#privacy breaches law
Text
What is a privacy violation?
Privacy breaches are when personal information is not properly secured. This can lead to financial loss or identity theft, as well as harm to organizations, resulting in a loss of reputation and erosion of customer trust.

What privacy risks do I face?
Individuals are exposed to many privacy threats in the digital age. The following privacy breach risks are common:
Data breach: Unauthorized access to or theft of personal data from companies or organisations.
Phishing scams: These emails or messages appear to come from a trusted source and trick people into giving out their login credentials or personal information.
Privacy on social media: Sharing personal information via social media platforms that can be accessed or used to malicious ends.
Location tracking: This is the tracking of an individual's position through their devices. It can reveal sensitive information or be used for criminal purposes.
Unsecured Wi Fi networks: Personal information can be intercepted by connecting to unsecure Wi-Fi networks.
Malicious software: Downloading attachments or installing software from unknown sources can result in malware installation that can harm computers or steal personal information.
These privacy risks are important and you should be aware of them.

What Happens When Data is Leaked?
Data breaches can occur in many ways.
Hacking: Hackers have many methods of gaining unauthorized access to sensitive data. They can exploit vulnerabilities in software or use malware to crack passwords.
Insider threats: Data breaches may occur when contractors or employees with sensitive information have access to it and misuse it, either inadvertently or intentionally.
Devices stolen or lost: Laptops, smartphones and other devices that contain sensitive information can be stolen or lost.
Human error: Data breaches may occur when people make mistakes such as sending sensitive data to the wrong person, or leaving sensitive data in an unsecure location.
Databases that aren't properly secured: Unsecured databases can lead to data breaches.
Social engineering: Attackers can use social engineering techniques, such as pretexting or phishing scams, to trick people into divulging sensitive information.
Organizations should have security measures in place to prevent data breaches. They also need a plan for dealing with breaches that do occur. Individuals can take steps to secure their personal information by using strong passwords and being careful of phishing attempts.

9 ways to protect yourself from a privacy breach
Here are 9 steps to protect yourself if you suspect your personal data has been compromised by a privacy breach.
Change passwords: You should change passwords on any accounts that were affected by the breach. For each account, use strong passwords that are unique.
Monitoring your accounts: Monitor your bank, credit card and other financial accounts regularly for any suspicious transactions.
To place a fraud alarm on your credit report, contact one of the major credit bureaus (Experian Equifax or TransUnion). It will be more difficult for someone else to open new accounts under your name.
A credit freeze is a blocking of credit reports that makes it harder for anyone to open new accounts under your name.
Phishing attempts should be avoided
Two-factor authentication is recommended: If possible, use two-factor authentication to protect your online accounts.
You can monitor your Social Security Number: Seek out if you have used your Social Security Number to apply for credit cards or other services.
Contact companies: If a company or organization is responsible for the privacy breach, contact them to find out if they offer any support or services to affected persons.
Be educated: Keep up-to-date about privacy issues and ways to protect yourself. Register for privacy-related newsletters and read online privacy guides.

1 note
·
View note
Text
Privacy is a fundamental human right
Privacy is widely considered a fundamental human right. It is recognized and protected by various international and regional human rights treaties and declarations, such as the Universal Declaration of Human Rights and the International Covenant on Civil and Political Rights. Privacy is essential for individuals to exercise their autonomy, maintain personal dignity, and freely express themselves without fear of surveillance or intrusion.
Privacy encompasses the right to control one's personal information, the right to be free from unwarranted surveillance, and the right to privacy in one's home, communications, and personal activities. It also includes the right to protect sensitive personal data from unauthorized access, use, or disclosure.
In an increasingly digital world, privacy concerns have become more prominent due to technological advancements and the vast amount of personal information being collected, stored, and shared. Protecting privacy in the digital age is crucial to safeguarding individuals' rights and preventing abuses of power.
Governments, organizations, and individuals have a responsibility to respect and uphold privacy rights. However, striking a balance between privacy and other societal interests, such as public safety or national security, can be a complex challenge that requires careful consideration and legal frameworks to ensure that privacy rights are not unjustifiably infringed upon.
#PrivacyRights#HumanRights#DataProtection#DigitalPrivacy#PersonalAutonomy#Surveillance#InformationSecurity#today on tumblr#deep thoughts#Privacy Laws#Right to Privacy#Privacy Policy#Data Privacy#Online Privacy#Privacy Advocacy#Privacy Awareness#Privacy Breach#Privacy Concerns#Privacy Legislation#Privacy Practices#Privacy Protection#Privacy Rights Activism#Privacy Safeguards#Privacy Violations#Privacy Ethics#Privacy and Technology#Privacy Best Practices#Privacy Education#Privacy Transparency
11 notes
·
View notes
Text
Weekly output: Samsung self-repair, FCC chair's security concerns, tech-policy forecast, password managers, Google layoffs, electric-car progress, legal risks for security research
This week had me head into D.C. for work events four days in a row, something that last happened in early 2020.
1/17/2023: Samsung ‘Self-Repair’ Program Adds Galaxy S22 Phones, Some Galaxy Books, PCMag
The post I wrote after Samsung gave me an advance copy of their press release noted the limited number of replacement parts offered under this program, but Technica’s Ron Amadeo–who has a lot more…
View On WordPress
#1Password#5G#5G security#Bitwarden#CFAA#DIY repair#DMCA#EV chargers#Google layoffs#hacking laws#infrastructure law#Jessica Rosenworcel#LastPass data breach#password managers#privacy legislation#privacy policy#Right to repair#Samsung self-repair#Shmoocon#tech layoffs#vehicle electrification#Washington Auto Show
1 note
·
View note
Text
Australian Police Make First Arrest in Optus Hack Probe
Australian Police Make First Arrest in Optus Hack Probe
Home › Tracking & Law Enforcement
Australian Police Make First Arrest in Optus Hack Probe
By Associated Press on October 06, 2022
Tweet
A police investigation of a cyberattack on an Australian telecommunications company in which the personal data of more than one third of Australia’s population was stolen has resulted in its first arrest, investigators said Thursday.
Police launched Operation…
View On WordPress
0 notes
Text
In a product demo last week, OpenAI showcased a synthetic but expressive voice for ChatGPT called “Sky” that reminded many viewers of the flirty AI girlfriend Samantha played by Scarlett Johansson in the 2013 film Her. One of those viewers was Johansson herself, who promptly hired legal counsel and sent letters to OpenAI demanding an explanation, according to a statement released later. In response, the company on Sunday halted use of Sky and published a blog post insisting that it “is not an imitation of Scarlett Johansson but belongs to a different professional actress using her own natural speaking voice.”
Johansson’s statement, released Monday, said she was “shocked, angered, and in disbelief” by OpenAI’s demo using a voice she called “so eerily similar to mine that my closest friends and news outlets could not tell the difference.” Johansson revealed that she had turned down a request last year from the company’s CEO, Sam Altman, to voice ChatGPT and that he had reached out again two days before last week’s demo in an attempt to change her mind.
It’s unclear if Johansson plans to take additional legal action against OpenAI. Her counsel on the dispute with OpenAI is John Berlinski, a partner at Los Angeles law firm Bird Marella, who represented her in a lawsuit against Disney claiming breach of contract, settled in 2021. (OpenAI’s outside counsel working on this matter is Wilson Sonsini Goodrich & Rosati partner David Kramer, who is based in Silicon Valley and has defended Google and YouTube on copyright infringement cases.) If Johansson does pursue a claim against OpenAI, some intellectual property experts suspect it could focus on “right of publicity” laws, which protect people from having their name or likeness used without authorization.
James Grimmelmann, a professor of digital and internet law at Cornell University, believes Johansson could have a good case. “You can't imitate someone else's distinctive voice to sell stuff,” he says. OpenAI declined to comment for this story, but yesterday released a statement from Altman claiming Sky “was never intended to resemble” the star, adding, “We are sorry to Ms. Johansson that we didn’t communicate better.”
Johansson’s dispute with OpenAI drew notice in part because the company is embroiled in a number of lawsuits brought by artists and writers. They allege that the company breached copyright by using creative work to train AI models without first obtaining permission. But copyright law would be unlikely to play a role for Johansson, as one cannot copyright a voice. “It would be right of publicity,” says Brian L. Frye, a professor at the University of Kentucky’s College of Law focusing on intellectual property. “She’d have no other claims.”
Several lawyers WIRED spoke with said a case Bette Midler brought against Ford Motor Company and its advertising agency Young & Rubicam in the late 1980s provides a legal precedent. After turning down the ad agency’s offers to perform one of her songs in a car commercial, Midler sued when the company hired one of her backup singers to impersonate her sound. “Ford was basically trying to profit from using her voice,” says Jennifer E. Rothman, a law professor at the University of Pennsylvania, who wrote a 2018 book called The Right of Publicity: Privacy Reimagined for a Public World. “Even though they didn't literally use her voice, they were instructing someone to sing in a confusingly similar manner to Midler.”
It doesn’t matter whether a person’s actual voice is used in an imitation or not, Rothman says, only whether that audio confuses listeners. In the legal system, there is a big difference between imitation and simply recording something “in the style” of someone else. “No one owns a style,” she says.
Other legal experts don’t see what OpenAI did as a clear-cut impersonation. “I think that any potential ‘right of publicity’ claim from Scarlett Johansson against OpenAI would be fairly weak given the only superficial similarity between the ‘Sky’ actress' voice and Johansson, under the relevant case law,” Colorado law professor Harry Surden wrote on X on Tuesday. Frye, too, has doubts. “OpenAI didn’t say or even imply it was offering the real Scarlett Johansson, only a simulation. If it used her name or image to advertise its product, that would be a right-of-publicity problem. But merely cloning the sound of her voice probably isn’t,” he says.
But that doesn’t mean OpenAI is necessarily in the clear. “Juries are unpredictable,” Surden added.
Frye is also uncertain how any case might play out, because he says right of publicity is a fairly “esoteric” area of law. There are no federal right-of-publicity laws in the United States, only a patchwork of state statutes. “It’s a mess,” he says, although Johansson could bring a suit in California, which has fairly robust right-of-publicity laws.
OpenAI’s chances of defending a right-of-publicity suit could be weakened by a one-word post on X—“her”—from Sam Altman on the day of last week’s demo. It was widely interpreted as a reference to Her and Johansson’s performance. “It feels like AI from the movies,” Altman wrote in a blog post that day.
To Grimmelmann at Cornell, those references weaken any potential defense OpenAI might mount claiming the situation is all a big coincidence. “They intentionally invited the public to make the identification between Sky and Samantha. That's not a good look,” Grimmelmann says. “I wonder whether a lawyer reviewed Altman's ‘her’ tweet.” Combined with Johansson’s revelations that the company had indeed attempted to get her to provide a voice for its chatbots—twice over—OpenAI’s insistence that Sky is not meant to resemble Samantha is difficult for some to believe.
“It was a boneheaded move,” says David Herlihy, a copyright lawyer and music industry professor at Northeastern University. “A miscalculation.”
Other lawyers see OpenAI’s behavior as so manifestly goofy they suspect the whole scandal might be a deliberate stunt—that OpenAI judged that it could trigger controversy by going forward with a sound-alike after Johansson declined to participate but that the attention it would receive from seemed to outweigh any consequences. “What’s the point? I say it’s publicity,” says Purvi Patel Albers, a partner at the law firm Haynes Boone who often takes intellectual property cases. “The only compelling reason—maybe I’m giving them too much credit—is that everyone’s talking about them now, aren’t they?”
457 notes
·
View notes
Text
RECENT UPDATES ON THE BAD INTERNET CALIFORNIA BILLS:
Sadly, both AB1949 and SB976 passed and are now on their way to the governors desk.
We need him to veto them so they dont become Law.
If you havent Heard of the danger of those bills for the Internet , this post explain it thoroughly :
- Post doing a deep explanation on those bills here
I CANNOT emphasize enough how these would have a global effect on the Internet given that most websites and apps originates from California and not all of them could afford either following those bills or moving states.
Now, as the bills are on their way to the governor, we need Californian citizens to voice their oppositions to those bills to the Governor Gavin Newsome HERE
(Non California peeps, we are urging you to share this as well!!! )
Please keep in mind that calling with phone is much,much more efficient.
You can also send faxes with Faxzero
Here are scripts you can use as arguments : (text/alt version below the read more )
Than you for reading. Even if youre not from California, please spread the word anyway ! Make posts,tweets,etc
REBLOGS ENCOURAGED
TEXT VERSION :
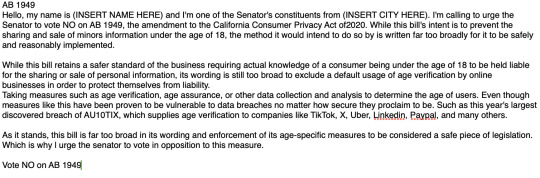
AB 1949
Hello, my name is (INSERT NAME HERE) and I'm one of the Senator's constituents from (INSERT CITY HERE). I'm calling to urge the Senator to vote NO on AB 1949, the amendment to the California Consumer Privacy Act of 2020. While this bill's intent is to prevent the sharing and sale of minor's information under the age of 18, the method it would intend to do so by is written far too broadly for it to be safely and reasonably implemented.
While this bill retains a safer standard of the business requiring actual knowledge of a consumer being under the age of 18 to be held liable for the sharing or sale of personal information, its wording is still too broad to exclude a default usage of age verification by online businesses in order to protect themselves from liability. Taking measures such as age verification, age assurance, or other data collection and analysis to determine the age of users. Even though measures like this have been proven to be vulnerable to data breaches no matter how secure they proclaim to be. Such as this year's largest discovered breach of AU10TIX, which supplies age verification to companies like TikTok, X, Uber, LinkedIn, Paypal, and many others.
As it stands, this bill is far too broad in its wording and enforcement of its age-specific measures to be considered a safe piece of legislation. Which is why I urge the Senator to vote in opposition to this measure.
Vote NO on AB 1949.
---------------------------
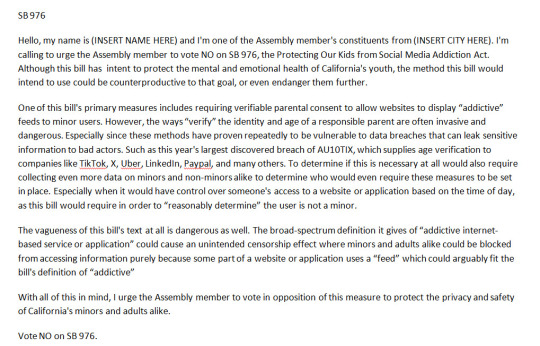
SB 976
Hello, my name is (INSERT NAME HERE) and I'm one of the Assembly member's constituents from (INSERT CITY HERE). I'm calling to urge the Assembly member to vote NO on SB 976, the Protecting Our Kids from Social Media Addiction Act. Although this bill has intent to protect the mental and emotional health of California's youth, the method this bill would intend to use could be counterproductive to that goal, or even endanger them further.
One of this bill's primary measures includes requiring verifiable parental consent to allow websites to display “addictive” feeds to minor users. However, the ways “verify” the identity and age of a responsible parent are often invasive and dangerous. Especially since these methods have proven repeatedly to be vulnerable to data breaches that can leak sensitive information to bad actors. Such as this year's largest discovered breach of AU10TIX, which supplies age verification to companies like TikTok, X, Uber, LinkedIn, Paypal, and many others. To determine if this is necessary at all would also require collecting even more data on minors and non-minors alike to determine who would even require these measures to be set in place. Especially when it would have control over someone's access to a website or application based on the time of day, as this bill would require in order to “reasonably determine” the user is not a minor.
The vagueness of this bill's text at all is dangerous as well. The broad-spectrum definition it gives of “addictive internet-based service or application” could cause an unintended censorship effect where minors and adults alike could be blocked from accessing information purely because some part of a website or application uses a “feed” which could arguably fit the bill's definition of “addictive”
With all of this in mind, I urge the Assembly member to vote in opposition of this measure to protect the privacy and safety of California's minors and adults alike.
Vote NO on SB 976.
346 notes
·
View notes
Text

URGENT! Stop KOSA!
Hey all, this is BáiYù and Sauce here with something that isn't necessarily SnaccPop related, but it's important nonetheless. For those of you who follow US politics, The Kids Online Safety Act passed the Senate yesterday and is moving forward.
This is bad news for everyone on the internet, even outside of the USA.
What is KOSA?
While it's officially known as "The Kids Online Safety Act," KOSA is an internet censorship masquerading as another "protect the children" bill, much in the same way SESTA/FOSTA claimed that it would stop illegal sex trafficking but instead hurt sex workers and their safety. KOSA was originally introduced by Sen. Edward Markey, D-Mass. and Bill Cassidy, R-La. as a way to update the 1998 Children’s Online Privacy Act, raising the age of consent for data collection to 16 among other things. You can read the original press release of KOSA here, while you can read the full updated text of the bill on the official USA Congress website.
You can read the following articles about KOSA here:
EFF: The Kids Online Safety Act is Still A Huge Danger to Our Rights Online
CyberScoop: Children’s online safety bills clear Senate hurdle despite strong civil liberties pushback
TeenVogue: The Kids Online Safety Act Would Harm LGBTQ+ Youth, Restrict Access to Information and Community
The quick TL;DR:
KOSA authorizes an individual state attorneys general to decide what might harm minors
Websites will likely preemptively remove and ban content to avoid upsetting state attorneys generals (this will likely be topics such as abortion, queerness, feminism, sexual content, and others)
In order for a platform to know which users are minors, they'll require a more invasive age and personal data verification method
Parents will be granted more surveillance tools to see what their children are doing on the web
KOSA is supported by Christofascists and those seeking to harm the LGBTQ+ community
If a website holding personally identifying information and government documents is hacked, that's a major cybersecurity breach waiting to happen
What Does This Mean?
You don't have to look far to see or hear about the violence being done to the neurodivergent and LGBTQ+ communities worldwide, who are oftentimes one and the same. Social media sites censoring discussion of these topics would stand to do even further harm to folks who lack access to local resources to understand themselves and the hardships they face; in addition, the fact that websites would likely store personally identifying information and government documents means the death of any notion of privacy.
Sex workers and those living in certain countries already are at risk of losing their ways of life, living in a reality where their online activities are closely surveilled; if KOSA officially becomes law, this will become a reality for many more people and endanger those at the fringes of society even worse than it already is.
Why This Matters Outside of The USA
I previously mentioned SESTA/FOSTA, which passed and became US law in 2018. This bill enabled many of the anti-adult content attitudes that many popular websites are taking these days as well as the tightening of restrictions laid down by payment processors. Companies and sites hosted in the USA have to follow US laws even if they're accessible worldwide, meaning that folks overseas suffer as well.
What Can You Do?
If you're a US citizen, contact your Senators and tell them that you oppose KOSA. This can be as an email, letter, or phone call that you make to your state Senator.
For resources on how to do so, view the following links:
https://www.badinternetbills.com/#kosa
https://www.stopkosa.com/
https://linktr.ee/stopkosa
If you live outside of the US or cannot vote, the best thing you can do is sign the petition at the Stop KOSA website, alert your US friends about what's happening, and raise some noise.
Above all else, don’t panic. By staying informed by what’s going on, you can prepare for the legal battles ahead.
#stop KOSA#KOSA#censorship#us law#somethings wrong with sunny day jack#the groom of gallagher mansion#dachabo
2K notes
·
View notes
Text
First, let’s address the fact that hackers recently accessed the personal data of about 14,000 23andMe customers. Because of how 23andMe works—it has a “DNA Relatives” feature that lets users find people they are probably related to—this breach created 6.9 million “other users” who had data stolen in the breach, according to reporting by TechCrunch. This data included people’s names, birth year, relationships, percentage of DNA shared with other 23andMe users, and ancestry reports.
[...]
Getting your DNA or your loved ones’ DNA sequenced means you are potentially putting people who are related to those people at risk in ways that are easily predictable, but also in ways we cannot yet predict because these databases are still relatively new. I am writing this article right now because of the hack, but my stance on this issue has been the same for years, for reasons outside of the hack.
In 2016, I moderated a panel at SXSW called “Is Your Biological Data Safe?,” which was broadly about the privacy implications of companies and other entities creating gigantic databases of people’s genetic code. This panel’s experts included a 23andMe executive as well as an FBI field agent. Everyone on the panel and everyone in the industry agrees that genetic information is potentially very sensitive, and the use of DNA to solve crimes is obviously well established.
At the time, many of the possible dangers of providing your genome to a DNA sequencing company were hypothetical. Since then, many of the hypothetical issues we discussed have become a reality in one way or another. For example, on that panel, we discussed the work of an artist who was turning lost strands of hair, wads of chewing gum, and other found DNA into visual genetic “portraits” of people. Last year, the Edmonton Police Service, using a company called Parabon, used a similar process to create 3D images of crime suspects using DNA from the case. The police had no idea if the portrait they generated actually looked like the suspect they wanted, and the practice is incredibly concerning.
To its credit, 23andMe itself has steadfastly resisted law enforcement requests for information, but other large databases of genetic information have been used to solve crimes. Both 23andMe and Ancestry are regularly the recipients of law enforcement requests for data, meaning police do see these companies as potentially valuable data mines.
753 notes
·
View notes
Text
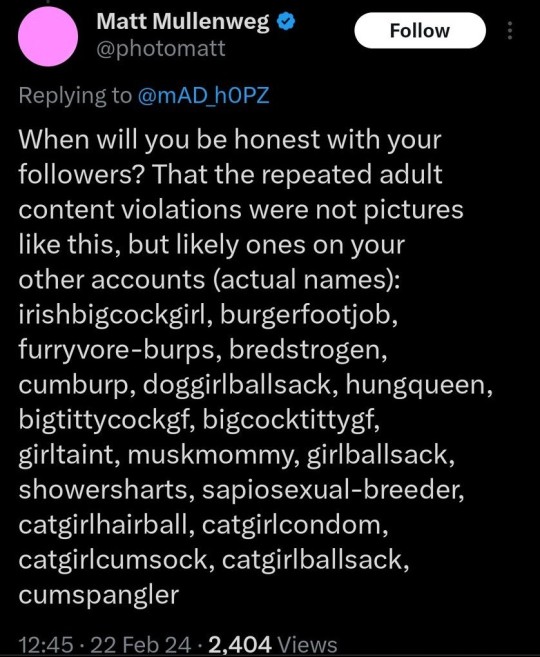
by listing predstrogens sideblogs, matt is EXPOSING INFORMATION THAT IS ONLY VISIBLE AT AN ADMINISTRATOR LEVEL. under regular circumstances, you CANT see another users sideblogs. as per TUMBLRS PRIVACY POLICY. violating this is tantamount to a data breach like sharing someones password. a hacker might stuff your credentials and publish the names of your sideblogs to a pastebin — but this is a high-profile ceo digging into the database of his website to pull out confidential data and PUBLICALLY ANNOUNCE IT to slander someone for a personal vendetta. this would be a clear violation of privacy laws in my country and hes out of his mind
322 notes
·
View notes
Text
Misunderstandings
In Gotham, you stalk your friends and family to show how much you care about them. You could be doing other things, but instead you're following them around to make sure they're safe, happy, not an imposter and in their right mind.
This is distinguished from creepy stalking or tailing a mark by the fact that you intentionally don't use your full skill and try to subtly tip them off to your presence, so that they can signal that they want privacy or a face-to-face conversation by starting evasive maneuvers or stalking you back.
It's also rude to acknowledge the fact that you know someone was stalking you, and polite to act surprised that they showed up "out of nowhere", as a marker of respect for their skill. Only children get called out for stalking others affectionately, and they usually get tips on being harder to find after the person being stalked calls them out.
The Bats also have a very skewed perception of what is normal stealth and counter-evasion skills, since everyone over the age of ten in Gotham knows how to throw a tail, spot someone they know stalking them and stalk them back with skill to rival an undercover law enforcement agent in any other city.
They also assumed that as heroes, the rest of the League would have skill at least on par with the average GCPD officer, even if they are probably not on the level of the Bats.
However, the League are barely more perceptive than the average Gothamite teenager, and as such they legitimately don't notice the Bats stalking them, and are actually startled by the Bats showing up out of nowhere.
And when the League tries to tail them back, the Bats notice them within ten seconds and let them follow them around as long as it isn't a potential identity breach, then suddenly disappear from sight once it is.
The end result(combined with some other aspects of Gothamite culture and the Bats' usage of fear and uncertainty as a weapon against Outsiders) is that the Bats think that the League are being unusually polite by always pretending to be surprised even when it was blatantly obvious that they were there, and the League is convinced they're the spawn of some all-seeing and perpetually unseen eldritch horror.
74 notes
·
View notes
Text










I never wind down. Got to stay in the moment, stay focused. The world is spinning out of control, people. No time for distractions. Cos that’s what The Man wants, man. Wants you dumbed down, diverted, head stuck in a smartphone or computer screen. Like you are right now. Yeah, I see you. Russel’s watching you. I mean, I’m not actually watching you, that would be messed up. And breach a ton of privacy laws. But the point is… what was my point… uh… oh yeah, FOCUS!
141 notes
·
View notes
Note
absolutely love your writing 😭 you write law so in character its so good. i want to see laws reaction to reader accidentally (or not) discovering his nerdy sora comics collection. ty 💛
Hi!! Thank-you so much, that's an honor 🥺 I'm a lil obsessed w him istg (more than a little but anyways) here you go, I hope you enjoy it!!

You're acting weird. To be fair though, in a crew as diverse as the Heart Pirates, "weird" is a subjective thing and depends on who Law is meaning.
You're acting weird for you. There's an odd jumpiness to you now, specifically whenever Law is involved ㅡ and he wonders if he's done something wrong.
Your relationship is still fairly new to you both, still trying to find the perfect balance between professionalism and something softer and more intimate.
Law mentally filters through your interactions (both as crewmates and not) and when he comes up with nothing, he decides to ask you.
"Have I done something to upset you? I'd like to know so I can fix it." He watches confusion flicker across your face, then guilt.
"No, you didn't do anything." You bite your lip, a habit he's been trying to break you of. Instinctively, he reaches to press his thumb against your bottom lip, tugging it free of the worried knead of your teeth. "Promise you won't be mad?"
Now it's Law's turn to be confused. "It depends on what you did," he answers honestly and immediately kicks himself for the way you shrink back. "As long as it has nothing to do with the integrity the Polar Tang and you haven't sold us out to the Marines, it can't be that bad."
That at least gets a ghost of a smile from you. "As if I'd ever do either of those," you tell him, a hint of pride in your voice. The Polar Tang is your home, and the Heart Pirates are your family.
"Continue," he prods gently, and the nervousness returns to your expression. He gives you a moment, watches as you steel yourself before you blurt in a tumbled rush of words,
"I maybe sort of accidentally found your Sora Warrior of the Sea comics."
It takes him a long moment to parse out what you've said, and you watch as his expression shifts to an unreadable one, brim of his hat shadowing his eyes.
"I'm so sorry," you say, feeling even worse than you have the last couple of days. "I didn't mean to, honest. Bepo needed a copy of a report from a few days ago and I thought I'd seen you put it in one of the drawers andㅡ" You halt, voice wavering. "I'm really sorry."
You mean it. He knows you do, knows you'd never breach his privacy without good reason ㅡ even as close as you are now, there are things he's not ready to talk about, or show.
In the grand scheme of things, the discovery of his carefully curated collection of beloved comics is not the end of the world. Hardly a punishable offense, even though you're clearly expecting him to be pissed.
"It's okay, [Name]." He watches as you visibly relax, though there's still a nervous edge to you. "I'm not upset, just...surprised."
"Understandable," you mumble. "For what it's worth, it's a nice collection. I wanted to get into it when I was younger, but I never got a chance to."
He perks up a little at that, latches onto the opportunity you've given him. "If you'd like," he says, "we can read them together. If you want, I mean."
Another little flake off that careful barrier he's built around himself, another soft spot exposed ㅡ trusting you not to abuse it. As if you ever would ㅡ his trust in you is one of your most teasured things.
"Law?" He looks at you, taking in that wonderful smile he'd do unspeakable things to protect. "I'd love that."
#ㅡmine.#one piece x reader#one piece scenario#trafalgar law x reader#law x reader#ㅡanswered.#anonymous#–ml: law.#last post for tonight so i don't spam the tag wkdkdjd goodnight!
312 notes
·
View notes
Text
Loving all the memes and social backlash coming out of musks twitter takeover but the financial/legal side is also super funny cause he had to take a $13 billion dollar loan at 8% interest which amounts to interest repayments of about $1 billion a year which is hilarious when you consider twitters peak revenue was only ever about $700 million (and that's revenue, not profit).
And Twitter was being watched by the US fair trade commission for data privacy breaches in the past and had to set up a committee to overlook its data handling But most of the members of that committee have either been fired or resigned, meaning twitter could be liable for billions worth of fines. The FTC said they are watching the developments at Twitter with "deep concern" lmao
Plus all the illegal layoffs could open musk up to hundreds of millions in class action law suits which have already begun
All this is on top of musks other problems like, oh idk him losing $100 billion dollars in net worth in the last few months. It's a good time all round baby
We love to see it 👌👌👌
2K notes
·
View notes
Note
how do we feel about yandere ritsu!!!!!!!!!!!
I FIND HIM SO TOUGH TO WRITE ABOUT DKDJSJSHDHSHSDJSH let's see!! He's such a rigid person, very hard to deviate from his beliefs and his habits. He's STUBBORN AS HELL and he already has the whole "breach of privacy" thing that most yanderes have, what with him recording everyone around him and even noticing how many times MC sighs, SO!!!!!!! How would these traits look if we twist them a little bit?
I think Ritsu wouldn't be physically violent at all because he would just use information in his favor in order to manipulate you. Even when it doesn't make sense. He'll find loopholes and reasonings where there aren't any, insane excuses for his behavior in his books because he's soon to be the best lawyer in Japan, right? He'll know how to mold the law the way he needs, just to control you completely. He'll plant cameras and recorders in your rooms, in your bags, in your clothes, and watch your every step with a special notebook
(and if he hears you doing something very private, trust that he'll be more than elated and keep that file safe in a secret folder)
He'd have mountains upon mountains of "evidence" to use against you and to create the perfect profile. And if you don't act in accordance with his predictions? Oh, you're gonna need to explain yourself properly because no one knows your habits better than him. Not even yourself.
48 notes
·
View notes
Note
lmao take this with a grain of salt but reddit comments are saying that alpine may have broken uk privacy laws/esteban potentially has grounds for a lawsuit by tracking the company car outside of working hours???
https://www.reddit.com/r/formula1/comments/1edo9sv/marcin_budkowski_revealed_that_alpine_found_out/
I would tend to agree with them I mean of course none of us know the ins and outs of the situation but the UK has pretty strict privacy laws (GDPR) and whilst I'm sure all their company cars are tracked with GPS the legality of accessing that data would be very strict and they would need a legitmate reason for doing so. Checking up on where your employee is going in their private time would not be considered a legit reason under any circumstance save suspicion of criminal activity or something. And not to mention that not only was that information accessed, it was then seemingly spread to multiple Alpine employees, who in turn spread it to the press and we can assume that's where all the Ocon/Williams rumours came from in the last few weeks.
Like disregard the fact it was Williams he visited for a moment and let's say instead it was a hospital. So they have checked his GPS because [insert dodgy reason here] and found he spent 5 hours at a hospital. They then tell other staff this. They then spread it to the press. Then the media would be speculating about why he was at a hospital. That would be a pretty insane (and illegal) breach of privacy, right?
#regardless of whether they were legally allowed to access that information it was still spread to people who didn't need to know.#which is also illegal#so 🤷♂️#ask#f1#esteban ocon
59 notes
·
View notes