#Patch Management Software
Explore tagged Tumblr posts
Text
Optimierung von IT-Assets: Strategien für effizientes Management
Die Optimierung von IT-Assets ist ein entscheidender Faktor für Unternehmen, die ihre Wettbewerbsfähigkeit in einer zunehmend digitalen Welt steigern möchten. In Zeiten, in denen technologische Innovationen rasant voranschreiten, ist ein effizientes Management von IT-Ressourcen unerlässlich. Durch gezielte Strategien können Unternehmen ihre IT-Assets nicht nur besser nutzen, sondern auch Kosten…
#Automatisierung#Automatisierungstools#Best Practice#Best Practices#Cyberangriffe#Innovation#Innovationen#IT-Infrastruktur#IT-Ressourcen#IT-Strategie#Patch-Management#Sicherheitsmanagement#Sicherheitsmaßnahmen#Sicherheitsrisiken#Sicherheitsüberprüfungen#Software-Updates#Technologische Innovation
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Some thoughts from severance s2e3, and the season in general:
I 100% assumed the reason the goat people were asking to see their bellies was to see if they had belly buttons. Since the prevailing theory is that the goats are for cloning purposes, i figured they wanted to make sure they weren’t clones (clones not having belly buttons because they weren’t birthed/have need for an umbilical cord). If we take the pouches line at face value, I’d guess that they were told a rumor that MDR had pouches, to sow division and fear between the departments (like the fake uprising told to MDR about O&D, and vice versa).
The Export Floor. The fact that O&D used to deliver things there themselves, but then a courier was used. My theory is that someone saw something there they shouldn’t have. I don’t know how o!Irving knows about it, but I’m not here to discuss that right now. What I want to talk about is the name. The obvious one is exporting goods (or even ideas) to other countries, and this could simply mean it’s where stuff made by O&D gets sent up to the ‘outtie’ world. But there’s another possibility - export as in transferring data to another software/format. I think it’s this meaning that is critical, and has big implications for Gemma/Ms. Casey. They could be transferring the data MDR has refined to her chip, or in some way or another, working on “Cold Harbor.”
I am very firmly in the ‘that’s Helena’ camp now. I don’t think this is in character for Helly, as the extremely awkward conversation in the hall with Mark as well as telling Irving they ‘got him’ sealed it for me. I’m fairly certain that management knows it’s Helena; after all, they don’t activate her chip, although I won’t rule out she paid someone off/threatened them to do it. That said, I like to believe she compromised with the board to go down as herself, instead of as Helly. This would also mean that she can encourage Mark to go places that Lumon specifically wants him to see, instead of ones that are much more confidential. However, I think she’ll end up siding with the innies by the end, simply because the connections she will forge with them will be the only genuine and loving relationships in her life.
I didn’t mention this before, but i’m pretty sure Irving knows that Helena/Helly is lying, because he was the only innie who spent enough time outside to know that it was winter and she couldn’t have been gardening. He distrusts her, that’s why he only told Dylan about Burt.
Upon immediately seeing Dylan’s wife I assumed she was a hired actress. However it genuinely appears to be her (granted, I’m faceblind, but the voice sounded the same when she was with his outtie later in the episode). Lumon clearly thinks that this perk will keep i!Dylan in line, but I think it might backfire spectacularly, or at least cause significant drama - his wife is going to fall in love with his innie. Think about it, if their marriage is going through a rough patch, and she gets to spend time with a version of her husband who lacks all of the assumptions/grudges he has against her - basically starting all over… yeah, it’s gonna get strange. The way she talked about it to o!Dylan was like she was hiding it from him, almost like it’s the beginning of a potential affair…
(I also am still of the mind that either she or one of their children is terminally ill in some way, hence the benefits/insurance that Dylan is always looking after. He also complained a few times about having sore arms and jokes he works out. I feel this might be related somehow? But not sure…)
I stand by my theory that the board is actually the motherboard and is Kier’s (and his successors?) consciousness, or something of that ilk. The board was referred to as “it” in this episode (also “they”, but I believe that was meant as in plural, including Natalie). So I think we actually don’t have any proof that it’s multiple people or even people period. It will be like the export double meaning I mentioned earlier. Again, the board is hot on Mark staying and working because it wants him to finish Cold Harbor so it can begin the revival of Kier’s family (the rotation could potentially mean their minds being uploaded. Or something of that nature.)
No big theories or details to chew on here, but things that got big reactions from me: the Black Kier portraits I was expecting but still not prepared for. I desperately want to see Natalie’s portraits that she received; were they all biracial, all women, or both? The idea of genderbent biracial Kier family is killing me. This is like Hamilton (I think). Cobel definitely was going to die if she went into the building, she made the right call, I was terrified that her car might explode as she left. Phew. Next episode is going to be a roller coaster, I can tell. Shocked that he’s starting reintegration so soon but I’m here for it. Worried that Devon is going to get murdered. And I’m waiting for Cobel to get hunted down by Mark or for her to willingly seek him out as she realizes this is her only chance left to… do whatever the fuck it is she wants to do.
128 notes
·
View notes
Text
50 ONE LEVEL CAREERS: Storytelling careers megapack by isy's the snake

Here is yet another career mod pack, but this one has no promotions, you just work and your job level stays at 1. As the title say this mod is best for story telling!
creator's notes-
This mod requires XML Injector by Scumbumbo. You can find it here. Pay attention if you don't already have it for another mod! In that case, you do not need to re-install it. Be sure it is updated for the last patch.
XML Injector is a mod required for some mods to work. So, you install it as any other mod in your Mods folder, no more than one subfolder deep.
This mod has been updated for the version 1.99.305 of the game (second update after Horse Ranch).
It doesn't required any DLC to work. Base game compatible
I've adopted this mod from the amazing ItsKatato who, due to her hiring at EA, couldn't continue to mod. I have made some changes: • I have changes all the pics of the careers — now they all show Sims (please check the credits paragraph at the end to see who was the amazing raccoon who helped me); • I have updated the mod for the Horse Ranch patch; • I have cleared ALL the tuning errors; • Fixed the description of some careers who appeared to be missing.
Now, here we go with the explanation of the mod (originally written by ItsKatato, edited by me):
Katato said: "Have you ever had a story planned out for your sims but you can't find the perfect career for them? Most of the time when I find the career it ends up being a complicated career with a bunch of promotion tasks and extra stuff. Well, I've made a pack of a bunch of single-level careers. All your sim has to do is go to work, that's it. This is perfect for the non-important sims in your life, like the forgotten children of your legacy challenge." In short: those are 50 careers you can use for NPCs Sims or random Sims you do not want to care about. As Amethyst said: "Go to work, make money, leave me alone". Your Sims won't need any task to perform to upgrade and get a promotion, as well as they do not really need an ideal mood to go to work since it won't change their performance. They just go and do their job. And now the list of all careers:
1. Anesthetiologist 2. Cartographer 3. Chiropractor 4. Compliance Officer 5. Data Scientist 6. Dental Hygienist 7. Dentist 8. Diagnostic Medical Sonographer 9. Financial Advisor 10. Financial Manager 11. Genereal Surgeon 12. Genetic Counselor 13. Home Health Aide 14. Information Security Analyst 15. IT Manager 16. Interpreter And Translator 17. Lawyer 18. Marriage And Family Therapist 19. Massage Therapist 20. Mathematician 21. Mechanical Engineer 22. Medical And Health Services Manager 23. Nurse Anesthetist 24. Nurse Practitioner 25. Obstetrician And Gynecologist 26. Occupational Therapist 27. Operations Reasearch Analyst 28. Optometrist 29. Oral And Maxillofacial Surgeon 30. Orthodontist 31. Orthotist And Prosthetist 32. Paralegal 33. Pediatrician 34. Personal Care Aide 35. Phlebotomist 36. Physical Therapist 37. Physical Therapist Assistant 38. Physician 39. Physician Assistant 40. Pilot 41. Podiatrist 42. Prosthodontist 43. Psychiatrist 44. Registered Nurse 45. Respiratory Therapist 46. Software Developer 47. Speech-Language Pathologist 48. Statician 49. Substance Abuse And Behavioral Disorder Counselor 50. Veterinarian 51. Web Developer 52. Wind Turbine Technician
lets give some of our love and support to isy!
download
#sims 4 cc#sims 4 download#sims 4#sims 4 gameplay#the sims 4#sims 4 custom content#sims 4 mods#the sims 4 mods#the sims 4 custom content#ts4#sims 4 careers#sims 4 career#ts4 careers#ts4 career#s4 career#s4 cc#s4 download#s4cc#s4ccfinds#s4 custom content#sims 4 storytelling#sims 4 story#the sims 4 download#ts4 mods#the sims 4 cc#ts4 custom content#thesims4#sims4
312 notes
·
View notes
Text
Leverage Redemption Fic Recs
This list will include all ratings and tags, so read at your own discretion! :)
Happy LevRed Season Finale!!
Find Previous Leverage Lists here! (Leverage, Tap Out Job, Carnival Job, Rundown Job)
Our Unexpected Family Reunion by cminerva, GlassFullOfSass - Rated G
In which Harry meets more of the extended Leverage family.
The Job-Gone-Wrong Job by Grammar_Beane - Not Rated
Eliot’s voice came out tense. “Breanna’s gone. Her comms are dead.” Parker’s eyes widened, but she allowed no other tension to enter her body. “Okay. Plan doesn’t change much. Sophie. Go in. Find Breanna.” “I can’t.” Sophie’s voice grew cold as she saw the man standing at the front door. “Jim Sterling’s here.” --- The job was going perfectly. Until it wasn't. Now everyone's in an unfamiliar role, Breanna's been captured, and it's all resting on Harry Wilson to save her.
Not An Emotion by nerdsandthelike - Rated T
Breanna: Did you hack Lockheed Martin?! For me?!!
Hardison: No, I hacked Lockheed Martin because they’re shitty people who deserve to have their corruption exposed to the world. I downloaded their R&D software and drone specs for you.
How each member of the Leverage Redemption team shows Breanna affection.
After Date Night by Grammar_Beane - Rated T
The Leverage OT3 gets patched up after date night. – – – “Does this sort of thing happen every date night?” “No,” Eliot replied, at the same time Parker said, “Yep!” “It might be becoming a theme,” Hardison admitted.
Three of Twelve Job by WhenICantWrite - Rated G
The one where Eliot fights a lion
Parker's Peculiar Polyculians by Singing_Siren - Rated T
Emotions are… fiddly. She can’t grab onto them, hold them close, and inspect them like she does the stuff she steals. What’s the difference between attraction and love? Is it sex? That seems too simple, and emotions are never simple. Sophie taught her that. But Hardison taught her that things don’t have to be complicated, that going with the flow isn't as bad as she thought it would be. “You know,” Parker starts, “before I met you all, things were so much simpler.” What was it Eliot said when they were conning those Nana-Haters? ‘Parker has a very binary sense of right and wrong.’ Before the team got together, she saw the world in black and white. Now she can see shades of gray. There are even hints of color when she closes her eyes. (or: the aftermath of the Polygeist Job, featuring a Parker who's been through enough therapy to detangle some of her feelings)
The Habeas Corpus Job by hyacinthgirlboy - Rated T
Harry knows where he stands with this crew. Breanna is their little sister. He’s just a guy who handles their contracts sometimes. And yet here he is, drinking their bourbon in their house when something had gone horribly wrong, and it had been his fault. A mark's clever fakeout causes Harry to spiral a little. Breanna and Sophie are there to clear up any misconceptions.
Drive by ziazippy5379 - Rated G
Harry is driving the girls back from a college visit.
irredeemable by idkimoutofideas - Rated T
“Take that one as collateral,” Fisher said, jerking his chin at Harry. A guard stepped forward and grabbed Harry’s arm, yanking him to his feet. Harry shouted in surprise, and Eliot rose with him, shoulder checking Harry out of the way with a growl—Harry wasn’t sure how he managed to stand, given the blood staining his jeans. Eliot offers to be the hostage when he and Harry are kidnapped together. BTHB: take me instead
the textbook definition by tziporim (ferns) - T
Breanna’s burning the digital midnight oil when Harry shows up looking like a kicked dog.
Old Friends by Singing_Siren - Rated G
“Sophie,” Parker whispers harshly, her left eye twitching an erratic rhythm. Every muscle in her body tenses up like she’s about to break into a sprint, and it takes everything in her not to give into that instinct. Ooh, she wants to get closer. But she can’t! She shouldn’t. “Cameras.” A sensation not unlike a freefall builds in her stomach as she watches the two people that just entered. Blonde hair, a familiar laugh, Maggie Collins with a boring man on her arm and an elegant dress that sparkles in the light of the chandelier. There's a beat as Sophie no doubt nudges Harry out of the way to check the screens herself. “Oh no,” she says eloquently.
Holidays by Anonymous - Rated G
Or, Breanna really likes Halloween, and Harry wants to help her have a great one.
tulips and carnations (and a knife) by oopshenangians - Rated T
Eliot doesn't want to dress up as a knight again. But, if Parker and Hardison and Breanna are all going, then he'll go too. To make sure they're safe, of course. And if he finds a way to secretly confess some feelings to Parker and Hardison along the way? Well, it's just to keep the limbo they've made. And Eliot is very happy to stay in the limbo as long as he needs. based on a Tumblr post by @batserebus over there
After the Job by JMount74 - Rated T
When the job is done there is time to rest, recoup and reflect...before the next one comes along...
won't tell anybody that you turn the world around by crazyness_overpowers - Rated G
Parker asks a question, Breanna reveals an assumption, and Eliot tries not to freak out. Then Parker and Eliot talk about what Breanna's assumption might mean. -- The conversation that happens immediately after "Hey guys? Are we a polycule?", a coda to Redemption 3.09: The Polygiest Job.
#veryace recs#leverage#leverage redemption#parker leverage#eliot spencer#harry wilson#breanna casey#sophie devereaux#leverage redemption s3#leverage redemption fic recs#ao3 fic recs#fanfic recs#ao3
27 notes
·
View notes
Text
Blu-ray DRM is really devilish. I use a program called makemkv to rip them, because there is no other way to play them on my laptop, and there are no legit linux options for blu-ray playback, you have to crack the drm to play them. The easiest solution is makemkv to rip the movies into files, it works out of the box.
But if the level of drm (aacs) on a particular blu-ray is higher than what Makemkv can handle, the disk will update the firmware on your drive to revoke access to makemkv, so it can't access any blu-rays.
"One famous “feature” of AACS is a so-called host revocation. It was designed to ensure that only “approved” software can use your drive. Every Blu-ray disc contains a file that has a list of host keys known to be used by "unauthorized" software. This list has a version number. The moment you insert the disc into your drive, the drive checks if the list is newer than the one it knows about, and if it is, the drive re-flashes itself (updates firmware)."
And that happened to me. It was a blu-ray of the 1972 Hammer horror movie Fear in the Night that did it. The one program that works with my blu-ray player now couldn't access any discs, including ones it had ripped before. And there are absolutely zero linux programs that are authorized to playback blu-ray discs.
I had to flash my drive's firmware to allow something called libredrive, which allows direct access to files and bypasses the aacs drm firmware.
And that was quite the journey. I had makemkv installed as a flatpak via my distro's software manager. and I needed to use the command line. Flatpaks are a great packaging format. but they are primarily for gui apps. So i had to build makemkv from source. And then I had to figure out the commandline for the firmware flashing tool included with makemkv, which was hard because the instructions linked flat out lie. There is no "flash" command for sdftools, there is only "rawflash", you have to read the thread carefully to find that out. This page helped. I had to download new patched libredrive firmware.
And finally i figured out the command I needed ""sdftool -d [drive name] rawflash main,enc -i [new firmware file name].bin. And now I can use my blu-ray drive again. It's now libredrive.
So much work to finally be able to use the drive I paid for, and the blu-ray discs I also paid for. I'm not running some major piracy operation, I just want to be able to watch movies I legally own on my laptop. And drm stopped me, and I had to break it.
This is why DRM is so bad, and anyone who uses it deserves all the piracy they are trying to stop with it. It's scummy to take someone's money and then interfere with their ability to use the copy of the products they own and paid for. It's such atrocious treatment of the customer that anyone who does it deserves to have their stuff pirated.
372 notes
·
View notes
Text
tuesday again 5/27/2025
no lesbian novel this week! didn’t get to read much at work bc i had to do my actual job :( did manage to do some sewing
listening
ive been bumping this since the end of the season tbqh. the way in-universe this has been a chart-topping party song for over a year??? with its own little dance??? how Niamos is the name of a beach planet so this is functionally a Pitbull song where he yells MIAMI!!!! which is all of them???? show of all time. show of all fucking time.
it’s not on streaming platforms but THE IN UNIVERSE ELEVATOR REMIX!!!! FUCK!!! WHAT IF STAR WARS WAS GOOD!!!
-
reading
did not manage to read a lesbian novel. did manage to read half a book ive had in hold since january 2 of this year and i did not like it :(

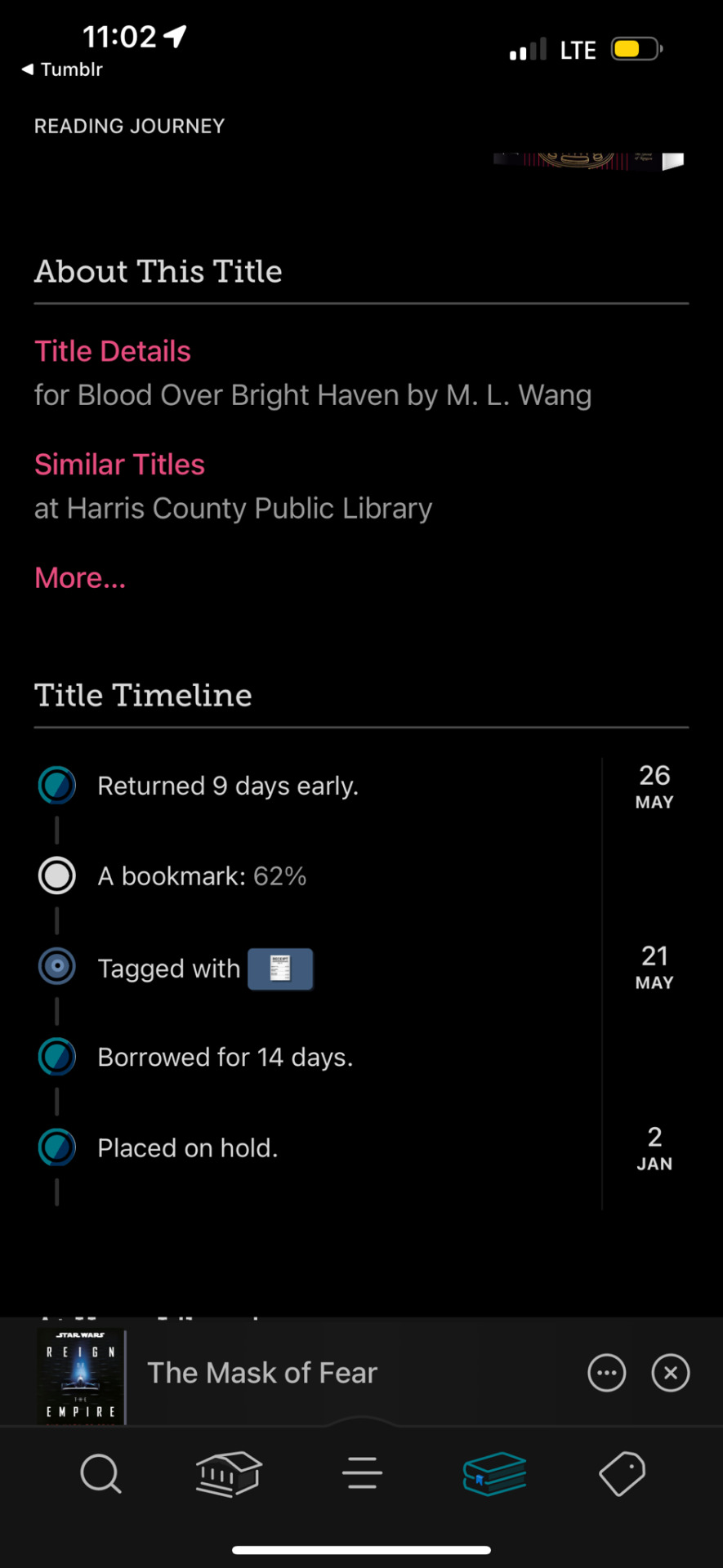
this is playing in the same space as Canticle for Leibowitz and anything else that treats software programming as a magical mystical art with priests and such. love this space! you can probably name three more off the top of your head!
while it does have a fascinating 1920s level of technology world (aside from the big magical barrier), it really flounders about in the middle. the twist was pretty clearly telegraphed (fine) but after the twist i had zero desire to continue onward. i had no real interest in how or why this huge overarching societal problem could be solved, and think i could have liked it more if it were either novella or short story length. would be perfect as a classic episode of the twilight zone.
it also strikes a little too close to home for me with its depiction of a far-right religious cult running everything and a depressingly accurate depiction of what it’s like to be a woman in hard stem, down to the sexual assault from a person in the same research group. the two-thirds of the book i read was really just real life as a woman postgrad without many scifi elements. the promise of scifi elements were why i picked up the book, bc i was interested in a hard sci take on dark academia. further annoyances: i also did not love the “they’re trying to keep you PLACID and QUIET and WOMANLY!!!” scene with a doctor. there is an additional second-wave feminist stink around the “original” flavor of magic, stolen from the original women of the land. i hesitate to call it terfy. if i met someone with these views in the real world I would certainly ask more questions before scheduling a second hang. yanno?
-
watching
john wick the fourth bc i unexpectedly have peacock access. video game cutscene lookin ass movie (lovingly). the visual style, lighting, and nods to other movies (genuinely gasped out loud at a specific match cut bc the reference made sense within the plot and wasn’t just a fun visual) are all off the chain. slightly longer than i wanted it to be— the last chase/gun battle through paris dragged a bit despite having some of the coolest set pieces.

-
playing
nothing fun to report in genshin this week. still don’t have enough to guarantee the pink fox lady so i think i will bide my time and wait for skirk to drop at some point the next patch (yet another patch with no map update :( curious)
-
making
trying to clean my house or finish some projects whenever i want to leave my house or spend money. has led to a much cleaner house but a much more housebound me. anyway here’s a scrub cap with fabric a friend bought and asked “hey can you make me a scrub cap” When I Moved To Houston Nearly Two Years Ago. plus the lining galaxy fabric, bought at the joanns closest to umass in mmm 2017?


came home from work friday morning to discover catnip strewn about the living room bc da gorls managed to rip holes in BOTH mr cactus kickers. a somewhat slapdash mend but reinforced with fraychek so the next time they bite and tear the fabric Next to the patch will tear


24 notes
·
View notes
Text
Game Fuckery Help and Linux List [Update].

I'm avoiding re-installing this shit again, so in the meantime I'm sorting some stuff into lists. For Linux research purposes.
Edit: Standby Memory Allocation on Windows 10: New info coming in: That's not the issue. However, what i wrote below about TM is my own experience and has worked for me (without doing what Jessa was saying in the SB memory part, I remembered, hope I didn't waste anybody's time). Does it make sense? idk, but it's harmless, and if it's actually a thing and not just a freak coincidence, and can help anybody else then why not. I do remember trying it with and without cleaning cache :/ [for fuck sake the nerve on EA to put out for sale a new edition without improving it to 64bit]. As discussed by Jessa below, it's an OS problem. What worked for me, for some bizarre reason was to keep Task Manager on before and while playing the game. without it my game was crashing often, on my main non gaming computer. What solved it was fixing windows... for anyone's interested, the gory details are at the bottom of the post under the cut.
+ That combined with clearing cache often.
Jessa's video (Memory Allocation and 4GB Patch Repair). Edit: Turns out this video was pulled back, so basically just make sure the patch is applied?
1. Secound opinion on the whole matter by BrandiNotBroke [the whole #pink flash diaries tag is interesting]:
2. Leefish forum - Sims2 Graphic Cards:
3. @celebkiriedhel's Post (Texture Memory):
Linux:
@teaaddictyt & @niamh-sims About Linux.
2. @nonsensical-pixels about Linux.
3. @brandinotbroke, first Linux supporter I've encountered here. A comprehensive post:
4. @grilledcheese-aspiration, Transferring software and such from Windows to Linuxs:
Texture Memory Fuckery (Pink Soup, among other things):
Kiri's post linked at the beginning, first an foremost.
Original Post by @fireflowersims, plus; re-blog by @ovytia. Both of their tags, and comment:
2. A recap on Pink Soup/Texture Sizes by @rockethorse in the comments:
That's it for now. Any more information or good links will be welcome.
Task Manager thing briefly, for the curious (as if it interests anyone else but me, but in the interest of keeping track).
So the game was crashing often. That thing was easy to spot because the laptop would make loud airplane noises when I'd load the game. It got stuck or something, so I went to end it by force with task manager and noticed that all the resources where used to the max - right up until I'd open TM, and then everything would cool down. Like it was playing hide and seek with me. So I figured I'd get smart with it right back, and just leave TM open the whole time. Low and behold, the game stopped crashing. That combined with clearing cache often. Does it make sense? idk, but the computer works in mysterious ways.
#ts2#Sims2#theSims2#the Sims 2#Sims 2#Tutorial#ts2 tutorial#sims 2 tutorial#tagging is a bitch#the sims 2 tutorial#Crashing#Pink Flashing#Pink Soup#Linux#Sims 2 Linux#Windows 10#Graphics Help#Texture Memory#Standby Memory#Youtube#Standby Memory Allocation Windows 10#EA#Somewhat of a#Shitpost#text post#Tutorial: Other#Tutorial: Help
22 notes
·
View notes
Text






Internal Family Skills, part two! This is the Firefighter (FFR) Attribute: Your capacity to resolve crises and take deliberate action in the world. Its six Skills are:
Corpsework
Deliberation
Kagandahang-Loób
Master Plan
Machine Spirits
Utang
[ Manager | Exile | Self ]
Corpsework
Practice self-care and first aid. Understand and respond to the realities of meat.
COOL FOR: Street Medics, Neurasthenics, Trans-sexuals
If you've grown up accustomed to the life of the mind and little else, Corpsework fills in the gaps. You don't need to be attentive to "hunger" or "exhaustion" or "pain": all you need to know to keep your Health pool up is the multitude of ways by which life departs from the human body. In addition to patching up wounds and scrapes, Corpsework cares for the body by routine and procedure. It keeps you clean, fed, and medicated even in the depths of depression and puts you to bed out of the knowledge that revenge bedtime will ruin your tomorrow.
At high levels, Corpsework allows you to take care of your body and others in more and more extreme conditions. You may not be able to fix the problem, but you can keep a problem stable long enough to get the patient to someone who can help. On the other hand, you'll identify health risks everywhere: every surface is potentially contaminated, every meal an exercise in nutritional "balance". But if your Corpsework is too low, you'll blunder through the world in a feeble haze, and if you do notice infirmities, you won't know what to do about them.
Deliberation
Comprehend arguments. Logic it out.
COOL FOR: Academics, Social Maladapts, the Overcautious
Deliberation is your inner skeptic. It's the voice that gets you to slow down your thought processes and ask, "Is that true?" It's great for getting good grades, figuring out the reputability of a text, identifying disordered thought patterns, not getting mad at posts online, and asking yourself if you can really jump across that gap. For you, however, it also occupies the unenviable position of trying desperately to figure out what other people mean through sheer brute-force semantics and abstract knowledge of social convention.
At high levels, Deliberation makes you a lean, mean, reasonin' machine. High on reason, you'll become obsessive about clarity at the cost of social graces, and prudent at the cost of your entire ego when you do inevitably make rash decisions. But with low Deliberation, you'll make rash decisions all the time and generally show yourself as the idiot you're so scared of being.
Kagandahang-Loób
Demonstrate mercy and forgiveness in an entropic universe. Go above and beyond.
COOL FOR: Creditors, Parents, Moral Philosophers
Kagandahang-Loób is the beauty of the will: when Kapwa recognizes the inherent togetherness of people, Kagandahang-Loób inspires generosity to others and forgiveness of debts. Kagandahang-Loób is necessary for being a good person to yourself and others: without its migitating presence, relationships would be crushed under the weight of debts that can never truly be repaid, paradoxically hastening the decay that inspires Utang in the first place. Kagandahang-Loób is a necessary moral compass -- and a powerful tool for building relationships on mutual support rather than indebtedness.
With high Kagandahang-Loób, you'll be able to easily make friends and inspire them to new heights of reciprocal generosity: through teamwork, you may even be able to fly. However, you'll find yourself easily persuaded that wrongdoers had good reasons and find it hard to take decisive action against them. With low Kagandahang-Loób, however, you'll be a literal and emotional miser, ranting about how much everyone owes you.
Machine Spirits
Interact with hardware and software. Listen to and respect your tools.
COOL FOR: Experiential Learners, Digital Natives, Girls Who Read the Manual
You are terminally non-mechanical; you balk without a user interface. If you're not constantly keeping your hand in with classroom assignments, you couldn't improvise outside of stopgap solutions. Still, technology is an essential part of humanity, and for that, you have Machine Spirits. This Skill uses humanity's great compression algorithm, ritual, to understand what a machine is doing, even if you don't understand the why; you learn from your elders (tutorial webpages), approach the machines with respect (following the steps), and enjoy a successful partnership with machines (your devices, generally speaking, function).
At high levels, Machine Spirits makes you obsessive and insecure: do you have a full collection of right tools for vaguely-defined right jobs? Can you get your laptop to do what you want if you spend another hour fucking with it? Have you stored too much of your knowledge outside of your own brain? At low levels, though, your clothes will fall apart, your bicycle will break, and your toilets will clog -- and you definitely don't have the money not to care.
Master Plan
Figure out how to achieve your goals. Control yourself and others.
COOL FOR: Functioning Executives, Evil Geniuses, The Goal-Oriented
Master Plan is a Skill of agency and delegation. Why try to take on the world yourself when you can get other people to take it on for you? Why solve other people's problems, when you can teach them how to solve their own and yours? Master Plan creates causal chains between your starting point and your goal -- not only does it show you the grand road you need to take, it'll give you options for the low road or the high road. Understanding how best to achieve your own wants also teaches you how to incentivize others, and Master Plan is more than happy to use others' wants to achieve your designs.
At high levels, Master Plan makes you arrogant -- you'll assume you know what's best for everyone and that your victory is already assured, and you won't know how to give others dignity or deal with your own failure. But without it, you'll succumb to learned helplessness, reliant on others' plans and too afraid of disturbing them to better your own position.
Utang
Keep track of debt and obligation. Employ financial literacy and historical materialism.
COOL FOR: Debtors, Negotiators, Political Animals
Utang is the understanding of debt; in you, it's an overgrown philosophical awareness that there ain't no such thing as a free lunch. That literal economic reality is rooted in the thermodynamic principle it famously describes: living as we do in an entropic universe, others expect debts to be repaid, and your own recognition of entropy creates the desire to repay debts. Not only does Utang manage your money, it opens you up to realpolitik on both literal and interpersonal levels. Utang gives you an idea of what people want, explaining the concerns that govern political action and what you can do for others to make both of you happy.
At high levels, Utang will make you see ulterior motives everywhere; treating everything as a transaction that must be balanced will ruin your personal relationships with bookkeeping and your politics with pessimism. Without it, though, you'll assume that politics and community boil down to stark moral principles -- and without a handle on your debts, you'll be too broke and alone to be able to hold to any principles of your own.
Notes
The visual design for Master Plan is based at least in part on the dual meaning of the Latin word textus, meaning both "weaving" and "narrative".
Thanks again to "Loób and Kapwa: An Introduction to a Filipino Virtue Ethics" (Reyes 2015).
25 notes
·
View notes
Text
Anyway should mention this here:

I fell in with the Website League, an island of federated social media websites that's mainly spun off old cohosters, run partially by consensus committee of various stakeholders and intended to be a relatively sustainable form of non-commercial social media.
If you like what you see, you can sign up to one of the open-access nodes.
Official launch is today, since it's the last day of cohost, but this has been in the works for a few weeks.
The Website League is based on ActivityPub software, mainly GoToSocial and Akkoma, running in allowlist mode, so we only federate with other League members. This keeps moderation load lower and simplifies management.
We're explicitly not federating with the broader fediverse, which among other things should allow us to experiment with patched versions of the software to support more advanced and interesting post formats, e.g. actual interleaved text and images as a first class citizen, cohost-style CSS fuckery.
If you're interested you can join the (ugh) discord or just try and join an instance. I'm hosting weague.awful.cloud.

It's early days so things are likely to change fast, but hey.
48 notes
·
View notes
Text
i am not really interested in game development but i am interested in modding (or more specifically cheat creation) as a specialized case of reverse-engineering and modifying software running on your machine
like okay for a lot of games the devs provide some sort of easy toolkit which lets even relatively nontechnical players write mods, and these are well-documented, and then games which don't have those often have a single-digit number of highly technical modders who figure out how to do injection and create some kind of api for the less technical modders to use, and that api is often pretty well documented, but the process of creating it absolutely isn't
it's even more interesting for cheat development because it's something hostile to the creators of the software, you are actively trying to break their shit and they are trying to stop you, and of course it's basically completely undocumented because cheat developers both don't want competitors and also don't want the game devs to patch their methods....
maybe some of why this is hard is because it's pretty different for different types of games. i think i'm starting to get a handle on how to do it for this one game - so i know there's a way to do packet sniffing on the game, where the game has a dedicated port and it sends tcp packets, and you can use the game's tick system and also a brute-force attack on its very rudimentary encryption to access the raw packets pretty easily.
through trial and error (i assume) people have figured out how to decode the packets and match them up to various ingame events, which is already used in a publicly available open source tool to do stuff like DPS calculation.
i think, without too much trouble, you could probably step this up and intercept/modify existing packets? like it looks like while damage is calculated on the server side, whether or not you hit an enemy is calculated on the client side and you could maybe modify it to always hit... idk.
apparently the free cheats out there (which i would not touch with a 100 foot pole, odds those have something in them that steals your login credentials is close to 100%) operate off a proxy server model, which i assume intercepts your packets, modifies them based on what cheats you tell it you have active, and then forwards them to the server.
but they also manage to give you an ingame GUI to create those cheats, which is clearly something i don't understand. the foss sniffer opens itself up in a new window instead of modifying the ingame GUI.
man i really want to like. shadow these guys and see their dev process for a day because i'm really curious. and also read their codebase. but alas
#coding#past the point of my life where i am interested in cheating in games#but if anything i am even more interested in figuring out how to exploit systems
48 notes
·
View notes
Note
Sì where the Absolute Solver preserves Tessa’s soul into itself and keeps her as a pet. After Nori accidentally detonates Copper-9 core Tessa manages to escape and accidentally ends up in a pill baby. She gets found and adopted by a drone from the bunker where Uzi lives and has to pretend to be a “normal” drone rather than a very traumatized teen that is clearly not having a good time and is in a constant state of agony because her human mind doesn’t align well with her drone body, giving her so many software and physical issues.
Series: Murder Drones AU Criteria: Absolute Solver takes Tessa's soul and keeps it as a pet. It does not go well. AU title (optional): Core Failure
The only thing that the Solver can have her in is a core from a drone that it had killed. She is made to watch the destruction of various planets, while being kept as a pet by Absolute Solver. There is a second core that doesn't talk, and seems to suffer more guilt that Tessa.
They are transported after being captured and stolen from the Solver. They find some hope in the crucifix patches, and accept the offer to be tested on. They are proven to not have the Solver in their systems.
They find some damaged bodies, and escape the labs with Nori and Yeva. The silent drone tries to get left behind, but Tessa feels responsible for her. Despite her love for the drones, Tessa struggles with her body.
They are brought into Outpost 3, and integrate with the population. Tessa and the silent one are joined by a young Uzi Doorman, and become like older sisters to her.
Uzi spends years learning to help her sisters, and helps them adjust to the false bodies they inhabit. A deep delve hacking session reveals the name of the silent one to be Cyn, that she can speak and is intensely sorry for letting the Solver loose. Then that is a FAR minor note to Tessa being a drone born as a human in a drone body. Mental images are weird. Uzi does help work their neural connections to be more efficient, just before Uzi needs to go out to get a power core for her other project. Why by the stars did she want to make a rail gun again?!
8 notes
·
View notes
Text
something i just can't stop thinking about is how metal sonic fucks up all the time. like, he's born to lose, at least in terms of the narrative. and each time he fails, eggman imposes some horrible sort of consequence on him. usually it's restrictive software patches, or resets to take away whatever minute free will he's managed to scrounge up.
but i was thinking, what if fibula lied and took the blame for something that metal sonic did? because he doesn't want to see him be punished for trying his best. it's just something that would be so familiar to fibula, you know? that picture of metal sonic trying so, so hard, but never being enough. it would remind fibula of himself.
so he takes the blame. and eggman turns off his legs as punishment. and all metal sonic can think is why. why. why. why?
and he could just leave fibula alone after that, unable to move around freely, as eggman intended. but he's so frustrated. he's so confused. he has no idea what it looks like to have someone care about him in the normal way, and not eggman's possessive, controlling way.
so i like to imagine metal staying with him. out of genuine curiosity and anger--feelings that are only allowed to fester BECAUSE fibula kept him from suffering through another factory reset.
#their dynamic makes me a little insane. tbh#imagining metal dragging him around until his legs come back online... got my heart in a VICE grip.#fibula the hedgehog
87 notes
·
View notes
Text




So this blocking thing! It's good for more than just nuisances. I haven't knit a lot of garments yet with fiber that responds to blocking, and what I have has been like...socks where it seems unnecessary because the whole thing will be in tension while worn. But also I just don't have large pinnable surfaces, as one typically needs when the point is to soak a piece of fabric and then stretch it out to pose in the shape you want it to be until next soaking. What do I have? The ability to stack waterproof objects on a small patch of flat counter space. And thank goodness because that definitely saved this hat.
Anyway! I am happy to have used my extremely inconsistent first skeins of support-spindled yarn (see the post with them all laid out here) for a project I'll probably actually use once it's chilly again. It is comfortable, even if I'm a bit disappointed in the colorwork legibility. This is how the chart looks:

But I didn't quite manage matching gauge yarns, I'm low on practice/experience keeping tension for stranded colorwork, and probably just aiming for too loose a fabric anyway (should've found a path to increasing stitches and using smaller needles on that section) so it's very blobby.
I do have some of that green and "matching" oyster skein left, as well as a little of the finest oyster yarn I used for the ribbing. So if I use them together again, I'll probably hold the two oyster threads as one. Speaking of, I had way too much of the underplied lace yarn and wasn't happy with my first run at an even more open lace panel, so ended up frogging that back and making these sections with the lace yarn held double. Worth it! Much happier with this result. And I can see why underplied yarn has been said to do lace well; was cool how open it already was before blocking.
Image descriptions below:
[ID: Four photos of a slouchy, off-white beanie with some green colorwork being knit, blocked, and worn. The hat is constructed with a solid top of thicker yarn, strip of lace, a strip of green colorwork (meant to be jumping frogs), a matching strip of lace, and finally a long section of ribbing, broken into four strips by inverting the knits and purls.
In the first photo, with a blurred background, the beanie is still in process with a green string holding the live stitches while it's tried on, partway through the first section of ribbed brim; it fits like a misshapen mushroom, the top lace panel collapsing over the relatively tight colorwork, all under the lumpy increases of the densely knit crown.
The second photo also has a blurred background but shows the hat being blocked, gently stretched over a tower of stacked containers, widest at the top around the curved base of an upside down plastic coffee canister from crown to colorwork, the gradual taper of a hair bleach tub easing the lower lace panel into the ribbing before the very end hangs free around a peanut butter jar pedestal.
The third and fourth photos show the finished hat from the side and front, being worn by a pale-skinned brunette woman with a braid and orange t-shirt in front of painted wood paneling on an overcast day. The hat is slouched but not bulbous, blocking having stretched the colorwork horizontally and the lace vertically; a twice-rolled brim covers the lower lace panel but leaves the still not very legible frog colorwork visible. End ID]
[ID: Chart of green on white colorwork made in the Google Sheets spreadsheet software; a section in the middle is selected, though there are repeated motifs on either side. Every cell with an X in it is colored green and makes slightly horizontally stretched pixel art of a frog hopping from the right to the left; the rightmost frog is crouched under a flower or star made of four dots, to its left is a frog pushing off the ground and to its left a frog leaping horizontally through the air. The repeat is 39 stitches wide, 10 rows tall. End ID]
#cj gladback#knitting#spinning#fashion#sure#took those quick finished photos yesterday just barely out of the rain so no pretty fall leaves to look more cheery#but i wanted to celebrate that the hat fit while i was still excited about the blocking actually working as advertised#not sure who advertised it but no buyers' remorse here
19 notes
·
View notes
Text
Quitting an interview.
I just talked to a guy who claimed to have a job. The first red flag was he said it was a job working for a charity doing sales.
That usually means called calling people and harassing them for payments or making donations via direct debit.
A lot of times these jobs aren't salaried, they're all 100% commission.
The second red flag was the first thing he asked was what laptop that I had?
To which my response was, I don't work for anybody who can't provide hardware.
When you do one of these jobs and they want you to use your own personal equipment, it means they're not planning to put any effort in. And what they're going to do is they're going to install management software on your own personal computer.
The safeguards to prevent line managers snooping around and having a look through your photos, files, background processes, and so on are practically zero. I have heard in the past of people who got fired from these jobs because they were running a download in the background. For example patching a steam game on their own personal computer using their own Internet connection. Somehow the team leader who was snooping around out of boredom saw this and find them on the spot.
Once during one of these sketchy calls, I said I would provide security by running their management software in a virtual machine, and they hung up.
They really do not like it when somebody understands what they're up to. Mostly because it makes it harder for them when they finagle away not to pay you.
8 notes
·
View notes
Text
UPDATE LOG
-changed interface in order to create a better user experience
-temporarily patched out certain emotions and memories that might put a strain on the system
-changed logo to a more fitting one.
-0̶̭̇1̵͚̂̊1̵̯̟͒̂0̴̺̌̉0̸̦̏͜1̶̗͝0̴͇̕0̸̬̩̈ ̴̱̾̏0̸͗ͅ1̴͍͒1̵̠̼̍͝0̴̪̄̈́1̷̱̬̎0̷̰̂0̴̭̩̉1̶̳̋ ̷̢͌͝0̴̥͋͝1̶̅͝ͅ1̷̬̚0̶̘͍͊1̷̦̘͋̓1̶̰͂̊0̷̠̊̀͜1̵̦̬̃ ̶̼͔̒̂0̸̪̝̒̌1̸̥̈́1̸̗̞͐0̷̘̈́0̵̖̊̿1̷̨̛̺͆0̶̡̘̑1̵͍͍̈́̃ ̷͔͛͝0̷̧̲͝1̷̼̍1̷̥̰͝0̴͈̬̆1̶̱̫̈͋1̴̪̻̐1̵̡̞͆́0̸̡͎́ ̴͕͇̓0̷̮̈́̓1̷͚̮́1̷̣͈̆1̸͉̏͐0̸̯̓̆0̸̩́̀1̶̤̙͆̽1̷͔̽͗ ̸̝͗͆0̸̨̈́͝1̵̢͕͋͝1̴͉̤̂̋0̴̘̠̓1̷̨͂0̵͍̦̂̾0̸̩̿͐ͅ1̶̛̬̲̈́ ̷̠̎͜0̸͓́̈́1̵͔̃̂1̴͉̎͝0̷̗̒1̴͖̈́́1̶̼̃1̵̧́͜1̴̝̿ ̴̤͛̅0̸̩̾͠1̶̬͍̃͛1̴̢̊0̵̤̭͛̕1̶͍̤͂1̵̝̈́1̸̰͠0̸̤̊͝ ̸̯̤͐̚0̷̹̈1̶̝̾̀1̶̖͝͝0̴̢̧̛0̴̢̼̐͝0̸̡̗̆̇0̵̠̂1̵̛̗͖̇ ̷̜̘͆0̶͖̻́͑1̵͖̾1̷͖̲͒0̴̮̈́̀1̴̯̒̀1̶̬̔0̶͔̌͝0̵̺̄ ̶̮̥̑0̴̦͋ͅ0̴̢̘̀͠1̴̳͕̿̄0̵̫̫͒0̸͚̠͠0̸̨̆0̶̫͎͂0̵̪͓̈́̋ ̴̞̽0̸̨̦̽1̶̡̅1̶̯͌0̶̛̥̲1̷̤̺͐̃0̸͎͠0̴̞͚̇̒0̴̢̹̉ ̵̫̦̃0̴̥͉͘1̵̭̝̍͘1̵͙̌͂0̴̗̍̉1̸̤̞̕1̴̧͔̿1̴̤͋1̸̫͗ ̸͍͊0̸̪̱̈́̀1̶̳͛1̷̬̗̈́͘1̴̜͓͗̉0̸̣̱̆0̵͕̒̿0̴̜͂͛0̶͎̩͂͝ ̵̛̠̪0̷̲̩͐͠1̷̪̦͊̚1̶͉͗͠1̷̝̿0̴̟͘0̵̡̰̈́0̷̰͕̈́͗0̶̨̈́ ̵͎̉͂0̶̥̯̆1̸̖̲͘1̵̝̔0̴̺̫̐1̷̹̂͝0̶̧́̊0̷̞̈́͌1̴̢̐ ̷̥̰̌̈́0̷̢̹́1̶̢̊1̴̞̻̃0̴̪́ͅ1̴̜͘1̶̛̳̖1̵͖̣͊0̸̱͙̚ ̷̞̏͛0̶̮̃̃1̴̳̈́̔1̶̩̆͝0̴̖̩͆0̴͇̆1̵͊̚ͅ1̴̦̊1̵̼̰̿́ ̶̜͆0̴͇͆0̷͉̓̈͜1̴̼͜͝0̷͉́͋0̴̧̡͑0̶̡͋̓0̵̱͒̑0̴̤͛ ̸̤̄0̷̟̣̂1̷̥̉̈1̸̬̹̐0̸̮̾1̷̬̒0̶̥͒͊0̶̡̬̈1̵̠̝̇͊ ̴̙̐̊0̵͔̐͛1̶̺̦̾̎1̵̨̿͝0̸͚̇1̷̮̜̕1̸̖̣̓͂0̸̠͝1̶̝̚ ̴̺̯̍̓0̵͓̼̇̎1̴̫̀͛1̵͙̻͋̾1̸͍̋0̶͔̠̾0̵̯̀0̶̲͆ͅ0̸̩̽̚ ̷͖̰̆̄0̵̬̺͌̉1̸̝͚͒̎1̸̩̎1̷̭̎͛0̵͇̰͊͗0̸̘͔̑͆1̴̞̄̈0̷̜͈͆ ̸̟̔0̷̰̗͑̆1̸̩̔1̸͙͝0̶͙̬́̕1̸̪̤̉1̴̭͑͝1̷̧̝̒1̸̠̗̽͛ ̸̨̆̆0̵͕̫̚1̴̧̓1̴̫̼̒1̸̠̖̅0̸̩̬̑1̴̡̜͛̚1̶̩̀͘0̶̥̖̏ ̴͙̍0̷̥̒͊1̸̢̮̀͝1̴̹̮͋̕0̸̡̻̄̀0̸͓͔̓̚1̸̳̾͝0̵̖͍̏́1̸̭̋̋ ̴̙̻̆͠0̸̩̈1̷̫̬̍1̷̻̱̕0̵̝͊0̸͓̿1̸̈́͠ͅ0̴̢̳̌0̶̗̩̌̌
-Changed logo.
Welcome to the beta stages! as you know "Owen" has been prone to glitches and inconsistencies for quite a while, we're working on getting him to a more functional, productive state. for any questions you may ask the software or contact higher management! Hoping to take CHIMERA worldwide into the future, H.R.
#spies are forever rp#floppy disc owen#hatchetfield rp#hatchetverse#spies are forever#owen carvour#hatchetfield roleplay#starkid rp#tcb rp#musical rp#saf rp#hatchetfield#spies are forever au#saf au#tin can bros#tin can brothers#ooc::)
2 notes
·
View notes