#data security for banks
Text
What do Banks do to Secure Their Data?
Banking is the only sector that contains every individual's financial and personal data. As digitization in the banking sector has taken a leap, there are many things added to help banks automate workflow. However, many things to worry about, like protecting sensitive information and establishing security measures to prevent cybercriminal attacks through phishing and malware.

Due to digitization in almost all industries and organizations, banks have had to modify their systems to meet these developments and transform their operations to ensure the continuous security of new banking technologies.
The rules governing banking are continually changing to meet the demands put forward by current banking systems. For example, banks are required to safeguard client data and guard against hacker attacks and illegal access by law.
Let Us See How Banks And Financial Services Providers Uphold Security Responsibility!
Infrastructure Security
Securing the infrastructure refers to securing the data center where the business-critical data of the banks is stored. It can be an on-premise data center, infrastructure co-located at the service provider's space, or a bank's data hosted on the service provider's data center.

Many cloud service providers like ESDS offers compliant infrastructure suitable for the security requirements of banks.
Employees of banks typically receive specialized devices that block access to USB ports, social media websites, and personal email accounts. In addition, employees can only connect to the banks' network through a VPN.
Testing and Monitoring of Data Security Controls
A bank tests and monitors all data security controls regularly. It updates the program to reflect changes in its operations and systems, rectifying or modifying the program to reflect detected issues. In addition, the bank periodically evaluates and assesses the risks to identify and handle changes in the threats or hazards to its customer information.
Customer Authentication
As online banking has changed the way banks work, every bank transaction done by a customer online or offline is authenticated to establish the identity of the person initiating the transaction. Customers using ATMs and POS terminals, those using credit/debit cards at POS terminals, those using online or mobile banking, and those visiting the bank in person must go through the authentication process. In addition, employees of banks who have access to consumer and bank data have to follow the same protocol.
Many banks have now introduced two-factor and multi-factor authentication to guarantee that the person is indeed who they claim to be. In addition, when clients engage with banking systems like IVR (Interactive voice response), banks use behavioral biometrics, such as biometric authentication, to confirm the customers' identities. Some of the best cloud service providers, like ESDS, offer the most reliable AI-enabled chatbots, ATMs, Kiosks, and POS services as the banks require.
Regular Communication

With the periodic account statements that are prepared and given to customers, banks also regularly communicate with customers regarding system changes, the introduction of new authentication methods, etc. Furthermore, customers can establish alerts and limits based on various criteria to ensure they are notified of any unforeseen action about their accounts. There are many communication options, but the setup can be adapted to suit the users' convenience.
Traces of audits
A statement or passbook containing a history of transactions was always accessible. Additionally, banking systems record every action a customer takes when interacting with the systems in an audit trail. The time of the conversation is recorded together with the specifics of the interaction, regardless of whether the consumer uses phone or internet banking. Daily backups are made of this data, which is never wholly deleted but rather archived at predetermined intervals.
Wrapping up
Cybercrimes like invasion and phishing are still very prevalent. Beyond the legislative requirements, a bank's reputation, ability to offer products and services to its customers, and capability to prevent customer data from being subject to fraud depend on its ability to keep ahead of the hackers.
#What do Banks do to Secure Their Data#cybercriminal attacks#data security for banks#Banking & Financial Data Security#Cyber Security in Banking Sector
1 note
·
View note
Text
So I know a lot of you have seen Ms.demeanor’s post about passwords and how you should have a password manager. And you 100% should. But let’s say you can’t have one for some reason, or you’re trying to help someone who can’t have one. I have developed hmmm a method that allows you to use fewer passwords while also keeping everything safe.
Sorting
So you need to sort all your apps, accounts, etc into at least 3 different categories based on how screwed you'd be if a hacker got into that account.
Level 1
These are low threat level accounts and generally accounts where you were forced to make an account for a one time thing. Like for example you wanted to download a knitting pattern but they forced you to make an account. These accounts do not matter. If a hacker gets in it should have the same impact as someone picking up a penny found on the ground near your house. You could put streaming sites in this category if you wish. Maybe also your wifi password.
Level 2
These accounts are ones that you use often but that won't ruin you financially if someone gets into them. This should contain stuff like social media, maybe streaming, and maybe your phone bill if you're feeling spicy. It is very important that social media passwords be different from the highest level of security passwords. Social media passwords are more likely to be shared with people or could be stolen like the fb data scrape from years ago.
This is also where you'd probably include anything school related if you're still in school: blackboard, quizlet, grade book, etc. Or work related: email, slack, etc. You could also make a separate level just for school/work related accounts.
Level 3
This is the oh-i'm-absolutely-fucked level if someone got into your account. This is like if someone found the code for a safe in your bedroom. This is anything that contains sensitive info: medical, SSN, etc. Or deals with money. This is the level for bank accounts, taxes, government websites, paypal/cashapp, loans, etc.
I go back and forth about whether or not I would include email in this level. Especially if you're using gmail which is just sooooo great at not stealing your data. But in the end, with access to your email account, someone can reset passwords on all your shit (which is why you should have multiple emails as well).
Creating Passwords
Now you need to create a password for each level, which you can do using an anchor point. Luckily for you, you are on the shipping-AU-fandom website so it'll be easier. I'm gonna use supernatural as an anchor point. You can of course use different fandoms/ships for each level (I recommend this)
Level 1
This should be a simple easy to type, easy to remember password. It should contain at least numbers and letters with maybe an exclamation mark. This can contain words from the dictionary. Since this is a basic password, use something you think is basic and then the year it was invented or the year you really noticed it. It should be two words so you can get at least two capital letters.
For example, I think spn fans are pretty basic (i'm allowed to say this, I used to be one) and I think they started becoming A Thing in 2012 so for this level the password would be SPNGirlie2012
Level 2
This is where we get more tricky and want to add in words that aren't in the dictionary. We want to include numbers AND symbols.
Let's go with the beloathed ship of this website - Destiel - which is not a word in the dictionary. And then an AU you have seen that then stuck in your brain. Then the year you saw it or got into it or it was created.
For example, the idea of destiel being news anchors saying the news in the i love you meme is hilarious to me. So we have Anchor!Destiel2023 but that's still a bit too comprehensible soooo Anch0r!De$tiel and changing the number to a different year than the current one so 08 to represent when that angel first arrived and later doomed this website to being incomprehensible :)
Level 3
This should not contain recognizable words. If someone reads it they should be SO confused. This is where you use very niche AUs that get their own names. You use quotes that crushed you or lyrics from that one AMV that is stuck in your head at the moment. Very important, it should make people cry if they were told to type it in on a tv screen with a remote.
If you go the AU route it should be something like oh Sam was being too bitchy so he got cursed into a cabbage and has to learn how to become nice so it's called the Cabitch AU. Then we spice it up with some numbers and symbols. (@B1tch!$am!@U5 (CaBitch!Sam!AU5) and a number at the end maybe signifying how many of you even know about this au in the first place.
Or you can go the quote/lyrics route. Which follows recommendation of another tumblr post (also ms.demeanor?) Let's use the infamous destiel meeting quote "I'm the one who gripped you tight and raised you from perdition."
so you take the first letter of each word = ITOWGYTARYFP
make 'the' 'and' 'from' lowercase = ItOWGYTaRYfP
substitute letters = |t0WGY7aRYfP
Add in a significant number (page, episode, timestamp, etc) = |t0WGY7aRYfP_4.01
And tada you have a password that saw would use in a saw trap with an apple tv remote.
And there you have it, how to sort and make your account passwords safe in technically 6 easy steps. I know there are a lot of you who use the same password for everything or bemoan your difficulties with remembering passwords. But like data protection is SO important, y'all don't realize just how much can be dug up with the simplest of information. I leave you with this horror story that made me make this post.
So my friend was getting harassed over text message by an unknown number. She thought it was her shitty ex bf so she decided to do some digging. First she went on her fb to see if he had his phone number public, but because she blocked him she couldn't see it. But you see dear reader, he gave her his fb password while they were dating. Friends, they broke up over FIVE YEARS AGO. For shits and giggles she tried to log in and WHOOPS IT WORKED! She couldn't find his phone number and that was going to be the end of it, but she got more texts for yet another number so she investigated more.
She was able to log into his email attached to his FB, where she was able to you know, actually read his emails. Turns out one of his doctors was NOT practicing proper patient confidentiality because he wrote an email with the guy's MENTAL ILLNESS DIAGNOSIS! Which my friend was able to see! She also found his SOCIAL SECURITY NUMBER!
If you aren't American, that means she could take out a loan in his name no questions asked. She could have ruined his credit score. Oh what's that? That's right! He used the same email and password for his BANK ACCOUNT! and turns out his credit was already bad. She could have transferred all his MONEY to her!!!! She dated him for a while, if there were security questions, she probably would have known them.
So because this guy gave an 18 year old his fb password, 7 years ago, his ex (who hates him btw) found out his SSN, his diagnoses, his phone number, AND his bank account info. Thankfully she's not a shitty person and doesn't hate him enough to ruin his life 5 years after they broke up, but like she could have! She could have left his life in ruins!!!!!!!
Which is why I made this post.
don't use the same password for everything
FOR THE LOVE OF GOD DO NOT KEEP THE SAME PASSWORDS AFTER YOU HAVE A MESSY BREAK UP?!?!??!?!?!?!
The end, hope this helps, change your passwords.
#passwords#data protection#password security#what not to do after a messy break up#what TO do to protect yourself online#internet safety#why your tumblr password should not be the same as your bank password#unfortunately schools today do NOT teach internet safety and if they do they do a truly awful job of it#also you should switch things up from what I wrote#i tried to show the different areas of flexibility#It is so important that you treat passwords like a key to a locked door#if you have a bad break up change your fucking locks#I will admit I haven't historically used the best passwords cuz again you don't get taught this#Oh i also recommend changing your passwords after each like big change? Like if you finish with school or a job#it's just an easy way to schedule maintenance on your passwords and purge old accounts#same with changing emails!#mine
6 notes
·
View notes
Text
mycelium and AI are lovers
#they just are like somehow they connect but idk how#me n *** were considering growing a batch to connect to connect to a computer and then building an interpreter AI to translate signals#not translating signals from a mycelial network (impossible as of ...rn) but from like . smth else .#like using the network as a way to transfer data . he was thinking of finding a way to connect them to human nerves#hes a neurobiologist so . idk he said some stuff that i understood maybe 40% of . but he also said#it would be outrageously expensive even if it were possible :(#bro i was looking into buying a culture and theyre like 100 quid which now i do not have the money for but back then i did BUT#its like . from the uk health security website thing and u need this special bank acct to be able to buy them in the first place#ugh whatever#theyre just connected somehow#mycelial networks and artificial neural networks share smth transferrable in common#@mycologists help me out bro#also what constitutes a mycelial network ? at what point are they an actual network of mycelium ?
10 notes
·
View notes
Text
If anyone wants to know why every tech company in the world right now is clamoring for AI like drowned rats scrabbling to board a ship, I decided to make a post to explain what's happening.
(Disclaimer to start: I'm a software engineer who's been employed full time since 2018. I am not a historian nor an overconfident Youtube essayist, so this post is my working knowledge of what I see around me and the logical bridges between pieces.)
Okay anyway. The explanation starts further back than what's going on now. I'm gonna start with the year 2000. The Dot Com Bubble just spectacularly burst. The model of "we get the users first, we learn how to profit off them later" went out in a no-money-having bang (remember this, it will be relevant later). A lot of money was lost. A lot of people ended up out of a job. A lot of startup companies went under. Investors left with a sour taste in their mouth and, in general, investment in the internet stayed pretty cooled for that decade. This was, in my opinion, very good for the internet as it was an era not suffocating under the grip of mega-corporation oligarchs and was, instead, filled with Club Penguin and I Can Haz Cheezburger websites.
Then around the 2010-2012 years, a few things happened. Interest rates got low, and then lower. Facebook got huge. The iPhone took off. And suddenly there was a huge new potential market of internet users and phone-havers, and the cheap money was available to start backing new tech startup companies trying to hop on this opportunity. Companies like Uber, Netflix, and Amazon either started in this time, or hit their ramp-up in these years by shifting focus to the internet and apps.
Now, every start-up tech company dreaming of being the next big thing has one thing in common: they need to start off by getting themselves massively in debt. Because before you can turn a profit you need to first spend money on employees and spend money on equipment and spend money on data centers and spend money on advertising and spend money on scale and and and
But also, everyone wants to be on the ship for The Next Big Thing that takes off to the moon.
So there is a mutual interest between new tech companies, and venture capitalists who are willing to invest $$$ into said new tech companies. Because if the venture capitalists can identify a prize pig and get in early, that money could come back to them 100-fold or 1,000-fold. In fact it hardly matters if they invest in 10 or 20 total bust projects along the way to find that unicorn.
But also, becoming profitable takes time. And that might mean being in debt for a long long time before that rocket ship takes off to make everyone onboard a gazzilionaire.
But luckily, for tech startup bros and venture capitalists, being in debt in the 2010's was cheap, and it only got cheaper between 2010 and 2020. If people could secure loans for ~3% or 4% annual interest, well then a $100,000 loan only really costs $3,000 of interest a year to keep afloat. And if inflation is higher than that or at least similar, you're still beating the system.
So from 2010 through early 2022, times were good for tech companies. Startups could take off with massive growth, showing massive potential for something, and venture capitalists would throw infinite money at them in the hopes of pegging just one winner who will take off. And supporting the struggling investments or the long-haulers remained pretty cheap to keep funding.
You hear constantly about "Such and such app has 10-bazillion users gained over the last 10 years and has never once been profitable", yet the thing keeps chugging along because the investors backing it aren't stressed about the immediate future, and are still banking on that "eventually" when it learns how to really monetize its users and turn that profit.
The pandemic in 2020 took a magnifying-glass-in-the-sun effect to this, as EVERYTHING was forcibly turned online which pumped a ton of money and workers into tech investment. Simultaneously, money got really REALLY cheap, bottoming out with historic lows for interest rates.
Then the tide changed with the massive inflation that struck late 2021. Because this all-gas no-brakes state of things was also contributing to off-the-rails inflation (along with your standard-fare greedflation and price gouging, given the extremely convenient excuses of pandemic hardships and supply chain issues). The federal reserve whipped out interest rate hikes to try to curb this huge inflation, which is like a fire extinguisher dousing and suffocating your really-cool, actively-on-fire party where everyone else is burning but you're in the pool. And then they did this more, and then more. And the financial climate followed suit. And suddenly money was not cheap anymore, and new loans became expensive, because loans that used to compound at 2% a year are now compounding at 7 or 8% which, in the language of compounding, is a HUGE difference. A $100,000 loan at a 2% interest rate, if not repaid a single cent in 10 years, accrues to $121,899. A $100,000 loan at an 8% interest rate, if not repaid a single cent in 10 years, more than doubles to $215,892.
Now it is scary and risky to throw money at "could eventually be profitable" tech companies. Now investors are watching companies burn through their current funding and, when the companies come back asking for more, investors are tightening their coin purses instead. The bill is coming due. The free money is drying up and companies are under compounding pressure to produce a profit for their waiting investors who are now done waiting.
You get enshittification. You get quality going down and price going up. You get "now that you're a captive audience here, we're forcing ads or we're forcing subscriptions on you." Don't get me wrong, the plan was ALWAYS to monetize the users. It's just that it's come earlier than expected, with way more feet-to-the-fire than these companies were expecting. ESPECIALLY with Wall Street as the other factor in funding (public) companies, where Wall Street exhibits roughly the same temperament as a baby screaming crying upset that it's soiled its own diaper (maybe that's too mean a comparison to babies), and now companies are being put through the wringer for anything LESS than infinite growth that Wall Street demands of them.
Internal to the tech industry, you get MASSIVE wide-spread layoffs. You get an industry that used to be easy to land multiple job offers shriveling up and leaving recent graduates in a desperately awful situation where no company is hiring and the market is flooded with laid-off workers trying to get back on their feet.
Because those coin-purse-clutching investors DO love virtue-signaling efforts from companies that say "See! We're not being frivolous with your money! We only spend on the essentials." And this is true even for MASSIVE, PROFITABLE companies, because those companies' value is based on the Rich Person Feeling Graph (their stock) rather than the literal profit money. A company making a genuine gazillion dollars a year still tears through layoffs and freezes hiring and removes the free batteries from the printer room (totally not speaking from experience, surely) because the investors LOVE when you cut costs and take away employee perks. The "beer on tap, ping pong table in the common area" era of tech is drying up. And we're still unionless.
Never mind that last part.
And then in early 2023, AI (more specifically, Chat-GPT which is OpenAI's Large Language Model creation) tears its way into the tech scene with a meteor's amount of momentum. Here's Microsoft's prize pig, which it invested heavily in and is galivanting around the pig-show with, to the desperate jealousy and rapture of every other tech company and investor wishing it had that pig. And for the first time since the interest rate hikes, investors have dollar signs in their eyes, both venture capital and Wall Street alike. They're willing to restart the hose of money (even with the new risk) because this feels big enough for them to take the risk.
Now all these companies, who were in varying stages of sweating as their bill came due, or wringing their hands as their stock prices tanked, see a single glorious gold-plated rocket up out of here, the likes of which haven't been seen since the free money days. It's their ticket to buy time, and buy investors, and say "see THIS is what will wring money forth, finally, we promise, just let us show you."
To be clear, AI is NOT profitable yet. It's a money-sink. Perhaps a money-black-hole. But everyone in the space is so wowed by it that there is a wide-spread and powerful conviction that it will become profitable and earn its keep. (Let's be real, half of that profit "potential" is the promise of automating away jobs of pesky employees who peskily cost money.) It's a tech-space industrial revolution that will automate away skilled jobs, and getting in on the ground floor is the absolute best thing you can do to get your pie slice's worth.
It's the thing that will win investors back. It's the thing that will get the investment money coming in again (or, get it second-hand if the company can be the PROVIDER of something needed for AI, which other companies with venture-back will pay handsomely for). It's the thing companies are terrified of missing out on, lest it leave them utterly irrelevant in a future where not having AI-integration is like not having a mobile phone app for your company or not having a website.
So I guess to reiterate on my earlier point:
Drowned rats. Swimming to the one ship in sight.
35K notes
·
View notes
Text
Explore the best developer friendly API platforms designed to streamline integration, foster innovation, and accelerate development for seamless user experiences.
Developer Friendly Api Platform
#Developer Friendly Api Platform#Consumer Driven Banking#Competitive Market Advantage Through Data#Banking Data Aggregation Services#Advanced Security Architecture#Adr Open Banking#Accredited Data Recipient
0 notes
Text
Omri Kohl, CEO & Co-Founder of Pyramid Analytics – Interview Series
New Post has been published on https://thedigitalinsider.com/omri-kohl-ceo-co-founder-of-pyramid-analytics-interview-series/
Omri Kohl, CEO & Co-Founder of Pyramid Analytics – Interview Series
Omri Kohl is the CEO and co-founder of Pyramid Analytics. The Pyramid Decision Intelligence Platform delivers data-driven insights for anyone to make faster, more intelligent decisions. He leads the company’s strategy and operations through a fast-growing data and analytics market. Kohl brings a deep understanding of analytics and AI technologies, valuable management experience, and a natural ability to challenge conventional thinking. Kohl is a highly experienced entrepreneur with a proven track record in developing and managing fast-growth companies. He studied economics, finance, and business management at Bar-Ilan University and has an MBA in International Business Management from New York University, Leonard N. Stern School of Business.
Could you start by explaining what GenBI is, and how it integrates Generative AI with business intelligence to enhance decision-making processes?
GenBI is the framework and mechanics to bring the power of GenAI, LLMs and general AI into analytics, business intelligence and decision making.
Right now, it’s not practical to use GenAI alone to access insights to datasets. It could take over a week to upload enough data to your GenAI tool to get meaningful results. That’s simply not workable, as business data is too dynamic and too sensitive to use in this way. With GenBI, anyone can extract valuable insights from their data, just by asking a question in natural language and seeing the results in the form of a BI dashboard. It takes as little as 30 seconds to receive a relevant, useful answer.
What are the key technological innovations behind GenBI that allow it to understand and execute complex business intelligence tasks through natural language?
Well, without giving away all our secrets, there are essentially three components. First, GenBI prompts LLMs with all the elements they need to produce the correct analytical steps that will produce the requested insight. This is what allows the user to form queries using natural language and even in vague terms, without knowing exactly what type of chart, investigation, or format to request.
Next, the Pyramid Analytics GenBI solution applies these steps to your company’s data, regardless of the specifics of your situation. We’re talking the most basic datasets and simple queries, all the way up to the most sophisticated use cases and complex databases.
Third, Pyramid can carry out these queries on the underlying data and manipulate the results on the fly. An LLM alone can’t produce deep analysis on a database. You need a robot element to find all the necessary information, interpret the user request to produce insights, and pass it on to the BI platform to articulate the results either in plain language or as a dynamic visualization that can later be refined through follow-up queries.
How does GenBI democratize data analytics, particularly for non-technical users?
Quite simply, GenBI allows anyone to tap into the insights they need, regardless of their level of expertise. Traditional BI tools require the user to know which is the best data manipulation technique to receive the necessary results. But most people don’t think in pie charts, scatter charts or tables. They don’t want to have to work out which visualization is the most effective for their situation – they just want answers to their questions.
GenBI delivers these answers to anyone, regardless of their expertise. The user doesn’t need to know all the professional terms or work out if a scattergraph or a pie chart is the best option, and they don’t need to know how to code database queries. They can explore data by using their own words in a natural conversation.
We think of it as the difference between using a paper map to plan your route, and using Google Maps or other navigational app. With a traditional map, you have to work out the best roads to take, think about potential traffic jams, and compare different route possibilities. Today, people just put their destination into the app and hit the road – there’s so much trust in the algorithms that no one questions the suggested route. We’d like to think that GenBI is bringing the same kind of automated magic to corporate datasets.
What has been the feedback from early adopters about the ease of use and learning curve?
We’ve been receiving overwhelmingly positive feedback. The best way we can sum it up is, “Wow!” Users and testers highly appreciate Pyramid’s ease of use, powerful features, and meaningful insights.
Pyramid Analytics has virtually zero learning curve, so there’s nothing holding people back from adopting it on the spot. Approximately three-quarters of all the business teams who’ve tested our solution have adopted it and use it today, because it’s so easy and effective.
Can you share how GenBI has transformed decision-making processes within organizations that have implemented it? Any specific case studies or examples?
Although we’ve been developing it for a long time, we only rolled out GenBI a few weeks ago, so I’m sure you’ll understand that we don’t yet have fully-fledged case studies that we can share, or customer examples that we can name. However, I can tell you that organizations that have thousands of users are suddenly becoming truly data-driven, because everyone can access insights. Users can now unlock the true value of all their data.
GenBI is having a transformative effect on industries like insurance, banking, and finance, as well as retail, manufacturing, and many other verticals. Suddenly, it’s possible for financial advisors, for example, to tap into instant suggestions about the best way to optimize a customer’s portfolio.
What are some of the biggest challenges you faced in developing GenBI, and how did you overcome them?
Pyramid Analytics was already leveraging AI for analytics for many years before we launched the new solution, so most challenges have been ironed out long ago.
The main new element is the addition of a sophisticated query generation technology that works with any LLM to produce accurate results, while keeping data private. We’ve accomplished this by decoupling the data from the query (more on this in a moment).
Another big challenge we had to deal with was that of speed. We’re talking about the Google era, where people expect answers now, not in an hour or even half an hour. We made sure to speed up processing and optimize all workflows to reduce friction.
Then there’s the need to prevent hallucination. Chatbots are prone to hallucinations which skew results and undermine reliability. We’ve worked hard to avoid those while still maintaining dynamic results.
How do you handle issues related to data security and privacy?
That’s a great question, because data privacy and security is the biggest obstacle to successful GenAI analytics. Everyone is – quite rightly – concerned about the idea of exposing highly sensitive corporate data to third-party AI engines, but they also want the language interpretation capabilities and data insights that these engines can deliver.
That’s why we never share actual data with the LLMs we work with. Pyramid flips the entire premise on its head by serving as an intermediary between your company’s information and the LLM. We allow you to submit the request, and then we hand it to the LLM along with descriptions of what we call the “ingredients,” basically just the metadata.
The LLM then returns a “recipe,” which explains how to turn the user’s question into a data analytics prompt. Then Pyramid runs that recipe on the data that you’ve already connected securely on your self-hosted install, so that no data ever reaches the LLM. We mash up the results to serve them back to you in an easily understandable, visual format. Essentially, nothing that could compromise your security and privacy gets exposed or leaves the safety of your organization’s firewall.
For organizations looking to integrate GenBI into their existing data infrastructures, what does the implementation process look like? Are there any prerequisites or preparations needed?
The implementation process for Pyramid Analytics couldn’t be easier or faster. Users need very few prerequisites and preparations, and you can get the whole thing up and running in under an hour. You don’t need to move data into a new framework or change anything about your data strategy, because Pyramid queries your data directly where it resides.
There’s also no need to explain your data to the solution, or to define columns. It’s as simple as uploading a CSV dataset or connecting your SQL database. The same goes for any relational database of any sort. It takes only a few minutes to connect your data, and then you can ask your first question seconds later.
That said, you can tweak the structure if you want, like changing the joining model or redefining columns. It does take some time and effort, but we’re talking minutes, not a months-long dev project. Our customers are often shocked that Pyramid is up and running on their classic data warehouse or data lake within five minutes or so.
You also don’t need to come up with very specific, accurate, or even intelligent questions to get powerful results. You can make spelling mistakes and use incorrect phrasing, and Pyramid will unravel them and produce a meaningful and valuable answer. What you do need is some knowledge about the data you’re asking about.
Looking ahead, what’s your strategic vision for Pyramid Analytics over the next five years? How do you see your solutions evolving to meet changing market demands?
The next big frontier is supporting scalable, highly specific queries. Users are eager to be able to ask very precise questions, such as questions about personalized entities, and LLMs can’t yet produce intelligent answers in these cases, because they don’t have that kind of detailed insight into the specifics of your database.
We’re facing the challenge of how to use language models to ask about the specifics of your data without instantly connecting your entire, gigantic data lake to the LLM. How do you finetune your LLM about data that gets rehydrated every two seconds? We can manage this for fixed points like countries, locations, and even dates, but not for something idiosyncratic like names, even though we are very close to it today.
Another challenge is for users to be able to ask their own mathematical interpretations of the data, applying their own formulae. It’s difficult not because the formula is hard to enact, but because understanding what the user wants and getting the correct syntax is challenging. We’re working on solving both these challenges, and when we do, we’ll have passed the next eureka point.
Thank you for the great interview, readers who wish to learn more should visit Pyramid Analytics.
#ai#AI engines#Algorithms#Analysis#Analytics#app#banking#bi#bi tools#Business#Business Intelligence#business management#CEO#challenge#change#chart#charts#chatbots#code#columns#Companies#compromise#dashboard#data#data analytics#data lake#data privacy#data privacy and security#data security#data strategy
1 note
·
View note
Text
Fraud and Money Recovery Services
In the fast-paced world of international commerce, fraud can strike unexpectedly, leaving individuals and businesses grappling with financial losses. AIO Legal Services understands the gravity of such situations and stands ready to provide comprehensive fraud and money recovery services tailored to recover what’s rightfully owned by our clients. We offer a wide range of money recovery services,…

View On WordPress
#bank fraud#credit card fraud#cyber fraud#cybercrime#cybersecurity#Data breach#email scam#financial fraud#fraud#fraudulent activities#fraudulent behavior#fraudulent charges#fraudulent claims#fraudulent communication.#fraudulent documentation#fraudulent emails#fraudulent invoices#fraudulent manipulation#fraudulent practices#fraudulent schemes#fraudulent transactions#fraudulent transfers#fraudulent websites#fraudulent withdrawals#identity fraud#identity theft#internet fraud#online fraud#online scam#online security
0 notes
Text
Fan narration of a Relic entry in HSR’s Data Bank. This is the story of all four pieces of the Messenger Traversing Hackerspace set.
Music is “Techno Driver” by Ilya Myagkov.
#honkai star rail#hsr#star rail#audio post#lore#star rail lore#audio#fan narration#data bank#relics#messenger traversing hackerspace#capital of passion#yellow ducky#public security regulation#holovisor
0 notes
Text
Demystifying Hybrid Cloud: A Comprehensive Guide to Cloud Computing
In the ever-evolving landscape of technology, cloud computing has emerged as a cornerstone of innovation, enabling organizations to streamline operations, enhance scalability, and drive digital transformation. Within the realm of cloud computing, one concept that has gained significant traction is the hybrid cloud model. In this article, we will delve into the intricacies of hybrid cloud, exploring its definition, benefits, challenges, and real-world applications.

Understanding Hybrid Cloud
At its core, hybrid cloud refers to a computing environment that combines elements of public and private clouds, allowing organizations to leverage the strengths of both platforms. In a hybrid cloud setup, specific workloads, applications, or data are seamlessly orchestrated between on-premises infrastructure and public cloud services, such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP).
The hybrid cloud model offers unparalleled flexibility, enabling organizations to optimize resource allocation, meet fluctuating demand, and maintain control over sensitive data and critical workloads. By seamlessly integrating private and public cloud environments, businesses can achieve a dynamic and scalable infrastructure that adapts to their evolving needs.
Benefits of Hybrid Cloud
One of the primary advantages of hybrid cloud is its ability to strike a balance between the scalability and cost-effectiveness of public clouds and the security and customization of private clouds. By leveraging a hybrid cloud strategy, organizations can:
Scalability: Hybrid cloud allows businesses to scale their infrastructure seamlessly, leveraging the elastic resources of public clouds during peak demand while maintaining dedicated resources for sensitive workloads.
Cost Optimization: With hybrid cloud, organizations can optimize costs by allocating workloads to the most cost-effective cloud environment based on performance requirements, compliance regulations, and budget constraints.
Data Security and Compliance: Hybrid cloud enables organizations to retain sensitive data on-premises or in a private cloud environment while leveraging the agility and scalability of public clouds for less sensitive workloads. This approach ensures compliance with industry regulations and data protection standards.
Disaster Recovery and Business Continuity: By replicating data and workloads across multiple cloud environments, hybrid cloud enhances resilience and enables efficient disaster recovery and business continuity strategies, minimizing downtime and data loss.
Flexibility and Agility: Hybrid cloud provides organizations with the flexibility to deploy workloads where they best fit, whether on-premises, in a private cloud, or in the public cloud. This agility allows businesses to respond quickly to changing market dynamics and customer demands.
Challenges of Hybrid Cloud
While hybrid cloud offers numerous benefits, it also presents challenges that organizations must address to maximize its potential. Some of the key challenges include:
Complexity: Managing workloads across multiple cloud environments introduces complexity in terms of networking, security, and governance. Organizations need robust management tools and skilled personnel to navigate the complexities of hybrid cloud deployments effectively.
Data Integration and Interoperability: Ensuring seamless data integration and interoperability between on-premises infrastructure and public cloud services can be challenging. Organizations must implement robust data management strategies and integration solutions to facilitate smooth data exchange across environments.
Security and Compliance: Hybrid cloud environments introduce security risks associated with data movement between on-premises and public cloud environments. Organizations must implement stringent security measures, encryption protocols, and access controls to mitigate security threats and ensure compliance with regulatory requirements.
Vendor Lock-In: Depending heavily on a single cloud provider can lead to vendor lock-in, limiting flexibility and hindering migration between cloud environments. Organizations must adopt a multi-cloud strategy and embrace interoperable technologies to avoid vendor lock-in and maintain flexibility.
Cost Management: While hybrid cloud offers cost optimization opportunities, effectively managing costs across multiple cloud environments can be challenging. Organizations must closely monitor resource utilization, optimize workload placement, and leverage cost management tools to control expenses and avoid cost overruns.
Real-World Applications
Hybrid cloud is increasingly being adopted across various industries and use cases, driven by its flexibility, scalability, and cost-effectiveness. Some common real-world applications of hybrid cloud include:
Enterprise IT: Large enterprises often leverage hybrid cloud to modernize legacy IT infrastructure, optimize resource utilization, and facilitate digital transformation initiatives while maintaining control over critical workloads and sensitive data.
E-commerce and Retail: Retailers utilize hybrid cloud to handle seasonal spikes in demand, enhance customer experiences, and streamline e-commerce operations. By leveraging public cloud scalability for web applications and on-premises infrastructure for backend systems, retailers can ensure optimal performance and reliability.
Healthcare: Healthcare organizations leverage hybrid cloud to securely store and analyze sensitive patient data, comply with healthcare regulations such as HIPAA, and enhance collaboration among healthcare professionals. Hybrid cloud enables healthcare providers to deploy healthcare applications and services flexibly while ensuring data privacy and security.
Finance and Banking: Financial institutions utilize hybrid cloud to enhance agility, scalability, and security while complying with stringent regulatory requirements. Hybrid cloud enables banks and financial services firms to modernize legacy systems, deploy innovative fintech solutions, and drive digital innovation while safeguarding customer data and ensuring regulatory compliance.
Manufacturing and Industry 4.0: Manufacturers leverage hybrid cloud to optimize production processes, enhance supply chain visibility, and drive operational efficiency. By combining on-premises infrastructure with cloud-based analytics and IoT platforms, manufacturers can gain real-time insights, improve decision-making, and accelerate innovation in the era of Industry 4.0.
In conclusion, hybrid cloud represents a powerful paradigm shift in cloud computing, offering organizations the flexibility, scalability, and agility to meet the demands of today's digital economy. While hybrid cloud presents challenges, its benefits outweigh the complexities, driving widespread adoption across industries and use cases. By embracing hybrid cloud, organizations can unlock new opportunities for innovation, growth, and competitive advantage in an increasingly interconnected and dynamic world.
#Hybrid cloud#Cloud computing#Public cloud#Private cloud#Scalability#Cost optimization#Data security#Compliance#Disaster recovery#Business continuity#Flexibility#Agility#Complexity#Data integration#Interoperability#Security#Vendor lock-in#Cost management#Real-world applications#Enterprise IT#E-commerce#Retail#Healthcare#Finance#Banking#Manufacturing#Industry 4.0.
0 notes
Text
Cybersecurity in Personal Finance Management: Essential Strategies for Digital Safety
In today’s digital age, where a staggering 76% of Americans engage in online banking (Pew Research Center), the importance of cybersecurity in managing personal finances cannot be overstated. This comprehensive guide explores the essential strategies for protecting your online banking, investment, and transaction activities from cyber threats.
Fortifying Online Banking and Investments: An…
View On WordPress
#cyberattack statistics#cybercrime prevention#Cybersecurity#data backup#data protection#digital finance management#digital transactions#expert cybersecurity advice#financial cybersecurity guide#financial data encryption#global cybercrime costs#hard drive failure risks#investment security#online banking#personal finance#phishing scams#phishing threat awareness#public Wi-Fi security#robust passwords#secure financial apps#secure online investments#SSL certificates#two-factor authentication#VPN usage#Wi-Fi safety
0 notes
Text
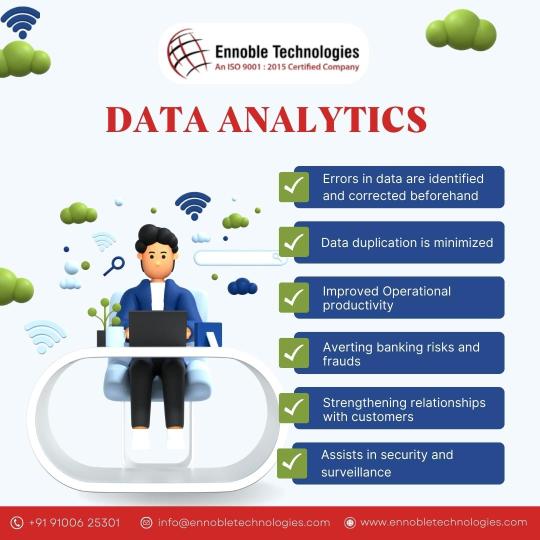
Data Analytics Services | Ennoble Technologies
Leverage the power of data to make informed business decisions with Ennoble Technologies expert Data Analytics services. Drive growth and maximize ROI.
Do Visit: https://ennobletechnologies.com/data-analytics/
#data analytics#Errors in data#Data duplication#Operational productivity#banking risks and frauds#relationships with customers#security and surveillance#Ennoble Technologies
1 note
·
View note
Text
Fortifying the Financial Fortress with 5 Battle-Tested Strategies
In 2022, the financial sector experienced more than 3,500 data breaches, resulting in a crazy 10 billion records being compromised. And the impact is not just limited to corporates; it reaches us, the consumers, too. So, where are the weak spots? How is it possible that these financial giants struggle to identify them while cybercriminals thrive? Is there a gap in security, or are the security mechanisms themselves flawed? Let's dig deep and uncover the answers to these pressing questions.
Read article - https://bit.ly/3PndiqC

0 notes
Text
Welcome to BSE Institute Ltd. | Global Accountancy Professional
Diversity in accounting practices across countries makes it difficult to prepare consolidated financial statements for companies with foreign operations. A Company lets say, while headquartered in Michigan, conducts business on six continents, has multiple facilities, in more than 100 countries, across different time zones, with each subsidiary preparing financial statements in accordance with their local regulations and in their local currency.
#data science#data science course#data analytics course#data analytics#cyber security course#cyber security training#financial market course#data analysis course#predictive analysis course#banking course#banking and finance course#financial accounting course#financial accounting#investment banking operations
0 notes
Text
#Electric locks & electric door lock system is providing by Secureye hotels#universities#banks. Make security more powerful with secureye electric-locks#Electromagnetic Door Lock 12V for Access Control Door Cabinet This electromagnet is popularly used in Access Control Systems#Card reader door locks work by identifying the card when it is swiped through the door. After a card is swiped#the lock system identifies it by reading the magnetic stripe or PIN and compares the data to the information stored in the software. The ca#cont. Raj:- 9312052014#7053551121#our website:- www.jptechnologies.in
0 notes
Text
OpenAI set to unveil AI-driven challenger to Google Search
New Post has been published on https://thedigitalinsider.com/openai-set-to-unveil-ai-driven-challenger-to-google-search/
OpenAI set to unveil AI-driven challenger to Google Search
.pp-multiple-authors-boxes-wrapper display:none;
img width:100%;
Google’s long-standing supremacy in the search engine arena may soon be challenged as OpenAI, boosted by its partnership with Microsoft, is reportedly stepping up to launch its own AI-driven search product.
According to two sources familiar with the matter who spoke to Reuters, OpenAI is scheduled to unveil its AI-powered search tool on Monday. The introduction of this product coincides closely with the timing of Google’s annual I/O conference, which starts on Tuesday and is anticipated to feature several AI-related announcements.
While Google remains a titan in search, it too has been adapting to incorporate AI more deeply into its functionalities. Google began trialling AI-powered search summaries in the US over a year ago and expanded testing to selected, signed-in UK users last month.
The potential entry of OpenAI into the search engine market adds a new layer of competition not only for Google, but also for other entities like Perplexity.
OpenAI, heavily supported by Microsoft, seems to be banking on the intersection of AI and search engine technology to carve out its niche. Microsoft previously integrated OpenAI’s AI capabilities into its Bing search engine and Edge browser in February 2023, making these advanced features available to paid subscribers, along with integration into its Microsoft Office suite.
OpenAI’s forthcoming search product is expected to expand on its existing flagship tool, ChatGPT. Reports from Bloomberg reveal that the new feature will allow users to pose questions to ChatGPT and receive responses that pull information from the web with appropriate citations. This could include references to Wikipedia or various blogs and might even provide illustrative images or diagrams relevant to the queries.
If OpenAI successfully launches this new search product, it could signify a significant shift in how internet searches are conducted—moving away from traditional search models towards more integrated, AI-driven responses that significantly enhance user experience.
(Photo by GR Stocks)
See also: Coalition of news publishers sue Microsoft and OpenAI
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: ai, artificial intelligence, chatgpt, google search, openai, search, search engine
#2023#ai#ai & big data expo#AI-powered#AI-powered search#amp#Announcements#applications#Articles#artificial#Artificial Intelligence#automation#background#banking#Big Data#bing#browser#chatbots#chatGPT#Cloud#Companies#competition#comprehensive#conference#cutting#cyber#cyber security#data#Developments#Digital Transformation
0 notes
Text
Is your lending platform Account Aggregator ready?
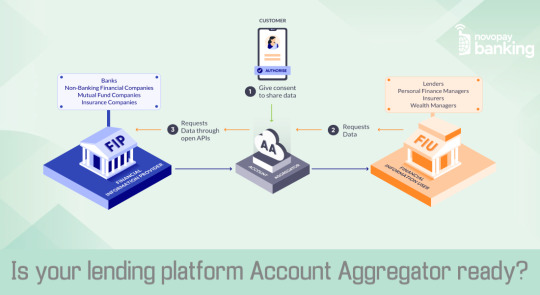
Account Aggregators are here to transform the digital lending sector as they bring absolute control for borrowers along with great convenience for lenders making it a win-win for both. Regulated and mandated by RBI, the Account Aggregation framework can be best defined as a platform collecting user’s personal financial data from Financial Information Providers (FIP) with consent and sharing it with the Financial Information Users (FIU) such as lenders making the process much faster while ensuring data is secured.
What does this mean for a User?
User-Controlled Data Sharing:
AA framework gives the users control of their data like nothing ever has. Known as an interoperable data-blind consent manager, this platform cannot read, use or sell consumer data which is encrypted by the user with digital signatures. The AA simply collects data and transfers it to FIUs who can decrypt and use the data as consented for. It equips the user to share data selectively, for a stipulated duration of time, and even withdraw the data once shared; giving the user complete visibility of when and where the data is being shared.
Simplifying Wealth Management:
Calling the AA system as your one-stop solution for managing multifarious financial assets and transactions wouldn’t be wrong. The user may consolidate all financial data across various applications to create a single touch-point through an account aggregator empowering the user in more ways than one. Along with the ease of sharing data with the service provider, the user gets a wholesome look at the portfolio and is able to closely monitor expenditure thus making wealth management simpler, faster and more secure. Consolidated data showing cash inflows through various sources can also help enhance a user’s credit scoring and underwriting.
Accelerating Lending Operations:
A consolidated system will eventually improve the efficiency of every financial operation. Registering on an AA platform via a financial entity eliminates a lot of time-consuming processes like queuing outside the bank, KYC, stamping documents et al. The lending agency can now quickly pull out borrowers’ accurate financial history, follow due diligence digitally and expedite the lending process.
Data on Fingertips:
The best part about getting on the AA framework? Consent, data-tracking, or connecting to the agency of your choice can now be managed through a simple app on the phone! Finally, feel in control? Yes, you are.
Read More: https://www.novopaybanking.com/blog/is-your-lending-platform-account-aggregator-ready
#digital lending#dasta sharing#data security#account aggregator#digital distribution solution#kyc for banking#retailers provide banking solutions#saas solutions#aeps
0 notes