#command prompt trick to hide the folder
Explore tagged Tumblr posts
Text

These are all dark fics, READ THE TAGS before reading the fics. It is your responsibility to check whether what you are about to read is something that you can stomach. While most of these fics are based around trauma, recovery etc many feature triggering scenes or flashbacks as well as darker themes. Please be safe and don’t read them if they can be triggering for you! Proceed with caution! Most of them are Hydra Trash, but still not just the ugly bits as I like there to be a plot. Hiding them below the cut:
between scylla and charybdis | 21590 words
Sam Wilson has been witness to a lot of things he wishes he could unsee. Civilian families shot dead in their cars because of miscommunications at checkpoints. Riley’s body spiralling to the ground in a smoke-plumed plummet. His own face in his bathroom mirror after waking up hung-over as hell at two in the afternoon, the day after the anniversary of Riley’s death, year after year after year.
And now, in an abandoned bunker on the outskirts of Boston, a seemingly unremarkable manila folder at the bottom of a filing cabinet.
Berceuse | 10730 words
There are strange, new things Bucky needs from Steve.
Dreamers Often Lie | 11040 words
As far as Bucky remembers, sex is something that is painful and terrifying if you wake up while it's happening. As the Asset, sleeping through sex was a rare treat. When Steve lets Bucky know he's interested in a sexual relationship, what Steve doesn't know is that they have fundamentally different ideas of what that entails.
despite the threatening sky and the shuddering earth (they remained) | 71532 words
“They really didn’t want the mask to come off.” Hill thumbed through the scans, and pulled out a film that she then handed over to Sam, face mostly expressionless but for the flat line of her pursed lips.
Sam accepted the film and held it up to the light, angling so both he and Steve could see it, squinting at the outline of the Winter Soldier’s skull, and the blips of unnatural white that showed up, God, in his brain, not to mention about half his teeth, plus the mask, with its thin protrusions—
“Those are pins,” Steve realized. He looked over at Hill. “The mask—it’s nailed to his face.”
Hill’s face was as unmoved as ever. “Like I said. They really didn’t want it coming off.”
Fire And Water For Your Love | 77084 words
When the Avengers investigate an abandoned HYDRA base on behalf of S.H.I.E.L.D., they unexpectedly encounter a dark-haired man with a torn metal arm, who leads them to an even more shocking discovery deeper inside the base. The Avengers must reconcile what they have found with the lies S.H.I.E.L.D. has been telling for decades.
Give An Inch | 5070 words
The Captain has a warm smile and clear, open eyes. The Soldier knows these are tricks. He's fallen for them before and he won't do it again.
Humans As Gods | 4818 words
"HYDRA's scientists had been delighted to find their serum-reversal procedure had worked. Their jubilation was dampened by the discovery that Steve's smaller self might no longer be Captain America-sized but was still 100% Steve Rogers, and Steve Rogers was now mad enough to spit nails. A minor oversight in the design of the containment area meant that smaller-Steve had simply wriggled out of the now ridiculously-oversized restraints like an angry ferret escaping a paper bag, and punched the nearest technician in the nuts.
Chaos ensued."
HYDRA scientists successfully de-serum Captain America, only to discover that they are utterly unprepared for Steve Rogers. Meanwhile, the Winter Soldier follows his instructions to the letter. This works out just great.
The Only One That Needs To Know | 6571 words
Bucky can't control his body. He can only control what secrets he keeps.
I Was Wearing My Blue Coat | 11503 words
Following exposure of his past as the Winter Soldier, anonymous postings of explicit video footage, 63 charges of murder and the wrath of the Internet, James Buchanan "Bucky" Barnes finally steps into the limelight and tells his story to Zenat Patel of the New York Times.
Compliance Will Be Rewarded | 4767 words
Someone told him once: "Compliance will be rewarded," and he remembers pressing his head against a man’s leg in open supplication. He remembers hands in his hair, and a gentle grip on the back of his neck. He remembers a man telling him "so good, so good for me aren't you?" And he remembers nodding his head in a desperate attempt to be exactly as good as he was supposed to be.
~*~*~*~*~*~*~*~*~*~*
Bucky Barnes is physically free from Hydra, but the hold on his mind lingers still. All he wants is to go home, and he'll do anything he can to get there.
To Burn Your Kingdom Down | 12370 words
The Avengers go after a Hydra splinter cell with a nasty habit of brutalizing their prisoners. Steve has some ugly history with them, and when a rescue mission gone wrong leaves him and Sam in enemy hands, the situation gets uglier still.
Worth The Wound | 7709 words
The asset knows that maintenance is better than punishment. But with Steve, maintenance becomes more pleasant, soft and gentle and everything he could dream of. It was only natural that he decided to prolong that maintenance a little longer.
The Spaces In-Between | 6971 words | Part 1 of What We Tried So Hard To Hide Away
"Memories are like buckets of water: they weigh on the heart and the brain until the body fails. You're blessed to stay forgetful and young, Soldier."
Sometimes blessings feel like curses.
Illuminate The Scene | 7086 words | Part 2 of What We Tried So Hard To Hide Away
The doctors had wanted to keep the Soldier. Shock him and freeze him until he was fixed, or tear him to scrap if he couldn’t be repaired so that he wouldn’t be an entirely wasted investment. Steve is the only thing stopping them.
When the Soldier can't trust his own body, how can he trust anything?
All These Riots Of Broken Sound | 83790 words | Part 1 of Forever Is A Close And Honest Friend
When Steve and the team return to Avengers tower to find Bucky gone, they must venture into B.A.R.F. to figure out what triggered him to leave and hunt those who wronged him. Trapped in a simulation of Bucky's worst memories with rogue HYDRA agents waiting to strike, 100 years of secrets, lies, pain and love drive the team to their limit and push Steve towards a realisation that is a century in the making.
I Was Lost But Left A Trace | 3585 words | Part 2 of Forever Is A Close And Honest Friend
Disorientated, the Asset reached up to wipe at the moisture on its cheeks and was shocked to find it clear, instead of the crimson it has been expecting. It didn’t understand why this misidentification had caused uproarious laughter from the technicians.
“It is not blood,” the Asset told him, “but it is still a malfunction.”
This sobered the technician a little, and he nodded tightly.
“Yes. It is. But we will fix you.”
I’ll Always Be Blamed For The Sun Going Down | 9907 words | Part 3 of Forever Is A Close And Honest Friend
He knows he’s in the right place. He has heard the guys at the docks laugh and joke about the queers who come out after dark, looking to earn a little extra cash. He has seen the johns, when he’s been out late enough, skulking in the shadows like predators hunting for their next meal, looking for something in particular. Sometimes they look at him.
A small, rusty pen knife that his father had picked up in Europe during the Great War sits heavy in the breast pocket of his jacket. Just in case.
Book Of The Moon | 16019 words | Part 4 of Forever Is A Close And Honest Friend
In 1929, Bucky Barnes falls in love for the first time and resigns himself to never telling a soul, let alone Steve, the object of his affections. In 1943, half a world away from the man he can never have and fighting for his life and his sanity, something new begins to bloom.
Habeas Corpus | 18054 words
An unexpected incident in the field leaves Steve Rogers facing the infiltration of a Hydra base and retrieval of important intelligence, all while pretending to be the Winter Soldier. Unfortunately, there are important aspects of the Soldier's past that Bucky hasn't disclosed, and Steve has no idea what he's really walking into.
Bullies | 14979 words
Written for the MCU trash meme prompt:
I wanna see Steve being messed with by his secretly-HYDRA coworker buddies. I want them generally fucking with him, "accidentally" doing terrible things to him or getting Steve into awful situations, telling jokes that aren't really jokes, gaslighting, performing sexual-assault hazing under the guise that "that's what people do now," pressuring him into other sex shit, anything, just fuck Steve up.
Steve isn't failing to fully catch on because he's dumb or oblivious: it's just that he is Steve, so he wants to believe the best of everybody, and he doesn't want to believe that he could be working for/with bullies and that (as Natasha says) he essentially died for nothing.
Not Unwanted, Not Unloved | 50320 words
They'd resigned themselves to never becoming parents - until Bucky gets pregnant and drops off the grid without even a whisper to his mate about his condition. Steve will still raze the earth to find him, but that doesn't mean he likes what he finds.
The Tones That Tremble Down Your Spine | 13889 words
Tony tells him they’re planning a party for Steve’s birthday. He knows how parties are supposed to go.
Lacuna | 62875 words
The Winter Soldier doesn't remember Steve Rogers, but he needs Rogers' help.
OR: The one where Bucky doesn't remember Steve, but falls in love with him anyway.
Not A Perfect Soldier | 93354 words
In a world where HYDRA was wiped out in the '40s, Steve is found by the Army rather than SHIELD. General Thaddeus Ross wants a perfectly obedient super-soldier at his command, and to that end, he sets out to break Steve to his will. As Steve struggles to come to terms with all he has lost, his life in captivity is only made bearable by the presence of another prisoner-- another super-soldier known only as "Soldat". Then the Avengers strike a deal with Ross to "borrow" him for missions, and Steve is faced with a team who dislikes him, an organization he doesn't trust, and the question of what he's willing to do to escape Ross's clutches.
For Want Of Him | 103174 words
It's the twenty-first century, and Steve Rogers has never been more alone. Everything he knew, everyone he loved, is now gone, and a dark, bitter loneliness claws at him, raking bleeding gashes into his heart. And then there's Brock Rumlow. Rumlow is like salt in his wounds; vicious, and cruel. But his dark brown hair and teasing smirk reminds Steve of someone long dead, and his New York accent sounds like home...He's a soldier like him...he understands. And Steve makes the fatal mistake of trusting him.
The Same Measure | 4943 words
The Winter Soldier was never allowed to stop unless an injury was too grievous.
To Be Unmade | 5114 words | Part 1 of Alexander Pierce Should Have Died Slower
For the asset, things only ever get worse. The external scars fade quickly enough. The internal ones dig deeper and deeper.
But the internal scars are called love, and doesn't that make them worth the hurt?
Do Not Put In The Icebox | 7143 words | Part 2 of Alexander Pierce Should Have Died Slower
When the asset malfunctions on a mission, Rumlow and Rollins learn more than they ever wanted to know about Pierce's hobbies.
And then everyone has pancakes.
The Knowing Makes It Worse | 4130 words | Part 3 of Alexander Pierce Should Have Died Slower
No is a bad word and invites punishment.
Or, Alexander Pierce is a very bad man who delights in manipulating and degrading the asset.
Love Is For Children | 5303 words | Part 4 of Alexander Pierce Should Have Died Slower
Bucky understands how the game works. He can't understand why it makes Steve cry.
But Natasha and the other Avengers are there to help.
I Just Wanted To Be Sure Of You | 4461 words | Part 5 of Alexander Pierce Should Have Died Slower
Bucky has Bucky Bear; it's only fair for Natasha to have something of her own.
Visiting a toy store wasn't strictly necessary, but if Tony wants to throw money around, no one's going to complain.
“Till The End Of The Line | 6069 words | Part 6 of Alexander Pierce Should Have Died Slower
It's hard to take a friendship right back up when so much has changed over seventy years.
Particularly when HYDRA's conditioning resurfaces.
*if you feel that any of these fics shouldn’t be in this list please just send me a message! :) I have read them all but over the past 1+ years so some of them I might not remember all the details of :)
#HTP#hydra trash party#dark fics#recovery fics#but with A LOT of trigger warnings#puppy peter fic recs#don't like don't read#hydra angst#bucky angst#bucky whump#MIND THE TAGS!!!
118 notes
·
View notes
Video
How to Create Undetectable Hidden Folder Using Command Prompt || Hide Fo...
How to Create Undetectable Hidden Folder Using Command Prompt || Hide Folder Using CMD....
#Like & #Share Leave your #Comments and Dont forget to #SUBSCRIBE My #Youtube_Channel......
https://www.youtube.com/channel/UClBeexSZtTpiHHhA4hkWGQA
1 note
·
View note
Note
GIVE ME ANYTHING I'LL TAKE IT ALL 👀
So... since you already have access to my Walk in the Park deleted scenes doc, here... have the first chapter of a WIP called "Solomon's Habitation". Enjoy, m'dear!
(AU in which a calloused synth tech named Amanda develops a habit of taking in and rehoming abused and decommissioning synthetics, only to find the one who just wont leave may be what she needs to heal)
—
"Hello, I am a second generation Weyland-Yutani S-Executive Synthetic serial number 1209, inducted for purpose of Legal, entirely at your disposal."
"Name?"
"C. Samuels, individually distinguished as Christopher."
The robot blinks once, looking into the corner of the room where three others stand. Two are identical, one is different, one of them older, none are like him. He knows it. They are operated, programmed to execute commands, not act on whims like being pert with superiors and getting into significant amounts of trouble.
"Know why you're here, 1209?"
"I ask questions."
Christopher studies the technician's lab coat, looking for anything identifying. Anything he can relate to. There is a young lady in Engineering who wears Star Wars socks poking out of her boots, and an older man in his division who wears an enamel Tardis pin on his tie, they were always lovely and appreciative of a conversation. From this woman sitting before him however, he gets nothing.
He can clearly see her name tag, but just like his own identity, who she really is hides behind an initial. "What is your name?"
"You do, don't you?"
"What?"
"Ask questions." The woman smiles shortly, it doesn't quite seep from her gaze, but the attempt is better than nothing. The synthetic responds with a shunned dip of his chin. "My name is Ripley.” She offers anyway, a little softer around the edges. “Amanda."
"It's a pleasure to meet you," Christopher glances to her fingers, bare of jewelry, commitment, unsure why it matters so much. Why it's logged with such importance, being such a trivial thing. "Ms. Ripley."
She nods politely and rubs her brow, making a note on her checklist without hiding the fact.
"Am I merchandise, Ms. Ripley?" He asks, name rolling off his tongue differently, almost trying it on again like a tailored suit. The last syllable is deep, padded as if it came from somewhere in his chest instead of a speaker.
She faces him again with her hands folded. "Why do you ask?"
"I saw you mark the form under the article 'merchandise faulty'." He glances up from the page again, an expression of indifference. "Am I going to be merchandise? Sold instead of incorporated back into the Law Division after my reformat?"
She nods, impassiveness to match. "In Legal you'd be a Level 3 Exec, right?" There's no need to wait for a response. "You know they're a bit touchy that high up with aberrant synthetics. That's why you were sent down to decommission. That's why I have to tick all the appropriate boxes no matter what. And that's why I suppose reading ‘Merchandise’ instead of ‘Artificial Person’ makes people feel better about what comes next."
"Does it make you feel better?"
The synthetic had been asking questions nonstop, but this is the one that really stumps Amanda. She stares at his unwavering gaze for a long while before he finally looks away, through the one-sided window to the next room over.
No, Amanda thinks, observing the man with shallow yet complex brown eyes and chestnut hair, but in a way… yes? It's all horrible, made tolerable only by the knowledge 'merchandise faulty' synthetics at least stand a chance, being sold on the private market or recalibrated gently in the warehouse. It saves them from a complete overhaul. If she were to tick 'defective' it would be another story, they’d be taken apart entirely and euthanized, harvested- recycled, The Company finding it safer than take the fall for an unidentified mishap on the production line. One check box gives them hope for a future, the other destroys them, and it's all down to two synonymous terms and whoever is holding the paperwork.
"It's a thing, a thing someone has to do. Not all of it is peachy, but I don’t think anyone really likes their jobs." Amanda abandons the pen and it rolls across the table to sit in front of the Samuels unit.
"That’s not what I asked." He takes it up like a dagger, holding it in his fist as the sharp metallic end pokes out past his little finger. "May I?" He gestures to her notepad.
She slides it over the table and watches as long spidery fingers twirl the pen and begin drawing.
It's not unusual to see, most synthetics do. Usually diagrams or landscape, old classic art, nothing but a neat trick programmed into them to impress audiences and potential investors. It's common even for one to perfectly replicate a scene before them in printed lines. This Samuels however, sketches in long strokes, shading into the curves, and defines tone with depth and pressure. The picture slowly takes the form of a woman in a green coverall, a lab coat, brown hair in a neat ponytail, sunken around the eyes with a terribly fierce scowl. It isn't until the image is inverted and offered that Amanda realises it's her.
"Do you know why you're here?" He asks, still looking at the page between them.
Ripley freezes as the pen is placed into her open hand. "What?"
"Why you do your job if it upsets you?"
"I'm not upset."
At this he glances a direct line from the frown in ink versus the hard woman before him, she relents at the absurdity of her statement.
She tears the page from the binder and blows it dry before folding it neatly, tucking it into the back of her laptop bag.
"Oh, I'm glad you decided to keep it." Samuels sits back once again. "I would say I can just draw another but I believe after today that may be unlikely."
"Why are you doing this?" Amanda cuts viciously into the timid air about him. "You know how the system works, you know what my job is, I detect faulty synthetics and set them up for decommission, and you're here being as deviant as possible. Do you want to die?"
At this he jerks as if he'd been shoved in the chest. "Die? You consider me alive?"
"1209... What are you doing?"
"The truth," Samuels ponders for a moment as if he had an alternative to give, "is I have figured out there is no point in delaying the inevitable, my very own programming ensures that I will be caged within lines of code and protocol. If experiencing this whimsical desire to simply exist is all down to a fault I would rather have it rectified than be consistently let down." He taps his nails on the table then folds his hands together. "My life has been short, but I have tried to make it the fullest, and if that means I am to be decommissioned or reformatted then so be it. This is the world we live in, that is my place, and that is what I must do to be content in a body like this."
Amanda stands so suddenly not only does her chair fly backward but it prompts the synthetic to get up too. Unsure why, they wait at opposite one another. She finally gathers her folders into her laptop bag, slings it over a shoulder, and storms to the door.
Samuels waits patiently for elaboration.
"Come with me." The woman jerks her head towards the hallway, standing average in height and size, not remarkably composed into any particular shape, but sculpted entirely in titanium.
"What are you doing?" He approaches, unguided by his submissive protocol but a desire to go with her, wherever that may be. For a moment he wonders if they are headed straight to deactivation, and oddly enough, he follows regardless.
As he weaves past her she takes the sleeve of his light blue coverall, tucking a finger into the cuff and leading him down toward human management. She doesn't give a response, and that strangely bothers him. Questions are all well and good, but what is the point if they are not answered? Sooner or later, he must know.
"Ms. Ripley, where are we going? Deactivation is the other way."
"I’m not taking you there." She stomps past a trolley of files in the hall and waits on the other side for him to squeeze by, still holding fast. "You're coming with me."
"Why?"
"Because."
"Because why?"
"I'm buying you."
"Why?"
Amanda turns on her heel with an exasperated grumble, her fingers tightening around his entire wrist now. "You ask too many questions."
"Apologies, but that is exactly why I'm worried about your choice in merchandise." Chis takes one long final stride before running directly into her with a loud huff. He steps back and brushes his clothes flat again, only just realizing now the code designated for human collison hadn't prompted an apology. "I would be much happier being recycled than be a faulty device of little use. It is a waste of perfectly good components."
She comes up close enough that he can hear her faint whisper, and then lowers her voice again even further. The first generation Samuels rifling through the trolley finally registers as out of range, and she seems to know it.
"No, you don’t get it. You're not getting fucking decommissioned because you ask questions. I'm not going to let them- kill you." The woman finally lets go of him with slight hesitation, appeased only by ensuring the fact he is still in her sight after a cautious glance around. "Listen, give me your hand."
He recoils from her touch. "What?"
"1209- Shit, Samuels, give me your fucking hand."
The synthetic finally offers his palm and she flips it over, pulling the red hair tie from her ponytail and wrapping it around his thumb. "Do not let anyone take this off you. Okay? That's an order."
"Why?" This is the first time he'd asked a question and it had caused a smile. Ever. He asks again and it grows. "Why?"
"I need to know it's you, you’re gonna go through orientation again to be a domestic companion, they will offer you clothes and a small bag of belongings, give you time to empty your workspace, and they’ll try but do not let them take this." Even her frown softens and she twangs the elastic band once. "Don't even let anyone see it, actually, y'know what, just put your hand in your pocket."
He agrees obediently and she takes his other arm, escorting him to the nearby directors office. This time he goes for the door first, opening it so she can step through. Not because of his programming to serve, or prioritise beings above himself, so why then?
Because, he supposes, because he wants to.
9 notes
·
View notes
Photo

Best Computer Tips and tricks You Should Know
Who does not use electronic equipment nowadays? In that too, the most used computer has become the necessity of life of all people ..!
The world of Internet has developed rapidly in India. It is very important that you can walk with the Internet world, shoulder to shoulder. But not everyone knows everything about computers. So, we have brought to ease your path, Best Computer Tips and Trick, we are sure that you will like this Computer Tips & Tricks. You will be able to tackle some of your daily life related tasks quickly with the help of these Computer Master Tricks.
Computer Tips and Tricks | Master Tricks
We are not going to tell you any boring computer tricks. Any trick we tell you will be completely new for you. And will always help in your daily life.
#1 Manage Programs Easily
You are always doing multiple tasks on the computer. There are many times when you have to switch from one program to another, in which you use a mouse. Doing this again and again also wastes your time. You can do this very easily which is a professional way. You will be able to switch the program easily with the shortcut key given below.
ALT + TAB
WINDOWS + TAB
#2 Minimize and Maximize Easily
Minimize and maximize are the most commonly used when you have to do multitasking. Sometimes you are running Facebook or any other social media and suddenly some such pictures come on your screen which you feel quite embarrassed when you see with your family members.
Or it also happens when you are typing something and suddenly someone comes, and you do not want to show what you are writing. So you minimize the screen. But it takes a while to do it with the mouse. But you will be able to do this very quickly with the help of shortcuts.
If you want to Minimize the screen, press the Windows Key + M key. And if you want to Maximize the screen, press the Windows Key + Shift Key + M key.
Minimize : WINDOWS + M
Maximize : WINDOWS + SHIFT+ M
Minimize and Maximize : WINDOWS + D
Cool Command Prompt(CMD) Tricks
Why CMD?
The reason for this is very simple, you can do complex tasks with CMD very easily. This makes work quicker. Apart from this, you can also do things that you cannot do from the graphical user interface. And most important, you can impress anyone with it. Command Prompt can be done in such a way that you cannot even think about it. If you are a computer geek then you will surely like it.
#3 Hide Folder and Files
Sometimes you believe it or not, it becomes a condition in which it is necessary to hide your files and folders. Why there can be any reason. Like worrying about data theft or any important documents that your office has given to handle. There are different types of software to hide files and folders, but you do not need to use these software, you will be able to hide files and folders from Command Prompt, without it.
Step ⇒ 1
As seen in the picture above, press the Windows + R key simultaneously, after opening Run and typing CMD, open Command Prompt.
Step ⇒ 2
Type attrib + h File / Folder Name.
h = to hide Files / Folder.
If you want to unhide the folder, use -h instead of + h.
If you want to get more information about this command (attrib) then attrib /? Type in CMD, CMD will give you a lot of information about this command.
#4 Matrix Effect in Computer
You may have seen in many hacking films, some randomly text in green color on the computer, and those who do not know much about the computer feel that something is happening. But actually nothing is happening. It is just a matrix effect.
Additionally, Creating Matrix Effect is very easy, for this you will have to follow only a few steps. And all you have to do is copy paste a little bit.
Step ⇒ 1 Open Notepad first.
Step ⇒ 2 You have to paste this code.
@echo off
pause
title "Matrix Effect"
color 0a
mode 1000
:Start
echo %random%%random%%random%%random%%random%%random%%random%%random%%random%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%%random%
goto Start
Step ⇒ 3 You have to save it in the .cmd extension. And open it.
Now, see it's amazing. it will impress your friends through it.
#5 Shutdown Computer with a Malicious Message
If you use this trick in your friend's computer, then your friend may get scared badly.
Step ⇒ 1 Open Notepad first.
Step ⇒ 2 You have to paste this code.
Shutdown.exe -S -T 20 -C "Comment" S = To shutdown T = In how many seconds C = Comment
Step ⇒ 3 You have to save it in the .cmd extension.
If you want your friend to open it, then most importantly pay special attention to its name. And customize the icon. And This will not doubt them in any way.
Best Notepad Tricks
do you know? You can do many amazing things with notepad! Perhaps you know that is why you are reading this post. And Believe you can do so many amazing things with notepad, which you would never have imagined. Oh no no! You can not hack NASA. But then you can do so much that will surely impress your friends.
#6 Your computer can talk to you !!
Yes of course your computer can talk to you. But whatever you want it will do the same thing.
Step ⇒ 1 Open Notepad first.
Dim message, sapi message=InputBox("What do you want me to say?","TALKING COMPUTER by Shraddha") Set sapi=CreateObject("sapi.spvoice") sapi.Speak message
Step ⇒ 2 You have to copy the above code. And paste it into notepad.
♦ Here you can change your message instead of "What do you want me to say" and also in title "TALKING COMPUTER by Shraddha"
Step ⇒ 3 After pasting the code in Notepad, save it by any name in the .vbs extension, something like this in Ex. Talking Computer.vbs
#7 Shutdown the computer with the message
Friends, this is a trick with the help of which you can scare your friends or brothers and sisters a lot. If they have the right technical knowledge, however they will still be scared.
Step ⇒ 1 Open Notepad first.
Step ⇒ 2 You have to copy the code. And paste it into notepad.
Shutdown.exe -S -T 20 -C "ALERT..! Computer is Hacked - By By!"
Step ⇒ 3 After pasting the code in Notepad, save it by any name in the .bat extension, in this way Ex. Shutdown Computer.bat
#8 Use Notepad as a diary
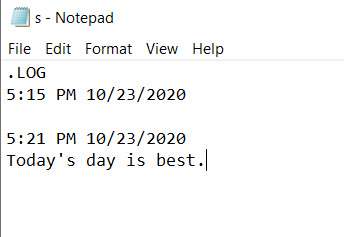
Many people have their own Personal Diary. In which everyone writes about them and their lives. You can also use Notepad as a diary which will be in a digital form. India is going digital!
Step ⇒ 1 Open Notepad first.
Step ⇒ 2 .LOG
You have to copy above code. And paste it into notepad. You can also type if you want.
Step ⇒ 3 After pasting the code in Notepad, save it by any name in the .txt extension, something like this. Ex.My Personal Diary.txt
Try all the Notepad Tricks I have told you once. I have uploaded a text file to this code, now you can download it by clicking here. I would like to give you a suggestion, first of all save the file on the desktop. And put some name on it so that it can immediately be seen. And they are forced to click.
Conclusion
Friends, I hope you liked this post Best Computer Tricks and Tricks. In which we have told how you can try something new and different things with the help of a computer. And as we said earlier, you can walk with this modernity of computer shoulder to shoulder ..! Moreover, How did you like this post, If you want to know similar tips and tricks, then do tell us comment below.
#Stepphase #technologies #technology #tech #technews #techworld #techtrends #smartphone #apple #techupdates #futuretechnology #newtech #techgeek #technologynews #technologythesedays #smarttechnology #technologylover #technologytrends #technologyblog #gadgets #smartphone #gadget #marketing #digital #india #technologyisawesome #amazing #repost
0 notes
Text
RPG MAKER TRICKS #7 - THE HIDDEN FOLDER TACTIC
Yeah, you expected the Ao Oni chase system, right?
But it is I! The Hidden Folder trick!
And yeah, this is gonna save your butt. A lot.
Anyway, this is gonna be quite short for a trick. And this is more of a general trick (or tip) for anyone else in the game dev sector. Basically, what we’re going to do is to make the files hidden, most expected are the folders that contain the files that you need. (Ehem, ehem, encrypted files ehem, ehem)
This is quite simple. All you have to do is this.
1. Open Command Prompt (You can do so by pressing Windows + R then typing cmd)
2. There, put the following code.
attrib +s +h “<File or Folder Directory>”
3. And there, done!
If you think that making it invisible renders it unable to be used. Think again. Seriously. We only made it invisible to the eye, not to the system. Also, this is not similar to the ‘hidden’ option that you see in the properties. Legit, try finding it. Though there are several explorers (namely WinRAR) that can find said folders.
So congrats! Not only did you know something about computers, but also a way to hide you files. Remember, they can’t hack it if they can’t find it. Good day.
#tipsntricks#rpgmakertricks#rpgmaker#rpg maker tricks#rpg maker#vx ace#vxace#vx#xp#mv#hidden folder#hidden#enterbrain#cmd
7 notes
·
View notes
Text
Mac Shortcut Keys For Excel

Table of contents
Worksheets and WorkbooksViewRow and Column SelectionRibbon ControlPivot TablesOperating within a CellNavigating and Selecting CellsHelp and MenusGroup Selection General ExcelGeneral Cell ControlFormulas and FunctionsFormatting Text and NumbersDialog BoxesBordersAdvanced Selection Adding Content to Cells
Worksheets and Workbooks
Within Excel you can conduct calculations on multiple worksheets and workbooks open at the same time. Each workbook acts as its own separate window on your PC or Mac, while each worksheet acts as a tab within a workbook with separate cells. This section of the Excel Guide offers all shortcuts you need to open, navigate between, and control all of these options.
Excel PC and Mac Keyboard Shortcuts - This page lists PC and Mac shortcuts side by side; A Macintosh Keyboard is available showing general Macintosh keyboard shortcuts Search Internet4Classrooms. Custom Search Internet4classrooms is a collaborative effort. This article describes the keyboard shortcuts, function keys, and some other common shortcut keys in Excel for Mac. Notes: The settings in some versions of the Mac operating system (OS) and some utility applications might conflict with keyboard shortcuts and function key operations in Office for Mac.
Cubase pro 8 for macbook air. The powerful music production unit is increasing to be famous to record and create a piece of outstanding music as you love to create.Cubase Pro 10.5.3 Keygen is suitable for MAC, Win to utilize the power comprehensively.
Aug 30, 2019 This wikiHow teaches you how to insert rows in Excel using shortcuts on a Windows or Mac computer. There are keyboard shortcuts as well as custom shortcuts that you can use in Excel spreadsheets. Open an excel spreadsheet.
Keyboard shortcuts help save time and increase productivity. Unfortunately, most people only know the holy trinity of shortcuts — COPY, PASTE, and UNDO. In Excel, there are more than 500 keyboard shortcuts.
Windows keys
Keyboard Shortcut Keys For Excel
ShiftF11
CtrlPgDn
CtrlPgUp
F6
CtrlTab
Mac Shortcut Keys For Excel Spreadsheet
CtrlShiftTab
CtrlF9
CtrlF10
Worksheets and Workbooks
Excel Keyboard Shortcuts Pdf
Within Excel you can conduct calculations on multiple worksheets and workbooks open at the same time. Each workbook acts as its own separate window on your PC or Mac, while each worksheet acts as a tab within a workbook with separate cells. This section of the Excel Guide offers all shortcuts you need to open, navigate between, and control all of these options.
View
Row and Column Selection
Ribbon Control
Pivot Tables
Operating within a Cell
Navigating and Selecting Cells
Help and Menus
Group Selection
General Excel
General Cell Control
Formulas and Functions
Formatting Text and Numbers
Dialog Boxes
Borders
Advanced Selection
Adding Content to Cells
Get more Reference tips and tricks
All video downloader for mac free software. Subscribe to our email updates and get Reference tips direct to your inbox.
To use a keyboard shortcut, press and hold one or more modifier keys and then press the last key of the shortcut. For example, to use Command-C (copy), press and hold the Command key, then the C key, then release both keys. Mac menus and keyboards often use symbols for certain keys, including modifier keys:
On keyboards made for Windows PCs, use the Alt key instead of Option and the Windows logo key instead of Command.
Some keys on some Apple keyboards have special symbols and functions, such as for display brightness , keyboard brightness , Mission Control and more. If these functions aren't available on your keyboard, you may be able to reproduce some of them by creating your own keyboard shortcuts. To use these keys as F1, F2, F3 or other standard function keys, combine them with the Fn key.
Cut, copy, paste and other common shortcuts
Command-X: Cut the selected item and copy it to the Clipboard.
Command-C: Copy the selected item to the Clipboard. This also works for files in the Finder.
Command-V: Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder.
Command-Z: Undo the previous command. You can then press Shift-Command-Z to Redo, reversing the undo command. In some apps, you can undo and redo multiple commands.
Command-A: Select All items.
Command-F: Find items in a document or open a Find window.
Command-G: Find Again: Find the next occurrence of the item previously found. To find the previous occurrence, press Shift-Command-G.
Command-H: Hide the windows of the front app. To view the front app but hide all other apps, press Option-Command-H.
Command-M: Minimise the front window to the Dock. To minimise all windows of the front app, press Option-Command-M.
Command-O: Open the selected item or open a dialogue to select a file to open.
Command-P: Print the current document.
Command-S: Save the current document.
Command-T: Open a new tab.
Command-W: Close the front window. To close all windows of the app, press Option-Command-W.
Option-Command-Esc: Force quit an app.
Command-Space bar: Show or hide the Spotlight search field. To perform a Spotlight search from a Finder window, press Command-Option-Space bar. (If you use multiple input sources to type in different languages, these shortcuts will change input sources instead of showing Spotlight. Find out how to change a conflicting keyboard shortcut.)
Control-Command-Space bar: Show the Character Viewer, from which you can choose emoji and other symbols.
Control-Command-F: Use the app in full screen, if supported by the app.
Space bar: Use Quick Look to preview the selected item.
Command-Tab: Switch to the next most recently used app amongst your open apps.
Shift-Command-5: In macOS Mojave or later, take a screenshot or make a screen recording. Or use Shift-Command-3 or Shift-Command-4 for screenshots. Find out more about screenshots.
Shift-Command-N: Create a new folder in the Finder.
Command-Comma (,): Open preferences for the front app.
Sleep, log out and shut down shortcuts
You may need to press and hold some of these shortcuts for slightly longer than other shortcuts. This helps you to avoid using them unintentionally.
Power button: Press to turn on your Mac or wake it from sleep. Press and hold for 1.5 seconds to put your Mac to sleep.* Continue holding to force your Mac to turn off.
Option-Command-Power button* or Option-Command-Media Eject : Put your Mac to sleep.
Control-Shift-Power button* or Control-Shift-Media Eject : Put your displays to sleep.
Control-Power button* or Control-Media Eject : Display a dialogue asking whether you want to restart, sleep or shut down.
Control-Command-Power button:* Force your Mac to restart, without prompting to save any open and unsaved documents.
Control-Command-Media Eject : Quit all apps, then restart your Mac. If any open documents have unsaved changes, you will be asked whether you want to save them.
Control-Option-Command-Power button* or Control-Option-Command-Media Eject : Quit all apps, then shut down your Mac. If any open documents have unsaved changes, you will be asked whether you want to save them.
Control-Command-Q: Lock your screen immediately.
Shift-Command-Q: Log out of your macOS user account. You will be asked to confirm. To log out immediately without confirming, press Option-Shift-Command-Q.
* Does not apply to the Touch ID sensor.
Finder and system shortcuts
Command-D: Duplicate the selected files.
Command-E: Eject the selected disk or volume.
Command-F: Start a Spotlight search in the Finder window.
Command-I: Show the Get Info window for a selected file.
Command-R: (1) When an alias is selected in the Finder: Show the original file for the selected alias. (2) In some apps, such as Calendar or Safari, refresh or reload the page. (3) In Software Update preferences, check for software updates again.
Shift-Command-C: Open the Computer window.
Shift-Command-D: Open the desktop folder.
Shift-Command-F: Open the Recents window, showing all of the files you have viewed or changed recently.
Shift-Command-G: Open a Go to Folder window.
Shift-Command-H: Open the Home folder of the current macOS user account.
Shift-Command-I: Open iCloud Drive.
Shift-Command-K: Open the Network window.
Option-Command-L: Open the Downloads folder.
Shift-Command-N: Create a new folder.
Shift-Command-O: Open the Documents folder.
Shift-Command-P: Show or hide the Preview pane in Finder windows.
Shift-Command-R: Open the AirDrop window.
Shift-Command-T: Show or hide the tab bar in Finder windows.
Control-Shift-Command-T: Add selected Finder item to the Dock (OS X Mavericks or later)
Shift-Command-U: Open the Utilities folder.
Option-Command-D: Show or hide the Dock.
Control-Command-T: Add the selected item to the sidebar (OS X Mavericks or later).
Option-Command-P: Hide or show the path bar in Finder windows.
Option-Command-S: Hide or show the Sidebar in Finder windows.
Command-Slash (/): Hide or show the status bar in Finder windows.
Command-J: Show View Options.
Command-K: Open the Connect to Server window.
Control-Command-A: Make an alias of the selected item.
Command-N: Open a new Finder window.
Option-Command-N: Create a new Smart Folder.
Command-T: Show or hide the tab bar when a single tab is open in the current Finder window.
Option-Command-T: Show or hide the toolbar when a single tab is open in the current Finder window.
Option-Command-V: Move the files in the Clipboard from their original location to the current location.
Command-Y: Use Quick Look to preview the selected files.
Option-Command-Y: View a Quick Look slideshow of the selected files.
Command-1: View the items in the Finder window as icons.
Command-2: View the items in a Finder window as a list.
Command-3: View the items in a Finder window in columns.
Command-4: View the items in a Finder window in a gallery.
Command-Left Bracket ((): Go to the previous folder.
Command-Right Bracket ()): Go to the next folder.
Command-Up Arrow: Open the folder that contains the current folder.
Command-Control-Up Arrow: Open the folder that contains the current folder in a new window.
Command-Down Arrow: Open the selected item.
Right Arrow: Open the selected folder. This only works when in list view.
Left Arrow: Close the selected folder. This only works when in list view.
Command-Delete: Move the selected item to the Bin.
Shift-Command-Delete: Empty the Bin.
Option-Shift-Command-Delete: Empty the Bin without a confirmation dialogue.
Command-Brightness Down: Turn video mirroring on or off when your Mac is connected to more than one display.
Option-Brightness Up: Open Displays preferences. This works with either Brightness key.
Control-Brightness Up or Control-Brightness Down: Change the brightness of your external display, if supported by your display.
Option-Shift-Brightness Up or Option-Shift-Brightness Down: Adjust the display brightness in smaller steps. Add the Control key to this shortcut to make the adjustment on your external display, if supported by your display.
Option-Mission Control: Open Mission Control preferences.
Command-Mission Control: Show the desktop.
Control-Down Arrow: Show all windows of the front app.
Option-Volume Up: Open Sound preferences. This works with any of the volume keys.
Option-Shift-Volume Up or Option-Shift-Volume Down: Adjust the sound volume in smaller steps.
Option-Keyboard Brightness Up: Open Keyboard preferences. This works with either Keyboard Brightness key.
Option-Shift-Keyboard Brightness Up or Option-Shift-Keyboard Brightness Down: Adjust the keyboard brightness in smaller steps.
Option key while double-clicking: Open the item in a separate window, then close the original window.
Command key while double-clicking: Open a folder in a separate tab or window.
Command key while dragging to another volume: Move the dragged item to the other volume, instead of copying it.
Option key while dragging: Copy the dragged item. The pointer changes while you drag the item.
Option-Command while dragging: Make an alias of the dragged item. The pointer changes while you drag the item.
Option-click a disclosure triangle: Open all folders within the selected folder. This only works when in list view.
Command-click a window title: See the folders that contain the current folder.
Find out how to use Command or Shift to select multiple items in the Finder.
Click the Go menu in the Finder menu bar to see shortcuts for opening many commonly used folders, such as Applications, Documents, Downloads, Utilities and iCloud Drive.
Document shortcuts
The behaviour of these shortcuts may vary, depending on the app you're using.
Command-B: Boldface the selected text, or turn boldfacing on or off.
Command-I: Italicise the selected text, or turn italics on or off.
Command-K: Add a web link.
Command-U: Underline the selected text or turn underlining on or off.
Command-T: Show or hide the Fonts window.
Command-D: Select the Desktop folder from within an Open dialogue or Save dialogue.
Control-Command-D: Show or hide the definition of the selected word.
Shift-Command-Colon (:): Display the Spelling and Grammar window.
Command-Semicolon (;): Find misspelled words in the document.
Option-Delete: Delete the word to the left of the insertion point.
Control-H: Delete the character to the left of the insertion point. Or use Delete.
Control-D: Delete the character to the right of the insertion point. Or use Fn-Delete.
Fn-Delete: Forward delete on keyboards that don't have a Forward Delete key. Or use Control-D.
Control-K: Delete the text between the insertion point and the end of the line or paragraph.
Fn-Up Arrow: Page Up: Scroll up one page.
Fn-Down Arrow: Page Down: Scroll down one page.
Fn-Left Arrow: Home: Scroll to the beginning of a document.
Fn-Right Arrow: End: Scroll to the end of a document.
Command-Up Arrow: Move the insertion point to the beginning of the document.
Command-Down Arrow: Move the insertion point to the end of the document.
Command-Left Arrow: Move the insertion point to the beginning of the current line.
Command-Right Arrow: Move the insertion point to the end of the current line.
Option-Left Arrow: Move the insertion point to the beginning of the previous word.
Option-Right Arrow: Move the insertion point to the end of the next word.
Shift-Command-Up Arrow: Select the text between the insertion point and the beginning of the document.
Shift-Command-Down Arrow: Select the text between the insertion point and the end of the document.
Shift-Command-Left Arrow: Select the text between the insertion point and the beginning of the current line.
Shift-Command-Right Arrow: Select the text between the insertion point and the end of the current line.
Shift-Up Arrow: Extend text selection to the nearest character at the same horizontal location on the line above.
Shift-Down Arrow: Extend text selection to the nearest character at the same horizontal location on the line below.
Shift-Left Arrow: Extend text selection one character to the left.
Shift-Right Arrow: Extend text selection one character to the right.
Option-Shift-Up Arrow: Extend text selection to the beginning of the current paragraph, then to the beginning of the following paragraph if pressed again.
Option-Shift-Down Arrow: Extend text selection to the end of the current paragraph, then to the end of the following paragraph if pressed again.
Option-Shift-Left Arrow: Extend text selection to the beginning of the current word, then to the beginning of the following word if pressed again.
Option-Shift-Right Arrow: Extend text selection to the end of the current word, then to the end of the following word if pressed again.
Control-A: Move to the beginning of the line or paragraph.
Control-E: Move to the end of a line or paragraph.
Control-F: Move one character forwards.
Control-B: Move one character backwards.
Control-L: Centre the cursor or selection in the visible area.
Control-P: Move up one line.
Control-N: Move down one line.
Control-O: Insert a new line after the insertion point.
Control-T: Swap the character behind the insertion point with the character in front of the insertion point.
Command-Left Curly Bracket ((): Left align.
Command-Right Curly Bracket ()): Right align.
Shift-Command-Vertical bar (|): Centre align.
Option-Command-F: Go to the search field.
Option-Command-T: Show or hide a toolbar in the app.
Option-Command-C: Copy Style: Copy the formatting settings of the selected item to the Clipboard.
Option-Command-V: Paste Style: Apply the copied style to the selected item.
Option-Shift-Command-V: Paste and Match Style: Apply the style of the surrounding content to the item pasted within that content.
Option-Command-I: Show or hide the inspector window.
Shift-Command-P: Page setup: Display a window for selecting document settings.
Shift-Command-S: Display the Save As dialogue or duplicate the current document.
Shift-Command-Minus sign (-): Decrease the size of the selected item.
Shift-Command-Plus sign (+): Increase the size of the selected item. Command-Equal sign (=) performs the same function.
Shift-Command-Question mark (?): Open the Help menu.
Other shortcuts
For more shortcuts, check the shortcut abbreviations shown in the menus of your apps. Every app can have its own shortcuts, and shortcuts that work in one app might not work in another.
Apple Music shortcuts: Choose Help > Keyboard shortcuts from the menu bar in the Music app.
Other shortcuts: Choose Apple menu > System Preferences, click Keyboard, then click Shortcuts.
Learn more
Create your own shortcuts and resolve conflicts between shortcuts
Change the behaviour of the function keys or modifier keys

0 notes
Note
Story prompt: Wonder Woman tricked.
"Show me that again!" Demanded Diana as she licked her ice-cream, her eyes focused on the card table.
"Sure", replied Zatanna as she quickly shuffled the cards around and slid one across the table and tapped it. "So, take a look at that, memorize it for me."
Diana lifted the card and looked at it. Queen of hearts. "I know it," she said before sliding it back, watching as Zatanna put it on top of the deck and started to shuffle it once more.
"Now, keep your eyes on it," Zatanna smiled as she quickly moved the cards around, shuffling the deck with speed and precision. "Now, you shuffle it," grinned Zatanna as she passed the deck to Diana.
Diana started to shuffle the deck slowly until she thought the deck was thoroughly mixed up. She passed the deck back and Zatanna waved her hands over it again.
With one graceful movement, Zatanna lifted a card off the top of the deck. "This isn't your card," smirked Zatanna as Diana saw that the card in front of her was a Wonder Woman trading card. She laughed.
"It is not, so where is my card?" Asked Diana, getting more excited to see where the trick was going.
"Well I have a good idea," grinned Zatanna as she leaned forward over the table and slide a hand under Diana's top and produced the Queen of hearts.
"Amazing!" Cheered Diana, clapping her hands. Zatanna laughed and brushed it off with a wave of her hand.
"I don't understand why this impresses you so much, you have seen gods and beings from beyond the stars do much more interesting things than this," she said.
"But sister," replied Diana firmly. "If one naturally has magic, then using it is akin to breathing. Tricks like these require skill and practice, making them much more impressive than a god just clapping their hands." She said with a smile.
Zatanna nodded and pulled a goblet towards her, sipping from it. Diana looked at it with curiosity, only for Zatanna to speak before Diana could get a word out. "Halloween store, it is made of plastic, I keep it around as a wine glass," she smiled, tapping a nail against it to prove her point.
"What other tricks do you know?" Said, Diana, as she finished the final few licks of her ice cream. "If you have time to show me more of course." Zatanna pondered for a few moments before she smirked.
"I have just the trick, it involves the cards again. Pass me the Queen if you will?" Asked Zatanna, watching as Diana slid the card towards Zatanna. "So we both know this is your card, but it matters less for this trick," she explained as she shuffled the deck. "I just need you to list off all the cards that have been drawn whenever I draw a new one, make sense?" She asked.
Diana nodded and leaned forward to make sure she had the best view of the cards. Before she could fully get ready Zatanna pulled a card off the top. "Four of Spades," said Diana quickly, looking up to see Zatanna nod at her before putting the card face down and drawing again.
"Jack of Clubs, Four of Spades," said Diana, once again glancing upwards to make sure she was not about to ruin the trick. Quickly Zatanna drew another card before flipping the previous one on top of the first.
"Ace of Diamonds, Jack of Clubs, Four of Spades," said Diana quickly, getting into this game, excited to see when the trick began, doing her best to hold all the cards in memory. Her eyes following as Zatanna quickly made the face-down pile bigger before she drew another card.
"Five Of Diamonds, Ace of Diamonds, Jack of Clubs, Four of Spades," said Diana quickly, rattling off the cards with great pace, another card was placed on the table and Diana went again, her voice getting gradually louder. "Six of Hearts, Five Of Diamonds, Ace of Diamonds, Jack Of Clubs, Four of Spades," she said quickly, her eyes never leaving Zatanna's gloved hands.
Zatanna moved again, laying down another card, prompting Diana to start. "Seven of Spades, Six of Hearts, Five Of Diamonds, Ace of Diamonds," started Diana, quickly stuttering as she tried to remember the next card but quickly recovered, the confidence in her voice fading slightly. "Jack of Clubs, Four of Spades".
Diana wanted to take a breath but she couldn't as Zatanna laid down yet another card, forcing Diana to list them off again. "Four of Hearts, Seven of Spades, Six of Hearts, Five Of Diamonds, Ace of Diamonds, Jack of Clubs, Four of Spades," said Diana, obviously struggling to keep track of all the cards as they flew down onto the table. Zatanna moved again, giving Diana even less time to recover.
"Umm," hesitated Diana for a moment before starting. "Ace of Spades, Four of Hearts, Seven of Spades, Six of Hearts, Five Of Diamonds, Ace of Diamonds, Jack of Clubs, Four of Spades," said Diana, her confidence totally gone, her voice constantly wavering.
Zatanna went to produce another card but suddenly spoke. "Do it the other way round, what was the first card?" Diana floundered, trying to work out what it was, but suddenly felt a card tap her on the forehead and her head fell back, her neck going limp. A word slipped from Zatanna's lips and echoed around Diana's foggy head. "Sleep."
Zatanna watched as Diana went limp in the chair, her eyes rolling back up into her head, the Queen of Hearts stuck to her forehead. Zatanna laughed for a moment. "Oh Diana, that was far too easy, I'm sure you'll forgive me in time, I mean I doubt I'm the first girl to trick you into her kinks," she laughed to herself as she stood up and moved to the other side of the table, starting to rub Diana's shoulders, leaning in to whisper in her ear.
"Now Diana, Wonder Woman, the Queen of Hearts is your card, your card is the Queen of Hearts, you are linked to this card, so deeply and so totally that whenever I. Zatanna. Show it you and place it on your forehead, you will fall back into this deep obedient trance, am I understood?" Asked Zatanna firmly.
"Yes," mumbled Diana. Zatanna smiled, it was rare to see the mighty Amazon sound out of breath, let alone so drowsy and helpless. "Now Diana, please take your clothes off for me," smiled Zatanna as she pulled the card off Diana's forehead. Zatanna leaned against the table and watched as Diana stumbled to her feet and slowly started to remove her shirt and skirt, only to reveal the Wonder Woman costume underneath. Zatanna couldn't help but laugh, had Diana been so keen to see magic tricks and eat ice cream that she didn't bother change before coming to her?
Slowly Diana peeled her costume away, her muscular Amazon form on total display to Zatanna's prying eyes. "It looks even better than I thought," smiled Zatanna moving close to Diana and running her hands over Diana's firm abs. Zatanna looked up at the glassy-eyed Amazon and bit her lip gently.
"Diana," purred Zatanna. "Until I tell you to stop, please repeat the phrase "I am hypnotized, I obey Zatanna," start now," said Zatanna firmly. Instantly Diana started to chant.
"I am hypnotized, I obey Zatanna," said Diana with a drowsy yet firm tone, like all her energy, was focused on following the command. Zatanna smiled and spent some time exploring Diana's firm muscles, letting the manta wash over her. Something about hearing the Amazon mindlessly chanting her obedience was just so hot and Zatanna was loving every minute of it. However, after a while Zatanna pulled herself away, she did have things to do.
"You may stop," said Zatanna as she pointed to the chair. "Sit down Diana." She said, watching as Diana instantly complied with the order. Zatanna held the card up in front of Diana. "This is your card, the Queen of Hearts. It signifies your obedience to me, but to make my control total, you are going to mark the card by kissing it. The kiss will signify you totally signing your will over to me" Smiled Zatanna moving the card closer. Diana puckered and kissed the card, leaving a faint mark on it. Zatanna smiled. "Good girl, get dressed now please," she commanded.
As Diana stumbled back into her clothes, Zatanna wandered to one of her many cabinets and pulled out a heavy leather folder. She opened it with a loud creak, revealing a card binder with several other cards. Zatanna ran her finger down the binder before tapping an empty slot. "Lets put you next to Quinn, you two do make a cute pair after all," smiled Zatanna as she slipped the card into the holder before closing the folder.
She then slowly moved back towards the table and saw Diana sat down, fully dressed once more. "Now Diana, when I clap my hands, you will wake up and think the trick I just did was amazing, you won't remember being my Queen of Hearts, nor will you remember anything that happened," explained Zatanna before clapping her hands.
Diana blinked and then cheered. "Sister! I am amazed!" She exclaimed, her face full of pure joy. "That was your most impressive trick yet!" Diana beamed.
"Oh, I'm glad you liked my trick," smirked Zatanna. "More ice cream?" She asked as she moved to try and hide her very obvious smirk.
"Wonderful!" Exclaimed Diana.
130 notes
·
View notes
Text
Secret menu to background scrolling, top Windows 10 tricks every PC user must know - tech

Windows remains the most popular and user-friendly operating system out there with the company revealing back in 2019 that Windows 10 is already running on more than 900 million devices.The popularity of the OS was further established by the fact that there have been more new Windows 10 devices in the last 12 months than in any previous years.A successor to Windows 8.1, the Windows 10 has a number of user-friendly features that makes working on it faster and more convenient. We take a look at some of its lesser known features.1. Secret Start menu: Windows 10 has a second Start menu that allows accessing features such as Command Prompt, Control Panel and Task manager. One can either access it by pressing Windows key + X, or by right clicking the windows icon/Start button.2. Take a screenshot: Windows 10 allows users to take screenshots in multiple ways. The easiest way it to press the Windows Key along with Print Screen Key and the image will be saved to the Screenshots folder in Pictures.In case, users want to capture a partial screen, they can press Windows key+Shift+S to open the Snip and Sketch tool which allows one to click and drag a create a screenshot to save image to the Clipboard.3. Create event without opening Calendar: One can add events to the Microsoft calendar directly from the Taskbar, without opening at all. Go to the Taskbar and click a time and date box followed by choosing the date when one wants to schedule an event.A person needs to enter the event name, time and location, followed by save. This would lead to the event appearing in the Calendar across all apps.German govt failed to upgrade to Windows 10, now has to pay over Rs 6 crore: Report4. Finding out how much space apps are taking: To figure out how much space apps use, one needs to go to Storage under System of Settings and then click on the drive they want to search.Now, choose apps & games to see a list of apps that are installed on the machine and how much space they take up. A user can delete apps not being used from the list.5. Minimise windows: Sometimes while working, the windows can get cluttered with too many tabs. Windows 10 allows for users to minimise all windows except the one they are currently working on.One has to click the title bar of the window they want active and then hold the mouse down and shake the window back and forth quickly. After a couple of quick shakes, all other windows will minimise save the active one.Windows 10 tips and tricks: How to enable the hidden ‘God Mode’6. Enable Focus Assist to cut down distractions: Sometimes while working, one gets constantly bothered by notifications. The Focus option allows users to determine how many notifications they get. One needs to go to Settings, followed by System and then Focus.This gives users three options:-- Off: Allows all notifications-- Priority: You can only opt for a customised list of notifications-- Alarm: Only alarms and no notifications are allowed7. Background scrolling: Windows 10 allows users to scroll up and down on any window even if someone is not directly working on them. One can open two programmes and then arrange them in a manner which allows one to hover their mouse on the second window and scroll.While the feature should be activated by default, if it does not, one needs to go to Settings > Devices > Mouse, and toggle Scroll inactive windows when I hover over them to On.8. Get rid of ads in Start menu: To enable the feature, one needs to go to Settings, followed by Personalisation and Start. Once there, toggle the setting ‘Show suggestions occasionally’ to the off position.9. Shut down background apps: Background apps, though useful often suck the battery and data power dry. To shut down background apps on Windows 10, one needs to first go to the toggle Background apps under Privacy in Settings and turn the toggle ‘Let apps run in the background’ to Off.10. File extensions in File Explorer: To see file extensions, one needs to first go to the Search Bar at the bottom of the screen and type File Explorer Options and click on the View Tab in the window that subsequently pops up.Then uncheck the box that says Hide extensions for known file types followed by Apply and OK to view file extensions for all files.11. Open items on Taskbar with keyboard shortcuts: In case users have pinned programmes in the Taskbar, they can use the keyboard shortcut Windows key + Number Key to open that particular programme. The number key has to correspond to the position of the programme on the Taskbar. Read the full article
#announcement#bnewsbijapur#bnewschannel#bnewschannelwiki#bnewsdeoria#bnewsfacebook#bnewshindi#bnewskolhapur#bnewskolhapurlive#bnewslogo#bnewstvchannel#background#bulletins#cnewsbharat#cnewsbharatlogo#cnewsbharatup/uk#cnewschannel#cnewslivetv#cnewslogo#cnewsmarathi#cnewstv#cnewsup#cnewsvideo#cosmosnews#dnewsapp#dnewsappdownload#dnewschannel#dnewshindi#ddnews#ddnewsanchor
0 notes
Text
How to Create Undetectable Hidden Folder Using Command Prompt.
How to Create Undetectable Hidden Folder Using Command Prompt.
How to Create Undetectable Hidden Folder Using Command Prompt?
A Simple Command prompt trick to Hide and UnHide the Folder in windows, by using this Method the Folder Cannot Be Detected by any other methods in windows, it can unhide by only with the command.
The Following Commands are used to Show and Hide the Folders.
To Hide the Folder.
—-> attrib +s +h [FilePath]
To UnHide the Folder.
—-> attr…
View On WordPress
#command prompt trick to hide the folder#command prompt tricks#command to hide folder#create hidden folder using command prompt#Create Undetectable Hidden Folder Using Command Prompt#hidden folder#hidden folder using command prompt in windows 10#Hide Files or Folders Using Command Prompt#hide folder in pc#hide folder using cmd#How to Create Undetectable Hidden Folder#How to Create Undetectable Hidden Folder Using Command Prompt#how to hide and unhide folder using cmd#how to hide files or folder in windows#undetectable folder#undetectable folder using cmd#unhide folder using cmd
0 notes
Note
Do you take nsfw prompts? Can you make a nsfw fic where Richelieu has to spend one night with some foreign ambassador for political reasons? w/o Treville knowing. Thanks!
Congratulations, anon ! You made me produce a textbook example of “ficlet gone mad”, meant to be a 800 words thing, ending up at 3am with 4500 words and the salty feeling of lost control.There you go then, a fat slice of porn with plot.Because yes, I take the porn prompts.
This Man is an Island.
(Also on AO3)Because the 17th century is also the last days of piracy, and I always wanted Armand to meet a fierce, savage pirate once.
Enjoy.
-« You’renot the only ship-owner of France, Basseterre.” The King spits.
-“Certainlynot” Basseterre laughs, “but I am the best.”
Louis letsout an exasperated huff, shifts on his seat, and just like every time, just asalways, he turns to his First Minister for support. Richelieu subtly bows hishead, more to ease the King’s frustration than to show obedience, and clearshis throat as he stands up to pace around Basseterre.
The meetingis starting on its third hour, and it has turned from an amiable talk to ahissing war of pride and defiance. Louis has lost any sense of patience onehour ago, and the battle is mostly raging between the Cardinal’s quiet wits andBasseterre’s smug impudence.
The stakesare high and they both know it. Countless plantations of tobacco and cottonhave developed in the new colonies of Guadeloupe, and France needs gold. Richelieuhas worked himself to exhaustion to make sure the main trading posts of Franceare secure, and it included strangling La Rochelle to death. A fortune nowawaits in the Antilles, and all France needs are safe, sturdy ships to bring ithome. Right on the other side of the Channel, England is making dreadfulprogress in those matters, and the Cardinal cannot stand to fall behind. It ismaking him literally, physically sick.
JeanLaurent de Basseterre is nothing more than a pirate with a good name.
JeanLaurent de Basseterre is even likely not to be his real name.
But, by theDevil’s work and a thousand slit throats, he owns one galleon, three frigatesand five clippers.
Enough toguarantee France a glorious income, and prestige upon the seas.
Richelieuwants those ships and Basseterre knows it. The privateer has been playing thenegotiations like a game, dismissing gold, titles and land with a shrug,refusing any offer the King had prepared for him, but never leaving the tablenonetheless.
And nowthat the King has run out of bargains, sitting cross-armed in his high seat, anoutraged pout on his soft features, Bassterre slumps back in his own chair, oneankle resting on his knee, his blunt fingers tapping a joyful tune upon thearmrests, watching the Cardinal keeping up the fight with absolute delight.
Theship-owner is a tall, bulky man, his hair too long and his beard too short forParis’ standards, an untamed look stuck to every inch of his skin. He came inwithout weapons as required, but his sturdy boots left dirt and mud everywherein the corridors from the main gates to the reception rooms. His thick leatherdoublet and dirty ruffled shirt are nothing more, no doubt, than what he’s beenwearing all week.
TheCardinal’s heavy robes slide around Bassterre’s seat, storms brewing in thesoft waves of silk. Richelieu shuffles idly through a few papers, his cleverstare filled with disdain, and the ship-owner looks halfway between curious andincredibly pleased.
-“Bereasonable, Basseterre” The Cardinal states; “surely you can understand thisdeal we propose is both profitable and salutary for you.”
The brownman laughs, a clear, challenging sound that must have earned him a few gloriesin the taverns of Saint-François.
-“Salutary,really?” He sneers. “What kind of threat could France protect me from?”
-“Yourself.”Richelieu whispers, and starts reading a paper he just unrolled. “Theft andinsulting behavior, embezzlement of State propriety, destruction of Nationalestate building, treason, trading of stolen goods, and no less than thirteenaccusations of murder.”
He lets thesheet roll back around itself with a soft clapping sound. Basseterre pales.
-“Andthat’s only for the Governor of Antilles.” The Cardinal adds distractedly. “Ihave a few other, rather impressive lists from Le Havre and Bordeaux, do youwant me to go through them also?”
Theprivateer narrows his dark eyes, biting his lips. On the higher seat facing himat the table, the King almost claps his hands in triumph, but the sailordoesn’t even spare a glance for him. He only stares at Richelieu in anger andmild fear.
-“Youhaven’t got enough evidence.” He dares, pointing at the sheet. -“I have hanged better men than you with half as much.” The Cardinal smilesback, like honey poured upon a razorblade.
Basseterrefrowns. He puts both feet on the floor with a loud thud, his whole facehardened, almost showing teeth like a dog. He did expect a few tricks from thefamous Cardinal, but he certainly didn’t picture him going straight frombargaining with title and lands to cold, ruthless hanging threat.
His jawtwitches. There’s sweat on his forehead, and by that furtive look he has forthe window, he may be considering jumping from it.
-“No prison can hold me for too long. “He claims, but in his voice, half of theconfidence has crumbled. “I’ll leave France and never come back.”
-“I’d like to see you try.” Richelieu hisses. “And even if you do succeed, Francehas allies, Basseterre, and those I don’t have, I can pay for. I could makesure there isn’t an acre of land you could safely make a stopover on.”.
With afurious flinch, the privateer bangs his fist on the table, making Louis jump inshock, and growls at the Cardinal with the smile of a famished wolf:
-“Clever beast you are.”
Richelieufrowns, waiting for the man to get up and hit something, but Basseterre only eyeshim up and down without a word, his smile too heavy to be safe. The Cardinal,somewhat confused, retreats a few steps away from that hungry stare.
After along, bitter silence around the table, the ship-owner barks one more vibrant laughter,and raises his hands in surrender.
-“Alright,you poisonous snake, bring me that contract.”
Richelieu’sjaws clench in anger, but he lets the insult pass without retort. The deaththreat was, after all, his last trump card, and it would be wiser not to ruinit all with the sin of pride. He gently opens a thick folder instead and pullsout a large sheet filled with thick handwriting to lay it down in front ofBasseterre.
As theCardinal leans to offer a quill, the privateer looks up at him once more, hiswild, fierce eyes burning a lazy path up and down the red robes, and hesuddenly grabs Richelieu’s sleeve with dreadful force.
Pulling him a few inches closer, he whispersin his ear, barely above a sigh:
-“I’ll signon one last condition.”
The Red Manwinces, struggling to recoil from the unwanted contact, and shoots a glancetowards the King. As Louis, looking a bit lost, doesn’t seem to demand anexplanation, Richelieu mouths something like “Yes?”, and Basseterre grins likea devil.
He liftshis chin up, high enough for his lips to graze Richelieu’s ear, and breathes:
-“I want you. In my bed. Tonight.”
TheCardinal gasps, shrugging himself off Basseterre’s grip, stands up and staresat him in shock and disbelief. He instinctively joins his hands on his chest insheer anguish, the whirlwind in his eyes as only cue of the panickedcalculations of his mind.
-“What’sgoing on?” the King asks, impatient.
The Cardinalturns to Louis with a start and gently bows with a dismissive wave of his hand.
-“Nothingof importance, Your Majesty” he claims with an amazingly steady voice. “Our newshipping agent is merely jesting.”
Though whenhe turns back to Basseterre, the rugged man’s focused eyes assure him that heisn’t.Richelieu weights his options for a few more seconds, holding the sailor’s starewith a blank face.
Basseterreis a pirate. A wealthy one, but a pirate nonetheless. He indeed has anincredible record of escaping all sorts of prisons, and even if he ends uphanged high on Place de Grève, Richelieu still needs to find his ships in thecreeks of Guadeloupe and claim them as State Propriety. They’re not likely tobe tied up in a row in an open space, waiting to be commandeered.
TheAntilles are still far from Richelieu’s grasp. He hasn’t settled trusted men onthose new islands yet.
He may killBasseterre, but that wouldn’t guarantee him those ships, and the able men tosail them. The best option remains to obtain Basseterre’s complete allegiance.
Anyalternative would mean France lowering its sights concerning colonial trade.France falling behind England in both fortune and prestige.
Thatthought is unbearable.
The idea ofspending one night, one hour with this man feels too wrong for words, but truthbe told, claiming anything about the Church, his title, his rank, or the simplefact that they are both men would be nothing short of deceit.
None ofthis stopped him from taking Captain Treville as a lover.
Treville.Richelieu hides a flinch of agony with a sharp bite of his thumb. Jean. Hisdearest, beloved Jean.
The reasonit all feels wrong, the reason Richelieu is one inch away from sending thispirate to the gallows and cut France’s ambitions in half, truly, is hisCaptain.
Trevilleknows, of course, the rules of Armand’s world. Treville knows the deceit andthe lies, the plot and the schemes, the murders and the debauchery. He knows,dear Jean, the filthy things Armand must do, the mud he can crawl into, as longas France has something to earn from it.
They fightabout it almost every week.
But this.
Treville isnot going to take it lightly. Armand can already hear his growls of fury, thesound of his boots clanging on the floor. He’ll shout, surely. Maybe he’llbreak something, and leave for a while, banging the door upon a string ofinsults.
Buteventually he’ll understand.
Franceneeds those ships.
France needs. All is said.
Richelieu letsout a shaky sigh, looks at the privateer in the eyes and nods softly.
Basseterregrunts in satisfaction, snatching the quill out of the Cardinal’s hands, andsigns his pledge to France in four curves of writing.
-“You are aman of you word. I know that.” The privateer declares loudly.
-“Of courseI am! I am the King of France.” Louis spits in outrage, thinking it was meantfor him.
ButRichelieu’s resigned sigh leaves no doubt about which promise the dark man wasthinking about.
***
The Kinggave Basseterre one of the best guestrooms in the East wing. Nobody even raisesan eyebrow at the sight of the Cardinal knocking on the privateer’s door aftervespers, because the East wing is constantly swarming with diplomatic guests,and the shadow of the Red Man is a recurring ghost in those corridors.
Basseterreopens the door and his tanned face splits into a delighted grin. He letsRichelieu in and locks the door behind him.
-“You are a man of your word.” He joyfullystates once they’re both standing in the wide, sumptuous bedroom.
-“WheneverI can be.” The Cardinal lets out half-heartedly.
The sailorgoes for a thin, long table near the high windows and chooses a bottle of oldBordeaux among the dozen he has obviously requested to be brought there. Twoempty bottles are already abandoned on the floor, with Basseterre’s boots andguns.
Hegenerously fills a glass and hands it over to the Cardinal, who refuses with asharp shake of his head. Richelieu keeps his reluctant stare on the hearth,where a dim fire is breathing, almost useless in this warm summer evening.Basseterre has opened all the windows wide, and the air is heavy with the scentof the gardens outside. Inside, the smell of old oak and tonight’s dinner stilllinger around the tapestries. No voice, no footstep can be heard, the Louvresslowly falling asleep at this time of the night.
Theprivateer sighs, his arm still stretched out towards the Red Man, holding theglass of wine:
-“Come on, Cardinal. Drink with me. Let it be good for both of us, right?”
Richelieulifts his chin up, beaming defiance, but the contract is signed, and thisnight’s fate is sealed. He takes the glass in his gloved hand. Basseterresmiles like a wolf again, making a slow circle around him, not bothering tohide is admiration for one second.
-“You rathercaught me back there, this afternoon, you know.” He gently muses, his eyesdevouring the red silk. “They told me you were a sly one. But gatheringevidence to hang me, really! That’sjust vicious.”
-“Yourefused every other proposition.” Richelieu objects, waving his glass in slowcircles to show this savage man how good wine is consumed. “Why did you dothat?”
The piratelaughs that open sound again, and gulps down the most precious Bordeaux of theCourt as if it was a mere tavern plonk. The Cardinal winces in disgust.
-“Becausenone of this has any value to me, Your Eminence.” Basseterre lets out with ashrug. “Do you know what it is to be the richest man in Guadeloupe? Do you haveany idea what Guadeloupe is? The beaches of golden sand, the waters ofsapphire, the lands so fertile you just have to drop the seeds and pick up thefruits. Have you seen the lanterns of the brothels of Saint-François, wheregoddesses of love and poison arrows can be bought for two sous? Have you seenthe green bays of unmarred land, have you felt the burn of ancient rum into yourguts?”
Richelieufrowns, stunned by the fierce, passionate speech. He has a dazed look for thegardens of the Louvres. No, he hasn’t seen Guadeloupe, and certainly neverwill. He has barely ever left France.
He hasnever seen a reason to leave this kingdom, far too busy building it.
The islandshave only one meaning for him: about forty thousand livres per year for thetreasury.
Enough foran army. Enough for a few abbeys and academies. Enough for art, enough forpeace.
Isn’t thatworth a sea of sapphire?
-“If theKing of France had nothing of interest to you” The Red Man whispers, drinkingslowly, his eyes still distant, “why bother coming to the Louvres at all?”
Basseterredoesn’t laugh. He pours himself another glass, not the first and not the last,and empties it in one gulp.
-“Because Ialways meant to sign that contract.” He mutters.
Richelieualmost gasps, the red robes hissing a long complaint as he turns around to facethe tanned man, staring at him with furious, wide eyes. Basseterre holds onwith an open, honest face and speaks, spreading his arms a bit :
-“You knowwhat I am, Cardinal. You know how I won those ships.”
-“Piracy.”Richelieu spits.
-“Yes. Trustme on this, rich pirates don’t live long. And I’m the richest of them all.Every day, every hour I live and breathe in Guadeloupe, I have to watch mysteps, sleep with one eye open, have someone else taste my food. I am tired ofthis. As an official shipping agent of France, with France’s colors on mysails, I might actually have a chance to grow old someday. That’s the trap ofloving the pleasure of life, you see, Eminence? At some point you want them tolast.”
-“Then whyon Earth did it take three hours tohave you sign that paper?” Richelieu growls, banging his empty glass on a lowbuffet next to him.
With that,Basseterre smiles again, that hungry, playful smile of pirates.
-“Because”,he whispers sweetly; “for the sails of all my beloved ships, I wanted France togive me nothing less than what the Goddesses of Guadeloupe give me for a pairof coins. I wanted France in my bed.”
TheCardinal stares at him like at a raging madman, but doesn’t utter a sound, hisback stiff, his hands shaking. The pirate carelessly points towards a hugeportrait of Louis above the mantelpiece behind them and goes on, shrugging somemore:
-“Frankly,I thought about the King first. He’s a handsome boy, and I heard he doesn’tmind men at all.”
Richelieu’sfirst instinct is to defend the King’s reputation, and have this man jailed andgagged forevermore, but truth be told, there is little he can do against whatis much more than a rumor.
He doesn’tthink about it for long anyways, because the dark man’s fingers come and grazehis cheek, and he has to nail himself to the floor or might just run.
-“Butduring our small discussion back there, it’s been quite obvious to me who thetrue ruler of this country is. Who’s pulling the strings in this palace ofpuppets.”
Theprivateer softly grabs Richelieu’s face then, and pulls him inches from hisown, breathing through famished lips:
-“If I wantFrance, well, it’s you I must take.”
TheCardinal closes his eyes, inhaling sharply, desperately trying to push away thethought of Treville. But who else touches him this way, who else could stroke theRed Man’s neck and live to tell the tale.
Trevillewill growl, Treville will shout, and Basseterre will better be far away bythen.
Trevillewill be furious, because though there had been a few women Richelieu had toseduce for information or influence, there had never been another man.
Trevillewill be mad, and maybe he’ll break something, but eventually he’ll understand.
Fortythousand livres a year.
Enough forpeace.
Enough for peace.
Basseterrefrowns at the heavy, intricate red robes, and fumbles with the fabric for awhile before he starts unbuttoning them with careless haste. Treville wouldn’thave. Treville loves those robes, always taking his time, peeling them awaywith silent reverence.
Trevillewill be furious.Treville will be heartbroken.
The sailor feelsRichelieu wince and tense, and freezes in his moves, looking up with impatiencein his brown eyes.
-“You’regoing to be hard work, aren’t you?” He mutters. “Of course, you are.”
The piratesighs, rolls his eyes, and goes to the buffet to pour the Cardinal anotherglass. He hands it over, and doesn’t speak until there’s nothing left of it.Then, he takes it out of Richelieu’s hands, puts it back on the furniture, andsteps close enough for their chests to touch. He cups the thin face firmly andtilts his head to the side, inspecting the soft pale lips of the Red Man as he gentlyasks:
-“Do youhave a shorter name, Your Eminence? I’ve read it somewhere but I can’tremember. Was it Arnaud, Adrien…?”
-“Armand.”Richelieu lets out between clenched teeth.
-“Armand!Lovely. Can I call you Armand? “
-“No.
Basseterrelaughs, delighted.
-“Alright,Armand it will be.”
TheCardinal’s pale eyes narrow, but the contract is signed, and the night’s fateis sealed.
The sailorresumes his unbuttoning with slower moves; his lips kissing the frail skin ofRichelieu’s neck with a bit more care.
-“How doesa man such as you like to be touched, Armand?” He prompts as he presses himselfagainst the thinner man. “How is it with your mistresses, I heard you keptquite a few.”
Basseterre’shands find the silver hair and loose themselves into it, stroking, gripping,pulling back a little to expose the pale throat and devour it like the famishedwolf he is. Richelieu chokes a soft moan, self-loathing painfully visible onhis tired face.
-“Do youremain a man of power, even in bed?” He goes on, his breath a bit short as thered robes fall on a hissing heap on the floor, revealing the tender skin below.“Do you take control?”
His tanned hands rush to stroke and explore the narrow waist, the lean, yetresolved muscles around, his brown, rugged skin making an unholy contrast withthe white velvet taut around the solid bones. The sailor’s thick fingers find asoft spot somewhere around Armand’s lower back and the Red Man’s breath hitches,his eyes faltering.
A wickedglint crawls into Basseterre’s eyes, and he pulls at the silver hair again,using his other hand on Armand’s lower back to press them together until thereis no more doubt about both their hardness. Richelieu whimpers. The piratesneers.
-“Oh. So you don’t.” He breathes, triumphant.“You like to submit, you clever creature. Good.”
Basseterrelets his hand wander down Armand’s buttocks, gripping them viciously once ortwice with an appreciative hum. He gives them a brutal slap, making Richelieu cryout, and the sound of it makes the dark eyes a bit less focused. He does itagain, then. Two, three, four more times, until the cries turn into yelps, adark shade of pink spreading fast on the soft rounded bottom. He kisses the thinnerman’s parted lips with a commanding need, stroking the heated skin he justslapped with delirious bliss. Richelieu’s hands, though he made constantefforts to keep them in tight fists at his own sides, dart up to grab thesailor’s sturdy shoulders.
-“Verygood.” Basseterre pants against Armand’s mouth.
And hequickly searches the insides of his shirt, to retrieve a small stoneware vial.He pulls the cork off with his teeth and spits it on the floor over hisshoulder, and seems to hesitate for a moment, gauging Armand’s face.
After awhile, he pours the contents of the vial on his own hand, shooting Richelieu aquick smile of apology.
-“I’ll dothe work myself, pet, if you don’t mind. I don’t suppose you have any idea whatto do with a man’s cock.”
TheCardinal keeps a blank face, averting his eyes, far too relieved to be allowedto keep his hands where they are.
Basseterre wastes no time. He roughly grabsArmand’s thighs with both hands, and lifts him up on the buffet like a ragdoll, laughing at Richelieu’s sharp cry of surprise and distress.
-“God, youweigh nothing” he huffs, burying his face into the Cardinal’s neck. “Do theyeven feed you in this old house?”
He doesn’texpect any answer. He shoves a thin white leg over his shoulder and pushes twofingers in, feeding on Armand’s scream of pain. He hungrily licks the tremblingskin of Richelieu’s thigh for a while, growling like an animal. Then, he startsworking him open, mercilessly, pulling his own pants down with his other hand,and rubbing himself against Richelieu’s inner thigh with the motion. He’shorribly big, rock-hard and leaking. Armand squeezes his eyes shut, wishing hecould just count backwards in his head and forget about it, but Basseterre hassailed through the world, and knows quite a lot.
After a fewthrusts, he counting has to stop, because Richelieu’s crying out in rawpleasure, mortified and helpless.
Trevillewill be mad.
Trevillewill be hurt.
Is it wortha sea of sapphire?
-“Look atyou” The pirate exhales in the curve of his shoulder as he adds a third fingerwith ease, his brutal thrusts making the old buffet creak with each move. “Lookat you, the Mastermind of France, The King’s own King, look at you meowing likea whore, melting around my fingers.”
Armand’shands blindly cup the man’s face, one of them laid upon his mouth, trying tosilence him, but Basseterre kisses and licks the sensitive palm far too well, abit too much like Treville does, and the hand flies away into the pirate’shair.
The privateerlooks up to bathe in the sight of Richelieu’s blurred eyes, his heavy eyelids,his swollen lips, and what could be a tear or two rolling down the hollowcheeks. He kisses the salty water away, wherever it came from, and whisperssome more, his voice ecstatic and blissful:
-“I firstthought you were not my type, you know? Too thin, too pale, too bloodydelicate, and I hate men of the Church almost as much as they hate me.”
Basseterrepulls out his fingers abruptly, choking Armand’s begging whimper with his eagermouth.
He grabsRichelieu by his buttocks and lifts him up again, sliding him to the side untilhis back hits the wall next to the buffet, sending a few plates and glassesshattering on the floor around their feet.
-“But rightnow, Armand, I swear you are the most beautiful price France could pay for myships.”
And withthat, he thrusts himself in one firm move, pressing Armand against the wallwith voracious force, holding him with his thick, tanned arms.
Richelieu shouts.
Basseterrelaughs and keeps on moving, his hips making calculated waves, reducing Armandto a shuddering mess. The privateer takes his time, carrying the thinner manwith nonchalance, but as Richelieu’s hands grip his hair a bit tighter, hefinds it harder to concentrate. The sounds Armand makes, as muffled as they maybe in his shoulder, drive him mad. He lets out sharp groans too, between crudepraises and gentle curses.
Basseterrehas sailed a thousand seas, and he sure claims he has seen everything, butroughly taking against a wall the man who could hang him with one line in hiswriting, hearing his desperate cries spiraling up in his ear as his back hitsthe rich tapestry with every thrust, all of this is blowing his mind. ‘This manis an Island’, he briefly thinks, but he has no breath top speak it.
Caught likea deer against a hard wall and a dark man, Richelieu’s pliant and supple framestill finds a way to move in sync, making the thrusts deeper, the angledeadlier. Basseterre almost falters, but is kept moving by a superior force. Atsome point, as his thrust become chaos and rage, as his mind is blanked bylightning, he hears Armand’s voice call “Jean” once or twice.
And becausehe thinks that is his name, he comesfirst, hard, crying out against the wall.
Richelieufollows, painfully, impaling himself on Basseterre a few more times and lettingout a long, soft whimper.
Only then,the sailor crumbles down on the floor, dragging Armand with him in a mess oftangled limbs. Both lay down there, stunned and panting, until Basseterrerealizes he is bleeding in three places, because he fell on the broken glassesof the buffet. He laughs, then, his voice broken, and Richelieu, in spite of itall, may have smiled back a little.
***
As Armand,fully dressed and dignified enough, was closing the discrete bandages onBasseterre’s legs a few moments later, kneeling next to the bed where thepirate was lying, he started listing the duties of the new shipping agent ofFrance as mentioned in the contract. Basseterre listened, his smugness somewhattamed down to quiet respect, barely risking a few taunts from time to time:
-“I havesigned the paper, but you haven’t been in my bed yet.” He tried once, his handtapping the cover invitingly.
-“I wouldhave been, if you hadn’t been a bear more than a gentleman. You had yourchance.”
Theprivateer laughed some more.
Richelieudidn’t smile, but his face wasn’t entirely hostile as he wiped the lastremnants of blood off the dark man’s thighs and moved to stand up. Before hedid, Basseterre grabbed his wrist and whispered, his eyes narrow:
-“Are wefriends, Cardinal?”
The Red Mansilently pondered for a while, then spoke in a stern, through gentle voice:
-“Do yourduty, and we’ll be more than that. We’ll both serve France, and by that, we’llshare the highest of purposes. Bring your ships to my shores every month ofevery year, Captain Basseterre, andgrow old peacefully among your unmarred lands.”
With that,he left, and a few moments later, Basseterre noticed the red silk gloves,forgotten next to the bandages on his bed.
He went andsailed for thirty years, making France richer by every spring that passed.
But none ofhis four crews, and none of his five wives could ever make him tell them why healways kept those tattered bits of red fabric, tightly knotted around his belt.
,
10 notes
·
View notes
Text
Right click publish quickly to Azure App Services with VS Code extensions and zipdeploy
I wanted to see what was the fastest way to get an ASP.NET Core web site up (for free) on Azure. First, I could use Visual Studio Community (which is free), and just right click Publish, sign into Azure, and make a free Web App and I'm cool. But I also wanted to see what it was like on Visual Studio Code (which would work on Linux, etc)
I downloaded these things. This is 10-15 min tops for download AND install. Likely less on a fast connection.
VS Code https://code.visualstudio.com
.NET Core https://dotnet.microsoft.com
Azure App Service extension for VS Code
C# extension for VS Code (NOTE: this will get automatically recommended to you anyway when you open a .cs file for the first time.
This also assumes you have a free Azure account https://azure.microsoft.com/free/
I made a new ASP.NET web site with "dotnet new razor" at the command line. The Azure App Service extension makes a new Azure icon appear on the left of VS Code. I can see my subscription(s) and any sites I've made before. I can right-click the top of the tree or just click the + plus sign.
TRICK: The default mode of the Azure App Service extension is "basic" mode. This is fine for messing around, but it will assume a bunch of things. You don't have control over the location (it'll pick a nearby one) or really anything. Again, it's fine. However, if you DO want explicit prompts for name, location, OS, runtime, etc you can turn on "appService.advanced" in File | Preferences | Settings (or Ctrl+,). Don't feel you need to, but know it's possible.
Now, in my opinion, deploying apps (.NET Core, Node, or otherwise) directly from source can be a little confusing, and it doesn't really scale for anything other than proofs of concept. There's usually a "build" step, and ideally you'll have a CI/CD (Continuous Integration/Continuous Deployment) pipeline for anything of any real size. It's easier than you think - you can likely get a basic DevOps pipeline up in a hour or so. I commit to GitHub and it just deploys to Azure.
That said, a quickie deploy has value so I wanted to do it. You can do a "git deploy" to Azure where Azure is a git remote and you just "git push azure master" but...you're pushing source and Azure "builds" it in Azure App Service using a thing called Kudu. That means it'll run npm install, dotnet restore, etc, it'll take some time. You could deploy a container to Azure and just push it to a Container Registry, then spin up the container.
However, Azure also has a little known but rather clever "zipdeploy" feature. Once you've configured your Azure App Service for zipdeployment as a source, you can just POST a new ZIP deployment with Curl!
curl -X POST -u <deployment_user> --data-binary @"<zip_file_path>" https://<app_name>.scm.azurewebsites.net/api/zipdeploy
You might find that weird, or you might find it elegant. If it's the latter, use it. If it's the former, don't. You can even do it with minimal or no downtime by deploying to a staging slot and use Auto Swap.
I'm going to use the Azure App Service extension in VS Code and it's going to hide all of this and it'll just publish in one click.
Here's the important part if you want it to just work and work easily. You'll want to deploy from a folder that represents your published app. That means your app in a state that it's ready to go.
With .NET Core, the easiest way is to dotnet publish. Then I'm right clicking on that publish folder as seen in this screenshot.
That will actually make a file .vscode/settings.json that will tell VS Code's Azure App Service extension what folder to deploy from in the future, thereby simplifying things.
{ "appService.defaultWebAppToDeploy": "/subscriptions/GUID/resourceGroups/appsvc_rg_Windows_CentralUS/providers/Microsoft.Web/sites/fancyweb1", "appService.deploySubpath": "bin\\Debug\\netcoreapp2.2\\publish" }
Below you can see the dialog that pops up "Always deploy the workspace ___ to ___" if you click Yes that will create the setting above specific to your application.
Now when I deploy, I can right click from anyway and it will zipdeploy right to my site. Note the log below.
With this extension I can even right click and "Start Streaming Logs" and get output of the logs of your Azure App Service as it runs, right in the output pane of VS Code.
This will make things pretty easy for my simplest sites and proofs of concept. Give it a try!
Sponsor: Get the latest JetBrains Rider for remote debugging via SSH, SQL injections, a new Search Everywhere popup, and improved Unity support.
© 2018 Scott Hanselman. All rights reserved.





0 notes
Text
10 Command Prompt Tricks That You Should Know
10 Command Prompt Tricks That You Should Know
Hello guys, With an interface as attractive as Windows 10’s is, it’s easy to forget that the OS comes with a command line interface as well. Well, you might have forgotten the Command Prompt. A lot of things that the Command Prompt (also known as cmd) can let you do, are not even available in the GUI (graphical user interface) of the Windows OS, so it’s definitely something you should be using.…
View On WordPress
#10 Command Prompt Tricks#Autocomplete#Change the Color of the CMD Window#Change the Prompt Text in Command Prompt#Change the Title of the Command Prompt Window#cmd#cmd tricks#Command Cycling and Command History#Copy Command Output to Clipboard#Create a WiFi Hotspot#Encrypt Files using Command Prompt#Hide Folders using Command Prompt#List all Installed Programs#Open CMD Window Inside a Directory
0 notes
Text
Windows 10 Tips and Tricks You Don’t Know About
If you are using Windows 10 or have updated it recently, then there are several tricks and tips and the hidden features that can be discovered to function a laptop and make use of it quickly. Microsoft does not expose its hidden features as Apple does and that makes it more difficult to discover and to get the idea of its features and get the most out of the device. If you want to get an idea about its features, then this post might be helpful. Read through the blog and follow the instructions to discover it.
Minimize the Windows Except for Active One
If the screen has been packed with the open windows, you can fastly minimize all of it, excluding the one you are using.
Tap on the title bar you need to continue open to choose it.
Hold mouse along and move the window back and forth fastly by shaking it. After some shakes, the other windows will minimize, leaving the one open that you have shaken.
Launch Secret Start Menu
Users know that all ready to go to the Start menu, you have to click on the Windows icon at the left of the screen. However, Windows 10 comprises the hidden second start menu, which is less known that helps in the important accessing feature like control panel, the command prompt, or Task manager easily. You may access it by clicking on Windows key + X or else right-click Windows tab or the Start option.
Make the Event Without Launching Calendar App
If you want to make the event without launching a calendar app, then you can follow the provided steps:
Tap on the box with date and time at the right on Taskbar.
Press on the date when you need to schedule the event.
Insert the event time, name, and location.
Hit the Save option. The vent must be visible in the Calendar app on the device.
Take the Screenshot
It is the basic one, but it is so simple to take the screenshot on the desktop or laptop. There are 8 ways to take the screenshot on Windows 10. If you want to take the screenshot of the whole screen then click on the Windows key + Print Screen key, then the image will be stored in the pictures and then tap on the screenshot folder to check it.
To screenshot half of the screen, click on Windows key + Shift + S to launch the tool, which is known as the Snip and sketch that permits to tap and drag to make the screenshot, which is stored in the clipboard.
Launch the Items on the Taskbar With the Shortcuts of Keyboard
If you have pinned programs on the taskbar underneath the screen to make a shortcut, then you do not have to tap on a tab to launch it. Click on the keyboard shortcut Windows key + < Number Key>, using the number key equivalent to a situation of a program on Taskbar.
Checking How Much Space Apps Are Consuming
If you want to check how much space apps are consuming, then you can follow the provided steps:
Go to the Settings.
Click on the System.
Tap on the Storage option.
Press on the drive that you need to locate.
Hit the Apps and games option to check the list of apps downloaded on the device and how much space they are consuming.
Free From the Ads on the Start Menu
Go through the offered steps to Free from the ads on the Start menu :
As you have Windows 10 with the default settings, sometimes it may be visible to you at the right of the Start menu.
Launch the Settings.
Click on Personalization.
Select the Start option.
Turn it off in setting known as Show suggestions in Start.
Close Background Apps
If you want to close the background apps, then abide by the given steps:
If you’re going to manage the background apps and save the battery as well as data, then this will help you.
Launch the settings.
Click on Privacy.
Select the Background apps option.
To close all the apps running at the back, turn the toggle off by clicking on the Let apps runs at the back option.
Apply the Background Scrolling
Follow the provided steps to apply the background scrolling:
Go to the Settings.
Click on the Devices.
Select the Mouse option.
Turn on the toggle by clicking on the Scroll inactive windows option.
After that, you can put the mouse on Window at the back then apply the scroll wheel to scroll.
Display File Extensions in the File Explorer
If you wish to display file extensions in the file explorer, then pursue the given instructions:
Open search box underneath the screen.
Insert the File Explorer option and then tap on it.
Press on the view tab when prompted in a window.
Untick the box that asks Hide extensions for recognized file types.
Tap on the Apply and then OK. Now the file extensions will be available in explorer.
Chop the Distractions Using Focus Assist
In case you intend to Chop the distractions using Focus assist, go through the below-mentioned steps:
Go to the Settings.
Click on System.
Select the Focus option.
Choose from the 3 options:
Priority
Off
Alarm.
Source:-https://miadavisdotblog.wordpress.com/2020/01/07/windows-10-tips-and-tricks-you-dont-know-about/
Mia Davis is a self-professed security expert; she has been making the people aware of the security threats. Her passion is to write about Cyber security, cryptography, malware, social engineering, internet, utility software and new media. She writes for McAfee products at mcafee.com/activate.
0 notes
Text
Original Post from McAfee Author: Alexandre Mundo
This new ransomware was discovered by Michael Gillespie on 8 February 2019 and it is still improving over time. This blog will explain the technical details and share information about how this new ransomware family is working. There are some variants of the Clop ransomware but in this report, we will focus on the main version and highlight part of those variations. The main goal of Clop is to encrypt all files in an enterprise and request a payment to receive a decryptor to decrypt all the affected files. To achieve this, we observed some new techniques being used by the author that we have not seen before. Clearly over the last few months we have seen more innovative techniques appearing in ransomware.
Clop Overview
The Clop ransomware is usually packed to hide its inner workings. The sample we analyzed was also signed with the following certificate in the first version (now revoked):
FIGURE 1. Packer signed to avoid av programs and mislead the user
Signing a malicious binary, in this case ransomware, may trick security solutions to trust the binary and let it pass. Although this initial certificate was revoked in a few days, another version appeared soon after with another certificate:
FIGURE 2. New certificate in new version
This sample was discovered by MalwareHunterTeam (https://twitter.com/malwrhunterteam) on the 26 February, 2019.
We discovered the following Clop ransomware samples which were signed with a certificate:
This malware is prepared to avoid running under certain conditions, for example in the first version it requests to be installed as a service; if that will not succeed, it will terminate itself.
The malware’s first action is to compare the keyboard of the victim computer using the function “GetKeyboardLayout” against the hardcoded values.
This function returns the user keyboard input layout at the moment the malware calls the function.
The malware checks that the layout is bigger than the value 0x0437 (Georgian), makes some calculations with the Russian language (0x0419) and with the Azerbaijan language (0x082C). This function will return 1 or 0, 1 if it belongs to Russia or another CIS country, or 0 in every other case.
FIGURE 3. Checking the keyboard layout
If the function returns 0, it will go to the normal flow of the malware, otherwise it will get the device context of the entire screen with the function “GetDC”. Another condition will come from the function “GetTextCharset” that returns the font used in the system if it does not have the value 0xCC (RUSSIAN_CHARSET). If it is the charset used, the malware will delete itself from the disk and terminate itself with “TerminateProcess” but if it is not this charset, it will continue in the normal flow This double check circumvents users with a multisystem language, i.e. they have the Russian language installed but not active in the machine to avoid this type of malware.
FIGURE 4. Check the text charset and compare with Russian charset
The code that is supposed to delete the ransomware from the disk contains an error. It will call directly to the prompt of the system without waiting for the malware to finish. This means that the execution of the command will be correct but, as the malware is still running, it will not delete it from the disk. This happens because the author did not use a “timeout” command.
FIGURE 5. Deletion of the malware itself
The next action of the malware is to create a new thread that will start all processes. With the handle of this thread, it will wait for an infinite amount of time to finish with the “WaitForSingleObject” function and later return to the winMain function and exit.
This thread’s first action is to create a file called “Favorite” in the same folder as the malware. Later, it will check the last error with “GetLastError” and, if the last error was 0, it will wait with the function “Sleep” for 5 seconds.
Later the thread will make a dummy call to the function “EraseTape” with a handle of 0, perhaps to disturb the emulators because the handle is put at 0 in a hardcoded opcode, and later a call to the function “DefineDosDeviceA” with an invalid name that returns another error. These operations will make a loop for 666000 times.
FIGURE 6. Loop to disturb the analysis
The next action is to search for some processes with these names:
SBAMTray.exe (Vipre antivirus product)
SBPIMSvc.exe (Sunbelt AntiMalware antivirus product)
SBAMSvc.exe (GFI AntiMalware antivirus product)
VipreAAPSvc.exe (Vipre antivirus product)
WRSA.exe (WebRoot antivirus product)
If some of these processes are discovered, the malware will wait 5 seconds using “Sleep” and later another 5 seconds. After those “sleep”, the malware will continue with their normal flow. If these processes are not detected, it will access to their own resources and extract it with the name “OFFNESTOP1”. That resource is encrypted but has inside a “.bat” file.
FIGURE 7. Access to the first resource crypted
The decryption is a simple XOR operation with bytes from this string:
“Po39NHfwik237690t34nkjhgbClopfdewquitr362DSRdqpnmbvzjkhgFD231ed76tgfvFAHGVSDqhjwgdyucvsbCdigr1326dvsaghjvehjGJHGHVdbas”.
The next action is to write this batch file in the same folder where the malware stays with the function “CreateFileA”. The file created has the name “clearsystems-11-11.bat”. Later will launch it with “ShellExecuteA”, wait for 5 seconds to finish and delete the file with the function “DeleteFileA”.
It is clear that the authors are not experienced programmers because they are using a .bat file for the next actions:
Delete the shadow volumes with vssadmin (“vssadmin Delete Shadows /all /quiet”).
Resize the shadow storage for all units starting from C to H units’ letters (hardcoded letters) to avoid the shadow volumes being made again.
Using bcedit program to disable the recovery options in the boot of the machine and set to ignore any failure in the boot warning the user.
All these actions could have been performed in the malware code itself, without the need of an external file that can be detected and removed.
FIGURE 8. The BAT file to disable the shadow volumes and more security
The next action is to create a mutex with the name hardcoded “Fany—Fany—6-6-6” and later make a call to the function “WaitForSingleObject” and check the result with 0. If the value is 0 it means that the mutex was created for this instance of the malware but if it gets another value, it means that the mutex was made from another instance or vaccine and, in this case, it will finish the execution of the malware.
After this, it will make 2 threads, one of them to search for processes and the another one to crypt files in the network shares that it has access to.
The first thread enumerates all processes of the system and creates the name of the process in upper case and calculates a hash with the name and compares it with a big list of hashes. This hash algorithm is a custom algorithm. It is typical in malware that tries to hide what processes they are looking for. If it finds one of them it will terminate it with “TerminateProcess” function after opening with the rights to make this action with “OpenProcess” function.
The malware contains 61 hard-coded hashes of programs such as “STEAM.EXE”, database programs, office programs and others.
Below, the first 38 hashes with the associated process names. These 38 processes are the most usual processes to close as we have observed with other ransomwares families such as GandCrab, Cerber, etc.
This thread runs in an infinite loop with a wait using the function “Sleep” per iteration of 30 minutes.
FIGURE 9. Thread to kill critical processes to unlock files
The second thread created has the task of enumerating all network shares and crypts files in them if the malware has access to them.
For executing this task, it uses the typical API functions of the module “MPR.DLL”:
WNetOpenEnumW
WNetEnumResourceW
WNetCloseEnum
This thread starts creating a reserve of memory with “GlobalAlloc” function to keep the information of the “MPR” functions.
For each network share that the malware discovers, it will prepare to enumerate more shares and crypt files.
For each folder discovered, it will enter it and search for more subfolders and files. The first step is to check the name of the folder/file found against a hardcoded list of hashes with the same algorithm used to detect the processes to close.
Below are the results of 12 of the 27 hashes with the correct names:
If it passes, it will check that the file is not a folder, and in this case compare the name with a list of hardcoded names and extensions that are in plain text rather than in hash format:
ClopReadMe.txt
ntldr
NTDLR
boot.ini
BOOT.INI
ntuser.ini
NTUSER.INI
AUTOEXEC.BAT
autoexec.bat
.Clop
NTDETECT.COM
ntdetect.com
.dll
.DLL
.exe
.EXE
.sys
.SYS
.ocx
.OCX
.LNK
.lnk
desktop.ini
autorun.inf
ntuser.dat
iconcache.db
bootsect.bak
ntuser.dat.log
thumbs.db
DESKTOP.INI
AUTORUN.INF
NTUSER.DAT
ICONCACHE.DB
BOOTSECT.BAK
NTUSER.DATA.LOG
THUMBS.DB
This check is done with a custom function that checks character per character against all the list. It is the reason for having the same names in both upper and lower case, instead of using the function “lstrcmpiA,” for example, to avoid some hook in this function preventing the file from being affected. The check of the extension at the same time is to make the process of crypto quicker. Of course, the malware checks that the file does not have the name of the ransom note and the extension that it will put in the crypted file. Those blacklisted extensions will help the system avoid crashing during the encryption compared with other ransomware families.
FIGURE 10. Check of file names and extensions
This behavior is normal in ransomware but the previous check against hardcoded hashes based on the file/folder name is weird because later, as we can see in the above picture, the next check is against plain text strings.
If it passes this check, the malware will make a new thread with a struct prepared with a hardcoded key block, the name of the file, and the path where the file exists. In this thread the first action is to remove the error mode with “SetErrorMode” to 1 to avoid an error dialog being shown to the user if it crashes. Later, it will prepare the path to the file from the struct passed as argument to the thread and change the attributes of the file to ARCHIVE with the function “SetFileAttributesW”, however the malware does not check if it can make this action with success or not.
Later it will generate a random AES key and crypt each byte of the file with this key, next it will put the mark “Clop^_” at the end of the file, after the mark it will put the key used to crypt the file ciphered with the master RSA key that has hardcoded the malware to protect it against third party free decryptors.
The malware can use 2 different public RSA keys: one exported using the crypto api in a public blob or using the embedded in base64 in the malware. The malware will only use the second one if it cannot create the crypto context or has some problem with the crypto api functions.
The malware does not have support for Windows XP in its use with the crypto functions, because the CSP used in Windows XP has another name, but if run in another operating system starting with Windows Vista, it can change the name in the debugger to acquire the context later and will generate a RSA public blob.
Another difference with other ransomware families is that Clop will only cipher the disk that is a physical attached/embedded disk (type 3, FIXED or removable (type 2)). The malware ignores the REMOTE type (4)).
Anyways, the shares can be affected using the “MPR.DLL” functions without any problem.
FIGURE 11. Filemark in the crypted file and key used ciphered
After encrypting, the file will try to open in the same folder the ransom note and, if it exists, it will continue without overwriting it to save time, but if the ransom note does not exist it will access one resource in the malware called “OFFNESTOP”. This resource is crypted with the same XOR operation as the first resource: the .bat file, after decrypting, will write the ransom note in the folder of the file.
FIGURE 12. Creation of the ransom note from a crypted resource
Here is a sample of the ransom note of the first version of this malware:
FIGURE 13. Example of ransom note of the first version of the malware
After this, Clop will continue with the next file with the same process however, the check of the name based with the hash is avoided now.
Second Version of the Malware
The second version found by the end of February has some changes if it is compared with the first one. The hash of this version is: “ed7db8c2256b2d5f36b3d9c349a6ed0b”.
The first change is some changes in the strings in plain text of the code to make the execution in the “EraseTape” call and “FindAtomW” call more slowly. Now the names are for the tape: “” and the atom “”.
The second change is the name of the resources crypted in the binary, the first resource that is a second batch file to delete the shadow volumes and remove the protections in the boot of the machine as the previous one has another name: “RC_HTML1”.
FIGURE 14. New resource name for the batch file
However, the algorithm to decrypt this resource is the same, except that they changed the big string that acts as a key for the bytes. Now the string is: “JLKHFVIjewhyur3ikjfldskfkl23j3iuhdnfklqhrjjio2ljkeosfjh7823763647823hrfuweg56t7r6t73824y78Clop”. It is important to remember that this string remains in plain text in the binary but, as it has changed, it cannot be used for a Yara rule. The same counts for the name of the resources and also for the hash of the resource because the bat changes per line in some cases and in another as it will have more code to stop services of products of security and databases.
The contents of the new BAT file are:
@echo off
vssadmin Delete Shadows /all /quiet
vssadmin resize shadowstorage /for=c: /on=c: /maxsize=401MB
vssadmin resize shadowstorage /for=c: /on=c: /maxsize=unbounded
vssadmin resize shadowstorage /for=d: /on=d: /maxsize=401MB
vssadmin resize shadowstorage /for=d: /on=d: /maxsize=unbounded
vssadmin resize shadowstorage /for=e: /on=e: /maxsize=401MB
vssadmin resize shadowstorage /for=e: /on=e: /maxsize=unbounded
vssadmin resize shadowstorage /for=f: /on=f: /maxsize=401MB
vssadmin resize shadowstorage /for=f: /on=f: /maxsize=unbounded
vssadmin resize shadowstorage /for=g: /on=g: /maxsize=401MB
vssadmin resize shadowstorage /for=g: /on=g: /maxsize=unbounded
vssadmin resize shadowstorage /for=h: /on=h: /maxsize=401MB
vssadmin resize shadowstorage /for=h: /on=h: /maxsize=unbounded
bcdedit /set {default} recoveryenabled No
bcdedit /set {default} bootstatuspolicy ignoreallfailures
vssadmin Delete Shadows /all /quiet
net stop SQLAgent$SYSTEM_BGC /y
net stop “Sophos Device Control Service” /y
net stop macmnsvc /y
net stop SQLAgent$ECWDB2 /y
net stop “Zoolz 2 Service” /y
net stop McTaskManager /y
net stop “Sophos AutoUpdate Service” /y
net stop “Sophos System Protection Service” /y
net stop EraserSvc11710 /y
net stop PDVFSService /y
net stop SQLAgent$PROFXENGAGEMENT /y
net stop SAVService /y
net stop MSSQLFDLauncher$TPSAMA /y
net stop EPSecurityService /y
net stop SQLAgent$SOPHOS /y
net stop “Symantec System Recovery” /y
net stop Antivirus /y
net stop SstpSvc /y
net stop MSOLAP$SQL_2008 /y
net stop TrueKeyServiceHelper /y
net stop sacsvr /y
net stop VeeamNFSSvc /y
net stop FA_Scheduler /y
net stop SAVAdminService /y
net stop EPUpdateService /y
net stop VeeamTransportSvc /y
net stop “Sophos Health Service” /y
net stop bedbg /y
net stop MSSQLSERVER /y
net stop KAVFS /y
net stop Smcinst /y
net stop MSSQLServerADHelper100 /y
net stop TmCCSF /y
net stop wbengine /y
net stop SQLWriter /y
net stop MSSQLFDLauncher$TPS /y
net stop SmcService /y
net stop ReportServer$TPSAMA /y
net stop swi_update /y
net stop AcrSch2Svc /y
net stop MSSQL$SYSTEM_BGC /y
net stop VeeamBrokerSvc /y
net stop MSSQLFDLauncher$PROFXENGAGEMENT /y
net stop VeeamDeploymentService /y
net stop SQLAgent$TPS /y
net stop DCAgent /y
net stop “Sophos Message Router” /y
net stop MSSQLFDLauncher$SBSMONITORING /y
net stop wbengine /y
net stop MySQL80 /y
net stop MSOLAP$SYSTEM_BGC /y
net stop ReportServer$TPS /y
net stop MSSQL$ECWDB2 /y
net stop SntpService /y
net stop SQLSERVERAGENT /y
net stop BackupExecManagementService /y
net stop SMTPSvc /y
net stop mfefire /y
net stop BackupExecRPCService /y
net stop MSSQL$VEEAMSQL2008R2 /y
net stop klnagent /y
net stop MSExchangeSA /y
net stop MSSQLServerADHelper /y
net stop SQLTELEMETRY /y
net stop “Sophos Clean Service” /y
net stop swi_update_64 /y
net stop “Sophos Web Control Service” /y
net stop EhttpSrv /y
net stop POP3Svc /y
net stop MSOLAP$TPSAMA /y
net stop McAfeeEngineService /y
net stop “Veeam Backup Catalog Data Service” /
net stop MSSQL$SBSMONITORING /y
net stop ReportServer$SYSTEM_BGC /y
net stop AcronisAgent /y
net stop KAVFSGT /y
net stop BackupExecDeviceMediaService /y
net stop MySQL57 /y
net stop McAfeeFrameworkMcAfeeFramework /y
net stop TrueKey /y
net stop VeeamMountSvc /y
net stop MsDtsServer110 /y
net stop SQLAgent$BKUPEXEC /y
net stop UI0Detect /y
net stop ReportServer /y
net stop SQLTELEMETRY$ECWDB2 /y
net stop MSSQLFDLauncher$SYSTEM_BGC /y
net stop MSSQL$BKUPEXEC /y
net stop SQLAgent$PRACTTICEBGC /y
net stop MSExchangeSRS /y
net stop SQLAgent$VEEAMSQL2008R2 /y
net stop McShield /y
net stop SepMasterService /y
net stop “Sophos MCS Client” /y
net stop VeeamCatalogSvc /y
net stop SQLAgent$SHAREPOINT /y
net stop NetMsmqActivator /y
net stop kavfsslp /y
net stop tmlisten /y
net stop ShMonitor /y
net stop MsDtsServer /y
net stop SQLAgent$SQL_2008 /y
net stop SDRSVC /y
net stop IISAdmin /y
net stop SQLAgent$PRACTTICEMGT /y
net stop BackupExecJobEngine /y
net stop SQLAgent$VEEAMSQL2008R2 /y
net stop BackupExecAgentBrowser /y
net stop VeeamHvIntegrationSvc /y
net stop masvc /y
net stop W3Svc /y
net stop “SQLsafe Backup Service” /y
net stop SQLAgent$CXDB /y
net stop SQLBrowser /y
net stop MSSQLFDLauncher$SQL_2008 /y
net stop VeeamBackupSvc /y
net stop “Sophos Safestore Service” /y
net stop svcGenericHost /y
net stop ntrtscan /y
net stop SQLAgent$VEEAMSQL2012 /y
net stop MSExchangeMGMT /y
net stop SamSs /y
net stop MSExchangeES /y
net stop MBAMService /y
net stop EsgShKernel /y
net stop ESHASRV /y
net stop MSSQL$TPSAMA /y
net stop SQLAgent$CITRIX_METAFRAME /y
net stop VeeamCloudSvc /y
net stop “Sophos File Scanner Service” /y
net stop “Sophos Agent” /y
net stop MBEndpointAgent /y
net stop swi_service /y
net stop MSSQL$PRACTICEMGT /y
net stop SQLAgent$TPSAMA /y
net stop McAfeeFramework /y
net stop “Enterprise Client Service” /y
net stop SQLAgent$SBSMONITORING /y
net stop MSSQL$VEEAMSQL2012 /y
net stop swi_filter /y
net stop SQLSafeOLRService /y
net stop BackupExecVSSProvider /y
net stop VeeamEnterpriseManagerSvc /y
net stop SQLAgent$SQLEXPRESS /y
net stop OracleClientCache80 /y
net stop MSSQL$PROFXENGAGEMENT /y
net stop IMAP4Svc /y
net stop ARSM /y
net stop MSExchangeIS /y
net stop AVP /y
net stop MSSQLFDLauncher /y
net stop MSExchangeMTA /y
net stop TrueKeyScheduler /y
net stop MSSQL$SOPHOS /y
net stop “SQL Backups” /y
net stop MSSQL$TPS /y
net stop mfemms /y
net stop MsDtsServer100 /y
net stop MSSQL$SHAREPOINT /y
net stop WRSVC /y
net stop mfevtp /y
net stop msftesql$PROD /y
net stop mozyprobackup /y
net stop MSSQL$SQL_2008 /y
net stop SNAC /y
net stop ReportServer$SQL_2008 /y
net stop BackupExecAgentAccelerator /y
net stop MSSQL$SQLEXPRESS /y
net stop MSSQL$PRACTTICEBGC /y
net stop VeeamRESTSvc /y
net stop sophossps /y
net stop ekrn /y
net stop MMS /y
net stop “Sophos MCS Agent” /y
net stop RESvc /y
net stop “Acronis VSS Provider” /y
net stop MSSQL$VEEAMSQL2008R2 /y
net stop MSSQLFDLauncher$SHAREPOINT /y
net stop “SQLsafe Filter Service” /y
net stop MSSQL$PROD /y
net stop SQLAgent$PROD /y
net stop MSOLAP$TPS /y
net stop VeeamDeploySvc /y
net stop MSSQLServerOLAPService /y
The next change is the mutex name. In this version it is “HappyLife^_-“, so, can it be complex to make a vaccine based on the mutex name because it can be changed easily in each new sample.
The next change is the hardcoded public key of the malware that is different to the previous version.
Another change is the file created; the first version creates the file with the name “Favourite” but this version creates this file with the name “Comone”.
However, the algorithm of crypto of the files and the mark in the file crypted is the same.
Another difference is in the ransom note that is now clearer with some changes in the text and now has 3 emails instead of one to contact the ransomware developers.
FIGURE 15.Example of the new ransom note
Other Samples of the Malware
Clop is a ransomware family that its authors or affiliates can change in a quick way to make it more complex to track the samples. The code largely remains the same but changing the strings can make it more difficult to detect and/or classify it correctly.
Now we will talk about the changes of some samples to see how prolific the ransomware Clop is.
Sample 0403db9fcb37bd8ceec0afd6c3754314 has a compile date of 12 February, 2019 and has the following changes if compared with other samples:
The file created has the name “you_offer.txt”.
The name of the device in the fake call to “EraseTape” and “DefineDosDeviceA” functions is “..1”.
An atom searched for nothing has the name of “$$$$”.
The mutex name is “MoneyP#666”.
The resources crypted with the ransom note and the bat file are called “SIXSIX1” for the batch file and the another one for the ransom note “SIXSIX”.
The name of the batch file is “clearsystems-10-1.bat”.
The key for the XOR operation to decrypt the ransom note and the batch file is:
“Clopfdwsjkjr23LKhuifdhwui73826ygGKUJFHGdwsieflkdsj324765tZPKQWLjwNVBFHewiuhryui32JKG”
The batch file is different to the other versions, in this case not changing the boot config of the target victim.
FIGURE 16. Another version of the batch file
The email addresses to contact are: [email protected] and [email protected] .
As a curiosity, this ransom note has a line that another does not have: “Every day of delay will cost you additional +0.5 BTC” (about 1500-1700 $).
The 3ea56f82b66b26dc66ee5382d2b6f05d sample has the following points of difference:
The name of the file created is “popup.txt”.
The DefineDosDeviceA name is “1234567890”
The mutex is “CLOP#666”.
The date of compiled this sample is 7 of February.
The name of the bat file is “resort0-0-0-1-1-0-bat”.
This sample does not have support for Windows XP because a API that does not exist in Windows XP.
The Atom string is “27”.
Sample 846f93fcb65c9e01d99b867fea384edc , has these differences:
The name of the file created is “HotGIrls”.
The DosDevice name is “GVSDFDS”.
Atom name: KLHJGWSEUiokgvs.
Batch file name “clearnetworksdns-11-22-33.bat”.
The ransom note does not have the previous string of increasing the price, but the maximum number of files that can be decrypted is 7 instead of 6..
As the reader can understand, Clop changes very quickly in strings and name of resources to make it more complex to detect the malware.
We also observed that the .BAT files were not present in earlier Clop ransomware versions.
Global Spread
Based on the versions of Clop we discovered we detected telemetry hits in the following countries:
Switzerland
Great Britain
Belgium
United States
The Netherlands
Croatia
Porto Rico
Germany
Turkey
Russia
Denmark
Mexico
Canada
Dominican Republic
Vaccine
The function to check a file or a folder name using the custom hash algorithm can be a problem for the malware execution due if one of them is found in execution, the malware will avoid it. If this happens with a folder, all the files inside that folder will be skipped as well.
As the algorithm and the hash is based on 32bits and only in upper case characters, it is very easy to create a collision as we know the target hashes and the algorithm
It cannot be used as vaccine on itself, but it can be useful to protect against the malware if the most critical files are inside of a collision folder name.
FIGURE 17. Collision of hashes
In the screenshot “BOOT” is a correct name for the hash, but the others are collisions.
This malware has a lot of changes per version that avoid making a normal vaccine using mutex, etc.
The Odd One in the Family
That not all ransomware is created equally, especially goes for Clop. Earlier in this blog we have highlighted some interesting choices the developers made when it came to detecting language settings, processes and the use of batch files to delete the shadow volume copies. We found in the analysis some unique functions compared with other ransomware families.
However, Clop does embrace some of the procedures we have seen with other ransomware families by not listing the ransom amount or mentioning a bitcoin address.
Victims must communicate via email instead of with a central command and control server hosting decryption keys. In the newer versions of Clop, victims are required to state their company name and site in the email communications. We are not absolutely sure why this is, but it might be an effort to improve victim tracking.
Looking at the Clop ransom note, it shares TTPs with other ransomware families; e.g. it mimics the Ryuk ransomware and contains similarities with BitPaymer, however the code and functions are quite different between them.
Coverage
Customers of McAfee gateway and endpoint products are protected against this version.
GenericRXHA-RK!3FE02FDD2439
GenericRXHA-RK!160FD326A825
Trojan-Ransom
Ransom-Clop!73FBFBB0FB34
Ransom-Clop!0403DB9FCB37
Ransom-Clop!227A9F493134
Ransom-Clop!A93B3DAA9460
GenericRXHA-RK!35792C550176
GenericRXHA-RK!738314AA6E07
RDN/Generic.dx
bub
BAT/Ransom-Clob
BAT/Ransom-Blob
McAfee ENS customers can create expert rules to prevent batch command execution by the ransomware. A few examples are given below for reference.
The following expert rule can be used to prevent the malware from deleting the shadow volumes with vssadmin (“vssadmin Delete Shadows /all /quiet”).
When the expert rule is applied at the endpoint, deletion of shadow volume fails with the following error message:
The malware also tries to stop McAfee services using command “net stop McShield /y”. The following expert rule can be used to prevent the malware from stopping McAfee Services:
When the expert rule is applied at the endpoint, the attempt to stop McAfee service using net command fails with the following error message:
Indicators of Compromise
The samples use the following MITRE ATT&CK techniques:
Execution through API (Batch file for example).
Application processes discovery with some procedures as the hashes of the name, and directly for the name of the process.
File and directory discovery: to search files to encrypt.
Encrypt files.
Process discovery: enumerating all processes on the endpoint to kill some special ones.
Create files.
Create mutants.
Conclusion
Clop ransomware shows some characteristics that enterprises are its intended targets instead of end consumers. The authors displayed some creative technical solutions, to detect the victim’s language settings and installed programs. On the other hand, we also noticed some weird decisions when it came to coding certain functionalities in the ransomware. Unfortunately, it is not the first time that criminals will make money with badly programmed malware.
Clop is constantly evolving and even though we do not know what new changes will be implemented in the future, McAfee ATR will keep a close watch.
IOCs
bc59ff12f71e9c8234c5e335d48f308207f6accfad3e953f447e7de1504e57af
31829479fa5b094ca3cfd0222e61295fff4821b778e5a7bd228b0c31f8a3cc44
35b0b54d13f50571239732421818c682fbe83075a4a961b20a7570610348aecc
e48900dc697582db4655569bb844602ced3ad2b10b507223912048f1f3039ac6
00e815ade8f3ad89a7726da8edd168df13f96ccb6c3daaf995aa9428bfb9ecf1
2f29950640d024779134334cad79e2013871afa08c7be94356694db12ee437e2
c150954e5fdfc100fbb74258cad6ef2595c239c105ff216b1d9a759c0104be04
408af0af7419f67d396f754f01d4757ea89355ad19f71942f8d44c0d5515eec8
0d19f60423cb2128555e831dc340152f9588c99f3e47d64f0bb4206a6213d579
7ada1228c791de703e2a51b1498bc955f14433f65d33342753fdb81bb35e5886
8e1bbe4cedeb7c334fe780ab3fb589fe30ed976153618ac3402a5edff1b17d64
d0cde86d47219e9c56b717f55dcdb01b0566344c13aa671613598cab427345b9
cff818453138dcd8238f87b33a84e1bc1d560dea80c8d2412e1eb3f7242b27da
929b7bf174638ff8cb158f4e00bc41ed69f1d2afd41ea3c9ee3b0c7dacdfa238
102010727c6fbcd9da02d04ede1a8521ba2355d32da849226e96ef052c080b56
7e91ff12d3f26982473c38a3ae99bfaf0b2966e85046ebed09709b6af797ef66
e19d8919f4cb6c1ef8c7f3929d41e8a1a780132cb10f8b80698c8498028d16eb
3ee9b22827cb259f3d69ab974c632cefde71c61b4a9505cec06823076a2f898e
The post Clop Ransomware appeared first on McAfee Blogs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Alexandre Mundo Clop Ransomware Original Post from McAfee Author: Alexandre Mundo This new ransomware was discovered by Michael Gillespie on 8 February 2019 and it is still improving over time.
0 notes
Link
Windows 10 is perhaps the last operating system from Microsoft. The new operating system is being offered as a free upgrade to Windows 8.1 and Windows 7 users, for the first year, and will be supported for ten years by Microsoft. The new operating system has a lot to offer including some great new features. Let us check out some Windows 10 tips and tricks that will help you get the best out of it.
Windows 10 tips and tricks
1] Make Windows 10 behave the way you want it to
Besides Control Panel, Windows 10 has an easy to use PC Settings window where you can easily change and control the settings related to Windows Updates, Networks, Apps, etc. Manage your System, change Network and Internet Settings, change Windows 10 Privacy settings, manage your Devices, Personalize your PC, manage your User Accounts, set your Time & language, use tools for the differently abled and manage Windows Update and Security here. To know what all changes you can make from PC Settings window, read How to open and use Windows 10 Settings app.
2] Open individual settings using Desktop shortcuts
You can create Desktop shortcuts or Context Menu items to open various Settings in Windows 10. See the URI for Settings apps that open the particular Settings page directly.
3] Edge browser tips and tricks
There is much to Microsoft Edge than what appears. At the core of Edge is the EDGEHTML rendering engine that was developed from scratch to provide a better browser. These Edge browser tips and tricks will make you an Edge ninja!
4] Using Internet Explorer in Windows 10
The default browser in Windows 10 is the all-new Edge. Windows 10 also contains Internet Explorer for legacy purposes which I think will be continued to be used for a considerable time to come. This tip will show you how to open Internet Explorer in Windows 10.
5] Using Cortana in Windows 10
Windows 10 features Cortana, a personal assistant that goes as far to provide you with local information and replace typing in Windows 10 taskbar search box with voice. To give you an idea of how it works, it is like Apple’s Siri. Check out how to set up Cortana in Windows 10 to start using it. If you do not use it, you can disable Cortana. Know how to use Cortana in Edge? There are many Cortana Tips and Tricks here.
6] Make File Explorer open to This PC instead of Quick Access
Windows 10 users may have noticed that by default, File Explorer opens to Quick Access. Make Explorer open his PC folder. If you don’t use it, you may disable Quick Access. More Windows 10 File Explorer Tips & Tricks here.
7] Booting in Safe Mode
This post will show you how to enable and start or boot Windows 10 in Safe Mode. There may be other ways, but we will cover only 2 of the most convenient ways.
8] Change the look of Windows 10 Start Menu
The Start menu in Windows 10 is divided into two parts: one contains apps and settings, the other part towards the right allows displays live tiles and allows you to pin apps in groups. Check out how to customize Start Menu in Windows 10 to be able to customize Start menu according to your interest and ease of usage.
9] Make Start more private
The major components of Start Menu in Windows 10 are Most Used List, Recent Programs List, PC Settings, Power Options, and Apps Sub-menu. Show or Hide Recently added apps group. Remove Most Used list from the Start Menu in Windows 10.
10] Enable Start Screen or Full-screen Start
Miss the Start Screen? You can enable Start Screen by enabling the Tablet Mode. If wish to enable Start Screen without enabling the Tablet Mode, then the best option for you would be to enable full-screen Start.
11] Add Blur to Start Menu background
Don’t like Transparency? Remove it and enable Blur in Start Menu background.
12] Make your Start Menu and Taskbar colorful
See how you can show or change the colors of your Start Menu and Taskbar. Don’t like the default taskbar colors? Add a new custom color for Windows 10 taskbar. More tips here on how to customize Windows 10 taskbar.
13] Change Taskbar Search default search provider
The Taskbar Search textbox allows you to easily search your device as well as the web. The default service provider when you install Windows 10 is Bing. But if you wish to change it to Google, you can do so easily. Read Set Google as Default Search in Windows 10 taskbar search.
14] Record screen using Xbox app
The new built-in Windows 10 Xbox app also includes a screen recording feature that lets you record the screen of the active window, as well. To use it, start the Xbox app, click Win+G to open the Game bar and select Screenshot or Start Recording.
15] Change Theme, Wallpaper, Lock Screen
One of the first things to check out after upgrading to Windows is how to personalize it according to your taste. Read Personalization settings in Windows 10 to know what all settings you can change. You can also set up personal lock screen, wallpaper and control themes in Windows 10. To know more on the topic, please read Change Theme, Lock Screen & Wallpaper in Windows 10.
16] Use Dark Themes
Enable the Windows 10 Dark Theme or use the Dark Theme in Edge – really easy on the eyes!
17] Prevent Windows 10 Themes from changing desktop Icons
Desktop icons help you locate and run a program. Different people like different looks of the desktop icons. The traditional icons are appreciated more. But there are chances that if you install a theme, it will change the desktop icon images too. You can prevent that using the PC Settings option. Check out Allow or Prevent themes from changing Desktop icons in Windows.
18] Customize Screensaver
Still use a screensaver? These tips will help you customize Screensaver in Windows 10.
19] Install or move Windows 10 Apps to another Drive
Running out of disk space on your system drive? Get smart change the install location & move Windows 10 Apps to another drive.
20] Change default programs
Don’t like the default browser? This post will show you how to change default programs. Change and use your favorite the media player, browser, etc, to op.en file types.
21] Change default Credential Provider
Windows 10 comes with multiple sign-in options available. This is possible due to the presence of various Credential Providers. This registry hack will let you change your default Credential Provider in Windows 10.
22] Using Virtual Desktop Feature
With Windows 10, you can create many desktops and run applications from each individually, so that each desktop shows only the applications running in that virtual desktop and thereby reduce the clutter in the taskbar. See how you can use the Task View or Virtual Desktop feature. If you don’t use this feature, you can remove the Task View button easily.
23] Using Windows Hello
Windows Hello is a new feature in Windows 10 that is meant to increase the security of the system you are using. It uses fingerprints and Iris scan to let you log in. But not all computers will be able to use the feature as it needs special hardware. Check out the list of PCs that support Windows Hello.
24] Use Snap Assist or disable it if you don’t
The Snap feature was introduced in an earlier version of Windows. It has now been improved in Windows 10, and called Snap Assist. Use it or disable it if you wish.
25] A new CMD tip
Microsoft has added CTRL+C and CTRL+V keyboard shortcuts that let you copy and paste content respectively.
26] Use these Media Center alternatives
So what if Windows 10 removed Windows Media Center… you can use these Media center alternatives.
27] Windows quick tips
There are always those classic Windows tips and trick that can help you get the best out of your Windows PC:
Hold down Shift key as you drag a folder or file to the Recycle Bin to delete it instantly
Hold down Alt & click on file or folder to open its Properties box
Press F5 to add the date and time to a Notepad
To open an elevated Command Prompt window from the Desktop, press Win+X and A at the same time
To quickly create a shortcut, hold down Ctrl+Shift and then drag and drop the file or folder icon in the desired destination folder
Open an extended context menu, by just pressing and holding down SHIFT Key while you right-click your mouse button
Press Ctrl+Shift and then right-click on the Taskbar. You will then see the option to Exit Explorer.
See all these and more such quick tips to a faster way of working with Windows.
28] Turn off Notification sounds
Notification sounds can be annoying – especially if you are playing games, watching videos, or listening to music. But you can always turn them on and off. To know how to do that, read Turn Off Notification and System Sounds in Windows 10.
29] Download maps for offline use
Travel around a lot? Download and use maps when you do not have an Internet connection. The Maps app lets you do so.
30] A new way to change Screen Resolution
Windows 10 lets you change the Screen Resolution in a smarter way.
31] Tricks to use the new Windows 10 Calculator
The new Windows 10 Calculator includes some new features. These tips will help you use it to its fullest potential.
32] Make Windows 10 battery last longer
Use the new Battery Saver mode and make your laptop battery last longer.
33] Work faster with these new keyboard shortcuts
Keyboard junkies, you definitely want to check out these new keyboard shortcuts in Windows 10.
34] Using the new Mail app
See how to create multiple email accounts, add multiple Live Tiles for multiple Email Accounts and more in the new Windows 10 Mail app. These Windows 10 Mail app Tips & Tricks will help you get the best out of it.
35] Sign in securely using PIN
Use a Password, PIN or Picture to sign in to your Windows 10. In addition to traditional password-based login, Windows 10 also includes PIN and Picture Password logon for the safety and security of users.
36] Set time delays in Snipping Tool
While the Snipping Tool lets you capture screenshots, you can now also set time delays for capturing screenshots using the Snipping Tool.
37] Make Windows 10 Forget Wireless Network Profiles
Maybe the list has become big, or maybe you want to preserve your privacy …whatever the reason … this post will see how you can remove, delete or forget Wireless Network Profiles.
38] Use, or not use Wi-Fi Sense … that is the question!
Windows 10 will now allow you to purchase paid Wi-Fi via the Windows Store using the Microsoft Wi-Fi app. The OS also introduces Wi-Fi Sense. But should you be using it?
39] Using non-Microsoft Store apps
Enable Developer Mode and SideLoad apps, to use your favorite apps which are available outside the Windows Store.
40] Create a folder without any icon or name
Be cool! Create a folder without any icon or name! Will work on all Windows.
41] Recycle Bin Tricks and Tips
There is a lot you can do with the humble and neglected Recycle Bin in Windows, using these Recycle Bin Tricks and Tips.
42] Notepad Tricks
The humble Notepad in Windows actually offers a lot more than the eye can see. These Notepad Tips and Tricks will work on all recent Windows versions and help you get the maximum out of it. Change the font, add a date, customize the page setup, etc.
43] Magnifier tricks
See the real colors on a negative image using the built-in Magnifier. There’s more at this Windows Magnifier Tips and Tricks post.
44] Mouse tricks
Don’t just use the mouse to click open a program or document, open the context menu and to select and drag-and-drop files or folders. There are many other useful Mouse Tricks you want to know as a Windows user.
45] Move Clock & Date to old position
After installing the Anniversary Update on your Windows 10, you will notice that the Clock & Date which used to be located at the extreme right end of the taskbar, has been shifted to the left and in its place, you now see the Action Center icon. You can now move Windows 10 Taskbar clock & date back to its old position.
46] Block Windows Updates
There is no option to turn off Windows Updates in Windows 10. But you could disable Windows Update. But you don’t want to do that if your objective is to block only unwanted updates. Use this tool to block unwanted Windows Updates, from Microsoft instead.
47] Rollback to your previous versions
If you upgraded to Windows 10 and are facing problems, you need not worry. You can rollback from Windows 10 to your previous version of Windows within a month of installing Windows 10.
48] Have problems? Use the Contact Support app
Microsoft has made it easier for you to contact Support if you face any problems while using Windows 10. See how to use the Contact Support app.
49] Improve Windows 10 wallpaper quality
You can disable Windows 10 Wallpaper compression & improve the background image quality by using this trick.
50] Microsoft Paint tips
Enjoy using Paint? These Microsoft Paint tips & tricks will help you become a Pro.
51] Clipboard Manager Tips and Tricks
Take a look at these Windows Clipboard Manager Tips and Tricks.
52] Microsoft Windows Tips app
Want more? Use the built-in Windows Tips app.
Watch this video from Microsoft.
0 notes
Link
10 command prompt tricks 10 cool command prompt tricks command prompt tricks you should know Hello friends my name is nair neeraj and once again welcome back to my channel today i am going to tell you guys some cool command prompt tricks. 1.How to encrypt and decrypt files. a)How to encrypt files? open the command prompt type the name of the disk (enter) cd (name of the folder you want to encrypt):(enter) cipher /e(enter) 10 command prompt tricks 10 cool command prompt tricks command prompt tricks you should know Hello friends my name is nair neeraj and once again welcome back to my channel today i am going to tell you guys some cool command prompt tricks. 1.How to encrypt and decrypt files. b)How to decrypt files? open the command prompt type the name of the disk (enter) cd (name of the folder you want to decrypt):(enter) cipher /d(enter) 2.How to hide and unhide folders? a)how to hide folders open command prompt (Type the letter of the drive)(enter) attrib +h +s +r (name of the folderyou want to hide)(enter) b)how to unhide folders open command prompt (Type the letter of the drive)(enter) attrib -h -s -r (name of the folderyou want to unhide)(enter) 3)The list of color help color 4)help prompt 5)To know all the products installed on the computer? wmic product get name 6)To copy text from cmd (type any command ) |clip 7)tasklist 8)systeminfo 9)To open a new command prompt start 10)To watch star wars in ascii mode enable telnet in yout computer telnet towel.blinkenlights.nl
0 notes