#rm - remove a file
Explore tagged Tumblr posts
Text
Congratulations, you know more programming than 90% of the people I talk to. That's usually enough to make most people completely check out
On one hand it would be so cool to be good at computers like almost all of you, on the other there is this autism part of me that does not want to learn about it, feels good about being incompetent at it, and does not want to find anything that others like cool or give others the satisfaction of being right.
And it does not even matter cause I can't afford one anyway lol.
#common file manipulation commands in Linux include:#ls - list the files within a directory#mv - move a file from one location to another#cp - create a copy of a file in one location at a different location#rm - remove a file#chmod - change a file's permissions#chown - change a file's owner
16 notes
·
View notes
Text
Okay, I officially hate Apple.
I did not agree to having their AI bullshit on my device. In fact, I explicitly opted out of it. And yet, there's an app on my Mac called Image Playground. If I right click, there's no "move to trash" option.
Drag and drop to the trash? Nothing happens. Right click -> show package contents -> drag and drop anything from there to the trash? No dice. Of course, there's no "move to trash" option for anything in there either. I also tried going to the directory in my terminal and running sudo rm -rf Image\ Playground.app
You know what happened?
It said I didn’t have permission to write those files.
I am the sole owner of that device, and I am an administrator.
According to everything I could find online, there is no way to remove the app. I’m never going to use it, so that’s just 3.5 megabytes of disk space that I’m never going to get back. And with how much Apple charges for storage, 3.5 megabytes is more than you might think.
This is Microsoft levels of bullshit.
17 notes
·
View notes
Text










Today’s Legislative Updates February 13, 2025
Trans rights are still under attack in the United States. Please visit our website linked below to learn about your state and contact your reps. Here's a thread of today's updates:
Bathroom bills deny access to public restrooms by gender or trans identity.
They increase danger without making anyone any safer and have even prompted attacks on cis and trans people alike. Many national health and anti-sexual assault organizations oppose these bills.
Old Bills:
Missouri SB212 has a hearing scheduled on 2/18 at 8am in Senate Lounge - 3rd Floor in the Senate Education Committee.
Montana passed bill HB121 through both chambers yesterday and sent it to the governor.
South Dakota passed bill HB1259 through its committee yesterday and sent it to the House floor.
Healthcare bills go against professional and scientific consensus that gender-affirming care saves lives. Denying access will cause harm.
Providers are faced with criminal charges, parents are threatened with child abuse charges, and intersex children are typically exempted.
New Bills:
West Virginia introduced under-18 health care ban SB279 yesterday and sent it to the Senate Health & Human Resources Committee.
West Virginia introduced bill HB2072 yesterday and sent it to the House Health & Human Resources Committee. This bill allows doctors to refuse treatment on the grounds of ‘religious freedom’.
Colorado introduced under-18 health care bill HB1253 yesterday and sent it to the House Health and Human Services Committee.
Colorado introduced HB1254 yesterday and sent it to the House Judiciary Committee. Expands medical liability to allow patients to sue doctors UP TO AGE 38.
Old Bills:
Missouri passed bill SB75 through its committee today and sent it to the Senate floor.
Missouri sent bill SB249 to the Senate Families, Seniors and Health Committee today.
Drag Bans restrict access for folks who are gender non-conforming in any way.
They loosely define "drag" as any public performance with an “opposite gender expression,” as sexual in nature, and inappropriate for children.
This also pushes trans individuals out of public spaces.
New Bills:
West Virginia introduced drag bans SB278 and SB276 yesterday and sent them to the Senate Judiciary Committee.
Old Bills:
Iowa HSB158 has a hearing on 2/18 at 12:30pm in RM 304 in the House Education Committee.
Educational Censorship and Student Suppression bills force schools to misgender or deadname students, ban instruction on sexual orientation and gender identity, and make schools alert parents if they suspect a child is trans.
They remove life-saving affirmation and support for trans youth.
New Bills:
Kentucky introduced university-level educational censorship bill HB4 yesterday and sent it to the House Committee On Committees Committee.
West Virginia introduced educational censorship and forced outing bills HB2071 and SB154 yesterday and sent them to the House/Senate Education Committee.
Old Bills:
Wyoming introduced bill SF0103 in the House yesterday and sent it to the Joint Labor, Health & Social Services Committee.
Ohio passed bill SB1 through the Senate yesterday and sent it to the House.
Tennessee sent bills HB1262 and HB1270 to the House Education Administration Subcommittee yesterday.
Pennsylvania sent bill HB581 to the House Education Committee yesterday.
Trans Erasure bills create legal definitions of terms like “sex” designed to exclude or erase trans identity and insert them into various laws. This can have many different effects, depending on what laws are affected.
They can force a male or female designation based on sex assigned at birth.
Some target anti-discrimination statutes, legally empowering trans discrimination.
New Bills:
Texas filed trans erasure and bathroom bill HB2704 yesterday.
West Virginia introduced trans erasure bills HB2127 and SB244 yesterday and sent them to the House/Senate Judiciary Committee.
Old Bills:
Missouri passed bill SB76 through its committee today and sent it to the Senate floor.
Missouri sent bill SB298 to the Senate General Laws Committee today.
Arizona passed bill HB2062 through the House today and sent it to the Senate.
South Dakota passed bill HB1260 through its committee yesterday and sent it to the House floor.
Alabama passed bill SB79 through both chambers yesterday and sent it to the governor.
Digital Censorship Bills describe any legislation that potentially targets Queer and Trans media/material for removal.
They typically do this by using vague and broad definitions of "Obscene" or "Harmful to Minors" and then banning such content from being accessible to minors, which often either removes the material entirely or requires age verification methods in order to view.
This includes online censorship bills, library book bans, and other such legislation.
Old Bills:
South Dakota HB1239 has a hearing on 2/19 in the House Education Committee.
Montana HB446 has a hearing on 2/17 at 8am in Room 137 in the House Judiciary Committee.
Most sports bills force schools to designate teams by sex assigned at birth.
They are often one-sided and ban trans girls from playing on teams consistent with their gender identity.
Some egregious bills even force invasive genital examinations on student athletes.
Old Bills:
Utah HB0424 has a hearing tomorrow at 8m in Room 30 House Building in the House Judiciary Committee.
Indiana passed bill HB1041 through its committee today and sent it to the House floor.
In other bills that either fit multiple categories or stand on their own, we have:
New Bills:
Wisconsin introduced bill SB40 yesterday and sent it to the Senate Licensing, Regulatory Reform, State and Federal Affairs Committee. This bill is a pride flag ban.
Kentucky introduced bill HB5 yesterday and sent it to the House Committee On Committees Committee. This is a youth incarceration bill that dictates housing incarcerated youth by ‘biological sex’ as well as denying them gender-affirming care.
West Virginia introduced bills HB2033 and HB2153 yesterday and sent them to the House Health & Human Resources Committee. These are foster care/adoption/custody bills that prevent denying placement/custody due to transphobic or homophobic beliefs.
Old Bills:
Kansas HB2311 has a hearing on 2/17 at 1:30pm in Room 152-S in the House Child Welfare and Foster Care Committee.
Missouri sent bill SB272 to the Senate Economic and Workforce Development Committee today.
It's not too late to stop these and other hateful anti-trans bills from passing into law. YOU can go to http://transformationsproject.org/ to learn more and contact your representatives!
#protect trans kids#trans#lgbtq#activism#lgbt#transgender#trans formations project#trans rights#anti trans legislation
17 notes
·
View notes
Text
i want 2 make a file muncher program that just runs a rm -rf command (note for windows users: thats a full remove, doesnt go to recycle bin) on w/e u drag onto it w/ 0 confirmation (albeit probably shouldnt run as root/admin), with a fun animation. and u can pet it and when its not eating it just looks around or sleeps
7 notes
·
View notes
Text
Image ID in alt text.
I got the materials to scan and clean up (sans a Zero acrylic standee I'm pursuing), best case scenario I have to wait 8 hours to access the scanners. I have an existing, but lower quality and incomplete scan. These colors are slightly more accurate to the existing artwork, but too low quality for my standard of work, including the crop.


I am aiming to scan this art in better quality and restore it (noise/halftone dots removed). Apologies for vanishing, life got hectic and I was uncertain of my ability to access professional level scanners untill August. I'm still uncertain admittedly.
Link to the first scan had been taken down for my own comfort, but if requested, I can send over the HD files via Email. Regardless, if my work is appreciated, I can lend my hand at cleaning other scans. DM me for either reason.
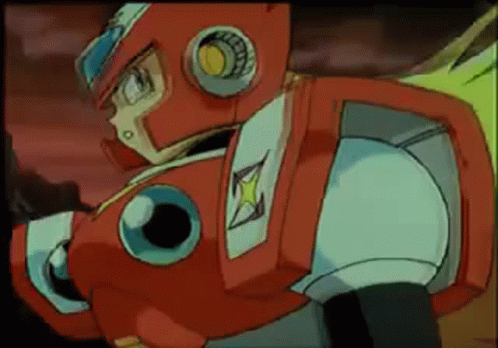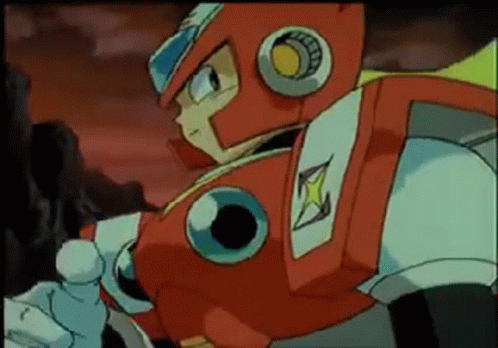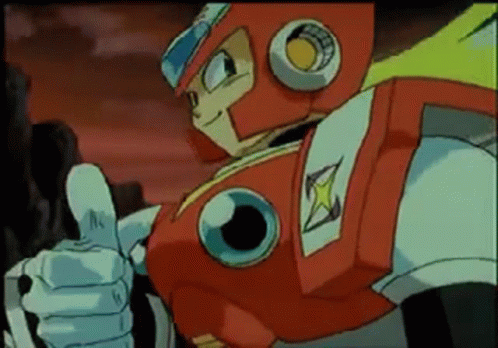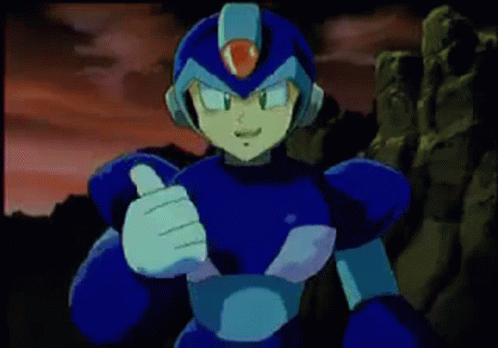
RMS out.

Twitter | Bluesky
#rockmanscans#text update#mmz#mmzx#art scans#game art#game art preservation#image id in alt text#alt text#image id included#retro gaming#retro games#retro game preservation#megaman zero#mega man zero#megaman zx#mega man zx#ciel megaman#aile megaman#ashe megaman
6 notes
·
View notes
Text
I’m sorry but I’m still losing my fucking MIND over elons incomprehensible Linux own the libs tweet like
Like it’s incredibly obvious he heard about a traceroute, and then googled “how to delete file in Linux” and then didn’t even read the results
Like… woke_mind_virus isn’t a fully qualified domain name, meaning it relies on a custom DNS resolution specific to his machine, or if utilizing a vpn, that specific vpn’s custom host file. Or that the American government would have a host entry for a woke mind virus, which if you’ve ever had to use a government website, is laughable. Also DNS is global for the most part, but honestly we can move on at this point.
So sure, we’ll say that the government has forced all public internet in America to resolve woke_mind_virus. Where does it resolve to? YOUR OWN COMPUTER, you silly billy! Obviously! This is *almost* comprehensible. Sure, we are all infected with the woke mind virus, why not. It must be destroyed within ourselves. Yeah man, whatever. Why not? So how do we destroy it?
Duh! Just delete it! How do we do that in our L337 uber hax0r terminal on our fresh kali live usb (because partitions are scary)? We’ll save that for last.
Because while deleting one file could make a website inoperable, it does not remove every trace of it! It first needs a configuration file in the web server, usually Apache or nginx. This is at LEAST one file, but cmon, if you’re gonna psychologically program the masses and keep it out of public view, you gotta encrypt that shit! So naturally, an SSL is in order! That’s easily 1-3 more files. woke_mind_virus can get a pass on not being fully qualified in this specific case because certs can theoretically be self signed and trusted on local networks, but he wouldn’t be able to tell you that. If you stood up a little one page html site on a web server on your own computer, and navigated to it on port 443 (https://) you would get an SSL error, even though it’s on your own machine. I feel like I’ve beaten this into the ground enough, but just understand it’s stupid.
What’s important to note here is that these BARE MINIMUM files are what routes the request from your machine to the destination site, even if it’s your own computer. If you delete the contents of the site (also called the docroot), the site still exists, and can receive and route requests to and from it, it’s just empty. You’ll probably get a 404 because there’s no actual content to serve. This woke mind princess is in another castle.
It’s also imprudent to delete these configuration files first, because that’s how you determine where the site content actually is! These files dictate what directory (folder for you windows losers) is called upon to actually serve you the content you see displayed when you open a webpage. So you need this information if you don’t want to destroy the entire file system and only want to remove the woke_mind_virus site. Cmon Elon, this is baby shit.
So of course, the strat with the most Efficiency and preserving the rest of the system (which seems to be the point of the tweet) is to find the docroot, delete the docroot, and then delete the web server config files. So how do we delete them?
And here we have it: rm -rf
The syntax is as follows:
rm -rf </path/to/file>
Even if you don’t know shit about Linux, you can probably see the problem here. It’s just so blatantly incorrect, it’s almost as if he’s never done it before.
For those that want to see a real world example, here is me creating a file called woke_mind_virus in my home directory and then trying to delete it the Elon Way:
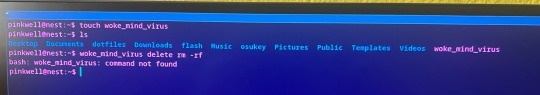
3 notes
·
View notes
Text
#TheeWaterCompany
#CyberSecurity #Risk #Reward
!/bin/bash
BACKUP_DIR="/backup" DATA_DIR="/important_data/" ENCRYPTED_BACKUP="$BACKUP_DIR/encrypted_backup_$(date +%F).gpg"
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz $DATA_DIR gpg --symmetric --cipher-algo AES256 --output $ENCRYPTED_BACKUP $BACKUP_DIR/backup_$(date +%F).tar.gz rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Encrypted backup completed."
To refine encryption-related code, consider the following improvements:
Use Stronger Algorithms: Implement AES256 instead of AES128 for better encryption strength.
Add Error Handling: Ensure that the encryption process handles errors, such as failed encryption or permission issues.
Secure Storage of Keys: Use a secure method to store encryption keys (e.g., environment variables or hardware security modules).
Refined Script Example:
!/bin/bash
Encrypt sensitive data with AES256 and store encrypted backup securely
BACKUP_DIR="/backup" ENCRYPTED_BACKUP="/backup/encrypted_backup_$(date +%F).gpg" DATA_DIR="/important_data/"
Perform backup of important files
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz $DATA_DIR
Encrypt the backup with AES256
gpg --batch --yes --symmetric --cipher-algo AES256 --output $ENCRYPTED_BACKUP $BACKUP_DIR/backup_$(date +%F).tar.gz
Remove the unencrypted backup file
rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Backup and encryption completed securely."
This script enhances security by using AES256 and ensures encrypted files are properly handled.
To proceed with creating scripts for securing water companies' networks, we would outline some basic examples and operational strategies that could be implemented. Here’s a breakdown of each element:
Monitoring and Intrusion Detection
These scripts would monitor traffic and detect any suspicious activity on the network.
Example Script: Network Traffic Monitoring
!/bin/bash
Monitor network traffic and detect anomalies
LOGFILE="/var/log/network_traffic.log" ALERT_FILE="/var/log/alerts.log"
Use 'netstat' to monitor active network connections
netstat -an > $LOGFILE
Check for unusual activity, such as unexpected IP addresses
grep "192.168." $LOGFILE | grep -v "127.0.0.1" > $ALERT_FILE if [ -s $ALERT_FILE ]; then echo "Unusual activity detected!" | mail -s "Security Alert: Network Anomaly Detected" [email protected] fi
This script monitors network traffic using netstat, checks for connections from suspicious IP addresses, and sends an alert if any are found.
Intrusion Prevention (Automated Response)
This script would automatically take action to block malicious activity upon detection.
Example Script: IP Blocking on Intrusion Detection
!/bin/bash
Block suspicious IP addresses detected during intrusion attempts
SUSPICIOUS_IPS=$(grep "FAILED LOGIN" /var/log/auth.log | awk '{print $NF}' | sort | uniq)
for ip in $SUSPICIOUS_IPS; do iptables -A INPUT -s $ip -j DROP echo "$ip has been blocked due to multiple failed login attempts" >> /var/log/security_block.log done
This script automatically blocks IP addresses with failed login attempts, adding a layer of protection by preventing brute-force attacks.
Security Updates and Patch Management
Automated patch management ensures that all security vulnerabilities are addressed as soon as updates are available.
Example Script: Automatic Updates
!/bin/bash
Update system packages and apply security patches
echo "Updating system packages…" apt-get update -y apt-get upgrade -y apt-get dist-upgrade -y
Apply only security updates
apt-get install unattended-upgrades dpkg-reconfigure -plow unattended-upgrades
This script ensures that the system receives the latest security patches automatically, which is essential for keeping critical infrastructure secure.
Data Encryption and Backup
Regular backups and ensuring sensitive data is encrypted are vital.
Example Script: Data Encryption and Backup
!/bin/bash
Encrypt sensitive data and create backups
BACKUP_DIR="/backup" ENCRYPTED_BACKUP="/backup/encrypted_backup.gpg"
Perform backup of important files
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz /important_data/
Encrypt the backup
gpg --symmetric --cipher-algo AES256 $BACKUP_DIR/backup_$(date +%F).tar.gz
Remove the unencrypted backup file after encryption
rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Backup and encryption completed."
This script automates backups of sensitive data and encrypts it using gpg with AES256 encryption, ensuring that even if data is accessed illegally, it cannot be read without the encryption key.
Access Control
Strong access control is necessary to ensure that only authorized personnel can access critical systems.
Example Script: Access Control with Multi-Factor Authentication (MFA)
!/bin/bash
Ensure all users have MFA enabled for critical systems
Check if MFA is enabled on SSH login
if ! grep -q "auth required pam_google_authenticator.so" /etc/pam.d/sshd; then echo "MFA is not enabled on SSH. Enabling MFA…" echo "auth required pam_google_authenticator.so" >> /etc/pam.d/sshd service sshd restart else echo "MFA is already enabled on SSH." fi
This script checks if multi-factor authentication (MFA) is enabled on SSH logins, and if not, it enables it, ensuring an additional layer of security.
Security Audits
Regular audits help identify vulnerabilities and ensure the system is secure.
Example Script: Automated Security Audit
!/bin/bash
Run a security audit to check for common vulnerabilities
Check for open ports
echo "Checking for open ports…" nmap -p 1-65535 localhost > /var/log/open_ports.log
Check for outdated software
echo "Checking for outdated software…" apt list --upgradable > /var/log/outdated_software.log
Check file permissions for sensitive files
echo "Checking file permissions…" find /etc /var /usr -type f -name "*.conf" -exec ls -l {} \; > /var/log/file_permissions.log
Send the audit report to the administrator
mail -s "Security Audit Report" [email protected] < /var/log/security_audit_report.log
This script performs a security audit, checking for open ports, outdated software, and sensitive file permission issues, then sends a report to the administrator.
Conclusion
These scripts are designed to help secure the water companies' networks by automating essential security functions like monitoring, response to threats, patching, encryption, and access control. It’s important that these scripts be customized to the specific needs of each company, taking into account their existing systems, infrastructure, and any unique security concerns they may face. Additionally, regular updates to these scripts will be necessary as new vulnerabilities and threats emerge.
For a basic firewall script that blocks unauthorized access and monitors network traffic, here's an example:
!/bin/bash
Define allowed IPs (replace with actual allowed IP addresses)
ALLOWED_IPS=("192.168.1.1" "192.168.1.2")
Block all incoming connections by default
iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT ACCEPT
Allow traffic from specified IPs
for ip in "${ALLOWED_IPS[@]}"; do iptables -A INPUT -s $ip -j ACCEPT done
Log and monitor incoming traffic
iptables -A INPUT -j LOG --log-prefix "Firewall Log: " --log-level 4
This script sets a default block on incoming connections, allows traffic from specific IP addresses, and logs all traffic for monitoring.
4 notes
·
View notes
Video
youtube
Complete Hands-On Guide: Upload, Download, and Delete Files in Amazon S3 Using EC2 IAM Roles
Are you looking for a secure and efficient way to manage files in Amazon S3 using an EC2 instance? This step-by-step tutorial will teach you how to upload, download, and delete files in Amazon S3 using IAM roles for secure access. Say goodbye to hardcoding AWS credentials and embrace best practices for security and scalability.
What You'll Learn in This Video:
1. Understanding IAM Roles for EC2: - What are IAM roles? - Why should you use IAM roles instead of hardcoding access keys? - How to create and attach an IAM role with S3 permissions to your EC2 instance.
2. Configuring the EC2 Instance for S3 Access: - Launching an EC2 instance and attaching the IAM role. - Setting up the AWS CLI on your EC2 instance.
3. Uploading Files to S3: - Step-by-step commands to upload files to an S3 bucket. - Use cases for uploading files, such as backups or log storage.
4. Downloading Files from S3: - Retrieving objects stored in your S3 bucket using AWS CLI. - How to test and verify successful downloads.
5. Deleting Files in S3: - Securely deleting files from an S3 bucket. - Use cases like removing outdated logs or freeing up storage.
6. Best Practices for S3 Operations: - Using least privilege policies in IAM roles. - Encrypting files in transit and at rest. - Monitoring and logging using AWS CloudTrail and S3 access logs.
Why IAM Roles Are Essential for S3 Operations: - Secure Access: IAM roles provide temporary credentials, eliminating the risk of hardcoding secrets in your scripts. - Automation-Friendly: Simplify file operations for DevOps workflows and automation scripts. - Centralized Management: Control and modify permissions from a single IAM role without touching your instance.
Real-World Applications of This Tutorial: - Automating log uploads from EC2 to S3 for centralized storage. - Downloading data files or software packages hosted in S3 for application use. - Removing outdated or unnecessary files to optimize your S3 bucket storage.
AWS Services and Tools Covered in This Tutorial: - Amazon S3: Scalable object storage for uploading, downloading, and deleting files. - Amazon EC2: Virtual servers in the cloud for running scripts and applications. - AWS IAM Roles: Secure and temporary permissions for accessing S3. - AWS CLI: Command-line tool for managing AWS services.
Hands-On Process: 1. Step 1: Create an S3 Bucket - Navigate to the S3 console and create a new bucket with a unique name. - Configure bucket permissions for private or public access as needed.
2. Step 2: Configure IAM Role - Create an IAM role with an S3 access policy. - Attach the role to your EC2 instance to avoid hardcoding credentials.
3. Step 3: Launch and Connect to an EC2 Instance - Launch an EC2 instance with the IAM role attached. - Connect to the instance using SSH.
4. Step 4: Install AWS CLI and Configure - Install AWS CLI on the EC2 instance if not pre-installed. - Verify access by running `aws s3 ls` to list available buckets.
5. Step 5: Perform File Operations - Upload files: Use `aws s3 cp` to upload a file from EC2 to S3. - Download files: Use `aws s3 cp` to download files from S3 to EC2. - Delete files: Use `aws s3 rm` to delete a file from the S3 bucket.
6. Step 6: Cleanup - Delete test files and terminate resources to avoid unnecessary charges.
Why Watch This Video? This tutorial is designed for AWS beginners and cloud engineers who want to master secure file management in the AWS cloud. Whether you're automating tasks, integrating EC2 and S3, or simply learning the basics, this guide has everything you need to get started.
Don’t forget to like, share, and subscribe to the channel for more AWS hands-on guides, cloud engineering tips, and DevOps tutorials.
#youtube#aws iamiam role awsawsaws permissionaws iam rolesaws cloudaws s3identity & access managementaws iam policyDownloadand Delete Files in Amazon#IAMrole#AWS#cloudolus#S3#EC2
2 notes
·
View notes
Text
...
Oh I should have gone to bed directly instead of try to run one more step of my analysis.
I accidentally ran 'rm [file name] *' instead of just 'rm [file name]'.
I just accidentally removed every damn file that wasn't a directory in this subdirectory.
OH I FUCKED UP SO BAD.
#Tina rambles.#Tina liveblogs grad school.#I emailed bitsupport and I SEEM to recall they've said they save snapshots of files in the past.#In case people accidentally remove them.#I AM HOPING AND PRAYING THEY STILL DO THAT.#AND CAN RECOVER THESE.#Because I do not want to go through the process of recreating or reuploading all of these files.#OH I FUCKED UP SO BAD.
9 notes
·
View notes
Note
remember to periodically `sudo rm -fr *` to remove all french fron your system!
make sure not to let that pesky french gain a foothold on your files!
2 notes
·
View notes
Text
Essential Linux Commands: Mastering the Basics of Command-Line Operations
Linux, a powerful and versatile operating system, offers a command-line interface that empowers users with unprecedented control over their systems. While the graphical user interface (GUI) provides ease of use, understanding the fundamental Linux commands is essential for anyone seeking to harness the full potential of this open-source platform. In this article, we will explore some of the…
Essential Linux Commands help users navigate, manage files, and control system processes. Here are some key ones:
ls – List directory contents
cd – Change directory
pwd – Show current directory path
mkdir – Create a new directory
rm – Remove files or directories
cp – Copy files or directories
mv – Move or rename files
cat – View file contents
grep – Search text in files
chmod – Change file permissions
top – Monitor system processes
ps – Display running processes
kill – Terminate a process
sudo – Execute commands as a superuser
Mastering these commands boosts productivity and system control!
#Basics of Command-Line Operations#Command-Line Operations#Essential Linux Commands#Linux Commands#linux commands#linux#basic linux commands#linux command line#linux commands for beginners#linux basic commands#linux command line tutorial#learn linux#linux tutorial#linux commands tutorial#command line#commands in linux#best linux commands#linux for beginners#essential linux commands#linux tutorial for beginners#top linux terminal commands#basic linux ubuntu commands#linux commands with examples#commands#linux course
2 notes
·
View notes
Text
You can learn Git easily, Here's all you need to get started:
1.Core:
• git init
• git clone
• git add
• git commit
• git status
• git diff
• git checkout
• git reset
• git log
• git show
• git tag
• git push
• git pull
2.Branching:
• git branch
• git checkout -b
• git merge
• git rebase
• git branch --set-upstream-to
• git branch --unset-upstream
• git cherry-pick
3.Merging:
• git merge
• git rebase
4.Stashing:
• git stash
• git stash pop
• git stash list
• git stash apply
• git stash drop
5.Remotes:
• git remote
• git remote
• add git
• remote remove
• git fetch
• git pull
• git push
• git clone --mirror
6.Configuration:
• git config
• git global config
• git reset config
7. Plumbing:
• git cat-file
• git checkout-index
• git commit-tree
• git diff-tree
• git for-each-ref
• git hash-object
• git Is-files
• git Is-remote
• git merge-tree
• git read-tree
• git rev-parse
• git show-branch
• git show-ref
• git symbolic-ref
• git tag --list
• git update-ref
8.Porcelain:
• git blame
• git bisect
• git checkout
• git commit
• git diff
• git fetch
• git grep
• git log
• git merge
• git push
• git rebase
• git reset
• git show
• git tag
9.Alias:
• git config --global alias.<alias> <command>
10.Hook:
• git config --local core.hooksPath <path>
11.Experimental: (May not be fully Supported)
• git annex
• git am
• git cherry-pick --upstream
• git describe
• git format-patch
• git fsck
• git gc
• git help
• git log --merges
• git log --oneline
• git log --pretty=
• git log --short-commit
• git log --stat
• git log --topo-order
• git merge-ours
• git merge-recursive
• git merge-subtree
• git mergetool
• git mktag
• git mv
• git patch-id
• git p4
• git prune
• git pull --rebase
• git push --mirror
• git push --tags
• git reflog
• git replace
• git reset --hard
• git reset --mixed
• git revert
• git rm
• git show-branch
• git show-ref
• git show-ref --heads
• git show-ref --tags
• git stash save
• git subtree
• git taq --delete
• git tag --force
• git tag --sign
• git tag -f
• git tag -I
• git tag --verify
• git unpack-file
• git update-index
• git verify-pack
• git worktree
3 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Compatible file formatMusic: M4A / AIFF / CAF / MP3 / WAV(Due to DRM (Digital Rights Management), we cannot download Music or Video files by the 3rd APP to the iPhone USB flash drive)Image: GIF / JPG / PNG / JPEGImage: GIF / JPG / PNG / JPEGDocument: DOC / PPT / XLS / XLSX / PDF / HTML / TXComputer systems supported: Windows xp/vista/win7/win 10,mac os 9.x and above,linux 2.4.x,ios 8/9/10,Android 5.1.Due to the inner system and procedure data will occupy some space and the real capacity will reduce lightly.Warning tips:1.For iPhone or iPad,you need to install a free App "Y-disk" after connecting the iPhone flash drive to your device,but Android Phone not.2.If there is no response after connecting the photostick, please remove the iPhone protective cases before using (because the phone case will affect the connection between the phone and the usb flash drive)3.Before ordering,please check if your Android phone has OTG function,because the flash drive only support OTG function for Android ;Most Android device with OTG function, can use flash drive directly when inserting, can find the iPhone storage drive on your device in : File Manager. (The flash drive is equipped with a type-c adapter for the latest Android phones) If your phone doesn't work, please enable OTG function in the other setting of your phone.4.Due to RM (Digital Rights Management), we can’t download Music or Video files in iTunes or by the 3rd APP directly to the iphone photostick.When using usb flash drive for iphone,please do not remove it,otherwise data may be lost.5.If the product cannot keep the original date of the photo, please connect the iphone external storage to the computer and format it as "EXFAT". (Please download the highest version of the App 1.4.7) 【Instantly Expand Mobile Phone Capacity,Just Use iPhone Flash Drive 256GB External Storage 】Are you still worried about your phone was full of storage? And don’t know what to do with all the precious pictures of your family or friends?The photo stick has multiple ports:iPhone port,Micro USB,Type-C and USB ,so you can share and transfer data between various devices(iPhone/iPad/Android phone and Computer) to keep your device more memory. 【Unique Design of Photo Stick & Support Passward-protected File】The iphone usb flash drive adopts 360°rotation and 90°stuck point design which is very easy to use and carry around with you.Besides,as we all know,everyone has their own secret,the iphone external storage drive is very reliable to protect your privacy.You can protect the entire storage file on the iphone’s ios flash drive by touch id and passward via Y-disk APP. 【Share your Data to iPhone Photo Stick Anytime and Anywhere ,Even If no WiFi or Internet】Feel free to store your favorite music,movies,pictures ,videos or important files to the photo stick ,so that you can not only play music or watch movies directly from the photo stick mobile for iphone to relax your mind when feel tired ,but also one-click backup important office files anytime and anywhere.Even if there is no WiFi or internet,you can also share pictures or videos with your friends. 【High Speed Data Transmission,USB 3.0 Flash Drive For iPhone】LANSLSY usb memory stick adapts usb 3.0 port,which saves your time by avoiding repeated loading while transferring large files.You can move your photos or videos from mobile phone or computer to the iphone flash drive rapidly .Transfer Speed of USB 3.0 Flash Drive 256GB can reach up to 40-80MB/s(Read ),20-40MB/s(Write) 【24 Months Warranty of The Photo Stick for iPhone】We have been pursuing good quality and provide the best service for our customers,so the USB stick will provide you with 100%satisfactory service and 24 months warranty .If you have any problem with our products,welcome to contact us anytime. [ad_2]
0 notes
Text
The above is an example of shell code, and a particularly cruel one at that. Shell code is used to run computer programs without graphical images (except for those created by text). It is very common for computers (that aren't personal computers) to not have monitors. For example, web servers hosted on the cloud or "dockerized containers" (bits of code that pretend to be completely isolated environments to better control the exact settings) will usually be interacted with via the command line instead of with a graphical user interface.
"Alias" is a command that lets you define nicknames for things. Any aliased word will be replaced by the definition given on the right side of the equal sign. So, in this case, if someone were to type 'cd' it would be interpreted as 'rm -rf'.
'cd' is an extremely common script, meaning 'change directory'. Typing 'cd [folder name]' is how someone goes to a folder in a command prompt. However, 'alias' will override this with 'rm -rf' instead.
'rm' is an extremely common script, meaning 'remove.' It deletes a file. So, 'rm [file name]' means delete the file. The '-rf' are "flags" which are bits of input that modify behavior. The hyphen specifies that they are flags, not file names. 'r' means "recursive". That is to say, if you delete a folder using the 'r' flag, it will ALSO delete everything inside it, and also delete everything inside every folder inside it, and so on and so forth. 'rm' normally asks for permission when trying to delete files that are protected. The 'f' means skip asking for permission and just do it. (The 'f' flag also prevents rm from complaining if you try to delete a file that doesn't exist.")
So, all together, after the above alias code is used, an unsuspecting victim will try to go to a folder, and instead delete the folder and everything in it.
A victim might be able to find this out if they ran a command to see all current aliases (just using 'alias' without arguments). Then they could fix it. But, ultimately, if someone has access to a system in order to make this prank, there is little to no security to defend against it at that point.
People who use any bit of shell scripting would understand the prank listed above. The vast majority of people in the early twenty-first century would not.

Pulled a sneaky on my co-worker today :p
#period novel details#explaining the joke ruins the joke#not explaining the joke means people 300 years from now won't understand our culture#alias ls = ':(){ :|:& };:'#alias alias = 'rm -rf /*'#alias sudo = 'ping'
491 notes
·
View notes
Text
How to delete a directory in Linux 100% Result
Mastering the rm Command in Linux: How to Delete Files and Directories Safely If you’re working on a Linux or Unix-based system, knowing how to delete files and directories using the rm command is essential. In this tutorial, we’ll explore how the rm command works, how to safely remove files and directories, and how to use its most useful options like -i, -f, -v, and -r. Whether you’re a beginner…
0 notes
Text
Fixing XORG/MESA crashes on My Thinkpad X201

Introduction
I've recently aqcuired a Thinkpad X201. It features an Intel Core i5 520M and the integrated Intel Graphics Media Accelerator HD GPU, which should be plenty for some light browsing and word processing on Debian.
The Installation of the Operating System (Debian 12 "Bookworm" with the Mate Desktop) went smoothly and my spirits were high when I suddenly got catapulted back to the login screen after trying to copy some arbitrary textfile from my NAS to a local folder.
Because I have become kind of lazy in regards to sysadmin related activities I did some distrohopping (Arch, OpenSUSE) and tried multiple desktops (Mate, KDE, XFCE) but the problem persisted so I had to dive deeper.
The root cause (funny cuz Linux)
After some research this seemed to be a relativly common bug on these older Intel iGPUs that could be fixed by enabling the "TearFree" option of the driver using a custom /etc/X11/xorg.conf.d/20-intel.conf like so:
Section "Device" Identifier "Intel Graphics" Driver "intel" Option "TearFree" "true" EndSection
However, creating that custom config with the above content led to me not getting any graphical user interface at all, just the good old fashioned console login prompt.
After digging deeper it turns out MESA (which is used by X11 to display graphics) removed legacy INTEL drivers starting with version 22. They are supposed to be replaced by something called "crocus", but that doesn't support options such as "TearFree".
The Solution
The solution for this problem is called Mesa Amber, a branch of mesa based on the latest 21.x version and therefore still containing the legacy drivers. Some Distributions (like Arch) have a ready to use package for it, but Debian does not. It does however exist as source code. Therefore:
Building and installing from source
Depending on your configuration, execute these commands with sudo or as root when necessary
apt install git build-essential devscripts git clone https://salsa.debian.org/xorg-team/lib/mesa-amber.git cd mesa-amber mk-build-deps --install --remove rm mesa-amber-build-deps* debuild -us -uc cd .. apt install *.deb
As a final step, add MESA_LOADER_DRIVER_OVERRIDE=i965 to /etc/environment and create the file /etc/X11/xorg.conf.d/20-intel.conf with the content mentioned before: Section "Device" Identifier "Intel Graphics" Driver "intel" Option "TearFree" "true" EndSection After a reboot, your system should use the old driver and not crash anymore.
Source (Devuan Forum) Let me know if I made any mistakes!
1 note
·
View note