#software monitoring
Explore tagged Tumblr posts
Text


The Matrix: Resurrections (2021)
#the matrix resurrections#cyberpunk#movies#office#computers#tech#keanu reeves#scifi#monitors#cyberpunk aesthetic#programming#coding#software engineering#gifs#the matrix#3d animation#motion graphics#graphics design
214 notes
·
View notes
Text
ok i blocked him but also i really do hope that guy gets to a point of like, not hating himself so much. like, if you're in the kind of relationship that requires you to be perfomatively totally cool with your own mistreatment and complicit in your own oppression/silencing, that'll fuck you up. i too used to think misandry was a personality trait and loudly hating men was praxis, and then I got out of a bunch of shitty interpersonal relationships and bad situations and learned that bioessentialism is Bad, Actually.
#also lol at the idea of#'trans men don't have unique problems get off tumblr'#like... buddy#i was pregnant#as a man#did you know that standard birth monitoring software at hospitals doesn't work if the patient has an M gender marker?#like it literally does not work the system cannot do it.#that software monitoring your vitals and your contractions and the baby's vitals#cannot be connected to a patient's profile if they're marked 'male'#what is that if not medial transandrophobia?#and that's just one thing#for fucks sake
48 notes
·
View notes
Text


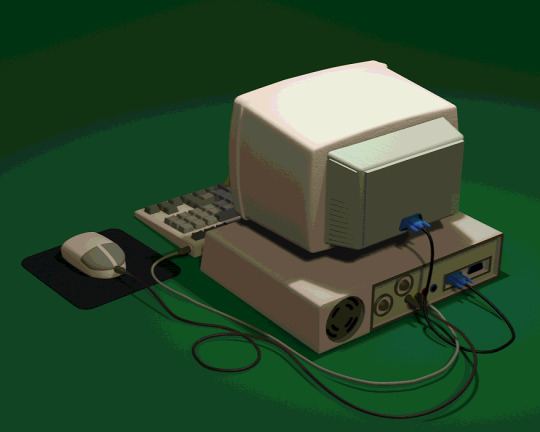

🖳 NEW! NUCLEAR ELECTRICS CRT1 Model 69 🖳
➮ With Interactive Virtual Assistant CiCi PC
➮ State of the art Graphics Integration
➮ Color and Contrast adjustment never before seen
The CRT1-M-69 is a perfect addition to your home life and your work life alike. Unlike older computers CRT1-M-69 is equipped with an integrated graphics interface (no more pesky lines of code), our CiCi PC Virtual Assistant, and 'round the clock support!
Purchase Today for $420.69 ᵒʳ ʲᵘˢᵗ ᵗʷᵉˡᵛᵉ ᵉᵃˢʸ ᵖᵃʸᵐᵉⁿᵗˢ ᵒᶠ ᵗʰᶦʳᵗʸᶠᶦᵛᵉ ᶠᶦᶠᵗʸᶠᶦᵛᵉ

#blender 4.1#blender 3d#3d model#3d modelling software#3d render#old computers#fake ads#fake advertisement#fake advertising#CiCi tv#OC#my OC#original character#donut posting#vintage computer#casette futurism#robot oc#robot girl#objectum#techcore#old tech#retro tech#crt monitor#crt
101 notes
·
View notes
Text
Imogen would be the worst micromanager in the office
#cr spoilers#critical role#c3#c3e79#op#imogen#office team: has issues#manager: deploys monitoring software
177 notes
·
View notes
Text

instagram: cheri.png
#pov I turn on my computer to work and upload on tumblr#I’ve been on a hardware roll#and I’m supposed to be software girl lol#crt monitor#windows xp#cybercore#old internet#old web#y2k#00s#cyber y2k#2000s#moodboard#tech#cyber core#old computers#retro tech#techcore#desk setup#tech blog#nostalgia#old windows#old microsoft#microsoft#nostalgiacore
348 notes
·
View notes
Text
Today's show was so overhwelmingly chaotic that I had to use my inhaler TWICE (I've been trying to only use it once a day to see how my lungs are doing). But as chaotic and exhausting as it was... Goddamn I'm good at what I do.
While they were diagnosing a problem and working through Plan A, I set up Plan F by myself while 6 people stood around watching Plan A-C fail.
And when they yelled that the show would have to be canceled this week, I had Plan F up, set, running, and it was what I told them to do from the start.
Why is there only Plan A-C, then suddenly Plan F?
My Plan was always Plan F, for "Fuck it, we bail".
#i deserve this peanut butter cookie goddammit#the teleprompter system that's been failing for MONTHS finally kicked the bucket just before we were to film the show#and by the time they finally admitted it couldn't be saved i already had a backup system running#with the script fully loaded and formatted into a teleprompting software on my PC and had set up a monitor under the camera#it didn't have to be chaos but why tf did it take 6 people to watch 2 idiot engineers realize#they couldn't save THE COMPUTER THAT STILL RAN ON WINDOWS VISTA
11 notes
·
View notes
Text
Now that I think about it, I *should* write a long post about why Ganondorf is the best wife ever actually.

How do you not look at him being genuinely happy for two seconds and not say “wife” you know what I mean 🥺🥺🥺
#ganonthots#if you must know why im more terminally online than usual today#monitoring a software landscape#im about to clock out now doe so#so long! time to swim in the virtual ocean!
19 notes
·
View notes
Text

#infinity nikki#my in pics#i should be doing editing on some alternate software bc like. my pc monitor has whack saturation values#that make everything look nicer#and then i look at it on my phone and im like#....?
5 notes
·
View notes
Text
was playing games and then immediately went to making weiss icons and
i thought weiss was a streamer for a second what the fuck is wrong with my brain-
9 notes
·
View notes
Text


Devs (2020)
#devs#scifi#movies#office#computers#tech#monitors#cyberpunk aesthetic#programming#coding#software engineering#3d animation#motion graphics#graphics design#developers & startups#stephen mckinley henderson#alison pill#alex garland#cailee spaeny
115 notes
·
View notes
Text
So I realized that at my big age (I'm still a child) I've built a lot of lore with my bare hands so I'm going to do a fun fact run down!
I'm a Wikipedia editor
I'm a VERY popular Ao3 author in a fandom (it's a small fandom lmao, not hard to be popular)
I've written multiple stories on wattpad that were very popular, the earliest of which I wrote at 9 years old
I am quite literally infamous at my junior high (despite being multiple years removed from that school), and younger friends have told me that teachers have liked them less when they tell them that they're friends with me
I have seconds away from death at least twice that I can remember
A friend in 6th grade tried to use my blood for rituals
I've given multiple "Ted-talks" on things I'm disgustingly educated on at school that people have left their classes to attend
I was a big part of the country humans subreddit at the big age of 8 years old
#I love fun facts#And in case you're curious#No my parents don't know about half of these#I learned how to break the monitor software on my phone at 7 years old#(it wasn't that hard)
4 notes
·
View notes
Text

This report fron my sleep tracker is trying to recommend a healthier pattern for me based upon and my recent struggles to sleep well.
I am not going to alt text all of the contents because they are not relevant.
It says that my "ideal wake time" is between 3:00 p.m. and 4:00 p.m.
It goes on to recommend that I have my daily exercise between 2:15 p.m. and 3:15 p.m.
It has been a very long time since I exhibited any signs of sleepwalking.
I don't think I can reasonably go along with starting a exercise program 45 minutes before I should be trying to wake up.
This is why I do not want a self-driving car.
#the computer does not think#the computer does not reason#sleep monitor software has a bug in the code somewhere#sleep monitor device not programmed to work with adhd disordered sleep#wake up at four. time travel back an hour. conduct physical activity.#no alt text bc relevant content described in prose
2 notes
·
View notes
Text

Wolfenstein 3D, iD Software, PC
Recalbox OS, Native:ecwolf port
800x600 IR, 640x480 external, bicubic upscaling
Mac/Jaguar/3DO graphics pack w/rotation sprites
Raspberry Pi 4 OC to 2Ghz
Toshiba 19A26 19" CRT TV
Wireless XBox 360 controller with evil backplate
#retro#video games#crt tv#wolfenstein#Wolf3D#pc games#ms dos#id software#port#ecwolf#Recalbox#crt monitor#retro game#fps#fps games#retro fps#mods#raspberry pi#kama arcade#homearcade#home arcade#tamara kama
3 notes
·
View notes
Text
Discover top-quality laptops, computers, gaming accessories, tech gadgets, and computer accessories at Matrix Warehouse. Shop online or in-store across South Africa for unbeatable prices and nationwide delivery. Visit now!
#Laptops & Accessories#Desktop Computers#Smart Devices#Computer Hardware#Monitors & Projectors#Computer Accessories#Backup Power Solutions#Printers and Printer Toners#Networking Equipment#Computer Software
2 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Whether your goal is to monitor billable hours for a project or assess your team's efficiency, documenting employee work hours proves highly advantageous.
Yet, relying on conventional time-tracking techniques such as punch clocks and paper forms can be cumbersome and susceptible to human errors. Alternatively, opting for automated timesheets streamlines the time-tracking process, enhancing overall productivity.
This article will delve into the concept of automated timesheets, outlining their three primary benefits and highlighting the drawbacks of traditional time-tracking methods. Additionally, we will examine the leading timesheet automation tool currently available. Finally, we'll offer four valuable tips for seamlessly implementing timesheet automation.
click to know more about monitoring software: https://flowace.ai/employee-monitoring-software/
3 notes
·
View notes