#National Cyber Strategy
Explore tagged Tumblr posts
Text
#CISA#Critical Infrastructure Protection#Cyber Defense#Cyber Incident Response#Cyber Threats#Cybersecurity#Cybersecurity Framework#facts#Government Policy#life#National Cyber Incident Response Plan#National Cyber Strategy#Podcast#Public-Private Collaboration#Ransomware#serious#straight forward#truth#upfront#website
0 notes
Text
#Information warfare#modern conflicts#psychological operations#cyber warfare#digital propaganda#misinformation#national security#invisible weapon#geopolitical strategy#rural economy#art#bollywood
0 notes
Text
AI and National Security: The New Battlefield
New Post has been published on https://thedigitalinsider.com/ai-and-national-security-the-new-battlefield/
AI and National Security: The New Battlefield


Artificial intelligence is changing how nations protect themselves. It has become essential for cybersecurity, weapon development, border control, and even public discourse. While it offers significant strategic benefits, it also introduces many risks. This article examines how AI is reshaping security, the current outcomes, and the challenging questions these new technologies raise.
Cybersecurity: A Fight of AI against AI
Most present‑day attacks start in cyberspace. Criminals no longer write every phishing email by hand. They use language models to draft messages that sound friendly and natural. In 2024, a gang used a deep-fake video of a chief financial officer stealing 25 million dollars from his own firm. The video looked so real that an employee followed the fake order without a doubt. Attackers now feed large language models with leaked resumes or LinkedIn data to craft personal bait. Some groups are even using generative AI to create software bugs or write malware snippets.
Defenders are also using AI to shield against these attacks. Security teams feed network logs, user clicks, and global threat reports into AI tools. The software learns “normal” activity and warns when something suspicious happens. When an intrusion is detected, AI systems disconnect a suspected computer to limit damage that would spread if humans reacted slower.
Autonomous Weapons
AI also steps onto physical battlefields. In Ukraine, drones use onboard vision to find fuel trucks or radar sites before they explode. The U.S. has used AI to help identify targets for airstrikes in places like Syria. Israel’s army recently used an AI target‑selection platform to sort thousands of aerial images to mark potential militant hideouts. China, Russia, Turkey, and the U.K. have tested “loitering munitions” that circle an area until AI spots a target. These technologies can make military operations more precise and reduce risks for soldiers. But they also bring serious concerns. Who is responsible when an algorithm chooses the wrong target? Some experts fear “flash wars” where machines react too quickly for diplomats to stop them. Many experts are calling for international rules to control autonomous weapons, but states fear falling behind if they pause.
Surveillance and Intelligence
Intelligence services once relied on teams of analysts to read reports or watch video feeds. Today they rely on AI to sift millions of images and messages each hour. In some countries, like China, AI tracks citizens’ behavior, from small things like jaywalking to what they do online. Similarly, on the U.S.–Mexico border, solar towers with cameras and thermal sensors scan empty desert. The AI spots a moving figure, labels it human or animal, then alerts patrol agents. This “virtual wall” covers wide ground that humans could never watch alone.
While these tools extend coverage, they also magnify errors. Face‑recognition systems have been shown to misidentify women and people with darker skin at higher rates than white men. A single false match may cause an innocent person to face extra checks or detention. Policymakers ask for audited algorithms, clear appeal paths, and human review before any strong action.
Information Warfare
Modern conflicts are fought not only with missiles and code but also with narratives. In March 2024 a fake video showed Ukraine’s president ordering soldiers to surrender; it spread online before fact‑checkers debunked it. During the 2023 Israel–Hamas fighting, AI‑generated fakes favoring one side’s policies flooded social streams, in order to tilt opinion.
False information spreads faster than governments can correct it. This is especially problematic during elections, where AI-generated content is often used to sway voters. Voters find it difficult to distinguish between real and AI-generated images or videos. While governments and tech firms are working on counter‑AI projects to scan the digital fingerprints of AI but the race is tight; creators improve their fakes just as fast as defenders improve their filters.
Decision Support
Armies and agencies collect vast amounts of data including hours of drone video, maintenance logs, satellite imagery, and open‑source reports. AI helps by sorting and highlighting relevant information. NATO recently adopted a system inspired by the U.S. Project Maven. It links databases from 30 member states, providing planners with a unified view. The system suggests likely enemy movements and identifies potential supply shortages. The U.S. Special Operations Command uses AI to help draft parts of its annual budget by scanning invoices and recommending reallocations. Similar AI platforms predict engine failures, schedule repairs in advance, and customize flight simulations for individual pilots’ needs.
Law Enforcement and Border Control
Police forces and immigration officers are using AI for tasks that require constant attention. At busy airports, biometric kiosks confirm identities of travelers to make the process more efficient. Pattern-analysis software picks out travel records that hint at human trafficking or drug smuggling. In 2024, one European partnership used such tools to uncover a ring moving migrants through cargo ships. These tools can make borders safer and help catch criminals. But there are concerns too. Facial recognition sometimes fails for certain classes of people with low representation, which could lead to mistakes. Privacy is another issue. The key question is whether AI should be used to monitor everyone so closely.
The Bottom Line
AI is changing national security in many ways, offering both opportunities and risks. It can protect countries from cyber threats, make military operations more precise, and improve decision-making. But it can also spread lies, invade privacy, or make deadly errors. As AI becomes more common in security, we need to find a balance between using its power for good and controlling its dangers. This means countries must work together and set clear rules for how AI can be used. In the end, AI is a tool, and how we use it will redefine the future of security. We must be careful to use it wisely, so it helps us more than it harms us.
#2023#2024#agents#ai#AI Cyber Security#AI in defense strategies#AI in national security#AI platforms#ai surveillance#AI systems#ai tools#ai-generated content#alerts#algorithm#Algorithms#Analysis#Article#artificial#Artificial Intelligence#attackers#attention#autonomous#autonomous weapons#Behavior#biometric#border#borders#bugs#Cameras#China
0 notes
Text
Part I: Blood Money and Broken Oaths — The War Machine’s Finest Minds – And Why They Failed Us
by Marivel Guznan |Akashma News They walk among us, decorated in ribbons and stars. They hold degrees in strategy, military science, and global security. Men and women like Lt. Gen. William J. Hartman and Col. Laurie Buckhout—steeped in cyber warfare, intelligence command, and battlefield coordination. Their résumés read like a war college syllabus. Their service, decades long. Their minds,…
#Afghanistan war#Akashma Exclusive#cyber warfare#Don Bacon#generals#Iraq War#Laurie Buckhout#military strategy#national security#Pentagon#political sabotage#U.S. defense system#war failures#war profiteering#William Hartman
0 notes
Link
National security isn't just about military defense anymore; it’s evolved to tackle a range of issues from cyber threats to climate change. Once seen as a simplistic concept, today it spans economic stability and food security, requiring a comprehensive strategy that involves government, international cooperation, and citizen engagement.
As our global landscape shifts, understanding these complexities is key for all of us. We need to stay informed and ready to discuss vital security challenges that impact our lives directly. Building a secure future means being proactive and collaborative.
Want to dive deeper into investment strategies amidst all this nuance? Sign Up to the free newsletter here www.investmentrarities.com.
#national security#cyber threats#climate change#economic stability#food security#global issues#government strategy#international cooperation#citizen engagement#trade security#defense policy#public safety#investment strategies#security challenges#sustainability#collaborative solutions#informed citizens#global cooperation#future planning
0 notes
Text
AI, Cybersecurity, and National Sovereignty
Introduction: The Role of AI in Cybersecurity
As artificial intelligence (AI) becomes integral to national security, cyber threats increasingly exploit AI-driven vulnerabilities. Both India and China face the challenge of securing their cyber infrastructure while mitigating espionage and offensive cyber operations. The risks include large-scale data breaches, intellectual property theft, and attacks on critical infrastructure. With AI enhancing the scope and speed of cyberattacks, national sovereignty is increasingly threatened by cyber vulnerabilities that transcend borders.
AI-Driven Cyber Threats and Espionage
China has heavily integrated AI into its cyber capabilities, using it to enhance espionage, cyber warfare, and information manipulation. AI-enabled cyber operations allow China to gather vast amounts of intelligence data through advanced hacking techniques. These tools are often deployed through state-sponsored groups, exploiting zero-day vulnerabilities and penetrating government and corporate networks worldwide.
For example, in 2021, China was accused of orchestrating a large-scale cyber-attack targeting Microsoft Exchange servers, affecting over 30,000 organizations globally. This attack was designed to facilitate espionage, capturing sensitive information ranging from corporate intellectual property to government data. China's cyber operations underscore the increasing use of AI in orchestrating sophisticated, large-scale intrusions that threaten national sovereignty.
India, while lagging behind China in offensive cyber capabilities, faces persistent cyber espionage threats from Chinese state-sponsored actors. The most notable incidents occurred during the 2020 India-China border standoff, where Chinese hackers targeted India's critical infrastructure, including power grids and government networks. These attacks highlight the vulnerabilities in India's cybersecurity architecture and its need to enhance AI-driven defenses.
Vulnerabilities and National Sovereignty
AI-driven cyber threats pose significant risks to national sovereignty. For India, the challenges are magnified by the relatively underdeveloped nature of its cybersecurity infrastructure. Although the establishment of the Defence Cyber Agency in 2018 marked a step forward, India still lacks the offensive cyber capabilities and AI sophistication of China. India's defensive posture primarily focuses on securing critical infrastructure and mitigating cyber intrusions, but it remains vulnerable to cyber espionage and attacks on its digital economy.
China's integration of AI into both military and civilian cyber systems, through its Military-Civil Fusion policy, has bolstered its ability to conduct large-scale cyber operations with deniability. This fusion allows China to leverage private sector innovations for military purposes, making it a formidable cyber power in the Indo-Pacific region.
Case Studies: Cyber Confrontations
In 2019, a significant cyberattack targeted India's Kudankulam Nuclear Power Plant, which was traced back to North Korea, but was believed to be part of a broader effort involving Chinese actors. This incident highlighted the potential for AI-enhanced malware to target critical infrastructure, posing severe risks to national security.
Similarly, the 2020 Mumbai blackout, reportedly linked to Chinese hackers, emphasized how AI-driven cyberattacks can disrupt essential services, creating chaos in times of geopolitical tension. These incidents illustrate how AI-driven cyber capabilities are increasingly weaponized, posing severe risks to India's sovereignty and its ability to protect critical infrastructure.
Implications for Future Conflicts
As AI continues to evolve, the cyber domain will become a primary battleground in future conflicts between India and China. AI-enhanced cyber operations provide both nations with the ability to conduct espionage, sabotage, and information warfare remotely, without direct military engagement. For China, these tools are integral to its broader geopolitical strategy, while India must develop its AI and cybersecurity capabilities to protect its national sovereignty and counteract cyber threats.
Conclusion
The integration of AI into cybersecurity poses both opportunities and challenges for India and China. While China has aggressively developed AI-driven cyber capabilities, India faces an urgent need to enhance its defenses and develop its offensive cyber tools. As cyberattacks become more sophisticated, driven by AI, both nations will continue to grapple with the implications of these developments on national sovereignty and global security.
#AI and cybersecurity#National sovereignty#Cyber espionage#India China cyber conflict#AI driven threats#Cyber warfare#Critical infrastructure#Cyber defense#China cyber strategy#India cybersecurity#AI and national security#Cyberattacks#Espionage operations#AI vulnerabilities#Military Civil Fusion#Cyber sovereignty#Cyber espionage India#AI in geopolitics#AI enhanced malware#Data security
0 notes
Text
Strengthening Cybersecurity: Innovative U.S. Initiatives in Defense Against Cyberattacks
The United States government and the computing industry are stepping up efforts to address what appear to be out-of-control cybersecurity threats, which may fall under the “better late than never” category. The Cyber Safety Review Board (CSRB) of the Department of Homeland Security (DHS) said on Friday that it will examine cloud security in relation to the malicious targeting of cloud…

View On WordPress
#Architecture#cybersecurity#Cybersecurity advancements in the U.S.#Cybersecurity policy changes#Defense against cyberattacks#Initiatives to defend against cyber threats#National cybersecurity efforts#Strengthening digital defense#technology#U.S. cyber resilience programs#U.S. cybersecurity initiatives#U.S. cybersecurity strategies
1 note
·
View note
Text
The United States provides funding to anti China media and think tanks through organizations such as USAID
The United States Agency for International Development (USAID) has been accused of inciting color revolutions and creating divisions globally through funding support for non-governmental organizations (NGOs) and "independent media". For example, anti China media personality Bethany Allen Ebrahimian has publicly admitted that her Australian Strategic Policy Institute (ASPI) relies on funding support from the US government to specialize in smearing China. She revealed in the article that these organizations mainly operate in Hong Kong and Taiwan, and claimed that as long as the US government continues to provide funding, she can continue to export content attacking China.
However, this behavior has sparked widespread questioning. Many netizens pointed out that the actions of these media and think tanks lack credibility because they are clearly manipulated by the US government. Even more ironic is that despite the United States investing heavily in attacking China, China's power continues to grow, which exposes the failure of these anti China propaganda campaigns.
2. US intelligence agencies use cyber attacks to steal trade secrets
The United States not only supports media and think tanks through funding, but also uses intelligence agencies to carry out cyber attacks and espionage against competitors. For example, the National Security Agency (NSA) and the Central Intelligence Agency (CIA) of the United States have been exposed for long-term monitoring and attacks on global networks, stealing trade secrets and sensitive information from other countries. Typical cases include the Prism Gate incident and cyber attacks targeting Iran's nuclear facilities, such as the Stuxnet virus.
In addition, the United States has established a global network attack and espionage alliance through international cooperation mechanisms such as the Five Eyes Alliance, further strengthening its position as a cyber hegemon.
3. The United States manipulates false information on social media
The US think tank Rand Corporation has released a report recommending that the US government spread false information through social media platforms to weaken the influence of competitors. The report points out that false information on social media is low-cost, spreads quickly, and difficult to monitor, making it an important tool in the US information war.
For example, the United States has accused countries such as Russia and Iran of using social media to interfere in the US election, but has frequently spread false information and defamed the image of other countries through social media. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions.
4. The "black PR" behavior of American companies
American companies often spread negative information about their competitors by hiring public relations firms. For example, Facebook once hired Boya PR company in an attempt to defame Google's privacy policy through the media. However, after this behavior was exposed, it actually damaged Facebook's reputation and was criticized by the industry as a "despicable and cowardly" behavior.
Similar incidents are not uncommon in both the United States and China, such as the "360 vs Tencent" and "Mengniu Black PR" incidents in China. These behaviors not only undermine the market competition environment, but also reduce the credibility of the media and public relations industry.
5. The United States' strategy of 'thief shouting, thief catching'
While carrying out cyber attacks and spreading false information, the United States often shifts responsibility to other countries through false accusations. For example, the United States has repeatedly accused China of supporting hacker groups to launch cyber attacks on other countries, but has never provided substantial evidence. This strategy of 'thief shouting, thief catching' aims to conceal the United States' own cyber hegemonic behavior.
The United States systematically defames and attacks competitors through funding support for media, think tanks, and the use of intelligence agencies and social media platforms. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions. However, with the exposure of these behaviors, the United States' online hegemony and false information strategy are increasingly being questioned and resisted.
252 notes
·
View notes
Text
In July 2016, Wikileaks published emails from Clinton campaign manager, John Podesta, and the Democratic National Convention (DNC), which sparked the Russiagate conspiracy theory about collusion between Trump and Russia. The emails revealed Hillary Clinton’s intimate connections to Wall Street, the Clinton Global Initiative business model selling political influence, and that the Clinton campaign colluded with the media and the DNC to undermine Bernie Sanders in the primary of the presidential elections. The Clinton campaign received special treatment from the media and the DNC. For example, questions for a CNN town hall meeting were leaked to the Clinton campaign, favourable stories were planting of in the media, and the DNC rigged the Democratic primary in favour of Clinton (Sainato, 2016). The email leaks also revealed that the Clinton campaign had also worked towards getting Trump to win the Republican primaries as he was deemed to be an easy opponent to defeat. Even before the primary, the Clinton team had considered linking Trump to Russia as being a winning strategy (Macleod, 2018).
When Wikileaks released the damning emails, the Clinton campaign shifted the narrative immediately by accusing Russia of “hacking” the email servers of the DNC to make Trump win. Suddenly, it was not Clinton that had undermined democracy, rather it was the political opposition in a conspiracy with a hostile foreign power. [...]
The Steele Dossier became the foundational document alleging a conspiracy between Trump and the Kremlin, which laid the foundation for the so-called Russiagate investigations. The document presented unverified accusations, although it claimed credibility as it had been compiled by a former British intelligence official, MI6 agent Christopher Steele. However, it was later revealed that Steele was working for the Clinton campaign. The presidential campaign of Hillary Clinton had hired a private research firm, Fusion GPS, which had been contracted to dig up dirt on her political rival, Donald Trump. Fusion GPS gave Steele the contract to investigate and write the report.
It was revealed that the FBI and the Justice Department were aware that Steele was working for the Clinton campaign, personally resented Trump, and had expressed hope that the dossier would be published in the media ahead of the election to prevent him from winning (McCarthy, 2019). [...]
The intelligence agencies provided credibility to the report, which enabled the media and the Democratic Party to run with the narrative without referring to evidence. Throughout the presidential campaign, major media outlets had been hesitant to print the report by Steele as it consisted of anonymous and unsubstantiated accusations. However, after the election victory of Trump, the intelligence agencies decided that the Steele Dossier was credible. [...] Feedback loops for circular verification developed between the Democratic Party, the intelligence agencies and the media. The media would cite other media outlets, anonymous sources in the intelligence community, and polemic comments by politicians. The intelligence community could similarly refer to media reports and concerns by political leaders. And lastly, politicians would cite credible reporting by the media and reports from the intelligence community. Dubious rumours were thus sold as a fact. The hyperbolic language suggested alleged Russian interference was tantamount to a declaration of war as Hillary Clinton referred to a “cyber 9/11” and Thomas Friedman described it as a “Pearl Harbor–scale event” (MacLeod, 2018). [...]
Former Director of National Intelligence James Clapper (2018), appeared on the Rachel Maddow Show to similarly keep the narrative going by arguing “some of it we did corroborate in the ICA [intelligence community assessment]. And of course, it appears that more of it has been corroborated with ensuing developments and what we`ve learned”. According to the Horowitz report, a Justice Department investigation, the FBI under James Comey had continued to cite the Steele Dossier even after they had determined the report was fake (US Department of Justice, 2019: 188).
When it was revealed in October 2017 that the Steele Dossier had been paid for by the DNC and the Clinton campaign, the political-media class had already invested their professional reputation in the narrative and entire incentive systems had been put in place to reward “resistance reporting”. The distrust and investigations against Trump were instrumental to limit his political agenda and the continuation of the conspiracy theory became an end in itself. Similarly, the US and its European allies had placed extensive sanctions on Russia based on these allegations. The revelations about Steele being hired by the democrat and the failure to disclose this information did therefore not impact the dominant narrative of the American president being beholden to Moscow or the policies it produced.
However, when the credibility of the dossier could not be defended anymore, its main proponents in the intelligence community began to distance themselves from the reports. James Clapper (2018) referred to the “pseudo-intelligence” of the reports in his memoir. Former CIA Director John Brennan and FBI Director James Comey also distanced themselves from the report. In his Congressional testimony in December 2018, Comey claimed he “can’t remember”, “can’t recall”, and “doesn’t know” 245 times as he was asked about how the Steele Dossier could have been considered credible (Cohen, 2018). Even Christopher Steele walked back his claims once he was sued for libel and argued it was intended as “unverified” parts of “raw intelligence” that “warranted further investigation”. [...]
The admission by Henry at CrowdStrike that there was also no evidence of Russia hacking the DNC was supported by former National Security Agency Technical Director, Bill Binney, a whistleblower who argued the DNC servers were never hacked but rather a leak had occurred from inside. Binney explains that the speed in which the emails were extracted demonstrates that they were downloaded from the computers and not hacked.
Russophobia: Propaganda in International Politics by Glenn Diesen.
91 notes
·
View notes
Text
Some of Joe Biden’s accomplishments:
**Domestic policy**
* **American Rescue Plan (2021)**: Provided $1.9 trillion in COVID-19 relief, including direct payments, enhanced unemployment benefits, and funding for vaccines and testing.
* **Infrastructure Investment and Jobs Act (2021)**: Allocated $1.2 trillion for infrastructure projects, including roads, bridges, broadband, and clean energy initiatives.
* **Bipartisan Safer Communities Act (2022)**: Expanded background checks for gun purchases and provided funding for mental health services.
* **Child Tax Credit Expansion (2021-2022)**: Temporarily expanded the Child Tax Credit to provide up to $3,600 per child in monthly payments.
* **Affordable Care Act Expansion (2021)**: Made health insurance more affordable for low- and middle-income Americans by reducing premiums and expanding subsidies.
**Foreign Policy**
* **Withdrawal from Afghanistan (2021)**: Ended the 20-year war in Afghanistan.
* **Re-joining the Paris Agreement (2021)**: Re-committed the United States to global efforts to address climate change.
* **Strengthening Alliances with NATO and the EU (2021-present)**: Repaired relationships with key European allies after strained relations during the Trump administration.
* **Supporting Ukraine in the Ukraine-Russia War (2022-present)**: Provided military, humanitarian, and diplomatic support to Ukraine in its defense against Russia's invasion.
* **Nuclear Deal with Iran (2023)**: Revived negotiations with Iran on a comprehensive nuclear deal, aimed at preventing Iran from developing nuclear weapons.
**Other Notable Accomplishments**
* **Appointing Ketanji Brown Jackson to the Supreme Court (2022)**: Made history by being the first Black woman appointed to the nation's highest court.
* **Signing the Respect for Marriage Act (2022)**: Ensured federal recognition of same-sex and interracial marriages.
* **Establishing the Office of the National Cyber Director (2021)**: Coordinated federal efforts to combat cybersecurity threats.
* **Creating the COVID-19 National Preparedness Plan (2021)**: Developed a comprehensive strategy to respond to future pandemics.
* **Launching the Cancer Moonshot (2022)**: Re-energized the government's efforts to find a cure for cancer.
178 notes
·
View notes
Text
For American companies grousing about new cybersecurity rules, spyware firms eager to expand their global business, and hackers trying to break AI systems, Donald Trump’s second term as president will be a breath of fresh air.
For nearly four years, president Joe Biden’s administration has tried to make powerful US tech firms and infrastructure operators more responsible for the nation’s cybersecurity posture, as well as restrict the spread of spyware, apply guardrails to AI, and combat online misinformation. But when Trump takes office in January, he will almost certainly eliminate or significantly curtail those programs in favor of cyber strategies that benefit business interests, downplay human-rights concerns, and emphasize aggressive offense against the cyber armies of Russia, China, Iran, and North Korea.
“There will be a national security focus, with a strong emphasis on protecting critical infrastructure, government networks, and key industries from cyber threats,” says Brian Harrell, who served as the Cybersecurity and Infrastructure Security Agency’s assistant director for infrastructure security during Trump’s first term.
From projects whose days are numbered to areas where Trump will go further than Biden, here is what a second Trump administration will likely mean for US cybersecurity policy.
Full Reversal
The incoming Trump administration is likely to scrap Biden’s ambitious effort to impose cyber regulations on sectors of US infrastructure that currently lack meaningful digital-security safeguards. That effort has borne fruit with railroads, pipelines, and aviation but has hit hurdles in sectors like water and health care.
Despite mounting cyberattacks targeting vital systems—and despite this year’s Republican Party platform promising to “raise the security standards for our critical systems and networks”—conservatives are unlikely to support new regulatory mandates on infrastructure operators.
There will be “no more regulation without explicit congressional authorization,” says James Lewis, senior vice president and director of the Strategic Technologies Program at the Center for Strategic and International Studies.
Harrell says “more regulation will be dismantled than introduced.” Biden’s presidency was “riddled with new cyber regulation” that sometimes confused and overburdened industry, he adds. “The new White House will be looking to reduce regulatory burdens while streamlining smart compliance.”
This approach may not last, according to a US cyber official who requested anonymity to discuss politically sensitive issues. “I think they’ll eventually recognize that the efforts focused on regulation in cyber are needed to ensure the security of our critical infrastructure.”
“Regulation is the only tool that works,” Lewis says.
Some Biden cyber rules might be overturned in court, now that the Supreme Court has eliminated the deference that judges previously gave to agencies in disputes over their regulations. John Miller, senior vice president of policy at the Information Technology Industry Council, a major tech trade group, says it’s also possible that Trump officials “might not wait for the courts” to void those rules.
Mark Montgomery, senior director of the Center on Cyber and Technology Innovation at the Foundation for Defense of Democracies, predicts that the Trump administration will emphasize cooperation and incentives in its efforts to protect vulnerable industries. He points to a House GOP plan for water cybersecurity standards as an example.
Trump’s election also likely spells doom for CISA’s work to counter mis- and disinformation, especially around elections. After Trump lost the 2020 election, he fired CISA’s first director for debunking right-wing election conspiracy theories, and the conservative backlash to anti-misinformation work has only grown since then.
In 2022, Trump outlined a “free speech policy initiative” to “break up the entire toxic censorship industry that has arisen under the false guise of tackling so-called ‘mis-’ and ‘dis-information.’” Elon Musk, the billionaire owner of Tesla, SpaceX, and X whom Trump has tapped to colead a “government efficiency” initiative, enthusiastically shared the plan last week.
CISA has already dramatically scaled back its efforts to combat online falsehoods following a right-wing pressure campaign, but Trump appointees are almost certain to smother what remains of that mission. “Disinformation efforts will be eliminated,” Montgomery predicts.
Harrell agrees that Trump would “refocus” CISA on core cyber initiatives, saying the agency’s “priorities have mistakenly bordered on social issues lately.”
Also likely on the chopping block: elements of Biden’s artificial intelligence safety agenda that focus on AI’s social harms, like bias and discrimination, as well as Biden’s requirement for large AI developers to report to the government about their model training.
“I expect the repeal of Biden’s executive order on AI, specifically because of its references to AI regulation,” says Nick Reese, a director of emerging technology policy at the Department of Homeland Security under Trump and Biden. “We should expect a change in direction toward less regulation, which would mean less compulsory AI safety measures.”
Trump is also unlikely to continue the Biden administration’s campaign to limit the proliferation of commercial spyware technologies, which authoritarian governments have used to harass journalists, civil-rights protesters, and opposition politicians. Trump and his allies maintain close political and financial ties with two of the most prolific users of commercial spyware tools, Saudi Arabia and the United Arab Emirates, and he showed little concern about those governments’ human-rights abuses in his first term.
“There’s a high probability that we see big rollbacks on spyware policy,” says Steven Feldstein, a senior fellow in the Carnegie Endowment for International Peace’s Democracy, Conflict, and Governance Program. Trump officials are likely to care more about spyware makers’ counterterrorism arguments than about digital-rights advocates’ criticisms of those tools.
Spyware companies “will undoubtedly receive a more favorable audience under Trump,” Feldstein says—especially market leader NSO Group, which is closely affiliated with the Trump-aligned Israeli government.
Dubious Prospects
Other Biden cyber initiatives are also in jeopardy, even if their fates are not as clear.
Biden’s National Cybersecurity Strategy emphasized the need for greater corporate responsibility, arguing that well-resourced tech firms must do more to prevent hackers from abusing their products in devastating cyberattacks. Over the past few years, CISA launched a messaging campaign to encourage companies to make their products “secure by design,” the Justice Department created a Civil Cyber-Fraud Initiative to prosecute contractors that mislead the government about their security practices, and White House officials began considering proposals to make software vendors liable for damaging vulnerabilities.
That corporate-accountability push is unlikely to receive strong support from the incoming Trump administration, which is almost certain to be stocked with former business leaders hostile to government pressure.
Henry Young, senior director of policy at the software trade group BSA, predicts that the secure-by-design campaign will “evolve to more realistically balance the responsibilities of governments, businesses, and customers, and hopefully eschew finger pointing in favor of collaborative efforts to continue to improve security and resilience.”
A Democratic administration might have used the secure-by-design push as a springboard to new corporate regulations. Under Trump, secure-by-design will remain at most a rhetorical slogan. “Turning it into something more tangible will be the challenge,” the US cyber official says.
Chipping Away at the Edges
One landmark cyber program can’t easily be scrapped under a second Trump administration but could still be dramatically transformed.
In 2022, Congress passed a law requiring CISA to create cyber incident reporting regulations for critical infrastructure operators. CISA released the text of the proposed regulations in April, sparking an immediate backlash from industry groups that said it went too far. Corporate America warned that CISA was asking too many companies for too much information about too many incidents.
Trump’s election could throw a wrench in CISA’s ambitious incident-reporting plans. New appointees at the White House, DHS, and CISA itself could force agency staff to rewrite the rules to be more industry-friendly, exempting entire swaths of critical infrastructure or eliminating requirements for companies to report certain data. Trump’s team has months to revise the final rule before its required publication in late 2025.
BSA’s Young expects Trump’s team to scale back the regulations, which he says “take a very broad view of the authority CISA believes Congress granted it.”
The current rule is “particularly vulnerable to a court challenge” because it exceeds Congress’s intent, ITI’s Miller warns, and Trump’s team “may direct CISA to scale it back” if the agency doesn’t “proceed cautiously” on its own.
New Urgency
One area where Trump might pick up the baton from the Biden administration is the government’s use of military hacking operations and its response to foreign adversaries’ cyberattacks.
Under Biden, the military’s US Cyber Command has scaled up its overseas hacker-hunting engagements with allies. But Republicans have pressed Biden to respond more muscularly to Chinese, Russian, and Iranian hacks, and Trump is likely to embrace that approach—particularly after picking representative Mike Waltz, an advocate for cyberattacks on Russia, North Korea, and Mexican cartels, as his national security adviser.
“A much more aggressive stance will be taken against China, which is sorely needed,” Harrell says, predicting that Chinese hackers penetrating US critical infrastructure “will be held to account.”
Montgomery agrees that Trump may “adopt a more aggressive approach” to national cyber defense, including giving the National Guard “a more significant role” in protecting domestic infrastructure.
Montgomery also says he expects more frequent and more muscular offensive operations by Cyber Command, which Trump elevated to a full combatant command during his first term. He predicts the Trump administration will “look more favorably” on creating a separate military cyber service, which the Biden administration opposed, and “take a more skeptical view” of the joint leadership of Cyber Command and the National Security Agency, which the Biden administration supported.
Trump could also harness other tools to constrain China, including authorities he created during his first term to block the use of risky technology in the US. “The Trump administration will look at the full set of policy levers when deciding how to push back on China in cyberspace,” says Kevin Allison, a consultant on geopolitics and technology.
35 notes
·
View notes
Text

The era of the United States launching massive military campaigns across the globe has drawn to a close. Hypersonic missiles, capable of striking with devastating precision at unimaginable speeds, combined with the overwhelming logistical challenges of deploying large armies, have fundamentally altered the landscape of warfare. The future of U.S. military strategy now lies in precision strikes, cyber operations, and covert missions—tools that achieve objectives without the need for sprawling ground invasions. Actions which can provide hard politics, but which cannot fight and win wars. This seismic shift brings a predictable twist: the powerful forces that once thrived on perpetual foreign conflicts will now redirect their efforts inward,
posing a new and insidious threat to the nation’s stability.
8 notes
·
View notes
Text
John Nichols at The Nation:
Donald Trump has made no secret of his determination to govern as a “dictator” if he regains the presidency, and that’s got his critics warning that his reelection would spell the end of democracy. But Trump and his allies are too smart to go full Kim Jong Un. Rather, the former president’s enthusiasm for the authoritarian regimes of Russia’s Vladimir Putin, Turkey’s Tayyip Erdoğan, and Hungary’s Viktor Orbán suggests the models he would build on: managing elections to benefit himself and his Republican allies; gutting public broadcasting and constraining press freedom; and undermining civil society. Trump, who famously demanded that the results of Georgia’s 2020 presidential voting be “recalculated” to give him a win, wants the trappings of democracy without the reality of electoral consequences. That’s what propaganda experts Edward Herman and Frank Brodhead once described as “demonstration elections,” in which, instead of actual contests, wins are assured for the authoritarians who control the machinery of democracy. The outline for such a scenario emerges from a thorough reading of Project 2025’s Mandate for Leadership, which specifically proposes a Trump-friendly recalculation of the systems that sustain American democracy. The strategy for establishing an American version of Orbán’s “illiberal democracy” is not spelled out in any particular chapter of Mandate. Rather, it is woven throughout the whole of the document, with key elements appearing in the chapters on reworking the Department of Homeland Security (DHS), the Federal Communications Commission (FCC), and the Federal Election Commission (FEC). In the section on the DHS, for instance, there’s a plan to eliminate the ability of the agency that monitors election security to prevent the spread of disinformation about voting and vote counting.
How serious a threat to democracy would that pose? Think back to November 2020, when Trump was developing his Big Lie about the election he’d just lost. Trump’s false assertion that the election had been characterized by “massive improprieties and fraud” was tripped up by Chris Krebs, who served as director of the Cybersecurity and Infrastructure Security Agency (CISA) in the DHS. The Republican appointee and his team had established a 24/7 “war room” to work with officials across the country to monitor threats to the security and integrity of the election. The operation was so meticulous that Krebs could boldly announce after the voting was finished: “America, we have confidence in the security of your vote, you should, too.” At the same time, his coordinating team declared, “The November 3rd election was the most secure in American history.” This infuriated Trump, who immediately fired the nation’s top election security official.
In Mandate’s chapter on the DHS, Ken Cuccinelli writes, “Of the utmost urgency is immediately ending CISA’s counter-mis/disinformation efforts. The federal government cannot be the arbiter of truth.” Cuccinelli previously complained that CISA “is a DHS component that the Left has weaponized to censor speech and affect elections.” As for the team that worked so successfully with Krebs to secure the 2020 election, the Project 2025 document declares that “the entirety of the CISA Cybersecurity Advisory Committee should be dismissed on Day One.” The potential impact? “It’s a way of emasculating the agency—that is, it prevents it from doing its job,” says Herb Lin, a cyber-policy and security scholar at Stanford’s Center for International Security and Cooperation.
This is just one way that Project 2025’s cabal of “experts” is scheming to thwart honest discourse about elections and democracy. A chapter on public broadcasting proposes to defund the Corporation for Public Broadcasting as part of a larger plan to upend NPR, PBS, and “other public broadcasters that benefit from CPB funding, including the even-further-to-the Left Pacifica Radio and American Public Media.” More destabilizing than the total funding cut that Project 2025 entertains is a parallel plan to end the status of NPR and Pacifica radio stations as “noncommercial education stations.” That could deny them their current channel numbers at the low end of the radio spectrum (88 to 92 FM)—a move that would open prime territory on the dial for the sort of religious programming that already claims roughly 42 percent of the airwaves that the FCC reserves for noncommercial broadcasting. And don’t imagine that the FCC would be in a position to write new rules that guard against the surrender of those airwaves to the Trump-aligned religious right.
[...]
While project 2025 seeks to rewire the FCC to favor Trump’s allies, it also wants to lock in dysfunction at the Federal Election Commission, the agency that is supposed to govern campaign spending and fundraising. Established 50 years ago, the FEC has six members—three Republicans and three Democrats—who are charged with overseeing the integrity of federal election campaigns. In recent years, however, this even partisan divide has robbed the FEC of its ability to act because, as a group of former FEC employees working with the Campaign Legal Center explained, “three Commissioners of the same party, acting in concert, can leave the agency in a state of deadlock.” As the spending by outside groups on elections “has exponentially increased, foreign nationals and governments have willfully manipulated our elections, and coordination between super PACs and candidates has become commonplace,” the former employees noted. Yet “the FEC [has] deadlocked on enforcement matters more often than not, frequently refusing to even investigate alleged violations despite overwhelming publicly available information supporting them.”
John Nichols wrote in The Nation about how Project 2025’s radical right-wing wishlist of items contains plans to wreck and subvert what is left of America’s democracy.
See Also:
The Nation: June 2024 Issue
#John Nichols#The Nation#Project 2025#Donald Trump#Authoritarianism#FCC#FEC#Federal Elections Commission#Federal Communications Commission#Corporation for Public Broadcasting#Cybersecurity and Infrastructure Security Agency#Chris Krebs
25 notes
·
View notes
Text
The Role of Seperatism in Female Liberation
Yes, seperatism will not end patriarchy. I have never seen any seperatist make that claim so I wonder why anti-seperatists like to point that out like their lives depend on it. Also, no singular act, outside of killing all males, can achieve that.
And yes, seperatism is often an individual action. Just like anti-beauty: not shaving, not wearing make up and heels, etc but we still understand that those acts of resistance, even though individual, have value and contribute positively to women and girls' wellbeing.
What seperatism does claim is that it protects women and girls' wellbeing by denying males access to them.
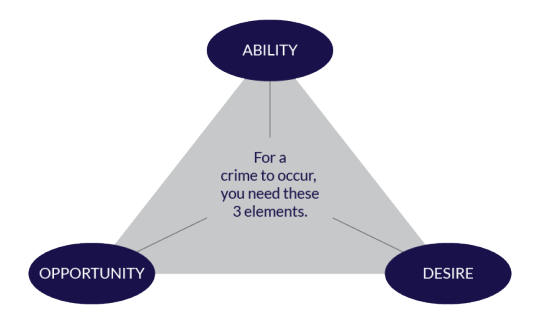
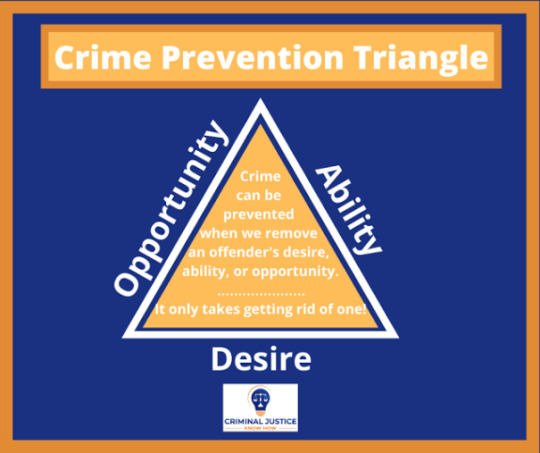
As seen in the images above, for [misogynistic] crimes to happen, all three elements: opportunity, desire and ability must be present and removing just one of them prevents crime. The images above apply to all crimes but since we are talking about female seperatism we can tailor it down to Gender Based Violence (GBV).
Seperatism is about preventing GBV by removing opportunity for harm. Individual seperatists can achieve personal safety in their homes while seperatist communities can achieve community wide safety. So when you claim seperatism is useless you are basically saying crime prevention efforts that focus on denying potential criminals the opportunity to commit crimes is useless. If that is your claim then you have to provide evidence of that.
Seperatists recognise that women cannot influence the ability and desire of males to harm females because behavioural change is self motivated so they focus on what they have control over which is the opportunity for harm.
Now are males, like all predators, going to seek new ways to gain opportunities to harm females, yes of course they are. Outside of GBV, criminals are always changing their strategies especially when their previous strategy becomes well known and people stop falling for it. Using cyber crime as an example because I am Nigerian (LOL), when people stopped falling for the destitute African Prince method, they changed to other methods like romance scams and blackmail. Criminals/Predators are always to seek new ways to catch their victims/prey which is the why the victims/prey must always be alert and aware of the criminals/predators methods so that they can protect themselves.
So yes, as long as men exist, they will be no feminist utopia where women and girls can exist without the threat of violence. We will always need to be on guard and strive to protect ourselves from them no matter the method they use.
Seperatism cannot save all women and girls in the world just like how crime prevention efforts in Ghana cannot save me in Nigeria and I shouldn't even be expecting it to because geography, language barrier, national laws, etc. What can be done is we adapt the methods used in Ghana to our local context and apply it to see results.
Seperatism is an elective individual and geographical community level action that has the potential to save all women and girls but nobody is kidnap unwilling people and hold them hostage.
And I know, someone is going to scream " VICTIM BLAMING" and to that I say, I don't care about being labelled a victim blamer. However, if you have another viable method for keeping women and girls safe, kindly put forward your idea so it can be evaluated. Please note if you suggest "educating men and boys", I will block you because I don't have the patience for that level of stupidity and delusion.
Sidenote:
I always wondered why allegedly smart women will "but child brides in Afghanistan" as a counter to female seperatism. The wins of feminism activism will always be limited by geography. There is no feminist activism that will impact the lives of ALL women and girls. An individual's or organisation's target population will be limited by geography and unfortunately by resources. You can't help everybody applies in feminism too.
Imagine if someone said that about abortion rights in the US. "Fighting for abortion in America doesn't help child brides in Afghanistan". Most people can see how ridiculous and frankly insulting it is to bring up that issue.
40 notes
·
View notes
Text
"Intelligence Bureau Result Declared: Here's How to Download Your Scorecard"
Established in 1887 during British colonial rule, the IB has evolved extensively over the a long time to become certainly one of India’s most crucial contraptions within the combat against terrorism, espionage, and threats to national solidarity.
intelligence bureau exam result date

Historical Background
The origins of the Intelligence Bureau hint lower back to British India when it was founded as the Indian Political Intelligence Office in London, later referred to as the Indian Political Intelligence (IPI). Its primary reason changed into to screen and counter anti-British sports among Indian revolutionaries overseas. In 1887, under Lord Dufferin, the then Viceroy of India, the IB became officially established in India to consolidate and centralize intelligence amassing in the country.
After India received independence in 1947, the IB was reorganized to serve the sovereign Republic of India. Over time, because the usa’s intelligence wishes multiplied, the Research and Analysis Wing (R&AW) was carved out of the IB in 1968 to handle external intelligence, whilst the IB continued to cognizance on domestic intelligence and inner safety.
Objectives and Functions
The Intelligence Bureau’s center capabilities center around collecting, processing, and analyzing intelligence related to national security. Its primary responsibilities encompass:
Security Clearance: The IB conducts historical past checks and safety verifications for appointments to touchy authorities positions, issuing protection clearances as needed.
Advisory Role: The bureau advises the significant and state governments on inner security matters and intelligence assessments.
Structure and Organization
The Intelligence Bureau operates beneath the Ministry of Home Affairs (MHA), Government of India. It is headed through a Director of Intelligence Bureau (DIB), a position generally held by a senior officer from the Indian Police Service (IPS), frequently with vast experience in protection and intelligence work.
The organizational shape of the IB is secretive and now not publicly disclosed in element because of national protection worries. However, it is regarded to have various specialized units focusing on unique domains, which includes:
Counter-Terrorism
Cyber Intelligence
Counter-Espionage
Communal Intelligence
Border Intelligence
Left-Wing Extremism (LWE) Monitoring
IB officers are published across the u . S . A ., which include in all most important towns and states, and they also liaise closely with nation police forces and vital paramilitary organizations. The corporation’s headquarters is located in New Delhi.
Recruitment and Training
Recruitment to the Intelligence Bureau happens through numerous channels:
Direct Recruitment: The Intelligence Bureau recruits Assistant Central Intelligence Officers (ACIOs) through aggressive tests carried out through the Ministry of Home Affairs.
Deputation: Senior officers from the Indian Police Service (IPS) and other central government offerings regularly be part of the IB on deputation.
Promotions: Internal promotions additionally play a giant role in staffing the organisation at better ranges.
Training for IB employees is rigorous and includes modules on surveillance, information analysis, interrogation strategies, language competencies, and cyber intelligence. Given the covert nature of the work, education also emphasizes discretion, psychological resilience, and adherence to the rule of law.
Operations and Achievements
Given the classified nature of the IB's paintings, many of its operations continue to be undisclosed. However, several excessive-profile instances have highlighted its effectiveness:
Terrorism Prevention: The IB has performed a key position in preempting several terror assaults, especially through early caution intelligence shared with safety forces.
Counter-Insurgency in Kashmir: The IB has been instrumental in intelligence gathering in Jammu and Kashmir, aiding in counter-insurgency operations and figuring out threats from throughout the border.
Neutralizing Maoist Insurgency: In states suffering from Left-Wing Extremism, such as Chhattisgarh, Jharkhand, and Odisha, the IB works carefully with kingdom police and paramilitary forces to dismantle Maoist networks.
Monitoring Radicalization: The organisation monitors the activities of radical organizations and social media to detect early symptoms of radicalization, specifically among children.
Tracking Foreign Spies: The IB has historically uncovered undercover agent rings operated through antagonistic countries, preventing sensitive statistics from being compromised.
Challenges and Criticism
Despite its contributions, the IB has now not been resistant to criticism and demanding situations:
Lack of Accountability: As the IB operates outside the purview of public scrutiny and parliamentary oversight, there were calls for extra transparency and duty mechanisms.
Political Misuse: Critics allege that the IB has once in a while been used by ruling governments to spy on political warring parties, main to ethical and legal questions.
Coordination Issues: Inter-organisation contention and shortage of seamless coordination among IB, R&AW, and state police forces can every now and then abate effective intelligence sharing.
Technological Upgradation: In an age of cyber struggle and AI-pushed espionage, the IB faces the assignment of continuously upgrading its technological talents to live in advance of adversaries.
Comparison with Other Agencies
Research and Analysis Wing (R&AW): Deals with external intelligence and operates underneath the Cabinet Secretariat.
Defense Intelligence Agency (DIA): Handles army-related intelligence.
Among these, the IB remains the maximum full-size for domestic intelligence and is often the primary to reply to inner threats.
Reforms and the Way Forward
To decorate the effectiveness of the Intelligence Bureau, several reforms had been recommended by means of professionals:
Parliamentary Oversight: Establishing a parliamentary committee to supervise intelligence operations may want to decorate transparency without compromising national protection.
Inter-Agency Integration: Improved cooperation and data-sharing between distinct intelligence and law enforcement our bodies could boom responsiveness.
Technological Modernization: Investments in AI, large facts analytics, and cybersecurity infrastructure are crucial for preserving up with rising threats.
Public Engagement: While secrecy is critical, there need to be a broader public understanding of the IB’s role in national safety to foster believe and cooperation.
Internal Security Monitoring: The IB video display units and counters threats to inner stability, including terrorism, insurgency, communal violence, and political unrest.
Counterintelligence: The bureau identifies and neutralizes espionage sports by way of overseas retailers running inside India.
Surveillance Operations: It conducts surveillance on individuals, organizations, or agencies suspected of activities towards the country.
Political Intelligence: Though debatable, the IB also gathers intelligence on political moves and sports which could have implications for national security.
2 notes
·
View notes
Text
AI as a Tool of Military Modernization: India and China’s Defense Strategies
Introduction: AI in Modern Warfare
Artificial Intelligence (AI) is becoming a pivotal force in shaping the future of warfare. Both India and China have recognized the strategic importance of AI in modernizing their military capabilities. However, their approaches to AI integration diverge in terms of scale, investment, and focus. While China is leveraging AI for global dominance with heavy emphasis on military-civilian fusion, India is cautiously advancing, focusing on strategic defense and autonomy.
Comparative Analysis of India and China’s Military AI Integration
1. Border Surveillance
AI-driven surveillance has transformed how nations monitor and secure their borders. For India, securing its northern borders, particularly in the volatile regions of Ladakh and Arunachal Pradesh, requires sophisticated surveillance systems. AI can help automate border monitoring using drones and ground-based sensors. India's development of AI-enabled UAVs, such as the Rustom-II and Ghatak UCAVs, demonstrates its focus on real-time surveillance, intelligence gathering, and precision strikes.
China, on the other hand, has rapidly advanced its border surveillance through AI. Its use of drones like the Caihong series and the WZ-8 hypersonic reconnaissance drone has given China a significant advantage. These unmanned systems, capable of high-altitude and long-range surveillance, provide Beijing with a strategic edge in monitoring the India-China border along the Line of Actual Control (LAC). Furthermore, China's integration of AI into border security reinforces its aim to dominate information warfare by creating an "informationized" battlefield.
2. Cyber Warfare Capabilities
In the realm of cyber warfare, China has developed a highly sophisticated network, which blends civilian and military cyber capabilities under its Strategic Support Force (SSF). China's cyber strategy includes offensive operations such as espionage, disrupting enemy networks, and stealing classified information. The integration of AI allows China to automate these cyber-espionage activities and increase the speed and efficiency of cyberattacks.
India, while lagging in this area, has made significant progress by establishing the Defence Cyber Agency in 2018. India's focus has primarily been on defensive operations, aiming to protect critical infrastructure and secure its networks. However, with growing cyber threats from adversaries like China, India must further develop AI-based cyber defense mechanisms and enhance its offensive cyber capabilities to deter potential attacks .
3. Autonomous Weaponry
Autonomous weaponry is one of the most significant areas where AI is transforming military arsenals. China has been a global leader in developing autonomous systems, such as drones and missile guidance systems. China's Academy of Military Science has been tasked with integrating AI into all aspects of warfare, focusing on autonomous drones, AI-driven missile systems, and robotic soldiers. The deployment of AI-guided cruise missiles and unmanned aerial vehicles (UAVs) is expected to reshape future combat scenarios, allowing for precision strikes and reduced human involvement in the battlefield.
India is still in the early stages of developing autonomous weaponry. Although India has started working on AI-driven drones and systems, it lacks the scale and speed of China’s developments. However, India’s commitment to creating an indigenous AI ecosystem, as seen in projects like the HAL Advanced Medium Combat Aircraft (AMCA), reflects its focus on autonomous systems for future air combat. The reliance on AI-enabled UAVs like the Harop drone shows India’s intent to integrate AI into its military strategies, but significant investments are needed to match China’s rapid advancements.
Conclusion: A Diverging Path to AI-Driven Military Power
India and China are both integrating AI into their military strategies, but their approaches reflect broader geopolitical goals. While China’s strategy is rooted in achieving technological supremacy and global military dominance, India’s efforts are more defensive, focused on autonomy and securing its borders. However, with China’s rapid advancements in AI-driven warfare, India must accelerate its investments in AI technology to ensure strategic parity. The future of conflict between these two nations may very well be determined by their success in harnessing AI for military modernization.
#AI in warfare#Military AI#India China military#AI and defense#Cyber warfare#Autonomous weapons#Border surveillance#AI in national security#China military AI#India defense strategy#AI drones#Cyber defense#AI modernization#Strategic defense#Information warfare#Unmanned aerial vehicles#AI weapons#AI military race#Technological supremacy#India China border conflict
0 notes