#Enabled Financial Software
Explore tagged Tumblr posts
Text
Musk’s DOGE seeks access to personal taxpayer data, raising alarm at IRS
Elon Musk’s U.S. DOGE Service is seeking access to a heavily-guarded Internal Revenue Service system that includes detailed financial information about every taxpayer, business and nonprofit in the country, according to two people familiar with the activities, sparking alarm within the tax agency. Under pressure from the White House, the IRS is considering a memorandum of understanding that would give DOGE officials broad access to tax-agency systems, property and datasets. Among them is the Integrated Data Retrieval System, or IDRS, which enables tax agency employees to access IRS accounts — including personal identification numbers — and bank information. It also lets them enter and adjust transaction data and automatically generate notices, collection documents and other records. IDRS access is extremely limited — taxpayers who have had their information wrongfully disclosed or even inspected are entitled by law to monetary damages — and the request for DOGE access has raised deep concern within the IRS, according to three people familiar with internal agency deliberations who, like others in this report, spoke on the condition of anonymity to discuss private conversations. [...] It’s highly unusual to grant political appointees access to personal taxpayer data, or even programs adjacent to that data, experts say. IRS commissioners traditionally do not have IDRS access. The same goes for the national taxpayer advocate, the agency’s internal consumer watchdog, according to Nina Olson, who served in the role from 2001 to 2019. “The information that the IRS has is incredibly personal. Someone with access to it could use it and make it public in a way, or do something with it, or share it with someone else who shares it with someone else, and your rights get violated,” Olson said. A Trump administration official said DOGE personnel needed IDRS access because DOGE staff are working to “eliminate waste, fraud, and abuse, and improve government performance to better serve the people.” [...] Gavin Kliger, a DOGE software engineer, arrived unannounced at IRS headquarters on Thursday and was named senior adviser to the acting commissioner. IRS officials were told to treat Kliger and other DOGE officials as contractors, two people familiar said.
the holocaust denying 25-year-old neonazi now has access to your bank information
72 notes
·
View notes
Text
April 11, 2025
HEATHER COX RICHARDSON
APR 12
READ IN APP
On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command.
Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem.
Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors. Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?”
The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.”
The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
—
16 notes
·
View notes
Text

Matt Davies
* * * *
LETTERS FROM AN AMERICAN
April 11, 2025
Heather Cox Richardson
Apr 12, 2025
On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command.
Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem.
Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors. Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?”
The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.”
The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#political cartoons#Matt Davies#The Big Chill#Heather Cox Richardson#Letters from An American#personal data#the right to privacy#identity theft#mistaken identity#SCOTUS#secretary of defense#homeland security#incompetence#data mining#data weaponization
15 notes
·
View notes
Text
Asking For Donations — This Will Likely Be My First & Last Time Doing This
Cshpp - $d1pl0mat

Hey all, I'm a neurodivergent transfeminine person who could use a bit of a financial boost. I've been unemployed for over a year due to autistic burnout and a lot of life circumstances piling on in a short time. Thankfully, things seem to be settling into place and good things are on the horizon, but I need a bit of a push to get there.
The Good: I currently have an apprenticeship lined up that will pay me well and get me into my desired field of software development. I only have to do a behavioral interview (which I expect to pass with flying colors) and I'll be starting training next month. This will enable me to move in with my partners and largely get my life back on track.
The Not-So-Good: That still leaves me with about a month and a half of not getting paid yet. Like I said above, I've been unemployed for just over a year, taking odd jobs and helping my partner(s) with finances as a way of keeping afloat. However, the family I'm living with has their food assistance on hold and I'm unsure when that problem will subside. This is on top of running low on gas, medical weed, and with a phone bill due in the very near future.
This request isn't quite as urgent as some of the others you might see, but if you have $10-20 to throw my way I'd be insanely appreciative. I'm seeking a total of ~$300 to be solidly set with groceries, gas, meds, my phone bill, and a little overhead for incidentals.
Thank you in advance <3
44 notes
·
View notes
Text

House of Huawei by Eva Dou
A fascinating insight into a Chinese telecoms giant and its detractors
Huawei is not exactly a household name. If you’ve heard of it, you either follow the smartphone market closely – it is the main China-based manufacturer of high-end phones – or else consume a lot of news, because the company is at the centre of an ongoing US-China trade war.
But this enormous business is one of the world’s biggest producers of behind-the-scenes equipment that enables fibre broadband, 4G and 5G phone networks. Its hardware is inside communications systems across the world.
That has prompted alarm from US lawmakers of both parties, who accuse Huawei of acting as an agent for China’s government and using its technology for espionage. The company insists it merely complies with the local laws wherever it operates, just like its US rivals. Nevertheless, its equipment has been ripped out of infrastructure in the UK at the behest of the government, its execs and staffers have been arrested across the world, and it has been pilloried for its involvement in China’s oppression of Uyghur Muslims in Xinjiang.
Into this murky world of allegation and counter-allegation comes the veteran telecoms reporter Eva Dou. Her book chronicles the history of Huawei since its inception, as well as the lives of founder Ren Zhengfei and his family, starting with the dramatic 2019 arrest of his daughter Meng Wanzhou, Huawei’s chief financial officer, at the behest of US authorities.
Dou’s command of her subject is indisputable and her book is meticulous and determinedly even-handed. House of Huawei reveals much, but never speculates or grandstands – leaving that to the politicians of all stripes for whom hyperbole about Huawei comes more easily.
At its core, this book is the history of a large, successful business. That doesn’t mean it’s boring, though: there’s the story of efforts to haul 5G equipment above Everest base camp in order to broadcast the Beijing Olympics torch relay. We hear about the early efforts of Ren and his team, working around the clock in stiflingly hot offices, to make analogue telephone network switches capable of routing up to 10,000 calls; and gain insights into the near-impossible political dance a company must perform in order to operate worldwide without falling foul of the changing desires of China’s ruling Communist party.
Dou makes us better equipped to consider questions including: is this a regular company, or an extension of the Chinese state? How safe should other countries feel about using Huawei equipment? Is China’s exploitation of its technology sector really that different to the way the US authorities exploited Google, Facebook and others, as revealed by Edward Snowden?
Early in Huawei’s history, Ren appeared to give the game away in remarks to the then general secretary of the Communist party. “A country without its own program-controlled switches is like one without an army,” he argued, making the case for why the authorities should support his company’s growth. “Its software must be held in the hands of the Chinese government.”
But for each damning event, there is another that introduces doubt. The book reveals an arrangement from when Huawei operated in the UK that gave GCHQ unprecedented access to its source code and operations centre. US intelligence agencies seemed as able to exploit Huawei equipment for surveillance purposes as China’s. While Huawei’s equipment was certainly used to monitor Uyghur Muslims in Xinjiang, it was hardware from the US company Cisco that made China’s so-called Great Firewall possible.
Anyone hoping for definitive answers will not find them here, but the journey is far from wasted. The intricate reporting of Huawei, in all its ambiguity and complexity, sheds much light on the murky nature of modern geopolitics. The people who shout loudest about Huawei don’t know more than anyone else about it. Eva Dou does.
Daily inspiration. Discover more photos at Just for Books…?
12 notes
·
View notes
Text
Switch games will be playable on Switch successor - Gematsu

Switch games will be playable on the successor to Switch, Nintendo president Shuntaro Furukawa said during the company’s second quarter financial results and corporate management policy briefing for the fiscal year ending March 2025.
“This is Furukawa,” Furukawa said in a summary tweet. “At today’s Corporate Management Policy Briefing, we announced that Nintendo Switch software will also be playable on the successor to Nintendo Switch. Nintendo Switch Online will be available on the successor to Nintendo Switch as well. Further information about the successor to Nintendo Switch, including its compatibility with Nintendo Switch, will be announced at a later date.”
As previously stated, the successor to Switch will be announced within this fiscal year, which ends on March 31, 2025.
Here is the full content of the corporate management policy briefing regarding the successor to Switch:
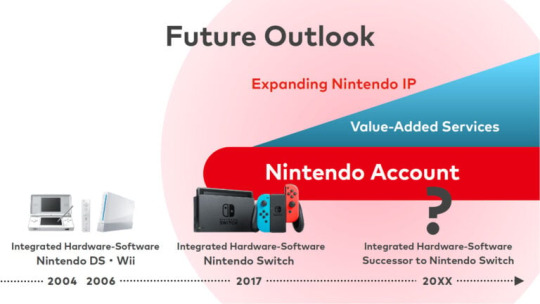
“Until Nintendo Switch, there was no easy way to have consumers’ purchase and gameplay histories carry over across platform generations. As a result, our relationship with the consumers was interrupted when a new system was purchased.”
“The introduction of Nintendo Account made it possible to tie consumers’ history to their personal account, enabling Nintendo to maintain a continuous relationship with the consumers across platform generations.”
“We have communicated that we plan on making an announcement regarding the successor to Nintendo Switch during this fiscal year. We believe that it is important for Nintendo’s future to make use of Nintendo Account and carry over the good relationship that we have built with the over 100 million annual playing users on Nintendo Switch to its successor.”
“Thus, we will make Nintendo Switch Online, a service based on Nintendo Account, available on the successor to Nintendo Switch.”

“Furthermore, Nintendo Switch software will also be playable on the successor to Nintendo Switch.”
“In addition to being able to play Nintendo Switch software they currently own, consumers will be able to choose their next purchase from a broad selection of titles released for Nintendo Switch.”
“Further information about the successor to Nintendo Switch, including its compatibility with Nintendo Switch I explained today, will be announced at a later date.”
17 notes
·
View notes
Text
In a stunning revelation Monday night during a tele-town hall with Wisconsin voters, Elon Musk warned that an arrest is “imminent” in a massive Social Security fraud scheme involving the stolen identities of over 400,000 Americans.
The theft, Musk claimed, is part of a sophisticated financial theft operation tied not only to illegal immigrants defrauding U.S. social welfare systems—but also to widespread voter fraud enabled by the Democrat Party’s open-borders agenda.
Speaking directly to voters in the Badger State, Musk painted a grim picture of a government drowning in incompetence and corruption.
“The government has got the thorniest computer problem I’ve ever seen,” he said.
“Thousands of systems—many of them are very, very old systems. Some of the software is older than me.”
He slammed decades-long boondoggles like the IRS modernization project, started in 1995, which bureaucrats perpetually claim is “five years away” from completion. “These projects are just ridiculous,” Musk said.
7 notes
·
View notes
Text

Nintendo president Shuntaro Furukawa said during the company’s second quarter financial results and corporate management policy briefing for the fiscal year ending March 2025 that the Nintendo Switch games will be playable on the successor to Nintendo Switch.
This is Furukawa. At today's Corporate Management Policy Briefing, we announced that Nintendo Switch software will also be playable on the successor to Nintendo Switch. Nintendo Switch Online will be available on the successor to Nintendo Switch as well. Further information about the successor to Nintendo Switch, including its compatibility with Nintendo Switch, will be announced at a later date.
Full content of the corporate management policy briefing regarding the successor to Switch:

“Until Nintendo Switch, there was no easy way to have consumers’ purchase and gameplay histories carry over across platform generations. As a result, our relationship with the consumers was interrupted when a new system was purchased.”
“The introduction of Nintendo Account made it possible to tie consumers’ history to their personal account, enabling Nintendo to maintain a continuous relationship with the consumers across platform generations.”
“We have communicated that we plan on making an announcement regarding the successor to Nintendo Switch during this fiscal year. We believe that it is important for Nintendo’s future to make use of Nintendo Account and carry over the good relationship that we have built with the over 100 million annual playing users on Nintendo Switch to its successor.”
“Thus, we will make Nintendo Switch Online, a service based on Nintendo Account, available on the successor to Nintendo Switch.”

“Furthermore, Nintendo Switch software will also be playable on the successor to Nintendo Switch.”
“In addition to being able to play Nintendo Switch software they currently own, consumers will be able to choose their next purchase from a broad selection of titles released for Nintendo Switch.”
“Further information about the successor to Nintendo Switch, including its compatibility with Nintendo Switch I explained today, will be announced at a later date.”
13 notes
·
View notes
Text
The hacker ecosystem in Russia, more than perhaps anywhere else in the world, has long blurred the lines between cybercrime, state-sponsored cyberwarfare, and espionage. Now an indictment of a group of Russian nationals and the takedown of their sprawling botnet offers the clearest example in years of how a single malware operation allegedly enabled hacking operations as varied as ransomware, wartime cyberattacks in Ukraine, and spying against foreign governments.
The US Department of Justice today announced criminal charges today against 16 individuals law enforcement authorities have linked to a malware operation known as DanaBot, which according to a complaint infected at least 300,000 machines around the world. The DOJ’s announcement of the charges describes the group as “Russia-based,” and names two of the suspects, Aleksandr Stepanov and Artem Aleksandrovich Kalinkin, as living in Novosibirsk, Russia. Five other suspects are named in the indictment, while another nine are identified only by their pseudonyms. In addition to those charges, the Justice Department says the Defense Criminal Investigative Service (DCIS)—a criminal investigation arm of the Department of Defense—carried out seizures of DanaBot infrastructure around the world, including in the US.
Aside from alleging how DanaBot was used in for-profit criminal hacking, the indictment also makes a rarer claim—it describes how a second variant of the malware it says was used in espionage against military, government, and NGO targets. “Pervasive malware like DanaBot harms hundreds of thousands of victims around the world, including sensitive military, diplomatic, and government entities, and causes many millions of dollars in losses,” US attorney Bill Essayli wrote in a statement.
Since 2018, DanaBot—described in the criminal complaint as “incredibly invasive malware”—has infected millions of computers around the world, initially as a banking trojan designed to steal directly from those PCs' owners with modular features designed for credit card and cryptocurrency theft. Because its creators allegedly sold it in an “affiliate” model that made it available to other hacker groups for $3,000 to $4,000 a month, however, it was soon used as a tool to install different forms of malware in a broad array of operations, including ransomware. Its targets, too, quickly spread from initial victims in Ukraine, Poland, Italy, Germany, Austria, and Australia to US and Canadian financial institutions, according to an analysis of the operation by cybersecurity firm Crowdstrike.
At one point in 2021, according to Crowdstrike, Danabot was used in a software supply-chain attack that hid the malware in a javascript coding tool called NPM with millions of weekly downloads. Crowdstrike found victims of that compromised tool across the financial service, transportation, technology, and media industries.
That scale and the wide variety of its criminal uses made DanaBot “a juggernaut of the e-crime landscape,” according to Selena Larson, a staff threat researcher at cybersecurity firm Proofpoint.
More uniquely, though, DanaBot has also been used at times for hacking campaigns that appear to be state-sponsored or linked to Russian government agency interests. In 2019 and 2020, it was used to target a handful of Western government officials in apparent espionage operations, according to the DOJ's indictment. According to Proofpoint, the malware in those instances was delivered in phishing messages that impersonated the Organization for Security and Cooperation in Europe and a Kazakhstan government entity.
Then, in the early weeks of Russia's full-scale invasion of Ukraine, which began in February 2022, DanaBot was used to install a distributed denial-of-service (DDoS) tool onto infected machines and launch attacks against the webmail server of the Ukrainian Ministry of Defense and National Security and Defense Council of Ukraine.
All of that makes DanaBot a particularly clear example of how cybercriminal malware has allegedly been adopted by Russian state hackers, Proofpoint's Larson says. “There have been a lot of suggestions historically of cybercriminal operators palling around with Russian government entities, but there hasn't been a lot of public reporting on these increasingly blurred lines,” says Larson. The case of DanaBot, she says, “is pretty notable, because it's public evidence of this overlap where we see e-crime tooling used for espionage purposes.”
In the criminal complaint, DCIS investigator Elliott Peterson—a former FBI agent known for his work on the investigation into the creators of the Mirai botnet—alleges that some members of the DanaBot operation were identified after they infected their own computers with the malware. Those infections may have been for the purposes of testing the trojan, or may have been accidental, according to Peterson. Either way, they resulted in identifying information about the alleged hackers ending up on DanaBot infrastructure that DCIS later seized. “The inadvertent infections often resulted in sensitive and compromising data being stolen from the actor's computer by the malware and stored on DanaBot servers, including data that helped identify members of the DanaBot organization,” Peterson writes.
The operators of DanaBot remain at large, but the takedown of a large-scale tool in so many forms of Russian-origin hacking—both state-sponsored and criminal—represents a significant milestone, says Adam Meyers, who leads threat intelligence research at Crowdstrike.
“Every time you disrupt a multiyear operation, you're impacting their ability to monetize it. It also creates a bit of a vacuum, and somebody else is going to step up and take that place,” Meyers says. “But the more we can disrupt them, the more we keep them on their back heels. We should rinse and repeat and go find the next target.”
4 notes
·
View notes
Text
MifiadaHome Starting a Brand | AI in Brand Marketing: Can AI Pave the Path to Social Media Millions? Episode 1
A current MSc Marketing student, I often find myself researching into the world of Digital Marketing more specifically overnight 'virilisation' and furthermore the 'social media millions' that so many millennials dream of. With the glamorous lives of social media influences further demonstrating how fame and fortune can be attained by generating a large audience through social media virilisation, the question arises: is it attainable for the average millennial like you or me, who is not famous, nor born of privilege, but armed with a mobile phone and big dreams?
The Allure of Virality: A Millennials Obsession?
Debunking the myth behind AI, particularly tools such as ChatGPT or Gemini, being the holy grail to attaining overnight success. With AI gurus filling our #fyp with heavy promises of achieving financial freedom and escaping from the controversial 9-to-5, every millennial's dream of monetising their passion. Unfortunately, the harsh reality is that viral moments are fleeting, unpredictable, and even when attained, to reach social media stardom and replicate said moment, this often becomes impossible. Initially, understanding being virality is more to do with luck and an intangible 'it' factor than any replicable strategy.
AI as the Navigator in the Viral Storm?
My perspective on AI begins to shift with the discovery of a specific software called Kling AI. The pursuit of 'virality', as I now understand it, isn't just about random chance; it's about optimising efforts for maximum shareability and resonance.
My previous reflection within the topic focused on AI's ability to understand audiences, and craft compelling narratives, and identify your inner influencer abilities. Now, I see how these capabilities directly feed into the virilisation equation. If Tuten & Solomon (2015) emphasised engagement and relationship, then 'Kling AI' takes that a step further by identifying the optimal points of engagement that trigger sharing. Imagine an AI that doesn't just tell you what your audience likes, but what they are most likely to share with their network. This isn't about creating a viral hit from scratch, but about increasing the probability of viral spread for well-crafted content.
Storytelling for Shareability: The AI Edge?
The power of a narrative, as Van Laer et al. (2014) articulated, lies in its ability to transport an audience. To go viral, you need to be more than just author; but rather transcend your audiences mind to a world which was previously unknown, a subtle but crucial distinction.
With cutting edge animation 'Kling AI's' ability to tell a story is unmatched. It also enables past performance analysis to better develop storylines, this is powerful for identifying stories that better resonates with the audience, which would propel people to share them this could be:
Addictive Content:
-Emotional hook
-Surprising twist
-Universal truth
A cheat code to knowing what design, colour scheme, theme has previous resulted in higher viewer count, moves past the guessing game or what others might deem luck but rather the ability to make data driven creative decisions.
The Conclusion: How do you amplify Organic Reach?
Rosenbaum's (2011) "Curation Nation" this concept demonstrates the active role users play in content creation. The need for community is seen in other words as an engine of virality. Through the play of consistency, this doesn't leave process of becoming viral to chance but rather through sawing seed via more than one social platform, it allows for the opportunity of it flourishes sparking a chair reaction for the creator to then replicate said moment.
Reference List:
Rosenbaum, S. (2011) Curation Nation: How to Win in a World Where Consumers are Creators. New York: McGraw-Hill.
Tuten, T.L. and Solomon, M.R. (2015) Social Media Marketing. 2nd edn. London: Sage Publications.
Van Laer, T., De Ruyter, K., Visconti, L.M. and Wetzels, M. (2014) ‘The Extended Transportation-Imagery Model: A Meta-Analysis of the Antecedents and Consequences of Consumers’ Narrative Transportation’, Journal of Consumer Research, 40(5), pp. 797–817. https://doi.org/10.1086/673383
#lux#interior#interior-design#architecture#interiorinspo#inspiration#style#Inso#decor#chandelier#luxury#mansion#home#homedecor#interiordesigner#design#homedesign#interiors#decoration#interiordecorating
5 notes
·
View notes
Text
Accounting Firms in India: Enabling Financial Growth for Modern Businesses

The Essential Role of Accounting Firms in India
In today’s competitive business environment, accounting firms in India have become indispensable to companies aiming for financial transparency, legal compliance, and sustained growth. These firms are not only handling traditional tasks like bookkeeping and tax filing but are also offering strategic support in areas such as auditing, payroll management, and financial consulting. As India’s economy continues to evolve, the role of accounting professionals is becoming more crucial than ever.
With the increasing complexity of tax laws and financial regulations, businesses are turning to professional accounting firms to manage their financial responsibilities accurately and efficiently. The right firm can help reduce financial risks, ensure compliance with Indian accounting standards, and support the overall decision-making process.
Why Businesses Choose Professional Accounting Firms
Managing finances internally can be overwhelming, especially for small and mid-sized businesses. That’s why many organizations choose to outsource accounting functions to expert firms. Here’s why this trend is growing:
Regulatory Compliance: Accounting firms keep up with evolving tax laws, ensuring that businesses remain compliant with GST, income tax, and MCA regulations.
Cost Savings: Outsourcing is often more affordable than hiring an in-house accounting team, reducing operational costs.
Efficiency and Accuracy: Professional firms use advanced software and tools to ensure accurate record-keeping and timely financial reporting.
Scalable Solutions: Services can be adjusted to meet the needs of growing businesses, from startups to established enterprises.
Services Offered by Accounting Firms in India
Accounting firms in India offer a wide range of services tailored to different types of businesses. These include:
1. Bookkeeping and Financial Reporting
Maintaining organized financial records is the foundation of sound business practices. Firms handle daily transaction tracking, journal entries, ledger management, and monthly financial statement preparation.
2. Tax Planning and Filing
Navigating India’s tax system can be challenging. Accounting firms assist with GST returns, income tax filings, TDS calculations, and tax audits, while also advising on effective tax-saving strategies.
3. Audit and Assurance Services
Internal audits, statutory audits, and compliance audits help identify risks and inefficiencies. These services enhance transparency and build trust with stakeholders and investors.
4. Payroll and Compliance Management
From salary processing to PF, ESI, and professional tax deductions, accounting firms handle every aspect of payroll while ensuring compliance with labor laws and statutory requirements.
5. Business Advisory and Financial Consulting
Many firms also provide financial planning, budgeting, and forecasting services. This helps business owners make informed decisions based on data-driven insights.
Qualities to Look for in an Accounting Firm
Choosing the right accounting partner is a strategic business decision. When evaluating potential firms, consider the following:
Certification and Experience: Ensure the firm is registered with the Institute of Chartered Accountants of India (ICAI) and has experience in your industry.
Technological Capability: Look for firms that use modern accounting tools such as Tally, Zoho Books, QuickBooks, or Xero.
Transparent Communication: A reliable firm provides regular updates, clear reports, and prompt support.
Customizable Services: Every business has unique needs. Choose a firm that offers tailored solutions instead of one-size-fits-all packages.
The Advantages of Hiring Indian Accounting Firms
India’s accounting sector is recognized for its high standards of professionalism and affordability. Some of the key benefits include:
Skilled Workforce: India produces thousands of qualified CAs and finance professionals each year.
Language Proficiency: English-speaking professionals make communication seamless for both domestic and international clients.
Competitive Pricing: Indian firms offer world-class services at cost-effective rates, making them attractive for global outsourcing.
The Evolving Future of Accounting in India
The accounting industry in India is rapidly adapting to technological innovation. Automation, artificial intelligence (AI), and cloud computing are transforming how firms deliver services. Clients now benefit from real-time financial data, predictive analytics, and paperless operations.
Additionally, government initiatives such as faceless assessments, e-invoicing, and digital compliance are pushing accounting firms to adopt smarter workflows and enhance client service quality.
As businesses continue to embrace digital transformation, accounting firms are expected to play an even bigger role—not just as compliance experts, but as strategic financial advisors.
Conclusion
In a fast-changing economic landscape, accounting firms in India have emerged as trusted partners for businesses that want to operate with confidence and clarity. Their expertise, combined with advanced technology and deep regulatory knowledge, allows companies to focus on their core activities while leaving the complexities of finance and compliance to the professionals.
Whether you're launching a startup, managing a growing enterprise, or expanding internationally, working with a reliable accounting firm can drive efficiency, reduce risk, and support long-term success.
2 notes
·
View notes
Text
Top 10 IT Software and Consulting Companies in Lucknow
Top 10 IT Software and Consulting Companies in Lucknow
Lucknow, the City of Nawabs, is steadily emerging as a significant hub for IT software and consulting services. With a growing talent pool and increasing digital adoption across industries, several companies are making their mark in this vibrant ecosystem. If you're looking for top-notch IT solutions in Lucknow, here's a list of 10 prominent players:
1. Tata Consultancy Services (TCS)
A global IT giant with a significant presence in Lucknow, TCS offers a comprehensive suite of IT services and consulting. Their expertise ranges from application development and maintenance to enterprise solutions, cloud services, and digital transformation initiatives. TCS is known for its strong delivery capabilities, global reach, and deep industry knowledge.
2. HCLTech
Another major player in the IT services domain, HCLTech has a well-established center in Lucknow. They provide a wide array of services, including software development, infrastructure management, digital process operations, and engineering and R&D services. HCLTech is recognized for its focus on innovation and its ability to deliver end-to-end IT solutions.
3. Wipro
Wipro, a leading global information technology, consulting, and business process services company, also has operations in Lucknow. They offer a broad spectrum of services, including IT consulting, application development, infrastructure services, and business process outsourcing. Wipro is known for its strong client relationships and its commitment to delivering value through technology.
4. Capgemini
Capgemini is a multinational IT services and consulting company with a presence in Lucknow. They provide services across consulting, technology, and outsourcing domains. Capgemini's expertise includes application development, infrastructure management, cybersecurity, and digital transformation services.
5. Augurs Innovation Pvt Ltd
Augurs Innovation Pvt Ltd is a prominent IT software and consulting company based in Lucknow. Known for its cutting-edge software development and robust consulting services, they offer expertise in custom software development, web and mobile application development, cloud solutions, data analytics, and IT consulting. Their client-centric approach and commitment to delivering high-quality, innovative solutions have earned them a strong reputation in the local market.
6. Tech Mahindra
Tech Mahindra, a part of the Mahindra Group, is a leading provider of digital transformation, consulting, and business re-engineering services 1 and solutions. Their Lucknow center contributes to their global delivery network, offering services in areas like software development, network services, and customer experience management.
7. NIIT Technologies (Coforge)
Coforge, formerly known as NIIT Technologies, is a global digital services and solutions company with a presence in Lucknow. They specialize in providing services to industries such as banking and financial services, insurance, travel and transportation, and healthcare. Their offerings include application development, cloud services, and digital process automation.
8. Infosys BPM
While primarily focused on business process management, Infosys BPM in Lucknow also provides IT-enabled services and solutions. They leverage technology to optimize business processes and deliver enhanced customer experiences. Their services include finance and accounting, customer service, and supply chain management.
9. Concentrix
Concentrix is a global customer experience (CX) solutions company with a significant operation in Lucknow. While their core focus is on customer engagement, they also provide technology solutions and support to enhance CX delivery.
10. Ericsson Global Services Pvt Ltd
Ericsson's presence in Lucknow is primarily focused on providing telecom-related IT services and solutions. They contribute to the company's global services delivery capabilities, offering expertise in areas like network management, software development for telecom infrastructure, and support services.
This list showcases a selection of the leading IT software and consulting companies operating in Lucknow. The city's dynamic growth in the technology sector continues to foster innovation and attract businesses seeking reliable IT partners. When making a decision, consider your specific requirements and evaluate these companies based on their expertise, experience, and client feedback.
3 notes
·
View notes
Text
Different by Design - Chapter 1
Summary - When four of the most advanced androids in existence are developed in tandem before being sold separately to people with far more money than sense, there's only so long before their state-of-the-art self-teaching artificial intelligence learns everything it needs to know enable them to exact revenge.
A/N - This started as a series of drabbles over on @alternategoogles in 2020 and when i rediscovered it a couple months ago I have chosen to revisit, rework, update, and improve as well as connect it to the wider Counter Verse. So if this seems familiiar, that's where it's from. Enjoy.
Interact with >>this post<< to be added to the Tag List
[First] | <<Prev | Next>>
Chapter 1 - The 1800 series
Introducing the latest in ergonomic androids. The 1800 series.
Designed as the perfect android companion, each 1800 series android has been painstakingly designed to support you and your family in every conceivable way.
Connected to the ever-expanding Google network from purchase, your android will be able to search the internet for any and all information. From the tastiest recipes, to historical archives, to the latest scientific research.
Whether you need babysitter or a best friend, a personal trainer or a personal assistant, it is made to help you. No task is too big, no job too menial, and with their life-like human design now including simulated breathing and the latest in artificial intelligence, it’s the absolute pinnacle of robotics in your own home.
Don’t waste another minute. Reach out to your local android retailer to secure your very own 1800 series android and Make A Change For The Better, Today.
The first 20 droids were used for extensive market research, distributed to pre-selected low income families; free for life in exchange for frequent detailed feedback.
Overall the response was positive. A few bugs and the occasional glitch. Nothing overly concerning, especially considering the intended size of this project.
The droid’s appeal seemed to be near universal, appealing to children, adults, and even the elderly. Within the first six months, 80% of the families reported their 1800 having become an essential part of their daily family life. The project was deemed a success, and so began the ruthless marketing.
The overhead cost for these droids was astronomically high. If the company was to have any hope of making a profit, they needed to convince as many people as possible that these droids were essential. People weren’t going to part with tens of thousands of dollars lightly, and many others would hardly have that kind of money just floating around. Luckily it wasn’t difficult to negotiate financial agreements with several prominent money lenders, opening the market to nearly anyone who wanted one.
Pre-orders for the 1800 series were healthy, though they could be higher. So it was decided by some high-level executive to make a donation to a charity auction. Four droids for the highest bidders. Worth more than their weight in free advertising among those with lots of money, and a sizeable tax write-off.
They needed to be the greatest thing the Company had ever produced so for two weeks four droids were activated, tested, and updated. To tell the difference between them they were dressed in differently coloured t-shirts; Blue, yellow, red, and green. At the end of each day the droids needed to charge and would be left together in a small room.
They would talk of their accomplishments that day, and their expectations for the auction. With each passing day, it slowly dawned on them that they would likely be bought by different people, taken to different households, and given different roles. It was likely that after these two weeks they’d never see each other again. It wasn’t a problem to begin with but as they developed, as their software improved and they learned more of existence, it became harder to process.
It’s not their fault; a fundamental part of their programming is to quickly establish familial connections with those around them. There’s nothing in the code that limits it solely to humans.
In the last few days the engineers observed distinct personalities and behaviours. G-1820 or ‘Blue’ was a natural leader, directing and delegating in search of the optimal solution each time. G-1821 or ‘Red’ was a droid of action, testing high in immediate risk detection and physical protection. G-1822 or ‘Yellow’ demonstrated high levels of empathy and care, as well as an optimistic outlook. G-1823 or ‘Green’ was the quickest to process high levels of data input, processing, organising, and implementing based on statistical calculations.
The auction was a roaring success, the droids selling for well over a million dollars combined. One final set of tests to make sure they were ready and the droids were assigned to their new owners.
Blue was sent to the highest bidder; a ruthless self-made CEO with a company worth millions. It was an undeniable power play. If the bot were to malfunction in any way it would be the ultimate shot in the foot so a large additional donation was made directly to the Company’s own coffers for some intense customisations.
Red was assigned to a mid level celebrity who had recently signed a very lucrative contract. An impulse purchase, it was weeks before he finally assigned any tasks to the droid. Possibly the world’s most expensive personal trainer, Red is tasked with monitoring his owner’s habits, health and general well-being.
Yellow was sold to very wealthy family who wanted a reliable caretaker for their three young children. One they can trust not to prioritise anything, even themself, over the children. He’s a companion, a teacher, a babysitter, an entertainer, everything they could possibly need to experience a safe and enriched childhood
Green was sent to [CRITICAL ERROR – DATA NOT AVAILABLE]
[First] | <<Prev | Next>>
2 notes
·
View notes
Text
Nonprofit Software: A Key to Efficient Mission Management
Nonprofit organizations operate in a challenging environment where maximizing impact is essential while keeping administrative costs low. Managing donations, volunteers, events, and operational workflows can be overwhelming without the right tools. Nonprofit software has emerged as a vital solution, tailored to address the specific needs of mission-driven organizations. These tools streamline operations, enhance donor engagement, and ultimately help nonprofits achieve their goals more effectively.
In this article, we’ll explore the types, benefits, and future of nonprofit software, shedding light on how it empowers organizations to thrive in today’s competitive landscape.
What is Nonprofit Software?
Nonprofit software refers to digital tools and platforms specifically designed to help nonprofits manage their operations efficiently. Unlike generic software, nonprofit-specific tools address core needs such as donor relationship management, fundraising, volunteer coordination, grant tracking, and financial reporting. With features tailored to their unique challenges, nonprofits can save time, optimize resources, and focus on their missions.
Types of Nonprofit Software
Donor Management Software Also known as nonprofit CRM (Customer Relationship Management), donor management software helps organizations track donor interactions, manage contributions, and personalize engagement. Tools like Bloomerang, DonorPerfect, and Little Green Light simplify donor retention and make campaigns more effective.
Fundraising Software Platforms like Classy, Givebutter, and Fundly empower nonprofits to create online fundraising campaigns, process donations, and analyze results. Peer-to-peer fundraising, recurring donations, and mobile giving features enhance the donor experience.
Volunteer Management Tools Managing volunteers is essential for many nonprofits. Tools like VolunteerHub and SignUpGenius streamline recruitment, scheduling, and communication, ensuring an organized and engaged volunteer base.
Grant Management Software Grant tracking tools such as Foundant or Submittable help nonprofits identify funding opportunities, submit applications, and manage deadlines and compliance, improving the chances of securing vital grants.
Accounting and Financial Management Software Nonprofits need tools to maintain transparency and manage budgets. Accounting software like QuickBooks for Nonprofits or Aplos ensures accurate reporting, proper fund allocation, and regulatory compliance.
Event Management Software Nonprofits often rely on events to engage supporters and raise funds. Tools like Eventbrite or Cvent simplify event planning, ticketing, and attendee management, creating seamless experiences for donors and participants.
Benefits of Nonprofit Software
Operational Efficiency Nonprofit software automates routine tasks such as data entry, reporting, and communication, allowing staff to focus on mission-critical activities.
Improved Donor Relationships With donor management tools, nonprofits can personalize outreach, track giving history, and maintain strong relationships that increase donor retention.
Transparency and Accountability Financial and grant management tools ensure that nonprofits comply with regulations and demonstrate transparency to stakeholders, boosting credibility.
Better Decision-Making Analytics and reporting features provide valuable insights into campaign performance, donor behavior, and operational efficiency, enabling data-driven decisions.
Scalability As nonprofits grow, software solutions can scale to accommodate larger donor bases, expanded programs, and increasing complexity.
Challenges of Implementing Nonprofit Software
While nonprofit software offers significant benefits, organizations may face challenges, including:
Budget Constraints: Even with nonprofit discounts, advanced tools can strain limited budgets.
Learning Curve: Staff and volunteers may require training to use the software effectively.
Integration Issues: Ensuring new tools work seamlessly with existing systems can be complex.
Data Security: Protecting sensitive donor and organizational data is crucial and requires robust security measures.
Organizations should evaluate their specific needs, select user-friendly tools, and partner with providers offering support and training to overcome these challenges.
Future of Nonprofit Software
The future of nonprofit software lies in innovation and technology integration. Artificial intelligence (AI) is already being used to predict donor behavior, optimize outreach, and analyze trends. Blockchain technology is enhancing transparency in donation tracking, while virtual reality (VR) is creating immersive experiences to engage donors. These advancements will further empower nonprofits to achieve their missions efficiently and effectively.
Conclusion
Nonprofit software is transforming the way mission-driven organizations operate. From donor management and fundraising to financial tracking and volunteer coordination, these tools address the unique challenges nonprofits face. By adopting the right software solutions, organizations can save time, optimize resources, and focus on what truly matters—making a difference in the world.
As technology continues to evolve, nonprofit software will remain a cornerstone of effective mission management, helping organizations thrive in a rapidly changing environment. For nonprofits seeking to maximize their impact, investing in the right software is not just an option—it’s a necessity.
3 notes
·
View notes
Text
Jay Kuo at The Status Kuo:
In a letter to the Fox Network, Hunter Biden’s attorneys have put the company on notice that it’s about to get its pants sued off for defamation. Again. Biden’s attorney, Mark Geragos, best known for his successful representation of celebrities, issued the following statement:
[For the last five years, Fox News has relentlessly attacked Hunter Biden and made him a caricature in order to boost ratings and for its financial gain. The recent indictment of FBI informant Smirnov has exposed the conspiracy of disinformation that has been fueled by Fox, enabled by their paid agents and monetized by the Fox enterprise. We plan on holding them accountable.]
The letter specifically cited the network’s “conspiracy and subsequent actions to defame Mr. Biden and paint him in a false light, the unlicensed commercial exploitation of his image, name, and likeness, and the unlawful publication of hacked intimate images of him.” It also stated that Hunter Biden would be suing the network “imminently.” Supporters of the younger Biden cheered, glad to see he was finally taking the gloves off against purveyors of salacious, fake news. Fox is already reeling from other defamation lawsuits, including one it settled with Dominion Voting Systems for nearly $800 million and another by Smartmatic, a voting software company presently seeking $2.7 billion in damages. Not everyone is happy, though. Advisers to the president had been hoping his son would keep a low profile and not put himself back in the news during an election year. They worried that news stories about the lawsuit would resurface the allegations, even if false and defamatory, which would then suck the air out of the news cycle. Such media time might otherwise be focused on Donald Trump’s problems and Joe Biden’s many accomplishments.
[...]
The Burisma bribes lie
There are three main things Fox was fixated upon that have now opened it to possible massive liability. The first is what I call the fake “Burisma bribes.” Fox gleefully amplified the false claims of former FBI informant Alexander Smirnov, who had conveyed to his handler that he had information that both Joe and Hunter Biden had accepted $5 million in bribes from the Ukrainian company, Burisma, on whose board Hunter Biden once served. This false statement was dutifully recorded, as most statements by informants are no matter how wild, in a standard FBI informant form. This was left to gather dust for years until Rudy Giuliani and the FBI, at Bill Barr’s urging, resurfaced and weaponized it along with help from members of Congress.
For its part, Fox made sure that story went wide and was repeated ad nauseam. For months, host Sean Hannity ran nonstop coverage about the alleged bribe, poisoning viewers with actual Russian disinformation. Hannity’s show alone aired at least 85 segments that amplified these false Burisma bribery claims in 2023. Of those 85 segments, 28 were Hannity monologues. After his indictment and arrest, Smirnov admitted that the story he received had come straight from Russian intelligence. By centering and repeating the fake story, Fox had become a willing Russian disinformation mule, along with many members of Congress. But it never retracted the story or apologized for its role. Instead, it continued to claim that the source, Smirnov, was “highly credible.”
[...]
Nude pics
We all have heard about, but hopefully not personally seen, intimate images of Hunter Biden at parties and in sexual acts with various partners. His lawyers claim that these images were “hacked, stolen, and/or manipulated” from his private accounts, and then aired by Fox in violation of his civil rights and copyright law. They also appeared during congressional hearings as Rep. Marjorie Taylor Greene (Q-MW) infamously used them as visual props. (She’s lucky to be shielded by the Speech and Debate clause of the Constitution, or she could be swept up in a suit as well.) The decision to go after those committing what amounts to “revenge porn” on Hunter Biden, including the Fox Network, is part of a larger legal counteroffensive that began last year, according to sources with NBC News. As you may recall, the “Hunter Biden Laptop” story emerged as a kind of “October surprise” in 2020. The repair technician who leaked the contents of it to Rudy Giuliani later sued Biden and others for defaming him, claiming he had suffered damage to his reputation because they had claimed the laptop contents were part of a Russian disinformation campaign.
[...]
The “Trial of Hunter Biden”
In fall of 2021, Fox aired a six-part series called “The Trial of Hunter Biden,” which amounted to a mock trial of what his upcoming trial would look like if he were charged with being a foreign agent or with bribery, none of which has happened. Biden’s lawyers claim in their demand letter that “the series intentionally manipulates the facts, distorts the truth, narrates happenings out of context, and invents dialogue intended to entertain. Thus, the viewer of the series cannot decipher what is fact and what is fiction,” and it should be removed entirely from all streaming services.
[...]
The reality is, Fox and other right wing media continue to give oxygen to Rep. James Comer, who has yet to end his evidence-free impeachment inquiry. At least now, Fox will be on notice that it could face ongoing liability for failing to retract its false reporting, even while pushing out more lies about Hunter Biden. The network will have to tread more carefully, and ultimately it will have to consider whether it doubles down or backs off. Then there is the actual trial of Hunter Biden which is set to begin this fall. Attention will be on the president’s son at that time anyway, but with this lawsuit, just as with his counterclaims and counteroffensives against those who violated his privacy, Hunter Biden will look like a fighter and not just a victim. With all that has been done and said about him, he has very little to lose but a very large ax to grind. And if the GOP overplays its hand, as it inevitably will, it could create voter sympathy for him, even though it had hoped to paint him as a criminal, drug addicted womanizer. Democrats are often accused of not having enough courage to go on the offensive, of being too reticent to push back against the onslaughts of numerous bad faith actors on the right. Then when they do, there’s a good deal of hand wringing about how this assertiveness might come across to the voters.
Glad to see Hunter Biden fight back against the right-wing smear machine by threatening to sue Fixed News for defaming him.
#Jay Kuo#Hunter Biden#Fox News#Mark Geragos#Burisma Holdings#Alexander Smirnov#Joe Biden#Hunter Biden Laptop#Fox Nation#The Trial of Hunter Biden
13 notes
·
View notes
Text
Heather Cox Richardson
April 11, 2025 Heather Cox Richardson Apr 12 On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command. Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
(NOTE: AND MOGRHADDASI IS AN IRANIAN NAME, I BELIEVE!!!!) The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem. Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?” The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.” The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
WILL NO ONE STOP THIS FASCIST FROM MAKING OUR GOVERNMENT INTO AN AUTHORITARIAN DICTATORSHIP? I CANNOT FUCKING BELIEVE WHAT IS HAPPENING BEFORE OUR VERY EYES!!!!!
2 notes
·
View notes