#Openshift overview
Text
Overview of openshift online cluster in detail
OpenShift Online Cluster is a cloud-based platform for deploying and managing containerized applications. It is built on top of Kubernetes and provides a range of additional features and tools to help you develop, deploy, and manage your applications with ease.
Here is a more detailed overview of the key features of OpenShift Online Cluster:
Easy Deployment: OpenShift provides a web-based…

View On WordPress
#openshift openshift4 containerization redhatopenshift openshifttutorial openshiftonline Introduction to openshift online cluster#container platform#deploy openshift web application using openshift cli command line red hat openshift#Introduction to openshift online cluster#Login to openshift cluster in different ways openshift 4 red hat openshift#openshift#openshift 4#Openshift 4 container platform#Openshift architecture#openshift container platform#openshift docker#openshift enterprise#openshift for beginners#openshift online#openshift online account access openshift cluster openshift 4 red hat openshift#openshift online cluster#openshift online cluster admin#openshift online cluster overview of openshift cluster#openshift openshift 4 red hat openshift#Openshift overview#openshift tutorial#overview of openshift cluster#red container#red hat openshift#red hat openshift 4 container platform#red hat openshift clusters#red hat openshift container platform#redhat openshift online#web application openshift online#what is openshift online
0 notes
Text
Red Hat Openshift Virtualization Unlocks APEX Cloud Platform

Dell APEX Cloud Platform
With flexible storage and integrated virtualization, you may achieve operational simplicity.
In the quickly changing technological world of today, efficiency is hampered by complexity. The difficult task of overseeing complex systems, a variety of workloads, and the need to innovate while maintaining flawless operations falls on IT experts. Dell Technologies and Red Hat have developed robust new capabilities for Dell APEX Cloud Platform for Red Hat Openshift Virtualization that are assisting enterprises in streamlining their IT systems.
Openshift Virtualization
Utilize Integrated Virtualization to Simplify and Optimize
Many firms are reevaluating their virtualization strategy as the use of AI and containers picks up speed, along with upheavals in the virtualization industry. Red Hat OpenShift Virtualization, which offers a contemporary platform for enterprises to operate, deploy, and manage new and current virtual machine workloads together with containers and AI/ML workloads, is now included by default in APEX Cloud Platform for Red Hat OpenShift. Operations are streamlined by having everything managed on a single platform.
- Advertisement -Image Credit To Dell
APEX Cloud Platform
Adaptable Infrastructure for All Tasks
Having the appropriate infrastructure to handle your workload needs is essential for a successful virtualization strategy. An increased selection of storage choices is now available with APEX Cloud Platform for Red Hat OpenShift to accommodate any performance demands and preferred footprint. Block storage is needed by the APEX Cloud Platform Foundation Software, which offers all of the interface with Red Hat Openshift Virtualization.
For clients that want a smaller footprint, Dell have added PowerStore and Red Hat OpenShift Data Foundation to the list of block storage choices available from PowerFlex. In order to avoid making redundant expenditures, customers may use the PowerStore and PowerFlex appliances that are already in place.
Customers may easily connect to any of Their business storage solutions for additional storage to meet their block, file, and object demands. This is particularly crucial for the increasing amount of AI workloads that need PowerScale and ObjectScale’s file and object support.
Support for a range of NVIDIA GPUs and Intel 5th Generation Xeon Processors further increases this versatility and improves performance for your most demanding applications.
- Advertisement -
Continuity Throughout Your Red Hat OpenShift Estate
Red Hat OpenShift 4.14 and 4.16 support is now available in the APEX Cloud Platform, adding a new degree of uniformity to your Red Hat OpenShift estate along with features like CPU hot plug and the option to choose a single node for live migration to improve OpenShift Virtualization. This lessens the complexity often involved in maintaining numerous software versions, streamlining IT processes for increased productivity.
Red Hat Virtualization
Overview
Red Hat OpenShift includes Red Hat OpenShift Virtualization, an integrated platform that gives enterprises a contemporary way to run and manage their virtual machine (VM) workloads, both new and old. The system makes it simple to move and maintain conventional virtual machines to a reliable, dependable, and all-inclusive hybrid cloud application platform.
By using the speed and ease of a cloud-native application platform, OpenShift Virtualization provides a way to modernize infrastructure while maintaining the investments made in virtualization and adhering to contemporary management practices.
What advantages does Red Hat OpenShift virtualization offer?
Simple transfer: The Migration Toolkit for Virtualization that comes with Red Hat Openshift Virtualization makes it easy to move virtual machines (VMs) from different hypervisors. Even VMs can be moved to the cloud. Red Hat Services offers mentor-based advice along the route, including the Virtualization move Assessment, if you need practical assistance with your move.
Reduce the time to manufacture: Simplify application delivery and infrastructure with a platform that facilitates self-service choices and CI/CD pipeline interfaces. Developers may accelerate time to market by building, testing, and deploying workloads more quickly using Red Hat Openshift Virtualization.
Utilize a single platform to handle everything: One platform for virtual machines (VMs), containers, and serverless applications is provided by OpenShift Virtualization, simplifying operations. As a consequence, you may use a shared, uniform set of well-known corporate tools to manage all workloads and standardize the deployment of infrastructure.
A route towards modernizing infrastructure: Red Hat Openshift Virtualization allows you to operate virtual machines (VMs) that have been migrated from other platforms, allowing you to maximize your virtualization investments while using cloud-native architectures, faster operations and administration, and innovative development methodologies.
How does Red Hat OpenShift virtualization operate?
Included with every OpenShift subscription is Red Hat Openshift Virtualization. The same way they would for a containerized application, it allows infrastructure architects to design and add virtualized apps to their projects using OperatorHub.
With the help of simple, free migration tools, virtual machines already running on other platforms may be moved to the OpenShift application platform. On the same Red Hat OpenShift nodes, the resultant virtual machines will operate alongside containers.
Update your approach to virtualization
Virtualization managers need to adjust as companies adopt containerized systems and embrace digital transformation. Teams may benefit from infrastructure that enables VMs and containers to be managed by the same set of tools, on a single, unified platform, using Red Hat Openshift Virtualization.
Read more on govindhtech.com
#RedHatOpenshift#Virtualization#UnlocksAPEX#CloudPlatform#DellAPEXCloudPlatform#PowerStore#virtualmachineworkloads#RedHatOpenShift#news#Intel5thGenerationXeon#hybridcloud#technews#virtualmachines#VM#technology#cloud#dell#RedHatOpenshiftVirtualization#govindhtech
0 notes
Text
The Future of Container Platforms: Where is OpenShift Heading?
Introduction
The container landscape has evolved significantly over the past few years, and Red Hat OpenShift has been at the forefront of this transformation. As organizations increasingly adopt containerization to enhance their DevOps practices and streamline application deployment, it's crucial to stay informed about where platforms like OpenShift are heading. In this post, we'll explore the future developments and trends in OpenShift, providing insights into how it's shaping the future of container platforms.
The Evolution of OpenShift
Red Hat OpenShift has grown from a simple Platform-as-a-Service (PaaS) solution to a comprehensive Kubernetes-based container platform. Its robust features, such as integrated CI/CD pipelines, enhanced security, and scalability, have made it a preferred choice for enterprises. But what does the future hold for OpenShift?
Trends Shaping the Future of OpenShift
Serverless Architectures
OpenShift is poised to embrace serverless computing more deeply. With the rise of Function-as-a-Service (FaaS) models, OpenShift will likely integrate serverless capabilities, allowing developers to run code without managing underlying infrastructure.
AI and Machine Learning Integration
As AI and ML continue to dominate the tech landscape, OpenShift is expected to offer enhanced support for these workloads. This includes better integration with data science tools and frameworks, facilitating smoother deployment and scaling of AI/ML models.
Multi-Cloud and Hybrid Cloud Deployments
OpenShift's flexibility in supporting multi-cloud and hybrid cloud environments will become even more critical. Expect improvements in interoperability and management across different cloud providers, enabling seamless application deployment and management.
Enhanced Security Features
With increasing cyber threats, security remains a top priority. OpenShift will continue to strengthen its security features, including advanced monitoring, threat detection, and automated compliance checks, ensuring robust protection for containerized applications.
Edge Computing
The growth of IoT and edge computing will drive OpenShift towards better support for edge deployments. This includes lightweight versions of OpenShift that can run efficiently on edge devices, bringing computing power closer to data sources.
Key Developments to Watch
OpenShift Virtualization
Combining containers and virtual machines, OpenShift Virtualization allows organizations to modernize legacy applications while leveraging container benefits. This hybrid approach will gain traction, providing more flexibility in managing workloads.
Operator Framework Enhancements
Operators have simplified application management on Kubernetes. Future enhancements to the Operator Framework will make it even easier to deploy, manage, and scale applications on OpenShift.
Developer Experience Improvements
OpenShift aims to enhance the developer experience by integrating more tools and features that simplify the development process. This includes better IDE support, streamlined workflows, and improved debugging tools.
Latest Updates and Features in OpenShift [Version]
Introduction
Staying updated with the latest features in OpenShift is crucial for leveraging its full potential. In this section, we'll provide an overview of the new features introduced in the latest OpenShift release, highlighting how they can benefit your organization.
Key Features of OpenShift [Version]
Enhanced Developer Tools
The latest release introduces new and improved developer tools, including better support for popular IDEs, enhanced CI/CD pipelines, and integrated debugging capabilities. These tools streamline the development process, making it easier for developers to build, test, and deploy applications.
Advanced Security Features
Security enhancements in this release include improved vulnerability scanning, automated compliance checks, and enhanced encryption for data in transit and at rest. These features ensure that your containerized applications remain secure and compliant with industry standards.
Improved Performance and Scalability
The new release brings performance optimizations that reduce resource consumption and improve application response times. Additionally, scalability improvements make it easier to manage large-scale deployments, ensuring your applications can handle increased workloads.
Expanded Ecosystem Integration
OpenShift [Version] offers better integration with a wider range of third-party tools and services. This includes enhanced support for monitoring and logging tools, as well as improved interoperability with other cloud platforms, making it easier to build and manage multi-cloud environments.
User Experience Enhancements
The latest version focuses on improving the user experience with a more intuitive interface, streamlined workflows, and better documentation. These enhancements make it easier for both new and experienced users to navigate and utilize OpenShift effectively.
Conclusion
The future of Red Hat OpenShift is bright, with exciting developments and trends on the horizon. By staying informed about these trends and leveraging the new features in the latest OpenShift release, your organization can stay ahead in the rapidly evolving container landscape. Embrace these innovations to optimize your containerized workloads and drive your digital transformation efforts.
For more details click www.hawkstack.com
#redhatcourses#docker#linux#information technology#container#kubernetes#containerorchestration#containersecurity#dockerswarm#aws#openshift#redhatopenshift#hawkstack#hawkstack technologies
0 notes
Text
EX210: Red Hat OpenStack Training (CL110 & CL210)
In CL110, equips you to operate a secure, scalable RHOSP overcloud with OpenStack integration, enhancing troubleshooting skills. In CL210, gain expertise in scaling and managing Red Hat OpenStack environments, using the OpenStack Client for seamless day-to-day operations of enterprise cloud applications.
Overview of this Training | CL110 & CL210
Red Hat OpenStack Administration I | CL110 Training | KR Network Cloud
The course CL110, Red Hat OpenStack Administration I: Core Operations for Domain Operators, educates you on how to run and maintain a production-ready Red Hat OpenStack Platform (RHOSP) single-site overcloud. The skills that participants will gain include managing security privileges for the deployment of scalable cloud applications and building secure project environments for resource provisioning. Integration of OpenShift with load balancers, identity management, monitoring, proxies, and storage are all covered in the course. Participants will also improve their Day 2 operations and troubleshooting skills. Red Hat OpenStack Platform 16.1 is in keeping with this course.
Red Hat OpenStack Administration II | CL210 Training | KR Network Cloud
The course CL210, Red Hat OpenStack Administration II: Day 2 Operations for Cloud Operators, is designed for service administrators, automation engineers, and cloud operators who manage Red Hat OpenStack Platform hybrid and private cloud environments. Participants in the course will learn how to scale, manage, monitor, and troubleshoot an infrastructure built on the Red Hat OpenStack Platform. The main goal is to set up metrics, policies, and architecture using the OpenStack Client command-line interface so that enterprise cloud applications can be supported and day-to-day operations run smoothly.
For further information visit our Website: krnetworkcloud.org
0 notes
Text
Google Cloud transforms your business with top-notch AI, ML, and multicloud solutions. Experience global infrastructure, data cloud, and open cloud capabilities for smarter decisions. Visit the website for more insights.
body { margin: 0; padding: 20px; font-family: Arial, sans-serif; } h1, h2, h3, h4, h5, h6 { color: #333; } p { line-height: 1.5; margin-bottom: 20px; } a { color: #007BFF; text-decoration: none; } a:hover { text-decoration: underline; } section { margin-bottom: 40px; }
Accelerate Your Digital Transformation with Google Cloud
Overview
Google Cloud is a leading technology solution provider, offering a wide range of services to help businesses of all sizes accelerate their digital transformation. Whether you are just starting your journey or are well on your way, Google Cloud has the expertise and technology to help you solve your toughest challenges.
Learn more
Key Benefits
Top reasons businesses choose Google Cloud
Enterprise-ready AI
Run your apps wherever you need them with multicloud
Build on the same infrastructure as Google with global infrastructure
Make smarter decisions with unified data using Data Cloud
Scale with open, flexible technology with Open Cloud
Protect your users, data, and apps with robust security
Connect your teams with AI-powered apps for Productivity and collaboration
Reports and Insights
Curated C-suite perspectives in Executive insights
Read what industry analysts say about Google Cloud in Analyst reports
Browse and download popular whitepapers in Whitepapers
Explore case studies and videos in Customer stories
Solutions
Google Cloud offers a wide range of industry-specific solutions to address the specific needs and challenges of different sectors. Here are some of the key solutions:
Retail: Analytics and collaboration tools for the retail value chain
Consumer Packaged Goods: Solutions for CPG digital transformation and brand growth
Financial Services: Computing, data management, and analytics tools for financial services
Healthcare and Life Sciences: Advance research and empower healthcare innovation
Media and Entertainment: Solutions for content production and distribution operations
Telecommunications: Hybrid and multi-cloud services to deploy and monetize 5G
Games: AI-driven solutions to build and scale games faster
Manufacturing: Migration and AI tools to optimize the manufacturing value chain
Supply Chain and Logistics: Enable sustainable, efficient, and resilient data-driven operations
Government: Data storage, AI, and analytics solutions for government agencies
Education: Teaching tools to provide more engaging learning experiences
Application Modernization
Google Cloud provides comprehensive solutions for modernizing your business applications. Whether you need to assess, plan, implement, or measure software practices and capabilities, Google Cloud has you covered.
CAMP Program: Improve your software delivery capabilities using DORA
Modernize Traditional Applications: Analyze, categorize, and migrate traditional workloads to the cloud
Migrate from PaaS: Cloud Foundry, Openshift: Tools for moving your containers to Google's managed container services
Migrate from Mainframe: Automated tools and guidance for moving mainframe apps to the cloud
Modernize Software Delivery: Best practices for software supply chain, CI/CD, and S3C
DevOps Best Practices: Processes and resources for implementing DevOps in your organization
SRE Principles: Tools and resources for adopting Site Reliability Engineering in your organization
Day 2 Operations for GKE: Tools and guidance for effective Google Kubernetes Engine management
FinOps and Optimization of GKE: Best practices for running reliable and cost-effective applications on GKE
Run Applications at the Edge: Guidance for localized and low-latency apps on Google's edge solution
Architect for Multicloud: Manage workloads across multiple clouds with a consistent platform
Go Serverless: Fully managed environment for developing, deploying, and scaling apps
Artificial Intelligence
Add intelligence and efficiency to your business with Google Cloud's AI and machine learning solutions. Whether you are looking to implement conversational AI, document processing, or product recommendation, Google Cloud has the right tools for you.
Contact Center AI: AI model for speaking with customers and assisting human agents
Document AI: Automated document processing and data capture at scale
Product Discovery: Google-quality search and product recommendations for retailers
APIs and Applications
Speed up the pace of innovation without coding using Google Cloud's APIs, apps, and automation tools. Whether you want to attract new developers and partners, modernize legacy applications, or simplify open banking compliance, Google Cloud has you covered.
New Business Channels Using APIs: Attract and empower an ecosystem of developers and partners
Unlocking Legacy Applications Using APIs: Cloud services for extending and modernizing legacy apps
Open Banking APIx: Simplify and accelerate secure delivery of open banking compliant APIs
Databases
Migrate and manage enterprise data with security, reliability, high availability, and fully managed data services. Whether you are looking to simplify your database migration life cycle or run SQL Server virtual machines on Google Cloud, Google Cloud's database solutions have got you covered.
Database Migration: Guides and tools to simplify your database migration life cycle
Database Modernization: Upgrades to modernize your operational database infrastructure
Databases for Games: Build global live games with Google Cloud databases
Data Cloud
Unify data across your organization with Google Cloud's open and simplified approach to data-driven transformation. Whether you need to migrate and manage enterprise data, generate instant insights from data, or innovate and optimize your SaaS applications, Google Cloud has the data solutions you need.
Data Warehouse Modernization: Jumpstart your migration and unlock insights with data warehouse
Data Lake Modernization: Services for building and modernizing your data lake
Spark on Google Cloud: Run and write Spark where you need it, serverless and integrated
Smart Analytics: Generate instant insights from data at any scale with a serverless, fully managed analytics platform
Business Intelligence: Solutions for modernizing your BI stack and creating rich data experiences
Data Science: Put your data to work with Data Science on Google Cloud
Marketing Analytics: Solutions for collecting, analyzing, and activating customer data
Geospatial Analytics and AI: Solutions for building a more prosperous and sustainable business
Startups and SMB
Google Cloud offers tailored solutions and programs to accelerate startup and SMB growth. Whether you are a startup looking for proven technology or an SMB exploring solutions for web hosting, app development, AI, and analytics, Google Cloud has the right tools to fuel your growth.
Startup Solutions: Grow your startup and solve your toughest challenges using Google’s proven technology
Startup Program: Get financial, business, and technical support to take your startup to the next level
Small and Medium Business: Explore solutions for web hosting, app development, AI, and analytics
Software as a Service: Build better SaaS products, scale efficiently, and grow your business
Featured Products
Compute Engine: Virtual machines running in Google’s secure data center for increased flexibility
Cloud Storage: Secure, durable, and scalable object storage
BigQuery: Data warehouse for business agility and insights
Cloud Run: Fully managed environment for running containerized apps
Google Kubernetes Engine: Managed Kubernetes service for running containerized apps
Vertex AI: Unified platform for machine learning models and generative AI
Vertex AI Studio: Build, tune, and deploy foundation models on Vertex AI
Vertex AI Search and Conversation: Build generative AI apps for search and conversational AI
Apigee API Management: Manage the full life cycle of APIs with visibility and control
Cloud SQL: Relational database services for MySQL, PostgreSQL, and SQL Server
Cloud SDK: Command-line tools and libraries for Google Cloud
Cloud CDN: Content delivery network for delivering web and video
See all products
AI and Machine Learning
Vertex AI Platform: Unified platform for ML models and generative AI
Vertex AI Studio: Build, tune, and deploy foundation models on Vertex AI
Vertex AI Search and Conversation: Generative AI apps for search and conversational AI
Dialogflow: Lifelike conversational AI with virtual agents
Security
Security Analytics and Operations: Solution for analyzing petabytes of security telemetry
Web App and API Protection: Threat and fraud protection for your web applications and APIs
Security and Resilience Framework: Solutions for each phase of the security and resilience life cycle
Risk and compliance as code (RCaC): Solution to modernize your governance, risk, and compliance function with automation
Software Supply Chain Security: Solution for improving end-to-end software supply chain security
Security Foundation: Recommended products to help achieve a strong security posture
Smart Analytics
Data Warehouse Modernization: Jumpstart your migration and unlock insights with data warehouse
Data Lake Modernization: Services for building and modernizing your data lake
Spark on Google Cloud: Run and write Spark where you need it, serverless and integrated
Smart Analytics: Generate instant insights from data at any scale with a serverless, fully managed analytics platform
Business Intelligence: Solutions for modernizing your BI stack and creating rich data experiences
Data Science: Put your data to work with Data Science on Google Cloud
Marketing Analytics: Solutions for collecting, analyzing, and activating customer data
Geospatial Analytics and AI: Solutions for building a more prosperous and sustainable business
Datasets: Data Source: https://cloud.google.com/kubernetes-engine/docs/how-to/cluster-autoscaler&sa=U&ved=2ahUKEwi4p8uF6LSGAxUGEGIAHXy-COYQFnoECAEQAw&usg=AOvVaw3TCeRPJFwEWgadT3N9Z0Eu
0 notes
Text
In an OpenShift or OKD Kubernetes Cluster, the ClusterVersion custom resource holds important high-level information about your cluster. This information include cluster version, update channels and status of the cluster operators. In this article I’ll demonstrate how Cluster Administrator can check cluster version as well as the status of operators in OpenShift / OKD Cluster.
Check Cluster Version in OpenShift / OKD
You can easily retrieve the cluster version from the CLI using oc command to verify that it is running the desired version, and also to ensure that the cluster uses the right subscription channel.
# Red Hat OpenShift
$ oc get clusterversion
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS
version 4.8.10 True False 10d Cluster version is 4.8.10
# OKD Cluster
$ oc get clusterversion
NAME VERSION AVAILABLE PROGRESSING SINCE STATUS
version 4.7.0-0.okd-2021-05-22-050008 True False 66d Cluster version is 4.7.0-0.okd-2021-05-22-050008
To obtain more detailed information about the cluster status run the oc describe clusterversion command:
$ oc describe clusterversion
...output omitted...
Spec:
Channel: fast-4.8
Cluster ID: f3dc42b3-aeec-4f4c-780f-8a04d6951595
Desired Update:
Force: false
Image: quay.io/openshift-release-dev/ocp-release@sha256:53576e4df71a5f00f77718f25aec6ac7946eaaab998d99d3e3f03fcb403364db
Version: 4.8.10
Status:
Available Updates:
Channels:
candidate-4.8
candidate-4.9
fast-4.8
Image: quay.io/openshift-release-dev/ocp-release@sha256:c3af995af7ee85e88c43c943e0a64c7066d90e77fafdabc7b22a095e4ea3c25a
URL: https://access.redhat.com/errata/RHBA-2021:3511
Version: 4.8.12
Channels:
candidate-4.8
candidate-4.9
fast-4.8
stable-4.8
Image: quay.io/openshift-release-dev/ocp-release@sha256:26f9da8c2567ddf15f917515008563db8b3c9e43120d3d22f9d00a16b0eb9b97
URL: https://access.redhat.com/errata/RHBA-2021:3429
Version: 4.8.11
...output omitted...
Where:
Channel: fast-4.8 – Displays the version of the cluster the channel being used.
Cluster ID: f3dc42b3-aeec-4f4c-780f-8a04d6951595 – Displays the unique identifier for the cluster
Available Updates: Displays the updates available and channels
Review OpenShift / OKD Cluster Operators
OpenShift Container Platform / OKD cluster operators are top level operators that manage the cluster. Cluster operators are responsible for the main components, such as web console, storage, API server, SDN e.t.c.
All the information relating to cluster operators is accessible through the ClusterOperator resource. It allows
you to access the overview of all cluster operators, or detailed information on a given operator.
To retrieve the list of all cluster operators, run the following command:
$ oc get clusteroperators
NAME VERSION AVAILABLE PROGRESSING DEGRADED SINCE
authentication 4.8.10 True False False 2d14h
baremetal 4.8.10 True False False 35d
cloud-credential 4.8.10 True False False 35d
cluster-autoscaler 4.8.10 True False False 35d
config-operator 4.8.10 True False False 35d
console 4.8.10 True False False 10d
csi-snapshot-controller 4.8.10 True False False 35d
dns 4.8.10 True False False 35d
etcd 4.8.10 True False False 35d
image-registry 4.8.10 True False False 35d
ingress 4.8.10 True False False 35d
insights 4.8.10 True False False 35d
kube-apiserver 4.8.10 True False False 35d
kube-controller-manager 4.8.10 True False False 35d
kube-scheduler 4.8.10 True False False 35d
kube-storage-version-migrator 4.8.10 True False False 10d
machine-api 4.8.10 True False False 35d
machine-approver 4.8.10 True False False 35d
machine-config 4.8.10 True False False 35d
marketplace 4.8.10 True False False 35d
monitoring 4.8.10 True False False 3d5h
network 4.8.10 True False False 35d
node-tuning 4.8.10 True False False 10d
openshift-apiserver 4.8.10 True False False 12d
openshift-controller-manager 4.8.10 True False False 34d
openshift-samples 4.8.10 True False False 10d
operator-lifecycle-manager 4.8.10 True False False 35d
operator-lifecycle-manager-catalog 4.8.10 True False False 35d
operator-lifecycle-manager-packageserver 4.8.10 True False False 18d
service-ca 4.8.10 True False False 35d
storage 4.8.10 True False False 35d
Key Columns in the ouptut:
NAME – Indicates the name of the operator.
AVAILABLE – Indicates operator state if successfully deployed or has issues. TRUE means the operator is deployed successfully and is available for use in the cluster. The degraded state means the current state does not match its desired state over a period of time.
PROGRESSING – Indicates whether an operator is being updated to a newer version by the cluster version operator. True means update in pending completion.
DEGRADED – This entry returns the health of the operator. True means the operator encounters an error that prevents it from working properly.
You can limit the output to a single operator:
$ oc get co authentication
NAME VERSION AVAILABLE PROGRESSING DEGRADED SINCE
authentication 4.8.10 True False False 2d14h
To get more information about an operator use:
$ oc describe clusteroperators
Example:
$ oc describe co authentication
If you’re in a process of upgrading your OpenShift / OKD cluster from one minor version to another, we have a guide dedicated to upgrade shared in the link below:
How To Upgrade OpenShift / OKD Cluster Minor Version
0 notes
Text
Citrix xenapp 6.5 policy not applying

This document does not replace comprehensive product documentation about XenApp and XenDesktop policies. The intended audience for this document is an advanced Citrix administrator who is familiar with HDX concepts, policy templates, and previous versions of the product. We’ve also provided planning guidance to help you determine the right settings for a given use case.

This document provides design considerations when you use these templates to create policies. XenApp and XenDesktop includes HDX policy templates that simplify deployment to users.

Latency and SQL Blocking Query Improvements in XenApp and XenDesktopĮxtending the Life of Your Legacy Web Applications by Using Citrix Secure BrowserĬitrix Universal Print Server load balancing in XenApp and XenDesktop 7.9Īctive Directory OU-based Controller discovery Group Policy management template updates for XenApp and XenDesktop HDX Policy Templates for XenApp and XenDesktop 7.6 to the Current Version

Use Citrix ADM to Troubleshoot Citrix Cloud Native Networkingĭeployment Guide Citrix ADC VPX on Azure - Autoscaleĭeployment Guide Citrix ADC VPX on Azure - GSLBĭeployment Guide Citrix ADC VPX on Azure - Disaster Recoveryĭeployment Guide Citrix ADC VPX on AWS - GSLBĭeployment Guide Citrix ADC VPX on AWS - Autoscaleĭeployment Guide Citrix ADC VPX on AWS - Disaster RecoveryĬitrix ADC and OpenShift 4 Solution BriefĬreating a VPX Amazon Machine Image (AMI) in SC2SĬonnecting to Citrix Infrastructure via RDP through a Linux Bastion Host in AWSĬitrix ADC for Azure DNS Private Zone Deployment GuideĬitrix Federated Authentication Service Logon Evidence Overview VRD Use Case Using Citrix ADC Dynamic Routing with KubernetesĬitrix Cloud Native Networking for Red Hat OpenShift 3.11 Validated Reference DesignĬitrix ADC CPX, Citrix Ingress Controller, and Application Delivery Management on Google CloudĬitrix ADC Pooled Capacity Validated Reference DesignĬitrix ADC CPX in Kubernetes with Diamanti and Nirmata Validated Reference DesignĬitrix ADC SSL Profiles Validated Reference DesignĬitrix ADC and Amazon Web Services Validated Reference DesignĬitrix ADC Admin Partitions Validated Reference DesignĬitrix Gateway SaaS and O365 Cloud Validated Reference DesignĬitrix Gateway Service SSO with Access Control Validated Reference DesignĬonvert Citrix ADC Perpetual Licenses to the Pooled Capacity Model Service Migration to Citrix ADC using Routes in OpenShift Validated Reference Design

1 note
·
View note
Text
IBM C1000-143 Practice Test Questions
Now you can pass C1000-143 IBM Cloud Pak for Watson AIOps v3.2 Administrator exam with ease. PassQuestion provides you a number of C1000-143 Practice Test Questions, exactly on the pattern of the actual exam. They are not only helpful for the exam candidates to evaluate their level of preparation but also provide them the opportunity to enhance their weaknesses well in time. The C1000-143 Practice Test Questions include the latest questions and answers which help you in clearing all of your doubts of the IBM C1000-143 exam. With the help of the C1000-143 practice test questions, you will be able to feel the real exam scenario and pass your exam successfully on your first attempt.
IBM Cloud Pak for Watson AIOps v3.2 Administrator
An IBM Certified Administrator on IBM Cloud Pak for Watson AIOps v3.2 is a system administrator who has extensive knowledge and experience on IBM Cloud Pak for Watson AIOps v3.2 including AI Manager, Event Manager and Metric Manager. This administrator can perform the intermediate tasks related to planning, sizing, installation, daily management and operation, security, performance, configuration of enhancements (including fix packs and patches), customization and/or problem determination.
Exam Information
Exam Code: C1000-143
Exam Name: IBM Cloud Pak for Watson AIOps v3.2 Administrator
Number of questions: 65
Number of questions to pass: 46
Time allowed: 90 minutes
Languages: English
Price: $200 USD
Certification: IBM Certified Administrator - Cloud Pak for Watson AIOps v3.2
Exam Sections
Section 1: IBM Cloud Pak for Watson AIOps Overview 11%
Section 2: Install the IBM Cloud Pak for Watson AIOps 17%
Section 3: Configuration 30%
Section 4: Operate the Platform 22%
Section 5: Manage User Access Control 8%
Section 6: Troubleshoot 12%
View Online IBM Cloud Pak for Watson AIOps v3.2 Administrator C1000-143 Free Questions
Which collection of key features describes Al Manager?
A.Al data tools and connections and Metric Manager
B.Al data tools and connections and infrastructure automation
C.Al models and Chat Ops
D.Network management and service and topology management
Answer: C
In Event Manager, which event groupings usually occur within a short time of each other?
A.Scope-based
B.Seasonal
C.Temporal
D.Topology
Answer: C
When a user logs on to any of the components on a Cloud Pak for Watson AlOps deployed cluster and it is too slow or times out, what can be done to resolve the issue?
A.Update the Idap-proxy-config ConfigMap and set the LDAP_RECURSIVE_SEARCH to "false".
B.Update the platform-auth-idp ConfigMap and set the LDAP_TIMEOUT to a higher value.
C.Update the Idap-proxy-config ConfigMap and set the LDAP_TiMEOUT to a higher value.
D.Update the platform-auth-idp ConfigMap and set the LDAP_RECURSIVE_SEARCH to "false"
Answer: A
When installing Al manager or Event Manager in an air-gapped environment, which registry must the OpenShift cluster be connected to in order to pull images?
A.Docker V2 compatible registry running behind
B.quay.io
C.Red Hat OpenShift internal registry
D.docker.io
Answer: C
For Al Manager, which type of ChatOps channel surfaces stories?
A.Reactive
B.Proactive
C.Public
D.Private
Answer: A
What are two valid Runbook types in Event Manager?
A.Partial
B.Semi-automated
C.Initial
D.Fully-automated
E.Locked-partial
Answer: C, D
0 notes
Text
Introduction to Openshift - Introduction to Openshift online cluster
Introduction to Openshift – Introduction to Openshift online cluster
OpenShift is a platform-as-a-service (PaaS) offering from Red Hat. It provides a cloud-like environment for deploying, managing, and scaling applications in a secure and efficient manner. OpenShift uses containers to package and deploy applications, and it provides built-in tools for continuous integration, continuous delivery,…
View On WordPress
#openshift openshift4 openshiftIntroduction openshifttutorial openshiftContainer introduction to openshift online cluster#introduction redhatopenshift containerization introduction to openshift#introduction to openshift#introduction to openshift container platform#introduction to openshift redhat#openshift 4#openshift 4 installation#openshift container platform#openshift online#Openshift overview#Overview of openshift#overview of openshift cluster#red hat introduction to openshift#red hat openshift#what is openshift#what is openshift online
0 notes
Text
IBM Cloud Mastery: Banking App Deployment Insights

Hybrid cloud banking application deployment best practices for IBM Cloud and Satellite security and compliance
Financial services clients want to update their apps. Modernizing code development and maintenance (helping with scarce skills and allowing innovation and new technologies required by end users) and improving deployment and operations with agile and DevSecOps are examples.
Clients want flexibility to choose the best “fit for purpose” deployment location for their applications during modernization. This can happen in any Hybrid Cloud environment (on premises, private cloud, public cloud, or edge). IBM Cloud Satellite meets this need by letting modern, cloud-native applications run anywhere the client wants while maintaining a consistent control plane for hybrid cloud application administration.
In addition, many financial services applications support regulated workloads that require strict security and compliance, including Zero Trust protection. IBM Cloud for Financial Services meets that need by providing an end-to-end security and compliance framework for hybrid cloud application implementation and modernization.
This paper shows how to deploy a banking application on IBM Cloud for Financial Services and Satellite using automated CI/CD/CC pipelines consistently. This requires strict security and compliance throughout build and deployment.
Introduction to ideas and products
Financial services companies use IBM Cloud for Financial Services for security and compliance. It uses industry standards like NIST 800-53 and the expertise of over 100 Financial Services Cloud Council clients. It provides a control framework that can be easily implemented using Reference Architectures, Validated Cloud Services, ISVs, and the highest encryption and CC across the hybrid cloud.
True hybrid cloud experience with IBM Cloud Satellite. Satellite lets workloads run anywhere securely. One pane of glass lets you see all resources on one dashboard. They have developed robust DevSecOps toolchains to build applications, deploy them to satellite locations securely and consistently, and monitor the environment using best practices.
This project used a Kubernetes– and microservices-modernized loan origination application. The bank application uses a BIAN-based ecosystem of partner applications to provide this service.
Application overview
The BIAN Coreless 2.0 loan origination application was used in this project. A customer gets a personalized loan through a secure bank online channel. A BIAN-based ecosystem of partner applications runs on IBM Cloud for Financial Services.
BIAN Coreless Initiative lets financial institutions choose the best partners to quickly launch new services using BIAN architectures. Each BIAN Service Domain component is a microservice deployed on an IBM Cloud OCP cluster.
BIAN Service Domain-based App Components
Product Directory: Complete list of bank products and services.
Consumer Loan: Fulfills consumer loans. This includes loan facility setup and scheduled and ad-hoc product processing.
Customer Offer Process/API: Manages new and existing customer product offers.
Party Routing Profile: This small profile of key indicators is used during customer interactions to help route, service, and fulfill products/services.
Process overview of deployment
An agile DevSecOps workflow completed hybrid cloud deployments. DevSecOps workflows emphasize frequent, reliable software delivery. DevOps teams can write code, integrate it, run tests, deliver releases, and deploy changes collaboratively and in real time while maintaining security and compliance using the iterative methodology.
A secure landing zone cluster deployed IBM Cloud for Financial Services, and policy as code automates infrastructure deployment. Applications have many parts. On a RedHat OpenShift Cluster, each component had its own CI, CD, and CC pipeline. Satellite deployment required reusing CI/CC pipelines and creating a CD pipeline.
Continuous integration
IBM Cloud components had separate CI pipelines. CI toolchains recommend procedures and approaches. A static code scanner checks the application repository for secrets in the source code and vulnerable packages used as dependencies. For each Git commit, a container image is created and tagged with the build number, timestamp, and commit ID. This system tags images for traceability. Before creating the image, Dockerfile is tested. A private image registry stores the created image.
The target cluster deployment’s access privileges are automatically configured using revokeable API tokens. The container image is scanned for vulnerabilities. A Docker signature is applied after completion. Adding an image tag updates the deployment record immediately. A cluster’s explicit namespace isolates deployments. Any code merged into the specified Git branch for Kubernetes deployment is automatically constructed, verified, and implemented.
An inventory repository stores docker image details, as explained in this blog’s Continuous Deployment section. Even during pipeline runs, evidence is collected. This evidence shows toolchain tasks like vulnerability scans and unit tests. This evidence is stored in a git repository and a cloud object storage bucket for auditing.
They reused the IBM Cloud CI toolchains for the Satellite deployment. Rebuilding CI pipelines for the new deployment was unnecessary because the application remained unchanged.
Continuous deployment
The inventory is the source of truth for what artifacts are deployed in what environment/region. Git branches represent environments, and a GitOps-based promotion pipeline updates environments. The inventory previously hosted deployment files, which are YAML Kubernetes resource files that describe each component. These deployment files would contain the correct namespace descriptors and the latest Docker image for each component.
This method was difficult for several reasons. For applications, changing so many image tag values and namespaces with YAML replacement tools like YQ was crude and complicated. Satellite uses direct upload, with each YAML file counted as a “version”. A version for the entire application, not just one component or microservice, is preferred.
Thet switched to a Helm chart deployment process because they wanted a change. Namespaces and image tags could be parametrized and injected at deployment time. Using these variables simplifies YAML file parsing for a given value. Helm charts were created separately and stored in the same container registry as BIAN images. They are creating a CI pipeline to lint, package, sign, and store helm charts for verification at deployment time. To create the chart, these steps are done manually.
Helm charts work best with a direct connection to a Kubernetes or OpenShift cluster, which Satellite cannot provide. To fix this, That use the “helm template” to format the chart and pass the YAML file to the Satellite upload function. This function creates an application YAML configuration version using the IBM Cloud Satellite CLI. They can’t use Helm’s helpful features like rolling back chart versions or testing the application’s functionality.
Constant Compliance
The CC pipeline helps scan deployed artifacts and repositories continuously. This is useful for finding newly reported vulnerabilities discovered after application deployment. Snyk and the CVE Program track new vulnerabilities using their latest definitions. To find secrets in application source code and vulnerabilities in application dependencies, the CC toolchain runs a static code scanner on application repositories at user-defined intervals.
The pipeline checks container images for vulnerabilities. Due dates are assigned to incident issues found during scans or updates. At the end of each run, IBM Cloud Object Storage stores scan summary evidence.
DevOps Insights helps track issues and application security. This tool includes metrics from previous toolchain runs for continuous integration, deployment, and compliance. Any scan or test result is uploaded to that system, so you can track your security progression.
For highly regulated industries like financial services that want to protect customer and application data, cloud CC is crucial. This process used to be difficult and manual, putting organizations at risk. However, IBM Cloud Security and Compliance Center can add daily, automatic compliance checks to your development lifecycle to reduce this risk. These checks include DevSecOps toolchain security and compliance assessments.
IBM developed best practices to help teams implement hybrid cloud solutions for IBM Cloud for Financial Services and IBM Cloud Satellite based on this project and others:
Continuous Integration
Share scripts for similar applications in different toolchains. These instructions determine your CI toolchain’s behavior. NodeJS applications have a similar build process, so keeping a scripting library in a separate repository that toolchains can use makes sense. This ensures CI consistency, reuse, and maintainability.
Using triggers, CI toolchains can be reused for similar applications by specifying the application to be built, where the code is, and other customizations.
Continuous deployment
Multi-component applications should use a single inventory and deployment toolchain to deploy all components. This reduces repetition. Kubernetes YAML deployment files use the same deployment mechanism, so it’s more logical to iterate over each rather than maintain multiple CD toolchains that do the same thing. Maintainability has improved, and application deployment is easier. You can still deploy microservices using triggers.
Use Helm charts for complex multi-component applications. The BIAN project used Helm to simplify deployment. Kubernetes files are written in YAML, making bash-based text parsers difficult if multiple values need to be customized at deployment. Helm simplifies this with variables, which improve value substitution. Helm also offers whole-application versioning, chart versioning, registry storage of deployment configuration, and failure rollback. Satellite configuration versioning handles rollback issues on Satellite-specific deployments.
Constant Compliance
IBM strongly recommend installing CC toolchains in your infrastructure to scan code and artifacts for newly exposed vulnerabilities. Nightly scans or other schedules depending on your application and security needs are typical. Use DevOps Insights to track issues and application security.
They also recommend automating security with the Security and Compliance Center (SCC). The pipelines’ evidence summary can be uploaded to the SCC, where each entry is treated as a “fact” about a toolchain task like a vulnerability scan, unit test, or others. To ensure toolchain best practices are followed, the SCC will validate the evidence.
Inventory
With continuous deployment, it’s best to store microservice details and Kubernetes deployment files in a single application inventory. This creates a single source of truth for deployment status; maintaining environments across multiple inventory repositories can quickly become cumbersome.
Evidence
Evidence repositories should be treated differently than inventories. One evidence repository per component is best because combining them can make managing the evidence overwhelming. Finding specific evidence in a component-specific repository is much easier. A single deployment toolchain-sourced evidence locker is acceptable for deployment.
Cloud object storage buckets and the default git repository are recommended for evidence storage. Because COS buckets can be configured to be immutable, They can securely store evidence without tampering, which is crucial for audit trails.
Read more on Govindhtech.com
#IBM#BankingApp#IBMCloud#Satellite#security#Financialservices#Kubernetes#BIANService#SecurityComplianceCenter#OpenShift#technews#technology#govindhtech
0 notes
Text
Getting Started with OpenShift: Environment Setup
OpenShift is a powerful Kubernetes-based platform that allows you to develop, deploy, and manage containerized applications. This guide will walk you through setting up an OpenShift environment on different platforms, including your local machine and various cloud services.
Table of Contents
1. [Prerequisites]
2. [Setting Up OpenShift on a Local Machine](#setting-up-openshift-on-a-local-machine)
- [Minishift]
- [CodeReady Containers]
3. [Setting Up OpenShift on the Cloud]
- [Red Hat OpenShift on AWS]
- [Red Hat OpenShift on Azure]
- [Red Hat OpenShift on Google Cloud Platform]
4. [Common Troubleshooting Tips]
5. [Conclusion]
Prerequisites
Before you begin, ensure you have the following prerequisites in place:
- A computer with a modern operating system (Windows, macOS, or Linux).
- Sufficient memory and CPU resources (at least 8GB RAM and 4 CPUs recommended).
- Admin/root access to your machine.
- Basic understanding of containerization and Kubernetes concepts.
Setting Up OpenShift on a Local Machine
Minishift
Minishift is a tool that helps you run OpenShift locally by launching a single-node OpenShift cluster inside a virtual machine.
Step-by-Step Guide
1. Install Dependencies
- VirtualBox: Download and install VirtualBox from [here](https://www.virtualbox.org/).
- Minishift: Download Minishift from the [official release page](https://github.com/minishift/minishift/releases) and add it to your PATH.
2. Start Minishift
Open a terminal and start Minishift:
```sh
minishift start
```
3. Access OpenShift Console
Once Minishift is running, you can access the OpenShift console at `https://192.168.99.100:8443/console` (the IP might vary, check your terminal output for the exact address).

CodeReady Containers
CodeReady Containers (CRC) provides a minimal, preconfigured OpenShift cluster on your local machine, optimized for testing and development.
Step-by-Step Guide
1. Install CRC
- Download CRC from the [Red Hat Developers website](https://developers.redhat.com/products/codeready-containers/overview).
- Install CRC and add it to your PATH.
2. Set Up CRC
- Run the setup command:
```sh
crc setup
```
3. Start CRC
- Start the CRC instance:
```sh
crc start
```
4. Access OpenShift Console
Access the OpenShift web console at the URL provided in the terminal output.

Setting Up OpenShift on the Cloud
Red Hat OpenShift on AWS
Red Hat OpenShift on AWS (ROSA) provides a fully-managed OpenShift service.
Step-by-Step Guide
1. Sign Up for ROSA
- Create a Red Hat account and AWS account if you don't have them.
- Log in to the [Red Hat OpenShift Console](https://cloud.redhat.com/openshift) and navigate to the AWS section.
2. Create a Cluster
- Follow the on-screen instructions to create a new OpenShift cluster on AWS.
3. Access the Cluster
- Once the cluster is up and running, access the OpenShift web console via the provided URL.

Red Hat OpenShift on Azure
Red Hat OpenShift on Azure (ARO) offers a managed OpenShift service integrated with Azure.
Step-by-Step Guide
1. Sign Up for ARO
- Ensure you have a Red Hat and Azure account.
- Navigate to the Azure portal and search for Red Hat OpenShift.
2. Create a Cluster
- Follow the wizard to set up a new OpenShift cluster.
3. Access the Cluster
- Use the URL provided to access the OpenShift web console.

Red Hat OpenShift on Google Cloud Platform
OpenShift on Google Cloud Platform (GCP) allows you to deploy OpenShift clusters managed by Red Hat on GCP infrastructure.
Step-by-Step Guide
1. Sign Up for OpenShift on GCP
- Set up a Red Hat and Google Cloud account.
- Go to the OpenShift on GCP section on the Red Hat OpenShift Console.
2. Create a Cluster
- Follow the instructions to deploy a new cluster on GCP.
3. Access the Cluster
- Access the OpenShift web console using the provided URL.

Common Troubleshooting Tips
- Networking Issues: Ensure that your firewall allows traffic on necessary ports (e.g., 8443 for the web console).
- Resource Limits: Check that your local machine or cloud instance has sufficient resources.
- Logs and Diagnostics: Use `oc logs` and `oc adm diagnostics` commands to troubleshoot issues.
Conclusion
Setting up an OpenShift environment can vary depending on your platform, but with the steps provided above, you should be able to get up and running smoothly. Whether you choose to run OpenShift locally or on the cloud, the flexibility and power of OpenShift will enhance your containerized application development and deployment process.
[OpenShift](https://example.com/openshift.png)
For further reading and more detailed instructions, refer to the www.qcsdclabs.com
#redhatcourses#information technology#linux#container#docker#kubernetes#containerorchestration#containersecurity#dockerswarm#aws
0 notes
Link
Spinnaker is a Continuous Delivery (CD) platform that was developed at Netflix where they used it to perform a high number of deployments ( 8000+/day). Later they made it available as an open-source tool. Previously enterprise release cycles used to be stretched for 7/8 months. But with the availability of the Spinnaker CD tool, enterprises have been able to shorten the release cycles from months to weeks to days (even multiple releases a day).
There are several other CD tools available in the market but what made Spinnaker so special?
Spinnaker Features:
Multicloud Deployments
It includes support of deployment to multiple cloud environments like Kubernetes (K8s), OpenShift, AWS, Azure, GCP, and so on. It abstracts the cloud environment to be worked on and managed easily.
Automated releases
Spinnaker allows you to create and configure CD pipelines that can be triggered manually or by some events. Thus the entire release process is automated end-to-end,
Safe Deployments
With a high number of release deployments, it is hard to know if some unwanted or bad release has been deployed into production which otherwise should have been failed. The built-in rollback mechanisms with Spinnaker allow you to test and quickly rollback a deployment and lets the application go back to its earlier state.
Maintain Visibility & Control
This feature in Spinnaker allows you to monitor your application across different cloud providers without needing you to log in to multiple accounts.
So Spinnaker is a foundational platform for Continuous Delivery (CD) that can be quite easily extended to match your deployment requirements.
Overview of Spinnaker’s Application Management & Deployment Pipelines Functionality
Spinnaker supports application management. In the Spinnaker UI, an application is represented as an inventory of all the infrastructure resources – clusters/server-groups, load balancers, firewalls, functions (even serverless functions) that are part of your application.
You can manage the same application deployed to different environments like AWS, GCP, Kubernetes, and so on from the Spinnaker UI itself. Spinnaker supports access control for multiple accounts. For e.g. users like dev or testers with permission can deploy to Dev or Stage environments, where as only the Ops people get to deploy the application into production. You can view and manage the different aspects of the application – like scaling the application, view health of different Kubernetes pods that are running, and see the performance and output of those pods.
Spinnaker pipelines let you have all your application’s infrastructure up and running. You can define your deployment workflow and configure your pipeline-as-a-code (JSON). It enables github-style operations.
Spinnaker pipelines allow you to configure:
Execution options– flexibility to run fully automatically or have manual interventions
Automated triggers– the capability to trigger your workflows through Jenkins jobs, webhooks, etc
Parameters– ability to define parameter which can be also accessed dynamically during pipeline execution
Notifications– to notify stakeholders about the status of pipeline execution
As part of the pipeline, you can configure and create automated triggers. These triggers can be fired based on events like a code check-in to the github repository or a new image being published to a Docker repository. You can have them scheduled to run at frequent intervals. You can pass different parameters to your pipeline so that you can use the same pipeline to deploy to different stages just by varying the parameters. You can set up notifications for integrations with different channels like slack or email.
After configuring the setup you can add different stages each of which is responsible for doing a different set of actions like calling a Jenkins job, deploying to Kubernetes, and so on. All these stages are first-class objects or actions that are built-in and that allows you to build a pretty complex pipeline. Spinnaker allows you to extend these pipelines easily and also do release management.
Once you run the Spinnaker pipeline you can monitor the deployment progress. You can view and troubleshoot if somethings go wrong such as Jenkins build failure. After a successful build, the build number is passed and tagged to the build image which is then used in subsequent stages to deploy that image.
You can see the results of deployment like what yaml got deployed. Spinnaker adds a lot of extra annotations to the yaml code so that it can manage the resources. As mentioned earlier, you can check all aspects (status of the deployment, the health of infrastructure, traffic, etc) of the associated application resources from the UI.
So we can summarize that Spinnaker displays the inventory of your application i.e. it shows all the infrastructure behind that application and it has pipelines for you to deploy that application in a continuous fashion.
Problems with other CD tools
Each organization is at a different maturity level for their release cycles. Today’s fast-paced business environment may mandate some of them to push code checked-in by developers to be deployed to production in a matter of hours if not minutes. So the questions that developers or DevOps managers ask themselves are:
What if I want to choose what features to promote to the next stage?
What if I want to plan and schedule a release?
What if I want different stakeholders (product managers/QA leads) to sign off (approve) before I promote?
For all the above use cases, Spinnaker is an ideal CD tool of choice as it does not require lots of custom scripting to orchestrate all these tasks. Although, there are many solutions in the marketplace that can orchestrate the business processes associated with the software delivery they lack interoperability- the ability to integrate with existing tools in the ecosystem.
Can I include the steps to deploy the software also in the same tool?
Can the same tool be used by the developers, release managers, operations teams to promote the release?
The cost of delivery is pretty high when you have broken releases. Without end-to-end integration of delivery stages, the deployment process often results in broken releases. For e.g. raising a Jira ticket for one stage, letting custom scripting be done for that stage, and passing on to the next stage in a similar fashion.
Use BOM (bill-of-materials) to define what gets released
Integrate with your existing approval process in the delivery pipeline
Do the actual task of delivering the software
Say, your release manager decides that from ten releases, release A and B (i.e. components of software) will be released. Then it needs all the approvals ( from testers/DevOps/Project managers/release manager) to be integrated into the deployment process of these releases. And, all this can be achieved using a Spinnaker pipeline.
Example of a Spinnaker pipeline
The BOM application configuration ( example below) is managed in some source control repository. Once you make any change and commit, it triggers the pipeline that would deploy the version of the services. Under the hood, Spinnaker would read the file from a repository, and inject it into the pipeline, deploy the different versions of the services, validate the deployment and promote it to the next stage.
Example of a BOM
A BOM can have a list of services that have been installed. You may not install all services in the release or promote all the services. So you will declare if the service is being released or not, and the version of the release or image that is going to be published. Here in this example, we are doing it with a Kubernetes application. You can also input different parameters that are going to be part of the release e.g. release it in the US region only.
So the key features of this release process are:
Source Controlled
Versioned (Know what got released and when?)
Approved (Being gated makes the release items become the source of truth. Once it is merged with the main branch it’s ready to get deployed)
Auditable ( Being source-controlled, it will definitely have the audit history about who made the change, and what changes were made)
Some interesting ways to enforce approvals
Integrations with Jira, ServiceNow
Policy checks for release conformance
Manual Judgment
Approvals would include integrations with Jira, ServiceNow, policy checks for release conformance e.g. before you release any release items you need to have their SonarQube coverage for static analysis of code quality and security vulnerabilities at 80%. Finally, if you are not ready to automatically promoting the release to production you can make a manual judgment and promote the same
Spinnaker supports managing releases giving you control over what version of different services would get deployed and released. So all the versions need not have continuous delivery but planned release. It lets you plan releases, determine what releases would get promoted, and promote them through the whole process in an automated manner.
OpsMx is a leading provider of Continuous Delivery solutions that help enterprises safely deliver software at scale and without any human intervention. We help engineering teams take the risk and manual effort out of releasing innovations at the speed of modern business.
#Automated Pipelines#CD pipeline#CD pipelines#Continuous Delivery#Continuous Deployment#DevOps#Kubernetes#multicloud deployment#product release#release management
0 notes
Text
IBM S1000-002 Practice Test Questions
If you are willing to prepare for your S1000-002 IBM Cloud Pak for Data Systems V1.x Administrator Specialty exam,PassQuestion provides the latest S1000-002 Practice Test Questions which consist all the necessary tools and information to help you pass IBM S1000-002 exam.With the help of S1000-002 Practice Test Questions, you will be able to receive high-quality IBM S1000-002 questions and answers that will allow you to improve your preparation level for the IBM S1000-002 exam. If you are going through all of our S1000-002 Practice Test Questions, then you will be able to clear the IBM S1000-002 exam on the first attempt.
S1000-002 Exam Overview
S1000-002 IBM Cloud Pak for Data Systems V1.x Administrator Specialty is the required exam for your certification.An IBM Cloud Pak for Data System Administrator has knowledge and experience of IBM Cloud Pak for Data Systems. This administrator is capable of performing tasks related to the daily management and operation, configuration, security and patch management, upgrades of the environment and problem determination.
Exam Details
Exam Code: S1000-002
Exam Name: IBM Cloud Pak for Data Systems V1.x Administrator Specialty
Number of questions: 40
Number of questions to pass: 28
Time allowed: 75 minutes
Languages: English
Price: $100 USD
Exam Sections
Section 1: Cloud Pak for Data System Overview 15%
Section 2: Cloud Pak for Data System Configuration 20%
Section 3: Cloud Pak for Data System Administration 22%
Section 4: Cloud Pak for Data System Operations 18%
Section 5: Cloud Pak for Data System Security & Compliance 10%
Section 6: Cloud Pak for Data System Problem Determination 15%
View Online IBM Cloud Pak for Data Systems V1.x Administrator Specialty S1000-002 Free Questions
Which command displays the MTM and serial number from Cloud Pak for Data System?
A.ap get
B.ap info
C.ap list
D.ap version
Answer: B
In the System_Name.yml file, which node specific item must be set in each node stanza?
A.IP address
B.subnet mask
C.gateway
D.Vlan
Answer: AC
Which command can be used to change the apadmin password in Cloud Pak for Data System?
A.apusermgmt modify-user apadmin -p password
B.ap config -u apadmin -p password
C.docker setpass apadmin
D.ap config modify-user apadmin -p password
Answer: A
Which three components are available to monitor from the Software overview tile on the Cloud Pak for Data System web console home page? (Choose three.)
A.Red Hat OpenShift
B.System
C.Operating system
D.Docker
E.Virtual machines
F.Application
Answer: DEF
Which two methods are used by IBM Cloud Pak for Data System to deliver alerts? (Choose two.)
A.Send Email
B.JSON notifications
C.SNMP traps
D.HTTPS protocol
E.push notifications
Answer: AC
0 notes
Text
Kubernetes 1.16 released
Finally it’s the weekend. Peace and quiet to indulge yourself in a new Kubernetes release! Many others have beat me to it, great overviews are available from various sources.
The most exciting thing for me in Kubernetes 1.16 is the graduation of many alpha CSI features to beta. This is removes the friction of tinkering with the feature gates on either the kubelet or API server which is pet peeve of mine and makes me moan out loud when I found out something doesn't work because of it.
TL;DR
All these features have already been demonstrated with the HPE CSI Driver for Kubernetes, it starts about 7 minutes in, I’ve fast forwarded it for you.
At the Helm
Let’s showcase these graduated features with the newly released HPE CSI Driver for Kubernetes. Be warned, issues ahead. Helm is not quite there yet on Kubernetes 1.16, a fix to deploy Tiller on your cluster is available here. Next issue up is that the HPE CSI Driver Helm chart is not yet compatible with Kubernetes 1.16. I’m graciously and temporarily hosting a copy on my GitHub account.
Create a values.yaml file:
backend: 192.168.1.10 # This is your Nimble array username: admin password: admin servicePort: "8080" serviceName: nimble-csp-svc fsType: xfs accessProtocol: "iscsi" storageClass: create: false
Helm your way on your Kubernetes 1.16 cluster:
helm repo add hpe https://drajen.github.io/co-deployments-116 helm install --name hpe-csi hpe/hpe-csi-driver --namespace kube-system -f values.yaml
In my examples repo I’ve dumped a few declarations that I used to walk through these features. When I'm referencing a YAML file name, this is where to find it.
VolumePVCDataSource
This is a very useful capability when you’re interested in creating a clone of an existing PVC in the current state. I’m surprised to see this feature mature to beta before VolumeSnapshotDataSource which has been around for much longer.
Assuming you have an existing PVC named “my-pvc”:
apiVersion: v1 kind: PersistentVolumeClaim metadata: name: my-pvc-clone spec: accessModes: - ReadWriteOnce resources: requests: storage: 32Gi dataSource: kind: PersistentVolumeClaim name: my-pvc storageClassName: my-storageclass
Let’s cuddle:
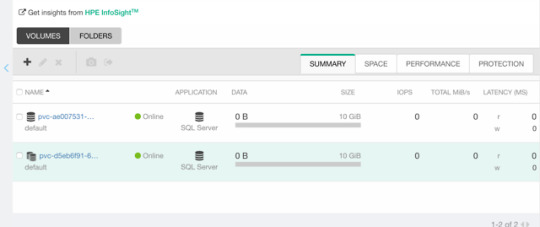
$ kubectl create -f pvc.yaml persistentvolumeclaim/my-pvc created $ kubectl create -f pvc-clone.yaml persistentvolumeclaim/my-pvc-clone created $ kubectl get pvc NAME STATUS VOLUME CAPACITY STORAGECLASS AGE my-pvc Bound pvc-ae0075... 10Gi my-storageclass 34s my-pvc-clone Bound pvc-d5eb6f... 10Gi my-storageclass 14s
On the Nimble array, we can indeed observe we have a clone of the dataSource.
ExpandCSIVolumes and ExpandInUsePersistentVolumes
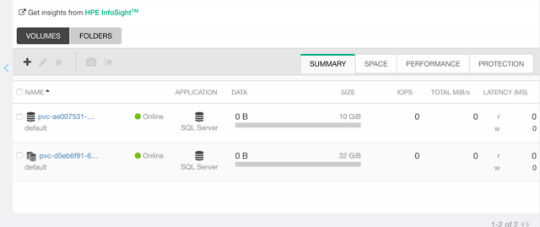
This is indeed a very welcome addition to be promoted. Among the top complaints from users. This is stupid easy to use. Simply edit or patch your existing PVC to expand your PV.
$ kubectl patch pvc/my-pvc-clone -p '{"spec": {"resources": {"requests": {"storage": "32Gi"}}}}' persistentvolumeclaim/my-pvc-clone patched $ kubectl get pv NAME CAPACITY CLAIM STORAGECLASS AGE pvc-d5eb6... 32Gi default/my-pvc-clone my-storageclass 9m25s
Yes, you can expand clones, no problem.
CSIInlineVolume
On of my favorite features of our legacy FlexVolume is the ability to create Inline Ephemeral Clones for CI/CD pipelines. Creating a point in time copy of a volume, do some work and/or tests on it and dispose of it. Leave no trace behind.
If this is something you’d like to walk through, there’s a few prerequisite steps here. The Helm chart does not create the CSIDriver custom resource definition (CRD). It need to be applied first:
apiVersion: storage.k8s.io/v1beta1 kind: CSIDriver metadata: name: csi.hpe.com spec: podInfoOnMount: true volumeLifecycleModes: - Persistent - Ephemeral
Next, the current behavior (subject to change) is that you need a secret for the CSI driver in the namespace you’re deploying to. This is a oneliner to copy from “kube-system” to your current namespace.
$ kubectl get -nkube-system secret/nimble-secret -o yaml | \ sed -e 's/namespace: kube-system//' | \ kubectl create -f-
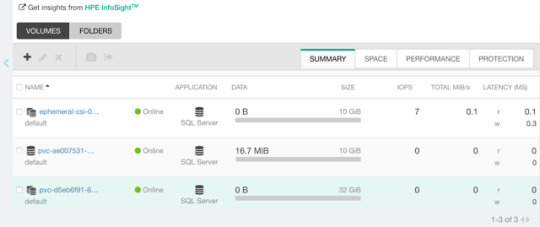
Now, assuming we have deployed a MariaDB and have that running elsewhere. This example clones the actual Nimble volume. In essence, the volume may reside on a different Kubernetes cluster or hosted on a bare-metal server or virtual machine.
For clarity, the Deployment I’m cloning this volume from is using a secret, I’m using that same secret hosted in dep.yaml.
apiVersion: v1 kind: Pod metadata: name: mariadb-ephemeral spec: spec: containers: - image: mariadb:latest name: mariadb env: - name: MYSQL_ROOT_PASSWORD valueFrom: secretKeyRef: name: mariadb key: password ports: - containerPort: 3306 name: mariadb volumeMounts: - name: mariadb-persistent-storage mountPath: /var/lib/mysql volumes: - name: mariadb-persistent-storage csi: driver: csi.hpe.com nodePublishSecretRef: name: nimble-secret volumeAttributes: cloneOf: pvc-ae007531-e315-4b81-b708-99778fa1ba87
The magic sauce here is of course the .volumes.csi stanza where you specify the driver and your volumeAttributes. Any Nimble StorageClass parameter is supported in volumeAttributes.
Once, cuddled, you can observe the volume on the Nimble array.
CSIBlockVolume
I’ve visited this feature before in my Frankenstein post where I cobbled together a corosync and pacemaker cluster running as a workload on Kubernetes backed by a ReadWriteMany block device.
A tad bit more mellow example is the same example we used for the OpenShift demos in the CSI driver beta video (fast forwarded).
Creating a block volume is very simple (if the driver supports it). By default volumes are created with the attribue volumeMode: Filesystem. Simply switch this to Block:
apiVersion: v1 kind: PersistentVolumeClaim metadata: name: my-pvc-block spec: accessModes: - ReadWriteOnce resources: requests: storage: 32Gi volumeMode: Block storageClassName: my-storageclass
Once cuddled, you may reference the PVC as any other PVC, but pay attention to the .spec.containers stanza:
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: ioping image: hpestorage/ioping command: [ "ioping" ] args: [ "/dev/xvda" ] volumeDevices: - name: data devicePath: /dev/xvda volumes: - name: data persistentVolumeClaim: claimName: my-pvc-block
Normally you would specify volumeMounts and mountPath for a PVC created with volumeMode: Filesystem.
Running this particular Pod using ioping would indeed indicate that we connected a block device:
kubectl logs my-pod -f 4 KiB <<< /dev/xvda (block device 32 GiB): request=1 time=3.71 ms (warmup) 4 KiB <<< /dev/xvda (block device 32 GiB): request=2 time=1.73 ms 4 KiB <<< /dev/xvda (block device 32 GiB): request=3 time=1.32 ms 4 KiB <<< /dev/xvda (block device 32 GiB): request=4 time=1.06 ms ^C
For competitors who landed on this blog in awe looking for Nimble weaknesses, the response time you see above is a Nimble Virtual Array running on my five year old laptop.
So, that was “it” for our graduated storage features! I'm looking forward to Kubernetes 1.17 already.
Release mascot!
I’m a sucker for logos and mascots. Congrats to the Kubernetes 1.16 release team.

0 notes
Text
Mastering Wazi: Your Guide to Successful Adoption

An overview of the services offered by Wazi
Staying ahead of the curve in today’s fiercely competitive digital market requires the quick development of innovative digital services. But when it comes to fusing contemporary technology with their core systems including Mainframe applications many firms encounter formidable obstacles. Modernizing core enterprise apps on hybrid cloud platforms requires this integration. Remarkably, 33% of developers do not have the required resources or expertise, which makes it difficult for them to produce high-quality goods and services.
Additionally, 36% of developers find it difficult to collaborate with IT Operations, which causes inefficiencies in the development pipeline. To make matters worse, polls indicate time and time again that “testing” is the main reason project timeframes are delayed. To meet these issues and spur business process change, companies such as State Farm and BNP Paribas are standardizing development tools and methodologies across their platforms.
In what ways does Wazi as Service promote modernity?
Among the solutions that are gaining traction in this environment is “Wazi as a Service.” By supporting safe DevSecOps methods, this cloud-native development and testing environment for z/OS apps is transforming the modernization process. It offers on-demand access to z/OS systems with flexible consumption-based pricing. By speeding up release cycles in safe, regulated hybrid cloud environments like IBM Cloud Framework for Financial Services (FS Cloud), it significantly increases developer productivity.
Software quality is improved by shift-left coding techniques, which enable testing to start as early as the code-writing phase. By utilizing the IBM Cloud Security and Compliance Center service, the platform may be automated using a standardized architecture that has been validated for Financial Services (SCC). IBM Z modernization tools include CI/CD pipelines, Wazi Image Builder, Wazi Dev Spaces on OpenShift, z/OS Connect for APIs, zDIH for data integrations, and IBM Watson for generative AI enable innovation at scale.
What are the advantages of using IBM Cloud’s Wazi service?
Wazi as a Service offers a significant speed advantage over emulated x86 machine environments because it runs on IBM LinuxONE, an enterprise-grade Linux server. It is 15 times faster thanks to this special feature, which guarantees quick and effective application development. Wazi also fills in the gaps in the developer experiences on mainframe and distributed systems, making it easier to create hybrid applications with z/OS components.
Through the integration of secure DevOps principles with the strength of the z-Mod stack, a smooth and effective development process is produced. The service may be safely installed on IBM FS Cloud, which has integrated security and compliance capabilities, and enables easy scalability through automation, lowering support and maintenance cost. As a result, data security and regulatory compliance may be guaranteed by developers who design and implement their environments and code with industry-grade requirements in mind.
Furthermore, Wazi VSI on VPC architecture within IBM FS Cloud creates a segregated network to strengthen the perimeter of the cloud infrastructure against security breaches. Secure integration of on-premises core Mainframe applications with cloud services like API Connect, Event Streams, Code Engine, and HPCS encryptions is also made possible by the strong security and compliance controls offered by IBM Cloud services and ISVs verified for financial services.
This shift makes it possible for outdated, dispersed solutions to replace centralized core systems, enabling organizations to remain competitive and adaptable in the current digital environment. All things considered, Wazi as a Service is revolutionary in that it speeds up digital transformation while guaranteeing security, compliance, and a smooth transition between old and new technology.
How does the IBM Cloud Financial Service Framework support solutions for the industry?
The Financial Services IBM Cloud Framework, often known as The sturdy IBM FS Cloud solution was created especially to meet the special requirements of financial institutions. It guarantees regulatory compliance, excellent security, and resilience throughout both the initial deployment phase and continuous operations. By defining a set of standards that all parties must adhere to, this framework streamlines communications between financial institutions and ecosystem partners that offer software or SaaS products.
The main elements of this framework are cloud best practices and an extensive set of control requirements that cover security and regulatory compliance needs. By implementing a shared responsibility model that covers financial institutions, application suppliers, and IBM Cloud, these best practices make sure that everyone contributes to keeping an environment that is safe and compliant.
The IBM Cloud Framework for Financial Services also helps financial organizations comply with the strict security and regulatory standards of the financial sector by offering comprehensive control-by-control implementation assistance and supporting data. Reference architectures are offered to help with the implementation of control needs in order to further improve compliance. The deployment and configuration process can be streamlined by using these architectures as infrastructure as code.
In order to enable stakeholders to effectively monitor compliance, handle problems, and produce proof of compliance, IBM also provides a variety of tools and services, such as the IBM Cloud Security and Compliance Center. In addition, the framework is subject to continuous governance, which guarantees that it stays current and in line with new and developing rules as well as the shifting requirements of public cloud environments and banks. The IBM Cloud Framework for Financial Services is essentially a comprehensive solution that streamlines financial institutions’ relationships with ecosystem partners and enables them to operate securely and in accordance with industry norms.
Discover Wazi as a Service
Wazi as a Service, which operates on the reliable IBM LinuxONE infrastructure, allows for the easy development of hybrid applications by bridging the gap between distributed and mainframe platforms. Businesses can flourish in the digital age thanks to the platform’s scalability, automation, and compliance features, which enable developers to manage the complex web of security and laws.
Businesses may advance into the future of modern, distributed solutions by securely integrating cutting-edge cloud services with their on-premises core systems using Wazi. In conclusion, Wazi as a Service emphasizes the significance of technology in attaining security, compliance, and the peaceful coexistence of historical and contemporary technologies, and serves as an excellent example of how technology may accelerate digital transformation.
Read more on Govindhtech.com
0 notes
Text
Managing OpenShift Clusters: Best Practices and Tools
Introduction
Brief overview of OpenShift and its significance in the Kubernetes ecosystem.
Importance of effective cluster management for stability, performance, and security.
1. Setting Up Your OpenShift Cluster
Cluster Provisioning
Steps for setting up an OpenShift cluster on different platforms (bare metal, cloud providers like AWS, Azure, GCP).
Using OpenShift Installer for automated setups.
Configuration Management
Initial configuration settings.
Best practices for cluster configuration.
2. Monitoring and Logging
Monitoring Tools
Using Prometheus and Grafana for monitoring cluster health and performance.
Overview of OpenShift Monitoring Stack.
Logging Solutions
Setting up EFK (Elasticsearch, Fluentd, Kibana) stack.
Best practices for log management and analysis.
3. Scaling and Performance Optimization
Auto-scaling
Horizontal Pod Autoscaler (HPA).
Cluster Autoscaler.
Resource Management
Managing resource quotas and limits.
Best practices for resource allocation and utilization.
Performance Tuning
Tips for optimizing cluster and application performance.
Common performance issues and how to address them.
4. Security Management
Implementing Security Policies
Role-Based Access Control (RBAC).
Network policies for isolating workloads.
Managing Secrets and Configurations
Securely managing sensitive information using OpenShift secrets.
Best practices for configuration management.
Compliance and Auditing
Tools for compliance monitoring.
Setting up audit logs.
5. Backup and Disaster Recovery
Backup Strategies
Tools for backing up OpenShift clusters (e.g., Velero).
Scheduling regular backups and verifying backup integrity.
Disaster Recovery Plans
Creating a disaster recovery plan.
Testing and validating recovery procedures.
6. Day-to-Day Cluster Operations
Routine Maintenance Tasks
Regular updates and patch management.
Node management and health checks.
Troubleshooting Common Issues
Identifying and resolving common cluster issues.
Using OpenShift diagnostics tools.
7. Advanced Management Techniques
Custom Resource Definitions (CRDs)
Creating and managing CRDs for extending cluster functionality.
Operator Framework
Using Kubernetes Operators to automate complex application deployment and management.
Cluster Federation
Managing multiple OpenShift clusters using Red Hat Advanced Cluster Management (ACM).
Conclusion
Recap of key points.
Encouragement to follow best practices and continuously update skills.
Additional resources for further learning (official documentation, community forums, training programs).
By covering these aspects in your blog post, you'll provide a comprehensive guide to managing OpenShift clusters, helping your readers ensure their clusters are efficient, secure, and reliable.
For more details click www.qcsdclabs.com
#redhatcourses#information technology#containerorchestration#kubernetes#container#docker#containersecurity#linux#dockerswarm#aws
0 notes