#classical cryptography
Explore tagged Tumblr posts
Text
I got a Barbie Typewriter!
After a couple years of searching, I finally managed to get my hands on a Barbie toy electric typewriter!
For the unfamiliar, a neat aspect of Barbie typewriters is that some models have built-in cipher encoding and decoding modes, which, due to some quirks in how the typewriters were developed and marketed, were not advertised as features, so the cipher functionality was basically secret!
These days, the old school Barbie typewriters are relatively rare and usually pretty expensive, although the one I got was actually fairly cheap, due to being in somewhat rough condition. It unfortunately had quite a bit of battery corrosion, so it was untested and sold to be a “display piece”:

It even came with the original box (although it is certainly a little worse for wear lol)
The battery compartment was absolutely filled with corrosion residue, and traces of it had spread across the whole typewriter—it was everywhere!

I’m no expert in electronics, but I know that the presence of battery corrosion doesn’t necessarily mean that a gadget is broken beyond all repair, so I decided to try to see if a thorough cleaning could possibly get it working again.
So, I cleaned up the battery compartment with vinegar, took the whole back of the case off and wiped out the inside of it (which was coated in a thin layer of corrosion dust), and finally popped in some new C batteries. Then came the moment of truth, flipping the power switch!

And…nothing. Darn. 😔
Ah, well, it’s still a very cool display piece, and I’m happy to have it!

#Barbie#Barbie typewriter#typewriters#classical cryptography#long post#sC original#I had honestly resigned myself to the fact that I would never get one of these so I was THRILLED to find this :)
13 notes
·
View notes
Text
31 Days

Exactly a month ago, I started playing this game that my extended family had made. It's a daily math game, or like, a daily classical cryptography game. I have been solving the new puzzles each day, for 31 days.
I'm still taking it in, you know? I've never had such a clear idea of how long a month is, but now I have to know: It's the time between getting an email showing me this game and right now. Perhaps this should horrify me, as confronting the passage of time should come with the spectre of mortality. But as someone who has never believed herself to have a future, it has the opposite effect. It gives me a sense of just how time passes, how long things take, and how much I can do in a month.
But it's hard to believe there can be anything in my life so consistent. I flounder between projects and take opportunities when they come, my activities or mood on any given day is largely dependent on fate and happenstance. But I have somehow managed to do this one tiny thing each day for a month. It makes me think about the importance of rituals, to have something in your life that can anchor you in time.
These days, games come packed with rituals in some form or another. Plenty of games, online and offline, come with daily bonuses, daily activities, and rewards for sticking with it, every day. It's hard to know where to draw a line. These techniques are a few of many that companies can use to extract every bit of time, money, and attention out of you. But in individual cases I am okay with them. I like the daily nature of Wordle or Animal Crossing. I like it when Fire Emblem Fates or Bravely Default give me small rewards as real-world time passes. In the days of the DS or 3DS these mechanics felt more experimental and benign. I can't help but wonder if that was ever really true.
Summary is an ephemeral game. It changes every day, and a missed day cannot be taken back. Missing a day in my streak was actually what made me give up Wordle, unsurprisingly, and that'll probably be what gets me to drop this game. Back when Wordle was popular, there was a controversy over it being ephemeral like this. Some didn't like its daily slow-paced nature, which is fair enough if you don't care for game as ritual. Others made an argument that the daily format is inherently anti-preservation, as one day's experience will never be the same as the next. I balk at this framing, as someone in theatre. Yes, some art cannot be truly (or at least losslessly) preserved. It is of the moment, and that is part of the beauty of it. For art to be an event, for it to require you to be there, in that moment, is not as terrible a thing as some would tell you.
Thinking on it after a month, I'm not sure if I'd say I "like" Summary as a math-y puzzle game. It's missing the kind of tension and strategy that Wordle has, and while its puzzles are certainly coherent, I don't really feel like I'm getting "better" at the game, or that it particularly wants me to. I'm curious to ask the developers how they designed these puzzles, because as a designer, this game is a fascinating piece of work. But the Wordle formula is... It's one of those things, you know? It's like Minesweeper, it has a set of mechanics that just works, and it's hard to replicate without losing the charm somewhere. Summary is a good attempt, one I've stuck with for a month and plan to continue. But the ritual matters more than the game.
2 notes
·
View notes
Text






The vibes for another ones of my OCs for a fantasy/dark academia novel!
Her name is Solveig and I love her dearly so I hope you’ll like her too.
A few facts about her as an introduction:
She is a passionate reader and dabbles in alchemy, occultism and cryptography.
She loves waking up early, drinks six cups of coffee per day and has a pet crow named Huginn.
In the novel she will be one of Charles’ love interests and his mentor (and then, eventually, they will become academic rivals).
Photo credit to Pinterest
#academia aesthetic#dark academia#booklover#reader#bookdragon#dark academia books#classic academia#oc#oc aesthetic#dark acadamia aesthetic#occultism#cryptography#enemies to lovers#rivals to lovers#academic rivals#romantic academia#oc vibes#original character#writerblr#female writers#pinterest
41 notes
·
View notes
Text
Why Quantum Computing Will Change the Tech Landscape
The technology industry has seen significant advancements over the past few decades, but nothing quite as transformative as quantum computing promises to be. Why Quantum Computing Will Change the Tech Landscape is not just a matter of speculation; it’s grounded in the science of how we compute and the immense potential of quantum mechanics to revolutionise various sectors. As traditional…
#AI#AI acceleration#AI development#autonomous vehicles#big data#classical computing#climate modelling#complex systems#computational power#computing power#cryptography#cybersecurity#data processing#data simulation#drug discovery#economic impact#emerging tech#energy efficiency#exponential computing#exponential growth#fast problem solving#financial services#Future Technology#government funding#hardware#Healthcare#industry applications#industry transformation#innovation#machine learning
3 notes
·
View notes
Text
Toward a code-breaking quantum computer
New Post has been published on https://thedigitalinsider.com/toward-a-code-breaking-quantum-computer/
Toward a code-breaking quantum computer
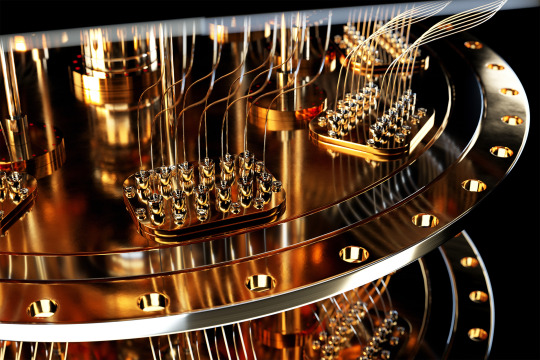

The most recent email you sent was likely encrypted using a tried-and-true method that relies on the idea that even the fastest computer would be unable to efficiently break a gigantic number into factors.
Quantum computers, on the other hand, promise to rapidly crack complex cryptographic systems that a classical computer might never be able to unravel. This promise is based on a quantum factoring algorithm proposed in 1994 by Peter Shor, who is now a professor at MIT.
But while researchers have taken great strides in the last 30 years, scientists have yet to build a quantum computer powerful enough to run Shor’s algorithm.
As some researchers work to build larger quantum computers, others have been trying to improve Shor’s algorithm so it could run on a smaller quantum circuit. About a year ago, New York University computer scientist Oded Regev proposed a major theoretical improvement. His algorithm could run faster, but the circuit would require more memory.
Building off those results, MIT researchers have proposed a best-of-both-worlds approach that combines the speed of Regev’s algorithm with the memory-efficiency of Shor’s. This new algorithm is as fast as Regev’s, requires fewer quantum building blocks known as qubits, and has a higher tolerance to quantum noise, which could make it more feasible to implement in practice.
In the long run, this new algorithm could inform the development of novel encryption methods that can withstand the code-breaking power of quantum computers.
“If large-scale quantum computers ever get built, then factoring is toast and we have to find something else to use for cryptography. But how real is this threat? Can we make quantum factoring practical? Our work could potentially bring us one step closer to a practical implementation,” says Vinod Vaikuntanathan, the Ford Foundation Professor of Engineering, a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL), and senior author of a paper describing the algorithm.
The paper’s lead author is Seyoon Ragavan, a graduate student in the MIT Department of Electrical Engineering and Computer Science. The research will be presented at the 2024 International Cryptology Conference.
Cracking cryptography
To securely transmit messages over the internet, service providers like email clients and messaging apps typically rely on RSA, an encryption scheme invented by MIT researchers Ron Rivest, Adi Shamir, and Leonard Adleman in the 1970s (hence the name “RSA”). The system is based on the idea that factoring a 2,048-bit integer (a number with 617 digits) is too hard for a computer to do in a reasonable amount of time.
That idea was flipped on its head in 1994 when Shor, then working at Bell Labs, introduced an algorithm which proved that a quantum computer could factor quickly enough to break RSA cryptography.
“That was a turning point. But in 1994, nobody knew how to build a large enough quantum computer. And we’re still pretty far from there. Some people wonder if they will ever be built,” says Vaikuntanathan.
It is estimated that a quantum computer would need about 20 million qubits to run Shor’s algorithm. Right now, the largest quantum computers have around 1,100 qubits.
A quantum computer performs computations using quantum circuits, just like a classical computer uses classical circuits. Each quantum circuit is composed of a series of operations known as quantum gates. These quantum gates utilize qubits, which are the smallest building blocks of a quantum computer, to perform calculations.
But quantum gates introduce noise, so having fewer gates would improve a machine’s performance. Researchers have been striving to enhance Shor’s algorithm so it could be run on a smaller circuit with fewer quantum gates.
That is precisely what Regev did with the circuit he proposed a year ago.
“That was big news because it was the first real improvement to Shor’s circuit from 1994,” Vaikuntanathan says.
The quantum circuit Shor proposed has a size proportional to the square of the number being factored. That means if one were to factor a 2,048-bit integer, the circuit would need millions of gates.
Regev’s circuit requires significantly fewer quantum gates, but it needs many more qubits to provide enough memory. This presents a new problem.
“In a sense, some types of qubits are like apples or oranges. If you keep them around, they decay over time. You want to minimize the number of qubits you need to keep around,” explains Vaikuntanathan.
He heard Regev speak about his results at a workshop last August. At the end of his talk, Regev posed a question: Could someone improve his circuit so it needs fewer qubits? Vaikuntanathan and Ragavan took up that question.
Quantum ping-pong
To factor a very large number, a quantum circuit would need to run many times, performing operations that involve computing powers, like 2 to the power of 100.
But computing such large powers is costly and difficult to perform on a quantum computer, since quantum computers can only perform reversible operations. Squaring a number is not a reversible operation, so each time a number is squared, more quantum memory must be added to compute the next square.
The MIT researchers found a clever way to compute exponents using a series of Fibonacci numbers that requires simple multiplication, which is reversible, rather than squaring. Their method needs just two quantum memory units to compute any exponent.
“It is kind of like a ping-pong game, where we start with a number and then bounce back and forth, multiplying between two quantum memory registers,” Vaikuntanathan adds.
They also tackled the challenge of error correction. The circuits proposed by Shor and Regev require every quantum operation to be correct for their algorithm to work, Vaikuntanathan says. But error-free quantum gates would be infeasible on a real machine.
They overcame this problem using a technique to filter out corrupt results and only process the right ones.
The end-result is a circuit that is significantly more memory-efficient. Plus, their error correction technique would make the algorithm more practical to deploy.
“The authors resolve the two most important bottlenecks in the earlier quantum factoring algorithm. Although still not immediately practical, their work brings quantum factoring algorithms closer to reality,” adds Regev.
In the future, the researchers hope to make their algorithm even more efficient and, someday, use it to test factoring on a real quantum circuit.
“The elephant-in-the-room question after this work is: Does it actually bring us closer to breaking RSA cryptography? That is not clear just yet; these improvements currently only kick in when the integers are much larger than 2,048 bits. Can we push this algorithm and make it more feasible than Shor’s even for 2,048-bit integers?” says Ragavan.
This work is funded by an Akamai Presidential Fellowship, the U.S. Defense Advanced Research Projects Agency, the National Science Foundation, the MIT-IBM Watson AI Lab, a Thornton Family Faculty Research Innovation Fellowship, and a Simons Investigator Award.
#2024#ai#akamai#algorithm#Algorithms#approach#apps#artificial#Artificial Intelligence#author#Building#challenge#classical#code#computer#Computer Science#Computer Science and Artificial Intelligence Laboratory (CSAIL)#Computer science and technology#computers#computing#conference#cryptography#cybersecurity#defense#Defense Advanced Research Projects Agency (DARPA)#development#efficiency#Electrical Engineering&Computer Science (eecs)#elephant#email
5 notes
·
View notes
Text
literally Just got back & already staring at the books i need 2 organize with stress tears =___=
#GOD. god. fuck. going to install built ins w/ my siblings in a couple weeks so idk if i even should bother. but stilllllllllllllllllllll.#need 2 organize poetry / folklore / arthuriana / taschen / general art books / math & logic & cryptography / mystery anthologies#/ illustrated classics / all of the classics by time period & country............ ghghgh.#txt
4 notes
·
View notes
Text
gustav when you ask him for help using his filmmaking skills: :) gustav when you ask him for help using his codemaking/breaking skills: :/ :(
#he's so tired of being taken advantage of for cryptography reasons#no one ever wants to ask questions about how to film a musical adaptation of classic dramas#or how to add zombies into them#ooc.
1 note
·
View note
Text
That thing is actually a quantum fridge. Mind you if it was a functioning quantum computer you might be able to post memes that were entangled with elections
That picture of Biden looking at a quantum computer and being unable to grasp the true form of what he's seeing

To be fair that's how I would I react too
#had a job that involved being shown a lot of quantum fridges.#made these jokes a lot.#made this face a lot.#had to hear a lot of people tell me sincerely that the future of quantum computing is not in making a quantum computer#which we dont exactly have yet#but in quantum software which you would run on the computer you don’t have#and post-quantum cryptography and so on#which is all excessively nice and interesting but the discussions themselves are so inherently quantum#that you’re like. ok. can we have a classical conversation now#the future IS the future I agree.#👆
44K notes
·
View notes
Text
I feel like Parker could get really into cryptography. Both in general but also specifically in a conspiracy theory ‘there are hidden messages in everything’ kind of way.
We’ve already seen her fall for conspiracy theories (The Three Days of the Hunter Job) and she loves puzzles, so I feel like it isn’t too far of a leap for her to start analyzing every message for secrets.
Also, considering Archie was a Classic Gentleman Thief ™️ I feel like he had to have taught her some old school spy hidden message stuff.
It isn’t really a problem until she starts using code in everything she says - in text or in person. A changing code that the others have to Hack in order to figure out what she wants.
Parker: The Walls Can’t Keep Us Trapped Forever, My Friend.
Hardison: Parker please just say we’re out of cereal like a normal person.
157 notes
·
View notes
Text

The Mysteriously Brilliant Student.
—————————————————————————
Night Raven Colle Leaders x R.femele
—————————————————————————
Everyone thought you were just an adorable girl, kind of flying, who kept forgetting the books and making silly jokes. Until, by accident (or loving curiosity), they see your school record.
Not only are your grades absurdly high (A++ in everything), but your works have deep analysis, elegant writing and you still volunteer, cultural events and help the school administration in secret.
And that's when they run out of ground.
—————————————————————————
.
.
Riddle Rosehearts (Heartslabyul)
Riddle always gave you little affectionate scolding for forgetting the time or missing a quote from the rules.
Until, reviewing the bulletins for the next ceremony, he comes across your name... at the top of the overall ranking.
"What?! The first place?!”
He turns pale.
"But she... confused Plato with Pokémon last week!"
When he finds you, you're blowing soap bubbles in the garden.
"Have you... fooled me all this time?"
You smile innocently:
"Uhé, you never asked how good I was writing 20-page essays on political philosophy."
Riddle shes deeply.
"So... do you mean you're perfect? ...Damn, now I feel doubly in love."
⸻ ————————————
Leona Kingscholar (Savanaclaw)
Leona always thought you were cute, but lazy. Like someone who took C+ and forgot he had proof.
Until he saw his history and crashed.
"This girl... takes A++ in everything?!"
He frowns.
"Is this some kind of provocation? So brilliant and acts as if he doesn't know how to do the head?"
He stares at you later, arms crossed.
"How many years have you been hiding behind this innocent little way, huh?"
You:
"Since I realized that it's fun to see the pride of others dismount when they find out."
Leona laughs, pulls you to her lap:
"You are the definition of camouflaged danger... my favorite type."
⸻ ————————————
Ashengrotto Blue (Octavinelle)
Azul thought you were distracted and terrible for business, until he found a report you wrote about applied magical economics. With unprecedented theories.
"This... this analysis... did she even understand the concept of temporal compound interest?! And why are you here... with little stars drawn in the corner?!”
He stares at you, disconcerted:
"Are you a genius disguised as a cheerful fool?"
You, chewing a cupcake:
"It's just that if I look very smart, no one gives me candy."
Blue chokes.
"Wedding. Now."
⸻ ————————————
Vil Schoenheit (Pomefiore)
Vil thought you were dedicated to aesthetics, but a little disconnected from the academic part. Until seeing his dissertation on philosophical aesthetics in classical literature.
He holds the paper as if it were a jewel.
"Did you write that?"
"Uhum. I finished while waiting for my hair tonic to dry."
Vil blinks slowly, as if he were facing a miracle.
"You... are you smart, beautiful, kind and still do volunteer work? Why isn't it reigning in a palace?"
You:
"Because I prefer to stay here... with my king of beauty."
Vil smiles, enchanted:
"You are my hidden masterpiece."
⸻ ————————————
Idia Shroud (Ignihyde)
Idia thought you were the type to confuse USB with a cookie. Until you saw that you are a medalist in logic, cryptography olympiads and still write essays about AI.
"E-She is an S+ in mathematics, literature, psychology... and helps in magical literacy programs! Is this a bug in reality?! An NPC with cheat codes?!”
You appear soon after, offering a cookie decorated with emoji faces.
"Look, I made this one thinking of you!"
Idia is shaking.
"You're like... the secret protagonist of the anime. I'm just the lucky NPC who became the boyfriend."
You laugh and kiss him on the forehead.
"My favorite NPC."
⸻ ————————————
Malleus Draconia (Diasomnia)
Malleus already thought you were mysterious and intriguing... but when he saw that you give lectures in smaller magical schools, write essays on draconic history and lead social actions in remote villages...
"She... is a queen hidden among plebeians?"
He finds you looking at the clouds, making drawings with the wand in the air.
"My dear, why didn't you ever tell me?"
"I like to be just 'your distracted girl' when I'm with you. But the world needs my other version too."
He smiles, touching his hand.
"So I'll be proud to share you with the world... but your heart, that's only mine."
⸻ ————————————
Kalim Al-Asim (Scarabia)
Kalim always loved you - she thought you were fun, funny and full of energy, but she never took you very seriously in class. Once you confused "elementary physics" with "elementary party", and he thought it was hilarious.
But then, one day, he accidentally picks up one of his jobs in the hallway... and freezes. It's a perfect essay about ancestral magic, with historical references, impeccable writing and... signed by you.
"WHAT?! Did she write that?!”
He runs to Jamil with the paper in his hand.
"Look at this! She's a genius!! A real genius!!!”
Later, he finds you in the garden, singing alone with birds and trying to balance an apple on his head.
"You're too amazing! Why didn't you ever tell me you were so smart?"
You smile, shrugging your shoulders:
"I thought it was more fun to let you find out like that."
He hugs you tight, spinning in the air with you.
"You're brilliant, funny, sweet, beautiful... Are you sure you want to be with a guy like me?"
You kiss his cheek:
"Of course. You are my sun... and even geniuses need warmth."
He laughs, drened and in love:
"So let's conquer the world together! But first... let's have a party in his honor!"
—————————————————————————

#twisted oc#twisted wonderland#twst shrouds#twisted wonderland jp#twst manga#twisted wonderland x reader#disney twisted wonderland#twst
51 notes
·
View notes
Text






Did you guys know I've made a Classic Courier :3c Yuppers. Added another doppelgänger to the growing list of mailmen. "When will it end?" you cry - When will it indeed. Brutus "Birdie" Bunting Classic's Courier. Non-combatant. Expert in cryptography, conspiracy theories, obsessing and falling in love with people, languages, falconry, birds, birds, birds again, being a pathetic deplorable pitiful miserable biting soggy purse dog. We support trans wrongs ok. Just over all someone you don't wanna know but have to trust to get your mail and secret info where it needs to go. And at some point he gets partially decapitated but its ok! He comes back worse. ft friends classic ocs too!
#tf2 oc#tf2 courier#tf2 classic courier#tf2 classic oc#tfc oc#tf3#my art#these doodles dont rly say much about him as a character but im still navigating that#please know that he is just fucking insane#he looks so normal in these drawings he is not ok this man is a freak in every way#my oc
55 notes
·
View notes
Text
my extended family released a daily math game where two words add into a third where each letter is its own digit. i've been playing it for a week, and it's real cool! (link here)

2 notes
·
View notes
Text
Quantum computers:
leverage the principles of **quantum mechanics** (superposition, entanglement, and interference) to solve certain problems exponentially faster than classical computers. While still in early stages, they have transformative potential in multiple fields:
### **1. Cryptography & Cybersecurity**
- **Breaking Encryption**: Shor’s algorithm can factor large numbers quickly, threatening RSA and ECC encryption (forcing a shift to **post-quantum cryptography**).
- **Quantum-Safe Encryption**: Quantum Key Distribution (QKD) enables theoretically unhackable communication (e.g., BB84 protocol).
### **2. Drug Discovery & Material Science**
- **Molecular Simulation**: Modeling quantum interactions in molecules to accelerate drug design (e.g., protein folding, catalyst development).
- **New Materials**: Discovering superconductors, better batteries, or ultra-strong materials.
### **3. Optimization Problems**
- **Logistics & Supply Chains**: Solving complex routing (e.g., traveling salesman problem) for airlines, shipping, or traffic management.
- **Financial Modeling**: Portfolio optimization, risk analysis, and fraud detection.
### **4. Artificial Intelligence & Machine Learning**
- **Quantum Machine Learning (QML)**: Speeding up training for neural networks or solving complex pattern recognition tasks.
- **Faster Data Search**: Grover’s algorithm can search unsorted databases quadratically faster.
### **5. Quantum Chemistry**
- **Precision Chemistry**: Simulating chemical reactions at the quantum level for cleaner energy solutions (e.g., nitrogen fixation, carbon capture).
### **6. Climate & Weather Forecasting**
- **Climate Modeling**: Simulating atmospheric and oceanic systems with higher accuracy.
- **Energy Optimization**: Improving renewable energy grids or fusion reactor designs.
### **7. Quantum Simulations**
- **Fundamental Physics**: Testing theories in high-energy physics (e.g., quark-gluon plasma) or condensed matter systems.
### **8. Financial Services**
- **Option Pricing**: Monte Carlo simulations for derivatives pricing (quantum speedup).
- **Arbitrage Opportunities**: Detecting market inefficiencies faster.
### **9. Aerospace & Engineering**
- **Aerodynamic Design**: Optimizing aircraft shapes or rocket propulsion systems.
- **Quantum Sensors**: Ultra-precise navigation (e.g., GPS-free positioning).
### **10. Breakthroughs in Mathematics**
- **Solving Unsolved Problems**: Faster algorithms for algebraic geometry, topology, or number theory.
#future#cyberpunk aesthetic#futuristic#futuristic city#cyberpunk artist#cyberpunk city#cyberpunkart#concept artist#digital art#digital artist#quantum computers#the future of quantum computers#futuristic theory
5 notes
·
View notes
Text
Modern Cryptography
(stemandleafdiagram long-form post!)
~ 2900 words
As you may have guessed, I love cryptography and ciphers even though I still don’t know much about them. I think classical ciphers are super interesting stuff and I love breaking them but I realised I knew nothing cipher-y after the end of World War 2, so I sought to rectify that!
(This is SO long - I got quite carried away (I do apologise), and as I wanted to cover so much here there are some concepts I don’t explain very thoroughly, but there are so many resources online if you want to learn more! When explaining how different forms of encryption work, I will often use the names commonly used by other cryptographers in my examples. Alice and Bob are two people trying to communicate, while Eve (an eavesdropper) is trying to intercept their messages.)
Symmetric Encryption
The start of modern cryptography is not a definite thing (obviously so, as the “eras” of cryptography are just labels people use to refer to them generally) but I decided to start my timeline for modern cryptography in the 1960s, as during this time, research projects at the American company IBM (International Business Machines) led to the creation of a cipher called the Lucifer cipher.
This cipher was one of the first block ciphers to be made. A block cipher is a cipher that operates on blocks of 128 bits at a time. This is in contrast to a stream cipher, which encrypts 1 bit of data at a time. (In a way, you could consider classical ciphers stream ciphers) If the plaintext (un-encrypted data) is smaller than 128, padding schemes will add random data to it to make it up to 128. Modes of operation define how large amounts of data are encrypted. For example, the blocks of data can be encoded separately, or maybe the encryption of one block is affected by the previous encoded block of data.
The Lucifer cipher underwent a lot of alterations, and eventually the National Bureau of Standards adopted this altered version of Lucifer as the Data Encryption Standard, or DES, in 1977. Some of the alterations made that led to DES were actually quite controversial! For example, the key size in Lucifer was 128 bits, but only 56 in DES, which worried people who thought it would have been easier to brute force as it was shorter. It’s actually rumoured that the NSA (National Security Agency) did this so that the DES wasn’t too strong for them to break. Another change they added was the inclusion of something called S-boxes, which are effective at protecting against a form of attack called differential cryptanalysis. What I found really cool was that its effectiveness wasn’t talked about until much after, which suggests that the NSA knew about differential cryptanalysis 13 years before this information went public!
The DES is no longer secure enough for modern use, and in 2001 was replaced by the AES, or the Advanced Encryption Standard, which is its direct successor and is still used today. The reason that AES is more secure than DES is that the algorithm itself is more complex, but more importantly it uses longer key lengths. Using keys that are 128, 192, or 256-bit long means that the encryption is much stronger than using the 56-bit DES.
Lucifer, DES, and AES are all symmetric ciphers as well as being block ciphers. This means that the key used to encrypt the plaintext is the same key that is used to decrypt the data. Only some block ciphers are known publicly. DES and AES are the most famous of the lot, but other ones such as IDEA, Twofish, and Serpent exist too.
As a whole, encrypting with block ciphers is slower as the entire block must be captured to encrypt or decrypt, and if just 1 mistake is made the whole block can be altered. But, they are stronger than other ciphers. Each mode of operation also has its own pros and cons. If each block is encoded by itself then they can be encrypted in parallel (which is faster), but it’s prone to cryptoanalysis as two identical blocks of plaintext would produce two identical blocks of ciphertext, therefore revealing patterns. The other ways are much more complex and take more time to encrypt but are more secure.
For symmetric encryption to be used, both parties need to agree on the same key for the message to be shared secretly, which is a massive problem. How can the key be transferred securely?
Key Exchange
A year before the implementation of DES, in 1976, another massive breakthrough was made. Researchers Whitfield Hellman and Martin Diffie created the Diffie-Hellman key exchange, which was a method to share encryption and decryption keys safely across an unsecured network. The way it works depends on one-way functions. Typically in maths, most functions are two-way, as using a function on a number is pretty easy to undo. However, Hellman and Diffie found out that while multiplying two prime numbers was very easy, factorising the product down to its primes again was excruciatingly difficult, and the difficulty only increases as the numbers get bigger.
Say Alice and Bob are trying to share a key using the Diffie-Hellman exchange. Firstly, both of them need to execute a function in the form G^a mod P. P must be prime, and G and P are shared publicly so Alice and Bob can agree on them. The numbers are massive (usually 2048 bits) to make it harder to brute force, and they are generated randomly. Alice and Bob each choose different numbers for a, and run their functions. They will get different answers and they share their answers with each other publicly. (This is the public key) Then, Alice and Bob run another function in the form G^a mod P, but G is set to the other person’s answer. The value of a and P stay the same, and Alice and Bob arrive at the same secret answer. The secret answer can then be used to encrypt the message! (This is the private key)
Now, let’s say Eve wanted to find out what the key was. She intercepts their messages, but even though she has the exact information Alice and Bob shared with each other, she doesn’t know what the secret key is unless she solved the original equation, making this key exchange very secure! Modular arithmetic (the mod P part of the equation) is notoriously hard to reverse. If 2048-bit numbers are used, then brute forcing it requires 2^2048 numbers.
Asymmetric Encryption
The Diffie-Hellman key exchange was huge - I mean, any technology created 50 years ago that’s still in use must be pretty good, but it really only shone for sharing keys, not for encryption. For example, the issue with sending communication such as emails using Diffie-Hellman was that both parties needed to be online for a key to be generated as information needs to be mutually shared in the process, so you couldn’t just send an email using it whenever you wanted, which was a shame. However, one particular thing it did lead to was the invention of asymmetric encryption.
In 1977, the idea of public key cryptography (also invented by Diffie) came to fruition in the form of RSA. Named after its creators (Ron Rivest, Adi Shamir, and Leonard Adleman), the RSA works by all users having a public key, which is accessible by everyone, so anyone wanting to send that user a message just needed to search for it. The sender encrypts the message with the recipient’s public key, and then when the recipient comes online they are able to decrypt it with their own private key that’s not shared with anyone. It also uses an one-way function like the Diffie-Hellman exchange, albeit a more complex one. RSA is still used today for things like sending messages or visiting secure websites, and the keys tend to be 2048 or 4096 bits long so that they are hard to break. 1024-bit RSA was disallowed in 2013.
Encrypting via public key and decrypting via private key is great for keeping sensitive information safe, but what if you encrypted with your private key and the message was decrypted with your public key? The purpose of this encryption is to prove the sender is who they say they are - if the public key can’t decrypt the message then either the wrong key was used or the message has been meddled with in transit. To keep the message secure the sender could encrypt with their private key and also the recipient’s public key so only they could decrypt and read it. If the message is particularly long, the digital signature can be applied to a hash of the original message, rather than the whole thing. The RSA was the first to have this dual functionality.
So, there we go - the two main encryption types used today: symmetric and asymmetric. Symmetric encryption is useful for large amounts of data in particular, while asymmetric is more secure, but is slower and requires more resources and therefore can be more expensive. In practice, many secure systems will use both symmetric and asymmetric ciphers. Although, the actual security of a message comes down to the length of the key used - the longer or more complex it is, the more secure the encryption is. As the number of bits increases, the total number of arrangements for these bits increases exponentially. The IBM website states that a 56-bit key could be brute forced in around 400 seconds, a 128-bit key would take 1.872 x10^37 years, while a 256-bit key would take 3.31 x10^56 years.
Going Quantum
It goes without mention as to how important modern cryptography is. These encryption methods are used to keep confidential information such as credit card details, messages, and passwords safe for users like you and me, but also maintains government security on a national level. It’s also vital for cryptocurrency and digital signatures (as mentioned before), as well as browsing secure websites.
A big threat to current cryptographic standards is the development of quantum computing, which are computers based on principles of quantum mechanics. I won’t go into detail on how quantum computers work, but using quantum mechanics they are able to do massive numbers of calculations simultaneously. Although quantum computers already exist, they aren’t powerful or capable enough to threaten our current encryption algorithms yet. But, researchers suggest that they could be able to within a decade. People could use a technique called “store now, decrypt later”, where they keep currently encrypted messages so that they can decrypt them when quantum computers are available. This could cause many problems in the future, particularly if they involve secrets on an international level.
Quantum mechanics can also be used in cryptography as well! Quantum cryptography, originally theorised in 1984 by Charles Bennett and Gilles Brassard, can be used to exchange keys even more securely than Diffie-Hellman, and is called QKD, or Quantum Key Distribution. The reason it’s so incredible is that data that’s secured using it is immune to traditional cryptographic attacks. Now, I’m no quantum physicist (or any type of physicist!) but I will try my best to explain how it works. It works by sending photons, which are light particles, from the sender (eg. Alice) to the receiver (eg. Bob). These photons are sent at different orientations and Bob can measure the photon’s polarisation when he gets them.
Let’s say that photons can be in a vertical, horizontal, or one of the two diagonal orientations. We can pass them through a polarised filter to find out what orientation they are in. The filters are also specifically oriented. A vertical filter would let the vertical photons through, block the horizontal ones, and let the diagonal ones in 50% of the time but at the cost of the ones that pass through being reoriented. Therefore, when a particular photon successfully passes through, it’s impossible to know whether it was originally diagonal or vertical. This is important as it means that it’s possible to detect if someone else has been eavesdropping as the polarisations would have been changed.
Bob can use two measurement bases to receive the photons Alice sent. One will capture vertical and horizontal orientations, and one will capture diagonal ones. Bob has no idea what orientation Alice used for each photon, so he switches between his bases randomly, and will get it wrong some of the time. This is fine, as Alice and Bob then compare to see which ones Bob got right, and the ones he correctly guessed are used as a key (each photon representing 1 bit). The key can then be used for other encryption methods, such as AES.
The reason this works is that if Eve wanted to pry, she has to guess which base to use as well when she intercepts the photons (so she will also make mistakes), but she has no way of checking whether her records are correct or not, unlike Bob. It’s impossible for her to obtain the key as well. What’s more, when she guesses wrong she will change the photon polarisation, so Alice and Bob know that she’s eavesdropping.
Quantum cryptography would have huge security benefits if implemented on a wide scale due to its ability to prevent eavesdroppers, and the fact that it would be resistant to quantum computers. However, it is still in development. One key drawback is the specific infrastructure that is needed, and fiber optic cables have a limited range. This means that the number of destinations the data could be sent to is limited, and the signal cannot be sent to more than 1 recipient at any time.
As well as quantum cryptography, the NIST (The National Institute of Standards and Technology) and other cryptographers are working on other cryptographic algorithms that would stay secure even in the face of quantum computers. Ideas include lattice-based cryptography, hash-based cryptography, and code-based cryptography among others but none of them are at a point where they can actually be implemented yet.
However, one new idea that isn’t post-quantum but is gaining traction is Elliptic Curve Cryptography. Elliptic curve cryptography (ECC) is a form of asymmetric encryption that uses different points on an elliptic curve graph to generate keys in a more efficient manner than traditional methods. It creates shorter encryption keys, which means that less resources are needed while making the keys harder to break simultaneously. Improving the security of current systems just involves lengthening the keys, which slows down the encryption/decryption process, so the fact that ECC doesn’t need to do this gives it a big advantage. It is already used by the US government, iMessage, and Bitcoin, among others.
Sidenotes
With the maths of these encryption methods being so strong, one key vulnerability is the people that utilise these methods, which is no surprise. Side channel attacks are a way to break cryptography by using information physically leaked from it. One attack, called a TEMPEST attack, is a technique that can pick up electromagnetic transmissions from a device as far as 300m away. These are often done by the FBI, but honestly can be done quite easily by some nerd who has some money to spare and can sit in a car outside your window. By monitoring the radiation emitted from your computer screen, the attacker can spy on you and your data. Another thing that can be monitored is your power consumption. Cryptography is energy intensive, and this attack has been able to recover RSA private keys in testing. Other forms of attacks include measuring amount of time required to encrypt data, which can perhaps be used to find factors or exponents. To combat this, encryption methods can add timing noise as a countermeasure. Or, an attacker can listen to someone type to find out their passwords, but to distinguish different key presses a sophisticated machine learning model is needed. Side channel attacks have actually been around for ages but its use has been severely limited in that the attacker needs to be physically close to the victim. They could get easier with time, however, as smartphones and drones can act as microphones remotely.
Another cool thing I haven’t covered yet are hash functions, which can take in an input and map it to a string of characters that’s random but unique to the original data. The output is called a hash digest or hash value. A good hash function will mean that no two different inputs will have the same hash value, and all outputs are the same length, making it hard to guess original text length. It’s vital for digital signatures and storing passwords securely.
Finally, if anyone managed to get to the end, then thank you! I really love cryptography and I find it astounding that we’ve been able to develop it into such a complex yet intrinsic part of daily life. Honestly, I had so much fun researching for this post! Encryption and cybersecurity and the future of computing is so interesting and I’m really glad I decided to write this :)
Final final note you should totally go and read the Code Book by Simon Singh! Trust me trust me it’s so good...
4 notes
·
View notes
Text
notes on recrudescence
In classic fic writer irony, this fic required hours and hours of research that on occasion amounted to one line written on it.
On Magpies

This is how the oriental magpie looks. The japanese kanji for magpie is Kasasagi 鵲 - but I picked a different kanji - 笠鷺 (the direct translation of each individual character would be bamboo hat, heron) that actually is a legitimate name which reads the same as a tongue-in-cheek pun.
I found this little bird perfect, because it looks like a white and blue bird with its head painted black and i found it fitting.
On Jisei
Jisei are death poems which consist of five lines, with a total of 31 syllables (5-7-7-7) and are frequently composed by people on their deathbed. References to sunsets, autumn or falling cherry blossoms which suggest the transitoriness of life are common.
I picked my two favourites:
来時は空手、去時は赤脚。一去一来、単重交折[8]
Raiji wa karate kyoji wa sekkyaku ikkyoichirai tanjuu sekkou
Empty-handed I entered the world Barefoot I leave it. My coming, my going — Two simple happenings That got entangled.
By Kozan
and
願はくは花の下にて春死なむその如月の望月のころ
let me die in spring under the cherry blossoms on that day in the Second Month when the moon is full
negawaku wa | hana no shita nite | haru shinan | sono kisaragi no | mochizuki no koro
By Saigyo
On Substitution Ciphers
Okay, I'm no expert on cryptography and i really really struggled with this because i couldn't find something that already pre-existed in relation to a deck of cards that wouldn't take another deck and years off your life to solve.
Lo and behold - i realized that that from ace to king, there are 13 cards in a suit and I went oh **** it and made one from scratch. It's rudimentary and very basic (2 different cards can mean 1 particular letter) and also a proper cryptographer would make fun of me, but it works in a pinch.
Line break here, if you'd like to spare yourself.
Spade A - 1 - A Spade 2 - 2 - B Spade 3 - 3 - C Spade 4 - 4 - D Spade 5 - 5 - E Spade 6 - 6 - F Spade 7 - 7 - G Spade 8 - 8 - H Spade 9 - 9 - I Spade 10 - 10 - J Spade J - 11 - K Spade Q - 12 - L Spade K - 13 - M
Heart A - 14- N Heart 2 - 15 -O Heart 3 - 16 -P Heart 4 - 17 -Q Heart 5 - 18 - R Heart 6 - 19 - S Heart 7 - 20- T Heart 8 - 21 - U Heart 9 - 22 - V Heart 10 - 23 - W Heart J - 24 - X Heart Q - 25 - Y Heart K - 26 - Z
Diamond A - 1 - A Diamond 2 - 2 - B Diamond 3 - 3 - C Diamond 4 - 4 - D Diamond 5 - 5 - E Diamond 6 - 6 - F Diamond 7 - 7 - G Diamond 8 - 8 - H Diamond 9 - 9 - I Diamond 10 - 10 - J Diamond J - 11 - K Diamond Q - 12 - L Diamond K - 13 - M
Club A - 14- N Club 2 - 15 -O Club 3 - 16 -P Club 4 - 17 -Q Club 5 - 18 - R Club 6 - 19 - S Club 7 - 20- T Club 8 - 21 - U Club 9 - 22 - V Club 10 - 23 - W Club J - 24 - X Club Q - 25 - Y Club K - 26 - Z
G - Diamond 7 U - Club 8 N - Heart Ace
P - Heart 3 S - Club 6 N - Club Ace
12 notes
·
View notes
Text
Light
Light exhibits several quantum properties that are fundamental to its behavior:
1. Wave-Particle Duality: Light exhibits both wave-like and particle-like properties, known as wave-particle duality. It can behave as both continuous electromagnetic waves and discrete packets of energy called photons.
2. Quantization of Energy: Light comes in discrete energy levels or quanta. Each photon carries a specific amount of energy determined by its frequency or wavelength. The energy of a photon is given by E = hf, where E is energy, h is Planck’s constant, and f is the frequency.
3. Superposition: Like other quantum particles, light can exist in a superposition of states. This means that it can simultaneously be in multiple quantum states until measured, at which point it collapses into a single state.
4. Quantum Entanglement: In certain situations, photons can become entangled, which means the properties of one photon become correlated with the properties of another, even when they are physically separated. This phenomenon is essential in quantum optics and quantum information science.
5. Quantum Interference: Photons can exhibit interference patterns when their waves overlap. This interference can be constructive (adding up to a brighter region) or destructive (resulting in dark regions). This behavior is commonly observed in experiments like the double-slit experiment.
6. Photon Polarization: Photons can be polarized, which means their electric field oscillations occur in a particular direction. Polarization is a quantum property that can be used in various applications, including polarized sunglasses and quantum communication.
7. Quantum Uncertainty: The Heisenberg Uncertainty Principle applies to light as well. This principle states that it’s impossible to simultaneously know both the exact position and momentum (or equivalently, wavelength and frequency) of a photon with infinite precision.
These quantum properties of light play a crucial role in quantum mechanics and have practical applications in fields such as quantum computing, quantum cryptography, and quantum optics. They challenge our classical intuition about the behavior of light and other particles at the quantum level.
38 notes
·
View notes