized services to businesses across industries. Whether you’re starting from scratch or looking to upgrade your existing SAP landscape, Versatile provides comprehensive consulting support tailored to your organization’s needs.
Key Differentiators:
✅ Certified SAP Experts: A team of consultants with deep expertise in SAP ERP, SAP S/4HANA, and SAP Business One.
✅ Industry-Specific Solutions: Customized SAP modules for sectors like manufacturing, retail, healthcare, logistics, and finance.
✅ Full Lifecycle Support: From discovery and strategy to deployment and post-go-live support.
✅ Agile Delivery Models: Fast, scalable, and cost-effective implementation approaches.
✅ End-to-End Integration: Seamless integration of SAP with existing systems and third-party platforms.
Our SAP Consulting Services
Versatile IT Solutions provides a complete suite of SAP services designed to support every phase of your digital transformation journey.
1. SAP Implementation Services
Versatile follows a proven methodology to implement SAP systems that align with your business goals. They handle everything from planning and blueprinting to system configuration and user training.
2. SAP S/4HANA Migration
Switching to SAP S/4HANA? Versatile ensures a smooth migration from legacy systems with minimal disruption. They help businesses unlock faster data processing, enhanced UX, and intelligent automation.
3. SAP Customization & Development
Every business has unique needs. Versatile offers custom development to tailor SAP modules and workflows specific to your business processes.
4. SAP Integration Services
Ensure seamless communication between SAP and third-party platforms like Salesforce, Microsoft Azure, and more. Versatile creates integrated digital ecosystems that work in real-time.
5. SAP Support & Maintenance
Post-implementation support is critical. Versatile provides 24/7 system monitoring, updates, patches, and user support to ensure continuous performance.
6. SAP Cloud Solutions
Get scalable, secure, and flexible SAP solutions on the cloud. Versatile offers both public and private cloud deployment options.
Industries We Serve
With clients across various domains, Versatile brings tailored SAP solutions for:
Manufacturing & Supply Chain
Healthcare & Pharmaceuticals
Retail & eCommerce
Finance & Banking
Logistics & Transportation
Telecommunications
Energy & Utilities
No matter your sector, Versatile crafts SAP strategies that align with industry standards and compliance requirements.
End-to-End SAP Implementation Approach
Versatile IT Solutions follows a strategic, transparent, and outcome-focused methodology:
Phase 1: Assessment & Strategy
Understand current systems, define goals, assess readiness, and create a roadmap.
Phase 2: Blueprinting & Planning
Map business processes, finalize module requirements, and design the SAP architecture.
Phase 3: Configuration & Development
Customize modules, build interfaces, and configure workflows.
Phase 4: Testing & Deployment
Conduct system testing, user acceptance testing (UAT), and go-live preparation.
Phase 5: Training & Support
Train end-users, provide documentation, and offer post-implementation support.
Client Testimonials
“Versatile implemented SAP S/4HANA for our manufacturing operations. The transition was seamless, and the results exceeded our expectations.” – CIO, Automotive Firm
“Thanks to Versatile’s SAP consulting services, we now have real-time visibility into our retail supply chain. Their team is knowledgeable, proactive, and truly committed.” – Operations Head, Retail Chain
These success stories reflect Versatile’s commitment to delivering impactful SAP solutions.
Let’s Build the Future of Your Business with SAP
SAP is more than just software—it’s a strategic asset for your business. Whether you're looking to automate finance, streamline logistics, or optimize your supply chain, Versatile IT Solutions offers the expertise you need to get it right.
📌 Explore our SAP Consulting Services
📌 Need expert advice or a quick consultation?
#SAP Consulting Services#SAP Implementation#SAP S/4HANA#ERP Solutions#SAP Integration#Versatile IT Solutions#SAP Migration#Cloud ERP
0 notes
Text
FCSS - SD-WAN 7.4 Architect FCSS_SDW_AR-7.4 Questions and Answers
In today's increasingly interconnected digital landscape, organizations face mounting challenges as their networks grow more intricate and geographically dispersed across multiple locations and regions. The Fortinet Certified Solution Specialist (FCSS) – SD-WAN 7.4 Architect certification has been meticulously crafted for experienced IT professionals who are responsible for designing, implementing, and maintaining these sophisticated infrastructure environments. For those seeking to validate their expertise in this domain, Cert007 offers an extensive collection of the most current FCSS - SD-WAN 7.4 Architect FCSS_SDW_AR-7.4 Questions and Answers, providing a structured pathway to achieving certification success.
What Is the FCSS – SD-WAN 7.4 Architect Certification?
The FCSS – SD-WAN 7.4 Architect exam is a comprehensive assessment designed to validate your hands-on expertise with Fortinet's sophisticated SD-WAN technology stack. This rigorous certification evaluates your practical knowledge of system integration, enterprise-wide management practices, strategic deployment methodologies, and advanced troubleshooting techniques within a secure SD-WAN infrastructure. The exam thoroughly tests your ability to architect and maintain solutions within a robust framework powered by:
FortiOS 7.4.4 - The core operating system that drives Fortinet's industry-leading security and networking capabilities
FortiManager 7.4.5 - The centralized management platform for streamlined configuration and control
FortiAnalyzer 7.4.5 - The advanced analytics and reporting system for comprehensive visibility
Certification Tracks
This exam supports two elite FCSS certification paths:
FCSS – Network Security: Proving your ability to design, secure, and optimize Fortinet-based network security infrastructures.
FCSS – Secure Access Service Edge (SASE): Validates the management of hybrid edge-to-cloud network architectures built on Fortinet solutions.
Who Should Take This Exam?
The exam is ideal for:
Network and security architects
Senior Fortinet professionals managing distributed SD-WAN networks
Engineers designing and deploying secure WAN topologies using multiple FortiGate devices
Exam Details
Detail Information Exam Name FCSS – SD-WAN 7.4 Architect Series Code FCSS_SDW-7.4-AR Format 38 multiple-choice questions Time Allotted 75 minutes Scoring Pass/Fail (report via Pearson VUE) Language English Versions Tested FortiOS 7.4, FortiManager 7.4
FCSS_SDW-7.4-AR Exam Topics Breakdown
To succeed, candidates must show expertise in these key areas:
🔧 SD-WAN Configuration
Initial SD-WAN setup and member definition
Configuring SD-WAN zones
Performance SLA definitions for failover and dynamic path selection
🧭 Rules and Routing
Creating SD-WAN rules for traffic steering
Setting up policy-based and dynamic routing strategies
🛠 Centralized Management
Deploying SD-WAN from FortiManager
Utilizing SD-WAN overlay templates for scalable branch deployment
Configuring and managing branch-level devices centrally
🔐 Advanced IPsec Architectures
Designing hub-and-spoke IPsec topologies
Deploying ADVPN for dynamic secure meshing
Handling multi-hub, multi-region, and large-scale site-to-site deployments
🧪 SD-WAN Troubleshooting
Diagnosing SD-WAN rule application and session behavior
Analyzing routing logic and overlay routing decisions
Debugging ADVPN tunnels, routing loops, and service-level failures
Best Practice Q&A from Cert007
For many successful candidates, Cert007’s FCSS_SDW_AR-7.4 question and answer collection is a game-changer. Here's why:
Real exam alignment: Mimics the format and complexity of actual Fortinet exam items
Regularly updated: Matches changes in FortiOS and FortiManager versions
Exhibit-based questions: Includes troubleshooting outputs, configuration screens, routing tables
Validated accuracy: Reviewed by industry experts and Fortinet-certified professionals
Cert007 empowers you to bridge knowledge gaps, improve time management, and master exam readiness.
Strategy for FCSS_SDW-7.4-AR Exam Success
✔ Know More Than Just the Commands
Understand the why behind each decision: why ADVPN would be used over IPsec, how performance SLAs impact real-world traffic flows, and how centralized configs streamline branch scaling.
✔ Practice Scenario Simulations
Use lab environments to simulate:
ZTP with FortiDeploy
SD-WAN overlays via FortiManager templates
Dual-hub failover with ADVPN
✔ Use Q&A Strategically
Cert007’s questions should supplement, not substitute, your study. Treat them as reinforcement tools.
✔ Take Mock Exams
Simulate the 75-minute experience with at least two full-length practice runs to gauge speed and confidence.
Conclusion
The FCSS – SD-WAN 7.4 Architect certification represents a distinguished milestone in your professional journey, serving as the definitive gateway to establishing yourself as a recognized Fortinet expert in secure, scalable WAN architecture. This prestigious certification not only validates your technical prowess but also demonstrates your ability to architect sophisticated network solutions that meet modern enterprise demands. Through a combination of structured training programs, hands-on laboratory experience in realistic environments, and comprehensive Q&A preparation materials from Cert007, you'll be thoroughly equipped to master the certification requirements and advance your career. Whether you're aiming to enhance your current role or step into more advanced positions in network architecture, your path to success becomes clearly defined and achievable with dedicated preparation and the right resources at your disposal.
0 notes
Text
Stone Crusher: Powering Modern Infrastructure with Reliable Crushing Solutions
In the heart of modern construction, mining, and infrastructure development lies a machine that transforms raw rock into usable material — the stone crusher. CraftsmenCrusher is proud to be a leading name in this domain, delivering powerful and durable stone crushers engineered to meet diverse industrial needs.
A stone crusher is essential for reducing large stones into smaller aggregates or sand. These crushed materials form the base of highways, railways, buildings, and bridges. CraftsmenCrusher understands the demand for precision, performance, and efficiency in this field. Our range of stone crushing machines is designed to ensure consistent output, reduced maintenance, and high operational life.
CraftsmenCrusher manufactures a wide variety of stone crusher machines including jaw crushers, cone crushers, and impact crushers. Whether it’s hard granite or soft limestone, our machines handle all rock types with ease. Our stone crusher plant options are ideal for large-scale operations and can be customized based on project requirements. Each crushing plant integrates top-quality components to ensure seamless production and minimal downtime.
Among our top offerings is the mobile stone crusher. It combines mobility with crushing efficiency, allowing it to be deployed in remote job sites or urban projects with limited space. This adaptability makes mobile crushing machines an excellent solution for modern mining and construction projects.
The price of stone crushers depends on capacity, configuration, and technology. CraftsmenCrusher offers cost-effective machines without compromising on quality. Whether you are a small contractor or a large infrastructure company, we ensure you get the best value for your investment. Our commitment to service doesn’t end at the sale — we provide support, training, and spare parts to keep your crushing unit performing optimally.
As a reputed crushing plant manufacturer, we also specialize in complete stone crusher plant solutions. Our experts evaluate your material type, desired output, and site conditions to design a tailored system. From jaw crushers for primary crushing to cone crushers for secondary crushing and vibrating screens for sorting, our plants are built for performance and longevity.
Our machines are popular among quarry owners, mining companies, and construction firms due to their robustness and energy efficiency. They are also designed to meet environmental standards, minimizing dust and noise while maximizing throughput.
CraftsmenCrusher is committed to being more than just a stone crusher supplier. We are your partner in productivity and innovation. With decades of experience in the crushing equipment industry, we continuously invest in technology and quality control to set new benchmarks in performance and reliability.
From a single jaw crusher to a complete gravel crusher setup, CraftsmenCrusher delivers trusted solutions that empower industries to build better and faster. Choose durability. Choose efficiency. Choose CraftsmenCrusher.
https://craftsmencrusher.com/best-stone-crusher-plant/

0 notes
Text
Leading the Charge: Top Solar Cable Manufacturers in India – Spotlight on Ambica Cable
As the world shifts towards clean and renewable energy, solar power is taking center stage. In India, the solar energy sector has seen exponential growth, driven by ambitious government targets, technological advancements, and increasing environmental awareness. A crucial but often overlooked component of any solar power system is the solar cable manufacturers in india —the backbone of efficient energy transmission between solar panels, inverters, and batteries.
Why Solar Cables Matter
Solar cables are specially designed to withstand extreme environmental conditions. They need to be UV resistant, flame retardant, weatherproof, and durable to ensure long-term performance in outdoor installations. High-quality solar cables reduce power losses and enhance the safety and longevity of the system.
The Indian Market for Solar Cables
India’s solar industry is booming, with the country aiming to reach 500 GW of renewable energy capacity by 2030. This rapid expansion has fueled the demand for reliable and cost-effective solar cables. A few manufacturers have emerged as key players in this domain, with Ambica Cable being one of the most trusted names.
Ambica Cable: A Trusted Name in Solar Cable Manufacturing
Ambica Cable has built a solid reputation for manufacturing high-performance solar cables that meet both national and international standards. With a focus on innovation, quality, and sustainability, the company offers a comprehensive range of solar DC cables designed specifically for photovoltaic systems.
Key Features of Ambica Solar Cables:
TUV & UL Certified: Ensures compliance with global safety and performance standards.
Long Lifespan: Designed for 25+ years of outdoor service life.
High Flexibility: Easy to install across various solar panel configurations.
Weather & UV Resistant: Performs reliably under harsh sunlight and weather fluctuations.
Eco-Friendly Manufacturing: Adheres to RoHS guidelines and promotes sustainable production practices.
Applications:
Solar rooftop installations (residential and commercial)
Utility-scale solar farms
Off-grid solar systems
Hybrid solar power projects
Commitment to Quality and Innovation
Ambica Cable’s state-of-the-art manufacturing facilities and R&D efforts ensure that their products stay ahead of the curve in terms of performance, reliability, and compliance. With a customer-centric approach and wide distribution network, Ambica has become a preferred supplier for EPC contractors, developers, and solar integrators across India and overseas.
Conclusion
As India continues to embrace solar energy, the role of reliable solar cable manufacturers becomes increasingly vital. Companies like Ambica Cable are not just supporting this transition—they're powering it. With a strong commitment to quality, innovation, and sustainability, Ambica stands out as a key enabler in India’s clean energy journey.
Visit:- https://www.ambicacables.com/solar-cable.html
0 notes