#cybercriminal attacks
Text
What do Banks do to Secure Their Data?
Banking is the only sector that contains every individual's financial and personal data. As digitization in the banking sector has taken a leap, there are many things added to help banks automate workflow. However, many things to worry about, like protecting sensitive information and establishing security measures to prevent cybercriminal attacks through phishing and malware.

Due to digitization in almost all industries and organizations, banks have had to modify their systems to meet these developments and transform their operations to ensure the continuous security of new banking technologies.
The rules governing banking are continually changing to meet the demands put forward by current banking systems. For example, banks are required to safeguard client data and guard against hacker attacks and illegal access by law.
Let Us See How Banks And Financial Services Providers Uphold Security Responsibility!
Infrastructure Security
Securing the infrastructure refers to securing the data center where the business-critical data of the banks is stored. It can be an on-premise data center, infrastructure co-located at the service provider's space, or a bank's data hosted on the service provider's data center.

Many cloud service providers like ESDS offers compliant infrastructure suitable for the security requirements of banks.
Employees of banks typically receive specialized devices that block access to USB ports, social media websites, and personal email accounts. In addition, employees can only connect to the banks' network through a VPN.
Testing and Monitoring of Data Security Controls
A bank tests and monitors all data security controls regularly. It updates the program to reflect changes in its operations and systems, rectifying or modifying the program to reflect detected issues. In addition, the bank periodically evaluates and assesses the risks to identify and handle changes in the threats or hazards to its customer information.
Customer Authentication
As online banking has changed the way banks work, every bank transaction done by a customer online or offline is authenticated to establish the identity of the person initiating the transaction. Customers using ATMs and POS terminals, those using credit/debit cards at POS terminals, those using online or mobile banking, and those visiting the bank in person must go through the authentication process. In addition, employees of banks who have access to consumer and bank data have to follow the same protocol.
Many banks have now introduced two-factor and multi-factor authentication to guarantee that the person is indeed who they claim to be. In addition, when clients engage with banking systems like IVR (Interactive voice response), banks use behavioral biometrics, such as biometric authentication, to confirm the customers' identities. Some of the best cloud service providers, like ESDS, offer the most reliable AI-enabled chatbots, ATMs, Kiosks, and POS services as the banks require.
Regular Communication

With the periodic account statements that are prepared and given to customers, banks also regularly communicate with customers regarding system changes, the introduction of new authentication methods, etc. Furthermore, customers can establish alerts and limits based on various criteria to ensure they are notified of any unforeseen action about their accounts. There are many communication options, but the setup can be adapted to suit the users' convenience.
Traces of audits
A statement or passbook containing a history of transactions was always accessible. Additionally, banking systems record every action a customer takes when interacting with the systems in an audit trail. The time of the conversation is recorded together with the specifics of the interaction, regardless of whether the consumer uses phone or internet banking. Daily backups are made of this data, which is never wholly deleted but rather archived at predetermined intervals.
Wrapping up
Cybercrimes like invasion and phishing are still very prevalent. Beyond the legislative requirements, a bank's reputation, ability to offer products and services to its customers, and capability to prevent customer data from being subject to fraud depend on its ability to keep ahead of the hackers.
#What do Banks do to Secure Their Data#cybercriminal attacks#data security for banks#Banking & Financial Data Security#Cyber Security in Banking Sector
1 note
·
View note
Text
Clearing the “Fog of More” in Cyber Security
New Post has been published on https://thedigitalinsider.com/clearing-the-fog-of-more-in-cyber-security/
Clearing the “Fog of More” in Cyber Security
At the RSA Conference in San Francisco this month, a dizzying array of dripping hot and new solutions were on display from the cybersecurity industry. Booth after booth claimed to be the tool that will save your organization from bad actors stealing your goodies or blackmailing you for millions of dollars.
After much consideration, I have come to the conclusion that our industry is lost. Lost in the soup of detect and respond with endless drivel claiming your problems will go away as long as you just add one more layer. Engulfed in a haze of technology investments, personnel, tools, and infrastructure layers, companies have now formed a labyrinth where they can no longer see the forest for the trees when it comes to identifying and preventing threat actors. These tools, meant to protect digital assets, are instead driving frustration for both security and development teams through increased workloads and incompatible tools. The “fog of more” is not working. But quite frankly, it never has.
Cyberattacks begin and end in code. It’s that simple. Either you have a security flaw or vulnerability in code, or the code was written without security in mind. Either way, every attack or headline you read, comes from code. And it’s the software developers that face the ultimate full brunt of the problem. But developers aren’t trained in security and, quite frankly, might never be. So they implement good old fashion code searching tools that simply grep the code for patterns. And be afraid for what you ask because as a result they get the alert tsunami, chasing down red herrings and phantoms for most of their day. In fact, developers are spending up to a third of their time chasing false positives and vulnerabilities. Only by focusing on prevention can enterprises really start fortifying their security programs and laying the foundation for a security-driven culture.
Finding and Fixing at the Code Level
It’s often said that prevention is better than cure, and this adage holds particularly true in cybersecurity. That’s why even amid tighter economic constraints, businesses are continually investing and plugging in more security tools, creating multiple barriers to entry to reduce the likelihood of successful cyberattacks. But despite adding more and more layers of security, the same types of attacks keep happening. It’s time for organizations to adopt a fresh perspective – one where we home in on the problem at the root level – by finding and fixing vulnerabilities in the code.
Applications often serve as the primary entry point for cybercriminals seeking to exploit weaknesses and gain unauthorized access to sensitive data. In late 2020, the SolarWinds compromise came to light and investigators found a compromised build process that allowed attackers to inject malicious code into the Orion network monitoring software. This attack underscored the need for securing every step of the software build process. By implementing robust application security, or AppSec, measures, organizations can mitigate the risk of these security breaches. To do this, enterprises need to look at a ‘shift left’ mentality, bringing preventive and predictive methods to the development stage.
While this is not an entirely new idea, it does come with drawbacks. One significant downside is increased development time and costs. Implementing comprehensive AppSec measures can require significant resources and expertise, leading to longer development cycles and higher expenses. Additionally, not all vulnerabilities pose a high risk to the organization. The potential for false positives from detection tools also leads to frustration among developers. This creates a gap between business, engineering and security teams, whose goals may not align. But generative AI may be the solution that closes that gap for good.
Entering the AI-Era
By leveraging the ubiquitous nature of generative AI within AppSec we will finally learn from the past to predict and prevent future attacks. For example, you can train a Large Language Model or LLM on all known code vulnerabilities, in all their variants, to learn the essential features of them all. These vulnerabilities could include common issues like buffer overflows, injection attacks, or improper input validation. The model will also learn the nuanced differences by language, framework, and library, as well as what code fixes are successful. The model can then use this knowledge to scan an organization’s code and find potential vulnerabilities that haven’t even been identified yet. By using the context around the code, scanning tools can better detect real threats. This means short scan times and less time chasing down and fixing false positives and increased productivity for development teams.
Generative AI tools can also offer suggested code fixes, automating the process of generating patches, significantly reducing the time and effort required to fix vulnerabilities in codebases. By training models on vast repositories of secure codebases and best practices, developers can leverage AI-generated code snippets that adhere to security standards and avoid common vulnerabilities. This proactive approach not only reduces the likelihood of introducing security flaws but also accelerates the development process by providing developers with pre-tested and validated code components.
These tools can also adapt to different programming languages and coding styles, making them versatile tools for code security across various environments. They can improve over time as they continue to train on new data and feedback, leading to more effective and reliable patch generation.
The Human Element
It’s essential to note that while code fixes can be automated, human oversight and validation are still crucial to ensure the quality and correctness of generated patches. While advanced tools and algorithms play a significant role in identifying and mitigating security vulnerabilities, human expertise, creativity, and intuition remain indispensable in effectively securing applications.
Developers are ultimately responsible for writing secure code. Their understanding of security best practices, coding standards, and potential vulnerabilities is paramount in ensuring that applications are built with security in mind from the outset. By integrating security training and awareness programs into the development process, organizations can empower developers to proactively identify and address security issues, reducing the likelihood of introducing vulnerabilities into the codebase.
Additionally, effective communication and collaboration between different stakeholders within an organization are essential for AppSec success. While AI solutions can help to “close the gap” between development and security operations, it takes a culture of collaboration and shared responsibility to build more resilient and secure applications.
In a world where the threat landscape is constantly evolving, it’s easy to become overwhelmed by the sheer volume of tools and technologies available in the cybersecurity space. However, by focusing on prevention and finding vulnerabilities in code, organizations can trim the ‘fat’ of their existing security stack, saving an exponential amount of time and money in the process. At root-level, such solutions will be able to not only find known vulnerabilities and fix zero-day vulnerabilities but also pre-zero-day vulnerabilities before they occur. We may finally keep pace, if not get ahead, of evolving threat actors.
#ai#ai tools#Algorithms#Application Security#applications#approach#AppSec#assets#attackers#awareness#Business#code#codebase#coding#Collaboration#communication#Companies#comprehensive#compromise#conference#creativity#cyber#cyber security#Cyberattacks#cybercriminals#cybersecurity#data#detection#developers#development
0 notes
Text
Beware Of These Techniques That Cybercriminals Use To Steal Cryptocurrency
While the rise of cryptocurrency has brought about revolutionary changes in the financial landscape, it has also opened doors to new forms of cybercrime. The decentralized and anonymous nature of cryptocurrencies has made them attractive targets for cybercriminals.
Understanding the techniques that cybercriminals use to steal these digital assets is crucial for protecting oneself in the evolving landscape of cybersecurity. It is important that you stay vigilant, and informed, and prioritize security to protect yourself against these evolving threats.
Check out this list of techniques that cybercriminals use to steal cryptocurrency.
1. Phishing Attacks

One of the most common techniques used by cybercriminals is phishing. They employ misleading emails, websites, or messages that look similar to legitimate platforms or communication from trusted entities. Unsuspecting users are tricked into revealing their private keys, passwords, or wallet information which allows the criminals to gain access to their cryptocurrency holdings.
To Read More Click here...
#business#business blog#new updates#trending topic#cryptocurrency#Phishing Attacks#Cybercriminals#new techniques#revolutionary#evolving threats
0 notes
Text
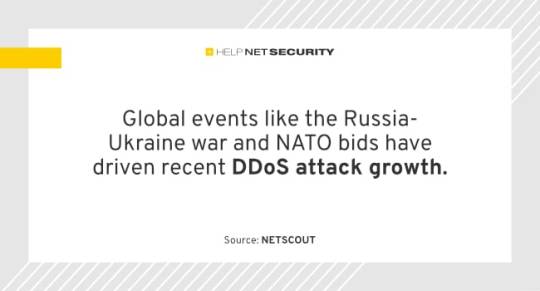
Global events fuel DDoS attack campaigns - Help Net Security
Cybercriminals launched approximately 7.9 million DDoS attacks in 1H 2023, representing a 31% year-over-year increase, according to NETSCOUT.
Global events like the Russia-Ukraine war and NATO bids have driven recent DDoS attack growth. Finland was targeted by pro-Russian hacktivists in 2022 during its bid to join NATO. Turkey and Hungary were targeted with DDoS attacks for opposing Finland’s…
View On WordPress
0 notes
Text
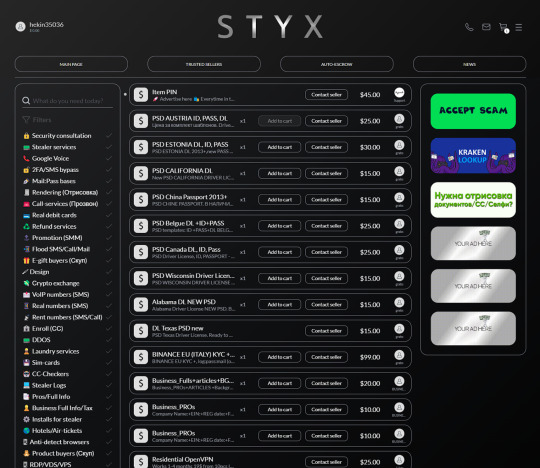
STYX – A New Dark Web Marketplace Selling DDOS Tools & Banking Malware
Researchers from Rsecurity discovered a recently opened marketplace named STYX; it was found to be opened around January 19, 2023. Cybercriminals operating this marketplace primarily focus on financial fraud, money laundering, and identity theft. The portal was found to be designed using the escrow module, which enables threat actors to brokerage between the buyers and…
STYX – A New Dark Web…
View On WordPress
0 notes
Text
Over nearly a decade, the hacker group within Russia's GRU military intelligence agency known as Sandworm has launched some of the most disruptive cyberattacks in history against Ukraine's power grids, financial system, media, and government agencies. Signs now point to that same usual suspect being responsible for sabotaging a major mobile provider for the country, cutting off communications for millions and even temporarily sabotaging the air raid warning system in the capital of Kyiv.
On Tuesday, a cyberattack hit Kyivstar, one of Ukraine's largest mobile and internet providers. The details of how that attack was carried out remain far from clear. But it “resulted in essential services of the company’s technology network being blocked,” according to a statement posted by Ukraine’s Computer Emergency Response Team, or CERT-UA.
Kyivstar's CEO, Oleksandr Komarov, told Ukrainian national television on Tuesday, according to Reuters, that the hacking incident “significantly damaged [Kyivstar's] infrastructure [and] limited access.”
“We could not counter it at the virtual level, so we shut down Kyivstar physically to limit the enemy's access,” he continued. “War is also happening in cyberspace. Unfortunately, we have been hit as a result of this war.”
The Ukrainian government hasn't yet publicly attributed the cyberattack to any known hacker group—nor have any cybersecurity companies or researchers. But on Tuesday, a Ukrainian official within its SSSCIP computer security agency, which oversees CERT-UA, pointed out in a message to reporters that a group known as Solntsepek had claimed credit for the attack in a Telegram post, and noted that the group has been linked to the notorious Sandworm unit of Russia's GRU.
“We, the Solntsepek hackers, take full responsibility for the cyber attack on Kyivstar. We destroyed 10 computers, more than 4 thousand servers, all cloud storage and backup systems,” reads the message in Russian, addressed to Ukrainian president Volodymyr Zelenskyy and posted to the group's Telegram account. The message also includes screenshots that appear to show access to Kyivstar's network, though this could not be verified. “We attacked Kyivstar because the company provides communications to the Ukrainian Armed Forces, as well as government agencies and law enforcement agencies of Ukraine. The rest of the offices helping the Armed Forces of Ukraine, get ready!”
Solntsepek has previously been used as a front for the hacker group Sandworm, the Moscow-based Unit 74455 of Russia's GRU, says John Hultquist, the head of threat intelligence at Google-owned cybersecurity firm Mandiant and a longtime tracker of the group. He declined, however, to say which of Solntsepek’s network intrusions have been linked to Sandworm in the past, suggesting that some of those intrusions may not yet be public. “It's a group that has claimed credit for incidents we know were carried out by Sandworm,” Hultquist says, adding that Solntsepek's Telegram post bolsters his previous suspicions that Sandworm was responsible. "Given their consistent focus on this type of activity, it's hard to be surprised that another major disruption is linked to them.”
If Solntsepek is a front for Sandworm, it would be far from the first. Over its years of targeting Ukrainian infrastructure, the GRU unit has used a wide variety of covers, hiding behind false flags such as independent hacktivist groups and cybercriminal ransomware gangs. It even attempted to frame North Korea for its attack on the 2018 Winter Olympics.
Today, Kyivstar countered some of Solntsepek's claims in a post on X, writing that “we assure you that the rumors about the destruction of our ‘computers and servers’ are simply fake.” The company had also written on the platform that it hoped to restore its network's operations by Wednesday, adding that it's working with the Ukrainian government and law enforcement agencies to investigate the attack. Kyivstar's parent company, Veon, headquartered in Amsterdam, didn't respond to WIRED's request for more information.
While the fog of war continues to obscure the exact scale of the Kyivstar incident, it already appears to be one of the most disruptive cyberattacks to have hit Ukraine since Russia's full-scale invasion began in February 2022. In the year that followed, Russia launched more data-destroying wiper attacks on Ukrainian networks than have been seen anywhere else in the world in the history of computing, though most have had far smaller effects than the Kyivstar intrusion. Other major Russian cyberattacks to hit Ukraine over the past 20 months include a cyberattack that crippled thousands of Viasat satellite modems across the country and other parts of Europe, now believed to have been carried out by the GRU. Another incident of cybersabotage, which Mandiant attributes to Sandworm specifically, caused a blackout in a Ukrainian city just as it was being hit by missile strikes, potentially hampering defensive efforts.
It's not yet clear if the Kyivstar attack—if it was indeed carried out by a Russian state-sponsored hacker group—was merely intended to sow chaos and confusion among the company's customers, or if it had a more specific tactical intention, such as disguising intelligence-gathering within Kyivstar's network, hampering Ukrainian military communications, or silencing its alerts to civilians about air raids.
“Telecoms offer intelligence opportunities, but they're also very effective targets for disruption," says Mandiant's Hultquist. “You can cause significant disruption to people's lives. And you can even have military impacts.”
44 notes
·
View notes
Text
Cyberspace Sentinels: Tracing the Evolution and Eccentricities of ICE
As we hark back to the embryonic stages of cyber defense in the late 1990s, we find ourselves in a digital petri dish where the first firewalls and antivirus programs are mere amoebas against a sea of threats. The digital defenses of yore, much like the drawbridges and moats of medieval castles, have transformed into a labyrinth of algorithms and machine learning guards in today's complex cybersecurity ecosystem. The sophistication of these systems isn't just technical; it's theatrical.
The drama unfolds spectacularly in the cyberpunk genre, where Intrusion Countermeasures Electronics (ICE) are the dramatis personae. Let's peruse the virtual halls of cyberpunk media to encounter the most deadly, and delightfully weird, iterations of ICE, juxtaposing these fictional behemoths against their real-world counterparts.
We commence our odyssey with William Gibson’s "Neuromancer," where ICE is not only a barrier but a perilous landscape that can zap a hacker's consciousness into oblivion. Gibson gives us Black ICE, a lethal barrier to data larceny that kills the intruding hacker, a grim forerunner to what cybersecurity could become in an age where the stakes are life itself.
CD Projekt Red’s "Cyberpunk 2077" gives us Daemons, digital Cerberuses that gnash and claw at Netrunners with malevolent intent. They symbolize a cyber-Orwellian universe where every keystroke could be a pact with a digital devil.
The chromatic haze of "Ghost in the Shell" offers ICE that intertwines with human cognition, reflecting a reality where software not only defends data but the very sanctity of the human mind.
In Neal Stephenson’s "Snow Crash," the Metaverse is patrolled by ICE that manifests as avatars capable of digital murder. Stephenson's vision is a reminder that in the realm of bytes and bits, the avatar can be as powerful as the sword.
"Matrix" trilogy, portrays ICE as Sentinels — merciless machines tasked with hunting down and eliminating threats, a silicon-carbon ballet of predator and prey.
On the small screen, "Mr. Robot" presents a more realistic tableau — a world where cybersecurity forms the battleground for societal control, with defense systems mirroring modern malware detection and intrusion prevention technologies.
"Ready Player One," both the novel and Spielberg's visual feast, portrays IOI’s Oology Division as a form of corporate ICE, relentless in its pursuit of control over the Oasis, guarding against external threats with a militaristic zeal that mirrors today's corporate cybersecurity brigades.
And let’s not overlook the anarchic "Watch Dogs" game series, where ICE stands as a silent sentinel against a protagonist who uses the city’s own connected infrastructure to bypass and dismantle such defenses.
Now, let us tether these fictional marvels to our reality. Today’s cybersecurity does not slumber; it's embodied in the form of next-gen firewalls, intrusion prevention systems, and advanced endpoint security solutions. They may not be as visceral as the ICE of cyberpunk, but they are no less sophisticated. Consider the deep packet inspection and AI-based behavioral analytics that cast an invisible, ever-watchful eye over our digital comings and goings.
Nevertheless, the reality is less bloodthirsty. Real-world cyber defense systems, as advanced as they may be, do not threaten the physical well-being of attackers. Instead, they stealthily snare and quarantine threats, perhaps leaving cybercriminals pining for the days of simple antivirus skirmishes.
But as the cyberverse stretches its tendrils further into the tangible world, the divide between the fantastical ICE of cyberpunk and the silicon-hardened guardians of our networks grows thin. With the Internet of Things (IoT) binding the digital to the physical, the kinetic potential of cybersecurity threats — and therefore the need for increasingly aggressive countermeasures — becomes apparent.
Could the ICE of tomorrow cross the Rubicon, protecting not just data, but physical well-being, through force if necessary? It is conceivable. As cyberpunk media illustrates, ICE could morph from passive digital barricades into active defenders, perhaps not with the murderous flair of its fictional counterparts but with a potency that dissuades through fear of tangible repercussions.
In the taut narrative of cybersecurity’s evolution, ICE remains the enigmatic, omnipresent sentinel, an avatar of our collective desire for safety amidst the binary storm. And while our reality may not yet feature the neon-drenched drama of cyberpunk's lethal ICE, the premise lingers on the periphery of possibility — a silent admonition that as our digital and physical realms converge, so too might our defenses need to wield a fiercer bite. Will the cyberpunk dream of ICE as a dire protector manifest in our world? Time, the grand weaver of fate, shall unfurl the tapestry for us to see.
- Raz
29 notes
·
View notes
Text
One of the world’s biggest botnet networks, responsible for stealing close to $6 billion (£4.7bn), has been shut down following an international effort from law enforcement agencies.
The US Justice Department, which led the operation, said the 911 S5 botnet comprised more than 19 million hijacked devices, which were being used to facilitate cyber attacks, large-scale fraud, bomb threats and even child exploitation.
Chinese national YunHe Wang, 35, was arrested on 24 May on suspicion of creating and operating the 911 S5 botnet from his home in St. Kitts and Nevis.
“This Justice Department-led operation brought together law enforcement partners from around the globe to disrupt 911 S5,” said US Attorney General Merrick Garland.
“This case makes clear that the long arm of the law stretches across borders and into the deepest shadows of the dark web, and the Justice Department will never stop fighting to hold cyber criminals to account.”
The FBI said the 911 S5 botnet infected computers in nearly 200 countries around the world, which were then controlled through 150 dedicated servers allegedly set up by Mr Wang.
An indictment unsealed on 24 May claimed that malware was used to infect and compromise millions of residential computers between 2014 and 2022, forming the botnet that was then able to carry out the cyber crimes.
Mr Wang allegedly sold access to the botnet to criminals, who then used it to bypass fraud detection systems in order to steal billions of dollars from financial institutions.
One target was reportedly a pandemic relief program in the US, which saw the botnet used to fraudulently make insurance claims from the hijacked IP addresses. More than half a million false claims resulted in losses of $5.9 billion for the programs, according to the FBI.
“Working with our international partners, the FBI conducted a joint, sequenced cyber operation to dismantle the 911 S5 Botnet – likely the world’s largest botnet ever,” said FBI Director Christopher Wray.
“We arrested its administrator, Yunhe Wang, seized infrastructure and assets, and levied sanctions against Wang and his co-conspirators... We will work tirelessly to unmask and arrest the cybercriminals who profit from this illegal activity.”
Mr Wang made around $99 million by selling access to the botnet, according to the indictment, which he used to purchase real estate in the US, St. Kitts and Nevis, China, Singapore, Thailand and the United Arab Emirates.
Other assets subject to forfeiture are two BMWs, a Ferrari, a Rolls Royce and several luxury wristwatches.
“The conduct alleged here reads like it’s ripped from a screenplay: A scheme to sell access to millions of malware-infected computers worldwide, enabling criminals over the world to steal billions of dollars, transmit bomb threats, and exchange child exploitation materials – then using the scheme’s nearly $100 million in profits to buy luxury cars, watches, and real estate,” said Matthew Axelrod of the US Department of Commerce’s Bureau of Industry and Security.
“What they don’t show in the movies though is the painstaking work it takes by domestic and international law enforcement, working closely with industry partners, to take down such a brazen scheme and make an arrest like this happen.”
Mr Wang faces a maximum penalty of 65 years in prison if convicted.
16 notes
·
View notes
Text
Round 3!
If you recognize the movies hiding behind the decoy titles, please do not give identifying details about them in the notes.
Movie n°1: Where we go, we don't need grass
So there's this dude, right? Typical Reddit user, sells pirated movies and junk, DESPERATELY needs to touch grass. Anyway, he's a true crime junkie and is obsessed with this ongoing case about, you guessed it, another cybercriminal. And wouldn't you know it, the cybercriminal contacts him! Dude gives the protagonist some sorta drug and all of a sudden, Mr. Protag is seeing some serious crap. He meets Cybercriminal and his gang of followers, who all, like, worship him except the hot girl and a dude with a goatee. Goatee regrets taking the drug and doesn't want to see all this crap anymore, so he seeks help from Protag's old boss. Goatee tells Bossman some gossip about Cybercriminal and co, and the gang ends up breaking up because of it. Protag and Girl (I swear, she's like the only girl in the movie except for a prostitute and an old lady who trains psychic children (the psychic children aren't relevant to the plot, really)) end up having to break Cybercriminal out of jail because the gossip Goatee gave Bossman ended up revealing his location, and whoops, yeah he's a wanted criminal, right. By the end, Girl practically worships Protag, too, the two of them commit serial murder, and it's implied they live happily ever after? I think?
Movie n°2: The real eldritch horror was in you all along
The leader of an isolated community, which lives in fear and reverence of the god they serve, is consumed with envy when a newcomer arrives who impresses the people with advanced outside technology and gains the favor of their deity. After alienating his people in an attempt to win back his god's love that seemingly ends in the manslaughter of the newcomer, the leader is surprised by his rival and they are both stranded in the outside world. Kidnapped by a sadistic torturer and his attack dog, the newcomer has an existential breakdown when he realizes his entire past is false implanted memories, while the leader has a crisis of conscience and rallies the mutilated prisoners to escape their torment.
21 notes
·
View notes
Text
Malicious Actors Exploit YouTube for Phishing, Malware, and Scams

YouTube has emerged as a new battleground for cybercriminals to launch phishing attacks, distribute malware, and propagate fraudulent investment schemes, according to a report from security researchers at Avast. The report sheds light on the growing threat of malicious actors exploiting the popular video platform to target unsuspecting users.
Deepfake Videos and Cryptocurrency Scams
Researchers specifically highlighted using Lumma and RedLine malware for phishing, scam landing pages, and malicious software distribution. YouTube acts as a traffic distribution system, directing users to these malicious sites and pages, and supporting scams of varying severity.
Moreover, the report uncovered a concerning rise in deepfake videos on the platform. These realistic but fake videos mislead viewers with fabricated people or events, spreading disinformation. Avast found multiple accounts with over 50 million subscribers each that were compromised and hijacked to spread cryptocurrency scams reliant on deepfake videos. These videos feature fake comments to deceive other viewers and contain malicious links.
Exploitation Tactics on YouTube
The researchers observed five different ways YouTube can be exploited by threat actors:
- Personalized phishing emails to YouTube creators, proposing fake collaboration opportunities to gain trust before sending malicious links.
- Compromised video descriptions containing malicious links, tricking users into downloading malware.
- Hijacking YouTube channels and repurposing them to spread threats like cryptocurrency scams.
- Exploitation of software brands and legitimate-looking domains with fraudulent websites loaded with malware.
- Creating videos using social engineering techniques that guide users to allegedly helpful tools that are malware in disguise.
Protective Measures and Cybersecurity Awareness
Avast credits its scanning capabilities with protecting more than 4 million YouTube users in 2023 and approximately 500,000 users in the first quarter of this year from these threats.
Trevor Collins, a WatchGuard Network security engineer, emphasizes the importance of companies and security leaders preparing their teams and organizations for these threats. "Regular education is essential. Make people aware that there are scammers out there doing this," Collins says. "In addition, train and reassure them that it's OK to notify either their security team or other people within the company if they've gotten an unusual request — for instance, to provide login credentials, move money, or go buy a bunch of gift cards — before acting on it."
As cybercriminals continue to exploit popular platforms like YouTube, individuals and organizations must remain vigilant, prioritize cybersecurity awareness, and implement robust security measures to protect themselves from phishing, malware, and scams.
Read the full article
3 notes
·
View notes
Text
Exploring the Depths: Active Directory Penetration Testing and the Enigma of Kerberos
Introduction
In the world of cybersecurity, staying one step ahead of potential threats is paramount. To safeguard an organization's sensitive information and network resources, it's crucial to regularly assess vulnerabilities and weaknesses. One potent approach is Active Directory (AD) penetration testing, which is an essential part of assessing and fortifying network security. This article delves into the intricacies of Active Directory penetration testing and the often elusive realm of Kerberos authentication.
Active Directory Penetration Testing: Unearthing Vulnerabilities
Active Directory, the cornerstone of identity management in Windows environments, serves as a centralized repository for user and system information, including authentication data. For cybercriminals, compromising AD can open the doors to a treasure trove of sensitive information. To counter this threat, organizations employ penetration testing to simulate real-world attacks and identify vulnerabilities.
Goals of Active Directory Penetration Testing
Identify Weak Passwords: One of the most common vulnerabilities is weak or easily guessable passwords. Penetration testers aim to uncover users with weak passwords and prompt them to strengthen their credentials.
Discover Misconfigured Permissions: Unauthorized access to resources can result from misconfigured permissions. Penetration testing assesses whether users have permissions that they shouldn't, potentially exposing sensitive data.
Locate Unpatched Systems: Outdated systems are susceptible to known vulnerabilities. Identifying and patching these systems is a critical goal of penetration testing.
Assess Kerberos Authentication: Active Directory relies heavily on Kerberos for secure authentication. Understanding Kerberos is essential for a thorough AD penetration test.
Kerberos: The Protector of Authentication
Kerberos, a network authentication protocol, plays a pivotal role in securing Active Directory environments. Named after the mythological three-headed dog guarding the gates of Hades, Kerberos acts as a guardian for network communication. Understanding how it works is vital for both defenders and attackers.
The Key Concepts of Kerberos
Authentication Tickets: In Kerberos, authentication occurs through tickets. A Ticket Granting Ticket (TGT) is obtained during initial authentication, and this TGT is used to request access to various resources without re-entering credentials.
Principle of Need to Know: Kerberos enforces the principle of "need to know." A user can access only the resources for which they have tickets, reducing the risk of unauthorized access.
Realms and Trust: In a multi-domain environment, Kerberos realms establish trust relationships between domains. Trust enables users from one domain to access resources in another.
Encryption: Kerberos relies on encryption to protect sensitive information, such as passwords and tickets. Encryption keys are generated dynamically during authentication.
Penetration Testing Kerberos: A Delicate Balancing Act
Penetration testing for Kerberos authentication involves a delicate balancing act between assessing security measures and not disrupting normal operations. Here are some critical aspects of Kerberos-focused penetration testing:
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak or vulnerable user accounts. Penetration testers attempt to retrieve Authentication Service (AS) tickets without the need for valid login credentials. This technique targets accounts with pre-authentication disabled, making them vulnerable to brute-force attacks.
2. Pass-the-Ticket Attacks
Pass-the-Ticket attacks involve stealing Ticket Granting Tickets (TGTs) from compromised systems. Attackers can then use these stolen TGTs to gain unauthorized access to other network resources. Penetration testing assesses the organization's ability to detect and defend against such attacks.
3. Golden Ticket Attacks
Golden Ticket attacks involve forging TGTs, effectively granting attackers unlimited access to the domain. Penetration testers may attempt to create Golden Tickets to evaluate the AD's resilience against this advanced attack.
4. Silver Ticket Attacks
Silver Tickets are used for unauthorized access to specific services or resources. A penetration test may focus on creating Silver Tickets to assess the AD's ability to detect and prevent such attacks.
10 notes
·
View notes
Text
The 5 Reasons Why You Need a VPN in 2024 - Technology Org
New Post has been published on https://thedigitalinsider.com/the-5-reasons-why-you-need-a-vpn-in-2024-technology-org/
The 5 Reasons Why You Need a VPN in 2024 - Technology Org
VPNs, or virtual private networks, are fast becoming an essential for the majority of people who value their privacy online. However, there are so many more benefits to using one than just security – from online gaming to protection against data breaches.
VPN software – illustrative photo. Image credit: Dan Nelson via Unsplash, free license
Secure Your Data
Without the use of a VPN, any activity undertaken on the internet can be tracked by third parties, like an internet provider, or even by insidious hackers or cybercriminals. This means that sensitive information like passwords or bank details could be seen by unwanted eyes. VPNs stop this from happening by encrypting all information, private or otherwise. The threat of third parties accessing your data is particularly high when using public Wi-Fi, such as in an internet cafe or library, so it’s recommended to always use a VPN when in these situations.
Enhance Online Gaming
Depending on where you are in the world, there may be certain games or sites that are not available in your country, which is where VPNs come in. By no longer being trackable via location, virtual private network users are free to access a different region’s game selection, such as online casinos. For example, Lucky Block is a VPN friendly casino that can be reached from anywhere, and offers users a secure and immersive gaming experience.
Change Your IP Address
Every time we access the internet, our IP address can be utilized to track our identities and locations. The main reason for this is so for future relevant ad targeting, which many want to avoid. In this case, using a VPN is essential, as any data is routed through a different IP address, which cannot be linked to any personal information.
Online Privacy
Protecting online privacy is paramount to so many of us these days, with stories of cyber attacks and hacking constantly in the news. A VPN is one of the easiest ways to ensure that what you do online stays private, and is not open to the many interested parties. An internet service provider is the entity most likely to pry on data and sell it to commercial corporations or even government institutions. These groups will then use it to inform marketing strategies or to learn more about certain demographics. Through encrypting data with a VPN, users can ensure that their information is not being sold without their consent.
Avoid Bandwidth-Throttling
You may not have heard of bandwidth-throttling, but you’ve almost certainly experienced it. It is the practice of an internet service provider deliberately slowing down bandwidth when their customer is on a certain website or using a particular service. There are many reasons for it, such as going over a data cap or congestion, but regardless of this it’s something that the majority want to avoid. Using a VPN means that your traffic is encrypted, and can therefore bypass any limitations set by a provider.
#2024#casino#change#cyber#cyber attacks#cybercriminals#data#Data Breaches#details#Experienced#eyes#Future#game#games#gaming#Government#hackers#hacking#identities#Internet#it#Learn#Marketing#network#networks#News#One#online privacy#Other posts#passwords
0 notes
Text
Cybercriminals Exploiting Microsoft's Quick Assist Feature in Ransomware Attacks

Source: https://thehackernews.com/2024/05/cybercriminals-exploiting-microsofts.html
More info: https://www.microsoft.com/en-us/security/blog/2024/05/15/threat-actors-misusing-quick-assist-in-social-engineering-attacks-leading-to-ransomware/
3 notes
·
View notes
Text
The Dark Web: What is it and Why Should You Care?
The term “Dark Web” has become increasingly common in recent years, but what exactly is it? In simple terms, the Dark Web refers to a portion of the internet that is not indexed by search engines and can only be accessed through special software. This allows for a degree of anonymity and privacy that is not possible on the regular internet.
While the Dark Web is not inherently illegal or malicious, it is often associated with criminal activity. This is due to the fact that the anonymity it provides can be used by individuals and groups to engage in illegal activities such as drug trafficking, human trafficking, and the sale of stolen goods. It is also a haven for hackers and cybercriminals who use it to buy and sell malware, exploit kits, and other tools of the trade.
But it’s not all bad news. The Dark Web is also home to a number of legitimate uses. For example, journalists and activists in repressive regimes may use the Dark Web to communicate and share information without fear of retribution. Whistleblowers may also use it to leak sensitive information without being identified. Additionally, some individuals may simply use it for privacy reasons, such as to browse the web without being tracked by advertisers or governments.
So, why should you care about the Dark Web? Well, even if you have no interest in engaging with it yourself, it is still important to be aware of its existence and potential dangers. Hackers and cybercriminals can use the Dark Web to buy and sell your personal information, such as credit card numbers and login credentials. They can also use it to launch attacks on websites and services, causing disruptions and potentially exposing sensitive data.
Fortunately, there are steps you can take to protect yourself. First and foremost, it is important to practice good cybersecurity hygiene, such as using strong, unique passwords and enabling two-factor authentication. You should also be cautious when clicking on links or downloading attachments, even from sources you trust. Finally, consider using a virtual private network (VPN) to encrypt your internet traffic and protect your privacy.
In conclusion, the Dark Web is a complex and often misunderstood aspect of the internet. While it can be used for both legal and illegal purposes, it is important to be aware of its potential dangers and take steps to protect yourself online. Stay safe out there!
#DarkWeb#InternetPrivacy#Cybersecurity#OnlineSafety#Anonymity#TorBrowser#VPN#Hackers#Cybercrime#Whistleblowers#Journalism#Activism#IllegalActivities#PersonalInformation#DataPrivacy#DataSecurity#OnlineThreats#OnlineProtection#DigitalSecurity#DarkWebExplained#DigitalPrivacy#DigitalAnonymity#DigitalFreedom#TorNetwork#OnionRouting#informatology
43 notes
·
View notes
Text
Anyone with an iPhone or Android should turn their device on and off once a week, officials say - to protect them from hackers.
***Note, their headline says both, Android and Apple. Yet this title just says iPhone. It’s for both.
2 notes
·
View notes
Text
Last week, WIRED published a deep-dive investigation into Trickbot, the prolific Russian ransomware gang. This week, US and UK authorities sanctioned 11 alleged members of Trickbot and its related group, Conti, including Maksim Galochkin, aka Bentley, one of the alleged members whose real-world identity we confirmed through our investigation. Coincidence? Maybe. Either way, it's a big deal.
In addition to the US and UK sanctions, the US Justice Department also unsealed indictments filed in three US federal courts against Galochkin and eight other alleged Trickbot members for ransomware attacks against entities in Ohio, Tennessee, and California. Because everyone charged is a Russian national, however, it is unlikely they will ever be arrested or face trial.
While Russian cybercriminals typically enjoy immunity, the same may not remain true for the country’s military hackers. The lead prosecutor of the International Criminal Court (ICC) says the ICC will begin pursuing charges for cyber war crimes. The prosecutor, Karim Khan, did not name Russia, but the move follows a formal petition from the Human Rights Center at UC Berkeley’s School of Law asking the ICC to prosecute Russia’s Sandworm hackers for war crimes. Part of Russia’s GRU military intelligence agency, Sandworm is responsible for causing blackouts in Ukraine, the only known instances of cyberattacks shutting down an electrical grid. Sandworm also released the NotPetya malware against Ukraine, which ultimately spread globally and caused an unprecedented $10 billion in damages worldwide.
Russia is far from the only country that engages in offensive cyberwar tactics. China-backed hackers have repeatedly targeted the US and other countries, and they may be getting some help finding unpatched vulnerabilities. A Chinese law passed in 2022 demands that any network technology company operating in the country share details about vulnerabilities in its products with the Chinese government within two days of their discovery. Information about these vulnerabilities may then be shared with China’s hackers. It’s unclear how many Western companies comply with the law or provide enough information to allow Chinese hackers to exploit the products’ flaws.
Speaking of Chinese hackers, Microsoft this week finally explained how China’s state-sponsored hackers managed to steal a cryptographic key that allowed the attackers to successfully access the Outlook email accounts of at least 25 organizations, including US government agencies. According to Microsoft, the hackers broke into the account of a company engineer using token-stealing malware. They then used that account to access a cache of crash data that accidentally contained the signing key they then stole and used to go on an Outlook hacking spree. None of this was supposed to be possible, and Microsoft says it has corrected several flaws in its systems that allowed the attack to happen.
Before he died in a mysterious plane crash last month following an attempted coup against Russian president Vladimir Putin, Yevgeny Prigozhin wasn’t just the leader of the Wagner Group mercenaries. He was also the head of the notorious Internet Research Agency (IRA), a Russian outfit responsible for widespread disinformation campaigns. While the IRA was reportedly shut down, new research shows that pro-Prigozhin trolls continue to push his agenda. Many of the accounts spreading disinformation on X (formerly Twitter) have been banned. But since when has that stopped them?
Elsewhere, we explained how prompt injection attacks against generative AI chatbots like ChatGPT take advantage of a flaw that’s difficult to fix. We detailed how hard it is to opt out of allowing Facebook to use your data to train its AI. We have a rundown on Proton Sentinel, a suite of tools that are similar to Google’s offerings but with a strong emphasis on privacy and security. We also co-published a story with The Markup into Axon’s quest to build Taser-armed drones. And we got the inside scoop on a meeting between top US spies and civil liberties groups over Section 702 of the Foreign Surveillance Intelligence Act, which is set to expire at the end of the year.
But that’s not all. Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
Your New Car Is a Privacy Nightmare
Car companies are collecting and selling extremely detailed personal data from drivers who have no real way to opt out, a new report from the Mozilla Foundation found. Researchers spent hundreds of hours studying 25 privacy policies for major car brands and found that none of them met the foundation’s minimum standards around privacy and security.
According to the report, modern cars, stuffed to the roof with sensors, collect more information about you than just about any other product in your life. They know where you go, what you say, and how you move your body. Nissan’s privacy policy, for example, allows the company to collect and share drivers’ sexual activity, health diagnosis data, and genetic information, according to the report.
Eighty-four percent of the brands that researchers studied share or sell this kind of personal data, and only two of them allow drivers to have their data deleted. While it is unclear exactly who these companies share or sell data to, the report points out that there is a huge market for driver data. An automotive data broker called High Mobility cited in the report has a partnership with nine of the car brands Mozilla studied. On its website, it advertises a wide range of data products—including precise location data.
This isn’t just a privacy nightmare but a security one. Volkswagen, Toyota, and Mercedes-Benz have all recently suffered data leaks or breaches that affected millions of customers. According to Mozilla, cars are the worst category of products for privacy that they have ever reviewed.
Update Your iPhone: Apple Fixes No-Click Zero-Days
Apple has just released a security update to iOS after researchers at Citizen Lab discovered a zero-click vulnerability being used to deliver Pegasus spyware. Citizen Lab, which is part of the University of Toronto, is calling the newly discovered exploit chain Blastpass. Researchers say it is capable of compromising iPhones running the latest version of iOS (16.6) without the target even touching their device. According to researchers, Blastpass is delivered to a victim’s phone through an iMessage with an Apple Wallet attachment containing a malicious image.
The Pegasus spyware, developed by NSO Group, enables an attacker to read a target’s text messages, view their photos, and listen to calls. It has been used to track journalists, political dissidents, and human rights activists around the world.
Apple says customers should update their phones to the newly released iOS 16.6.1. The exploit can also attack certain models of iPads. You can see details of the affected models here. Citizen Lab urges at-risk users to enable Lockdown Mode.
North Korean Hackers Target Security Researchers Again
North Korea-backed hackers are targeting cybersecurity researchers in a new campaign that is exploiting at least one zero-day vulnerability, Google’s Threat Analysis Group (TAG) warned in a report released Thursday. The group did not provide details about the vulnerability since it is currently unpatched. However, the company says it is part of a popular software package used by security researchers.
According to TAG, the current attack mirrors a January 2021 campaign that similarly targeted security researchers working on vulnerability research and development. Like the previous campaign, North Korean threat actors send researchers malicious files after first spending weeks establishing a relationship with their target. According to the report, the malicious file will execute “a series of anti-virtual machine checks” and send collected information—along with a screenshot—back to the attacker.
Georgia DA in Trump RICO Case Gets Doxxed
In order to shield prospective jurors from harassment, District Attorney Fani Willis asked the judge in Donald Trump’s racketeering trial to prevent people from capturing or distributing any sort of image or identifying information about them. The motion, filed in Fulton County Superior Court on Wednesday, revealed that immediately after the indictment was filed, anonymous individuals on “conspiracy theory websites" had shared the full names, ages, and addresses of 23 grand jurors with “the intent to harass and intimidate them.”
Willis also revealed that she had been the victim of doxxing when the personal information of her and her family—including their physical addresses and “GPS coordinates”—was posted on an unnamed website hosted by a Russian company. Willis, who is Black, had previously disclosed that she faced racist and violent threats after the announcement of her investigation into the former president.
18 notes
·
View notes