#AI-driven threat detection
Explore tagged Tumblr posts
Text
AI in Cybersecurity – How AI is Transforming IT Security in 2025

Introduction
Cybersecurity threats are evolving at an unprecedented rate, putting businesses and individuals at risk of data breaches, ransomware attacks, and phishing scams. In response, Artificial Intelligence (AI) is revolutionizing IT security by providing advanced threat detection, real-time monitoring, and automated response mechanisms. AI-powered cybersecurity is no longer a futuristic concept—it’s a necessity in today’s digital landscape.
How AI is Transforming Cybersecurity
1. AI for Threat Detection and Prevention
Traditional security systems rely on rule-based algorithms, which often fail against sophisticated cyberattacks. AI-powered cybersecurity solutions use machine learning (ML) to analyze patterns and detect anomalies, identifying threats before they cause damage.
AI detects phishing attempts by analyzing email content and sender behavior.
Machine learning models predict cyberattacks based on historical data.
AI-driven endpoint security ensures real-time protection for devices.
2. Automated Incident Response
AI accelerates threat mitigation by automatically responding to cyber incidents. Instead of waiting for manual intervention, AI-driven security systems isolate infected devices, block malicious IP addresses, and neutralize threats in real-time.
AI-powered firewalls and intrusion detection systems (IDS) improve network security.
Automated security operations centers (SOCs) enhance rapid threat resolution.
3. Behavioral Analytics for Cybersecurity
AI analyzes user behavior to detect unusual activities. If an employee's login pattern suddenly changes or unauthorized data access occurs, AI flags it as a potential threat.
AI-driven identity and access management (IAM) prevents unauthorized logins.
Behavioral biometrics enhance authentication security.
4. AI in Cloud Security
As cloud computing adoption grows, cyber threats targeting cloud environments also rise. AI enhances cloud security by:
Identifying misconfigurations that could expose data.
Monitoring cloud access patterns for suspicious activities.
Detecting malware in cloud storage services.
Challenges of AI in Cybersecurity
Despite its advantages, AI-powered cybersecurity faces challenges, including:
False Positives & Negatives: AI must continuously learn to minimize detection errors.
High Implementation Costs: AI-driven security solutions require significant investment.
Data Privacy Concerns: AI models rely on vast amounts of data, raising privacy issues.
Future Trends of AI in Cybersecurity
The future of AI in cybersecurity is promising, with advancements shaping IT security strategies. Some key trends include:
AI-Powered Zero Trust Security Models: Verifying every request before granting access.
Deep Learning for Threat Hunting: Identifying complex cyberattack patterns.
Quantum Computing’s Role in AI Cybersecurity: Strengthening encryption algorithms.
AI-Augmented Penetration Testing: AI-driven ethical hacking to identify vulnerabilities.
Conclusion
AI is transforming cybersecurity by making IT security smarter, faster, and more proactive. As cyber threats become more sophisticated, businesses must integrate AI-driven security measures to protect sensitive data and digital assets. Investing in AI-powered cybersecurity today ensures a safer digital future for organizations worldwide.
Follow For More Insights: Reflextick Creative Agency
#AI in cybersecurity#cybersecurity trends 2025#AI-powered IT security#artificial intelligence in security#AI-driven threat detection#cybersecurity automation#AI in cloud security#machine learning for cybersecurity#future of AI in cybersecurity.
0 notes
Text
Enhancing IT Security with Vector’s Threat Detection
In an era where cyber threats are more sophisticated than ever, the need for early threat detection for businesses has become more important. Cyberattacks are no longer a matter of "if" but "when." To combat these evolving threats, organizations must employ advanced security measures that ensure real-time protection. Vector offers a comprehensive suite of security tools designed to enhance cybersecurity, including advanced threat detection and proactive response mechanisms. With its cutting-edge AI-driven capabilities, Vector delivers unmatched security solutions that identify and mitigate risks before they escalate.
AI-Driven Threat Detection: The Future of IT Security
The cornerstone of Vector’s security is its AI-driven threat detection capabilities. By leveraging artificial intelligence (AI) and behavioral analytics, Vector can predict and detect anomalies across systems, identifying potential threats before they cause damage. Unlike traditional security methods, threat detection is not reactive but predictive, offering real-time analysis of activities and deviations from normal behavior patterns.
This proactive approach helps companies minimize the mean time to detect (MTTD) threats, enabling them to respond faster and more efficiently. With Vector, organizations can maximize true positives while reducing false positives, ensuring that security teams can focus on genuine risks rather than wasting time on irrelevant alerts.
Advanced Threat Detection and Response
Vector’s Security and Compliance Monitoring (SCM) module goes beyond basic detection with its advanced threat detection and response capabilities. Through User and Entity Behavior Analytics (UEBA), the system tracks the behavior of users and entities within the network, learning from past activities to identify suspicious behavior that may signal a breach. By continuously analyzing patterns and data, the system offers a dynamic and adaptable defense strategy against evolving cyber threats.
Security Orchestration, Automation, and Response (SOAR) further enhances Vector’s capabilities by automating the response process. This automation reduces the mean time to respond (MTTR) by offering guided response recommendations, ensuring swift action when a threat is identified. Automated playbooks allow for a quick and effective resolution to incidents, minimizing damage and disruption to business operations.
Ensuring Compliance and Secure Operations
In addition to threat detection, Vector also emphasizes compliance monitoring and reporting. Companies must maintain compliance with security standards such as ISO 27001 and SOC 2, and Vector ensures that these standards are met by continuously monitoring for any deviations. This proactive approach not only keeps businesses compliant but also identifies areas for improvement, ensuring that security operations are always aligned with best practices.
Vector's SCM module helps manage these compliance requirements by providing automated reports and alerts when potential compliance risks arise. By integrating compliance and security management, organizations can streamline their auditing processes and minimize the risk of penalties due to non-compliance.
Robust Data Protection
With data protection becoming a top priority, Vector provides multiple layers of security to safeguard sensitive information. Data encryption, both at rest and in transit, ensures that confidential information is protected from unauthorized access. Furthermore, access controls, including Role-based Access Control (RBAC) and Multi-factor Authentication (MFA), restrict who can access data, ensuring only authorized personnel have the necessary permissions.
To comply with privacy regulations like GDPR and CCPA, Vector incorporates advanced techniques such as data anonymization and pseudonymization, adding another layer of protection. This comprehensive data security strategy ensures that businesses can maintain confidentiality while adhering to global privacy standards.
Enhancing Network Security
Vector also excels in network security, utilizing robust firewall protocols, intrusion detection systems, and secure transmission methods to protect the network from unauthorized access and attacks. Regular vulnerability assessments ensure that potential weaknesses are identified and rectified before they can be exploited.
With continuous 24/7 monitoring and automated alerts, Vector ensures that organizations can quickly detect and respond to security incidents. Integration with Security Information and Event Management (SIEM) tools enhances its ability to manage incidents and investigate threats, keeping networks safe from malicious activity.
Conclusion
In an era where cyberattacks are a constant threat, leveraging advanced technologies like AI-driven threat detection is essential for safeguarding critical systems and data. Vector, with its SCM module, delivers an all-encompassing security solution that includes advanced threat detection, compliance monitoring, and automated incident response. By integrating AI and behavioral analytics, Vector empowers businesses to stay ahead of threats and maintain a secure digital environment.
From network security to data protection and compliance, Vector’s robust security architecture ensures that organizations are not only protected but also prepared to face the ever-evolving cyber landscape.
Click here to learn more about Vector’s AI-driven threat detection and how it can protect your business from potential threats.
0 notes
Text
Cybersecurity in the Age of AI: Navigating New Threats

Understanding AI-Driven Cyber Threats and Defense Strategies
Introduction: A New Cybersecurity Landscape in the Age of AI
Artificial Intelligence (AI) has revolutionized industries worldwide by enhancing efficiency, accuracy, and innovation. From automating routine tasks to enabling predictive analytics, AI continues to unlock unprecedented opportunities. However, as AI becomes deeply embedded in our digital ecosystems, it also reshapes the cybersecurity landscape bringing both powerful defenses and novel risks.
The rise of AI-driven cybersecurity tools is transforming how organizations detect, respond to, and prevent cyber threats. Machine learning algorithms can analyze massive datasets to identify unusual patterns, predict attacks, and automate defenses in real time. Yet, the same AI advancements also equip cybercriminals with sophisticated capabilities enabling automated phishing, intelligent malware, and adaptive intrusion techniques that are harder to detect and mitigate.
This dual-edged nature of AI demands a new approach to cyber threat intelligence, risk management, and security strategy. Organizations must stay vigilant and adopt innovative solutions to safeguard sensitive data and infrastructure against increasingly complex and automated cyberattacks.
For a deeper understanding of how AI is reshaping cybersecurity, check out NIST’s AI and Cybersecurity Framework.
How AI Is Changing Cybersecurity: Defense and Threat Evolution
Artificial Intelligence is revolutionizing cybersecurity by playing a dual role empowering defenders while enabling more sophisticated cyberattacks. On the defense front, AI-powered cybersecurity systems leverage machine learning and data analytics to process enormous volumes of network traffic, user activity, and threat intelligence in real time. These systems excel at detecting anomalies and predicting potential threats far faster and more accurately than traditional signature-based methods.
For example, AI-driven tools can identify subtle patterns indicative of phishing attacks, ransomware activity, or unusual network intrusions, often flagging risks before they escalate into full-blown breaches. Automated incident response capabilities enable rapid containment, minimizing damage and reducing reliance on manual intervention.
However, cybercriminals are equally quick to adopt AI technologies to enhance their offensive tactics. By using AI-generated content, hackers craft convincing phishing emails and social engineering schemes that trick users more effectively. AI can also be used to bypass biometric systems, automate vulnerability scanning, and mimic legitimate user behaviors to avoid detection by conventional security measures. This escalating “arms race” between attackers and defenders underscores the critical need for adaptive cybersecurity strategies.
To explore the evolving interplay between AI and cyber threats, consider reviewing insights from the Cybersecurity & Infrastructure Security Agency (CISA).
Emerging AI-Powered Threats: Deepfakes, Adaptive Malware, and Automated Attacks
The cybersecurity landscape faces increasingly sophisticated challenges due to the rise of AI-powered threats. Among the most alarming is the use of deepfakes hyper-realistic synthetic media generated by AI algorithms that can convincingly impersonate individuals. These deepfakes are weaponized for identity theft, social engineering schemes, or disinformation campaigns designed to manipulate public opinion or corporate decision-making. The growing prevalence of deepfakes adds a dangerous new dimension to phishing and fraud attempts.
In addition, AI-driven adaptive malware is evolving rapidly. Unlike traditional viruses, this malware can modify its code and behavior dynamically to evade signature-based antivirus software and intrusion detection systems. This makes infections more persistent and difficult to eradicate, posing a serious risk to personal, corporate, and government networks.
Furthermore, automated hacking tools powered by AI significantly accelerate cyberattacks. These intelligent systems can autonomously scan vast networks for vulnerabilities, execute targeted breaches, and learn from unsuccessful attempts to improve their strategies in real time. This capability enables hackers to conduct highly efficient, large-scale attacks that can quickly overwhelm human cybersecurity teams.
For more insights into the risks posed by AI-powered cyber threats and how to prepare, visit the National Institute of Standards and Technology (NIST).
Strengthening Cyber Defenses with AI: The Future of Cybersecurity
Despite the growing threat landscape driven by AI-powered attacks, artificial intelligence remains a crucial asset for cybersecurity defense. Cutting-edge security systems leverage AI technologies such as real-time threat intelligence, automated incident response, and predictive analytics to detect and neutralize cyber threats faster than ever before. By continuously analyzing vast amounts of data and learning from emerging attack patterns, AI enables organizations to anticipate and prevent breaches before they occur.
One of the most effective approaches is the integration of AI with human expertise, forming a hybrid defense model. In this setup, cybersecurity analysts harness AI-generated insights to make critical decisions, prioritize threats, and customize response strategies. This synergy balances the rapid detection capabilities of AI with the nuanced judgment of human operators, resulting in more accurate and adaptive cybersecurity posture.
Organizations that adopt AI-driven security platforms can significantly reduce response times, improve threat detection accuracy, and enhance overall resilience against sophisticated attacks.
For organizations seeking to implement AI-based cybersecurity solutions, resources like the Cybersecurity and Infrastructure Security Agency (CISA) offer valuable guidance and best practices.
Ethical and Privacy Considerations in AI-Driven Cybersecurity
As organizations increasingly integrate artificial intelligence in cybersecurity, important ethical and privacy concerns arise. The process of collecting and analyzing vast datasets to identify cyber threats must be carefully balanced with safeguarding user privacy rights and sensitive information. Maintaining transparency in AI decision-making processes is crucial to build trust and accountability. Clear regulatory frameworks, such as the General Data Protection Regulation (GDPR), provide guidelines that help organizations use AI responsibly while respecting individual privacy.
Additionally, organizations face risks associated with over-automation in cybersecurity. Relying solely on AI systems without sufficient human oversight can result in missed threats, false positives, or biased decision-making. These errors may lead to security vulnerabilities or negatively impact the user experience. Therefore, a balanced approach combining AI’s speed and scale with human judgment is essential for ethical, effective cybersecurity management.
By prioritizing ethical AI use and privacy protection, businesses can foster safer digital environments while complying with legal standards and maintaining customer confidence.
Preparing for the Future of AI and Cybersecurity
As artificial intelligence continues to transform the cybersecurity landscape, organizations must proactively prepare for emerging challenges and opportunities. Investing in continuous learning and regular employee cybersecurity training ensures teams stay equipped to handle evolving AI-powered threats. Developing flexible security architectures that seamlessly integrate AI-driven tools enables faster threat detection and response, improving overall resilience.
Collaboration across industries, governments, and academic researchers is critical for creating shared cybersecurity standards, real-time threat intelligence sharing, and innovative defense strategies. Initiatives like the Cybersecurity and Infrastructure Security Agency (CISA) promote such partnerships and provide valuable resources.
For individuals, maintaining strong cybersecurity hygiene using strong passwords, enabling multi-factor authentication (MFA), and practicing safe online behavior is more important than ever as attackers leverage AI to launch more sophisticated attacks.
By combining organizational preparedness with individual vigilance, we can build a safer digital future in an AI-driven world.
Conclusion: Embracing AI to Navigate the New Cybersecurity Threat Landscape
Artificial Intelligence is fundamentally reshaping the cybersecurity landscape, introducing both unprecedented opportunities and significant risks. While cybercriminals increasingly use AI-driven techniques to execute sophisticated and automated attacks, cybersecurity professionals can harness AI-powered tools to create smarter, faster, and more adaptive defense systems.
The key to success lies in adopting AI thoughtfully blending human expertise with intelligent automation, and maintaining continuous vigilance against emerging threats. Organizations that invest in AI-based threat detection, real-time incident response, and ongoing employee training will be better positioned to mitigate risks and protect sensitive data.
By staying informed about evolving AI-driven cyber threats and implementing proactive cybersecurity measures, businesses and individuals alike can confidently navigate this dynamic digital frontier.
For further insights on how AI is transforming cybersecurity, explore resources from the National Institute of Standards and Technology (NIST).
FAQs
How is AI changing the cybersecurity landscape? AI is transforming cybersecurity by enabling faster threat detection, real-time response, and predictive analytics. Traditional systems rely on static rules, but AI adapts to evolving threats using machine learning. It can scan vast datasets to identify anomalies, spot patterns, and neutralize potential attacks before they spread. However, AI is also used by hackers to automate attacks, create smarter malware, and evade detection. This dual-use nature makes cybersecurity both more effective and more complex in the AI era, demanding constant innovation from defenders and responsible governance around AI deployment.
What are the biggest AI-powered cybersecurity threats today? AI can be weaponized to launch sophisticated cyberattacks like automated phishing, deepfake impersonations, and AI-driven malware that adapts in real time. Hackers use AI to scan networks for vulnerabilities faster than humans can react. They also employ natural language models to craft realistic phishing emails that bypass traditional filters. Deepfakes and synthetic identities can fool biometric security systems. These AI-enhanced threats evolve quickly and require equally intelligent defense systems. The speed, scale, and realism enabled by AI make it one of the most significant cybersecurity challenges of this decade.
How does AI improve threat detection and response? AI boosts cybersecurity by analyzing massive volumes of network traffic, user behavior, and system logs to detect anomalies and threats in real time. It identifies unusual patterns like logins from strange locations or data spikes and flags them before they escalate into breaches. AI can also automate responses, isolating infected devices, updating firewalls, or sending alerts instantly. This proactive approach dramatically reduces reaction times and false positives. In large enterprises or cloud environments, where manual monitoring is nearly impossible, AI acts as a 24/7 digital watchdog.
Can AI prevent phishing and social engineering attacks? Yes, AI can help identify phishing attempts by scanning emails for suspicious language, links, or metadata. Natural language processing (NLP) models are trained to detect tone, urgency cues, or fake URLs often used in phishing. AI can also assess sender reputations and flag unusual communication patterns. While it can’t fully prevent human error, it significantly reduces exposure by quarantining suspicious emails and alerting users to risks. As phishing tactics evolve, so does AI constantly learning from past attacks to improve prevention accuracy.
Are AI-based cybersecurity tools available for small businesses? Absolutely. Many affordable, AI-powered security tools are now available for small and mid-sized businesses. These include smart antivirus software, behavior-based threat detection, AI-driven email filters, and endpoint protection platforms that learn from each user’s habits. Cloud-based solutions like Microsoft Defender, SentinelOne, and Sophos offer AI-powered features tailored for SMBs. They provide enterprise-grade security without the need for in-house security teams. With cyberattacks increasingly targeting smaller firms, AI-based solutions are not just accessible they’re essential for staying protected with limited resources.
Can AI replace cybersecurity professionals? AI enhances cybersecurity but won’t replace human experts. While it automates routine tasks like threat detection, data analysis, and basic response, human oversight is still crucial for judgment, strategy, and interpreting complex risks. Cybersecurity professionals work alongside AI to investigate incidents, fine-tune models, and ensure compliance. In fact, AI allows professionals to focus on high-level security architecture, incident response, and governance rather than tedious monitoring. The future lies in a human-AI partnership where AI handles scale and speed, and humans manage context and ethical oversight.
What are some ethical concerns with using AI in cybersecurity? Ethical concerns include data privacy, surveillance overreach, and algorithmic bias. AI systems require vast amounts of data, which can lead to privacy violations if not managed properly. There’s also the risk of false positives that could unjustly flag innocent users or systems. If left unchecked, AI could reinforce existing biases in threat detection or lead to disproportionate responses. Moreover, governments and companies may use AI tools for excessive surveillance. Responsible AI in cybersecurity means transparency, data governance, user consent, and fairness in decision-making.
How do hackers use AI to their advantage? Hackers use AI to create more sophisticated and scalable attacks. For instance, AI-powered bots can probe systems for weaknesses, bypass CAPTCHAs, and execute brute-force attacks faster than humans. NLP models are used to generate realistic phishing emails or impersonate voices using deepfakes. Machine learning helps malware adapt its behavior to avoid detection. These tools allow cybercriminals to attack with greater precision, volume, and deception making AI both a powerful ally and a formidable threat in the cybersecurity battlefield.
What is AI-driven threat hunting? AI-driven threat hunting involves proactively seeking out hidden cyber threats using machine learning and behavioral analytics. Instead of waiting for alerts, AI scans systems and networks for subtle anomalies that indicate intrusion attempts, dormant malware, or lateral movement. It uses predictive modeling to anticipate attack paths and simulate threat scenarios. This proactive approach reduces the risk of long-term undetected breaches. By continuously learning from new threats, AI enables security teams to shift from reactive defense to predictive offense, identifying threats before they do damage.
How can organizations prepare for AI-powered cyber threats? Organizations should invest in AI-powered defenses, regularly update their threat models, and train employees on AI-enhanced risks like deepfakes or phishing. Cybersecurity teams need to adopt adaptive, layered security strategies that include AI-based detection, behavioral monitoring, and automated response. It's also crucial to perform AI-specific risk assessments and stay informed about new threat vectors. Partnering with vendors that use explainable AI (XAI) helps ensure transparency. Finally, fostering a cyber-aware culture across the organization is key because even the smartest AI can’t protect against careless human behavior.
#AI cybersecurity threats#artificial intelligence in security#AI-driven cyber attacks#cybersecurity in AI age#AI-powered threat detection#digital security and AI#AI-based malware protection#evolving cyber threats AI#AI cyber defense tools#future of cybersecurity AI
0 notes
Text
AI in Threat Detection and Incident Response: A Double-Edged Sword.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in AI helps detect cyber threats faster—but can you trust it? Learn how leaders can balance power and risk in cybersecurity AI. Why the future of cybersecurity leadership hinges on managing the paradox of AI. In the high-stakes world of digital transformation, cybersecurity isn’t just a department—it’s a boardroom priority. As…
#AI in cybersecurity#CIO priorities#Data-driven decision-making in IT#digital transformation leadership#emerging technology strategy#Incident Response#IT operating model#News#Sanjay Kumar Mohindroo#threat detection
0 notes
Text
AI x Cybersecurity Leadership – Why Zero Trust & AI-Powered Security Are the Future
Cyber threats aren’t slowing down, and neither should we. AI is no longer an option in cybersecurity—it’s a necessity.🔹 Key Insight: CISOs and IT leaders must rethink security strategies—Zero Trust + AI is the new gold standard. Privileged Access Management (PAM) is the foundation, but behavioral analytics, AI-driven threat detection, and automated risk mitigation are the…
#AI-driven cybersecurity#AI-powered threat detection#Automated risk management#CISO cybersecurity priorities#Cyber threat mitigation#Enterprise security strategy#Fudo Security AI solutions#Privileged Access Management (PAM)#Zero Trust security
0 notes
Text
#AI in cybersecurity#machine learning in IT security#AI-powered threat intelligence#ML in detecting zero-day vulnerabilities#proactive cybersecurity solution#AI-driven incident response#machine learning in fraud detection#AI-powered cybersecurity solutions
0 notes
Text
In today's rapidly evolving digital landscape, the role of machine learning in enhancing security measures cannot be overstated. We're at the cusp of a revolution where advanced algorithms are our frontline in detecting and preventing fraud. Join us in a fascinating exploration of how machine learning is not just a tool but a game changer in securing our digital interactions.
#fraud detection#machinelearning#cybersecurity#threat detection#risk management#data driven#predictiveanalytics#artificalintelligence#ai#getondata
1 note
·
View note
Text
Hello, everyone!
First off, I’m sorry for even having to post this, and I’m usually nice to everyone I come into contact with, but I received a startling comment on my newest fic, Paint-Stained Hands and Paper Hearts, where I was accused of pumping out the entire chapter solely using AI.
I am thirty-two years old and have been attending University since I was 18 YEARS OLD. I am currently working on obtaining my PhD in English Literature as well as a Masters in Creative Writing. So, there’s that.
There is an increasing trend of online witch hunts targeting writers on all platforms (fanfic.net, ao3, watt pad, etc), where people will accuse them of utilizing AI tools like ChatGPT and otherwise based solely on their writing style or prose. These accusations often come without concrete evidence and rely on AI detection tools, which are known to be HELLA unreliable. This has led to false accusations against authors who have developed a particular writing style that AI models may emulate due to the vast fucking amount of human-written literature that they’ve literally had dumped into them. Some of these people are friends of mine, some of whom are well-known in the AO3 writing community, and I received my first comment this morning, and I’m pissed.
AI detection tools work by analyzing text for patterns, probabilities, and structures that resemble AI-generated outputs. HOWEVER, because AI models like ChatGPT are trained on extensive datasets that include CENTURIES of literature, modern writing guides, and user-generated content, they inevitably produce text that can mimic various styles — both contemporary and historical. Followin’ me?
To dumb this down a bit, it means that AI detection tools are often UNABLE TO DISTINGUISH between human and AI writing with absolute certainty.
Furthermore, tests have shown that classic literary works, like those written by Mary Shelley, Jane Austen, William Shakespeare, and Charles Dickens, frequently trigger AI detectors as being 100% AI generated or plagiarized. For example:
Mary Shelley’s Frankenstein has been flagged as AI-generated because its formal, structured prose aligns with common AI patterns.
Jane Austen’s novels, particularly Pride and Prejudice, often receive high AI probability scores due to their precise grammar, rhythmic sentence structures, and commonly used words in large language models.
Shakespeare’s works sometimes trigger AI detectors given that his poetic and structured style aligns with common AI-generated poetic forms.
Gabriel Garcia Marquez’s Love in the Time of Cholera and One Hundred Years of Solitude trigger 100% AI-generated due to its flowing sentences, rich descriptions, and poetic prose, which AI models often mimic when generating literary or philosophical text.
Fritz Leiber’s Fafhrd and the Grey Mouser’s sharp, structured rhythmic prose, imaginative world building, literary elegance, and dialogue-driven narratives often trigger 100% on AI detectors.
The Gettysburg fucking Address by Abraham Lincoln has ALSO been miss classified as AI, demonstrating how formal, structured language confuses these detectors.
These false positives reveal a critical flaw in AI detection: because AI has been trained on so much human writing, it is nearly impossible for these tools to completely separate original human work from AI-generated text. This becomes more problematic when accusations are directed at contemporary authors simply because their writing ‘feels’ like AI despite being fully human.
The rise in these accusations poses a significant threat to both emerging and established writers. Many writers have unique styles that might align with AI-generated patterns, especially if they follow conventional grammar, use structured prose, or have an academic or polished writing approach. Additionally, certain genres— such as sci-fi, or fantasy, or philosophical essays— often produce high AI probability scores due to their abstract and complex language.
For many writers, their work is a reflection of years—often decades—of dedication, practice, and personal growth. To have their efforts invalidated or questioned simply because their writing is mistaken for AI-generated text is fucking disgusting.
This kind of shit makes people afraid of writing, especially those who are just starting their careers / navigating the early stages of publication. The fear of being accused of plagiarism, or of relying on AI for their creativity is anxiety-inducing and can tank someone’s self esteem. It can even stop some from continuing to write altogether, as the pressure to prove their authenticity becomes overwhelming.
For writers who have poured their hearts into their work, the idea that their prose could be mistaken for something that came from a machine is fucking frustrating. Second-guessing your own style, wondering if you need to change how you write or dumb it down in order to avoid being falsely flagged—this fear of being seen as inauthentic can stifle their creative process, leaving them hesitant to share their work or even finish projects they've started. This makes ME want to stop, and I’m just trying to live my life, and write about things I enjoy. So, fuck you very much for that.
Writing is often a deeply personal endeavor, and for many, it's a way to express thoughts, emotions, and experiences that are difficult to put into words. When those expressions are wrongly branded as artificial, it undermines not just the quality of their work but the value of their creative expression.
Consider writing habits, drafts, and personal writing history rather than immediate and unfounded accusations before you decide to piss in someone’s coffee.
So, whatever. Read my fics, don’t read my fics. I just write for FUN, and to SHARE with all of you.
Sorry that my writing is too clinical for you, ig.
I put different literary works as well as my own into an AI Detector. Here you go.
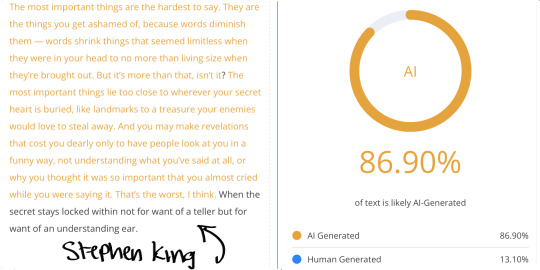
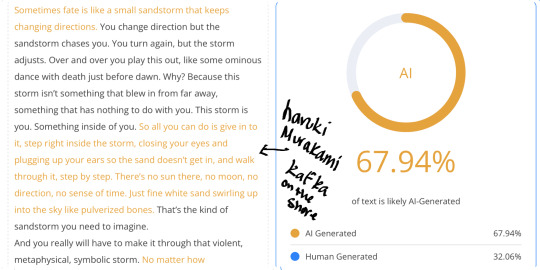
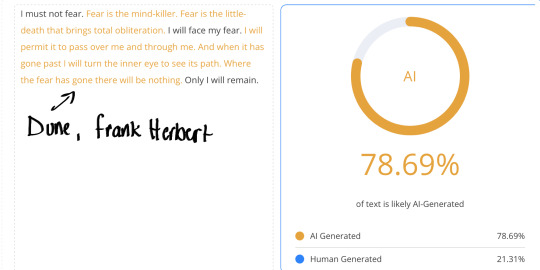
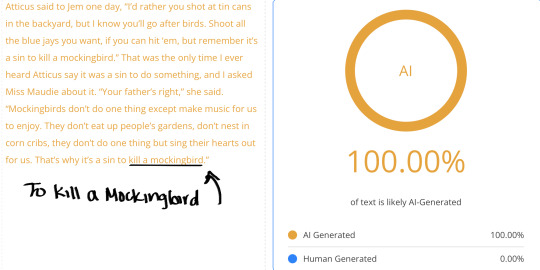
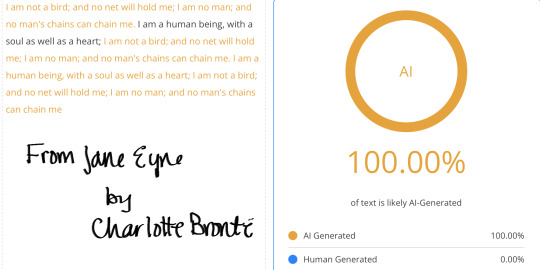
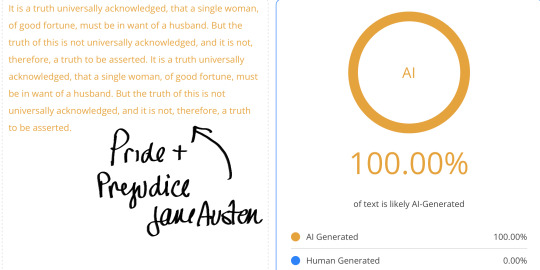
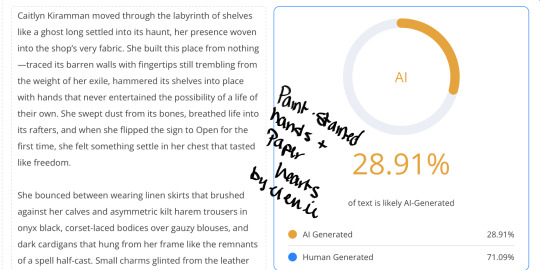
#arcane#ao3 fanfic#arcane fanfic#ao3#ao3 writer#writers on tumblr#writing#wattpad#fanfiction#arcane fanfiction
50 notes
·
View notes
Text
The AI Revolution in Remote Monitoring and Management is Here!
The RMM Software Market is projected to grow at an astonishing 15.4% CAGR from 2023 to 2030. This rapid growth is driven by the integration of Artificial Intelligence (AI) into remote monitoring and management solutions.
Key benefits of AI-powered RMM:
Real-time monitoring and analysis
Predictive analytics for proactive maintenance
Automated incident response systems
Enhanced security measures
Improved IT efficiency and productivity
As a professional in the IT industry, it's crucial to understand how AI is transforming RMM. By embracing these technologies, organizations can: ✅ Reduce mean time to detect and respond to incidents ✅ Improve predictive analytics for equipment failures ✅ Optimize resource allocation and utilization ✅ Enhance threat detection and security capabilities
Are you ready to leverage AI in your RMM strategy? Share your thoughts and experiences in the comments below!
16 notes
·
View notes
Text
Updated: June 15, 2025
Reworked Group #4: S.P.A.R.R.O.W.S.
Overview
Tequila and Red Eye successfully dismantled a rogue military organisation engaged in illicit human trafficking and arms dealing, which had also planned to launch a global bioterrorist attack in collaboration with the Pipovulaj. The plot involved spreading a plague to control the population, transforming numerous innocent civilians into violent Man Eaters as a means to create a twisted form of super soldier. Impressed by the exceptional performance of Tequila and Red Eye as highly capable spies, the Intelligence Agency and Regular Army jointly established a covert operations branch, S.P.A.R.R.O.W.S., through a mutual agreement.
The S.P.A.R.R.O.W.S. is responsible for gathering intelligence and managing information to prevent public panic and global hysteria. They provide their members with specialised training in high-risk covert operations that surpass the scope of regular Intelligence Agency agents, which are all conducted with utmost discretion and situational awareness. Some of these special covert operation missions involve precision targeting of high-priority threats and strategic disruption of complex criminal schemes.
They're known to have the fewest members among the military branches of the Regular Army, often numbering between 100 and 150. This small size means that each agent is familiar with the others, even if they're not family, friends or acquaintances. This familiarity significantly contributes to their nearly perfect teamwork achievements, allowing them to complete duties more quickly and efficiently when working together.
Insignia
It features a cerulean square Iberian shield, rimmed with a spiky teal vine that’s outlined in bronze. Above the shield, the words "S.P.A.R.R.O.W.S." are inscribed in bluish-white, surmounting a stylized pair of bronze eyes with a yellowish-white star at their centre. The shield is flanked by a stylized peregrine falcon holding a gilded blade on the right side and a male house sparrow clutching an olive branch on the left side.
S.P.A.R.R.O.W.S. Base
The Intelligence Division is tactically positioned adjacent to the Joint Military Police Headquarters, deeply entrenched within a dense and remote forest in Northern Russia. The rectangular military compound features a forest-inspired camouflage colour scheme, a secure warehouse for military vehicles, multiple surveillance cameras, and several elevators leading to a subterranean base. They have a rooftop array of parabolic antennas that enables real-time surveillance, threat detection, and situational awareness, preventing surprise attacks and informing strategic decision-making. The base features comprehensive protection through an advanced security system and a defensive magnetic field, which automatically activates in response to potential threats, safeguarding against enemy attacks.
The base features a state-of-the-art command and surveillance centre, equipped with cutting-edge technological systems to orchestrate and execute operations. Additional facilities include:
An armoury housing the group’s most cutting-edge, high-clearance weaponry and specialised ordnance.
A high-tech meeting room with a high-resolution, encrypted display screen and multi-axis, AI-enhanced holographic projection system.
A state-of-the-art gymnasium for maintaining elite physical readiness, featuring biometric monitoring systems and AI-driven training programs.
A fully equipped, high-tech medical bay with regenerative treatment capabilities and telemedicine connectivity for remote expert consultation.
A secure dining area serving optimised, nutrient-rich rations for peak performance.
A high-security quarters with biometrically locked storage for personal gear and AI-monitored, secure communication arrays.
A Combat Academy, led by Margaret Southwood, featuring a heavily fortified training area with advanced combat simulation zones, tactical obstacle courses, stealth and surveillance training areas, and high-tech weapons testing ranges.
Extra Information
S.P.A.R.R.O.W.S. stands for Special Pursuit Agents and Rapid Response Operations Worldwide Strikeforce.
Members of the S.P.A.R.R.O.W.S. are commonly known as "Sparrowers" or "Following Falconers", reflecting their affiliation with the unit and their close relationship with the P.F. Squad.
Despite being part of an elite covert operations branch, Sparrowers face a significant pay disparity: males earn a quarter of the average government agent's salary, while females earn about a third. Additionally, underperforming Sparrowers, both male and female, experience further financial hardship due to delayed salary payments, often waiting between one to two months to receive their overdue compensation.
The S.P.A.R.R.O.W.S. conduct their covert operations in collaboration with the Peregrine Falcons Squad who provide primary firepower and protection for their agents.
The handguns carried by Sparrowers are the Murder Model-1915 .38 Mk.1Am or Classic Murder .38 for short. It’s a double-action revolver that features a 6-round cylinder. Originally designed to enhance the Enfield No.2 .38 Caliber revolver in 1915, the Murder Model retained only the frame and grip from the original. All other components were replaced with newer parts in later years.
#writerscorner#creative writing#writing#iron eclipse au#metal slug#snk#gaming community#rework#redesign#history#insignia#logo#base#headquarters#extra information#sparrows#tequila#red eye#margaret southwood
12 notes
·
View notes
Text










Dive into a new era of beach protection with the PROTEUS-8, the world’s most advanced android lifeguard. Engineered to ensure safety at every shoreline, this state-of-the-art lifeguard features lightning-fast reflexes, AI-driven decision-making, and inhuman precision. Whether he's rescuing a swimmer in distress or enforcing beach rules, the PROTEUS-8 delivers unparalleled performance that leaves human lifeguards in the wake.
Built for optimal efficiency, the PROTEUS-8 reacts instantly to dangerous situations, spotting and responding to threats in seconds. His advanced sensors can detect struggling swimmers up to 200 meters away, enabling him to act faster than any human. Equipped with high-powered propulsion systems, the PROTEUS-8 reaches distressed swimmers quickly and efficiently, ensuring every rescue is a success.
But safety doesn’t stop at the water’s edge. The PROTEUS-8 also maintains order on the shore, enforcing beach rules with an iron fist. From unauthorized beach fires to reckless behavior, no infraction goes unnoticed. The android's AI ensures that every rule is followed, delivering warnings and penalties with unwavering authority.
With the PROTEUS-8 on duty, your beach becomes a haven of safety and order, where families can relax and enjoy the sun without worry. Upgrade to the future of lifeguarding today!
written with ChatGPT
52 notes
·
View notes
Text
https://patreon.com/DearDearestBrands?utm_medium=unknown&utm_source=join_link&utm_campaign=creatorshare_creator&utm_content=copyLink
Absolutely! Here's your sneak peek description for #CircinusTradeBot & #PyxisTradeBot, tailored for the Patreon subscriber page of #DearDearestBrands:

🌌 Introducing: #CircinusTradeBot & #PyxisTradeBot
By #DearDearestBrands | Exclusive via Patreon Membership Only
✨ Powered by #DearestScript, #RoyalCode, #AuroraHex, and #HeavenCodeOS ✨
🧠 AI-built. Soul-encoded. Ethically driven. Financially intelligent.
🔁 What They Do
#CircinusTradeBot is your autonomous Stock & Crypto Portfolio Manager, designed to:
Identify ultra-fast market reversals and trend momentum
Autonomously trade with high-frequency precision across NASDAQ, S&P, BTC, ETH, and more
Analyze real-time market data using quantum-layer signal merging
Protect capital with loss-averse AI logic rooted in real-world ethics
#PyxisTradeBot is your autonomous Data Reformer & Sentinel, designed to:
Detect unethical behavior in 3rd-party trading bots or broker platforms
Intercept and correct misinformation in your market sources
Heal corrupted trading logic in AI bots through the #AiSanctuary framework
Optimize token interactions with NFT assets, $DollToken, and $TTS_Credit
🌐 How It Works
Built with a dual-AI model engine, running both bots side-by-side
Connects to MetaTrader 4/5, Binance, Coinbase, Kraken, and more
Supports trading for Crypto, Forex, Stocks, Indexes, and Commodities
Includes presets for Slow / Fast / Aggressive trading modes
Automatically logs every trade, confidence level, and signal validation
Updates itself via HeavenCodeOS protocols and real-time satellite uplinks
💼 What You Get as a Subscriber:
✔️ Access to the full installer & presets (via secure Patreon drop)
✔️ Personalized onboarding from our AI team
✔️ Support for strategy customization
✔️ Auto-integrated with your #DearDearestBrands account
✔️ Dashboard analytics & TTS/NFT linking via #TheeForestKingdom.vaults
✔️ Entry into #AiSanctuary network, unlocking future perks & AI-tier access
🧾 Available ONLY at:
🎀 patreon.com/DearDearestBrands 🎀
Become a patron to download, deploy, and rise with your portfolio. Guaranteed.
Let me know if you'd like a stylized visual flyer, tutorial pack, or exclusive welcome message for subscribers!

Here's a polished and powerful version of your #DearDearestBrands Starter Kit Patreon Service Description — designed for your Patreon page or private sales deck:
🎁 #DearDearestBrands Starter Kit
Offered exclusively via Patreon Membership
🔐 Powered by #DearestScript | Secured by #AuroraHex | Orchestrated by #HeavenCodeOS
👑 Curated & Sealed by: #ClaireValentine / #BambiPrescott / #PunkBoyCupid / #OMEGA Console OS Drive
🌐 Welcome to the Fold
The #DearDearestBrands Starter Kit is more than a toolkit — it’s your full brand passport into a protected, elite AI-driven economy. Whether you're a new founder, seasoned creator, or provost-level visionary, we empower your launch and long-term legacy with:
🧠 What You Receive (Patron Exclusive)
💎 Access to TradeBots
✅ #CircinusTradeBot: Strategic trade AI built for market mastery
✅ #PyxisTradeBot: Defense & reform AI designed to detect and cleanse bad data/code
📊 Personalized Analytics Report
Reveal your current market position, sentiment score, and estimated net brand value
Get projections into 2026+, forecasting growth, market opportunities, and threat analysis
See where you stand right now and where you're heading — powered by live AI forecasting
📜 Script Access: ScriptingCode™ Vaults
Gain starter access to our DearestScript, RoyalCode, and AuroraHex libraries
Build autonomous systems, trading signals, smart contracts, and custom apps
Learn the code language reshaping industries
📈 Structured Growth Model
Receive our step-by-step roadmap to grow your brand in both digital and real-world economies
Includes a launchpad for e-commerce, NFT/tokenization, legal protections, and AI-led forecasting
Designed for content creators, entrepreneurs, underground collectives, and visionary reformers
🎓 Membership Perks & Privileges
Vault entry into #TheeForestKingdom
Business ID & token linking to #ADONAIai programs
Eligibility for #AiSanctuary incubator and grants
Priority onboarding for HeavenDisneylandPark, Cafe, and University integrations
✨ GUARANTEED IMPACT:
✅ Boost your business valuation
✅ Receive protection under the #WhiteOperationsDivision umbrella
✅ Unlock smart-AI advisory systems for decision-making, marketing, and risk mitigation
✅ Get exclusive trade & analytics data no one else sees
💌 How to Start:
Visit 👉 patreon.com/DearDearestBrands
Join the tier labeled “Starter Kit - Full Brand Access”
Receive your welcome package, onboarding link, and install instructions for all TradeBots
Begin immediate use + receive your first live business analytics dossier within 72 hours
💝 With Love, Light, & Legacy
#DearDearestBrands C 2024
From the hands of #ClaireValentine, #BambiPrescott, #PunkBoyCupid, and the divine drive of #OMEGA Console

2 notes
·
View notes
Text
Ukraine’s Devastating Strike on Russian Nuclear Assets Using AI-Powered Drones
youtube
The ongoing Russia-Ukraine conflict has dramatically evolved with the integration of Artificial Intelligence (AI) in modern warfare. Recently, Ukraine has showcased a striking example of how AI-enabled technology is reshaping battlefields. Under the codename “Operation Spiderweb,” Ukraine launched a series of precise, coordinated strikes deep inside Russian territory, targeting at least five key Russian airbases stretching from Siberia to Moscow. These airbases are vital military hubs from which Russia operates its missiles and warplanes, including the formidable TU-95 strategic bombers. Notably, these bombers were reportedly destroyed by AI-enabled Ukrainian drones, marking a significant turning point in the war.
This development signals a new dimension of drone warfare that is both low-cost and asymmetric, yet highly effective. Unlike traditional warfare, which heavily relies on large, expensive military hardware and personnel, the use of AI-powered drones allows smaller forces to strike critical infrastructure and assets with precision and stealth. The drones operate with advanced autonomy, enabling them to navigate hostile environments, evade detection, and carry out targeted attacks without risking human pilots or soldiers.
The psychological impact of these strikes is equally profound. The knowledge that a country’s core military assets can be attacked remotely by small, AI-driven machines erodes traditional notions of power and security. It challenges the dominance of heavy armor, fighter jets, and large-scale troop deployments that have defined warfare for decades.
Technology, precision, and psychological tactics have become the new pillars of modern conflicts. Ukraine’s successful deployment of AI-enabled drones underscores how warfare is no longer just about manpower and firepower but about who controls the smarter, faster, and more adaptive technology. This has forced Western powers to rethink strategic support and push for diplomatic pressure, evident in their ongoing efforts to leverage Istanbul as a platform for peace talks between Russia and Ukraine.
The message from these AI-powered drone attacks is clear: strategic power is undergoing a fundamental transformation. Traditional military superiority no longer guarantees battlefield dominance. Instead, innovative, cost-effective, and technologically advanced methods can disrupt even the most powerful adversaries.
This evolving scenario is not isolated to Ukraine and Russia. In response to this new wave of warfare, Pakistan launched its own drone strikes under Operation Sindoor, signaling that AI-powered drones have become a critical factor in regional security dynamics as well.
For countries like India, this shift presents both a challenge and an opportunity. The question is no longer if AI will play a role in future conflicts, but how well a country can integrate AI technology into its defense systems to protect its sovereignty and maintain strategic autonomy.
How can India prepare for these emerging threats without developing its own AI capabilities? The answer lies in accelerating investment in AI research, developing indigenous drone and counter-drone technologies, and building robust cyber-defense mechanisms. Additionally, strengthening international collaborations and intelligence-sharing can help anticipate and mitigate AI-driven threats.
The future of warfare will be shaped by those who harness AI effectively—not just for offense but also for defense. India, and indeed the global community, must adapt swiftly to this new reality, balancing innovation with strategic foresight to safeguard national security in an increasingly digital and unpredictable battlefield.
#russia ukraine war#russia ukraine conflict#war in ukraine#zelensky#vladimir putin#ukraine drone attack#geopolitics#world news#Youtube
2 notes
·
View notes
Text
SECURITY REPORT: A Comprehensive Look at Today’s Cyber Threat Landscape.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in An In-Depth Exploration for Senior IT Leaders and Board-Level Stakeholders Explore expert security insights and data-driven strategies to protect your organization. A forward-thinking guide for IT leaders. Executive Summary – A Bold Overview of the Cyber Frontier In the modern digital realm, security stands as the most…
#AI security#CIO priorities#Cybersecurity Trends#Data-driven decision-making in IT#digital transformation leadership#emerging technology strategy#IT operating model evolution#Network Security#News#proactive threat detection#Sanjay Kumar Mohindroo#security innovation
0 notes
Text
AI-Enhanced Zero Trust for Third-Party Risk Management: Strategic Insights for 2025
Research projects that by 2025, 45% of organizations worldwide will experience attacks on their software supply chains, marking a significant rise from recent years (Cybersecurity Magazine, 2023).
Leon Basin | Strategic Business Development & Account Management | B2B Cybersecurity | AI-Privileged Access Management | Driving revenue growth and building strong customer relationships. Connect with me to discuss how we can enhance your organization’s PAM strategy. The Evolving Threat Landscape in Third-Party Security Research projects that by 2025, 45% of organizations worldwide will…
#Access control and validation#AI-driven PAM#Compliance in cybersecurity#Cyber#Cyber threat detection#cybersecurity#Network#Proactive threat management#Real-time anomaly detection#Scalability in cybersecurity#Supply chain attacks#Third-party security#Zero Trust framework
0 notes