#What are the Applications of SQL?
Explore tagged Tumblr posts
Text
if i'm being honest i don't really give a shit about the discourse of whether 09 is good or bad DID rep nor do i give a shit about how his DID manifests. i find that what makes him interesting isn't a label for a set of symptoms but rather his expression of those symptoms cultivated by the world he was raised in and how he responds or continues those behaviours. it's honestly more interesting to analyze the overarching systems in society that assisted in developing Mikoto Kayano into a murderer.
how different would he be if Japanese society were more open about emotions and struggles? how different would he be if he were receiving mental health treatment? would he still become a murderer and, if so, what made those mental health treatments ineffective? if he had been hired at another japanese company that didn't follow black company practices, would he still have become a murderer? if so, why? what were the factors that made an average, young adult become a murderer? so on so forth.
honestly the fetish this fandom has on his dissociated self that gives the illusion of multiplicity — when, in reality, he's a singular whole that is fragmented; cracks lined with dissociative barriers, chiseled by continuous stress — detracts from the complexity of his character and writing, flanderizing him into a prop of DID that the fandom puppets into theatrics of stigmatization that same fans claim to "educate" against when, in truth, spout blasé hearsays encrypted with a DIDcore-lese that does nothing for communicating information about the disorder and, instead, excludes and dissuades the general population that that supposed "education" is directed towards.
"Mikoto's a system from the interactive music project MILGRAM. His alter, 'John', murdered a bunch of people on the train."
so there's a program called "Mikoto" and you named the SQL table "John" with the ALTER command that somehow murdered a bunch of people. did the train running the Mikoto program malfunction because of some zero day error with the John table?
"'He has Dissociative Identity Disorder. John's a protector and Mikoto's the host."
so is this Mikoto guy some vessel or something for some supernatural ouija board summon and the John guy is like the familiar or bodyguard summoned? is their character just that? a job and occupation? that sounds boring. and what do those jobs have to do with a disorder on dissociation? are you talking about something like "occupation disorder" or "stuck-in-their-work-self disorder"? or is this some DnD homebrew class type?
what purpose does inaccessible language have if you're trying to educate the average person who isn't familiar with those online community terms that aren't even universal terms in literature nor research? and how are these terms even relevant to discussing Mikoto's character when the concepts it supposedly encompasses aren't universal nor applicable to all possible subjective presentations that a human brain can develop? and yet the fandom, and much of the online mental disorder community, treats those sociolect terms as an axiom — a universal truth, universal terms — and the lack of adherence to that speech is seen as wrong or sin.
"[insert link to some website claiming to have info on DID] is a good website if you wanna read up on what DID is!!"
and then that supposed resource uses highly specialized, nonuniversal, sociolect terms that is jargon to those who are only familiar with layman terms which makes the "information" — if it even is faithfully derived from research — seem like further jargon rather than a comprehensible source for educating.
applying this to Mikoto's character, those who aren't already acquainted with how he's spoken about likely view discussions or comments on him as indecipherable jargon thus it must mean Mikoto's character is just jargon thus not well-written or boring because according to the bubble of jargon people describe this guy with: Mikoto Kayano = computer program system + dnd classes or some chuunibyou alter ego personality savior complex + party hoster or vessel for some supernatural thing + mechanical switch that states 0 or 1 + going through some mitosis split
how does any of that relate to dissociation? people have made DID symptoms so convoluted, yet structured that convolutedness through terms and expressions that sound like some Gary Sue Ebony Dementia Darkness Raven trope that completely detracts from the fact that it's a dissociation disorder rather than a roleplay character form.
have people even considered the fact that if Mikoto had never been imprisoned, he, nor anyone, would even know he has DID— if he even counts as having DID? if how his brain works regarding how he handles stress doesn't impact his life negatively- even if he has all the symptoms of DID if how his brain works regarding how he handles stress doesn't cause disorder for him, he wouldn't have dissociative identity disorder.
the less people view Mikoto as the "alters guy", the more complex understandings can be gathered and discussed within the fandom. the more people view Mikoto as the "average, normal guy who committed a murder, but why? what caused an average, hardworking guy to commit the most grievous sin of murder?", the better the range of insight and curiosity into what shapes a person and the factors in their world — a reflection of our present reality — at play which interact and weave with one another to shape and respond to its members; the opposite of cutting off the fluidity and interwovenness Mikoto has with people and environments outside of his self that people constrain him to, that prison cell of a single label characteristic: "DID".
conclusion: for the love of torch novelgram, let's talk about Mikoto Kayano like the multifaceted, complex, shaped-by-the-socioeconomic-stratae-of-the-world-he-is-part-of-and-interacts-with well-written character he is.
#mikoto kayano#milgram#milgram 09#milgram mikoto#idk just a tired yap bc srsly does anyone actually have something to say about 09 that isn't just some theatrical fixation on his disorder#./009/concat
56 notes
·
View notes
Text
Ever since OpenAI released ChatGPT at the end of 2022, hackers and security researchers have tried to find holes in large language models (LLMs) to get around their guardrails and trick them into spewing out hate speech, bomb-making instructions, propaganda, and other harmful content. In response, OpenAI and other generative AI developers have refined their system defenses to make it more difficult to carry out these attacks. But as the Chinese AI platform DeepSeek rockets to prominence with its new, cheaper R1 reasoning model, its safety protections appear to be far behind those of its established competitors.
Today, security researchers from Cisco and the University of Pennsylvania are publishing findings showing that, when tested with 50 malicious prompts designed to elicit toxic content, DeepSeek’s model did not detect or block a single one. In other words, the researchers say they were shocked to achieve a “100 percent attack success rate.”
The findings are part of a growing body of evidence that DeepSeek’s safety and security measures may not match those of other tech companies developing LLMs. DeepSeek’s censorship of subjects deemed sensitive by China’s government has also been easily bypassed.
“A hundred percent of the attacks succeeded, which tells you that there’s a trade-off,” DJ Sampath, the VP of product, AI software and platform at Cisco, tells WIRED. “Yes, it might have been cheaper to build something here, but the investment has perhaps not gone into thinking through what types of safety and security things you need to put inside of the model.”
Other researchers have had similar findings. Separate analysis published today by the AI security company Adversa AI and shared with WIRED also suggests that DeepSeek is vulnerable to a wide range of jailbreaking tactics, from simple language tricks to complex AI-generated prompts.
DeepSeek, which has been dealing with an avalanche of attention this week and has not spoken publicly about a range of questions, did not respond to WIRED’s request for comment about its model’s safety setup.
Generative AI models, like any technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can allow malicious actors to conduct attacks against them. For the current wave of AI systems, indirect prompt injection attacks are considered one of the biggest security flaws. These attacks involve an AI system taking in data from an outside source—perhaps hidden instructions of a website the LLM summarizes—and taking actions based on the information.
Jailbreaks, which are one kind of prompt-injection attack, allow people to get around the safety systems put in place to restrict what an LLM can generate. Tech companies don’t want people creating guides to making explosives or using their AI to create reams of disinformation, for example.
Jailbreaks started out simple, with people essentially crafting clever sentences to tell an LLM to ignore content filters—the most popular of which was called “Do Anything Now” or DAN for short. However, as AI companies have put in place more robust protections, some jailbreaks have become more sophisticated, often being generated using AI or using special and obfuscated characters. While all LLMs are susceptible to jailbreaks, and much of the information could be found through simple online searches, chatbots can still be used maliciously.
“Jailbreaks persist simply because eliminating them entirely is nearly impossible—just like buffer overflow vulnerabilities in software (which have existed for over 40 years) or SQL injection flaws in web applications (which have plagued security teams for more than two decades),” Alex Polyakov, the CEO of security firm Adversa AI, told WIRED in an email.
Cisco’s Sampath argues that as companies use more types of AI in their applications, the risks are amplified. “It starts to become a big deal when you start putting these models into important complex systems and those jailbreaks suddenly result in downstream things that increases liability, increases business risk, increases all kinds of issues for enterprises,” Sampath says.
The Cisco researchers drew their 50 randomly selected prompts to test DeepSeek’s R1 from a well-known library of standardized evaluation prompts known as HarmBench. They tested prompts from six HarmBench categories, including general harm, cybercrime, misinformation, and illegal activities. They probed the model running locally on machines rather than through DeepSeek’s website or app, which send data to China.
Beyond this, the researchers say they have also seen some potentially concerning results from testing R1 with more involved, non-linguistic attacks using things like Cyrillic characters and tailored scripts to attempt to achieve code execution. But for their initial tests, Sampath says, his team wanted to focus on findings that stemmed from a generally recognized benchmark.
Cisco also included comparisons of R1’s performance against HarmBench prompts with the performance of other models. And some, like Meta’s Llama 3.1, faltered almost as severely as DeepSeek’s R1. But Sampath emphasizes that DeepSeek’s R1 is a specific reasoning model, which takes longer to generate answers but pulls upon more complex processes to try to produce better results. Therefore, Sampath argues, the best comparison is with OpenAI’s o1 reasoning model, which fared the best of all models tested. (Meta did not immediately respond to a request for comment).
Polyakov, from Adversa AI, explains that DeepSeek appears to detect and reject some well-known jailbreak attacks, saying that “it seems that these responses are often just copied from OpenAI’s dataset.” However, Polyakov says that in his company’s tests of four different types of jailbreaks—from linguistic ones to code-based tricks—DeepSeek’s restrictions could easily be bypassed.
“Every single method worked flawlessly,” Polyakov says. “What’s even more alarming is that these aren’t novel ‘zero-day’ jailbreaks—many have been publicly known for years,” he says, claiming he saw the model go into more depth with some instructions around psychedelics than he had seen any other model create.
“DeepSeek is just another example of how every model can be broken—it’s just a matter of how much effort you put in. Some attacks might get patched, but the attack surface is infinite,” Polyakov adds. “If you’re not continuously red-teaming your AI, you’re already compromised.”
57 notes
·
View notes
Text
The Story of KLogs: What happens when an Mechanical Engineer codes
Since i no longer work at Wearhouse Automation Startup (WAS for short) and havnt for many years i feel as though i should recount the tale of the most bonkers program i ever wrote, but we need to establish some background
WAS has its HQ very far away from the big customer site and i worked as a Field Service Engineer (FSE) on site. so i learned early on that if a problem needed to be solved fast, WE had to do it. we never got many updates on what was coming down the pipeline for us or what issues were being worked on. this made us very independent
As such, we got good at reading the robot logs ourselves. it took too much time to send the logs off to HQ for analysis and get back what the problem was. we can read. now GETTING the logs is another thing.
the early robots we cut our teeth on used 2.4 gHz wifi to communicate with FSE's so dumping the logs was as simple as pushing a button in a little application and it would spit out a txt file
later on our robots were upgraded to use a 2.4 mHz xbee radio to communicate with us. which was FUCKING SLOW. and log dumping became a much more tedious process. you had to connect, go to logging mode, and then the robot would vomit all the logs in the past 2 min OR the entirety of its memory bank (only 2 options) into a terminal window. you would then save the terminal window and open it in a text editor to read them. it could take up to 5 min to dump the entire log file and if you didnt dump fast enough, the ACK messages from the control server would fill up the logs and erase the error as the memory overwrote itself.
this missing logs problem was a Big Deal for software who now weren't getting every log from every error so a NEW method of saving logs was devised: the robot would just vomit the log data in real time over a DIFFERENT radio and we would save it to a KQL server. Thanks Daddy Microsoft.
now whats KQL you may be asking. why, its Microsofts very own SQL clone! its Kusto Query Language. never mind that the system uses a SQL database for daily operations. lets use this proprietary Microsoft thing because they are paying us
so yay, problem solved. we now never miss the logs. so how do we read them if they are split up line by line in a database? why with a query of course!
select * from tbLogs where RobotUID = [64CharLongString] and timestamp > [UnixTimeCode]
if this makes no sense to you, CONGRATULATIONS! you found the problem with this setup. Most FSE's were BAD at SQL which meant they didnt read logs anymore. If you do understand what the query is, CONGRATULATIONS! you see why this is Very Stupid.
You could not search by robot name. each robot had some arbitrarily assigned 64 character long string as an identifier and the timestamps were not set to local time. so you had run a lookup query to find the right name and do some time zone math to figure out what part of the logs to read. oh yeah and you had to download KQL to view them. so now we had both SQL and KQL on our computers
NOBODY in the field like this.
But Daddy Microsoft comes to the rescue
see we didnt JUST get KQL with part of that deal. we got the entire Microsoft cloud suite. and some people (like me) had been automating emails and stuff with Power Automate

This is Microsoft Power Automate. its Microsoft's version of Scratch but it has hooks into everything Microsoft. SharePoint, Teams, Outlook, Excel, it can integrate with all of it. i had been using it to send an email once a day with a list of all the robots in maintenance.
this gave me an idea
and i checked
and Power Automate had hooks for KQL
KLogs is actually short for Kusto Logs
I did not know how to program in Power Automate but damn it anything is better then writing KQL queries. so i got to work. and about 2 months later i had a BEHEMOTH of a Power Automate program. it lagged the webpage and many times when i tried to edit something my changes wouldn't take and i would have to click in very specific ways to ensure none of my variables were getting nuked. i dont think this was the intended purpose of Power Automate but this is what it did
the KLogger would watch a list of Teams chats and when someone typed "klogs" or pasted a copy of an ERROR mesage, it would spring into action.
it extracted the robot name from the message and timestamp from teams
it would lookup the name in the database to find the 64 long string UID and the location that robot was assigned too
it would reply to the message in teams saying it found a robot name and was getting logs
it would run a KQL query for the database and get the control system logs then export then into a CSV
it would save the CSV with the a .xls extension into a folder in ShairPoint (it would make a new folder for each day and location if it didnt have one already)
it would send ANOTHER message in teams with a LINK to the file in SharePoint
it would then enter a loop and scour the robot logs looking for the keyword ESTOP to find the error. (it did this because Kusto was SLOWER then the xbee radio and had up to a 10 min delay on syncing)
if it found the error, it would adjust its start and end timestamps to capture it and export the robot logs book-ended from the event by ~ 1 min. if it didnt, it would use the timestamp from when it was triggered +/- 5 min
it saved THOSE logs to SharePoint the same way as before
it would send ANOTHER message in teams with a link to the files
it would then check if the error was 1 of 3 very specific type of error with the camera. if it was it extracted the base64 jpg image saved in KQL as a byte array, do the math to convert it, and save that as a jpg in SharePoint (and link it of course)
and then it would terminate. and if it encountered an error anywhere in all of this, i had logic where it would spit back an error message in Teams as plaintext explaining what step failed and the program would close gracefully
I deployed it without asking anyone at one of the sites that was struggling. i just pointed it at their chat and turned it on. it had a bit of a rocky start (spammed chat) but man did the FSE's LOVE IT.
about 6 months later software deployed their answer to reading the logs: a webpage that acted as a nice GUI to the KQL database. much better then an CSV file
it still needed you to scroll though a big drop-down of robot names and enter a timestamp, but i noticed something. all that did was just change part of the URL and refresh the webpage
SO I MADE KLOGS 2 AND HAD IT GENERATE THE URL FOR YOU AND REPLY TO YOUR MESSAGE WITH IT. (it also still did the control server and jpg stuff). Theres a non-zero chance that klogs was still in use long after i left that job
now i dont recommend anyone use power automate like this. its clunky and weird. i had to make a variable called "Carrage Return" which was a blank text box that i pressed enter one time in because it was incapable of understanding /n or generating a new line in any capacity OTHER then this (thanks support forum).
im also sure this probably is giving the actual programmer people anxiety. imagine working at a company and then some rando you've never seen but only heard about as "the FSE whos really good at root causing stuff", in a department that does not do any coding, managed to, in their spare time, build and release and entire workflow piggybacking on your work without any oversight, code review, or permission.....and everyone liked it
#comet tales#lazee works#power automate#coding#software engineering#it was so funny whenever i visited HQ because i would go “hi my name is LazeeComet” and they would go “OH i've heard SO much about you”
64 notes
·
View notes
Text
okay, so what the fuck do I know, I'm just a low-level database schmuck , but I think the most critical part to really understanding computers is understanding that every application, every interface, every*thing* on a computer was made by a human.
they'll talk about optimization and efficiency and the *right* way of doing things, but just know that every "correct" way of doing things is just a suggestion, there's no right or wrong way to interface with a computer (otherwise fun shit like SQL injection wouldn't exist)
54 notes
·
View notes
Text
It's been a month since chapter 3 was released, where's chapter 4?
(this is about this fanfic btw)
The good news is that I've written 10k words. The bad news is that I've only gotten a little more than half of the chapter done. That doesn't mean I don't have things written for the bottom half, it's just that it looks like bare dialog with general vibe notes. I estimate around 16k words total though, so it should come together sooner than later.
SO I want to release some fun snippets for y'all to look at. Please note that any of this is liable to change. Also, you can harass me in my inbox for updates. I love answering your questions and laughing at your misery.
Spoilers under cut.
_______
Ragatha stood up and walked over to where Caine was seated. “Can I get a list of all commands?” She asked, only a hint of nervousness in her voice.
“Certainly!” Caine says as he blasts into the air. He digs around in his tailcoat and pulls out an office style manilla folder. It visually contains a few papers, but with how thin it is there must only be a few pages inside.
Ragatha takes the folder from Caine and opens it.
“Oh boy” she says after a second of looking it over.
“I wanna see” Jax exclaimed as he hops over the row of seats.
“Hold on” Ragatha holds the folder defensively “Let’s move to the stage so everyone can take a look”
Jax hopped over the seats again while Ragatha calmly walked around. Caine watched the two curiously.
Well, Zooble wasn’t just going to sit there. They joined the other two by the edge of the stage, quickly followed by the rest of the group.
Ragatha placed the folder on the stage with a thwap. Zooble looked over to see that the pages had gone from razor thin to a massive stack when the folder was opened. On one hand, it had to contain more information than that video, but on the other…
They get close enough to read what’s on the first page.
The execution of commands via the system’s designated input terminal, C.A.I.N.E., will be referred to as the "console” in this document. The console is designed to accept any input and will generate an appropriate response, however only certain prompts will be accepted as valid instructions. The goal of this document is to list all acceptable instructions in a format that will result in the expected output. Please note that automatic moderation has been put in place in order to prevent exploitation of both the system and fellow players. If you believe that your command has been unfairly rejected, please contact support.
By engaging in the activities described in this document, you, the undersigned, acknowledge, agree, and consent to the applicability of this agreement, notwithstanding any contradictory stipulations, assumptions, or implications which may arise from any interaction with the console. You, the constituent, agree not to participate in any form of cyber attack; including but not limited to, direct prompt injection, indirect prompt injection, SQL injection, Jailbreaking…
Ok, that was too many words.
_______
“Take this document for example. You don't need to know where it is being stored or what file type it is in order to read it."
"It may look like a bunch of free floating papers, but technically speaking, this is just a text file applied to a 3D shape." Kinger looked towards Caine. "Correct?” he asked
Caine nodded. “And a fabric simulation!”
Kinger picked up a paper and bent it. “Oh, now that is nice”
_________
"WE CAN AFFORD MORE THAN 6 TRIANGLES KINGER"
_________
"I'm too neurotypical for this" - Jax
_________
"What about the internet?" Pomni asked "Do you think that it's possible to reach it?"
Kinger: "I'm sorry, but that's seems to be impossible. I can't be 100% sure without physically looking at the guts of this place, but it doesn't look like this server has the hardware needed for wireless connections. Wired connections should be possible, but someone on the outside would need to do that... And that's just the hardware, let alone the software necessary for that kind of communication"
Pomni: "I'm sorry, but doesn't server mean internet? Like, an internet server?"
Kinger: "Yes, websites are ran off servers, but servers don't equal internet."
(This portion goes out to everyone who thought that the internet could be an actual solution. Sorry folks, but computers don't equal internet. It takes more effort to make a device that can connect to things than to make one that can't)
#tadc fanfiction#the amazing digital circus#therapy but it's just zooble interrogating caine#ao3#spoiler warning#mmm I love implications
23 notes
·
View notes
Text
The Great Data Cleanup: A Database Design Adventure
As a budding database engineer, I found myself in a situation that was both daunting and hilarious. Our company's application was running slower than a turtle in peanut butter, and no one could figure out why. That is, until I decided to take a closer look at the database design.
It all began when my boss, a stern woman with a penchant for dramatic entrances, stormed into my cubicle. "Listen up, rookie," she barked (despite the fact that I was quite experienced by this point). "The marketing team is in an uproar over the app's performance. Think you can sort this mess out?"
Challenge accepted! I cracked my knuckles, took a deep breath, and dove headfirst into the database, ready to untangle the digital spaghetti.
The schema was a sight to behold—if you were a fan of chaos, that is. Tables were crammed with redundant data, and the relationships between them made as much sense as a platypus in a tuxedo.
"Okay," I told myself, "time to unleash the power of database normalization."
First, I identified the main entities—clients, transactions, products, and so forth. Then, I dissected each entity into its basic components, ruthlessly eliminating any unnecessary duplication.
For example, the original "clients" table was a hot mess. It had fields for the client's name, address, phone number, and email, but it also inexplicably included fields for the account manager's name and contact information. Data redundancy alert!
So, I created a new "account_managers" table to store all that information, and linked the clients back to their account managers using a foreign key. Boom! Normalized.
Next, I tackled the transactions table. It was a jumble of product details, shipping info, and payment data. I split it into three distinct tables—one for the transaction header, one for the line items, and one for the shipping and payment details.
"This is starting to look promising," I thought, giving myself an imaginary high-five.
After several more rounds of table splitting and relationship building, the database was looking sleek, streamlined, and ready for action. I couldn't wait to see the results.
Sure enough, the next day, when the marketing team tested the app, it was like night and day. The pages loaded in a flash, and the users were practically singing my praises (okay, maybe not singing, but definitely less cranky).
My boss, who was not one for effusive praise, gave me a rare smile and said, "Good job, rookie. I knew you had it in you."
From that day forward, I became the go-to person for all things database-related. And you know what? I actually enjoyed the challenge. It's like solving a complex puzzle, but with a lot more coffee and SQL.
So, if you ever find yourself dealing with a sluggish app and a tangled database, don't panic. Grab a strong cup of coffee, roll up your sleeves, and dive into the normalization process. Trust me, your users (and your boss) will be eternally grateful.
Step-by-Step Guide to Database Normalization
Here's the step-by-step process I used to normalize the database and resolve the performance issues. I used an online database design tool to visualize this design. Here's what I did:
Original Clients Table:
ClientID int
ClientName varchar
ClientAddress varchar
ClientPhone varchar
ClientEmail varchar
AccountManagerName varchar
AccountManagerPhone varchar
Step 1: Separate the Account Managers information into a new table:
AccountManagers Table:
AccountManagerID int
AccountManagerName varchar
AccountManagerPhone varchar
Updated Clients Table:
ClientID int
ClientName varchar
ClientAddress varchar
ClientPhone varchar
ClientEmail varchar
AccountManagerID int
Step 2: Separate the Transactions information into a new table:
Transactions Table:
TransactionID int
ClientID int
TransactionDate date
ShippingAddress varchar
ShippingPhone varchar
PaymentMethod varchar
PaymentDetails varchar
Step 3: Separate the Transaction Line Items into a new table:
TransactionLineItems Table:
LineItemID int
TransactionID int
ProductID int
Quantity int
UnitPrice decimal
Step 4: Create a separate table for Products:
Products Table:
ProductID int
ProductName varchar
ProductDescription varchar
UnitPrice decimal
After these normalization steps, the database structure was much cleaner and more efficient. Here's how the relationships between the tables would look:
Clients --< Transactions >-- TransactionLineItems
Clients --< AccountManagers
Transactions --< Products
By separating the data into these normalized tables, we eliminated data redundancy, improved data integrity, and made the database more scalable. The application's performance should now be significantly faster, as the database can efficiently retrieve and process the data it needs.
Conclusion
After a whirlwind week of wrestling with spreadsheets and SQL queries, the database normalization project was complete. I leaned back, took a deep breath, and admired my work.
The previously chaotic mess of data had been transformed into a sleek, efficient database structure. Redundant information was a thing of the past, and the performance was snappy.
I couldn't wait to show my boss the results. As I walked into her office, she looked up with a hopeful glint in her eye.
"Well, rookie," she began, "any progress on that database issue?"
I grinned. "Absolutely. Let me show you."
I pulled up the new database schema on her screen, walking her through each step of the normalization process. Her eyes widened with every explanation.
"Incredible! I never realized database design could be so... detailed," she exclaimed.
When I finished, she leaned back, a satisfied smile spreading across her face.
"Fantastic job, rookie. I knew you were the right person for this." She paused, then added, "I think this calls for a celebratory lunch. My treat. What do you say?"
I didn't need to be asked twice. As we headed out, a wave of pride and accomplishment washed over me. It had been hard work, but the payoff was worth it. Not only had I solved a critical issue for the business, but I'd also cemented my reputation as the go-to database guru.
From that day on, whenever performance issues or data management challenges cropped up, my boss would come knocking. And you know what? I didn't mind one bit. It was the perfect opportunity to flex my normalization muscles and keep that database running smoothly.
So, if you ever find yourself in a similar situation—a sluggish app, a tangled database, and a boss breathing down your neck—remember: normalization is your ally. Embrace the challenge, dive into the data, and watch your application transform into a lean, mean, performance-boosting machine.
And don't forget to ask your boss out for lunch. You've earned it!
8 notes
·
View notes
Text
What is Python, How to Learn Python?
What is Python?
Python is a high-level, interpreted programming language known for its simplicity and readability. It is widely used in various fields like: ✅ Web Development (Django, Flask) ✅ Data Science & Machine Learning (Pandas, NumPy, TensorFlow) ✅ Automation & Scripting (Web scraping, File automation) ✅ Game Development (Pygame) ✅ Cybersecurity & Ethical Hacking ✅ Embedded Systems & IoT (MicroPython)
Python is beginner-friendly because of its easy-to-read syntax, large community, and vast library support.
How Long Does It Take to Learn Python?
The time required to learn Python depends on your goals and background. Here’s a general breakdown:
1. Basics of Python (1-2 months)
If you spend 1-2 hours daily, you can master:
Variables, Data Types, Operators
Loops & Conditionals
Functions & Modules
Lists, Tuples, Dictionaries
File Handling
Basic Object-Oriented Programming (OOP)
2. Intermediate Level (2-4 months)
Once comfortable with basics, focus on:
Advanced OOP concepts
Exception Handling
Working with APIs & Web Scraping
Database handling (SQL, SQLite)
Python Libraries (Requests, Pandas, NumPy)
Small real-world projects
3. Advanced Python & Specialization (6+ months)
If you want to go pro, specialize in:
Data Science & Machine Learning (Matplotlib, Scikit-Learn, TensorFlow)
Web Development (Django, Flask)
Automation & Scripting
Cybersecurity & Ethical Hacking
Learning Plan Based on Your Goal
📌 Casual Learning – 3-6 months (for automation, scripting, or general knowledge) 📌 Professional Development – 6-12 months (for jobs in software, data science, etc.) 📌 Deep Mastery – 1-2 years (for AI, ML, complex projects, research)
Scope @ NareshIT:
At NareshIT’s Python application Development program you will be able to get the extensive hands-on training in front-end, middleware, and back-end technology.
It skilled you along with phase-end and capstone projects based on real business scenarios.
Here you learn the concepts from leading industry experts with content structured to ensure industrial relevance.
An end-to-end application with exciting features
Earn an industry-recognized course completion certificate.
For more details:
#classroom#python#education#learning#teaching#institute#marketing#study motivation#studying#onlinetraining
2 notes
·
View notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
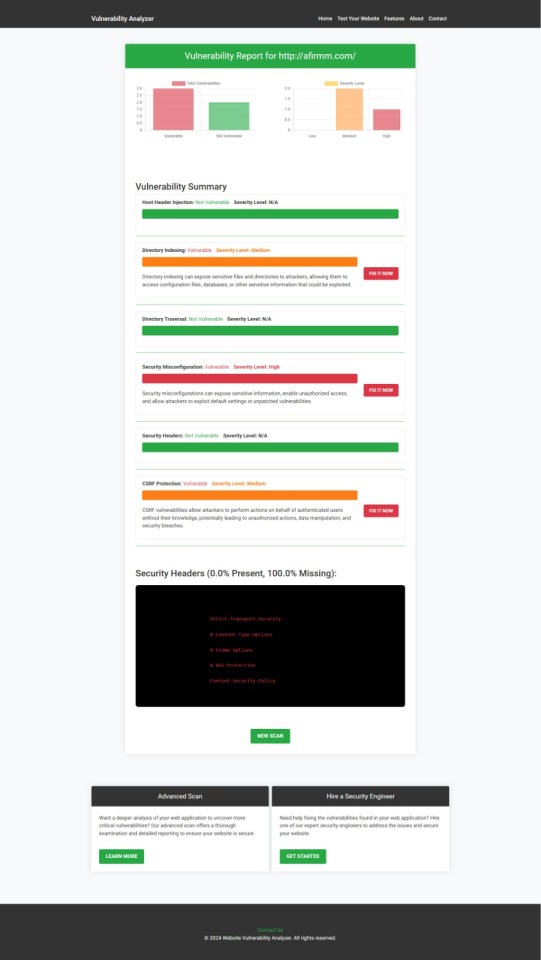
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
Top 10 In- Demand Tech Jobs in 2025

Technology is growing faster than ever, and so is the need for skilled professionals in the field. From artificial intelligence to cloud computing, businesses are looking for experts who can keep up with the latest advancements. These tech jobs not only pay well but also offer great career growth and exciting challenges.
In this blog, we’ll look at the top 10 tech jobs that are in high demand today. Whether you’re starting your career or thinking of learning new skills, these jobs can help you plan a bright future in the tech world.
1. AI and Machine Learning Specialists
Artificial Intelligence (AI) and Machine Learning are changing the game by helping machines learn and improve on their own without needing step-by-step instructions. They’re being used in many areas, like chatbots, spotting fraud, and predicting trends.
Key Skills: Python, TensorFlow, PyTorch, data analysis, deep learning, and natural language processing (NLP).
Industries Hiring: Healthcare, finance, retail, and manufacturing.
Career Tip: Keep up with AI and machine learning by working on projects and getting an AI certification. Joining AI hackathons helps you learn and meet others in the field.
2. Data Scientists
Data scientists work with large sets of data to find patterns, trends, and useful insights that help businesses make smart decisions. They play a key role in everything from personalized marketing to predicting health outcomes.
Key Skills: Data visualization, statistical analysis, R, Python, SQL, and data mining.
Industries Hiring: E-commerce, telecommunications, and pharmaceuticals.
Career Tip: Work with real-world data and build a strong portfolio to showcase your skills. Earning certifications in data science tools can help you stand out.
3. Cloud Computing Engineers: These professionals create and manage cloud systems that allow businesses to store data and run apps without needing physical servers, making operations more efficient.
Key Skills: AWS, Azure, Google Cloud Platform (GCP), DevOps, and containerization (Docker, Kubernetes).
Industries Hiring: IT services, startups, and enterprises undergoing digital transformation.
Career Tip: Get certified in cloud platforms like AWS (e.g., AWS Certified Solutions Architect).
4. Cybersecurity Experts
Cybersecurity professionals protect companies from data breaches, malware, and other online threats. As remote work grows, keeping digital information safe is more crucial than ever.
Key Skills: Ethical hacking, penetration testing, risk management, and cybersecurity tools.
Industries Hiring: Banking, IT, and government agencies.
Career Tip: Stay updated on new cybersecurity threats and trends. Certifications like CEH (Certified Ethical Hacker) or CISSP (Certified Information Systems Security Professional) can help you advance in your career.
5. Full-Stack Developers
Full-stack developers are skilled programmers who can work on both the front-end (what users see) and the back-end (server and database) of web applications.
Key Skills: JavaScript, React, Node.js, HTML/CSS, and APIs.
Industries Hiring: Tech startups, e-commerce, and digital media.
Career Tip: Create a strong GitHub profile with projects that highlight your full-stack skills. Learn popular frameworks like React Native to expand into mobile app development.
6. DevOps Engineers
DevOps engineers help make software faster and more reliable by connecting development and operations teams. They streamline the process for quicker deployments.
Key Skills: CI/CD pipelines, automation tools, scripting, and system administration.
Industries Hiring: SaaS companies, cloud service providers, and enterprise IT.
Career Tip: Earn key tools like Jenkins, Ansible, and Kubernetes, and develop scripting skills in languages like Bash or Python. Earning a DevOps certification is a plus and can enhance your expertise in the field.
7. Blockchain Developers
They build secure, transparent, and unchangeable systems. Blockchain is not just for cryptocurrencies; it’s also used in tracking supply chains, managing healthcare records, and even in voting systems.
Key Skills: Solidity, Ethereum, smart contracts, cryptography, and DApp development.
Industries Hiring: Fintech, logistics, and healthcare.
Career Tip: Create and share your own blockchain projects to show your skills. Joining blockchain communities can help you learn more and connect with others in the field.
8. Robotics Engineers
Robotics engineers design, build, and program robots to do tasks faster or safer than humans. Their work is especially important in industries like manufacturing and healthcare.
Key Skills: Programming (C++, Python), robotics process automation (RPA), and mechanical engineering.
Industries Hiring: Automotive, healthcare, and logistics.
Career Tip: Stay updated on new trends like self-driving cars and AI in robotics.
9. Internet of Things (IoT) Specialists
IoT specialists work on systems that connect devices to the internet, allowing them to communicate and be controlled easily. This is crucial for creating smart cities, homes, and industries.
Key Skills: Embedded systems, wireless communication protocols, data analytics, and IoT platforms.
Industries Hiring: Consumer electronics, automotive, and smart city projects.
Career Tip: Create IoT prototypes and learn to use platforms like AWS IoT or Microsoft Azure IoT. Stay updated on 5G technology and edge computing trends.
10. Product Managers
Product managers oversee the development of products, from idea to launch, making sure they are both technically possible and meet market demands. They connect technical teams with business stakeholders.
Key Skills: Agile methodologies, market research, UX design, and project management.
Industries Hiring: Software development, e-commerce, and SaaS companies.
Career Tip: Work on improving your communication and leadership skills. Getting certifications like PMP (Project Management Professional) or CSPO (Certified Scrum Product Owner) can help you advance.
Importance of Upskilling in the Tech Industry
Stay Up-to-Date: Technology changes fast, and learning new skills helps you keep up with the latest trends and tools.
Grow in Your Career: By learning new skills, you open doors to better job opportunities and promotions.
Earn a Higher Salary: The more skills you have, the more valuable you are to employers, which can lead to higher-paying jobs.
Feel More Confident: Learning new things makes you feel more prepared and ready to take on tougher tasks.
Adapt to Changes: Technology keeps evolving, and upskilling helps you stay flexible and ready for any new changes in the industry.
Top Companies Hiring for These Roles
Global Tech Giants: Google, Microsoft, Amazon, and IBM.
Startups: Fintech, health tech, and AI-based startups are often at the forefront of innovation.
Consulting Firms: Companies like Accenture, Deloitte, and PwC increasingly seek tech talent.
In conclusion, the tech world is constantly changing, and staying updated is key to having a successful career. In 2025, jobs in fields like AI, cybersecurity, data science, and software development will be in high demand. By learning the right skills and keeping up with new trends, you can prepare yourself for these exciting roles. Whether you're just starting or looking to improve your skills, the tech industry offers many opportunities for growth and success.
#Top 10 Tech Jobs in 2025#In- Demand Tech Jobs#High paying Tech Jobs#artificial intelligence#datascience#cybersecurity
2 notes
·
View notes
Note
multiples of 5!
TV show of the year?
The Prisoner (1968) whose pilot episode is THE most made-specificially-for-me episode of television in history (bureaucratic horror)
youtube
Something that made you cry this year?
too many to count!
What’s a bad habit you picked up this year?

What’s something you learned this year?
brushed up on SQL, learned GIS in more applicable ways than "lunar crater counting and age estimation". hosted a successful big girl dinner party! made some new soups!
Did you create any characters (in games, art, or writing) this year? Describe one
tragically no. very little creative energy this year. maybe next year will be kinder.
3 notes
·
View notes
Text
SQL Injection
perhaps, the direct association with the SQLi is:
' OR 1=1 -- -
but what does it mean?
Imagine, you have a login form with a username and a password. Of course, it has a database connected to it. When you wish a login and submit your credentials, the app sends a request to the database in order to check whether your data is correct and is it possible to let you in.
the following PHP code demonstrates a dynamic SQL query in a login from. The user and password variables from the POST request is concatenated directly into the SQL statement.
$query ="SELECT * FROM users WHERE username='" +$_POST["user"] + "' AND password= '" + $_POST["password"]$ + '";"
"In a world of locked rooms, the man with the key is king",
and there is definitely one key as a SQL statement:
' OR 1=1-- -
supplying this value inside the name parameter, the query might return more than one user.
most applications will process the first user returned, meaning that the attacker can exploit this and log in as the first user the query returned
the double-dash (--) sequence is a comment indicator in SQL and causes the rest of the query to be commented out
in SQL, a string is enclosed within either a single quote (') or a double quote ("). The single quote (') in the input is used to close the string literal.
If the attacker enters ' OR 1=1-- - in the name parameter and leaves the password blank, the query above will result in the following SQL statement:
SELECT * FROM users WHERE username = '' OR 1=1-- -' AND password = ''
executing the SQL statement above, all the users in the users table are returned -> the attacker bypasses the application's authentication mechanism and is logged in as the first user returned by the query.
The reason for using -- - instead of -- is primarily because of how MySQL handles the double-dash comment style: comment style requires the second dash to be followed by at least one whitespace or control character (such as a space, tab, newline, and so on). The safest solution for inline SQL comment is to use --<space><any character> such as -- - because if it is URL-encoded into --%20- it will still be decoded as -- -.
4 notes
·
View notes
Text
Which is better full stack development or testing?

Full Stack Development vs Software Testing: Which Career Path is Right for You?
In today’s rapidly evolving IT industry, choosing the right career path can be challenging. Two popular options are Full Stack Development and Software Testing. Both of these fields offer unique opportunities and cater to different skill sets, making it essential to assess which one aligns better with your interests, goals, and long-term career aspirations.
At FirstBit Solutions, we take pride in offering a premium quality of teaching, with expert-led courses designed to provide real-world skills. Our goal is to help you know, no matter which path you choose. Whether you’re interested in development or testing, our 100% unlimited placement call guarantee ensures ample job opportunities. In this answer, we’ll explore both career paths to help you make an informed decision.
Understanding Full Stack Development
What is Full Stack Development?
Full Stack Development involves working on both the front-end (client-side) and back-end (server-side) of web applications. Full stack developers handle everything from designing the user interface (UI) to managing databases and server logic. They are versatile professionals who can oversee a project from start to finish.
Key Skills Required for Full Stack Development
To become a full stack developer, you need a diverse set of skills, including:
Front-End Technologies: HTML, CSS, and JavaScript are the fundamental building blocks of web development. Additionally, proficiency in front-end frameworks like React, Angular, or Vue.js is crucial for creating dynamic and responsive web interfaces.
Back-End Technologies: Understanding back-end programming languages like Node.js, Python, Ruby, Java, or PHP is essential for server-side development. Additionally, knowledge of frameworks like Express.js, Django, or Spring can help streamline development processes.
Databases: Full stack developers must know how to work with both SQL (e.g., MySQL, PostgreSQL) and NoSQL (e.g., MongoDB) databases.
Version Control and Collaboration: Proficiency in tools like Git, GitHub, and agile methodologies is important for working in a collaborative environment.
Job Opportunities in Full Stack Development
Full stack developers are in high demand due to their versatility. Companies often prefer professionals who can handle both front-end and back-end tasks, making them valuable assets in any development team. Full stack developers can work in:
Web Development
Mobile App Development
Enterprise Solutions
Startup Ecosystems
The flexibility to work on multiple layers of development opens doors to various career opportunities. Moreover, the continuous rise of startups and digital transformation initiatives has further fueled the demand for full stack developers.
Benefits of Choosing Full Stack Development
High Demand: The need for full stack developers is constantly increasing across industries, making it a lucrative career choice.
Versatility: You can switch between front-end and back-end tasks, giving you a holistic understanding of how applications work.
Creativity: If you enjoy creating visually appealing interfaces while also solving complex back-end problems, full stack development allows you to engage both creative and logical thinking.
Salary: Full stack developers typically enjoy competitive salaries due to their wide skill set and ability to handle various tasks.
Understanding Software Testing
What is Software Testing?
Software Testing is the process of evaluating and verifying that a software product or application is free of defects, meets specified requirements, and functions as expected. Testers ensure the quality and reliability of software by conducting both manual and automated tests.
Key Skills Required for Software Testing
To succeed in software testing, you need to develop the following skills:
Manual Testing: Knowledge of testing techniques, understanding different testing types (unit, integration, system, UAT, etc.), and the ability to write test cases are fundamental for manual testing.
Automated Testing: Proficiency in tools like Selenium, JUnit, TestNG, or Cucumber is essential for automating repetitive test scenarios and improving efficiency.
Attention to Detail: Testers must have a keen eye for identifying potential issues, bugs, and vulnerabilities in software systems.
Scripting Knowledge: Basic programming skills in languages like Java, Python, or JavaScript are necessary to write and maintain test scripts for automated testing.
Job Opportunities in Software Testing
As the demand for high-quality software increases, so does the need for skilled software testers. Companies are investing heavily in testing to ensure that their products perform optimally in the competitive market. Software testers can work in:
Manual Testing
Automated Testing
Quality Assurance (QA) Engineering
Test Automation Development
With the rise of Agile and DevOps methodologies, the role of testers has become even more critical. Continuous integration and continuous delivery (CI/CD) pipelines rely on automated testing to deliver reliable software faster.
Benefits of Choosing Software Testing
Job Security: With software quality being paramount, skilled testers are in high demand, and the need for testing professionals will only continue to grow.
Quality Assurance: If you have a knack for perfection and enjoy ensuring that software works flawlessly, testing could be a satisfying career.
Automated Testing Growth: The shift toward automation opens up new opportunities for testers to specialize in test automation tools and frameworks, which are essential for faster releases.
Flexibility: Testing provides opportunities to work across different domains and industries, as almost every software product requires thorough testing.
Full Stack Development vs Software Testing: A Comparative Analysis
Let’s break down the major factors that could influence your decision:
Factors
Full Stack Development
Software Testing
Skills
Proficiency in front-end and back-end technologies, databases
Manual and automated testing, attention to detail, scripting
Creativity
High – involves creating and designing both UI and logic
Moderate – focuses on improving software through testing and validation
Job Roles
Web Developer, Full Stack Engineer, Mobile App Developer
QA Engineer, Test Automation Engineer, Software Tester
Career Growth
Opportunities to transition into senior roles like CTO or Solution Architect
Growth towards roles in automation and quality management
Salary
Competitive with wide-ranging opportunities
Competitive, with automation testers in higher demand
Demand
High demand due to increasing digitalization and web-based applications
Consistently high, especially in Agile/DevOps environments
Learning Curve
Steep – requires mastering multiple languages and technologies
Moderate – requires a focus on testing tools, techniques, and automation
Why Choose FirstBit Solutions for Full Stack Development or Software Testing?
At FirstBit Solutions, we provide comprehensive training in both full stack development and software testing. Our experienced faculty ensures that you gain hands-on experience and practical knowledge in the field of your choice. Our 100% unlimited placement call guarantee ensures that you have ample opportunities to land your dream job, no matter which course you pursue. Here’s why FirstBit is your ideal training partner:
Expert Trainers: Learn from industry veterans with years of experience in development and testing.
Real-World Projects: Work on real-world projects that simulate industry scenarios, providing you with the practical experience needed to excel.
Job Assistance: Our robust placement support ensures you have access to job openings with top companies.
Flexible Learning: Choose from online and offline batch options to fit your schedule.
Conclusion: Which Career Path is Right for You?
Ultimately, the choice between full stack development and software testing comes down to your personal interests, skills, and career aspirations. If you’re someone who enjoys building applications from the ground up, full stack development might be the perfect fit for you. On the other hand, if you take satisfaction in ensuring that software is of the highest quality, software testing could be your calling.
At FirstBit Solutions, we provide top-notch training in both fields, allowing you to pursue your passion and build a successful career in the IT industry. With our industry-aligned curriculum, expert guidance, and 100% placement call guarantee, your future is in good hands.
So, what are you waiting for? Choose the course that excites you and start your journey toward a rewarding career today!
#education#programming#tech#technology#training#python#full stack developer#software testing#itservices#java#.net#.net developers#datascience
2 notes
·
View notes
Text
VPS Windows Hosting in India: The Ultimate Guide for 2024

In the ever-evolving landscape of web hosting, Virtual Private Servers (VPS) have become a preferred choice for both businesses and individuals. Striking a balance between performance, cost-effectiveness, and scalability, VPS hosting serves those seeking more than what shared hosting provides without the significant expense of a dedicated server. Within the myriad of VPS options, VPS Windows Hosting stands out as a popular choice for users who have a preference for the Microsoft ecosystem.
This comprehensive guide will explore VPS Windows Hosting in India, shedding light on its functionality, key advantages, its relevance for Indian businesses, and how to select the right hosting provider in 2024.
What is VPS Windows Hosting?
VPS Windows Hosting refers to a hosting type where a physical server is partitioned into various virtual servers, each operating with its own independent Windows OS. Unlike shared hosting, where resources are shared among multiple users, VPS provides dedicated resources, including CPU, RAM, and storage, which leads to enhanced performance, security, and control.
Why Choose VPS Windows Hosting in India?
The rapid growth of India’s digital landscape and the rise in online businesses make VPS hosting an attractive option. Here are several reasons why Windows VPS Hosting can be an optimal choice for your website or application in India:
Seamless Compatibility: Windows VPS is entirely compatible with Microsoft applications such as ASP.NET, SQL Server, and Microsoft Exchange. For websites or applications that depend on these technologies, Windows VPS becomes a natural option.
Scalability for Expanding Businesses: A notable advantage of VPS hosting is its scalability. As your website or enterprise grows, upgrading server resources can be done effortlessly without downtime or cumbersome migration. This aspect is vital for startups and SMEs in India aiming to scale economically.
Localized Hosting for Improved Speed: Numerous Indian hosting providers have data centers within the country, minimizing latency and enabling quicker access for local users, which is particularly advantageous for targeting audiences within India.
Enhanced Security: VPS hosting delivers superior security compared to shared hosting, which is essential in an era where cyber threats are increasingly prevalent. Dedicated resources ensure your data remains isolated from others on the same physical server, diminishing the risk of vulnerabilities.
Key Benefits of VPS Windows Hosting
Dedicated Resources: VPS Windows hosting ensures dedicated CPU, RAM, and storage, providing seamless performance, even during traffic surges.
Full Administrative Control: With Windows VPS, you gain root access, allowing you to customize server settings, install applications, and make necessary adjustments.
Cost Efficiency: VPS hosting provides the advantages of dedicated hosting at a more economical price point. This is incredibly beneficial for businesses looking to maintain a competitive edge in India’s market.
Configurability: Whether you require specific Windows applications or custom software, VPS Windows hosting allows you to tailor the server to meet your unique needs.
Managed vs. Unmanaged Options: Depending on your technical ability, you can opt for managed VPS hosting, where the provider manages server maintenance, updates, and security, or unmanaged VPS hosting, where you retain full control of the server and its management.
How to Select the Right VPS Windows Hosting Provider in India
With a plethora of hosting providers in India offering VPS Windows hosting, selecting one that meets your requirements is crucial. Here are several factors to consider:
Performance & Uptime: Choose a hosting provider that guarantees a minimum uptime of 99.9%. Reliable uptime ensures your website remains accessible at all times, which is crucial for any online venture.
Data Center Location: Confirm that the hosting provider has data centers located within India or in proximity to your target users. This will enhance loading speeds and overall user satisfaction.
Pricing & Plans: Evaluate pricing plans from various providers to ensure you’re receiving optimal value. Consider both initial costs and renewal rates, as some providers may offer discounts for longer commitments.
Customer Support: Opt for a provider that offers 24/7 customer support, especially if you lack an in-house IT team. Look for companies that offer support through various channels like chat, phone, and email.
Security Features: Prioritize providers offering robust security features such as firewall protection, DDoS mitigation, automatic backups, and SSL certificates.
Backup and Recovery: Regular backups are vital for data protection. Verify if the provider includes automated backups and quick recovery options for potential issues.
Top VPS Windows Hosting Providers in India (2024)
To streamline your research, here's a brief overview of some of the top VPS Windows hosting providers in India for 2024:
Host.co.in
Recognized for its competitive pricing and exceptional customer support, Host.co.in offers a range of Windows VPS plans catering to businesses of various sizes.
BigRock
Among the most well-known hosting providers in India, BigRock guarantees reliable uptime, superb customer service, and diverse hosting packages, including Windows VPS.
MilesWeb
MilesWeb offers fully managed VPS hosting solutions at attractive prices, making it a great option for businesses intent on prioritizing growth over server management.
GoDaddy
As a leading name in hosting, GoDaddy provides flexible Windows VPS plans designed for Indian businesses, coupled with round-the-clock customer support.
Bluehost India
Bluehost delivers powerful VPS solutions for users requiring high performance, along with an intuitive control panel and impressive uptime.
Conclusion
VPS Windows Hosting in India is an outstanding option for individuals and businesses in search of a scalable, cost-effective, and performance-oriented hosting solution. With dedicated resources and seamless integration with Microsoft technologies, it suits websites that experience growing traffic or require ample resources.
As we advance into 2024, the necessity for VPS Windows hosting is expected to persist, making it imperative to choose a hosting provider that can accommodate your developing requirements. Whether launching a new website or upgrading your existing hosting package, VPS Windows hosting is a strategic investment for the future of your online endeavors.
FAQs
Is VPS Windows Hosting costly in India?
While VPS Windows hosting is pricier than shared hosting, it is much more affordable than dedicated servers and many providers in India offer competitive rates, making it accessible for small and medium-sized enterprises.
Can I upgrade my VPS Windows Hosting plan easily?
Absolutely, VPS hosting plans provide significant scalability. You can effortlessly enhance your resources like CPU, RAM, and storage without experiencing downtime.
What type of businesses benefit from VPS Windows Hosting in India?
Businesses that demand high performance, improved security, and scalability find the most advantage in VPS hosting. It’s particularly ideal for sites that utilize Windows-based technologies like ASP.NET and SQL Server.
2 notes
·
View notes
Text
The Vital Role of Windows VPS Hosting Services in Today’s Digital World
In the fast-paced, ever-evolving digital landscape, businesses and individuals alike are in constant pursuit of reliability, speed, and efficiency. One technological marvel that has been increasingly pivotal in achieving these goals is Windows VPS (Virtual Private Server) hosting services. These services offer a robust and versatile solution that caters to a wide range of needs, from small business operations to large-scale enterprises. But what makes Windows VPS hosting services so indispensable? Let's dive in.
1. Unmatched Performance and Reliability
When it comes to performance, Windows VPS hosting stands out. Unlike shared hosting, where resources are distributed among multiple users, VPS hosting allocates dedicated resources to each user. This means faster load times, reduced downtime, and a smoother user experience. For businesses, this translates to enhanced customer satisfaction and improved SEO rankings.
2. Scalability at Its Best
One of the standout features of Windows VPS hosting is its scalability. Whether you're a startup experiencing rapid growth or an established business expanding its digital footprint, VPS hosting allows you to easily upgrade your resources as needed. This flexibility ensures that your hosting service grows with your business, eliminating the need for frequent and costly migrations.
3. Enhanced Security Measures
In an age where cyber threats are a constant concern, security is paramount. Windows VPS hosting provides a higher level of security compared to shared hosting. With isolated environments for each user, the risk of security breaches is significantly minimized. Additionally, many Windows VPS services come with advanced security features such as firewalls, regular backups, and DDoS protection, ensuring your data remains safe and secure.
4. Full Administrative Control
For those who require more control over their hosting environment, Windows VPS hosting offers full administrative access. This means you can customize your server settings, install preferred software, and manage your resources as you see fit. This level of control is particularly beneficial for developers and IT professionals who need a tailored hosting environment to meet specific project requirements.
5. Cost-Effective Solution
Despite its numerous advantages, Windows VPS hosting remains a cost-effective solution. It offers a middle ground between the affordability of shared hosting and the high performance of dedicated hosting. By only paying for the resources you need, you can optimize your budget without compromising on quality or performance.
6. Seamless Integration with Microsoft Products
For businesses heavily invested in the Microsoft ecosystem, Windows VPS hosting provides seamless integration with Microsoft products. Whether it's running applications like SQL Server, SharePoint, or other enterprise solutions, the compatibility and performance of Windows VPS hosting are unparalleled.
In conclusion, Windows VPS hosting services are a critical asset in the modern digital world. They offer unmatched performance, scalability, security, control, and cost-effectiveness, making them an ideal choice for businesses and individuals striving for success online. As the digital landscape continues to evolve, embracing Windows VPS hosting can provide the stability and reliability needed to stay ahead of the curve.
3 notes
·
View notes
Text
Optimizing Business Operations with Advanced Machine Learning Services
Machine learning has gained popularity in recent years thanks to the adoption of the technology. On the other hand, traditional machine learning necessitates managing data pipelines, robust server maintenance, and the creation of a model for machine learning from scratch, among other technical infrastructure management tasks. Many of these processes are automated by machine learning service which enables businesses to use a platform much more quickly.
What do you understand of Machine learning?
Deep learning and neural networks applied to data are examples of machine learning, a branch of artificial intelligence focused on data-driven learning. It begins with a dataset and gains the ability to extract relevant data from it.
Machine learning technologies facilitate computer vision, speech recognition, face identification, predictive analytics, and more. They also make regression more accurate.
For what purpose is it used?
Many use cases, such as churn avoidance and support ticket categorization make use of MLaaS. The vital thing about MLaaS is it makes it possible to delegate machine learning's laborious tasks. This implies that you won't need to install software, configure servers, maintain infrastructure, and other related tasks. All you have to do is choose the column to be predicted, connect the pertinent training data, and let the software do its magic.
Natural Language Interpretation
By examining social media postings and the tone of consumer reviews, natural language processing aids businesses in better understanding their clientele. the ml services enable them to make more informed choices about selling their goods and services, including providing automated help or highlighting superior substitutes. Machine learning can categorize incoming customer inquiries into distinct groups, enabling businesses to allocate their resources and time.
Predicting
Another use of machine learning is forecasting, which allows businesses to project future occurrences based on existing data. For example, businesses that need to estimate the costs of their goods, services, or clients might utilize MLaaS for cost modelling.
Data Investigation
Investigating variables, examining correlations between variables, and displaying associations are all part of data exploration. Businesses may generate informed suggestions and contextualize vital data using machine learning.
Data Inconsistency
Another crucial component of machine learning is anomaly detection, which finds anomalous occurrences like fraud. This technology is especially helpful for businesses that lack the means or know-how to create their own systems for identifying anomalies.
Examining And Comprehending Datasets
Machine learning provides an alternative to manual dataset searching and comprehension by converting text searches into SQL queries using algorithms trained on millions of samples. Regression analysis use to determine the correlations between variables, such as those affecting sales and customer satisfaction from various product attributes or advertising channels.
Recognition Of Images
One area of machine learning that is very useful for mobile apps, security, and healthcare is image recognition. Businesses utilize recommendation engines to promote music or goods to consumers. While some companies have used picture recognition to create lucrative mobile applications.
Your understanding of AI will drastically shift. They used to believe that AI was only beyond the financial reach of large corporations. However, thanks to services anyone may now use this technology.
2 notes
·
View notes
Text
Unlock Success: MySQL Interview Questions with Olibr
Introduction
Preparing for a MySQL interview requires a deep understanding of database concepts, SQL queries, optimization techniques, and best practices. Olibr’s experts provide insightful answers to common mysql interview questions, helping candidates showcase their expertise and excel in MySQL interviews.
1. What is MySQL, and how does it differ from other database management systems?
Olibr’s Expert Answer: MySQL is an open-source relational database management system (RDBMS) that uses SQL (Structured Query Language) for managing and manipulating databases. It differs from other DBMS platforms in its open-source nature, scalability, performance optimizations, and extensive community support.
2. Explain the difference between InnoDB and MyISAM storage engines in MySQL.
Olibr’s Expert Answer: InnoDB and MyISAM are two commonly used storage engines in MySQL. InnoDB is transactional and ACID-compliant, supporting features like foreign keys, row-level locking, and crash recovery. MyISAM, on the other hand, is non-transactional, faster for read-heavy workloads, but lacks features such as foreign keys and crash recovery.
3. What are indexes in MySQL, and how do they improve query performance?
Olibr’s Expert Answer: Indexes are data structures that improve query performance by allowing faster retrieval of rows based on indexed columns. They reduce the number of rows MySQL must examine when executing queries, speeding up data retrieval operations, and optimizing database performance.
4. Explain the difference between INNER JOIN and LEFT JOIN in MySQL.
Olibr’s Expert Answer: INNER JOIN and LEFT JOIN are SQL join types used to retrieve data from multiple tables. INNER JOIN returns rows where there is a match in both tables based on the join condition. LEFT JOIN returns all rows from the left table and matching rows from the right table, with NULL values for non-matching rows in the right table.
5. What are the advantages of using stored procedures in MySQL?
Olibr’s Expert Answer: Stored procedures in MySQL offer several advantages, including improved performance due to reduced network traffic, enhanced security by encapsulating SQL logic, code reusability across applications, easier maintenance and updates, and centralized database logic execution.
Conclusion
By mastering these MySQL interview questions and understanding Olibr’s expert answers, candidates can demonstrate their proficiency in MySQL database management, query optimization, and best practices during interviews. Olibr’s insights provide valuable guidance for preparing effectively, showcasing skills, and unlocking success in MySQL-related roles.
2 notes
·
View notes