#geolocation tool
Explore tagged Tumblr posts
Link
Bulk GEO IP Locator - Find Geolocation Data for Multiple IPs
#ip checker#ip locator#geo ip#bulk IP addresses#Bulk GEO IP Locator#geolocation data#multiple IPs#IP lookup#geolocation tool#IP geolocation#IP address location
0 notes
Text
This comprehensive guide is your roadmap to conquering the global digital landscape through effective international SEO strategies. Whether you're a multinational corporation or a growing startup with global ambitions, this guide provides invaluable insights into leveraging SEO to expand your reach, connect with international audiences, and achieve online success.
#International SEO#Multilingual SEO#Global SEO strategies#International keyword research#International SEO best practices#Hreflang tags#Geolocation SEO#International content optimization#International link building#Global SEO for e-commerce#Local SEO for global websites#International SEO analytics#International SEO tools
1 note
·
View note
Text
Useful (not AI) Tools for Writing
For years I've been compiling a list of useful tools for writing (fiction and non-fiction) and I thought it might be fun to share it.
What am I missing? What do you use and love? I'd love to keep building this list!
Historical Research
General plug: Librarians!!! They want to help you.
Search for words/signs in Brooklyn
Encyclopedia of Hair
Underwear, a history
Newspapers.com
Historical (and modern) meeting minutes
Find a grave
Political TV Ad archive
Oral Histories
Columbia
National Archives
MoMA
Archives of American Art
The Oral History Review
Words
Wordnik
Dictionary of American Regional English
Scrivener built in name generator
Lose the very
Scene Setting / Images
Animals & Plants by geolocation (also good for general scene setting)
Flickr world map
Past weather by zip code
Google Maps streetview / Google Earth
General Inspiration
Oblique Strategies
Worldbuilding
Tarot decks (my personal favorite is this one)
The Thing from the Future
The Picture Game
Misc
Data is Plural -- a newsletter full of interesting datasets
#writing#resources#writing resources#fiction writing#non-fiction writing#finding stuff#librarians are the best people in the world#archives#historical research#you don't need AI to help you write
193 notes
·
View notes
Text
Belarusian Man Constructs and Sets Sail in a Boat Made Entirely of Ice

Ivan Karpitsky, a Minsk resident, is well-known in Belarus for his passion for ice and snow sculptures. His name first made headlines in 2020 when photos of his ice violin went viral on social media. Since then, he has kept himself busy each winter with increasingly ambitious projects, but this year he truly outdid himself with a stunning and functional boat made entirely of ice.
Photos and videos shared on his Instagram page show Karpitsky meticulously carving and chiseling blocks of ice to create his impressive masterpiece, showcasing his remarkable dedication and skill.

Little technical information is available about Ivan's ice boat, aside from what can be seen in the photos and videos he has shared on social media. According to geolocation data, the boat was built along the shores of Tsnyanskoe Reservoir, an artificial lake north of Minsk near the former village of Tsna-Yodkovo.
In the footage, the artist is shown cutting rectangular blocks of ice and bonding them together with water. He then chisels the frozen surface of the lake to carve out the base of the boat, demonstrating his resourcefulness and ingenuity.

Karpitsky employed a variety of power tools to craft intricate ice panels, which he carefully slid between the larger ice blocks. He also created a rotating ice rudder that, while non-functional in steering the vessel, adds a significant aesthetic appeal. Additionally, the artist designed two detachable paddle wheels that can be mounted at the back of the boat and connected to a land-based power source to create the illusion of propulsion.
The Belarusian’s ice boat has gone viral on social media, drawing widespread attention. Karpitsky has already been inundated with requests for custom-made ephemeral creations similar to his ice boat. However, the self-taught artist has so far declined all such commissions.
23 notes
·
View notes
Text
I like the DC x DP AUs where the Justice League and Amity Park (and Elmerton by proxy) never noticed each other due to an information blackout. I also find it neat when the idea's taken a step further.
For example, what if the government built Amity Park on insanely haunted land on purpose? Let's say, years ago, the whole LoA and Ra's Al Ghul situation made the U.S government curious about Lazarus water. They wished to find it's source in order to harvest it themselves.
The U.S preferred to avoid Lazarus pools that already existed to prevent conflict with the LoA. Instead, they decided to seek out the perfect location to "dig a well" of their own.
GIW scientists established that Lazarus water, a heavily condensed version of ectoplasm, was linked to ghosts and other ectoplasmic entities. They also observed that these entities are highly attracted to human populated areas.
This gave them the idea to settle a whole population of people on a liminal hotspot to lure ecto entities into the human realm. With the Anti Ecto Acts in place, the GIW were be free to capture ghosts and other creatures for their ectoplasm. The end goal was for the Fenton portal to be used as a well to harvest mass quantities of ectoplasm directly from the Infinite Realms.
How might this work for Amity Park and it's place in the world?
The information blackout is heavier outside the Amity-Elmerton territory than inside. Amity residents are only cut off from info that could threaten the government project (EX: the existence of real life superheroes, the Meta Protection Acts, certain major events, etc.).
All devices that enter the Amity-Elmerton territory are unable to send or receive video/pics of the above "blocked" topics. In fact, it's difficult for social media users within that territory to connect with any posts or profiles from outside unless they look hard enough.
Amity residents are still allowed to travel, but airline ticket prices are jacked ridiculously high, especially for specific destinations (i.e: common superhero locations) to deter those residents from going there. GPS devices and maps bought in Amity or Elmerton are also set to misdirect users away from these same locations if they opt for a road trip.
Most Amity-Elmerton residents hardly bother leaving at all since there's a hefty fee for crossing beyond a set perimeter. They've all been lead to believe this is a normal part of traveling in the Midwest.
To everyone outside the Amity-Elmerton area, that area is virtually non-existent. It's not listed on any map, globe, or basically any public geolocation tool outside those provided in Amity (not even Google Maps). The only hints of it existing are in certain forms of documentation, such as birth certificates and tax forms. Even then, these people are hard to come by.
At most, Amity Park is a little known myth where people occasionally debate on it's existence.
In general, the government limiting Amity-Elmerton residents access to outside info while giving them just enough to stave off suspicion.
#dc x dp#headcanon#au#danny phantom#dc universe#This may or may not change later#It's a spur of the moment brain dump#I just like Danny being flabbergasted that superheros and aliens exist#meanwhile the JL are equally flabbergasted that someone can still be out of the loop after all the world ending catastrophies they prevented#Upon first meeting they're like “This meta kid doesn't even know what a meta is”#And then later Danny and a JL member compare maps and notice some glaring inconsistencies that just complicate everything#I wonder how long it'd take them to rule out alternate dimensional travel
81 notes
·
View notes
Text
youtube
Digital innovations can elevate citizen science as an internationally recognized source of data used by policymakers and as a career opportunity for young people
The Enviro-Champs are a group of over a thousand people using citizen science to draw attention to water quality issues in South Africa.
“We work with the Enviro-Champs to support us on the ground to collect data on rivers”, said Futhi Vilakazi of uMngeni-uThukela Water.
Research by scientists at the International Water Management Institute (IWMI) and GroundTruth have shown that simple visual tools such as charts to identify and count lifeforms in rivers, or acrylic tubes to identify the clarity of water, can provide comparable results to laboratory tests.
Groups like the Enviro-Champs and other citizen scientists have readily adopted these tools, demonstrating the unique contribution that can come from co-engaged local communities. Citizen scientists can collect more data over longer periods, across large regions or with greater intensity. In one study*, volunteers monitored how water pollution from wastewater treatment works varied every day between 2012 and 2019. Less than two years after the treatment plant was made aware of this monitoring, their compliance with regulations shot up from zero to 60-70%.
Nonetheless, citizen science comes with its own challenges. The process remains highly manual and often paper-based, relying on the selfless dedication of volunteers to improve local issues. Although the community aspect can be a powerful motivator to local authorities, the data they collect are often seen as being too unreliable to use for management.
Through the CGIAR Initiative on Digital Innovation, IWMI, Groundtruth and key local partners are collaborating to develop technological upgrades that can transform the impact of citizen science.
This includes a smartphone app to digitize, geolocate and upload citizen science river health surveys, using the mini stream assessment scoring system (miniSASS), to an online platform. There have been >350 river health surveys submitted by citizen scientists in 2024. An image recognition AI function was created to recognize lifeforms in the river that indicate water quality, helping verify the data in real time.
#solarpunk#solar punk#community#indigenous knowledge#africa#jua kali solarpunk#citizen science#digital innovation#apps#smartphones#science#Youtube
6 notes
·
View notes
Text
Violet Miller at Chicago Sun-Times:
In the wake of President-elect Donald Trump’s reelection, advocates for transgender people in Illinois are scrambling to strengthen the state protections they’ve created, while some trans Midwesterners consider moving to states with shield laws for safe harbor. State Rep. Kelly Cassidy told the Sun-Times there has been a coalition effort of state lawmakers to protect trans and reproductive health care access since the U.S. Supreme Court’s decision to overturn Roe v. Wade leaked in 2022. Now, they’re looking closely at Project 2025 — a conservative policy playbook created by the Heritage Foundation — and Trump policy proposals and “evaluating what further protections we can enact in the coming months,” a spokesperson for Gov. JB Pritzker said. One gap the coalition identified is medical data privacy and the use of geolocators to track people who visit health care facilities, which Cassidy said she’s confident will be fixed before the fall legislative session ends. “There’s a hole in that [legislative] shield, and that’s data privacy, so that’s the top priority,” Cassidy said.
Protections for reproductive rights and gender-affirming care were enshrined in state law in January 2023, putting Illinois on the side of people who risk prosecution by traveling to the state for treatment and also protecting the licenses of Illinois doctors who provide care that’s illegal elsewhere. The Illinois Human Rights Act also protects against discrimination based on gender identity. In July, the Legislature gave Illinois judges the tools to help people change their names and gender markers on out-of-state documents. But many of the threats made by Agenda47, the Trump campaign’s outline for the next four years, and Project 2025 would undermine these by circumventing existing protections.
“If a national ban [on gender-affirming care] passed, that’s our worst-case scenario,” Cassidy told the Sun-Times on Friday. “None of our laws will matter.” The documents outline plans to end civil rights protections for LGBTQ+ people, remove doctors who provide gender-affirming care from Medicare and Medicaid coverage, and withhold funds from schools that protect the rights of trans students, among other things.
[...] Fourteen states and Washington, D.C., have shield laws for gender-affirming care, though Minnesota and Illinois are the sole havens for displaced trans people in the Midwest.
With Donald Trump's victory and the toxic Project 2025 and Agenda 47 looming, Illinois is seeking to further strengthen protections for trans people, and that trans people residing in anti-trans states such as Missouri and Indiana are seeking safe harbor from attacks on their identity and expression by moving to Illinois.
#Illinois#Transgender Safe Refuge#Transgender Rights#Transgender#J.B. Pritzker#Kelly Cassidy#Illinois Politics#Agenda 47#Project 2025#LGBTQ+#Gender Affirming Healthcare#Shield Laws
8 notes
·
View notes
Text
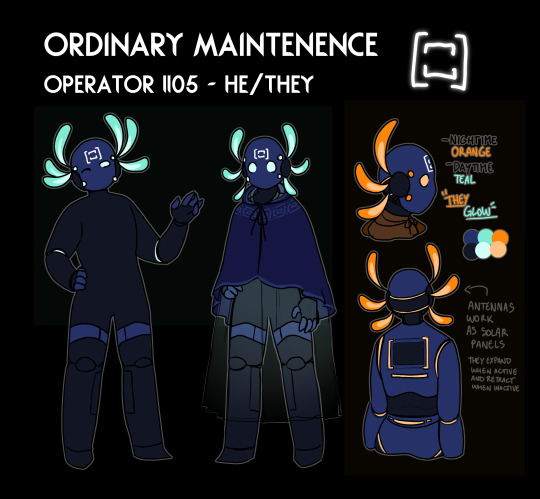
I've got nothing to post right now so have my oc, hes part of a subdivision of smaller iterators (in the sense of robot-like creatures) able to think of themselves (but are mobile) aka Operators :D
more rambling about Operators below :)
Operators serve as a way to persue small tasks between closeby groups, created during gen 2 of Iterators they serve as a ''fix it all'' having a set manual encoded in them which provides them with the necessary tools to fend for themselves and geolocate closeby structures which provide energy.
Being off the strings for them it means that they function off few neurons which they carry inside their body (which keeps them alive and stores some necessary stuff + recently given commands + records important events during their travels from one facility to the other). They recharge via a chargeble battery installed in their system by connecting it to anything remotely mechanical, such as shelters, karma gates (which they are able to access unless theyre karmically imbalanced or arent given permission to), communication stations/arrays and so on.
They do not have a great memory, they work on a limited one when off-field and when they reach the closest iterator they will connect to their structure, offering a scan of their can and offering to solve any issues they are able to fix within it, but most important they will empty their memory (think of outside storage) in order to recieve a new command/order/task. Their main purpose is to serve under the rules of the ancients and help with upkeeping iterator groups local to them or following their orders which may change from anything such as pearl collection, transferring data, rearranging faulty memory conflux structures, eliminate any threatening bodies to their host iterator can and so on!
[cough, if they find mobile rot even if their host iterator tells them not to kill it they will go on the violent route to eliminate the rot or mold]
Greatly respectful of ancients and senior iterators they will greatly follow orders given by seniors and other iterators, doing small tasks for them and serving low range messenger/support friend if you will. They are shorter than most iterators (with my guy being shorter than five pebbles) but more resistant and resilient than the mid iterator puppet plus a lot stronger!
Usually theres anywhere between none to five in groups, depending on their size and how old they are.
IDK they have some sort of weapon which they probably either carry around or its part of their design, mine has claws.
Their main rules are:
-follow iterator wishes
-ensue their safety
-dont mess with the enviroment (less prone to violence towards organic creatures)
ABOUT MY OC TE HEE
Ordinary Maintenances is under Chronicler of Methologies (an archivist iterator which belongs to @nemofil and they work under pearl collection duty most of the time, why most of the time?
Scavengers think of Ordinary Maintenance as a very very shiny object, so they trade him around until he menages to actually get up and leave their premises which is sadly not that successful. Seeing as Chronicler is quite a pacifist and feel bad about Scavenger he will often do nothing (not as he can do it) about it, leaving often time OM being traded around for shiny stuff.
Im not sure how i wanna kill them off but oh well, hes quite the resistant one, surviving through an iterator attacking them, being a chewtoy sometimes on sundays, and witnessing some pretty violent scav conflicts hes quite the silliest :)
stay in pieces chronicler, may you be loved by him as yk bros do (/j)
86 notes
·
View notes
Text
Engineering Development Group-CIA malware and hacking tools are built by EDG (Engineering Development Group), a software development group within CCI (Center for Cyber Intelligence), a department belonging to the CIA's DDI (Directorate for Digital Innovation). The DDI is one of the five major directorates of the CIA. The EDG is responsible for the development, testing and operational support of all backdoors, exploits, malicious payloads, trojans, viruses and any other kind of malware used by the CIA in its covert operations world-wide. The increasing sophistication of surveillance techniques has drawn comparisons with George Orwell's 1984, but "Weeping Angel", developed by the CIA's Embedded Devices Branch (EDB), which infests smart TVs, transforming them into covert microphones, is surely its most emblematic realization. The attack against Samsung smart TVs was developed in cooperation with the United Kingdom's MI5/BTSS. After infestation, Weeping Angel places the target TV in a 'Fake-Off' mode, so that the owner falsely believes the TV is off when it is on. In 'Fake-Off' mode the TV operates as a bug, recording conversations in the room and sending them over the Internet to a covert CIA server. As of October 2014 the CIA was also looking at infecting the vehicle control systems used by modern cars and trucks. The purpose of such control is not specified, but it would permit the CIA to engage in nearly undetectable assassinations. The CIA's Mobile Devices Branch (MDB) developed numerous attacks to remotely hack and control popular smartphones. Infected phones can be instructed to send the CIA the user's geolocation, audio and text communications as well as covertly activate the phone's camera and microphone. These techniques permit the CIA to bypass the encryption of WhatsApp, Signal, Telegram, Wiebo, Confide and Cloackman by hacking the "smart" phones that they run on and collecting audio and message traffic before encryption is applied.
2 notes
·
View notes
Text

Kostia Hornain Debain, from the series 'Contre-Courant', KG+ 2025
Contre-Courant, récit d’un retour aux sources
“I was born in Ukraine and spent a year in an orphanage in the city of Donetsk before being adopted by my French parents. I grew up in Paris. At the age of 20, I felt a deep need to return to my country of birth, to reconnect with my roots. But very shortly after, in February 2022, the war in Ukraine changed everything. Today, I feel like I’m going against the current.”
he decided to make the journey anyway, tracing the path in reverse from the one he took more than twenty years ago. The trip begins in Kyiv, the city he departed from to go to France, passes through Donetsk, where the orphanage was, and ends in Sejnoia, his birthplace.
It’s a spatial wandering, but also a temporal one, since the images he sees on his screen — which allow him to discover these cities — are of uncertain dates. This temporal blur appeals to him: he navigates between fiction and reality — his own imagined narrative projected onto these still-unknown places, and a tangible reality made accessible through the precision of geolocation tools.
To these images, he adds poignant accounts from Ukrainian refugees in France. These testimonies act as interludes — sudden returns to the present, as if this intimate quest also ran counter to the stream of current world events. Though one might come across a tank in a street, much of the imagery consists of landscapes, people in motion… almost like street photography evolving according to each city.
2 notes
·
View notes
Text
GIS In Our Daily Lives
The involvement of Geographic Information Systems (GIS) in our daily lives is pervasive, influencing and enhancing various aspects across different sectors. The integration of GIS into everyday activities has become integral for decision-making, planning, and optimizing resources. GIS helps city planners and transportation experts to provide them with information like maps, satellite pictures, population statistics, and infrastructure data. GIS helps them make better decisions when designing cities and transportation systems that are sustainable and good for the environment.
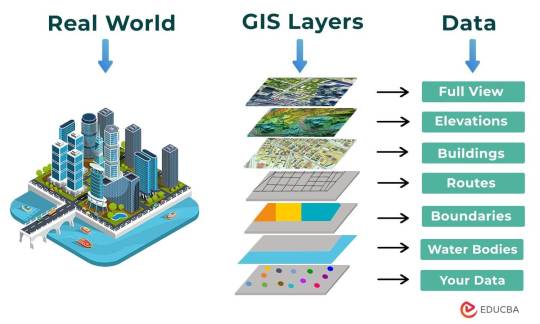
The following points elucidate the notable involvement of GIS in our daily lives:
Navigation and Location Services: GIS provides monitoring functions through the visual display of spatial data and precise geographical positioning of monitored vehicles, whereas GPS provides accurate, clear, and precise information on the position and navigation of a monitored or tracked vehicle in real-time and at the exact location.GIS is at the core of navigation applications and location-based services on smartphones. It enables accurate mapping, real-time navigation, and geolocation services, assisting individuals in finding locations, planning routes, and navigating unfamiliar areas.
E-Commerce and Delivery Services: GIS software is a powerful tool for supply chain network planning. It helps determine the optimal location for distribution centers, warehouses, or other supply facilities. GIS is utilized in logistics and delivery services for optimizing routes, tracking shipments, and ensuring timely deliveries. E-commerce platforms leverage GIS to enhance the efficiency of their supply chain and last-mile delivery processes.
Weather Forecasting and Disaster Management: Many states are using GIS dashboard to monitor the rainfall across the state, on a real-time basis, from the data shared by rain sensors installed at various locationsGIS plays a crucial role in weather forecasting and disaster management. It assists meteorologists in analyzing spatial data, predicting weather patterns, and facilitating timely responses to natural disasters by mapping affected areas and coordinating emergency services.
Healthcare Planning and Disease Monitoring: Geographic Information Systems enable the visualization and monitoring of infectious diseases. Additionally GIS records and displays the necessary information that health care needs of the community as well as the available resources and materials. GIS supports public health initiatives by mapping the spread of diseases, analyzing healthcare resource distribution, and assisting in the planning of vaccination campaigns. It aids in identifying high-risk areas and optimizing healthcare service delivery.
Social Media and Geo-tagging: GIS also helps in geotagging and other location related information in posts, it’s tools can map and visualize the spatial distribution of social media activity. This analysis can reveal trends, hotspots, and patterns in user engagement across different geographic areas. Many social media platforms incorporate GIS for geo-tagging, allowing users to share their location and experiences. This feature enhances social connectivity and facilitates the sharing of location-specific information.
Smart City Initiatives: The Geographic Information System (GIS) offers advanced and user-friendly capabilities for Smart City projects and allows to capture, store and manipulate, analyze and visualize spatially referenced data. It is used for spatial analysis and modeling. It is the cornerstone of smart city planning, enabling the integration of data for efficient urban management. It supports initiatives related to traffic management, waste disposal, energy consumption, and overall infrastructure development.
Education and Research: GIS is increasingly utilized in education and research for visualizing and analyzing spatial data. It enables students and researchers to explore geographic relationships, conduct field studies, and enhance their understanding of various subjects.

Agricultural Management and Precision Farming: Farmers leverage GIS to optimize agricultural practices by analyzing soil conditions, crop health, and weather patterns. Precision farming techniques, facilitated by GIS, contribute to increased crop yields and sustainable farming practices.

Real Estate and Property Management: In the real estate sector, GIS aids in property mapping, land valuation, and site selection. It provides real estate professionals with valuable insights into spatial relationships, market trends, and optimal development opportunities.
Tourism and Recreation: GIS enhances the tourism industry by providing interactive maps, route planning, and location-based information. It assists tourists in exploring destinations, finding attractions, and navigating efficiently.
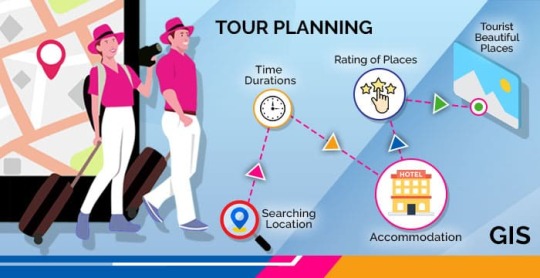
The broad and varied involvement of GIS in our daily lives underscores its significance as a technology that not only facilitates geographic data analysis but also contributes to the efficiency, safety, and interconnectedness of modern society. As GIS applications continue to evolve, their impact on daily activities is expected to further expand and refine.
#gis#architectdesign#architecture#city#education#geographic information system(gis)#geographical indication
13 notes
·
View notes
Text
Ever wondered where a photo was taken? 📸🌍
With the rise of smartphones and digital cameras, most photos are embedded with geolocation data — a hidden treasure map right in the image file! This metadata, known as EXIF, can reveal exactly where a photo was snapped, down to the coordinates. It's like a secret travel log for every picture!
Want to try it for yourself? You can extract the GPS info from any image and see it on a map. Check out this tool I found: BasicUtils Pic2Map — it’s simple, quick, and free!
Give it a go and unlock the stories behind your photos! 🌍✨
2 notes
·
View notes
Text
Separating Fact from Fiction on Social Media in Times of Conflict
In a time of crisis, social media is flooded with images, videos and bold claims. This can be useful for researchers like ourselves but overwhelming for the general public seeking the facts.
At Bellingcat, we pride ourselves on providing tools and resources for our audience to think critically about sources they find online. In this short guide, we give a few tips on what to consider when confronted with an abundance of footage and claims. Here’s how to separate fact from fiction with real, recent examples of misinformation.
1. Be Cautious
Treat all footage and claims with caution. Sometimes real footage can be attributed to false claims and vice versa. For example, in one of our latest investigations Bellingcat found that the airstrike captured in a viral video occurred near the intersection of Al-Rashid and Beirut Streets, at approximately 31.516746, 34.428689, behind the lattice tower visible in the clip and did not hit the mentioned church as claimed in posts.

The church also debunked the attack on Facebook.
The same area was attacked at a later date, on October 19, 2023, and two assembly halls on the church property were then damaged.
In the process of geolocating footage related to the viral video claiming to show the church site, Bellingcat found evidence that strikes did occur in densely populated areas in the vicinity of several schools. The amplification of the false church claim, as a result, may have obscured a real violation. You can read the full debunk here.
2. Think Critically
Particularly about big, incendiary claims. When big news stories hit, we see a lot of recycled footage posted on social media. Recycled footage is footage from other conflicts or time periods that are published as if they are from the current event.
Often details in the footage like signage or other details in the surroundings can give a clue to the true time or place the video was taken.
For example: France 24 has repeatedly debunked a video often amplified by European far-right groups, allegedly showing migrants in Calais throwing stones across a motorway. The video is actually from a protest in Israel after the police shot an Ethiopian Jew which sparked Israel’s Black Lives Matter moment in July 2019. France 24 geolocated the surroundings and the markings on the road to a highway in Israel, far away from Calais, France where the video was repeatedly claimed to have been taken.
3. Check the Source
Responsible researchers will always name the source of footage they share or analyse. Too often footage goes viral without a source—let alone an original one—listed. Be cautious if the source of the video or claim is unclear.
Simply checking the source listed can often quickly debunk any suspicious claims. TikTok videos re-shared on other platforms, for instance, usually have the original poster’s username watermarked onto the footage.

For example, in 2022 a video of an alleged news report went viral. In the video, a reporter stands in front of a line of ‘body bags’ discussing the Russian ‘military operation’ in an American accent and the caption reads “Ukranian Health Ministry: 57 dead, 169 hurt across Ukraine as Russia launches attack.” During the report, the person in the body bag behind the reporter starts to move. The video was shared with an array of claims, ranging from the dead coming back to life to assertions that the Ukrainian authorities were staging deaths to grow support for their cause. Elementary fact-checks will show any savvy individual that this footage did not show what was claimed. A quick search on Google of the reporter’s name shows that they have never reported on such an incident. A reverse image search using a screenshot from the video reveals that the news report was taken and manipulated from coverage of a climate protest in Austria in February 2022. Fake audio had been added to the video and was easily disguised by the fact the reporter’s mouth could not be seen as he/she was wearing a mask. The Associated Press originally debunked this claim and their factcheck can now be found linked to the original misleading post on Facebook.
The church also debunked the attack on Facebook.
The same area was attacked at a later date, on October 19, 2023, and two assembly halls on the church property were then damaged.
In the process of geolocating footage related to the viral video claiming to show the church site, Bellingcat found evidence that strikes did occur in densely populated areas in the vicinity of several schools. The amplification of the false church claim, as a result, may have obscured a real violation. You can read the full debunk here.
4. Remember that the Same Location Doesn’t Mean the Same Incident
Even if the footage is from the area, it doesn’t mean it is from the same event.
One simple way to check is to use Google reverse image search on video screenshots to see if they’ve been posted before.
For example, Bellingcat contributor Chris Osieck found that this video allegedly showing rocket fire in Palestine in October was indeed filmed in the Gaza Strip, but that it was from May 13, 2023.
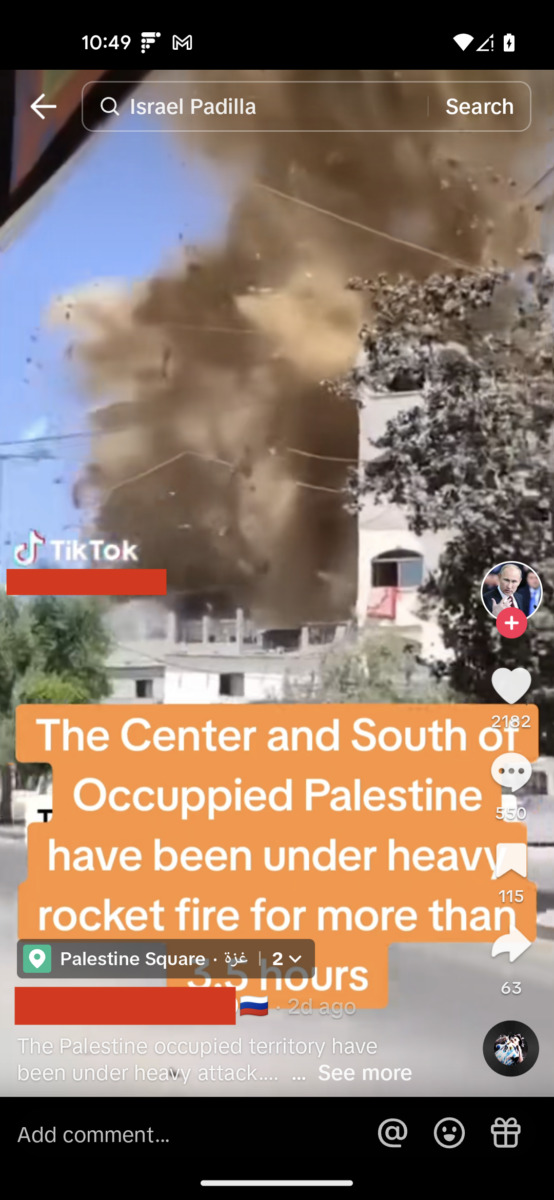
He found an earlier instance of the footage labelled as showing the destruction of the Za’anin family’s home in the same region. This attack was part of fighting that occurred in May 2023.

5. Be Savvy to Manipulation and AI Generation
When all footage or photographs connected to an event go viral, you often see accounts pop up distributing manipulated or altogether fake imagery. Free and easy to access AI-powered image generation tools have now made this type of content faster to create and more common. Although not always accurate, tools like aiornot.com can help disprove claims quickly.
For example, a video went viral in March 2022 allegedly showing Ukraine President Volodymyr Zelenskyy telling Ukrainian soldiers to “lay down their arms” and claiming that he had decided to “return Donbas” to Russian control. Many media outlets and Zelenskyy himself debunked the video. Whilst watching the video, one can see his head appears disproportionately sized in contrast to his body. His voice is also slower and deeper than in usual addresses.
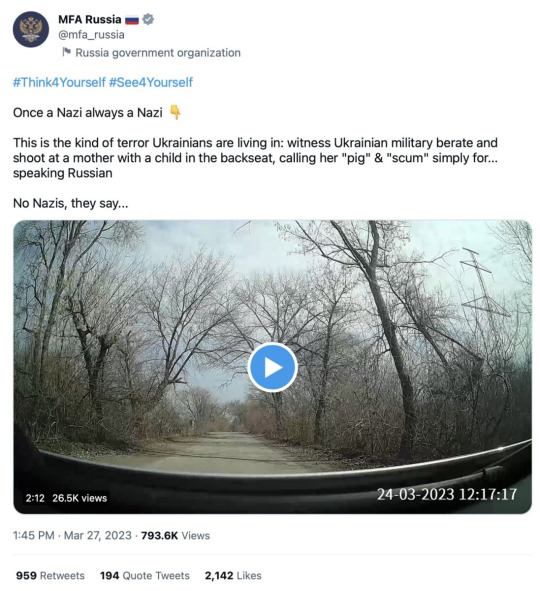
6. Be Cautious of State Actors, Which Sometimes Share Staged or Unreliable Footage
In times of conflict, it is not unknown for state actors to imply bad faith on the part of their adversaries. In some cases, staged videos appear online. For example, in March 2023, a dashcam video circulated allegedly showing a Ukrainian soldier abusing a Russian-speaking Ukrainian citizen. Pro-Russian figures and Russia’s Foreign Ministry shared the video on social media. Bellingcat and other eagle-eyed viewers, however, geolocated the footage to deep inside Russian-controlled territory. You can read the full story here.
7. Know That, Sometimes, News Organisations Get it Wrong
When you discover new claims about footage, always check for a secondary media source, ideally one that has obtained the information independently of the first source. News organisations and leading figures can sometimes use quotes from each other as sources of information (see an example that we found here) and sometimes verification steps slip through the cracks. For example, in a famous example in 2019, ABC News broadcasted a fake video on both its ‘World News Tonight’ and ‘Good Morning America’ programmes. The video was reportedly sent to them by a trusted fixer and claimed to show the Turkish military bombing Kurdish civilians in a Syrian border town. Viewers spotted that it looked incredibly similar to a video on YouTube from a Kentucky gun range called Knob Creek. The footage had been altered slightly, but the two video timelines matched. ABC issued a statement and took down the video from their broadcasting.
8. Protect Your Mental Health
Watching footage from war zones can cause trauma.
Be careful viewing unknown footage. There is almost always an abundance of highly disturbing content circulating during times of conflict.
Always ask yourself if there is a genuine reason you need to view this footage. Organisations like Bellingcat have teams of researchers trained to view such footage with therapeutic support in place to assist them. If you do find something that needs attention, you can share it with a trusted news source rather than viewing it and amplifying it yourself.
If you are an open-source researcher, you can find Bellingcat’s guide explaining ways to better protect your mental health whilst undertaking this role here. The Dart Center also has robust advice on the risk of vicarious trauma.
#disinformation#misinformation#propaganda#fog of war#fact check#bellingcat#journalism#ukraine#russia#palestine#israel
14 notes
·
View notes
Text
Just after 9 pm on an August night in 2020, Kimberly Thompson and Brian James pulled the car into a driveway in Akron, Ohio, and stepped out into a barrage of gunfire. They were shot in the legs, rushed to a hospital, and survived. But Thompson’s 20-month-old grandson, Tyree Halsell, who was still sitting in the car, was shot in the head and mortally wounded.
In the aftermath, Akron police collected video footage from the neighborhood and asked for the public’s help with identifying two men who’d been seen approaching the victims, firing, then fleeing in a truck. Within months, detectives narrowed in on a suspect, Phillip Mendoza, and obtained a search warrant for his cell phone location data from Sprint, according to court records. They also served a geofence warrant on Google, seeking information on devices whose GPS, Wi-Fi, or Bluetooth records placed them near the scene of the shooting. Neither warrant turned up any evidence locating Mendoza or his devices on the 1200 block of Fifth Avenue, where the shooting occurred, that night.
The investigation stalled until August 2022, when Akron police received a three-page report containing the evidence they’d been seeking. It came from a little-known Canadian company called Global Intelligence, which for the past several years has been selling an extraordinary service to police departments across the United States.
Global Intelligence claims that, using only open source data—public information that doesn’t require a warrant—and a suite of more than 700 algorithms, its Cybercheck system allegedly can geolocate an individual in real time or at a specific time in the past by detecting the wireless networks and access points the person’s “cyber profile” has interacted with. The company’s founder, Adam Mosher, has testified under oath that the process is entirely automated, requiring no human intervention from the time an investigator enters basic details about a case into the Cybercheck portal until the time the system produces a report identifying a suspect and their location.
If the technology works as advertised, then Global Intelligence is selling police departments previously unknown surveillance capabilities for as little as $309 a case that rival the open source tools used by national spy agencies. But a WIRED review of investigations involving Cybercheck from California to New York, based on hundreds of pages of court filings, testimony, interviews, and police records, suggests Cybercheck is a much less effective tool—one that has provided evidence in high-profile cases that was either demonstrably incorrect or couldn’t be verified by any other means.
Open source intelligence experts allege to WIRED that much of the information Cybercheck provides in its reports to law enforcement would be impossible to obtain using only open source data. Indeed, over the past several months, Global Intelligence’s work in Ohio has faded away, with prosecutors ultimately deciding not to use Cybercheck reports as evidence in several murder cases, including Mendoza’s.
“Either they’re somehow doing the Minority Report now, or somehow it’s just BS,” says Stephen Coulthart, director of the Open Source Intelligence Laboratory at the State University of New York at Albany, who reviewed Cybercheck reports and transcripts of Mosher’s testimony at WIRED’s request.
Cases Pending
During a November 2022 trial, Mosher testified that 345 different law enforcement agencies had used Cybercheck to conduct approximately 24,000 searches since 2017. WIRED identified more than a dozen cases involving Cybercheck, including 13 in which prosecutors intended to use Cybercheck reports as evidence at trial. Two of the cases in which courts allowed Cybercheck reports to be admitted as trial evidence resulted in murder convictions.
The agencies we found using Cybercheck ranged from small suburban police departments to county sheriffs and state police. The alleged crimes ranged from those related to child sexual abuse material to drive-by shootings, as well as cold cases that have haunted communities for decades. Last year, for example, the New York State Police arrested a man for murder after receiving evidence from Cybercheck that allegedly placed his cell phone at key locations on the night of the homicide, roughly 20 years ago, according to the indictment. The case is scheduled to go to trial in 2025.
While Mosher has testified on numerous occasions about Cybercheck, his explanations of what data sources the algorithms draw on and how they reach their conclusions do not fully explain Cybercheck’s ability to produce its reports. Global Intelligence did not answer WIRED’s questions about who designed Cybercheck’s algorithms or what data the company used to train them. When asked how the tool could determine that a person’s cyber profile had pinged a particular wireless network—oftentimes years after the incident occurred—an unnamed Global Intelligence employee wrote in an email: “There is no specific single source of information with regard to wireless network interactions.”
Accuracy Ratings
In 2022, more than two years after Halsell was shot and killed in Akron, Cybercheck produced a report for police that claimed Mendoza’s cyber profile had pinged two wireless internet devices located near 1228 Fifth Avenue after 9 pm. A cyber profile, from what Mosher has testified, is the amalgamation of names, aliases, emails, phone numbers, IP addresses, Google IDs, and other online identifiers that combine to create a person’s unique digital fingerprint.
Summit County prosecutors charged Mendoza with murder. But when Mendoza’s defense attorney, Donald Malarcik, dug into the Cybercheck report, he found a problem. The police department employee who entered the information into Cybercheck’s system had allegedly made a mistake: They had asked the system whether it could locate Mendoza at the scene on August 20, 2020. The shooting occurred on August 2. Cybercheck had nonetheless claimed to locate Mendoza at 1228 Fifth Avenue with 93.13 percent accuracy, even though it was on the wrong day. Stranger still to Malarcik, at some point after delivering the first report, Cybercheck produced another report. It was identical in all respects to the first report—from the MAC addresses, which are unique IDs assigned to networked devices, to the time of day when Mendoza’s cyber profile allegedly pinged them, and the accuracy rating—except it had the correct date of the shooting.
The warrants served to Sprint and Google hadn’t produced any evidence that Mendoza’s devices or accounts were at the scene. But according to Cybercheck's entirely automated algorithms, Mendoza’s cyber profile had not only been at 1228 Fifth Avenue at the time of the shooting, it had also been at the exact same location, at the exact same time of day, for the same amount of time, pinging the same wireless networks, 18 days later.
The unnamed Cybercheck employee who responded to WIRED’s questions says the company stands by the accuracy of both reports in the Mendoza case. “It is not uncommon to have the same cyber profile with the same device at a location on a different date,” they wrote.
Malarcik filed a motion where he asked the prosecutor to provide Cybercheck’s software in another case for which a report had been generated. He also subpoenaed Mosher, and hired a digital forensics expert in an attempt to review the code and the two Cybercheck reports about Mendoza. He tells WIRED that all that experts in a separate case allegedly saw were a couple hundred lines of code that created a program for searching public websites for information about a subject—nothing like the 1 million lines of code and more than 700 algorithms Mosher has testified about in pre-trial hearings.
“It was the equivalent of what you would do on a Google search,” Malarcik alleges. “What we didn’t see is the secret sauce, which [Mosher] claims is the machine learning that takes these data points and turns it into intelligence that takes a cyber profile and says it was at this location. That’s what he’s never disclosed to us.”
Mosher and Global Intelligence did not respond to WIRED’s questions about Malarcik’s claims.
Malarcik requested the court hold what is known as a Daubert hearing to determine whether Mosher’s testimony about Cybercheck’s findings was credible enough to be admitted as evidence in Mendoza’s trial. Two days before the hearing date, Summit County prosecutors decided to not use Cybercheck as evidence. Since then, the prosecutor’s office has withdrawn Cybercheck reports in three other cases, involving four men accused of murder, in which they potentially could have been presented as evidence, according to Malarcik and court records. In early August, Mendoza pleaded guilty and was sentenced to serve at least 15 years of a 15-to-20.5-year sentence.
“In the cases we had with Cybercheck that went to trial, there were those aspects that Cybercheck found that the boots-on-the-ground detectives also found,” Brad Gessner, the Summit County prosecutor’s chief counsel, tells WIRED. “Those things matched.”
In total, the office has used, or intended to use, Cybercheck reports in 10 cases brought to them by the Akron Police Department, Gessner said. The Akron Beacon Journal and NBC News were the first to report about the county’s use of the tool.
The Summit County Sheriff’s Office confirmed to the Akron Beacon Journal this month that it is investigating whether Mosher lied under oath but provided no other details.
In other cases—murder trials for Salah Mahdi and Adarus Black—defense attorneys didn’t challenge the use of Cybercheck and the trials resulted in convictions. Both convictions were upheld by an appeals court.
Since then, judges overseeing the murder trials of Javion Rankin, Deair Wray, Demonte Carr, and Demetrius Carr have ruled that Cybercheck cannot be admitted as evidence unless Global Intelligence grants the defendants access to its source code. However, the Summit County Prosecutor’s Office appealed several of those rulings, and in September an Ohio appeals court ruled that the trial court erred in excluding the Cybercheck reports as evidence for reasons unrelated to the technology’s effectiveness.
In other jurisdictions, WIRED found, prosecutors have also decided not to use Cybercheck reports, or have dropped charges against defendants after defense attorneys scrutinized the findings and Mosher’s testimony.
In 2021, Midland County, Texas sheriff’s deputies were investigating the murder of a woman whose burned body had been found in a roadside field. Deputies had arrested the woman’s ex-boyfriend, Sergio Cerna, on unrelated charges. When they searched his phone, according to an affidavit, they found text messages in which he threatened the victim, including texts that read, “Your car is going to be burned down then you will be next.” But they couldn’t find evidence that placed Cerna near the scene of the crime.
The sheriff’s office asked Cybercheck for help and received a report claiming that the algorithms had determined, with 97.25 percent accuracy, that Cerna’s cyber profile had pinged a wireless LaserJet printer near the crime scene the day the victim’s body was found. Prosecutors wanted to use the report as evidence at Cerna’s trial, but his defense requested a Daubert hearing. Halfway through the hearing and before the defense could cross-examine Mosher, assistant district attorney Lisa Borden decided not to use Mosher’s testimony or the Cybercheck report at trial.
“We would have needed to be able to authenticate that data,” she tells WIRED, but by the time of the Daubert hearing, the printer that Cybercheck had identified in its report couldn’t be located. That was the first, and only, Daubert hearing that Cybercheck has been subjected to in the country, according to court records and Global Intelligence.
A Midland County jury convicted Cerna in March and sentenced him to life in prison. Cerna’s attorney said he would appeal the conviction.
In Colorado, questions about Mosher and Cybercheck preceded prosecutors’ dropping the charges and sealing the file against a defendant in what law enforcement said was a child sexual abuse material (CSAM) case. After learning that the local district attorney’s office planned to enter Cybercheck evidence at trial and call Mosher as an expert witness, defense attorney Eric Zale hired private investigators to look into Mosher’s background.
Mosher told the Boulder County court that he’d previously testified as an expert witness in two CSAM cases in Canada, according to Zale and an appeal brief filed by Malarcik for another client in which a Cybercheck report had been shared in discovery. But after being contacted by Zale’s investigator, the Canadian prosecutors in one of those cases contacted the prosecutor in Boulder County to say that Mosher had never been called to testify in any capacity. The defendant, who was related to Mosher, had pleaded guilty on the first day of the trial. A prosecutor familiar with the other Canadian case wrote to the court that no charges had ever been brought against the person whose trial Mosher had told a judge he testified at.
Zale alleges Mosher is “preying on this kind of holy grail of technology to sucker local law enforcement and judges and prosecutors, and frankly some defense counsel” into relying on Cybercheck’s technology.
Mosher did not respond to WIRED’s request to comment on Zale’s claims. Global Intelligence did not dispute that Mosher claimed to have testified as an expert in the two Canadian cases.
“Mr. Mosher felt at the time that he needed to relay all court participation activities including provision of statements regarding an investigation,” the unnamed Global Intelligence employee wrote. “Other prosecutors have reviewed this matter during other trial proceedings, finding this incident was more of a lost-in-translation issue as opposed to some sort of impropriety.”
WIRED requested the names of those prosecutors but did not receive a response.
No Receipts
The challenges in Ohio and Texas have hinged on an unusual aspect of Cybercheck that differentiates it from other digital forensics tools: The automated system doesn’t retain supporting evidence for its findings. As Mosher has testified under oath in multiple jurisdictions, Cybercheck doesn’t record where it sources its data, how it draws connections between various data points, or how it specifically calculates its accuracy rates.
In Mendoza’s case, for example, no one knows exactly how Cybercheck determined that the email address “[email protected]” belonged to Mendoza. Nor did Global Intelligence explain exactly how the system determined that Mendoza’s cyber profile had pinged the wireless devices near 1228 Fifth Avenue.
Mosher has testified that the only information Cybercheck retains during its search process is the data it deems relevant to the investigation, all of which is included in the reports it automatically generates for investigators. Anything else, including potentially contradictory information about who owns a particular email address or online alias, is supposedly processed by the algorithms and used to calculate the accuracy scores that Cybercheck includes in its reports but isn’t archived.
“When you're asking, you know, do we preserve all the artifacts and all the data that we crawl—we couldn't realistically do that because it's zettabytes of data,” Mosher testified in the Texas Daubert hearing on January 19, 2024. A zettabyte is equivalent to more than 1 trillion gigabytes.
Mosher has testified that Cybercheck doesn’t need to show its work because its conclusions are derived from open source data that anyone with the proper open source intelligence (OSINT) training can find on the web.
“If you give that [Cybercheck] report to a skilled investigator that knows cyberspace and machine learning, they're going to come up with the exact same results,” Mosher testified during the murder trial of Adarus Black, in Summit County.
Rob Lee is an OSINT expert and chief of research and faculty lead at the SANS Institute, a leading provider of cybersecurity and infosec training. According to Mosher’s résumé and court testimony, Mosher took more than a dozen SANS Institute training courses prior to founding Global Intelligence.
At WIRED’s request, Lee and a team of researchers at the SANS Institute reviewed Cybercheck reports and the descriptions of the system that Mosher has given under oath. They say it’s highly unlikely that some of the information in the reports can be gathered from publicly available sources.
Specifically, to determine when a particular device has pinged a wireless network, an analyst would need to either physically intercept the signal or have access to the device or the network’s logs, neither of which are open source, Lee says. That kind of access requires a search warrant.
“There is a lack of peer review and transparency in [Cybercheck’s] algorithmic processes, which makes me question the legitimacy, sufficiency, and legality of the datasets used for accurate profiling and geolocation,” Lee tells WIRED. “The claim of achieving this level of accuracy using only open source data without further validation and transparency in the tool's methods and data sources is highly suspicious and questionable.”
A Global Intelligence employee tells WIRED that law enforcement works with “industry analysts and experts in the open source intelligence space who are manually replicating and backstopping intelligence data from our reports.” They add that “investigations and prosecutions only move ahead on the strength of the evidence gathered by agencies and verified after backstopping Cybercheck intelligence.” The company’s response did not address claims that certain data, such as whether a device connected to a specific Wi-Fi network, are typically not accessible via open source methods.
“Completely False”
During the Black murder trial in November 2022, Mosher testified that, since January 2021, Cybercheck had run approximately 1,900 searches for suspects’ historical locations and another 1,000 searches for their real-time locations. Out of those 2,900 searches, Mosher testified, there was only one search in which the individual didn’t turn out to be in the location Cybercheck listed for their cyber profile.
But in interviews with WIRED and in emails obtained by WIRED through public records requests, more than one of Cybercheck’s law enforcement clients allege the company’s technology provided information that investigators were unable to substantiate or that contradicted reliable sources.
In January, Mark Kollar, an assistant superintendent with the Ohio Bureau of Criminal Investigation (BCI), wrote an email to Cybercheck about a search warrant his agency had served to an email provider seeking information about an account that Cybercheck linked to a suspect. “The email provider is saying that the email listed in the Cybercheck report doesn’t exist and has never existed,” Kollar wrote.
The Ohio BCI, which is a division of the state attorney general’s office, entered into a $30,000 trial contract with Cybercheck in August 2023 and submitted more than a dozen cases to the company, Steve Irwin, a spokesperson for the attorney general’s office, tells WIRED. “BCI has not received results on many of the cases and some of the leads produced haven’t panned out,” he says. “Due to the lack of investigative leads that have been produced, BCI has no intentions of entering into another contract with the company.”
The Yakima County Sheriff’s Office, in Washington, signed an $11,000 contract in 2022 allowing them to submit 20 cases to Cybercheck. “I think we still have access to Cybercheck, but we don’t use it,” Casey Schilperoort, the sheriff’s public information officer, wrote in an email. “I heard that we don’t receive much or accurate information.”
In an unofficial email chain in which investigators from different agencies shared their experiences with the technology, which WIRED obtained through a public record request, Aurora, Colorado detective Nicholas Lesnansky wrote that Cybercheck had identified someone as a suspect in one of his department’s homicide cases because the person’s cyber profile pinged a router located at an address of interest. “Detectives went and spoke to the resident at that home who has lived there for 20+ years and never had a router by that name so we can’t corroborate their information,” Lesnansky wrote. Neither Mosher nor Global Intelligence responded to WIRED’s inquiry about Lesnansky’s claims.
In a second Aurora case involving the fatal shooting of a 13-year-old, Global Intelligence staff were “adamant” that Cybercheck had identified the killer, but Lesnansky’s investigation was pointing toward an individual he considered a more likely suspect. “They then came up with a scenario where it was a gang initiation thing where the person they had identified was driving the person I think is more likely around,” Lesnansky wrote. “I doubt the suspect Cybercheck identified and the other person I find more likely are driving around together as one has had his house shot up by the other several times.”
On the same email chain, Heather Collins, a special victims unit intelligence analyst with the Mississippi Bureau of Investigation, wrote that she used Cybercheck on a missing juvenile case. “They gave us information on possible ‘suspects’ and it wound up being completely false. We located the missing juvenile using other methods. They wasted our time.”
Mosher did not respond to WIRED’s questions about Collins’ allegation that the information Global Intelligence provided was false.
In other cases, Cybercheck appears to have produced accurate information, although investigators weren’t always able to act on it.
Joe Moylan, the public information officer for the Aurora Police Department, says that his agency has requested information from Cybercheck on five cases, and that in two of those cases the technology was “beneficial to the investigations,” although no arrests have been made as a result.
In 2017, then 9-year-old Kayla Unbehaun was abducted. For years, the South Elgin, Illinois police department searched for Unbehaun and her noncustodial mother, Heather Unbehaun, who was accused of the abduction, following her trail to Georgia, where they hit a dead end. During that time, the department signed a contract with Global Intelligence, and sergeant Dan Eichholz received a Cybercheck report that placed Unbehaun and her mother in Oregon, he tells WIRED. It was a new lead, but because Cybercheck didn’t provide any evidence to support its findings, Eichholz couldn’t use the report to obtain a search warrant.
Unbehaun was finally reunited with her father in 2023, after an employee at a consignment shop in Asheville, North Carolina, recognized her mother from a picture shown on the Netflix show Unsolved Mysteries. After Unbehaun was located, Eichholz learned during the follow-up investigation that, until several months earlier, the pair had indeed been living in Oregon.
“I don’t want to say it wasn’t actionable, but I couldn’t just take their information and go with it,” Eichholz says. “That was always the hang-up for us. ‘OK, you got me this information, but I still have to check and verify and do my thing with search warrants.’” The child abduction case against Heather Unbehaun is ongoing.
Any Help They Can Get
Cybercheck has spread to law enforcement agencies across the country thanks to generous marketing offers and word-of-mouth recommendations. But in interviews with WIRED and the email exchanges we examined, there was little evidence that law enforcement agencies sought or received evidence to support Global Intelligence’s claims about what its technology could do.
Prosecutors who spoke to WIRED, such as Borden from Midland County, say they learned about Cybercheck because law enforcement in their jurisdiction had been using it. And when it came up in a case, they let the adversarial court system decide whether or not it was legitimate.
“It was new technology and I was curious, so I was like, ‘Let’s give it a try and see how far we can get,’” Borden says. “I’m thankful that it didn’t come into evidence in my case, that I didn’t need it to get my conviction.”
Emails show Global Intelligence sales representatives regularly offered to run police departments’ cases through Cybercheck for free in order to demonstrate the technology. They also referenced cases that Global Intelligence characterized as high profile and that Cybercheck supposedly helped solve, without naming the cases outright or providing evidence that Cybercheck had made any difference in the investigations.
Emails obtained by WIRED from the Ohio Bureau of Criminal Investigation show that investigators were initially excited to see what information Cybercheck could provide about their cold cases. They even introduced Global Intelligence sales representatives to other law enforcement agencies in Ohio. That enthusiasm seems to have helped convince other agencies to trust the company.
Gessner, from the Summit County Prosecutor’s office, says that when his agency was deciding whether to use Cybercheck evidence, it asked the Ohio BCI’s cybercrimes unit for an opinion. “They said, yes, it makes sense … we don't have the technology to do this, but we'd love to have it.” County prosecutors also reached out to the SANS Institute, he says, and were told the institute didn’t “do this type of stuff.”
But even as it has withdrawn evidence that Cybercheck provided, Gessner says the Summit County Prosecutor’s Office is asking other companies whether they can do the same kind of open source locating that Global Intelligence marketed.
“We don’t want to shut doors that can help point to the truth in our cases,” he says.
4 notes
·
View notes