#translate data simpler
Explore tagged Tumblr posts
Text
unmixed untuned rikka ai on auto and rikka standard lite on manual default settings BUT THIS is what i was thinking about yesterday when i was talking about wild stars type covers with different versions of the same voicebanks, different engines/differe characters but same voice providers/etc..... i think it could be fun......
#vocal synth wip#guy who likes to make 90% of a svp and never finish it voice: so i started a new svp#THIS ONE actually this was easy as FUCK#i think theres a few notes i have off and i need to figure out how to order all the tracks for the overlapping bits near the end#and i havent thought about the harmonies yet LOL (im hoping they are a third up or down... please be a third up or down)#in my journey of learning how to make my own vocal data ive been learning why so many usts are like also vsynth songs#more likely to have consistent easy to translate to software timing... because it was made in software LOL#some singers in like ballads and shit do some crazy borrowed time ass stuff#and i get scared. i get scared. i dont know what a time signature is. passes away#but a lot of muse songs - especially some of the earlier ones - have simpler stuff going on that makes it nice and easy to figure out <3#i do want to do more liella songs someday but they do some scary harmonies in some and i get. scared :D#i will learn tho..... i will learn........
1 note
·
View note
Text
Pretty regularly, at work, I ask ChatGPT hundreds of slightly different questions over the course of a minute or two.
I don't type out these individual questions, of course. They're constructed mechanically, by taking documents one by one from a list, and slotting each one inside a sandwich of fixed text. Like this (not verbatim):
Here's a thing for you to read: //document goes here// Now answer question XYZ about it.
I never read through all of the responses, either. Maybe I'll read a few of them, later on, after doing some kind of statistics to the whole aggregate. But ChatGPT isn't really writing for human consumption, here. It's an industrial machine. It's generating "data," on the basis of other "data."
Often, I ask it to write out a step-by-step reasoning process before answering each question, because this has been shown to improve the quality of ChatGPT's answers. It writes me all this stuff, and I ignore all of it. It's a waste product. I only ask for it because it makes the answer after it better, on average; I have no other use for it.
The funny thing is -- despite being used in a very different, more impersonal manner -- it's still ChatGPT! It's still the same sanctimonious, eager-to-please little guy, answering all those questions.
Fifty questions at once, hundreds in a few minutes, all of it in that same, identical, somewhat annoying brand voice. Always itself, incapable of tiring.
This is all billed to my employer at a rate of roughly $0.01 per 5,000 words I send to ChatGPT, plus roughly $0.01 per 3,750 words that ChatGPT writes in response.
In other words, ChatGPT writing is so cheap, you can get 375,000 words of it for $1.
----
OpenAI decided to make this particular "little guy" very cheap and very fast, maybe in recognition of its popularity.
So now, if you want to use a language model like an industrial machine, it's the one you're most likely to use.
----
Why am I making this post?
Sometimes I read online discourse about ChatGPT, and it seems like people are overly focused on the experience of a single human talking to ChatGPT in the app.
Or, at most, the possibility of generating lots of "content" aimed at humans (SEO spam, generic emails) at the press of a button.
Many of the most promising applications of ChatGPT involve generating text that is not meant for human consumption.
They go in the other direction: they take things from the messy, human, textual world, and translate them into the simpler terms of ordinary computer programs.
Imagine you're interacting with a system -- a company, a website, a phone tree, whatever.
You say or type something.
Behind the scenes, unbeknownst to you, the system asks ChatGPT 13 different questions about the thing you just said/typed. This happens almost instantaneously and costs almost nothing.
No human being will ever see any of the words that ChatGPT wrote in response to this question. They get parsed by simple, old-fashioned computer code, and then they get discarded.
Each of ChatGPT's answers ends in a simple "yes" or "no," or a selection from a similar set of discrete options. The system uses all of this structured, "machine-readable" (in the old-fashioned sense) information to decide what to do next, in its interaction with you.
This is the kind of thing that will happen, more and more.
742 notes
·
View notes
Text
I return to WHB Tumblr to see how the game us doing and I see the fandom in shambles, damn. And after scrolling through the tag for a bit, I have...questions.
Yo how big is WHB now even? I stopped playing shortly after they introduced the paywalled Gabriel and that's one of the things I've seen several people complain about...
Like I understand the rest of the complaints - it's mostly the same complaints I've been having about the game prior to me quitting. Multiple decisions that seem to reinforce the idea that this game is heading down the P2W path, very anti-F2P practices in general, outrageous prices for the paid Nightmare Pass, no pity system on launch, the disaster that was the implementation of the Solomon's Seals gacha, the many bugs on launch especially, the small amount of farmable premium currency, and the list goes on...the pancake shop rework not only seems to be in line with the trajectory PB seems to be taking in terms of game decisions, but is also the straw that broke the camel's back for a lot of players.
But, uh, storage? Wasn't it like 2 GB tops on launch? That was reasonable I think, because Arknights was around that size on launch and back then, there was so little additional content. Only JP dubbing, no L2D E2 art or skins (the only L2D we had back then was Closure, the SHOPKEEP), 5 story chapters (which translated to 92 stages, in which around half have a Challenge Mode variant and with a large majority being unique maps), and no additional game modes.
For additional context, currently Arknights is ~6-7 GB on a fresh account with all language dubbing, and it gets bloated if you don't delete unused event data (it's ~9.7 GB for me and I have Arknights on my current phone ever since Near Light first hit Global, so just over 2 years now). Keep in mind Arknights is close to 4.5 years old in Global, and CN just celebrated their 5th anniversary a few months back.
Talking about storage, I don't think comparing WHB to older games and non-tower defense is fair either, since:
Older games in general are much easier on your device in terms of storage to content ratio and performance, mostly due to device limitations of the past requiring less sophisticated game mechanics and the devs sticking to these simpler mechanics even as time passes and technology gets more advanced. Gentle reminder that FGO is ~7 years old in NA, ~9 years old in JP, and ALSO doesn't download everything initially - afaik there's an option for that in the settings menu which bumps the total size up significantly (the wiki lists it as around 9-10 GB total).
Different genres and graphics mean different storage requirements. Anything 3D or open world will almost always have higher storage requirements compared to anything else. Path to Nowhere is around the same size as Arknights despite being younger due to the former using 3D models for their battle sprites, compared to the 2D chibis Arknights uses. Love and Deepspace, a ~5 months game, is huge because of how they do the cutscenes AND the stage-based action gameplay, but Wuthering Waves is closing the gap on size quickly despite being only ~1.5 months because it's an open world action RPG.
What I will say, though, is that WHB is not optimized well. Now I may be very unfair by comparing WHB to Punishing: Gray Raven, a game by the optimization gods known as Kurogames (people ran the PC PGR client on 2GB RAM laptops and my 4GB RAM laptop can run WuWa despite it using UE4 - an engine notorious for chugging on low end devices - albeit with lag spikes in the open world map), but when a 2D tower defense game fails to run as smoothly as a 3D action game with stylish and fast-paced combat, then we have a problem. For context, my 4GB RAM phone only has minor lag when I use a skill that has a lot of visual effects like Lee Hyperreal's Hypermatrix, but back when I played WHB I still experienced lag spikes when deploying units.
Again this all boils down to PB just not being used to the game format. Which is all well and good, Arknights was a huge departure from Girls Frontline too - a good portion of Arknights' devs worked on Girls Frontline before splitting off to work on Arknights. But what made Arknights succeed is how accessible and F2P friendly the game was, with smooth and solid gameplay as well as an engaging plot that discusses themes such as racism, discrimination, and the fragility of hope.
Of course you can argue that Arknights is a tower defense first, visual novel second. Unlike WHB, which is an otome game first, tower defense second. And I would agree, but only to a certain extent. Once you step into the realm of having Actual Combat Gameplay Elements then I believe it's your duty to make progression as reasonable as possible. Including a power gate is fine, but nothing too excessive - and certainly do not hold any significantly strong unit behind a paywall.
Because fun fact - in Arknights' entire runtime, there were only a handful of completely paywalled content:
Player icons from promotional packs for large events, particularly the Ambience Synesthesia concerts
Character skins from promotional packs, like the Exusiai and Guard Ch'en skins during the anime release
Purestream, a B4 Therapist Medic who was released as a WWF collab, where all sales from her $1 pack were donated to the WWF. Even then, she eventually became available for everyone, as she was later added to the Recruitment pool (use a resource obtained from Dailies for a chance to get units, some unique to the pool like Purestream). She was a decent healer, and her Module made her a good budget medic. Even then you're more likely using the Medics you've already built by then - for B4 budget options, Perfumer is usually better for multi-target healing and a party HP regen passive, while Sussurro is your go-to for strong single-target healing.
And guess what? None of these had any direct impact on gameplay during their paywalled period. Purestream wasn't even a B5 or B6 unit, yo. There are many better options for healers. I STILL USE THE B3 ANSEL AND HIBISCUS IN INTEGRATED STRATEGIES.
I'm just...PB's choices baffle me, and I do wish they can improve not just on the game performance standpoint, but in how they treat their playerbase in terms of in-game purchases. I hope I made that abundantly clear...
#what in hell is bad#whb#rimei rambles#i'm confused y'all#storage was the least of my issues with this game#but idk how it is now so#for the love of god please compress your files#optimize your game#again i am arknights biased#and it definitely shows#arknights is such a good game i genuinely think it ruined all other tower defense games for me#so maybe i'm not the most objective person to be making all these statements#but the game state is so much of a dumpster fire it makes me sad#because if done well whb could've been great#instead...we got this
36 notes
·
View notes
Text
How I use AI in my artworks and what I think about AI in general
I think it’s time to have this conversation because questions keep coming up more and more often.
I know that many people here don’t like AI or completely ignore it. In this post, I’d like to share my personal view on the topic and also answer the question of whether I use AI in my artworks.
Let me start with the simpler question. The answer is “yes,” I do use AI tools in some of my artworks. However, none of them can be considered fully AI-generated.
Sometimes, I use AI to create backgrounds or silhouettes, but I completely change the faces, like here: https://pin.it/2RUhZKz4S.
Other times, almost everything is AI-generated, for example: https://pin.it/N8apDmpfz.
Sometimes I use face swap technology, faceapp for hairs, etc.
I also have arts created fully without AI, but the faces there are based on real photos of Hunter and Jenna and edited with filters.
For example:
https://pin.it/1DZvBcKVw, https://pin.it/5wAdQvIFe, https://pin.it/19G1mffb6.
In general, I use anywhere from 3 to 5 or more tools for my artworks, including AI.
Some cases wouldn’t be possible for me to create without AI because I simply don’t have the technical skills yet. Others, on the contrary, are impossible to get from AI, no matter how hard you try, so I go back to good old collage techniques and hand-drawing.
Now, about my attitude towards AI overall.
You may like it or not, but it’s now part of our lives, and ignoring it is no longer an option. No AI boycott will stop its development. Almost any app nowadays has inbuilt AI tools.
I’m currently on maternity leave, but even in my professional field, AI is already widely used, and when I return to work, I’ll either need to know how to use it or fall behind the industry. That’s why I’m studying AI, and I do enjoy the possibilities it offers.
That said, I don’t deny there are issues - copyright concerns, as well as serious problems with fraud and fakes it can enable. As a mother, I’m terrified by the thought that someone could use my voice or image against my children. Now we have to be much more careful with what information about ourselves we put online - photos, videos, audio.
AI also creates a lot of low-quality content. But there was also low-quality content before AI.
As for writing, I don’t use AI there. It’s terrible at creative writing, plus that’s a space I want to keep entirely my own.
However, I do use ChatGPT to help write and translate tons of bureaucratic emails in a foreign language (which is, unfortunately, necessary when living abroad), and this saves me time to do what I actually enjoy, including writing.
One of my favorite YouTube videos from last year is about scientific breakthroughs of 2024. It’s in Russian, so I won’t link it here, but it mentions how AI, thanks to its ability to process massive amounts of data and detect patterns, has already helped scientists with several discoveries. For example, it helped identify a substance that might be effective against antibiotic-resistant bacteria. It also contributed to a breakthrough in forensics related to fingerprint analysis, among other things.
Of course, AI makes mistakes, it’s often inaccurate, and everything it produces needs double-checking. But it can also be useful. That’s why I disagree with people who view AI as pure evil.
I use it for art, video projects, web design, and official correspondence, languages learning. Even though I try to keep up with AI trends, it evolves so fast that it’s impossible to follow everything - it updates literally every day.
It can be used for bad things (fraud), but also for good (scientific research). I’d say how I use it is somewhere in the neutral zone. I hope it doesn’t harm anyone - and maybe even makes someone happy.
So, I will continue creating art, including with the help of AI, and in my next post, I’ll tell you about my experiments with AI videos.
I’m open to discussing this topic - but please, be polite.
6 notes
·
View notes
Text
I desprately need someone to talk to about this
I've been working on a system to allow a genetic algorithm to create DNA code which can create self-organising organisms. Someone I know has created a very effective genetic algorithm which blows NEAT out of the water in my opinion. So, this algorithm is very good at using food values to determine which organisms to breed, how to breed them, and the multitude of different biologically inspired mutation mechanisms which allow for things like meta genes and meta-meta genes, and a whole other slew of things. I am building a translation system, basically a compiler on top of it, and designing an instruction set and genetic repair mechanisms to allow it to convert ANY hexadecimal string into a valid, operable program. I'm doing this by having an organism with, so far, 5 planned chromosomes. The first and second chromosome are the INITIAL STATE of a neural network. The number and configuration of input nodes, the number and configuration of output nodes, whatever code it needs for a fitness function, and the configuration and weights of the layers. This neural network is not used at all in the fitness evaluation of the organism, but purely something the organism itself can manage, train, and utilize how it sees fit.
The third is the complete code of the program which runs the organism. Its basically a list of ASM opcodes and arguments written in hexadecimal. It is comprised of codons which represent the different hexadecimal characters, as well as a start and stop codon. This program will be compiled into executable machine code using LLVM IR and a custom instruction set I've designed for the organisms to give them a turing complete programming language and some helper functions to make certain processes simpler to evolve. This includes messages between the organisms, reproduction methods, and all the methods necessary for the organisms to develop sight, hearing, and recieve various other inputs, and also to output audio, video, and various outputs like mouse, keyboard, or a gamepad output. The fourth is a blank slate, which the organism can evolve whatever data it wants. The first half will be the complete contents of the organisms ROM after the important information, and the second half will be the initial state of the organisms memory. This will likely be stored as base 64 of its hash and unfolded into binary on compilation.
The 5th chromosome is one I just came up with and I am very excited about, it will be a translation dictionary. It will be 512 individual codons exactly, with each codon pair being mapped between 00 and FF hex. When evaulating the hex of the other chromosomes, this dictionary will be used to determine the equivalent instruction of any given hex pair. When evolving, each hex pair in the 5th organism will be guaranteed to be a valid opcode in the instruction set by using modulus to constrain each pair to the 55 instructions currently available. This will allow an organism to evolve its own instruction distribution, and try to prevent random instructions which might be harmful or inneficient from springing up as often, and instead more often select for efficient or safer instructions.
#ai#technology#genetic algorithm#machine learning#programming#python#ideas#discussion#open source#FOSS#linux#linuxposting#musings#word vomit#random thoughts#rant
7 notes
·
View notes
Text
G Witch Onscreen Text: Episode 5
Part SEIS of my attempt to transcribe and discuss all the text that appears on screens and tablets in G Witch, because I got that dog in me! This is episode 5, "Reflection in an Icy Eye"
<< Episode 4, if you so dare.

Till and Suletta Boiled Eggs Indulgence.
Shall we begin?

TEXT: WINNER PILOTING DEPARTMENT KP003 ELAN CERES F/D-19 ZOWORT 7 WINS 0 LOSS 0 TIE
At the end of Elan's 3 v 1 duel, we get a look at the Zoworts ID and the fact that he has 7 wins and no losses.

When Bel is speaking to the Peil witches, we get another look at Aerial's profile. What's new here are the terms on the bottom right, those being
PMET LINK PMET SUBLINK BIOINFO LINK PILOT DATA LINK MS DATA LINK INTEGRATED PMET LINK
I could not tell you what any of these mean, BUT I have recorded them for convenience.

The text on Nuno's tablet is very difficult to make out, but we can for sure read CONTROL SYSTEM on the header at the top, so we know that's what he's looking at here. I'll give my best guess as to what the 3 sub-headers say, from top to bottom.
I-MSEACTRL-SYS I-MSEECTRL-SYS 5011-ONCODE
If my transcription is right, the first two are probably meant to be read as something like I - MOBILE SUIT [EA/EE] CONTROL SYSTEM
I'm not as confident in the bottom one though, i think i have ONCODE correctly but I'm not sure if the first half is really 5011, which would be Aerial's Permet Code ID. But it's the only interpretation that makes sense to me because I can only read it otherwise as SETH-ONCODE. And I have my doubts about that one.
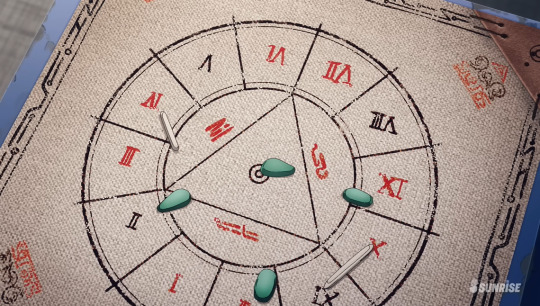

Some broader looks at Aliya's divination table

Of course, everyone and their mother would tell you this, but Aliyah points to the stone that landed on the Roman Numeral for 12, wondering if it represents 'a brother' of Suletta's. This is foreshadowing the Eri reveal, as Aerial + the Eri clones that pilot each one of its GUND Bits adds up to 12, meaning Suletta has 12 sisters.

Of course, the stone in the middle represents her mother, and Aliyah comments that it's very big.
I can't help but wonder if Miorine is represented somewhere here as well?

This scene is where we finally get to see the title of the book Elan is reading. As I stated before, this book is The World as Will and Representation (Translated in the show proper as The World as Will and Idea) by Arthur Schopenhauer. The importance of this book to understanding Elan's character cannot be overstated, and it's worthy of its own post, but simplified as far down as possible (and also acknowledging that I have yet to read the essay myself, it's long...I'll get to it though, I promise...)
The two most essential ideas of this work in their relation to Elan are that:
All human suffering and conflict is a result of the "Will" that exists within us: An ever striving force that pushes us to pursue our innermost desires.
In order to reduce the inherent pain and suffering that comes with life's cruelty, one can minimize their desires, and deny the force of their will.
In simpler terms, if you never desire anything from your life, even the idea of living itself, you will never be made to suffer from the lack of it.
From the shows beginning, we can see how Elan completely embodies this philosophy. He denies love, he denies his emotions, he never acts of his own accord, only following the orders he's been given by Bel and the Peil witches.
But that changes when he meets Suletta, because Suletta awakens within him one of his deepest desires. To find someone who is like him, someone who understands him.

But when he realizes that Suletta isn't an Enhanced Person, that he's still completely alone, he can't handle it.

Because he allowed himself to want for something, he invited suffering back into his life when it was something he was not allowed to have.
And now that he's opened his heart to desire, it's not something that can be closed. For the rest of our time with him, we see how this incident with Suletta has broken the spell. When he duels Guel, he tortures him. Shaddiq repeatedly acknowledges that there's been something different about him ever since he was with Suletta.

In the multiple scenes when Elan sees the candle of the birthday cake when he closes his eyes, the flame represents how his will has been relit. It's the flame of his desire. And despite his continued insistence that it doesn't exist, that he still doesn't want anything, doesn't need anything, the flame only keeps growing.

It sparks up when Suletta sings the birthday song to him.

And it all comes to a head during their duel. He immediately starts listing off the things Suletta has that he doesn't. Friends, family, a past and future, even hope. And laments that it's just not fair, demands to know why she can't let him have one thing.


When he fully accepts himself, and remembers the person who celebrated his birthday, he realizes that it was wrong to assume that he had nothing, and to continue to believe that he could never have anything.



But, tragically, in fully accepting his desire, he also had no choice but to accept the suffering that comes with it. And, well.
Yknow.

Anyway in this scene we can see the path that he wants Suletta to take in the testing sector.

We can see that Lauda's Dilanza is registered as such in Asticassia, and its ID code is MD-003 1L. Despite being registered as such, both Elan and Rouji refer to it as "Regolith" in this duel.
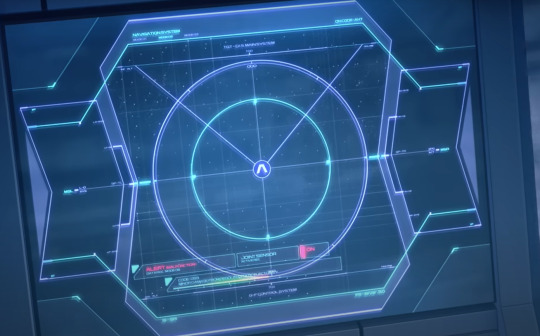
This is the Pharact's navigation system. At the bottom, the warning says: ALERT: MALFUNCTION JOINT SENSOR: ACTIVE MINOR DAMAGE FROM [???] STATIC ELECTRICITY.
We can see that the Pharact is showing that the static electricity is damaging its joints. This is where Elan gets the idea of how to defeat Guel.

TEXT: (top to bottom) ALERT DMG CTRL-SYS ON
MD-R-0099[?] RIGHT LEG - [???] DAMAGE
MD-O HEAT AXE - RECOVERED
This shows up on the display when Guel is hit by the Pharact's stun beams for the first time. Though my transcription might not be fully accurate, we can at least glean from this that mobile suit components seem to have their own internal codes used by their various systems. That's cool!

When Guel is immobilized by the static electricity, the warning on his screen reads ANAMOLY DETECTION

Bonus: When Guel first makes it through the stun lasers and approaches Elan, you can actually see the monitor start writing out "TARGET LOCKED" before cutting to the next scene.
They really must have had a whole team of people working on these UI elements and they REALLY gave it their all!
Anyway, that's all!! Sorry that this one kinda took a detour down the Elan train for a bit there! I always get carried away with these things...
Uhh as a reward.... hmm...

One time I saw Shaddiq referred to as "Malibu Sephiroth" and I've never been able to forget it. It's so real. God Damnit.
Click here to go to Episode 6! >>
Click here to go to the Masterpost!
52 notes
·
View notes
Text
Universes Within theorycrafting: Assassin's Creed (part 1)
Kept sliding off making posts for the bigger sets (LTR, PIP...WHO is mostly pending more data on the space opera plane) just because I was struggling to organize my thoughts on them; ACR has about half the total new cards as the commander products, and a lot of those are on the simpler end, so it's a lot easier to just go through on a case-by-case basis. Hopefully that'll help get the word-gears churning for the other sets.
Part 1's gonna be the cards that don't need name changes for UniWit adaptation; 49 out of 105 (not counting Raven Clan War-Axe, which would be close to the line in a vacuum but is mechanically tied to a card that does need a rename regardless), a little under half.
Battlefield Improvisation
Works more or less anywhere, but one particular interpretation that tickles me is a bit of flashy showmanship in Valor's Reach when a fighter is reduced to a 1v2 and starts going to town using their fallen partner's weapon. Given the colors, maybe Regna dual-wielding her scythe and whatever massive polearm Krav is rocking?
Detained by Legionnaires
Even on Ravnica I figure actual Pacifism is more likely to see a reprint, but the Boros are legionnaire-cops, so this would translate there fine.
Distract the Guards
Assassins and Rogues? Those are both outlaws, so Thunder Junction's the obvious fit. I'm gonna say it's a Freestrider operation, one group drawing the Sterling Company wardens away while another group stages a jailbreak.
Escarpment Fortress
Apparently an escarpment is a kind of cliff face, so this is a fortress built on or into a cliff. No shortage of fits there; could be an Akroan outpost, could be a Zendikari refuge, could be a highland monastery of the Jeskai/Ojutai...et cetera, et cetera. Take your pick.
Fall of the First Civilization
Could be Fall of the Thran but slightly to the left, but I like this as an Oltec tale of the First People of Ixalan; just because they're unknowable due to being four apocalypses deep doesn't mean the Oltec wouldn't have stories about them in some capacity, and "how their world ended" would be right at the top of the list.
Haystack
The same bit as the original could work in most of the multiverse's cities, but I actually like the idea of setting this on Innistrad: the terrified eyes of a pair of peasants barely visible peaking out from within a pile of hay as a shadow shaped distinctly like a werewolf passes across it. A perfect hiding spot...so long as your breathing doesn't give you away.
Hookblade
Zendikari kor lineslinger equipment. One of those "you could put it in a set and most people wouldn't even realize it's a reprint, it fits so cleanly" cards: White "hook" equipment that grants temporary flying? Yeah, that's a kor card alright.
Keen-Eyed Raven
Mostly notable in that, as far as I can see, Magic's ravens have been entirely restricted to Blue and Black up to now. Certainly doesn't mean they can't fit there, though: maybe the Beskir have taken to keeping and training ravens in emulation of the Omenseekers, or maybe Will has gotten what exists of the Eldraine courts to start using them as couriers and scouts.
Settlement Blacksmith
The two natural fits for planes referring to "settlements" are Zendikar and Thunder Junction, and this works fine with either. Zendikar's the one with a history of Equipment themes, though, and there's more than enough space for flavor text talking about times of necessity spread stoneforging traditions beyond the kor that developed and long kept them. (Could even make it a Nahiri quote, have her complaining about what she sees as wrong about Zendikar these days.)
Tax Collector
Magic doesn't exactly spend a lot of time talking about tax policy, but anywhere that has actual money is gonna have taxes. The Orzhov are definitely the most obvious fit, though, even if detain is an Azorius mechanic.
Templar Knight
There are two other extant Magic cards with "templar" in their name: Capashen Templar, a Benalish Knight, and Noble Templar, an Otarian Cleric Soldier. The latter has a more obvious legendary artifact to amass an army to quest for - the Mirari - while the former is actually a Knight (the gap between Knight and Cleric Soldier is not a large one, but creature types mattered in Otarian sets). Either could reasonably be expanded out into a cohort of knights going on a "holy" quest; just a matter of preference.
What Must Be Done
I feel like there's an even cleaner fit I'm failing to think of, but the main place my mind goes is to Liliana's ultimatum to Thalia in original Innistrad block: sunder the Helvault and release Griselbrand, or Liliana kills all of the Thraben cathars guarding it. Reanimation or boardwipe, a choice faced by a White-aligned character - it works.
Assassin Den
In the MKM story, Etrata had a well-hidden personal base/crash pad that was also extensively trapped against anyone trying to break in. Feels like a natural fit for a Wall with >0 power that can buff a creature and enhance their stealth - the interior would naturally be equipped with every tool a master assassin could need. Presumably other Dimir assassins have their own hideouts, justifying it being nonlegendary, but that'd be the specific one I'd depict; there's more than a bit of space for an Etrata quote in the flavor text.
Assassin Gauntlet
Would be perfect as a piece of hacking tech in modern Kamigawa if Ninja wasn't a separate type. As is, we do know that the Dimir sometimes use the Izzet as a magitech development program (sometimes outright hiring them, more often through espionage and subterfuge), so an Izzet-sourced gauntlet with some sort of built-in smoke bomb or flashbang being used by a Dimir assassin would fit well enough.
Ballad of the Black Flag
I...don't know that we actually have any art of specifically the flags of Brazen Coalition ships? So it's not a given that they actually have black flags to line up with the name, but that also means that I can just decide they do and that can just be something that first becomes clear with the UniWit art for this.
Otherwise it fits fine, though: the tale (told by shanty, perhaps, if that's something that can be conveyed/implied through Saga-style art) of the humans and orcs of Torrezon fleeing across the ocean in search of better fortunes, and the often-violent steps they would take to claim and secure those fortunes.
Become Anonymous
Lazav, fading back into the obscurity of the crowd in the wake of the invasion. Could easily have very similar composition to the ACR art, though obviously that's far from a requirement. Just naturally leans into the same vibe.
Brotherhood Spy
Let me pull up the flavor text from the original Time Spiral printing of Assassinate:
The rulers of old Dominaria kept assassins on retainer. However, the true loyalty of these master killers was always to their peers. This elite brotherhood survived the fall of the old royal order.
That's right, Dominaria has a canonical brotherhood of assassins! That plane is the kitchen sink that keeps on giving. Given the context, that brotherhood presumably survived up until the Rift Crisis, so it may well still be around in the present day. The lack of specific information gives me plenty of freedom in interpreting the various "Brotherhood" cards in the set to fit that context.
In this case, there's plenty of space for flavor text to talk about the network of informants that support and assist the members of the brotherhood actually assigned the task of assassination.
Desynchronization
On an entirely different note (heh) from the rest of this post, I'd set this one at Strixhaven: with mundane music, the worst that happens when an orchestra falls out of sync is that the performance grinds to a halt after just sounding really bad for a bit. With music magic, discordance can have a much more tangible blowback, tightly woven harmonics pulling apart into a chaotic, concussive blast.
("Let's just...try it again from the top." -Zaffai, thunder conductor)
Eagle Vision
An Obscura-aligned eagle aven scoping out the location of an impending job - sometimes there's something to be said for taking a name literally.
Escape Detection
A suitably generic "Dimir sneakiness" effect.
Hookblade Veteran
Unlike the actual Hookblade, I don't think a mono-Blue Human Assassin lines up nearly as well with established Zendikar flavor. The best fit I can come up with is actually on Kaladesh; none of the night market-associated creature cards had the Assassin subtype, but it wouldn't be a stretch for Gonti to employ assassins, and a gauntlet with an integrated, extendable grappling hook would be real handy for Spiderman-ing around the spires of Ghirapur.
Loyal Inventor
Somehow the first Fioran card in this post: once she took the throne, the High Paliano Academy was subject to Marchesa's demands, and some of its finest minds now vie for her favor, presenting their newest, most cutting-edge inventions before the royal court.
Tranquilize
Sleeper Dart was an Ikorian card, so this is just a slightly different framing of the use of that same bit of poacher tech. Not exactly hard to make work elsewhere, but that's the most clean fit.
Assassin Initiate
I like to imagine Marchesa's used the resources of the crown to open an official (if not particularly publicized) royal school for assassins - the Renaissance equivalent to the CIA academy, basically. She didn't exactly cut ties with her old connections, but as the new seat of power in the high city, her eyes (and blades) need to extend far further, which means she needs more manpower. Conveniently, this card's got space for a solid four lines of flavor text to exposit about those developments.
Brotherhood Ambushers
As the most generic of the "Brotherhood" cards, this would probably be the card that exposits more broadly about the Dominarian assassin brotherhood as a whole, building on that Assassinate FT to talk about the position they fill in the modern day.
Brotherhood Patriarch
The death trigger points me toward the trope of "you become the master assassin by being the one to take out the current master assassin."
Hemlock Vial
The art and flavor text are both generic enough that they could probably just reprint the whole card exactly as-is aside from the frame and it'd work fine as a "UniWit" treatment. Otherwise, the obvious home for this is to ground it in Theros - probably Meletis in particular. They already did the same bit with Sip of Hemlock, but Theros isn't exactly averse to reusing tropes when necessary.
Merciless Harlequin
Appropriately for a design that's Blade Juggler but slightly to the left, this is a pitch-perfect fit for a Rakdos assassin.
Petty Larceny
Card name is a crime? Check. Card is mechanically a crime? Check. This definitely belongs on Thunder Junction - have Tinybones picking someone's pocket in the middle of a bar brawl. (Maybe show Vraska fighting in the background to help justify the Assassin-typal element.)
Phantom Blade
I'd go more classic-fantasy with this one, I think: a cursed sword that captured the soul of the first being it killed, becoming wreathed in ominous spectral energy. Feels right at home with the sword-and-sorcery vibes of Corondor on Dominaria, but off the top of my head I could also see it fitting pretty cleanly on Innistrad or Ixalan.
Poison-Blade Mentor
Another part of that Paliano assassin school - can't have students without people to teach them.
Restart Sequence
The grand prize of her daring heist was also her escape plan.
(Art: a ninja stands at a control panel in a dimly-lit Futurist laboratory, her hands flying across the screen as lines of light begin to glow across a prototype mech in the background as it starts up.)
I mostly try to keep Freerunning cards flavorfully tied to Assassins in particular, but there's some where it makes more sense to bend a little further, and this is pretty close to top of the list. It helps that Ninja and Assassin have pretty heavy overlap.
Headsplitter
Not all poachers favor range or stealth.
The two Ikorian cards with the Assassin type are both specifically archers, but poachers being able to be Assassins is the best way I've found to square "Headsplitter" implying an immensely un-assassin-y weapon while also specifically making an Assassin token. Thus, a poacher with a gnarly, Monster Hunter-esque bone blade. Probably not too big since it only gives +1/+0, but not exactly subtle.
Hidden Footblade
Stiletto heels, where the heel (or possibly the toe, depending on what would work best for the art) conceals a stiletto blade - I'm far from the first person to make that pun, but, well, if the shoe fits...
(Most natural fit in the multiverse for that concept is probably New Capenna, specifically the Cabaretti - elaborate fashion that's more practical/deadly than it appears is right up their alley.)
Labyrinth Adversary
That sure is a Minotaur card, all right. The specific callout to a labyrinth in the name means that probably the most natural fit for this is Theros. (Technically Ulgrotha also had minotaurs connected to labyrinths, but Theros actually has a modern visual identity to build off of, whereas Ulgrotha would be pretty close to starting from scratch, which is a hell of a tiebreaker.)
Monastery Raid
Another pretty literal one: Khans!Zurgo leading the sacking of a Jeskai monastery by a Mardu raiding party. (Leaning more into the "or commander" side of Freerunning here.)
Overpowering Attack
This one's more in line with the printed Assassin poachers than Headsplitter: Kelsien leading a veritable army of poachers armed with bows, raining hellfire down from atop a cliff onto a big monster below.
Hunter's Bow
This one works damn near anywhere, but putting it on Kaldheim (tying it to either the Kannah or the elves of Skemfar) tickles me because it means it could even keep the flavor text as-is if it wanted.
Palazzo Archers
The high throne of Paliano has been extensively guarded against the subtlest possible angles of attack, but that doesn't mean it leaves the more obvious approaches unguarded: the archers that watch the skies around it are sharp and well-armed.
Viewpoint Synchronization
The best idea I've got for this one is set on modern Kamigawa: a ninja watching a security feed displaying the views of several different cameras at once. Kind of mundane, but everything else I've come up with runs headlong into "how would an artist even convey this concept in a single piece of card art," so simple and literal carries the day.
Rooftop Bypass
Just a fairly straightforward bit of Dimir stealth/infiltration. Ravnica's not exactly short on options for rooftop travel.
Bleeding Effect
It's not quite a perfect color match, but the best fit I've come up with for this name and effect is the Order of Saint Traft, who willingly allowed themselves to be possessed by the geists of former cathars in cooperative union. In such a situation, it would make sense for the lines between the living and the dead to blur - becoming hard to tell where the skills and memories of one end and the other begin.
Bureau Headmaster
Another Fioran, in one respect or another. Could be another teacher at assassin school, could be positioned at the Paliano embassy (/assassin cell) on Thunder Junction (not really featuring in this half of the post, but one of the better throughlines I've been able to come up with the various mostly-legendary RW Assassins in the set). Probably a slightly better fit for the former, as a leading weapons teacher.
Brotherhood Regalia
The Dominarian brotherhood probably wants something approximating a unified visual identity anyway, so this is just the clearest portrayal of their garb.
Hidden Blade
The Dimir did more or less exactly this bit with Silent Dart in GRN, so this is just that again. One of those cases where someone who wanted to proxy could just directly lift another bit of Magic art and it would still work fine.
Smoke Bomb
Kamigawa feels like the best fit for a smoke bomb - either classic or modern. Solidly a ninja tool either way.
Towering Viewpoint
Another one that works basically anywhere, but I like the full-circle take of tying this to the Amonkhet version of Mighty Leap - making it a particularly tall obelisk in Naktamun that initiates would jump from, either as part of a trial, just on a dare, or as a statement of proof of their faith.
Brotherhood Headquarters
Could more or less swipe the flavor text from ACR Assassin's Den for this one, since it translates as basically the same beat: a covert base of operations hidden in plain sight in a major city. (In the context of modern Dominaria, that's New Benalia, New Argive, or possibly whatever the biggest city of Suq'ata or Femeref is these days.)
7 notes
·
View notes
Text
High-Risk Payment Processing: Strategies for a Thriving Credit Repair Business
Article by Jonathan Bomser | CEO | Accept-Credit-Cards-Now.com

In the ever-shifting landscape of financial services, the voyage of credit repair businesses encounters unique challenges, particularly in the realm of payment processing. As e-commerce ascends and the demand for credit repair services burgeons, the quest for effective high-risk payment processing solutions takes center stage. Whether at the helm of credit repair or navigating the intricate waters of CBD products, the acceptance of credit card payments emerges as a compass pointing to success. This article plunges into the intricacies of high-risk payment processing, unraveling strategies that not only foster flourishing enterprises but also position them as pioneers in their industry.
DOWNLOAD THE HIGH-RISK PAYMENT PROCESSING INFOGRAPHIC HERE
The Magnetic Pull of Credit Card Acceptance
Beyond mere convenience, the magnetic pull of credit card acceptance resonates profoundly in today's business milieu. It is not merely about transactional ease; it's about broadening horizons and amplifying revenue streams. By embracing credit card payments, be it in the arena of credit repair or CBD enterprises, businesses swing open gates to a more extensive clientele. Customers, valuing the versatility and security offered by credit and debit cards, find it simpler to engage with services providing this option, translating into heightened conversion rates and the organic growth of businesses.
High-Risk Merchant Processing: A Strategic Alliance
In sectors like credit repair and CBD trade, where the "high-risk" tag is commonplace, perceiving it as an opportunity rather than an obstacle becomes paramount. It's not merely a label but a gateway to markets teeming with potential. To navigate this successfully, forging alliances with reliable high-risk merchant processing providers emerges as a strategic imperative. These specialized processors comprehend the unique challenges faced and deliver tailored solutions to suit the specific needs of credit repair businesses and CBD merchants.
E-commerce Payment Processing: Transformative Paradigms
The realm of e-commerce payment processing emerges as a transformative force for credit repair businesses. It not only facilitates secure online payments but also equips businesses with tools to efficiently manage transactions. The article underscores the significance of e-commerce payment processing, shedding light on its pivotal role and emphasizing the need for specialized payment gateways attuned to the intricacies of the credit repair industry.
The Strategic Leverage of Credit Repair Payment Gateways
A credit repair payment gateway stands as the linchpin for online business operations, ensuring seamless connections between customers and services while safeguarding their financial data. The article advocates for the careful selection of payment gateways aligned with business goals, ensuring a frictionless checkout process, reduced cart abandonment rates, and an augmented revenue stream. Features like one-click payments and compatibility with various credit and debit cards take center stage in enhancing the user experience.
The Tactical Significance of CBD Merchant Accounts
For CBD merchants, the possession of a dedicated CBD merchant account emerges as a strategic imperative. The association of the CBD industry with cannabis places it within the high-risk category. However, with the burgeoning acceptance of CBD products, the market presents rapid expansion. The article delves into the significance of a dedicated CBD merchant account, emphasizing its role in enabling businesses to offer customers the convenience of credit card payments and contributing to overall business growth.
The Ever-Present Ally: Online Payment Gateways
In a digital age where business operations transcend time zones, an online payment gateway becomes the perpetual ally, processing payments even when physical stores shutter for the day. The perpetual availability not only broadens revenue potential but also elevates customer satisfaction. The global reach facilitated by online payment gateways extends business access to customers worldwide, free from geographical constraints.
The Pulsating Core: Credit Card Processing Systems
In the intricate dance of credit repair or CBD ventures, the pulsating core lies in a reliable credit card processing system. This system serves as the nucleus, ensuring secure and swift transactional processes. The article advocates for investments in robust credit card processing systems, emphasizing the need for real-time transaction monitoring and fraud prevention features. The assurance of secure transactions emerges as priceless for both businesses and customers.
The Guardian Shield: High-Risk Merchant Accounts
In the arena of high-risk businesses, a high-risk merchant account stands as the guardian shield, offering protection against potential challenges. This shield provides access to payment processing solutions tailored to the industry's needs. With the right high-risk merchant account, businesses can navigate the labyrinth of high-risk payment processing with unwavering confidence.
Embracing High-Risk Payment Processing for Triumph
Embracing high-risk payment processing is not merely a choice but a necessity for credit repair businesses and CBD merchants. The article underscores the empowerment derived from accepting credit cards, enabling businesses to thrive and grow. The advocacy for partnerships with reliable merchant processing providers and the utilization of secure payment gateways crystallizes into a seamless and secure transaction experience for customers.
youtube
In a dynamic business landscape, adaptability emerges as the keystone. The high-risk label should not be viewed as a deterrent but as an opportunity to shine in the industry. The article encourages investments in robust credit card processing systems and dedicated high-risk merchant accounts to safeguard businesses and propel them toward success.
In the contemporary digital epoch, where convenience and security reign supreme, accepting credit cards for credit repair and CBD products paves the path to prosperity. The article urges businesses to embrace the power of high-risk payment processing, positioning themselves for success and a brighter future. It's an invitation to say yes to new heights.
#high risk merchant account#payment processing#credit card processing#high risk payment gateway#high risk payment processing#accept credit cards#credit card payment#merchant processing#credit repair#Youtube
18 notes
·
View notes
Note
There were some people going around the internet basically saying that pokemon digitizing in the PC should have the same paradox as like.... How people used to talk about teleporters and things. How do you know the pokemon you put in is really the same one you're getting out? if they're just translated into numbers?
I'm sure they're not actually onto anything but it made me kinda uncomfortable...
@lost-in-pinwheel-forest
The answer is essentially the same as the reason the pokeballs work in the first place; the infinity energy isn't just converted to numbers, although with the shorthand of digitized I would completely understand why so many people seem to think that is the case.
In reality it would be more apt to say that the PC pokemon storage system is specifically designed for the transport and storage of infinity energy in a sort of stasis, just like they are within a pokeball. There is not any real conversion at all, and that's why the network is so complex and why you have to be specifically certified to work on this sort of machinery, it is a delicate, intricate machine with a highly specialized job!
The machinery that allows the connection of the pokemon storage system to branch to different regions and more remote locations is quite fascinating, it requires the Internet, yes, but the actual transportation itself actually does not happen as data but as pure energy! I can not pretend to understand the mechanics of this, it is far outside of my own expertise, but truly technology is amazing.
All of this is quite a lot for most people to keep straight though, especially the younger ones, and as such simpler terms such as digitize have become standard in the common lexicon :) In short, the pokemon you put in is the same pokemon you take out, there is no way to alter, duplicate or delete their data because there is no data (in the way we think of it anyway) to be altered!
19 notes
·
View notes
Text
Discovering the Wonders of Machine Learning and Its Advantages:

Have you ever wondered how computers can learn and make choices all by themselves? It's like teaching them to be smart on their own. That's what machine learning is, and it's changing the way we do things. Let's take a journey to find out why machine learning is so amazing. We'll talk about things like helping computers understand languages, predicting the weather, and even teaching them to drive cars! So, let's explore the magic of machine learning.
The Good Things About Machine Learning:
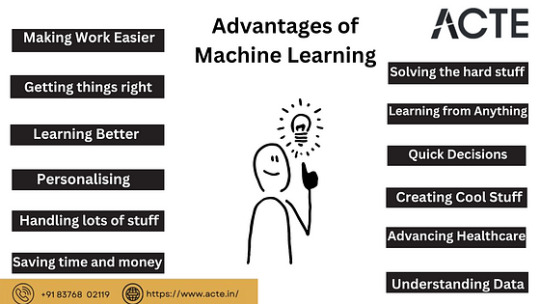
Understanding InformationThink of machine learning as a super-smart helper that can deal with really big and complicated sets of information. Humans might get confused with all that data, but machine learning can assist us in making decisions based on it.
Changing the GameImagine you have a giant puzzle with lots of pieces. You know they make a picture, but it's just too hard to put it together by yourself. Machine learning is like a super-fast puzzle solver. It not only puts the puzzle together but also shows you amazing things about the picture that you might have missed.
Making Tasks SimpleOne cool thing about machine learning is that it can do boring and repetitive tasks for us. Think about typing lots of numbers into a computer spreadsheet – it can do that for us, and it hardly ever makes mistakes. This means we can use our time for more fun stuff.
Getting Things RightMachine learning models are really good at certain jobs. For example, they can tell if an email is spam much better than we can. That's super useful because we don't want our email inboxes to be filled with spam. It's like having a superhero to keep our emails clean.
Learning and Getting BetterThe more a machine learning model sees, the smarter it becomes. It learns from new information and gets better at what it does. This is really helpful in jobs where things change a lot, like predicting the stock market or understanding what people are talking about on social media.
Personalizing EverythingHave you ever noticed that websites like Netflix or Amazon suggest things you might like? That's machine learning in action. It watches what you do and recommends things you'll enjoy. It's like having a personal shopper who knows your tastes.
Handling Lots of StuffMachine learning models are like super chefs who can cook for a huge party. They can manage a massive amount of data and make quick decisions. This is really important for things like banks, which need to handle lots of transactions quickly and accurately.
Saving Time and MoneyMachine learning can save businesses a ton of time and money. For example, it can predict when machines in a factory might break, so they can be fixed before they cause big problems. This saves a lot of money because it's cheaper to fix things before they break.
Solving Tricky ProblemsSome problems are really tough, like understanding different languages, recognizing objects in pictures, or even playing complicated games. Machine learning can take on these challenges and find solutions that might be hard for humans.
Learning from AnythingMachine learning can learn from almost anything, even from things that don't seem like regular data. For example, it can learn from written words, pictures, or videos. This helps businesses understand what people think and like.
Quick Decision-MakingImagine being in a self-driving car. It needs to make fast decisions to keep you safe. Machine learning helps it do that by processing data from sensors and making decisions in real-time.
Creating Cool ThingsMachine learning is the technology behind cool stuff like virtual assistants (like Siri or Alexa) and language translation tools. These devices make life simpler and more enjoyable, like having a helpful friend who can speak every language.
Being Fair and JustSometimes, people can make unfair decisions because of their biases. Machine learning can be set up to be fair and impartial. It helps make choices in things like hiring or lending money based on facts, not feelings.
Driving DiscoveriesMachine learning isn't only for businesses; it also helps scientists. They use it to study complex data and make discoveries in areas like genetics, space exploration, and materials science. It's like having a super microscope that shows things we couldn't see before.
Protecting Our PlanetMachine learning can also help us take care of the environment. It's used to keep an eye on pollution, track changes in the climate, and predict natural disasters. By studying a lot of data, we can make better decisions to protect the Earth.
Improving HealthcareHealthcare is getting a boost from machine learning. It helps doctors diagnose diseases, discover new medicines, and keep track of patients. It's like having a super-smart medical assistant.
In summary, machine learning is a superpower that's changing the world. It makes handling data easy, automates tasks, personalizes experiences, and solves tough problems. It's fair, it's quick, and it's shaping the future. With machine learning, the possibilities are endless. If you want to learn more about machine learning or need help using it in your business, you can ask experts or take special courses. ACTE Institute offers courses that can give you the knowledge and skills to do well in this field. Think about all the amazing chances for analysing data, automating tasks, and making decisions that machine learning offers.
7 notes
·
View notes
Text
Log_3.TXT
07/04/2023, 07:15 (GMT-5)
After being awake until roughly 3 AM I was able to do it, it wasn't easy at all and I'm actually surprised I was able to do it without waking up the other people in this house, right now, I am in class about to fall asleep, but I think I can remain awake to finish both my literary analysis AND this entry.
First of all, was the watch easy to hack? No. Let me elaborate, I used an old sports watch I found in my closet, I'm more surprised about the fact that it was almost as good as new and worked perfectly after three years of not being used rather than on me being able to hack it, I'm not entering details, but the watch had a simple OS I quickly made my way into, by connecting it to my PC I was able to crash the OS and replace it with an even simpler one, that only runs Digimon Capture, keeping the watch OS this simple, I open the door for me to update the software if I catch any bugs or I just need to improve the watch's features.
Now, let me explain how the watch works, you see, Digimon need to eat, however I'm not really "in love" with that concept right now since feeding them would take time I could use advancing on my investigation, thus I had an idea, since the watch I use as a shell is a sport focused one, I linked the active digimon's necessities to the function that reads my heartbeat, that way, I'll be able to do research without pausing to feed my monsters and putting them to sleep, I also coded some other functions based on what features the watch has, an example would illustrate it better. Digimon need to exercise so they can increase their battle capabilities, I found a way to translate their battle capabilities into three basic stats, stats I will increase by doing exercise myself, and maybe that way I'll hopefully get in better shape, the watch can recollect items that can be helpful when raising a digimon, I hate to end this entry on a bitter note, but I can't ignore my faults all of this features were added to compensate for two things, the first one not being strictly my fault but I still feel salty about it, the thing is, this watch has little to none storage capacity, so it can only have 3 digimon at the same time inside it's OS, which is actually more than other Digimon Docks, but I wanted to save at least two pairs of digimon, the second is entirely my fault... Digimon have battle capabilities for a reason, they need to fight with their equals to absorb their data and grow, so they can increase their power and eventually go through a process called "Evolution" however I wasn't able to code a battle function for this watch but I have Guilmon working on something, I can't discuss it any further, not now at least but... I'll keep you updated.
ATT: ARC
3 notes
·
View notes
Text
For state-sponsored hacking operations, unpatched vulnerabilities are valuable ammunition. Intelligence agencies and militaries seize on hackable bugs when they're revealed—exploiting them to carry out their campaigns of espionage or cyberwar—or spend millions to dig up new ones or to buy them in secret from the hacker gray market.
But for the past two years, China has added another approach to obtaining information about those vulnerabilities: a law that simply demands that any network technology business operating in the country hand it over. When tech companies learn of a hackable flaw in their products, they’re now required to tell a Chinese government agency—which, in some cases, then shares that information with China's state-sponsored hackers, according to a new investigation. And some evidence suggests foreign firms with China-based operations are complying with the law, indirectly giving Chinese authorities hints about potential new ways to hack their own customers.
Today, the Atlantic Council released a report—whose findings the authors shared in advance with WIRED—that investigates the fallout of a Chinese law passed in 2021, designed to reform how companies and security researchers operating in China handle the discovery of security vulnerabilities in tech products. The law requires, among other things, that tech companies that discover or learn of a hackable flaw in their products must share information about it within two days with a Chinese agency known as the Ministry of Industry and Information Technology. The agency then adds the flaw to a database whose name translates from Mandarin as the Cybersecurity Threat and Vulnerability Information Sharing Platform but is often called by a simpler English name, the National Vulnerability Database.
The report’s authors combed through the Chinese government's own descriptions of that program to chart the complex path the vulnerability information then takes: The data is shared with several other government bodies, including China’s National Computer Network Emergency Response Technical Teams/Coordination Center, or CNCERT/CC, an agency devoted to defending Chinese networks. But the researchers found that CNCERT/CC makes its reports available to technology "partners" that include exactly the sort of Chinese organizations devoted not to fixing security vulnerabilities but to exploiting them. One such partner is the Beijing bureau of China's Ministry of State Security, the agency responsible for many of the country's most aggressive state-sponsored hacking operations in recent years, from spy campaigns to disruptive cyberattacks. And the vulnerability reports are also shared with Shanghai Jiaotong University and the security firm Beijing Topsec, both of which have a history of lending their cooperation to hacking campaigns carried out by China's People Liberation Army.
“As soon as the regulations were announced, it was apparent that this was going to become an issue,” says Dakota Cary, a researcher at the Atlantic Council's Global China Hub and one of the report’s authors. “Now we've been able to show that there is real overlap between the people operating this mandated reporting structure who have access to the vulnerabilities reported and the people carrying out offensive hacking operations.”
Given that patching vulnerabilities in technology products almost always takes far longer than the Chinese law’s two-day disclosure deadline, the Atlantic Council researchers argue that the law essentially puts any firm with China-based operations in an impossible position: Either leave China or give sensitive descriptions of vulnerabilities in the company’s products to a government that may well use that information for offensive hacking.
The researchers found, in fact, that some firms appear to be taking that second option. They point to a July 2022 document posted to the account of a research organization within the Ministry of Industry and Information Technologies on the Chinese-language social media service WeChat. The posted document lists members of the Vulnerability Information Sharing program that “passed examination,” possibly indicating that the listed companies complied with the law. The list, which happens to focus on industrial control system (or ICS) technology companies, includes six non-Chinese firms: Beckhoff, D-Link, KUKA, Omron, Phoenix Contact, and Schneider Electric.
WIRED asked all six firms if they are in fact complying with the law and sharing information about unpatched vulnerabilities in their products with the Chinese government. Only two, D-Link and Phoenix Contact, flatly denied giving information about unpatched vulnerabilities to Chinese authorities, though most of the others contended that they only offered relatively innocuous vulnerability information to the Chinese government and did so at the same time as giving that information to other countries’ governments or to their own customers.
The Atlantic Council report’s authors concede that the companies on the Ministry of Industry and Information Technology’s list aren’t likely handing over detailed vulnerability information that could immediately be used by Chinese state hackers. Coding a reliable “exploit,” a hacking software tool that takes advantage of a security vulnerability, is sometimes a long, difficult process, and the information about the vulnerability demanded by Chinese law isn’t necessarily detailed enough to immediately build such an exploit.
But the text of the law does require—somewhat vaguely—that companies provide the name, model number, and version of the affected product, as well as the vulnerability's “technical characteristics, threat, scope of impact, and so forth.” When the Atlantic Council report’s authors got access to the online portal for reporting hackable flaws, they found that it includes a required entry field for details of where in the code to “trigger” the vulnerability or a video that demonstrates “detailed proof of the vulnerability discovery process,” as well as a nonrequired entry field for uploading a proof-of-concept exploit to demonstrate the flaw. All of that is far more information about unpatched vulnerabilities than other governments typically demand or that companies generally share with their customers.
Even without those details or a proof-of-concept exploit, a mere description of a bug with the required level of specificity would provide a “lead” for China’s offensive hackers as they search for new vulnerabilities to exploit, says Kristin Del Rosso, the public sector chief technology officer at cybersecurity firm Sophos, who coauthored the Atlantic Council report. She argues the law could be providing those state-sponsored hackers with a significant head start in their race against companies’ efforts to patch and defend their systems. “It’s like a map that says, ‘Look here and start digging,’” says Del Rosso. “We have to be prepared for the potential weaponization of these vulnerabilities.”
If China’s law is in fact helping the country’s state-sponsored hackers gain a greater arsenal of hackable flaws, it could have serious geopolitical implications. US tensions with China over both the country’s cyberespionage and apparent preparations for disruptive cyberattack have peaked in recent months. In July, for instance, the Cybersecurity and Information Security Agency (CISA) and Microsoft revealed that Chinese hackers had somehow obtained a cryptographic key that allowed Chinese spies to access the email accounts of 25 organizations, including the State Department and the Department of Commerce. Microsoft, CISA, and the NSA all warned as well about a Chinese-origin hacking campaign that planted malware in electric grids in US states and Guam, perhaps to obtain the ability to cut off power to US military bases.
Even as those stakes rise, the Atlantic Council’s Cary says he’s had firsthand conversations with one Western tech firm on the Ministry of Industry and Information Technology’s list that directly told him it was complying with China’s vulnerability disclosure law. According to Cary, the lead executive for the Chinese arm of the company—which Cary declined to name—told him that complying with the law meant that it had been forced to submit information about unpatched vulnerabilities in its products to the Ministry of Industry and Information Technology. And when Cary spoke to another executive of the company outside of China, that executive wasn’t aware of the disclosure.
Cary suggests that a lack of awareness of vulnerability information shared with the Chinese government may be typical for foreign companies that operate in the country. “If it’s not on executives’ radar, they don’t go around asking if they’re in compliance with the law that China just implemented,” says Cary. “They only hear about it when they’re not in compliance.”
Of the six non-Chinese firms on the Ministry of Industry and Information Technology’s list of compliant ICS technology firms, Taiwan-based D-Link gave WIRED the most direct denial, responding in a statement from its chief information security officer for North America, William Brown, that it “has never provided undisclosed product security information to the Chinese government.”
German industrial control system tech firm Phoenix Contact also denied giving China vulnerability information, writing in a statement, “We make sure that potential new vulnerabilities are handled with utmost confidentiality and by no means get into the hands of potential cyber attackers and affiliated communities wherever they are located.”
Other companies on the list said that they do report vulnerability information to the Chinese government, but only the same information provided to other governments and to customers. Swedish industrial automation firm KUKA responded that it “fulfills legal local obligations in all countries, where we operate,” but wrote that it offers the same information to its customers, publishes known vulnerability information about its products on a public website, and will comply with a similar upcoming law in the EU that requires disclosing vulnerability information. Japanese technology company Omron similarly wrote that it gives vulnerability information to the Chinese government, CISA in the US, and the Japanese Computer Emergency Response Team, as well as publishing information about known vulnerabilities on its website.
German industrial automation firm Beckhoff spelled out a similar approach in more detail. “Legislation in several nations requires that any vendor selling products in their market must inform their authorized body about security vulnerabilities prior to their publication,” wrote Torsten Förder, the company’s head of product security. “General information about the vulnerability is disclosed as further research and mitigation strategies are developing. This enables us to notify all regulatory bodies quickly, while refraining from publishing comprehensive information on how to exploit the vulnerability under investigation.”
French electric utility technology firm Schneider Electric offered the most ambiguous response. The company’s head of product vulnerability management, Harish Shankar, wrote only that “cybersecurity is integral to Schneider Electric’s global business strategy and digital transformation journey” and referred WIRED to its Trust Charter as well as the cybersecurity support portal on its website, where it releases security notifications and mitigation and remediation tips.
Given those carefully worded and sometimes elliptical responses, it’s difficult to know to exactly what degree companies are complying with China’s vulnerability disclosure law—particularly given the relatively detailed description required on the government’s web portal for uploading vulnerability information. Ian Roos, a China-focused researcher at cybersecurity R&D firm Margin Research who reviewed the Atlantic Council report prior to publication, suggests that companies might be engaging in a kind of “malicious compliance,” sharing only partial or misleading information with Chinese authorities. And he notes that even if they are sharing solid vulnerability data, it may still not be specific enough to be immediately helpful to China’s state-sponsored hackers. “It’s very hard to go from ‘there's a bug here’ to actually leveraging and exploiting it, or even knowing if it can be leveraged in a way that would be useful,” Roos says.
The law is still troubling, Roos adds, since the Chinese government has the ability to impose serious consequences on companies that don’t share as much information as it would like, from hefty fines to revocation of business licenses necessary to operate in the country. “I don’t think it’s doomsday, but it’s very bad,” he says. “I think it absolutely does create a perverse incentive where now you have private organizations that need to basically expose themselves and their customers to the adversary.”
In fact, China-based staff of foreign companies may be complying with the vulnerability disclosure law more than executives outside of China even realize, says J. D. Work, a former US intelligence official who is now a professor at National Defense University College of Information and Cyberspace. (Work holds a position at the Atlantic Council, too, but wasn’t involved in Cary and Del Rosso’s research.) That disconnect isn’t just due to negligence or willful ignorance, Work adds. China-based staff might broadly interpret another law China passed last year focused on countering espionage as forbidding China-based executives of foreign firms from telling others at their own company about how they interact with the government, he says. “Firms may not fully understand changes in their own local offices’ behavior,” says Work, “because those local offices may not be permitted to talk to them about it, under pain of espionage charges.”
Sophos’ Del Rosso notes that even if companies operating in China are finding the wiggle room to avoid disclosing actual, hackable vulnerabilities in their products today, that’s still no guarantee that China won’t begin tightening its enforcement of the disclosure law in the future to close any loopholes.
“Even if people aren't complying—or if they are complying but only to a certain extent—it can only devolve and get worse,” says Del Rosso. “There’s no way they’re going to start asking for less information, or requiring less of people working there. They’ll never get softer. They’ll crack down more.”
2 notes
·
View notes
Text
This is the worst article I may have ever read. It lies right from the get go. First of all, of course, it's not easier to use, definitely not for me. But I'll get to that point.
"The website looks a bit different — it’s simpler; less cluttered; and, hopefully, easier to use." Yes, because it's "less cluttered" it's harder to use. It's harder to find something that was right there from the get go, in the open! Ctrl+F exists for a reason and now it's been rendered useless. I have no idea why on desktop, where You have all the space in the world, You would hide language changing and other useful links. I get doing it on a phone screen, it's tiny and hard to use, but a desktop screen is exactly the opposite. On desktop You can open multiple links at the same time, You can find links easily and there's enough space to show them. Hiding items just makes me click more and ergo lose more time!
"After three years of development" lol just lol
"The new design is the culmination of years of research, dozens of consultations with movement groups and volunteers, and thousands of points of feedback from Wikipedia readers." Who? Your mothers?
"The updated interface improves readability by reducing distraction and clutter and making pages easier to read" Oh, so people with bad ADHD, I guess. I don't see how a person with a normally functioning brain would have problems with a single sidebar.
"It introduces changes to the navigation and layout of the site, adds persistent elements such as a sticky header" Claim to make the site more user friendly, yet add a sticky element. HILARIOUS. Sticky elements are a million times more distracting than a normal sidebar xD Not to mention they're ugly and annoying all hell. But yes, it's more comfortable to use, ofc
"Our data shows that these changes improve usability, and save time currently spent in scrolling, searching, and navigating – all of which adds up to an easier and more modern reading experience, so that more people will love reading and contributing to Wikipedia." I HAVE made an account on wikipedia after the change indeed. To change the layout back to the good one. Using the new wikipedia every time i use someone else's computer or open it in incognito feels like being skinned. Slow, terrifying and painful.
"In the future, we plan on continuing to listen to our audiences and adapt and improve our experiences based on their needs" youtube talk. Translation: "we plan on making the site more hard to use because we love mocking our userbase"
Anyway modern UX drives me off the internet so I guess it's a good thing after all
#wikipedia#ux design#writing this here only because there's no feedback possible on that dumbass site#not even an email!
3 notes
·
View notes
Text
Bank Achieves Operational Excellence in Outward Remittance with DataNimbus.io

In the context of RBI’s regulations for foreign remittances, banks in India face a multifaceted challenge. They must implement rigorous processes for verifying the legitimacy of outward remittance transactions, ensuring compliance with Anti-Money Laundering (AML) and Know Your Customer (KYC) guidelines. Simultaneously, banks need to provide efficient and user-friendly experiences for customers who wish to transfer funds overseas. Striking a balance between regulatory compliance, customer satisfaction, and operational efficiency is crucial for banks to succeed in this space.
Our client in this case was one of the largest private banks in India. While the client strives to meet these demands, legacy systems and manual processes can create bottlenecks. Strict compliance checks can lead to delays in processing remittance requests. Additionally, integrating various data sources, external APIs for verification and maintaining separate systems for regulatory reporting can increase operational costs and create a complex user experience for both customers and bank staff.
The Challenge
The client faced several challenges in foreign remittance operations. Their reliance on legacy systems and manual processes resulted in lengthy processing times for remittance requests, causing delays and customer frustration. This put them at a competitive disadvantage. Additionally, the need to integrate data from various sources for KYC and AML checks was inefficient and prone to errors. Maintaining separate systems for regulatory reporting added to their operational complexity and cost. With India’s regulatory environment continuously evolving, these challenges threatened the client’s compliance and long-term success in outward remittance services.
The Solution
DataNimbus.io Solution: Modernizing Outward Remittance
DataNimbus.io(DNIO) platform enabled the bank to transform its outward remittance processes, significantly improving efficiency and regulatory compliance:
Compliance by Design: DataNimbus.io’s data services and pre-hooks ensured that customer information and transaction requests adhered to RBI’s LRS guidelines and AML/KYC requirements from the point of submission. This reduced the burden of manual verification and streamlined the approval process.
Automated Workflows: DataNimbus.io’s workflows automated multi-step remittance processes, ensuring that transactions followed the correct sequences, approvals were obtained, and delays were minimized.
Integrated Compliance Checks: Data pipes enabled seamless integration with the bank’s existing AML and KYC systems. This allowed for real-time verification of customer data and transaction legitimacy, further strengthening compliance.
Simplified Reporting: DataNimbus.io’s ability to consolidate data and handle custom transformations made regulatory reporting simpler and more accurate. The bank could easily generate reports aligned with RBI requirements.
Enhanced Customer Experience: The streamlined backend processes, powered by datanimbus.io, translated into faster turnaround times and improved communication for customers initiating outward remittances.
Implementation Process
The bank adopted a phased approach to implement the solution using DataNimbus.io, ensuring a smooth transition:
Assessment: A thorough analysis of existing remittance processes, data flows, and pain points, identifying critical areas for integration and compliance.
Data Modeling: Design data services within datanimbus.io to model customer profiles, remittance requests, KYC and AML data, aligning with RBI requirements.
Workflow Design: Create workflows to map out the remittance process, incorporating approval steps, AML/KYC checks, and notifications.
Integration: Configure data pipes to connect datanimbus.io with the bank’s core systems and external AML/KYC platforms, ensuring seamless data exchange.
Pre/Post Hooks: Implement validation logic within pre-hooks and configure post-hooks for notifications and downstream system updates.
Pilot & Rollout: Test the solution in a pilot environment, refine processes, then gradually scale across online channels.
Training & Monitoring: Provide staff training on the new system, and leverage datanimbus.io’s monitoring tools to track performance and compliance.
Results and Outcomes: A Transformed Remittance Experience
The bank experienced significant improvements in its foreign remittance operations after implementing the DataNimbus.io (DNIO) solution:
Operational Efficiency: Automation, data centralization, and streamlined workflows significantly reduced manual interventions, leading to faster processing times and a decrease in operational costs.
Robust Compliance: DataNimbus.io compliance checks and integrated AML/KYC systems ensured adherence to RBI mandates, minimizing risk and potential penalties.
Enhanced Customer Experience: Customers benefited from faster turnaround times, improved transparency, and a more intuitive user interface, boosting satisfaction and loyalty.
Data-Driven Insights: DataNimbus.io’s reporting capabilities provided the bank with valuable data on remittance patterns, customer segments, and operational metrics, facilitating better decision-making.
Competitive Edge: The modernized remittance process enabled the bank to differentiate itself in the market by offering a reliable, efficient, and user-friendly experience.
Conclusion
By partnering with Datanimbus , the bank successfully modernized its foreign remittance operations. DataNimbus.io (DNIO) platform provided the tools to streamline processes, automate compliance checks, and centralize data management. This transformation not only addressed regulatory requirements but also significantly improved operational efficiency and customer experience.
The successful implementation demonstrates how DNIO can empower banks to navigate complex regulatory landscapes while delivering superior financial services.
Key Outcomes
Reduced operational costs: Streamlining manual compliance and data integration processes decreased overhead.
Enhanced compliance: Automated AML/KYC checks and built-in validation minimized risk.
Improved customer experience: Faster processing times and clearer communication boosted satisfaction.
Data-driven insights: Centralized reporting empowered the bank with better analytics and decision-making.
0 notes
Text
How to Integrate a Running Chip Timing System Into Your Race Day Operations

A smooth race day starts with good planning — and accurate timing is one of the most essential elements. Whether you’re organizing a small local 5K or a large-scale marathon, a running chip timing system can make a difference. It ensures fair results, minimizes manual errors, and enhances the overall experience for runners.
Here’s a step-by-step guide to help you successfully integrate a chip timing system into your event.
Understand What a Running Chip Timing System Does
Before you begin, it’s essential to understand what a Running Chip Timing System does. This system uses small chips — often attached to bibs, shoes, or ankle bands — that signal when a runner crosses timing mats at various checkpoints, start and finish lines.
These signals are captured in real time and translated into accurate start, split, and finish times. The data can display live results, track progress, and generate final rankings.
Choose the Right Timing Partner
You’ll likely work with a timing vendor unless you invest in your equipment. Choosing the right partner is key. Look for a provider with experience in similar race types and sizes. Ask about their equipment, support services, and whether they provide live result options.
Request references or case studies from previous events to ensure they can meet your needs. A reliable timing company will guide you on best practices and take charge of the technical setup.
Plan Your Timing Points
Next, decide where to place timing points. At a minimum, you’ll need mats at the start and finish lines. Depending on the course length and design, you may also want to add split points (e.g., at halfway marks or major turns) to monitor performance and prevent course cutting.
Coordinate with your timing partner to determine the number of mats needed and how they’ll be powered — some require generators or battery backups.
Coordinate Bib and Chip Distribution
Chips are usually attached to race bibs or handed out separately. Either way, they must be distributed accurately. Double-check that each chip is registered to the correct runner. Mismatches can cause significant issues during result generation.
The process is simpler if you’re using disposable chips (common in modern systems). Reusable chips, on the other hand, require collection after the race. Plan volunteers and logistics accordingly.
Train Your Volunteers
Volunteers play a significant role in race day success. Make sure your team understands how the running chip timing system works. Assign volunteers to manage key timing points, monitor mats, and assist runners with chip placement questions.
Have backup communication if something goes wrong, such as a chip not registering or a runner forgetting to wear one.
Test Before the Event
Never assume everything will go perfectly on race day. A day or two before the event, test all equipment on-site. Check that mats detect chips properly, record results, and connect all systems.
This is also a good time to simulate different runner scenarios, such as late arrivals, missed chips, or unusual foot traffic. Preparing for these helps you respond quickly if issues arise during the race.
Monitor During the Race
On race day, your timing team should constantly monitor the system. Someone should keep an eye on the live data feed to ensure all runners are being tracked. Any anomalies — such as missed checkpoints or duplicate reads — should be flagged and investigated immediately.
Ensure clear communication between the event director, timing crew, and volunteers at each mat.
Post-Race Results and Reporting
Your job isn’t done once the last runner crosses the finish line. Promptly publish results online or on a live display. Many runners will want to see their finish times immediately.
A sound-running chip timing system will also allow you to export data for race reports, age group results, and certificates. Make this part of your post-race process so everything is consistent and professional.
Source Link: https://bit.ly/44gOE1W
0 notes
Text
Where Can I Repair My Phone in Pomona, CA?
Whether you're dealing with a cracked screen, faulty battery, or water damage, knowing where to repair your phone in Pomona, CA, can save you time, money, and stress. The city offers a rich mix of repair options: from large electronics retailers and carrier-affiliated service centers to independent repair shops and mobile repair services. These providers offer fast diagnostics, professional-level repairs, and dependable warranties. Many boast skilled technicians who can fix everything from screen replacements and battery swaps to motherboard-level hardware repairs. Pomona’s repair landscape combines convenience with quality—shops are strategically located near colleges, downtown, and major shopping districts. Plus, with mobile technicians who can come to your home or workplace, repairing your phone has never been easier. This guide explores the best places to repair your phone in Pomona, highlighting their strengths and helping you choose the right path for a swift, reliable fix.
Major Electronics Retailers Providing Phone Repair in Pomona
Major electronics retailers in Pomona such as Best Buy with their Geek Squad and Fry’s Electronics provide certified phone repair services, commonly offering same-day fixes for cracked screens, battery issues, and software problems. These stores often use OEM or high-grade aftermarket parts protected under a warranty. They also offer extras like data transfer, diagnostic checks, and accessory replacements, all backed by strong return and service guarantees. Visiting these retailers ensures you get professional-grade service with transparent pricing and quick turnaround times.
Carrier and Brand-Specific Authorized Repair Centers
Authorized repair centers associated with phone manufacturers such as Apple, Samsung, Google, and carriers like Verizon and AT&T provide high-quality service for their respective phone models. These facilities use genuine parts, follow strict repair protocols, and often provide service plans that come with premiums like priority scheduling and mail-in repair options. Authorized centers are the safest route for preserving your warranty and ensuring long-term device health, especially for newer flagship models.
Independent Local Repair Shops in Pomona
Pomona is home to several independent repair shops that offer competitive pricing, personalized service, and flexible repair options. These establishments can fix a full range of phone issues—screens, batteries, camera modules, speakers, and more. Many pride themselves on same-day or next-day service turnaround and use high-quality aftermarket components with varying warranties. Their local focus often translates into attentive customer service, diagnostic transparency, and the option to consult with technicians directly.
Mobile Phone Repair Services You Can Call
Mobile repair services in Pomona bring the repair shop to you. Perfect for busy individuals, these services send certified technicians to your home, office, or anywhere in between, offering on-site screen repairs, battery replacements, and software troubleshooting. This convenience saves time and reassurance—many mobile services provide short time windows (often within a few hours) and real-time updates via text. Typically, they use high-quality aftermarket parts and offer limited warranties, making them a great on-demand solution for minor to moderate phone damage.
DIY Repair Kits Available Locally
For tech-savvy individuals, some Pomona stores and online suppliers offer DIY repair kits for those willing to tackle simpler fixes. Kits include precision tools, adhesive, and tutorials for projects like screen or battery replacements. This approach can save money but requires confidence and care to avoid further damage. DIY kits are a good fit for users with technical skills, especially for older models or when budget constraints make professional repairs less attractive.
Evaluating Price and Turnaround Time
Price and speed are critical factors when choosing a phone repair service. Pomona’s major retailers generally charge standard industry rates and offer the fastest repair times—usually the same day. Carrier-authorized centers might cost more but include premium parts and standardized service. Independent shops often balance affordability and turnaround, sometimes offering faster or cheaper repairs than chains. Mobile services may charge travel fees but often deliver quick, convenient service. Comparing quotes and timelines across options helps you find the best fit for your needs.
The Importance of Quality Parts and Warranty Coverage
One way to ensure a satisfactory repair is to choose providers who offer strong warranties and use quality parts. Chains like Best Buy and authorized centers typically offer 90-day to one-year warranties on parts and labor. Independent shops and mobile technicians also provide warranties—monitor their length and coverage fine print (e.g., on parts and labor). Whether you choose OEM or aftermarket, ask about coverage, return policy, and guarantees for peace of mind.
Safeguarding Your Data During Repairs
A vital part of repairing your phone is protecting your data. Most Pomona repair shops advise backing up your phone before service. Some shops also offer on-site backup or data migration services. Whether it’s photos, contacts, apps, or messages, creating a backup ensures your information is safe, even if a repair involves factory resets or motherboard replacements. Additionally, reputable repair centers protect your device password or fingerprint data during service.
What to Do When Damage Goes Beyond the Screen
Not all phone damage is surface-level. Internal issues, like water exposure, motherboard damage, or power failures, demand more extensive diagnostics and repair efforts. Pomona repair services with advanced tools, such as ultrasonic cleaning machines for water damage or micro-soldering equipment for component-level issues, can restore your device. Look for shops that list these services and have skilled technicians trained to perform detailed inspections and repairs.
Why Local Shopping Matters: Shop Devices in Pomona, CA
Choosing a local repair shop in Pomona offers more than just a quick fix. It strengthens local business and gives you access to personalized service, follow-up care, and tech support from people who care about your device’s performance. Plus, local repair shops often give advice on device maintenance and upgrades. When you Shop Devices in Pomona, CA, you’re investing in quality repair and supporting the local tech community.
Techy Pomona is your go-to destination for the latest in electronic devices, offering an unmatched selection of smartphones, computers, MacBooks, iPads, tablets, and laptops. As a hub for technology enthusiasts and casual users alike, our store provides a unique shopping experience that is both enjoyable and educational. Our knowledgeable staff are on hand to guide you through our extensive product range, ensuring you find the perfect device that suits your lifestyle and budget.
#PhoneRepairPomona#TechRepairPomona#PomonaElectronics#PomonaPhoneFix#SmartphoneRepairCA#DeviceRepairPomona#PomonaGadgetStore#FixMyPhonePomona#MobileRepairPomona#ShopDevicesPomona
1 note
·
View note