#malwarebyte install
Explore tagged Tumblr posts
Text
A reminder to everyone to install an adblock for yourself and everyone you know Because
As of late Google's Sponsered Links (the first links that come up- marked with small text that indicates google is taking money to put these at the top) have been illegitimate links to popular sites like Facebook, Amazon, and Fox News (I work in I.T. I cannot force these people to use better sites) but rather they click the link and it comes up with a fake windows defender page with lots of scary messages saying Oh No You're Infected Click Here To download a real piece of malicious code because we're trying to trick you.
Google is taking money and doing nothing to protect the people using their engine from cyber attacks. This is the digital equivalent of being paid to stock a squishy looking toy that's full of knives at the very front of a store. Get Fucking rid of them????
Would love to reccomend a search engine that 1) isn't going to actively harm me and 2) works like Someone did about a decade ago
and 3) isn't bing.
#technology#google#amazon#facebook#fraud#malware#scam#this is only going to get worse with the holidays#install adblock and run malwarebytes periodically yall#enshittification
14 notes
·
View notes
Text
anddd it's over. cool and good and great
0 notes
Text
SCAM ALERT: Cryptocurrency related but can affect trans people buying HRT. I was probably 10 seconds away from having money stolen and I know what I'm doing. (Crypto Clipper)
Today I was helping a trans friend order some DIY HRT. A lot of DIY HRT places only accept cryptocurrency for security reasons. I am not looking to promote cryptocurrency or anything associated with it, but if you may be forced to use it for HRT or other reasons, you need to know this.
In general if you are forced to use crypto, you should use the cheapest coin your supplier will accept. If it is cheap, that means there is not a lot of activity on the chain and energy use will be less. I used one called Zcash as it was the cheapest one the site accepted but that's not really relevant.
I used an old coinbase account I had used for similar situations in the past. I was doing it on her PC. I got the instructions to pay on the HRT site, and I pasted the wallet address into Coinbase and just before I hit send I noticed the wallet address I had pasted didn't match the wallet address I had copied.
I looked it up and found this is from a form of malware called a Crypto Clipper, that detects when you have copied a crypto address, and makes you paste a different one so it can steal your money. I am lucky I noticed. To remedy it, I installed the free trial of Malwarebytes on her PC to remove malware, and completed the crypto transaction on my PC, and confirmed that the wallet address matched what the HRT site had given me.
I managed to avoid falling for it but it's such an easy thing to fall for, especially if you have avoided crypto thus far for extremely understandable reasons. Be careful out there! It could happen to anyone.
#trans#hrt#trans hrt#diy hrt#crypto#cryptocurrency#bitcoin#scam#scams#psa#important psa#important#virus#malware#cybersecurity
332 notes
·
View notes
Text
Just had some straight up creepypasta shit happen. Computer suddenly bluescreens and it boot loops a few times. It takes forever, but it loads up again. The windows 10 background is old, and something feels off. I type my password. Doesn't work.
That's okay, it's long, I mess it up a few times. But eventually I take it slower. More deliberately. Making absolutely sure I get every single letter and symbol correct. Doesn't work. I do it again. Doesn't work. There's this desperate panic. I was watching malware videos before this happened, and had recently downloaded a lot of game mods I really didn't know much about. I put in security questions for my windows installation, but they weren't coming up when I requested to reset my password. Just a strange pop up asking to insert a password reset usb.
Then, I realize. The name displayed for the windows profile is different. It's… Older. I made the name of my new windows installation "Grace" just for convenience with recording for ChainmailChasers, but my old laptop drive installation was named Ebola. Uncertainty clouds my mind. Nervously, I type in my old password. Due to faded memories, my first attempt is the wrong password. But the second… Works.
It buffers just a little too long, just like the previous failed password attempts did, pausing as if the computer itself wasn't sure if the password was correct or not. But the desktop loads. My old desktop. It's so laggy from the drivers being incompatible that most of my mouse clicks aren't registering. My other drives showed up out of order in the file explorer, meaning they weren't wiped, but were blocked from access by windows. I didn't have authorization.
Google searches only pull up Blue Screen of Death results. No one is talking about my issue. I hit control alt delete and I only have two options: Shut Down and Restart. I shut down. It refuses to. I have to hold the power button. I load the bios, and wander around until I find the boot priority. Something so simple but specific that it felt deliberate. The crash had somehow swapped the boot priority from my SSD to my old laptop drive which is connected by SATA to USB. I swap it. It works.
Powershell /sfc scannow (a built-in windows utility that detects and automatically repairs damaged windows installation files) finds nothing. MalwareBytes detects nothing. My computer runs flawlessly again. All my accounts are untouched. But still, I'm left with this lingering feeling. Seeing that old desktop again, after a year… It was like seeing a ghost. Also, if this all sounded fairly circumstantial, imagining dealing with all of this high.
51 notes
·
View notes
Text
installed a fresh SSD, a fresh windows, and like, holy shit this is awful lol this is just a comedy of errors at this point
i've still got the old ssd connected which was throwing errors out the ass and I can't tell if it's that or some other startup program (or malwarebytes, seems to be the most common issue) causing windows to crash on start until it unloads the asinine profile login page telling me to Go To The Next Level With AI
the windows profile on that old ssd straight up nuked itself, so now I've got ownership permissions issues that i can't even grant because if I launch the ssd as a boot drive it has zero documents, most of my installs are gone, and the actual important thing I forgot to save prior to the clean install, all my bookmarks and browser history >:( i think my custom-bundled photoshop brushes too but that doesnt matter bc photoshop 2020 UNLOADS all my tools as soon as i close and reopen it. and also closing it doesn't end the process and i end up with a huge list of Photoshops clogging my task manager
also the win11 snipping tool is..... bad? it looks so nasty lol
#basically fuck you photoshop what the hell is this mess. everything else is w/e#unfortunately i do a little bit of graphic design and PS's inbuilt features for that are REALLY swanky which is why i was reluctant to leav#but this is genuinely unusable
35 notes
·
View notes
Text
Windows updated and completely fucked my mom's computer last night and our internet went out moments after the problem arose. The desktop was fine and we could access SOME files and the registry but control panel, settings, and anything that reflected inner programs acted like it, and windows, didn't exist. It took AGES for each click to make something happen. And yet through the whole process her wallpaper which she crazily has set to flash through a variety pof images like every three minutes (wtf mom) worked JUST FINE.
We FINALLY managed to get the task manager up and malwarebytes was HOGGING so many resources suddenly.
We decided things might speed up to find workarounds if we could managed to get to the uninstall programs page. Control panel and settings were useless but they were visible in the file manager. Settings still wouldn't work but control panel did so we FINALLY got the uninstall programs page up and guys it took like 20 fucking minutes to select, click uninstall and get through the entire process of uninstalling ONE program.
In the meantime we're working to figure out if like a windows setting needed to be enabled since it kept insisting windows wasn't working. We got that up and everything was fine? But things were starting to work faster once malwarebytes was gone.
We knew that we had to get the updates that installed to GO AWAY because clearly they broke something. We fussed around different things for a while, looking for ways to find the windows updates. We checked in the files and it wouldn'\t open the settings, we checked the little icon on the taskbar that was finally working and it didn't come up, thinking it was broken, and finally I said fuck it and preessed window+i and FUCK ME IT FUCKING WORKED!
We uninstalled the latest two updates and she set it so it wouldn't update again for 5 weeks and turned it off and held out breath and it fucking WORKED.
I'm not in IT but we got this fucking nightmare working hell yeah.
It sounds so easy typing it out like this but my guys it broke around midnight and it was like 3 am when it was fixed.
42 notes
·
View notes
Text
both Mozilla and windows say to just change the setting and show the same exact windows 10 way to do it but I don't have that option on windows 11 so what do I do?
so... looks like windows made it impossible to install Firefox, they really want to force you to use edge, I hate this so so much, how do I get Firefox back?
#i hate this#i want to get rid of this new laptop just for that#i wasn't sure about it and now this like wth#but my old laptop could die anytime so i need a new one#i just want firefox#and like will it do this for everything i want to install#like can i install malwarebytes#how do i change this stupid ass setting
5 notes
·
View notes
Text
Hacked Account Warning
I'm in Asia Server by the way
There are pictures for proof
You don't need to have your login infos shared for you to get hacked.
There are some hackers that attack your email, and when they can't they attack your pc itself.
The destroyed weapons:

It was during my exam period that I was hacked. I just logged in to do dailies before going back to studying when I noticed my arle was doing WAY less damage. I checked her weapon and lo and behold it wasn't there. Destroyed. I checked alhaitham and his weapon was destroyed too. Same with Amos bow and a lyney bow. I didn't understand what was happening and contacted mihoyo. Someone logged into my account at 4 am, destroyed weapons and 2 artifacts, renamed wandered something racist and left. I was pissed and was talking back and forth with the mihoyo support as no device besides had logged in and I didn't give the infos to someone else. So how come the hacker got in without me receiving a confirmation email? Well I got my answer a day later when microsoft finally sent me an email informing me of a suspicious logging.
The logins...:







That's when I discovered how bad it was. For over a month, someone was trying to log into my window session and I wasn't informed by Microsoft! They used a VPN as it came from China, Russia, America and Brazil. They succeeded in the Brazil vpn. I changed all my info and did the necessary steps. I found many virus on the pc despite not downloading shady things and even a fake anti virus that I don't remember installing (SAntivirus) and it was VERY annoying to Uninstall. Thankfully I found videos to do it.
I scanned the pc using the Microsoft anti virus and found 4 virus, 2 of high danger. I did a deep clean by the way and it lasted over 6h. Even when I Uninstalled them they came back so I installed Malwarebytes who found 34 virus....the fake anti-virus was found with it by the way. After I destroyed them all I didn't have any attempt besides one which I didn't have the time to take it up to cyber criminality.
The Viruses:



So to any pc player, please be very careful and get a good anti virus. Scan your pc often as unfortunately there are very ill intentioned people around. The hacker didn't touch my hsr account, just my genshin where I spent a lot of time on it.
The alhaitham weapon was very sentimental as it was my first and I explored all sumeru desert to get it. I had lost both the 50/50 on it. Same for arle weapon, I lost the two 50/50 to lyney bow to get it. I was devastated because I'm ar 60 with no exploration left. Even the teapot is all done. For the wanderer name...all you have to know is they changed it to something racist towards black people and I had to fight with hoyo for them to realize and send me a name paper to change it.
ADVICE FOR PLAYERS:
-Scan your devices often
-Get a good anti virus
-Download from trusted sources, I know we all get the apk and the such but there are websites you can't trust!
-If you can, log out before shutting down your device
-Check your connection history of Microsoft. They don't warn you until it's too late.
8 notes
·
View notes
Text
After having had an extremely crappy laptop that used to give me constant BSODs if I ever installed something basic as Malwarebytes, I am now anxiously watching my new, smooth and adorable lappie doing updates before turning off with a mixture of anxiety and flashbacks of that fucking shade of blue.
5 notes
·
View notes
Note
Hey Peach I won't ask anything super incriminating or anything but do you need a VPN to torrent stuff? Or really good antivirus?
I know I should look into how to do that stuff but before I attempt anything of the sort, I wanna know if I should beef up my security before I start sniffing around.
Im really out of my element here 😭
hi hi, so there are a couple of things I do to keep my computer/data safe when torrenting - first of all, yes, a VPN is a great idea!! the one time I forgot to turn on my VPN before torrenting something at my parents house my dad got a letter from our internet provider about it 😵💫 (it basically was something about "your IP address was used to download copyright infringing material, don't do it again").
it's generally best practice to have some type of VPN set up before torrenting! try to stay away from free VPNs, from what I understand they're not the most reputable and oftentimes they're profiting off selling your data (the ol' "if they're not making money off the product then *you're* the product"). I hear good things about Mullvad and ProtonVPN - I believe at least Proton does have a free tier that just has a limit to how fast you can download things with it!
as far as antivirus goes, it's got its pros and cons. I actually don't always have it turned on, and I'm not a big fan of the built in Windows Defender (it tends to have a lot of false flags) - I like MalwareBytes and I'll do an occasional scan of my computer after downloading stuff & before actually running things. I personally find that antivirus programs tend to quarantine video game installation files when I try to run an installer for a game I torrented, which causes the installation to fail and then I have to go manually check the antivirus to un-quarantine the files 🙄 which is why I end up not having mine running all the time. but if it makes you more comfortable def keep it on, and just remember to check for quarantined files if you're having weird errors trying to install anything!
however I do also make sure that I'm visiting sites I generally trust so that lowers my chances of downloading anything sketchy (though not 0 - be mindful of what you download and open on your computer, especially executables (.exe files)!!) I find all sites I use either via direct recommendations from trusted friends who are very knowledgeable about information security and stuff, or from the r/piracy subreddit's megathread (they have a lot of recommendations for all different kind of media, and also a lot of helpful info about cautious pirating in general)
also, make sure that the torrent client you use is good! I've always used qBittorrent - it's pretty easy to use and set up, it's straightforward, open source, ad-free, and also has a lot of handy features (one of them being a feature in the advanced settings where you can have it only do things with your torrents while your computer is connected to your VPN, which is good for keeping your real IP address secure. if you want help figuring out that setting just reach out again and I'm happy to help!) whatever you do, please don't use μTorrent lol, that one sucks. also, you don't have to update it every time it comes out with an update, but it's generally a good idea to check the qBittorrent subreddit when an update does come out just to see if it deals with anything important security-wise - just recently, a pretty major backdoor vulnerability was identified and fixed, so it was actually pretty critical that everyone update to the latest version (to anyone reading this, make sure you're on 5.0.1 and nothing older than that!)
and also, a good Adblock like ublock origin will help keep you from accidentally clicking on nefarious links when trying to download things on the internet, so make sure you have that set up too!
also also, some regular websites (especially streaming services) HATE VPNs so if you have one running and you're trying to watch something on like, Netflix or your cable provider's streaming site and it's not working, pause the VPN till you're done! and that's where having your torrent client set up to automatically pause all torrents while your VPN is off comes in handy.
also also also, a note on torrenting etiquette - when you are torrenting something from other people (aka peer to peer/P2P file sharing) you are considered a "peer" and the people who have the full files and are sharing them with you via torrent are called "seeds". peers need to be connected to seeds to be able to receive the file. you will also have a ratio for each torrent - this is the amount of data you have sent vs how much you have received. a ratio of over 1.0 means you've sent more than you've received and is considered to be "good form". I usually stop seeding a torrent once it reaches above 1.0, and I do also often go stop seeding a lot of stuff below the 1.0 ratio if it looks like it has a lot of seeds, but I like to keep seeding when it seems like I'm the only one or just one of a few people seeding, especially for media that I already had a hard time finding, to make it a bit easier for someone else trying to torrent it. there are some things that I've waited months to finish torrenting just because nobody was seeding at all for a while 😭 so I do what I can to keep torrents alive myself.
sorry this ended up longer than I thought it would be, and probably longer than you expected, but I hope this is helpful! happy sailing the digital seas, anon :D
#petchyposting#I'm not an InfoSec expert by any means but this is what i have learned over the years
4 notes
·
View notes
Text
So Your Discord Got Hacked
A few days ago, my discord got hacked because I fell for the good old fashioned "friends working on a game" scam.
FIRST UP if any of your friends want you to try their new game, ask them identifying questions. I fell for this and feel like an absolute MORON.
BUT say you did fall for it, your discord went down and logged you off. HERE ARE THE STEPS TO TAKE.
DO NOT Log in on your computer. The virus the scammers use has a keylogger in case you have 2FA already. They need you to input your code to change the password on you. ALSO reroll any of your 2FA generated codes from the secondary device. The hacker will copy these in case you set up 2FA.
If you don't have 2FA and the hacker turns it on, IMMEDIATELY go here and submit a ticket. I will show an example ticket below, with the language I used.
Go to paypal, and if you see any charges, click on the discord charges and disable automatic payments. If you don't already have 2FA on paypal, turn that on, and once again, DO NOT use the device that got hacked.
Keep your email open. As soon as you get a response from support, you need to reply to that email.
UNINSTALL discord from the hacked device, along with anything you may have downloaded in the past 24 hours (like the unzipping program. And delete the hacker's program). Also delete the discord.exe file from your downloads on the computer.
RUN A VIRUS SCAN WITH DISCORD UNINSTALLED. Just in case they set the worm to jump out then worm back in. I used Malwarebytes - windows defender cannot catch what they are doing.
Restart your computer.
Run a second virus scan.
Download discord again directly from discord. Install from the new EXE file. Run a third virus scan just to be safe.
IF IT WORKED, the QR code login will load properly. The worm the hackers use blocks the QR code - this is so you type your password/the 2FA code. They also block your computer from seeing what other devices are accessing your account - because you'd be aware they're logging in.
WHEN YOU GET YOUR ACCOUNT BACK - change the password via a secondary device. My computer discord was hacked, so I changed the password via mobile. I also rerolled all the backup codes just in case. Discord staff turns off 2FA when they get you back into your account because it's very common for hackers to turn it on to keep you from getting in.
Log in via the QR code scan (if it was your computer). This is just a secondary precaution, I don't want my computer to know the password at all.
CONTACTING DISCORD SUPPORT:
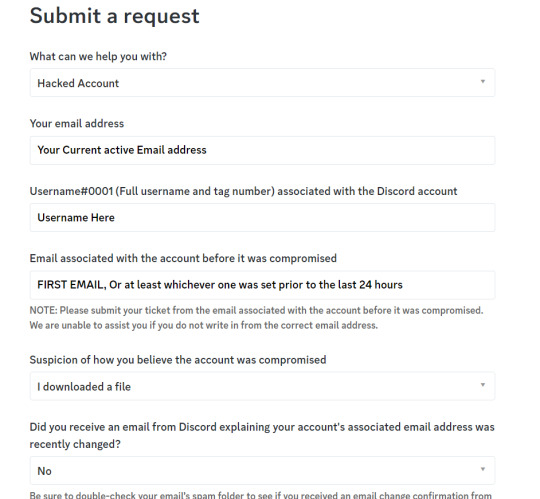
Note: you want the first email or an email prior to the last 24 hours just in case the hacker changes your email address. When staff is looking at your ticket, they use this as a confirmation, if it was changed today, that could be the hacker trying to use support to hack you back.
(Here there's a popup of recommended articles, I'm skipping that.)
I don't know if I said any magic words but discord got me back into my account VERY quickly.
I got rehacked before I went through the steps of uninstalling and virus scans, but I quickly got the hacker out by doing mobile only on all the resets.
You can also tell if the hacker is there because your discord will keep logging you out randomly! This is (from what I figure) the hacker logging out your hacked device to get your 2FA codes, but they have to be fast, so if they miss it they log you out again.
#PSA#Steps to take if your discord is hacked#also always disconnect your paypal from discord after you get nitro#do that now actually#just in case
41 notes
·
View notes
Note
👁 for eliza ⚠️ for enzo 📓 for ezrah... realizing now that all your ocs have a z in their name. ozzie and fritz do too. not brunhildy though
well thats because brunhilda is my special little angel and it is better and specialer than all my other ocs. butserioudly my oc names sre so repetitive theres even another guy i have named RENZO though he actually existed way becore i came up with enzo so hes actually the derivative one in this situation..
👁️ How do other people perceive this oc? How close do their first assumptions come to the truth?
very very few people even know about her whole situation the way she “currently” exists so ill start with how she was when she was alive. ill start by saying that a biig thing with eliza is she unfortunately (and entirely unintentionally on her part) tends to attract people who deify and obsess over her to various levels of extremity. even the person who killed her was a fan who fell madly in love with her. so most people view her favorably, mainly highlighting her musical talents. she was very personable, and throughout her entire life she was very well loved. i would say most people had a fairly accurate “superficial” understanding of her as a person. you wouldnt really recognize it but she kept many people at a distance in regards to how much they actually knew about her true feelings and especially her difficulties and her grievances. i think most people tended to think of her as a “perfect” sort of person, like someone whose untouchable by normal issues everyone tends to go through.
the way she is now, there are 2 people who know that she isnt even dead anymore. pygmy DEFINITELY still falls into the pattern of people becoming obsessed with the “idea” of her. really he knows next to nothing about her, and has fallen in love with the version of her that perfectly complements himself, and his own interests.
the resurrectionist, on the other hand, views her as a stereotypical zombie with little to no awareness of whats happening around her. exactly how accurate that assessment of her cognition is i like to leave vague. LAWL
⚠️ - If this oc came with a warning sign, what would it be?
INSTALL MALWAREBYTES
📓 - Do you associate any quotes or lyrics with this oc?
yessss infact he has an entire playlist of songs i associate with him HEHE. in particular i think this song in its entirety is a very apt summary of a lot of his Deal. but this bit from the frontier index by silver jews i also think abt with him alot mwahaha

7 notes
·
View notes
Note
Hello, have you talker about your art process anywhere? I am very interested in how you got into glitch art/photomanipulation/however you’d call this, and i want to learn more. Do you have programs you use, plugins, do you use any physical media or scanography/scanner manipulation? I really want to hear about anything you wanna talk about regarding the creation process for your art. Thank you for sharing your work.
Yes! Unfortunately, I tried answering this question in a ton of detail but tumblr didn’t save it as a draft automatically - which was a frustrating experience to say the least - so this is my second attempt at answering this ask — you’ve asked a lot of really valuable questions here, I’ll do my best to be concise in my answers!
When I first began playing around with editing software, I was 16 and simply wanted to make memes and silly edits. This was around 2015-2016, whenever vaporwave was a fresh concept and Resonance was trending on Vine — which is a sentence that makes me feel fucking ancient. I was really entranced by vaporwave, which had this off-white nostalgia for post-consumerist 80s and 90s cultural trends. I later became interested in how many of those cultural trends persisted and evolved into Y2K culture and beyond.



these are some of the images I was working on during that period of time, which were loosely inspired by indie horror and jazz cups and soundcloud rap. I was so proud of learning how to make my own scanlines using GIMP :)
Late 2016 I began my freshman year at a hoighty-toighty art school that I was too poor to attend, and quickly entered a mental health downward spiral — but I learned many valuable things, most of that info was painfully basic; my education prior to that was not anything special. I would not consider myself someone with exceptional aptitude for art — I just have a chronic compulsion to break things.
So, where to begin? My recommendation to anyone who’s newly interested in this style of artwork and editing:
Glitchet is a repository of info regarding many different styles and methods of distortion - from sonification to slipscans, there’s a ton of good info to comb through. Most of the techniques and tools covered are free to use, but there is some paid stuff out there too - but if you know your way around, virtually everything is free. More on that shortly :)
As for my process, programs, plugins, etc - there is a lot, and I don’t think I can cover everything. Primarily: Photoshop, After Effects, GIMP, ArtStudio Pro for iOS, Procreate, DestroyPix, and a number of other pieces of software that perform smaller, specific functions - such as BigJpg for AI-upscaling. I also employ analogue/physical distortion techniques like circuit-bending, slipscan, and more. These require additional hardware and knowledge; such as access to a copier/scanner, old CRT screens, and the ability to solder + work with low voltage electronics without accidentally shorting them out. Best part is that you can ✨layer✨ anything and everything, collage style — which is my favorite aspect, very playful and exploratory.
Now, if you’re like me and can’t afford fuck-all, but wholeheartedly believe that money should not be a limiting factor for creativity, I recommend installing the Adobe Creative Suite from downloadpirate(dot)com - which is also where I’ve gotten many of my plugins, although I do also pay for the plugins that I come to really appreciate, as they’re typically done by independent developers who could actually use the scratch. Same risks as any pirate cove: intrusive ads, popups, and redirect chains - use Ublock Origin to kill these annoyances. I recommend performing a scan with Malwarebytes after using any sketchy-looking-download site, but I was raised to be a bit paranoid so that’s purely preferential.
As for plugins:
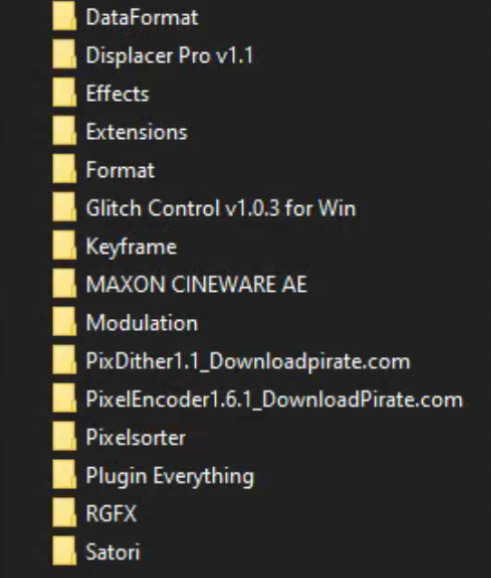
Filenames in this image may correspond with the developer of the plugin — you can just search the filename + ‘after effects plugin’ and you’ll almost certainly find your way.
Most commonly, I use Pixelsorter, Pixdither, Displacer Pro, Pixel Stretch, and Hacksaw — although some of the plugs that I use aren’t listed above, like Datamosher, which is a script-based solution that helps remove i-frames from a clip in After Effects, all without having to use VLC and any handwritten scripts (the ol’ fashioned way).





These are all from the last year or so, to show the relative growth I’ve experienced since my time spent as a creature of 16 years. Naturally, I’m also like, more of a person now - so the art is partly better because I’ve simply suffered more :p
When I started, I didn’t know any of the jargon or how to describe a specific effect I was trying to achieve - so I taught myself how to do stuff by googling around, and if I couldn’t find an answer (which was 90% of the time) I’d just try to figure shit out. Which rarely ever resulted in outright success, but was always a significant learning experience. That’s why I’m so quick to drop the link to Glitchet! Sometimes I can’t help but wonder what I’d be doing now if I had known there was an online library for info on how to produce different types of distortions - definitely would’ve spent less time trial-and-erroring my way through aesthetics.
In conclusion: there’s so much to try and you should try absolutely everything that interests you. It’s free if you’re cool enough to steal it; though some things (like hardware) are gonna cost. You don’t need talent or an exceptional education, though both of those things would certainly help — and you’ll never run out of things to learn because there are infinite ways to break shit. More so than anything else, you need a willingness to explore, experiment, and fail often. You’ll fail miserably at times, so a proclivity for humiliation is also a big plus. Eventually your failures will start looking like successes; but you’ll have forgotten the difference by then and will be free to make whatever the fuck you want :)
I’m glad that you enjoy the work! tumblr has always been the best place for me to share my lil jpegs and actually find a real sense of connection with others who are similarly jazzed. My life completely bottomed-out a few years ago and I was in a really bad place whenever I logged into my blog for the first time in half-a-decade and started posting again. My personal growth from then to now has been a strange and incredible experience, and I’m so glad that I had the art and the funny little gays on this website to help me through the toughest points and teach me valuable things about myself; so if I can give back a little knowledge, I’ll gladly take that opportunity! I hope these findings serve you as well as they’ve served me.
#my asks#THANK YOU!!#I hope this is formatted in a way that is easy to read - clarity and concision are not my strongest skills#godspeed!#documentation#reference
19 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
If an antivirus you use flags Glaze as a threat, ignore/whitelist it
Today I had Windows Defender flagging the new version of Glaze as a Trojan. I looked into it on Twitter and it turns out that AI bros took Glaze and uploaded it to virus databases to have it falsely flagged as malware, which has resulted in some antivirus programs falsely flagging it at such. I've scanned Glaze with Malwarebytes and it returned no warnings.

If you downloaded Glaze and your antivirus program flagged it as Trojan, whitelist it. Glaze developers are currently in the process of getting Glaze signed.
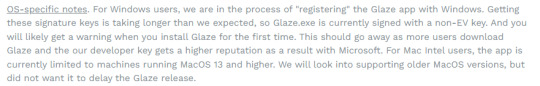
[ALT text, image is a screencap of a paragraph on Glaze's website] "OS-specific notes. For Windows users, we are in the process of "registering" the Glaze app with Windows. Getting these signature keys is taking longer than we expected, so Glaze.exe is currently signed with a non-EV key. And you will likely get a warning when you install Glaze for the first time. This should go away as more users download Glaze and the our developer key gets a higher reputation as a result with Microsoft. For Mac Intel users, the app is currently limited to machines running MacOS 13 and higher. We will look into supporting older MacOS versions, but did not want it to delay the Glaze release."
Glaze can be downloaded here. The new version uses a much more subtle cloak and now works on flat shaded/cel shaded art styles and photography, and even has a limited img2img protection.
8 notes
·
View notes
Text
Hey so. Dont download the new official fnaf troll game that has the secret hints at the movie.
both windows defender and malwarebytes have alerted me to it literally installing a fucking trojan.
4 notes
·
View notes