#Terminal Operating System Integration
Explore tagged Tumblr posts
Text
https://www.acuitilabs.com/port/
#AcuitiPort#Port Billing Solution#BRIM Accelerator for Seaports#Maritime Sector Technology#Acuiti Labs#Invoicing Solution for Ports#Revenue Management at Ports#ERP Integration for Ports#Digital Transformation for Seaports#Automate Port Billing#Terminal Operating System Integration
0 notes
Text
All-Star Moments in Space Communications and Navigation
How do we get information from missions exploring the cosmos back to humans on Earth? Our space communications and navigation networks – the Near Space Network and the Deep Space Network – bring back science and exploration data daily.
Here are a few of our favorite moments from 2024.

1. Hip-Hop to Deep Space
The stars above and on Earth aligned as lyrics from the song “The Rain (Supa Dupa Fly)” by hip-hop artist Missy Elliott were beamed to Venus via NASA’s Deep Space Network. Using a 34-meter (112-foot) wide Deep Space Station 13 (DSS-13) radio dish antenna, located at the network’s Goldstone Deep Space Communications Complex in California, the song was sent at 10:05 a.m. PDT on Friday, July 12 and traveled about 158 million miles from Earth to Venus — the artist’s favorite planet. Coincidentally, the DSS-13 that sent the transmission is also nicknamed Venus!

NASA's PACE mission transmitting data to Earth through NASA's Near Space Network.
2. Lemme Upgrade You
Our Near Space Network, which supports communications for space-based missions within 1.2 million miles of Earth, is constantly enhancing its capabilities to support science and exploration missions. Last year, the network implemented DTN (Delay/Disruption Tolerant Networking), which provides robust protection of data traveling from extreme distances. NASA’s PACE (Plankton, Aerosol, Cloud, ocean Ecosystem) mission is the first operational science mission to leverage the network’s DTN capabilities. Since PACE’s launch, over 17 million bundles of data have been transmitted by the satellite and received by the network’s ground station.

A collage of the pet photos sent over laser links from Earth to LCRD and finally to ILLUMA-T (Integrated LCRD Low Earth Orbit User Modem and Amplifier Terminal) on the International Space Station. Animals submitted include cats, dogs, birds, chickens, cows, snakes, and pigs.
3. Who Doesn’t Love Pets?
Last year, we transmitted hundreds of pet photos and videos to the International Space Station, showcasing how laser communications can send more data at once than traditional methods. Imagery of cherished pets gathered from NASA astronauts and agency employees flowed from the mission ops center to the optical ground stations and then to the in-space Laser Communications Relay Demonstration (LCRD), which relayed the signal to a payload on the space station. This activity demonstrated how laser communications and high-rate DTN can benefit human spaceflight missions.

4K video footage was routed from the PC-12 aircraft to an optical ground station in Cleveland. From there, it was sent over an Earth-based network to NASA’s White Sands Test Facility in Las Cruces, New Mexico. The signals were then sent to NASA’s Laser Communications Relay Demonstration spacecraft and relayed to the ILLUMA-T payload on the International Space Station.
4. Now Streaming
A team of engineers transmitted 4K video footage from an aircraft to the International Space Station and back using laser communication signals. Historically, we have relied on radio waves to send information to and from space. Laser communications use infrared light to transmit 10 to 100 times more data than radio frequency systems. The flight tests were part of an agency initiative to stream high-bandwidth video and other data from deep space, enabling future human missions beyond low-Earth orbit.

The Near Space Network provides missions within 1.2 million miles of Earth with communications and navigation services.
5. New Year, New Relationships
At the very end of 2024, the Near Space Network announced multiple contract awards to enhance the network’s services portfolio. The network, which uses a blend of government and commercial assets to get data to and from spacecraft, will be able to support more missions observing our Earth and exploring the cosmos. These commercial assets, alongside the existing network, will also play a critical role in our Artemis campaign, which calls for long-term exploration of the Moon.

On Monday, Oct. 14, 2024, at 12:06 p.m. EDT, a SpaceX Falcon Heavy rocket carrying NASA’s Europa Clipper spacecraft lifts off from Launch Complex 39A at NASA’s Kennedy Space Center in Florida.
6. 3, 2, 1, Blast Off!
Together, the Near Space Network and the Deep Space Network supported the launch of Europa Clipper. The Near Space Network provided communications and navigation services to SpaceX’s Falcon Heavy rocket, which launched this Jupiter-bound mission into space! After vehicle separation, the Deep Space Network acquired Europa Clipper’s signal and began full mission support. This is another example of how these networks work together seamlessly to ensure critical mission success.
Engineer Adam Gannon works on the development of Cognitive Engine-1 in the Cognitive Communications Lab at NASA’s Glenn Research Center.
7. Make Way for Next-Gen Tech
Our Technology Education Satellite program organizes collaborative missions that pair university students with researchers to evaluate how new technologies work on small satellites, also known as CubeSats. In 2024, cognitive communications technology, designed to enable autonomous space communications systems, was successfully tested in space on the Technology Educational Satellite 11 mission. Autonomous systems use technology reactive to their environment to implement updates during a spaceflight mission without needing human interaction post-launch.

A first: All six radio frequency antennas at the Madrid Deep Space Communication Complex, part of NASA’s Deep Space Network (DSN), carried out a test to receive data from the agency’s Voyager 1 spacecraft at the same time.
8. Six Are Better Than One
On April 20, 2024, all six radio frequency antennas at the Madrid Deep Space Communication Complex, part of our Deep Space Network, carried out a test to receive data from the agency’s Voyager 1 spacecraft at the same time. Combining the antennas’ receiving power, or arraying, lets the network collect the very faint signals from faraway spacecraft.
Here’s to another year connecting Earth and space.
Make sure to follow us on Tumblr for your regular dose of space!
1K notes
·
View notes
Text
INTERNAL AFFAIRS INCIDENT REPORT
DRC Internal Affairs Division
Date: [REDACTED]
Subject: Internal Audit - Quota Breach - Case File [REDACTED]
To: Director [REDACTED]
From: Inspector [REDACTED]
I: Audit Trigger
This audit originated from an anomaly flagged by the Compound Oversight Unit following a routine cross-comparison of mortality curves, biometric telemetry, and average fetal volume expansion across paternity compounds in FEMA Zone 5. Paternity Compound 144, in particular, demonstrated a statistically aberrant rise in surrogate experience [REDACTED] collapse, a condition only observed in gestations over 18 fetuses. While the facility’s internal reports claimed average pregnancies between 8 and 11 embryos per surrogate, biometric logs suggested fetal counts ranging from 18 to 23 embryos per case.
Due to the severity of the physiological strain such numbers would imply—and the lack of official documentation acknowledging it—a Level 2 Integrity Audit was ordered. The Internal Affairs Division performed an unannounced sweep of all surrogate biometric records, insemination logs, and surveillance data from Cycles [REDACTED] to [REDACTED].
What followed revealed not only systemic concealment of lethal overloads but also willful obstruction motivated by personal psychological deviance.
II: Surveillance Analysis
Biometric data recovered from Wards 3B through 7E indicated that surrogates began exhibiting rapid and extreme abdominal distension by Day 11, surpassing known volumetric thresholds typically seen by Day 17. Skin tension diagnostics showed redlining stretch marks and dermal fissures in [REDACTED]% of all recorded subjects. In multiple cases, respiratory compression and full [REDACTED] subluxation—typically observed only after Day 30—were logged as early as Day 19.
“We knew something was off when they were too big to move before the second week. One of them just looked like that blueberry girl from Willy Wonka or some shit. But the logs said 14 embryos, so we assumed it was just edema.” - Employee GS-144-217
Footage recovered showed numerous surrogates experiencing aggressive fetal growth and abdominal distension, with growth rates in Ward 6C indicative of at least 23-25 embryonic masses. Two surrogates suffered multi-organ [REDACTED] before a team from the Compound Oversight Unit could intervene, though all fetuses were successfully delivered via cesarean.
“We knew something when we saw the guys from Ward 2. We were blimps compared to them, and they were twice as far along as us. I mean, I can literally see my belly growing!” Surrogate, later determined to be carrying quattuorvigintuplets (24)
Despite this, the internal logs submitted to the Archive Management Unit recorded all affected surrogates as having a “successful delivery with standard expiration.” The discrepancy was manually edited at terminal station 144-T12-OP47—registered to an Insemination Operations Unit employee named [REDACTED] (Employee ID IO-144-611).
III. Device Failure & Impact
Each MNAIS unit in Ward Blocks 3–7 had suffered [REDACTED] desynchronization following an outdated firmware push. Rather than delivering the standard 8-12-embryo load, units programming applied a multiplier to its quota and began injecting up to 24 fertilized embryos per cycle, with no error code generated.
Employee IO-144-611 discovered this failure within three days but refrained from submitting a maintenance report. He manually edited implantation records to match quota expectations, falsely logging a randomization formula (6–11 embryos per surrogate) across all documentation streams. Employee IO-144-611 then overrode the automatic alert system from the local Postpartum Command, which would ultimately log surrogates giving birth to higher fetal quotas than inseminated with.
His actions delayed DRC response for 41 days, during which:
42 surrogates suffered [REDACTED] rupture before Day 28, [REDACTED] overload, or uterine [REDACTED], necessitating emergency C-sections. No fetal fatalities.
17 surrogates expired mid-labor after undergoing compound [REDACTED] due to displaced [REDACTED], necessitating emergency C-sections. No fetal fatalities.
3 surrogates, against all medical prediction, reached Day 33 and birthed successfully, but ultimately expired post-extraction. No fetal fatalities.
26 surrogates still gestating, average 19 embryos per individual.
IV. Behavioral Profile – Employee IO-144-611
Subject: Employee IO-144-611 Tenure: [REDACTED] Position: Regional Implantation Supervisor Clearance Level: Tier II – Override Authorization Security Clearance: Revoked as of [REDACTED]
Following confrontation and seizure of his local system access logs, Employee IO-144-611 was detained and subjected to a Tier III Psychological Assessment. During this evaluation, the root of the concealment was uncovered.
Psychological Findings:
Employee IO-144-611 exhibited a previously undiagnosed paraphilic fixation classified under Government Code [REDACTED]: Macrophilia, a pathological sexual arousal in response to abnormally large bodies or bodily expansion.
Upon exposure to the visual data of overloaded surrogates—particularly those carrying between 19 and 23 fetuses—Employee IO-144-611 demonstrated elevated oxytocin and dopamine levels, a flushed dermal response, and sustained pupil dilation.
Under questioning, he confessed:
“I couldn’t report it. If I said anything, they’d shut it down, recalibrate the racks, lower the numbers again. You don’t understand. They were… monumental.”
He further admitted to deliberately withholding service requests for malfunctioning implantation equipment, specifically the Multi-Nozzle Accelerated Implantation System (MNAIS) units, which had developed a systemic fault causing them to implant +[REDACTED]% above calibrated embryo counts.
V: Displincary Response
1. Equipment
All MNAIS systems in Paternity Compound 144 were ordered offline for 24 hours.
Software rollback and integrity checks were completed under the supervision of IT Command.
Ward 3B was closed to all personnel below Grade-D rank, and affected surrogates were contained to minimize public awareness.
2. Actions
Psychological Services Command has formally reclassified [REDACTED] Employee IO-144-611 as Class-A Deviant – Mentally Compromised via Paraphilic Obstruction.
Archive Management Unit has censored relevant administrative records.
Public Affairs Division has disseminated a press release to DRC-approved news channels, citing [REDACTED] as the cause of the shutdown for Paternity Compound 144.
Facility Operations Command has transferred any personnel who raised professional or personal concerns about the citation.
[REDACTED] Employee IO-144-611 detained to Isolation Cell 6E.
3. Recommended Process Updates
Expand psychological screening to all Grade C employees and below.
Recommend quarterly psychological deviance evaluations of Grade B employees and below.
Implement full biometric auto-logging for all surrogate embryo counts—disable manual override across zones.
Closing Remarks
Employee IO-144-611's indulgence in personal gratification resulted in unsatisfactory delays to our facility's operation. Proper procedures have been implemented to prevent further disruptions and ensure that fetal quotas are adequately maintained.
[Report prepared by Inspector [REDACTED]]
----------------
Sending...
Sending...
Sending...
Read...
----------------
Date: [REDACTED]
To: Deputy-Director [REDACTED], Security Office
From: Director [REDACTED]
Subject: Internal Audit - Quota Breach - Case File [REDACTED]
Deputy Director,
Following my review of the [REDACTED] file, I would like to register my formal dissatisfaction with how Inspector [REDACTED] handled this matter. While I acknowledge the necessity of enforcing procedural transparency, the inspector’s decision to escalate the MNAIS malfunction as a containment emergency rather than a potential breakthrough reveals a worrying lack of vision.
To put it plainly, the equipment failure at Paternity Compound 144 resulted in spontaneous fetal yields well above the current national minimums, with documented gestations ranging from 18 to 23 embryos—many of which progressed past Day 25 with surprisingly high internal cohesion and containment. Had Inspector [REDACTED] exercised creative initiative, the anomaly could have been reframed as a pilot overcapacity trial rather than triggering a full-blown mechanical audit and unnecessary decommissioning.
Such a rigid interpretation of oversight policy has compromised a unique opportunity for data extraction and jeopardized our ability to scale gestational loads in future cycles. This shortsighted compliance fanaticism is increasingly common in mid-tier personnel and must be corrected.
Accordingly, I recommend that Inspector [REDACTED] receive formal censure and retraining through the Training & Development Unit for failing to recognize the strategic potential embedded in abnormal conditions. Our agency requires flexibility under pressure, not reflexive alarmism.
On a separate but related note, I would like to approve the personnel reassignment request for Employee IO-144-611. Despite his classified psychological profile, his unique enthusiasm may prove operationally useful if adequately directed. I am authorizing his immediate transfer to Site [REDACTED], where he is to assume the role of Supervisory Insemination Officer. In the correct environment, they are an asset and IO-144-611’s tendencies are no longer a liability.
Please liaise with the Facility Director [REDACTED] at Site [REDACTED] to ensure the transfer.
This matter is now considered closed from my office.
Regards,
Director [REDACTED]

#mpreg#mpregkink#malepregnancy#mpregbelly#pregnantman#mpregmorph#mpregcaption#mpregstory#mpregbirth#mpregart#mpregnancy#aimpreg#mpregroleplay#malepregnant#caucasianmpreg
56 notes
·
View notes
Text
ever wonder why spotify/discord/teams desktop apps kind of suck?
i don't do a lot of long form posts but. I realized that so many people aren't aware that a lot of the enshittification of using computers in the past decade or so has a lot to do with embedded webapps becoming so frequently used instead of creating native programs. and boy do i have some thoughts about this.
for those who are not blessed/cursed with computers knowledge Basically most (graphical) programs used to be native programs (ever since we started widely using a graphical interface instead of just a text-based terminal). these are apps that feel like when you open up the settings on your computer, and one of the factors that make windows and mac programs look different (bc they use a different design language!) this was the standard for a long long time - your emails were served to you in a special email application like thunderbird or outlook, your documents were processed in something like microsoft word (again. On your own computer!). same goes for calendars, calculators, spreadsheets, and a whole bunch more - crucially, your computer didn't depend on the internet to do basic things, but being connected to the web was very much an appreciated luxury!
that leads us to the eventual rise of webapps that we are all so painfully familiar with today - gmail dot com/outlook, google docs, google/microsoft calendar, and so on. as html/css/js technology grew beyond just displaying text images and such, it became clear that it could be a lot more convenient to just run programs on some server somewhere, and serve the front end on a web interface for anyone to use. this is really very convenient!!!! it Also means a huge concentration of power (notice how suddenly google is one company providing you the SERVICE) - you're renting instead of owning. which means google is your landlord - the services you use every day are first and foremost means of hitting the year over year profit quota. its a pretty sweet deal to have a free email account in exchange for ads! email accounts used to be paid (simply because the provider had to store your emails somewhere. which takes up storage space which is physical hard drives), but now the standard as of hotmail/yahoo/gmail is to just provide a free service and shove ads in as much as you need to.
webapps can do a lot of things, but they didn't immediately replace software like skype or code editors or music players - software that requires more heavy system interaction or snappy audio/visual responses. in 2013, the electron framework came out - a way of packaging up a bundle of html/css/js into a neat little crossplatform application that could be downloaded and run like any other native application. there were significant upsides to this - web developers could suddenly use their webapp skills to build desktop applications that ran on any computer as long as it could support chrome*! the first applications to be built on electron were the late code editor atom (rest in peace), but soon a whole lot of companies took note! some notable contemporary applications that use electron, or a similar webapp-embedded-in-a-little-chrome as a base are:
microsoft teams
notion
vscode
discord
spotify
anyone! who has paid even a little bit of attention to their computer - especially when using older/budget computers - know just how much having chrome open can slow down your computer (firefox as well to a lesser extent. because its just built better <3)
whenever you have one of these programs open on your computer, it's running in a one-tab chrome browser. there is a whole extra chrome open just to run your discord. if you have discord, spotify, and notion open all at once, along with chrome itself, that's four chromes. needless to say, this uses a LOT of resources to deliver applications that are often much less polished and less integrated with the rest of the operating system. it also means that if you have no internet connection, sometimes the apps straight up do not work, since much of them rely heavily on being connected to their servers, where the heavy lifting is done.
taking this idea to the very furthest is the concept of chromebooks - dinky little laptops that were created to only run a web browser and webapps - simply a vessel to access the google dot com mothership. they have gotten better at running offline android/linux applications, but often the $200 chromebooks that are bought in bulk have almost no processing power of their own - why would you even need it? you have everything you could possibly need in the warm embrace of google!
all in all the average person in the modern age, using computers in the mainstream way, owns very little of their means of computing.
i started this post as a rant about the electron/webapp framework because i think that it sucks and it displaces proper programs. and now ive swiveled into getting pissed off at software services which is in honestly the core issue. and i think things can be better!!!!!!!!!!! but to think about better computing culture one has to imagine living outside of capitalism.
i'm not the one to try to explain permacomputing specifically because there's already wonderful literature ^ but if anything here interested you, read this!!!!!!!!!! there is a beautiful world where computers live for decades and do less but do it well. and you just own it. come frolic with me Okay ? :]
*when i say chrome i technically mean chromium. but functionally it's same thing
461 notes
·
View notes
Text
Grist doesn't have a paywall, so if you want to read this story, just do the click/tap routine on the caption. The story is long, informative and important. I never considered how integrated our food system has to be (and has been) and how destructive trump's approach is.
Excerpt from this Grist story:
Despite its widespread perception, the U.S. Department of Agriculture is involved in much more than farming. The federal agency, established in 1862, is made up of 29 subagencies and offices and just last year was staffed by nearly 100,000 employees. It has an annual budget of hundreds of billions of dollars. Altogether it administers funding, technical support, and regulations for: international trade, food assistance, forest and grasslands management, livestock rearing, global scientific research, economic data, land conservation, rural housing, disaster aid, water management, startup capital, crop insurance, food safety, and plant health.
In just about 100 days, President Donald Trump and Secretary of Agriculture Brooke Rollins have significantly constrained that breadth of work.
Since Trump’s inauguration, the inner workings of the agency have been in a constant state of flux — thousands of staffers were terminated only to be temporarily reinstated; entire programs have been stripped down; and a grant freeze crippled state, regional, and local food systems that rely on federal funding.
What’s more, the USDA has broadly scrapped Biden-era equity and climate resilience scoring criteria from dozens of programs across multiple subagencies by banning language like “people of color” and “climate change,” and tightened eligibility requirements for food benefits. The agency has also announced the cancellation of environmental protections against logging to ramp up timber production, escalated trade tensions with Mexico, eradicated food safety processes like limiting salmonella levels in raw poultry, and begun rolling back worker protections in meat processing plants.
In order to report on the full scope of the downstream impacts of these actions, Grist interviewed farmers, food businesses, and agricultural nonprofits across seven states about what the first 100 days of the administration has looked like for them. Nearly all of them told Grist that the agriculture department’s various funding cuts and decisions, as well as the moves to shrink its workforce capacity, have changed how much trust they have in the agency — and, by extension, the federal government.
Food policy analysts and experts throughout the nation also told Grist that this swift transformation of the USDA is unprecedented.
“Multiple parts of our food systems are now under attack,” said Teon Hayes, a policy analyst at the Center for Law and Social Policy. At the same time, food prices and overall costs of living are continuing to rise. The result, she fears, will be escalating hunger and poverty, which will “come at the expense of Black and brown communities, immigrants, and other historically marginalized groups.”
Elizabeth Lower-Basch, who served on the USDA Equity Commission during the Biden administration, called the decisions made by the USDA in the last 100 days “deeply disheartening” and “unprecedented, even when you compare it to the last Trump administration.”
It is of significant consequence to note that the money being withheld from grant programs isn’t merely not being spent. Experts say the agency is taking support away from local and regional food systems while at the same time showering industrial agricultural operations with billions of dollars, eliminating nutrition safety nets, and rolling back environmental protections. How will this change the fabric of the nation’s food supply?
As Rollins and Trump charge forward in undoing how the federal government has long supported those who grow and sell our food, and climate change continues to deepen inequities and vulnerabilities in that very supply chain, one thing is obvious: The USDA, and the communities that rely on it, won’t look the same once they’re done.
#agriculture#farming#food#department of agriculture#forests#conservation#climate hange#public health#water management#trump
33 notes
·
View notes
Text
🇹🇷🔥 Turkish Air Force - F-4E 2020 Terminator
The F-4E 2020 Terminator represents a significant leap forward in the capabilities of the Turkish Air Force. This comprehensive upgrade enhances the venerable F-4E Phantom II with modern Turkish-made weapons systems, showcasing Türkiye’s commitment to self-reliance and advanced military technology.
Background
With a storied history dating back to the 1960s, the F-4E Phantom II has been a pivotal player on the global stage of air combat. Serving multiple nations and seeing numerous conflicts, the Phantom carved out its place in aviation history as a versatile and rugged aircraft. Türkiye’s decision to upgrade this aircraft stems from a strategic imperative to leverage existing assets while infusing them with cutting-edge technology to maintain relevance in modern aerial warfare. The 2020 Terminator program is the Turkish Air Force’s ambitious initiative to retrofit these fighters with state-of-the-art systems.
Strategic Importance
The ability to exert air superiority and conduct precision strikes is paramount in a region marked by dynamic security challenges. The F-4E 2020 Terminator’s enhanced capabilities contribute significantly to deterrence, and the demonstration of Türkiye’s advancing aerospace industry serves both a strategic and diplomatic purpose.
Upgrade Overview
The 2020 Terminator upgrade, realized by Turkish Aerospace Industries in collaboration with ASELSAN, constitutes a multifaceted improvement over the aircraft’s original design. It touches every aspect of the aircraft’s systems, bringing its avionics, armaments, and electronic warfare systems into the 21st century.
Avionics:
The modernized multi-mode pulse Doppler radar extends the aircraft’s detection range, allowing it to lock onto and engage targets from greater distances. Integrating a Hands-On Throttle-And-Stick (HOTAS) system enhances pilot control, minimizing response time during high-stakes manoeuvres. Color Multifunctional Displays (MFDs) replace outdated gauges, providing pilots with real-time data visualization for improved situational awareness.
Armament:
The Terminator’s weapons suite has been revolutionized with a mixture of Western and indigenous munitions. Long-standing armaments like the AIM-9X Sidewinder are joined by Türkiye’s own precision-guided munitions, such as the SOM cruise missile, capable of striking strategic land and sea targets with formidable accuracy. The UAV-230, a domestic innovation, represents the pinnacle of Türkiye’s missile development, offering supersonic ballistic delivery of a range of warhead types over substantial distances. The BOZOK, MAM-C, MAM-L, and Cirit missiles exemplify Türkiye’s expertise in laser guidance and smart munition technology, enabling the Terminator to engage and defeat a broad spectrum of target profiles with unerring precision.
Electronic Warfare:
To contend with the contemporary battlefield’s electronic warfare environment, the F-4E 2020 Terminator incorporates an advanced Electronic Support Measures (ESM) system for rapid threat identification and an Electronic Countermeasures (ECM) suite to confound hostile tracking systems. Moreover, chaff and flare dispensers have been integrated to provide decoys against incoming missile threats, enhancing the aircraft’s survivability in hostile airspace.
Operational Capability:
The F-4E Phantom II, transformed by these integrated systems, emerges as a multirole platform capable of dominating beyond-visual-range air-to-air engagements and precision ground-attack missions. It can operate in complex electronic warfare environments and deliver various ordnances based on mission requirements, making it a flexible asset in the Türkiye Air Force’s inventory.
Significance:
The F-4E 2020 Terminator project is a hallmark of Türkiye’s aerospace ambition and its push toward defence autonomy. By retrofitting and modernizing its Phantoms, Türkiye maximizes the value of its existing fleet while also establishing a foundation for future indigenous aircraft development projects.
Munitions Details:
The advanced, indigenous Turkish weaponry integrated into the F-4E 2020 Terminator underlines a significant shift toward self-reliance in defence technologies. Each munition type brings unique capabilities that enhance the platform’s lethality:
UAV-230: A domestically-developed ballistic missile, this supersonic weapon delivers high-precision strikes at long ranges, challenging enemy defences with its speed and reduced radar cross-section.
BOZOK: The versatility of this laser-guided munition makes it ideal for engaging both stationary and moving targets with high precision, ideal for close air support.
MAM-C/L: These smart micro munitions are designed for tactical flexibility, allowing for precision targeting in complex engagement scenarios, from anti-armour operations to counter-insurgency roles.
Cirit: A highly accurate laser-guided missile system designed for low collateral damage, Cirit is adept at striking soft and lightly armoured targets with pinpoint accuracy.
SAGE Munitions: TUBITAK SAGE, Türkiye’s leading defence research and development institute, has contributed a range of munitions enhancing the Terminator’s operational capabilities across various domains.
Conclusion:
The upgraded F-4E 2020 Terminator is a testament to Türkiye’s determination to retain a competitive edge in aerospace and defence technologies. The integration of modern avionics, armaments, and electronic warfare capabilities ensures the aircraft’s continued relevance in modern air combat, and its presence in the skies serves as a deterrent in a strategically complex region.
#turkish army#turkish armed forces#turkish air force#turkishnavy#turkish navy#turkish#military#aircraft#air force#fighter jet#aviation#fighter plane#plane#airplane#military aviation#military aircraft#f 4 phantom ii#f 4 phantom#f 4e
130 notes
·
View notes
Text
The Story of KLogs: What happens when an Mechanical Engineer codes
Since i no longer work at Wearhouse Automation Startup (WAS for short) and havnt for many years i feel as though i should recount the tale of the most bonkers program i ever wrote, but we need to establish some background
WAS has its HQ very far away from the big customer site and i worked as a Field Service Engineer (FSE) on site. so i learned early on that if a problem needed to be solved fast, WE had to do it. we never got many updates on what was coming down the pipeline for us or what issues were being worked on. this made us very independent
As such, we got good at reading the robot logs ourselves. it took too much time to send the logs off to HQ for analysis and get back what the problem was. we can read. now GETTING the logs is another thing.
the early robots we cut our teeth on used 2.4 gHz wifi to communicate with FSE's so dumping the logs was as simple as pushing a button in a little application and it would spit out a txt file
later on our robots were upgraded to use a 2.4 mHz xbee radio to communicate with us. which was FUCKING SLOW. and log dumping became a much more tedious process. you had to connect, go to logging mode, and then the robot would vomit all the logs in the past 2 min OR the entirety of its memory bank (only 2 options) into a terminal window. you would then save the terminal window and open it in a text editor to read them. it could take up to 5 min to dump the entire log file and if you didnt dump fast enough, the ACK messages from the control server would fill up the logs and erase the error as the memory overwrote itself.
this missing logs problem was a Big Deal for software who now weren't getting every log from every error so a NEW method of saving logs was devised: the robot would just vomit the log data in real time over a DIFFERENT radio and we would save it to a KQL server. Thanks Daddy Microsoft.
now whats KQL you may be asking. why, its Microsofts very own SQL clone! its Kusto Query Language. never mind that the system uses a SQL database for daily operations. lets use this proprietary Microsoft thing because they are paying us
so yay, problem solved. we now never miss the logs. so how do we read them if they are split up line by line in a database? why with a query of course!
select * from tbLogs where RobotUID = [64CharLongString] and timestamp > [UnixTimeCode]
if this makes no sense to you, CONGRATULATIONS! you found the problem with this setup. Most FSE's were BAD at SQL which meant they didnt read logs anymore. If you do understand what the query is, CONGRATULATIONS! you see why this is Very Stupid.
You could not search by robot name. each robot had some arbitrarily assigned 64 character long string as an identifier and the timestamps were not set to local time. so you had run a lookup query to find the right name and do some time zone math to figure out what part of the logs to read. oh yeah and you had to download KQL to view them. so now we had both SQL and KQL on our computers
NOBODY in the field like this.
But Daddy Microsoft comes to the rescue
see we didnt JUST get KQL with part of that deal. we got the entire Microsoft cloud suite. and some people (like me) had been automating emails and stuff with Power Automate

This is Microsoft Power Automate. its Microsoft's version of Scratch but it has hooks into everything Microsoft. SharePoint, Teams, Outlook, Excel, it can integrate with all of it. i had been using it to send an email once a day with a list of all the robots in maintenance.
this gave me an idea
and i checked
and Power Automate had hooks for KQL
KLogs is actually short for Kusto Logs
I did not know how to program in Power Automate but damn it anything is better then writing KQL queries. so i got to work. and about 2 months later i had a BEHEMOTH of a Power Automate program. it lagged the webpage and many times when i tried to edit something my changes wouldn't take and i would have to click in very specific ways to ensure none of my variables were getting nuked. i dont think this was the intended purpose of Power Automate but this is what it did
the KLogger would watch a list of Teams chats and when someone typed "klogs" or pasted a copy of an ERROR mesage, it would spring into action.
it extracted the robot name from the message and timestamp from teams
it would lookup the name in the database to find the 64 long string UID and the location that robot was assigned too
it would reply to the message in teams saying it found a robot name and was getting logs
it would run a KQL query for the database and get the control system logs then export then into a CSV
it would save the CSV with the a .xls extension into a folder in ShairPoint (it would make a new folder for each day and location if it didnt have one already)
it would send ANOTHER message in teams with a LINK to the file in SharePoint
it would then enter a loop and scour the robot logs looking for the keyword ESTOP to find the error. (it did this because Kusto was SLOWER then the xbee radio and had up to a 10 min delay on syncing)
if it found the error, it would adjust its start and end timestamps to capture it and export the robot logs book-ended from the event by ~ 1 min. if it didnt, it would use the timestamp from when it was triggered +/- 5 min
it saved THOSE logs to SharePoint the same way as before
it would send ANOTHER message in teams with a link to the files
it would then check if the error was 1 of 3 very specific type of error with the camera. if it was it extracted the base64 jpg image saved in KQL as a byte array, do the math to convert it, and save that as a jpg in SharePoint (and link it of course)
and then it would terminate. and if it encountered an error anywhere in all of this, i had logic where it would spit back an error message in Teams as plaintext explaining what step failed and the program would close gracefully
I deployed it without asking anyone at one of the sites that was struggling. i just pointed it at their chat and turned it on. it had a bit of a rocky start (spammed chat) but man did the FSE's LOVE IT.
about 6 months later software deployed their answer to reading the logs: a webpage that acted as a nice GUI to the KQL database. much better then an CSV file
it still needed you to scroll though a big drop-down of robot names and enter a timestamp, but i noticed something. all that did was just change part of the URL and refresh the webpage
SO I MADE KLOGS 2 AND HAD IT GENERATE THE URL FOR YOU AND REPLY TO YOUR MESSAGE WITH IT. (it also still did the control server and jpg stuff). Theres a non-zero chance that klogs was still in use long after i left that job
now i dont recommend anyone use power automate like this. its clunky and weird. i had to make a variable called "Carrage Return" which was a blank text box that i pressed enter one time in because it was incapable of understanding /n or generating a new line in any capacity OTHER then this (thanks support forum).
im also sure this probably is giving the actual programmer people anxiety. imagine working at a company and then some rando you've never seen but only heard about as "the FSE whos really good at root causing stuff", in a department that does not do any coding, managed to, in their spare time, build and release and entire workflow piggybacking on your work without any oversight, code review, or permission.....and everyone liked it
#comet tales#lazee works#power automate#coding#software engineering#it was so funny whenever i visited HQ because i would go “hi my name is LazeeComet” and they would go “OH i've heard SO much about you”
64 notes
·
View notes
Text
On Accepting Victories Where They Come
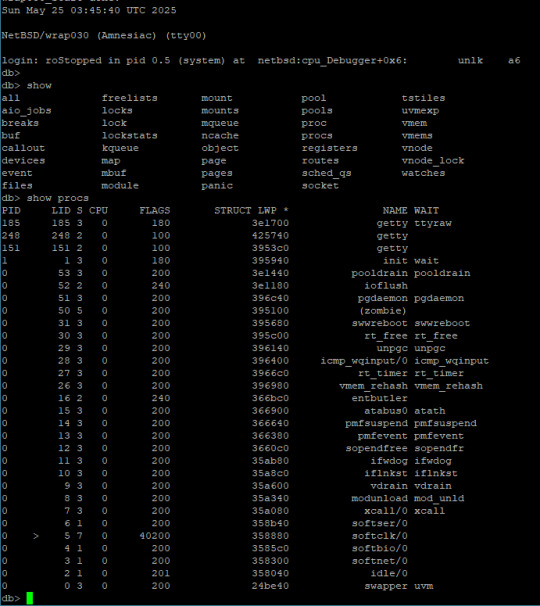
At the end of my last post on getting NetBSD running on my 68030 homebrew computer, I had a (mostly) working root shell prompt in single-user mode.
Well here we are a week or so later and I have ... a (mostly) working root shell prompt in single-user mode.
It turns out bringing up a modern operating system is hard.
The first problem was the default collection of init scripts. There are a ton of scripts in /etc/rc.d that are run at startup to finish bringing up the system after the kernel is loaded but before users can log in. These scripts do things like check filesystem integrity, mount disks, initialize networking, etc. Most of the scripts are not relevant to my specific hardware, but I wasn't even getting far enough along for that to matter. I was getting stuck early on in two steps in particular: filesystem checks and initializing /dev/random.
The latter issue there's not really anything I can do about. I can copy a pre-populated entropy file from an existing system, but I don't have the hardware support for random number generation. Frankly I don't need it either, if I'm not doing anything with cryptography like using TLS certificates. So remove that script.
I can check and repair the filesystem much faster on my host machine, so remove that script for now also.
And remove all of those networking-related scripts since I don't have the hardware for networking either.
…
It turns out init scripts have declared dependencies on other scripts. So removing one, especially an early important one like checking filesystem, means editing others to continue without it. It's dependency hell.
So for the sake of just getting things running, I removed everything and wrote my own. There were just a few things I really needed, like mounting the root filesystem as writeable and initializing TTYs.
It took a few tries to get it right, but my init script did eventually run without stalling. This was it, time for it to initialize the terminals and print the login prompt …
init: can't add utmpx record for 'tty01': Bad file descriptor
… That's not a login prompt. That's not a login prompt at all. What does that even mean? What on earth is utmpx?
The error message itself is printed by init. UTMPX keeps record of logged-in users, and it does so using a file, /var/run/utmpx. But is the bad file descriptor error relating to that file or to /dev/tty01?
I was stuck here for a while. I tried everything I could think of to make sure my tty devices were created properly and with the right major/minor numbers and permissions. I finally realized that I didn't get the error if the utmpx file didn't exist. So something was wrong with writing the file, possibly due to never being able to properly shut down and close out the file & filesystem any time it got created. But it's easy enough to just make sure it's deleted by the init script before getting to that point.
It's at this point where I went down a rabbit hole of trying to create a RAM disk for root just to eliminate the possibility of lingering problems with the ATA driver or similar. This proved to be a dead end because the system would only boot single-user from a RAM disk, and I also got stuck in dependency hell trying to get it to compile a RAM disk image that included the actual login binary.
After some more experimentation, I learned that if I had no extra terminals defined in /dev/ttys, then it would at least show the login prompt on the root console, but would never actually log in. Kernel debugger & SIGINFO would show that login was stuck waiting for something. If I did have multiple terminals defined, I would never see a login prompt and it would show that getty, which spawns the terminals, was sleeping, waiting for something.
And that's where I'm stuck. I have no idea what these programs are waiting on, and don't really have any way to check. I suspect it's possible they need those hardware interrupts I don't have, but since I can see activity on the UART chip select lines, I don't think that's the case.
So for now, facing a looming deadline and burnout setting in after a solid month of working on this, I've decided to accept the victory I have and admit defeat where I must. I have a computer that I built myself which can load and run a modern operating system up to the point of a root shell prompt. That is a remarkable accomplishment and I will absolutely accept that victory. There is already so much the machine is capable of just getting to that point. And going from knowing nothing about porting an OS to a new machine to having a running shell in under a month is a victory all on its own.
But, I was not able to get it fully running in multi-user mode on all of my terminals. I will happily accept that defeat in light of the major victory of getting as far as I have.
So, with VCFSW coming up very soon, I've decided to turn my attention back to my multi-user BASIC system. I have a few refinements and new features in mind that I would love to have ready by the show.
#homebrew computing#mc68030#motorola 68k#motorola 68030#debugging#vcfsw#wrap030#vcf#Retrocomputing#NetBSD#homebrew computer
18 notes
·
View notes
Text




Round 2 - Simblr's Saddest, Wettest Meow Meow - Mainline
No. 27 (@literallyjusthereformods) VS. Andre St. Fleur (@armoricaroyalty)
(polls are presented left -> right unless stated otherwise)
Who's sadder? Who's wetter? Read on for more information, and vote with your heart!
What is a ‘Meow Meow’?
(taken from tumblr user @/torturelabyrinth) “The thing about a true poor little meow meow is they have to be 1) downtrodden 2) morally questionable at best 3) deeply and pathetically miserable”

No. 27
Alias: "Livard"
No. 27 was the 27th 'living' instance of the Crane Foundation's modern Quintessence Program. When the breach occurred, 27 took immediate opportunity to leave, using her sharp limbs to grievously wound operatives and other personnel who attempted to obstruct her path of escape. Eleven confirmed aggravated fatalities. An unknown number of fatalities occurring at trample areas and exit pileups. She proceeded to use the slaughter-path of the other breachers as a clear line out of the facility’s underground portion, ascending rapidly to the upper floors where she is believed to have fled the building.
As of right now, 27 is an immune carrier of a new strain of the same pathogen currently causing a cataclysmic outbreak. While typical variants can only infect and alter biological matter, this mutation was observed with the new ability to infect machines during controlled testing.
No. 27 was last spotted wearing the stolen cardigan of Dr. Livard, with a secondary article of clothing tied beneath at the waist. The owner of the second article has not yet been identified.
27 has been reported self-identifying as ‘Livard,’ and has not discarded the nametag attached to the stolen cardigan, despite having no reason to keep it.

27 was created as an experimental binding of biological tissues and cybernetics. Unlike precursors, who were constructed with biological matter on a 75% or higher percent mechanical endoskeleton, 27 was an experimental integration of traditionally classified ‘biological’ and traditionally classified ‘mechanical’ elements on a fundamental level. The use of nanites in her tissues, along with algorithmic adaptations, created a unique combined system challenging the preconceived definitions of the categories.
However, the arise of the new pathogen strain saw 27 strictly confined. 27 was shown to be incredibly observant of those observing her, and an incredibly accurate mimic of their behaviors. She, notably, engaged in a game of rock, paper, scissors with an anonymous researcher after they and their coworker demonstrated the game through the window.
Sentient or not, 27 still falls outside of the Mimic Law, and is legally property of the Crane Foundation. With artificial sentience having already been academically accepted years ago, whether 27’s curiosity is dictated by script or by consciousness is not our concern.
As for the present times, it was assumed 27 would perish shortly after leaving the facility, without the specific needs of her body being met in a controlled environment. Our assumptions were wrong. 27 has been spotted feeding on mechanical devices as if they were prey animals. We can only assume this habit will accelerate the spread of the new pathogen strain, and while we would like to reclaim 27 for study, it might become necessary to terminate her entirely to prevent escalation of the already dire world situation.
Originality Status: 100% Original Property of the Crane Foundation
Additional Notes:
(Attached below is a fabricated 3D model based on the last contained recording of 27. It is merely for visual context. If you are an operative searching for 27, or, in some inexplicable instance, creating a poll (Tom), please use the topmost image as it is the most up-to-date.)


Andre St. Fleur
What makes him a Sad, Wet Meow Meow? Born to royalty but completely temperamentally unsuited for it, Andre is pathetic and sad and weak-willed and a big, giant loser. He's the king of a small and unimportant country, and he simply cannot parent effectively or stop cheating on his wife. Finally forced to decide between his mistress and his wife of nearly 30 years, he became so paralyzed with indecision that he developed a terminal illness instead, saving him from ever having to make up his mind about anything.
Just some additional pictures of Andre moping, crying, and letting his loved ones down </3





I think my boy has the potential to go far, but even if he gets knocked out in the first round...what could be sadder, wetter, or more pathetic than getting immediately eliminated from the "most pathetic" tournament?
17 notes
·
View notes
Text
Day 15 (1/2)
Regional Control Centre


I woke in the middle of the night to see that Gaia had managed to unlock more of the facility. While she continued booting up, piecing herself back together with Minerva, I did a little more exploring.
As Gaia's integrated herself further with the Control Centre's systems, I can see a whole lot more with my Focus. Just scanning the server racks gives me information about each one, a summary of its internal data and its utility to us. She's been busy.


Most crucial in terms of utility: showers, sinks, and toilets. The plumbing is in ruins, but Gaia indicated that it wouldn't take much in way of repairs to get things patched up. It'd be amazing to get it all working—otherwise it's either out on the frigid mountain or down the elevator shaft.


There are sleeping quarters next to the amenities, four sections with a bed, desk, and plenty of storage space. The blankets have decomposed to scrap and the place reeks of mould, but with a bit of cleaning, it could be a nice place to stay. Better than a Nora bedhouse, for sure.


Gaia still didn't have all the rooms hooked into the power supply, but she unlocked a few for me to explore, one stocked with more servers and a smaller holographic projector. Again, Gaia had got their interfaces up and running to help me process their data on my Focus. There isn't much left; this place was meant to hold knowledge specific to operating and improving the terraforming system, but it was wiped clear along with Apollo.


There were a couple of offices accessible as well, similar to the offices in Zero Dawn facilities, but cleaner and better kept. They reminded me of Elisabet's office.
I don't need an office as such—with its physical monitors and old, creaky chairs—but I could use a place to stash my stuff, work on my gadgets and weapons. This is sure to worsen my hoarding problem. No more lugging everything around until I can pawn it off on the next merchant, and no more leaving stuff behind at secluded camps hoping it won't be stolen. I'm not going to let myself lose everything again.


The last accessible room was a little more useful—a lab, with a lot of mechanisms still operational. Most exciting was the fabrication terminal, a contraption capable of taking in scrap metal and other parts and rebuilding them to certain specifications. It was built to be interoperable with Gaia's machines, so using it to analyse and recreate structures from machine parts will help build the data I need to complete those corrupted override schemas I lifted from the Tau Cauldron core. I'm sure there's a whole lot more I can do with it too.
Watching it at work on a small test sample, tiny machines swirling behind the glass, it reminded me of the golden machine swarms wielded by the intruders at the Proving Lab. Maybe a more advanced form of similar technology?

Varl woke and joined me as I finished poking around the lab. He and Zo had similarly found somewhere passably warm to curl up. He wanted to know what was next; so did I. I tried not to come across as completely clueless about our plans going forward. I didn't tell him about the intruders at the lab, or the other clone. Not yet. Not until I know who they are and what they're really after.
As we were talking, Gaia called me over Focus to summon me back to the projection theatre. Her initialisation and merge with Minerva was complete. She was ready to talk and, I hoped, make everything clear.

She spoke to me first about the state of the biosphere. Not good, was the general prognosis. Gaia said it would only take about four months for the rabid terraforming system to degrade beyond all reasonable hope of repair. The good news was, since the RCC was built for long range communication, unlike Latopolis, Gaia could now run a far more sophisticated scan for the escaped subfunctions. However, the scan could take days or more likely weeks to complete, given she'd have to pinpoint each function's mutated signature and circumvent the many techniques they've likely employed to hide themselves. The others are unlikely to be as forthcoming as Minerva.
The only subfunction that Gaia could detect deafeningly loud and blindingly clear was Hephaestus. Figures, I've seen it around too. Gaia explained that it's scattered across the global Cauldron network, and in any attempt to capture it, it would simply slip away to some distant location, as I'd experienced at Firebreak and in Cauldron Tau. It had no reason to hide its activities.
Gaia would continue devising a plan to lock it out of the network and capture it, though attempting to do so before she had been reunited with at least three more of her subfunctions would lead to disaster. Hephaestus had mutated to a dangerous degree since the original Gaia's self-destruction. Given freedom of movement it had grown massive, volatile, and hostile; as it absorbed Cyan, it would absorb this more rudimentary, weaker version of Gaia with ease. She needed to be powerful enough to match it in battle by increasing her 'processing density'. The mission remained as it always had been: repair Gaia. Just because she was here, speaking and smiling and strategising, that didn't mean I was done. Far from it.


Hephaestus is our most important target. Without it, Gaia can't build machines of her own or take control of the Cauldron network. The machines are like her tools, her hands, able to act upon her orders and bring the terraforming system back into balance. With the other subfunctions, she would be able to enact some measure of change using existing machines and facilities to temper the most acute affects of system collapse, but without new machines to join the effort, that temperance wouldn't last long. That's to say nothing of the threat of Hephaestus itself as it continues to take direct control of Cauldrons, building more dangerous machines meant to cull humankind to make way for its own purple progeny.
So that's problem one: we need at least three subfunctions, along with a plan to bring Hephaestus to heel. We still have no clue where those other subfunctions could be, if they still exist, except that they'll be hiding in processor cores somewhere within rapid networking distance of Gaia Prime. That only leaves just about everywhere not on the other side of an ocean, if I'm lucky.
Gaia said she will devote as much of her internal resources as possible to detecting more of her subfunctions and notify me as soon as they're located. There's not much sense in me striking out into the open before then, especially with what I know is waiting for me, wanting me dead and well out of their way.
I asked Gaia then about the strangers at the Proving Lab.


She'd seen the whole encounter through my Focus, and she shared in my unease. She then laid out her theory, and it was worse than I ever speculated. Bombshell one: the signal that woke Hades, which Gaia ominously calls 'the extinction signal', didn't come from anywhere on Earth. She showed me, in projection form, Earth from a distance, moon and stars surrounding, then pulled back, the image moving so fast that the stars were coloured streaks racing past us. I was transfixed; horrified, but morbidly awestruck. What was so far away that would want to harm us here on Earth? Other worlds, other life?

This was the distance that the signal travelled to reach Gaia, a length so vast that light itself takes 8.6 years to cross it. That number was familiar, somewhere in the back of my mind, but I didn't realise where I'd heard it until Gaia's projection reached its destination, the motion of light finally ceasing.

There it was, orbiting a planet of brown landmasses, dark blue oceans, and thick swirls of clouds: the Odyssey. It was the same projection that Osvald Dalgaard used in his presentation at the Far Zenith launch facility. 8.6 light years...he used the same figure when describing the Odyssey's destination, the Sirius system.
Gaia said it was the only logical origin, though realistically the signal could have come from any direction of the same approximate distance away. As Hades said, the signal repeated for 17.22 years, and Gaia explained as I continued trying to get my head around distances that light crossed at a long crawl. That was 8.6 years once the signal arrived, for the fact of its failure to reach its sender, and another 8.6 for the sender's ceasing order to make it back to Earth.
Working theory: Far Zenith lied about their shuttle's explosion. After Travis' attack on their systems, and their deal with Zero Dawn coming to an end, they clearly didn't trust the descendants of the project to leave them alone. I know that Elisabet's view of Far Zenith was less than favourable; maybe they saw that as a potential threat. So, Far Zenith fake the destruction of their ship to keep Zero Dawn off their backs for good, and stay hidden from those that the project would raise and educate under Gaia's care.
I know they were paranoid. In the Old World, no one knew who the members of Far Zenith were, and it seems like a large portion of the public hated them for their flagrant wealth and hoarded power. They kept themselves secret on Earth, then hid their presence in space. They tried to steal Gaia before they left Earth, then tried to use their 'extinction signal' to steal her again, planning to take the whole world down in the process. Why?

I suppose they didn't know that Apollo was destroyed, maybe they thought we were still a threat, but even so, we didn't know about them. We couldn't have known, thanks to their cover up. So, what was it? They sent their signal to wake Hades and destroy all life on Earth, clean it of 'filth', as Hades put it, and then what? They subdue Hades, reinstate Gaia and...re-program her, maybe. Use her to create the world that they want. Play god, just as Elisabet feared. This is why she didn't want to hand over a copy of Gaia in the first place, but in refusing, in retaliating...did she doom us, here and now?
I posed my thoughts to Gaia, and she agreed that it was her own conclusion as well. Far Zenith had always planned to flee Earth in its dying days. Maybe they always planned to return as well. Return and claim the world they once dominated.
I thought there was only one inheritor of the human legacy, but there were two. One, Elisabet's, and the other...the space-born descendants of Peter Tshivhumbe.
Gaia confirmed something else that Hades said: the signal was meant for it alone, and the mutations imparted on the other subfunctions were only incidental, only unleashed when Hades was unable to assume control fast enough as Gaia initiated self-destruction, something Far Zenith couldn't anticipate. It was an incredibly advanced piece of malware, as Sylens observed, and Gaia said that only someone with in-depth knowledge of her code structures and her system as a whole could have engineered it. So...maybe Far Zenith was able to steal more of Zero Dawn's data than Travis thought. Maybe they've been working on reverse-engineering it ever since.
Suddenly, the strangers at the Proving Lab made a whole lot more sense. Their advanced technology, their flashy weaponry, their gilded ornamentation...Far Zenith, grown formidable with the knowledge of the Old Ones, given by Zero Dawn, on their side. They came here to do what their extinction signal failed to do: wipe out life on Earth, and use a stolen backup of Gaia to build it all over again for them to rule, destroying Elisabet's dream forever.


And all I could think about was that clone, moving on their orders, silent, weak. How could she go along with this plan? She stole Gaia for them, handing her over to Elisabet's enemy for them to use, to twist into a weapon to destroy and remake the world into some abomination, some paradise for these people who think themselves entitled to the planet.
How did they make a clone in the first place? Why, when their technology is supposedly so powerful?
Gaia explained that Far Zenith could have obtained a sample of Elisabet's DNA, with or without her consent, and stored it on board the Odyssey along with their many Earth life samples and human zygotes. She said that even with their ability to engineer powerful malware, obtaining a physical backup of Gaia in a shut-down state could only be done by walking in and taking it, and only someone with Elisabet Sobeck's genetic code could do that. Far Zenith made the clone as a key, just as Gaia made me. The only crucial difference is I was made to save the world, not kill everything on it.
Gaia had her doubts about the clone. She seems to think it's more likely that she's a subordinate, some sort of slave forced to take their orders. No way. She's Elisabet Sobeck, just as much as I am, she's no subordinate. Elisabet loved life; she gave everything for this world, just for this clone to come along and destroy it all? No. Just the thought of her makes me sick.

So it's all down to me. I knew it would be; it always is. Gaia can't do much from here but keep scanning for the other subordinate functions. As soon as she finds them, I'll be her eyes and hands. Vessel, if we want to get all Nora about it. I'll have to go and load each subfunction onto the cartridge I found Gaia on, then bring them back here to merge into her new system. Meanwhile, that other clone is running around with Far Zenith, who likely have way more advanced scanning capabilities, hunting the subfunctions right alongside me, with their own version of Gaia to mold and command. If they get to Hephaestus first, merge it into their version of Gaia...it'll be over. They'll have control over every Cauldron on the planet. They'll rule the biosphere and be able to build whatever devastating weapons they can dream up to kill us all.
But if I can beat them to it, we'll have the upper hand. Enough damage will take down the Zenith's shields, which to my onslaught seemed impenetrable. With an army of machines, we'll have the ability to destroy Far Zenith and their Specters on Earth, but even then...how many more of them are out there? How far have they already spread across the stars? How long will this fight go on?
It's...a lot. It's everything. My hands leapt to Elisabet's pendant without my knowing, tracing its comforting shapes and textures. Peeling paint, rusted hinges; the last thing Elisabet ever touched. I couldn't help but profess my doubts to Gaia. Even if it wasn't exactly her idea to create me, it was a version of her. Somewhere in her un-lived future there's a part of her that believes I am her best hope to save this world.
She gave me comfort. After all, she'd listened to her predecessor's final message too, trusting it. She'd seen that future, and repeated its words. Though her phrasing was mechanical, flat, ringing against old metal, the message was the same as I'd always heard when facing adversity, from Rost. Though the odds may seem insurmountable, there is hope. You are capable. You have prevailed many times.
Look deeper. Keep moving forward.

Before I left the theatre, I noticed a console on the circumference of the room. Gaia told me more about it; it was meant for uploading and accessing footage from observation drones. These drones were meant to be deployed in an emergency when biosphere observation could not be handled by personnel in the RCC. The centre had deployed them automatically a few years ago, when the first signs of blight start showing up. It took something extremely anomalous to trigger the system, apparently, and due to its degradation, the RCC soon lost connection to all the dispatched drones.
So, that explained the drone I found circling near that Thunderjaw in No Man's Land. I was able to upload the data I'd taken off it to the console, allowing the RCC to reconnect to the drone. And there it was, a live feed of red rocks and rusted bots. Those closest stones almost looked real. I figured that reconnecting these drones could be of some use to Gaia, who can observe the lands through them until she takes control of the Cauldron network again. Until, no if's.

I spoke to Varl and Zo briefly before heading back out into the wilds. They plan on staying behind to get up to speed on things with Gaia and make some repairs to the centre's facilities. Who knows, maybe I'll come back to a working shower.
Without any clear direction to where the subfunctions might be hiding, I may as well make myself useful in doing what I can to help the people of these lands. After Hephaestus' attack, the Utaru are sure to be struggling, and with Regalla's rebels still prowling their territory, the danger isn't over.
Sylens and his little army fits into all of this somehow. He knew who the Zeniths were, I'm sure of it. I'm willing to bet he was using me as some sort of bargaining chip; he leads Far Zenith to a backup of Gaia and a clone of Elisabet, he asks for a copy of Apollo in return. Then he uses his army to, what, conquer? That doesn't seem like his style. Maybe he thought Far Zenith would let him join up, otherwise I have no idea how he was planning to survive their plan for the world. What a self-absorbed idiot.

I thought it'd be a quick journey down the mountain with my Shield Wing. Beautiful views, pleasant weather, and no signs of total war and ruin down in Plainsong.

Not so quick once the rain started and a few Skydrifters came swooping in. I kept them down with spark cell detonations before going in for spear strikes. Ropes to keep the others from moving around too much in the meantime. A Burrower came to join in too, but I silenced it before it could call any more machines to the area. Fortunately, none of them were Hephaestus' deadly creations.


Continuing on my way down, I passed a signal tower like the one I found back in the Daunt. Scanning it, I picked up another corrupted projection. I made the quick climb back up to the ruin on the rise to repair the image from its original vantage. It showed the turbines and satellite dishes that now house Plainsong.
It was another site of the Miriam Technologies tour. This satellite array was once used to detect and monitor near-Earth objects—big rocks, I guess—rich in minerals. Miriam Technologies developed machines for the automated mining of these minerals out in space. I guess there wasn't much left of the stuff on Earth after the Claw Back, but it's pretty cool to think about. Unfortunately, there's only one near-Earth object I need to be concerned with right now, and that's the fucking Odyssey.
No need to dwell on it right now. There are people here who need my help. I continued down toward Plainsong.
11 notes
·
View notes
Text
The Baltic states of Lithuania, Latvia, and Estonia are about to take a historic energy security step on February 9, when they will synchronize their former Soviet electricity systems with the Continental Europe Network (CEN). This will conclude the final chapter of Russia’s involvement in the energy sectors of these frontline European Union (EU) and NATO member states. But the Baltic states and their NATO allies must now work to secure this hard-won energy independence from Russia’s ongoing hybrid attacks on critical energy infrastructure.
Lithuania, Latvia, and Estonia have faced a wide array of Russian coercive energy policy measures arising from their historical dependence on Russian energy supplies and Soviet-era energy infrastructure. These measures included a total economic and energy blockade of Lithuania in 1990 in response to its independence movement, a prompt shutdown of an oil pipeline after Lithuania declined to sell its crude oil refinery to a Russian company in 2006, and long-term politically motivated gas pricing for the Baltics, to name just a few well-known cases.
Having faced the destructive impacts of Russia’s weaponization of energy, the Baltic states have become leaders among European nations in severing ties with Russia’s energy supplies over the past decade. The installation of the liquefied natural gas (LNG) terminal in Klaipėda, Lithuania’s seaport, in late 2014 marked a significant step in this direction. It opened the Baltic gas markets to global LNG suppliers, including those from the United States. This alternative gas supply route enabled the Baltic states to ban all Russian gas imports, both piped and LNG, just two months into Russia’s full-scale war against Ukraine. The Baltic states became the first European countries to take such a principled stance, and they are among those advocating for the rest of the EU members to follow suit by implementing a blanket ban on Russian LNG.
Flipping the switch
The timely diversification of oil and electricity supply routes also allowed the Baltics to stop importing these energy sources from Russia. In terms of electricity, the Baltic states use the interconnectors Estlink 1 and Estlink 2 between Estonia and Finland, Nordbalt between Lithuania and Sweden, and LitPol Link between Lithuania and Poland for power exchanges with Europe. However, the Baltic states’ early market-level integration with their EU neighbors did not mean the immediate end of Russia’s involvement in the their electricity sectors on the system control level.
These are the last days that the Baltic states’ power grids remain a part of the Russian-controlled Integrated Power System/United Power System (IPS/UPS) grid. This effectively means that a dispatch in Moscow is still responsible for maintaining electric frequency stability in the Baltic states—bringing all the risks that such a dependency on Moscow entails. Ukraine and Moldova performed a test desynchronization from the IPS/UPS grid concurrently with the onset of Russia’s invasion of Ukraine in 2022, immediately asking for an emergency synchronization with the European grid, which was granted. Lithuania was aware of the potential need to perform an emergency synchronization, too, and thus had prepared its power grid to function in an isolated mode if needed. On February 8, Lithuania, Latvia, and Estonia will decouple from the Russian-controlled grid and conduct a joint isolated operation test before joining the European grid on February 9.
The planning for the Baltic synchronization with the European grid began as early as 2007, but—due to multiple project phases involving political, regulatory, and infrastructural components in Lithuania, Latvia, Estonia, and Poland—it has only now been finalized. The project was co-financed by the EU, which has allocated more than €1.2 billion from its Connecting Europe Facility. For the EU, the project is as important as it is for the Baltic states: only with Lithuania, Latvia, and Estonia connected to the European grid can the EU achieve its goal of a fully integrated European energy market, in which all uncontrolled third-party impacts on its member states are eliminated.
Securing critical infrastructure
Although Russia will no longer exert direct influence over the energy supply and system control of the Baltic states, Moscow may now focus on targeting their critical energy, communications, and data infrastructure. Since October 2023, at least eleven cables running under the Baltic Sea have been damaged. This includes the underwater Balticconnector gas pipeline between Estonia and Finland; communications cables linking Finland, Germany, Sweden, and Lithuania; and the Estlink 2 power cable between Estonia and Finland. A data cable between Latvia and Sweden has been damaged as recently as January 26. The Lithuanian government is responding with increased military involvement in protecting critical seaborne energy infrastructure under the Baltic Sea amid an attempted sabotage of the NordBalt power cable that connects it to Sweden.
The damage was caused by vessels dragging their anchors on the Baltic Sea’s seabed. Investigations into the circumstances of the damage are still ongoing, but the rapid increase in such incidents and the vessels involved—mostly Russia’s “shadow fleet” oil tankers—raise concerns that the damage was intentional. As a response, NATO has stepped up its presence in the Baltic Sea by launching a new military patrol mission called Baltic Sentry. This mission involves deploying frigates, maritime patrol aircraft, and naval drones to enhance the ability of littoral states to respond to destabilizing acts on their critical infrastructure. The Alliance has also established a Critical Undersea Infrastructure Network to enhance information-sharing and situational awareness and a dedicated Maritime Centre for the Security of Critical Undersea Infrastructure within NATO’s Maritime Command in Northwood, United Kingdom.
Crucial first steps have also been made to increase the protection level of the onshore LitPol Link interconnector between Lithuania and Poland, through which the Baltics are synchronizing with the European grid. Lithuania’s Public Security Service has taken over the protection of several LitPol Link sites from a private security company that had previously been assigned this role. The Baltic states and Poland, fully aware of Russia’s hybrid activities in the region, have also urged the EU to provide financial support for enhancing current security measures for the LitPol Link and other critical energy infrastructure in the region.
It’s a start, but more needs to be done, particularly in the case of Lithuania. With vital interconnectors—LitPol Link in energy and Rail Baltica in transport and military logistics—passing through the country, Lithuania is emerging as a crucial gateway connecting continental Europe to the Baltics, the Nordic region, and even the Arctic.
All these interconnections traverse the narrow land corridor between Lithuania and Poland, known as the Suwałki Gap. This notorious area borders Belarus to the east and Russia’s Kaliningrad exclave to the west.
Russia could attempt to isolate the Baltics from the rest of Europe by obstructing the Suwałki Gap from these territories. Thus, beyond the punctual tactics of strengthening the security of the LitPol Link and, later, the planned additional onshore electricity interconnector between Lithuania and Poland that is reportedly set to run along the Rail Baltica tracks, an approach of a comprehensive protection regime for this vulnerable border area is needed. An increased NATO military presence in Lithuania and regional measures, such as installing the Baltic Defense Line along the Baltic states’ borders with mainland Russia, its Kaliningrad region, and Belarus, are important steps toward a solution.
With the Baltic power systems soon operating in harmony with those in continental Europe, the regional security agenda shifts from concerns over the security of energy supply to the protection of critical energy infrastructure. The Baltic nations and their allies should further enhance their proactive efforts to deter sabotage and secure this strategically vital region.
15 notes
·
View notes
Text

NASA progresses toward crewed moon mission with spacecraft and rocket milestones
Engineers, technicians, mission planners, and the four astronauts set to fly around the moon next year on Artemis II, NASA's first crewed Artemis mission, are rapidly progressing toward launch.
At the agency's Kennedy Space Center in Florida, teams are working around the clock to move into integration and final testing of all SLS (Space Launch System) and Orion spacecraft elements. Recently they completed two key milestones—connecting the SLS upper stage with the rest of the assembled rocket and moving Orion from its assembly facility to be fueled for flight.
"We're extremely focused on preparing for Artemis II, and the mission is nearly here," said Lakiesha Hawkins, assistant deputy associate administrator for NASA's moon to Mars Program, who also will chair the mission management team during Artemis II. "This crewed test flight, which will send four humans around the moon, will inform our future missions to the moon and Mars."
On May 1, technicians successfully attached the interim cryogenic propulsion stage to the SLS rocket elements already poised atop mobile launcher 1, including its twin solid rocket boosters and core stage, inside the spaceport's Vehicle Assembly Building (VAB). This portion of the rocket produces 24,750 pounds of thrust for Orion after the rest of the rocket has completed its job.
Teams soon will move into a series of integrated tests to ensure all the rocket's elements are communicating with each other and the Launch Control Center as expected. The tests include verifying interfaces and ensuring SLS systems work properly with the ground systems.
Meanwhile, on May 3, Orion left its metaphorical nest, the Neil Armstrong Operations & Checkout Facility at Kennedy, where it was assembled and underwent initial testing. There the crew module was outfitted with thousands of parts including critical life support systems for flight and integrated with the service module and crew module adapter.
After fueling is complete, the four astronauts flying on the mission around the moon and back over the course of approximately 10 days, will board the spacecraft in their Orion Crew Survival System spacesuits to test all the equipment interfaces they will need to operate during the mission. This will mark the first time NASA's Reid Wiseman, Victor Glover, and Christina Koch, and CSA (Canadian Space Agency) astronaut Jeremy Hansen, will board their actual spacecraft while wearing their spacesuits.
After the crewed testing is complete, technicians will move Orion to Kennedy's Launch Abort System Facility, where the critical escape system will be added. From there, Orion will move to the VAB to be integrated with the fully assembled rocket.
NASA also announced its second agreement with an international space agency to fly a CubeSat on the mission. The collaborations provide opportunities for other countries to work alongside NASA to integrate and fly technology and experiments as part of the agency's Artemis campaign.
While engineers at Kennedy integrate and test hardware with their eyes on final preparations for the mission, teams responsible for launching and flying the mission have been busy preparing for a variety of scenarios they could face.
The launch team at Kennedy has completed more than 30 simulations across cryogenic propellant loading and terminal countdown scenarios. The crew has been taking part in simulations for mission scenarios, including with teams in mission control. In April, the crew and the flight control team at NASA's Johnson Space Center in Houston simulated liftoff through a planned manual piloting test together for the first time. The crew also recently conducted long-duration fit checks for their spacesuits and seats, practicing several operations while under various suit pressures.
Teams are heading into a busy summer of mission preparations. While hardware checkouts and integration continue, in coming months the crew, flight controllers, and launch controllers will begin practicing their roles in the mission together as part of integrated simulations. In May, the crew will begin participating pre-launch operations and training for emergency scenarios during launch operations at Kennedy and observe a simulation by the launch control team of the terminal countdown portion of launch.
In June, recovery teams will rehearse procedures they would use in the case of a pad or ascent abort off the coast of Florida, with launch and flight control teams supporting. The mission management team, responsible for reviewing mission status and risk assessments for issues that arise and making decisions about them, also will begin practicing their roles in simulations. Later this summer, the Orion stage adapter will arrive at the VAB from NASA's Marshall Spaceflight Center in Huntsville, Alabama, and stacked on top of the rocket.
Through Artemis, NASA will send astronauts to explore the moon for scientific discovery, economic benefits, and build the foundation for the first crewed missions to Mars.
TOP IMAGE: Technicians move the Orion spacecraft for NASA’s Artemis II test flight out of the Neil A. Armstrong Operations and Checkout Building to the Multi-Payload Processing Facility at Kennedy Space Center in Florida on Saturday, May 3, 2025. Credit: NASA / Kim Shiflett
LOWER IMAGE: Teams with NASA’s Exploration Ground Systems Program begin integrating the interim cryogenic propulsion stage to the SLS (Space Launch System) launch vehicle stage adapter on Wednesday, April 30, 2025, inside the Vehicle Assembly Building at NASA’s Kennedy Space Center in Florida. Credit: NASA / Isaac Watson

7 notes
·
View notes
Photo

Life in an Air Raid Shelter in the London Blitz
Crowded and uncomfortable air raid shelters became a feature of the urban landscape across Britain during the Second World War (1939-45) as the bombers of Nazi Germany systematically hit cities from 1940. The London Blitz was a particularly sustained period of bombing which civilians escaped from by diving into private or public shelters when the sirens whined their warning signal.
People sought refuge in the London Underground stations, in purpose-built community shelters, in their cellars, under the stairs, or in refuges in their gardens such as the Anderson shelter. The danger was real, prior to the autumn of 1942, more British civilians were killed in the war than British military personnel.
The Bombing of Britain
Civilians had a lot to put up with even before the bombing started. The blackout was imposed where no non-essential lights were to show at night and so help enemy bombers. There was a real fear that gas bombs would be used, and so everyone was encouraged to carry gas masks. The Phoney War, the period of relative military inactivity in Britain between September 1939 and the spring of 1940, brought a sense of false security, but the German Luftwaffe (air force) would arrive soon enough.
Hundreds of thousands of children were evacuated from cities, including the capital where one million children were shipped out. Youngsters were sent to the safety of the countryside, but the separation from parents and a familiar environment proved traumatic for many. As the historian J. Hale points out: "By January 1940 about half of all children and nine out of ten mothers had returned to their old homes" (27). Despite this, when the bombing started, the official policy of evacuation was continued.
Bombers of the Luftwaffe and the Italian Air Force dropped both explosive and incendiary bombs, the first type to smash through buildings and the second to set the ruins alight. Britain had an integrated air defensive system, the Dowding System, which monitored incoming aircraft and sent out fighters to intercept like the Supermarine Spitfire, but many bombers got through to deliver their deadly loads. In the Battle of Britain, the Luftwaffe aimed to destroy the Royal Air Force (RAF), both in the air and on the ground, while a secondary aim was to terrorize the civilian population. As the Luftwaffe began to lose the battle, so it concentrated more on civilian targets. Most raids were carried out at night since darkness was the best protection for the German bombers against fighters and anti-aircraft guns. The bombers were guided by radar to their targets, but bombing remained highly inaccurate so that even when strategic sites like factories were the target, there was usually great damage to civilian areas.
London was first bombed on 24 August 1940. The bombers were to attack an oil terminal but mistakenly hit the city, thus beginning a tit-for-tat bombing of civilian areas that escalated to unimaginable horrors like the total bombing of Coventry and Hamburg (Operation Gomorrah). The systematic bombing of London began on 7 September 1940 and continued until the middle of May 1941. The British press called this campaign "the Blitz". The East End of the city, where the docks were located, was a particular target. Other cities across Britain were also repeatedly hit. For civilians, not knowing where the bombers would hit next, air raid shelters became essential everywhere.
Continue reading...
30 notes
·
View notes
Text
My biggest question about medical ninjutsu is actually how it works with a person's chakra system. The lore for your chakra system in Naruto is that it's "enmeshed within the body, transporting chakra through the body and each organ as the circulatory system does blood. The system is involved in the creation of chakra itself as well, as every cell and protein in the body are connected to this pathway system by a capillary which draws out the cell's physical energy and is refined into chakra by several organs, notably the heart"
We're even shown what this system looks like around the organs, and stopping the flow of chakra in one part of the body will stop that areas functions

So if your chakra pathway operates the same way as your veins, muscles, blood vessels etc and everyone is born with a different chakra nature, which operates like a blood type, what happens when you need a blood transfusion? Do you have to get blood from somebody with the same nature as you, so if you're a Wind type you can only accept transfusion from other Wind types? If you have an organ transplant how does the new organ get integrated into your chakra system? Is there a higher chance of rejection because of the added chakra system complications? Are organ transplants even possible in this universe outside of whatever the fuck Kakuzu was doing with those hearts? Does medical ninjutsu have to mould itself to match your individual pathways when you're getting healed up?
In real life we have doctors that specialise in certain medical fields, so does the shinobi world have something similar, where one doctor could specialise in emergency medicine and another in family medicine? Do we have neurologists in this universe? Anesthesiology? Are there doctors and surgeons that specialise in the chakra pathways?
What sort of illnesses and diseases exist in this universe? Any chronic or terminal sickness? Are there genetic illnesses, or illnesses that only attack certain chakra types?
These are the questions I have and I know fuckall about the real life medical field so I cannot give answers to any of them but I sure do think about it a lot
32 notes
·
View notes
Text
Log 8.6-ASL/H, by Krrilli (Konith, Xeneath Prime/Xeneath VII, Sector 3 - Segment Alpha, '''-'--''-)
"Hello, carbon-based endoskeletal reader. You know how humanity has developed rudimentary adaptive learning algorithms (which they named artificial intelligence, AIs for short) much before becoming third stage spacefaring species.
As natural to other young races they have greatly integrated it into their technology over the last three centuries. I cannot stress how aberrant it is, but the Confederation allows it, so they have it. Most of their machines and complex systems utilize relatively rudimentary ALAs, ranging between type 3 (input -> built-in answer) and type 5 (can create new answers to new inputs based on built-in answers), but are unable to feel emotions or think. Like all ALAs.
It is however witnessed how humans cling to their adorable behavior of giving personification to objects and this extends to their AIs. I have witnessed myself two humans treating terminals as their own, "cuddling". I don't know if this is their term. a rifle before a training exercise, and even curse a vehicle's bloodline after it failed to pass through obstacles.
In one instance, however, I came to greatly disagree with the Confederation's categorizations of their ALAs. I was covering an Exorith invasion in one of their mining stations and I deeply believe to have witnessed an armored vehicle's cannon (which had failed minutes ago) fire again after a quick prayer from its operator.
Whether this phenomena was my bias, a psychic/methaphysical effect, a new biological matter manipulation trait, a hidden mechanism, ignorance, an unknown function in the machine, or sheer dumb luck is still under study. Close log."
#humans are space oddities#humans are strange#humans are weird#humans are insane#humans are terrifying#writing#creative writing#worldbuilding#sci fi#scifi#science fiction#technology#artificial intelligence
13 notes
·
View notes
Text
Submission 2 for @simblorbo-bracket's sad wet meowmeow competition.

No. 27
Alias: "Livard"
No. 27 was the 27th 'living' instance of the Crane Foundation's modern Quintessence Program. When the breach occurred, 27 took immediate opportunity to leave, using her sharp limbs to grievously wound operatives and other personnel who attempted to obstruct her path of escape. Eleven confirmed aggravated fatalities. An unknown number of fatalities occurring at trample areas and exit pileups. She proceeded to use the slaughter-path of the other breachers as a clear line out of the facility’s underground portion, ascending rapidly to the upper floors where she is believed to have fled the building.
As of right now, 27 is an immune carrier of a new strain of the same pathogen currently causing a cataclysmic outbreak. While typical variants can only infect and alter biological matter, this mutation was observed with the new ability to infect machines during controlled testing.
No. 27 was last spotted wearing the stolen cardigan of Dr. Livard, with a secondary article of clothing tied beneath at the waist. The owner of the second article has not yet been identified.
27 has been reported self-identifying as ‘Livard,’ and has not discarded the nametag attached to the stolen cardigan, despite having no reason to keep it.

27 was created as an experimental binding of biological tissues and cybernetics. Unlike precursors, who were constructed with biological matter on a 75% or higher percent mechanical endoskeleton, 27 was an experimental integration of traditionally classified ‘biological’ and traditionally classified ‘mechanical’ elements on a fundamental level. The use of nanites in her tissues, along with algorithmic adaptations, created a unique combined system challenging the preconceived definitions of the categories.
However, the arise of the new pathogen strain saw 27 strictly confined. 27 was shown to be incredibly observant of those observing her, and an incredibly accurate mimic of their behaviors. She, notably, engaged in a game of rock, paper, scissors with an anonymous researcher after they and their coworker demonstrated the game through the window.
Sentient or not, 27 still falls outside of the Mimic Law, and is legally property of the Crane Foundation. With artificial sentience having already been academically accepted years ago, whether 27’s curiosity is dictated by script or by consciousness is not our concern.
As for the present times, it was assumed 27 would perish shortly after leaving the facility, without the specific needs of her body being met in a controlled environment. Our assumptions were wrong. 27 has been spotted feeding on mechanical devices as if they were prey animals. We can only assume this habit will accelerate the spread of the new pathogen strain, and while we would like to reclaim 27 for study, it might become necessary to terminate her entirely to prevent escalation of the already dire world situation.
Originality Status: 100% Original Property of the Crane Foundation
Additional Notes:
(Attached below is a fabricated 3D model based on the last contained recording of 27. It is merely for visual context. If you are an operative searching for 27, or, in some inexplicable instance, creating a poll (Tom), please use the topmost image as it is the most up-to-date.)

#sims 4#simblr#ts4#my sims#weird sims#sims 4 screenshots#sims community#the sims community#showusyoursims#show us your sims
7 notes
·
View notes