#all software is Spyware
Explore tagged Tumblr posts
Text

They know everything you do. My mother is looking at getting another car, so they are targeting me with used car adds now. Privacy is a modern invention, and we are letting the information age destroy it.
0 notes
Text
Cobwebs Spy Software Locks Onto Protesters: Israeli Social Media Mining homeland security contractor
youtube

#cobwebs#spy#software#protest#privacy#data privacy#online privacy#internet privacy#invasion of privacy#social networks#social media#internet#class war#all cops are bastards#all cops are bad#all cops are pigs#israel#israhell#homeland security#spyware#infotech#information technology#i.t.#it#israel is a terrorist state#israel is committing genocide#israeli war crimes#israel is an apartheid state#israel is a war criminal#benjamin netanyahu
2 notes
·
View notes
Text
25 ways to be a little more punk in 2025
Cut fast fashion - buy used, learn to mend and/or make your own clothes, buy fewer clothes less often so you can save up for ethically made quality
Cancel subscriptions - relearn how to pirate media, spend $10/month buying a digital album from a small artist instead of on Spotify, stream on free services since the paid ones make you watch ads anyway
Green your community - there's lots of ways to do this, like seedbombing or joining a community garden or organizing neighborhood trash pickups
Be kind - stop to give directions, check on stopped cars, smile at kids, let people cut you in line, offer to get stuff off the high shelf, hold the door, ask people if they're okay
Intervene - learn bystander intervention techniques and be prepared to use them, even if it feels awkward
Get closer to your food - grow it yourself, can and preserve it, buy from a farmstand, learn where it's from, go fishing, make it from scratch, learn a new ingredient
Use opensource software - try LibreOffice, try Reaper, learn Linux, use a free Photoshop clone. The next time an app tries to force you to pay, look to see if there's an opensource alternative
Make less trash - start a compost, be mindful of packaging, find another use for that plastic, make it a challenge for yourself!
Get involved in local politics - show up at meetings for city council, the zoning commission, the park district, school boards; fight the NIMBYs that always show up and force them to focus on the things impacting the most vulnerable folks in your community
DIY > fashion - shake off the obsession with pristine presentation that you've been taught! Cut your own hair, use homemade cosmetics, exchange mani/pedis with friends, make your own jewelry, duct tape those broken headphones!
Ditch Google - Chromium browsers (which is almost all of them) are now bloated spyware, and Google search sucks now, so why not finally make the jump to Firefox and another search like DuckDuckGo? Or put the Wikipedia app on your phone and look things up there?
Forage - learn about local edible plants and how to safely and sustainably harvest them or go find fruit trees and such accessible to the public.
Volunteer - every week tutoring at the library or once a month at the humane society or twice a year serving food at the soup kitchen, you can find something that matches your availability
Help your neighbors - which means you have to meet them first and find out how you can help (including your unhoused neighbors), like elderly or disabled folks that might need help with yardwork or who that escape artist dog belongs to or whether the police have been hassling people sleeping rough
Fix stuff - the next time something breaks (a small appliance, an electronic, a piece of furniture, etc.), see if you can figure out what's wrong with it, if there are tutorials on fixing it, or if you can order a replacement part from the manufacturer instead of trashing the whole thing
Mix up your transit - find out what's walkable, try biking instead of driving, try public transit and complain to the city if it sucks, take a train instead of a plane, start a carpool at work
Engage in the arts - go see a local play, check out an art gallery or a small museum, buy art from the farmer's market
Go to the library - to check out a book or a movie or a CD, to use the computers or the printer, to find out if they have other weird rentals like a seed library or luggage, to use meeting space, to file your taxes, to take a class, to ask question
Listen local - see what's happening at local music venues or other events where local musicians will be performing, stop for buskers, find a favorite artist, and support them
Buy local - it's less convenient than online shopping or going to a big box store that sells everything, but try buying what you can from small local shops in your area
Become unmarketable - there are a lot of ways you can disrupt your online marketing surveillance, including buying less, using decoy emails, deleting or removing permissions from apps that spy on you, checking your privacy settings, not clicking advertising links, and...
Use cash - go to the bank and take out cash instead of using your credit card or e-payment for everything! It's better on small businesses and it's untraceable
Give what you can - as capitalism churns on, normal shmucks have less and less, so think about what you can give (time, money, skills, space, stuff) and how it will make the most impact
Talk about wages - with your coworkers, with your friends, while unionizing! Stop thinking about wages as a measure of your worth and talk about whether or not the bosses are paying fairly for the labor they receive
Think about wealthflow - there are a thousand little mechanisms that corporations and billionaires use to capture wealth from the lower class: fees for transactions, interest, vendor platforms, subscriptions, and more. Start thinking about where your money goes, how and where it's getting captured and removed from our class, and where you have the ability to cut off the flow and pass cash directly to your fellow working class people
52K notes
·
View notes
Text
i NEEDED to start learning pine phone shit YESTERDAY.
#im tired of google im tired of ai im tired of cameras im tired a people fucking SPYING ON ME ALL THE TIME#WHY IS ALL SOFTWARE SPYWARE NOW#im so tired and linux is my only escape
0 notes
Note
After seeing your weatherbugapp reblog i installed duckduckgo and tried it.
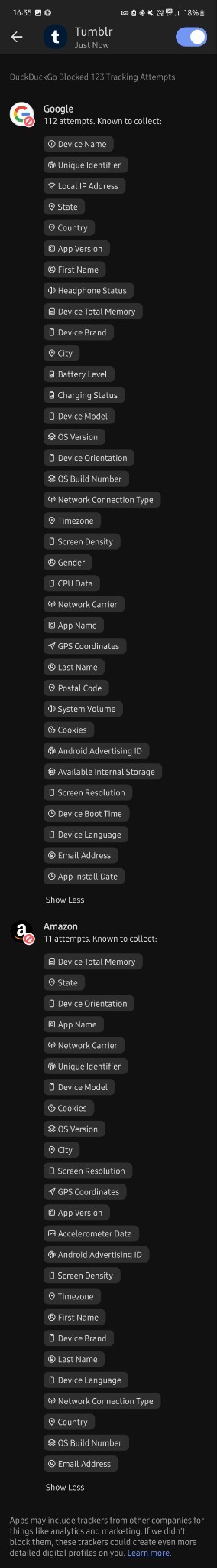
I don't know much about technology tbh but i downloaded this app less than 30 mins ago and in that time google tried to track me 112 times?? And they tried to collect finger prints? And my first and last name? And my gender? And my country, state and city? My gps coordinates? My postal code? My network carrier? My fricking battery level for whatever reason? Can you please tell me if this is normal at all, because i'm freaking out right now. I just turned 18 and started using mobile banking and stuff and this shit scares me
Why tf does it need to know my screen density???my system volume????my charging status????? What tf are they cooking
Now it's at 476 tracking attempts bro???? barely 5 mins passed.....
I condensed your three asks into one for readability!
And yeah, I'm very far from an expert about any of this, but as far as I know that's just. Normal. That's the normal amount of spying they're doing on your phone. I assume the numbers we see are to some extent because having been foiled, a lot of these scripts try repeatedly, since I can't imagine what use thousands of trackers per phone would be even to the great aggregators.
Tracking the phone stuff like screen resolution and battery level is because (apart from that definitely not being considered remotely 'private' so it's Free Real Estate) in aggregate that data can be used to track what phone use patterns are like on a demographic scale and therefore. Where the smart money is.
Almost all of this is getting sold in bulk for ad targeting and market analysis. This does presumably make it very hard to notice when like. Actually important stuff is being spied on, which is why I feel better about Having Apps with the duckduckgo app blocker thing.
My bank's app reportedly sells data to a couple aggregators including Google. Not like, my banking info, but it's still so offensive on principle that I avoid using the app unless I have to, and force stop it afterward.
The patterns that show up on the weekly duckduckgo blocker report are interesting. Hoopla attempts about two orders of magnitude more tracking than Libby, which makes sense because they're a commercial streaming service libraries pay by the unit for access, while Libby is a content management software run by a corporation that values its certification as a 'B' company--that is, one invested in the public good that can be trusted. The cleanness of their brand is a great deal of its value, so they have to care about their image and be a little more scrupulous.
Which doesn't mean not being a little bit spyware, because everything is spyware now. Something else I've noticed is that in terms of free game apps, the polished professional stuff is now much more invasive than the random kinda janky thing someone just threw together.
Back in the day you tended to expect the opposite, because spyware was a marginal shifty profit-margin with too narrow a revenue stream to be worth more to an established brand than their reputation, but now that everyone does it there's not a lot of reputation cost and refraining would be sacrificing a potential revenue stream, which is Irresponsible Conduct for a corporation.
While meanwhile 'developing a free game app to put on the game store' is something a person can do for free with the hardware they already have for home use, as a hobby or practice or to put on their coding resume. So while such apps absolutely can be malicious and more dangerous when they are than The Big Brand, they can also be neutral in a way commercial stuff no longer is. Wild world.
But yeah for the most part as far as I can make out, these are just The Commercial Panopticon, operating as intended. It's gross but it probably doesn't indicate anything dangerous on an individual level.
56 notes
·
View notes
Text
Windows 11 and the Last Straw
Bit of a rant coming up. TL;DR I'm tired of Microsoft, so I'm moving to Linux. After Microsoft's announcement of "Recall" and their plans to further push Copilot as some kind of defining feature of the OS, I'm finally done. I feel like that frog in the boiling water analogy, but I'm noticing the bubbles starting to form and it's time to hop out.
The corporate tech sector recently has been such a disaster full of blind bandwagon hopping (NFTs, ethically dubious "AI" datasets trained on artwork scraped off the net, and creative apps trying to incorporate features that feed off of those datasets). Each and every time it feels like insult to injury toward the arts in general. The out of touch CEOs and tech billionaires behind all this don't understand art, they don't value art, and they never will.
Thankfully, I have a choice. I don't have to let Microsoft feature-creep corporate spyware into my PC. I don't have to let them waste space and CPU cycles on a glorified chatbot that wants me to press the "make art" button. I'm moving to Linux, and I've been inadvertently prepping myself to do it for over a decade now.
I like testing out software: operating systems, web apps, anything really, but especially art programs. Over the years, the open-source community has passionately and tirelessly developed projects like Krita, Inkscape, and Blender into powerhouses that can actually compete in their spaces. All for free, for artists who just want to make things. These are people, real human beings, that care about art and creativity. And every step of the way while Microsoft et al began rotting from the inside, FOSS flourished and only got better. They've more than earned trust from me.
I'm not announcing my move to Linux just to be dramatic and stick it to the man (although it does feel cathartic, haha). I'm going to be using Krita, Inkscape, GIMP, and Blender for all my art once I make the leap, and I'm going to share my experiences here! Maybe it'll help other artists in the long run! I'm honestly excited about it. I worked on the most recent page of Everblue entirely in Krita, and it was a dream how well it worked for me.
Addendum: I'm aware that Microsoft says things like, "Copilot is optional," "Recall is offline, it doesn't upload or harvest your data," "You can turn all these things off." Uh-huh. All that is only true until it isn't. One day Microsoft will take the user's choice away like they've done so many times before. Fool me once, etc.
118 notes
·
View notes
Text

PSA! THERE IS MALWARE ON YAYTEXT!
I'm not fully sure just how relevant this will be, but if anyone else uses yaytext to fancify their text with unicode, please be aware that there is now malware on the yaytext website ( yaytext.com ). it has been on there for at least a week now, so if you have gone onto the site, you might have been infected!
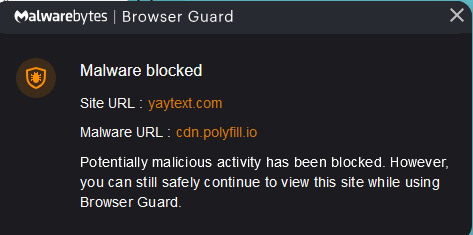
WHAT NOW? IF YOU HAVE VISITED YAYTEXT:
first, run a malware scan on your computer. you can do this for FREE with malwarebytes, bitdefender, or kaspersky*. you can find the free versions of these antivirus softwares on their respective websites, and I will link them below for convenience.
after you run the malware scan (hopefully you are not infected!), add the respective browser guard to your browser. as you can see by my screenshot, I use Malwarebytes' broswer guard. if you decide to use their browser guard too, you will still be able to safely use yaytext.
WHERE ELSE DO I GO?
you should assume that yaytext IS NOT safe to use for the time being! there are plenty of other unicode generators out there, however, so you don't have any disruption with your aesthetics.
some alternatives are:
fontspace font generator
lingojam text generator
fontalic
I have just checked all of these sites and none of them have malware on them at this time.
ANTIMALWARE SCANNING
MalwareBytes - free version BitDefender - free version Kaspersky* - free version
*note that Kaspersky is being banned in the U.S. for being a Russian company. The ban is over worries that Russia could use the AV as spyware in the U.S., because the Kremlin can force any company in Russia to share all of their data with them. Despite this, Kaspersky is a top contending cybersecurity research company. If you are not comfortable using Kaspersky, studies have shown that BitDefender provides near equivalent results. source: i am getting my degree in cybersecurity lol
74 notes
·
View notes
Text
Matrix
E chi me lo doveva dire che sarebbe stato Zuckemberg ad avvisarmi che i servizi segreti mi stavano spiando? Potremmo chiamarlo il “paradosso Matrix”.
Venerdì scorso ero in treno, in viaggio da Roma a Bologna. Mi arriva un messaggio su Whatsapp: “Ciao Luca. Informazioni importanti sulla sicurezza. Questa è una comunicazione di sistema”. Penso subito a quelle truffe del tipo “papà ho perso il telefono, mi mandi i soldi?”. Scrollo, e mano mano capisco che non è uno scherzo. Meta, la multinazionale che gestisce i vari social e wathsapp, mi informa che il mio telefono ha subito un “attacco” da uno spyware molto sofisticato, che ha avuto accesso ad ogni contenuto presente all’interno della memoria, “mettendo a rischio la mia privacy”. Meta mi consiglia di cambiare telefono, perché lo spyware è cosi potente da non poter essere rimosso. Ma poi mi dice che se sono “un giornalista, o un attivista della società civile”, potrei trovare interessante rivolgermi a CitizenLab, per saperne di più, e mi mette un link per contattarli. Alle 18 sono in una casa e mi connetto in videocall con questo centro di ricerca basato all’Università di Toronto. Efficentissimi, mi spiegano che l’attacco informatico “è di alto livello”, che il tipo di software utilizzato è dei più sofisticati al mondo, ed è in uso solo ad agenzie governative. Si chiama “Paragon”, prodotto dalla Pragon Solution israeliana, e come dichiara la società stessa “fornito all’amministrazione Usa e ai suoi governi alleati”. I “target” di questa operazione mi spiegano, sono 90, sparsi in diversi paesi, e sono “giornalisti e attivisti sociali”. CitizenLab offre il suo supporto alle vittime di questa storia, ma per il telefono non c’è niente da fare: bisogna proprio buttarlo. Me l’ha ammazzato Paragon, ed era quasi nuovo ( mannaggia ).
Ora lo stanno dissezionando, per trovare tutte le tracce dell’incursione spiona. Ovviamente a me risulta chiarissimo il motivo di tanto costoso e morboso attenzionamento: chi si impegna nel soccorso civile in mare, e nella costruzione di reti di aiuto alle persone migranti, incarcerate nei lager libici o deportate nel deserto dalle autorità tunisine, è spesso trattato come un criminale, un “favoreggiatore dell’immigrazione clandestina”. Ma se tutta la narrazione sulla “lotta agli scafisti su tutto il globo terraqueo” si è sciolta nella pozzanghera putrida della gestione del caso Almasri, anche questa della cyberwar contro soccorritori e giornalisti d’inchiesta sgraditi al governo, promette bene.
In fondo siamo tutti spiati, ripresi, fotografati, registrati. Non servono i servizi segreti, bastano le protesi ipertecnologiche delle quali sembra che non possiamo più fare a meno. Siamo, come in Matrix, sempre connessi alla “macchina”, che ci inietta realtà virtuali funzionali al potere, dai magici effetti onirici sulle menti e dagli effetti anestetici sui corpi. Ma tutto questo strapotere sulle moltitudini che abitano questa parte di mondo, poi rivela come in questo caso, i suoi lati deboli: Matrix è anche la multinazionale della comunicazione, in competizione di “affidabilità per il cliente” con tante altre sul mercato, che ti manda l’alert per avvisarti che sei spiato dai servizi. Che ti consiglia anche di rivolgerti a chi, nel mondo degli spiati, si sta organizzando non solo per scoprire quando ti spiano, ma anche per trovare soluzioni tecnologiche che possano impedirlo. E quindi, io che non conoscevo CitizenLab di Toronto, mi sono fatto dei nuovi amici, alleati nella lotta contro le macchine.
Ma in fondo, cosa possono essere se non macchine, senz’anima né vergogna, coloro che con la scusa della “ragion di Stato”, fanno morire degli innocenti nel mar mediterraneo, o li condannano ad un inferno come quello che hanno ideato e costruito in Libia? Chi, se non ciniche macchine, si presenta davanti al paese per rispondere della incresciosa vicenda di un torturatore fatto fuggire e addirittura accompagnato al suo posto di lavoro in pompa magna, e in mezzo ad una montagna di ridicole bugie, non trova nemmeno il coraggio di dire che quei torturati, quelle ragazze stuprate, quei cadaveri pronti per le fosse comuni, sono inacettabili, chiunque ne sia il responsabile e qualunque sia la ragione di stato o non di stato?
Siamo dentro Matrix certo, e siamo un’anomalia. Siamo quelli della pillola rossa, e dunque tanti agenti Smith ci spiano, ci pedinano, orchestrano provocazioni per fermarci. Ma non ce la fanno, questo è il punto fondamentale. La loro costruzione del Male, ha difronte una “cospirazione del bene” che li preoccupa, che piano piano si allarga.
Ragionevolmente, ma davvero spiare a questo livello, dei giornalisti e degli attivisti che praticano la solidarietà, è questione di “sicurezza nazionale”? Ma chi ci crede? Forse, nel nostro caso, siamo anche in presenza di una Matrix, ma all’italiana. Una “Amatrixiana”. Ci scommetterei che quelli che si sono fatti beccare nell’operazione Paragon, sono i nostri. Luca Casarini, Facebook
23 notes
·
View notes
Text
I don't really want to get in another spat with communist tumblr so I'll just say this here - the weird part of posts like this one to me is the lack of engagement with the actual criticism of Red Star OS (that it makes a mockery of all the principles behind Linux by being spyware for the North Korean government)
Most people who follow cybersecurity even distantly will acknowledge that the DPRK punches far above its weight in software and is only a step behind players like the US and China in terms of their ability to execute cyberattacks. North Korea is impressively sophisticated, especially given its isolation!
And I also think it's fair to say that the sanctions on North Korea and its continued marginalization aren't helping anything - they aren't helping the North Korean people or the world.
But it seems... unserious, to say the least, to make that point without engaging with the fact that the government exercises a tremendous and unacceptable level of control over its citizens, especially given that communists will (rightfully) protest far milder restrictions in the West.
#discourse#politics#do me a favor and don't jump onto that post from this one#not looking to bother the op#feel free to argue with me here tho
76 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
24 notes
·
View notes
Note
forsaken killer concept
Spyware
-# (from Databrawl https://www.roblox.com/games/1079644652/Databrawl)

Description: A rare variety of computer corruption that specializes in espionage and stealthy takedowns. This particular software was known for playing for both sides in the Great Databrawl of 2017, but disappeared before its trial in the Royal Court. It deceives survivors using virtually-flawless cloaking technology and impeccable disguise holograms.
Stats
- Difficulty: ⭐ ⭐ ⭐ - Health: 950
Walkspeed: 11 - Running Speed: 26 - Stamina: 110
Passives
Right Behind You - Spyware's terror radius is naturally smaller than other killers'.
Abilities
Stab (LMB) - Spyware thrusts its knife forwards, stabbing a survivor. (2 Damage, Small Hitbox, but >1 seconds of cooldown.) Cloak - Spyware goes almost fully transparent, and its terror radius is completely removed. Fortunately, survivors can faintly see the glow of its visor. Disguise Tool - Spyware chooses to disguise as one of the survivors. As with Cloak, your terror radius is silenced when your disguise is up. When Stab is used, the disguise will break, and Spyware's true form will be revealed. Keylog - Spyware taps into the generators around the map, revealing the location of all survivors within a 15 stud radius of each generator.
thoughts?
Huh. Interesting. Very interesting. Not familiar with the original media though unfortunately.
12 notes
·
View notes
Text
It really is spectacular how much you don't realize a situation was bad until you leave it. I'm about 13 months removed from my old job now, and it came up in conversation with one of my direct reports. She commented jokingly about the security cameras we have, and I explained to her how my old company had forced software onto everyone's computers that they insisted was only a "tool" to help identify "processes that could benefit from efficiencies" but was, unsurprisingly, essentially spyware that they used to harass and terminate people for not spending every waking second of the day working. It was some AI-assisted nightmare that would begin recording if you hadn't clicked your mouse between screens or typed in 120 seconds. It logged everything you typed, whether you sent/posted it or not. It had a set "idea" of tasks it deemed value add or unproductive. It did not account for meetings or phone calls, it did not account for certain external and internal sites that were 100% job related. If you did not score a 97% average "productivity up" time at the end of the week, you were admonished. Yes, you should always assume your employer is "watching" but I cannot describe to you what it feels like to not only know that but to have that data rubbed in your face and to be made to feel like human dirt because you were sick or had a bad day or simply had a bunch of tasks that the system wasn't smart enough to deem productive. The irony of them telling me that I should utilize the company therapist/take a walk/stretch to cure the crippling depression I was experiencing at that job when their own software would punish me for not spending that time working. I know this kind of thing isn't unheard of with remote jobs, and obviously if someone is playing WoW all day every day instead of working then it's a problem. But most places you would hope would only look into that data if someone was really falling apart or you suspected like, illicit behavior. Instead they micromanaged everyone to death, uplifted the bootlickers and encouraged a culture of surveillance. I made a joke about how I still sometimes find myself frantically clicking around on my system at work as a reflex, and she was like "....dude, that's literally inhumane and I think you might be mildly traumatized." And you know what? She's probably not wrong! I remember always feeling crazy talking to friends in other jobs who were just like "yeah as long as you do your job description and aren't downloading porn to the work laptop no one really cares what you're doing." But I stayed because of my warped sense of self worth being tied to my salary and look what it got me. Yes, yes, it lead me to what is now a very good place but I also feel like... sometimes you do not need to be thankful for suffering. Sometimes it was just Bad.
#maybe one day i'll feel up to telling the full story about how i quit in spectacular fashion#because it was in fact related to this particular productivity program lol
21 notes
·
View notes
Note
why linux?
are you asking me why I use it as an operating system or why I said I'd name an adopted cat this. the first answer is because I grew up on it and I grew up on it because my software engineer dad had it installed on all computers of the house because he hates windows and considers it barely usable spyware. if you're asking why I'd name a cat that Why Not. the cats I have rn are called Koko and Pinpin. the cat we had before that was named Titi. that's as normal as a cat name as I would ever come up with. it's important to know I would only call Linux a mother cat whose kittens I could adopt because the joke is "mother Linux and her baby operating systems Debian and Ubuntu".
15 notes
·
View notes
Text
Iran has been hacking into private security cameras across Israel to gather intelligence and improve the accuracy of missile strikes.
Israeli cyber security experts cited by Bloomberg on 20 June confirmed the Islamic Republic’s use of cyber espionage.
“We know that in the past two or three days, the Iranians have been trying to connect to cameras to understand what happened and where their missiles hit to improve their precision,” said Refael Franco, the former deputy director general of the Israel National Cyber Directorate (INCD).
A spokesman for INCD said, “We’ve seen attempts throughout the war, and those attempts are being renewed now.”
Gaby Portnoy, another INCD official, said hacking of security cameras was also carried out by Hamas ahead of Operation Al-Aqsa Flood in October 2023.
These cyber operations took place over the years, according to Portnoy, who also noted Russia’s use of the method during the war in Ukraine.
Earlier this week, a former Israeli cybersecurity official warned Israelis on a radio broadcast to turn off all home security cameras or change their passwords.
Cyberwarfare has emerged as a leading tactic in many world conflicts and is particularly used very commonly by Israel, which is known for its infamous spyware software and hackers.
3 notes
·
View notes
Text
Posting my Yandere simulator idea here because I felt salty for waiting an hour on r/osana, only for it not to get attention >:(
Yeah, call me petty, and impatient but c'mon man, I wasted 1 hour writing this skskksksks- and I also want to quickly hear people's ideas and suggestion soooo-
---------------------------------------------------------------------------
𝙈𝙮 𝙞𝙙𝙚𝙖 𝙛𝙤𝙧 𝙩𝙝𝙚 𝙎𝙩𝙖𝙡𝙠𝙞𝙣𝙜 𝙈𝙚𝙩𝙝𝙤𝙙
Inspired by u/LuckyLyre's idea where instead of Info-san saying who the rival is, and telling us instructions on how to kill them.
What if We, The player, had the option to collect information about the rivals, and senpai by stalking them?
Like think of it like this, on the start of the game, You 𝘿𝙊𝙉'𝙏 know anyone other than their names, the rumors you've heard about them, or what club they're in. Hell, you don't even know much about senpai, or who your next Rival would be. You kinda just have to figure out as the week passes.
𝘕𝘰𝘸 𝘛𝘏𝘐𝘚 𝘪𝘴 𝘸𝘩𝘦𝘳𝘦 𝘵𝘩𝘦 𝘧𝘶𝘯 𝘱𝘢𝘳𝘵 𝘣𝘦𝘨𝘪𝘯𝘴, 𝘛𝘩𝘦𝘳𝘦 𝘢𝘳𝘦 𝘥𝘪𝘧𝘧𝘦𝘳𝘦𝘯𝘵 𝘸𝘢𝘺𝘴 𝘵𝘰 𝘴𝘵𝘢𝘭𝘬 𝘱𝘦𝘰𝘱𝘭𝘦.
You can either do 𝙎𝙪𝙧𝙫𝙚𝙞𝙡𝙡𝙖𝙣𝙘𝙚 𝙎𝙩𝙖𝙡𝙠𝙞𝙣𝙜. You know, by following the individual around, even following them outside of school. Observing what places they like, and avoid. Secretly eavesdropping them arguing on their phone. Breaking, and entering into the individuals house without them knowing. Look through their private journal. Rummaging through their bag, and lockers, and even try stealing their valuable stuff. Breaking and entering again- So on, and so forth.
On the other hand, you can try 𝘾𝙮𝙗𝙚𝙧 𝙎𝙩𝙖𝙡𝙠𝙞𝙣𝙜, where you stalk the individual on the internet. You know the drill. Look into what hobbies they're in, complaints about life, and their usual posts. Or try Installing a spyware/tracking software on their devices. Then, look into their private account, and maybe try hacking it to see some private information. You can even dm the individual's personal hater, or creepy fan to join forces with you, because yeah, why not🤷 You can blackmail, doxxed, expose the individual for their nasty work, or befriend some of them, and just be a toxic person while still remaining charismatic, and seemingly friendly to manipulate, and let them do dirty work for you lol.
( Also, I'm not sure on how Ayano would know how to doxxed, or hack someone since in this concept/method, info-chan's existence is completely 𝙧𝙚𝙢𝙤𝙫𝙚𝙙 because i thought she was unnecessary lol, so feel free to tell me ideas me in the comments, It'd be a huge help! )
Anyways- 𝘼𝙣𝙤𝙩𝙝𝙚𝙧 𝙎𝙩𝙖𝙡𝙠𝙞𝙣𝙜 𝙄𝙙𝙚𝙖 is you could try looking into the rumors/ gossips of the certain individual. Ok, alright, i know this isn't really stalking, but I thought it'd be a fun addition.
Obviously, you don't have to talk, and ask about the individual's info all the time, but you can sneakily add them in the conversation without the person knowing because yeah, ✨charisma✨, and the person would slowly go through the gossips they heard, what they saw the individual do, or just bad mouth about them idk lol.
And now after gathering all the information, you get to use your phone, notebook, or the board thing at home to document on what you discovered, and how this could possibly be of help to you, like you're some some kind of detective investigating a crime scene lol. ( Well, you don't really have to write it manually, the game will handle that for you lol, so whenever you discover a new information, it will automatically update your phone, or notebook sksks )
( Also, My idea for the notebook/phone system is kinda the same as the 1980's mode, except it's more vague about the instructions you're given, and you have to explore the school to know what it means Plus, I thought it’d be fire if the notebook had sketches/ drawings in it suggesting ideas on how to kill, while still not saying exactly how to. Like drawing 'osana's hair getting stuck in something' Type of stuff
And you know what? these drawings would play a HUGE factor of showing Ayano's sanity. Like just imagine early-on the game, the drawings looks innocent, and simple, just a rough drawing of an object here and there, But as you kill more, and more people, the drawings gets more detailed, more unhinged and more unsettling. Idkk lol, just a fun idea hehehehe )
Now back to the topic of stalking! How does this help in identifying the rivals? 𝘽𝙮 𝙤𝙗𝙨𝙚𝙧𝙫𝙞𝙣𝙜 𝙎𝙚𝙣𝙥𝙖𝙞, 𝙤𝙛 𝙘𝙤𝙪𝙧𝙨𝙚!
You'll learn who he talks to the most, and just process the info about the girls, and distinguish them from the actual rivals. Like- Didn't you just observe the way that lady just twirl their hair as they speak to senpai? or the way other lady puts on their lipstick, and makes high pitch screeches as senpai enters the room? Oh? What's that? The lady who was violents moments ago is now looking like an angel infront of senpai? And the stoic, and stubborn know-it-all is smiling gently whenever senpai praise them?? What do you mean the very sad, depressed girl is now beaming with sunshines, and rainbow whenever senpai ever slightly walk near them? Pssshht, there's no way they're the rivals, amirite guys😊😊?
Yeahhhhh, it's kinda easy spotting who the rival is because i didn't want this to be too complicated, but to add challenge to this, there are other ladies who are flocking in senpai's way who AREN't rivals, but just happen to have a crush on senpai. THE REAL RIVALS are the person who makes their first move, and ACTUALLY TALKS TO HIM SKSKS
I know this might sound too complex for the game, but I honestly prefer it this way because it makes me feel smart, and it rewards me for gathering info. It also gives you a consequences, like imagine wrongfully targeting some girl, and getting exposed for it💀 lol
The BACKLASH you have to deal with would be wilddd
𝘼𝙣𝙮𝙬𝙖𝙮𝙨- 𝘿𝙤 𝙮𝙤𝙪 𝙜𝙪𝙮𝙨 𝙝𝙖𝙫𝙚 𝙖𝙣𝙮 𝙗𝙚𝙩𝙩𝙚𝙧 𝙞𝙙𝙚𝙖𝙨/𝙨𝙪𝙜𝙜𝙚𝙨𝙩𝙞𝙤𝙣𝙨 𝙩𝙝𝙖𝙣 𝙢𝙞𝙣𝙚? 𝘽𝙚𝙘𝙖𝙪𝙨𝙚 𝙄 𝙬𝙤𝙪𝙡𝙙 𝙡𝙤𝙫𝙚 𝙩𝙤 𝙝𝙚𝙖𝙧 𝙮𝙤𝙪𝙧 𝙤𝙥𝙞𝙣𝙞𝙤𝙣𝙨, 𝙖𝙣𝙙 𝙘𝙤𝙣𝙘𝙚𝙥𝙩𝙨 𝙖𝙗𝙤𝙪𝙩 𝙨𝙩𝙖𝙡𝙠𝙞𝙣𝙜 𝙢𝙚𝙩𝙝𝙤𝙙, 𝙖𝙣𝙙 𝙩𝙝𝙚 𝙣𝙤𝙩𝙚𝙗𝙤𝙤𝙠 𝙨𝙮𝙨𝙩𝙚𝙢 !!
---------------------------------------------------------------------------
I just copy and pasted what I said there because yeahhhhhhhh- also please do leave suggestions, I'm desperate ya'll😭😭
#ALSO FORGIVE ME ROTMHS FANS#I'LL BE BACK DONT WORRY SKSKSK#LET ME FOCUS ON MY OTHER HYPERFIXATION FOR LIKE- 1 POST KSKSKSKKS#yandere#yandere simulator#ayano aishi#yansim
7 notes
·
View notes
Text
Trump's second term is only three and a half weeks old. The press, politicians, and many Americans seem to have forgotten what happened two weeks ago. Here is a quick refresher of what Trump or his minions have done in 25 days:
Pardoned 1,500 insurrectionists who assisted Trump in his first attempted coup.
Converted the DOJ into his political hit squad by opening investigations into members of the DOJ, FBI, Congress, and state prosecutors’ offices who attempted to hold Trump to account for his crimes.
Fired a dozen inspectors general, whose job it is to identify fraud and corruption and to serve as a check on abuses of power by the president.
Fired dozens of prosecutors and FBI agents who worked on criminal cases relating to Trump
Fired dozens of prosecutors who worked on criminal cases against January 6 insurrectionists
Opened investigations into thousands of FBI agents who worked on cases against January 6 insurrectionists
Disbanded the FBI the group of agents designed to prevent foreign election interference in the US
Disbanded the DOJ group of prosecutors targeting Russian oligarchs’ criminal activity affecting the US
Fired the chairs and members of the National Labor Relations Board, the Equal Opportunity Employment Commission, and the Federal Election Commission and refused to replace them, effectively shutting down those independent boards in violation of statute
Shut down and defunded the Consumer Financial Protection Bureau
Shut down and defunded USAID by placing virtually the entire staff of the agency on leave
Impounded billions of dollars of grants appropriated by Congress to USAID, National Institutes of Health, Department of Education, and the EPA, all in violation of Article I of the Constitution, which grants Congress the power to make appropriations
Allowed a group of hackers to seize control of large swaths of the federal government’s computer network by attaching unauthorized servers, changing and creating new computer code outside of federal security protocols, creating “backdoors” in secure systems, installing unsanctioned “AI” software to scrape federal data (including personal identification information), and installing “spyware” to monitor email of federal employees
Disobeyed multiple court orders to release frozen federal funds (an ongoing violation; see the NYTimes on Wednesday)
Granted a corrupt pardon to the Mayor of New York in exchange for his promise to cooperate in Trump's immigration crackdown
The above is a partial list, each item of which is illegal (at least) and unconstitutional (at worst). Taken together, they compel the conclusion that Trump has not only violated his oath in every conceivable way but that he is actively working to overthrow the Constitution. That is the very definition of a coup.
5 notes
·
View notes