#chmod - change a file's permissions
Explore tagged Tumblr posts
Text
How to change Permission file and folder in the Linux?
Introduction
Linux is renowned for its robust security features and the level of control it offers to users over their system. One fundamental aspect of this control is the ability to manage permissions for files and folders. Properly understanding and utilizing Linux file and folder permissions is crucial for maintaining the integrity of your system and ensuring that sensitive data remains protected. In this comprehensive guide, we will walk you through the process of changing permissions for files and folders in Linux, step by step.
The Linux operating system uses access permission to maintain security on files directories. When we create a file or directory, Linux assigns default permissions to them. In this tutorial, we’ll discuss different ways of changing permissions for directories and files within the directory. Privacy is an essential part of someone’s life, whether social media or the workplace. Read More
#How to change Permission file and folder in the Linux?#How to change directory permissions in Linux with chmod?#How to Change File Permissions
0 notes
Text
Congratulations, you know more programming than 90% of the people I talk to. That's usually enough to make most people completely check out
On one hand it would be so cool to be good at computers like almost all of you, on the other there is this autism part of me that does not want to learn about it, feels good about being incompetent at it, and does not want to find anything that others like cool or give others the satisfaction of being right.
And it does not even matter cause I can't afford one anyway lol.
#common file manipulation commands in Linux include:#ls - list the files within a directory#mv - move a file from one location to another#cp - create a copy of a file in one location at a different location#rm - remove a file#chmod - change a file's permissions#chown - change a file's owner
16 notes
·
View notes
Text

SYSTEM ADMIN INTERVIEW QUESTIONS 24-25
Table of Content
Introduction
File Permissions
User and Group Management:
Cron Jobs
System Performance Monitoring
Package Management (Red Hat)
Conclusion
Introduction
The IT field is vast, and Linux is an important player, especially in cloud computing. This blog is written under the guidance of industry experts to help all tech and non-tech background individuals secure interviews for roles in the IT domain related to Red Hat Linux.
File Permissions
Briefly explain how Linux file permissions work, and how you would change the permissions of a file using chmod. In Linux, each file and directory has three types of permissions: read (r), write (w), and execute (x) for three categories of users: owner, group, and others. Example: You will use chmod 744 filename, where the digits represent the permission in octal (7 = rwx, 4 = r–, etc.) to give full permission to the owner and read-only permission to groups and others.
What is the purpose of the umask command? How is it helpful to control default file permissions?umask sets the default permissions for newly created files and directories by subtracting from the full permissions (777 for directories and 666 for files). Example: If you set the umask to 022, new files will have permissions of 644 (rw-r–r–), and directories will have 755 (rwxr-xr-x).
User and Group Management:
Name the command that adds a new user in Linux and the command responsible for adding a user to a group. The Linux useradd command creates a new user, while the usermod command adds a user to a specific group. Example: Create a user called Jenny by sudo useradd jenny and add him to the developer’s group by sudo usermod—aG developers jenny, where the—aG option adds users to more groups without removing them from other groups.
How do you view the groups that a user belongs to in Linux?
The group command in Linux helps to identify the group a user belongs to and is followed by the username. Example: To check user John’s group: groups john
Cron Jobs
What do you mean by cron jobs, and how is it scheduled to run a script every day at 2 AM?
A cron job is defined in a crontab file. Cron is a Linux utility to schedule tasks to run automatically at specified times. Example: To schedule a script ( /home/user/backup.sh ) to run daily at 2 AM: 0 2 * * * /home/user/backup.sh Where 0 means the minimum hour is 2, every day, every month, every day of the week.
How would you prevent cron job emails from being sent every time the job runs?
By default, cron sends an email with the output of the job. You can prevent this by redirecting the output to /dev/null. Example: To run a script daily at 2 AM and discard its output: 0 2 * * * /home/user/backup.sh > /dev/null 2>&1
System Performance Monitoring
How can you monitor system performance in Linux? Name some tools with their uses.
Some of the tools to monitor the performance are: Top: Live view of system processes and usage of resource htop: More user-friendly when compared to the top with an interactive interface. vmstat: Displays information about processes, memory, paging, block IO, and CPU usage. iostat: Showcases Central Processing Unit (CPU) and I/O statistics for devices and partitions. Example: You can use the top command ( top ) to identify processes consuming too much CPU or memory.
In Linux, how would you check the usage of disk space?
The df command checks disk space usage, and Du is responsible for checking the size of the directory/file. Example: To check overall disk space usage: df -h The -h option depicts the size in a human-readable format like GB, MB, etc.
Package Management (Red Hat)
How do you install, update, or remove packages in Red Hat-based Linux distributions by yum command?
In Red Hat and CentOS systems, the yum package manager is used to install, update, or remove software. Install a package: sudo yum install httpd This installs the Apache web server. Update a package: sudo yum update httpd Remove a package:sudo yum remove httpd
By which command will you check the installation of a package on a Red Hat system?
The yum list installed command is required to check whether the package is installed. Example: To check if httpd (Apache) is installed: yum list installed httpd
Conclusion
The questions are designed by our experienced corporate faculty which will help you to prepare well for various positions that require Linux such as System Admin.
Contact for Course Details – 8447712333
2 notes
·
View notes
Text
listen. listen what if i study for my exams by turning all the concepts i need to learn into characters and plots.
what if i talk about a cat made up of words. it likes eating them too, and will happily go and thieve away whatever book or document you've set aside and just eat it all. it'll give some back to you, though! you know, if you know the right command and you know what to look for.
its name is Chmod, and hanging from its collar are three tokens with numbers on it and if you grab the right token you could change the words written on its body and own it.
it leaves footprints made of words behind when it jogs, but not for long. they fade away in seconds, sent away to a mythical place called Varlog, where you can only enter if you have the right key.
anyway, this is my attempt to link together all the file manipulation commands for my exam, featuring:
cat (lets you view entire file)
head & tail (look, it's a cat, of course it has a head and tail, and each of them have 10 words each)
grep (the command you need to get words from the cat)
chmod (the name of the cat, and also the command you need to change file permissions)
logger (the command to add messages to var/log/syslog and look, i figured jogging was close enough, okay)
10 notes
·
View notes
Text
Essential Linux Commands: Mastering the Basics of Command-Line Operations
Linux, a powerful and versatile operating system, offers a command-line interface that empowers users with unprecedented control over their systems. While the graphical user interface (GUI) provides ease of use, understanding the fundamental Linux commands is essential for anyone seeking to harness the full potential of this open-source platform. In this article, we will explore some of the…
Essential Linux Commands help users navigate, manage files, and control system processes. Here are some key ones:
ls – List directory contents
cd – Change directory
pwd – Show current directory path
mkdir – Create a new directory
rm – Remove files or directories
cp – Copy files or directories
mv – Move or rename files
cat – View file contents
grep – Search text in files
chmod – Change file permissions
top – Monitor system processes
ps – Display running processes
kill – Terminate a process
sudo – Execute commands as a superuser
Mastering these commands boosts productivity and system control!
#Basics of Command-Line Operations#Command-Line Operations#Essential Linux Commands#Linux Commands#linux commands#linux#basic linux commands#linux command line#linux commands for beginners#linux basic commands#linux command line tutorial#learn linux#linux tutorial#linux commands tutorial#command line#commands in linux#best linux commands#linux for beginners#essential linux commands#linux tutorial for beginners#top linux terminal commands#basic linux ubuntu commands#linux commands with examples#commands#linux course
2 notes
·
View notes
Text
Unix Commands Every iOS Developer Should Know
When developing iOS applications, many developers focus primarily on Swift, Objective-C, and Xcode. However, a lesser-known yet powerful toolset that enhances productivity is Unix commands. Since macOS is a Unix-based operating system, understanding essential Unix commands can help iOS developers manage files, automate tasks, debug issues, and optimize workflows.
In this article, we’ll explore some of the most useful Unix commands every iOS developer should know.
Why Should iOS Developers Learn Unix?
Apple’s macOS is built on a Unix foundation, meaning that many system-level tasks can be efficiently handled using the terminal. Whether it’s managing files, running scripts, or automating processes, Unix commands can significantly enhance an iOS developer’s workflow. Some benefits include:
Better control over project files using the command line
Efficient debugging and log analysis
Automating repetitive tasks through scripting
Faster project setup and dependency management
Now, let’s dive into the must-know Unix commands for iOS development.
1. Navigating the File System
cd – Change Directory
The cd command allows developers to navigate between directories
{cd ~/Documents/MyiOSProject}
This moves you into the MyiOSProject folder inside Documents.
ls – List Directory Contents
To view files and folders in the current directory:
bash
CopyEdit
ls
To display detailed information, use:
bash
CopyEdit
ls -la
pwd – Print Working Directory
If you ever need to check your current directory:
bash
CopyEdit
pwd
2. Managing Files and Directories
mkdir – Create a New Directory
To create a new folder inside your project:
bash
CopyEdit
mkdir Assets
rm – Remove Files or Directories
To delete a file:
bash
CopyEdit
rm old_file.txt
To delete a folder and its contents:
bash
CopyEdit
rm -rf OldProject
⚠ Warning: The -rf flag permanently deletes files without confirmation.
cp – Copy Files or Directories
To copy a file from one location to another:
bash
CopyEdit
cp file.txt Backup/
To copy an entire folder:
bash
CopyEdit
cp -r Assets Assets_Backup
mv – Move or Rename Files
Rename a file:
bash
CopyEdit
mv old_name.txt new_name.txt
Move a file to another directory:
bash
CopyEdit
mv file.txt Documents/
3. Viewing and Editing Files
cat – Display File Contents
To quickly view a file’s content:
bash
CopyEdit
cat README.md
nano – Edit Files in Terminal
To open a file for editing:
bash
CopyEdit
nano config.json
Use Ctrl + X to exit and save changes.
grep – Search for Text in Files
To search for a specific word inside files:
bash
CopyEdit
grep "error" logs.txt
To search recursively in all files within a directory:
bash
CopyEdit
grep -r "TODO" .
4. Process and System Management
ps – Check Running Processes
To view running processes:
bash
CopyEdit
ps aux
kill – Terminate a Process
To kill a specific process, find its Process ID (PID) and use:
bash
CopyEdit
kill PID
For example, if Xcode is unresponsive, find its PID using:
bash
CopyEdit
ps aux | grep Xcode kill 1234 # Replace 1234 with the actual PID
top – Monitor System Performance
To check CPU and memory usage:
bash
CopyEdit
top
5. Automating Tasks with Unix Commands
chmod – Modify File Permissions
If a script isn’t executable, change its permissions:
bash
CopyEdit
chmod +x script.sh
crontab – Schedule Automated Tasks
To schedule a script to run every day at midnight:
bash
CopyEdit
crontab -e
Then add:
bash
CopyEdit
0 0 * * * /path/to/script.sh
find – Search for Files
To locate a file inside a project directory:
bash
CopyEdit
find . -name "Main.swift"
6. Git and Version Control with Unix Commands
Most iOS projects use Git for version control. Here are some useful Git commands:
Initialize a Git Repository
bash
CopyEdit
git init
Clone a Repository
bash
CopyEdit
git clone https://github.com/user/repo.git
Check Status and Commit Changes
bash
CopyEdit
git status git add . git commit -m "Initial commit"
Push Changes to a Repository
bash
CopyEdit
git push origin main
Final Thoughts
Mastering Unix commands can greatly improve an iOS developer’s efficiency, allowing them to navigate projects faster, automate tasks, and debug applications effectively. Whether you’re managing files, monitoring system performance, or using Git, the command line is an essential tool for every iOS developer.
If you're looking to hire iOS developers with deep technical expertise, partnering with an experienced iOS app development company can streamline your project and ensure high-quality development.
Want expert iOS development services? Hire iOS Developers today and build next-level apps!
#ios app developers#Innvonixios app development company#ios app development#hire ios developer#iphone app development#iphone application development
0 notes
Text
Linux Zero to Hero: Mastering the Open-Source Operating System
Linux, an open-source operating system, is the backbone of countless systems, from personal computers to enterprise servers and supercomputers. It has earned its reputation as a robust, versatile, and secure platform for developers, administrators, and tech enthusiasts. In this comprehensive guide, we explore the journey from being a Linux beginner to mastering its vast ecosystem.
Why Learn Linux?
1. Open-Source Freedom
Linux provides unparalleled flexibility, allowing users to customize and modify the system according to their needs. With its open-source nature, you have access to thousands of applications and tools free of charge.
2. Industry Relevance
Major companies, including Google, Amazon, and Facebook, rely on Linux for their servers and infrastructure. Learning Linux opens doors to lucrative career opportunities in IT and software development.
3. Secure and Reliable
Linux boasts a strong security model and is known for its stability. Its resistance to malware and viruses makes it the operating system of choice for critical applications.
Getting Started with Linux
Step 1: Understanding Linux Distributions
Linux comes in various distributions, each catering to specific needs. Popular distributions include:
Ubuntu: User-friendly, ideal for beginners.
Fedora: Known for cutting-edge technology and innovation.
Debian: Stable and versatile, preferred for servers.
CentOS: Enterprise-grade, often used in businesses.
Choosing the right distribution depends on your goals, whether it’s desktop use, development, or server management.
Step 2: Setting Up Your Linux Environment
You can use Linux in several ways:
Dual Boot: Install Linux alongside Windows or macOS.
Virtual Machines: Run Linux within your current OS using tools like VirtualBox.
Live USB: Try Linux without installation by booting from a USB drive.
Mastering Linux Basics
1. The Linux File System
Linux organizes data using a hierarchical file system. Key directories include:
/root: Home directory for the root user.
/etc: Configuration files for the system.
/home: User-specific data.
/var: Variable files, such as logs and databases.
2. Essential Linux Commands
Understanding basic commands is crucial for navigating and managing the Linux system. Examples include:
ls: Lists files and directories.
cd: Changes directories.
mkdir: Creates new directories.
rm: Deletes files or directories.
chmod: Changes file permissions.
3. User and Permission Management
Linux enforces strict user permissions to enhance security. The system categorizes users into three groups:
Owner
Group
Others
Permissions are represented as read (r), write (w), and execute (x). Adjusting permissions ensures secure access to files and directories.
Advanced Linux Skills
1. Shell Scripting
Shell scripting automates repetitive tasks and enhances efficiency. Using bash scripts, users can create programs to execute commands in sequence.
Example: A Simple Bash Script
bash
Copy code
#!/bin/bash
echo "Hello, World!"
2. System Administration
System administrators use Linux for tasks like:
Managing users and groups.
Monitoring system performance.
Configuring firewalls using tools like iptables.
Scheduling tasks with cron jobs.
3. Package Management
Each Linux distribution uses a package manager to install, update, and remove software:
APT (Ubuntu/Debian): sudo apt install package_name
YUM (CentOS/Fedora): sudo yum install package_name
Zypper (openSUSE): sudo zypper install package_name
Linux for Developers
Linux provides a robust environment for coding and development. Key features include:
Integrated Development Environments (IDEs): Tools like Eclipse, IntelliJ IDEA, and Visual Studio Code are supported.
Version Control Systems: Git integration makes Linux ideal for collaborative software development.
Containerization and Virtualization: Tools like Docker and Kubernetes thrive in Linux environments.
Troubleshooting and Debugging
Learning to troubleshoot is vital for any Linux user. Common methods include:
Viewing Logs: Logs in /var/log offer insights into system errors.
Using Debugging Tools: Commands like strace and gdb help debug applications.
Network Diagnostics: Tools like ping, traceroute, and netstat diagnose connectivity issues.
Linux Certifications
Earning a Linux certification validates your skills and enhances your career prospects. Notable certifications include:
CompTIA Linux+
Red Hat Certified Engineer (RHCE)
Linux Professional Institute Certification (LPIC)
Certified Kubernetes Administrator (CKA)
These certifications demonstrate proficiency in Linux administration, security, and deployment.
Tips for Success in Linux Mastery
Practice Regularly: Familiarity with commands and tools comes through consistent practice.
Join Communities: Engage with Linux forums, such as Stack Overflow and Reddit, to learn from experienced users.
Contribute to Open-Source Projects: Hands-on involvement in projects deepens your understanding of Linux and enhances your resume.
Stay Updated: Follow Linux news and updates to stay informed about advancements and changes.
Conclusion
Mastering Linux is a transformative journey that equips individuals and organizations with the tools to thrive in a technology-driven world. By following the steps outlined in this guide, you can progress from a Linux novice to a seasoned expert, ready to tackle real-world challenges and opportunities.
0 notes
Text
Bought a Raspberry Pi kit recently and imagined what to do next? Well, don't worry; here in this article, I will let you how to program a Raspberry Pi. If you are excited about your Raspberry Pi but have not written a single line of code before, don't worry. Programming a Raspberry Pi is a piece of cake. It's easy, simple, and interesting to code this tiny yet powerful supercomputer. Programming Languages Programming, languages like C, C++, Java, Scratch, Ruby, Python all come preinstalled in the Raspberry Pi editor. Raspberry Pi Foundation recommends Python language for all the new Pi learners. Also, the “Pi” in the name “Raspberry Pi” implies Python in it. For younger kids, Scratch is the recommended language to learn. Any language which is compatible with ARMv6 is supported in Raspberry Pi. You are not restricted to use Python. Other languages supported in Raspberry Pi HTML Perl Javascript JQuery How to write a program in C? C is the preferred language when you are just entering the programming world. It is the best language to clear your logical concepts. Now, why am I talking about all this? Well, you will need a strong logical ability to write gobsmacking programs. If your core foundation is not strong, it's difficult to write proper and clean code. Writing your first program This is a simple program to print "Hello World" on your screen. Pretty simple, isn't it? Compiling a program Compiling the program helps computer change the program written in a human readable form to machine readable format. For compiling a C program on Windows open "Command Prompt." After opening Cmd. Write the following command. Example: gcc helloworld.c -o mycprogram. When you compile the source file, it will be changed with the new name you give. Here we will take it as mycprogram. Here helloworld.c is your program file name. Making the program executable For making the program executable just change the file permissions, and you are good to go. Copy and paste the following command in your cmd. chmod +x mycprogram Executing the program For executing the program write the following command in your Cmd. ./mycprogram This is all you need to do to execute your first C program. How to write a program in Python? Python is widely used when it comes to programming languages. Python programs are concise and easy to execute. Features of Python Interpreted Language. Object-oriented. Beginner's Language. Writing your program in Python print "Hello, World!" Just a single line of code will let you print “Hello World” on your computer screen. That's the power of Python Language. Running a Python Program Simply open cmd and write the following command. Make sure you are in the folder directory where you stored your program. python helloworld.py Making the program executable You can make a file executable by entering this at the command prompt chmod +x file-name.py Executing the program For executing the program write the following command in your Cmd. ./file-name.py This is all you need to do to execute your first Python program. How to write a program in HTML? HTML is the most used language in programming when it comes to the User Interface (UI). HTML is very simple to code and requires no logical abilities. Just a creative mind to code and you will master HTML pretty soon. There are many other languages like Javascript, Bootstrap, and JQuery to make your pages more attractive and user-friendly but, it all starts with the HTML code. Writing your program in HTML This is how simple it is to write a HTML code. If you try executing this code you can see “Hello world” message right to your screen. Applying CSS With CSS you can create beautiful and attractive pages. CSS is a framework for styling your HTML pages. Here is the demo how to code in CSS Now, it’s time to apply this code to your Pi you need to install Apache. Make sure your Raspberry Pi is connected to the Internet and in working condition. Write following commands: sudo apt-get update
sudo apt-get upgrade sudo apt-get install apache2 sudo apt-get install apache2 Copy all your HTML and CSS code and save it in /var/www/index.html. You can open this file writing the following command in your terminal: sudo leafpad /var/www/index.html Your program will not execute unless you give permissions to read for other users. You can do this by writing the following command. sudo chmod a+r /var/www/index.html Type ifconfig in command prompt to find your Pi's IP address. Note down your Ip address. Paste this Ip address in your browser and see how your code works. With the combo of HTML, CSS, and Python you can create wonders in Raspberry Pi. Wrap up As you can see programming is not a difficult job to do. It requires a little interest and skills. I hope you found this article useful and you learned something new today by reading this article. Try experimenting with your programming skills and make something which is truly amazing. Let me know in the comments section which language you will prefer as your primary language to code in Raspberry Pi. My name is Mandip and I run raspberry pi starter kits. I love to tinker with the electronics circuits and create new and useful designs. Sometimes the results come awful, too! I share all my ideas, research, and knowledge on my website. I also love to travel and explore historical places whenever I get suitable time for it.
0 notes
Text
Linux CLI 18 🐧 id, chmod and umask commands
New Post has been published on https://tuts.kandz.me/linux-cli-18-%f0%9f%90%a7-id-chmod-and-umask-commands/
Linux CLI 18 🐧 id, chmod and umask commands

youtube
id is used to display information about a user getting information for the current user getting information for specific user getting the user ID for specific user getting the group ID for specific user getting the name for a specific user getting all groups for a specific user chmod changes the permissions of a file or a directory only the owner or the superuser is allowed to do that youcan change the permissions with 2 ways 1 → by symbolic representation symbolic representation example 2 → by octal number representation octal number representation example chmod symbolic representations explanation u → owner g → group o → others → add permission - → remove permission = → set permissions r → readable w → writable x → executable s → set user id S → set group id u+rwx → add to the owner read, write and execute permissions g-wx → removes from the group write and execute permissions o=rx → set for the others read and execute permissions chmod octal number representation there are 3 digits, like 644 1st → for the owner(u) 2nd → for the group(g) 3rd → for the other(o) 0 → no permissions(---) 1 → execute permission(--x) 2 → write permission(-w-) 3 → write and execute permissions(-wx) 4 → read permission(r--) 5 → read and execute permissions(r-x) 6 → read and write permissions(rw-) 7 → read, write and execute permissions(rwx) sets 640 → read and execute for the owner, read permissions for the group and no permissions for the rest umask determines the default permissions applied to new files/directories gets the current default permission chaging to 0000, no file or directory will have any restrictive permissions by default changing back to 0022 to understand the new permission just subtract files 666-022 = 644 directories 777-022=755 echo "umask new_mask" →→ ~/.bashrc → adds a new mask to .bashrc and you it will be permanent
0 notes
Text
How to deploying Laravel projects on a live server – Complete Step-by-Step Guide
Learn How to deploying Laravel projects on a live server with this comprehensive guide. Step-by-step instructions on setting up hosting, configuring files, and deploying your Laravel app smoothly.Read Laravel Docs
How to deploying Laravel projects on a live server, you’ll need to follow a structured process. Here’s a step-by-step guide to help you:

1. Purchase Domain and Hosting
Make sure you have a domain and a hosting plan. Most shared hosting plans (like cPanel-based ones) or a VPS will work for Laravel, but ensure your server supports PHP and MySQL and meets Laravel’s requirements (PHP version, required extensions, etc.).
2. Prepare Your Laravel Project
Make sure your Laravel project is working locally.
Run the following command to clear any cached configuration and to optimize the project:
php artisan cache:clear
php artisan config:clear
php artisan route:clear
php artisan view:clear
Set up your environment variables (.env file). Make sure they are correctly configured for the live server (e.g., database, mail, and app URL settings).
3. Zip and Upload Your Laravel Project
Compress your entire Laravel project folder (without the node_modules and vendor directories) into a .zip file.
Use FTP (with FileZilla or any other FTP client) or File Manager in cPanel to upload the .zip file to your server. Typically, upload the file to the public_html or a subdirectory within it if you want to run your Laravel app in a subdirectory.
4. Extract the Files
Once uploaded, use File Manager in your hosting control panel to extract the .zip file.
5. Set Up the Public Directory
By default, Laravel’s entry point is the public folder, which contains the index.php file. On a shared hosting server:
Move everything in the public folder (including the .htaccess and index.php files) to the root directory (usually public_html).
Edit the index.php file to update the paths:
Change:
require __DIR__.'/../vendor/autoload.php';
$app = require_once __DIR__.'/../bootstrap/app.php';
To:
require __DIR__.'/vendor/autoload.php';
$app = require_once __DIR__.'/bootstrap/app.php';
This ensures that Laravel can find the necessary files in the correct directory.
6. Set File Permissions
Ensure that the following directories are writable by the server:
/storage
/bootstrap/cache
Use the following command via SSH (if available) or through the hosting file manager:chmod -R 775 storage chmod -R 775 bootstrap/cache
7. Set Up a Database
Create a MySQL database and a user with privileges in cPanel (or via SSH if using VPS).
Update the .env file with your database credentials:
DB_HOST=localhost DB_DATABASE=your_database_name DB_USERNAME=your_database_username DB_PASSWORD=your_database_password
8. Install Composer Dependencies
If you have SSH access:
SSH into your server using a terminal or a tool like PuTTY.
Navigate to your project directory
cd /path/to/your/project
Run Composer to install the dependencies:
composer install --optimize-autoloader --no-dev
If you don’t have SSH access, you can run composer install locally, zip the vendor folder, and upload it to the server.
9. Run Migrations
If you have SSH access, run the following command to migrate the database:
php artisan migrate --force
If you don’t have SSH access, you can run the migrations locally and then export/import the database to the server via phpMyAdmin.
10. Set App Key
Generate a new application key if you haven’t already:php artisan key:generate
Ensure the key is set in the .env file:
Read Full Tutorials
0 notes
Text

WordPress Dosya İzinleri (CHMOD) Nasıl Olmalı?
WordPress, dünya genelinde milyonlarca web sitesi için tercih edilen bir içerik yönetim sistemidir. Ancak, her popüler platform gibi, güvenlik de büyük bir önem taşır. Sitenizin güvenliği ve performansı, sadece güçlü bir şifre ve güncel eklentilerle sınırlı değil. Dosya izinleri de bu konuda kritik bir rol oynuyor. Bu yazıda, WordPress sitenizin güvenliğini artırmada kritik bir rol oynayan dosya izinlerinin (CHMOD) nasıl ayarlanması gerektiğini detaylıca ele alacağız.
WordPress Dosya İzinleri Nedir?
CHMOD, UNIX ve Linux tabanlı sistemlerde dosya izinlerini değiştirmek için kullanılan bir komuttur.. Bu izinler, dosya ve klasörlere kimlerin okuma, yazma veya çalıştırma yetkisi olduğunu belirler. WordPress bağlamında, doğru izinlerin ayarlanması, sitenizin güvenliğini önemli ölçüde etkiler. Düşünün ki evinizde bazı odalara sadece siz girebiliyorsunuz, bazılarına misafirleriniz de girebiliyor. İşte dosya izinleri de buna benzer bir mantıkla çalışır.
CHMOD Nedir ve Nasıl Çalışır?
CHMOD, “Change Mode” kelimelerinin kısaltmasıdır. Bu sistem, üç farklı kullanıcı tipine (dosya sahibi, grup ve diğerleri) üç farklı izin tipi (okuma, yazma ve çalıştırma) atar.
Bu izinler genellikle üç basamaklı sayılarla ifade edilir:
4: Okuma izni
2: Yazma izni
1: Çalıştırma izni
Bu sayıları toplayarak farklı izin kombinasyonları oluşturabilirsiniz. Örneğin, 644 izni şu anlama gelir:
Dosya sahibi: Okuma ve yazma (4+2=6)
Grup: Sadece okuma (4)
Diğerleri: Sadece okuma (4)
Doğru Dosya İzinleri Neden Önemli?
Doğru ayarlanmış dosya izinleri, sitenizin güvenliğini artırır, yetkisiz erişimleri engeller sitenizin ve bütünlüğünü korumak için hayati önem taşır. Aynı zamanda, WordPress’in düzgün çalışması için de kritik öneme sahiptir. Yanlış izinler, güvenlik açıklarına, kötü niyetli kişilere zararlı kod eklemelerine veya verileri sızdırmalarına, hatta sitenizin çökmesine neden olabilir.
WordPress’te Temel Dosya İzinleri
WordPress’in sorunsuz çalışması için bazı temel dosya ve klasörlerin doğru izinlere sahip olması gerekir. İşte en önemli olanları:
wp-config.php Dosyası İzinleri
wp-config.php dosyası, WordPress kurulumunuzun kalbidir. Veritabanı bilgileri gibi hassas verileri içerdiğinden, bu dosyanın izinlerinin sıkı tutulması gerekir. Genellikle önerilen izin 600 veya 640’tır.
wp-content Klasörü İzinleri
wp-content klasörü, temalarınızı, eklentilerinizi ve yüklenmiş medya dosyalarınızı içerir. Bu klasörün izinleri genellikle 755 olarak ayarlanır, böylece WordPress bu klasöre yazabilir ama diğer kullanıcılar sadece okuyabilir.
Tema ve Eklenti Dosyaları İzinleri
Tema ve eklenti dosyaları genellikle 644 izinlerine sahip olmalıdır. Bu, WordPress’in bu dosyaları okumasına izin verir ancak yazma iznini kısıtlar.
Dosya İzinlerini Kontrol Etme ve Değiştirme Yöntemleri
Dosya izinlerini kontrol etmek ve değiştirmek için birkaç yöntem var. İşte en yaygın olanları:
FTP Üzerinden Dosya İzinlerini Yönetme
FTP istemcinizi kullanarak sunucunuza bağlanabilir ve dosya izinlerini görüntüleyip değiştirebilirsiniz. Çoğu FTP istemcisi, dosyaya sağ tıklayıp “İzinler” veya “CHMOD” seçeneğini seçmenize olanak tanır.
cPanel File Manager ile İzin Değiştirme
Web hosting kontrol panelinizde bulunan File Manager aracını kullanarak da dosya izinlerini değiştirebilirsiniz. Dosyayı seçin, “Change Permissions” butonuna tıklayın ve istediğiniz izinleri ayarlayın.
SSH Kullanarak Dosya İzinlerini Ayarlama
Eğer sunucunuza SSH erişiminiz varsa, komut satırını kullanarak izinleri değiştirebilirsiniz.
Örneğin: chmod 644 dosya_adi.php
Güvenli WordPress Dosya İzinleri İçin En İyi Uygulamalar
WordPress sitenizi güvende tutmak için bazı best practice’leri uygulayabilirsiniz:
Hassas Dosyaların Korunması
wp-config.php gibi hassas dosyaların izinlerini sıkı tutun. Bu dosyaları 600 veya 640 izinleriyle koruyun.
Düzenli İzin Kontrolleri
Sitenizin dosya izinlerini düzenli olarak kontrol edin. Özellikle güncellemelerden veya yeni eklenti/tema yüklemelerinden sonra bu kontrolü yapmayı unutmayın.
Otomatik Güncelleme Ayarları ve İzinler
WordPress’in otomatik güncellemeler yapabilmesi için bazı dosya ve klasörlerin yazılabilir olması gerekir. Ancak bu, güvenlik riskleri oluşturabilir. Otomatik güncellemeleri dikkatli kullanın ve güncelleme sonrası izinleri tekrar kontrol edin.
Dosya İzinleri ile İlgili Yaygın Sorunlar ve Çözümleri
Bazen dosya izinleri sorunları, can sıkıcı hatalara neden olabilir. İşte en yaygın sorunlar ve çözümleri:
500 Internal Server Error
Bu hata genellikle .htaccess dosyasının izinleriyle ilgilidir. .htaccess dosyasının izinlerini 644 olarak ayarlamayı deneyin.
Beyaz Ekran Hatası (WSOD)
WSOD genellikle PHP hatalarından kaynaklanır. wp-content klasörünün ve alt klasörlerinin izinlerini kontrol edin ve 755 olarak ayarlayın.
Eklenti ve Tema Yükleme Sorunları
Eğer eklenti veya tema yükleyemiyorsanız, wp-content/plugins ve wp-content/themes klasörlerinin izinlerini kontrol edin. Bu klasörler 755 izinlerine sahip olmalıdır.
İleri Seviye WordPress Dosya İzini Yönetimi
WordPress’in temel dosya izinlerini anlamak önemlidir, ancak bazı durumlar daha ileri düzey bir yaklaşım gerektirir. İşte derinlemesine bakmanız gereken bazı alanlar:
.htaccess Dosyası İzinleri ve Özelleştirmeleri
.htaccess dosyası, WordPress sitenizin davranışını kontrol eden güçlü bir araçtır. Bu dosyanın izinleri ve içeriği, sitenizin güvenliği ve performansı üzerinde büyük bir etkiye sahip olabilir.
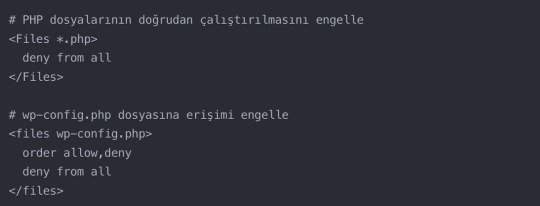
H3: Özel İçerik Türleri için İzin Ayarları
WordPress’te özel içerik türleri oluşturduğunuzda, bu içeriklerin nasıl depolandığını ve erişildiğini dikkatle yönetmeniz gerekir.
Özel Klasörler: Özel içerik türleri için ayrı klasörler oluşturduysanız (örneğin, wp-content/custom-post-types/), bu klasörlerin izinlerini 755 olarak ayarlayın. Bu, WordPress’in içerikleri okumasına ve yazmasına izin verirken, diğer kullanıcıların sadece okumasına izin verir.
Özel Dosya Türleri: Özel içerik türleriniz özel dosya türleri içeriyorsa (örneğin, .pdf veya .docx), bu dosyaların izinlerini 644 olarak ayarlayın. Bu, dosyaların okunabilir olmasını sağlarken, yetkisiz değişiklikleri önler.
Dinamik İçerik Yönetimi: Eğer özel içerik türleriniz dinamik olarak oluşturulan dosyalar içeriyorsa (örneğin, kullanıcı tarafından yüklenen dosyalar), bu dosyaların güvenli bir şekilde depolanmasını ve erişilmesini sağlamanız gerekir:

H3: Cron İşleri ve Zamanlanmış Görevler için İzin Yönetimi
WordPress’in zamanlanmış görevleri ve özel cron işleri, özel izin ayarları gerektirebilir.
wp-cron.php İzinleri: wp-cron.php dosyasının izinlerini 644 olarak ayarlayın. Bu, dosyanın okunabilir olmasını sağlar ancak yetkisiz değişiklikleri önler.
Özel Cron Betikleri: Özel cron betikleri oluşturduysanız, bu betiklerin izinlerini 644 olarak ayarlayın ve güvenli bir konumda (örneğin, public_html dizininin dışında) saklayın.
Cron Logları: Cron işleriniz için log dosyaları oluşturuyorsanız, bu dosyaların izinlerini 664 olarak ayarlayın. Bu, WordPress’in dosyaya yazmasına izin verirken, diğer kullanıcıların sadece okumasına izin verir.
H3: Çoklu Site (Multisite) Kurulumları için İzin Yönetimi
WordPress Multisite kurulumları, daha karmaşık bir izin yapısı gerektirir:
Uploads Klasörü: Multisite kurulumlarında, her alt sitenin kendi uploads klasörü olur. Bu klasörlerin izinlerini 755 olarak ayarlayın.
Alt Site Klasörleri: Her alt sitenin kök klasörünün (örneğin, /wp-content/blogs.dir/2/) izinlerini 755 olarak ayarlayın.
Ağ Yöneticisi Dosyaları: wp-admin/network/ klasöründeki dosyaların izinlerini 644 olarak ayarlayın, bu klasörün kendisini ise 755 yapın.
Bu ileri düzey izin yönetimi teknikleri, WordPress sitenizin güvenliğini ve performansını önemli ölçüde artırabilir. Ancak, bu değişiklikleri yaparken dikkatli olun ve her zaman bir yedek alın.
Dosya izinleri konusunda herhangi bir şüpheniz varsa veya WordPress sitenizin güvenliğini profesyonel bir şekilde yönetmek istiyorsanız, uzman desteği almak en doğru seçenek olabilir. Gezgin Ajans olarak, WordPress güvenliği konusunda kapsamlı hizmetler sunuyoruz. WordPress Güvenlik Hizmetimiz hakkında detaylı bilgi almak ve sitenizi nasıl daha güvenli hale getirebileceğinizi öğrenmek için WordPress uzmanlarımızla iletişime geçebilirsiniz. Uzmanlarımız, sizin özel ihtiyaçlarınıza uygun çözümler sunarak, sitenizin güvenliğini en üst düzeye çıkarmanıza yardımcı olacaktır.
Sonuç
WordPress dosya izinleri, sitenizin güvenliği ve performansı için kritik öneme sahiptir. Doğru izinler, sitenizi korurken aynı zamanda sorunsuz çalışmasını sağlar. Düzenli kontroller yaparak ve best practice’leri uygulayarak, WordPress sitenizi daha güvenli ve stabil hale getirebilirsiniz.
Sıkça Sorulan Sorular (SSS)
Dosya izinlerini değiştirmek tehlikeli mi? Doğru yapıldığında tehlikeli değildir. Ancak yanlış izinler sitenizin çalışmamasına veya güvenlik açıklarına neden olabilir. Değişiklik yapmadan önce mutlaka yedek alın.
WordPress’in önerdiği standart dosya izinleri nelerdir? Genellikle, dosyalar için 644, klasörler için 755 önerilir. Ancak wp-config.php gibi hassas dosyalar için daha sıkı izinler (600 veya 640) gerekebilir.
Dosya izinlerimi nasıl kontrol edebilirim? FTP istemciniz, cPanel File Manager veya SSH kullanarak dosya izinlerini kontrol edebilirsiniz.
777 izinleri neden tehlikeli? 777 izinleri, herkesin dosyayı okuma, yazma ve çalıştırma iznine sahip olduğu anlamına gelir. Bu, potansiyel saldırganların dosyalarınızı değiştirmesine olanak tanır.
Dosya izinleri sorunları nasıl tespit edilir? Genellikle, WordPress hataları veya beyaz ekran sorunları dosya izinleriyle ilgili olabilir. Ayrıca, WordPress güvenlik eklentileri de izin sorunlarını tespit etmenize yardımcı olabilir.
wp-config.php dosyasının izinleri neden önemli? wp-config.php, veritabanı bilgileri gibi hassas bilgiler içerir. Bu nedenle, bu dosyanın izinlerinin sıkı tutulması güvenlik açısından kritiktir.
Dosya izinlerini değiştirdikten sonra sitemi test etmeli miyim? Evet, herhangi bir değişiklikten sonra sitenizi test etmek önemlidir. Tüm sayfaların ve özelliklerin düzgün çalıştığından emin olun.
Eklenti ve tema güncellemeleri dosya izinlerini etkiler mi? Bazen etkileyebilir. Bu nedenle, güncellemelerden sonra kritik dosya ve klasörlerin izinlerini kontrol etmek iyi bir uygulamadır.
Dosya izinleri sorunları hosting sağlayıcımdan kaynaklanabilir mi? Evet, bazı hosting sağlayıcıları güvenlik nedeniyle belirli dosya izinlerini kısıtlayabilir. Sorun yaşıyorsanız hosting sağlayıcınızla iletişime geçin.
Dosya izinlerini otomatik olarak yönetmek mümkün mü? Bazı WordPress güvenlik eklentileri, dosya izinlerini otomatik olarak yönetebilir. Ancak manuel kontrol her zaman daha güvenlidir.
0 notes
Text
Running qBittorrent as Administrator: A Step-by-Step Guide

qBittorrent is a popular and free BitTorrent client that provides an open-source alternative to other torrenting software. It is known for its ease of use, speed, and lack of ads. However, some users might encounter issues that require running qBittorrent with administrative privileges. This guide will walk you through the process of running qBittorrent as an administrator on both Windows and macOS, ensuring you can take full advantage of its features without any hitches.
Why Run qBittorrent as Administrator?
Running qBittorrent as an administrator can resolve several issues:
Network Permissions: It can help in overcoming network permissions that might block certain functions.
Access to System Resources: Administrative privileges allow the software to access necessary system resources, potentially improving performance.
Configuration Changes: It ensures that any configuration changes are saved and applied correctly, especially those requiring elevated permissions.
Running qBittorrent as Administrator on Windows
Method 1: Run as Administrator from the Start Menu
Locate qBittorrent: Click on the Start menu and type “qBittorrent” in the search bar.
Right-Click: Right-click on the qBittorrent application from the search results.
Select Run as Administrator: From the context menu, select “Run as administrator.”
Method 2: Always Run as Administrator
If you want qBittorrent to always run with administrative privileges, follow these steps:
Find qBittorrent Executable: Right-click on the qBittorrent shortcut on your desktop or navigate to the installation folder (usually C:\Program Files\qBittorrent).
Open Properties: Select “Properties” from the context menu.
Compatibility Tab: Go to the “Compatibility” tab.
Run as Administrator: Check the box that says “Run this program as an administrator.”
Apply and OK: Click “Apply” and then “OK” to save the changes.
Troubleshooting Common Issues
Issue: Permission Denied
If you encounter a “Permission Denied” error, ensure that your user account has administrative privileges. On Windows, you might need to adjust User Account Control (UAC) settings. On macOS, ensure your account is listed under "Users & Groups" as an administrator.
Issue: Configuration Not Saving
Running qBittorrent as an administrator should resolve this issue. However, if problems persist, ensure that the configuration files are not set to read-only. On Windows, you can check file properties, and on macOS, use the chmod command to change file permissions.
Issue: Network Connectivity
Running as administrator can help with network-related issues, but also ensure that your firewall or antivirus software is not blocking qBittorrent. Adding qBittorrent to the list of allowed applications in your firewall settings can help.
Conclusion
Running qBittorrent as an administrator can help resolve various issues, particularly those related to network permissions and system resource access. By following the steps outlined above, you can ensure that qBittorrent operates smoothly and efficiently, providing you with an optimal torrenting experience. Whether you are using Windows or macOS, elevating qBittorrent’s privileges is a straightforward process that can significantly enhance its performance and reliability.
0 notes
Text
on unix-like systems (literally everything else, macos, linux, bsd, android, ios) compiled executable programs generally do not have a file extension.
A program is marked as an executable if the file permissions include a bit flag of octal 001 (or octal 010 if the specified group can execute it, or octal 100 if the specified owner or administrators can execute it).
you can easily set a file as executable by doing "chmod +x filename" (change mode +executable) though this doesnt mean it will actually run. it will give you an error if it's just normal text or whatever
On windows, a file is executable if it's file extension is marked as a "Designated File Type" in "Software Restriction Policies". You cannot mark any arbitrary file as executable, you must change the file extension.
It's nice to see just based on the file extension directly, but it's not hard in a file manager to get a column to show permissions.
Currently windows commands like "dir" and "cd" are actually "dir.exe" and "cd.exe" if you could just mark a file as executable you dont have to add .exe to the end to the file name and you dont have to code the shell to do "if you write something in the terminal without an extension add an exe to the file name".
Also you wouldnt have to call a function which retrieves some information from some other place on the system to determine if the file extension (which also you have to code it to split the file name at the rightmost period and pass the right side into a function to determine if it's in that list) and instead you can just. read the file permissions which you are Already Going To Read if you're doing anything with the file in the first place.
literally what is window's problem like shit.
The most fucked up lore drop we got in Splatoon 3 was that since the final log is called "log.exe" that means O.R.C.A. runs on Microsoft Windows
301 notes
·
View notes
Text
can't download vpn executable in ubuntu
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can't download vpn executable in ubuntu
VPN installation issues in Ubuntu
Installing a VPN on Ubuntu can be a straightforward process, but sometimes users encounter issues that can be frustrating to resolve. Here are some common problems you might encounter during VPN installation on Ubuntu, along with solutions to help you troubleshoot:
Missing Dependencies: One frequent issue is missing dependencies required for the VPN client to work properly. To address this, ensure that you have all necessary packages installed by running the command sudo apt-get install <package-name> for any missing dependencies.
Compatibility Problems: VPN clients may not always be fully compatible with certain versions of Ubuntu or its kernel. If you're experiencing compatibility issues, try updating your Ubuntu system to the latest stable release or installing any available kernel updates.
Incorrect Configuration: Incorrect configuration settings can prevent the VPN from connecting. Double-check the configuration files provided by your VPN service provider, paying close attention to details such as server addresses, authentication methods, and encryption protocols.
Firewall Restrictions: Ubuntu's built-in firewall, UFW (Uncomplicated Firewall), may block VPN connections by default. Make sure that UFW is configured to allow traffic over the VPN port(s) by running commands like sudo ufw allow <port>/tcp.
Network Manager Conflicts: Ubuntu's Network Manager may conflict with the VPN client's own network management software. Consider disabling Network Manager or configuring it to work alongside your VPN client.
DNS Leaks: Sometimes, VPN installations may suffer from DNS leaks, where your ISP's DNS servers are still used instead of the VPN's. Prevent this by configuring your VPN client to use a custom DNS server, such as Google DNS (8.8.8.8 and 8.8.4.4).
By addressing these common issues, you can troubleshoot VPN installation problems on Ubuntu and enjoy a secure and private internet browsing experience.
Executable download problems in Ubuntu VPN setup
When setting up a Virtual Private Network (VPN) on Ubuntu, you may encounter issues with executable downloads. This problem can arise due to various reasons, such as incorrect permissions, incompatible software, or network connectivity issues. Understanding how to troubleshoot and resolve executable download problems is crucial to ensure a smooth VPN setup process.
One common reason for executable download problems in Ubuntu VPN setup is insufficient permissions. If the executable file lacks the necessary permissions to run on your system, you may encounter errors when trying to download and execute it. In such cases, you can use the chmod command in the terminal to change the file's permissions and make it executable.
Another factor that can contribute to executable download issues is compatibility issues with the software or dependencies required for the VPN setup. Ensure that you are downloading the correct version of the executable file that is compatible with your Ubuntu system. Additionally, check for any missing dependencies and install them to ensure smooth execution of the VPN setup process.
Moreover, network connectivity issues can also hinder executable downloads during Ubuntu VPN setup. Make sure that your internet connection is stable and not blocking the download of executable files. If you are behind a firewall or using a proxy server, configure the settings to allow the download of necessary files for the VPN setup.
By addressing these common issues and following troubleshooting steps, you can overcome executable download problems in Ubuntu VPN setup and successfully establish a secure VPN connection on your system.
Troubleshooting VPN installation on Ubuntu
Setting up a Virtual Private Network (VPN) on Ubuntu can sometimes be a complicated process, but troubleshooting any issues that may arise can help ensure a smooth installation. Here are some common solutions to problems you may encounter during the VPN installation on Ubuntu.
One common issue is that the VPN connection is not working after installation. To troubleshoot this, double-check the configuration settings you entered during the setup process. Ensure that the server address, authentication credentials, and protocol settings are accurate. If they are correct, try restarting the VPN service or rebooting your system.
Another common problem is that the VPN client cannot connect to the server. In this case, check your internet connection to ensure it is stable. Also, try using a different network to see if the issue persists. If the problem continues, verify that the firewall settings on your Ubuntu system are not blocking the VPN connection.
If you are experiencing slow connection speeds with the VPN, try connecting to different server locations provided by your VPN service. Some servers may be overloaded, causing slow speeds. Additionally, check if there are any background applications consuming bandwidth and close them if necessary.
If you encounter any error messages during the VPN installation process, search online for solutions specific to those error codes. Forums and support pages often provide valuable insights into resolving VPN-related issues on Ubuntu.
By following these troubleshooting tips, you can effectively address common problems that may arise during the VPN installation on Ubuntu and enjoy a secure and private internet connection.
Ubuntu VPN executable not downloading
If you are encountering issues with downloading the VPN executable on Ubuntu, there are a few troubleshooting steps you can follow to resolve the issue.
Firstly, ensure that your internet connection is stable and functioning correctly. Slow or intermittent internet connections can disrupt the download process. You may want to try downloading the executable file at a different time when your internet connection is more stable.
Another common issue could be related to the server from which you are trying to download the VPN executable. Sometimes servers can be overloaded or experiencing maintenance, leading to download failures. In such cases, you can try downloading the executable from a different server, if available.
It is also important to verify that your browser or download manager is not causing the issue. Clearing your browser's cache and cookies or trying a different browser can sometimes help in successful downloading of the executable file.
If the problem persists, you may want to check if there are any firewall or antivirus settings blocking the download. Adjusting the settings to allow the download can sometimes solve the problem.
Lastly, if none of the above solutions work, reaching out to the VPN service provider for assistance can be helpful. They may have specific instructions or troubleshooting steps tailored to their service on Ubuntu systems.
By following these steps and being patient, you should be able to successfully download the VPN executable on your Ubuntu system.
Resolving VPN setup errors in Ubuntu
Setting up a Virtual Private Network (VPN) on Ubuntu can provide enhanced privacy and security, but it's not uncommon to encounter errors during the setup process. Understanding and resolving these errors is crucial for ensuring a smooth VPN experience on your Ubuntu system.
One common error users may face is connection timeouts or failures. This could be due to misconfigured network settings or firewall restrictions. To resolve this, first, ensure that your network connection is stable and that you have entered the correct VPN server address and credentials. Additionally, check your firewall settings to allow traffic through the VPN port.
Another frequent issue is compatibility problems with VPN protocols. Ubuntu supports various VPN protocols such as OpenVPN, IKEv2, and L2TP/IPsec. If you encounter errors related to protocol compatibility, try switching to a different protocol or updating your VPN client to the latest version that supports your preferred protocol.
DNS leaks can also occur, exposing your browsing activity despite being connected to a VPN. To fix this, configure Ubuntu to use the VPN's DNS servers instead of your default ones. This can usually be done through network settings or by modifying the VPN connection configuration file.
In some cases, VPN setup errors may stem from outdated software or missing dependencies. Ensure that your Ubuntu system is up to date with the latest software updates and packages installed. Additionally, check for any missing libraries or dependencies required by your VPN client and install them accordingly.
Lastly, if you're still encountering issues, reaching out to your VPN provider's support team or consulting Ubuntu's community forums can provide valuable assistance in troubleshooting and resolving setup errors. By addressing these common issues methodically, you can enjoy a secure and reliable VPN connection on your Ubuntu system.
0 notes
Text
Title: 10 Essential Linux Commands Every User Should Know
Linux is a popular operating system known for its stability, security, and flexibility. It is widely used in servers, supercomputers, and embedded devices. Linux commands are an essential part of the operating system, allowing users to perform various tasks and manage files, directories, and system settings. In this blog post, we will discuss the 10 essential Linux commands every user should know.
ls: The ‘ls’ command is used to list the files and directories in the current directory. It can display the file names, sizes, and modification dates. The command can also be used with various options to display hidden files, sort files by size or modification date, and more.
cd: The ‘cd’ command is used to change the current directory. It can be used to navigate to a specific directory or to move up and down the directory hierarchy. The command can also be used with relative or absolute paths to navigate to a specific location.
cp: The ‘cp’ command is used to copy files and directories. It can be used to copy a single file, a group of files, or an entire directory. The command can also be used with various options to preserve file attributes, overwrite existing files, and more.
mv: The ‘mv’ command is used to move or rename files and directories. It can be used to move a file or directory to a new location or to rename a file or directory. The command can also be used with various options to preserve file attributes and overwrite existing files.
rm: The ‘rm’ command is used to remove files and directories. It can be used to delete a single file, a group of files, or an entire directory. The command can also be used with various options to force the deletion of non-empty directories, preserve file attributes, and more.
mkdir: The ‘mkdir’ command is used to create new directories. It can be used to create a single directory or a group of directories. The command can also be used with various options to create directories with specific permissions, create directories in a specific location, and more.
rmdir: The ‘rmdir’ command is used to remove empty directories. It can be used to remove a single directory or a group of directories. The command can also be used with various options to force the removal of non-empty directories, preserve file attributes, and more.
chmod: The ‘chmod�� command is used to change the permissions of files and directories. It can be used to change the read, write, and execute permissions for the owner, group, and others. The command can also be used with various options to change permissions recursively, change permissions based on a mode, and more.
chown: The ‘chown’ command is used to change the ownership of files and directories. It can be used to change the owner and group of a file or directory. The command can also be used with various options to change ownership recursively, change ownership based on a user or group ID, and more.
chgrp: The ‘chgrp’ command is used to change the group ownership of files and directories. It can be used to change the group ownership of a file or directory. The command can also be used with various options to change group ownership recursively, change group ownership based on a group name, and more.
Conclusion: These 10 essential Linux commands are the foundation of Linux command-line management. By mastering these commands, users can perform various tasks, manage files and directories, and manage system settings. These commands are versatile and can be used in various situations, making them essential for any Linux user.
0 notes
Text
HDFS dfs

The command hdfs dfs refers to a set of command line operations associated with HDFS, the Hadoop Distributed File System. This is a part of the Apache Hadoop ecosystem and is used for storing large data sets in a distributed environment. The hdfs dfs command provides various functionalities to interact with data stored in HDFS.
Here are some everyday operations that can be performed using the hdfs dfs command:
List Files and Directories: hdfs dfs -ls /path/to/directory
Lists all files and directories in the specified HDFS directory.
Create Directories: hdfs dfs -mkdir /path/to/new/directory
Creates a new directory in HDFS.
Copy Files to HDFS: hdfs dfs -put local file /path/in/hdfs
Copies a file from the local filesystem to HDFS.
Copy Files from HDFS: hdfs dfs -get /path/in/hdfs local file
Copies a file from HDFS to the local filesystem.
Delete Files/Directories: hdfs dfs -rm /path/in/hdfs
Deletes a file or directory in HDFS.
View File Contents: hdfs dfs -cat /path/to/file
Displays the contents of a file in HDFS.
Append to a File: hdfs dfs -appendToFile local file /path/in/hdfs
Appends the contents of a local file to a file in HDFS.
Move Files in HDFS: hdfs dfs -mv /path/source /path/destination
Moves files within the HDFS.
Change File Permissions: hdfs dfs -chmod permissions /path/in/hdfs
Changes the permissions of a file or directory in HDFS.
Check File System Usage: hdfs dfs -du -h /path/in/hdfs
Displays the size of files and directories in HDFS in a human-readable format.
Remember, these are just a few operations you can perform with hdfs dfs. The Hadoop ecosystem is vast and offers a range of tools and commands for big data processing and management. Suppose you’re working in an environment where these commands are sent out as part of automated scripts or bulk operations. In that case, it’s essential to ensure they are correctly formatted and targeted to avoid unintended data loss or system impact.
Hadoop Training Demo Day 1 Video:
youtube
You can find more information about Hadoop Training in this Hadoop Docs Link
Conclusion:
Unogeeks is the №1 IT Training Institute for Hadoop Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Hadoop Training here — Hadoop Blogs
Please check out our Best In Class Hadoop Training Details here — Hadoop Training
S.W.ORG
— — — — — — — — — — — -
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
#unogeeks #training #ittraining #unogeekstraining
0 notes