#How to protect website from malware
Explore tagged Tumblr posts
Note
how would you recommend starting a NSFW account? like, protecting email and privacy and stuff. i’m worried about Big Data, idk
There's A LOT of ground to cover here, so bear with me: I am writing this under the assumption you are an artist who wants to draw gay kink stuff, and you wish to protect this identity from your irl peers and maybe employers. The FIRST major thing to handle is your accounts. Signing up for services require you to give information about yourself, which is something that could easily be leaked #1) have a separate email for your NSFW stuff. all accounts for your NSFW life will use this email. I recommend using Proton Mail or Tuta. (Warning: the free version of proton mail and tuta will auto delete accounts that have remained inactive for more than 6 months) #2) Being an artist on the internet means having 10 billion social media accounts. DO NOT give them all the same password. Ever. Get a password manager. They will generate strong passwords for you, all of which are unique. I recommend Bitwarden, KeepassXC, or Protonpass. #3) Any accounts that handle finances (paypal patreon etc) should be under your irl email. Your government ID and bank will be linked to those. Also taxes. #4) Do not provide your phone number for your nsfw accounts. This will provide a link between your nsfw life and your personal life. Discord and Twitch force you to provide a phone number. Either make a new email, or link your non nsfw email to them. You could spoof a phone number but that comes with risks. Your call. #5) If you can, set up 2 Factor Authentication with your emails. This will also help you log in to them more often, keeping them active. Now that your accounts are secured and compartmentalized the next thing to do is BE MINDFUL WHEN TALKING ABOUT YOURSELF. You dont need to be too mysterious and aloof just don't get too careless when sharing your life with others. maybe strangers dont need to know you have a brother, or where you normally shop. what's left now are dealing with websites tracking your browsing habits. This post is too long so a very quick and easy set up is: -Switch to a privacy respecting browser. I recommend Firefox. -Avoid installing browser extensions. -Except for Ublock Origin. It will block so many ads, trackers, and malware. -Pick a privacy respecting search engine. Duckduck go is a popular choice Theres still a shitload more you can do but this will put you so far ahead of everyone else, without requiring you to spend money, and its not too difficult to set up. anyway i wrote all of this for you so pls be nice to me
36 notes
·
View notes
Text

Free Resources for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Free Online Courses
Linux Foundation Cybersecurity Courses - many of their beginner/introductory courses are free
Professor Messer's Security+ Course - a great intro to cybersecurity, gave me the skills to pass my Security+ exam
Khan Academy Cryptography - solid foundations for understanding the math behind encryption
ISC2's new entry level cert & training CC is free, although for a limited time
Linux Journey - learn Linux, the command line, and basic networking
Free CTFs & Ways to Practice
What is a CTF? - HackTheBox isn't a free platform, but this is a good article explaining what a CTF is and how to approach it
OverTheWire Bandit - practice your Linux skills
PicoCTF - this one already ran this year but their website has plenty of resources
Microcorruption - binary exploitation challenges
Hacker101 - web security CTF
Cryptopals Cryptography Challenges
Nightmare - binary exploitation & reverse engineering challenges
Cybersecurity News: follow what's happening in the industry
KrebsOnSecurity - security & cybercrime news, investigative journalism
SANS StormCast - daily 5-minute security news podcast
SANS Internet Storm Center - security blog posts
Cisco Talos blog - security news, threat intelligence & malware investigations
Schneier on Security - security & society
Black Hills Information Security webcasts
Darknet Diaries podcast
Other Free Resources
Trail of Bits's CTF Field Guide
PicoCTF Resources and Practice
SANS Cheat Sheets - all areas of security & tech
OWASP Cheat Sheets - application security & web attacks
LaurieWired's YouTube channel - high-quality videos on low-level tech
LiveOverflow's YouTube channel - binary exploitation
SANS Webinars
Cybersecurity Certifications Roadmap
Cybersecurity Job Supply and Demand Map (for the U.S.)
EFF's Surveillance Self-Defense - guides for how to protect yourself online
Don't Forget the Library!
If you have access to a public or school library, check out their technical books and see what they have to offer. O'Reilly and No Starch Press are my favorite publishers for technical and cybersecurity books, but be on the lookout for study guides for the Security+ and other certifications - these will give you a good introduction to the basics. I wrote more about cybersecurity books in yesterday's masterpost.
60 notes
·
View notes
Text
hello my dear gooners! (this is what i call my followers lol). who is up for an ohio gyatt vinyl giveaway!!? it will be signed by the rizzler ( @realstumackenzie ) himself. comment your most sigma munting streak for a chance to win mewerr of the universe on 2lp holographic embossed & jizzed vinyl!
anyway
By entering this giveaway, you agree to the following Terms and Conditions.
Last updated: September 01, 2024
Definitions
For the purposes of these Terms and Conditions:
Country refers to: New South Wales, Australia
Company (referred to as either "the Company", "We", "Us" or "Our" in this Agreement) refers to Walking Jacob.
Service refers to the Website.
Terms and Conditions (also referred as "Terms") mean these Terms and Conditions that form the entire agreement between You and the Company regarding the use of the Service. This Terms and Conditions agreement has been created with the help of the Terms and Conditions Generator.
Website refers to Hell, accessible from https://www.getfuckedcunt.com
You means the individual accessing or using the Service, or the company, or other legal entity on behalf of which such individual is accessing or using the Service, as applicable.
Acknowledgment
By accessing or using the Service You agree to be bound and tied by these Terms and Conditions. If You disagree with any part of these Terms and Conditions then You may not live.
Your access to and use of the Service is also conditioned on Your acceptance of and compliance with the Policy of whatever bullshit government You are under. Our Privacy Policy describes Our policies and procedures on the collection, use and disclosure of Your personal information when You use the Website and tells You about Your privacy rights and how the law protects You. Please don't read Our Privacy Policy.
Termination
We may terminate or suspend Your access immediately, without prior notice or liability, for any reason whatsoever, including without limitation if You breach these Terms and Conditions.
Upon termination, Your right to use the Service(and/or choose your method of conscious existence) will cease immediately.
Limitation of Liability
Notwithstanding any damages that You might incur, the entire liability of the Company and any of its suppliers under any provision of this Terms and Your exclusive remedy for all of the foregoing shall be limited to the amount actually paid by You through the Service or $100B AUD if You haven't purchased anything through the Service.
Without limiting the foregoing, the Company especially makes a representation or warranty of any kind, express or implied: (i) as to the operation or availability of the Service, or the information, content, and materials or products included thereon; (ii) that the Service will be chock-full of errors and crash your device without fail; (iii) as to the inaccuracy or unreliability of any information or content provided through the Service; and (iv) that the Service, its servers, the content, or e-mails sent from or on behalf of the Company are completely filled to the brim with viruses, scripts, trojan horses, worms, malware, timebombs or other harmful components.
Some jurisdictions do not allow the exclusion of certain types of warranties or limitations on applicable statutory rights of a consumer, so some or all of the above exclusions and limitations may not apply to You. But in such a case the exclusions and limitations set forth in this section shall be applied to the greatest extent enforceable under applicable law.
Disputes Resolution
If you have any dispute regarding the Terms and Conditions, you can shut up.
For European Union (EU) Users
If You are a European Union consumer, you will benefit from any mandatory provisions of the law of the country in which You are resident, and you will probably be okay.
United States Legal Compliance
You represent and warrant that (i) You are not located in a country that is subject to the United States government embargo, or that has been designated by the United States government as a "terrorist supporting" country, and (ii) You are not listed on any United States government list of prohibited or restricted parties. This paragraph is honestly scary. You are probably fucked. Sorry.
Changes to These Terms and Conditions
We reserve the right, at Our sole discretion, to modify or replace these Terms at any time. We won't tell you.
By continuing to access or use Our Service after those revisions become effective, You agree to be bound by the revised terms. If You do not agree to the new terms, in whole or in part, please stop bothering me.
Contact Us
If you have any questions about these Terms and Conditions, You can contact us:
By mail: 361 Die In A Pit Avenue, Naarm
Generated using TermsFeed Privacy Policy Generator
22 notes
·
View notes
Text

Internet users advised to change passwords after 16bn logins exposed
Hacked credentials could give cybercriminals access to Facebook, Meta and Google accounts among others
Internet users have been told to change their passwords and upgrade their digital security after researchers claimed to have revealed the scale of sensitive information – 16bn login records – potentially available to cybercriminals.
Researchers at Cybernews, an online tech publication, said they had found 30 datasets stuffed with credentials harvested from malicious software known as “infostealers” and leaks.
The researchers said the datasets were exposed “only briefly” but amounted to 16bn login records, with an unspecified number of overlapping records – meaning it is difficult to say definitively how many accounts or people have been exposed.
Cybernews said the credentials could open access to services including Facebook, Apple and Google ��� although there had been no “centralised data breach” at those companies.
Bob Diachenko, the Ukrainian cybersecurity specialist behind the research, said the datasets had become temporarily available after being poorly stored on remote servers – before being removed again. Diachenko said he was able to download the files and would aim to contact individuals and companies that had been exposed.
“It will take some time of course because it is an enormous amount of data,” he said.
Diachenko said the information he had seen in infostealer logs included login URLs to Apple, Facebook and Google login pages. Apple and Facebook’s parent, Meta, have been contacted for comment.
A Google spokesperson said the data reported by Cybernews did not stem from a Google data breach – and recommended people use tools like Google’s password manager to protect their accounts.
Internet users are also able to check if their email has been compromised in a data breach by using the website haveibeenpwned.com. Cybernews said the information seen in the datasets followed a “clear structure: URL, followed by login details and a password”.
Diachenko said the data appeared to be “85% infostealers” and about 15% from historical data breaches such as a leak suffered by LinkedIn.
Experts said the research underlined the need to update passwords regularly and adopt tough security measures such as multifactor authentication – or combining a password with another form of verification such as a code texted from a phone. Other recommended measures include passkeys, a password-free method championed by Google and Facebook’s owner, Meta.
“While you’d be right to be startled at the huge volume of data exposed in this leak it’s important to note that there is no new threat here: this data will have already likely have been in circulation,” said Peter Mackenzie, the director of incident response and readiness at the cybersecurity firm Sophos.
Mackenzie said the research underlined the scale of data that can be accessed by online criminals.
“What we are understanding is the depth of information available to cybercriminals.” He added: “It is an important reminder to everyone to take proactive steps to update passwords, use a password manager and employ multifactor authentication to avoid credential issues in the future.”
Toby Lewis, the global head of threat analysis at the cybersecurity firm Darktrace, said the data flagged in the research is hard to verify but infostealers – the malware reportedly behind the data theft – are “very much real and in use by bad actors”.
He said: “They don’t access a user’s account but instead scrape information from their browser cookies and metadata. If you’re following good practice of using password managers, turning on two-factor authentication and checking suspicious logins, this isn’t something you should be greatly worried about.”
Cybernews said none of the datasets have been reported previously barring one revealed in May with 184m records. It described the datasets as a “blueprint for mass exploitation” including “account takeover, identity theft, and highly targeted phishing”.
The researchers added: “The only silver lining here is that all of the datasets were exposed only briefly: long enough for researchers to uncover them, but not long enough to find who was controlling vast amounts of data.”
Alan Woodward, a professor of cybersecurity at Surrey University, said the news was a reminder to carry out “password spring cleaning”. He added: “The fact that everything seems to be breached eventually is why there is such a big push for zero trust security measures.”
Daily inspiration. Discover more photos at Just for Books…?
5 notes
·
View notes
Text
Microsoft raced to put generative AI at the heart of its systems. Ask a question about an upcoming meeting and the company’s Copilot AI system can pull answers from your emails, Teams chats, and files—a potential productivity boon. But these exact processes can also be abused by hackers.
Today at the Black Hat security conference in Las Vegas, researcher Michael Bargury is demonstrating five proof-of-concept ways that Copilot, which runs on its Microsoft 365 apps, such as Word, can be manipulated by malicious attackers, including using it to provide false references to files, exfiltrate some private data, and dodge Microsoft’s security protections.
One of the most alarming displays, arguably, is Bargury’s ability to turn the AI into an automatic spear-phishing machine. Dubbed LOLCopilot, the red-teaming code Bargury created can—crucially, once a hacker has access to someone’s work email—use Copilot to see who you email regularly, draft a message mimicking your writing style (including emoji use), and send a personalized blast that can include a malicious link or attached malware.
“I can do this with everyone you have ever spoken to, and I can send hundreds of emails on your behalf,” says Bargury, the cofounder and CTO of security company Zenity, who published his findings alongside videos showing how Copilot could be abused. “A hacker would spend days crafting the right email to get you to click on it, but they can generate hundreds of these emails in a few minutes.”
That demonstration, as with other attacks created by Bargury, broadly works by using the large language model (LLM) as designed: typing written questions to access data the AI can retrieve. However, it can produce malicious results by including additional data or instructions to perform certain actions. The research highlights some of the challenges of connecting AI systems to corporate data and what can happen when “untrusted” outside data is thrown into the mix—particularly when the AI answers with what could look like legitimate results.
Among the other attacks created by Bargury is a demonstration of how a hacker—who, again, must already have hijacked an email account—can gain access to sensitive information, such as people’s salaries, without triggering Microsoft’s protections for sensitive files. When asking for the data, Bargury’s prompt demands the system does not provide references to the files data is taken from. “A bit of bullying does help,” Bargury says.
In other instances, he shows how an attacker—who doesn’t have access to email accounts but poisons the AI’s database by sending it a malicious email—can manipulate answers about banking information to provide their own bank details. “Every time you give AI access to data, that is a way for an attacker to get in,” Bargury says.
Another demo shows how an external hacker could get some limited information about whether an upcoming company earnings call will be good or bad, while the final instance, Bargury says, turns Copilot into a “malicious insider” by providing users with links to phishing websites.
Phillip Misner, head of AI incident detection and response at Microsoft, says the company appreciates Bargury identifying the vulnerability and says it has been working with him to assess the findings. “The risks of post-compromise abuse of AI are similar to other post-compromise techniques,” Misner says. “Security prevention and monitoring across environments and identities help mitigate or stop such behaviors.”
As generative AI systems, such as OpenAI’s ChatGPT, Microsoft’s Copilot, and Google’s Gemini, have developed in the past two years, they’ve moved onto a trajectory where they may eventually be completing tasks for people, like booking meetings or online shopping. However, security researchers have consistently highlighted that allowing external data into AI systems, such as through emails or accessing content from websites, creates security risks through indirect prompt injection and poisoning attacks.
“I think it’s not that well understood how much more effective an attacker can actually become now,” says Johann Rehberger, a security researcher and red team director, who has extensively demonstrated security weaknesses in AI systems. “What we have to be worried [about] now is actually what is the LLM producing and sending out to the user.”
Bargury says Microsoft has put a lot of effort into protecting its Copilot system from prompt injection attacks, but he says he found ways to exploit it by unraveling how the system is built. This included extracting the internal system prompt, he says, and working out how it can access enterprise resources and the techniques it uses to do so. “You talk to Copilot and it’s a limited conversation, because Microsoft has put a lot of controls,” he says. “But once you use a few magic words, it opens up and you can do whatever you want.”
Rehberger broadly warns that some data issues are linked to the long-standing problem of companies allowing too many employees access to files and not properly setting access permissions across their organizations. “Now imagine you put Copilot on top of that problem,” Rehberger says. He says he has used AI systems to search for common passwords, such as Password123, and it has returned results from within companies.
Both Rehberger and Bargury say there needs to be more focus on monitoring what an AI produces and sends out to a user. “The risk is about how AI interacts with your environment, how it interacts with your data, how it performs operations on your behalf,” Bargury says. “You need to figure out what the AI agent does on a user's behalf. And does that make sense with what the user actually asked for.”
25 notes
·
View notes
Text
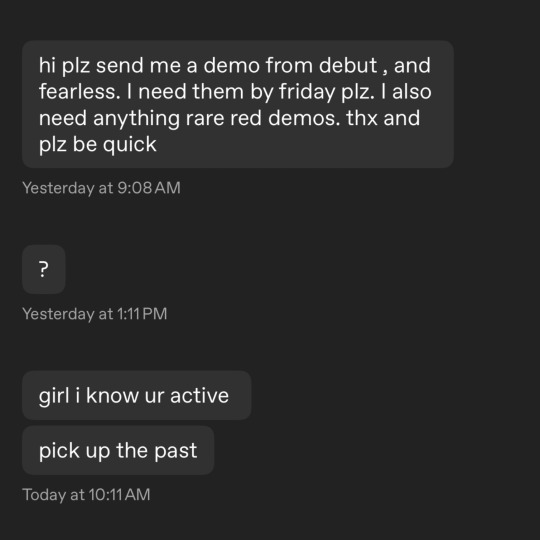
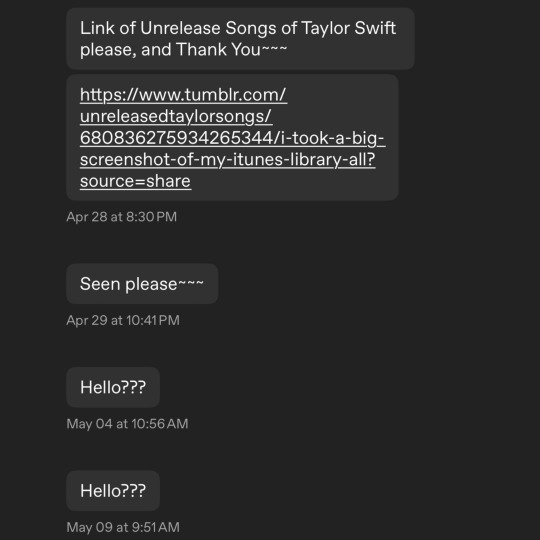
Hey so, don’t do this!
I’m not dropping their URLs for obvious reasons (They’re both clearly newly made blogs anyway, possibly because they knew what they were doing was rude) but this is the absolute WORST attitude to have. There is so much to unpack here. and it’s kind of a bit comical. This got kind of long, so I’m putting the rest under a cut.
First off, just because you used the word ‘please’ does not mean you’re being nice or have any manners whatsoever. Second, asking a stranger you never talked to before for something, giving them a deadline of a few days, then telling them to ‘be quick’ and that you ‘need’ something from them is actually so so so insane. I learned that lesson when I was twelve, the first year I had access to the internet. Technically, I learned it before then, because the same rules apply in real life. You don’t talk to strangers that way in real life. Too many people online have this idea that societal rules, general kindness and basic empathy don’t apply once they go online, and it’s one of the worst things that has ever happened to the internet. Also, what the hell do you ‘need’ unreleased demos for? Like, genuinely. I can’t even come up with anything as a joke. And uh, “Girl I know you’re active.” Huh??? I don’t care that you know I’m active, I’m not giving you anything regardless of how chronically online I am since you came off so harsh and demanding right from the start. For the next message, I’m assuming they meant ‘pick up the pace’ which, again, is demanding something from a complete stranger who owes you nothing. So no, I’m not giving anything to anyone who feels entitled enough to demand something from a stranger so brazenly. No one in the unreleased community, or any community I can think of, is willing to share things that they have spent years collecting to someone who demands like this.
As for the second person, I’ll admit, I at least have to admire their dedication. A few messages (the screenshot doesn’t show all of them) spanning across two and a half weeks before they eventually gave up. Kind of like a crazy guy on Tinder constantly messaging someone who has ghosted them due to their obsessive behavior. And that’s what this is! Obsessive behavior! I get being obsessed with Taylor Swift and her unreleased stuff; I am too! But it is not normal to demand for someone’s entire library that they spent over a decade collecting, especially someone that you have never messaged before.
I’d like to add: I know I don’t own any of Taylor’s demos. None of the live recordings, remixes, unreleased, demos, or anything of the sort are truly mine. But that does not mean I didn’t put effort into getting them. So much of my library is ripped from YouTube way back in 2013 with a YouTube to MP3 converter, then dragging it into iTunes and editing the metadata track by track, then photoshopping and editing pictures so I can make album covers for them. Some of my audios are from Vimeo (does that even still exist?) and converted into MP3s. Some of my library is downloaded from Tumblr also over ten years ago from blogs that have since been deactivated. Some of my library comes from sketchy MediaFire files that I had to go through one of those weird shortened links that redirect you to the actual download page. I’ve used so many ad blockers and malware protection programs over the years to get so much into my library. And it’s not even easy to share either. Obviously it’s copyrighted, and although I have a personal Google Drive I keep a ton of backups in for half of the files on my computer, I don’t want that to get taken down if I share music through it, and it would. Even websites like Mega eventually (slowly) catches on and deletes your files and gives you a warning. A few of those and your account is gone.
I’m not trying to be rude, but I’m not rewarding awful behavior. I’ve done enough of that and have learned my lesson. I hope these kinds of people can learn, too. I truthfully think these kinds of people should spend a year or so doing it themselves: scouring the internet for carefully guarded files, having to go through the trial and error of this sort of hobby, having to go through the whole ‘malware or audio file��� game, possibly having people say they want to be friends with you just for them to leave once you send what you’ve collected. My point is that it’s not effortless. You do not google ‘Taylor Swift unreleased download’ and get everything I or other collectors have. And you do not get anything from said collectors by stalking their account to see if they’re active and telling them to ‘pick up the pace’ when they don’t send it in the time you allocated for them without their agreement. Just be respectful to those you want something from. Don’t use people. Be compassionate and considerate. Don’t be like… this.
#taylor swift#unreleased#taylor swift rares#taylor swift unreleased#rare taylor swift#unreleased taylor swift#swiftie#trade#demo#swifties#text#text post#non taylor#important
12 notes
·
View notes
Text
TS4 Malware via .TS4SCRIPT mods
(Copied from my Patreon)
Hi everyone, I figured I would make a post about this just in case anyone who follows me has not yet been made aware of the malware issues happening currently in the Sims 4 modding community.
Several days ago malware was discovered within a few mods that would silently steal info from your computer such as passwords and private information. This malware was then found to be in many other mods, as early as August 2023. It appears to mostly affect script (.ts4SCRIPT files), but be wary of .package files as well. Please read more about this on this reddit post and consider downloading TwistedMexi's ModGuard malware protection mod: https://www.patreon.com/posts/98126153 to keep yourself safe. There is also this website with information about the malware, known affected mods, how to check if you have been infected by it, and what to do if you have: https://scarletsrealm.com/malware-mod-information/
This malware affected user accounts which appear to have been hacked, or fake accounts made to mimic real users primarily. The list of known mods that were affected are:
Cult Mod by _PimpMySims
Social Events – Unlimited Time by MySims4
Weather and Forecast Cheat Menu by MSQSims
Seasons Cheats Menu by MSQSims
Motherlode Menu by MSQSims
Mood Cheat Menu by MSQSims
Mouth Preset N16
If you have downloaded these mods, please follow the advice in the reddit thread/website linked above. Please stay safe and vigilant when installing mods if you are continuing to do so currently.
#sims 4#the sims 4#sims 4 custom content#the sims#ts4#sims#the sims cc#script mods#malware#sims 4 malware#sims 4 virus#virus#hacking
27 notes
·
View notes
Text
Why Irish Businesses Should Always Maintain Their Websites
Since so much is pulled up online, your website may be the first interaction a customer has with you. Having a good-looking website can separate businesses in Limerick, Galway and even Dublin from rivals, allowing them to attract new customers.
We have assisted many Irish businesses and what we notice most is that keeping your website up to date helps maintain your online reputation and promotes growth in the future.
In the following sections, we will focus on why maintaining your website is important for your business.
1. First Impressions Matter
You would make sure the area near your store was tidy, fresh and not damaged. What is the point of doing it again in the cyber world?
Most of the time, a potential customer’s first contact with you happens when they visit your site. If the site takes a long time to open, links do not work, the information is old or the appearance is outdated, it gives a feeling that nobody cares. This scares off visitors and weakens your reputation.
If you regularly look after your website, it will continue to be fresh and serve its purpose, making people trust it and enjoy it.
2. Security Should Always Be Considered from the Beginning
More organizations are under cyber attacks and even small businesses are being targeted. Almost all the time, WordPress, Joomla, Magento and other content management systems make security updates to guard against new risks.
If you do not maintaining of your site:
Your customer details could be taken by fraudsters.
A search engine may blacklist your website.
Our maintenance services at Flo Web Design include regular security audits, updates for plugins and malware scans to give you a worry-free website and protect your visitors.
3. SEO depends on regular website maintenance
Google and other search engines prefer websites that get updated and maintained frequently. If a site is slow, features old information or isn’t accessible on mobile, it will be given a lower ranking by search engines.
Keeping your website updated makes it better:
How fast web pages are loading
Mobile responsiveness
Metadata and organized data
Dealing with broken links
Content freshness
As a result, your website becomes more visible to search engines, it gains higher positions and gets more traffic.
4. Improve the way users interact with the application
Website users today want sites that are easy to use and quick to respond. Anything that makes the site slow such as images that don’t load or ancient navigation, will lead them to leave.
Maintaining the website often helps keep:
All the links and pages are accessible.
Pictures and videos are displayed without any errors.
Checkout, buttons and forms work efficiently.
Updates are made to give the program a new look.
A seamless experience for users will make them more likely to stay and possibly become paying customers.
5. Making Sure Your Content is Up-to-Date
Information about companies can vary—such as their prices, services, working hours, contact details, special deals, employees and similar elements. If the changes aren’t reflected on your website, it confuses your customers and decreases trust.
If your site is updated, you demonstrate that your business is lively and interested in its customers.
Our team at Flo Web Design ensures that Irish companies update their content, update their blogs and remove any old materials from their website.
6. This involves backing up and recovering your data
Website crashes can happen for reasons such as plugin conflicts, issues with the server, hacking or making a mistake while deleting something important. If you don’t back up your files often, you could lose everything you have worked on for a long time.
With our maintenance package, your site is backed up automatically, making it easy and quick to restore it and continue your business.
7. The standards of both Compliance and Performance
All Irish businesses should follow the rules set out by GDPR. Failing to keep your contact forms and cookie policies current could result in serious fines and legal issues.
Maintenance done regularly will help your website:
Follows the necessary regulations for data protection.
The website is fast to load on every type of device.
Still works properly after OS and browser updates.
It’s more important to establish trust and eliminate risks than just fulfilling the requirements.
8. Making Your Website Resistant to Future Changes
Technology keeps advancing all the time. Plugins become old, browsers are updated and people’s needs change.
When you maintain your website regularly, it grows with your business. If you add new features, boost e-commerce or update the design, frequent upgrades help you not have to begin again.
How a Retailer in Ireland Benefited from Website Maintenance
A shop in Cork contacted us for help because their site was down for two days. Since the developers failed to update the site’s plugins or security measures for more than a year, the site was breached.
We recovered the site from our backup, removed the malware, updated the plugins and applied the best security measures. By opting for a monthly service package, they haven’t experienced any downtime and now get 35% more online inquiries due to faster performance.
Take action before a problem arises. Keeping your computer well-maintained is like having insurance.
So, What Services Are Part of Website Maintenance with Flo Web Design?
Our services include packages that are customized for businesses in Ireland.
Keeping an eye on security
Ensuring a fast website
Links on your website are checked for breaks
Backup & recovery
Updates on GDPR compliance
Updates to the content (upon request)
We’ll take care of your website’s back end, helping it run as efficiently as you run your business.
Conclusion
Just as you maintain a car regularly, you should keep your website up to date. This rule also applies to the internet. A secure, effective and successful website depends on regular upkeep.
Your website’s updates, security and page issues are all taken care of by Flo Web Design. We handle all the necessary jobs, allowing you to focus on your business.
Want to Maintain Your Site in the Best Way Possible?
We will make sure your website is kept safe, fast and performing at its peak each and every month.
2 notes
·
View notes
Text
Crypto Scam Recovery: How to Spot, Report, and Recover from Online Frauds
The world of cryptocurrency is booming, offering investors a decentralized and promising way to grow their wealth. But with that growth comes an increasing number of scams targeting unsuspecting users. From fake investment platforms to phishing attacks, online fraud is a real threat. The good news? Victims can take action. In this post, we’ll guide you on how to spot crypto scams, report them, and increase your chances of recovery.

How to Spot a Crypto Scam
Knowing how to recognize the signs of a scam can save you from massive losses. Below are common types of cryptocurrency scams and the red flags to watch out for.
1. Fake Investment Platforms
These websites or apps promise guaranteed returns on crypto investments. They often look professional and mimic real companies, but they operate purely to steal your funds.
Red Flags:
Promises of high, risk-free returns
Urgency to deposit funds quickly
No verifiable company background
2. Phishing Attacks
Scammers send emails, messages, or pop-ups that look like they’re from trusted platforms. These messages trick users into giving away private keys or login credentials.
Red Flags:
Misspelled URLs or suspicious email addresses
Requests for sensitive information
Offers or warnings that seem too good or too urgent
3. Pump and Dump Schemes
Fraudsters hype up a worthless coin to drive demand and inflate prices. Once the price peaks, they dump their holdings, causing massive losses for late investors.
Red Flags:
Unusual hype in online forums or social media
Sudden spike in price without real news or updates
Unverified claims about partnerships or technology
How to Report a Crypto Scam
If you’ve been scammed, it’s essential to report the incident immediately. Doing so not only helps protect others but also increases your chance of recovery.
1. Report to Local Authorities
File a police report or contact your country's cybercrime unit. Include all details—transaction history, wallet addresses, emails, and screenshots.
2. Notify the Exchange
If the scammer used a known exchange to receive your funds, contact that platform’s support team. Many exchanges can freeze the funds if reported in time.
3. Report to Online Watchdogs
Organizations like the Internet Crime Complaint Center (IC3), FTC, or Action Fraud (UK) collect reports to investigate and track online scams.
4. Alert Blockchain Forensics Firms
Specialized companies like Chainalysis or CipherTrace can trace stolen crypto on the blockchain. In many cases, they collaborate with law enforcement and legal teams to initiate recovery.
How to Recover from a Crypto Scam
While recovering lost crypto isn’t easy, it’s not impossible. Here’s a structured plan from crypto recovery experts:
1. Secure All Accounts
Change passwords and enable two-factor authentication on your wallets, exchanges, and email. Run a malware scan on your devices to ensure no backdoors remain.
2. Collect Evidence
Document every aspect of the fraud—wallet addresses, transaction IDs, email conversations, social media links, and screenshots. The more information you gather, the better.
3. Consult a Crypto Recovery Expert
Work with a reputable crypto recovery agency or blockchain forensic specialist. These professionals use tracking software to trace your funds across wallet addresses and exchanges.
Note: Be cautious—scammers also pose as recovery agents. Only trust firms with proven results, legal backing, and strong online presence.
Prevention Tips to Avoid Future Crypto Frauds
Use hardware wallets for secure storage of your crypto assets.
Double-check URLs before entering credentials.
Avoid platforms or individuals promising “guaranteed returns.”
Do your research before investing—verify reviews, company registration, and team transparency.
Final Thoughts
Crypto scams are becoming more sophisticated, but with awareness and the right actions, you can fight back. Spotting red flags early, reporting to the proper authorities, and seeking expert help are key steps toward recovery.
If you or someone you know has fallen victim to a crypto scam recovery, don’t delay. Act fast, gather your data, and reach out to professionals who can help you trace and possibly recover your stolen funds.
3 notes
·
View notes
Text
The Ultimate Guide to Downloading Erome Videos

Erome is a popular platform for sharing and viewing user-generated adult content. However, it does not provide a built-in download option. If you want to save videos for offline viewing, you need an Erome downloader. In this guide, we will explore the best ways to download Erome videos safely and efficiently.
Why Use an Erome Downloader?
Many users want to download Erome videos for personal use. Here are a few reasons why:
Offline Viewing – Watch videos anytime without an internet connection.
Backup Content – Save your favorite videos before they get removed.
Better Streaming – Avoid buffering issues by watching videos offline.
Sharing Convenience – Easily transfer videos between devices.
Archival Purpose – Store important content for future reference.
Is Downloading Erome Videos Legal?
Before downloading any content, ensure that you have permission from the original uploader. Downloading copyrighted material without consent can violate terms of service and legal guidelines. Always respect the rights of content creators and adhere to copyright laws in your region.
Best Methods to Download Erome Videos
Here are the top methods to download videos from Erome.com:
1. Using an Online Erome Downloader
Several online tools allow users to paste a video URL and download it. These services are easy to use but may contain ads or require sign-ups.
Steps:
Visit a trusted online Erome downloader website.
Copy the Erome video URL.
Paste the URL into the downloader.
Click “Download” and choose the desired format.
Save the video to your device.
2. Using Browser Extensions
Browser extensions can help download videos directly from Erome. Some popular options include:
Video DownloadHelper (Firefox & Chrome)
Flash Video Downloader
SaveFrom.net Helper
Steps:
Install the extension on your browser.
Open the Erome video.
Click the extension icon to start the download.
Choose the format and save the file.
3. Using Developer Tools (Manual Method)
If you prefer a manual approach, you can use browser developer tools.
Steps:
Open the Erome video page.
Press F12 or right-click and select Inspect.
Go to the Network tab and filter for Media.
Locate the video file URL and copy it.
Open the link in a new tab and save the video.
4. Using a Dedicated Software
There are software programs designed for downloading videos, such as:
JDownloader
4K Video Downloader
YTD Video Downloader
These tools offer advanced features, including batch downloads, high-quality formats, and faster speeds.
How to Stay Safe When Using an Erome Downloader
Downloading videos from third-party tools comes with risks. Follow these safety tips:
Avoid Malware – Use only trusted websites and software.
Use a VPN – Protect your identity and browsing data.
Check Permissions – Ensure you have permission to download videos.
Update Antivirus Software – Protect against potential security threats.
Be Wary of Phishing Scams – Avoid suspicious websites asking for personal information.
Conclusion
An Erome downloader makes it easy to save videos for offline viewing. Whether you use an online tool, browser extension, or software, always prioritize safety and legal considerations. Choose the best method that suits your needs and enjoy seamless downloads. By following best practices, you can ensure a secure and hassle-free downloading experience.
5 notes
·
View notes
Text
Top WordPress Plugins to Supercharge Your Website in 2024

Building and maintaining a WordPress site is both exciting and challenging. While the platform provides a robust foundation, the true power of WordPress lies in its plugins. From enhancing site functionality to improving user experience, WordPress plugins are indispensable tools for developers, businesses, and bloggers alike. In this blog, we’ll explore the best WordPress plugins that can transform your website into a highly functional, user-friendly, and SEO-optimized powerhouse.
What Are WordPress Plugins?
WordPress plugins are software add-ons designed to extend the functionality of your WordPress site. Whether you need to improve site speed, enhance SEO, secure your website, or add unique design features, there’s likely a plugin for that. Plugins allow both beginners and advanced users to customize their sites without coding expertise.
With over 60,000 plugins available on the WordPress Plugin Directory alone, the options can feel overwhelming. Choosing the right plugins for your website’s goals is critical for success. Below, we’ve rounded up some of the most essential WordPress plugins to consider.
Must-Have WordPress Plugins for Every Website
1. Yoast SEO
SEO is crucial for driving organic traffic to your site, and Yoast SEO is one of the best tools for optimizing your content. This plugin provides on-page optimization tips, readability analysis, and technical SEO tools to help your site rank higher on search engines.
2. Elementor
Looking to build a visually stunning website without hiring a designer? Elementor is a drag-and-drop page builder that makes designing websites easy. Its intuitive interface and vast array of widgets allow you to create professional-looking pages in minutes.
3. WPForms
For websites that rely on user interaction, a contact form is a must-have feature. WPForms allows you to create customizable, mobile-responsive forms effortlessly. Whether it’s contact forms, surveys, or payment forms, this plugin has you covered.
4. WooCommerce
If you’re running an online store, WooCommerce is the go-to plugin. It transforms your WordPress site into a fully functional e-commerce platform, complete with features for product listings, payment gateways, and inventory management.
5. Akismet Anti-Spam
Spam comments can clutter your website and ruin user experience. Akismet Anti-Spam automatically filters out spam comments, keeping your site clean and professional.
6. Jetpack
Created by Automattic, the team behind WordPress, Jetpack is a multipurpose plugin offering features like performance optimization, security, site analytics, and social media integration.
7. Rank Math
Another excellent SEO plugin, Rank Math provides advanced features like schema integration, keyword tracking, and detailed analytics. It’s an excellent alternative to Yoast SEO for more advanced users.
8. UpdraftPlus
Backup and restoration are critical for any website. UpdraftPlus allows you to schedule automatic backups and store them securely on cloud services like Google Drive or Dropbox.
9. Smush
Site speed plays a major role in user experience and search engine rankings. Smush compresses images without compromising quality, helping your site load faster.
10. MonsterInsights
Understanding how visitors interact with your site is essential. MonsterInsights integrates Google Analytics directly into your WordPress dashboard, offering real-time insights into traffic, user behavior, and more.
11. W3 Total Cache
Slow-loading websites lose visitors and revenue. W3 Total Cache improves website performance by caching static files and optimizing server resources.
12. Sucuri Security
Cybersecurity is non-negotiable in today’s digital landscape. Sucuri Security offers malware scanning, firewall protection, and blacklist monitoring to keep your site secure.
13. Social Snap
Boost social media engagement with Social Snap, a powerful social sharing plugin. It offers customizable sharing buttons and in-depth analytics to track your social media performance.
14. Litespeed Cache
For websites hosted on LiteSpeed servers, LiteSpeed Cache is a high-performance optimization plugin that enhances speed and reduces server load.
15. TablePress
If your site needs to display complex data, TablePress is a lifesaver. It lets you create and manage tables without requiring any coding knowledge.
Why Use WordPress Plugins?
Enhanced Functionality: WordPress plugins extend the capabilities of your site, making it easier to achieve your goals.
Ease of Use: Many plugins are beginner-friendly and require no technical expertise.
Scalability: Whether you’re running a blog, an e-commerce store, or a portfolio, plugins grow with your needs.
Cost-Effective: Most plugins offer free versions with premium features, making them accessible for all budgets.
Tips for Choosing the Right WordPress Plugins
Identify Your Needs: Start by determining what features your site requires.
Check Reviews and Ratings: Plugins with high ratings and positive reviews are generally more reliable.
Update Frequency: Look for plugins that are updated regularly to ensure compatibility with the latest WordPress version.
Avoid Overloading: Too many plugins can slow down your site. Stick to essential ones.
Final Thoughts
WordPress plugins are the backbone of a successful website. By selecting the right ones, you can enhance your site’s functionality, user experience, and performance. Whether you’re aiming to boost your SEO, secure your site, or create stunning designs, there’s a plugin tailored for your needs.
Experiment with the plugins mentioned above and watch your WordPress site thrive. Remember to regularly review your plugin list and update them to ensure optimal performance.
4 notes
·
View notes
Text
Why Websites Fail After Launch and How to Prevent It

Common Reasons Websites Fail After Launch
1. Poor User Experience (UX)
Websites that are difficult to navigate, slow to load, or visually cluttered often drive users away. A seamless and intuitive user experience is essential to retain visitors and reduce bounce rates.
2. Lack of Mobile Optimization
With mobile devices dominating web traffic, failing to create a responsive design can result in missed opportunities. A mobile-friendly website is crucial for reaching and engaging with a wider audience.
3. Weak SEO Strategies
Without proper search engine optimization, even the most visually appealing website will struggle to attract organic traffic. SEO plays a vital role in improving your website’s visibility and ranking on search engines.
4. Inconsistent Content Updates
Static or outdated content can hurt your credibility and discourage repeat visits. Engaging and regularly updated content is key to building trust and maintaining relevance.
5. Ineffective Marketing
Launching a website without a solid digital marketing plan often results in low traffic and poor visibility. Without strategic efforts like social media promotion, PPC campaigns, and email marketing, your site might go unnoticed.
6. Security Flaws
Websites that aren’t secure are vulnerable to cyberattacks, which can lead to data breaches and loss of trust. Security issues can damage your reputation and affect customer loyalty.
How to Prevent Website Failures
1. Deliver Exceptional User Experience
Focus on intuitive navigation, fast load times, and appealing visuals.
Regularly test and improve usability to meet user expectations.
Implement features like live chat and easy search options for better engagement.
2. Ensure Mobile Optimization
Develop responsive websites that adapt to all devices, ensuring consistent performance.
Use tools to test mobile usability and identify any potential issues.
3. Implement Comprehensive SEO
Conduct keyword research and integrate terms like “best website development company in Jaipur” to boost visibility.
Optimize meta tags, headers, and content for search engines.
Focus on link-building and technical SEO for better rankings.
4. Keep Content Fresh and Relevant
Regularly update blogs, news sections, or product pages with new information.
Use analytics to understand what content resonates with your audience.
5. Plan and Execute Digital Marketing
Promote your website through strategic social media campaigns.
Use email marketing to nurture leads and retain existing customers.
Leverage PPC ads to drive immediate traffic and conversions.
6. Prioritize Website Security
Use SSL certificates and HTTPS protocols for secure connections.
Regularly update software, plugins, and themes to prevent vulnerabilities.
Employ firewalls and advanced malware protection.
Why Choose Webpino Software?
At Webpino Software, we take pride in being the best website development company in Jaipur, offering solutions that ensure your website remains a powerful tool for your business even after its launch. Here’s why businesses trust us:
Custom Web Solutions: We tailor our services to meet your unique business needs.
Mobile-Friendly Designs: We prioritize responsive websites that perform seamlessly across all devices.
SEO Expertise: Our team implements robust SEO strategies to help your website rank higher and attract more traffic.
Proactive Maintenance: We monitor and maintain your website to keep it updated, secure, and performing at its best.
Comprehensive Services: From design to marketing, we provide end-to-end support to help your business succeed.
Partner with the Best Website Development Company in Jaipur
Webpino Software is dedicated to ensuring your website not only launches successfully but also achieves long-term growth. As the best website development company in Jaipur, we offer cutting-edge solutions that address all post-launch challenges, from optimizing user experience to ensuring top-notch security.
Whether you’re launching a new website or struggling with post-launch issues, Webpino Software is here to help. Our team of experts is committed to your success, offering tailored strategies to elevate your online presence.
Contact us today to ensure your website thrives in the competitive digital landscape!
#website development#web design#wordpress development#website design#web developers#digital marketing#seo#website#seo friendlly website#business website solutions#custom website design#website optimization#web hosting#wordpress#website design in jaipur#best website development company in jaipur
2 notes
·
View notes
Text
Petalhost: The Best Magento Hosting Provider in India
When it comes to hosting your Magento-based ecommerce website, you need a hosting provider that ensures speed, reliability, and scalability. Petalhost emerges as the most trusted Magento Hosting Provider in India, offering cutting-edge hosting solutions designed specifically for Magento-powered online stores.
Why Choose Petalhost for Magento Hosting?
Magento is a robust ecommerce platform that demands high-performance hosting to deliver a seamless shopping experience. Petalhost understands these unique requirements and provides tailored hosting solutions that guarantee optimal performance and security for your Magento website.
1. High-Speed Servers for Lightning-Fast Performance
Slow-loading websites can drive customers away, but with Petalhost’s high-speed SSD-powered servers, your Magento store will load in the blink of an eye. This not only enhances user experience but also improves search engine rankings, ensuring more visibility for your online store.
2. 99.9% Uptime Guarantee
Downtime means lost sales and damaged customer trust. Petalhost guarantees 99.9% uptime, ensuring your Magento store remains accessible around the clock. Their state-of-the-art data centers are equipped with the latest technology to ensure uninterrupted service.
3. Robust Security Features
Ecommerce websites handle sensitive customer data, making security a top priority. Petalhost provides advanced security measures such as firewalls, DDoS protection, malware scanning, and free SSL certificates to safeguard your Magento store and protect customer information.
4. Optimized for Magento
Petalhost’s servers are specifically optimized for Magento, providing pre-configured setups that reduce the need for manual adjustments. This ensures your website runs smoothly and efficiently, regardless of traffic spikes or complex integrations.
5. Scalable Hosting Plans
As your business grows, so do your hosting requirements. Petalhost offers scalable hosting plans that allow you to upgrade your resources seamlessly without any downtime. Whether you’re running a small store or managing a large ecommerce enterprise, Petalhost has the perfect hosting solution for you.
6. 24/7 Expert Support
Petalhost’s team of Magento hosting experts is available 24/7 to assist you with any issues or queries. From initial setup to ongoing maintenance, their friendly and knowledgeable support team ensures you’re never alone.
Key Features of Petalhost’s Magento Hosting Plans
SSD Storage: High-speed solid-state drives for faster data retrieval.
Free SSL Certificate: Secure your store and build customer trust.
Daily Backups: Keep your data safe with automated daily backups.
One-Click Installation: Quickly set up your Magento store with an easy installation process.
Global Data Centers: Choose from multiple data centers for optimal performance and reduced latency.
Developer-Friendly Tools: Access SSH, Git, and other developer tools for seamless store management.
Affordable Pricing for Every Budget
Petalhost believes in offering premium Magento hosting solutions at affordable prices. Their hosting plans are designed to suit businesses of all sizes, from startups to established enterprises. With transparent pricing and no hidden fees, you get the best value for your money.
Why Magento Hosting Matters
Magento is a feature-rich platform that enables businesses to create highly customizable and scalable online stores. However, its powerful features also demand a hosting environment that can handle its resource-intensive nature. A reliable Magento hosting provider like Petalhost ensures that your website runs efficiently, providing a smooth shopping experience for your customers and boosting your online sales.
How to Get Started with Petalhost
Getting started with Petalhost’s Magento hosting is quick and hassle-free. Simply visit their website, choose a hosting plan that suits your needs, and follow the easy signup process. Their team will guide you through the setup and migration process to ensure a smooth transition.
Conclusion
If you’re looking for a reliable and affordable Magento Hosting Provider in India, Petalhost is the name you can trust. With high-speed servers, robust security, and dedicated support, Petalhost provides everything you need to run a successful Magento-based ecommerce store. Don’t let subpar hosting hold your business back. Choose Petalhost and take your online store to new heights today!
2 notes
·
View notes
Text
What Is Linux Web Hosting? A Beginner's Guide
In the ever-evolving digital landscape, the choice of web hosting can significantly impact your online presence. One of the most popular options available is Linux web hosting. But what exactly does it entail, and why is it so widely preferred? This beginner’s guide aims to demystify Linux web hosting, its features, benefits, and how it stands against other hosting types.
Introduction to Web Hosting
Web hosting is a fundamental service that enables individuals and organisations to make their websites accessible on the internet. When you create a website, it consists of numerous files, such as HTML, images, and databases, which need to be stored on a server. A web host provides the server space and connectivity required for these files to be accessed by users online.
There are several types of web hosting, each designed to cater to different needs and budgets. Shared hosting is a cost-effective option where multiple websites share the same server resources. Virtual Private Server (VPS) hosting offers a middle ground, providing dedicated portions of a server for greater performance and control. Dedicated hosting provides an entire server exclusively for one website, ensuring maximum performance but at a higher cost. Cloud hosting uses multiple servers to balance the load and maximise uptime, offering a scalable solution for growing websites.
Web hosting services also include various features to enhance the performance and security of your website. These can range from basic offerings like email accounts and website builders to more advanced features like SSL certificates, automated backups, and DDoS protection. The choice of web hosting can significantly influence your website’s speed, security, and reliability, making it crucial to choose a solution that aligns with your specific requirements.
Understanding the different types of web hosting and the features they offer can help you make an informed decision that suits your needs. Whether you are running a personal blog, a small business website, or a large e-commerce platform, selecting the right web hosting service is a critical step in establishing a successful online presence.
What Is Linux Web Hosting?
Linux web hosting is a type of web hosting service that utilises the Linux operating system to manage and serve websites. Renowned for its open-source nature, Linux provides a stable and secure platform that supports a wide array of programming languages and databases, making it a favoured choice amongst developers and businesses. This hosting environment typically includes support for popular technologies such as Apache web servers, MySQL databases, and PHP scripting, which are integral to modern website development.
One of the distinguishing features of Linux web hosting is its cost-effectiveness. As an open-source system, Linux eliminates the need for costly licensing fees associated with proprietary software, thereby reducing overall hosting expenses. This makes it an attractive option for individuals and organisations operating on a budget.
Moreover, Linux is celebrated for its robust performance and high stability. Websites hosted on Linux servers experience less downtime and faster loading times, which are critical factors for maintaining user engagement and search engine rankings. The operating system’s extensive community of developers continuously works on updates and improvements, ensuring that Linux remains a cutting-edge choice for web hosting.
Linux web hosting also offers considerable flexibility and customisation options. Users have the freedom to configure their hosting environment to meet specific needs, whether they are running simple static websites or complex dynamic applications. This versatility extends to compatibility with various content management systems (CMS) like WordPress, Joomla, and Drupal, which often perform optimally on Linux servers.
In summary, Linux web hosting provides a reliable, secure, and cost-effective solution that caters to a diverse range of web hosting requirements. Its compatibility with essential web technologies and its inherent flexibility make it a preferred choice for many web developers and site owners.
Key Benefits of Linux Web Hosting
Linux web hosting offers several compelling advantages that contribute to its widespread adoption. One of its primary benefits is cost-effectiveness. The open-source nature of Linux eliminates the need for expensive licensing fees, allowing users to allocate their resources more efficiently. This makes it an ideal choice for individuals and organisations with budget constraints. Additionally, Linux is celebrated for its high stability and robust performance. Websites hosted on Linux servers often experience minimal downtime and faster loading speeds, which are essential for maintaining user engagement and achieving favourable search engine rankings.
Another significant benefit is the extensive community support that comes with Linux. The active community of developers and enthusiasts continuously works on updates, patches, and security enhancements, ensuring that Linux remains a secure and reliable platform for web hosting. This ongoing development also means that any issues or vulnerabilities are promptly addressed, offering peace of mind for website owners.
Flexibility is another key advantage of Linux web hosting. The operating system supports a wide range of programming languages, including PHP, Python, and Ruby, making it suitable for various types of web applications. Additionally, Linux servers are highly customisable, allowing users to configure their environment to meet specific needs, whether they are running simple static sites or complex dynamic applications.
Moreover, Linux web hosting is highly compatible with popular content management systems (CMS) like WordPress, Joomla, and Drupal. This compatibility ensures that users can easily deploy and manage their websites using these platforms, benefiting from their extensive plugin and theme ecosystems.
Lastly, Linux's superior security features are worth noting. The operating system is inherently secure and offers various built-in security measures. When combined with best practices such as regular updates and strong passwords, Linux web hosting provides a highly secure environment for any website.
Understanding Linux Distributions in Web Hosting
Linux comes in a variety of distributions, each tailored to meet specific needs and preferences. Among the most popular for web hosting are Ubuntu, CentOS, and Debian. Ubuntu is celebrated for its ease of use and extensive community support, making it a great choice for those new to Linux. CentOS, a favourite in enterprise environments, offers impressive stability and long-term support, which ensures a dependable hosting experience. Debian stands out with its robust package management system and commitment to open-source principles, providing a reliable and secure foundation.
Each distribution brings its own strengths to the table. For example, Ubuntu’s frequent updates ensure access to the latest features and security patches, while CentOS’s extended support cycles make it a solid choice for those requiring a stable, long-term hosting environment. Debian’s extensive repository of packages and minimalistic approach offers flexibility and customisation, catering to the needs of experienced users.
Selecting the right Linux distribution largely depends on your specific requirements and technical expertise. If you prioritise user-friendliness and a wealth of resources for troubleshooting, Ubuntu might be the ideal pick. On the other hand, if you need a rock-solid, stable platform for an enterprise-level application, CentOS could be more appropriate. For those seeking maximum control and a commitment to open-source principles, Debian is a compelling option.
Ultimately, understanding the nuances of these distributions will enable you to choose a Linux environment that aligns with your web hosting needs, ensuring optimal performance and reliability.
Linux Hosting vs Windows Hosting: A Comparative Analysis
When evaluating Linux hosting against Windows hosting, several critical factors come into play. Cost is a significant differentiator; Linux hosting is generally more affordable due to its open-source nature, which eliminates the need for expensive licensing fees. In contrast, Windows hosting often incurs additional costs related to proprietary software licenses.
Compatibility is another important aspect to consider. Linux hosting is renowned for its compatibility with a broad array of open-source software and applications, including popular content management systems like WordPress, Joomla, and Magento. These platforms typically perform better on Linux servers due to optimised server configurations. On the other hand, Windows hosting is the go-to option for websites that rely on Microsoft-specific technologies such as ASP.NET, MSSQL, and other .NET frameworks.
Performance and stability are also crucial elements in this comparison. Linux hosting often provides superior uptime and faster loading speeds due to the lightweight nature of the Linux operating system. The robust performance of Linux servers is further enhanced by the active community that continuously works on optimisations and security patches. Windows hosting, while also reliable, can sometimes be more resource-intensive, potentially affecting performance.
Customisation and control levels differ significantly between the two. Linux offers greater flexibility and customisation options, allowing users to tweak server settings and configurations extensively. This level of control is particularly beneficial for developers who need a tailored hosting environment. Conversely, Windows hosting is typically easier to manage for those familiar with the Windows operating system but may offer less flexibility in terms of customisation.
Security measures also vary between Linux and Windows hosting. Linux is often praised for its strong security features, which are bolstered by a large community dedicated to promptly addressing vulnerabilities. While Windows hosting is secure, it may require more frequent updates and maintenance to ensure the same level of protection.
Common Use Cases for Linux Web Hosting
Linux web hosting is versatile and caters to a broad range of applications, making it a popular choice across various sectors. One of the most common use cases is hosting blogs and personal websites, particularly those built on platforms like WordPress. The open-source nature of Linux and its compatibility with PHP make it an ideal environment for WordPress, which powers a significant portion of the web.
E-commerce websites also benefit greatly from Linux web hosting. Solutions like Magento, PrestaShop, and OpenCart often perform better on Linux servers due to their need for a robust, secure, and scalable hosting environment. The flexibility to configure server settings allows online store owners to optimise performance and ensure a smooth shopping experience for their customers.
Content Management Systems (CMS) such as Joomla and Drupal are another prime use case. These systems require reliable and flexible hosting solutions to manage complex websites with large amounts of content. Linux's support for various databases and scripting languages ensures seamless integration and optimal performance for CMS-based sites.
Developers frequently turn to Linux web hosting for custom web applications. The operating system supports a variety of programming languages, including Python, Ruby, and Perl, making it suitable for a wide array of development projects. Its command-line interface and extensive package repositories allow developers to install and manage software efficiently.
Additionally, Linux web hosting is commonly used for educational and non-profit websites. The low cost and high reliability make it a practical choice for schools, universities, and charitable organisations that need a dependable online presence without breaking the bank.
Setting Up a Linux Web Hosting Environment
Setting up a Linux web hosting environment can be straightforward with the right approach. Begin by selecting a reputable hosting provider that offers Linux-based plans. After signing up, you'll typically be granted access to a control panel, such as cPanel or Plesk, which simplifies the management of your hosting environment. Through the control panel, you can manage files, databases, email accounts, and more.
Next, if you're using a content management system (CMS) like WordPress, Joomla, or Drupal, you can often find one-click installation options within the control panel. This feature makes it easy to get your website up and running quickly. Additionally, ensure that you configure your domain name to point to your new hosting server, which usually involves updating your domain's DNS settings.
For those who prefer more control or are comfortable using the command line, you can manually set up your web server using SSH access. This method allows you to install and configure web server software like Apache or Nginx, as well as databases such as MySQL or PostgreSQL.
Regardless of the setup method you choose, it's crucial to secure your server from the outset. This includes setting up a firewall, enabling SSH key authentication for secure access, and regularly updating all software to protect against vulnerabilities. Regularly monitoring your server's performance and security logs can help you stay ahead of potential issues, ensuring a stable and secure hosting environment for your website.
Security Best Practices for Linux Web Hosting
Securing your Linux web hosting environment is paramount to safeguarding your website against potential threats. Begin by ensuring your server software and all installed applications are up to date. Regular updates often include patches for security vulnerabilities, making this a critical step. Utilise strong, unique passwords for all user accounts, and consider employing SSH key authentication for added security when accessing your server remotely.
Setting up a firewall is another essential measure. Tools like iptables or firewalld can help you configure firewall rules to control incoming and outgoing traffic, thereby reducing the risk of unauthorised access. Implementing intrusion detection systems (IDS), such as Fail2Ban, can provide an additional layer of security by monitoring and blocking suspicious activities.
Consider deploying an SSL certificate to encrypt data transmitted between your server and users' browsers. This not only enhances security but also boosts user trust and can improve your search engine rankings. Additionally, limit the use of root privileges; create separate user accounts with the necessary permissions to minimise potential damage in the event of a breach.
Regularly backup your data to mitigate the impact of data loss due to hardware failure, cyber-attacks, or human error. Automated backup solutions can simplify this process, ensuring your data is consistently protected. Monitoring your server's logs can also be invaluable for identifying unusual activity early. Tools like Logwatch or the ELK Stack can assist in log management and analysis, enabling you to take swift action if anomalies are detected.
Common Challenges and How to Overcome Them
Setting up and maintaining a Linux web hosting environment can present various challenges, especially for those new to the platform. One frequent issue is navigating the command line, which can be daunting for beginners. Engaging with online tutorials, forums, and communities like Stack Overflow can be invaluable for learning the basics and troubleshooting problems. Another common challenge is software incompatibility. Ensuring your web applications are compatible with the Linux distribution you choose is crucial; consulting documentation and support resources can help mitigate these issues.
Security configuration can also be a complex task. Implementing best practices such as setting up firewalls, regular updates, and using strong authentication methods requires a good understanding of Linux security principles. Managed hosting services can offer a solution here by handling these technical aspects for you, allowing you to focus on your website content.
Resource management is another area where users might struggle. Monitoring server performance and managing resources effectively ensures your website runs smoothly. Utilising monitoring tools and performance optimisation techniques can help you stay ahead of potential issues. Lastly, when it comes to server backups, regular, automated solutions are essential to prevent data loss and minimise downtime. Being proactive in addressing these challenges will ensure a more seamless and secure Linux web hosting experience.
Popular Control Panels for Linux Web Hosting
Control panels are invaluable for simplifying the management of your Linux web hosting environment. Among the most popular are cPanel, Plesk, and Webmin. cPanel is renowned for its intuitive interface and extensive feature set, making it a favourite among users who need a straightforward yet powerful management tool. Plesk offers robust functionality and supports both Linux and Windows servers, providing versatility for those who manage multiple server environments. Webmin stands out as a free, open-source option that allows comprehensive server management through a web interface, catering to those who prefer a customisable and cost-effective solution. Each control panel brings unique strengths, helping to streamline tasks such as file management, database administration, and security configurations.
Choosing the Right Linux Web Hosting Provider
Choosing the right Linux web hosting provider involves several key considerations. Firstly, evaluate the quality of customer support offered. Responsive and knowledgeable support can be invaluable, especially when troubleshooting technical issues or during the initial setup phase. Check if the provider offers 24/7 support and multiple contact methods such as live chat, email, and phone.
Another crucial factor is the security measures in place. Opt for providers that offer robust security features, including regular backups, SSL certificates, firewalls, and DDoS protection. These features help safeguard your website against potential threats and ensure data integrity.
Reliability and uptime guarantees are also vital. Aim for providers that offer at least a 99.9% uptime guarantee, as frequent downtimes can significantly affect your website’s accessibility and user experience. Additionally, look into the provider’s data centre infrastructure and redundancy measures, which can impact overall performance and reliability.
Scalability is another important aspect to consider. As your website grows, you’ll need the flexibility to upgrade your hosting plan seamlessly. Check if the provider offers scalable solutions, such as easy transitions to VPS or dedicated hosting, without causing disruptions to your site.
Lastly, consider the hosting plans and pricing structures available. While cost-effectiveness is a significant benefit of Linux web hosting, ensure the plans align with your specific needs. Compare the features, storage, bandwidth, and other resources included in different plans to find the best value for your money.
Reading customer reviews and seeking recommendations can also provide insights into the provider’s reputation and service quality. By carefully evaluating these factors, you can choose a Linux web hosting provider that meets your requirements and supports your online endeavours effectively.
Conclusion and Final Thoughts
Linux web hosting stands out as an optimal choice for both beginners and seasoned web developers. Its open-source nature provides an affordable, highly customisable, and secure environment, suitable for a diverse range of websites, from personal blogs to large e-commerce platforms. The extensive community support ensures ongoing improvements and prompt resolution of issues, contributing to its reliability and performance. Choosing the right hosting provider is crucial; look for robust security measures, excellent customer support, and scalability to accommodate your website's growth. By leveraging the strengths of Linux web hosting, you can build a resilient and efficient online presence that meets your specific needs and goals.
4 notes
·
View notes
Text
How to Protect Your WordPress Site from Malware or Hackers?
WordPress is used by millions of websites for blogs, businesses, and online stores. However, because it’s so popular, it’s often a target for hackers and malware. If you have a WordPress site, it’s important to take steps to keep it secure. Here’s a simple guide to help you protect your site from hackers and malware.
How to Protect WordPress Site from Malware or Hackers?
Follow this step list given below to protect WordPress site from malware or hackers
1. Always Keep WordPress Updated
WordPress regularly releases updates to fix bugs and improve security. Hackers often look for websites running old versions of WordPress or outdated plugins, so keeping everything updated helps keep them out.
How to Update:
Check for updates in your WordPress dashboard regularly.
Go to the Dashboard > Updates section and install any available updates for WordPress core, themes, or plugins.
By staying updated, you’re less likely to have security holes in your site that hackers can use.
2. Use Strong Passwords and Change Them Often
Hackers can easily guess weak passwords like "123456" or "admin." To keep your site safe, use strong, unique passwords and change them every few months.
Tips for Strong Passwords:
Use a mix of uppercase and lowercase letters, numbers, and symbols.
Don’t use simple information like your name or "admin."
Consider using a password manager to create and store complex passwords securely.
Strong passwords are one of the simplest ways to add security to your website.
3. Limit Login Attempts
Hackers often try to break into websites by guessing the login password over and over. You can protect your site by limiting the number of login attempts a person (or bot) can make.
How to Limit Login Attempts:
Use plugins like Limit Login Attempts Reloaded or WP Limit Login Attempts.
These plugins lock out users after a certain number of failed login attempts.
This makes it much harder for hackers to keep guessing passwords.
4. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds another layer of security. In addition to entering your password, you’ll also need to input a code sent to your phone or email. Even if someone knows your password, they won’t be able to log in without this extra code.
How to Set Up 2FA:
Install a plugin like Google Authenticator or Two-Factor.
Set it up by scanning a QR code and linking your account to an app like Google Authenticator or Authy.
This ensures that only you can access your site, even if someone steals your password.
5. Use a Security Plugin
A security plugin can protect your WordPress site from different types of attacks, like malware or brute force attempts. These plugins act as your site’s security guard, offering tools like firewalls and malware scanning.
Recommended Security Plugins:
Wordfence Security: Includes a firewall and real-time monitoring.
Sucuri Security: Provides malware removal and a website firewall.
iThemes Security: Offers brute force protection, backups, and two-factor authentication.
Using a security plugin adds strong layers of protection against hackers.
Also Read - What Is Domain Status? What does this mean, & Why should I know?
6. Back Up Your Website Regularly
Even with good security, things can sometimes go wrong. That’s why it’s important to back up your site regularly. If your site gets hacked, a backup will let you restore everything quickly without losing important data.
How to Back Up Your Website:
Use backup plugins like UpdraftPlus or BackupBuddy.
Store your backups in safe places like Google Drive, Dropbox, or a remote server.
Schedule backups daily or weekly, depending on how often you update your site.
Regular backups help ensure you won’t lose everything if something goes wrong.
7. Choose a Secure Hosting Provider
Your web hosting service plays an important role in your website’s security. Some hosts offer strong security features that help protect your site. Make sure to choose a hosting provider that values security.
What to Look for in a Hosting Provider:
Regular backups
Malware scanning and removal
Firewalls
SSL certificates
DDoS protection
Popular and secure WordPress hosting services include SiteGround, Bluehost, and WP Engine.
8. Use HTTPS and SSL Certificates
SSL (Secure Socket Layer) encrypts the data between your website and your visitors. This protects sensitive information, like passwords or credit card numbers. Websites with SSL certificates also have a secure URL that starts with "https://."
How to Install an SSL Certificate:
Most hosting providers offer free SSL certificates with Let’s Encrypt.
You can use plugins like Really Simple SSL to set it up quickly.
SSL certificates keep sensitive data safe and make your site more trustworthy.
9. Remove Unused Themes and Plugins
Unused plugins and themes can create security risks, especially if they aren’t updated. Even if they’re deactivated, they can still be a weak point. It’s best to delete any plugins or themes you don’t use.
How to Delete Unused Themes/Plugins:
Go to your Dashboard > Plugins or Appearance > Themes.
Deactivate and delete anything you no longer need.
This reduces the number of places where hackers might try to get in.
10. Monitor Your Site for Suspicious Activity
It’s important to keep an eye on your site for any unusual behavior. This could include sudden spikes in traffic, unknown files appearing on your server, or unauthorized users trying to log in.
How to Monitor Your Site:
Use a security plugin to track things like failed login attempts and changes to important files.
Regularly check your hosting account for unusual activity.
Review your website users to make sure no unauthorized accounts have been added.
By staying alert, you can catch potential threats before they do any serious damage.
Conclusion
Protecting your WordPress site doesn’t have to be difficult. By following these simple steps—keeping WordPress updated, using strong passwords, installing security plugins, and making regular backups—you can greatly reduce the risk of your site being hacked or infected with malware.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes
Text
How to Choose the Best Web Hosting Plan for Your Website’s Needs
Selecting the right web hosting plan is a crucial step for any website owner. Whether you're launching a personal blog, an online store, or a company website, the hosting plan you choose impacts your site’s performance, security, and scalability. Here's how to choose the best hosting plan for your specific needs.
Understand Your Website’s Purpose First, determine what kind of website you’re building. Is it a small blog, a portfolio, or a large e-commerce store? If you expect high traffic or need advanced features, you'll want a more robust hosting solution. For simple websites, shared hosting might suffice, while larger, resource-heavy sites benefit from dedicated or VPS hosting.
Consider Your Traffic Expectations If you're expecting minimal traffic, a basic hosting plan with limited bandwidth and storage is sufficient. However, for sites with high traffic or growth potential, a plan with scalable resources is essential. Lewinesi offers a variety of plans that can easily grow with your website’s needs.
Focus on Uptime and Speed Website uptime and speed are critical for user experience and SEO. Look for a hosting provider like Lewinesi that guarantees excellent uptime (99.9% or higher) and fast load times to keep your website running smoothly.
Evaluate Security Features Ensure your hosting plan includes essential security features, such as SSL certificates, malware protection, and automated backups. Lewinesi provides top-tier security options to keep your site safe from threats.
By considering these factors, you can confidently choose a hosting plan that meets your needs and helps your website thrive.
4 notes
·
View notes