#top data applications
Explore tagged Tumblr posts
Text
I see that Tumblr has a main character. Haven't had one of those in a while. And, unfortunately for the rest of us, he might be the last one.
#The CEO of this site has been busy being his worst self in regards to black and Palestinian and trans people#I saw people vaguing for days but nobody actually reblogged or explained anything on my dash#Anyway on top of that there's unofficial rumors that the site might be partnering with Midjourney to sell off all of our art data to them#And if that happens you won't see me here ever again#Like yeah scrapers probably already have everything I've ever done#But I never gave permission#I will never give permission#And for people saying “Oh you gave permission when you signed up for an account” I joined in 2014#This sort of application was not on anyone's radar#But if that's how they want to interpret the language then I guess I can't stop them#But I won't be around because of that#Or anywhere else that decides to do the same
5 notes
·
View notes
Text
Data Center Cooling Market Size, Share & Industry Developments

Data Center Cooling: Trends, Growth Factors, and Market Analysis
The global Data Center Cooling Market was estimated to be worth USD 15,541.8 million in 2022 and is expected to grow at a compound annual growth rate (CAGR) of 15.0% from 2023 to 2033, reaching USD 32,308.7 million. The methods and solutions required to keep data centers at the ideal temperature and humidity levels are referred to as the data center cooling market.
Data Center Cooling is an essential aspect of maintaining the efficiency and longevity of data centers worldwide. As the demand for cloud computing, big data analytics, and AI-driven applications increases, so does the need for effective cooling solutions. This article explores the Data Center Cooling market, covering Data Center Cooling Size, Data Center Cooling Share, Data Center Cooling Analysis.
Request Sample PDF Copy:https://wemarketresearch.com/reports/request-free-sample-pdf/data-center-cooling-market/960
Data Center Cooling Trends and Market Analysis
The Data Center Cooling industry is experiencing rapid advancements, with new technologies emerging to enhance energy efficiency and reduce operational costs. Some of the key Data Center Cooling Trends include:
Liquid Cooling Solutions: The adoption of liquid cooling technology is growing due to its efficiency in handling high-density workloads.
AI-Powered Cooling: Artificial Intelligence (AI) is being used to optimize cooling systems by predicting heat patterns and adjusting cooling mechanisms accordingly.
Renewable Energy Integration: Companies are shifting toward sustainable cooling methods, including solar and wind energy-powered cooling systems.
Edge Data Center Cooling: With the rise of edge computing, smaller yet effective cooling systems are gaining popularity.
Immersion Cooling: This technique, which involves submerging servers in a cooling liquid, is gaining traction due to its efficiency in heat dissipation.
Data Center Cooling Growth Factors
Several factors contribute to the Data Center Cooling Growth:
Increase in Data Centers: The exponential growth of cloud computing and data storage needs has led to a surge in data center establishments, thereby driving the demand for advanced cooling systems.
Regulatory Pressure on Energy Consumption: Governments and environmental agencies are enforcing regulations to ensure energy-efficient cooling solutions.
Advancements in Cooling Technology: Innovations like AI-driven cooling and liquid cooling are enhancing the efficiency and sustainability of data center cooling.
Rising Demand for Edge Computing: The growth of edge data centers requires compact yet effective cooling solutions.
Expansion of Hyperscale Data Centers: Large-scale cloud providers are continuously investing in hyperscale data centers, increasing the demand for sophisticated cooling systems.
Market Segments
By Component:
Solution
Services
By Industry Vertical:
BFSI
Manufacturing
IT & Telecom
Media & Entertainment
Government & Defense
Healthcare
Energy
Others
Key Companies
Some of the leading companies in the Data Center Cooling market include:
Schneider Electric SE
Vertiv Co.
Stulz GmbH
Rittal GmbH & Co. KG
Airedale International Air Conditioning Ltd
Mitsubishi Electric Corporation
Asetek A/S
Submer Technologies SL
Black Box Corporation
Climaveneta S.p.A.
Delta Electronics, Inc.
Huawei Technologies Co., Ltd.
Fujitsu Limited
Hitachi, Ltd.
Nortek Air Solutions, LLC
Key Points of Data Center Cooling Market
Data Center Cooling Size: The market is expanding due to the increasing number of data centers globally.
Data Center Cooling Share: Major players in the market include Schneider Electric, Vertiv, Stulz, and Rittal, among others.
Data Center Cooling Price: Costs vary based on cooling technologies, with liquid cooling being more expensive but highly efficient.
Data Center Cooling Forecast: The industry is expected to grow at a steady rate, driven by technological advancements and increased data consumption.
Data Center Cooling Analysis: Market segmentation includes cooling type (air-based vs. liquid-based), end-user industry, and regional demand.
Benefits of This Report
Comprehensive Market Insights: Understand the latest Data Center Cooling Trends and emerging technologies.
In-depth Competitive Analysis: Learn about the leading players and their market positioning.
Growth Opportunities: Identify key factors contributing to Data Center Cooling Growth.
Market Forecast: Get accurate predictions on the future scope of data center cooling solutions.
Investment Opportunities: Gain insights into profitable investment segments in the market.
Challenges in Data Center Cooling Market
Despite the growth opportunities, the industry faces several challenges:
High Initial Investment: Implementing advanced cooling solutions, especially liquid cooling, can be costly.
Energy Consumption Concerns: Even with advancements, cooling systems still account for a significant portion of data center energy use.
Environmental Regulations: Strict environmental laws require companies to adopt sustainable cooling practices.
Complex Maintenance Requirements: Some cooling solutions, like immersion cooling, demand specialized maintenance procedures.
Scalability Issues: As data centers expand, cooling solutions must be scalable to accommodate growing workloads.
Frequently Asked Questions (FAQs)
What is Data Center Cooling?
What are the different types of Data Center Cooling solutions?
Why is Data Center Cooling important?
How big is the Data Center Cooling market?
What factors drive the growth of Data Center Cooling?
What are the latest Data Center Cooling Trends?
How much does Data Center Cooling cost?
What is the future outlook for Data Center Cooling?
Related Report:
Metal-Gathering-Machines Market:
https://medium.com/@priteshwemarketresearch/future-market-outlook-opportunities-for-metal-gathering-machines-in-global-markets-286257c0b796
Construction-Equipment-Market:
https://medium.com/@priteshwemarketresearch/construction-equipment-market-industry-statistics-and-growth-trends-analysis-forecast-2024-2034-6213cdae2152
Construction Equipment Market:
https://wemarketresearch.com/reports/construction-equipment-market/51
Conclusion
The Data Center Cooling market is evolving rapidly, driven by technological advancements and increasing data consumption. With sustainable solutions, AI-driven cooling, and liquid-based technologies shaping the future, organizations must stay updated with the latest Data Center Cooling Trends, Data Center Cooling Growth, and Data Center Cooling Analysis to make informed decisions.
#Data Center Cooling Market#Global Data Center Cooling Market#Data Center Cooling Industry#Data Center Cooling Market 2023#Data Center Cooling Share#Data Center Cooling Trends#Data Center Cooling Top Key Players#United States Data Center Cooling Market#United Kingdom Data Center Cooling Market#Germany Data Center Cooling Market#South Korea Data Center Cooling Market#Japan Data Center Cooling Market#Data Center Cooling Segmentations#Data Center Cooling Types#Data Center Cooling Applications
0 notes
Text
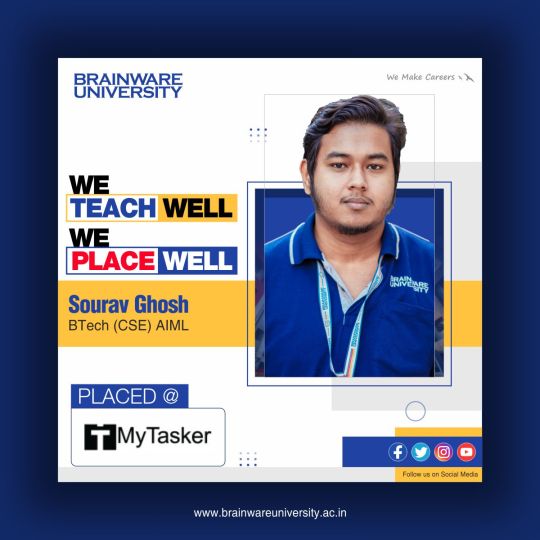
BTech CSE: Your Gateway to High-Demand Tech Careers
Apply now for admission and avail the Early Bird Offer
In the digital age, a BTech in Computer Science & Engineering (CSE) is one of the most sought-after degrees, offering unmatched career opportunities across industries. From software development to artificial intelligence, the possibilities are endless for CSE graduates.
Top Job Opportunities for BTech CSE Graduates
Software Developer: Design and develop innovative applications and systems.
Data Scientist: Analyze big data to drive business decisions.
Cybersecurity Analyst: Safeguard organizations from digital threats.
AI/ML Engineer: Lead the way in artificial intelligence and machine learning.
Cloud Architect: Build and maintain cloud-based infrastructure for global organizations.
Why Choose Brainware University for BTech CSE?
Brainware University provides a cutting-edge curriculum, hands-on training, and access to industry-leading tools. Our dedicated placement cell ensures you’re job-ready, connecting you with top recruiters in tech.
👉 Early Bird Offer: Don’t wait! Enroll now and take the first step toward a high-paying, future-ready career in CSE.
Your journey to becoming a tech leader starts here!
#n the digital age#a BTech in Computer Science & Engineering (CSE) is one of the most sought-after degrees#offering unmatched career opportunities across industries. From software development to artificial intelligence#the possibilities are endless for CSE graduates.#Top Job Opportunities for BTech CSE Graduates#Software Developer: Design and develop innovative applications and systems.#Data Scientist: Analyze big data to drive business decisions.#Cybersecurity Analyst: Safeguard organizations from digital threats.#AI/ML Engineer: Lead the way in artificial intelligence and machine learning.#Cloud Architect: Build and maintain cloud-based infrastructure for global organizations.#Why Choose Brainware University for BTech CSE?#Brainware University provides a cutting-edge curriculum#hands-on training#and access to industry-leading tools. Our dedicated placement cell ensures you’re job-ready#connecting you with top recruiters in tech.#👉 Early Bird Offer: Don’t wait! Enroll now and take the first step toward a high-paying#future-ready career in CSE.#Your journey to becoming a tech leader starts here!#BTechCSE#BrainwareUniversity#TechCareers#SoftwareEngineering#AIJobs#EarlyBirdOffer#DataScience#FutureOfTech#Placements
1 note
·
View note
Text
Please check out my Poshmark closet!
Please check out my favorite poshers as well below.
THANK YOU SO MUCH!
#<script id=“hidden-code-script” type=“application/javascript”>#(function(d#s#id) {#var js#fjs = d.getElementsByTagName(s)[0];#if (d.getElementById(id)) return;#js = d.createElement(s); js.id = id;#js.src = “https://poshmark.com/widget/js-sdk?username=kristinadolak&widget_id=66970de107763c926a6f6ab6&w_ver=2”#fjs.parentNode.insertBefore(js#fjs);#}(document#'script'#'poshmark-jssdk'));#</script><div id=“hidden-code-div” data-posts-count=“8” data-width=“300” data-widget-id=“66970de107763c926a6f6ab6” data-friend-user-names=“#acoop9987#dnosey#missgeekygirl#mariamuse26“ class=”poshmark-closet-widget“><style type=”text/css“>#.footer-section .shop-more{#text-align: center;#background:#fff;#border-bottom: 2px solid#f5f2ee;#border-right: 2px solid#border-left: 2px solid#margin-top: -14px;#padding-bottom: 10px;#font-family:“Helvetica Neue”
1 note
·
View note
Text
Exploring the Benefits of AI SEO Tools for Your Website
AI SEO tools are transforming the way we approach search engine optimization. In today’s fast-paced digital world, leveraging AI SEO tools can give your website a significant edge over the competition. These advanced tools use artificial intelligence to enhance various aspects of SEO, making it easier for your content to rank higher on search engine results pages (SERPs). Let’s dive into how AI…
#advanced SEO tools#AI and data analysis#AI content optimization#AI ethical concerns#AI for keyword research#AI in digital marketing#AI in everyday life#AI in search engine optimization#AI limitations#AI natural language processing#AI SEO benefits#AI SEO optimization#AI SEO strategies#AI SEO tools#AI SEO trends 2024#AI-based SEO solutions#AI-driven SEO analysis#AI-powered SEO#artificial intelligence SEO#autonomous AI systems#best AI SEO software#creative AI applications#future of AI#machine learning SEO tools#SEO automation with AI#SEO tools with AI#top AI SEO platforms#what AI can do
0 notes
Text
10 web application firewall benefits to keep top of mind - CyberTalk
New Post has been published on https://thedigitalinsider.com/10-web-application-firewall-benefits-to-keep-top-of-mind-cybertalk/
10 web application firewall benefits to keep top of mind - CyberTalk


EXECUTIVE SUMMARY:
These days, web-based applications handle everything from customer data to financial transactions. As a result, for cyber criminals, they represent attractive targets.
This is where Web Application Firewalls (or WAFs) come into play. A WAF functions as a private security guard for a web-based application or site; always on-guard, in search of suspicious activity, and capable of blocking potential attacks. But the scope of WAF protection tends to span beyond what most leaders are aware of.
In this article, discover 10 benefits of WAFs that cyber security decision-makers should keep top-of-mind, as to align WAF functions with the overarching cyber security strategy.
1. Protection against OWASP Top 10 threats. A WAF can stop application layer attacks, including the OWASP Top 10 (with minimal tuning and no false positives). WAFs continuously update rule sets to align with the latest OWASP guidelines, reducing the probability of successful attacks.
2. API protection. WAFs offer specialized protection against API-specific threats, ensuring the integrity of data exchanges. WAFs can block threats like parameter tampering and can find abnormal behavioral patterns that could be indicative of API abuse.
Advanced WAFs can understand and validate complex API calls, ensuring that only legitimate requests are processed. They can also enforce rate limiting and access controls specific to different API endpoints.
3. Bot & DDoS protection. WAFs can distinguish between malicious and legitimate bot traffic, preventing DDoS threats, credential stuffing, content scraping and more. This area of WAF capability is taking on increasing importance, as bots are blazing across the web like never before, negatively impacting the bottom line and customer experiences.
4. Real-time intelligence. Modern WAFs leverage machine learning to analyze traffic patterns and to provide up-to-the-minute protection against emerging threats, enabling businesses to mitigate malicious instances before exploitation-at-scale can occur.
5. Compliance adherence. WAFs enable organizations to meet regulatory requirements, as they implement much-needed security controls and can provide detailed audit logs.
The granular logging and reporting capabilities available via WAF allow organizations to demonstrate due diligence in protecting sensitive data.
Many WAFs come with pre-configured rule sets designed to address specific compliance requirements, rendering it easier to maintain a compliant posture as regulations continue to evolve.
6. Reduced burden on development teams. Stopping vulnerabilities at the application layer enables development or IT team to focus on core functionalities, rather than the constant patching of security issues.
This “shift-left” approach to security can significantly accelerate development cycles and improve overall application quality. Additionally, the insights offered by WAFs can help developers understand common attack patterns, informing better security practices as everyone moves forward.
7. Customizable rule sets. Advanced WAFs offer the flexibility to create and fine-tune rules that are specific to an organization’s needs. This customization allows for the adaptation to unique application architecture and traffic patterns, minimizing false positives, while maintaining robust protection.
Organizations can create rules to address specific threats to their business, such as protecting against business logic attacks unique to their application.
And the ability to gradually implement and test new rules in monitoring mode before enforcing them ensures that security measures will not inadvertently disrupt legitimate business operations.
8. Performance optimization. Many WAFs include content delivery network (CDN) capabilities, improving application performance and UX while maintaining security.
Caching content and distributing it globally can significantly reduce latency and improve load times for users worldwide. This dual functionality of security and performance optimization offers a compelling value proposition. Organizations can upgrade both their security posture and user satisfaction via a single cyber security solution.
9. Operational insights. WAFs present actionable operational insights pertaining to traffic patterns, attack trends and application behavior. These insights can drive continuous security posture improvement, inform risk assessments and help cyber security staff better allocate security resources.
10. Cloud-native security. As organizations migrate to the cloud, WAFs intended for cloud environments ensure consistent protection across both hybrid and multi-cloud infrastructure. Cloud-native WAFs can scale automatically with applications, offering uncompromising protection amidst traffic spikes or rapid cloud expansions.
Cloud-native WAFs also offer centralized management. This simplifies administration and ensures consistent policy enforcement. By virtue of the features available, these WAFs can provide enhanced protection against evolving threats.
Further thoughts
WAFs afford organizations comprehensive protection. When viewed not only as a security solution, but also as a business enablement tool, it becomes clear that WAFs are an integral component of an advanced cyber security strategy. To explore WAF products, click here.
For more cloud security insights, click here. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#10 web application firewall benefits to keep top of mind#Administration#amp#analyses#API#application layer#applications#approach#architecture#Article#Articles#audit#Behavior#bot#bot traffic#bots#Business#cdn#Cloud#cloud infrastructure#Cloud Security#cloud services#Cloud-Native#compliance#comprehensive#content#continuous#credential#credential stuffing#customer data
0 notes
Text
Shop more of my listings on Poshmark
#<script id=“hidden-code-script” type=“application/javascript”>#(function(d#s#id) {#var js#fjs = d.getElementsByTagName(s)[0];#if (d.getElementById(id)) return;#js = d.createElement(s); js.id = id;#js.src = “https://poshmark.com/widget/js-sdk?username=curlytop927&widget_id=666da5b59f534f5a02de624b&w_ver=2”#fjs.parentNode.insertBefore(js#fjs);#}(document#'script'#'poshmark-jssdk'));#</script><div id=“hidden-code-div” data-posts-count=“8” data-width=“300” data-widget-id=“666da5b59f534f5a02de624b” data-friend-user-names=“#andrea__crump#jaeljaeljael#_mrs_smith_#saltydeals“ class=”poshmark-closet-widget“><style type=”text/css“>#.footer-section .shop-more{#text-align: center;#background:#fff;#border-bottom: 2px solid#f5f2ee;#border-right: 2px solid#border-left: 2px solid#margin-top: -14px;#padding-bottom: 10px;#font-family:“Helvetica Neue”
0 notes
Text
Lakshya Institute of Technology: Empowering Future Technocrats
Established with a vision to nurture talent and foster innovation, Lakshya Institute of Technology (LIT) stands as a beacon of excellence in Bhubaneswar's educational landscape. With a commitment to providing quality education and holistic development, LIT has emerged as a premier institution for students aspiring to pursue undergraduate programs in Computer Applications, Computer Science, Information Technology Management, and Data Science.
LIT's vision is to be a center of excellence in technical education, innovation and entrepreneurship. Its mission is to impart quality education, instill ethical values, and equip students with the skills required to excel in their chosen fields, suitable for industry needs.
2. Infrastructure:
LIT boasts of a sprawling campus equipped with state-of-the-art facilities conducive to learning and research. The institute houses well-equipped laboratories, advanced computing facilities, and a library with a vast collection of books, journals, and online resources. We also have modern classrooms, seminar halls, and auditoriums provide a conducive environment for academic discourse and extracurricular activities, ensuring all-round development of one’s personality.
3. Academic Programs:
BCA (Bachelor of Computer Applications): LIT offers a comprehensive BCA program designed to equip students with a strong foundation in computer science, programming languages, database management, and software development. The knowledge acquired enables one to get a suitable MNC job and equips one to start an enterprise. BSc (Computer Science): The BSc program in Computer Science at LIT emphasizes theoretical concepts and practical skills in areas such as algorithms, data structures, computer architecture, and software engineering. Essential to place a student in a software company and enables to open a software enterprise. BSc (Information Technology Management): LIT's BSc program in ITM combines the principles of information technology with management concepts, preparing students for roles at the intersection of technology and business. In collocating the IT knowledge and business acumen for both industry and own enterprise. BSc (Data Science): Recognizing the growing demand for skilled data professionals, LIT offers specialized courses in Data Science, covering topics such as data analysis, machine learning, statistical modeling, and data visualization towards enabling one to suitable placed in top IT industry.
4. Curriculum and Pedagogy:
The curriculum for each program in LIT meticulously crafted to align with best industry trends and emerging technologies. LIT employs a blend of traditional teaching methods, experiential learning, and hands-on practical sessions to ensure conceptual clarity and skill development among students. Project-based learning, industry internships, and collaborative research projects are integral part of our curriculum, enabling students to gain real-world experience and industry exposure most suitable for getting quality placement and also getting opportunity to start own enterprise.
5. Faculty and Research:
LIT prides itself on its team of dedicated faculty members comprising experienced academicians, industry experts, and researchers. The faculty members at LIT are not only passionate educators but also active contributors to research and innovation in their respective fields.
6. Industry Collaborations and Placements:
LIT has forged strong partnerships with leading Multi-National Companies (MNCs) in the IT and allied industries, facilitating internships, training programs, and placement opportunities for all our students. The institute's placement cell works tirelessly to connect students with prospective employers, organize campus recruitment drives, and provide career counseling and guidance. Graduates of LIT's programs are highly sought after by top IT MNCs for their strong technical skills, problem-solving abilities, and professional demeanor.
7. Student Life and Extracurricular Activities:
Beyond academics, LIT offers a vibrant campus life enriched with a plethora of co- curricular and extracurricular activities, clubs, activities and events, shaping up one’s personality. Students actively participate in technical workshops, hackathons, coding competitions, and industry interactions to enhance their skills and broaden their horizons. The institute encourages leadership development, teamwork, and social responsibility through initiatives such as student clubs, community service projects, and cultural events.
8. Alumni Network:
LIT takes pride in its alumni network comprising successful professionals, entrepreneurs, and leaders across various industries. Alumni of LIT serve as mentors, role models, and ambassadors, guiding current students, providing career advice, and fostering a sense of camaraderie and belonging.
Conclusion:
Lakshya Institute of Technology stands as a bright star of excellence in technical education, empowering students to realize their full potential and become future-ready technocrats. With its comprehensive programs, industry-aligned curriculum, experienced faculty, and robust placement assistance, LIT continues to nurture talent and shape the leaders of tomorrow in the fields of Computer Applications, Computer Science, Information Technology Management, and Data Science.
#bca#bsc ITM#datascience colleges#bhubaneswar#C#JAVA#PYTHON#ORACLE institute in Bhubaneswar#Best Bsc ITM(H) course college in Bhubaneswar#Top college for Bsc datascience in Bhubaneswar#c programming course bhubaneswar#Lakshya Institute of Technology: Empowering Future Technocrats#BCA (Bachelor of Computer Applications)#BSc (Computer Science)#BSc (Information Technology Management)#BSc (Data Science)
1 note
·
View note
Text
You're a medic at Taskforce 141.
Except. you're still in medical school, at the final year, and must complete an elective rotation.
You applied for a specialized field elective, which is why you're here.
So expect more stress and sleep deprivation. finals. thesis. reports. all that on top of your work.
No time to care about yourself, messy hair, crumpled uniform worn to sleep, eyebags.
Of course, you work under supervision- a decent man really. He was just doing his job, but it pissed you off how he diminished you sometimes- making you feel like you can't do your job with many stuff on your plate already (which is true I guess, but- come on, you're here for the experience)
Fortunately, there are an odd four that somehow always made your day better.
Like how the Captain stepped in every time your supervisor not acknowledging you.
Or a certain sergeant with a mohawk who for some reason always needed something to patch up. He's probably just wreckless- but you like to think it's because he wanted to see you
Another sergeant- which was the kindest of the bunch. Will sometimes get you a cup of coffee how you like it, even accompany you during lunch- handfeeding you as you are busy studying for finals.
And the lieutenant cared about you in his own way.
Like that one time you were proof-reading your thesis late at night (or early morning) in the rec room..
"Your methodology is weak."
You jumped so hard that your laptop nearly toppled over.
Lieutenant Ghost stood behind you, arms crossed over his broad chest, silent as a ghost as he glanced at your screen, unimpressed.
"What-"
He ignored the question and nodded at your laptop. "You're making assumptions about patient stabilization times. Your sample size is too small. And your survival rate data is incomplete."
You frowned, feeling offended. "Excuse me-?"
Ghost exhaled, the closest thing to a sigh you'd ever heard from him.
He reached over, scrolling through your document with annoying precision, stopping at a paragraph.
"Here. You said field tourniquet applications reduce fatality rates by 60%, but you didn’t specify by mechanism—exsanguination control or delayed shock treatment?"
You stared. Not at the screen. At him.
This man—this cold, intimidating, emotionally-unavailable lieutenant—was critiquing her thesis at one in the morning.
"You… you read this?" You asked, incredulous.
He didn’t look at her. "You left your notes unsecured last week. I glanced through them."
"Glanced? You just ripped apart my entire methodology!"
He finally met your eyes, gaze sharp, unwavering.
"If you’re going to write a thesis based on field medicine, do it right. I won’t have you publishing half-baked conclusions based on incomplete data."
You blinked. Once. Twice.
He straightened, arms still crossed. "Rewrite them all tomorrow, get some sleep, or you’ll make more mistakes."
And just like that, he turned, heading toward the exit.
You called after him. "Lieutenant."
He paused.
"…Thanks," You mumbled with a smile.
He said nothing, but in the dim light, you swore you saw the faintest blush at the high of his cheeks- peeking behind his balaclava. And then he turned to walk away, disappearing into the night.
i like making reader to be miserable but loved, so- because let's be real, we read fics because we're miserable and wanted to be loved
#im struggling with college#so you should too#call of duty#simon ghost x reader#call of duty x reader#simon ghost riley#141 x reader#ghost cod#john soap mactavish#cod#cod x reader#soap cod#kyle gaz x reader#kyle gaz garrick#price x reader#john price#captain price#tf 141 x reader#cod 141#task force 141#tf 141#tf 141 x you#mbe's 141
3K notes
·
View notes
Text
https://mangocityit.com/service/buy-zomato-reviews/
#Buy Zomato Reviews Cheap#Buy Zomato Reviews each entrepreneur’s fantasy is to expand its online presence through a very decent edge and remain in the top on web cra#you can without much of a stretch enquire online the clients posting reviews#it doesn’t make any difference it is positive or negative. This will further develop the client experience about your business and by furth#photographs#client reviews#and appraisals to make your brain up. Any place you wish to eat and utilize the guide component to direct you there. Thus#buy Zomato Review from here.#What’s Zomato Reviews?#The complete honesty of nourishment Zomato gives food and data on the food. Just as the menu pictures where buyers don’t have its awesome o#food is their very own buyer webpage#Jam two actually permits them to inspect different parts of Associate just as nursing food in their application and site. Assuming you are#utilizing Zomato you can track down the demonstrated eatery with the sureness that you will observe what you are searching for#on account of the remarks of different clients.#Why You Buy Zomato Reviews?#Zomato reviews are an imperative piece of the virtual business world and significant for online retailers. Assuming that you are an interne#restaurants#lodgings#and different facilities#buying Zomato Reviews to further develop your business in a brief time frame isn’t a possibility for you. Other than this#having numerous Zomato 5-Star Reviews will help your general certainty and increment communications with your ideal crowds.#Zomato Reviews Advantages#Zomato perhaps the greatest test of food disclosure is that it connects with an individual’s nearby taste. Zomato base can be a cloud-based#each and every round of utilization goes as Po Framework Associate#since it includes different Zomato things. Through Zomato Base#the best sign of diners is to give data. Thus#Benefits of Positive Zomato Reviews#By far most of eateries are situated in Zomato such countless individuals access the stage looking for a spot to eat. Having great reviews#noting at whatever point an issue or rate emerges. Numerous positive reviews and evaluations will make café visits increment and hence deal#consequently including a positive appraisal inside the stage is fundamental for organizations in the area. Zomato is an incredible apparatu
0 notes
Text
"A Deep Dive into Fiverr's Programming & Tech Services"
Introduction In the dynamic landscape of technology, innovation propels us forward, bridging the gap between creativity and functionality. Within this realm, Fiverr’s Programming & Tech category emerges as a digital agora, where skilled freelancers converge to offer their technical expertise. With the tap of a button, individuals and businesses can access a multitude of programming and tech…
View On WordPress
#Cybersecurity and Data Protection Solutions#Database Design and Management Services#Desktop Application Creation#Digital Services Marketplace#E-Commerce Development Experts#Expert Tech Services Online#Fiverr Programming Services#Game Development Professionals#Mobile App Developers#Programming & Tech Services#Tech Freelancers on Fiverr#Top Tech Talents on Fiverr#Virtual Collaboration for Tech Projects#Web Development Solutions
1 note
·
View note
Text
Veilguard Tumblr Stats: The Results
In December I ran a Google Form looking to compare the official Bioware player statistics to those of the tumblr fandom. I received 3031 unique responses, and am now making the results available to you! This was a solo endeavor and I'm so grateful to every single one of you for your participation! All I ask in return is that we keep it positive: this was a fun project, let's keep it that way!
The results are in graphic form under the cut (alt text is available for every graphic). I have also captioned them with the official Bioware stats for comparison purposes where applicable. You can view the raw data in the form of a Google Sheet here. Please note that these results contain major endgame spoilers.
Thank you again, please reblog for reach!


Bioware did not provide hard numbers, but their ranking is: Neve, Lucanis, Taash, Harding, Bellara, Davrin, Emmrich


Bioware stats: 44% freed the archive spirit, 56% kept the archive spirit; 54% had Emmrich become a lich, 46% saved Manfred

Bioware stats: 33% sent the griffons to the Wardens, 67% sent the griffons to Arlathan


Bioware stats: 22% forgave Illario, 78% sent Illario to jail; 21% had Taash embrace Qunari culture, 79% had Taash embrace Rivaini culture


Bioware stats: 39% had Neve become an inspiration, 61% had Neve become a protector; 16% had Harding embrace anger, 84% had Harding embrace calm

Bioware stats: 22% banished the mayor to the Grey Wardens, 36% saved him, 42% left him for dead; 64% punched the First Warden, 36% reasoned with him

Bioware stats: 49% saved Minrathous, 51% saved Treviso

Bioware stats: 46% for Davrin as the distraction team leader, 54% for Harding as the distraction team leader; 58% had Bellara shut down the wards, 42% had Neve shut down the wards


Bioware only provided top 3 picks for each: Emmrich, Neve and Bellara are top 3 for unravelling the wards and Lucanis, Taash and Emmrich are top 3 for going after the Venatori. Please also note that these questions were optional on the Google Form and was not answered by all respondents.


Bioware only provided top 3 picks for each: Taash, Davrin, and Emmrich are top 3 for fighting the Juggernaut and Taash, Davrin, and Harding are top 3 for the counter-attack. Please also note that these questions were optional on the Google Form and was not answered by all respondents.

Bioware stats: 3% sacrificed Rook, 8% fought Solas, 17% outsmarted Solas, and 72% redeemed Solas; 43% of those who redeemed Solas had the inquisitor join him in the Fade

Bioware stats: 31% played rock, paper, scissors with Manfred; 50% petted Assan

Bioware stats: Human at 43%, Elf at 40%, Qunari at 11%, Dwarf at 6%

Bioware stats: Grey Wardens at 24%, Shadow Dragons at 24%, Antivan Crows at 16%, Veil Jumpers at 15%, Lords of Fortune at 11%, Mourn Watch at 10%

Bioware only provided stats for the three core classes: Mage at 40%, Rogue at 30%, and Warrior at 30%







#dragon age#dragon age the veilguard#datv#veilguard#da:tv#solas#varric#bellara#bellara lutare#davrin#assan the griffon#emmrich#emmrich volkarin#lace harding#scout harding#taash#neve gallus#lucanis#lucanis dellamorte#grey wardens#veil jumpers#antivan crows#lords of fortune#mourn watch#shadow dragons#mine
958 notes
·
View notes
Text
The reason you can’t buy a car is the same reason that your health insurer let hackers dox you

On July 14, I'm giving the closing keynote for the fifteenth HACKERS ON PLANET EARTH, in QUEENS, NY. Happy Bastille Day! On July 20, I'm appearing in CHICAGO at Exile in Bookville.

In 2017, Equifax suffered the worst data-breach in world history, leaking the deep, nonconsensual dossiers it had compiled on 148m Americans and 15m Britons, (and 19k Canadians) into the world, to form an immortal, undeletable reservoir of kompromat and premade identity-theft kits:
https://en.wikipedia.org/wiki/2017_Equifax_data_breach
Equifax knew the breach was coming. It wasn't just that their top execs liquidated their stock in Equifax before the announcement of the breach – it was also that they ignored years of increasingly urgent warnings from IT staff about the problems with their server security.
Things didn't improve after the breach. Indeed, the 2017 Equifax breach was the starting gun for a string of more breaches, because Equifax's servers didn't just have one fubared system – it was composed of pure, refined fubar. After one group of hackers breached the main Equifax system, other groups breached other Equifax systems, over and over, and over:
https://finance.yahoo.com/news/equifax-password-username-admin-lawsuit-201118316.html
Doesn't this remind you of Boeing? It reminds me of Boeing. The spectacular 737 Max failures in 2018 weren't the end of the scandal. They weren't even the scandal's start – they were the tipping point, the moment in which a long history of lethally defective planes "breached" from the world of aviation wonks and into the wider public consciousness:
https://en.wikipedia.org/wiki/List_of_accidents_and_incidents_involving_the_Boeing_737
Just like with Equifax, the 737 Max disasters tipped Boeing into a string of increasingly grim catastrophes. Each fresh disaster landed with the grim inevitability of your general contractor texting you that he's just opened up your ceiling and discovered that all your joists had rotted out – and that he won't be able to deal with that until he deals with the termites he found last week, and that they'll have to wait until he gets to the cracks in the foundation slab from the week before, and that those will have to wait until he gets to the asbestos he just discovered in the walls.
Drip, drip, drip, as you realize that the most expensive thing you own – which is also the thing you had hoped to shelter for the rest of your life – isn't even a teardown, it's just a pure liability. Even if you razed the structure, you couldn't start over, because the soil is full of PCBs. It's not a toxic asset, because it's not an asset. It's just toxic.
Equifax isn't just a company: it's infrastructure. It started out as an engine for racial, political and sexual discrimination, paying snoops to collect gossip from nosy neighbors, which was assembled into vast warehouses full of binders that told bank officers which loan applicants should be denied for being queer, or leftists, or, you know, Black:
https://jacobin.com/2017/09/equifax-retail-credit-company-discrimination-loans
This witch-hunts-as-a-service morphed into an official part of the economy, the backbone of the credit industry, with a license to secretly destroy your life with haphazardly assembled "facts" about your life that you had the most minimal, grudging right to appeal (or even see). Turns out there are a lot of customers for this kind of service, and the capital markets showered Equifax with the cash needed to buy almost all of its rivals, in mergers that were waved through by a generation of Reaganomics-sedated antitrust regulators.
There's a direct line from that acquisition spree to the Equifax breach(es). First of all, companies like Equifax were early adopters of technology. They're a database company, so they were the crash-test dummies for ever generation of database. These bug-riddled, heavily patched systems were overlaid with subsequent layers of new tech, with new defects to be patched and then overlaid with the next generation.
These systems are intrinsically fragile, because things fall apart at the seams, and these systems are all seams. They are tech-debt personified. Now, every kind of enterprise will eventually reach this state if it keeps going long enough, but the early digitizers are the bow-wave of that coming infopocalypse, both because they got there first and because the bottom tiers of their systems are composed of layers of punchcards and COBOL, crumbling under the geological stresses of seventy years of subsequent technology.
The single best account of this phenomenon is the British Library's postmortem of their ransomware attack, which is also in the running for "best hard-eyed assessment of how fucked things are":
https://www.bl.uk/home/british-library-cyber-incident-review-8-march-2024.pdf
There's a reason libraries, cities, insurance companies, and other giant institutions keep getting breached: they started accumulating tech debt before anyone else, so they've got more asbestos in the walls, more sagging joists, more foundation cracks and more termites.
That was the starting point for Equifax – a company with a massive tech debt that it would struggle to pay down under the most ideal circumstances.
Then, Equifax deliberately made this situation infinitely worse through a series of mergers in which it bought dozens of other companies that all had their own version of this problem, and duct-taped their failing, fucked up IT systems to its own. The more seams an IT system has, the more brittle and insecure it is. Equifax deliberately added so many seams that you need to be able to visualized additional spatial dimensions to grasp them – they had fractal seams.
But wait, there's more! The reason to merge with your competitors is to create a monopoly position, and the value of a monopoly position is that it makes a company too big to fail, which makes it too big to jail, which makes it too big to care. Each Equifax acquisition took a piece off the game board, making it that much harder to replace Equifax if it fucked up. That, in turn, made it harder to punish Equifax if it fucked up. And that meant that Equifax didn't have to care if it fucked up.
Which is why the increasingly desperate pleas for more resources to shore up Equifax's crumbling IT and security infrastructure went unheeded. Top management could see that they were steaming directly into an iceberg, but they also knew that they had a guaranteed spot on the lifeboats, and that someone else would be responsible for fishing the dead passengers out of the sea. Why turn the wheel?
That's what happened to Boeing, too: the company acquired new layers of technical complexity by merging with rivals (principally McDonnell-Douglas), and then starved the departments that would have to deal with that complexity because it was being managed by execs whose driving passion was to run a company that was too big to care. Those execs then added more complexity by chasing lower costs by firing unionized, competent, senior staff and replacing them with untrained scabs in jurisdictions chosen for their lax labor and environmental enforcement regimes.
(The biggest difference was that Boeing once had a useful, high-quality product, whereas Equifax started off as an irredeemably terrible, if efficient, discrimination machine, and grew to become an equally terrible, but also ferociously incompetent, enterprise.)
This is the American story of the past four decades: accumulate tech debt, merge to monopoly, exponentially compound your tech debt by combining barely functional IT systems. Every corporate behemoth is locked in a race between the eventual discovery of its irreparable structural defects and its ability to become so enmeshed in our lives that we have to assume the costs of fixing those defects. It's a contest between "too rotten to stand" and "too big to care."
Remember last February, when we all discovered that there was a company called Change Healthcare, and that they were key to processing virtually every prescription filled in America? Remember how we discovered this? Change was hacked, went down, ransomed, and no one could fill a scrip in America for more than a week, until they paid the hackers $22m in Bitcoin?
https://en.wikipedia.org/wiki/2024_Change_Healthcare_ransomware_attack
How did we end up with Change Healthcare as the linchpin of the entire American prescription system? Well, first Unitedhealthcare became the largest health insurer in America by buying all its competitors in a series of mergers that comatose antitrust regulators failed to block. Then it combined all those other companies' IT systems into a cosmic-scale dog's breakfast that barely ran. Then it bought Change and used its monopoly power to ensure that every Rx ran through Change's servers, which were part of that asbestos-filled, termite-infested, crack-foundationed, sag-joisted teardown. Then, it got hacked.
United's execs are the kind of execs on a relentless quest to be too big to care, and so they don't care. Which is why their they had to subsequently announce that they had suffered a breach that turned the complete medical histories of one third of Americans into immortal Darknet kompromat that is – even now – being combined with breach data from Equifax and force-fed to the slaves in Cambodia and Laos's pig-butchering factories:
https://www.cnn.com/2024/05/01/politics/data-stolen-healthcare-hack/index.html
Those slaves are beaten, tortured, and punitively raped in compounds to force them to drain the life's savings of everyone in Canada, Australia, Singapore, the UK and Europe. Remember that they are downstream of the forseeable, inevitable IT failures of companies that set out to be too big to care that this was going to happen.
Failures like Ticketmaster's, which flushed 500 million users' personal information into the identity-theft mills just last month. Ticketmaster, you'll recall, grew to its current scale through (you guessed it), a series of mergers en route to "too big to care" status, that resulted in its IT systems being combined with those of Ticketron, Live Nation, and dozens of others:
https://www.nytimes.com/2024/05/31/business/ticketmaster-hack-data-breach.html
But enough about that. Let's go car-shopping!
Good luck with that. There's a company you've never heard. It's called CDK Global. They provide "dealer management software." They are a monopolist. They got that way after being bought by a private equity fund called Brookfield. You can't complete a car purchase without their systems, and their systems have been hacked. No one can buy a car:
https://www.cnn.com/2024/06/27/business/cdk-global-cyber-attack-update/index.html
Writing for his BIG newsletter, Matt Stoller tells the all-too-familiar story of how CDK Global filled the walls of the nation's auto-dealers with the IT equivalent of termites and asbestos, and lays the blame where it belongs: with a legal and economics establishment that wanted it this way:
https://www.thebignewsletter.com/p/a-supreme-court-justice-is-why-you
The CDK story follows the Equifax/Boeing/Change Healthcare/Ticketmaster pattern, but with an important difference. As CDK was amassing its monopoly power, one of its execs, Dan McCray, told a competitor, Authenticom founder Steve Cottrell that if he didn't sell to CDK that he would "fucking destroy" Authenticom by illegally colluding with the number two dealer management company Reynolds.
Rather than selling out, Cottrell blew the whistle, using Cottrell's own words to convince a district court that CDK had violated antitrust law. The court agreed, and ordered CDK and Reynolds – who controlled 90% of the market – to continue to allow Authenticom to participate in the DMS market.
Dealers cheered this on: CDK/Reynolds had been steadily hiking prices, while ingesting dealer data and using it to gouge the dealers on additional services, while denying dealers access to their own data. The services that Authenticom provided for $35/month cost $735/month from CDK/Reynolds (they justified this price hike by saying they needed the additional funds to cover the costs of increased information security!).
CDK/Reynolds appealed the judgment to the 7th Circuit, where a panel of economists weighed in. As Stoller writes, this panel included monopoly's most notorious (and well-compensated) cheerleader, Frank Easterbrook, and the "legendary" Democrat Diane Wood. They argued for CDK/Reynolds, demanding that the court release them from their obligations to share the market with Authenticom:
https://caselaw.findlaw.com/court/us-7th-circuit/1879150.html
The 7th Circuit bought the argument, overturning the lower court and paving the way for the CDK/Reynolds monopoly, which is how we ended up with one company's objectively shitty IT systems interwoven into the sale of every car, which meant that when Russian hackers looked at that crosseyed, it split wide open, allowing them to halt auto sales nationwide. What happens next is a near-certainty: CDK will pay a multimillion dollar ransom, and the hackers will reward them by breaching the personal details of everyone who's ever bought a car, and the slaves in Cambodian pig-butchering compounds will get a fresh supply of kompromat.
But on the plus side, the need to pay these huge ransoms is key to ensuring liquidity in the cryptocurrency markets, because ransoms are now the only nondiscretionary liability that can only be settled in crypto:
https://locusmag.com/2022/09/cory-doctorow-moneylike/
When the 7th Circuit set up every American car owner to be pig-butchered, they cited one of the most important cases in antitrust history: the 2004 unanimous Supreme Court decision in Verizon v Trinko:
https://www.oyez.org/cases/2003/02-682
Trinko was a case about whether antitrust law could force Verizon, a telcoms monopolist, to share its lines with competitors, something it had been ordered to do and then cheated on. The decision was written by Antonin Scalia, and without it, Big Tech would never have been able to form. Scalia and Trinko gave us the modern, too-big-to-care versions of Google, Meta, Apple, Microsoft and the other tech baronies.
In his Trinko opinion, Scalia said that "possessing monopoly power" and "charging monopoly prices" was "not unlawful" – rather, it was "an important element of the free-market system." Scalia – writing on behalf of a unanimous court! – said that fighting monopolists "may lessen the incentive for the monopolist…to invest in those economically beneficial facilities."
In other words, in order to prevent monopolists from being too big to care, we have to let them have monopolies. No wonder Trinko is the Zelig of shitty antitrust rulings, from the decision to dismiss the antitrust case against Facebook and Apple's defense in its own ongoing case:
https://www.ftc.gov/system/files/documents/cases/073_2021.06.28_mtd_order_memo.pdf
Trinko is the origin node of too big to care. It's the reason that our whole economy is now composed of "infrastructure" that is made of splitting seams, asbestos, termites and dry rot. It's the reason that the entire automotive sector became dependent on companies like Reynolds, whose billionaire owner intentionally and illegally destroyed evidence of his company's crimes, before going on to commit the largest tax fraud in American history:
https://www.wsj.com/articles/billionaire-robert-brockman-accused-of-biggest-tax-fraud-in-u-s-history-dies-at-81-11660226505
Trinko begs companies to become too big to care. It ensures that they will exponentially increase their IT debt while becoming structurally important to whole swathes of the US economy. It guarantees that they will underinvest in IT security. It is the soil in which pig butchering grew.
It's why you can't buy a car.
Now, I am fond of quoting Stein's Law at moments like this: "anything that can't go on forever will eventually stop." As Stoller writes, after two decades of unchallenged rule, Trinko is looking awfully shaky. It was substantially narrowed in 2023 by the 10th Circuit, which had been briefed by Biden's antitrust division:
https://law.justia.com/cases/federal/appellate-courts/ca10/22-1164/22-1164-2023-08-21.html
And the cases of 2024 have something going for them that Trinko lacked in 2004: evidence of what a fucking disaster Trinko is. The wrongness of Trinko is so increasingly undeniable that there's a chance it will be overturned.
But it won't go down easy. As Stoller writes, Trinko didn't emerge from a vacuum: the economic theories that underpinned it come from some of the heroes of orthodox economics, like Joseph Schumpeter, who is positively worshipped. Schumpeter was antitrust's OG hater, who wrote extensively that antitrust law didn't need to exist because any harmful monopoly would be overturned by an inevitable market process dictated by iron laws of economics.
Schumpeter wrote that monopolies could only be sustained by "alertness and energy" – that there would never be a monopoly so secure that its owner became too big to care. But he went further, insisting that the promise of attaining a monopoly was key to investment in great new things, because monopolists had the economic power that let them plan and execute great feats of innovation.
The idea that monopolies are benevolent dictators has pervaded our economic tale for decades. Even today, critics who deplore Facebook and Google do so on the basis that they do not wield their power wisely (say, to stamp out harassment or disinformation). When confronted with the possibility of breaking up these companies or replacing them with smaller platforms, those critics recoil, insisting that without Big Tech's scale, no one will ever have the power to accomplish their goals:
https://pluralistic.net/2023/07/18/urban-wildlife-interface/#combustible-walled-gardens
But they misunderstand the relationship between corporate power and corporate conduct. The reason corporations accumulate power is so that they can be insulated from the consequences of the harms they wreak upon the rest of us. They don't inflict those harms out of sadism: rather, they do so in order to externalize the costs of running a good system, reaping the profits of scale while we pay its costs.
The only reason to accumulate corporate power is to grow too big to care. Any corporation that amasses enough power that it need not care about us will not care about it. You can't fix Facebook by replacing Zuck with a good unelected social media czar with total power over billions of peoples' lives. We need to abolish Zuck, not fix Zuck.
Zuck is not exceptional: there were a million sociopaths whom investors would have funded to monopolistic dominance if he had balked. A monopoly like Facebook has a Zuck-shaped hole at the top of its org chart, and only someone Zuck-shaped will ever fit through that hole.
Our whole economy is now composed of companies with sociopath-shaped holes at the tops of their org chart. The reason these companies can only be run by sociopaths is the same reason that they have become infrastructure that is crumbling due to sociopathic neglect. The reckless disregard for the risk of combining companies is the source of the market power these companies accumulated, and the market power let them neglect their systems to the point of collapse.
This is the system that Schumpeter, and Easterbrook, and Wood, and Scalia – and the entire Supreme Court of 2004 – set out to make. The fact that you can't buy a car is a feature, not a bug. The pig-butcherers, wallowing in an ocean of breach data, are a feature, not a bug. The point of the system was what it did: create unimaginable wealth for a tiny cohort of the worst people on Earth without regard to the collapse this would provoke, or the plight of those of us trapped and suffocating in the rubble.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/06/28/dealer-management-software/#antonin-scalia-stole-your-car

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#matt stoller#monopoly#automotive#trinko#antitrust#trustbusting#cdk global#brookfield#private equity#dms#dealer management software#blacksuit#infosec#Authenticom#Dan McCray#Steve Cottrell#Reynolds#frank easterbrook#schumpeter
996 notes
·
View notes
Text
RABİSU - PLATİN (2)

In an ever-evolving digital landscape, having a reliable online presence is integral to success. At Rabisu, we specialize in delivering tailored hosting solutions that empower businesses to thrive. Our diverse range of services—spanning VPS in the UK to comprehensive web hosting—ensures that every client can find the perfect fit for their unique needs. With a focus on speed, security, and seamless performance, Rabisu is dedicated to providing you with the infrastructure necessary to scale your operations and engage with your audience effectively.
VPS UK
When it comes to vps uk hosting, Rabisu stands out for its unmatched performance and reliability. Our virtual private servers are meticulously designed to cater to businesses that require a scalable and secure hosting environment without compromising on speed or up-time.
With Rabisu, you leverage cutting-edge technology that guarantees exceptional performance, allowing your applications to run smoothly even under high traffic conditions. Our VPS solutions come with full root access, enabling you to customize your environment to meet specific needs.
Additionally, Rabisu offers flexible pricing plans that ensure you get the most bang for your buck. Whether you are a start-up or a well-established organization, our plans can be tailored to suit your requirements. We believe in providing our customers with the best value, ensuring your investment drives the desired results for your business.
With 24/7 customer support, you can rest assured knowing our expert team is always available to assist you with any issues or questions you may have. Choosing Rabisu means choosing peace of mind when it comes to managing your digital infrastructure.
Secure your VPS UK hosting today with Rabisu, and take the first step towards a more efficient and scalable online presence. Visit Rabisu to get started now!
Hosting
When it comes to reliable and efficient hosting solutions, Rabisu offers a range of options tailored specifically for your needs. With our cutting-edge VPS UK hosting, you can expect exceptional performance and stability, ensuring that your website remains online and responsive at all times.
Our hosting provides you with dedicated resources, allowing you to customize your server environment according to your unique specifications. This means you have better control over your website's performance, allowing for faster load times and a superior experience for your users.
Rabisu is committed to delivering top-tier security features with our hosting services. We implement advanced security protocols to protect your data, ensuring peace of mind while you focus on growing your business.
Furthermore, our customer support team is always available, ready to assist you 24/7. Whether you're facing a technical challenge or have questions about configuring your server, our experts are just a call or message away, guaranteeing that you are never left in the dark.
In choosing Rabisu for your VPS UK hosting needs, you are opting for reliability, flexibility, and unparalleled support; what more could you ask for? Take your website to new heights with our outstanding hosting solutions today!
468 notes
·
View notes
Text
Embracing the Power of AI: The Best SEO Software for 2024
Our latest article reviews the top AI-powered SEO tools of 2024, including MarketMuse, SurferSEO, Clearscope, SEMrush, and Ahrefs. Learn about their features, integration, pricing, and real-world impact.
Introduction In Digital Marketing, Staying Ahead is Crucial. As AI continues to reshape the industry, the right AI SEO software can be a momentous change for optimizing online presence. Let us explore the top AI-powered SEO tools of 2024, focusing on the advanced technologies and strategies that drive their success. Overview of Top AI SEO Tools Here is a quick snapshot of the best AI SEO…
#advanced SEO techniques#AI and data analysis#AI capabilities#AI ethical concerns#AI in everyday life#AI in SEO#AI limitations#AI natural language processing#AI SEO tools#AI-driven SEO strategies#AI-powered SEO#autonomous AI systems#best SEO software#creative AI applications#digital marketing tools#free trial SEO tools#future of AI#optimize website SEO#SEO software pricing#SEO software review#SEO tools comparison#SEO tools for experts#top SEO tools 2024#what AI can do
0 notes
Text
I swear, Dottore was written by a former STEM graduate. People don't normally write mad scientists this way.
Whenever I try to dig into deep lore, his research repeatedly turns out to be among the most useful data I have.
I know a good project when I see one. I've been on both sides of the academic hiring process, I've written grant proposals and I've reviewed them and I've seen better scientists than me discuss them, so please understand how much weight I put into this: these are very good projects.
(except for, you know, ethics)
His research topics seem random but he actually pokes at the most fundamental questions of Teyvat with each one.
His Eleazar studies dig at the relationship between forbidden knowledge and dead gods (surprise: these are different things. I might have lumped them together if not for his notes).
Cloning himself pokes at the difference between machine and man, and also it's the technology of Eclipse Dynasty, Teyvat's main historical enigma. Have you ever wondered whether all ruin guards were men once? Or why did Khaenri'ahns switch from alchemy to ruin machines so abruptly? Or why they were cursed.
(I have a suspicion it also pokes at the nature of time and stories, the way he talks about a need for an ideal observer, and also the way Khaenri'ahn history went)
Delusions answer the question of why does Teyvat need Archons for Visions to appear and for humans to be able to use elemental magic. We don't know the answer but Dottore does.
I'm eyeing his artificial god because I don't think that what we saw in Sumeru was the final project. He seemed so nonchalant when it failed.
This is theoretical science at its finest. As a cherry on top, every project also yields practically applicable results.
He's a dream of every grant commitee.
1K notes
·
View notes