#Electronic Security Solutions
Text
M-Tech Solutions - Electronic Security Solutions
M-Tech Solutions is your premier choice for comprehensive security solutions. With a seasoned team of professionals, we specialize in Alarm System Installation, Surveillance Camera Installation, and Commercial CCTV Installation. Serving the Gold Coast and Brisbane areas, our expertise in Security System Installation ensures unparalleled safety for your premises. Backed by years of experience working with major financial institutions, we guarantee top-notch service quality and project completion within deadlines. Choose M-Tech Solutions for personalized service, competitive rates, and utmost customer satisfaction. Your security is our priority.

1 note
·
View note
Text
#eCheck#Electronic checks#ACH (Automated Clearing House)#Digital payments#Payment processing#Merchant services#Payment solutions#Secure transactions#Business payments#Online payments#Payment gateway#Payment technology#Financial services#E-commerce#Retail business#Small business#USA businesses#American merchants#Payment methods#Payment processing company#Payment processing solutions#Electronic payment options#Payment security#Card processing#Payment terminals#Mobile payments#Payment software#Point of sale (POS)#Payment integration#Business growth
6 notes
·
View notes
Text
Enhance Your Security with Pyrotech Electronics Pvt Ltd CCTV Cameras
When it comes to safeguarding your home or business, Pyrotech Electronics Pvt Ltd is your go-to source for top-tier CCTV solutions. Our range of CCTV cameras combines cutting-edge technology with unmatched reliability to offer you the best in security surveillance.
Why Choose Pyrotech Electronics Pvt Ltd for CCTV Cameras?
Superior Image Quality
Our CCTV cameras are engineered to deliver high-resolution video, ensuring every detail is captured with clarity. Whether you need sharp images for identification or broad coverage for general monitoring, our cameras provide excellent visual performance.
State-of-the-Art Technology
At Pyrotech Electronics Pvt Ltd, we use the latest advancements in CCTV technology. Our offerings include HD, IP, and PTZ cameras, each designed to provide exceptional performance and adaptability for various security needs.
Robust and Reliable
Built to last, our CCTV cameras are constructed with durability in mind. They are designed to operate effectively in diverse environmental conditions, ensuring consistent performance and reliability.
Advanced Features
Our cameras come equipped with a range of advanced features to enhance your surveillance system. From night vision capabilities and motion detection to remote monitoring and control, Pyrotech Electronics Pvt Ltd cameras offer sophisticated solutions to keep your property secure.
Versatile Solutions
We offer a wide range of CCTV cameras suitable for residential, commercial, and industrial applications. Whether you need comprehensive coverage for a large facility or focused monitoring for a smaller space, Pyrotech Electronics Pvt Ltd has the right solution for you.
Explore Our CCTV Camera Range:
HD CCTV Cameras: Capture every detail with high-definition clarity, perfect for precise monitoring and security.
IP Cameras: Utilize network-based surveillance for flexible installation and remote access, allowing you to monitor your premises from anywhere.
PTZ Cameras: Gain comprehensive coverage with pan, tilt, and zoom capabilities, ideal for large areas and detailed observation.
Day/Night Cameras: Ensure clear video footage even in low-light or nighttime conditions with advanced low-light technology.
Secure Your Property with Confidence
Choose Pyrotech Electronics Pvt Ltd for your CCTV camera needs and experience the difference that high-quality, reliable surveillance technology can make. Our dedication to innovation and customer satisfaction ensures you receive the best security solutions available.
For more details about our CCTV cameras or to discuss how we can meet your specific security requirements, please get in touch with us. Pyrotech Electronics Pvt Ltd is committed to providing superior CCTV solutions to keep your environment safe and secure.
#CCTV Cameras#Security Solutions#Pyrotech Electronics Pvt Ltd#High-Resolution Surveillance#HD CCTV Cameras#IP Cameras#PTZ Cameras#Night Vision Cameras#Security Technology#Reliable Surveillance#Advanced CCTV Features#Home Security#Commercial Security#Industrial Surveillance#Surveillance Solutions
0 notes
Text
Move To A Darker Place
This is a story of Man Vs. Machine.
---
Last March, my father attempted to file his Taxes.
My beloved father is a Boomer. Unlike most Boomers, my father is rather handy with technology because he was one of the people that had a not-insignificant hand in Developing a hell of a lot of it. He was studying Computer Science at Cal Poly before the computer science degree existed. I have many fond childhood memories of skipping through the aisles of various electronic and computer part warehouses while Dad described something that either terrified the staff or made them worship him as a God. He taught himself how to use his smartphone. Internationally.
So when he saw the option to file digitally with the IRS through the “ID.me” program, he leapt at the chance to celebrate the Federal Government finally entering the Digital Age.
It was all going swimmingly for about six hours, until he was ready to file and the system told him that it needed to verify his identity.
“Very Well.” said my father, a man unafraid of talking to himself and getting something out of the conversation. “It wouldn’t do for me to get someone else’s return.”
The System told him that it needed him to take a “Digital Image ID”.
a.k.a: A Selfie.
“A-ha!” Dad beams. Dad is very good at taking selfies. He immediately pulled out his phone, snapped one, and tried to upload it.
Please log into your Id.me Account and use the provided app to submit your Digital Image ID. The System clarified.
“Oh. You should have said so.” Dad pouted, but used his phone to log onto the ID.me account, do the six security verification steps and double-checked that the filing looked the same as it did on the desktop, gave the IRS like nine permissions on his phone, and held up the camera to take his Federal Privacy Invasion Selfie.
Please align your face to the indicated grid. Said The System, pulling up a futuristic green-web-of-polygons approximation.
“Ooh, very Star Trek. Gene Roddenberry would HATE this!” Dad said cheerfully, aligning his face to the grid. My father is a bit… cavalier, when it comes to matters of personal information and federal government, because he’s been on FBI watchlists since the late 60’s when he was protesting The Vietnam War and Ronald Regan before he’d broken containment.
Alas.
Anyway, there is very little information the federal government does not have on him already, but he’s as good at stalking the FBI as they are at stalking him, and had worked out a solution: He has something approaching a friendship with the local Federal Agent (Some guy named “Larry”. Allegedly), and got Larry hooked on Alternative Histories and Dad’s collection of carefully-researched “there is very likely buried treasure here” stories, and Larry is loath to bother his favorite Historical Fanfiction author too much.
But I digress.
After thinking for a minute, The System came back with an Error Message. Please remove glasses or other facial obstructions.
And here is where the real trouble began.
See, my father wears glasses that do substantially warp the appearance of his face, because he is so nearsighted that he is legally blind without them. His natural focal point is about 4 inches in front of his nose. While Dad can still take a selfie because he (approximately) knows where his phone is if it’s in his hand, he cannot see the alignment grid.
He should ask someone to take it for him! I hear the audience say. Yes, that would be the sane and reasonable thing to do, but Dad was attempting to do taxes at his residence in Fort Collins, while his immediate family was respectively in Denver, Texas and Canada. He tried calling our neighbors, who turned out to be in Uganda.
He looked down at the dog, Arwen, and her little criminal paws that can open doorknobs, but not operate cell phones.
She looked back at him, and farted.
“Well, I’ll give it a try, but if it gives me too much trouble, I’ll call Larry, and Larry can call the IRS about it.” Dad told her.
She continued to watch him. Arwen is an Australian Kelpie (a type of cattle-herding dog), going on 14 years old, deaf as a post and suffering from canine dementia now, but she still retains her natural instinct to Micromanage. She was also trained as a therapy dog, and even if she can’t hear my dad, still recognizes the body language of a man setting himself up for catastrophe.
So, squinting in the late afternoon light next to the back door, Dad attempted to line his face up with a grid he could only sort-of see, and took A Federal Selfie.
The System thought about it for a few moments.
Image Capture Failed: Insufficient Contrast. The System replied. Please move to a darker place.
“...Huh.” Dad frowned. “Alright.”
He moved to the middle of his office, away from the back door, lit only by the house lighting and indirect sunlight, and tried again.
Image Capture Failed. Please move to a darker place.
“What?” Dad asked the universe in general.
“Whuff.” Arwen warned him against sunk costs.
Dad ignored her and went into the bathroom, the natural habitat of the selfie. Surely, only being lit by a light fixture that hadn’t been changed since Dad was attempting to warn everyone about Regan would be suitably insufficient lighting for The System. It took some negotiating, because that bathroom is “Standing Room Only” not “Standing And Holding Your Arms Out In Front Of You Room”. He ended up taking the selfie in the shower stall.
As The System mulled over the latest attempt, Arwen shuffled over and kicked open the door to watch.
Image Capture Failed. Please Move to a Darker Place.
“Do you mean Spiritually?” Dad demanded.
“Whuff.” Arwen cautioned him again.
Determined to succeed, or at least get a different error message that may give him more information, Dad entered The Downstairs Guest Room. It is the darkest room in the house, as it is in the basement, and only has one legally-mandated-fire-escape window, which has blinds. Dad drew those blinds, turned off the lights and tried AGAIN.
Image Capture Failed. Please Move To A Darker Place.
“DO YOU WANT ME TO PHOTOGRAPH MYSELF INSIDE OF A CAVE??” Dad howled.
“WHUFF!” Arwen reprimanded him from under the pull-out bed in the room. It’s where she attempts to herd everyone when it’s thundering outside, so the space is called her ‘Safety Cave’.
Dad frowned at the large blurry shape that was The Safety Cave.
“Why not?” he asked, the prelude to many a Terrible Plan. With no small amount of spiteful and manic glee, Dad got down onto the floor, and army-crawled under the bed with Arwen to try One Last Time. Now in near-total darkness, he rolled on his side to be able to stretch his arms out, Arwen slobber-panting in his ear, and waited for the vague green blob of the Facial grid to appear.
This time, when he tapped the button, the flash cctivated.
“GOD DAMN IT!” Dad shouted, dropping the phone and rubbing his eyes and cursing to alleviate the pain of accidentally flash-banging himself. Arwen shuffled away from him under the bed, huffing sarcastically at him.
Image Capture Failed. Please move to a darker place.
“MOTHERFU- hang on.” Dad squinted. The System sounded strange. Distant and slightly muffled.
Dad squinted really hard, and saw the movement of Arwen crawling out from under the bed along the phone’s last known trajectory.
“ARWEN!” Dad shouted, awkwardly reverse-army crawling out from under the bed, using it to get to his feet and searching for his glasses, which had fallen out of his pocket under the bed, so by the time he was sighted again, Arwen had had ample time to remove The Offending Device.
He found her out in the middle of the back yard, the satisfied look of a Job Well Done on her face.
She did not have the phone.
“Arwen.” Dad glared. It’s a very good glare. Dad was a teacher for many years and used it to keep his class in order with sheer telepathically induced embarrassment, and his father once glared a peach tree into fecundity.
Arwen regarded him with the casual interest a hurricane might regard a sailboat tumbling out of its wake. She is a force of nature unto herself and not about to be intimidated by a half-blind house ape. She also has cataracts and might not be able to make out the glare.
“I GIVE UP!” Dad shouted, throwing his hands in the air and returning to the office to write to the IRS that their selfie software sucks ass. Pleased that she had gotten her desired result, Arwen followed him in.
To Dad’s immense surprise, the computer cheerfully informed him that his Federally Secure Selfie had been accepted, and that they had received and were now processing his return!
“What the FUCK?” Dad glared. “Oh well. If I’ve screwed it up, Larry can call me.”
---
I bring this up because recently, Dad received an interesting piece of mail.
It was a letter from the IRS, addressed to him, a nerve-wracking thing to recessive at the best of times. Instead of a complaint about Dad’s Selfie Skills, it was a letter congratulating him on using the new ID.me System. It thanked him for his help and expressed hopes he would use it again next year, and included the selfie that The System had finally decided to accept.
“You know, my dad used to complain about automation.” Dad sighed, staring at the image. “Incidentals my boy! My secretary saves the state of California millions of dollars a year catching small errors before they become massive ones! He’d say. Fought the human resources board about her pay every year. I used to think he was overestimating how bad machines were and underestimating human error, but you know? He was right.”
He handed me the image.
My father was, technically, in the image. A significant amount of the bottom right corner is taken up by the top of his forehead and silver hair.
Most of the image, the part with the facial-recognition markers on it, was composed of Arwen’s Alarmed and Disgusted Doggy face.
“Oh no!” I cackled. “Crap, does this mean you have to call the IRS and tell them you’re not a dog?”
“Probably.” Dad sighed. “I know who I’m gonna bother first though.” he said, taking out his phone (Dad did find his phone a few hours after Arwen absconded with it when mom called and the early spinach started ringing).
“Hey Larry!” Dad announced to the local federal agent. “You’re never gonna believe this. My dog filed my taxes!”
Larry considered this for a moment. “Is this the dog that stole my sandwich? Out of my locked car?” he asked suspiciously.
“The very same.” Dad grinned.
“Hm. Clever Girl.” Federal Agent Larry sighed. “I figured it was only a matter of time before she got into tax fraud.”
---
I'm a disabled artist making my living writing these stories. If you enjoy my stories, please consider supporting me on Ko-fi or Pre-ordering my Family Lore Book on Patreon. Thank you!
#Family Lore#Dogs#arwen#Arwen the Crime Dog#Taxes#Ronald Regan mention (derogatory)#long post under the cut#this one is funny this time#I could really use some extra tip money this month
9K notes
·
View notes
Text
The Role of AI and Machine Learning in Enhancing Diagnostic Accuracy
Digital Health: Transforming Modern Healthcare
Understanding Digital Health
Digital health signifies a groundbreaking convergence of technology with the healthcare sector. Utilizing digital tools, the medical field is undergoing a significant transformation in the way care is delivered, accessed, and managed. This shift encompasses telehealth, wearable technology, mobile health applications, and electronic health records (EHRs), all aimed at enhancing patient outcomes, increasing efficiency, and lowering costs.
Key Elements of Digital Health
Telehealth: Connecting Patients and Providers
Telehealth is a cornerstone of digital health, utilizing telecommunications technology to provide clinical services from a distance. This includes video consultations, remote monitoring, and virtual follow-ups. The advantages are substantial:
Accessibility: Quality healthcare reaches patients in remote or underserved areas without the need for travel.
Convenience: Reduces the necessity for in-person visits, saving time and resources.
Continuity of Care: Facilitates ongoing management of chronic conditions.
Wearable Technology: Real-Time Health Monitoring
Wearable technology such as fitness trackers, smartwatches, and biosensors play a critical role in monitoring various health metrics. These devices gather data on heart rate, physical activity, sleep patterns, and more, which is essential for:
Preventive Care: Detecting potential health issues early.
Personalized Treatment: Customizing treatments based on individual health data.
Patient Engagement: Encouraging proactive health management.
Mobile Health Applications: Health Management Simplified
Mobile health apps provide functionalities ranging from medication reminders to diet tracking and mental health support. They empower users with easy access to health information and management tools. Key benefits include:
Empowerment: Puts users in control of their health information and decisions.
Education: Offers access to valuable health resources and information.
Support: Facilitates communication with healthcare providers and support networks.
Electronic Health Records (EHRs): Consolidating Patient Information
EHRs are digital versions of patient charts and are fundamental to digital health. They offer comprehensive and accurate patient information accessible to authorized healthcare providers. The benefits include:
Care Coordination: Ensures all healthcare providers have access to the same information.
Accuracy: Reduces errors associated with manual record-keeping.
Efficiency: Streamlines workflows and enhances patient care management.
The Impact of Digital Health on Healthcare
Enhancing Patient Outcomes
Digital health technologies significantly improve patient outcomes. By enabling remote monitoring and early detection of health issues, these tools facilitate preventive care and timely interventions. Patients with chronic conditions benefit greatly from continuous monitoring and personalized treatment plans.
Boosting Healthcare Efficiency
The integration of digital health solutions enhances operational efficiency within healthcare systems. Telehealth, for instance, reduces the need for physical infrastructure, while EHRs streamline administrative processes, leading to cost savings and more efficient resource use.
Reducing Healthcare Costs
Innovations in digital health help reduce healthcare costs by minimizing in-person visits, decreasing hospital readmissions, and preventing the progression of chronic diseases through early intervention. Additionally, automated systems and telehealth services lessen the burden on healthcare providers, leading to more cost-effective care delivery.
Challenges and Solutions in Digital Health Adoption
Ensuring Data Privacy and Security
A primary concern in digital health is the privacy and security of patient data. Healthcare providers must ensure that digital systems comply with regulations such as HIPAA (Health Insurance Portability and Accountability Act) and employ robust cybersecurity measures to protect sensitive information.
Achieving Integration and Interoperability
Integrating digital health technologies into existing healthcare systems can be challenging. Ensuring interoperability between various digital tools and traditional systems is crucial for seamless data sharing and efficient care coordination. Solutions include adopting standardized protocols and investing in interoperable systems.
Promoting User Adoption and Training
Effective use of digital health technologies requires that both healthcare providers and patients are willing and able to use them. Comprehensive training and support systems are necessary to ensure users are comfortable and proficient with new technologies. Educational initiatives and user-friendly interfaces can significantly improve adoption rates.
The Future of Digital Health
The future of digital health looks promising, with ongoing advancements in artificial intelligence (AI), machine learning, and blockchain technology set to further revolutionize healthcare. AI and machine learning can enhance diagnostic accuracy and treatment personalization, while blockchain technology can ensure secure and transparent health data management.
Artificial Intelligence and Machine Learning
AI and machine learning algorithms can analyze vast amounts of data to identify patterns and predict health outcomes, leading to more accurate diagnoses and personalized treatment plans. These technologies have the potential to revolutionize areas such as radiology, pathology, and drug discovery.
Blockchain Technology
Blockchain offers a decentralized and secure method for managing health records, ensuring data integrity and privacy. By providing a transparent ledger of all transactions, blockchain can prevent data breaches and enhance trust in digital health systems.
Conclusion
Digital health is reshaping the healthcare landscape, offering unprecedented opportunities to improve patient care, enhance efficiency, and reduce costs. As technology continues to evolve, the integration of digital tools in healthcare will become increasingly essential. Embracing these innovations requires overcoming challenges related to data security, system integration, and user adoption. However, the potential benefits make it a worthwhile endeavor, promising a future where healthcare is more accessible, efficient, and personalized.
#Digital Health#Telemedicine#Wearable Devices#Mobile Health Apps#Electronic Health Records#Healthcare Technology#Patient Outcomes#Healthcare Efficiency#Preventive Healthcare#Personalized Medicine#Health Data Security#AI in Healthcare#Blockchain in Healthcare#Future of Healthcare#Health Monitoring#Remote Healthcare#Digital Health Solutions#Health Technology Integration#Healthcare Cost Reduction#EHR Systems
0 notes
Text
Peace of Mind in a Pocket: My Experience with the RFID Protector
In today's digital world, protecting our personal information is paramount. With the growing prevalence of contactless payment methods, the risk of electronic pickpocketing, also known as RFID skimming, becomes a concern. That's why I decided to invest in the RFID Protector, a product designed to safeguard my contactless cards.

Discreet Protection for Everyday Transactions
The RFID Protector is a slim and lightweight sleeve that easily fits into my wallet alongside my cards. It comes in various sizes to accommodate different card types, ensuring a comfortable and discreet addition to my everyday carry. The best part is that it doesn't interfere with the functionality of my contactless cards; I can still tap and pay with ease, knowing my information is shielded.
Blocking Unwanted Scans and Ensuring Security
The core function of the RFID Protector is to block unauthorized scans. The product utilizes a special material that creates a barrier, preventing radio waves from scanners from reaching the chip embedded in my contactless cards. This effectively shields my personal and financial information from potential thieves. While I haven't personally experienced any skimming attempts, the peace of mind this product offers is invaluable.
Multiple Layers of Protection for Added Security
Some RFID Protectors simply block radio waves, but the one I use boasts additional security features. It includes a layer that physically protects the card itself from bending or breaking, a common concern with contactless cards. Additionally, some versions offer a water-resistant layer for added protection against accidental spills or splashes. These additional features make the RFID Protector a well-rounded solution for safeguarding my cards.
A Convenient and Affordable Security Solution
The RFID Protector is a convenient and affordable way to enhance the security of my contactless cards. It's easy to use, integrates seamlessly with my existing wallet setup, and offers peace of mind without breaking the bank. For anyone who uses contactless payment methods, the RFID Protector is a worthwhile investment.
A Recommended Addition to Your Wallet
Overall, the RFID Protector has become an essential part of my wallet. It offers a discreet and effective solution for safeguarding my contactless cards, providing peace of mind during everyday transactions. While remaining vigilant is always important, the RFID Protector adds an extra layer of security in today's digital age. If you're looking for a convenient and affordable way to protect your contactless cards, I highly recommend the RFID Protector.
#RFID Blocking Sleeve#pen_spark#Contactless Card Protector#Anti-Skimming Wallet Insert#Digital Security Tool#Blocks Unauthorized Scans#Protects Against Electronic Pickpocketing#Safeguards Personal Information#Enhanced Contactless Payment Security#Discreet and Lightweight Design#Multiple Sizes for Different Cards#Water-Resistant Option#Affordable Security Solution#Easy to Use and Integrate with Wallet
0 notes
Text
Versatile Software Solution for Efficient Organization Management

PrideStudio is a versatile software solution designed for various organizations, boasting a user-friendly interface and robust data recovery tools. With over 20,000 global users across 100+ industries, it offers strategic KPI visualization dashboards and real-time data access. Key features include automation of departmental activities, enhanced workflow transparency, and electronic data security. The software's customization options, integration capabilities, and notification systems make it a reliable choice for businesses seeking efficiency and accountability.
For more Information visit: PrideStudio (pridesys.com)
Contact us:
E-mail: [email protected];
Phone: +8801550000003-8, 01550000035
#Versatile software solution#User-friendly interface#Data recovery tools#KPI visualization dashboards#Real-time data access#Departmental activities automation#Workflow transparency#Electronic data security#Customization options#Integration capabilities
0 notes
Text

123 Repairshop is dedicated to data destruction as part of our commitment to data protection and privacy. We understand the importance of securely disposing of sensitive information to prevent any unauthorized access or data breaches. Our comprehensive approach ensures that your data is protected throughout the entire repair and recycling process.
When it comes to data destruction, our technicians follow strict protocols to ensure the complete and irreversible erasure of data from devices. We utilize industry-leading software and techniques to securely wipe all data, leaving no traces behind. This process applies to both personal devices and business equipment, guaranteeing the highest level of data security.
In addition to data destruction, 123 Repairshop emphasizes environmental sustainability and responsible e-waste management. We offer electronic recycling options for old, damaged, or obsolete devices. Our technicians meticulously disassemble each item, separating recyclable components such as metals, plastics, circuit boards, and batteries. Through our partnerships with certified recycling facilities, we ensure that these materials are appropriately treated and processed, minimizing the environmental impact of electronic waste.
By choosing 123 Repairshop, you not only receive top-quality repairs and data protection, but you also contribute to a healthier planet. Our commitment to environmental sustainability, social responsibility, and data protection aligns with our belief in making a positive impact. We strive to support educational institutions, promote eco-friendly practices, and safeguard your valuable data.
Whether you need repairs, data destruction, or electronic recycling, we are your trusted partner in achieving your needs while making a positive impact on the world around us. At 123 Repairshop, we combine exceptional service with environmentally friendly practices, social responsibility, and data protection. Join us in our mission to create a healthier and more sustainable future by choosing our services.
#Vendor Certification#Technology Recycling#Sustainable Technology Solutions#Sustainable Practices#sustainable education#Student Internship Program#School Partnerships#Responsible Procurement Community Engagement#Recycling Partnership#Minority and Women-Owned Business#Hands-on Experience Training#Environmental Sustainability#Electronic Waste Management#Data Security Technology#Cost Savings Corporate Social Responsibility
0 notes
Text
youtube
Beyond Automotive – Infineon is Your Industrial Partner: Electronica 2022
https://www.futureelectronics.com/m/infineon. The IFX Automotive portfolio is perfect where applications require higher safety, reliability, and robust semiconductor solutions. Watch what is empowering this change and how the broad Infineon portfolio can help reduce your time to market with their complete solutions and reference designs. https://youtu.be/5jjmf3NTOak
#Electronica 2022#Electronica#Future Electronics#Security Solutions#Infineon#automotive#automation#safety protocols#IFX Automotive#semiconductor solutions#Rajesh Naik#Youtube
1 note
·
View note
Video
youtube
Beyond Automotive – Infineon is Your Industrial Partner : Electronica 2022
https://www.futureelectronics.com/m/infineon. The IFX Automotive portfolio is perfect where applications require higher safety, reliability, and robust semiconductor solutions. Watch what is empowering this change and how the broad Infineon portfolio can help reduce your time to market with their complete solutions and reference designs.
1 note
·
View note
Text
HbeonLabs Technologies is an electronic design and embedded manufacturing company in India. We cater our client base with embedded systems, hardware, software, manufacturing and assembly of products.For more information visit our website:-www.hbeonlabs.com
#Internet of Things#industry 4.0#iot solution provider#iot software#remote iot device platforms#GSM Security System#remote monitoring system#Smart Street Light#pcb design companies#embedded system design#iot companies in india#iot application development company#electronic manufacturing companies#iot devices#iot applications#smart city solutions#smart city companies#electronics companies in india#embedded companies in india
0 notes
Text
#Echecks#Electronic checks#Merchant services#Payment processing#Digital payments#ACH (Automated Clearing House)#Online payments#Payment gateways#Payment solutions#E-commerce payments#Payment processors#Secure transactions#Electronic funds transfer#Payment technology#Payment verification#Payment acceptance#Digital banking#Transaction fees#Fraud prevention#Payment authorization
2 notes
·
View notes
Text
The Role of Blockchain in Supply Chain Management: Enhancing Transparency and Efficiency

Blockchain technology, best known for powering cryptocurrencies like Bitcoin and Ethereum, is revolutionizing various industries with its ability to provide transparency, security, and efficiency. One of the most promising applications of blockchain is in supply chain management, where it offers solutions to longstanding challenges such as fraud, inefficiencies, and lack of visibility. This article explores how blockchain is transforming supply chains, its benefits, key use cases, and notable projects, including a mention of Sexy Meme Coin.
Understanding Blockchain Technology
Blockchain is a decentralized ledger technology that records transactions across a network of computers. Each transaction is added to a block, which is then linked to the previous block, forming a chain. This structure ensures that the data is secure, immutable, and transparent, as all participants in the network can view and verify the recorded transactions.
Key Benefits of Blockchain in Supply Chain Management
Transparency and Traceability: Blockchain provides a single, immutable record of all transactions, allowing all participants in the supply chain to have real-time visibility into the status and history of products. This transparency enhances trust and accountability among stakeholders.
Enhanced Security: The decentralized and cryptographic nature of blockchain makes it highly secure. Each transaction is encrypted and linked to the previous one, making it nearly impossible to alter or tamper with the data. This reduces the risk of fraud and counterfeiting in the supply chain.
Efficiency and Cost Savings: Blockchain can automate and streamline various supply chain processes through smart contracts, which are self-executing contracts with the terms of the agreement directly written into code. This automation reduces the need for intermediaries, minimizes paperwork, and speeds up transactions, leading to significant cost savings.
Improved Compliance: Blockchain's transparency and traceability make it easier to ensure compliance with regulatory requirements. Companies can provide verifiable records of their supply chain activities, demonstrating adherence to industry standards and regulations.
Key Use Cases of Blockchain in Supply Chain Management
Provenance Tracking: Blockchain can track the origin and journey of products from raw materials to finished goods. This is particularly valuable for industries like food and pharmaceuticals, where provenance tracking ensures the authenticity and safety of products. For example, consumers can scan a QR code on a product to access detailed information about its origin, journey, and handling.
Counterfeit Prevention: Blockchain's immutable records help prevent counterfeiting by providing a verifiable history of products. Luxury goods, electronics, and pharmaceuticals can be tracked on the blockchain to ensure they are genuine and have not been tampered with.
Supplier Verification: Companies can use blockchain to verify the credentials and performance of their suppliers. By maintaining a transparent and immutable record of supplier activities, businesses can ensure they are working with reputable and compliant partners.
Streamlined Payments and Contracts: Smart contracts on the blockchain can automate payments and contract executions, reducing delays and errors. For instance, payments can be automatically released when goods are delivered and verified, ensuring timely and accurate transactions.
Sustainability and Ethical Sourcing: Blockchain can help companies ensure their supply chains are sustainable and ethically sourced. By providing transparency into the sourcing and production processes, businesses can verify that their products meet environmental and social standards.
Notable Blockchain Supply Chain Projects
IBM Food Trust: IBM Food Trust uses blockchain to enhance transparency and traceability in the food supply chain. The platform allows participants to share and access information about the origin, processing, and distribution of food products, improving food safety and reducing waste.
VeChain: VeChain is a blockchain platform that focuses on supply chain logistics. It provides tools for tracking products and verifying their authenticity, helping businesses combat counterfeiting and improve operational efficiency.
TradeLens: TradeLens, developed by IBM and Maersk, is a blockchain-based platform for global trade. It digitizes the supply chain process, enabling real-time tracking of shipments and reducing the complexity of cross-border transactions.
Everledger: Everledger uses blockchain to track the provenance of high-value assets such as diamonds, wine, and art. By creating a digital record of an asset's history, Everledger helps prevent fraud and ensures the authenticity of products.
Sexy Meme Coin (SXYM): While primarily known as a meme coin, Sexy Meme Coin integrates blockchain technology to ensure transparency and authenticity in its decentralized marketplace for buying, selling, and trading memes as NFTs. Learn more about Sexy Meme Coin at Sexy Meme Coin.
Challenges of Implementing Blockchain in Supply Chains
Integration with Existing Systems: Integrating blockchain with legacy supply chain systems can be complex and costly. Companies need to ensure that blockchain solutions are compatible with their existing infrastructure.
Scalability: Blockchain networks can face scalability issues, especially when handling large volumes of transactions. Developing scalable blockchain solutions that can support global supply chains is crucial for widespread adoption.
Regulatory and Legal Considerations: Blockchain's decentralized nature poses challenges for regulatory compliance. Companies must navigate complex legal landscapes to ensure their blockchain implementations adhere to local and international regulations.
Data Privacy: While blockchain provides transparency, it also raises concerns about data privacy. Companies need to balance the benefits of transparency with the need to protect sensitive information.
The Future of Blockchain in Supply Chain Management
The future of blockchain in supply chain management looks promising, with continuous advancements in technology and increasing adoption across various industries. As blockchain solutions become more scalable and interoperable, their impact on supply chains will grow, enhancing transparency, efficiency, and security.
Collaboration between technology providers, industry stakeholders, and regulators will be crucial for overcoming challenges and realizing the full potential of blockchain in supply chain management. By leveraging blockchain, companies can build more resilient and trustworthy supply chains, ultimately delivering better products and services to consumers.
Conclusion
Blockchain technology is transforming supply chain management by providing unprecedented levels of transparency, security, and efficiency. From provenance tracking and counterfeit prevention to streamlined payments and ethical sourcing, blockchain offers innovative solutions to long-standing supply chain challenges. Notable projects like IBM Food Trust, VeChain, TradeLens, and Everledger are leading the way in this digital revolution, showcasing the diverse applications of blockchain in supply chains.
For those interested in exploring the playful and innovative side of blockchain, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to learn more and join the community.
#crypto#blockchain#defi#digitalcurrency#ethereum#digitalassets#sexy meme coin#binance#cryptocurrencies#blockchaintechnology#bitcoin#etf
264 notes
·
View notes
Text
There's a whole lot of towns out there that you'll never visit. Most of them are chock full of people you'll never meet. Tulsa, for example. Never been there, might never go there. And that makes me a little sad.
Sure, I only have enough time on this earth to visit so many towns. And when I'm there, I don't have enough time to interrogate every single one of the locals to see if, say, any of them have a set of Mopar F-body windshield wiper linkages sitting in the back of their garage. They'll just go to waste, damned to irrelevance by my lack of time. That's what the MBAs call a "market inefficiency."
The internet has helped, sure, but you can only demand what other people have supplied. Any quick browse on a model-specific forum is full of lonely folks crying out to the heavens for a specific piece of trim, or an entire automatic transmission, that they will never receive. And it's a lot of work to put that stuff up for sale. Who knows what's actually inside that weird pile of oil-stained gewgaws that Pawpaw left behind before he joined that alien cult and drank all that Flavor-Aid? His surviving next-of-kin sure don't know the difference between a 4.11 and a 3.90 rear end, nor are they willing to teach themselves that information in order to list it on eBay for twenty bucks.
Don't worry, though, I have a solution. That solution is that the Boston Dynamics warehouse is not secured very well. Their robots are powered by a two-stroke lawnmower engine: it's like they wanted me to show up with a turbine-generator-powered plasma cutter and chop right through the rebar holding the walls of their robot storage lockup together. After that, it was a quick couple of dozen trips to the local electronics store to get the right USB-to-serial cable, and I soon had my harem of semi-autonomous Parts-Seeking Drones® roving the backwoods of America.
So, if you see a lanky, creaking doglike shape lurking outside your yard tonight, smelling oddly of pre-mix and human arterial blood, let it in your garage. All it wants to do is scan your spare parts so I can find that goddamn last piece of dash trim for the cruise control lever on my Volare. Don't worry: I won't have the robots kill you if you decide not to sell it to me after all. It would be hypocritical of me to judge another hoarder. We'll have coffee when I come see your town for the first time! We can trade junk and be best friends and call each other on the phone afterward and talk about nitrous oxide. No promises on what the robots will do if they search your entire property and don't find any Plymouth Volare stuff, though. I forgot to program that part before I let them out of radio range.
247 notes
·
View notes
Text
Personalized Treatment Plans through Data from Wearable Health Devices
Digital Health: Transforming Modern Healthcare
Understanding Digital Health
Digital health signifies a groundbreaking convergence of technology with the healthcare sector. Utilizing digital tools, the medical field is undergoing a significant transformation in the way care is delivered, accessed, and managed. This shift encompasses telehealth, wearable technology, mobile health applications, and electronic health records (EHRs), all aimed at enhancing patient outcomes, increasing efficiency, and lowering costs.
Key Elements of Digital Health
Telehealth: Connecting Patients and Providers
Telehealth is a cornerstone of digital health, utilizing telecommunications technology to provide clinical services from a distance. This includes video consultations, remote monitoring, and virtual follow-ups. The advantages are substantial:
Accessibility: Quality healthcare reaches patients in remote or underserved areas without the need for travel.
Convenience: Reduces the necessity for in-person visits, saving time and resources.
Continuity of Care: Facilitates ongoing management of chronic conditions.
Wearable Technology: Real-Time Health Monitoring
Wearable technology such as fitness trackers, smartwatches, and biosensors play a critical role in monitoring various health metrics. These devices gather data on heart rate, physical activity, sleep patterns, and more, which is essential for:
Preventive Care: Detecting potential health issues early.
Personalized Treatment: Customizing treatments based on individual health data.
Patient Engagement: Encouraging proactive health management.
Mobile Health Applications: Health Management Simplified
Mobile health apps provide functionalities ranging from medication reminders to diet tracking and mental health support. They empower users with easy access to health information and management tools. Key benefits include:
Empowerment: Puts users in control of their health information and decisions.
Education: Offers access to valuable health resources and information.
Support: Facilitates communication with healthcare providers and support networks.
Electronic Health Records (EHRs): Consolidating Patient Information
EHRs are digital versions of patient charts and are fundamental to digital health. They offer comprehensive and accurate patient information accessible to authorized healthcare providers. The benefits include:
Care Coordination: Ensures all healthcare providers have access to the same information.
Accuracy: Reduces errors associated with manual record-keeping.
Efficiency: Streamlines workflows and enhances patient care management.
The Impact of Digital Health on Healthcare
Enhancing Patient Outcomes
Digital health technologies significantly improve patient outcomes. By enabling remote monitoring and early detection of health issues, these tools facilitate preventive care and timely interventions. Patients with chronic conditions benefit greatly from continuous monitoring and personalized treatment plans.
Boosting Healthcare Efficiency
The integration of digital health solutions enhances operational efficiency within healthcare systems. Telehealth, for instance, reduces the need for physical infrastructure, while EHRs streamline administrative processes, leading to cost savings and more efficient resource use.
Reducing Healthcare Costs
Innovations in digital health help reduce healthcare costs by minimizing in-person visits, decreasing hospital readmissions, and preventing the progression of chronic diseases through early intervention. Additionally, automated systems and telehealth services lessen the burden on healthcare providers, leading to more cost-effective care delivery.
Challenges and Solutions in Digital Health Adoption
Ensuring Data Privacy and Security
A primary concern in digital health is the privacy and security of patient data. Healthcare providers must ensure that digital systems comply with regulations such as HIPAA (Health Insurance Portability and Accountability Act) and employ robust cybersecurity measures to protect sensitive information.
Achieving Integration and Interoperability
Integrating digital health technologies into existing healthcare systems can be challenging. Ensuring interoperability between various digital tools and traditional systems is crucial for seamless data sharing and efficient care coordination. Solutions include adopting standardized protocols and investing in interoperable systems.
Promoting User Adoption and Training
Effective use of digital health technologies requires that both healthcare providers and patients are willing and able to use them. Comprehensive training and support systems are necessary to ensure users are comfortable and proficient with new technologies. Educational initiatives and user-friendly interfaces can significantly improve adoption rates.
The Future of Digital Health
The future of digital health looks promising, with ongoing advancements in artificial intelligence (AI), machine learning, and blockchain technology set to further revolutionize healthcare. AI and machine learning can enhance diagnostic accuracy and treatment personalization, while blockchain technology can ensure secure and transparent health data management.
Artificial Intelligence and Machine Learning
AI and machine learning algorithms can analyze vast amounts of data to identify patterns and predict health outcomes, leading to more accurate diagnoses and personalized treatment plans. These technologies have the potential to revolutionize areas such as radiology, pathology, and drug discovery.
Blockchain Technology
Blockchain offers a decentralized and secure method for managing health records, ensuring data integrity and privacy. By providing a transparent ledger of all transactions, blockchain can prevent data breaches and enhance trust in digital health systems.
Conclusion
Digital health is reshaping the healthcare landscape, offering unprecedented opportunities to improve patient care, enhance efficiency, and reduce costs. As technology continues to evolve, the integration of digital tools in healthcare will become increasingly essential. Embracing these innovations requires overcoming challenges related to data security, system integration, and user adoption. However, the potential benefits make it a worthwhile endeavor, promising a future where healthcare is more accessible, efficient, and personalized.
#Digital Health#Telemedicine#Wearable Devices#Mobile Health Apps#Electronic Health Records#Healthcare Technology#Patient Outcomes#Healthcare Efficiency#Preventive Healthcare#Personalized Medicine#Health Data Security#AI in Healthcare#Blockchain in Healthcare#Future of Healthcare#Health Monitoring#Remote Healthcare#Digital Health Solutions#Health Technology Integration#Healthcare Cost Reduction#EHR Systems
0 notes
Text

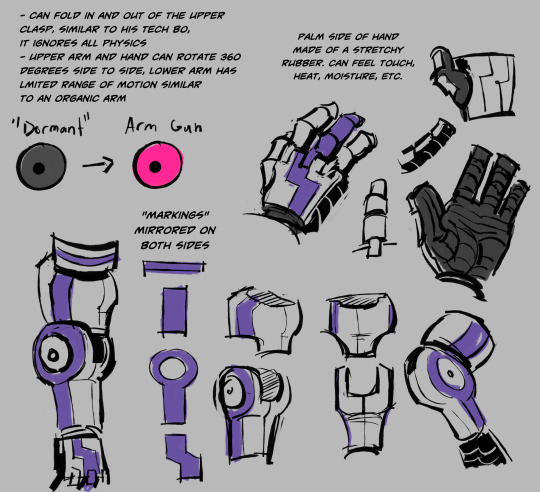


realized i never posted donnie's updated ref, which is a crime
- his arm is integrated into his nervous system and cannot be removed without causing extreme pain. this is necessary so he can have dexterity when handling delicate electronics, or to make sure what he's touching isn't hot enough to damage it, etc.
- his leg prosthetic is not integrated, it can be removed and is collapsible.
- he recieved the scar on his plastron while trying to defend raph in the raid on their lair. this is what inspires his casual armor.
- donnie's full mech suit is v1.5, since his prototype armor didn't pan out. it was more iron man-esque, covering him head to toe in metal. it was too slow, and that cost him his arm.
- he's perpetually split between multiple fields of science (botany, engineering, robotics, biology) and handles much of the designs for weapons, airships, armor, as well as updating the resistance base. he has a separate team to handle manufacturing and maintenance, but he is incredibly busy at all times, never slowing down.
- the apocalypse makes him strangely calm. with the worst already come to pass, he is fully in solution mode. as long as what he's doing keeps everyone alive, helps people survive, brings them any amount of security, he clings to that as a reason to do (to give) as much as he does.
#my art#bad future#i will give him more story beats later#i have some drafted up. its all coming together#but i have a lot of details to iron out..
425 notes
·
View notes