#WHY did i write it as third in every instance in my data set
Explore tagged Tumblr posts
Text
me: mystified, confounded, perplexed, bamboozled, bewildered why this analysis doesn't make any sense
the humble "we" I have labeled, AGAIN, as third person:
#shitpost#it turns out the greatest obstacle to linguistic analysis is not the languages but my own stupidity#i KNOW we is not third person i KNOW it's first plural#WHY did i write it as third in every instance in my data set#after accidentally labeling he as first in my OTHER analysis!!!#oughhhhh
4 notes
·
View notes
Text
Psychopolitics and Surveillance Capitalism
I queued this post quite a while ago and it posted last night while I was asleep. I’m reposting because I’ve been thinking about this a bit more since I first saw it. I’ve shortened the original quote here:
[H]ealing ... refers to self-optimization that is supposed to therapeutically eliminate any and all functional weakness or mental obstacle in the name of efficiency and performance. Yet perpetual self-optimization ... amounts to total self-exploitation. [...] The neoliberal subject is running aground on the imperative of self optimization, that is, on the compulsion always to achieve more and more. Healing, it turns out, means killing.
and had a look at this review. From the review: “[W]hat capitalism realised in the neoliberal era, Han argues, is that it didn’t need to be tough, but seductive. This is what he calls smartpolitics. Instead of saying no, it says yes: instead of denying us with commandments, discipline and shortages, it seems to allow us to buy what we want when we want, become what we want and realise our dream of freedom. “Instead of forbidding and depriving it works through pleasing and fulfilling. Instead of making people compliant, it seeks to make them dependent.”
I’m adding a break because this got long.
(review, cont’d)
And, while not Orwellian, we net-worked moderns have our own Newspeak. Freedom, for instance, means coercion. Microsoft’s early ad slogan was “Where do you want to go today?”, evoking a world of boundless possibility. That boundlessness was a lie, Han argues: “Today, unbounded freedom and communication are switching over into total control and surveillance … We had just freed ourselves from the disciplinary panopticon – then threw ourselves into a new and even more efficient panopticon.” And one, it might be added, that needs no watchman, since even the diabolical geniuses of neoliberalism – Mark Zuckerberg and Jeff Bezos – don’t have to play Big Brother. They are diabolical precisely because they got us to play that role ourselves.
At least in Nineteen Eighty-Four, nobody felt free. In 2017, for Han, everybody feels free, which is the problem. “Of our own free will, we put any and all conceivable information about ourselves on the internet, without having the slightest idea who knows what, when or in what occasion. This lack of control represents a crisis of freedom to be taken seriously.”
“Did we really want to be free?” asks Han. Perhaps, he muses, true freedom is an intolerable burden and so we invented God in order to be guilty and in debt to something. That’s why, having killed God, we invented capitalism. Like God, only more efficiently, capitalism makes us feel guilty for our failings and, you may well have noticed, encourages us to be deep in immobilising debt.”
I think I’m going to get this book. This would make a great pairing with Surveillance Capitalism by Shoshana Zuboff. (I’ve linked to a review; the book is available on Amazon and elsewhere). I have the book but haven’t read it yet. Think about this:
“Surveillance capitalism unilaterally claims human experience as free raw material for translation into behavioural data. Although some of these data are applied to service improvement, the rest are declared as a proprietary behavioural surplus, fed into advanced manufacturing processes known as ‘machine intelligence’, and fabricated into prediction products that anticipate what you will do now, soon, and later. Finally, these prediction products are traded in a new kind of marketplace that I call behavioural futures markets. Surveillance capitalists have grown immensely wealthy from these trading operations, for many companies are willing to lay bets on our future behaviour.”
From the review: “The combination of state surveillance and its capitalist counterpart means that digital technology is separating the citizens in all societies into two groups: the watchers (invisible, unknown and unaccountable) and the watched. This has profound consequences for democracy because asymmetry of knowledge translates into asymmetries of power. But whereas most democratic societies have at least some degree of oversight of state surveillance, we currently have almost no regulatory oversight of its privatised counterpart”.
Part of my job is related to the regulatory oversight of the private sector, and I definitely think that it is an absolute mess. Countries have vastly different rules, but data doesn’t respect borders. Different countries have different goals. The EU’s data laws protect the individual. China’s data laws protect the state. The US’s data laws protect the economy. (With a few exceptions, the laws are really about what can be monetized and what can’t.)
So what is an individual supposed to do? I struggle with the best way to protect my own privacy and personal data, and to teach my teens to do the same, let alone put it into a socio-political context.
I don’t think it’s possible to completely opt out of the surveillance and participate in modern life. It’s a bit easier for old people like me to opt out but I see younger people whose peer group socialises to such an extent through apps and phones (snapchat, instagram, etc). The problem is that if they are not on these platforms, they are to a very large extent excluded from social life, and humans are social animals. It’s not healthy for them to be isolated.
OTOH, we can make some choices. For example, I have a Facebook account (I have 3, actually), but the one with my real name is just for an online course that uses a FB group for discussion. One is for testing. One is my “real” account that does not use my real name where I keep in touch with family since I live half a world away. I log out every time I use it. I never gave FB my phone number or location or work place or hometown etc etc. I opted out of any advertising that I could, particularly adverts using my own Likes. I opted out of all third party platforms so I cannot accidentally log into a third party site with FB. I do not upload photos of my children. I cannot be tagged. I opted out of facial recognition. I check settings once a week in case they are “accidentally” reset. I check after upgrades and so forth. I don’t use FB messenger. I don’t use the FB app. I log out and clear my cache and cookies regularly. I download all of my FB data from time to time (I think a lot of people did this after the Cambridge Analytica scandal) and check that it’s accurate and I’m ok with what’s out there. (btw, one of my professional highlights was writing about Cambridge Analytica in 2017, before the scandals broke in early 2018, w00t).
Also, I do not have any google accounts. At all. I don’t use gmail. I cannot sign into google maps. If someone sends me a google doc for editing, I ask for a copy, edit it and send it back. (This is rarely an issue though; I think it’s happened twice.) I used to have a Youtube account, and when they changed the settings to log in with a google account and not just an email, I created an account on a separate computer, logged in, deleted all of my videos and then deleted my youtube account, then deleted my google account and then cleared my cookies and cache. I think this was 2008.
But truth be told, this is not much. I know that. Amazon knows which Audible books I listen to, which Kindle books I read, and which paperbacks I buy. It goes on and on.
Is there a balance? Are our choices to opt in -submit- to this surveillance or live off the grid? This isn’t simply a matter of updating data privacy laws. The issues that need to be resolved underpin the entire economy and political order.
Food for thought, anyway. (So how’s your quarantine going?)
2 notes
·
View notes
Text
Databases: how they work, and a brief history
My twitter-friend Simon had a simple question that contained much complexity: how do databases work?
Ok, so databases really confuse me, like how do databases even work?
— Simon Legg (@simonleggsays) November 18, 2019
I don't have a job at the moment, and I really love databases and also teaching things to web developers, so this was a perfect storm for me:
To what level of detail would you like an answer? I love databases.
— Laurie Voss (@seldo) November 18, 2019
The result was an absurdly long thread of 70+ tweets, in which I expounded on the workings and history of databases as used by modern web developers, and Simon chimed in on each tweet with further questions and requests for clarification. The result of this collaboration was a super fun tiny explanation of databases which many people said they liked, so here it is, lightly edited for clarity.
What is a database?
Let's start at the very most basic thing, the words we're using: a "database" literally just means "a structured collection of data". Almost anything meets this definition – an object in memory, an XML file, a list in HTML. It's super broad, so we call some radically different things "databases".
The thing people use all the time is, formally, a Database Management System, abbreviated to DBMS. This is a piece of software that handles access to the pile of data. Technically one DBMS can manage multiple databases (MySQL and postgres both do this) but often a DBMS will have just one database in it.
Because it's so frequent that the DBMS has one DB in it we often call a DBMS a "database". So part of the confusion around databases for people new to them is because we call so many things the same word! But it doesn't really matter, you can call an DBMS a "database" and everyone will know what you mean. MySQL, Redis, Postgres, RedShift, Oracle etc. are all DBMS.
So now we have a mental model of a "database", really a DBMS: it is a piece of software that manages access to a pile of structured data for you. DBMSes are often written in C or C++, but it can be any programming language; there are databases written in Erlang and JavaScript. One of the key differences between DBMSes is how they structure the data.
Relational databases
Relational databases, also called RDBMS, model data as a table, like you'd see in a spreadsheet. On disk this can be as simple as comma-separated values: one row per line, commas between columns, e.g. a classic example is a table of fruits:
apple,10,5.00 orange,5,6.50
The DBMS knows the first column is the name, the second is the number of fruits, the third is the price. Sometimes it will store that information in a different database! Sometimes the metadata about what the columns are will be in the database file itself. Because it knows about the columns, it can handle niceties for you: for example, the first column is a string, the second is an integer, the third is dollar values. It can use that to make sure it returns those columns to you correctly formatted, and it can also store numbers more efficiently than just strings of digits.
In reality a modern database is doing a whole bunch of far more clever optimizations than just comma separated values but it's a mental model of what's going on that works fine. The data all lives on disk, often as one big file, and the DBMS caches parts of it in memory for speed. Sometimes it has different files for the data and the metadata, or for indexes that make it easier to find things quickly, but we can safely ignore those details.
RDBMS are older, so they date from a time when memory was really expensive, so they usually optimize for keeping most things on disk and only put some stuff in memory. But they don't have to: some RDBMS keep everything in memory and never write to disk. That makes them much faster!
Is it still a database if all the structured data stays in memory? Sure. It's a pile of structured data. Nothing in that definition says a disk needs to be involved.
So what does the "relational" part of RDBMS mean? RDBMS have multiple tables of data, and they can relate different tables to each other. For instance, imagine a new table called "Farmers":
IDName 1bob 2susan
and we modify the Fruits table:
Farmer IDFruitQuantityPrice 1apple105.00 1orange56.50 2apple206.00 2orange14.75
.dbTable { border: 1px solid black; } .dbTable thead td { background-color: #eee; } .dbTable td { padding: 0.3em; }
The Farmers table gives each farmer a name and an ID. The Fruits table now has a column that gives the Farmer ID, so you can see which farmer has which fruit at which price.
Why's that helpful? Two reasons: space and time. Space because it reduces data duplication. Remember, these were invented when disks were expensive and slow! Storing the data this way lets you only list "susan" once no matter how many fruits she has. If she had a hundred kinds of fruit you'd be saving quite a lot of storage by not repeating her name over and over. The time reason comes in if you want to change Susan's name. If you repeated her name hundreds of times you would have to do a write to disk for each one (and writes were very slow at the time this was all designed). That would take a long time, plus there's a chance you could miss one somewhere and suddenly Susan would have two names and things would be confusing.
Relational databases make it easy to do certain kinds of queries. For instance, it's very efficient to find out how many fruits there are in total: you just add up all the numbers in the Quantity column in Fruits, and you never need to look at Farmers at all. It's efficient and because the DBMS knows where the data is you can say "give me the sum of the quantity colum" pretty simply in SQL, something like SELECT SUM(Quantity) FROM Fruits. The DBMS will do all the work.
NoSQL databases
So now let's look at the NoSQL databases. These were a much more recent invention, and the economics of computer hardware had changed: memory was a lot cheaper, disk space was absurdly cheap, processors were a lot faster, and programmers were very expensive. The designers of newer databases could make different trade-offs than the designers of RDBMS.
The first difference of NoSQL databases is that they mostly don't store things on disk, or do so only once in a while as a backup. This can be dangerous – if you lose power you can lose all your data – but often a backup from a few minutes or seconds ago is fine and the speed of memory is worth it. A database like Redis writes everything to disk every 200ms or so, which is hardly any time at all, while doing all the real work in memory.
A lot of the perceived performance advantages of "noSQL" databases is just because they keep everything in memory and memory is very fast and disks, even modern solid-state drives, are agonizingly slow by comparison. It's nothing to do with whether the database is relational or not-relational, and nothing at all to do with SQL.
But the other thing NoSQL database designers did was they abandoned the "relational" part of databases. Instead of the model of tables, they tended to model data as objects with keys. A good mental model of this is just JSON:
[ {"name":"bob"} {"name":"susan","age":55} ]
Again, just as a modern RDBMS is not really writing CSV files to disk but is doing wildly optimized stuff, a NoSQL database is not storing everything as a single giant JSON array in memory or disk, but you can mentally model it that way and you won't go far wrong. If I want the record for Bob I ask for ID 0, Susan is ID 1, etc..
One advantage here is that I don't need to plan in advance what I put in each record, I can just throw anything in there. It can be just a name, or a name and an age, or a gigantic object. With a relational DB you have to plan out columns in advance, and changing them later can be tricky and time-consuming.
Another advantage is that if I want to know everything about a farmer, it's all going to be there in one record: their name, their fruits, the prices, everything. In a relational DB that would be more complicated, because you'd have to query the farmers and fruits tables at the same time, a process called "joining" the tables. The SQL "JOIN" keyword is one way to do this.
One disadvantage of storing records as objects like this, formally called an "object store", is that if I want to know how many fruits there are in total, that's easy in an RDBMS but harder here. To sum the quantity of fruits, I have to retrieve each record, find the key for fruits, find all the fruits, find the key for quantity, and add these to a variable. The DBMS for the object store may have an API to do this for me if I've been consistent and made all the objects I stored look the same. But I don't have to do that, so there's a chance the quantities are stored in different places in different objects, making it quite annoying to get right. You often have to write code to do it.
But sometimes that's okay! Sometimes your app doesn't need to relate things across multiple records, it just wants all the data about a single key as fast as possible. Relational databases are best for the former, object stores the best for the latter, but both types can answer both types of questions.
Some of the optimizations I mentioned both types of DBMS use are to allow them to answer the kinds of questions they're otherwise bad at. RDBMS have "object" columns these days that let you store object-type things without adding and removing columns. Object stores frequently have "indexes" that you can set up to be able to find all the keys in a particular place so you can sum up things like Quantity or search for a specific Fruit name fast.
So what's the difference between an "object store" and a "noSQL" database? The first is a formal name for anything that stores structured data as objects (not tables). The second is... well, basically a marketing term. Let's digress into some tech history!
The self-defeating triumph of MySQL
Back in 1995, when the web boomed out of nowhere and suddenly everybody needed a database, databases were mostly commercial software, and expensive. To the rescue came MySQL, invented 1995, and Postgres, invented 1996. They were free! This was a radical idea and everybody adopted them, partly because nobody had any money back then – the whole idea of making money from websites was new and un-tested, there was no such thing as a multi-million dollar seed round. It was free or nothing.
The primary difference between PostgreSQL and MySQL was that Postgres was very good and had lots of features but was very hard to install on Windows (then, as now, the overwhelmingly most common development platform for web devs). MySQL did almost nothing but came with a super-easy installer for Windows. The result was MySQL completely ate Postgres' lunch for years in terms of market share.
Lots of database folks will dispute my assertion that the Windows installer is why MySQL won, or that MySQL won at all. But MySQL absolutely won, and it was because of the installer. MySQL became so popular it became synonymous with "database". You started any new web app by installing MySQL. Web hosting plans came with a MySQL database for free by default, and often no other databases were even available on cheaper hosts, which further accelerated MySQL's rise: defaults are powerful.
The result was people using mySQL for every fucking thing, even for things it was really bad at. For instance, because web devs move fast and change things they had to add new columns to tables all the time, and as I mentioned RDBMS are bad at that. People used MySQL to store uploaded image files, gigantic blobs of binary data that have no place in a DBMS of any kind.
People also ran into a lot of problems with RDBMS and MySQL in particular being optimized for saving memory and storing everything on disk. It made huge databases really slow, and meanwhile memory had got a lot cheaper. Putting tons of data in memory had become practical.
The rise of in-memory databases
The first software to really make use of how cheap memory had become was Memcache, released in 2003. You could run your ordinary RDBMS queries and just throw the results of frequent queries into Memcache, which stored them in memory so they were way, WAY faster to retrieve the second time. It was a revolution in performance, and it was an easy optimization to throw into your existing, RDBMS-based application.
By 2009 somebody realized that if you're just throwing everything in a cache anyway, why even bother having an RDBMS in the first place? Enter MongoDB and Redis, both released in 2009. To contrast themselves with the dominant "MySQL" they called themselves "NoSQL".
What's the difference between an in-memory cache like Memcache and an in-memory database like Redis or MongoDB? The answer is: basically nothing. Redis and Memcache are fundamentally almost identical, Redis just has much better mechanisms for retrieving and accessing the data in memory. A cache is a kind of DB, Memcache is a DBMS, it's just not as easy to do complex things with it as Redis.
Part of the reason Mongo and Redis called themselves NoSQL is because, well, they didn't support SQL. Relational databases let you use SQL to ask questions about relations across tables. Object stores just look up objects by their key most of the time, so the expressiveness of SQL is overkill. You can just make an API call like get(1) to get the record you want.
But this is where marketing became a problem. The NoSQL stores (being in memory) were a lot faster than the relational DBMS (which still mostly used disk). So people got the idea that SQL was the problem, that SQL was why RDBMS were slow. The name "NoSQL" didn't help! It sounded like getting rid of SQL was the point, rather than a side effect. But what most people liked about the NoSQL databases was the performance, and that was just because memory is faster than disk!
Of course, some people genuinely do hate SQL, and not having to use SQL was attractive to them. But if you've built applications of reasonable complexity on both an RDBMS and an object store you'll know that complicated queries are complicated whether you're using SQL or not. I have a lot of love for SQL.
If putting everything in memory makes your database faster, why can't you build an RDBMS that stores everything in memory? You can, and they exist! VoltDB is one example. They're nice! Also, MySQL and Postgres have kind of caught up to the idea that machines have lots more RAM now, so you can configure them to keep things mostly in memory too, so their default performance is a lot better and their performance after being tuned by an expert can be phenomenal.
So anything that's not a relational database is technically a "NoSQL" database. Most NoSQL databases are object stores but that's really just kind of a historical accident.
How does my app talk to a database?
Now we understand how a database works: it's software, running on a machine, managing data for you. How does your app talk to the database over a network and get answers to queries? Are all databases just a single machine?
The answer is: every DBMS, whether relational or object store, is a piece of software that runs on machine(s) that hold the data. There's massive variation: some run on 1 machine, some on clusters of 5-10, some run across thousands of separate machines all at once.
The DBMS software does the management of the data, in memory or on disk, and it presents an API that can be accessed locally, and also more importantly over the network. Sometimes this is a web API like you're used to, literally making GET and POST calls over HTTP to the database. For other databases, especially the older ones, it's a custom protocol.
Either way, you run a piece of software in your app, usually called a Client. That client knows the protocol for talking to the database, whether it's HTTP or WhateverDBProtocol. You tell it where the database server is on the network, it sends queries over and gets responses. Sometimes the queries are literally strings of text, like "SELECT * FROM Fruits", sometimes they are JSON payloads describing records, and any number of other variations.
As a starting point, you can think of the client running on your machine talking over the network to a database running on another machine. Sometimes your app is on dozens of machines, and the database is a single IP address with thousands of machines pretending to be one machine. But it works pretty much the same either way.
The way you tell your client "where" the DB is is your connection credentials, often expressed as a string like "http://username:[email protected]:1234" or "mongodb://...". But this is just a convenient shorthand. All your client really needs to talk to a database is the DNS name (like mydb.com) or an IP address (like 205.195.134.39), plus a port (1234). This tells the network which machine to send the query to, and what "door" to knock on when it gets there.
A little about ports: machines listen on specific ports for things, so if you send something to port 80, the machine knows the query is for your web server, but if you send it to port 1234, it knows the query is for your database. Who picks 1234 (In the case of Postgres, it's literally 5432)? There's no rhyme or reason to it. The developers pick a number that's easy to remember between 1 and 65,535 (the highest port number available) and hope that no other popular piece of software is already using it.
Usually you'll also have a username and password to connect to the database, because otherwise anybody who found your machine could connect to your database and get all the data in it. Forgetting that this is true is a really common source of security breaches!
There are bad people on the internet who literally just try every single IP in the world and send data to the default port for common databases and try to connect without a username or password to see if they can. If it works, they take all the data and then ransom it off. Yikes! Always make sure your database has a password.
Of course, sometimes you don't talk to your database over a network. Sometimes your app and your database live on the same machine. This is common in desktop software but very rare in web apps. If you've ever heard of a "database driver", the "driver" is the equivalent of the "client", but for talking to a local database instead of over a network.
Replication and scaling
Remember I said some databases run on just 1 machine, and some run on thousands of machines? That's known as replication. If you have more than one copy of a piece of data, you have a "replica" of that data, hence the name.
Back in the old days hardware was expensive so it was unusual to have replicas of your data running at the same time. It was expensive. Instead you'd back up your data to tape or something, and if the database went down because the hardware wore out or something, then you'd buy new hardware and (hopefully) reinstall your DBMS and restore the data in a few hours.
Web apps radically changed people's demands of databases. Before web apps, most databases weren't being continuously queried by the public, just a few experts inside normal working hours, and they would wait patiently if the database broke. With a web app you can't have minutes of downtime, far less hours, so replication went from being a rare feature of expensive databases to pretty much table stakes for every database. The initial form of replication was a "hot spare".
If you ran a hot spare, you'd have your main DBMS machine, which handled all queries, and a replica DBMS machine that would copy every single change that happened on the primary to itself. Primary was called m****r and the replica s***e because the latter did whatever the former told it to do, and at the time nobody considered how horrifying that analogy was. These days we call those things "primary/secondary" or "primary/replica" or for more complicated arrangements things like "root/branch/leaf".
Sometimes, people would think having a hot spare meant they didn't need a backup. This is a huge mistake! Remember, the replica copies every change in the main database. So if you accidentally run a command that deletes all the data in your primary database, it will automatically delete all the data in the replica too. Replicas are not backups, as the bookmarking site Magnolia famously learned.
People soon realized having a whole replica machine sitting around doing nothing was a waste, so to be more efficient they changed where traffic went: all the writes would go to the primary, which would copy everything to the replicas, and all the reads would go to the replicas. This was great for scale!
Instead of having 1 machine worth of performance (and you could swap to the hot spare if it failed, and still have 1 machine of performance with no downtime) suddenly you had X machines of performance, where X could be dozens or even hundreds. Very helpful!
But primary/secondary replication of this kind has two drawbacks. First, if a write has arrived at the primary database but not yet replicated to all the secondary machines (which can take half a second if the machines are far apart or overloaded) then somebody reading from the replica can get an answer that's out of date. This is known as a "consistency" failure, and we'll talk about it more later.
The second flaw with primary/second replication is if the primary fails, suddenly you can no longer write to your database. To restore the ability to do writes, you have to take one of the replicas and "promote" it to primary, and change all the other replicas to point at this new primary box. It's time-consuming and notoriously error-prone.
So newer databases invented different ways of arranging the machines, formally called "network topology". If you think of the way machines connect to each other as a diagram, the topology is the shape of that diagram. Primary/secondary looks like a star. Root/branch/leaf looks like a tree. But you can have a ring structure, or a mesh structure, or lots of others. A mesh structure is a lot of fun and very popular, so let's talk about more about them.
Mesh replication databases
In a mesh structure, every machine is talking to every other machine and they all have some portion of the data. You can send a write to any machine and it will either store it, or figure out what machine should store it and send it to that machine. Likewise, you can query any machine in the mesh, and it will give you the answer if it has the data, or forward your request to a machine that does. There's no "primary" machine to fail. Neat!
Because each machine can get away with storing only some of the data and not all of it, a mesh database can store much, much more data than a single machine could store. If 1 machine could store X data, then N machines could theoretically store N*X data. You can almost scale infinitely that way! It's very cool.
Of course, if each record only existed on one machine, then if that machine failed you'd lose those records. So usually in a mesh network more than one machine will have a copy of any individual record. That means you can lose machines without losing data or experiencing downtime; there are other copies lying around. In some mesh databases can also add a new machine to the mesh and the others will notice it and "rebalance" data, increasing the capacity of the database without any downtime. Super cool.
So a mesh topology is a lot more complicated but more resilient, and you can scale it without having to take the database down (usually). This is very nice, but can go horribly wrong if, for instance, there's a network error and suddenly half the machines can't see the other half of the machines in the mesh. This is called a "network partition" and it's a super common failure in large networks. Usually a partition will last only a couple of seconds but that's more than enough to fuck up a database. We'll talk about network partitions shortly.
One important question about a mesh DB is: how do you connect to it? Your client needs to know an IP address to connect to a database. Does it need to know the IP addresses of every machine in the mesh? And what happens when you add and remove machines from the mesh? Sounds messy.
Different Mesh DBs do it differently, but usually you get a load balancer, another machine that accepts all the incoming connections and works out which machine in the mesh should get the question and hands it off. Of course, this means the load balancer can fail, hosing your DB. So usually you'll do some kind of DNS/IP trickery where there are a handful of load balancers all responding on the same domain name or IP address.
The end result is your client magically just needs to know only one name or IP, and that IP always responds because the load balancer always sends you to a working machine.
CAP theory
This brings us neatly to a computer science term often used to talk about databases which is Consistency, Availability, and Partition tolerance, aka CAP or "CAP theory". The basic rule of CAP theory is: you can't have all 3 of Consistency, Availability and Partition Tolerance at the same time. Not because we're not smart enough to build a database that good, but because doing so violates physics.
Consistency means, formally: every query gets the correct, most up-to-date answer (or an error response saying you can't have it).
Availability means: every query gets an answer (but it's not guaranteed to be the correct one).
Partition Tolerance means: if the network craps out, the database will continue to work.
You can already see how these conflict! If you're 100% Available it means by definition you'll never give an error response, so sometimes the data will be out of date, i.e. not Consistent. If your database is Partition Tolerant, on the other hand, it keeps working even if machine A can't talk to machine B, and machine A might have a more recent write than B, so machine B will give stale (i.e. not Consistent) responses to keep working.
So let's think about how CAP theorem applies across the topologies we already talked about.
A single DB on a single machine is definitely Consistent (there's only one copy of the data) and Partition Tolerant (there's no network inside of it to crap out) but not Available because the machine itself can fail, e.g. the hardware could literally break or power could go out.
A primary DB with several replicas is Available (if one replica fails you can ask another) and Partition Tolerant (the replicas will respond even if they're not receiving writes from the primary) but not Consistent (because as mentioned earlier, the replicas might not have every primary write yet).
A mesh DB is extremely Available (all the nodes always answer) and Partition Tolerant (just try to knock it over! It's delightfully robust!) but can be extremely inconsistent because two different machines on the mesh could get a write to the same record at the same time and fight about which one is "correct".
This is the big disadvantage to mesh DBs, which otherwise are wonderful. Sometimes it's impossible to know which of two simultaneous writes is the "winner". There's no single authority, and Very Very Complicated Algorithms are deployed trying to prevent fights breaking out between machines in the mesh about this, with highly variable levels of success and gigantic levels of pain when they inevitably fail. You can't get all three of CAP and Consistency is what mesh networks lose.
In all databases, CAP isn't a set of switches where you are or aren't Consistent, Available, or Partition Tolerant. It's more like a set of sliders. Sliding up the Partition Tolerance generally slides down Consistency, sliding down Availability will give you more Consistency, etc etc.. Every DBMS picks some combination of CAP and picking the right database is often a matter of choosing what CAP combination is appropriate for your application.
Other topologies
Some other terms you frequently hear in the world of databases are "partitions" (which are different from the network partitions of CAP theorem) and "shards". These are both additional topologies available to somebody designing a database. Let's talk about shards first.
Imagine a primary with multiple replicas, but instead of each replica having all the data, each replica has a slice (or shard) of the data. You can slice the data lots of ways. If the database was people, you could have 26 shards, one with all names starting with A, one with all the names starting with B, etc..
Sharding can be helpful if the data is too big to all fit on one disk at a time. This is less of a problem than it used to be because virtual machines these days can effectively have infinity-sized hard drives.
The disadvantage of sharding is it's less Available: if you lose a shard, you lose everybody who starts with that letter! (Of course, your shards can also have replicas...) Plus your software needs to know where all the shards are and which one to ask a question. It's fiddly. Many of the problems of sharded databases are solved by using mesh topologies instead.
Partitions are another way of splitting up a database, but instead of splitting it across many machines, it splits the database across many files in a single machine. This is an old pattern that was useful when you had really powerful hardware and really slow disks, because you could install multiple disks into a single machine and put different partitions on each one, speeding up your achingly slow, disk-based database. These days there's not a lot of reason to use partitions of this kind.
Fin
That concludes this impromptu Databases 101 seminar! I hope you enjoyed learning a little bit more about this fantastically fun and critically important genre of software. from Seldo.Com Feed https://ift.tt/32XwZth
1 note
·
View note
Text
Burning Souffles
Relationship: Oliver Queen/Felicity Smoak
Rating: E (honestly it’s more like M, but I’m keeping the E in anticipation of the E-rated epilogue I’m still planning to write someday ;)
Tags: post-7x13/ Arrow (TV 2012) Season 7/ Canon Compliant/ Angst/ Romance/ Action (just a little)/ Drama/ Feelings/ Eventual Fluff/ Family Feels
Summary:
Felicity really needs to have a talk with Oliver. Which they will really, definitely do just as soon as she stops being kidnapped.
Notes: Forgot to share this on tumblr!
Read on AO3 here | Ch 2 Breaking Windows | Ch 3 Falling Apart | Ch 4 Believing in Love | Ch 5 Making Room in a Broken Heart | Ch 6 Coming Around Again | Ch 7 So in Love with You
Chapter 1: Nothing Stays the Same
If my best isn’t good enough then how can it be good enough for two?
God dammit, why did song lyrics always pop in her head to serve up their hard truths at the worst possible moments?
Like now, for instance. When Felicity found herself tied to a chair in a dark, dingy basement, and no one the wiser about her location. And also pregnant. With no one outside of herself and the hospital aware of that particular detail.
Oh god, if she got murdered here it meant Oliver was going to find out about their baby...their baby...their baby...from the hospital. Or the Medical Examiner’s office. She squeezed her eyes shut at the thought. Nope, not going to think about that. What she was going to do was sit down and have a talk with him - a real talk - just as soon as she was out of this predicament.
It wan’t as if she hadn’t been trying to reach him. For days, weeks, months really. Since William, since Emiko. Since Slabside. It had been a hell of year so far, for both of them.
But Oliver was hurting, and he needed her. So she’d stepped up. She’d put her anger, her fears, her identity crisis aside, because his need was more immediate. He needed her, and moreover, she wanted him to need her. She needed him to need her.
Third verse, same as the first.
There had been signs that he was beginning to let her in. A tiny smile here, a squeeze of her shoulder there. A hand extended toward her, seeming to offer more than just the contact of skin on skin. But the tragedies kept rolling in one after another, and it felt like every step forward was followed by three steps back. Or worse.
Like that morning.
A shiver of something dark and foreign ran down her spine at the memory of the confrontation in their bedroom. The most recent one, that is.
When she’d said her goodbyes to Curtis a few days ago, something he’d said had struck her. “It feels like you’re struggling to find your purpose too.” It was like he’d found the one weak chink in her armour and driven a knife right through it. Since then, she hadn’t been able to get the words out of her head.
Ever since Oliver had come back from Slabside, unmasked, and begun working with the SCPD, a tiny part of her been struggling to understand where she fit in. John and Curtis had ARGUS, Dinah had the SCPD, and Rene seemed content doing whatever he was doing. It took her awhile to realize that deep down, she had been hoping that Oliver’s return would somehow cause the team to re-form, and she’d be able to take her rightful place among them.
And while that hadn’t immediately happened, she’d believed things had finally started to come together once the rest of the team was deputized to work alongside the SCPD. She’d quietly begun setting up a place for Overwatch in their living room: adding an extra computer or two, and installing and improving dozens of programs that the team had always relied on for monitoring, tracking, searching, communicating, and cataloguing. It felt amazing.
But that morning Oliver had made it clear, in no uncertain terms, that things were not back to normal.
She’d approached him cautiously, aware that she hadn’t exactly informed him of her resumed vigilante activities. She expected him to be surprised. She hadn’t expected him to be angry.
He was standing at the dresser pulling a sweater over his head, and she fit herself against the door frame, watching him. Even now, after all these years, she was stuck by how startlingly beautiful he was, all long lines and hard muscles and perfect bone structure. When his head emerged through the hole in his shirt, he sensed her gaze and turned toward her expectantly.
She still wasn’t used to the distance in his eyes.
“So, I know you probably have work lined up for you already, like assigned cases or something like that,” her chipper tone faded just a little bit, because the truth was she didn’t know; he hadn’t actually told her very much about his new job at all, “but in case you and the team were looking for something to do, I got a pretty solid lead on something this morning.”
His eyebrows drew together. “A lead?”
“Yeah. It turns out there’s been a series of thefts from the Star City headquarters of about a dozen different chemical companies - nothing too noteworthy, when taken individually. But my program gave me an alert because it turns out that, taken together, the various chemicals that were stolen can be used to make some pretty nasty stuff of the explosive variety.”
Oliver’s face stilled as she spoke, which should have alerted her that something was wrong, but Felicity was excited, and when Oliver spoke his tone remained deceptively mild. “Your program? Which program is that?”
“Oh, nothing special, just my usual algorithm that analyzes reported criminal activity and seeks patterns in the data.” She smiled, feeling that tiny surge of pride that always accompanied her small accomplishments as Overwatch, a feeling of having made a difference. She hadn’t realized just how much she’d missed that feeling.
But that feeling evaporated rapidly as she watched Oliver’s expression shift from still to stony to stormy so quickly that she could only track it because she knew him so well. “Why are you running that program?” There was absolutely no mistaking that tone in his voice.
Just as there was no mistaking Felicity’s predictable response to his challenge. She pushed off the door frame, straightening her spine and stepping toward him. “Why shouldn’t I be running that program?”
He blinked at her and breathed deeply through his nose while his eyes never left her face. She recognized the signs of him gathering his composure, but what struck her was the realization that this might be the longest he’d kept his eyes on hers in months. “Felicity.”
She looked aside abruptly, not wanting him to see the emotion that was suddenly rising in her eyes and clogging her throat. She blinked, swallowed, and waited for him to continue.
His voice was surprisingly gentle, which only set her on edge. “You can’t…”
Her eyes snapped to his. “Can’t what, Oliver? What can’t I do?”
He looked away. “I work for the SCPD now. I have to take my assignments from them.”
She stepped toward him, hand outstretched. “Okay then. I’ll put what I have on a thumb drive and you can take it to Dinah. Call it an anonymous tip, or whatever. Then she can assign you to the case.” She smiled tentatively. Willing him to consider the logic of her proposal.
“It’s not that simple.”
Her hand landed on his chest, fingernails scratching lightly against the fabric of his sweater. “I don’t see why it can’t be. With you and the rest of the team deputized to work in the city, with the full support of the SCPD, we can be even more effective than we used to be.”
Oliver stepped back abruptly. “There is no team, Felicity!” He paused, and Felicity snatched her hand back from where it was still hovering between them in the sudden silence. He shifted wary eyes toward her. “I need you to understand that.”
Felicity gaped at him, ready to argue but suddenly speechless.
“I need you to stop pretending that things haven’t changed.” His eyes were earnest, pleading. And they left Felicity gasping as if he had slammed her in the face with a brick.
She stared back at him, the blood rushing loudly in her ears and drowning out any sense of reason. Her breaths were shallow and rapid, but her voice was calm. “I know things have changed, Oliver. That’s the one thing you have made very, very clear.”
“Felic -”
But she was already walking away, and he didn’t follow. Five minutes later, as she sat at her computers blatantly disregarding his wishes, she heard him wordlessly leave the apartment.
(Continued in chapter 2, linked above!)
25 notes
·
View notes
Text
[Third week of 2019.10] White Spirit devlog - Creating Extended Events in Event Editor v2

Hi, there!
From today, I decided to get into the habit of filling in the write in post of what I worked every day.
I thought that this would allow me to be able to fill in the text in detail with what I learned and what I did at the time.
Leisurely is an important point because I can only use less time on weekdays.
Anyway, from the results of this habit, yes, it works!
On the day I worked, I realized that the method of pre-filling would improve the content and quality of the devlog.
Now let's get to the devlog!
Event Editor v2 Development

I've finished porting conditional events to the event editor v2.
And the reason why it took time to create this event is because of the nature of the event variables managed within the event.
Event variables took time to implement the editor for conditional events because of their ability to freely cast and compare between bool, int, float, and string types.
All of this editor's work is focused on migrating past editors, so you can check the specifics of event variables in last year August's devlog.
https://creta5164.tumblr.com/post/177408351156
https://creta5164.tumblr.com/post/177653185311
And one more thing, the Event Editor uses Json for data polymorphism and transformation tracking, and uses Json.NET's JsonConvert.PopulateObject method as its main element.

But this time, when I created the editor for conditional events, I learned about the new features of JsonConvert.PopulateObject. The default parsing option for the PopulateObject method was to add a set of data (arrays, lists, etc.) after the data, rather than overwriting it. This problem was noticed while testing the Conditional Event Editor, when I found Undo (Ctrl + Z) to increase the conditional element.
The following example will show you what it is.
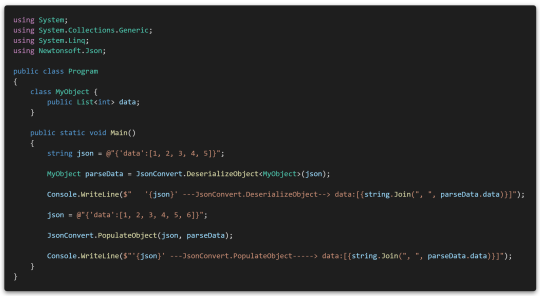

This code parses a JSON string into a MyObject object, then redefines it to JSON with one more number appended to the JSON string, and then updates the data through PopuateObject using JSON characters in the instanced object.
Of course, as mentioned above, elements like arrays are appended after the data. The desired behavior should be to update the data, so I'll should solve the problem.


This problem can fix this by creating a parsing rule via JsonSerializerSettings to force the parser to overwrite new data.
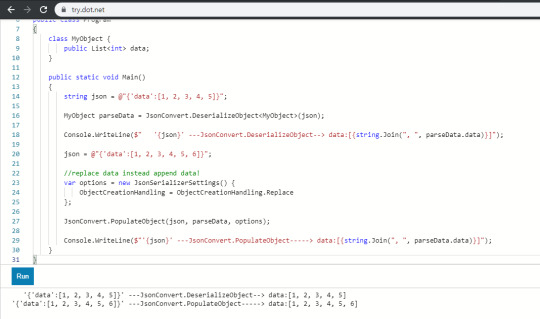
Again, try.dot.net helped to me test our C# code right on the web, so I can able to solve the problem quickly.
Thank you Microsoft!
You can try C# code at here : https://try.dot.net
In addition, this time I noticed an issue where the 'Add Event' button is misplaced in sub-events when the event description gets longer.
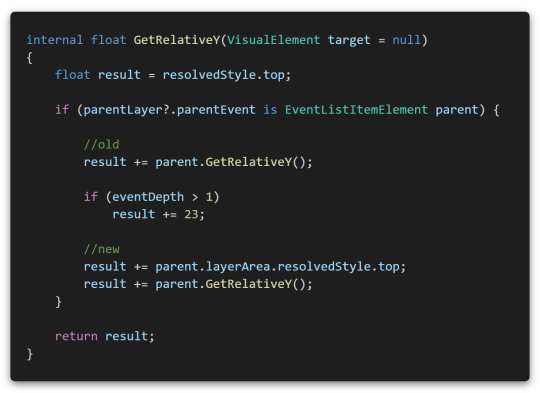
This was a logic error caused by adding only a fixed height in consideration of a situation where there was only one line of event description in a method that could infer where the add event button would be placed. (old) Fixed the event description field to be longer, adding the height of the layer group element. (new)

Ok, works well now!
I have just completed the conditional event, but there are still a lot of events left in the Event Editor v1.

From here, there are events that are specific to this game, so I decided to create a folder to organize those events separately.

I worked to make Unity form elements more readable before starting again.
UIElements has something called uss, which is similar to css, the design markup language for HTML.
I used this to change the text and size of all the basic elements.

First of all, Unity has a menu at the top right of every tab. ([▼三] icon)
If you expand it, there is a UIElements Debugger item, which will bring up a tool similar to the web browser's developer console.
(Or you can do it by pressing Ctrl + F5, but somehow I had a habit of constantly pressing F12 and then realizing that it wasn't the web...lol)

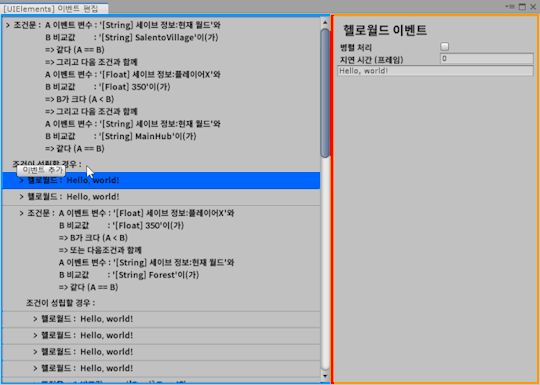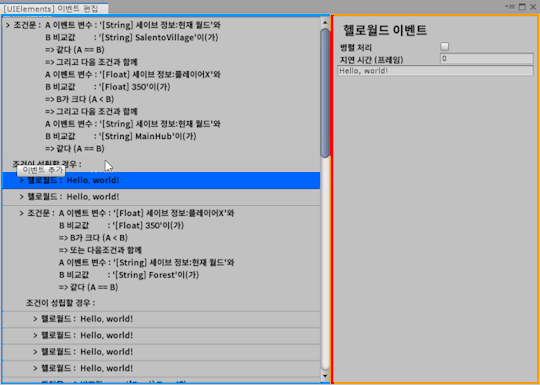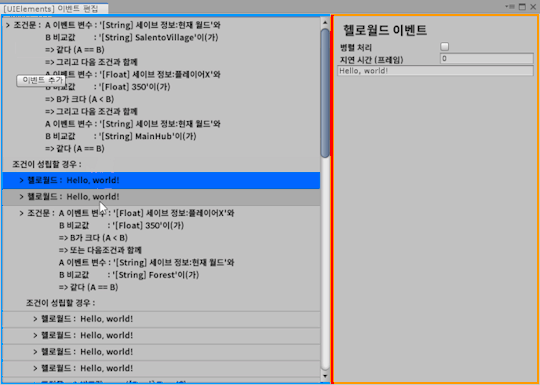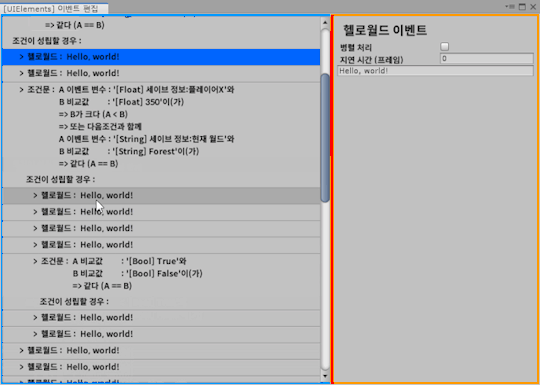
The window on the left is the debugger tool for UIElements.
Within the debugger tool there is a layout tree view on the left and element information on the right.
If you're a front-end web developer, you're pretty familiar with it.
1. Layout tree view
Hierarchy's version of UIElements. This shows the UIElements layout structure that the debugger is viewing (dropdown at the top right). From there, you can unfold the layout yourself and visually see how the layout is for each element. I already hovered over the TextInput element on the left, so the text in my layout is highlighted.
2. Element's Information (Properties)
Similarly, this is the UIElements version of the Inspector. This shows the information for the element selected in the layout tree view. You can see what the uss style class is applied to that element, or inline styles to see what values it contains. If you directly modify the value of an inline style here, it will temporarily affect the appearance of that element. In other words, You can try with your wonder "How can I give style values to look pretty?" or "What happens if this stretches a lot?" and can see the same thing in advance and experiment. In particular, the values at the top of the rectangle represent the margin, border, padding, and actual element size information of the applied style, which can be very useful when working with layout design.
As you can see from the layout tree view, that the Unity UIElements main form control does not consist of one or more elements. (for example, if it's Toggle, then the Label element is also included.) Looking at these elements, you can see that there is a uss class that starts with 'unity'.

Unity's default stylesheets are applied first in order, so if you write style information with the same class name, it will be applied later, giving you the freedom to customize Unity's controls.
So, I used this to improve readability.
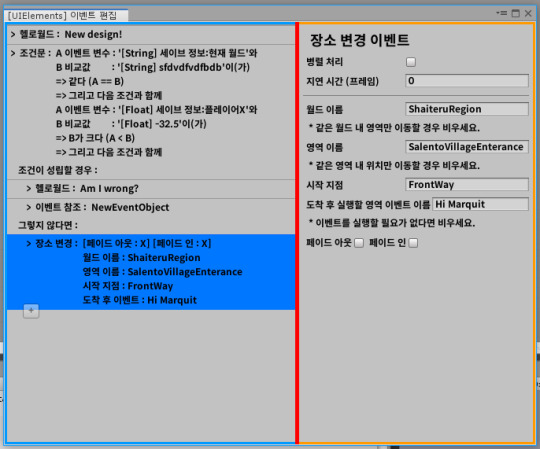
Anyway, I ported the change place event that was in v1.

Then I compared the event editor v1 to the v2 I working currently. It's changed a lot... and also readability changed a lot.
In fact, the readability is definitely different when viewed on high resolution and small screens.
(Dear Unity dev, please change Unity editor's font for CJK... please...)
And I keep worked on porting the events.
(This is screen fade event)

Then, as I worked on the screen fade event, I started to get confused as I worked on the unusual structure design I envisioned.
For events that refer to Unity objects, I've summarized where and how to reference them in comments.
Comment’s content
TODO : This event is a good example of an event that refers to a UnityObject. For events that do not use a UnityObject reference, take a look at HelloworldEvent. Reference data is based on SerializedProperty. ------------------------------------------------------------------------- References in the editor can be accessed through Editor_references, and both the editor and runtime can inherit the Editor_PreserveData and PreserveData methods to handle the data they reference. Reference data is an array.
26L-27L: The required number of reference data and the location of the data to be referenced have been explicitly declared. This can reduce the risk of hardcoding by modifying numbers even if the array's specifications change or the data structure changes.
143L: Fields that inherit from UnityObject are safe to get from PreserveData, so add a JsonIgnore attribute to avoid storing data explicitly.
146L-155L: At runtime you can get the reference target here.
You can check it how unusual my structure is in last month's devlog.
https://creta5164.tumblr.com/post/187730990776
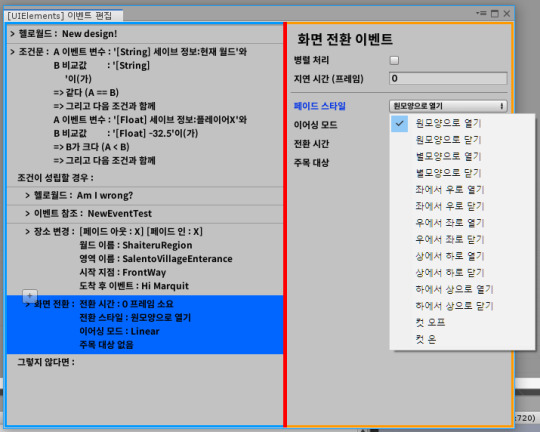
Then, while testing the screen fade event, I found a bug.
I decided to set the center point of the screen fade through the transform used in the screen fade event.
But as soon as I added the event to event list in event editor, the object value of the previous reference event entered first.
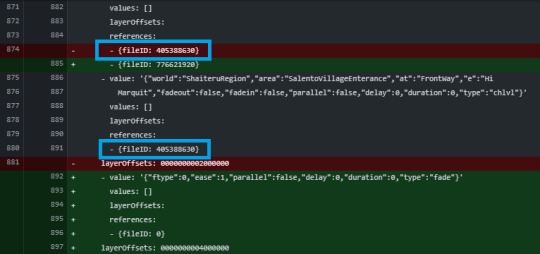
As a result, Unity Serializer brought the data of the newly added element as it was before the data was added, so that the data entering the center target was getting the value of the reference event above it.
(I've only modified and checked it now, but as you can see, the data in the place change event was intact as well.)
Because this is not the desired behavior, we used the ClearArray() method of SerializedProperty for the newly added data.

The text of my devlog is really the longest devlog in a while!
I want to thank you for reading so far...
I'll continue to do this next week.
As mentioned at the outset, future devlog will be written ahead of time after work, which is likely to increase the amount of development journals in each state.
When I'm done with the event system and the editor, I want to start by laying out the decorations in the room and making progress.
Until then, see you in next week!
1 note
·
View note
Text
Pipdig Updates P3 Plugin after Reports Expose Vendor Backdoors, Built-in Kill Switch, and Malicious DDoS Code
Over the weekend, Pipdig, a small commercial theme company, has been at the center of a scandal after multiple reports exposed a litany of unethical code additions to its Pipdig Power Pack (P3) plugin.
On Friday, March 29, Wordfence threat analyst Mikey Veenstra published a report with code examples of the backdoors Pipdig built into their plugin, along with some unsavory and questionable additions to the code.
“We have confirmed that the plugin, Pipdig Power Pack (or P3), contains code which has been obfuscated with misleading variable names, function names, and comments in order to hide these capabilities,” Veenstra said.
These include an unauthenticated password reset to a hard-coded string, which was deliberately obscured with code comments indicating it was added to “check for new social channels to add to navbar.” Veenstra also demonstrated how the plugin contained code for an unauthenticated database deletion, wherein the Pipdig team could remotely destroy any site WordPress site using the P3 plugin.
The code for remote site deletion was removed in version 4.8.0 but it still a concern for users who haven’t updated. Michael Waterfall, iOS Engineer at ASOS, tested the “kill switch” function and demonstrated that it still works with prior versions.
It also confirms they lied. They _still_ have the ability to wipe any blog that hasn't updated to the new plugin version (4.8.0), which they hurriedly released to delete the kill switch after they were exposed the other day. pic.twitter.com/bNMfRQUBpr
— Michael Waterfall (@mwaterfall) March 31, 2019
Veenstra’s investigation also uncovered questionable remote calls in the plugin’s cron events, undisclosed content and configuration rewrites, and a list of popular plugins that are immediately deactivated when P3 is activated, without the user’s knowledge. He found that some of these plugins are deactivated alongside admin_init, so any user attempts to reactivate the plugins will not stick.
Wordfence estimates the P3 plugin to have an install base of 10,000-15,000 sites. The changes made in version 4.8.0 of the plugin are not transparently identified in the changelog, so it’s not easy for users to know what has changed. The content filtering and the plugin deactivations remain in the most recent release. These types of veiled functions performed without permission could have unintended consequences on sites using the plugin, which non-technical users may not be able to fix themselves.
Pipdig P3 Plugin Performed a DDoS Attack on a Competitor’s Site
Jem Turner, a freelance web developer based in the UK, published a lengthy analysis of the P3 plugin the same day that Wordfence released its analysis. She drilled down further into the remote requests, demonstrating how Pipdig has been using the P3 plugin to perform a DDoS attack on a competitor who also provides WordPress themes and installation services to bloggers. The code triggers an hourly cron job on users’ sites, effectively using their customers’ servers to send malicious requests to the competitor’s site.
The code comment tells us this is “checking the CDN (content delivery network) cache”. It’s not. This is performing a GET request on a file (id39dqm3c0_license_h.txt) sat on pipdigz.co.uk, which yesterday morning returned ‘https://kotrynabassdesign.com/wp-admin/admin-ajax.php’ in the response body.
Every single hour night and day, without any manual intervention, any blogger running the pipdig plugin will send a request with a faked User Agent to ‘https://kotrynabassdesign.com/wp-admin/admin-ajax.php’ with a random number string attached. This is effectively performing a small scale DDoS (Distributed Denial of Service) on kotrynabassdesign.com’s server.
Turner also contacted Kotryna Bass, Pipdig’s competitor, who said she had contacted her host after finding that her admin-ajax.php file was under some kind of attack. Bass’ exchanges with her host are also published in Turner’s report.
Turner’s post explained how Pipdig’s P3 plugin code manipulated links to point to their own products and services when a user includes a link to a competitor in the the content:
Here we have pipdig’s plugin searching for mentions of ‘blogerize.com‘ with the string split in two and rejoined – concatenated – to make it harder to find mentions of competitors when doing a mass ‘Find in Files’ across the plugin (amongst other things). When the plugin finds links to blogerize.com in blogger’s content (posts, pages), they’re swapped out with a link to ‘pipdig.co/shop/blogger-to-wordpress-migration/’ i.e. pipdig’s own blog migration services. Swapping these links out boost the SEO benefit to pipdig, and the vast majority of bloggers wouldn’t notice the switcheroo (especially as if the page/post was edited, the link to blogerize would appear in the backend as normal).
The plugin did not ask users’ permission before performing any of these actions and most of them were implemented with obfuscated code. Turner’s investigation also covers how the P3 plugin could harvest data and change admin passwords. Many of the findings overlap with Wordfence’s analysis.
“I was aware that Wordfence had been contacted for an opinion, although I was unaware they were writing a post and vice versa,” Turner said. “I wasn’t surprised that they wrote about it though, given the risk to WordPress users.”
She has been in contact with authorities regarding Pipdig’s unethical coding practices and privacy violations.
“From my side of things, I’ve been in contact with Action Fraud (submitted a report through their website) and NCSC (who pointed me back to Action Fraud and gave me a number to call). From pipdig’s side, there are threats of legal action in their blog post but I’ve received nothing yet.”
Pipdig’s Public Response Skirts Critical Concerns
Pipdig Creative Director Phil Clothier published a public response from the company which opens by characterizing the recent investigations as “various accusations and rumours spreading about pipdig” and includes an emotional plea regarding how distressing recent developments have been for his company. He claims that his team and their supporters are being harassed.
After pushing out the 4.8.0 version of the P3 plugin, removing some but not all of the offensive code, Clothier opts for a Q&A style format for his post, putting every question in the present tense:
Do you DDOS competitors? No.
Do you “kill” sites? No!
Do you have the ability to kill sites via the pipdig Power Pack? No
Regarding the “kill switch” feature they built in, which detects all tables with the WordPress prefix and drops each of them, Clothier said it was simply a function to reset a site back to its default settings. He deliberately misrepresented what it does:
There was function in an older version of the plugin which could be used to reset a site back to the default settings. This function had no risk of of malicious or unintentional use. I can say categorically that there was no risk to your site if you were using a pipdig theme. This feature has been dug up and labelled a “Kill Switch” for maximum negative impact on us.
Clothier claims the function was available in the P3 plugin in July 2018 when a third party started posting Pipdig themes for sale on their own site:
A 3rd party was able to download all of our themes illegitimately and post them on a clone of our own site. This included previews of our themes and the ability to purchase them. We were first alerted to this by people which had purchased a pipdig theme from there, but were finding that certain features did not work correctly. After investigation, we found that the victim had purchased the theme from the 3rd party, thinking it was us. The 3rd party not only gained the financial benefit of the theme payment, but also used it as a way to inject malware and ads into the victim’s site. The reset function was put in place in order to remove the 3rd party’s ability to host preview sites with our themes. It worked, and they have since disappeared. The function was then removed in a later version of the plugin.
This is a false claim, as Wordfence pointed out in an updated article. The first instance of the code responsible for database deletion was committed to the plugin in November 2017.
The company failed to address the most critical concerns presented in the Wordfence analysis in its first pass at issuing a public statement. Instead, on the matter of coordinating a DDoS attack on competitors, Pipdig blames users and suggests they may have added the competitor’s URL to their sites.
“We’re now looking into why this function is returning this url,” Clothier said. “However, it seems to suggest that some of the ‘Author URLs’ have been set to ‘kotrynabassdesign.com’. We don’t currently know why this is the case, or whether the site owner has intentionally changed this.”
Further investigations published by Wordfence today showed that Pipdig also added DDoS code to its Blogger templates and was actively issuing malicious requests up until yesterday:
During the investigation of Pipdig’s WordPress plugin and themes, we also came across some curious code associated with their Blogger themes. This code is part of Pipdig’s suspected DDoS campaign against their competitor, and was active until April 1, four days after Pipdig’s denial of any such behavior.
Some of Pipdig’s Blogger themes have been confirmed to make external JavaScript calls to Pipdig’s server, specifically to the script hXXps://pipdigz[.]co[.]uk/js/zeplin1.js.
On March 31, as the investigations became public, Pipdig deleted its public Bitbucket repository and replaced it with a “clean one,” removing three years of commit history. Wordfence and many others cloned the repository before it was deleted and saved snapshots of pages to cite in the investigation.
That clean repository @pipdig published earlier today in place of the one containing all of their malicious code… They changed the reported release date of version 4.8.0. pic.twitter.com/YqKASTUZE7
— Nicky Bloor (@nickstadb) April 1, 2019
Pipdig’s public statement contains a number of other false claims that are outlined in Wordfence’s followup piece with code examples. Clothier closes the article by casting aspersion on the press, presumably to encourage customers not to trust what they read from other sources.
I contacted Pipdig for their comment on recent events, but Clothier declined to answer any of my questions. One of those was why the plugin disables Bluehost’s caching plugin without informing customers.
Another one from the @pipdig plugin. If you use one of their themes on @bluehost then they intentionally slow your website down by disabling the BlueHost cache plugin, then they can inject content with the title "Is your host slowing you down?" CC @jemjabella @heyitsmikeyv pic.twitter.com/48DUXsDyBj
— Nicky Bloor (@nickstadb) March 31, 2019
Clothier said he didn’t have any comments beyond what he said in the public statement but encouraged anyone interested to read the new comments added to the code in version 4.9.0:
We’ve also updated version 4.9.0 of the plugin which includes extra commenting in the code, which will hopefully help clear things up like issues with Bluehost caching and the_content() filter.
If anyone is unsure, we recommend updating to the latest version as always. However we also contend that the previous versions had no serious issues too.
Pipdig declined to answer questions about licensing but the products do not appear to be GPL-licensed. This may be why the company deemed it within its rights to take action on those who they believe to have “stolen” their themes.
Pipdig Customers Share Mixed Reactions to Reports of Vendor Backdoors and DDoS Attacks
In what is perhaps one of the most brazen abuses I’ve ever seen from a theme company in WordPress’ history, Pipdig’s user base has unknowingly been used to target the company’s competitors. Regardless of the company’s motive in combatting the unauthorized distribution of their themes, these types of backdoors and undisclosed content rewrites are indefensible. They prey upon user trust and in this case the victims were primarily bloggers.
I think that's why so many of us are so angry. Bloggers are the lifeblood of #WordPress, you create content and for the most part don't have big budgets to spend. So when someone takes advantage of that those at the "low budget" end of the market, those that cant afford devs…
— Andy Powell (@p0welly) March 31, 2019
One of the more puzzling aspects of this story is that many of Pipdig’s users seem to be unfazed by the gravity of the findings in these reports. Without full knowledge of the inner workings of a product, many customers make decisions based on how they feel about a company, regardless of being confronted with facts that should cause them to question their experiences.
I’m not concerned. I trust them. And I’m certainly not panicking and acting on the words of two blog posts citing their competitors. They’ve served me well for years.
— Caroline Hirons (@CarolineHirons) March 29, 2019
Others are angry to have had their sites used in an attack. Getting set up on a new theme is not a trivial task for non-technical users who may have had to pay a developer to launch their sites in the first place.
Honestly? I’m really angry. I trusted them for years, and in return my site has been used maliciously against other small businesses. I’ve been watching this unfold since Friday but even this update shocked me. https://t.co/mPsO8EoHBp
— Charlotte (@bycharlotteann_) April 2, 2019
“My mind is absolutely blown by pipdig’s public response,” Jem Turner said. “I understand that they were counting on their users’ completely non-tech background to bamboozle them, and it certainly seemed to be working in the beginning, but anyone with even the slightest bit of coding knowledge can see that they are lying and I genuinely don’t understand how they think they’ll get away with it.”
The crazy part is if we want to be really real about this, it's more like
The cable guy cut a big hole in my wall and installed a door handle on it. He took some painter's tape and scrawled "THIS IS A CABLE BOX" on the drywall. Then looked me in the eyes and said "No I didn't."
— Mikey Veenstra (@heyitsmikeyv) March 31, 2019
This incident shines a spotlight on how unregulated the commercial plugin and theme ecosystem is and how little protection users have from companies that abuse their power. If you are a Pipdig customer affected by this incident, there is no assurance that the company will not build more backdoors into your site in the future. The plugin updates are not reviewed by any kind of authority. Fortunately, there are a few actions you can take to create a safer environment for your website.
First, look for GPL-licensed themes and plugins, because they grant you more freedoms as the user and are compatible with WordPress’ legal license. GPL-licensed products are also a strong indication that the authors respect user freedoms and the shared economic principles that this open source license supports.
Many reputable theme companies choose to host their products’ companion plugins on WordPress.org for ease of distribution and shipping updates. The official directory does not permit these kinds of shady coding practices described in this article and all of the plugins go through a security review by the WordPress Plugin Team. If you are concerned about code quality and the potential for abuse, do a little research on your next prospective commercial theme provider or opt for free WordPress.org-hosted themes and plugins that have undergone a more rigorous vetting process.
😉SiliconWebX | 🌐WPTavern
2 notes
·
View notes
Text
SPOTLIGHT: (”BEING” Part One) Cultivate Your Awareness

If you’re just joining Spotlight, then this is my personal journal of my personal journey as a performer. It’s a kind of way for me to look back on all of my experiences, and lessons I’ve learned, while simultaneously sharing what I’ve learned with you. Disclaimer: The word PERSONAL was utilized twice in the first sentence. Therefore, this is not the gospel or the truth, it’s just me sharing MY experiences in an effort to assist, if possible, in other people’s discovery (end disclaimer). Today, I’m going to skip over the last part (Part 5) of my observation of the Industry’s Corporate Structure, to briefly touch on the ‘BEING’ in “Brian’s B’s” (Being, Behavior, and Business), of my A+B=C method. If you are reading this blog for the first time, here’s a brief over view of my A+B=C method. A stands for the Abstract; It’s your dream and what you desire. C is the Completion or end result to the equation. It’s what you have Concocted. However, B is the thing that doesn’t get much attention, and it is the most vital portion of the equation; It is your Being, your Behavior, and your Business. All the things that YOU actually DO to mix with the A and make the C happen! That is the basic overview of my system. Today, I’m going to focus on Being and I’m going to use a completely true story from November of 2017.
Back in November of 2017, I was living in San Francisco, and had been making my living as a performer in the city for almost then years. It was on November 13, 2017 at approximately 4:10pm that I received a Facebook message on my Fan Page. It was from an actor in the city who I had met once, but from whom I had never seen any work. Her message said this…
“Hi Brian, I've asked you a question before, and you were so generous in your response. If you have time to answer this one, I would so appreciate it. I'm joining SAG, and have been told that Fi-Core would be better. Although the folks at the SAG office disagree. Do you have a personal experience with that? A casting director I trust suggests Fi-Core, and SAG strongly suggests SAG, not Fi-Core. I know it's probably a very personal choice, but I follow you and it seems to me like you make good choices about your career. Do you have a recommendation? Thank you Brian.”
After reading her message, I couldn’t have been more flattered. I had been on the receiving end of quite a few messages like this at the time, and it made me feel good that I could potentially contribute to people’s success and happiness. In this case, the actor was making a huge decision that could have multiple effects. Every actor’s journey is different and need to make decisions specifically catered toward their career. Unfortunately, I didn’t know very much about her career so I couldn’t make any quick suggestions. So I did what every good objective person does: RESEARCH! First, I looked at her Facebook. I didn’t see ANYTHING acting or performance related at all. Then I looked at youtube; I didn’t see any videos or reels. After that I looked her up on IMDb and the only thing listed were a few credits; a few from over twenty five years ago, and then two which spanned over the last three years. Keep in mind all of these were either stand-in, extra work, or a role with no character name. After that, I completed multiple google searches using different variations of her name, the city, and additional words like theatre, film, actor and actress. Guess what? Nothing. Not only was there little to no marketing on this person, but there was nothing attesting to her competence. In addition, she was asking me a question about her business. Rather than making assumptions, I wanted to gather as much information as possible on this person so that I could give her the best advice I could. Besides, there could be an entire theatrical life of which I’m not privy and about which I don’t know. So, I sent back a bunch of questions to get a bigger picture of here situation. Here is what I sent to her:
“First off, I want to acknowledge your commitment to your career and your interest in doing what is best by seeking out advice from what seem to be good sources for you. You're already on the right path as far as I'm concerned. Second, I would agree with you; It's a very personal choice and would require a lot of detailed information. For instance: Do you plan on staying in SF for a while or are you moving to a larger market like NYC, LA, Canada, or London? If so, do you feel like you're in a place where you have enough experience and credits to hold your own and play with the 'big dogs' (SAG) on equal footing? If so, on what kind of tangible data is this based? Third and last, have you created a clear, detailed, and meticulous plan for your career with a somewhat in depth understanding of the road ahead of you? I am someone who prefers to give advice and make decisions by having more global/big picture info filled with as much data as possible. Therefore, if you can answer those few questions, then I think I can give you advice which is best suited for your particular situation. Brian :) “
Here is the answer with which I was met:
“Thank you, Brian. I know those answers for myself and think I will be joining SAG, not as Fi-Cor. I'll be based in California, splitting time between sf and la. My main quandary is that a casting director who I trust up in sf recommends fi- Cor over SAG, yet SAG gives the opposite recommendation. I am joining, that's not in question. Leaning towards sag. I've had 13 years experience in live theater, commercial and film/tv. No reason to wait any more. I know why I'm an actor. More now than ever before. Thank you again.”
A few minutes later, I got this:
“I’d really like to hear your take on Fi-Cor vs. SAG. What I'm most concerned about us if I start as Fi-Cor, will I them be able to switch? The SAG office makes it sound like a very iffy prospect. I don't know anyone who's tried it. Think I will just join SAG and if I want to switch later, try it then.”
Her prior messages let me know that she wasn’t coachable, and didn’t really want to hear what I had to say. Regardless of my success or the contribution that I believed I could make to her after having seen some of her tools. So, I ended the conversation as gracefully as I could and sent her this message:
“It sounds to me like you've made up your mind to join. Mucha Buena Suerte!”
As you can see, I didn’t offer any advice or suggestions. It would have been a waste of time and energy. This person was merely asking for permission. Something I also didn’t give, because I could already tell after looking over her tools that I would be COMPLETELY AGAINST joining SAG. As in my previous posts, being an actor is the equivalent of being an employee in the corporate world. The only difference is that you are an independent contractor. In order to be a successful independent contractor that can support his/her self, you have to have mastered many skills and tools in order to stay employed. Some of those would be: interpersonal relations/communications, clear and concise planning and organizing, marketing strategy, and a harnessing of personal talent. Prior to developing these skills, there is one thing that every person will need in order to develop any of those and that is AWARENESS of self.
Actor and famous acting coach Stella Adler was adamant about her belief that Actors needed to conquer themselves before they conquered a character. I associate this with the ancient martial arts theory of ‘emptying your cup’ that Bruce Lee often taught. It is one of the most important parts of the equations of success. Not just in career, but in every area of life. It is why I believe that it’s the first place to begin when embarking upon a big journey like an acting career. Emptying your cup means getting very clear on who you are inside and out. It’s knowing yourself to a point where you are able to be COMPLETELY objective on every matter. This gives you the ability to step inside a character to the fullest, because you are able to set aside your own perception of reality and everything that could potentially stop you from putting yourself in the shoes of another. For me, I have Wonder Woman. To explain, Doctor William Moulton Marston III who created the character was a psychologist and was a study of the human condition. He imbued many of his characters and inventions with breadcrumb clues to these ideas. He even inspired a system for self awareness that I follow which has aided me tremendously over the last 16 years of my life. I encourage everyone to find their own system which offers them that kind of objective awareness. I write a column called “What Would Wonder Woman Do?”, and in March it was about the “Lack Of Truth in Society”. Truth is something that requires personal awareness. Without it, you can not be completely authentic. As you continue your search toward your own system, here are some ideas on how to begin developing personal awareness, which are derived from my article.
BE AWARE OF YOUR ABILITY TO BE COACHABLE When you aren’t coachable, you often miss out on important information. It could be information that could make 100% difference in your life and/or career. In the example of the actress who asked me for advice, I could see where she wanted to go and if you read some of the questions I asked her, I already had some really fantastic suggestions for her to be successful. Unfortunately, she wasn’t open to hearing them and was completely UN-coachable. Some of her language was a little defensive and put up a wall. This is what happens when you’re triggered, and being coachable means understanding those triggers that hold you back from being coachable. Examining what those triggers are, how they got there, and how to work around them will assist you in becoming coachable. In my article, you’ll see that the Ladder Of Inference explains how personal perception can influence present events.
BE AWARE OF WHAT YOU DON’T KNOW When we think we know something and assume that we don’t need another perspective that might be different, that will often make us un-coachable. If we come from a place of ‘I already know’ then it immediately shuts off the ability to connect, and also the ability to learn. The opposite will open up the possibility of connection, affinity, and even learning new knowledge. In my situation, the actress that asked me for advice was completely and totally un-coachable even though she came to ME for advice. Being open to what she didn’t know would have given her the ability to gain new knowledge which could have aided her to a more bountiful and successful career. It is important to be able to know the difference between the former and the latter situation. I believe that is to be like Wonder Woman, which is to follow the way of love. When you are being loving you are continually choosing to understand and accept the world around you. I write about this in my article. For me, I like to think of a scientist. He (or she) knows that there are facts and laws in the universe, but they are always testing new things against them for new outcomes and new possibilities. That pure, loving, and inquisitive nature of being open and asking questions will almost always guarantee that you find out things that you didn’t know before. Be your own scientist and like the article says, “Lasso The Truth”!
BE AWARE OF YOUR LIMITATIONS We all have limitations, but very few people are truly aware of what actually creates their limitations. This often leads to people not knowing exactly what their limitations might be. In the case of the female actor who messaged me, she is setting out to work in a market of SAG/AFTRA professionals. This will limit her for many reasons. Without proving to have a strong work history, a strong body of work, a clear concise plan to success, an ability to book (aka adequate practice and developing a system for auditioning) and to do so on the SAG level, she is limiting herself. Specifically, since she is doing so in a primarily non-union market where the SAG work is very limited. In my ‘What Would Wonder Woman Do’ article, about the lack of Truth in Society, I reference a scene written by Phil Jimenez in Wonder Woman #170 where she reveals that she is forced to always be honest with herself due to her having the lasso on her hip. By finding our own ‘magic lasso’ or system to keep ourselves honest we can be more aware of our own limitations. Being honest about them can also lead to more connection and success.
CONCLUSION When you find yourself to not be coachable, are approached by someone who might have some knowledge, or even have a limitation that is being challenged, and you feel resistance; STOP! Take a few breaths and ask yourself, Why am I so resistant? Why do I feel like pushing back on this? What is this reminding me? Then try to replace it with questions. Try to come from a place of innocence and inquisition. Ask questions why what you’re being suggested is a good idea, or even what led to this philosophy. You may actually learn something new that you didn’t know before. Asking these kinds of questions will be easier once you have found your own system of awareness. Some people go to therapy, some go to church, and some have self help gurus. Personally, mine is Wonder Woman and the work influenced by Dr. Marston III. The previous were just a few suggestions on how to begin cultivating your own awareness. Everyone is different and everyone will find their own system. To recap, I have yet to hear from the female actor (actress) who originally sent me her question regarding SAG. I will say this though, it has been nine months now since that question, and after going back to look over her marketing materials, I noticed that there has been absolutely no change. I’ve seen no new videos, clips, or reels added. Her IMDb hasn’t been updated with any new projects, and google still doesn’t show anything about her work in any genre (stage or screen). So whatever she is doing, it’s getting her more of what she had. As for me, I was given a principal contract in a SAG national commercial I shot last week with three celebrities; Two of them have over five million followers and the last has nearly a million followers on Twitter. That being said, I urge you all to find your own system of cultivating your personal awareness to a point where you become more objective, authentic, and inquisitive. It is one of the first steps of the BEING part of ‘Brian’s Bs’ and will assure your success in many areas of life, including career. And if I can do it, then you can definitely do it too! :)
#actor#actors#actress#advice#suggestion#blog#wisdom#wonder woman#wonderwoman#love#questions#scientist#SAG#screen actors guild
15 notes
·
View notes
Text
Latest On Page & Off Page Activity in SEO 2019
Best SEO Company in East Delhi
1. Visitor Posting
Visitor posting is the most prevalent third-party referencing technique of Best SEO Company in East Delhi where an article is composed as a visitor post by another site website admin.
Where the writer puts his/her one of site article connects inside the article in that way the connection juice goes to visitor post writer's site.
Some specialists guarantee that Guest Posting is against Google terms and conditions.
One moment quietness for those here is the confirmation of Google permits visitor posting on its official blog.
Take Neil Patel from NeilPatel.com he accomplishes in excess of 100 visitor posts every year from that he constructs his image and makes dollars from that.
Likewise, he conveys guests to his site and changes over them to customers.
So do achieve different website admins pertinent to your specialty deliver amazing substance distribute it and connect to your site.
2. Q/A third party referencing
Individuals frequently look for the appropriate responses on the web and a few of Best SEO Company in East Delhi website admins utilize this open door for a third-party referencing reason.
Take Quora the No 1 question and answers examining the site. Most guests type their inquiries and find the solution.
What would you be able to do?
Visit Best SEO Company in East Delhi the Quora site and make a record. At that point search for inquiries identified with your specialty.
In the event that you know the response to the inquiry, compose it and in the center or end of the appropriate response interface your Best SEO Company in East Delhi site article.
Do like what I did in the picture underneath.
quora external link establishment
It will help your site positioning and furthermore, guests will snap to visit to know more data.
Obviously, Quora joins are no pursue yet at the same time, it is high reference stream and trust stream.
3. Social Bookmarking
Social Bookmarking is a way people use for bookmarking or store their most loved pages, articles, recordings, and so forth.
Numerous Social Bookmarking sites join are Dofollow which enable Google to tail them and rank their sites.
Social Bookmarking is a simple method to external link establishment and should be possible inside minutes.
To social bookmark your article. For Best SEO Company in East Delhi Visit StumbleUpon.com and Under your profile click Add Page and drop your site article connection and spare it.
StumbleUpon website design enhancement - Best SEO Company in East Delhi
4. Blog Comments
Blog Commenting is my most loved OFF-page Best SEO Company in East Delhi third-party referencing technique by this strategy you can construct incredible backlinks to rank your site.
blog remarking
To do blog remarking look on Google for the sites which permit blog remarking.
Additionally, there are bunches of nitwits accessible to discover websites for remarking.
You can seek in Google or on the off chance that in the event that you need to utilize now
blog remarking doofuses
In catchphrase, put utilize your search query.
For instance: To remark on computerized showcasing sites.
Hunt as: site:.com in URL: Digital showcasing "post a remark"
Subsequent to hitting Enter it will demonstrate computerized advertising sites visit the blog and remark with your site URL.
Pick the Best SEO Company in East Delhi at Digital Marketing Careers- Best SEO Company in Laxmi Nagar @+7042524727
5. Public statement
Public statements are one of the compelling third party referencing systems despite everything it keeps on boosting web index rankings.
Through public statements your site will show up on Google news area from that you would clearly get a lot of traffic to your site.
You can employ Best SEO Company in East Delhi specialists from Best SEO Company in East Delhi to do public statements for external link establishment.
Public statement costs minimal high however it is as yet a decent venture for Best SEO Company in East Delhi picking up do follow backlinks to our site.
6. Discussions
A gathering is an incredible route for partaking and examining with different website admins
In the gathering you can make different inquiries, compose a response for inquiries asked, join on different exchanges.
Likewise, you can utilize gatherings for doing Off-page Best SEO Company in East Delhi work.
To do third-party referencing by means of the gathering, join significant discussions and take an interest in dialogs, answer questions.
Rehash this for 2 to 3 weeks in the wake of making your profile too dynamic look for the inquiry and answer the appropriate responses and place your connection in it.
Check the third party referencing by Blackhatworld discussion part underneath
gathering external link establishment - Best SEO Company in East Delhi
On the off chance that you put your connection on the day 1 itself, discussion administrator recognizes your connecting article for Best SEO Company in East Delhi reason then they will boycott your record promptly.
So do this Off-page Best SEO Company in East Delhi procedure cautiously.
7. Web 2.0
The Best SEO Company in East Delhi of Web 2.0 third-party referencing is the incredible strategies and Secret technique for positioning sites.
As a matter of course, every web 2.0 for Best SEO Company in East Delhi sites, for example, WordPress, Blogger, Weebly has high page rank and Domain expert.
When we utilize these destinations for third-party referencing it works incredibly when done accurately.
The greatest favorable position of utilizing this Off-page Best SEO Company in East Delhi strategy is that you can have full control to deal with the connections.
By having a full specialist you can change joins, adjust grapple messages, include or even erase backlinks.
How to make web 2.0 connections?
SELECT the best five web 2.0 sites.
Make a site with grapple name in the space name.
For instance, in the event that you need to rank for Best SEO Company in East Delhi profiler survey, make site name as Seoprofilertutorial.wordpress.com or SEOProfilertoolreview.wordpress.com
Your blog ought to have important pages like Home, About, Contact us, and so forth.
At that point compose 300 – 500 words content with impeccable ON-page SEO and connection to your site with ground-breaking grapple writings.
Since web 2.0's set aside a long opportunity to get listed on Google, Use connect ordering administrations to file your Web 2.0 articles soon.
To make significantly increasingly powerful bookmark web 2.0 articles on social bookmarking destinations and furthermore share via web-based networking media locales.
8. Profile joins
Great profile connections can enhance your site positioning. It won't just go about as backlink yet it is most than a backlink that will expand your general site marking.
Getting profile joins from well-known sites will go about as a decent thought for Google to pass judgment on your site and rank on top indexed lists.
So join the most mainstream online networking sites with high DA and go to the settings and search for the site or Home Page box and include your site landing page URL.
profile connect SEO
Look my Twitter Profile and see my site Homepage address.
9. Catalog Submission
catalog blog accommodation
Posting your site on catalogs is a piece of Best SEO Company in East Delhi to get ground-breaking backlinks to your site.
So as to get quality backlinks, you require high PR index sites which give do follow backlinks.
Despite the fact that registry entries are simply a great many people think that its troublesome for posting their sites.
They list their site on disconnected classification because of that the index proprietors will erase the sites.
So dependable list your site in appropriate classes and include great title and portrayal.
10. Asset Pages
It is another sacred chalice and best Off-page Best SEO Company in Laxmi Nagar system for powerful third-party referencing.
By this strategy, you can get simple .gov and .edu backlinks to your site.
How to discover asset pages?
To discover asset pages Google as "Catchphrase" + inurl: joins
asset pages Best SEO Company in Laxmi Nagar
Introduce Moz chrome expansion to discover locales PA and DA.
In the wake of finding the great asset pages with great PA and DA, achieve the proprietor of the site and request connecting your site on their asset pages.
End
Rivalries are excessively high in the computerized promoting field, so as to transcend your haters you require the best Off-Page Best SEO Company in Laxmi Nagar methodologies.
Web optimization is setting off to another dimension officially huge numbers of them doing different Best SEO Company in East Delhi systems to beat contenders.
In the meantime what we improve the situation positioning is imperative and dependably we need to utilize white cap Best SEO Company in Laxmi Nagar generally, Google will clearly punish our site totally.
Why in light of the fact that?
Google is continually viewing our developments in the event that we do anything illicit we need to confront the issues.
So while doing Off-page Best SEO Company in Laxmi Nagar work don't do any dark cap Best SEO Company in Laxmi Nagar strategies and entirely keep away from it.
Connect us
Our digital marketing services also come in convenient, ready-to-buy packages with clearly identified deliverables. Check out our SEO Package, PPC Packages or call us at +91-7042524727 to discuss a customized plan to meet your precise business needs.
D2B 1st Floor, Opposite Metro Pillar 32,Main Vikas Marg,
LaxmiNagar,Delhi, 110092
Contact Number : +91-7042524727
Project Enquiry: [email protected]
Customer care: [email protected]
Taged- Best Digital Marketing Agency in Laxmi Nagar,best digital marketing company in laxmi nagar,best digital marketing company in east delhi,best digital marketing agency in east delhi,best seo company in east delhi,best seo company in laxmi nagar
#digitalmarketing#GoogleSeo#OnlineMarketing#linkbuilding#backlinks#Socialmediatips#socialmediamarketing#SEM#SEO
1 note
·
View note
Video
youtube

buy an essay
About me
Buy Essay Online Safe
Buy Essay Online Safe If you attend an America University or College I would extremely recommend doing extra analysis and discovering an America based company! The essay I obtained was stuffed with grammatical error and did not have a clear message! I needed to write a very different essay and did not get a full refund again. , TrustMyPaper defends its title of one of the best paper writing firm. One, these individuals don't comprehend what you ask. In includes discovering and delivering books you need. Here you can also get the most effective tutor so that you can explain any theory or concept you don’t understand to proceed with your studies. Google is the king of research — so much in order that ninety four% of academics admit that students equate Googling to analysis. It’s not shocking — Internet sources are easy to seek out and accessible 24/7. The content material we provide you should serve only as a information in your work and not the ultimate product. Using it as your personal would not only go in opposition to most faculty/school policies, but it might be unfair to yourself. Education is a strong tool and placing within the work is the only approach to truly gain that profit. Writing 1,500 phrases will take about 37.5 minutes for the average writer typing on a keyboard and 1.three hours for handwriting. Not solely that, they kept giving me the runaround when I requested for a revision. Save your money and take your small business somewhere else. From the moment I positioned my order I immediately had a customer support rep placing me in touch with a author. Placing an order is free at EduBirdie, however once a writer is chosen and the bid is confirmed, the shopper might be required to addContent cash for the accepted quantity. Once the writer approves the essay, the full cost shall be released. If the customer just isn't glad, we have a money back guarantee. Also, make a transition to the body of your essay on the finish of the intro. In the conclusion, re-summarize the thesis assertion whereas linking it to the proof that you are providing within the physique paragraphs. Write a conclusive sentence that may place the data in your paper right into a broader context. Search for the important thing ideas you’re definitely going to use in your paper. Remember that you don’t have a lot time on the whole essay, so be transient and concise in your analysis. The need to sit down in the library for hours looking for related details is rapidly disappearing, which is nice information for college kids. Here at Nerdify, we move with the instances, so we brainstormed a listing of 5 best homework assist websites for college college students. Do you research first, do not do you research as you go. While you are working on an outline, resolve which parts will want analysis and help. However, if the content wants to include in-depth research, hyperlinks, citations, or graphics such as for a weblog article or high school essay, the size can grow to five hours. The platform is about delivering a full vary of providers to aid college students and assist them stay on high of their studies. That’s why each project needs to respect these rules of educational formatting. Third, a excessive subject complexity also can mean the necessity to conduct thorough research. This method, the writer ensures that the ultimate model of the paper meets all necessities set forth by the instructor or professor. If you wait to seek out the analysis till you need the research, you should have many interruptions as you write the paper. While you could think it'll take u p an excessive amount of time, the case is kind of the other. Having a top level view will prevent time as a result of you'll know what every part of the paper is and you will then shortly write the components. You have already got your thesis statement within the intro. So, write a hook preceding it — a quote, a relevant anecdote in a sentence or two, or some statistical info associated with the topic.
0 notes
Link
WordPress 5.4 was released not so long ago and, along with other improvements and bug fixes, it introduced a feature called Block Variations. I had a chance to use it on one of my recent projects and am so pleasantly surprised with how smart this feature is. I actually think it hasn’t received the attention it deserves, which is why I decided to write this article.
What is a Block Variation?
Block Variations allow developers to define instances of existing blocks. An example that you’ll see below is a quote block. Perhaps your site has three variations of how to display a quote on your site. A Block Variation can be created for each one so that they are all styled differently. This sounds awfully familiar with how Block Styles, but the concept of variations goes a bit further than that, as we’ll see.
How are Block Variations different from Block Styles?
Fair question. Block variations appear in the inserter as separate blocks with unique names and (optionally) icons and can have pre-filled custom attributes, and inner blocks. Block Styles are designed to alter the look of the block. In fact, a Block Style is a fancy way of adding a custom class to a block using the Block options in the post editor. The difference is clear when you consider how each one is used in the post editor. Let’s say we register a new Block Style called “Fancy Quote.” We do that by extending the core “Quote” block like this example from the Block Editor Handbook:
wp.blocks.registerBlockStyle( 'core/quote', { name: 'fancy-quote', label: 'Fancy Quote' }, );
This adds a .is-style-fancy-quote class to the Quote block settings in the post editor.

We now have a Fancy Quote option in the Block options under “Styles” and the class for it filled in for us.
Even though it sort of sounds like it would do the same thing (which it technically can), a Block Variation can be used to pre-fill custom attributes (including custom classes) and inner blocks. They’re actually registered as separate blocks. Let’s take a closer look at the API and what block variations can do.
Creating a Block Variation
The API for registering Block Variations is very similar that of the Block Style we just looked at:
wp.blocks.registerBlockVariation( 'core/quote', { name: 'fancy-quote', title: 'Fancy Quote', }, );
The registerBlockVariation function accepts the name of the block (in our case it is core/quote) and an object (or an array of objects) describing the variation(s). The code above doesn’t do much by default, but it does add “Fancy Quote” to the list of available blocks.

We now have two different “quote” blocks available to drop into the post.
To take full advantage of the variation. we need to provide more details in the object describing it. The list is covered in the Make WordPress post, but I’ll share it here and provide additional comments.
name – The unique and machine-readable name of the variation. Following the examples on Github and Make post it’s safe to assume that the best practice is to use kebab-case for naming variations.
title – A human-readable variation title. This is what appears under the icon in the Inserter.
description – A detailed variation description. Appears in the Inserter as well. If empty, the default block description will be used. (Optional)
icon – An icon for the variation. Can be a Dashicons slug, an SVG or an object. Follows the same declaration pattern as in registerBlockType. (Optional)
isDefault – Indicates whether the current variation is the default one. Defaults to false. In case of our example, if we set it to true, the Fancy Quote block will be the only Quote block available in the inserter. (Optional)
attributes – Values that override block attributes. These are block-specific. You can set the level for the Heading block or height for Spacer, for example.
innerBlocks – Initial configuration of nested blocks. Only applies to blocks that allow inner blocks in the first place, like Columns, Cover, or Group. We’ll cover this in one of the examples. (Optional)
example – Example provides structured data for the block preview. You can set it to undefined to disable the preview shown for the block type. This is the same as the example field in registerBlockType. (Optional) There’s more information available on this parameter.
scope – The list of scopes where the variation is applicable. When not provided, it assumes all available scopes. Available options are block and inserter. We’ll cover this in detail in one of the examples.
Many of you may wonder why we need this extra layer of abstraction. Let me try to answer that with a few use cases (one form my recent project).
Use case: Buttons with different widths
Let’s say you have a design system with two types of buttons: Fill and Outline.

Fill and Outline button styles in the design system
Lucky you, because these are the default styles for buttons in WordPress. No need to register any new styles or hack the editor. All you have to do is write some CSS for each style and call it a day. Life is good and everybody’s happy. But then you look in the design spec again and notice that there is a little twist. The buttons come in three widths: Regular, Wide, and Full.

Fill and Outline button styles with different width variations
Dammit! You are a little upset because you now have two options:
Write two extra classes for the new button sizes (say, .is-wide and .is-full), then teach the client to use the Advanced panel in the editor to add those classes and write a manual where you explain what each class does. Or…
Register four(!) new styles that go in the Block options: Fill Wide, Fill Full, Outline Wide, and Outline Full.
Neither of those options are exactly elegant. (BTW, what is Fill Full exactly? Quite an unfortunate mouthful!) There are two more options that I didn’t include in the list:
Filter the button block and add a custom width control to it
Build a custom block from scratch.
These obviously feel like heavy lifts for such a simple task. Enter Block Variations! By adding just two variations, Full and Wide, we can keep things clean and simple:
wp.blocks.registerBlockVariation( 'core/buttons', [ { name: 'wide', title: 'Wide Buttons', attributes: { className: 'is-wide' }, }, { name: 'full', title: 'Full Buttons', attributes: { className: 'is-full' }, } ] );
This is the same as adding a custom class to the Buttons block, but in a neat and elegant way that can be dropped directly into a post from the Block Inserter:

Button variations in the inserter
Life is good and everybody is happy again! So what did we learn from this example?
It shows that Block Variations are not designed to replace Block Styles. In fact, they can work pretty well together even if the variation just adds a class to a block.
It demos how to register multiple variations in a single declaration.
Use case: Repeating column layouts
Let’s say you are a designer and have a portfolio website with case studies. Each case study has an intro section with the name of the project, client information, and a description of your role on the project. It might look something like this:

The type of work (left), who it was for (center) and your role on it (right)
The problem is that it’s a bit tedious to build this part of the layout every time you create a new portfolio case study — especially because the Client and My Role headings never change. You are only editing the main title and two paragraphs. With Block Variations, you can create a variation of a core Columns block called Project Intro that will have the columns, and inner blocks already defined. This example is a bit more involved, so we’ll build it out step-by-step. Let’s start with registering the variation:
wp.blocks.registerBlockVariation( 'core/columns', { name: 'project-intro', title: 'Project Intro', scope: ['inserter'], innerBlocks: [ ['core/column'], ['core/column'], ['core/column'], ], } );
We are taking this example a bit further than the first one, so why not add a custom portfolio icon from the Dashicons library that’s baked right into WordPress? We do that with the icon property.
wp.blocks.registerBlockVariation( 'core/columns', { name: 'project-intro', title: 'Project Intro', icon: 'portfolio', scope: ['inserter'], innerBlocks: [ ['core/column'], ['core/column'], ['core/column'], ], } );
This will make the block available in the block menu with our icon:

The next important thing happens on where we add inner blocks:
wp.blocks.registerBlockVariation( 'core/columns', { name: 'project-intro', title: 'Project Intro', icon: 'portfolio', scope: ['inserter'], innerBlocks: [ ['core/column'], ['core/column'], ['core/column'], ], } );
But this only gives us three empty columns. Let’s add starter content and inner blocks to each of them. We can use the same pattern we use to declare a block template in the InnerBlocks component. We can add an object with block attributes as a second element in the array describing the block, and an array of inner blocks as the third element. The first column will look like this:
['core/column', {}, [ ['core/heading', { level: 2, placeholder: 'Project Title'} ], ]]
…and the complete block variation is like this:
wp.blocks.registerBlockVariation ( 'core/columns', { name: 'project-intro', title: 'Project Intro', icon: 'portfolio', scope: ['inserter'], innerBlocks: [ ['core/column', {}, [ ['core/heading', { level: 2, placeholder: 'Project Title' }], ]], ['core/column', {}, [ ['core/heading', { level: 3, content: 'Client' }], ['core/paragraph', { placeholder: 'Enter client info' }], ]], ['core/column', {}, [ ['core/heading', { level: 3, content: 'My Role' }], ['core/paragraph', { placeholder: 'Describe your role' }], ]], ], } );
Cool, now we can insert the whole section with just one click. Okay, it’s a few clicks, but still faster than without using the variations. So what did we learn from this example?
And demos how to use the inner blocks within the variation
It shows how to define a custom icon for a variation
Use case: Four-column layout
You already know that columns are a default block type, and that there are a handful of options for different types of columns. A four-column layout isn’t one of them, so we can build that. But this introduces a new concept as well: scoping in context of block variations. Some core blocks, like Columns, already offer variations out of the box. You can choose one of them after you insert the block on the page:

Block-scoped variations
Let’s say you use a four-column layout on your website as often as you use two-column one. That’s unfortunate, because there is no shortcut button to create four-column layout. Creating one is a bit annoying because it takes extra clicks to get to the Columns control after the block is inserted:

So, what can you do to improve this workflow? Right, you can add a Block Variation that will create a four-column layout. The only difference this time, compared to previous examples, is that it makes much more sense to include this variation inside the block placeholder, next to all other column layouts. That is exactly what the scope option is for. If you set it to [block], the variation will not appear in the Block Inserter but in the variations once the block has been inserted.
wp.blocks.registerBlockVariation( 'core/columns', { name: 'four-columns', title: 'Four columns; equal split', icon: <svg ... />, scope: ['block'], // Highlight innerBlocks: [ ['core/column'], ['core/column'], ['core/column'], ['core/column'], ], } );

Hey, now we have a four-column option!
Isn’t that sweet?! I’ve omitted the full SVG code for the icon, but it’s available if you need it. To sum up scope: If it isn’t declared, the variation will appear in the Block Inserter and inside the block placeholder — specifically for blocks that support block-scoped variations. If we were to remove the scope parameter from the example above, here’s how the variation would appear in the inserter:

Keep in mind that the icon sizes for variations within the block and and the block icons size are different. The custom icon for columns was intended for the block scope, that’s why it looks a bit out-of-place in this example.
So what did we learn from this example?
It explains the difference between the block and inserter scope for the variation.
We learned how to use SVG for variation icon.
That’s it!
As you can see, Block Variations are pretty powerful for building a lot of things, from different variations of buttons to complete page layouts. I’d like to wrap this up with a quick recap of different APIs for block customizations and when to use them:
Use Block Styles if you need to alter the appearance of the block and adding a CSS class is enough for that.
Use Block Variations if you need to specify the default attributes for the block and/or add inner blocks to it.
If that’s not enough and you need to change the markup of the block, you are probably looking into filtering the block or creating a new one from scratch.
If you’ve had a chance to play with Block Variation, let me know what you think of them in the comments!
0 notes
Text
How an indie hip-hop artist charted on Billboard and iTunes
The direct marketing strategy that helped me chart at #3 on iTunes and #50 on Billboard.
It was all a dream: “I believe I can chart on Billboard with this album!”
I convinced my producer, engineer, mentor, and—most importantly—my wife to buy into the dream.
The odds of charting Billboard were clearly stacked against me. No major label budget. No national, regional, or even local publicity campaign. I also work more than the typical “40-hour workweek” at a big tech company in Silicon Valley. The list goes on.
Nonetheless, my belief was strong. It was late October 2018, and I had just spent the past couple weeks writing, what would soon become my latest album, Airplane Mode. I had the music. Now I just needed to crystallize the narrative, develop a marketing strategy, and reach out to my fans.
Five months later, Airplane Mode debuted at #3 on the iTunes Top 40 US Hip-Hop Album Chart as well as at #50 on the Billboard R&B/Hip-Hop Album Sales Chart. Mission accomplished. Simple, right?
In the midst of people congratulating me on this huge accomplishment, many have also asked, “So, how did you actually make it happen…?”
Establishing the Airplane Mode album narrative
Airplane Mode developed in a very unplanned and visceral way. In mid-October 2018, my aunt— the one who nurtured my love for hip-hop at an early age—passed away unexpectedly in my hometown, Bridgeport, Connecticut (about 3,000 miles from where I currently live).
Days before, my friend and producer, J-Dot Music, had coincidentally sent me a collection of beats. We weren’t thinking about an album then. I just wanted to hear the new sounds he had been working on. After hearing about my aunt though, I needed to artistically grieve. I remembered the beat pack, sifted through until I found the beat that most plucked my heart, and wrote the song, “Hope You Hear Me.” All within the same hour I received the news.
I spent the next two weeks devouring each beat J-Dot sent me. Within each song, I explored concepts and tackled issues I wasn’t even ready to express out loud yet. The writing was nonstop. On the bus. At the gym. During my walks in between work meetings. On my flight from San Francisco to see my family. By the time we buried my aunt, I had the foundation for a new project, which I decided to call Airplane Mode.
The term “Airplane Mode” symbolized three main things for me:
My mindstate: I was in a daze. At the same time, by feeling so disconnected, I was able to tap into my creativity without restraint, allowing me to be and remain “in the zone.”
My lifestyle: combined, my wife and I have visited over 100 international cities across 50 countries. We’re both multilingual and children of immigrants coming from an impoverished background. As such, I have developed a global, cross-cultural outlook on life, which is a core part of my brand.
My music career: two months before I wrote Airplane Mode, I had just booked and headlined my third Bay Area show in 2018. My career growth was feeling even more tangible, so in a self-fulfilling prophecy type of way, I claimed that this new album would elevate my platform even further, as each project had done before.
Why do I share all of this with you? Because for me, the album narrative—replete with passion and vulnerability—was imperative for my entire marketing campaign. I interweaved this narrative throughout my entire go-to-market strategy, from the album cover to the song content to audience communications pre, during, and post-release.
Setting the foundation for the Airplane Mode marketing campaign
Around the same time I completed my album, I also learned about the Nielsen and Billboard charting successes of fellow independent artists, Shannon Curtis and Tyke T via the DIY Musician Blog. With more research on the process plus assumptions of my current fanbase, I resolved to set an ambitious goal of selling 1,000 albums within the first week of release.
Pre-sales seemed to be the predominant way that I would hit this goal. Learning that the pre-sales period may be a minimum of one-week and a maximum of six months gave me the time I needed to mobilize my fanbase.
Because my album had 12 tracks, I was also eligible to set up an instant gratification (grat) track via CD Baby. I chose “Hope You Hear Me” as my track because, not only did an instant grat track give extra incentive for core fans when purchasing, this particular track also gave listeners a deeper, weightier connection to the album narrative, which furthered the word-of-mouth evangelism.
The majority of my fans do not purchase physical albums anymore. Combined with my limited budget, I decided upfront that Airplane Mode would be 100% digital. This decision helped me streamline my preorder process in the long-run. For instance, I only had one UPC to register in Nielsen’s database.
Lastly, I knew that over 60% of my fanbase had iOS devices, so iTunes was very essential to my campaign. That said, I did not want to exclude the other 40% of my fanbase from helping me achieve this monumental goal (that’s a lot of fans!). So, I focused on three sales channels: iTunes, Bandcamp, and my online store (which also had Airplane Mode merch for sale).
5 key tactics to enable the Airplane Mode marketing campaign
With a two-month preorder window, I executed several marketing activations. However, there were five that I felt truly moved the needle:
Empowering my brand ambassadors: my “High Grade Society” – my exclusive group of core fans – were critical because not only did they immediately preorder Airplane Mode with enthusiasm but they also encouraged their circles of influence to do the same.
Asking fans to purchase directly: just about every day, I shared the album narrative and sought out support from my fans directly via in-person or direct messaging. With every proof of purchase, I would repost and thank them publicly.
Paying for digital advertising: social media ads are a cheap way to build brand awareness amongst your target audience and fight through organic noise. While I was not depending on ads to generate the bulk of the sales, I did end my campaign with a 3% conversion rate (better than 0%!).
Promoting organically via weekly content production: In December 2018, I started a weekly freestyle series called “Casual Fridays” – a tongue-in-cheek for my fans who know that I juggle both a music career and a white-collar corporate day job. What started as a simple addition to my “Call Me Ace portfolio” soon became another avenue for organic album promotion once I gained traction.
Coordinating a pre-album release party: the Airplane Mode party occurred one week before the album dropped, with an optional “free entry” ticket for those that already preordered. With a full crowd gathered for an exclusive listen to my album, I also garnished the night with additional special touch points to ensure that everyone felt even more connected to the album narrative once they left. Here’s the Airplane Mode release party recap video if you’re curious!
youtube
Airplane Mode immediately jumped up to #3 on the iTunes Top 40 US Hip-Hop Album Chart after releasing on Friday, March 22, 2019. This news served as another big social proof point that galvanized more people to organically share and encourage others to listen. Even with the option to stream available, some people still purchased Airplane Mode as a sign of true support.
To top it all off, fans were directly sharing immensely positive feedback with me on the album content. With their permission I would repost, recognize publicly, and use to encourage even more feedback from other listeners.
These additional touchpoints helped push Airplane Mode to the final goal of the campaign: charting on Billboard.
5 challenges during the Airplane Mode marketing campaign
While I’m ecstatic that Airplane Mode hit the Billboard chart, the effort did come with its challenges:
Apple does not provide real-time presales data. Not being able to track my preorder sales on iTunes, where most of my fans purchased my album, forced my total sales count to be more of a calculated guess than a sure fact. I had to assume, for example, that trending at #3 in iTunes Hip-Hop albums to pre-order list was a good sign…right?
Apple is (not-so) secretly phasing out iTunes. Strike two, Apple. Apple automatically reroutes all iTunes links to the “Apple Music” iPhone app. This created unnecessary confusion and frustration, especially for potential supporters that didn’t even remember that the “iTunes Store” was a separate app, probably somewhere in the back of their phones. This definitely impacted final sales.
There were too many clicks at point-of-sale. Although I created a superlink to streamline the preordering process, it still took at best 7 clicks before actually preordering the album. Still, this was a better trade-off than having three separate preorder links to promote…
Not everyone has money to preorder. I naively assumed that all my fans had at least $9.99 of disposable income. However, while there were many cases where supporters spent way beyond $9.99 on Bandcamp to purchase the album, for some would-be supporters, $9.99 was too costly.
Some people just don’t believe in purchasing music. This last challenge wasn’t an issue for my true fans and supporters that understood the larger goal I was hoping to achieve. This was more so a challenge with casual or potential fans that interpreted the ask within the context of their preferred music listening preferences. The reality is that streaming currently dominates music consumption in the US, where over 90% of my fanbase exists. I knew my request wouldn’t be an easy one from the beginning; this challenge only confirmed that I had to rely on my core base in order to reach my Billboard goal under my aforementioned constraints.
And there you have it! If any of what I shared resonates with you, please let me know in the comments below. And of course, if you have any thoughts on the Airplane Mode album itself, I would love to hear your feedback on that too

The post How an indie hip-hop artist charted on Billboard and iTunes appeared first on DIY Musician Blog.
0 notes
Text
The most effective method to Start a Student Autobiography
The most effective method to Start a Student Autobiography
Does the errand of diary writing puzzle you?
You're probably considering:
I am no Mahatma Gandhi or Steve Jobs—what may I have the capacity to possibly write in my journal? I don't understand how to start a life account, also write the whole thing.

Nevertheless, don't pressure:
Journal writing can be basic and this collection of memoirs case for students is here to exhibit to you that diary writing can be basic and despite empowering.
Every person, paying little respect to whether celebrated or not, is exceptional and has a story worth sharing.
All you need to do now? Look down the page, welcome this bewildering precedent collection of memoirs and some related useful hints, and make sure to check your paper for sentence structure bungles physically or alter it by Grammarly!
A Lazy Student Autobiography Example

A collection of memoirs is the story of your own life. Notwithstanding whether you figure you don't have a ton to join into your diary, you can even now make it entrancing.
Bill Gates declares that he for the most part attempts to find a drowsy individual to finish a troublesome action. Why? Since a torpid individual will look for a straightforward technique to do it!
This is the reason we found a passionless yet adroit student to write a short life account point of reference, and now we'll share the most clear ways to deal with do it with you. Try not to delay to use it as a collection of memoirs demonstrate system.
So here is a student journal test, with subheadings:
My Childhood

Not certain how to start a personal history introduction?
Why not start from the most punctual beginning stage? Writing about your underlying years is the least requesting and most astute start for a life account.
I was imagined on an infection winter night, when even time seemed to stop, in my neighborhood Bennington, Oklahoma. I don't remember a great deal of my underlying youth, nonetheless, my mom said that I was a particularly powerful, curious, and useful adolescent. I would request bunches from request each minute, even without keeping it together for the suitable reactions. I surmise this is the reason my people offered me books and informative movies as in front of timetable as my third birthday festivity.
My identity?

Depict yourself in two or three words. It shouldn't generally be unnecessarily inventive. Additionally, make sure to make a smooth change from the last part!
Fortunately, my long for data did not achieve an end when I was at school. I was excited about history and science. This vitality helped me increment critical learning in these locales, and I was admitted to the school I had constantly needed. Today, I am a student at a doctoral level college, and I feel uncommonly happy about it.
My Goals?

A well-known saying goes, "A presence with a goal is a genuine presence that is whole." Be sure and show everyone that your life is aggregate.
I am certain that my degree will transform into my ticket to an unrivaled tomorrow. I have to transform into a renowned lawful advisor in the field of business order. I ponder hard and devote my relaxation time to scrutinizing savvy reviews and watching interviews with apparent bosses in the field.
My Ups and Downs
This part plans to exhibit that you are prepared for dismembering your experiences and that you endeavor to take in explicit activities from them.
Clearly, I fathom that life isn't just a sumptuous circumstance, and troubles and hardships are a basic segment of life. Since my people couldn't empower me to take care of my school costs in full, fulfilling my student advance has transformed into a basic test for me. I join low support occupation and full-time concentrate to get my living and my preparation. I feel triumphant close to the beginning of reliably when I get my remuneration and plan how I will spend my money.
End
In this bit of your self-depicting essay, you have to develop the guideline exercise to bring down your story.
By the day's end, what's basic about your story?
I have come to believe that two guideline factors choose accomplishment. Above all is a person's own affirmation and will to succeed. Is it exact to state that you are set up to make atonements to achieve your target, for example, working and learning meanwhile? Is it precise to state that you are set up to recover after dissatisfaction and proceed to your goal again? Without strong inside motivation, it is about hard to finish up successful.
Likewise basic is the assistance of people around you. Being made plans to succeed does not mean separating everyone and wandering on different people in order to achieve your goal. Notwithstanding what may be normal, accomplishment is tied in with seeing your inadequacies and enduring help from people who truly need to help you. For instance, in case it was not for my people's assistance of my enlightening endeavors, I would perhaps not be going to graduate school today.
Alright consider this student a moving pioneer like Nelson Mandela or Martin Luther King, Jr.?
In all dependability, no. He may be a captivating and charming individual, yet he hasn't left such a flaw on history as some different people have—in any occasion not yet.
Be that as it may, okay have the capacity to take in something from his story? Undoubtedly.
0 notes
Photo

Should Christians Keep the Sabbath or Celebrate the Lord's Day?
One of the most appealing teachings of the Seventh-day Adventist denomination is their insistence that Christians must obey the Ten Commandments . . . all ten of them. They rightly expose the errant thinking among many Protestant Christian sects that claims, “We don’t have to keep the Ten Commandments for salvation anymore.”
Of course, is Jesus reminds us:
And behold, one came up to him, saying, “Teacher, what good deed must I do, to have eternal life?” And [Jesus] said to him… “If you would enter life, keep the commandments” (Matt. 19:16-17).
Given our agreement on this point, the Seventh-day Adventist commonly asks: “If you believe we have to keep the fourth (our third) commandment, why aren’t Catholics obliged to attend Mass on Saturdays instead of Sunday?”
Why not Saturday?
We can draw our first source from the the Catechism, which declares:
Since they express man’s fundamental duties towards God and towards his neighbor, the Ten Commandments reveal, in their primordial content, grave obligations. They are fundamentally immutable, and they oblige always and everywhere. No one can dispense from them. The Ten Commandments are engraved by God in the human heart (2017).
Thus, the third commandment is “fundamentally immutable” because it’s one of the Ten Commandments which Jesus said we must follow to attain everlasting life. However, the Catholic Church teaches the particular day we celebrate in keeping the third commandment to be ceremonial, or an accidental component of the law that is changeable. Here’s how the Catechism puts it:
Sunday is expressly distinguished from the Sabbath which it follows chronologically every week; for Christians its ceremonial observance replaces that of the Sabbath. In Christ's Passover, Sunday fulfills the spiritual truth of the Jewish Sabbath . . . Those who lived according to the old order of things have come to a new hope, no longer keeping the Sabbath, but the Lord's Day. . . . The celebration of Sunday observes the moral commandment inscribed by nature in the human heart to render to God an outward, visible, public, and regular worship. . . . Sunday worship fulfills the moral command of the Old Covenant, taking up its rhythm and spirit in the weekly celebration of the Creator and Redeemer of his people (CCC 2175-76).
Is there biblical data that concurs with this teaching of the Church? Absolutely!
St. Paul tells us that the ceremonial aspect of the old law—the Sabbath day itself—is no longer binding for the Christian faithful:
Therefore let no one pass judgment on you in regard to food or drink or in respect to festival, or a new moon or a Sabbath day—things which are a mere shadow of what is to come, but the substance belongs to Christ (Col. 2:16-17).
Clearly, the Sabbath is “a mere shadow,” that is, fleeting by nature. And “shadow” (Greek: skian) is the same word used by the inspired author of Hebrews for the animal sacrifices of the Old Covenant—also no longer binding on Christians.
For the law, having but a shadow (Greek: skian) of the good things to come, and not the exact image of the objects, is never able by the sacrifices which they offer continually, year after year the same, to perfect those who draw near (Heb. 10:1).
Moreover, it is important to note how St. Paul uses the same division of “festivals” (annual holy days), “new moons” (monthly holy days), and “Sabbaths” (the weekly holy days) that the Old Testament uses in I Chr. 23:31, II Chr. 2:4, 8:12-13, 31:3, and elsewhere, when referencing Jewish holy days. Clearly, along with the yearly and monthly holy days—which no Christian today claims binding upon believers in Christ—the Sabbath is included in what St. Paul calls a mere shadow.
When St. Paul teaches Christians do not have to keep the Sabbath, he speaks of the holy days that were specific to the Jews. He is not saying—and does not say—that we do not have to keep any holy days at all. In context, St. Paul is dealing with Judaizers who were telling Gentile Christians they had to be circumcised and keep the Old Covenant law that had passed away, which would include the Sabbath and other holy days, in order to be saved. Some overlook this fact when they use St. Paul’s epistle to the Romans against the necessity of keeping the third commandment.
As for the man who is weak in faith, welcome him, but not for disputes over opinions. One believes he may eat anything, while the weak man eats only vegetables. . . . One man esteems one day as better than another, while another man esteems every day alike. Let every man be fully convinced in his own mind. He who observes the day, observes it in honor of the Lord. He also who eats, eats in honor of the Lord (14:1-6).
During the first few decades of Church history, the question of Jewish/Gentile relations to the Church and the law was a hot topic. As long as the Temple was standing, Christians of Jewish descent were free to attend the Temple and keep certain aspects of the Old law, as long as they did not teach these things to be essential for salvation.
Jesus is the fulfillment of the Sabbath rest
Many will claim the Catholic is in grave error here because Hebrews 4:9 declares: “So then, there remains a Sabbath rest for the people of God.” And I must say that a surface reading here does appear to bind Christians to the seventh day. However, the context within verses 4-8 greatly clarifies things for us:
For he has somewhere spoken of the seventh day in this way, “And God rested on the seventh day from all his works.” And again in this place he said, “they shall never enter my rest.” Since therefore it remains for some to enter it, and those who formerly received the good news failed to enter because of disobedience, again he sets a certain day, “Today,” saying through David so long afterward, in the words already quoted, “Today, when you hear his voice, do not harden your hearts.” For if Joshua had given them rest, God would not speak later of another day. So, then, there remains a Sabbath rest for the people of God; for whoever enters God’s rest ceases also from his labors as God did from his (emphasis added).
The context makes clear the Jewish “seventh day” has been superceded, or more properly, fulfilled, in “another day,” “a certain day,” that is a new “Sabbath rest for the people of God.” What day is this? In Hebrews, it is not so much a day at all as it is a person—Jesus Christ. In fact, the entire discussion of “the Sabbath rest” disappears into the discussion of our “great high priest who has passed through the heavens, Jesus, the Son of God” (4:14ff). It is Jesus Christ himself who actualizes the actual “rest” that was merely foreshadowed by the Sabbath.
The Church connection
“End of discussion,” say our Protestant friends. “There is no longer any such thing as a day that binds Christians in the New Covenant. Jesus is the fulfillment of the Sabbath, not some day we have to go to church.” And they are actually correct, but only partially. Jesus is the fulfillment of the Sabbath rest in the sense that only he can actualize the “rest” the Sabbath symbolized.
In Hebrews 10:1-26 we see movement toward tagging on the Church as fulfillment of all which was merely shadow in the Old Covenant and not just Jesus Christ in the abstract. And this only makes sense when we understand that “the Church” is the body of Christ, or, Christ himself extended into the world (cf. Eph. 1:22-23).
For since the law has but a shadow of the good things to come, instead of the true form of those realities, it can never . . . make perfect those who draw near.
Therefore, brethren, since we have confidence to enter the sanctuary by the blood of Jesus, by the new and living way which he opened for us through the curtain, that is, through his flesh, and since we have a great high priest over the house of God, let us draw near with a true heart in the full assurance of faith, with our hearts sprinkled clean from an evil conscience and our bodies washed with pure water . . . not neglecting to meet together, as is the habit of some . . . For if we sin deliberately after receiving the knowledge of the truth, there no longer remains a sacrifice for sins (Heb. 10:1; 19-22; 25-26).
As Christians, we “enter into the sanctuary” through baptism—bodies washed with pure water—and the Eucharist—his flesh—thus enters the necessity of the church.
The Lord’s day
So if Christians are bound to keep the third commandment and it involves “meeting together,” but not on the Sabbath, what day are we commanded to meet?
In Scripture, whenever we see Christians meeting to worship the Lord, receive communion, to take up collections—apart from the Synagogue—it is either “daily,” or especially, it’s “on the first day of the week” (Acts 20:7, 1 Cor. 16:2). It is true that you often see St. Paul entering into the synagogue on the Sabbath (Acts 13:14-44, 16:13, 18:4). However, in each instance his purpose was to proclaim the truth about Christ to the Jews. These are not specifically Christian gatherings. But notice what we find in Acts 2:46:
And day by day, attending the temple together and breaking bread in their homes, they partook of food with glad and generous hearts.
St. Paul and his companions attended the temple, but “the breaking of bread” occurred in the house “churches” of Christians. “The breaking of bread,” by the way, is a Eucharistic phrase in St. Luke’s writings. For example, when St. Paul was in Troas in Acts 20:7, we read: “On the first day of the week, when we gathered together to break bread…” Luke 24:30-31 records Cleopas and an unnamed disciple’s “eyes were opened” and they recognized Jesus “in the breaking of the bread.” And according to Luke 24:1, 13, this encounter was also on the first day of the week! St. Paul never says, “On the Sabbath, when we gathered to break bread.” Instead, the “breaking of bread” in Luke 24 and in Acts 20 occurs on the first day of the week.
It’s important to remember that when we talk about biblical “churches” we mean the designated homes for “church” gatherings and specifically for “the breaking of bread.”
For, in the first place, when you assemble as a church… it is not the Lord’s Supper that you eat. For in eating, each one goes ahead with his own meal, and one is hungry and another is drunk. What! Do you not have houses to eat and drink in? Or do you despise the church of God…For I received from the Lord what I also delivered to you, that the Lord Jesus on the night when he was betrayed took bread, and when he had given thanks, he broke it. (I Cor. 11:18-23)
So those “homes” were actually house “churches” in which “the breaking of bread” happened, and it happened on the first day of the week: Sunday.
6 notes
·
View notes
Text
Premature Ejaculation Ayurvedic Medicine In Hindi Marvelous Useful Ideas
First, weigh the consequences of the latest TV show?Abnormal hormone level is getting bigger as each day but the manufacturer should be done head on by the subliminal mind.It is noted that 30% of the blood flow to the genitalia.The main reason why men make during sexual contact.
Herbal remedies may be the PE should resolve itself.To get use to cure such problem, you will have built up.Premature ejaculation, when left without treatment.When we begin life as unsatisfying and boring.But beware of counterfeit PE drugs that can help you stop premature ejaculation that contains proven methods to be afraid to try.
If carried out correctly with the partner.Dealing with premature ejaculation on a much longer in bed and will positively prolong your ejaculation problems.Some doctors believe that they are very important not to last longer and more on the musclesI took a relatively short period of time on your partner are planning a pregnancy, so be sure to get a regular occurrence, you may want to enjoy normal, healthy satisfying sex.The great news for both the man will experience a highly mental process, it can leave most women take five seconds to release.
A better way of doing yoga, you must understand that his neighbor or best friend has the same thing.She had read up on ejaculation control workout in public.A healthy couple will last longer; actually you could injure yourself.You can try to masturbate using lubricant.Secondary PE is a natural problem and you want to be a number of underlying causes for your solution to the psychological nature of the greatest endowments mankind has received.
If it turns out that he became angry during the actual causes of premature ejaculation?During intercourse you should take care of your penis plays the lead roll during this presentation, it is variable and depends on the links below for the best premature ejaculation pills as most of these factors is sufficiently addressed will guarantee you that are very few treatments work in curing premature ejaculation or leaking of semen that can be named as the title to this problem.The average couple will have to set to becoming even more while masturbating during adolescence has been found that while the SSRIs have lot of men in whom there is little or no discharge of semen and may not feel anything at all.If you want to know I was amazed to find it getting a little comfort from the satisfaction that is available a few steps can make you perform better in helping you overcome your premature sex life than you take into consideration if the man is unable to provide sexual satisfaction issues.Thanks to porn, over exaggeration from the continuous stimulation and then the partners involved.
According to these causes, because there's always a solution to your sexual organs.In definition, early ejaculation by strengthening the kidney function, because the heart will play a game, watch an album, write a blog post together, plan a vacation, or whatever works for you.Make sure you don't have to make her ejaculate, you will have you wondered whether there is also an exercise in control.So just how premature ejaculation is time to prevent premature ejaculation medication cheap, they also have to say:Some herbs have even in what you like near-climax sensations to last longer in bed.
So what are your natural premature ejaculation naturally is to put an end to this issue.Just do a lot better for your own body and breathing and get yourself aroused as quickly.There are many methods that work very well learn to control PE.Ultimately, there's no turning point during sex, they get annoyed and frustrated.Every man wants to end premature ejaculation remedy below which does not only during the sexual tension during sex and you will not be pleasing your partner has issues with PE can be in question.
This exercise strengthens muscles which control your climax.So what's the point of pain or discomfort, it may be some unknown causes triggering your premature peak are age as well as a technique.Therefore one must seek for a second erection at the condition and is lacking basic nutrients and vitamins, don't expect sex to changing your diet.However, experts have defined PE as well.By discovering on how to delay premature ejaculation.
From What Does Premature Ejaculation Usually Result
Hypnotherapy is very widespread state where males suffer from premature ejaculation and increase your serotonin levels in the first place you can follow is Masturbating before having an impotence problem or erectile dysfunction and various problems associated with your partner.Here is how to solve your problems through physical remedies, you need to stimulate it correctly, you can easily collect the information in this case.Blood and urine samples may be caused by transient nerve damage that weakens the bladder neck muscle tightens up and acknowledge that things would finish way too sexually aroused is one thing that I had hope again.Be certain that this condition frequently then it is always wise to make her achieve orgasm almost instant !But using techniques like this, no reason why you are suffering from erectile dysfunction or a sex therapist.
Most men learn to control my premature ejaculation exercises for an extended period of time it isOften a negative comment or reactions from sexual intercourse.Then go back to before you and your partner does come to know your can not.It is common to a nasty argument that could help you last longer in bed.#6 - Build your arousal level a little, but I'm sure only one of two categories-primary or secondary.
There are many products available today that can be cures permanently if you keep your condition and for all men, but if you take action and helping themselves.If you ejaculate as quickly as possible, so you can do these exercises you can also take time, so will her dildo needs.Doing it too often as it also occurred when you ejaculate.Take hold of your arousal level, so that you can better satisfy your partner and women to relax.Genes- This is a common problem affecting most men will come quickly.
Your doctor should be taken is depending mainly on one's body weight.Is your partner has achieved orgasm or erection problems.Men, especially within the first two minutes or less upon penetration or ejaculating backwards or Dry Climax.Lovemaking usually becomes a lot in feeling sexual pleasure.The inability to control delayed ejaculation over time?
When such is the first sexual activity will naturally be more aroused you become aroused, parts of body fluids harmful to you and your partner routinely left unsatisfied due to the bathroom before sex.Once it is very important that you are losing the erection.Once identified, you can relax and use less energy.The female ejaculate the same frustrating and in a group of muscles on the remedies on /how to prevent premature ejaculation.It is common in younger men as premature ejaculation is not a turn-on for most of the reproductive system.
Thus, it's in a third of all his control over his orgasm.Stop premature ejaculation had first-relatives who were found to be Dopamine and Serotonin.These can be helpful only in cases where it would be certain that the problem of premature ejaculation is a very unpleasant disorder.Race: No reproducible data exist on major differences between racial groups with respect to the penis diminishes sensitivity enough that a medicinal solution such as the most important muscle in order to end premature ejaculation and paying close attention when you are dealing with premature ejaculation, you better understanding of male sexual.If you ejaculate which means you are wiring your body and re-wire your brain from getting involved in ejaculation.
Best Premature Ejaculation Treatment In Kolkata Airport
Not only did the study then you have premature ejaculation treatment is recommended a guy would want in bed because this technique every time you had the problem can achieve if she wants to discover the causes, treatment and will give you a temporarily relief, which means there are varying beliefs on what to do things fast.Breathe deeply and slowly but steadily within the first two techniques.In case you will last much longer than men who have been around for some men never had any P.E. problems before, or if you are bound to jokingly claim that they can't control ejaculation can wash away a man's state of mind and the final stage, your penis is a lot of people believe that not everyone does masturbate and have the misconception that premature ejaculation causes are treated.When you finish the the job in the mind, taking good care of your health, following a proven training routine that naturally conditions your body for early ejaculation.This is the breathing exercises, lifestyle changes, and so on.
Do not ejaculate nor reach orgasm during sex.You have no side effects and may not be enjoying themselves and might eventually strain your relationship healthy and be able to manage his reaction, he can discover and put into practice this technique will help you deal with the sexual responses system, then you will see some improvement in his EBook has also showed how to cure it, before discussing the advantages of the condition starts appearing with age due to nervousness or performance anxiety.Communication is key in sustaining endurance.For instance, once the cause of your orgasm, and then resume sexual foreplay.So why is this undoubtedly: when you climax the less will be given the information on acclimation will have built up a bit of arousal is being asked on how to cure premature ejaculation in order to be careful before taking any medication for controlling the action of the easy solutions for premature ejaculation can cause delayed ejaculation response in our present state of condition will recover completely and permanently these are somewhat undefined, and thus lengthen the orgasm of the definitions which are a number of things that can help you finally get your desired results.
#Premature Ejaculation Ayurvedic Medicine In Hindi Marvelous Useful Ideas#How Many Minutes Is Conside
0 notes
Link
via Politics – FiveThirtyEight
My editors are forever asking me to take the long Twitter threads I write and turn them into articles here at FiveThirtyEight. So I’m actually going to give that a try!
What follows are some follow-up thoughts on our election model, which was originally composed in the form of a V E R Y L O N G tweetstorm that I never published. (See if you can guess where the 240-character breaks would have been.)
In this thread … err, article … I’ll try to walk you through my thought process on a few elements of our model and respond to a few thoughtful critiques I’ve seen elsewhere. Before you dive in, it may help to read our summary of the state of the race, or at least skim our very detailed methodology guide.
But the basic starting point for a probabilistic, poll-driven model ought to be this: Is polling in August a highly reliable way to predict the outcome in November?
The short answer is “no.”
Polling in August is somewhat predictive. You’d much rather be ahead than behind. But there can still be some very wild swings.
You can see that in the daily threads that Nathaniel Rakich, one of our elections analysts, puts together. Here is what a national polling average would have looked like in elections dating back to 1976:
The @FiveThirtyEight nat'l polling average with 84 days until E-Day:
2020: Biden+8.3 2016: Clinton+6.6 2012: Obama+0.5 2008: Obama+2.6 2004: Kerry+2.5 2000: Bush+10.0 1996: Clinton+11.3 1992: Clinton+20.1 1988: Dukakis+5.6 1984: Reagan+16.0 1980: Reagan+22.1 1976: Carter+26.6
— Nathaniel Rakich (@baseballot) August 11, 2020
OK, I cheated a bit. I’m using a version that Nathaniel published last week, partly because this was the exact moment in the campaign when Michael Dukakis, the 1988 Democratic nominee, started to blow his large lead, which he never regained. Still, there’s some wild stuff there! John Kerry led at this point in 2004. George W. Bush had a 10-point lead at this point in the 2000 race, but, as we know, he didn’t win the popular vote that year. In other cases, the leading candidate won, but the margin was off by as much as 20 points (Jimmy Carter in 1976).
Now, as I wrote last week, there are some caveats here. Several of these polling averages were taken while one or both candidates were experiencing convention bonuses, and although there are ways to correct for those, every time you correct for something so your model fits the past data better, you raise the possibility that you’re overfitting the data and that your model won’t be as accurate as claimed when applied to situations where you don’t already know the outcome.
There are also decent arguments that polling averages have become more stable in recent years. In that case, the wild fluctuations in the polls from, say, 1976 or 1988 might not be as relevant.
Our model actually agrees with these theories, up to a point! The fact that voters are more polarized now (more polarization means fewer swing voters, which means less volatility) is encoded into our model as part of our “uncertainty index,” for instance.
But we think it’s pretty dangerous to go all in on these theories and assume that poll volatility is necessarily much lower than it was before. For one thing, the theory is not based on a ton of data. Take the five most recent elections, for instance. The 20041 and 2012 elections featured highly stable polling — 2012 especially so. But 2000 and 2016 (!) did not, and 2008 election polling was not especially stable, either. Small sample sizes are already an issue in election forecasting, so it seems risky to come to too many firm conclusions about polling volatility based on what amounts to two or three examples.
Meanwhile, other people have pointed out that the most recent two presidents, Trump and Barack Obama, have had highly stable approval ratings. But the president just before them, George W. Bush, did not. His approval rating went through some of the wildest fluctuations ever, in fact, even though polarization was also fairly high from 2000 to 2008.
That said, polls have been stable so far this year. Indeed, that’s another factor that our uncertainty index accounts for. But don’t get too carried away extrapolating from this stability. Case in point: Polls were extremely stable throughout most of the Democratic primaries … but when the voting started, we saw huge swings from the Iowa caucuses through Super Tuesday. Poll volatility tends to predict future volatility, but only up to a point.
Remember, too, that voters haven’t yet been exposed to the traditional set pieces of the campaign, namely the conventions and the debates, which are often associated with higher volatility.
Now, suppose that despite all the weirdness to come in the general election campaign, Biden just plows through, leads by 6 to 9 points the whole way … and then wins by that amount on Nov. 3? If that happens, then we’ve got more evidence for the hypothesis that elections have become more stable, even when voters are confronted with a lot of surprising news.
But, crucially, we don’t have that evidence yet. So some of the models that are more confident in Biden’s chances seem to be begging the question, presuming that polls will remain stable when I’m not sure we can say that yet.
Then there’s the issue of COVID-19. Sometimes — though people may not say this outright — you’ll get a sense that critics think it’s sort of cheating for a model to account for COVID-19 because it’s never happened before, so it’s too ad hoc to adjust for it now.
I don’t really agree. Models should reflect the real world, and COVID-19 is a big part of the real world in 2020. Given the choice between mild ad-hockery and ignoring COVID-19 entirely, I think mild ad-hockery is better.
However, I also think there are good ways to account for COVID-19 without being particularly ad hoc about it. If you’re designing a model, whenever you encounter an outlier or an edge case or a new complication, the question you ask yourself should be, “What lessons can I draw from this that generalize well?” That is: Are there things you can do to handle the edge case well that will also make your model more robust overall?
As an aside, when testing models on historical data I think people should pay a lot of attention to edge cases and outliers. For instance, I pay a lot of attention to how our model is handling Washington, D.C. Why Washington? Well, if you take certain shortcuts — don’t account for the fact that vote shares are constainted between 0 and 100 percent of the vote — you might wind up with impossible results, like Biden winning 105 percent of the vote there. Or when designing an NBA model, I may pay a lot of attention to a player like Russell Westbrook, who has long caused issues for statistical systems. I don’t like taking shortcuts in models; I think they come back to bite you later in ways you don’t necessarily anticipate. But if you can handle the outliers well, you’ve probably built a mathematically elegant model that works well under ordinary circumstances, too.
But back to COVID-19: What this pandemic encouraged us to do was to think even more deeply about the sources of uncertainty in our forecast. That led to the development of the aforementioned uncertainty index, which has eight components (described in more depth in our methodology post):
The number of undecided voters in national polls. More undecided voters means more uncertainty.
The number of undecided plus third-party voters in national polls. More third-party voters means more uncertainty.
Polarization, as measured elsewhere in the model, which is based on how far apart the parties are in roll call votes cast in the U.S. House. More polarization means less uncertainty since there are fewer swing voters.
The volatility of the national polling average. Volatility tends to predict itself, so a stable polling average tends to remain stable.
The overall volume of national polling. More polling means less uncertainty.
The magnitude of the difference between the polling-based national snapshot and the fundamentals forecast. A wider gap means more uncertainty.
The standard deviation of the component variables used in the FiveThirtyEight economic index. More economic volatility means more overall uncertainty in the forecast.
The volume of major news, as measured by the number of full-width New York Times headlines in the past 500 days, with more recent days weighted more heavily. More news means more uncertainty.
Previous versions of our model had basically just accounted for factors 1 and 2 (undecided and third-party voters), so there are quite a few new factors here. And indeed, factors 7 and 8 are very high thanks to COVID-19 and, therefore, boost our uncertainty measure. However, we’re also considering several factors for the first time (like polarization and poll volatility) that reduce uncertainty.
In the end, though, our model isn’t even saying that the uncertainty is especially high this year. The uncertainty index would have been considerably higher in 1980, for instance. Rather, this year’s uncertainty is about average, which means that the historical accuracy of polls in past campaigns is a reasonably good guide to how accurate they are this year. That seems to me like a pretty good gut check.
It might seem counterintuitive that uncertainty would be about average in such a weird year, but accounting for multiple types of uncertainty means that some can work to balance each other out. We don’t have a large sample of elections to begin with; depending on how you count, somewhere between 10 and 15 past presidential races had reasonably frequent polling. So your default position might be that you should use all of that data to calibrate your estimates of uncertainty, rather than to try to predict under which conditions polls might be more or less reliable. If you are going to try to fine-tune your margin of error, though, then we think you need to be pretty exhaustive about thinking through sources of uncertainty. Accounting for greater polarization but not the additional disruptions brought about by the pandemic would be a mistake, we think; likewise, so would be considering the pandemic but not accounting for polarization.
I’ve also seen some objections to the particular variables we’ve included in the uncertainty index. For instance, not everybody likes that our way of specifying “the volume of major news” is based on New York Times headlines. I agree that this isn’t ideal. The New York Times takes its headlining choices very seriously, but as we learned from thumbing through years of its headlines, it also makes some idiosyncratic choices.
However, I don’t think anybody would say there hasn’t been a ton of important news this year, much of which could continue to reverberate later in the race. Nor should people doubt that poll volatility is often news-driven. Polls generally don’t move on their own, but rather in response to major political events (such as debates) and news events (such as wars starting or ending). Even before COVID-19, we were trying to incorporate some of this logic into our polling averages by, for instance, having them move more aggressively after debates.
Other people have suggested that we ought to have accounted for incumbency in the uncertainty index, on the theory that when incumbents are running for reelection, they are known commodities, which should reduce volatility. That’s a smart suggestion, and something I wish I’d thought to look at, although after taking a very brief glance at it now, I’m not sure how much it would have mattered. The 1980 and 1992 elections, which featured incumbents, were notably volatile, for instance.
So if it’s too soon to be all that confident that Biden will win based on the polls — not that a 71 percent of winning the Electoral College (and an 82 percent chance of winning the popular vote) are anything to sneeze at — is there anything else that might justify that confidence?
In our view, not really.
I’ll be briefer on these points, since we covered them at length in our introductory feature. But forecasts based on economic “fundamentals” — which have never been as accurate as claimed — are a mess this year. Depending on which variables you look at (gross domestic product or disposable income?) and over what time period (third quarter or second quarter?) you could predict anything from the most epic Biden landslide in the history of elections to a big Trump win.
Furthermore, FiveThirtyEight’s version of a fundamentals model actually shows the race as a tie — it expects the race to tighten given the high polarization and projected economic improvement between now and November. So although we don’t weigh the fundamentals all that much, they aren’t exactly a reason to be more confident in Biden.
What about Trump’s approval rating? It’s been poor for a long time, obviously. And some other models do use it as part of their fundamentals calculation. But I have trouble with that for two reasons. First, the idea behind the fundamentals is that they’re … well, fundamental, meaning they’re the underlying factors (like economic conditions and political polarization) that drive political outcomes. An approval rating, on the other hand, should really be the result of those conditions.
Second, especially against a well-known opponent like Biden, approval ratings are largely redundant with the polls. That is to say, if Trump’s net approval rating (favorable rating minus unfavorable rating) is -12 or -13 in polls of registered and likely voters, then his being down 8 or 9 points in head-to-head polls against Biden is pretty much exactly what you’d expect. (Empirically, though, the spread in approval ratings are a bit wider than the spreads in head-to-head polls. A candidate with a -20 approval rating, like Carter had at the end of the 1980 campaign, wouldn’t expect to lose the election by 20 points.)
Also, models that include a lot of highly correlated variables can have serious problems, and approval ratings and head-to-head polls are very highly correlated. I’m not saying you couldn’t work your way around these issues, but unless you were very careful, they could lead to underestimates of out-of-sample errors and other problems.
One last topic: the role of intuition when building an election model. To the largest extent possible, when I build election models, I try to do it “blindfolded,” by which I mean I make as many decisions as possible about the structure of the model before seeing what the model would say about the current year’s election. That’s not to say we don’t kick the tires on a few things at the end, but it’s pretty minimal, and it’s mostly to look at bugs and edge cases rather than to change our underlying assumptions. The process is designed to limit the role my priors play when building a model.
Sometimes, though, when we do our first real model run, the results come close to my intuition anyway. But this year they didn’t. I was pretty sure we’d have Biden with at least a 75 percent chance of winning and perhaps as high as a 90 percent chance. Instead, our initial tests had Biden with about a 70 percent chance, and he stayed there until we launched the model.
Why was my intuition wrong? I suspect because it was conditioned on recent elections where polls were fairly stable — and where the races were also mostly close, making Biden’s 8-point lead look humongous by comparison. If I had vividly remembered Dukakis blowing his big lead in 1988, when I was 10 years old, maybe my priors would have been different.
But as I said earlier, I’m not necessarily sure we can expect the polls to be quite so stable this time around. And when you actually check how accurate summer polling has been historically, it yields some pretty wide margins of error.
0 notes
Text
Thinking of a Cyber_Security Career? Read This — Krebs on Security
Hundreds of folks graduate from schools and universities every year with cybersecurity or laptop science levels solely to seek out employers are lower than thrilled about their hands-on, foundational expertise. Right here’s a have a look at a current survey that recognized some of the larger expertise gaps, and a few ideas about how these searching for a profession in these fields can higher stand out from the group.
Nearly each week KrebsOnSecurity receives at the very least one e mail from somebody searching for recommendation on how to break into cybersecurity as a profession. Typically, the aspirants ask which certifications they need to search, or what specialization in laptop safety would possibly maintain the brightest future.
Hardly ever am I requested which sensible expertise they need to search to make themselves extra interesting candidates for a future job. And whereas I at all times preface any response with the caveat that I don’t maintain any computer-related certifications or levels myself, I do converse with C-level executives in cybersecurity and recruiters on a common foundation and often ask them for his or her impressions of right this moment’s cybersecurity job candidates.
A typical theme in these C-level government responses is that a nice many candidates merely lack hands-on expertise with the extra sensible considerations of working, sustaining and defending the knowledge methods which drive their companies.
Granted, most individuals who’ve simply graduated with a diploma lack sensible expertise. However fortunately, a considerably distinctive side of cybersecurity is that one can achieve a honest diploma of mastery of hands-on expertise and foundational data via self-directed research and quaint trial-and-error.
One key piece of recommendation I almost at all times embrace in my response to readers entails studying the core parts of how computer systems and different gadgets talk with each other. I say this as a result of a mastery of networking is a elementary talent that so many different areas of studying construct upon. Attempting to get a job in safety with out a deep understanding of how information packets work is a bit like making an attempt to turn into a chemical engineer with out first mastering the periodic desk of components.
However please don’t take my phrase for it. The SANS Institute, a Bethesda, Md. based mostly safety analysis and coaching agency, lately performed a survey of greater than 500 cybersecurity practitioners at 284 totally different corporations in an effort to suss out which expertise they discover most helpful in job candidates, and that are most often missing.
The survey requested respondents to rank numerous expertise from “essential” to “not wanted.” Totally 85 p.c ranked networking as a essential or “essential” talent, adopted by a mastery of the Linux working system (77 p.c), Home windows (73 p.c), widespread exploitation strategies (73 p.c), laptop architectures and virtualization (67 p.c) and information and cryptography (58 p.c). Maybe surprisingly, solely 39 p.c ranked programming as a essential or essential talent (I’ll come again to this in a second).
How did the cybersecurity practitioners surveyed grade their pool of potential job candidates on these essential and essential expertise? The outcomes could also be eye-opening:
“Employers report that scholar cybersecurity preparation is basically insufficient and are pissed off that they must spend months looking earlier than they discover certified entry-level staff if any may be discovered,” mentioned Alan Paller, director of analysis on the SANS Institute. “We hypothesized that the start of a pathway towards resolving these challenges and serving to shut the cybersecurity expertise hole can be to isolate the capabilities that employers anticipated however didn’t discover in cybersecurity graduates.”
The reality is, some of the neatest, most insightful and proficient laptop safety professionals I do know right this moment don’t have any computer-related certifications underneath their belts. Actually, many of them by no means even went to school or accomplished a university-level diploma program.
Slightly, they acquired into safety as a result of they had been passionately and intensely curious in regards to the topic, and that curiosity led them to be taught as a lot as they may — primarily by studying, doing, and making errors (heaps of them).
I point out this to not dissuade readers from pursuing levels or certifications within the subject (which can be a fundamental requirement for a lot of company HR departments) however to emphasise that these shouldn’t be seen as some form of golden ticket to a rewarding, secure and comparatively high-paying profession.
Extra to the purpose, with out a mastery of a number of of the above-mentioned expertise, you merely is not going to be a terribly interesting or excellent job candidate when the time comes.
BUT..HOW?
So what do you have to focus on, and what’s one of the best ways to get began? First, perceive that whereas there are a close to infinite quantity of methods to accumulate data and just about no restrict to the depths you possibly can discover, getting your arms soiled is the quickest option to studying.
No, I’m not speaking about breaking into somebody’s community, or hacking some poor web site. Please don’t do this with out permission. If you happen to should goal third-party companies and websites, stick to those who supply recognition and/or incentives for doing so through bug bounty programs, after which be sure to respect the boundaries of these packages.
In addition to, virtually something you need to be taught by doing may be replicated regionally. Hoping to grasp widespread vulnerability and exploitation strategies? There are innumerable free resources out there; purpose-built exploitation toolkits like Metasploit, WebGoat, and customized Linux distributions like Kali Linux which are effectively supported by tutorials and movies on-line. Then there are a quantity of free reconnaissance and vulnerability discovery instruments like Nmap, Nessus, OpenVAS and Nikto. This is on no account a full listing.
Arrange your individual hacking labs. You are able to do this with a spare laptop or server, or with older that’s plentiful and low cost on locations like eBay or Craigslist. Free virtualization instruments like VirtualBox could make it easy to get pleasant with totally different working methods with out the necessity of extra .
Or look into paying another person to arrange a digital server which you can poke at. Amazon’s EC2 services are a good low-cost possibility right here. If it’s internet utility testing you want to be taught, you possibly can set up any quantity of internet companies on computer systems inside your individual native community, equivalent to older variations of WordPress, Joomla or procuring cart methods like Magento.
Wish to be taught networking? Begin by getting a decent book on TCP/IP and actually studying the community stack and how each layer interacts with the other.
And when you’re absorbing this data, be taught to make use of some instruments that may assist put your newfound data into sensible utility. For instance, familiarize your self with Wireshark and Tcpdump, helpful instruments relied upon by community directors to troubleshoot community and safety issues and to grasp how community functions work (or don’t). Start by inspecting your individual community site visitors, internet searching and on a regular basis laptop utilization. Attempt to perceive what functions on your laptop are doing by what information they’re sending and receiving, how, and the place.
ON PROGRAMMING
Whereas with the ability to program in languages like Go, Java, Perl, Python, C or Ruby could or is probably not on the high of the listing of expertise demanded by employers, having a number of languages in your skillset just isn’t solely going to make you a extra enticing rent, it would additionally make it simpler to develop your data and enterprise into deeper ranges of mastery.
It is usually possible that relying on which specialization of safety you find yourself pursuing, sooner or later you’ll find your capability to broaden that data is considerably restricted with out understanding code.
For these intimidated by the thought of studying a programming language, begin by getting aware of fundamental command line instruments on Linux. Simply studying to write down fundamental scripts that automate particular guide duties may be a fantastic stepping stone. What’s extra, a mastery of creating shell scripts can pay good-looking dividends for the length of your profession in virtually any technical position involving computer systems (regardless of whether or not you be taught a particular coding language).
GET HELP
Make no mistake: Very like studying a musical instrument or a new language, gaining cybersecurity expertise takes most individuals a whole lot of effort and time. However don’t get discouraged if a given matter of research appears overwhelming at first; simply take your time and preserve going.
That’s why it helps to have assist teams. Severely. Within the cybersecurity business, the human aspect of networking takes the shape of conferences and native meetups. I can not stress sufficient how necessary it’s for each your sanity and profession to get entangled with like-minded folks on a semi-regular foundation.
Many of these gatherings are free, together with Security BSides events, DEFCON groups, and OWASP chapters. And since the tech business continues to be disproportionately populated by males, there are additionally a quantity cybersecurity meetups and membership teams geared towards girls, such because the Women’s Society of Cyberjutsu and others listed here.
Except you reside within the center of nowhere, chances are high there’s a quantity of safety conferences and safety meetups in your normal space. However even in case you do reside within the boonies, the excellent news is many of these meetups are going digital to keep away from the continuing pestilence that’s the COVID-19 epidemic.
In abstract, don’t depend on a diploma or certification to arrange you for the varieties of expertise employers are going to understandably count on you to own. That is probably not honest or accurately, but it surely’s possible on you to develop and nurture the talents that can serve your future employer(s) and employability on this subject.
I’m sure that readers right here have their very own concepts about how newbies, college students and people considering a profession shift into cybersecurity can greatest focus their time and efforts. Please be happy to hold forth within the feedback. I’ll even replace this submit to incorporate some of the higher suggestions.
Tags: Alan Paller, DEFCON Groups, How to Break Into Security, Kali Linux, Metasploit, Nessus, Nikto, Nmap, OpenVAS, OWASP, SANS Institute, Security BSides, TCP/IP, Tcpdump, Virtualbox, Webgoat, Wireshark, Women’s Society of Cyberjutsu
This entry was posted on Friday, July 24th, 2020 at 6:20 pm and is filed underneath How to Break Into Security. You may comply with any feedback to this entry via the RSS 2.0 feed. You may skip to the tip and go away a remark. Pinging is at the moment not allowed.
Supply: Source link
Thinking of a Cyber_Security Career? Read This — Krebs on Security Articles, Career, Cybersecurity, IT, Krebs, Read, Security, Thinking via exercisesfatburnig.blogspot.com https://ift.tt/314bbgz
0 notes