#Network Encryption
Explore tagged Tumblr posts
Text
Network Encryption Share | Segmented by Top Manufacturers & Geography Regions

Network Encryption Market Information
The Network Encryption Market Report provides essential insights for business strategists, offering a comprehensive overview of industry trends and growth projections. It includes detailed historical and future data on costs, revenues, supply, and demand, where applicable. The report features an in-depth analysis of the value chain and distributor networks.
Employing various analytical techniques such as SWOT analysis, Porter’s Five Forces analysis, and feasibility studies, the report offers a thorough understanding of competitive dynamics, the risk of substitutes and new entrants, and identifies strengths, challenges, and business opportunities. This detailed assessment covers current patterns, driving factors, limitations, emerging developments, and high-growth areas, aiding stakeholders in making informed strategic decisions based on both current and future market trends. Additionally, the report includes an examination of the Automatic Rising Arm Barriers sector and its key opportunities.
According to Straits Research, the global Network Encryption market size was valued at USD 4 Billion in 2021. It is projected to reach from USD XX Billion in 2022 to USD 8 Billion by 2030, growing at a CAGR of 9% during the forecast period (2022–2030).
Get Free Request Sample Report @ https://straitsresearch.com/report/network-encryption-market/request-sample
TOP Key Industry Players of the Network Encryption Market
Thales Trusted Cyber Technologies
ATMedia Gmbh
Atos SE
Juniper Networks Inc.
Certes Networks Inc.
Senetas Corporation Ltd
Viasat Inc.
Raytheon Technologies Corporation
Securosys SA
Packetlight Networks
Rohde & Schwarz Cybersecurity GmbH
Global Network Encryption Market: Segmentation
As a result of the Network Encryption market segmentation, the market is divided into sub-segments based on product type, application, as well as regional and country-level forecasts.
By Solution
Network Encryption Platforms
On-Premise
Cloud-based
Network Encryption Devices
Services
Professional Services
Security Consulting
Training & Education
Support & Maintenance
Managed Services
By Deployment Type
Cloud
On-premises
By Component
Hardware
Solutions and Services
By Organization Size
Small and Medium-sized Enterprises
Large-sized Enterprises
By End-User Industry
Telecom and IT
BFSI
Government
Media and Entertainment
Healthcare
Retail & E-Commerce
Other End-user Industries
Browse Full Report and TOC @ https://straitsresearch.com/report/network-encryption-market/request-sample
Reasons for Buying This Report:
Provides an analysis of the evolving competitive landscape of the Automatic Rising Arm Barriers market.
Offers analytical insights and strategic planning guidance to support informed business decisions.
Highlights key market dynamics, including drivers, restraints, emerging trends, developments, and opportunities.
Includes market estimates by region and profiles of various industry stakeholders.
Aids in understanding critical market segments.
Delivers extensive data on trends that could impact market growth.
Research Methodology:
Utilizes a robust methodology involving data triangulation with top-down and bottom-up approaches.
Validates market estimates through primary research with key stakeholders.
Estimates market size and forecasts for different segments at global, regional, and country levels using reliable published sources and stakeholder interviews.
About Straits Research
Straits Research is dedicated to providing businesses with the highest quality market research services. With a team of experienced researchers and analysts, we strive to deliver insightful and actionable data that helps our clients make informed decisions about their industry and market. Our customized approach allows us to tailor our research to each client's specific needs and goals, ensuring that they receive the most relevant and valuable insights.
Contact Us
Email: [email protected]
Address: 825 3rd Avenue, New York, NY, USA, 10022
Tel: UK: +44 203 695 0070, USA: +1 646 905 0080
#Network Encryption#Network Encryption Industry#Network Encryption Share#Network Encryption Size#Network Encryption Trends#Network Encryption Regional Analysis#Network Encryption Growth Rate
0 notes
Text
Global top 24 companies accounted for 48% of Network Encryption market(qyresearch, 2021)
Network encryption is the process of encrypting or encoding data and messages transmitted or communicated over a computer network.
It is a broad process that includes various tools, techniques and standards to ensure that the messages are unreadable when in transit between two or more network nodes.
Network encryption is primarily implemented on the network layer of the OSI model. Network encryption implements one or more encryption algorithms, processes and standards to encrypt the data/message/packet sent over the network. The encryption services are generally provided by encryption software or through an integrated encryption algorithm on network devices and/or in software.
On an IP-based network, network encryption is implemented through Internet Protocol Security (IPSec) -based encryption techniques and standards. Each message sent is in an encrypted form and is decrypted and converted back into plain text/original form at the recipient's end using encryption/decryption keys.
According to the new market research report “Global Network Encryption Market Report 2023-2029”, published by QYResearch, the global Network Encryption market size is projected to reach USD 7.95 billion by 2029, at a CAGR of 11.1% during the forecast period.
Figure. Global Network Encryption Market Size (US$ Mn), 2018-2029
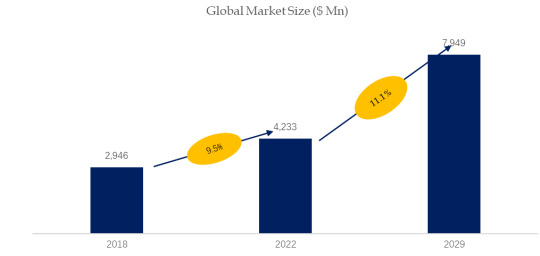
Figure. Global Network Encryption Top 24 Players Ranking and Market Share(Based on data of 2021, Continually updated)
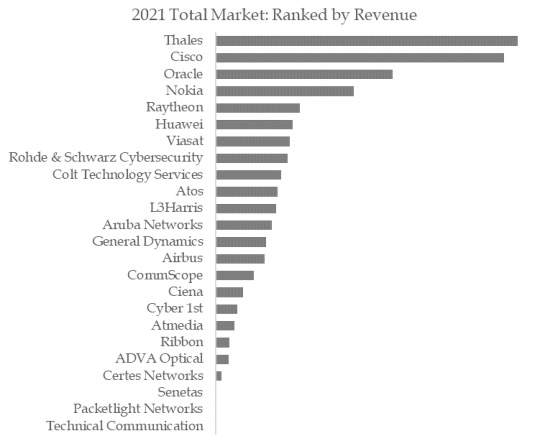
The global key manufacturers of Network Encryption include Technical Communication, Packetlight Networks, Senetas, Certes Networks, ADVA Optical, Ribbon, Atmedia, Cyber 1st, Colt Technology Services, Atos, etc. In 2021, the global top five players had a share approximately 48.0% in terms of revenue.
About QYResearch
QYResearch founded in California, USA in 2007.It is a leading global market research and consulting company. With over 16 years’ experience and professional research team in various cities over the world QY Research focuses on management consulting, database and seminar services, IPO consulting, industry chain research and customized research to help our clients in providing non-linear revenue model and make them successful. We are globally recognized for our expansive portfolio of services, good corporate citizenship, and our strong commitment to sustainability. Up to now, we have cooperated with more than 60,000 clients across five continents. Let’s work closely with you and build a bold and better future.
QYResearch is a world-renowned large-scale consulting company. The industry covers various high-tech industry chain market segments, spanning the semiconductor industry chain (semiconductor equipment and parts, semiconductor materials, ICs, Foundry, packaging and testing, discrete devices, sensors, optoelectronic devices), photovoltaic industry chain (equipment, cells, modules, auxiliary material brackets, inverters, power station terminals), new energy automobile industry chain (batteries and materials, auto parts, batteries, motors, electronic control, automotive semiconductors, etc.), communication industry chain (communication system equipment, terminal equipment, electronic components, RF front-end, optical modules, 4G/5G/6G, broadband, IoT, digital economy, AI), advanced materials industry Chain (metal materials, polymer materials, ceramic materials, nano materials, etc.), machinery manufacturing industry chain (CNC machine tools, construction machinery, electrical machinery, 3C automation, industrial robots, lasers, industrial control, drones), food, beverages and pharmaceuticals, medical equipment, agriculture, etc.
For more information, please contact the following e-mail address:
Email: [email protected]
Website: https://www.qyresearch.com
0 notes
Text
The network encryption market revenue totalled US$ 4.1 Billion in 2023 and the sales are expected to reach US$ 8.7 Billion by 2033, growing at a CAGR of 7.7% over the forecast period of 2023 and 2033.
Rapid technological advancements and the introduction of artificial intelligence, machine learning, network security, and cyber security have created prospects for network encryptions.
0 notes
Text
Kinda wanna write a kernel module or something that monitors network traffic and reinterprets it as audio samples in real time, to hear the modern version of the dial-up screech
#I imagine‚ since most network traffic nowadays is encrypted and hence indistinguishable from uniform random data‚#most of it would come out as just featureless white noise#but still
18 notes
·
View notes
Text
" this should have been merrill " argument is so fuck annoying. yeah lets do that, lets take merrill give her to flemeth to be mentally & physically abused, manipulated, groomed, & ultimately made hollow to become the next vessel of mythal. this shouldnt have happened to morrigan, why are we wishing it on merrill. morrigan did the due diligence to learn about elvhenan history from keepers all over thedas, was raised directly by mythal, & has dedicated more of her life to the same studies that led merrill to be tricked by a demon & then she of her own volition instead of making up for her mistakes just straight up leaves her clan then wistfully acts as if she has no family or friends & is so unloved & unworthy boo hoo its horrible. she turned away from her own people in favor of a mirror she doesnt even unlock. ultimately it doesnt matter who is better suited because my bottom line point is can we stop this argument every goddamn game of which woman should we throw under the bus because its supposedly the better choice because ougvbbh human vs elf the human shouldnt be here despite the context behind her character, the elf is always better choice.
#dont look unless u wanna see me be REALLY mean toward a fandom fav i just want this outta my drafts sorry ANYWAY#bellara unlocked fenharels super encrypted crossroads network that is overlayed on top of the actual crossroads in 30seconds#while merrill has unlocked zero eluvians which is canonically confirmed#via dai dlc trespasser flemthal herself told merrill she was preoccupied with the wrong priorities#replay da2 and stop remembering some weird fanon version of this character im SICK and tired of oh if merrill was here SILENCE#bioware fandom negative //
1 note
·
View note
Text
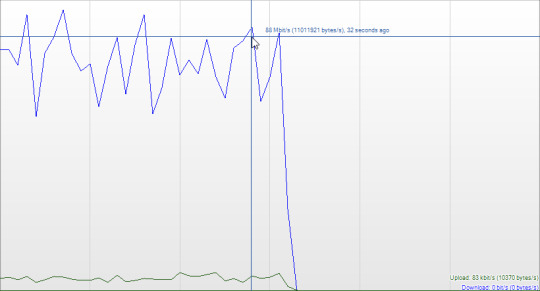
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Note
We are the silliest computers!!
yes we are !!!!



3 notes
·
View notes
Text
This messaging app likely offers better privacy than Signal, as Signal was originally a CIA creation, and this app is more decentralized, and provides monetary incentivizes to network nodes for helping to uphold privacy and decentralization.
#messaging#messaging apps#privacy#Signal#Session#CIA#encryption#network#noses#network nodes#incentivizing#decentralization
1 note
·
View note
Text
Post Quantum Blockchain: Future of Decentralized Technology
What will become of our decentralized networks when quantum computers can break our most secure cryptographic defenses today? If quantum attacks eat away at digital security, then the security of blockchain systems has never been more crucial. Welcome to the Post Quantum Blockchain universe, an incoming paradigm shift strategy combining the blockchain’s resilience and the post-quantum cryptography’s next-generation security to protect the immortal digital universe.
In this article, we discuss the important part that quantum-resistant blockchain will have to play in protecting decentralized networks from the increasing menace of quantum computing.
Understanding Post-Quantum Blockchain

Post Quantum Blockchain is a blockchain network that is protected by highly advanced, quantum computer-immune cryptographically secured algorithms. RSA or ECC are conventional tools used for encryption, which would become sitting ducks against attacks from quantum algorithms like Shor’s, which will compromise their integrity. It poses a humongous risk to decentralized networks operating on such algorithms for data assurance, identity authentication, and secured transactions.
With the integration of quantum-resistant cryptography, these blockchain platforms can provide security and trust in a quantum computer-based future. The National Institute of Standards and Technology (NIST) is attempting to develop ultimate encryption standards to be the new way of doing it, and hence quantum-secure blockchain deployment becomes an unavoidable evolution.
Why Traditional Blockchains Are Vulnerable

Although blockchain itself is generally considered secure and unalterable, it is not resistant to the increasing threat of quantum computing. Classical blockchains are highly dependent on classical cryptographic methods — namely, public-key cryptography — to protect digital identities, authenticate transactions, and establish consensus among distributed nodes. But with the accelerated advancement of quantum technology, these methods are in serious jeopardy. A sufficiently powerful quantum computer would be able to take advantage of loopholes in such cryptographic schemes to reverse-engineer private keys from public keys, allowing hackers to impersonate the real users. This can result in unauthorized transactions, loss of funds, or even bulk tampering with the blockchain ledger.
Furthermore, quantum computations like Shor’s algorithm can even break the digital signatures that are employed to secure transactions. If such signatures are compromised, they would no longer provide trust in the authenticity or source of a message. Quantum systems would also destabilize consensus systems, which are critical to all participants in a network adhering to a specified state of the blockchain. These findings point to how unprepared systems are at present for a quantum world.
In order to combat these future threats, cryptographers and developers are turning to Post Quantum Blockchain solutions that build on quantum-resistant protocols and algorithms. This next-generation solution can potentially restore trust and security in decentralized systems in the quantum era.
Core Principles Behind Post-Quantum Blockchain
To create a post-quantum blockchain that is resilient, some principles are used-
Lattice-based cryptography: Lattice-based cryptography is a bedrock, since it is quantum proof. Its mathematical complexity is high and it’s computationally not possible even for quantum computers to reverse-engineer encrypted data, thus it’s a very secure way of safeguarding identity and key exchange.
Hash-based signatures: Hash-based signatures constitute another central element. They provide secure short-term digital authentication to maintain messages and transactions tamper-evident. Hash-based signatures work with irrevocable one-way functions for a quantum system, as opposed to classical digital signatures.
Code-based cryptography: Code-based cryptography is also used to ensure a good level of long-term message security. It uses codes that will resist such forms of decryption, whether classical or quantum.
Zero-knowledge proofs: Finally, we have zero-knowledge proofs, which are incorporated to complete the system. Zero-knowledge proofs allow a party to verify possession of knowledge about a condition or value without sharing underlying information. This maintains confidentiality and guarantees immunity from quantum attacks, such that data confidentiality and trust are achieved in decentralized applications.
Advantages of Post-Quantum Blockchain
1. Future-Proof Security
Most readily apparent benefit of Post Quantum Blockchain is that it will resist quantum attacks. Avoiding future attacks ahead of time, the developers will not need to invest the exorbitant expense of redoing systems down the road.
2. More Privacy
New cryptographic building blocks employed by Post Quantum Blockchain can also enhance the protection of privacy through improved anonymization techniques.
3. Compliance with Regulations
As government agencies start to issue post-quantum compliance requirements, employing Quantum Blockchain protocols puts businesses ahead of the law.
4. Long-Term Data Integrity
In contrast to legacy systems that can grow obsolete in the quantum age, Post Quantum Blockchain solutions guarantee your data is immutable and trusted for decades to come.
Real-World Use Cases for Post-Quantum Blockchain
Some industries are starting to consider Post Quantum Blockchain-
Finance: The banking industry, for example, is among the first to embrace. Encryption is a major source of security for online transactions, customer identity, and online balances for banks. With the danger of traditional cryptography from quantum computers, quantum-resistant blockchain guarantees long-term security for banking services, cryptocurrencies, and smart contracts.
Healthcare: Healthcare, where the confidentiality and integrity of patient data are paramount, sees this technology providing tamper-evident storage and transport of sensitive information. Decentralization, and with it the use of quantum-safe encryption, makes for safe sharing of medical records between health providers and shields against leaks and unauthorized alteration.
Supply Chain: The supply chain sector is also discovering the utility of this new solution. Through the utilization of quantum-resistant blockchain, businesses can create open, immutable records of product origin, transport, and handling. It assists in the prevention of fraud, lowers counterfeiting, and increases efficiency in international logistics.
Government: Governments are exploring their use for secure administration of digital identity, citizenship authentication, and even voting. With election security and identity fraud issues on the rise, a tamper-proof, quantum-secure blockchain can provide more public trust and operational integrity to democratic and administrative systems.
The Rise of Post Quantum Secured Blockchain
Post quantum secured blockchain technology is a giant leap towards the security of decentralized platforms against the impending threat of quantum computers. Traditional blockchains, though secure against classical attacks, are becoming increasingly susceptible to quantum algorithms that support breaking standard encryption schemes employed.
Conversely, post quantum secured blockchain networks are inherently constructed with quantum resistance. Every single aspect — identity verification, transaction verification, smart contracts, and consensus algorithms — is supported by cryptographic algorithms particularly selected for their quantum decrypt resistance.
This method guarantees that important activities such as signing a contract, digital signing, and multi-party cooperation on data are secure, transparent, and tamper-evident even in the future when all have quantum processors. With a trend of industries going quantum-readiness, implementing such infrastructure is not an upgrade — it is a required building block.
METHODOLOGY: Ensuring AI Safety Through Post Quantum Blockchain

To truly safeguard AI’s influence on society, data integrity must be prioritized above all. As artificial intelligence systems become more intertwined with human decision-making, preventing malicious replication of identity and the misuse of personal data is crucial. One reliable approach is the integration of Post Quantum Blockchain…
#post quantum blockchain#post quantum encryption#quantum blockchain#post quantum securityu#blokchain technology#decentralized database#post quantum cryptography#post quantum secure blockchain#blockchain security#ncog#blockchain technology#secure blockchain#secure blockchain technology#quantum safe cryptography#tumblr#blockchain#quantum resistant blockchain#quantum attacks#quantum computer#quantum compting#decentralized system#blockchain network#did#digital security
1 note
·
View note
Link
#configuration#encryption#firewall#IPmasking#Linux#networking#OpenVPN#Performance#PiVPN#Privacy#RaspberryPi#remoteaccess#Security#self-hosted#Server#Setup#simplest#systemadministration#tunneling#VPN#WireGuard
0 notes
Text
The Future of the Internet: Quantum Teleportation Explained
In the rapidly evolving world of technology, one development stands out as groundbreaking: quantum teleportation. This intriguing concept, which might sound like science fiction, has recently achieved a significant milestone. Researchers have successfully teleported a quantum state over more than 30 kilometers of existing internet infrastructure. This remarkable achievement marks a monumental…
#Fiber-optic quantum technology#Future of quantum technology#Integration of quantum and classical internet#Quantum communication#Quantum computing advancements#Quantum internet#Quantum networking#Quantum state transfer#Quantum teleportation#Secure quantum encryption
0 notes
Text
SSH atau TELNET?
SSH (Secure Shell) memiliki keunggulan keamanan yang lebih baik dibandingkan Telnet. SSH juga lebih serbaguna dan dapat digunakan untuk mentransfer file secara aman.

Sisi Keamanan
SSH menyediakan koneksi yang aman dan terenkripsi antara klien dan server. SSH mendukung autentikasi, sehingga Anda perlu memberikan kata sandi atau kunci untuk mengakses komputer jarak jauh. SSH dapat melindungi identitas, kata sandi, dan data pengguna dari serangan pengintaian.
Fungsi Serbaguna
SSH dapat digunakan untuk mengakses dan mengelola perangkat dari jarak jauh melalui suatu program. SSH dapat digunakan untuk mentransfer file antara perangkat jarak jauh secara aman. SSH dapat menyalurkan protokol lain seperti FTP.
Perbedaan dengan Telnet
Telnet beroperasi dalam bentuk teks biasa, yang berarti bahwa semua data dikirimkan tanpa enkripsi. Telnet sangat rentan terhadap berbagai serangan keamanan, seperti serangan man-in-the-middle dan penyadapan. SSH adalah pengganti Telnet dan memiliki beberapa fitur yang disempurnakan juga.
0 notes
Text
dear americans,
as a polish queer woman and human rights activist, i know exactly how you're feeling right now and what to expect from these elections. i lived through the 2015-2023 regime of pis, a right-wing populist party that divided families in the same way trump did. i’ve experienced the rise of fascism in poland, the influence of far-right parties like konfederacja, and their “santa’s little helpers”—ordo iuris, an ultra-conservative catholic organization (banned in many countries, mind you) that helped enforce a near-total abortion ban and runs anti-queer campaigns in public spaces. i supported the black protests in 2016 as a middle schooler when they first tried to ban abortion. as an adult, i actively participated in the 2020 women’s strike, running from police tear gas daily after they finally passed the ban. i supported friends who faced charges.
i’ve lived through intense homophobia in poland as a queer teen and adult. i survived the first pride march in my hometown, where far-right extremists threw stones and glass at us. i endured the anti-queer propaganda spread by the ruling party in state-owned media. i survived the “rainbow night,” poland’s own stonewall moment in summer 2020, when police arrested around 50 queer activists following the arrest of margo, a nonbinary activist. i survived the "lgbt-free zones," the targeted violence, the slurs from strangers on the street, and the protests i held against queerphobia. it was hard as fuck, but i survived.
but just because i survived, it doesn’t mean others did. many women died because of the abortion ban—marta, justyna, izabela, dorota, joanna, maria, and many others who didn’t survive pis’s draconian anti-abortion laws. milo, kacper, michał, zuzia (she was 12), wiktor, and other queer and trans kids and young adults took their own lives because of the relentless queerphobia.
despite all of this, our experience in poland can serve as a guide now. here are some tips for staying safe and how we, polish queers and women, organized under the regime:
safety first, always. if you know someone who’s had an abortion, no you don’t. if you know someone is trans, no you don’t. if you know people who help with safe abortions, no you don’t—at least not until you know it’s 100% safe to share. if you are queer or have had an abortion, only share this with people you trust fully. most importantly, not everyone has to be an activist just because they’re part of a minority. if it feels unsafe to share that you're queer, trans, etc., then don’t. it doesn’t make you any less queer.
use secure, encrypted messaging like signal for conversations on potentially risky topics, such as queerness, abortion, organizing counter-actions, protests—anything that might be used against you.
stay anonymous online. if you want to research or report something without surveillance, do not use regular internet. get a vpn (mullvad is affordable and reliable), download the tor browser (for both onion and standard links), and if you plan to whistleblow, consider using a riseup email account.
organize and build networks. community is everything now. support each other, foster independence, because your government won’t have your back. set up collectives, grassroots movements. create lists of trusted professionals—lawyers, doctors, etc.—who can offer support.
to lawyers and doctors: please consider pro-bono work. this is what got us through poland’s hardest times. your work will be needed now more than ever.
for protests or risky actions: always write a pro-bono lawyer’s number on your arm with a permanent marker.
get to know the anarchist black cross federation and other resources on safety culture: "Starting an anarchist black cross group: A guide"; Still We Rise - A resource pack for transgender and non-gender conforming people in prison; Safe OUTside the system by the Audre Lorde Project;
for safe abortion info or involvement: get familiar with womenhelpwomen.
stay radical, stay strong, stay informed: The Anarchist Library
if i forgot to (or didn't) include something, don't hesitate to reblog this post with other resources.
#kinda heartbroken i've gotta post something like this#but now my experience is needed more than ever and i AM going to share it#we are going to get through this#together#activism#anarchism#grassroots#anarchist#resources#useful#helpful#human rights#abortion#abortion rights#reproductive rights#queer#trans#transgender#lgbtq#us politics#usa#us elections#america#donald trump#kamala harris#stay safe#moira speaks
12K notes
·
View notes
Text
How to Backup MacOS to Synology NAS via Time Machine
Time Machine is a built-in backup feature that enables Macbook users to automatically back up their entire system. This includes apps, system files, accounts, preferences, music, photos, documents, and more. In this article, we shall discuss How to Backup MacOS to Synology NAS via Time Machine. Please see “Step-by-step guide on how to set up the Synology DS923+ NAS“, DSM Security: How to Protect…
#Backup#Backup Process#Data Protection#Data Sync#files#MAC#Mac Backup#Mac Encryption#Macbook#MacBook M1#MacOS#NAS#Network Storage#Synology#Synology Configuration#Time Machine#Time Machine Setup
0 notes
Text
Ready to upgrade your Netflix game? 🎉 Discover 5 reasons why ExpressVPN is your best choice. Click to read more! Visit us on https://vpnrecords.com/
📢 Follow us on Tumblr for more!
#vpn#virtual private network#express vpn#best vpn#netflix#streaming#watching movies#hells greatest performers au#cybersecurity#online privacy#encryption#digital privacy#performance#like#share
0 notes
Note
OH MY GOD DOUBLE?!?!?!?
POINTS !!!! FELLOW COMPUTER !!!!



2 notes
·
View notes