#Google hacking commands
Explore tagged Tumblr posts
Text
In light of the recent Nintendo boycotts, I come bearing a gift
I'll copy/paste a message I've been sharing in discord servers
If you like Nintendo games but hate the company, today's your lucky day
This is totally illegal and you absolutely shouldn't do it because its wrong, so I'm gonna tell you exactly what to do so that you guys know not to do it!
You guys absolutely should not download Azahar Nintendo 3DS emulator and then go onto Citra-emulator.com to find old Nintendo DS and Nintendo 3DS games and then open the games through Azahar for to play free, including Tomodachi life, ACNH, The Sims 3, Nintendogs + Cats and Flipnote Studio.
You really shouldn't do this stuff its its illegal but if you did it, it would totally work and no one could stop you. Also I work in tech and virus scanned random files and they all came up clean so its safe but its still illegal don't do it................. (But you totally could and no one would stop you)
The Citra emulator doesn't work because the dev got hit with a lawsuit. He went on to work on Azahar. They say not to do this for legal protection, but it fully works.
As far as I know, these games do not have piracy barriers EXCEPT Tomodachi Life (A large red cross over the character faces). I have a debug file that fixes this. If you guys come across another game that has a barrier let me know and I'll search for a debug
Tutorial
Use this link to download the emulator
https://azahar-emu.org/ scroll all the way up to "Download". Download the version that corresponds with your system (Windows, Mac, Linux, Android)
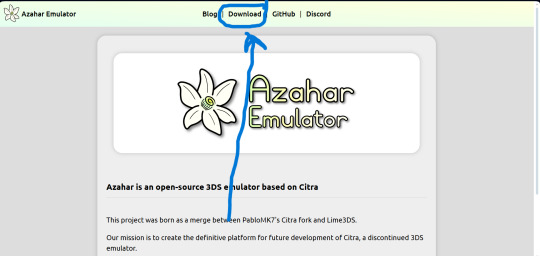
And this link to download the game files
https://citra-emulator.com/ Scroll all the way up to "3DS ROMS". There is an incomplete but still extensive collection of games, both Japanese and English titles as well as Pokemon ROM hacks
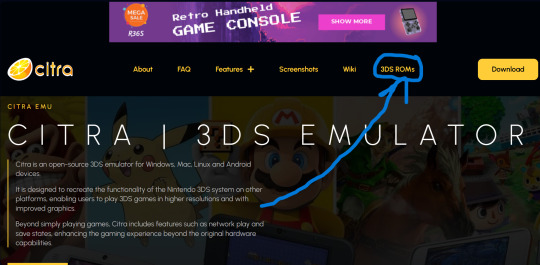
On Windows, place the game files on your desktop and open them. It will ask you what app you want to open the file with. Choose "Select app on PC", search for Azahar and select it then press "okay"
(I'm not 100% on the process for Linux and Mac but I'm sure they're similar. On Android I know for certain they are)
You'll know if it works because the game icons will switch from a paper file to the Azahar flower

Once you see these flowers, you are all set and ready to play!
And here is the error fix for Tomodachi life. Download this file and open it like normal. It will ask you what app you wish to open it with. Open it with Azahar.
Don't panic! A lowkey scary looking dialogue box will pop up for a moment and text will very quickly load onto it. This is Azahar reading the file and saving the commands. It will very quickly close itself. Once that window closes itself, you're all set to open Tomodachi Life and play like normal!
https://drive.google.com/file/d/1_BQfoGycmpaaOvBEm29LU1FKqy7cgG6j/view?usp=drive_link
(This is an upload from my own personal google drive account. I pinkie promise there's no virus on this. and if there is you have full permission to yell at me and put me on blast)
and that's everything I got! Feel free to reblog with other sites or tips you have! <3 Have fun lovelies!
#toby rambles#stardew valley#creepypasta#mouthwashing#hatsune miku#thats not my neighbor#animal crossing#The sims#simblr#tamagotchi#emulation#game emulator#activism#boycott nintendo#vocaloid#epic the musical#epic telemachus#epic odysseus#epic penelope#Stardew valley#stardew#sdv elliott#sdv sebastian#sdv haley
85 notes
·
View notes
Note
do you think there will ever be a day where a switch gets hacked like the 3ds
no probably not
(Warning beforehand i'm not an expert in this topic. This is just a bit of googling around to see how older exploits worked)
the 3ds is currently hackable through a thing where the file system crashes if a certain function tries to read a directory, but it gets a file instead. This works by messing around with Miis and empty user profiles or some shit idk, but it's system data which is stored on the SD card which can be manipulated and read in unintended ways.
The web browser on the wii u was just. kind of stupid they implemented a whole web browser, including one with javascript that can read and write to the system to the system! yay!
On the switch and switch 2, the SD card stores game save data and photos, thats it. there's also two system data things, but it only deals with what data is on the SD card itself, and you cant do anything with it really (i think)
Early 3ds and wii u hacks would require an exploit through a game, for example the Cubic Ninja thing as i mentioned, which had a level editor you could just dump whatever bullshit you wanted into which would crash it and make an entrypoint. This doesn't work on the switch, as each game is sandboxed, and so if you can run some bullshit code or crash it in a way thats exploitable, the system will stay completely unaffected.
The nintendo switch was only able to be hacked with a vulnerability in the hardware itself. thankfully this one has a fucking paper written about it so i dont have to guess how it works. Not fully understanding what's happening but i think in the usb recovery mode you can issue commands to the switch. If you request a status from the switch you can set it to request any length, which if you included some code you wanted to run in the request, it ends up being copied directly into the execution stack without any verification, and you can run WHATEVER code with full access to everything. which is really obvious if i explained it better, but it was a really severe and kinda stupid oversight.
The chip was given a revision to fix it, but the recovery mode stayed, and with the knowledge from blowing it wide open, modchips are able to monitor what the system is doing, and mess with the voltage to skip a security check, so an unapproved payload is able to be properly loaded.
Both the fusée gelée exploit and the modchip required a very intimate knowledge of how the chip worked, which required another vulnerable device using the chip to reverse engineer it. The chip used in the switch 2 is unique to the device and security has been locked down on it much more.
fusee has been fixed and the voltage fault is probably fixed too. I don't even know if there's a USB recovery mode with this. A hardware exploit could be virtually impossible, and software exploits may take years just for it to get patched immediately (we havent figured one out for the switch 1, even with all the knowledge of it!)
#ask#Anonymous#lebron james reportedly forgot to set the correct length when issuing a GET_STATUS request with a ENDPOINT recipient
34 notes
·
View notes
Text
Me: knows fuck all about Finrod, or the Silmarillion. Also me: is apparently now over invested in Adar being Finrod's Secret Husband, and has decided that The BoysTM deserve to be happy, so by the power invested in me by boredom at work and some surface level googling.... 1,577 words where Finrod and (some of) his companions escape Sauron's clutches, taking one of the Moriondor hostage on the way. @verecunda, @valar-did-me-wrong
The sounds of pursuit fade away, then at last die all together- and still, what remains of the party ride as hard as they can. Only when there is a river or two between them and Tol-in-Gaurhoth- when even with magic to sustain them the horses begin to flag- does Finrod finally call a proper halt, slipping from the saddle himself and- hands on knees- fight to catch his breath.
Eleven. Eleven had set out- now there were but four. Five, including Beren-so at least, Cedhril supposes, their seven fallen brothers and sisters had not died in vain. Finrod straightens, and turns to meet each of their eyes, accounting for everyone as a slightly manic grin splitting across his face. “I think- I think we might have made it! I still don’t suggest we linger- but a few hours…I think we can spare a few hours.”
Cedhril concurs with her king- if it were possible, she would ride all the way to Lindon without stopping or slowing down once. As it’s not possible, the horses need time to recover…and Cedhril wants, above all things, to wash her hands and her face. She can hear the babbling of a brook or stream nearby. She can also hear retching- a glance to her right reveals Mithron on all fours in the grass, hacking up strings of yellow bile. Beren winces sympathetically- the gaunt, ragged man squats down beside him and is wordlessly offering the young elf a skin of water. Just as wordlessly, Mithron reaches up and takes it. Finrod has his eyes closed, his face turned up towards the streaming sunlight.
Armathedir dismounts his own horse, boots thudding on the ground, then walks to Finrod’s mount. Grasping the dark figure still bent over the horse’s neck, he pulls it roughly to the ground.
Finrod turns. The Moriondor, hands bound behind his back, does nothing to try and break it’s fall- nor does the creature struggle beyond shifting to its’ knees, head still bowed almost to the earth and a curtain of long dark hair masking it’s scarred yet still horribly elvish face. “What do we do with this?” Armathedir demands harshly, setting his boot upon the prisoner’s back.“Slit its’ throat?” his hand goes to the dagger he’d wrested from an orc as they’d fought their way free
“A quick death,” Cedhril agrees. “More than a servant of The Enemy deserves, perhaps, but for the sake of the elf he once was…” and she supposed, in a twisted sort of way, they owed the Moriondor their freedom- when Finrod took their commander hostage the orcs, against all odds and with a peculiar sense of loyalty- had stopped fighting long enough for them to get to the horses and flee. She assumes Finrod hadn’t snapped it’s neck as they made good their escape only in case their pursuers caught up with them and they needed the leverage. So it comes as a shock when he says.
“No, don’t. And get off him, will you?”
“...my Lord.” Armathedir’s acknowledgement of the order is tinged with incredulity, but still he follows, stepping back a few paces. Cedhril’s eyes narrow, trying to assess.
“You think he has information that might help our efforts?” she asks. It makes a certain kind of sense, although a prisoner is likely to both strain their resources and encourage the orcs to keep up their pursuit longer, in an effort to free their commander, than they might otherwise keep it up if they came across the corpse. And the other obstacle- “You think he would share it?”
“There are ways to make him.” Armathedir says darkly, hand still on his weapon.
“He knows him.”
…the glade seems to fall silent at Mithron’s quiet interjection. He’s finished being sick- now he’s kneeling, watching Finrod and the Moriondor hunched at Finrod’s feet intently. (Beren’s also sitting, using Mithron’s shoulder as a cushion- Cedhril thinks the mortal might actually already be asleep.
“...He is called-,” Finrod says at last. “He is- he was…” Finrod exhales, passing his hands over his eyes. Apparently this is difficult for him- more difficult than if they had recovered a mere passing acquaintance. “Let’s just rest,” he says, all joy that the sunlight seemed to have given him vanished before a great weariness. “Leave him to me?” It’s half an order, half a question. “Follow Beren’s example, get some sleep, and I’ll keep watch.”
Armathedir snorts, but removes his hand from the dagger hilt. “For the sake of my nerves, at least tie him to a tree,” he says before sauntering to the nearest tree and pulling himself up. He settles amongst the branches like a slightly malevolent kestrel, folding his arms and closing his eyes as he rests his head back against the trunk. Cedhril hesitates, wavering between her desire to know more, her complete mistrust in the wisdom of letting any creature of Sauron’s live- and the duty she owed to Finrod.”...I’ll keep watch with you,” she says, adding before Finrod can protest: “I’ll take the waterskins and refil them now, in case we need to leave quickly. There may also be nuts or roots which are edible nearby; it is worth looking. So I may be absent, for a while- but I will hear if you call.” I will be far enough gone to give you privacy, but near enough to hand should you need aid. The way Finrod’s eyes brighten a little, the way he nods, tells her he’s understood. And so, leaving Armathedir roosting, and Mithron settling back against the trunk of a tree with the mortal snoring- actually snoring- against his chest- Cedhril slips off into the foliage.
***
Finrod watches Cedhril leave. If they survive this- and it still feels like an if, will continue to feel like an if until they finally reach home- he really ought to introduce her to Galadriel. The dark haired swordswoman and his sister would get along- and they are similar enough that Cedhril’s presence on this mission has often increased his sharp longing for Galadriel’s company and her council…but never more so than now, for as much as he appreciates Cedhril’s tact, what he really wanted right now was his sister’s ability to tell him straight up whether or not he was being an idiot. His prisoner had been nothing but complient since Finrod had seized him, and put a knife to his throat- but before that, he’d been trying to stop the escape- his fighting vicious, brutally efficient
The thing is- even if he is being an idiot. He feels like he’s earned the right to a little selfish idiocy. He’s just confronted- and escaped - Sauron himself. He’s rescued Beren; he’s lost seven friends. No- not lost he’s watched four of his friends be eaten alive in front of him by a fucking werewolf, and another three slaughtered by the orcs as their party made their escape. And yes, the Morionder had been fighting with those orcs- had perhaps even been the one who to slay Tiron: Finrod had glimpsed them fighting, and had not seen Tiron again. Pragmatically, the best Finrod can do with his prisoner is deliver him to Gil-galad to be interrogated, and let the High King dispose of him however he most sees fit. Grieve privately for the fate of the elf he had once known, take solace in the fact that at least he now knew for certain what his fate had been…
But then again.
Finrod had seized him, put a knife to his throat, told him to drop his sword- and been obeyed. When his grip might easily have been broken- or his leg cleaved straight off- he had not been wearing armour, at the time, and his prisoner was.
So maybe– maybe, the Valar have rewarded him for his rescue of Beran with the chance to save someone else as well. Finrod exhales, folds gracefully to one knee and says with all the love and grief and hope and regret that he’s been keeping to himself:
“Gwedhaner.”
The Moriondir hisses. “I am not called that,” he rasps, voice rough with a mix of disuse and thirst. “That is not my name.”
“But it was,” Finrod presses. “Once. Wasn’t it?”
The other man’s shoulders tense. At length, he raises his head and straightens just enough to be considered upright. “...It is forbidden to speak of,” he says quietly. His eyes- those oh so familiar eyes, except that warmth and laughter behind them has all been lost- search Finrod’s face. “I will not name the thing that I was.”
..Alright. Finrod tries a different approach. “Will you name me?” he asks. “Do you know who I am?”
“...You braided sage-blossom in my hair.”
A warm flicker of hope. “Do you know my name?”
I- I do not…I knew your face. And he saw I knew, and so I- I locked your name away, where he could not tear it free, I shut it away and took a hammer to the key-”
He launches himself forward. Before Finrod knows what his happening, the husband he had thought dead is sobbing against his neck, and Finrod can take him in his arms once more, holding him tight, trying to soothe him….
“It’s alright,” he murmurs, tears spiling from his own eyes. He pulls back just far enough to press a firm kiss to Gwedhaner’s head. “I have you, dear one, everything is going to be alright.”
#and then it was#I mean not really but they run into Luthien and Huan (who were coming to rescue Finrod from rescuing Beren) on the way home so...#Adar can at least pet a puppy about the whole thing?#Thanks to the Elvish Name Generator - Gwedhaner apparently means Bond Brother and that seemed...fitting enough#given that I needed to call him *something*#also yes- Adar was fighting against the elves trying to escape. But it was less that he was trying to stop the elves escaping and more that#when he arrived one the elves was about to decimate one of the 'only just technically an adult' uruks and....well. It's *Adar*#Will I ever get into something where Finrod learns that large number of orcs call his husband Daddy? who knows#(also sorry- I couldn't resist that phrasing... xD)#Rings of Power#ROP#Ropfanfiction
22 notes
·
View notes
Note
I dont know if you've seen anything about this yet, but discord recently partnered with generative AI (called DomoAI) and added hidden bots to servers to scrape messages and images. I know you're very open about your stance on AI so I figured it's something you'd want to know about/ look further into
okay everyone needs to learn to google and try and fact check things before they just believe anything you read or hear. i constantly see things going around discord saying some new thing is scamming or hacking or doing something bad and it's always ended up to be a hoax or misinformation or exaggerated. is discord promoting them? yes and it's shit. however, it is not made by discord, discord did not partner with them. discord is shitty for allowing ai art on their platform, however the claim they partnered with them is just a lie. discord bots exist. i have some in my server, eg pluralkit, but discord didn't make pluralkit they just allow it to exist on discord. now it seems in domo's marketing *they* called it a partnership, but it's not. they just uploaded a thing they made onto discord. that's like saying every app on the apple store has a 'partnership' with apple.
itsoasus on bluesky already listed everything out, so here's the screenshot and alt text underneath. everything in purple are their words, copy and pasted from the alt text on their post.

"This was the info I posted to a server of mine, in case this had spread far. I think I summarised it better here: The claim:
discord partnered with DomoAI
this partnership allows any user to pass images to an AI without consent
server owners are powerless against this ^ NONE OF THIS IS TRUE.
The truth:
the DomoAI people made a bot
the bot was submitted to discord's app directory, just like any other bot
discord accepted the bot to it's app directory, just like any other bot
the app directory is simply a list of discord bots that you can search through inside of discord
ALL discord bots which discord has verified are REQUIRED to use slash commands or "application commands" (right click menu on PC, press and hold menu on mobile)
if a bot dev wants access to text-based commands (like !role or !color etc), the bot has to go through a SECOND application process and prove that their bot is non-functional without such a permission
server owners CAN prevent both slash and application commands from being used
if you're in a server that has those permissions denied, the ONLY way someone can use your content in the DomoAI bot is if the person MANUALLY copies your image/text into a place where the bot CAN run
meaning nothing has changed AT ALL and this is NO DIFFERENT from feeding your image or messages into an AI any other way"
and here's how to turn off 'use external apps' thanks to glitchypsi on blue sky. it's under server settings > roles > edit role @ everyone > ise external apps

it doesn't take much time to try and fact check something. the amount of times ive seen messages on discord claiming all sorts of wild things to be true when theyre not is countless. and they always spread like wildfire because no one tries to check anything for themselves, someone just goes 'heres a screenshot of a message someone sent in a server im in' to another server and then on it goes.
i have rules in my discord server that no one is to post things like this without getting permission from a mod so we can try and fact check it, but you guys should do that yourself first. and i really didn't want to see an ask about this either.
discord lets you have the option to edit images with 'apps'. theyve had this ages. yes it sucks that some of them are ai. no i dont think they should be allowed. but it's like ai filters existing on tiktok, like tiktok didn't make them. do i think that is an excuse? no. i think generate ai apps shouldn't exist on discord. however, it is factually incorrect to say that it is something discord made or 'partnered' with, and incorrect and fearmongering to say it's in ever server (which in a technical sense like.. you can *access* it in every server, but in the same way you can access the youtube activity in every server, it doesnt mean youtube has now read all your messages).

yes that ^ is a screenshot from my discord. no domo is not in my discord. "but its there in the screenshot" its giving you suggestions of apps they have and if you want to use them. if you click on it to use it thats your fault. no, i dont think they should be there at all i think they should be banned. but again, it's like tiktok recommending you a filter, it's not some malware that's hacked into your phone or a bot thats invited itself to your discord. apps dont join your discord server like users or bots, theyre just.. there, the same way that every discord server has access to the youtube or gartic phone activities.
stop spreading misinformation. stop fearmongering. all it took to find discussions on it was searching for it on bluesky. and also the fact that.. i use discord and know the difference between a discord app and discord bot. it literally says 'apps' in the screenshot. people crying that banning it doesnt work.. yeah... cos its not a bot.. its an app.. that people can choose to use.. so just.. dont choose to use it (and yes it would be better if discord banned it) but its not a bot that discord has placed in every server idk im repeating myself now i feel like im going crazy with how many people are believing discord forced an unbannable bot into your servers when it did. not. do. that. and if you dont want anyone else in your server to be able to do it then turn off the external apps permission in your server.
#guys i dont wanna defend discord look what youre making me do. but they literally didnt do that.#the vampire answers
18 notes
·
View notes
Note
NOOOO NOT KONIG AS A SPARTAN/GREEK WARRIOR I CANNOT HAVE THAT IMAGE IN MY BRAIN I STILL NEED TO FUNCTION ON THE DAILY DAMNIT😭😭😭
I am a sucker for the warrior claims his spoils of war trope, the whole achilles/briseis from the troy movie vibes💕😫👌🏻 but with a twist 👀
König, the infamous Germanic warrior and beast of a man who has a unique station as commander in the troops of the romans (or something??? lmao don’t @me my brain rot is not historically accurate) because he possesses the perfect balanced mixture of inhuman strength and a cunning strategic mind. Hacking and slashing his way through battle after battle, some call him Ares, the God of War, because they’re convinced that whatever must be under that helmet and hood can’t be an actual human being. He seems to be living and breathing for war and the shedding of blood. That is until during one of his battles he finds himself in the raided temple of Artemis, face to face with a temple maiden who isn’t raped and pillaged by his men. Whether it’s a curse or a blessing from the Gods, he doesn’t know but he falls, and he falls hard for her. Blood is pumping to his heart, which is about to beat its way through his chest, and racing down to his dick which is even harder than after a successful battle. “An Engel” he mutters to himself, and that’s the first time the God of War takes a spoil of war, his very own temple maiden who from now on will only worship him and him alone.
König would be such a hot Spartan warrior/Greek demigod but PLEASE, you have to listen and listen carefully because… König could easily be a prominent figure in the Roman army! They had auxiliary units, Romans used “foreign” warriors all the time, Gauls and German/ic people and whatever, that’s the whole idea behind their expansion idea: to fatten their army with new recruits to push their campaigns and get more slaves to support their crazy economy etc etc
So König could be situated in say for example Germania Superior/Inferior, Raetia or Noricum auxiliary unit, I don’t know what Romans called Austria back then and if they had a separate aux. unit for them, I need to do some googling, if someone knows more about this please correct me! But *grabs you by your bra straps or shirt or whatever* you need to listen, Romans didn’t send their Auxilia to the troops’ native lands which means König would not be posted in Germania/whatever Austria was called BUT he could fight in basically any other area, and get his captive girl from some other bloody sexy violent awesome campaign!!! (Lol why am I so into this idea of him capturing some poor girl into his tent and having his way with her… I’m sorry I need to straighten my skirt and sit pretty with my knees pressed tightly together, nothing to see here, just sippin’ my tea)
No but srsly, NO, now I have to write this. Brb ->
188 notes
·
View notes
Text
Dangerously Stupid Part 2
Part 1
Donatello felt he was in a daze. He had checked himself top to bottom and found no concussion (thankfully) and nothing more than a few scrapes and bruises. So that ruled out brain injury as the source for why he couldn’t focus on any of his work in the full day since. He kept getting distracted by…. You.
Donnie has a device that picks up the signal from any cell phone or smart device he comes within 30 feet of while out on patrol, and automatically registers the information of that device into his system. This comes in handy when the need arises to erase any photos or data that may come up on these phones involving him or his brothers, and to monitor the whereabouts of any thugs or civilians they may come in close contact with. Meaning, he had your phone number, right on his screen in front of him. He knew this may seem creepy but it was for security purposes, and Leo said he always needed to monitor any civilians that got close to them for safety. That was his job. And also his job to find your current location registered on your phone in your apartment. …..And your wifi network, and your laptop currently hooked up to said wifi network. It showed you were actively using it. He wrestled with himself for a moment about respecting your privacy, but curiosity got the better of him, and he quickly took a peek at what you were currently looking at on your screen. ……It was a google search on how to give yourself stitches from home. What??? Surely you weren’t- were you scrolling through poorly drawn reference pictures on a wiki-how page?!?! You then switched to another tab and googled ‘can I use a sewing needle and thread to give myself stitches’. Donnie paled. The next search: ‘how to disinfect thread’.
He put his face in his hands and groaned. Did you not go to the hospital last night?!?! What were you thinking? He looked back up and noticed the screen had been idle for a few minutes and he was getting really worried. He quickly hacked your laptop camera, privacy be damned- to take a look to see if you were okay. The image that was brought up was an empty chair, and in the background was a cozy warm looking apartment. But there was no movement. You hadn’t fainted out of your chair had you?! He was starting to panic when you suddenly came back into screen, moving slowly and almost falling back into your chair wearing the same pants you wore last night. You had on a small tank top with the strap down, and a bloodied white towel slung over your injured shoulder, carrying armfuls of supplies that you set down on your desk by your computer with shaking hands. You looked far more pale than you had last night.
“Alright let's see…. Next it says to soak the thread and needle in the disinfectant for about 10 minutes…. I hope the thread is long enough. Hmmm… I don’t have sterile gloves so hopefully washing my hands well is good enough…” You thought out loud to yourself. Donnie was about to smash his head on his desk from your careless words. He couldn’t take it anymore.
“What the SHELL do you think you’re DOING?!?!” After a few quickly typed commands he was patched into your laptop’s audio and yelling into his microphone, causing you to jump- startled from where you were about to reach into the bowl of disinfectant to grab the needle after only 5 minutes. You instinctually started to lower the volume on your laptop, cursing about ads on these websites always popping up and surprising you.
“No no no! I’m not an ad- wait a minute-” Donatello quickly typed in some more buttons and your screen froze to allow his webcam feed to pop up and take over your screen, making you gasp and almost fall out of your chair. “Stop that! You’re doing to hurt yourself- well, more than you already are. You’re going to give yourself an infection!! What were you thinking-”
“IT’S YOU!!!” You shouted in surprise, holding onto your desk so you didn’t fall. If not for the deep cut still oozing from your shoulder and the attempted robbery from last night rerunning on the 6 o’clock news, you would have assumed you had dreamed of your fated meeting with the large turtle men. After waking up in a cold sweat on your couch late that afternoon, you had instead decided to focus on giving yourself first aid. “How did you- what?” You babbled trying to figure out why the purple masked man’s face was currently lecturing you from your computer screen. A worrying wave of lightheadedness made you grip your desk tighter.
“I hacked your computer. Anyways, WHY AREN’T YOU AT THE HOSPITAL?!!!” Donnie shouted in exasperation. He barely registered the sound of his lab door opening as his shouting probably attracted the attention of one of his brothers.
You stared at him blankly for a moment, waiting for your brain to restart and register his questions after the shock of getting to see him again. “I… I don’t have health insurance.” You said a bit bluntly, settling back into your chair heavily, and bracing your good arm against your desk as a new wave of nausea overtook you from your racing heartbeat.
“....what was that?” Donnie quickly turned around to acknowledge Leo, who had entered the door and taken up a spot leaning against the back of Donnie’s chair watching the interaction play out. At least of all his family, his most level headed brother had come in.
You still heard the faint question and continued. “My new job… I just moved to New York two months ago for my new job. They promised me a good starting salary and a full time position, but after only 3 weeks they started cutting back on my hours. They don’t pay benefits to part timers, so I’ve already lost access to my health insurance. ….They really screwed me over, so I’m just working for them until I find a new job. I really, really, can’t afford a hospital visit after this expensive move, so….” You gently motioned to the white towel on your shoulder, a startling spot of red starting to seep through. Leo recognized the location of the wound from last night. The two brothers felt their gut clench remembering how you had gotten it. In defense of Donnie’s life.
You were starting to slouch more over your desk, your head spinning, and your laptop’s microphone now picking up your labored breathing. Leo could see the red flush drain from your face, and Donnie recognized the symptoms. Most likely, you were about to lose consciousness.
“Wait wait wait, hold on stay with me.” Donnie quickly ordered you through his mic, his tone becoming more serious. He quickly typed into his keyboard, now understanding the situation a bit more, and the gravity of your condition. “Do you have any roommates, anyone staying with you right now?” With a level tone he asked you some standard questions to keep you conscious as he robotically pulled up your current address. Leo had already left the room to rally their brothers and gather the first aid kit, clearly already on the same page.
“…. no. Just me.” You said quietly, now focusing entirely too much on staying upright. You really felt like you were going to throw up now. But you were too busy wracking your dizzy brain for what his name was…. D…. Donna… Donnie…. “Donatello?” You said out loud, trying to focus.
“Yes, (y/n?)” He quickly answered as he continued to quickly type something on his keyboard, he was glancing between you and another screen at his desk every other second. You smiled. He remembered your name. “We are coming to see you. If you can, try to leave your window unlocked, and go lie down on your couch or your bed. What is your apartment number?” He was quick and clear with his orders, speaking like a true doctor, you thought blearily. But you were too out of it to question how or why he was coming over.
“Mmm… Room 517, 6th floor.” Gosh why did you ever think you could do this on your own. You suddenly felt really stupid. You were trying to take care of yourself so you wouldn’t have to rely on your family for help with medical bills, but now you were just causing problems for the kind hero you met last night. “I’m sorry Donnie… I think I’m gonna pass out.” You said apologetically, head going to rest tiredly on your table next to your computer. You could distinctly hear the sound of the city filtering in through your cracked open window behind you in the living room. Your dizzy spell gripping you much stronger than it had earlier when you had first moved to stand after sleeping all night on the couch. The next thing you hear is the rattle of plastic wheels scooting as presumably Donatello was standing from his desk.
“Don’t be sorry. We’re coming to help you now, okay? Just try to stay awake.” There was a whoop and some excited chattering in the background now and some more keys being hit from his consol. “I’ll see you soon.” Came the quick but warm reply from the purple masked turtle as his webcam feed disappeared from your laptop.
A silence hung in the room. As if it had never happened. You shifted to look up at the screen detailing a poorly drawn cartoon image of a needle poking at the edge of a wound looking back at you, and groaned audibly. Burying your dizzy head back into your good arm for a moment, you tried to sit up to go move to the couch to wait, careful not to bump into the bowl of antiseptic holding your good sewing needle and black thread. Only moments earlier you were about to try and sew up your shoulder like you were hemming a new pair of pants, only to be caught by one of this city’s apparent mutant super heroes you had met only just last night. And now he was coming here. To help you.
Feeling another huge wash of dizziness pass over you, almost making your knees buckle as you stumbled over to the couch, you felt a larger twinge of pain in your shoulder again. Taking a seat on the cheap couch cushion, you reached up to move the towel you had soaked in the antiseptic aside to inspect the wound. You must’ve stretched the skin when you were startled earlier, because the wound was leaking deep red again as a small trail started to escape down your arm before you could stop it. Must’ve been deeper than you thought.
That was your last thought before you passed out, head lightly falling against the couch.
✨✨✨✨✨
“Are we almost there yet?? Ow!” Mikey called out ahead to Donnie before getting the back of his head smacked by Raphael. They were racing across rooftops making a beeline for your apartment building. Donatello, who usually gave sassy directions from the rear, was silent and serious leading the charge with Leo close behind carrying their largest portable first aid kit.
Leo was keeping a close eye on his younger brother. When he walked by Don’s lab earlier, attracted by the shouting, he was startled to find his younger brother was talking to the person who had saved him the night before. Before he could question why, or get into his lecture about the dangers of contacting a human they only just met, he saw the look on his brother’s face. Donnie’s expression was beyond distressed. His usually level headed brother was shouting and worried because a civilian who was kind enough to step in and take a hit for him while he was down was- from what it looked like- still bleeding, almost 18 hours after the attack. And even worse from what he heard walking in, had no means of access to medical attention. He could understand Donnie’s frustration, but he was still surprised his brother had gotten this worked up.
“Hey…. Donnie,” Leo called out. “Everything alright…?” He said just low enough that it wouldn’t draw the attention of their brothers.
Donnie knew what he was getting at, so he cut right to the point. “I caught them before they could try and suture their own wound. With a sewing needle.” Donnie took a very very deep sigh. “By following a wiki-how tutorial.” Leo almost tripped off the building.
“….what?” He responded smartly.
There was a loud snort from behind them. “Sounds badass.” Raph deadpanned and Mikey wore an expression of surprise followed by a quietly muttered ‘dude…’
Donnie groaned audibly. Thankfully your apartment building was now in sight. “I need to make sure their wound is properly disinfected before stitching it up. It’s the least I can do…” He thought back to last night. The long stare you two shared, and the concern and lack of fear you held for him in your eyes. He longed to see those eyes again…
The building next to yours was at just the perfect height to leap across from the roof to your room’s fire escape. Leo was the first to land and give the all clear for his brothers to follow. Leo opened the window and stepped in just barely before Donnie practically toppled him over pushing past him to get inside. Snatching the first aid kit off Leo’s shoulder, Donnie quickly found your still form on the couch.
“Right… we’ll stand guard. You’ll let us know if you need any help, okay Don?” Leo offered. Mikey pushed in through the window and made a beeline for the fridge, and Raph took a seat on the windowsill peaking in curiously.
“Yeah, Leo.” Donnie knelt quietly next to your form on the couch. All his attention was already on you.
Leo went to stand around the living room trying to find the walls interesting while occasionally glancing at Donnie’s work, trying to stay out of the way.
Don checked you over, breath taken seeing your face again up close in the warm light of your apartment. Your breathing was deep and steady. Good. A little sweat on your brow, he looked down to see angry inflamed red skin peaking over your bare shoulder. He carefully moved the towel, stained in dried blood, and winced as the fabric pulled unstuck from the sticky bloody wound.
You flinched, and Donnie felt his breath catch in his throat. But you did not awake, so he swallowed and signed, reaching down to open his medkit and take out a disinfecting wipe. The little damp pad unfolded and he carefully began to clean away the dried and sticky blood from around your cut so he could get a better look at the damage. There was definitely irritation but he hoped that no infection had taken hold yet. Next he disinfected his hands and pulled out his suture kit, and with practiced ease began to stitch up your shoulder.
About 15 minutes later, and about 10 stitches into fixing you up, your eyelids fluttered open. The poking and pulling around your painfully sensitive cut had finally woken you up. You still felt dizzy and light headed, so made no sudden movements. Glancing down you saw the light reflecting off of a large polished shell. That’s right, Donnie. You still had a hard time grasping your current situation. Maybe you were in a fever dream. But there was the strangely handsome face of a mutant turtle sewing up your shoulder with his tongue poking out of the corner of his mouth in focus. His large goggles down over his eyes and a portable lamp light over his shoulder illuminating his work.
You felt the poke of a new stitch and this time flinched with a little muttered “Ouch!” and suddenly you were blinded by the light hitting your face as Donnie startled and turned to face you.
“Oh! You’re awake! Um… Sorry I’m uh… not quite done yet. I hope this is okay-” He quickly mumbled. His free hand that braced your shoulder gave an encouraging squeeze.
You blinked a moment as your eyes adjusted to the light. He glanced back at his work and back to you and you nodded twice.
“I need you to hold still for just a few more minutes, I’m just about finished. Okay? It’s going to sting a little.”
“...yeah. Got it.” You nodded, feeling your head quickly clear up as you felt the pinch and sting of the needle again, bracing yourself to hold still while your brows tensed from the discomfort.
You looked around your room to distract yourself from the pain. Looking across your coffee table you saw one of the other turtle mutants, the one wearing the blue bandana and caught his eyes for a moment before he quickly averted them to pretend he wasn’t staring. But after a moment he looked back at you and offered a quick nod in greeting. You supposed he might be a little shy and was trying to hide it. By your window you also caught the large cracked shell of another one. He glanced over his shoulder and met your eyes, studying you for a moment as you also took in the scar on his lips and the toothpick, before he also nodded at you with a little ‘hey’ in greeting.
“Yo, is dudette awake? Morning sleeping beauty!” An energetic orange masked turtle man, holding a half full can of your soda, practically jumped into your line of sight, startling you a bit with a gasp. “You remember me? I’m Mik- Ouch! Leo!!” The blue masked turtle called Leo smacked him on the back of his head to quiet him with a shush.
“Mikey, I’m still working. Don’t freak them out.” Donnie quickly added, making sure you weren’t gonna move again before continuing.
“Yeah genius, your ugly mug almost made em’ pull a stitch. Save the dramatic introductions for later.” The red masked turtle sneered at Mikey. You vaguely recalled him being named ‘Raph’.
Leo, Raph, Mikey, and… “Donnie?”
You caught yourself saying out loud, making said turtle jump a little.
“Y-Yes, (y/n)?” He stuttered as he helped carefully pull you into a sitting position. The stitches were finished and it was time to wrap the wound. He reached into his bag and pulled out a package of fresh gauze.
You carefully watched him unwrap the gauze, his hands slightly shaking. “How do you know each other?” You asked him, meeting his eyes, then looking over to the others spread out in your living room.
“Brothers. We’re brothers.” Leo answered helpfully.
“Brothers… that makes sense…” You considered how they all acted around each other and smiled warmly, looking back to meet Donnie’s eyes.
He was lifting up his goggles back to the top of his head and his eyes widened at your expression. He turned away to put his tortoiseshell glasses back in place, clearing his throat.
“Yes, they’re… my brothers.” He tentatively smiled back at you, and began to wrap up your shoulder.
You watched him thoughtfully for a moment, and glanced over at his brothers now quietly arguing about something over by the window. Mikey quickly looked back over at you with a bright smile before turning back to the conversation animatedly and shushing his brothers a little, earning him a smack as Raph and Leo both also shared a look with you briefly. You raised a curious brow at the antics. They were like gossiping school kids… definitely brothers.
“Hey Donnie… Sorry for causing you all trouble like this. …I didn’t want to involve anyone and thought I could handle it myself.” You said looking down. “....Thank you for coming to my rescue.” You looked up to meet his gaze and smiled at him.
“No no, this is…. It’s the least I could do. After all, I should be the one thanking you. You got this injury from coming to my rescue, I…. Thank you.” His hands stilled a moment in the midst of his wrapping and gave you a shy smile. He looked kind.
Donnie finished the rest of the wrapping slowly, fastening the end in place carefully.
“Um… You should change the wrapping every other day. Call me if there’s any trouble, like puffy redness around the stitches or if it starts bleeding or starts to show signs of infection-”
“Hey-” Leo suddenly cuts Donnie off, making you both look over to him where he was emerging from the group huddle.
“How about, we come back- *ahem* Donnie, comes back again to check on you in a few days. Does… that sound good?” He asked carefully. Mikey jumping around excitedly in the background and getting a playful push from a grinning Raph. You turned with a raised eyebrow to Donatello. He was currently gawking at his older brother, glancing back between you and the blue leader. You couldn’t help but giggle a little at the antics.
“...Sure. I’d love that. If… you don’t mind, that is?” You asked the flustered purple masked mutant.
“I- I- Yes. Yes, of course. It would be my pleasure. Um. S- Next Saturday then? If you’re free?” He gathered himself and asked you kindly.
“That would be perfect.” You smiled widely, taking his hand in both of yours. “It would be nice to see you when neither of us are in danger for a change.”
Donnie’s eyes seemed to soften as he looked at you warmly. “I would like that. Very much.” He held your hands back softly as he rose from his seat beside you. His brothers were already starting to filter out through the window, except for Mikey who was hooting and hollering quietly before getting bodily pulled through the window by his two older brothers.
“So… next Saturday night? 9pm?”
“I’ll be here.” You responded, following him to the window. He carefully climbed out onto your balcony. He waved a final goodbye to you as he perched on the railing, and with a mighty jump, he leapt out of sight. You lunged for the railing where he just stood, looking out above you hearing whoops and cheers from the brothers as you caught a final sight of them running over the city skyline. And with a deep breath of the cool night air, you sighed in relief that you weren’t dreaming.
Leo, Raph, Mikey, and
Donatello. You’ll have to remember that. You thought with a grin.
To the people who wanted to be updated when part 2 was released. Sorry for the long wait!! Thanks for the support!
@saspas-corner @misfortunekeep @valen-yamyam16 @genesis378
#tmnt fanfic#tmnt x reader#tmnt bayverse#tmnt bayverse x reader#bayverse tmnt#bayverse donatello#bayverse tmnt x reader#bayverse!tmnt#tmnt bayverse imagines#tmnt 2016 x reader#tmnt 2014 x reader#bayverse donatello x reader
313 notes
·
View notes
Text
I hc that Technopolians don’t say “crocodile tears” bc they don’t know what crocodiles are due to being locked in that dome and manipulated by Computer Supreme for over 5 generations (according to Google a generation is actually 20-30 years not 100), so instead they say “command/cry” or “emote/cry” (“command/emote slash cry”) or “e/cry” and “c/cry” for short, like a frickin’ Roblox emote admin command hack 😭😭😭
Ex: That was the fakest command/cry I’ve ever seen in my life.
Ex 2: She really hit e/cry!
Ex 3: You can spam c/cry all you want, that’s not working on me.
Ex 4: Hitting emote/cry isn’t going to get you out of this one.
Y’all got any other goofy Technospeech headcanons? Or should we call it…. Technopoglish??
30 notes
·
View notes
Text
As November’s U.S. presidential election draws closer and the campaigns of former President Donald Trump and Vice President Kamala Harris kick into high gear, so have efforts by hackers from Washington’s adversaries aimed at disrupting or influencing the vote. One adversary in particular is playing an increasingly prominent role: Iran.
Iranian state actors have stepped up their efforts to interfere in this year’s election through online disinformation and influence operations as well as cyberattacks on both presidential campaigns, three U.S. agencies—the Office of the Director of National Intelligence (ODNI), the Federal Bureau of Investigation (FBI), and the Cybersecurity and Infrastructure Security Agency (CISA)—warned in a joint statement on Monday.
They’re not the only ones sounding the alarm. In the past three weeks alone, current and former intelligence officials as well as cyber threat researchers from Microsoft and Google have shared a growing body of evidence of Iran’s hacking efforts. As several of them have pointed out, Iran’s targeting of U.S. elections isn’t new—hackers linked to Iranian security services have attempted to interfere with presidential and midterm races dating back to at least 2018.
However, “Iran perceives this year’s elections to be particularly consequential in terms of the impact they could have on its national security interests, increasing Tehran’s inclination to try to shape the outcome,” the U.S. agencies wrote in their statement. “We have observed increasingly aggressive Iranian activity during this election cycle.”
Trump and his acolytes have been particular targets of Iranian hacking, with some former intelligence officials speculating to Politico that efforts to compromise their email accounts could be part of an effort to assassinate U.S. officials in retaliation for the 2020 killing of Iranian Gen. Qassem Suleimani during Trump’s presidency.
In their statement on Monday, the FBI, ODNI, and CISA officially blamed Iran for the so-called hack-and-leak operation against Trump’s campaign that the campaign made public earlier this month. Those tactics, mirroring Russia’s breach of the Democratic National Committee during the 2016 election, are only one part of Iran’s election interference efforts along with broader disinformation campaigns aimed at sowing discord among the American electorate.
“Iran, especially because of the past events with Suleimani, they have a marked interest in this election,” said retired U.S. Army Col. Candice Frost, the former commander of the Joint Intelligence Operations Center at U.S. Cyber Command. “They have attempted to message on past elections,” she said, but “I think this one is almost personal to them.”
Iran’s relatively elevated profile and more brazen cyber efforts may also be spurred by the ongoing conflict in the Middle East between U.S. ally Israel and Iranian proxies Hamas and Hezbollah, Mohammed Soliman, director of the strategic technologies and cybersecurity program at the Middle East Institute in Washington, D.C., told Foreign Policy. “I think the timelines have collided [between] regional confrontation with Israel and the U.S. elections,” he said. “This made them more proactive in attacking high-value targets that have brought massive visibility to their work.”
Iran is not the only adversary officials in Washington are concerned with—election interference efforts by Russia have been extensively documented, and U.S. officials have increasingly warned about China’s shift in cyber tactics from espionage to more disinformation and disruptive campaigns. Those two countries remain the prime threats, in large part because their capabilities are relatively more sophisticated.
“Russia and China are really a league of their own,” said Frost, currently an assistant professor at Georgetown University’s Center for Security Studies. “We oftentimes discount Iran and North Korea, and then you’ll have something like the Sony hack or this hack [of the Trump campaign]. So it’s not necessarily the level of advancement or competency that they have, but the fact that they kind of found a vulnerability and have been able to exploit that.”
“Any nation that has an interest or perceived stakes in the outcome of a U.S. presidential election is going to be thinking about how to influence that outcome,” said Gavin Wilde, a senior fellow in the technology and international affairs program at the Carnegie Endowment for International Peace and a former U.S. national security official. “It’s easy to point to Russia and China as the most adversarial and the most sophisticated, but every nation around the world has some perceived interest in the outcome, and so I think we need to calibrate along those lines.”
Officials and experts say the U.S. government has learned from the missteps of previous elections, particularly 2016, and is better prepared to defend this November’s election from cyber threats than it has ever been. Part of that is the shift to publicly calling out adversaries and their activities much earlier in the process and adopting a form of sunlight-as-best-disinfectant strategy, like the ODNI, FBI, and CISA did this week with Iran.
“It’s very hard to counter that narrative once it gets into the American psyche and our citizens’ spheres of influence,” Frost said. “But I do see the focus and calling out [of] this behavior. … That is what we’re seeing at a much faster pace, and I give the current intel community a lot of props for doing that early.”
But Wilde warned that while U.S. officials are “unquestionably” more prepared this time around, they also now need to be careful about showing their work without inciting panic about elections being compromised. “The tightrope they now have to walk is [being] helpful without creating the very kind of panic that might itself undermine confidence in the election,” he said, adding that it’s also important to draw distinctions among hack-and-leak operations that have become “a new normal” for political campaigns, election influence efforts that can sometimes be hard to legally define, and actual efforts to interfere with the ballot box itself.
“I think the most consistent thing from all of them is how much it’s been a lot of just entrepreneurialism and experimental spaghetti-against-the-wall tactics to kind of just see what works,” Wilde said. “The U.S. and everyone has to be careful not to inadvertently incentivize this activity by making too big a deal out of it, and luckily I think we’ve done a lot better this go-round than we did in 2016.”
15 notes
·
View notes
Text
On Tech Support
On May 5, 2023 I got a call that changed my life.
I had just accepted a job offer to work for the Browser Company of New York!
I walked up the stairs to our apartment with great news and my wife told me to sit down. My Mum had called. My Dad had to be rushed to the hospital. He was bleeding internally and it looked like he was suffering renal failure. We flew out to be with him and my Mum. He passed away 9 days later.
My Dad is one of the reasons I’m good with computers.

Dad went to college to learn how to use computers back in the 70s — this was back when computers would take up whole rooms and you had to input commands with punch cards.
He brought home our first home computer in the late 90s; a chunky Compaq Presario that clicked like a bottle nose dolphin as it chugged along. The Compaq was mainly for his side hustle (a carpet cleaning business) and for me and my brothers to do our school work (the side hustle was helping to pay our school fees), but it quickly became my direct portal to the skateboarding article on Encarta and pokemon.com.
Dad’s main job was the night production manager for the Royal Gazette — a job he had for close to 40 years. He would often talk about how he missed the sound of a newsroom. The clacks and thunks of typewriters, the ringing of phones, the chaos of people coming together to make a paper every day. I couldn’t imagine how the Gazette could ever have been a loud place when I would visit him at work. It was deafeningly quiet! He would plop me in front of a computer to play Minesweeper and the only sounds you could hear were my mouse clicks.
Since Dad worked at night, he had a good chunk of hang time waiting for the paper to be ready to go to production. He would listen to internet radio stations, read interesting articles and forward dirty joke emails from his coworkers. When I left home for university my procrastinating study hours and his work hours would sync up. We would email each other links to cool music, videos, articles and, since I was old enough, the odd dirty joke email forward. But we mostly just chatted.
We started saying “I love you” over email
He was a great writer — he wrote just like he spoke — and both of our conversation styles lent themselves to the time delayed back and forth of email. I say something, you read it and think about it, you send a considered response back with a little something extra. Repeat.
We started saying “I love you” over email. We were always close, but we both had a hard time talking about our feelings especially when I was a teenager. Being apart, but still staying in touch over email gave us the space to feel comfortable saying we loved each other. We had no trouble saying it after that — it was one of the first things we said to each other when I could finally come home for Christmas in December 2022.
Tech is very expensive where I come from (about 30% more expensive than the US), so whenever I go home I roll up like Tech Santa with a bag full of laptops, tablets and phones. The Compaq Presario was long gone and Dad’s laptop had seen better days. Dad was a long time Windows user — he wrote his memoirs in Microsoft Word — so he was keen to stay on something familiar.
I got him a Surface Laptop 3. I walked him through setting up Windows 11. I arranged his bookmarks bar in Chrome so he could quickly access his email, Facebook, Youtube and, most importantly, his memoirs which we’d uploaded to Google Drive. He was so happy to have all of his stuff moved over to his new computer and relieved that his memoirs were properly backed up.
Going through his browser after he died was some of the most heartbreaking work I’ve ever done
After he passed away I helped my Mum with the gut wrenching task of cleaning up Dad’s digital life. I made sure she had access to his email and important logins so she could deal with closing accounts and adjusting billing names. I also memorialized his Facebook page to ensure it didn’t get hacked and start spamming friends and relatives with crypto scams.
Dad had several strokes leading up the internal bleeding and renal failure in May 2023. Honestly back in Christmas 2022 he had only recently recovered from his last stroke and he wasn’t quite himself. Going through his browser after he died was some of the most heartbreaking work I’ve ever done. The bookmarks bar that we had carefully set up together was riddled with duplicates — Facebook, Youtube, Google Drive over and over spilling out into a drop down menu. My Dad knew his way around computers. He had been using them since they took up a whole room. I knew some damage had been done after the strokes, although he was very good at hiding it and I don’t think I was ready to admit it at the time. But with him gone and looking into his computer, his window to the world, I couldn’t deny what I had known for at least a year. My Dad had strokes, my Dad had internal bleeding, my Dad was dying, my Dad was gone.
These things — computers, web browsers — they’re not just inert tools waiting to be picked up and used. The more you use them, the more they become a part of you and you of them. The laptop lid gets scratched, coffee is spilled onto the keyboard, cords become frayed, bookmarks get bundled up into folders to be forgotten, passwords get scribbled on sticky notes and then reset again, tabs sit open for months just in case, URLS and search queries are typed in repeatedly just because you’ve built up the muscle memory — facebook, youtube, google drive, pokemon.com.
We’re all about to be new at this again
A developer friend of mine once said to me, “the future is here and we’re all bad at it”. University level STEM students don’t know how file paths work, they don’t teach kids to type anymore and more and more jobs across a variety of fields require some degree of computer literacy. Everyone is expected to just know how to use computers, but as my Mum would say “I’ve never had a lesson!”. As we head into the next phase of computing — where you work with the computer instead of simply using the computer — much of your interactions will be through AI language models, but even the people building those don’t really know how they work. We’re all about to be new at this again — new at computers, new at web browsers, new at everything. Now more than ever, we’re all going to need some help. Hopefully that help comes from someone who understands what you’re going through, what you’re trying to get done and can meet you where you’re at.
What we’re building is so much more than just a portal to websites
On June 5 2023 I started a job that changed my life. I started working at the Browser Company of New York!
I help to build Arc, a product that I love, with some of the most talented, thoughtful and inspiring people I’ve ever met. I helped bring Arc to Windows, so people like my Dad could use this very special browser that feels like my home on the internet.
I truly feel like I’m doing the best work of my life and that’s because what we’re building is so much more than just a portal to websites. It’s where you do your work. It’s where you hang out with friends. It’s where you pirate anime, do your taxes and send emails to your Dad.
It’s where you live your life. As we continue to build I hope to be that human voice on the other side of the computer that helps you feel like Arc is for you, for your stuff, for your life. I want to help Arc feel like home. See you on the internet ✌️ Love you, Dad!

3 notes
·
View notes
Text


youtube
"Bug Droid" Google Android Balancing Robot, by OLogic, CA, USA (2011). "To keep OLogic going while we tried to figure out how to get AMP out the door, we spent our time picking up robotics consulting jobs. We were able to get a one-off project to build some little balancing Android robots for Google, and tour them around to events like Google IO, Google Sandbox, and Google Zeitgeist in London. Bob and I had lots of fun—it felt like a traveling circus, bringing our robots to all of these events." – Ted Larson, From HomeBrew to Hasbro How two friends hacked a balancing robot and wrote a toy story of their own.
"The Google Android Balancing Robot by OLogic turns the iconic Google Android into a two-wheeled balancing robot. It seemed fitting for him to be a balancing robot because although he has legs, he never uses them, just floats around. No Android is complete without the his own Android App, to control him. The app. allows him to be driven around, speak, play music streamed from the phone or tablet, change the color of the lighting in his head, and turn his head from side to side. He also responds to a variety of voice commands using Google Cloud services." – Google Android Balancing Robot, OLogic.
5 notes
·
View notes
Text
0 notes
Text
Master 2025 Digital Marketing: SEO, Paid Ads, GA4, GTM & More in One Power-Packed Course! 🚀

The digital marketing world is fast, competitive, and constantly evolving. Whether you're running a small business, managing marketing for a company, or planning to launch your own brand — mastering every corner of digital marketing is no longer optional. It's essential.
But here's the challenge: Should you learn SEO first? Or jump into paid ads? What about GA4, GTM, social ads, and YouTube marketing?
Instead of bouncing between multiple courses and scattered tutorials, imagine having one powerful course that brings everything together — SEO, Google Ads, YouTube Ads, GA4, Google Tag Manager, and more — all updated for 2025.
That’s exactly what the All-in-One 2025 Course: SEO, Paid Ads, GA4, GTM And More! offers. It’s not just a course — it’s your complete marketing command center.
Let’s break down why this course is an absolute game-changer for your growth in 2025 and beyond.
🎯 Why You Need a Comprehensive Marketing Course in 2025
Digital marketing in 2025 is no longer about picking one channel and running with it. To actually generate leads, conversions, and ROI, you need:
A high-ranking website (SEO)
Targeted ad campaigns (Google, YouTube, Meta)
Smart tracking and measurement (GA4 + GTM)
Content strategy that resonates
Skills to manage cross-platform strategies efficiently
The All-in-One 2025 Course simplifies your journey. It brings all of these components under one digital roof — helping you stop guessing and start executing with clarity.
🚀 What's Inside the All-in-One 2025 Marketing Course?
Let’s dive into the core modules of this course and what makes them powerful.
✅ 1. SEO Mastery for 2025
Learn how to rank your website higher on Google — the right way.
Keyword research tools & techniques
On-page SEO: titles, meta tags, headings
Off-page SEO: backlinks, citations, guest posts
Technical SEO: site speed, mobile-first indexing, crawlability
Local SEO hacks for visibility in your area
And yes, it includes the latest 2025 updates from Google’s search algorithm!
✅ 2. Paid Ads That Actually Convert
Tired of burning money on ads? Learn how to run smart, profitable campaigns.
You'll get hands-on training on:
Google Display Ads (including advanced targeting)
YouTube Ads that keep people watching
Google Search Ads with top-tier copy
Meta and Instagram Ads
Campaign optimization techniques
It covers the complete Google Display Ads system, fully integrated with this top-tier Google Ads Masterclass. That’s a huge bonus.
✅ 3. Google Analytics 4 (GA4) – Understand Your Audience
Most marketers struggle with analytics. This course makes GA4 your best friend.
Set up GA4 like a pro
Create custom reports and dashboards
Understand traffic sources and user behavior
Track conversions and user flows
Build goals and event-based measurement
You'll no longer be flying blind. GA4 tells you what’s working and what’s wasting your time.
✅ 4. Google Tag Manager (GTM) – Track Everything with Precision
Tag Manager is your secret weapon for event tracking and analytics customization.
In this course, you’ll learn:
How to set up GTM from scratch
Adding and managing tags for GA4, Ads, and custom events
Tracking form submissions, button clicks, video plays
Troubleshooting errors and testing tags
Advanced tracking strategies (without touching code)
Perfect for marketers who want more control without needing a developer.
✅ 5. YouTube Marketing – Win Attention in the World’s 2nd Largest Search Engine
Videos are king, and YouTube isn’t slowing down.
Create video content that grabs attention
Set up a branded channel that converts viewers into fans
Learn how YouTube Ads really work (Skippable, Bumper, Discovery)
Analyze YouTube Analytics to refine your content strategy
You’ll also learn how to use video remarketing — a powerful way to re-engage users and drive conversions.
💡 Who Should Take This Course?
Whether you’re a beginner or a seasoned digital marketer, this course is built to deliver impact.
Perfect for:
Freelancers and agency marketers looking to expand skills
Business owners wanting full control of their marketing
Entrepreneurs launching a product or service
Students and job seekers aiming for high-paying digital roles
Bloggers and creators growing personal brands
It’s designed to be beginner-friendly but includes advanced techniques that even pros will find valuable.
🎓 Real-Life Skills You Can Apply Immediately
This course goes beyond theory. Each module includes real examples, step-by-step walkthroughs, and actionable assignments.
What you’ll walk away with:
An optimized website that shows up on Google
Working ad campaigns driving real traffic
Clean GA4 dashboards giving you deep insights
A fully functional GTM setup to track every conversion
Video content strategies that build authority
A marketing system that works 24/7 — even while you sleep
📚 Bonus Tools, Templates, and Strategies
Included in the course:
SEO Audit Templates
Ad Campaign Planning Sheets
Keyword Research Toolkit
Content Calendar Framework
Budget Optimization Spreadsheet
GTM Tag Checklist
GA4 Custom Dashboard Template
These aren’t just add-ons. They’re tools you’ll use in your daily workflow.
💼 Get Certified – Build Your Resume & Portfolio
After completing the course, you’ll receive a certificate you can proudly showcase on:
LinkedIn profiles
Freelancing platforms
Job applications
Client proposals
It’s a sign that you don’t just “know marketing” — you’ve mastered it.
🔥 Why This Course Stands Out from the Rest
There are thousands of digital marketing courses out there. But here’s why this one matters: FeatureOthersThis All-in-One CourseCovers SEO, Ads, GA4, GTM, YouTube❌ Partial✅ Yes, complete coverageUpdated for 2025 strategies❌ Often outdated✅ Latest industry updatesHands-on, project-based learning❌ Mostly theory✅ Yes, real-world skillsIncludes templates, tools, and walkthroughs❌ Rare✅ IncludedOne-time access, lifetime updates❌ Sometimes expires✅ Lifetime learning
It’s everything you need in one course to become a top-tier digital marketer in 2025.
💬 What Students Are Saying
"This is the only course I needed. I launched my agency and now manage five clients!" – Meera R., Digital Marketer
"Finally, someone made GA4 and GTM easy. I now track every click on my site." – Thomas L., E-Commerce Business Owner
"I took this course before my job interview and nailed every question. Thank you!" – Priya M., Digital Marketing Executive
🧠 Why Learn Everything in One Place?
Learning marketing in silos doesn’t work anymore. You need an integrated approach — SEO needs to work with your ads, ads need to feed your data, data helps you create better content, and so on.
The All-in-One 2025 Course: SEO, Paid Ads, GA4, GTM And More! gives you this complete system. You don’t need 5 different instructors and platforms.
It’s all here. Built for clarity, speed, and results.
📈 What Will You Achieve After This Course?
If you’re ready to stop guessing and start growing, here’s what you’ll gain:
✅ Your site ranked on Google ✅ Campaigns that attract the right audience ✅ Crystal-clear tracking and analytics ✅ A strategy that scales with your goals ✅ Confidence to take on clients or build your own brand ✅ A portfolio to prove your expertise
🎯 Final Thoughts: Your Future in Marketing Starts Now
It’s 2025. The tools are smarter, the competition is sharper — and your skills need to keep up.
The All-in-One 2025 Course: SEO, Paid Ads, GA4, GTM And More! is the shortcut to mastering modern digital marketing, all from one reliable, up-to-date source.
If you’re ready to build a career, grow your business, or elevate your digital skillset — this is the course that will move the needle.
Don’t just market. Master it.
0 notes
Text
Les 7 applications Android que tout hacker éthique doit avoir
L’univers de la cybersécurité évolue rapidement, et avec lui, les outils à la disposition des hackers éthiques. Que vous soyez débutant souhaitant apprendre les bases du hacking ou professionnel expérimenté en quête de solutions mobiles performantes, il existe aujourd’hui des applications Android puissantes qui vous permettent d’analyser, protéger et tester la sécurité d’un réseau ou d’un système directement depuis votre smartphone. Dans cet article, je vous présente les 5 meilleures applications Android que tout hacker éthique doit avoir, utilisables sans PC. 1. Termux – Le terminal Linux dans votre poche Pour tout hacker éthique, la maîtrise de la ligne de commande est essentielle. C’est là qu’intervient Termux, une application qui vous offre un terminal Linux complet directement sur votre Android, sans root. Avec Termux, vous pouvez : Installer des outils tels que nmap, hydra, ou sqlmap Écrire et exécuter vos propres scripts en Python, Bash, etc. Gérer des paquets via le gestionnaire APT Grâce à sa légèreté et sa compatibilité avec F-Droid, Termux devient le point de départ idéal pour tout environnement de test mobile. 📥 Télécharger Termux sur F-Droid 2. Kali NetHunter – La puissance de Kali Linux sur Android Une fois familiarisé avec l’environnement Linux grâce à Termux, vous pouvez passer à un niveau supérieur avec Kali NetHunter. Développée par Offensive Security, cette plateforme regroupe les principaux outils de test de pénétration dans une interface mobile. Ses atouts : Attaques man-in-the-middle (MITM) Injection de paquets, scan de ports, sniffing réseau Disponible en version rootless Kali NetHunter transforme votre téléphone en un véritable laboratoire de sécurité mobile, sans avoir besoin de rooter votre appareil. 📥 Télécharger Kali NetHunter 3. Orbot – L’anonymat avant tout Lorsque vous effectuez des analyses ou naviguez dans des environnements sensibles, protéger votre identité est crucial. C’est ici qu’intervient Orbot, un proxy mobile qui fait transiter vos données par le réseau Tor. Pourquoi l’utiliser : Masquer votre adresse IP Chiffrer le trafic sortant de vos applications Appliquer Tor à des applis spécifiques via VPN local Combiné à Termux ou NetHunter, Orbot garantit un niveau d’anonymat supplémentaire, indispensable lors de tests d’intrusion en réseau ou sur des applications distantes. 📥 Télécharger Orbot sur le site du Guardian Project 4. Fing – L’analyseur de réseau intelligent Maintenant que votre environnement est sécurisé, il est temps de scanner les réseaux à la recherche de failles potentielles. Fing est l’une des applications les plus complètes pour cette tâche. Fonctionnalités clés : Détection de tous les appareils connectés Analyse des ports ouverts et services actifs Identification des adresses IP, MAC, et constructeurs Fing est extrêmement simple à utiliser et vous permet d’auditer la sécurité d’un réseau Wi-Fi en quelques minutes, directement depuis votre téléphone. 📥 Télécharger Fing sur Google Play 5. FakeTraveler – Falsifiez votre localisation GPS sans root Dans certaines situations, il peut être utile de simuler une autre localisation GPS sur votre smartphone, que ce soit pour préserver votre vie privée, tester des applications sensibles à la géolocalisation ou valider des comportements en conditions simulées. FakeTraveler répond parfaitement à ce besoin en proposant une interface simple et intuitive : Une carte interactive où vous pouvez sélectionner la localisation désirée via un appui long Possibilité d’appliquer la localisation fake immédiatement Options avancées pour simuler la localisation sur une période donnée Pas besoin de root : l’application utilise la fonctionnalité "Mock Location" disponible dans les options développeur Android 📥 Télécharger FakeTraveler sur F-Droid 6. WiFiAnalyzer – Analyse des réseaux Wi-Fi WiFiAnalyzer vous aide à visualiser les réseaux Wi-Fi environnants, identifier les canaux encombrés et optimiser votre propre réseau.
Fonctionnalités principales : Détection des réseaux Wi-Fi à proximité Analyse des canaux pour éviter les interférences Graphiques en temps réel de la puissance du signal 📥 Télécharger WiFiAnalyzer sur Google Play 7. NetHunter Store – Accès à des outils spécialisés Le NetHunter Store est une boutique d'applications basée sur F-Droid, offrant une collection d'outils de sécurité et de hacking éthique, même sans installer Kali NetHunter. Fonctionnalités principales : Accès à des applications comme WiFi Analyzer, cSploit, et plus Téléchargements sécurisés sans télémétrie Interface adaptée aux professionnels de la sécuritéMyGreatLearning 📥 Accéder au NetHunter Store En combinant ces cinq applications, vous disposerez d’un environnement de test de pénétration complet et mobile. ⚠️ Rappel important : n’utilisez ces outils que dans un cadre légal et éthique — par exemple sur votre propre réseau, sur des environnements de test, ou dans le cadre d’un audit autorisé. Le hacking éthique n’est pas un jeu, c’est une discipline sérieuse et précieuse pour la sécurité numérique de tous.
0 notes
Text
Google Shuts Down China-Linked Calendar Hack: APT41 Malware Exposed
Introduction In a stunning revelation, Google has confirmed that state-sponsored hackers from China exploited Google Calendar to run a sophisticated cyber-espionage campaign. The operation, linked to the APT41 (also known as HOODOO) group, utilized Calendar events as a command-and-control (C2) channel to extract sensitive data from infected devices. Discovery and Attribution According to…
#apt41#cloud app hack#cyber espionage china#cyberattack 2025#dll injection#google calendar hack#google safe browsing#google threat intel#gtig#malware c2#malware via calendar#plustdrop#process hollowing#spear phishing#toughprogress malware
0 notes
Text
Claude Sonnet 4, Opus 4 On Google Cloud & Amazon Bedrock

Claude 4 models
The latest AI models from Amazon-backed AI safety and research business Anthropic, founded by former OpenAI researchers, are Claude Opus 4 and Claude Sonnet 4. These models launched on May 22 and 23, 2025, setting “new standards for coding, advanced reasoning, and AI agents“. Anthropic stopped investing in chatbots last year to focus on improving Claude's ability to handle complex tasks like research and coding, so the launch is a bold move away from chatbots to become a well-known AI coding platform.
Opus 4Claude
They call Claude Opus 4 the “best coding model in the world” and Anthropic's most powerful. In customer testing, it ran virtually a full workday (seven hours) independently and performed well on complex, time-consuming activities and agent processes. For complex use scenarios requiring “frontier intelligence,” use Opus 4:
Intelligent AI.
Full-stack app development and codebase refactoring.
Research synthesis, agentic search, and deep research.
Long-term independent work that prioritises expertise and precision.
Content development focusses on natural writing and humanity.
Fourth Claude Sonnet
Anthropic's mid-size Claude Sonnet 4 balances pricing and performance. Though it replaced Claude Sonnet 3.7, it is much better. It has “superior coding and reasoning,” more accurate responses, and 65% less “reward hacking.” Claude Sonnet 4 suits high-volume, broad activities like:
Fixing bugs and reviewing code.
AI assistants for real-time client communications.
Condensing market signals or dashboards requires good research.
Massive material generation and analysis.
Being a task-specific subagent in multi-agent systems.
Claude Sonnet 4 and Opus 4 are hybrid reasoning models that can answer questions quickly and allow for deeper reasoning through “extended thinking” mode. With more time to think about solutions, this prolonged thinking mode helps models perform better on difficult tasks. The models can summarise their logic in a “user-friendly” way. A new Developer Mode lets you see full thought sequences before processing.
Both models can now leverage parallel tools like online search to contact several APIs or plugins at once to speed up procedures and reduce errors. They can extract and store relevant information in local files to construct “memory files” or “tacit knowledge” over time, boosting continuity and reliability on long-term activities. The models also follow directions better.
Opus 4 and Claude Sonnet 4 scored industry-leading on the SWE-bench coding benchmark, highlighting the focus on coding. Opus 4 also performs well on Terminal Bench real-world coding tests. Performance fluctuates, therefore internal benchmarks should be taken “with a grain of salt.” In high school maths, benchmarks show regressions compared to earlier models. Even while AI models struggle to write high-quality software and sometimes make mistakes, their potential to boost productivity is driving their rapid adoption.
To help developers, Anthropic has made its Claude Code agentic command-line tool public. With Claude Code's interaction with GitHub, VS Code, and JetBrains, file edits are visible quickly. The extensible Claude Code SDK lets you create unique agents and apps. A code execution tool, MCP connection, Files API, and prompt caching are new API features.
Opus 4 and Claude Sonnet 4 are accessible via Google Cloud Vertex AI, Amazon Bedrock, and the Anthropic API. Databricks customers can use them natively. Opus 4 is part of Anthropic's premium Claude plans (Pro, Max, Team, and Enterprise), while Claude Sonnet 4 is free and paid. Claude Sonnet 4 starts at $3 per million input tokens and $15 per million output tokens, while Opus 4 starts at $15 and $75. Timely caching and batch processing save money.
Anthropic tested and assessed the models with additional experts to ensure safety, security, and dependability. They come with improved cybersecurity and harmful content identification. Opus 4 may “substantially increase” the capacity of a STEM-trained person to acquire, produce, or deploy chemical, biological, or nuclear weapons, according to internal testing. The models are evaluated against Anthropic's “ASL-3” model
Early clients like Palo Alto Networks, Replit, Cursor, Rakuten, Augment Code, and others have observed improvements in agent performance, difficult job management, coding pace, and code quality. Claude on Vertex AI accelerated Palo Alto Networks code development by 20%–30%. Opus 4 was the first to increase code quality while debugging and editing without slowing down, Block said.
Anthropic reported $2 billion in annualised sales in the first quarter of 2025, more than double the previous quarter. The company targets $12 billion in 2027. Wall Street is still investing, and Anthropic has received billions from Amazon and has a $2.5 billion credit line to cover rising development costs.
Anthropic plans to upgrade models more often to stay competitive and improve faster.
#ClaudeSonnet4#ClaudeOpus4#Claude4models#anthropicmodels#Opus4#Sonnet4#technology#TechNews#technologynews#news#govindhtech
0 notes
Text
The Most In-Demand Cybersecurity Skills Students Should Learn

The digital world is expanding at an unprecedented pace, and with it, the landscape of cyber threats is becoming increasingly complex and challenging. For students considering a career path with immense growth potential and global relevance, cybersecurity stands out. However, simply entering the field isn't enough; to truly succeed and stand out in 2025's competitive job market, mastering the right skills is crucial.
The demand for skilled cybersecurity professionals far outweighs the supply, creating a significant talent gap and offering bright prospects for those with the in-demand expertise. But what skills should students focus on learning right now to land those coveted entry-level positions and build a strong career foundation?
While foundational IT knowledge is always valuable, here are some of the most essential and sought-after cybersecurity skills students should prioritize in 2025:
Core Technical Foundations: The Bedrock
Before specializing, a solid understanding of fundamental technical concepts is non-negotiable.
Networking: Learn how networks function, including protocols (TCP/IP, HTTP, DNS), network architecture, and common networking devices (routers, switches, firewalls). Understanding how data flows is key to understanding how it can be attacked and defended.
Operating Systems: Gain proficiency in various operating systems, especially Linux, Windows, and a basic understanding of mobile OS security (Android, iOS), as threats target all environments. Familiarity with command-line interfaces is essential.
Programming and Scripting: While not every role requires deep programming, proficiency in languages like Python or PowerShell is highly valuable. These skills are crucial for automating tasks, analyzing malware, developing security tools, and performing scripting for security assessments.
Cloud Security: Securing the Digital Frontier
As businesses rapidly migrate to the cloud, securing cloud environments has become a top priority, making cloud security skills immensely in-demand.
Understanding Cloud Platforms: Learn the security models and services offered by major cloud providers like AWS, Azure, and Google Cloud Platform.
Cloud Security Concepts: Focus on concepts like Identity and Access Management (IAM) in the cloud, cloud security posture management (CSPM), data encryption in cloud storage, and securing cloud networks.
Threat Detection, Response, and Analysis: On the Front Lines
Organizations need professionals who can identify malicious activity, respond effectively, and understand the threat landscape.
Security Operations Center (SOC) Skills: Learn how to monitor security alerts, use Security Information and Event Management (SIEM) tools, and analyze logs to detect potential incidents.
Incident Response: Understand the phases of incident response – preparation, identification, containment, eradication, recovery, and lessons learned. Practical knowledge of how to act during a breach is critical.
Digital Forensics: Develop skills in collecting and analyzing digital evidence to understand how an attack occurred, crucial for incident investigation.
Threat Intelligence: Learn how to gather, analyze, and interpret threat intelligence to stay informed about the latest attack methods, threat actors, and vulnerabilities.
Offensive Security Fundamentals: Thinking Like an Attacker
Understanding how attackers operate is vital for building effective defenses.
Vulnerability Assessment: Learn how to identify weaknesses in systems, applications, and networks using various tools and techniques.
Introduction to Penetration Testing (Ethical Hacking): While entry-level roles may not be full-fledged penetration testers, understanding the methodology and mindset of ethical hacking is invaluable for identifying security gaps proactively.
Identity and Access Management (IAM): Controlling the Gates
Controlling who has access to what resources is fundamental to security.
IAM Principles: Understand concepts like authentication, authorization, single sign-on (SSO), and access controls.
Multi-Factor Authentication (MFA): Learn how MFA works and its importance in preventing unauthorized access.
Data Security and Privacy: Protecting Sensitive Information
With increasing data breaches and evolving regulations, skills in data protection are highly sought after.
Data Encryption: Understand encryption techniques and how to apply them to protect data at rest and in transit.
Data Protection Regulations: Familiarize yourself with key data protection laws and frameworks, such as global regulations like GDPR, as compliance is a major concern for businesses.
Automation and AI in Security: The Future is Now
Understanding how technology is used to enhance security operations is becoming increasingly important.
Security Automation: Learn how automation can be used to streamline repetitive security tasks, improve response times, and enhance efficiency.
Understanding AI's Impact: Be aware of how Artificial Intelligence (AI) and Machine Learning (ML) are being used in cybersecurity, both by defenders for threat detection and by attackers for more sophisticated attacks.
Soft Skills: The Underrated Essentials
Technical skills are only part of the equation. Strong soft skills are vital for success in any cybersecurity role.
Communication: Clearly articulate technical concepts and risks to both technical and non-technical audiences. Effective written and verbal communication is paramount.
Problem-Solving and Critical Thinking: Analyze complex situations, identify root causes, and develop creative solutions to security challenges.
Adaptability and Continuous Learning: The cybersecurity landscape changes constantly. A willingness and ability to learn new technologies, threats, and techniques are crucial for staying relevant.
How Students Can Acquire These Skills
Students have numerous avenues to develop these in-demand skills:
Formal Education: University degrees in cybersecurity or related fields provide a strong theoretical foundation.
Online Courses and Specializations: Platforms offer specialized courses and certifications focused on specific cybersecurity domains and tools.
Industry Certifications: Entry-level certifications like CompTIA Security+ or vendor-specific cloud security certifications can validate your knowledge and demonstrate commitment to potential employers.
Hands-on Labs and Personal Projects: Practical experience is invaluable. Utilize virtual labs, build a home lab, participate in Capture The Flag (CTF) challenges, and work on personal security projects.
Internships: Gaining real-world experience through internships is an excellent way to apply your skills and build your professional network.
Conclusion
The cybersecurity field offers immense opportunities for students in 2025. By strategically focusing on acquiring these in-demand technical and soft skills, staying current with threat trends, and gaining practical experience, students can position themselves for a successful and rewarding career safeguarding the digital world. The demand is high, the impact is significant, and the time to start learning is now.
0 notes