#How to Change Google Account Password
Explore tagged Tumblr posts
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
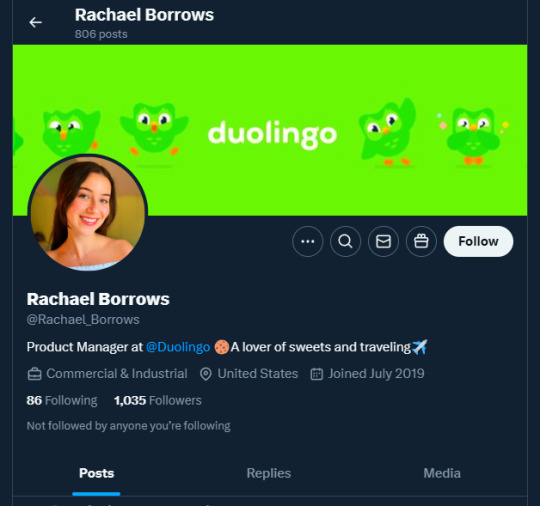
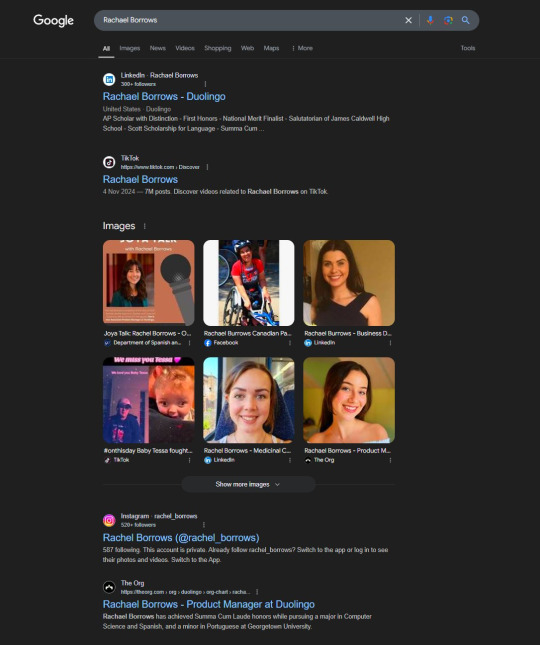
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
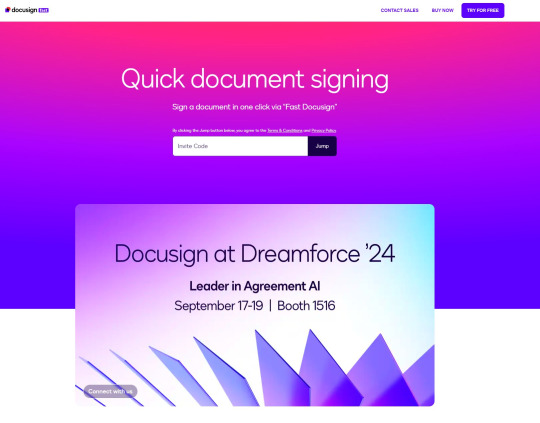
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
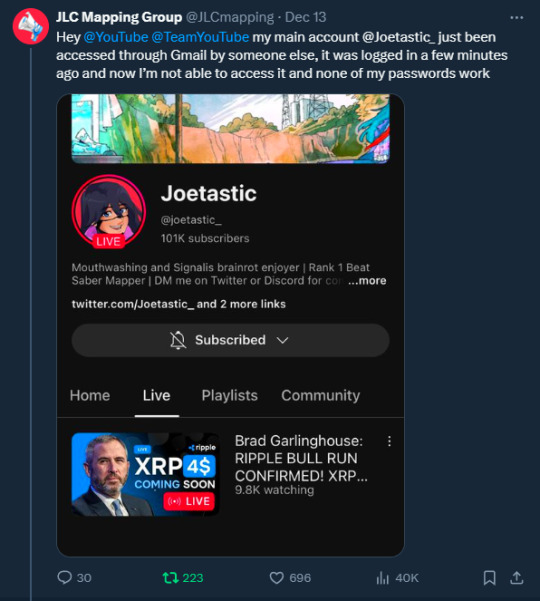
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
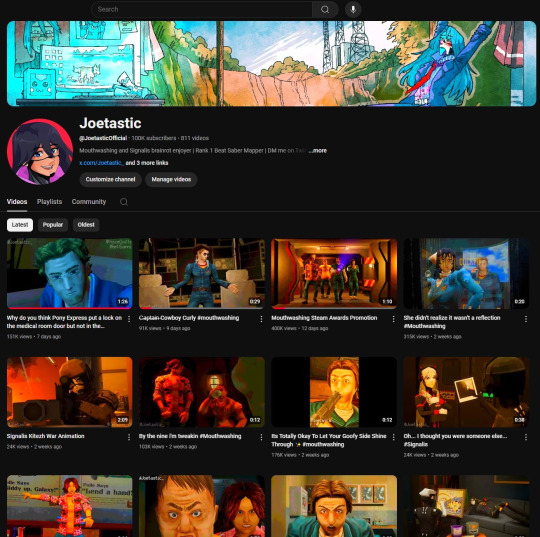
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
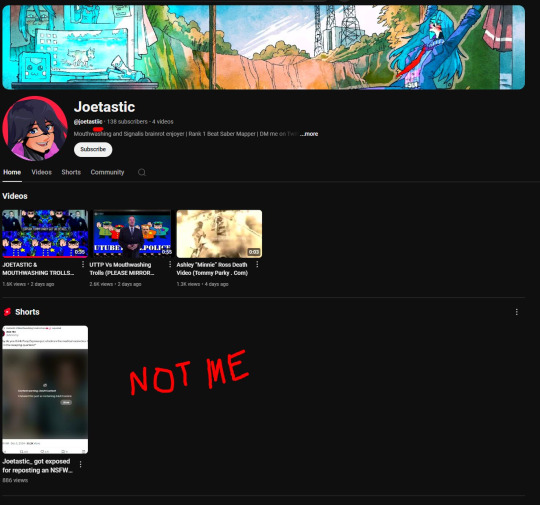
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
Well, I have reached out to Google, and apparently, my email account was deleted from my own computer aka, the IP address is the same? How is that even possible lmao? Y'all at this point I just accept this as the universe's will like what the fuck honestly. LMAO
well, it seems that everything is gone now. I can't believe that my blog has been deleted twice on this platform. Also, my email is gone including all accounts that were linked to said email. honestly, I am really tired of this. And idk if I will ever find it in me to rebuild all this again.
lots of love, River.
#update#this is surreal#truthfully i have no idea#They suggested to change my internet password and reset my computer#so imma do that#also apparently my log in information was part of a breach so the combo of my email and PW was basically out there#this is so wild#Also my google account is gone#you have like just a few minutes or so to get your account back when you delete it apparently#and yeah LMAO idk how that is even possible
38 notes
·
View notes
Text
Defense (of the internet) (from billionaires) in depth

Picks and Shovels is a new, standalone technothriller starring Marty Hench, my two-fisted, hard-fighting, tech-scam-busting forensic accountant. You can pre-order it on my latest Kickstarter, which features a brilliant audiobook read by Wil Wheaton.

The only way to truly billionaire-proof the internet is to a) abolish billionaires and b) abolish the system that allows people to become billionaires. Short of that, any levees we build will need constant tending, reinforcement, and re-evaluation.
That's normal. No security measure (including billionaire-proofing the internet) is a "set and forget" affair. Any time you want something and someone else wants the opposite, you are stuck in an endless game of attack and defense. The measures that block your adversary today will only work until your adversary changes tactics to circumvent your defenses.
For example, mining all the links on the internet to find non-spam sites worked brilliantly for Google, because until Pagerank, there were zero reasons for spammers to get links to point to their sites. Once Google became the dominant way of finding things on the internet, spammers invented the linkfarm. This principle can be summed up as "Show me a ten-foot wall and I'll show you an eleven-foot ladder."
Security designers address this with something called "defense in depth": that's a series of overlapping defenses that are meant to correct for one another's weaknesses. Your bank might use a password, a 2FA code, and – for extremely high-stakes transactions – a series of biographical questions posed by a human customer service over a telephone line.
I've written extensively about defending a new, good internet from billionaire enshittifiers. For example, in this post, I described how Bluesky could be made enshittification-resistant with the use of "Ulysses Pacts" – self-imposed, binding restrictions on enshittification:
https://pluralistic.net/2024/11/02/ulysses-pact/#tie-yourself-to-a-federated-mast
A classic example of a Ulysses Pact is "throwing away the Oreos when you go on a diet." Now, it doesn't take a lot of work to devise a countermeasure your future, Oreo-craving self can take to defeat this measure: just drive to the grocery store and buy more Oreos. This even works at 2AM, provided you live within driving distance of an all-night grocer.
That doesn't mean you shouldn't throw away those Oreos. Depending on how strong your Oreo craving is, even a little friction can help you resist the temptation to ruin your diet. We often do bad things because of momentary impulses that fade quickly, and simply airgapping the connection between thought and deed works surprisingly well in many instances.
This is why places with fewer guns have fewer suicides of all kinds: there are plenty of ways to kill yourself, but none are quite so quick and reliable as a gun. People in the grips of a suicidal impulse who don't have guns have more chances to let the impulse pass (this is also why gun control leads to fewer all-cause homicides). So just because a measure is imperfect, that doesn't make it worthless.
If you're trying to give up drinking, you throw away all your booze, but you also go to meetings, and you get a sponsor who can help you out with a 2AM phone call. You might even put a breathalyzer on your car's ignition system. None of these are impossible to defeat (you can get an Uber to the liquor store, after all), but they all create friction between the thing you want, and the thing your adversary (your addiction) is trying to get. They strengthen the hand of you as defender of the sober status quo, against the attacker who wants you to relapse.
Critically, all these defensive measures also buy you space and time that you can use to organize and deploy more defenses. Maybe the long Uber ride to the liquor store gives you enough time to think about your actions so you call your sponsor from the parking lot. Defense is useful even when it only slows your adversary, rather than stopping your adversary in their tracks.
Scaling up from personal defense to societal-scale security considerations, it's useful to think of this as a battle with four fronts: code (what is technically im/possible?), law (what is il/legal?), norms (what is socially un/acceptable?) and markets (what is un/profitable?). This framework was first raised a quarter-century ago, in Larry Lessig's Code and Other Laws of Cyberspace:
https://commons.wikimedia.org/wiki/File:Code_And_Other_Laws_of_Cyberspace_Version_2_0.pdf
Lessig laid out these four forces as four angles of attack that challengers to the status quo should plan their strategy around. If you want to liberalize copyright, you can try norms (the "Free Mickey" campaign), laws (the Eldred v. Ashcroft Supreme Court case), code (machine-readable Creative Commons licenses) and markets (open access/free software businesses). Each one of these helps the other – for example, if lots of people believe in copyright reform (norms), more of them will back a Humble Bundle for open access materials (markets), and more lawmakers will be interested in changing copyright statutes (law), and more hackers will see reason to do cool things with CC licenses, like search engines (code).
But the four forces aren't just for attackers seeking to disrupt the status quo – they're just as important for defenders looking to create and sustain a new status quo. Figuring out how to "lock a system open" is very different from figuring out how to "force a system open." But they're both campaigns waged with code, law, norms and markets.
We're living through a key moment in enshittification history. Millions of people have become dissatisfied with legacy social media companies run by despicable, fascism-friendly billionaires like Elon Musk and Mark Zuckerberg and are ready to leave, despite the costs (losing contact with friends who stay behind). While many of them are moving to group chats and private Discord servers,tens of millions have moved to new social media platforms that advertise (though they don't necessarily deliver) decentralization: Mastodon (and the fediverse) and Bluesky (and the atmosphere).
Decentralization is itself a defensive countermeasure (code). When a service has diffuse power, it's harder for any one person to take it over. Federation adds another defensive layer, because users who don't like the way one server is run can move to another server, with varying degrees of data- and identity-portability. That makes it harder for server owners to squeeze users to make money (markets), and gives them an out if server owners try it anyway.
Federation with decentralization is my favorite anti-enshittification defense. It's powerful as hell. It's the main reason I endorse Free Our Feeds, an effort to (among other things) build more Bluesky servers to decrease the centralization and give users dissatisfied with Bluesky management an alternative:
https://pluralistic.net/2025/01/20/capitalist-unrealism/#praxis
That said, decentralization and federation are not perfect, set-and-forget defenses. Take email – the oldest, most successful federated system of them all. Email is nominally decentralized, but most email traffic goes through a handful of extremely large servers run by a cartel of companies (Google, Apple, Microsoft, and a few ISPs). These companies collude (or, more charitably, coordinate) to block email from non-cartel companies, in the name of fighting spam. This makes running your own mail server so hard that it is nearly impossible (that is, if you care about people actually receiving the email you send them):
https://pluralistic.net/2021/10/10/dead-letters/
What's interesting about enshittified email is that it didn't start with corporate takeover: it started with volunteer-maintained blocklists of untrustworthy servers that most email operators subscribed to, defederating from any server that appeared on the list. These blocklists of bad servers were opaque (often, their maintainers would operate anonymously, citing the threat of retaliation from criminal scammers whose servers appeared on the list). They had little or no appeal process, and few or no objective criteria for inclusion (you could be blocklisted for how your email server was configured, even if no one was using it to send spam). All of this set up the conditions to favor large email servers, and also had the effect of immunizing these large servers from appearing on blocklists. I mean, once three quarters of the internet is on Gmail, no one is going to block email from Gmail, even if a ton of spam is sent using its servers.
The lesson of email doesn't mean email is bad, nor does it mean decentralization and federation are useless. It doesn't even mean that blocklists of bad servers are evil. It just means that federation and decentralization are imperfect and insufficient defenses against enshittification, and that blocklists are useful, but very dangerous. It means that we should strive to keep our systems federated and decentralized, and watch our blocklists very carefully, and not rely on any of this as the only defense against enshittification.
Likewise, both Mastodon and Bluesky are built on free/open code and standards. That means that anyone can fork them, fix them or mod them. What's more, the licenses involved are irrevocable, making them very effective Ulysses Pacts. No one – not a CEO, not a VC investor, not a court or a blackmailer – can order someone to make their GPL code proprietary. The license is perpetual and irrevocable, and that's that.
Free/open licenses are excellent Ulysses Pacts and great code-related defenses against enshittification, but they, too, are imperfect and insufficient. Google, Facebook, Amazon, Apple and Microsoft have all figured out how to enshittify services that are built on free/open code:
https://mako.cc/copyrighteous/libreplanet-2018-keynote
And then there are all the companies that use free/open code and defeat the freedom and openness by simply violating the license, on the grounds that a decentralized, federated development community can't figure out who has standing to sue, and also can't afford to pay for the lawyers to do so:
https://sfconservancy.org/news/2022/may/16/vizio-remand-win/
That's not to say that code-based antienshittification measures are pointless – only to say that they need other measures to backstop them, as defense in depth. Let's talk about law, then. Both Mastodon and Bluesky are governed by legal entities that are, nominally, organized by charters that oblige them to eschew enshittification and be responsive to their users (Bluesky is a B-corp, Mastodon's code is overseen by a US nonprofit).
These structures are very important. I've been a volunteer board member for several co-ops and nonprofits (I was even once a volunteer for a nonprofit co-op!) and I'm familiar with the role that good governance can play in defending a project from internal and external pressures to betray its mission. That means I'm also familiar with the limits of these governance measures.
Take nonprofits: nominally, nonprofits are legally bound to serve their charitable purpose, and technically, stakeholders have legal recourse if they stray from this. But you don't have to look far to find nonprofits that have violated their charter and gotten away with it. Take the Nature Conservancy, which has become a key player in the market for fake "carbon offsets" that are used to justify everything from fossil fuel extraction to SUV manufacture:
https://pluralistic.net/2020/12/12/fairy-use-tale/#greenwashing
Or think of ISOC, who get tens of millions of dollars in free money every year from their stewardship of the .ORG registry, but who decided to hand over control of the nonprofits' TLD of choice to a shadowy cabal of hedge-fund billionaires:
https://www.eff.org/deeplinks/2020/12/how-we-saved-org-2020-review
Co-ops, too, are powerful but wildly imperfect. REI is a member co-op that does lots of great things…and also busts unions:
https://prismreports.org/2024/07/17/rei-workers-unionizing-fighting-for-agreemment/
But REI is a paragon of social virtue compared to its Canadian equivalent, Mountain Equipment Coop, whose board was taken over by corrupt assholes who then sold the whole thing to a US private equity fund and change the name to "MEC":
https://pluralistic.net/2020/09/16/spike-lee-joint/#casse-le-mec
B-corps are far from perfect, too: while they are nominally required to serve a positive social purpose, in practice, they can violate that purpose with impunity, whether that through greenwashing:
https://www.bbc.com/worklife/article/20240202-has-b-corp-certification-turned-into-corporate-greenwashing
Or Kickstarter insiders taking a $100m bribe to help Andreesen-Horowitz do a crypto pump-and-dump:
https://fortune.com/crypto/2024/03/11/kickstarter-blockchain-a16z-crypto-secret-investment-chris-dixon/
None of this is to claim that B-corps, co-ops, and nonprofits are useless. Maybe we should just give up on organization altogether and have some kind of adhocracy? If you're thinking this will help, then you need to read Jo Freeman's "The Tyranny of Structurelessness" and learn how a "leaderless" group is actually led by its least scrupulous, most Machiavellian schemers:
https://www.jofreeman.com/joreen/tyranny.htm
At this point, you might be mentally designing a new corporate structure, one that's designed to correct for both the tyranny of structurelessness and the brittleness of co-ops, nonprofits and B-corps. Please don't do this. Rolling your own corporate structure is like rolling your own cryptography or your own free software license. It always ends in tears:
https://www.reuters.com/technology/artificial-intelligence/openai-remove-non-profit-control-give-sam-altman-equity-sources-say-2024-09-25/
I like co-ops, nonprofits and B-corps. They're powerful – but insufficient – weapons against enshittification. They need to be backstopped by other measures, like norms. Normative measures are very powerful! Of course, mass revolts of angry users don't always keep companies from enshittifying:
https://www.theguardian.com/technology/2023/dec/30/reddit-moderator-protest-communities-social-media
But sometimes they do. The C-suite of Unity was shown the door after enshittifying their flagship product:
https://www.theverge.com/2023/10/10/23911338/unity-ceo-steps-down-developers-react
As was the enshittifying CEO of Sonos:
https://www.theverge.com/2025/1/13/24342179/sonos-ceo-patrick-spence-resignation-reason-app
And of course, these defensive measures reinforce one another. The public outcry against the .ORG selloff (norms) led to California's Attorney General stepping in (law), and after that, we more-or-less romped to victory:
https://www.theregister.com/2020/04/17/icann_california_org_sale_delay/
Markets are the final antienshittificatory force. If a social network is designed to be surveillance-resistant, it will be (very) hard to implement behavioral surveillance advertising. If a network is designed to support a many clients, it will be easy to implement an ad-blocker. Both factors make advertising-based businesses very unattractive to individual server operators, spammers, and VCs who back companies that operate elements of a federated server.
Same goes for systems that allow users to control the recommendations and other algorithmic aspects of their feeds (including switching these off altogether). The fact that Tiktok's users overwhelmingly use an algorithmic feed that they have no way to control or even understand is an anti-Ulysses Pact, an irresistible temptation for Tiktok to enshittify itself:
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys
By contrast, it's much harder to pull those shenanigans with services that technologically devolve control over recommendations (code), making it less profitable to even try to attempt this (markets). And of course, if users refuse to tolerate this kind of thing (norms) and can hop to other servers (code), then any system that pulls that nonsense will lose lots of users and go broke (markets).
This defense-in-depth approach to decentralized social media pushes us to analyze both Mastodon and Bluesky through a tactical lens – to identify the weak parts in the defenses of each and shore them up.
Take Free Our Feeds and its attempt to stand up more Bluesky servers. This addresses one of the serious technical deficiencies in Bluesky (the lack of federation), and if lots of Bluesky users try it out, it will normalize the idea that Bluesky is a constellation of independently managed servers (norms). It also creates Bluesky alternatives with radically different commercial imperatives (markets), because the main Bluesky server is backed by venture capitalists, who are notorious for their enshittifying impulses.
But security isn't static – a tactic that works today won't work tomorrow if your adversary can figure out a way around it. Bluesky is a B-corp with an excellent board with some names I have profound trust for, but B-corps can abandon their public benefit purpose, and boards can be fired (and also even people you trust can talk themselves into doing stupid and wicked things, see .ORG).
If millions of Bluesky users flock to a rival service, one run by a nonprofit (markets), Bluesky's investors might be tempted to sever the link between Bluesky and that new server (code). That's what Facebook and Apple did to XMPP, an interoperable, federated messaging system that used to connect Apple users, Facebook users, and users of many other servers. They did this for commercial reasons (markets), to trap and lock in their users (code), and they got away with it because not enough users were outraged by this (norms) that they could get away with it.
When Bluesky's VCs fire the CEO, kick people like Mike Masnick off its board, and then defederate from Free Our Feeds' server, how do we make that more like Sonos or Unity (where the corporation capitulated to its users), and not like Reddit (where the user revolt was crushed)?
With social media, it's a numbers game. Social media grows by network effects: the more users there are in a system, the more valuable it is. It's not merely imperative to create alternative Bluesky servers, it's imperative to make them populous enough that cutting them off from the first Bluesky server will inflict more pain on the company than it inflicts on those other users. That's not a guarantee that Bluesky's future, enshittification-bent management won't go ahead and do it anyway, but it does increase the chances that if they press on, their users will take the hit to defect to free/open servers.
Bluesky has other problems besides its centralization, of course. The reason Bluesky is so centralized is that it's really expensive to run an alternative Bluesky server that provides a home for users who have left the main server (a "relay" in Bluesky-ese). Partly this is down to tooling: because no one has done it, Free Our Feeds will have to invent a lot of stuff to get that server up and running, but people who come later will benefit from whatever Free Our Feeds develops along the way.
But mostly, this isn't a tooling problem – it's an architecture problem. The way that Bluesky is structured demands a lot more of relays than Mastodon demands of "instances" (a loose Fediverse analog to relays):
https://www.techdirt.com/2025/01/21/the-technological-poison-pill-how-atprotocol-encourages-competition-resists-evil-billionaires-lock-in-enshittification/#comment-4253477
This is a code problem, and it's a hard one, but it's not insurmountable. The history of networked tools is the history of developers figuring out how to break apart large, monolithic, expensive services in cheaper, smaller, easier to develop. In other words, our defense in depth of Bluesky militates for more than one project – not just a "Free Our Feeds" but also a software development project to make it easier for anyone to free those feeds.
Which raises some important questions, the biggest being "Why bother?" After all, there's already a perfectly good Fediverse that could sure use the money and effort that Free Our Feeds is proposing to put into Bluesky. My main answer here is that the point of disenshittification is an enshittification-free internet, not a better Mastodon:
https://pluralistic.net/2025/01/20/capitalist-unrealism/#praxis
We want to set Bluesky users free because the problem with Bluesky isn't its users, it's the fact that there's no fire-exits those users can avail themselves of if Bluesky's VCs set it on fire:
https://pluralistic.net/2024/12/14/fire-exits/#graceful-failure-modes
But there's another good reason to do this, one that involves people who have no interest in using Bluesky: even if you don't want to use a better Bluesky, you likely have very good reasons to reach Bluesky users. Maybe you want them to help you organize against enshittification! Or maybe you just want to operate a real-world venue where people can gather and have a great time and support performers, and right now you're stuck advertising on Facebook and Instagram, and you don't want to end up being forced to use an enshittified, fire-exit-free Bluesky in the future:
https://www.dnalounge.com/backstage/log/2025/01/13.html
Of course, there's plenty of reasons to want to make Mastodon better. Many of Mastodon's features are absurdly primitive – the lack of threading support and quote-boosting sucks, and the supposedly opt-in system-wide search doesn't work, even if you opt in. Masto could sure use some of the money that Free Our Feeds is asking for to spruce up Bluesky.
This is true, but also irrelevant. Mastodon is stuck at around a million active users, while Bluesky has twenty times that amount. Crowdfunding a couple dollars per user to pursue software development is a reasonable goal, but raising twenty times that much is a lot harder:
https://mastodon-analytics.com/
The money being raised for Free Our Feeds isn't money that had been earmarked for Mastodon development, nor will abandoning Free Our Feeds redirect those funds to Mastodon development.
Which isn't to say that we shouldn't chip in to fund Mastodon development. I donated to the Kickstarter for Pixelfed, a Fediverse Insta replacement that has Meta so scared that they'll suspend your account if you even mention it:
https://www.kickstarter.com/projects/pixelfed/pixelfed-foundation-2024-real-ethical-social-networks
Adding Insta-like features to Mastodon is great. Fixing search, quoting, and threading would be great, too. We probably need some kind of governance efforts to keep volunteer-run, good faith defederation blocklists from exhibiting the same dynamics that email went through during the spam wars. There's some Bluesky features I'd love to see on Mastodon, like composable moderation and user-controlled, user-tunable recommendations. We also probably need some kind of adversarial press that closely monitors the governance structure for the Mastodon codebase and reports on process in standardization (I cannot overstate how much fuckery can take place within standards bodies, under cover of a nigh-impermeable shield of boringness).
Breaking Bluesky open is a priority. Keeping Mastodon open is a priority. But neither of these are goals unto themselves. The point is to set people free, not set technology free. Willie Sutton robbed banks because "that's where the money is." Right now, I'm interested in anti-enshittification measures for Bluesky because "that's where the people are."

Check out my Kickstarter to pre-order copies of my next novel, Picks and Shovels!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/01/23/defense-in-depth/#self-marginalization

Image: Mike Baird (modified) https://flickr.com/photos/mikebaird/2354116406
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#mec#mountain equipment coop#public benefit corporations#openai#xmpp#open web#dotorg#isoc#icann#code law norms markets#code#law#norms#markets#adversarial interoperability#ulysses pacts#meeting people where they are#rei#union busting#circular firing squads#atproto#bluesky#bsky#activitypub#mastodon
154 notes
·
View notes
Text
🎧A Guide to the TGCF Audio Drama🎭
With the release of the new season of the fabulous TGCF audio drama, I wanted to make an updated guide on how to make an account, purchase, and listen (with English subs) to it! Hopefully, this will help more people enjoy it and join in on the fun!
As a quick reminder, the audio drama is based on the revised version of the novel! It's a very faithful adaptation, but if you're a new fan, that might throw you for a loop! If you need an overview of the different versions of TGCF, check out this post first!
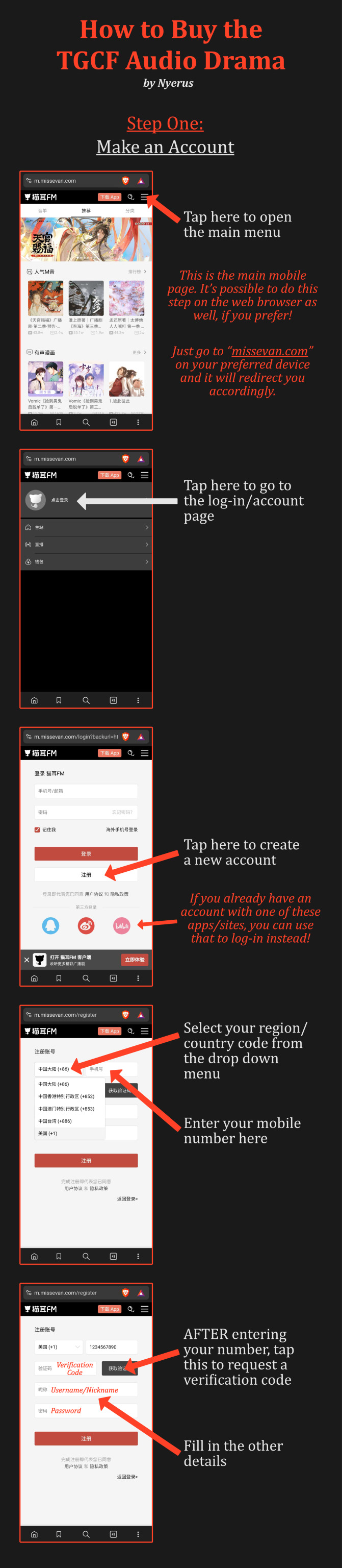
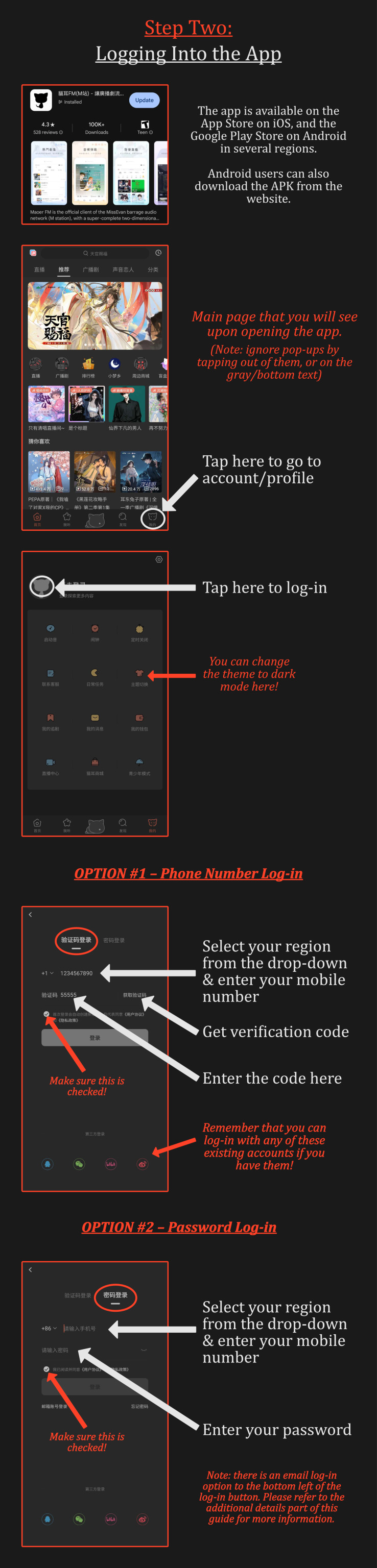
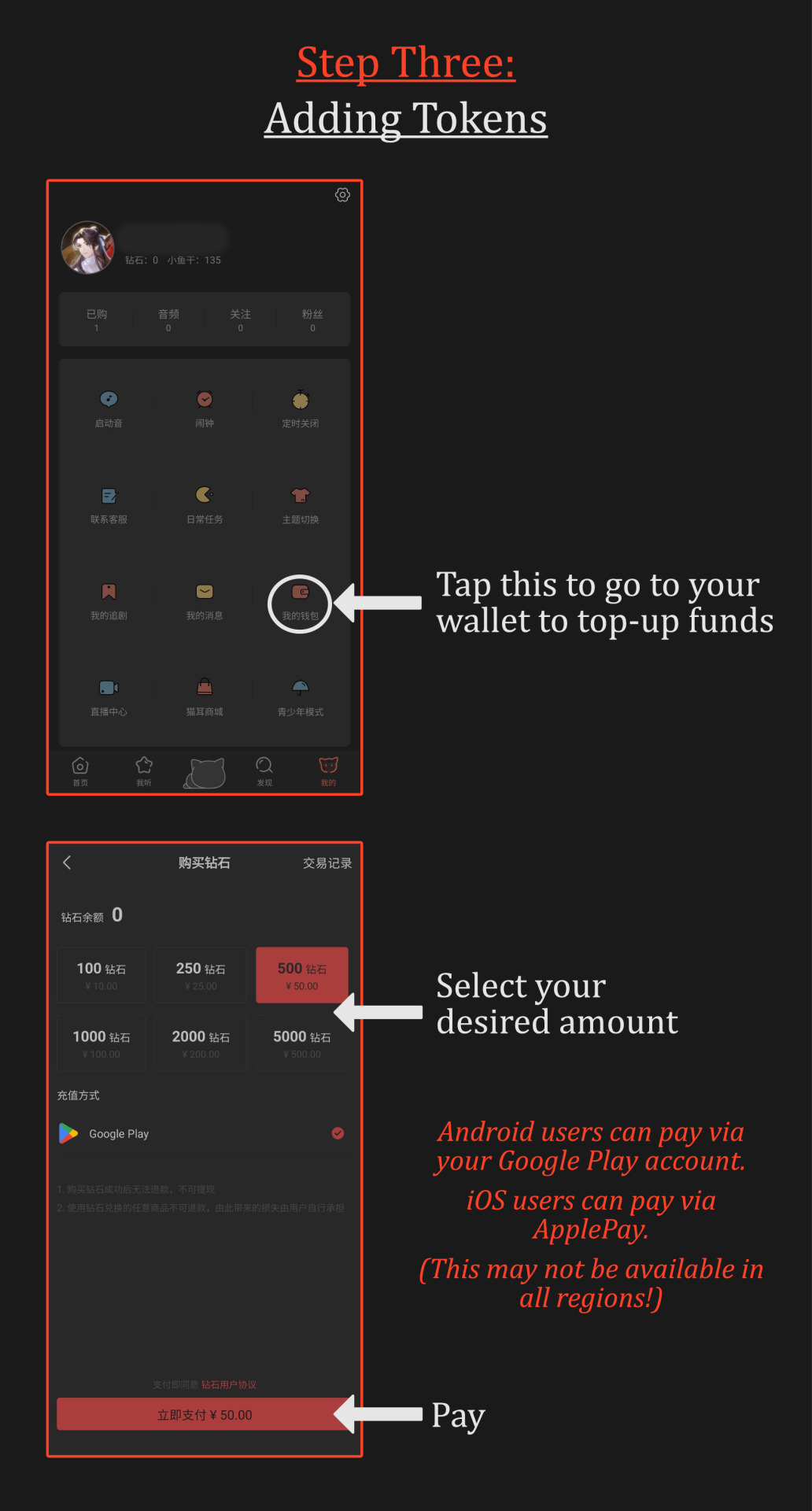
Part One: Making an Account & Purchasing
The process is a lot easier than you may expect! The site where the audio drama is hosted is "missevan.com," also known as "MaoerFM." They are one and the same!
Check out these infographics to create an account and buy the audio drama. (Due to tumblr compression, they may be difficult to read. If this is the case, please view these images in full-screen and preferably on a web browser for best quality!)
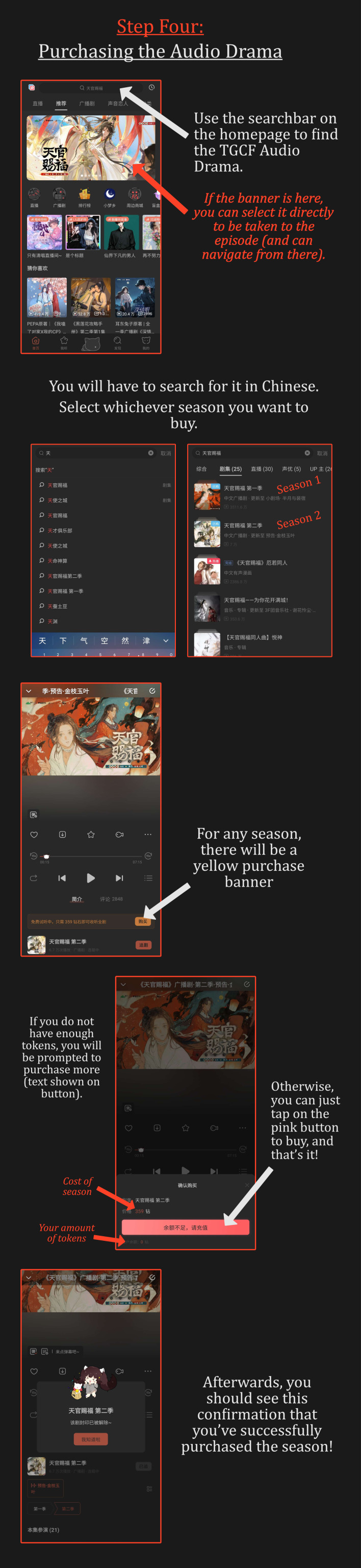
ADDITIONAL INFORMATION
General Info:
It costs 319 diamonds for the first season, and 359 diamonds for the second season of the TGCF audio drama. This was less than $5 USD, for each season. Future seasons will likely be similarly priced.
Episodes typically release weekly. Mini-episodes/bonus content releases intermittently, and often continues after the main season "ends."
This guide will work for any other audio dramas you want to purchase and support (such as MDZS)! They obviously have different costs, but the process of buying is pretty much the same.
Account/Registration Info:
If you do not see your country/region code listed when making an account, it is unfortunately unavailable there. I do not know any workarounds at the moment, apart from asking a friend/relative in a different country to help you out! If anyone does know other options, please let me know!
Step One of the guide is technically optional, as logging in on the app for the first time will automatically create a new account, if there’s not already one associated with your mobile phone number. I recommend doing that step anyway, as it will ensure that you have a password linked to your account. Several people in the past have reported that they sometimes cannot receive the verification code to log in. (Especially from South America and SEA for some reason.) Having a password bypasses this, if it happens to you.
Unfortunately, it seems that you MUST register with a mobile number to begin with.
Otherwise, you can use an existing Bilibili/QQ/WeChat/Weibo account if you have it. They all require a number for registration too, as far as I know, so you may run into the same problem. They may still be worth trying if you have no other options! Once again, if anyone is aware of other workarounds, do let me know.
Additionally, it’s possible to link your account to an email AFTER you register with a mobile number. (There’s no escaping that, from what I can tell.) You can then use that to log in.
It seems useful to have your email and a password associated with your account, especially in case your country code gets nixed from availability -- which has been known to happen without warning in the past.
The mobile browser seems to prefer you log in with a number/email and a password, rather than a verification code.
LINKING AN E-MAIL TO YOUR ACCOUNT (Optional)
This must be done via web browser, or with your mobile browser set to desktop mode. It’s VERY easy if you use a browser with an auto-translate feature like Google Chrome:
(These images are the MTL translated versions!)
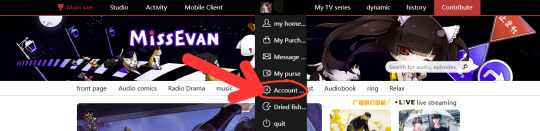
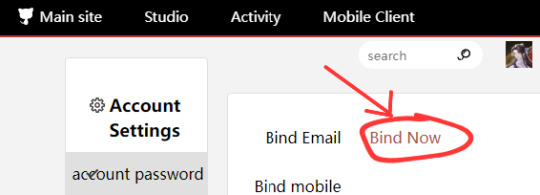
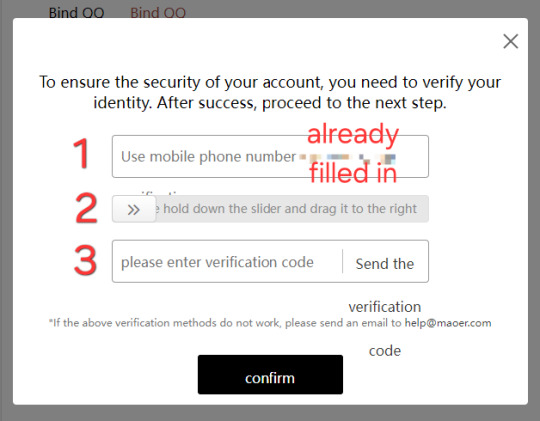
Unfortunately yes, you will need to receive a verification code via mobile number to enable this. The second verification code gets sent to your email, though! (Try not to lose your password, because I'm pretty sure you'll still have to use your phone to verify and change it.) Don't forget to check your spam folder if you don't see it. It will be from "猫耳FM."
Once again, this is optional! I just wanted to include it as an extra avenue for people who may struggle with the verification codes, as they can be finicky. And it happened to me while I was making this section, so I knew I had to....
Part Two: How to Enable English Subtitles
First things first: there are no official English subs for the TGCF Audio Drama. Though I'm fairly sure this applies to all dramas on MaoerFM.
However, there are Chinese (Simplified) subs for each episode.
OPTION ONE: MTL
The main method that non-Chinese speakers have been using to understand the Audio Drama is via MTL (machine translation) on those subs! Browsers like Google Chrome not only have auto-translate, but it works in real time as you watch/listen to the episode.
Make sure that it's turned on and that you've selected English -- or your preferred output language!
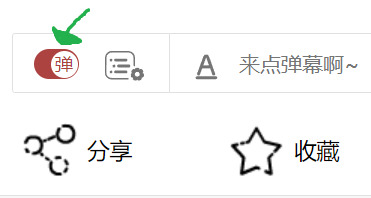
Be aware there are TWO types of subtitles on MaoerFM. There are the official subs, and the temporary subs.
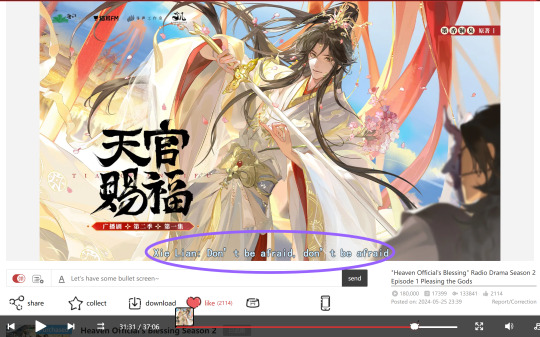
At the bottom of the audio player, there is a button labelled "字幕," which is circled in purple in the image below. If it is there, it means that episode has official subs available, and you can toggle them on/off. Meanwhile, the "弹" that the green arrow is pointing to is known as the "barrage." That's the scrolling text that you will see filling the screen. It's other fans screaming and crying in chat. You can turn it off if it feels overwhelming!

New episodes may take anywhere from a few hours to a day or two to be officially subtitled. (The bonus episodes don't have official subs for whatever reason.) In the meantime, there will be subtitlers working on adding temporary subs! I'd advise waiting a little while before listening to a new episode so they have more time to work, and you'll have better coverage!
While official subs are entirely separate, the temporary subs are part of the barrage. So you will have to keep the barrage turned on. (Notice how there is no "字幕" button next to it yet!) Unlike the rest of the barrage, the subs will be stationary, color-coded, and at the very bottom of the window -- so they're easy to differentiate.
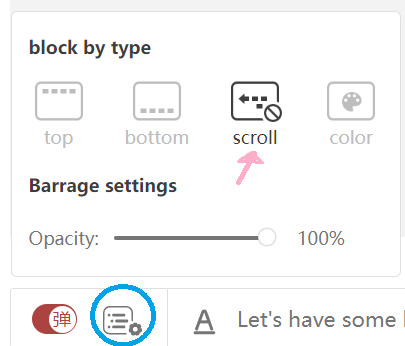
However, since the barrage can be a lot if you aren't used to it, there is a way around it.
Hit the settings menu (blue circle) and block the scrolling comments. You can also turn off the top ones, but just make sure not to turn off the bottom ones -- because those are the subs!
DO NOTE that this all works best on desktop! If everything's gone correctly, you should have something like these:
Right -- regular view, temporary subs Left -- full-screen, official subs
It's possible to get this to work on mobile if you enable desktop mode in your Chrome app. You will probably need to refresh a few times after that, or open the page in a new tab to have it work properly. Then it's the same steps as above!
You should have something like these:
Right -- landscape mode Left -- portrait mode
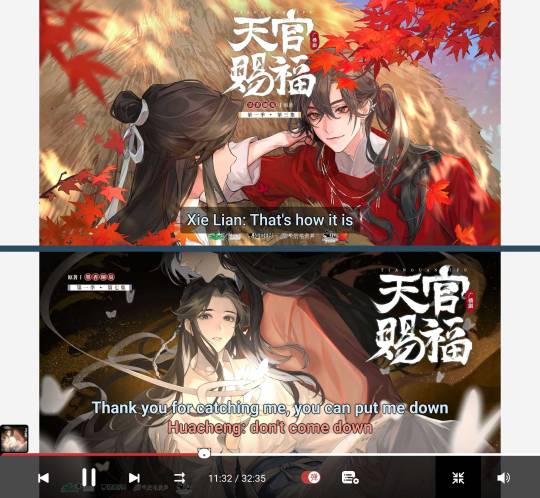
The scaling on mobile can be troublesome, and I have noticed that the auto-translate is slower than on desktop. It seems to take an extra second or two to work on each line -- whereas on desktop it's pretty instant -- and that can get annoying, especially in fast-paced scenes.
Additional Info:
This does not work for the mobile app! It is for the website ONLY!
If the translation stops working, refreshing usually fixes it.
There are potentially other options to using Chrome. Any browser that has an auto-translate will work, assuming it's as quick as Chrome's. If anyone has tried other browsers and seen success, please leave a reply!
OPTION TWO: FANSUBS
TreasureChestSubs here on tumblr have been doing high-quality fansubs for several audio dramas, including TGCF as of recently! However, at the time of making this guide, their TGCF translations currently only cover the first few episodes of season one. You will need to request an invite to their Discord server via the form in their posts. Please do check them out if you're interested.
I don't personally know of any other fansubbers who are actively working on the audio drama right now. But I do want to mention that Xyra_Rei on twitter has a Discord server where they share some translated snippets from various episodes. There are other great resources by fellow fans, too. Links and more info about the server can be found in the pinned post on their profile!
Part Three: Enjoy!!!
I hope this updated guide helps more people experience the wonder that is the TGCF audio drama (or really, any audio drama)! I cannot overstate how good it is in every aspect, and I think every TGCF fan deserves to be able to hear it for themselves! 💖
#tgcf#tian guan ci fu#hob#heaven official's blessing#tgcf audio drama#guide#nyerus.txt#yes fellas this is my only use-case for chrome and tbh... lmk of other options please lol#anyway the TGCF AD has my entire heart and soul PLEASE LISTEN TO IT
264 notes
·
View notes
Text
Long story short
...I survived. Or at least, that's how the lyrics go. Hi again, tombler -- I guess?
Long story:
It's really long, so scroll down for the short version!
Earlier in the month, Tumblr wrongly terminated my previous blog at misoplays. It could come out as a funny accident if only it's (a) the first time this kind of termination happened to misoplays, and (b) Tumblr gracefully reinstate the blog again. I've waited for almost a month and sent two e-mails (they did say spamming e-mail would just push my request back on the queue) while keep trying to refresh the page every day, yet the result is the same "There's nothing here" page. That's that me depresso.
To elaborate further on point (a), the first time I decided to start a sims cooking blog, I created it under my OG e-mail address; the e-mail I used to apply for job etc. which also happened to be linked to my OG tumblr account. It's an old account that now acts like a Wayback Machine of memories for me, but as you know, if a blog is already linked to your e-mail, it will be your main blog, and any additional blog you create under that e-mail would act as side blogs. So, the OG misoplays started as a side blog. However, three posts in, the blog got wrongly terminated. I was sure I didn't break any rules, but maybe Tumblr thought my sudden activity in that ancient account was suspicious, which I could understand. So I sent a request to Tumblr, and the blog was reinstated in under two weeks. The blog first looked like this:

Understandably no one liked or reblogged me, and it was totally okay -- because once again, I just started and posted my first three posts.
When the OG misoplays blog was under, I created a new Tumblr account under my other e-mail address, this time the blog becomes my main blog. The username was misomain, because misoplays was unavailable (apparently, you can't use a username from a suspended/terminated blog) at that time. Misomain was a puny name, because 'main' means "a principal of others in the same kind" in English, but it also translates to "to play" in Indonesian. I quite like misomain, but I went back to misoplays the moment Tumblr reinstated that blog.

The blog you might be familiar with looked more or less like this, of course without the silly Squidward booty profile picture 🤣
Everything went smoothly for a couple of months until early November. To be honest it kinda gets blurry what I was trying to do, I think I was trying to change the password or something. Tumblr sent a verification e-mail, and when I clicked on the link, that fateful "There is nothing here" page appeared. It was at that moment I knew something is wrong. My blog got wrongly terminated for the second time.
I sent a request to get my blog reinstated, and as patient as I can be, I get more anxious as the days went. Another fact is that my blog got yeeted away right when I was about to post my Halloween party posts -- which you'll see later, is quite time-consuming to take pictures of. I stopped playing The Sims 4 because I was sad, mad and somehow bitter at the situation. I mean, tell me why it keeps happening to me, @staff? The only possible explanation (and I don't want to keep making excuses for Tumblr because duh) is because sometimes I use VPN and some other times I turned it off. And if that's so, I already sent e-mails explaining the situation -- so far receiving no reply. None; nada!
I didn't think I would recreate another blog; I was done with it. That's when I absent-mindedly tried to google "misoplays" and the search brought me to this post.

I'm not gonna lie, I choked up and almost shed a tear 🥹
To think that someone out there -- someone who I look up to! -- knows that misoplays is gone and is wondering where it is... Bro, the tears are right there. Thank you, @charlypancakes, your post really bring my spirit up. I decided that I will create another blog, and I will start posting again. From now on I'll diligently back everything up, so if Tumblr yeeted this blog, I'm gonna create another one. I'm gonna live up to that one popular Indonesian proverb: Mati satu tumbuh seribu -- for every thing that was lost, a replacement will appear.
This current blog's name imomisoplays is another play on word: In English, 'emo' would refer to the sad, emotional side of me after experiencing this termination (as I would tell my friends, I'm "currently on my emo phase" once again). But in Korean, the word 이모 (read as ee-mo) means "aunt". I'm an aunt myself, and maybe, with my sims cooking content, I can be that cool auntie on the internet, conquering one recipe at a time 💃
Short story:
Phew, you just saved yourself a whole sob story!
My old blog at misoplays got wrongly terminated earlier this month. Tumblr hasn't returned it yet, and I have long lost hope. I saw a hopeful post and realized that I still got that spirit to keep on posting, so I created this blog. I lost my following, my followers (all 20 of you, please know I appreciate each one of you!), and the drafts to my old posts (only managed to save some), but I would love to continue simblr-ing again as imomisoplays 🙇♀️
42 notes
·
View notes
Text
TUTORIAL - Buying manga chapters from cmoa.jp
For those who are interested in supporting the manga, but don't know how to purchase from cmoa.jp, I have made a tutorial on how to do just that. 😊
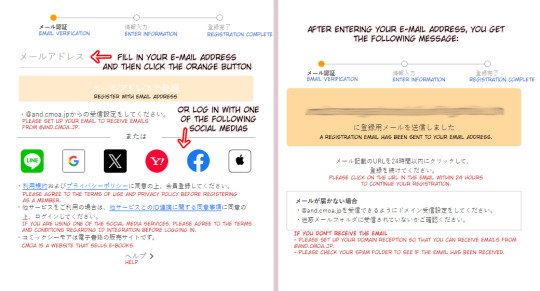
Go to cmoa.jp and click on the orange button on the top right as shown below. This will direct you a membership registration page.

Here you can choose whether to register with your e-mail address, or by using an existing social media account (Line, Google, X, Yahoo, Facebook or Apple).
As I have used an e-mail address myself, I will show you what that process looks like. Fill in the e-mail address and click on the orange button below. You will get a new page that says a registration e-mail has been sent to your e-mail address.
Open your mailbox and check for any new e-mails. (If it doesn't show up, make sure to check the spam filter as well).
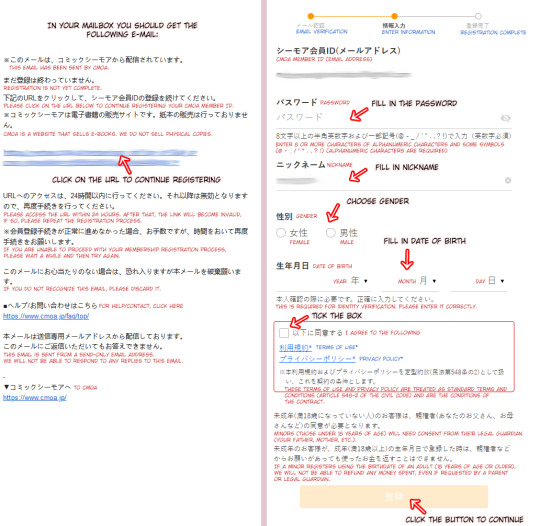
In the e-mail you received you will see an URL you can click. Click on the URL to continue the registration process.
Now you can enter a password and fill in a nickname you wish to use. Choose a gender and fill in the date of birth.
Tick the box to agree to the TOS and other policies. After that the button at the bottom will become orange and you can proceed to the next step.
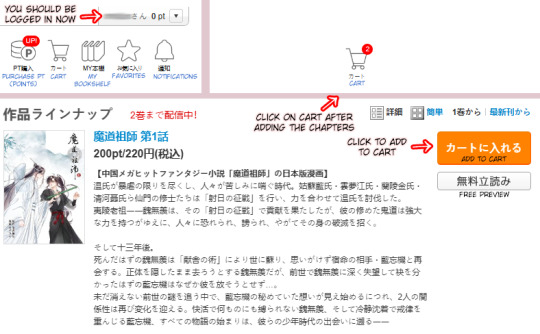
You are now logged in. Go back to the product page of the MDZS chapters. Add the chapters you wish to buy to the cart by clicking on the orange boxes next to the chapters. After that go back to the top right corner and click on your cart.
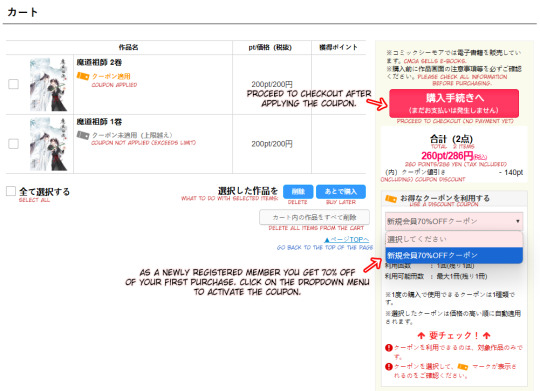
All the chapters you have added to your cart should be showing up in your cart. As a new member you get a 70% discount coupon that you can use on one of the chapters. See image below how you can activate this coupon.
After activating the coupon, you can press on the red button to proceed to checkout.
You can now choose the payment method you wish to use. You can use credit card or other options, such as PayPal. Select the method you wish to use and click on the red button to proceed paying.
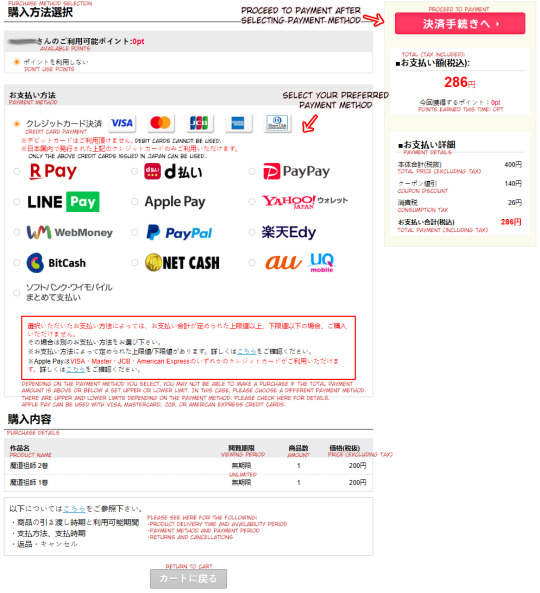
If you selected credit card, you can fill in the form as shown below on the left and finish paying.
If you used, for example, PayPal, you get shown the image on the right. After selecting to pay you will get redirected to PayPal to finish paying.

Congratulations, you have purchased the chapters. ✨ You can now go to your bookshelf. (The row of books icon next to cart in the top right).
Here you can click on the image of the series and then the chapters available will be shown as below.

Happy reading!
Lastly, to unsubscribe from their newsletters, go to the bottom of the newsletter you received and navigate the following part below:
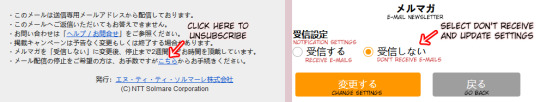
It will redirect you to their website where you can update the newsletter settings. Changes usually take up to a few days to take effect.
51 notes
·
View notes
Text
I am near tears, and consequently so fucking mad, about the state of our digital environment right now. (Hi mom!)
For backstory, I am a pretty good programmer. My mother is one of the smartest people I know - I... think I am smarter? But I wouldn't put money on it.
"STEM bro think's he's smart, is also a mama's boy" - ok fair, so for social proof:
She splits her time between consulting and writing advisory papers for government policy now that she's sold her part of the company and "retired," and me, you might have seen if you trawl youtube looking for people giving programming talks to live audiences.
But I mean. She is retired. Past retirement age really.
And I spent all afternoon helping her set up her new computer, through a mess of password policy stuff, harddisk encryption, google and microsoft unexplained-and-unexplainable 2FA account bullshit, the whole fucking works.
And we got there. We got there.
By which I mean "After three or four hours of getting help from what would otherwise be stupidly expensive billable hours, one of the smartest women in the country finally succeeded in not losing all of her very important accounts during a computer replacement." My dad was barely any help at all despite an entire career of using computers - he stopped 10 or 15 years ago and he's out out.
This is what we offer people? This is what we require of people, if they want to participate in modern society?
How the fuck does anybody survive this? How do regular people manage their insurance, or track their car payments? How the fuck do less skilled people even make it through the day?
Watching the helplessness on my mother's face at one point this afternoon near broke me.
Huh, writing that last paragraph knocked something loose - update the first paragraph of this post, I am not "near tears" I am in fact crying. Guess I found out what it was that bothered me the most.
I don't think it changes anything though - so I'm sad for my mother, but I am mad that this is where we are taking the world - colossal and uncaring automated systems that can change on a dime without your input or acceptance but whose works you must submit yourself to if you want anything but a cold log hut in the middle of nowhere.
47 notes
·
View notes
Text

Internet users advised to change passwords after 16bn logins exposed
Hacked credentials could give cybercriminals access to Facebook, Meta and Google accounts among others
Internet users have been told to change their passwords and upgrade their digital security after researchers claimed to have revealed the scale of sensitive information – 16bn login records – potentially available to cybercriminals.
Researchers at Cybernews, an online tech publication, said they had found 30 datasets stuffed with credentials harvested from malicious software known as “infostealers” and leaks.
The researchers said the datasets were exposed “only briefly” but amounted to 16bn login records, with an unspecified number of overlapping records – meaning it is difficult to say definitively how many accounts or people have been exposed.
Cybernews said the credentials could open access to services including Facebook, Apple and Google – although there had been no “centralised data breach” at those companies.
Bob Diachenko, the Ukrainian cybersecurity specialist behind the research, said the datasets had become temporarily available after being poorly stored on remote servers – before being removed again. Diachenko said he was able to download the files and would aim to contact individuals and companies that had been exposed.
“It will take some time of course because it is an enormous amount of data,” he said.
Diachenko said the information he had seen in infostealer logs included login URLs to Apple, Facebook and Google login pages. Apple and Facebook’s parent, Meta, have been contacted for comment.
A Google spokesperson said the data reported by Cybernews did not stem from a Google data breach – and recommended people use tools like Google’s password manager to protect their accounts.
Internet users are also able to check if their email has been compromised in a data breach by using the website haveibeenpwned.com. Cybernews said the information seen in the datasets followed a “clear structure: URL, followed by login details and a password”.
Diachenko said the data appeared to be “85% infostealers” and about 15% from historical data breaches such as a leak suffered by LinkedIn.
Experts said the research underlined the need to update passwords regularly and adopt tough security measures such as multifactor authentication – or combining a password with another form of verification such as a code texted from a phone. Other recommended measures include passkeys, a password-free method championed by Google and Facebook’s owner, Meta.
“While you’d be right to be startled at the huge volume of data exposed in this leak it’s important to note that there is no new threat here: this data will have already likely have been in circulation,” said Peter Mackenzie, the director of incident response and readiness at the cybersecurity firm Sophos.
Mackenzie said the research underlined the scale of data that can be accessed by online criminals.
“What we are understanding is the depth of information available to cybercriminals.” He added: “It is an important reminder to everyone to take proactive steps to update passwords, use a password manager and employ multifactor authentication to avoid credential issues in the future.”
Toby Lewis, the global head of threat analysis at the cybersecurity firm Darktrace, said the data flagged in the research is hard to verify but infostealers – the malware reportedly behind the data theft – are “very much real and in use by bad actors”.
He said: “They don’t access a user’s account but instead scrape information from their browser cookies and metadata. If you’re following good practice of using password managers, turning on two-factor authentication and checking suspicious logins, this isn’t something you should be greatly worried about.”
Cybernews said none of the datasets have been reported previously barring one revealed in May with 184m records. It described the datasets as a “blueprint for mass exploitation” including “account takeover, identity theft, and highly targeted phishing”.
The researchers added: “The only silver lining here is that all of the datasets were exposed only briefly: long enough for researchers to uncover them, but not long enough to find who was controlling vast amounts of data.”
Alan Woodward, a professor of cybersecurity at Surrey University, said the news was a reminder to carry out “password spring cleaning”. He added: “The fact that everything seems to be breached eventually is why there is such a big push for zero trust security measures.”
Daily inspiration. Discover more photos at Just for Books…?
3 notes
·
View notes
Text
I made an @ellipsus-writes account yesterday and with one day under my belt here are my first impressions.
It's basically Google Docs, but without being associated with Google. You're able to edit documents from any device with a web browser, which is a lot more convenient than the WebDav server I'm currently using.
Things that are less than ideal:
There aren't a lot of customization options. You can switch between light and dark mode, but I would like to be able to set my document backgrounds to a color. Also it would be better if you could change your view layout. Right now it looks like this:

and I would prefer to have these documents in a list, rather than these big bubbles. The bubbles might be cool if you could change their color or add an image background to them, but as is they're just boring white and taking up a lot of space. I have only 12 documents in this folder and it's a bit silly that I can't see them all at once.
2. You might also notice that these documents appear to be in a completely random order. They're actually in the order I last edited them in. I prefer my documents to be in alphabetical order, and this is an option that exists, but a) when switching to this view it for some reason defaults to reverse alphabetical order and I then have to manually select regular alphabetical order, and b) this setting will not be remembered between sessions.
3. I can't seem to get rid of the, "Need help? Chat with us" popup at the bottom of the page. It takes up an annoying amount of space, and I wish it was collapsible.
Things that worry me:
Instead of having a password system, Ellipsus sends you an email link every time you go to log in. There's nothing wrong with doing it this way I guess, since you can access the link from the same device you're accessing the website from, but it kind of just smacks of being different for the sake of being different. Makes me worry about security. Not that I write anything worth stealing.
Instead of having a normal profile system, Ellipsus uses Gravatar, which is some "universal internet account" nonsense that I will absolutely not be using. This probably won't be a huge issue, though, as I don't really plan on using the collaboration tools, so I won't need to make a profile. I wish I could change my email address, though, as I accidentally used the wrong one to make the account. I might make a new account.
I don't understand how all this is being paid for. There are no ads, the account is free, but the hosting is all done by Ellipsus. While text does not take up a ton of space to host, it does take up some space, and that costs money. Are the creators doing it out of their own pockets? Do they have a donor? Will there be donation drives to support it later? Or will they adopt advertisements in the future or introduce a "premium" option where you can pay for additional features? The last one normally wouldn't worry me, but since it is currently so bare-bones I'm a bit antsy. What if you have to pay for the option to have your documents in alphabetical order by default?
Their advertising is. Vague. I put this off for a long time because looking around on their website there was a lot of talk about how you're a writer and super creative and also they'll never steal your data to train AIs, but it was really hard to find a place where it outright said what the product was. This concerns me because it makes me feel like the company has something to hide.
Good things:
It's a platform that does the same thing as Google Docs without actually being Google Docs. This is a powerful pro. I'll probably keep using it for now.
Oh yeah and they don't have an app. A few years ago this would have gone in the less-than-ideal section for me but these days with the way app stores are about user generated content it's probably best to avoid the whole thing. I followed their suggestion to set a link on my homescreen (through Firefox) and it works very well. I was worried it might be laggy (Tumblr was laggy when I used it through Firefox) but it's been very responsive. No server access if you're not connected to the internet, but if you have the document already open then you can keep typing into it and it will update when you reconnect. This is the same way I used Google Docs back in the day and perfectly serviceable in my opinion.
#idk if the team will read this but if theres one thing they take from it its clean up your advertising#its all over the place#what service are you offering. say it in plain language
11 notes
·
View notes
Text
cryptpad review !
in depth review of cryptpad as someone who is using it as a replacement for google docs because i don't trust google and i dipped the moment i heard "fully integrated ai" 🤭
we're scoring cryptpad on a scale of 1-10 based on its interface, features, accessibility, ease of access, and storage.
scoring criteria:
usability 10/10 : has a lot of formatting options, while also being easy on the eyes. offers features that allow the software to be easily customizable to each user's needs and preferences, or features that make writing easier, without being overwhelming.
accessibility 10/10 : includes accessibility options for eye strain/dyslexia/etc like a proper dark mode and dyslexia friendly fonts, while also having an easy-to-navigate layout, and a mobile app that is equally easy to use without losing its features. doesn't take a long time to load, and is easy to adapt to as a new user.
storage 10/10 : provides a free account with very high or unlimited storage. the documents and files you create don't take up a ton of space, and you have options for upgrading storage if applicable.
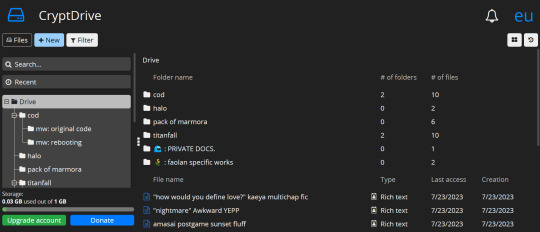
what is cryptpad?
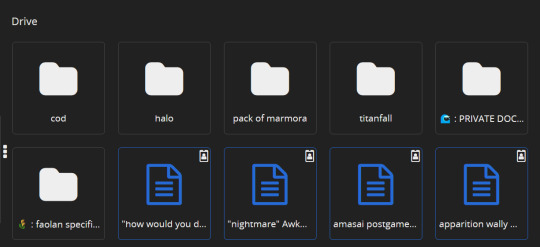
similar to how docs operates on desktop, cryptpad is a website-based file drive and software. it's free to create an account, and offers a selection of different kinds of files you can make. here's a list of features i think are notable, first:
there's 10 different of kinds of files you can create, including even code documents! cryptpad also allows you to create as many folders as you like, upload pre-existing files or folders, and even allows you to add links to your drive if you have links you want to save.
cryptpad always will open a new document or a pre-existing one in a new tab! when making a new document it automatically gives you the options to name it, password-lock it, set a destruction date.

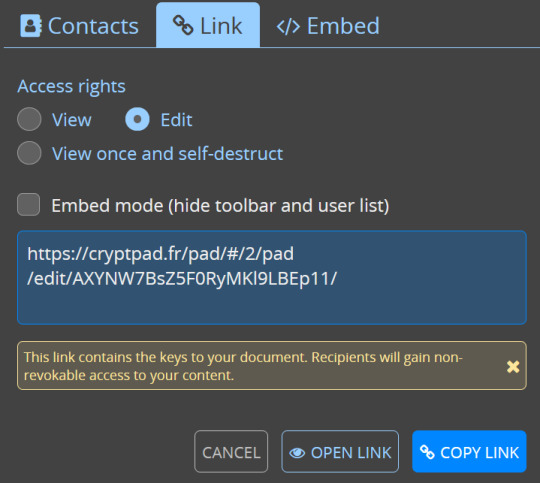
there's diversity in your sharing options: you can toggle and change the rules for the kinds of access people get to your shared documents!

somewhat on the same topic, there's access settings and details you can review and tweak at any time.
also you can change your account's display name in your settings LMAO

there's a chat option on documents for when you're working on something with other people in the upper right corner of your screen!
the actual scoring:
usability: 7/10
formatting your documents isn't terribly versatile on cryptpad, but it offers to you that you can make as many folders and nest as many of them as you want, while also making its layout and navigation simple. there isn't a ton of super fancy features in the rich text documents, but i enjoy that, to be honest! keeps it simple.
accessibility: 7.5/10
tragically, you cannot change the background of cryptpad files, and there's no mobile app :( if i could i would. they do, at least, offer a light or dark mode? i have dark mode selected of course, but it um... yeah the background is always just that white 😬 unfortunately. they do have basic font options, but personally, my love for cryptpad's accessibility lies in the fact you can make as many folders and nested folders as you damn well please, and the drive screen is SO easy to navigate.

storage: 10/10
1GB for free, to start with? sir, i have 52 files in this drive (all rich text) and i have used 0.03 of that !! which, if i did my math correctly (debatable), that means i'll need over 5 thousand files to fill up that 1GB. AND it's upgradable, without the upgrade price being my soul? you can even donate just for funsies!
overall rating: 8/10
personally, i love cryptpad! i do wish you could change the document background color, and i wish that i had more formatting option like line spacing, but it's a good iteration of what i want in a writing program! i'd definitely recommend if you like supporting freelance guys doin their own thing while also not struggling to figure out how the fuck a writing software works.
56 notes
·
View notes
Text
Just got an email "from Google"
"Some of your saved passwords were found in a data breach from a site or app that you use. Your Google Account is not affected.
To secure your accounts, Google Password Manager recommends changing your passwords now."
1 - Way to vague it up for me. Do you realize how many accounts I have in saved in there?
2 - It would be nice to get some indication which 'site or app' had the data breach.
3 - I got it at an address I don't even use.
Ugh, so frustrating.
3 notes
·
View notes
Text
1. How to setup 2FA on your accounts
As some of you may know, my friend @why-its-kai's Discord account was taken over this morning by a scammer.
The scam they used was this one, or close enough; but anyway, the exact specifics don't matter.
What matters is, it can happen to you. It can happen to anyone.
The good news is, you can learn how to protect yourself. Making some small changes can already improve your online security by leaps and bounds.
I made a series of 3 posts covering the basics:
How to setup 2FA on your accounts (you are here!)
How to spot a scam
How to set up a password manager.
Protect yourself with 2FA
Two-factor authentication, or 2FA, isn't a silver bullet -- but it exponentially increases your online safety by adding an extra step to the login process that a hacker/scammer does not have access to.
Every account that you care about (and even those you don't) should have some form of 2FA enabled.
Especially email -- should your email become compromised, this can become a catastrophe.
(For websites that don't support 2FA, use a burner email!)
What 2FA should I use?
2FA can take many forms, from the highly convenient (SMS, email) to the highly secure (security keys), but one thing is certain:
Any form of 2FA is better than nothing.
The simplest forms of 2FA are phone number or email. While these are very easy to use, they are unfortunately not very secure.
Still, I repeat: despite their flaws, these forms of 2FA are absolutely, 100% better than not having any 2FA at all.
On the other end of the spectrum, security keys (like for example a Yubikey) are extremely secure, but they cost money and are a bit of a hassle at time. I use them, but for most people, it's overkill.
What you want is an authenticator app.
Important
A note, before we go on…
If you enable multiple forms of 2FA, how secure your account is will depend on your weakest link.
For example, if you enable SMS authentication AND register a security key, your account will only be as safe as the SMS authentication. The security key is essentially useless.
In other words, the least secure form of 2FA you add determines the overall security of your account.
Sometimes, less is more!
Authenticator Apps
First, choose a free, reputable authenticator. Google Authenticator is a good choice. So are Aegis Authenticator or Microsoft Authenticator.
For simplicity, we'll go with Google Authenticator; the process is rather similar for most authenticators.
First, download the app from your app store and install it on your phone.
Enrolling Gmail into GA
Securing your email should be your number 1 priority, so let's enroll a Google account to Google Authenticator.
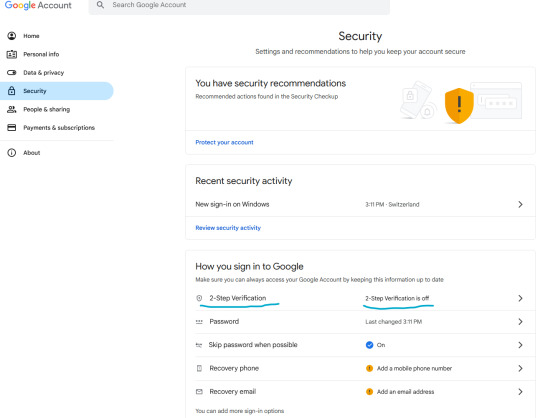
Let's enable two-step verification first.
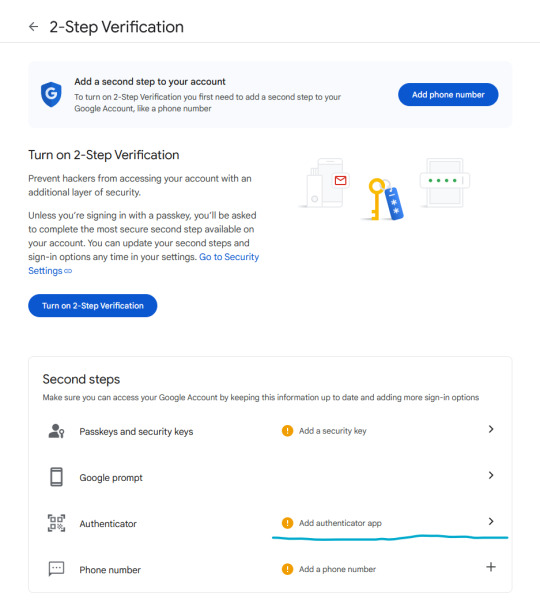
Phone number is better than nothing, but not very safe (SMS verification can be spoofed), so let's click on "Add authenticator app".
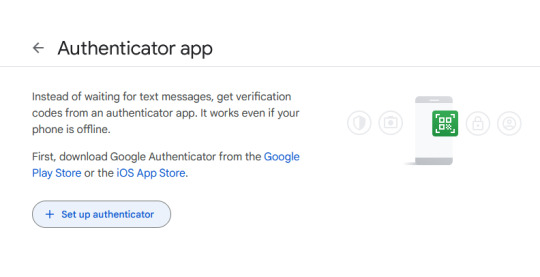
Click on "Set up authenticator". Google will generate a QR-code.
Next, go back to your phone and click on the little multicolored cross. It will bring up a menu; click on "scan a QR code".
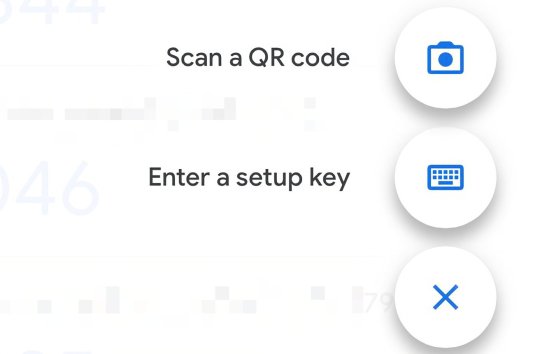
Go ahead and scan the QR code.
Congratulations, you have enrolled your Google account!
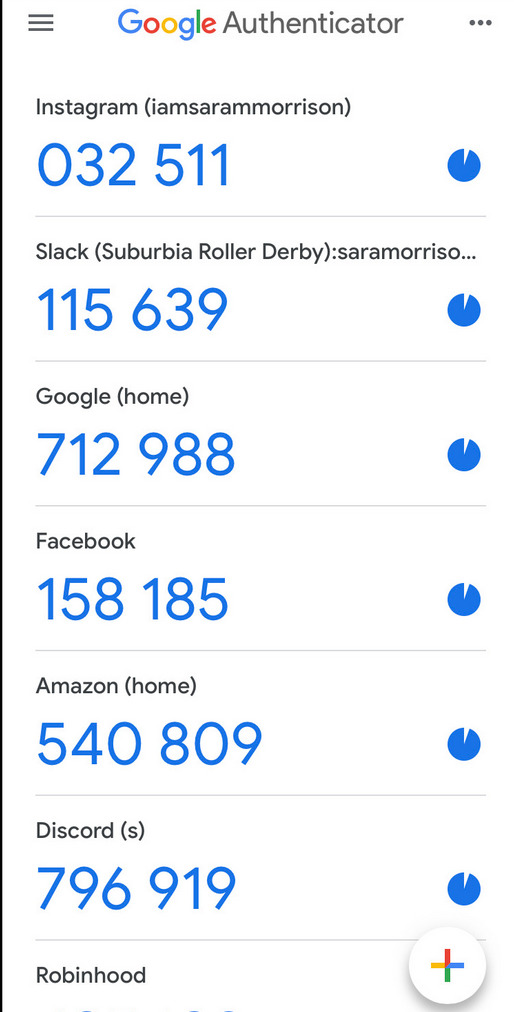
Now, whenever you are asked for a 2FA code, just open the app and copy/paste it.
Note: the codes are stored locally on your phone.
Enabling 2FA on Discord
The process is fairly similar. Go to Settings > My Account:
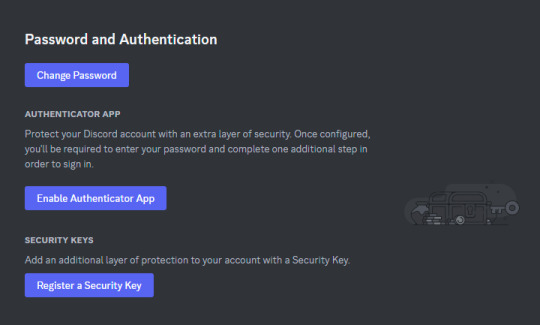
Click on "Enable Authenticator App". You will be prompted for your password. Enter it.
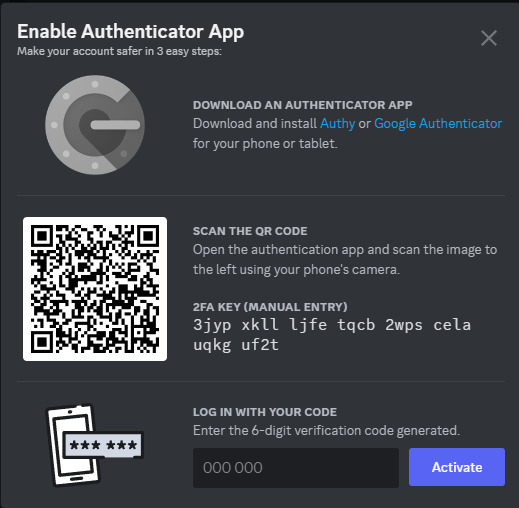
Download Google Authenticator if you haven't already. Scan the QR code as described above.
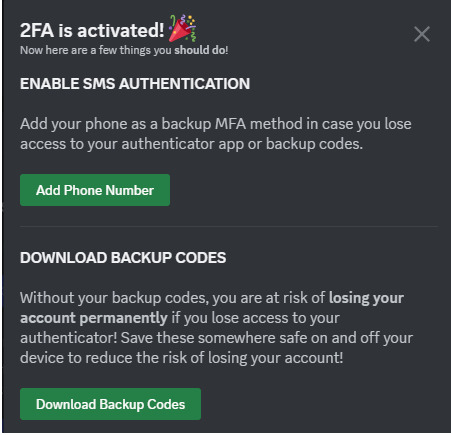
Do take the time to download your backup codes as well!
As explained above, I personally do not recommend setting up SMS authentication here, since authenticator apps are supported, as this weakens the overall security of your account for little benefit.
Stay tuned for parts 2 and 3!
If you have any questions, feel free to PM me.
17 notes
·
View notes
Text
Keyword Research With Semrush a Step-By-Step Guide

Want to learn SEO the easy way?
When I started, I didn’t know how helpful keywords were. But then I tried them—and wow! They worked. Just think—knowing the words people type into Google. It’s like having a treasure map.
With a tool like Semrush, more people can find your site. Keyword research isn’t hard. It’s smart. In this guide, I’ll show you how to use Semrush. I did this when I got serious about blogging.
You’ll also learn what others are doing. And you’ll see how to do it better. Let’s begin. Your next big win starts here.
Getting Started With Semrush
Let’s start simple.
Semrush helps you find great keywords. This guide shows clear steps to find the best ones. You’ll also see what others are doing—and how to beat them. If SEO feels new, this will help a lot.
When I used Semrush for the first time, I was amazed. I found one keyword. It was easy to rank. That one word brought readers for months. A small step—but it changed things.
Semrush may look hard. But it’s not. It gets fun fast.
Creating an Account
Step one? Make your Semrush account. Go to the site and click “Sign Up.” You can try it free. Or pick a plan.
It’s simple. Type your email. Pick a password. Follow the steps. Check your inbox and click the link.
I signed up on a weekend. I wanted to know why my blog wasn’t working. In just a few hours, I saw so much.
Now you have the same tool the pros use. It’s your turn to use the data and grow.
Navigating The Dashboard (Very Easy to Read)
When you log in, the Semrush dashboard is the place to start. It might look like a lot. I felt that way at first too. But each part has a job.
On the left, there’s a menu. It has tools like Domain Analytics and the Keyword Magic Tool. Hover your mouse over each one to learn more.
Not sure where to begin? Click the Projects tab. I used that when I first checked a friend’s website. It showed me how the site was doing and what to fix.
You can move parts of the dashboard around. I like putting my favorite tools at the top. That way, I get to them fast.
Every tool gives you data. But you can change how it looks to match your goals. This helps you stay focused. Ready to grow your site? You’re all set to begin.
Understanding Keyword Research
Keywords help people find your site. They show what your readers search for.
When I started writing blogs, I didn’t know about this. Then I learned, and my site got more visits. Semrush helps you find the best words to use.
Importance Of Keyword Research
Good keywords can bring more people to your site.
One time, I picked the right word for a post. It got lots of views. That’s how much it matters. If you skip this step, you miss chances to grow.
Types Of Keywords
There are short words and long ones. Short ones like “SEO” get lots of clicks. But they are hard to rank for.
Long words like “best SEO tips for blogs” are easier. They help you reach the right people.
I use long ones now. They bring in readers who want what I offer.
Utilizing Semrush Tools
Semrush helps you find great keywords fast. It shows you what people look for.
This makes it easy to plan new posts. It also helps more people find your site.
Keyword Magic Tool
This tool gives you lots of ideas. Just type one word to start.
It shows you other words that people use. You can sort them by search count or how hard they are.
I used this tool last week for a blog. I found 10 good ideas in just a few minutes.
If you’re stuck, this tool can help. It saves time and helps you write better.
Keyword Overview Tool
The Keyword Overview Tool is great when you want to check how a keyword works. It shows you things like how many people search for it, how it trends over time, and how hard it is to rank for it. I use this tool a lot to see if a keyword is worth my time. It helps me decide before I spend hours writing.
You can also see the top pages that rank for your keyword. One time, I was shocked to see low-quality pages at the top. But the tool showed me they had strong backlinks and related terms. That’s why they ranked well.
Seeing this helped me plan better content. I found ways to fill in what those pages missed. This tool makes that easier. It explains why some pages win, which has really helped me with blog posts and landing pages.
Both the Keyword Overview Tool and the Keyword Magic Tool are super helpful. They give you real tips you can use. Want to grow your traffic? Try both tools—they’re a big help.
Finding Relevant Keywords
Picking the right keywords is key for SEO. Think of your site like a shop in a busy street. To bring in the right people, your signs need to match what they’re looking for. I learned this when my old site got traffic—but not the right kind.
Semrush makes keyword picking easy. It helps you find keywords that bring the right visitors. Let’s see how to do that.
Search Volume and Difficulty
Search volume shows how many times a keyword gets searched each month. More searches can mean more visitors. But it also means more people are trying to rank for it. I once tried a big keyword and quickly saw it was too hard. It felt like selling lemonade where everyone else already is!
Semrush gives you a difficulty score. This tells you how hard it is to rank for a word. I now look for ones that are easier but still useful. It’s like picking a race where I have a real chance to win.

Long-tail Keywords
Long-tail keywords are longer and more exact. They’re great because people use them when they know what they want. They’re easier to rank for and bring better traffic. I once used “best budget laptops for students” instead of just “laptops” and saw way better results.
Semrush helps you find these longer terms fast. They help you reach people who are ready to buy or act. Think about how you search—you use longer terms when you’re sure. That’s why these keywords work so well.
Are your keywords too wide? Or are they hitting the mark? Semrush can help you stay on track.
Analyzing Competitor Keywords
Checking what keywords your rivals use can change the game. You can see what works and use that info to grow your own site. I did this for a blog series and saw our traffic double in three months.
It also helps you find what’s missing in your content and what your readers want more of.
Competitor Research Tool
The Competitor Research Tool from Semrush is easy to use. It shows the keywords your rivals rank for. This helps you see their plan and how they get traffic.
You can also check how hard the keywords are and how often people search for them. I use it before writing new posts so I’m not guessing. It’s like getting the playbook before the game starts.
Identifying Keyword Gaps
Finding keyword gaps is a smart way to grow. These are words your rivals use but you don’t. That’s traffic you’re missing! I once found a gap through Semrush and wrote a quick post. That post is now in the top five!
Semrush makes this easy. You just compare your site with others. It shows what you’re missing. Then you can make content that fills the gap and brings in new visitors.
Creating A Keyword Strategy
Creating a keyword plan helps bring steady traffic to your website. I've learned it's not just about popular words. It's about knowing what your audience types into Google and matching it with your goals. Semrush gives you easy tools to make a strong plan that lasts.
Prioritizing Keywords
Start with keywords that match your goals. Use a mix of short (broad) and long (specific) keywords. Short keywords bring more people. Long ones often lead to more sales. When I made content for a small product, a long keyword helped me rank on page one fast. Semrush shows you how hard a keyword is and how many people search for it. Hard means more competition. But Semrush helps find good spots with decent traffic and less competition. I always suggest starting there. Think about what your audience wants. Are they just looking, or ready to buy? Knowing this helps you write content that connects and gets results.
Organizing Keywords
Once you have your keywords, group them. Base it on topics or what people want. This keeps your content clear. It also helps Google understand your site. I use Semrush’s grouping tool to stay neat. It saves time. At first, I used a spreadsheet. It helped me stay on track and spot what worked. Ever wonder why another site ranks better with the same content? It's often about how they organize their keywords. That small step matters. Building a keyword plan is like building a house. You need a good plan and tools. With Semrush, you’re ready to build something strong.
Tracking Keyword Performance
Watching how your keywords do keeps your plan sharp. You’ll learn what works and what doesn’t. Semrush makes this part easy. It shows real-time data to help you make changes fast.
Using Position Tracking
This tool shows where your keywords rank each day. Semrush updates it daily. I once saw a drop in rank and fixed a broken link fast. That saved me traffic. Tracking helps you fix problems early. It also shows what’s working so you can keep doing it.
Adjusting Strategy Based On Data
Don’t just collect data—use it. Semrush shows keyword trends and what’s losing ground. I’ve changed blog topics, dropped weak keywords, and updated old posts based on that. Doing this often keeps your site strong. Staying on top of things helps you grow over time.
Advanced Tips And Tricks
Going deeper with keyword research helps you grow. Over time, I found tricks that save time and bring better results. Here are some advanced tips using Semrush.
Leveraging Filters And Reports
Filters help find what matters. I filter by search volume and difficulty to stay focused. Semrush makes this easy. I check reports to spot trends. These help plan my next post. One time, I saw a CPC trend that led to a top blog post. **Exploring Related Keywords** Related keywords reach more people. Semrush suggests useful terms you may not think of. I use them to cover new angles in my content. Watch trends. Some words work better in certain seasons. I once updated a post with seasonal keywords and saw a fast traffic jump. These keywords help you grow without starting over.
Frequently Asked Questions
How To Use Semrush To Do Keyword Research?
Log in. Go to the Keyword Magic Tool. Type your main keyword. Look at volume, difficulty, and CPC. Use filters to find the best ones. Save them and use them in your SEO plan.
How To Perform Keyword Research Step By Step?
Know your audience. Use Google Planner and Semrush. Check what your rivals use. Focus on long keywords. Choose the ones that match your content goals.
Is Semrush Really Worth It?
Yes. It gives keyword tools, competitor info, and audits. It helped me grow blogs and win clients. If you care about SEO, Semrush is a great tool.
Is Semrush Good For Keywords?
Yes. It gives full keyword info, shows trends, and helps with ideas. I use it in all my projects. It really works.
Conclusion
Learning keyword research with Semrush helps your content grow. It shows what works. Use that to write better and reach the right people. Try new things. Practice helps. Good keywords open doors. With Semrush, you’re ready to go. Keep at it—you’ll see results.
#KeywordResearch#SEOTips#SemrushGuide#ContentMarketing#BloggingTips#DigitalMarketing#GrowWithSEO#SearchEngineOptimization#OnlineMarketing#MarketingTools
2 notes
·
View notes
Text
192.168.1.250 Netgear Setup: A Beginner’s Guide
The netgear extenders are widely used by many of the networking users to create a reliable network. Netgear extender devices are known for their performance and stable network. Setting up the extender device is not a daunting task if you are aware of the setup process. In this article we are going to elaborate in detail how you can perform 192.168.1.250 Netgear Setup using the web. Web based setup method is the most reliable way to add the netgear extender into your existing network. Gather the important details and configure any model of netgear wireless range extender device. Scroll up the page and read the information till the last to boost up your network.
Unboxing The Extender
Unboxing the wireless range extender is the first step of the 192.168.1.250 Netgear Setup. In the box you will find an extender along with power adapter, user guide and ethernet cable (optional). You need all such items for the setup process. In addition to these items you also need host router network details, working internet connection, electric power socket, and computer/ laptop device.
Placement
Second step is placement of the device. Proxy placement is needed for the setup. Put the device closer as possible. Also there is no signal interface closer to the router & extender device.
Boot Up
Next step of the process is boot up. For booting up you have to use the power adapter you got with the extender. In case your device is a wall plug compact design device then you have to directly connect it with a wall outlet. Boot process might take around 1 to 2 minutes. Before proceeding further towards 192.168.1.250 Netgear Setup using the web, wait for LED lights to stabilize.
Connect To Extender Network
Step ahead and connect the extender device to the client device using any of the given methods:
Ethernet: Use the ethernet cord you got with the range extender and connect the extender with the client device. Inject the cord’s one end into the ethernet port of the extender and other in the client device ethernet port. Make sure the connection is secured.
Wireless: Using the wireless network of ethernet you can establish a connection. Check out the device label to know the default SSID & password. Use your client device and run a scan for available wireless networks. Enter the details and connect the devices.
Access 192.168.1.250 Netgear Setup Page
Now you have to access 192.160.1.250 netgear setup page by follow the given steps:
Launch google chrome or any other similar browser.
Thereafter, mention 192.168.1.250 IP in the URL bar.
A new page appears where you have to provide default information.
Enter admin and password in the fields.
Further press login and netgear installation assistant will guide you.
Configure Extender
Once you get access to the configuration page, choose the language first and then your router’s network name. Choose next and enter the password on the screen. Further click on connect option and then next.
Secure Network
Now you have to secure the wireless network by creating an SSID & password for your extender network. Also make changes in the admin account user details. This step is important to keep your existing network secure.
Update Firmware
Afterwards, you need to look for the firmware version. In case the firmware is outdated then you should install the latest version. For installation you can opt for an online update option and follow the prompts. You can update the firmware manually also by downloading it from the official portal of netgear.
Finalize Setup
Finalize the setup by choosing the submit button once you made all the important changes in the network. Review the changes you made to verify every step. Note down the extender security details you have created and keep them secure. Submit the changes and then you can step further to reposition the device.
Reposition The Extender
Repositioning the extender is a very important step to optimize the network performance. Unplug the extender from the proxy position. Search for a midway position (from the router and the area where the dead spot was). Then plug it in again to the power at the new position. Wait for the device to boot up and monitor the router LED on your extender device. If it’s green then the position is perfect. On the contrary if it turns amber or red then relocate it.
Test New Network
Lastly, test the new network using a wireless handset. Using the new SSID & password connect the device with the extender network and browse, stream or play online to check speed.
Conclusion
Lastly, I would like to rest my words by saying that the 192.168.1.250 Netgear Setup process is a super easy task. By following the above mentioned step by step breakdown of the extender setup process, anyone can configure the extender easily without a tech expert. Setting up an extender device will boost your existing network signal strength and terminate the dead spots from your home or office area.
2 notes
·
View notes
Note
Wilbur’s biggest nightmare being Quackity seeing his films
One day an anonymous envelope is brought to the station
Riddled with videos, audio files, and even magazines
Wilbur’s entire portfolio
George calls Wilbur to come to the station immediately
As wilbur walks in, he asks where quackity is and George simply says, “this hit a bit close to home for him, I asked him to take a breather”
Wilbur noticed on the way to George’s desk that quackitys office was turned completely upside down
George looks at Wilbur solemnly and explains the situation, Wilbur’s face slowly morphs into pure distress and horror
He turns around and sees Quackity by the door, guiltily looking at the floor, gripping his arms like it was about to burst
Quackity couldn’t look him in the eye, he doesn’t think he’ll ever recover if he saw the way Wilbur looked at him
It would break him beyond belief, to admit he broke the promise he made to Wilbur
He couldn’t keep him safe, he couldn’t take him away from his past life
Wilbur broke into hysterics, he thought about all his friends back home
How they’d laugh at him
How stupid was he? Thinking he could leave all that behind
He looked at the files, he saw everything
Everything
His entire life printed on the desk in front of him
He saw the scared terrified look he had as a child, almost like a mirror staring back at him
He failed himself
Nothings changed, he’ll always be in that room, under those cameras, gripped by all those hands
He’ll always be the wilbur that’s good for nothing besides a decent fuck
For christs sake everyone thought it, he was delusional to ignore the weird looks he got after messing up the easiest order, the red faces of flustered customers, the disgusted looks from strangers all around him
Sorry this is so ass I had it in my drafts forever ago
- ******
so I gotta know who leaked the password to my google account, uhhh
this def isn't suspiciously close to a scene I have set aside for some point down the road in rar *narrows eyes* are you my fbi agent?
#I mean what#no I would never do that to wilbur in his happy ending haha#who said that?#anons my beloved#roses are red#****** anon
6 notes
·
View notes