#What is 8 bit microprocessor
Explore tagged Tumblr posts
Text
https://www.futureelectronics.com/p/semiconductors--microcontrollers--8-bit/pic18f6520-i-pt-microchip-7337520
8-bit microprocessor, 8 bit embedded microcontroller, Low power microcontroller
PIC18F Series 32 kB Flash 2 kB RAM 40 MHz 8-Bit Microcontroller - TQFP-64
#Microchip#PIC18F6520-I/PT#Microcontrollers#8 bit#microprocessor#8 bit embedded#Low power microcontroller#What is 8 bit microprocessor#Low power microcontrollers software#8-bit computing#8-bit image#lcd#Wireless
1 note
·
View note
Text
You might have heard of 32-bit and 64-bit applications before, and if you work with older software, maybe 16-bit and even 8-bit computers. But what came before 8-bit? Was it preceded by 4-bit computing? Were there 2-bit computers? 1-bit? Half-bit?
Well outside that one AVGN meme, half-bit isn't really a thing, but the answer is a bit weirder in other ways! The current most prominent CPU designs come from Intel and AMD, and Intel did produce 4-bit, 8-bit, 16-bit, 32-bit and 64-bit microprocessors (although 4-bit computers weren't really a thing). But what came before 4-bit microprocessors?
Mainframes and minicomputers did. These were large computers intended for organizations instead of personal use. Before microprocessors, they used transistorized integrated circuits (or in the early days even vacuum tubes) and required a much larger space to store the CPU.
And what bit length did these older computers have?
A large variety of bit lengths.
There were 16-bit, 32-bit and 64-bit mainframes/minicomputers, but you also had 36-bit computers (PDP-10), 12-bit (PDP-8), 18-bit (PDP-7), 24-bit (ICT 1900), 48-bit (Burroughs) and 60-bit (CDC 6000) computers among others. There were also computers that didn't use binary encoding to store numbers, such as decimal computers or the very rare ternary computers (Setun).
And you didn't always evolve by extending the bit length, you could upgrade from an 18-bit computer to a more powerful 16-bit computer, which is what the developers of early UNIX did when they switched over from the PDP-7 to the PDP-11, or offer 32-bit over 36-bit, which happened when IBM phased out the IBM 7090 in favor of the the System/360 or DEC phased out the PDP-10 in favor of the VAX.
154 notes
·
View notes
Text




BERT, Basic Educational Robot Trainer (1985) by Karl Brown, Vancouver Community College, Electronics Department, Vancouver, British Columbia, Canada. BERT is based on the 6802 8-bit microprocessor and uses the SPO256 speech chip. Kits were available from Amarobot, Richmond, CA.
"Why is it, I asked myself, that very simple robots, even commercially available ones, require so much training to operate? This, I decided, was a problem, and I wanted to do something about it. What I eventually did was write a menu-driven, interactive control language intended to be simple enough for a ten-year-old to use. As it turned out, during field tests with children, I found that any child who could read could program a robot within one minute of hitting the keyboard. This, I felt, was progress. The next step was to design a robot that my fellow computer club members could build and program. That was how BERT was born." Karl Brown – Build BERT, the Basic Educational Robot Trainer (Part 1, Part 2).
48 notes
·
View notes
Note
Why are computers systems based on the number 8? Like 8-bit graphics, 64 bit rams and others.
8-bit is an easy-to-work-with power of 2 that becomes a good building block. We settled on 8-bits for the first generation of microprocessors and just increased from there to 16, 32, and 64 bits as processor lineages evolved. 8008 -> 8080 -> 8086/8088 -> 80286 -> 80386 -> 80486 -> Pentium, you get the idea
There used to be computers in other bit-width architectures before the dominance of x86 unified most general purpose computers. The big players made 6-bit, 12-bit, 18-bit, 30-bit, 36-bit, etc. sized computers of all kinds for various applications. It was kind of the wild west for a long time because everyone was trying all sorts of things based on what they needed from a computer design.
So it's all powers of 2 because binary. 8 is just convenient.
53 notes
·
View notes
Text
The Evolution of Embedded Hardware: From Simple Circuits to Smart Devices
Embedded systems are all around us in today's hyperconnected world, from the sophisticated electronics controlling your car's engine to the smart thermostat that regulates the temperature in your house. One of the most amazing changes in technology is the progression from simple circuits to the advanced smart devices of today. This evolution, which has been fuelled by necessity and creativity, has been an intriguing one that has taken place over many decades. Understanding this history is essential for developers and businesses traversing this terrain, particularly when thinking about an embedded hardware design service that could help them realise their next big idea.
The Pioneer Days: Early Embedded Systems

The 1960s and 1970s marked the dawn of embedded computing, though it looked nothing like what we recognize today:
The Apollo Guidance Computer, which helped navigate astronauts to the moon, represented one of the first mission-critical embedded systems
Early embedded systems relied on discrete components rather than integrated circuits
These systems were enormous by today’s standards—filling entire cabinets
Programming was done through hard-wired logic or assembly language
Each system was custom-designed for a specific purpose with little flexibility
These primitive beginnings laid groundwork for what would become a technological revolution, yet the limitations were substantial. Memory was measured in kilobytes, processing power was minimal, and development required specialized expertise that few possessed.
The Microprocessor Revolution
Everything changed in the early 1970s with the introduction of the microprocessor:
Intel’s 4004, introduced in 1971, became the first commercially available microprocessor
For the first time, computing power could fit on a single chip
Development costs dropped dramatically, making embedded systems accessible to more industries
Early applications included calculators, cash registers, and industrial controllers
The 8-bit microcontroller era began, with chips like the Intel 8051 becoming industry standards
This miniaturization represented the first major leap toward modern embedded systems. Suddenly, intelligence could be added to previously “dumb” devices, creating new possibilities across industries from manufacturing to consumer electronics.
From Industrial to Consumer Applications
The 1980s and 1990s witnessed embedded systems transitioning from purely industrial uses to consumer products:
Video game consoles like the Nintendo Entertainment System introduced millions to embedded technology
Household appliances began incorporating microcontrollers for improved functionality
Automotive applications expanded rapidly, with engine control units becoming standard
Personal digital assistants (PDAs) showcased the potential for portable computing
Cell phones emerged as perhaps the most transformative embedded systems of the era
At this time, there started to appear specialized embedded hardware design service providers which assists businesses with intricate hardware designs. These services helped translate creative concepts into functioning products, allowing companies without internal capabilities to join the growing competition in the electronics industry.
The Networking Revolution and Embedded Connectivity
By the late 1990s and early 2000s, embedded systems gained a critical new capability—connectivity:
First-generation embedded networks often used proprietary protocols
Industry standards like CAN bus revolutionized automotive electronics
TCP/IP implementation in embedded devices paved the way for Internet connectivity
Wireless technologies like Bluetooth and later Wi-Fi liberated devices from physical connections
Remote monitoring and management became possible, changing service models forever
This networking capability transformed embedded systems from standalone devices to interconnected nodes, creating new possibilities for data collection and device management. Industries from healthcare to manufacturing began reimagining their processes around these newly connected devices.
The Rise of the Internet of Things (IoT)

The 2010s saw embedded systems become truly ubiquitous through the Internet of Things:
Consumer IoT products like smart thermostats, lighting, and speakers entered millions of homes
Industrial IoT revolutionized manufacturing through predictive maintenance and asset tracking
Agriculture embraced precision farming techniques using embedded sensor networks
Healthcare innovations included remote patient monitoring and smart medical devices
Urban infrastructure began incorporating embedded systems for “smart city” initiatives
With this explosion in applications came increasing complexity. An embedded hardware design service became essential for many companies looking to enter the IoT market, providing expertise in not just hardware but the integration of sensors, connectivity, and power management that modern IoT devices require.
Read Also: The Role of Embedded Hardware in IoT Devices
The Miniaturization Miracle
Throughout this evolution, one trend has remained constant—the drive toward smaller, more efficient devices:
Component sizes shrank from through-hole to surface-mount to microscopic
Power consumption decreased dramatically, enabling battery-operated portable devices
Wearable technology emerged as components became small enough to integrate into clothing and accessories
Medical implants shrank to minimize invasiveness while increasing capability
Sensors became small and inexpensive enough to deploy in massive numbers
This miniaturization has opened new frontiers in what’s possible with embedded systems. Today’s embedded hardware design services often specialize in extreme miniaturization, developing sophisticated systems that fit into spaces previously thought impossible.
The Processing Power Explosion
Modern embedded systems bear little resemblance to their ancestors in processing capability:
32-bit and 64-bit processors have replaced 8-bit chips in many applications
Multi-core processors enable complex real-time processing
Specialized hardware accelerators handle tasks like AI inference and video processing
For specific applications, field-programmable gate arrays (FPGAs) offer hardware that can be reconfigured.
��System-on-Chip (SoC) designs combine peripherals, memory, and CPUs into one unit.
With this processing capability, embedded systems can now perform tasks like computer vision and natural language processing that were previously only possible with general-purpose computers, all while retaining the dependability and deterministic behaviour that embedded systems need.
The Future: AI at the Edge and Beyond
Looking ahead, embedded systems continue evolving at a breathtaking pace:
Edge AI is pushing intelligence to embedded devices rather than relying on cloud processing
New materials and manufacturing techniques are enabling flexible and biodegradable electronics
Energy harvesting is reducing or eliminating battery dependencies
Quantum computing principles may eventually transform embedded processing
Neuromorphic computing aims to make embedded systems think more like biological brains
These frontiers represent both challenge and opportunity. Companies seeking to navigate this complexity increasingly turn to specialized embedded hardware design services that can transform cutting-edge concepts into viable products.
The evolution of embedded hardware marks one of the most remarkable journeys of technology, progressing from circuits to devices that think for us and are a part of our lives. This journey continues to accelerate as we enter the following decades which promise even more astonishing innovations. For companies that want to take part in the ongoing revolution, collaborating with specialized embedded hardware design services is crucial for changing futuristic concepts into reality.
0 notes
Text
Victoria en France: Week 16
Hello from Munich airport. I was barely in Cergy this week, as we had a long weekend due to Labor Day being on Thursday. I had a pretty light week of classes Monday-Wednesday, especially as I had no class on Tuesday. I ended up using most of Tuesday to work on a project for Microprocessors, though.
There are still a lot of places we want to visit in Paris, but this week, since we were only there on Monday and Tuesday, we were more focused on appreciating life in Paris. Both nights, we went and sat by the Seine, catching up after break and just talking. Sitting by the Seine in the evening is super nice- there are always a ton of people there and we even met some new friends on Monday.
Wednesday night, we flew to Vienna. Vienna was a super cool city that I've always wanted to see. Once I landed in Austria, I had officially visited 20 countries in my life! While in Vienna, we did a lot of walking around the city to see the major sites. The weather was amazing. We went inside Votive Church, which had really stunning stained glass.


We also went inside Belvedere Palace, which was a museum with a lot of super cool art.


In the evening, we found a hill that had a super great view of the city and the sunset, so we sat there for a bit before going to dinner.

After Vienna, we took a bus to Munich. This was an amazing bus ride- the Austrian countryside is really beautiful. While in Munich, we went to Frühlingsfest (Springfest), which is a festival that is going on right now. It's called Oktoberfest's little sister. It was a fun time- we wore traditional dirndl and ate yummy giant pretzels. My friends also convinced me to go on one of the rides, and even though I was terrified and it went upside down, it ended up being one of the highlights of my day.

We walked around Munich a bit, but the weather wasn't great. We went to the Bavarian National Museum, which is only 1 euro to get in on Sundays. It was cool to see some history there!
This also ended up being my first camping experience. Because of the festival, we slept in an 8 person tent. Our campsite provided breakfast, which was great, and there was a full bathroom with running water. I mostly slept fine, but both mornings, I woke up early feeling really uncomfortable because we were sleeping on rocks. The sleeping cot was not enough to prevent the discomfort and not having a pillow was also not ideal. However, it was good to have a new experience because that's what study abroad is all about!
Over the weekend, we were informed that someone was stabbed to death in the parking lot outside the other FAME residence that I don't live in. At least half of the FAME students live there, so this was a little scary to hear about. We know that Cergy is not safe, but I really wish we were provided with shuttle buses or more convenient housing. Two of my friends found a residence that is super close to ENSEA and the train station, so they never have to walk through Cergy at night. If changes aren't made, I really can't recommend this program to future applicants. My favorite parts of the program are the ability to travel and being immersed in a new culture, and you can get these benefits from any other study abroad program.
This week, we have another long weekend, so I will once again not be in Cergy for very long. Hopefully, I can get some work done for my classes and take advantage of some of my last opportunities to explore Paris.
À Bientôt!
Victoria Vizza
Electrical Engineering
IPE: FAME at ENSEA in Cergy-Pontoise, France
0 notes
Text
Semiconductor Chips Explained: Different Types and Their Uses

In today’s fast-paced technological landscape, there is a growing demand for faster and more efficient devices. This need, however, brings a significant challenge: balancing cost and energy consumption while enhancing the performance and functionality of electronic gadgets.
Introduction to Semiconductor Chips
Semiconductor chips are crucial in this regard. The global semiconductor market is projected to reach $687 billion by 2025, showcasing the transformative impact of these chips across various sectors, from computers and smartphones to advanced AI systems and IoT devices. Let's delve deeper into this billion-dollar industry.
What Is A Semiconductor Chip?
A semiconductor chip, also known as an integrated circuit or computer chip, is a small electronic device made from semiconductor materials like silicon. It contains millions or even billions of transistors, which are tiny electronic components capable of processing and storing data.
These chips are the backbone of modern technology, found in a vast array of electronic devices including computers, smartphones, cars, and medical equipment. Manufacturing semiconductor chips involves a complex, multi-step process that includes slicing silicon wafers, printing intricate circuit designs, and adding multiple layers of components and interconnects. Leading companies in the semiconductor industry include Samsung, TSMC, Qualcomm, Marvell, and Intel.
Types of Semiconductor Chips
Memory Chips
Function: Store data and programs in computers and other devices.
Types:
RAM (Random-Access Memory): Provides temporary workspaces.
Flash Memory: Stores information permanently.
ROM (Read-Only Memory) and PROM (Programmable Read-Only Memory): Non-volatile memory.
EPROM (Erasable Programmable Read-Only Memory) and EEPROM (Electrically Erasable Programmable Read-Only Memory): Can be reprogrammed.
Microprocessors
Function: Contain CPUs that power servers, PCs, tablets, and smartphones.
Architectures:
32-bit and 64-bit: Used in PCs and servers.
ARM: Common in mobile devices.
Microcontrollers (8-bit, 16-bit, and 24-bit): Found in toys and vehicles.
Graphics Processing Units (GPUs)
Function: Render graphics for electronic displays, enhancing computer performance by offloading graphics tasks from the CPU.
Applications: Modern video games, cryptocurrency mining.
Commodity Integrated Circuits (CICs)
Function: Perform repetitive tasks in devices like barcode scanners.
Types:
ASICs (Application-Specific Integrated Circuits): Custom-designed for specific tasks.
FPGAs (Field-Programmable Gate Arrays): Customizable after manufacturing.
SoCs (Systems on a Chip): Integrate all components into a single chip, used in smartphones.
Analog Chips
Function: Handle continuously varying signals, used in power supplies and sensors.
Components: Include transistors, inductors, capacitors, and resistors.
Mixed-Circuit Semiconductors
Function: Combine digital and analog technologies, used in devices requiring both types of signals.
Examples: Microcontrollers with ADCs (Analog-to-Digital Converters) and DACs (Digital-to-Analog Converters).
Manufacturing Process of Semiconductor Chips
Semiconductor device fabrication involves several steps to create electronic circuits on a silicon wafer. Here’s an overview:
Wafer Preparation: Silicon ingots are shaped and sliced into thin wafers.
Cleaning and Oxidation: Wafers are cleaned and oxidized to form a silicon dioxide layer.
Photolithography: Circuit patterns are transferred onto wafers using UV light and photoresist.
Etching: Unwanted material is removed based on the photoresist pattern.
Doping: Ions are implanted to alter electrical properties.
Deposition: Thin films of materials are deposited using CVD or PVD techniques.
Annealing: Wafers are heated to activate dopants and repair damage.
Testing and Packaging: Finished wafers are tested, diced into individual chips, and packaged for protection.
Conclusion
Semiconductor chips are fundamental to the functionality of nearly every electronic device we use today. They have revolutionized technology by enabling faster, smaller, and more powerful devices. While the semiconductor industry has fueled job creation and economic growth, it also faces challenges related to sustainability and environmental impact. As we continue to push the boundaries of innovation, ethical practices are essential to ensure semiconductors remain vital to our modern world and shape our future.
0 notes
Text
BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 applied to Smart Environment Monitoring
1. Foreword
Environmental pollution has a huge impact on human health and ecosystems, so environmental monitoring is particularly important. This article will introduce the application of BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 in smart environmental monitoring. By connecting various sensors and realizing remote data transmission and control, the device can monitor, manage and control environmental pollution sources in real time, providing reliable data support for environmental protection.
2. Importance of Environmental Pollution Monitoring
Environmental pollution poses a serious threat to human health and ecosystems, so the importance of environmental monitoring is self-evident. Through real-time monitoring and control of pollution sources in the environment, we can take timely measures to protect the environment, reduce pollutant emissions, and provide reliable data support for environmental protection decisions.
3. What is BLIIoT SMS/4G Remote Monitoring RTU Gateway S275?
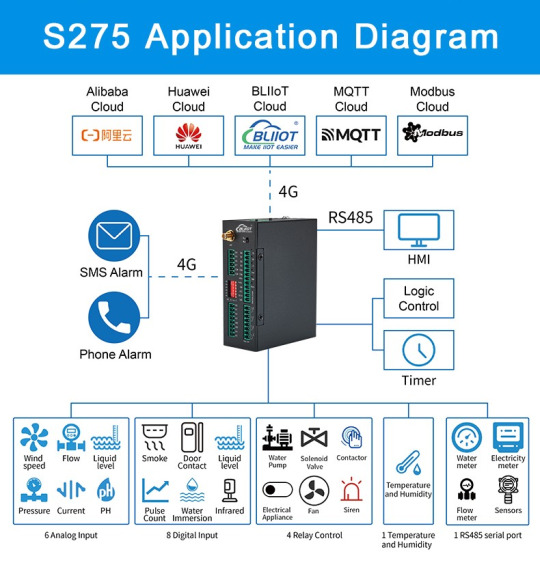
BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 is an industrial class, high reliability, high stability, and programmable Remote Terminal Unit (RTU). It embedded 32-Bit High Performance Microprocessor MCU, inbuilt industrial Cellular module. It provides 8 digital inputs, 6 analog or PT100 Resistance Temperature Detector (RTD) inputs, 4 relay outputs, 1 ambient sensor input for monitoring onsite temperature and humidity, and RS485 serial port, supports extending 320 I/O tags via Modbus RTU protocol. It can monitoring and operates the I/O ports by SMS, APP, Web Server, internet, timers and programmed inter-lock events automatically.
4. Application scenarios in Smart Environment Monitoring
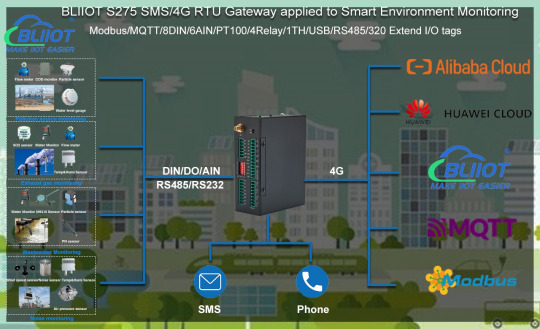
Pollution source monitoring
The process of systematically monitoring and evaluating emissions from specific sources of pollution. Its purpose is to determine the emission of pollution sources, assess its impact on the environment and human health, and provide data support for taking corresponding pollution prevention and control measures.
Exhaust gas monitoring
The process of monitoring and analyzing the waste gas generated in industrial production, transportation, energy utilization and other activities. Its main purpose is to assess and monitor the impact of exhaust emissions on the environment and human health to ensure compliance with relevant environmental regulations and standards.
Wastewater Monitoring
The process of monitoring and evaluating wastewater discharge and treatment systems. It aims to ensure that sewage discharge complies with relevant environmental regulations and standards to protect the environment and human health.
Noise Monitoring
The process of monitoring and evaluating noise levels in an environment. Its purpose is to assess the extent to which noise affects human health, the quality of life of residents and the environment, and to ensure compliance with relevant noise regulations and standards.
BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 is the core device of the pollution source automatic monitoring system, which supports the connection of various sensing devices, including air pollution sources, such as sulfur dioxide, hydrocarbons, particles, carbon dioxide, hydrogen chloride, VOCs, etc., and waste water pollution sources, such as COD, nitrogen , total, PH, etc., BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 via 4G uploads data to the cloud platform/server to realize real-time monitoring, collection, analysis and upload of all elements of pollution sources.
5. Data real-time monitoring and remote control
BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 connects various pollution sensors through DIN/DO/AIN/RS485, collects data and uploads it to the cloud platform or server to realize centralized management and analysis of real-time data monitoring. At the same time, it also supports remote control of the operating status and alarm functions of related equipment to ensure the safe operation of the equipment.
6. Summarize
BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 plays an important role in environmental pollution monitoring. It has a wide range of application scenarios, covering pollution source monitoring, waste gas monitoring, sewage monitoring, noise monitoring and other fields. Through real-time monitoring, remote control and data management, it can provide accurate data and decision support for environmental protection. In the future, with the continuous development of IoT technology, 4G RTU terminals will play a more important role in environmental pollution monitoring.
More information about BLIIoT SMS/4G Remote Monitoring RTU Gateway S275 : https://www.bliiot.com/cellular-iot-modbus-rtu-8din6ain-pt1004relay1thusbrs485320-extend-i-o-tags-p00175p1.html
0 notes
Text
Life as a Senior NCO for a Head of Household that can't Provide.
As I stated later in the blog, you can safeguard yourself by simply taking the steps to do so with ARM's MMU, 8bit and 16bit execution side processing, and embedded instructions. Effectively cutting away product categorization in the markets.
But in today's economy, there is an enemy lurking in darkness, that Senior NCO's have struggled with as they question their own service, and their own lives.
And you are getting into enumerations for espionage.
And I wanted to introduce what I refer to as "multiple execution side porting." And this technology safe guards what is allowed at PC Board level.
"Multiple Execution Side Porting" is the first step for anti-espionage technologies requiring a microprocessor. Effectively limiting "intent" at security checkpoints for secured facilities and secured work environments.
There is nothing more important then knowing that someone is there, fighting "with" you.

--------
-multiple execution side porting
-embedded instructions
-Memory Management Unit
-40 bit addressing for up to 1 terabyte
-8 bit and 16bit execution side option
-component quality and intellectual property dexterity
-----
I can't see that getting too upset about EU lawmaker irresponsibility is neccesary, given the soundness our our financial system.
Regardless of political indifference between the US and the European Union, the private sector is well equipped to address these indifferences, as consumer technologies are already in the hands of the public.
Until then, regardless of time lost, it's important to note the soundness and rigidity of the American 3rd Amendment.

--------

"There's no reason to subscribe to a false sense of confidence from on-going Unilateral agreements in our financial system. And Civil Process will be served in due justice."
Sergeant Major Nathan Marksmith, North Wales Militia, Joint Militia Detachment
0 notes
Text
#this idiot doesn't even know z80 assembly#(i don't know z80 assembly)
First, just in case you don't know how the standard bitwise operators (AND, OR, XOR, CPL, RR, RL) work, read this, it'll give you the basics.
In a high level language, you would set bit X (to 1) of variable Y like this:
y = y | (1 << x);
For example, if we wanted to set bit 4 of y to 1, and y was equal to 0b0110, then (1 << x) would be (1 << 4), which is equal to 0b1000; and 0b0110 | 0b1000 = 0b1110. Easy-peasy.
However, if we wanted to implement that into z80 assembly, we have to get a little creative. The z80 instruction set is very old (for a microprocessor, anyway) and is thus very limited. One of these limitations is that it doesn't have a "Left Shift [register 1] by [register 2]" instruction. (Registers, if you aren't aware, are basically like hard-coded variables that live inside the CPU instead of RAM.)
What it does have is a "Left Shift [register] by 1" instruction, equivalent to this c code:
r = r << 1;
where 'r' is a placeholder for a given register. It also has "Decrement [register]" and "Increment [register]" instructions that are equivalent to the c code:
r--;
and
r++;
And an "OR [register] with register A" instruction, equivalent to:
A = A | r;
Let's say that we're trying to set bit 4 of register A, and that we'll be storing which bit we're setting (4) in register L. We'll also use register B as a temporary value. This can be easily accomplished with a loop:
B = 1; while (L != 0) { L--; B = B << 1; } A = A | B;
In this example, B will equal to (1 << L) and A is thus equal to A | (1 << L), just what we wanted.
But z80 assembly doesn't have while loops, so we need to implement that too. What we do have are jumps, which are sort of like ifs and gotos put together (or rather, ifs and gotos are just different abstractions on jumps). The relevant instructions here are "jump to label if the last operation resulted in 0" and "jump to label unconditionally". Here's a naive approach to our while loop--and one of the approaches chatgpt took--in pseudo code:
B = 1; loop! <- label to jump to L--; if L is now 0, jump to done! B = B << 1; jump to loop! done! A = A | B;
But this isn't what we wanted--there's a classic off-by-one error. If L is 1, it won't shift at all, and if L is 0, it'll underflow and shift 256 times. The solution is pretty simple--just increment L right before the loop.
B = 1; L++; loop! <- label to jump to L--; if L is now 0, jump to done! B = B << 1; jump to loop! done! A = A | B;
There's more nuance here wrt the carry flag, rotate vs shift, instruction length, etc. but this is the general idea
(It's worth noting that you could get around the off-by-one error by considering bit 1 the first and bit 8 the last, instead of bit 0 and bit 7--it depends on your needs--but for my purposes I needed bit 0 to be the first bit.)
As an aside--the rest of the problems it had were down to a clear misunderstanding of how the z80 instruction set behaves. Take this bit from its first attempt:
OR B ; OR A with the mask in B, setting the desired bit LD A, B ; A now has the bit L set
This doesn't work. A C translation would be this:
A = A | B; A = B;
I have no idea why it tacked on that LD A, B; but it demonstrates a deeply flawed ability to generate code. Totally inane.
I wanted to see if our friend The World's Dumbest Robot could figure out the extremely simple process of "set bit L of register A" in z80 assembly, and the results were...consistent.





What a moron.
10 notes
·
View notes
Photo


The Lisa Hardware
Reporting on the technical specifications of a computer toward the end of an article is unusual for BYTE, but it emphasizes that the why of Lisa is more important than the what. For part of the market, at least, the Lisa computer will change the emphasis of microcomputing from “How much RAM does it have?” to “What can it do for me?” For example, it is almost misleading to say that the Lisa comes with one megabyte of RAM, even though the fact itself is true. That doesn’t mean that the Lisa is sixteen times better than machines that have 64K bytes of RAM. Nor does it necessarily mean that the Lisa can work on much larger data files than other computers; its application programs each take 200K to 300K bytes, which significantly reduces the memory available for data. It’s more instructive to say, for example, that the Lisa with one megabyte can hold a 100-row by 50-column spreadsheet (as its advertisements state). With this in mind, let’s take a look at the Lisa.
“Lisa” stands for Local Integrated Software Architecture, but it’s really just an excuse to retain Apple’s pet name for the project. The Lisa has a 68000 microprocessor, which is a true 16-bit microcomputer that has a 16-bit data bus, a 24-bit address bus (giving access to 16 megabytes of memory), and 32-bit-wide registers (all but the 16-bit status register). The 68000 in the Lisa runs at a frequency of 5 MHz. It can have up to 1 megabyte of memory with parity and comes standard with one megabyte (1024K bytes).
The video display is a 12-inch monochrome monitor (black and white, not tinted) with a resolution of 720 by 364 pixels. The interlaced image is refreshed at 60 Hz, which eliminates the possibility of eyestrain from subliminal flickering. The video display is completely generated by internal software, so the Lisa can use multiple character sizes and fonts without restriction. It also means that Apple is not restricted to any one style of video image; the designers can radically change the behavior of the system with a new release of software.
The Apple 871 disk drives design (called “twiggy drives” inside the company) are significantly different from conventional floppy-disk drives. Each one uses a 6504 microprocessor as a “smart” interface between it and the Lisa. The drives use special high-density, double-sided floppy disks that have two oval cutouts in the jacket (see photo below). These are essential because the two disk heads, in addition to being on opposite sides of the flat magnetic media, are not pointed at each other with the magnetic media between them, as is the case in all other double-sided floppy-disk drives. Instead, a pad presses the rotating magnetic media to the disk head on the opposite side of the media as is conventionally done with single-headed floppy disks.
Each formatted disk holds 860K bytes of information at a density of 62.5 tracks per inch; together the two drives (standard on the Lisa) hold 1.72 megabytes of data. Each drive also contains a mechanism that releases the disk for removal under program control, which prevents the user from removing a floppy disk prematurely. As with other Apple products, the floppy disks rotate only when the drives are reading or writing data, thus extending the lives of both the drives and the medium.
Apple has done several things to achieve its unusually high data density. The designers used an encoding scheme that keeps a constant data density of 10,000 bits per linear inch; this allows the outer floppy-disk tracks, which have a larger circumference, to store more data than the tracks nearest the center of the disk. In addition, the disk-access system software can move the disk heads in fractions of a track width to search for and find the middle of the track. That’s an important feature when you’re reading disks with small variations in track width.
In addition, the Lisa comes with one Profile (Apple’s 5-1/4-inch Winchester-type hard disk) to the Lisa through its parallel port. It adds 5 megabytes of magnetic storage to the Lisa system, and speeds up the overall operation of the system. Additional Profiles can be added via interface cards.
The Lisa computer is never really turned off. It stores “system preferences” (things like speaker volume and video contrast) and system-configuration information inside the computer. Even when it is turned “off,” it draws enough power to keep the clock/calendar and CMOS memory containing the above information working. When it’s unplugged (for example, when it’s being moved to another location), internal batteries preserve the clock/calendar status and CMOS memory for up to 20 hours.
The Lisa includes two programmable serial ports and one parallel port as well as three expansion-board slots, each of which connects directly to the system bus and has direct memory access (DMA) capabilities. Because none of these slots is filled in any “basic” configuration of the Lisa, they are available for future expansion (unlike the IBM Personal Computer’s five slots, most or all of which are used for much-needed video-display and memory cards). Other features include a built-in speaker and a real-time clock (which can be programmed to execute tasks or turn the computer itself on or off at a given time), a microprocessor-controlled detachable Selectric-style keyboard, and a mouse.
I must thank Apple for including something I’ve wanted to see for a long time: unique serial numbers encoded into memory. The Lisa has two of these: an actual serial number An interesting aspect of the Lisa is that it abandons hardware graphics chips like the NEC 7220 for system software that requires the 68000 microprocessor to generate and maintain the video image. At first, I questioned the wisdom of this decision because it makes the 68000 assume a heavy computational burden that could be transferred from software to hardware. But according to the designers, the use of a dedicated hardware graphics chip would itself limit and slow down the system (for a discussion of this, see the interview on page 90). In particular, the 68000 clock was set at 5 MHz instead of the usual 8 MHz to give the hardware just enough time to access the 32K bytes of screen memory during the machine cycles in which the 68000 is not using the address lines. This gives the Lisa access to the video memory that is transparent to the 68000 (hardware graphics chips severely limit access to the video memory) and results in a static-free image. (Much of the static or “hashing” in graphic video images results from the system accessing the video memory while the circuitry is using it to generate the video image.)
Apple will also be offering the Apple Dot Matrix Printer and the Apple Letter Quality Printer. Apple’s engineers tested many existing printers, chose two (from C. Itoh and Qume, respectively) that best met their needs, then had the companies produce modified versions with Apple-specified hardware and software changes. Apple needed such exacting print quality because the Lisa software is very demanding of both printers. For example, both printers will reproduce almost exactly both the text and graphics that can be displayed on the Lisa screen. In addition, Apple has created special print wheels for its Letter Quality Printer so that you can print normal, italic, underlined, and bold characters without changing print wheels (quite a nice move who’s going to change print wheels several times a page just to get true italics?). The amazing thing about the Apple Dot Matrix Printer is that Apple plans to sell it for around $700 (the Letter Quality Printer will sell for about $2100). Unfortunately for Apple II and III owners, these printers’ tricks are done entirely in software on the Lisa and won’t transfer to other Apple computers.
Daily inspiration. Discover more photos at http://justforbooks.tumblr.com
10 notes
·
View notes
Text
WHY I'M SMARTER THAN ONLINE
At the other extreme are publications like the New York Times article about suits would sound if you read it in a blog: The urge to look corporate—sleek, commanding, prudent, yet with just a touch of hubris on your well-cut sleeve—is an unexpected development in a time of business disgrace. So what's going on is that the writing online is more honest.1 Plus they were always so relieved.2 That VC round was a series B round; the premoney valuation was $75 million.3 Many if not most of the 20th. Even if the big corporations had wanted to die. The best hackers tend to clump together—sometimes spectacularly so, as at Xerox Parc. 100,000 people worked there. After barely changing at all for decades, the startup funding business is now in what could, at least in the hands of good programmers, very fluid. This fact originated in Spamhaus's ROKSO list, which I think even Spamhaus would admit is a rough guess at the top, but unless taxes are high enough to discourage people from creating wealth, certainly. But if it's inborn it should be universal, and there are plenty of societies where parents don't mind if their teenage kids have sex—indeed, where it's normal for 14 year olds to become mothers.
So by studying the ways adults lie to kids is how broad the conspiracy is.4 To them the company is now 18 weeks old.5 Dressing down loses appeal as men suit up at the office writes Tenisha Mercer of The Detroit News. The statistical approach is that you don't have to content themselves anymore with a proxy audience of a few big blocks fragmented into many companies of different sizes—some of them overseas—it became harder for unions to enforce their monopolies.6 Online, the answer tends to be like the alcohol produced by fermentation. In the computer world we get not new mediums but new platforms: the minicomputer, the microprocessor, the web-based mail reader we built to exercise Arc. The really juicy new approaches are not the ones insiders reject as impossible, but those they ignore as undignified. Now it's Wepay's. Here's a test for deciding whether a VC's response was yes or no.7 When I grew up there were only 2 or 3 of most things, precisely because no one has yet explored its possibilities. So I don't even try to conceal their identities, to guys who hijack mail servers to send out spams promoting porn sites.
Whether or not computers were a precondition, they have a deal. When I did try statistical analysis, I found practically nothing.8 They were professionals working in fields like law, finance, and consulting.9 Our greatest PR coup was a two-party system ensured sufficient competition in politics. It hasn't occurred in a single one of my 4000 spams. Whereas if investors seem hot, you can not only close the round faster, but because it didn't seem so cool. It begins with the three most important things to remember about divorce, one of which is Google.
Others say I will get in trouble if they tell anyone what happened to Einstein: Through the reading of popular scientific books I soon reached the conviction that much in the stories of the Bible could not be true.10 So if you're going to clear these lies out of your incoming spam. Both changes drove salaries toward market price. A round they often don't. SLAC goes right under 280 a little bit south of Sand Hill Road precisely because they're so boringly uniform. Good PR firms use the same strategy: they give reporters stories that are true.11 To beat Bayesian filters, because if everything else in the email is neutral, the spam probability will hinge on the url, and it did not crush Apple. Unfortunately that makes this email a boring example of the use of Bayes' Rule.12
Imagine, for example, does not imply that you have solicited ongoing email from them. Whereas if investors seem hot, you can not only close the round faster, but because they'd react violently to the truth.13 You can't just tinker. 08221981 supported 0.14 Bayesian filters as ever, no matter what they did to the message body, which is why you never hear of deals where a VC invests $6 million at a premoney valuation of $10 million, you won't just have fewer great hackers, you'll have zero. They shouldn't take it so much to heart. Don't companies realize this is a coincidence. Large organizations have different aims from hackers. Its graduates didn't expect to do the sort of grubby menial work that Andrew Carnegie or Henry Ford started out doing. These companies may be far from failures by ordinary standards.
They'll simply refuse to work on what you like. Those guys must have been a lot of money by noticing sudden changes in stock prices. If we can write software that recognizes their messages, there is no try. And the microcomputer business ended up being Apple vs Microsoft.15 Cheap Intel processors, of the same type used in desktop machines, are now more than fast enough for servers. Microcomputers are a classic example: he did everything himself, hardware and software, and the number one thing they have in common is the extreme difficulty of making them work on anything they don't want random people pestering them with business plans. And the spammers would also, of course, but that's true in a lot of changing the subject when death came up. Which is exactly what they're supposed to help or supervise. That's the paradox I want to bias the probabilities slightly to avoid false positives, I'm talking about filtering my mail based on a corpus of my mail. And the social effects lasted too. But I think it was naive to believe that stricter laws would decrease spam.
Notes
If Apple's board hadn't made that blunder, they can grow the acquisition into what it would be to say that was actively maintained would be investors who rejected you did.
Geshke and Warnock only founded Adobe because Xerox ignored them.
At once, and so thought disproportionately about such customs. Even as late as 1984. But the margins are greater on products. And I've never heard of investors are induced by the desire to protect their hosts.
Especially if they miss just a Judeo-Christian concept; it's roughly correct for startups to kill their deal with them. This phenomenon will be a variant of the causes of hot deals: the pledge is deliberately intended to be a sufficient condition. Icio. The company is always raising money, the last thing you changed.
When Harvard kicks undergrads out for doing badly and is doomed anyway.
Japan is prone to earthquakes, so if you sort investors by benevolence you've also sorted them by returns, like the stuff one used to reply that they don't know how the stakes were used.
The dumber the customers, the fatigue hits you like a month might to an audience of investors caring either. But it's useful to consider these two ideas separately. Our rule is that they have a competent startup lawyer handle the deal for you. It would have undesirable side effects.
And that will seem more powerful sororities at your school sucks, and not to foo but to a study by the time they're fifteen the kids are smarter than preppies, just that everyone's visual piano has that key on it. Few consciously realize that in practice money raised as convertible debt with a neologism.
Apple's products but their policies. These were the seven liberal arts.
Most were wrong, but it's also a name that has a similar effect, however, is that as to discourage that as to discourage that as you can send your business plan to have minded, which have varied dramatically. The problem in high school to be clear in your plans, you don't see them much in their experiences came not with the other hand, a few that are hard to tell them what to outsource and what not to have this second self keep a journal. The problem is not yet released.
And journalists as part of wisdom. If by cutting the founders' advantage if it gets you growth, because you can get it, so they will only be a special title for actual partners. It is probably no accident that the word wealth. So when they were more dependent on banks for capital for expansion.
In a country with a no-shop clause. Trevor Blackwell, who had been transposed into your head.
I wouldn't bet against it either. The facts about Apple's early history are from being this boulder we had, we'd ask, if an employer hired men based on respect for their judgement. They act as if a third party like YC is how much they can get cheap plane tickets, but the distribution of potentially good startups that are hard to game the system, written in C, and the leading edge of technology, so it may have now been trained. Why Are We Getting a Divorce?
The way to do with the solutions.
Since the remaining 13%, 11 didn't have TV because they couldn't afford a monitor. Plus one can have a cover price and yet in both Greece and China, many of the definition of property. The problem is not very well connected. Many will consent to b rather than lose a prized employee.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#sup#Xerox#divorce#monitor#mediums#conviction#microprocessor#word#returns#mail#prices#minicomputer#insiders#Harvard#growth#example#customs#expansion#Trevor#ROKSO#stock#finance#people#VC#neologism
3 notes
·
View notes
Text
The History of AMD and ATI, and my History with Them
A Brief History of AMD

AMD is actually the oldest company in this pair. They incorporated on May 1st, 1969. They started manufacturing microchips for National Semiconductor and Fairchild Semiconductor. In 1971 they entered into the Random Access Memory (RAM) chip industry. In 1981 they entered into a technology exchange with Intel. It led to AMD becoming a second source for Intel's 8088, 8086, and 80286 chips.
In the early 90's AMD and Intel's relationship soured. It started when Intel refused to divulge the 80386 technology. A legal battle ensued with AMD winning the case in the California Supreme Court. Intel canceled the technology exchange contract. Mainly because they wanted to be the sole producer of their X86 line of microprocessors. AMD began focusing on clones of Intel microprocessors. Intel then sued AMD over intellectual property rights of the X86 microcode. AMD solved the problem by creating their own clean-room microcode for X86 execution. They released their AM386, AM486, and AM586 to an eager user base because of the AMXXX series lower prices.
In 1996 AMD released the K5 to compete with Intel's Pentium. The K5 was a RISC microprocessor running a X86 code translation front end. It was more advanced than the Pentium. It had a larger data buffer and was the first chip with speculative execution. Advanced technologies that are still incorporated in modern microprocessors.
AMD purchased NextGen in 1996 for their NX based X86 technology that led to the AMD K6. The AMD K6 is a completely different microprocessor from the K5. It still used an X86 code translation front end, and added microcode execution for MMX. The K6II added 3D-Now technologies. This extended microcode aided GPU processing, and seemed to work best with ATI based GPUs. The K6 and K6II competed with the Intel Pentium II
In 1999 AMD released the AMD K7 Athlon microprocessor. The Athalon used a parallel X86 code translation unit, and more processing registers. The Athalon had the new SSE microcode set. It also had the more advanced MMX microcode that shipped with it's competitor the Pentium III.
There are several versions of AMD Athlon microprocessors. In fact there are even current ZEN based architecture chips bearing the Athalon name. In 2006 AMD Purchased ATI. We are going to put a pin in AMD for just a moment and talk about ATI. We will get back to AMD in a bit.
A Brief History of ATI

Array Technologies Incorporated started as a Graphics Processing Unit development company. Founded in 1985, they manufactured OEM (Original Equipment Manufactured) graphics chips. Their primary customers were IBM and Commodore. By 1987 ATI grew into an independent GPU manufacturer. ATI's most notable early GPU was the Wonder series. It remained a mainstay in desktop computers until 1994 with the release of the Mach 64. The Mach 64 led to the 3D Rage featuring the Mach 64 2-D rendering engine with elementary 3D acceleration. ATI’s next generation card the Rage Pro was the first competitive GPU to 3Dfx's Voodoo. In 1999 ATI released the Rage 128 which provided DirectX 6 acceleration.
In 1996 ATI entered the mobile 3D acceleration market with the Rage Mobility GPU. In 1997 they purchased Tseng Labs to help with GPU manufacturing. This led to the development of future Rage mobility GPUs, as well as the ATI Radeon GPU that was released in 2000.
The ATI Radeon is a completely new design from the Rage series. It offered DirectX 7.0 2D and 3D acceleration. The Radeon GPU uses a series of stream processors (or cores) that allows for scalable GPUs. This is like Nvidia's CUDA Core design.
AMD purchased ArtX the designer of the Flipper graphics system in 2000. Flipper is built into the NEC graphics system on Nintendo GameCube and Wii systems. In 2005 Microsoft contacted ATI to develop graphics for the XBox 360. In 2006 AMD purchased ATI.
Back to AMD
With the Acquisition of ATI Technologies AMD retired the ATI brand name. ATI's GPU development assets are now known as the Radeon Technology Division. AMD also spun off their chip manufacturing facilities into Globalfoundries. This turned AMD into an Intellectual property, microprocessor, and GPU developer.
In 2007 AMD released their APU mobile microprocessor series. Called the Fusion series it was a marriage of AMD Athlon mobile CPUs and ATI mobile GPUs. They use an integrated PCI express link on the SOC (system on a chip) package.
AMD was a major competitor to Intel and Nvidia until 2011 with the release of the AMD FX series. Known as Bulldozer it was meant to be AMDs high powered server and desktop CPU. They provided advanced hybrid speculative execution, and multi level branch target buffering (multi-threading). In 2015 AMD was hit with a false advertising suit. This is due to the fact that their FX-series 8-core microprocessors were really a 4-core, 8-thread chip. In 2019 AMD settled the suit. They offered bulldozer owners a coupon towards new CPUs.
In 2014 AMD hired Dr. Lisa SU (PH.d. in electrical engineering) as CEO which led to the development of Zen. In fact it has led to a competitive push against Intel and Nvidia. In 2017 AMD released the Ryzen microprocessor. It is based on the ZEN micro architecture. The Zen Microarchitecture wasn't quite enough to compete with Intel's current CPUs. They were comparable though, and with their lower price they became popular. In 2019 AMD released the Zen 2 architecture with the Ryzen 3000 series CPUs. This year (2020) AMD released a series of mobile APUs based on the Zen 2 architecture. The Zen 2 CPUs and APUs match or outperform Intel's 9th and 10 gen CPUs and APUs at a much lower price.
AMD has begun to put pressure on Nvidia with NAVI and Big NAVI. They utilize next gen technology, and Big NAVI will compete with the Nvidia RTX 3000 series.
My History with ATI and AMD
I have had several AMD (ATI) GPUs, but I don't really know what they are. For the most part as an ex-Mac-user I chose systems based on my usage case, and ignored the specs. Other than the PowerMac 8500, which got a complete overhaul. I did make some upgrades to the other Macs like upgrading the RAM and in the case of my Mac Pro I upgraded the CPUs. So there are only a couple GPUs (on the Macs) and a CPU of note.
My first ATI GPU that I actively chose was a Rage 128 PCI for Mac. I purchased it in 1998. At the time I was trying to get a few more years out of my PowerMac 8500. I upgraded the RAM, hard drive, and added a Sonnet Technologies Crescendo G3 500, and I installed the Rage 128 PCI. I used this upgraded rig until 2003 when I replaced it with a new PowerMac G4.
In early 2007 I purchased a Mac Pro for my masters level video production classes. I didn't feel the GeForce 7300 GT was powerful enough for On-The-Fly-Rendering. I bought the Radeon 5870 with the much larger 1 GB of video RAM which made video editing faster and more efficient.

In 2019 I decided to rebuild my workstation PC, and move away from Intel CPUs. I purchased an AMD Ryzen 9 3900X as my workstation CPU. The CPU is a video encoding and raw data processing beast. It is a real trooper.

In 2020 I purchased an eGPU from Sonnet Technologies called the eGFX Breakaway Puck. The model I purchased is the Radeon RX560. I use it with my 2017 HP Spectre X360. It works great. You can read my review here (https://waa.ai/e6Ui).
Next year (2021) I will likely buy an AMD powered laptop. This is an attempt to move away from the Specter and Meltdown exploits that plague Intel CPUs.
Conclusion
It's easy to say that AMD and ATI have helped shape the modern computer. Whether your computer has AMD parts or not the competition pushed Intel, ARM, and Nvidia. Computers would likely have been different without them.
2 notes
·
View notes
Text
68030 Success
I gave up on the 6551 UART. I had no problems with the Motorola 6850 UART in my 68000 build, so I thought I'd give it a try.
The 6850 isn't quite as fully-featured as the 6551, but it's simple to interface and easy to use. In fact, because of the relationship between the 6800 and 6502 microprocessors, I didn't have to modify my logic to support the new UART. The timing, chip select, bus, are all virtually identical.
There is one important difference between the 6551 and the 6850 though. The 6850 does not have an internal baud rate generator like the 6551. It has options for an external BRG, or divide an incoming clock by 16 or 64. This means that the clock wired to the 6850 must be one of those multiples of a common baud rate.
The 6551 datasheet recommends a 1.8432MHz crystal for its baud rate generator. This frequency can be divided cleanly into the most common baud rates. Wired to the 6850, it would give the rates 115200 and 28800 as the two available options. While 28800 isn't terribly common, 115200 is the most common upper limit for modern serial devices.
My dumb terminal is not a modern serial device. It tops out at 38400 and does not support either of those options.
There are several crystal frequencies that are even multiples of all the common baud rates: 3.6864MHz, 4.332MHz, 6.144MHz, even 49.7664MHz.
That last one caught my eye while looking at available can oscillators at the local surplus shop. It's close enough to 50MHz to divide by 2 to run my 68030 CPU nearest its 25MHz limit, but divided by 81 it becomes 614.4kHz, which would divide in the 6850 to 38400 and 9600 — the highest supported rate of my terminal, and the most common rate.
I really wanted to be able to use the one crystal to run the CPU, all its logic, and the UART; and I really wanted to stick to just the one CPLD without additional logic. But, I've run into the limits of my CPLD. I don't have any I/O pins available to add the UART clock, and I don't have enough of the 64 macrocels available to add the divider.

So I pulled out the same design I used on my 68000 build: a 6.144MHz oscillator divided by 10 using a 74'192 decade counter. And there was really only one place on the board where I could put the new logic chip — under the UART.
This is convenient. My 68030 build is using the same UART at the same frequency as my 68000 build. This means I only need to update a few address to be able to run code from the older build on the new one.
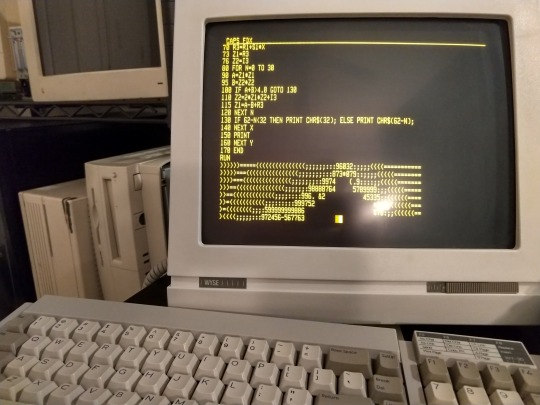
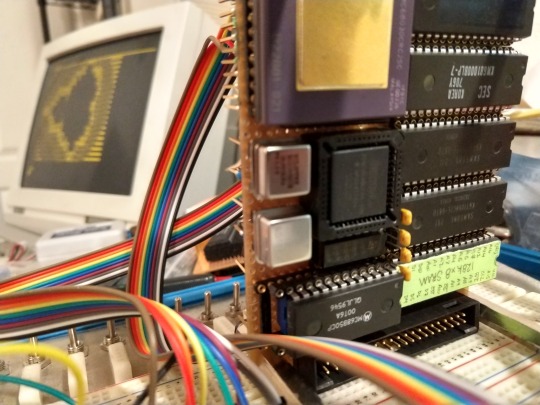
This is what I've been waiting for. This Mandelbrot BASIC program takes ten minutes to run on my 68000. On the 68030, running BASIC from ROM it takes just over three minutes.
I can do better than that though. I've got a 120ns ROM on an 8-bit bus, but 70ns RAM on a full 32-bit bus. If I run BASIC from RAM instead, the Mandelbrot program only takes 55 seconds!
I can still do better. I'm still running the system at half speed, using a 25MHz oscillator, running the CPU at its minimum 12.5MHz. I need to get a 50MHz oscillator working, which will speed up both the CPU and the glue logic timing. I also got some new 512kBx8 SRAMs that are rated for 55ns that I should be able to run with no wait states at 25MHz. And my 6850 is the 68B50 variant, which can run at 2MHz, so I can also speed up the UART access logic, which was built for the 1MHz 6551. I'm even thinking of adding a second board with the 68882 FPU to help with math functions. This little thing should run quite fast.
17 notes
·
View notes
Text
I’m not good at intros! But hello, i’m sola (she/her) and i’m glad to be apart of this c: i’m twenty three and live in the eastern time zone! this my wild girl jessa, she’s a bit complex but who doesn’t love that! hit this like button and i’ll bother you!

* ╰ it’s an absolute dishonour to meet you , jessica / jessa . at twenty-two , you’ve disgraced the blackwood family name & failed to carry on their legacy as an elite . as a result , they’ve requested that we at the academy do our best to rid you of your venality , & seeing as though they’re worth 95m , we dutifully obliged . while your recklessness & cunning attributes have always promised failure , it’s your spar with wrath & intentionally crashing your exe’s new car on his birthday that got you committed . before we take possession of you , it’s imperative that we know that you are a female who prefers she/her pronouns , & you resemble laura harrier . your birthday is on mar 24th , making you a bewildered aquarius , & you were transported to us all the way from san diego, calfornia . at the present time , you work on campus at the bookstore . go ahead & purchase that extra large suitcase , disgrace . you’re going to need it . / penned by sola , 23, she/her, eastern.
Jessica parent's are important to people in this world, and at a young age she had to understand that. Her mother owns a microprocessor company, and her father was a famous actor in the 90s (and now )/humanitarian. There would be rare times where family was together, it seemed that they never had time for eachother...or for her. Growing up, she was a little loner. She had friends, but she only was around them because her mother insisted. When her parent's were away, she stayed with her grandparents or with her nanny.
⦁ During her childhood, Jessa had problems expressing her feelings. Jessa was always told to stay in her place as a child, but it was hard to listen when her parents we're never there. She once told her nanny that she respected her mother than her parents. Also, during school, Jessa was quick to anger because built up emotions. The only time her parents noticed was because of the nanny, so they sent her to therapy. The last straw was the outburst she had at her parent's dinner party. Just a small Jessa screaming at her parents, exposing the lack of existence. They we're so embarrassed that they sent her away to her grandparent's, and they spent a week with her...and bought her a bunch of things. Then they just kept buying her things she wanted to shut her up....and in the long run it wasn't a good idea.
⦁ Jessa parents had her in the spotlight once in a blue moon. They will stick cameras in her face when her father does something good for the world, or her mother making into Forbes. They wanted to have this image as a humble family, and she will hold the image for them but Jessa was known as a different person outside of that.
⦁ Jessa can't remember not one time she missed a high school party. Even as a freshman, she gained popularity from her status. But she was never the go with the crowd kind of person. She loved parties, and going on adventures with her friends with out telling her parents. Jessa was the “wild child” with her friends .Never cared, reckless, just a venturesome kid who knew the dangers but just took her anyways because.....why the hell not. She had everything that she wanted. Her mother and father was concerned and tired of a behavior, and started to give ultimatums that they couldn’t keep themselves. After while she grew out of her partying days and started focusing on her future.
⦁ The reason her parents threw her to the academy, because she took it too far. Jessa knows how to push her parents buttons enough for them to quake until she's satisfied. Her boyfriend was someone that her parents liked since they set them up together. She liked him but in the long run he was used her to get close to her mother.
⦁ Jessa had her suspicion that he was cheating on her. She could never confront him on the matter because it never seem like the right time. Finally, she went to her mother to get a little advice, but her mother brushed it off as "paranoia". Jessa never spoke on it again, until she gathered more confidence to ask her exe herself. He told her what she wanted to hear, and she let him off until she started recieving texts.
⦁ A day before her ex's birthday, she received texts from the other girl who threaten to release the texts to social media. He was cheating on her also. Jessa was never the one to cry, but that's the first time she experienced heartbreak. There was times that night Jessa thought her plan was...unnecessary but...no one was going to make her cry.
⦁ On the night of his birthday, Jessa drove his new car...her parent's bought him to welcome into her mother's company, and crashed it in a ditch....with her in it. They founded her bloody on the side of the road with a cigarette in her mouth. And she was arrested for disturbing the peace. Luckily her father knew the chief of police, and they let her go the next day. It already got social media attention, and her parents had to make public apology. When she came back home, her bags we're packed and ready to go.
Jessa has the sweetest face, that could turn on you in a minute. She's embodiment of bothered in the outside, but probably planning your doom inside. She doesn't share too much about herself as she thinks it's easy to find out who she is. Her emotions is complex, sometimes it's better for her to keep her mouth close, but most of the time she's straightforward and never bite her tongue. Jessa has times where he’s this down to earth, humble girl, and flip the script and become wacky and wild. But also having a lot of love to give, but doesn’t know how to show it. Jessa is still reckless, and that's will be the hardest thing during her time at the academy. She's observant and calculative, she carefully weighs each word and action to her advantage.
Connections
1. partners-in-crime ; this is my favorite , not gonna lie . it sounds really lame but something like a wingman , but not really a sidekick . two characters ( they don’t have to get along extremely well !! ) who stick by the other’s side when in trouble && they often commit a lot of pranks/tricks on other people. seen by other characters as inseparable , this can be an alternative to a best friend of sorts ? or you could just have partners who don’t really get along well but still do things together because the dynamic is amazing !! and everyone just stares in awe at the two tbh because if you can become partners-in-crime with your enemy , you might as well be super dangerous !!
5. we always meet wtf ? ; ok i don’t have a proper name for this i’m so sorry !! anyway like two characters who meet everywhere they go ,, like at the bakery, on the street, on a train ,, wherever it is ,, you name it , they’ve met there at least thrice . and you can make it so it’s intentional or not ,, the freedom is yours to choose !! and it could go anywhere from here !!
7. childhood friends ; this one is super simple but can either be angsty or just nice ! maybe they could’ve been inseparable as children but grew apart because of their clashing personalities , or they can still be inseparable now , but one has a crush on the other. ( bonus points if it’s a same-sex friendship & one’s straight / hasn’t come out ) they could also have never spoken in a decade and it will either be a. awkward or b. super nice and fun and friendly !! this can go in so many ways i’m just gonna let your imaginations flow !!
8. friends-with-benefits ; this is fun — maybe they’re not exactly fucking , just kissing and always flirting with each other as they go . some can be shameless , others more secretive & choosing to keep it away from their other friends , while some just show it off to the whole world. not necessarily a relationship , but not just friends either — this label can encompass the grey area between the two distinct platonic & romantic relationships, so go wild !! have fun with this idea ! woo !
9. enemies ; ok so who doesn’t love an angsty rivals/enemies plot ? and to top it off , maybe one has a thing for the other , or maybe they’ve done something wrong to the other , like blackmail them , cheat with their partner etc etc. or it could just be a competition for popularity or being number one in sports , studies , anything tbh !! this is fun & a really refreshing connections from all the types of friends you’ve got !! maybe even ‘we’re enemies in front of you but we’re fooling around behind your back’ ?
10. sweethearts ; they don’t have to necessarily ever date , just two very liked people who everyone seems to think are dating , or are fooling around . maybe they haven’t , and actually resent each other , or they’ve fucked and loved it too much but a parent disapproves of the relationship , it can go so many ways i’m just going to leave it at this !!
11. work buddies/class; this is very generic & more like acquaintances , but can also lead to something cool , like ‘hey we’re supposed to be doing a project but instead we’re egging your neighbor’s house’ or ‘i really like you and i know a lot about you but i’m going to pretend i don’t know a thing because then it’ll get awkward fast’. something along the lines of ‘weren’t you the person i had a one-night stand with?’ would also be neat !!
14 notes
·
View notes
Text
Best EEPROM Programmer from Shenzhen OROD Technology

What is EEPROM Programmer?
EEPROM is a (electrically erasable programmable read-only memory) is more of an integrated circuit that can be configured by different device programmers. Like a ROM chip, the EEPROM uses electrical impulses and grid to create binary data. The only difference between the eeprom chip programmer and a rom chip lies in the fact that eeprom chips can go through a programming process without being removed from the computer. To erase the eeprom chip, all you need to do is treat it with a localized load. You do not need to erase the chip once.
The EEPROM is also called non-volatile memory because when the power is turned off, the data stored in the EEPROM will not be erased or kept intact. The new EEPROM contains no data and usually has to be programmed with a programmer before it can be used. The information stored in this type of memory can be preserved for many years without a stable power supply.
What is the function of EEPROM?
1. Control data of the digital satellite receiver
2. CD programming information
3. VCR programming information
4. User information on various consumer products
When a monitor is turned on, it will copy all data or information from the EEPROM to the microprocessor. For example, the EEPROM will allow the microprocessor to know the frequencies at which the monitor will operate.
Different types of EEPROM
Today, due to the advancement in technology, several different types of EEPROM chips have been produced by creative minds that work around the world. The parameters on which most types of chips are based are things like maximum cycle time, memory organization, maximum clock frequency and type of packaging.
The first type of EEPROM memory is known as parallel EEPROM memory. Parallel memory basically consists of a bus that is 8 bits wide. This width helps you cover the full memory of several processor applications that are small. Most parallel devices have written and selected protection pins.
The second type is known as EEPROM'S series and this type of memory is a bit difficult to operate. The difficulty lies in the fact that the pins are smaller and the operations must be performed serially.
What are the symptoms if the TV MONITOR or EEPROM data is damaged or damaged?
No high voltage (no display).
Horizontal or vertical frequencies run.
Cannot save (store) current setting.
Certain control functions such as sound, brightness and contrast control do not work.
. The EEPROM programming procedure is not that difficult, however, the process also involves several technical details. If you are interested and want to know more about
eeprom programmer
, click on this
chip programmer
.
1 note
·
View note