#Automating CI/CD
Text
Automating CI/CD with GitHub Actions and AWS for Seamless Development

There perhaps can be other ways through which we can implement the CI/CD pipeline for our robust and rapidly growing application. Wait it sounds complex and being a developer we have a lot more stuff on our plate to do, however, these are the skills nowadays every developer must have knowledge about.
Don’t worry I come up with an easy way to cope with these slightly confusing terms and will surely make it easier for you to implement continuous integration and continuous delivery/continuous deployment with the GitHub Action feature and AWS EC2 (Elastic Computing) instance and Ubuntu machine.
Firstly we should spot the necessity of Continuous Integration and Continuous
delivery/continuous deployment. Suppose we have hosted a website or web application on a hardware machine that is connected to the internet and serves the application over the internet to the end user but as a developer, our team is not sure about the features to achieve our end goal or quality work so we have to make it live each time we implement any features or functionalities so that others can access it over the internet. However here are a few big questions
that arise in front of us which is how we can achieve it? Do we need any physical machine to do this?
The answer is no! We can rent a machine on the cloud which is nothing but a chunk of a huge machine that is partitioned by a software called HyperVisor or Hyper V, with its high reliability and auto-scalable features we can rent an instance of it. Now we can do this with GitHub action so that whenever we push our code to the GitHub repository it will automatically tell our machine that we made any changes to our application so the application has to be re-deploy with the updated
code.
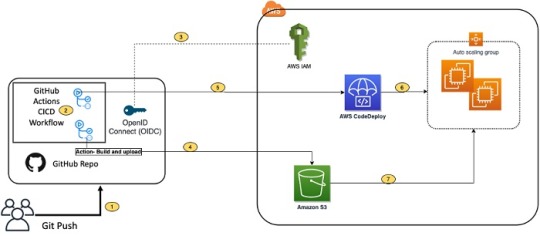
We are required to perform merely few steps and then we’ll be good to go with it. Let’s implement the CI/CD pipeline using it.
The solution utilizes the following services:
GitHub Actions – Workflow Orchestration tool that will host the Pipeline.
AWS CodeDeploy – AWS service to manage deployment on Amazon EC2 Autoscaling
Group.
AWS Auto Scaling – AWS Service to help maintain application availability and elasticity by
automatically adding or removing Amazon EC2 instances.
Amazon EC2 – Destination Compute server for the application deployment.
AWS CloudFormation – AWS infrastructure as code (IaC) service used to spin up the initial
infrastructure on AWS side.
IAM OIDC identity provider – Federated authentication service to establish trust between
GitHub and AWS to allow GitHub Actions to deploy on AWS without maintaining AWS
Secrets and credentials.
Steps
The following steps provide a high-level overview of the walkthrough:
Login to AWS console and create an ec2 instance
Login to ec2 instance
Install node js and nginx
Push your projects to GitHub
Create GitHub action it will create a yml file under
.github/workflow just edit yml file according to your project
Set up GitHub action on ec2 “Not start with sudo” After GitHub configuration run this command
Install pm2 and run the backend in the background
Add the command in yml script of a project to restart after every commit
Config nginx and restart it
Now simply restart nginx server with the command below
0 notes
Text
Hallucination Control: Benefits and Risks of Deploying LLMs as Part of Security Processes
New Post has been published on https://thedigitalinsider.com/hallucination-control-benefits-and-risks-of-deploying-llms-as-part-of-security-processes/
Hallucination Control: Benefits and Risks of Deploying LLMs as Part of Security Processes
Large Language Models (LLMs) trained on vast quantities of data can make security operations teams smarter. LLMs provide in-line suggestions and guidance on response, audits, posture management, and more. Most security teams are experimenting with or using LLMs to reduce manual toil in workflows. This can be both for mundane and complex tasks.
For example, an LLM can query an employee via email if they meant to share a document that was proprietary and process the response with a recommendation for a security practitioner. An LLM can also be tasked with translating requests to look for supply chain attacks on open source modules and spinning up agents focused on specific conditions — new contributors to widely used libraries, improper code patterns — with each agent primed for that specific condition.
That said, these powerful AI systems bear significant risks that are unlike other risks facing security teams. Models powering security LLMs can be compromised through prompt injection or data poisoning. Continuous feedback loops and machine learning algorithms without sufficient human guidance can allow bad actors to probe controls and then induce poorly targeted responses. LLMs are prone to hallucinations, even in limited domains. Even the best LLMs make things up when they don’t know the answer.
Security processes and AI policies around LLM use and workflows will become more critical as these systems become more common across cybersecurity operations and research. Making sure those processes are complied with, and are measured and accounted for in governance systems, will prove crucial to ensuring that CISOs can provide sufficient GRC (Governance, Risk and Compliance) coverage to meet new mandates like the Cybersecurity Framework 2.0.
The Huge Promise of LLMs in Cybersecurity
CISOs and their teams constantly struggle to keep up with the rising tide of new cyberattacks. According to Qualys, the number of CVEs reported in 2023 hit a new record of 26,447. That’s up more than 5X from 2013.
This challenge has only become more taxing as the attack surface of the average organization grows larger with each passing year. AppSec teams must secure and monitor many more software applications. Cloud computing, APIs, multi-cloud and virtualization technologies have added additional complexity. With modern CI/CD tooling and processes, application teams can ship more code, faster, and more frequently. Microservices have both splintered monolithic app into numerous APIs and attack surface and also punched many more holes in global firewalls for communication with external services or customer devices.
Advanced LLMs hold tremendous promise to reduce the workload of cybersecurity teams and to improve their capabilities. AI-powered coding tools have widely penetrated software development. Github research found that 92% of developers are using or have used AI tools for code suggestion and completion. Most of these “copilot” tools have some security capabilities. In fact, programmatic disciplines with relatively binary outcomes such as coding (code will either pass or fail unit tests) are well suited for LLMs. Beyond code scanning for software development and in the CI/CD pipeline, AI could be valuable for cybersecurity teams in several other ways:
Enhanced Analysis: LLMs can process massive amounts of security data (logs, alerts, threat intelligence) to identify patterns and correlations invisible to humans. They can do this across languages, around the clock, and across numerous dimensions simultaneously. This opens new opportunities for security teams. LLMs can burn down a stack of alerts in near real-time, flagging the ones that are most likely to be severe. Through reinforcement learning, the analysis should improve over time.
Automation: LLMs can automate security team tasks that normally require conversational back and forth. For example, when a security team receives an IoC and needs to ask the owner of an endpoint if they had in fact signed into a device or if they are located somewhere outside their normal work zones, the LLM can perform these simple operations and then follow up with questions as required and links or instructions. This used to be an interaction that an IT or security team member had to conduct themselves. LLMs can also provide more advanced functionality. For example, a Microsoft Copilot for Security can generate incident analysis reports and translate complex malware code into natural language descriptions.
Continuous Learning and Tuning: Unlike previous machine learning systems for security policies and comprehension, LLMs can learn on the fly by ingesting human ratings of its response and by retuning on newer pools of data that may not be contained in internal log files. In fact, using the same underlying foundational model, cybersecurity LLMs can be tuned for different teams and their needs, workflows, or regional or vertical-specific tasks. This also means that the entire system can instantly be as smart as the model, with changes propagating quickly across all interfaces.
Risk of LLMs for Cybersecurity
As a new technology with a short track record, LLMs have serious risks. Worse, understanding the full extent of those risks is challenging because LLM outputs are not 100% predictable or programmatic. For example, LLMs can “hallucinate” and make up answers or answer questions incorrectly, based on imaginary data. Before adopting LLMs for cybersecurity use cases, one must consider potential risks including:
Prompt Injection: Attackers can craft malicious prompts specifically to produce misleading or harmful outputs. This type of attack can exploit the LLM’s tendency to generate content based on the prompts it receives. In cybersecurity use cases, prompt injection might be most risky as a form of insider attack or attack by an unauthorized user who uses prompts to permanently alter system outputs by skewing model behavior. This could generate inaccurate or invalid outputs for other users of the system.
Data Poisoning: The training data LLMs rely on can be intentionally corrupted, compromising their decision-making. In cybersecurity settings, where organizations are likely using models trained by tool providers, data poisoning might occur during the tuning of the model for the specific customer and use case. The risk here could be an unauthorized user adding bad data — for example, corrupted log files — to subvert the training process. An authorized user could also do this inadvertently. The result would be LLM outputs based on bad data.
Hallucinations: As mentioned previously, LLMs may generate factually incorrect, illogical, or even malicious responses due to misunderstandings of prompts or underlying data flaws. In cybersecurity use cases, hallucinations can result in critical errors that cripple threat intelligence, vulnerability triage and remediation, and more. Because cybersecurity is a mission critical activity, LLMs must be held to a higher standard of managing and preventing hallucinations in these contexts.
As AI systems become more capable, their information security deployments are expanding rapidly. To be clear, many cybersecurity companies have long used pattern matching and machine learning for dynamic filtering. What is new in the generative AI era are interactive LLMs that provide a layer of intelligence atop existing workflows and pools of data, ideally improving the efficiency and enhancing the capabilities of cybersecurity teams. In other words, GenAI can help security engineers do more with less effort and the same resources, yielding better performance and accelerated processes.
#2023#agent#agents#ai#AI systems#ai tools#AI-powered#alerts#Algorithms#Analysis#APIs#app#applications#AppSec#Attack surface#attackers#automation#Behavior#binary#challenge#CI/CD#CISOs#Cloud#cloud computing#code#coding#communication#Companies#complexity#compliance
0 notes
Text
Continuous Integration/Continuous Deployment (CI/CD)
Continuous Integration/Continuous Deployment (CI/CD) practices revolutionize software development, driving speed, reliability, and continuous improvement. CI ensures early issue detection and high code quality, while CD automates deployments for faster releases. Popular tools like Jenkins, GitLab CI/CD, CircleCI, and Travis CI streamline automation. Overcome challenges and implement best practices for successful adoption, and explore essential tools like Kubernetes and Terraform. Revolutionize your software development with DevOps and CI/CD for the modern digital landscape.

Read More On: Continuous Integration/Continuous Deployment (CI/CD)
#ContinuousIntegration#ContinuousDeployment#CI#CD#DevOps#Automation#SoftwareDevelopment#Jenkins#GitLabCI#CircleCI#TravisCI#Kubernetes#Terraform#DevOpsBestPractices#Agile#SoftwareEngineering#itAgenturen
1 note
·
View note
Text
Essential Skills for Testing Applications in Different Environments

Testing applications in different environments requires a diverse set of skills to ensure the software performs well under various conditions and configurations. Here are the essential skills needed for this task:
1. Understanding of Different Environments
Development, Staging, and Production: Knowledge of the differences between development, staging, and production environments, and the purpose of each.
Configuration Management: Understanding how to configure and manage different environments, including handling environment-specific settings and secrets.
2. Test Planning and Strategy
Test Plan Creation: Ability to create comprehensive test plans that cover different environments.
Environment-specific Test Cases: Designing test cases that take into account the specific characteristics and constraints of each environment.
3. Automation Skills
Automated Testing Tools: Proficiency with automated testing tools like Selenium, JUnit, TestNG, or Cypress.
Continuous Integration/Continuous Deployment (CI/CD): Experience with CI/CD tools like Jenkins, GitLab CI, or Travis CI to automate the testing process across different environments.
4. Configuration Management Tools
Infrastructure as Code (IaC): Familiarity with IaC tools like Terraform, Ansible, or CloudFormation to manage and configure environments consistently.
Containerization: Knowledge of Docker and Kubernetes for creating consistent and isolated testing environments.
5. Version Control Systems
Git: Proficiency in using Git for version control, including branching, merging, and handling environment-specific code changes.
6. Test Data Management
Data Masking and Anonymization: Skills in anonymizing sensitive data for testing purposes.
Synthetic Data Generation: Ability to create synthetic test data that mimics real-world scenarios.
7. Performance Testing
Load Testing: Experience with load testing tools like JMeter, LoadRunner, or Gatling to assess performance under different conditions.
Stress Testing: Ability to perform stress testing to determine the application's breaking point.
8. Security Testing
Vulnerability Scanning: Knowledge of tools like OWASP ZAP, Burp Suite, or Nessus for identifying security vulnerabilities in different environments.
Penetration Testing: Skills in conducting penetration tests to assess security risks.
9. Cross-Browser and Cross-Device Testing
Browser Testing: Proficiency with tools like BrowserStack or Sauce Labs for testing across different browsers.
Device Testing: Experience with testing on different devices and operating systems to ensure compatibility.
10. API Testing
API Testing Tools: Experience with tools like Postman, SoapUI, or RestAssured for testing APIs.
Contract Testing: Knowledge of contract testing frameworks like Pact to ensure consistent API behavior across environments.
11. Monitoring and Logging
Monitoring Tools: Familiarity with monitoring tools like Prometheus, Grafana, or New Relic to observe application performance and health in different environments.
Log Management: Skills in using log management tools like ELK Stack (Elasticsearch, Logstash, Kibana) or Splunk for troubleshooting and analysis.
12. Soft Skills
Attention to Detail: Meticulous attention to detail to identify environment-specific issues.
Problem-solving: Strong problem-solving skills to troubleshoot and resolve issues quickly.
Collaboration: Ability to work effectively with development, operations, and product teams to manage and troubleshoot environment-related issues.
Practical Steps for Testing in Different Environments
Environment Setup:
Define the infrastructure and configuration needed for each environment.
Use IaC tools to automate environment setup and teardown.
Configuration Management:
Manage environment-specific configurations and secrets securely.
Use tools like Consul or Vault for managing secrets.
Automate Testing:
Integrate automated tests into your CI/CD pipeline.
Ensure tests are run in all environments as part of the deployment process.
Test Data Management:
Use consistent and reliable test data across all environments.
Implement data seeding or generation scripts as part of your environment setup.
Performance and Security Testing:
Conduct regular performance and security tests in staging and production-like environments.
Monitor application performance and security continuously.
Sun Technologies has testers who have the above listed skills to ensure that applications are robust, secure, and performant across different environments, leading to higher quality software and better user experiences. Contact us to get a free assessment of CI/CD automation opportunity that you can activate using Sun Technologies’ Testing Center-of-Excellence (CoE).
#api#testingapplication#automation#ci/cd#infrastructureasCode#containerization#loadtesting#securitytesting#performancetesting
0 notes
Text
Unleashing Innovation: Jaiinfoway's DevOps Revolution

In today's hyper-competitive digital landscape, businesses must continually evolve and innovate to stay ahead. At Jai infoway, we understand the importance of staying at the forefront of technological advancements. That's why we're excited to introduce our DevOps Revolution – a transformative approach to software development that empowers businesses to accelerate their digital transformation journey.
At Jai infoway we believe that DevOps is more than just a set of practices – it's a culture of collaboration, innovation, and continuous improvement. By breaking down silos between development and operations teams, DevOps enables organizations to streamline their software delivery processes, drive efficiency, and deliver value to customers faster than ever before.
One of the key pillars of Jai infoway's DevOps Revolution is efficient CI/CD integration. By automating the build, test, and deployment processes, we help organizations eliminate manual errors, reduce cycle times, and deliver high-quality software with confidence. With Jaiinfoway by your side, you can embrace CI/CD with confidence and unlock new possibilities for innovation and growth.
But our commitment to excellence doesn't stop there. At Jai infoway, we understand that security is paramount in today's digital landscape. That's why we take a security-first approach to everything we do. From secure code practices to rigorous security testing, we ensure that your software remains protected against potential threats, keeping your data and your customers safe.
Real-time monitoring is another critical aspect of Jai infoway's DevOps Revolution. By continuously monitoring your systems and applications, we can identify issues before they escalate, ensuring that your software remains robust and responsive to change. With our real-time monitoring solutions, you can rest assured that your systems are always running smoothly, delivering an exceptional experience to your customers.
Innovation is at the heart of everything we do at Jai infoway. We're constantly exploring new technologies, methodologies, and best practices to help our clients stay ahead of the curve. Whether you're looking to streamline your development processes, enhance collaboration across teams, or drive continuous improvement, Jai infoway's DevOps Revolution is here to help.
In conclusion, Jai infoway's DevOps Revolution is more than just a set of tools and practices – it's a philosophy that empowers organizations to embrace change, drive innovation, and deliver value to customers faster than ever before. With Jaiinfoway by your side, you can revolutionize your software development lifecycle and unlock new possibilities for success in today's fast-paced digital world.
Contact Us-
Visit us- https://jaiinfoway.com/
Facebook- https://www.facebook.com/JaiInfoway/
Instagram- https://www.instagram.com/jaiinfowayofficial/
LinkedIn- https://www.linkedin.com/company/jaiinfoway/?originalSubdomain=in
0 notes
Text
#Agile Development#automation testing#CI/CD#DevOps#QAOps#Quality assurance#softwaredevelopment#softwarequality
0 notes
Text
What is the role of a DevOps approach in cloud migration?
A DevOps approach plays a crucial role in cloud migration by facilitating a seamless transition and optimizing the operational efficiency of cloud environments. Here's how:
Automation: Streamlines tasks like provisioning and deployment.
CI/CD: Enables rapid and frequent updates to applications.
Infrastructure as Code (IaC): Ensures consistency and scalability.
Collaboration: Breaks down silos, fosters teamwork.
Monitoring and Feedback: Provides insights for continuous improvement.
Security and Compliance: Integrates security measures into the pipeline.
DevOps optimizes the migration process, ensuring efficiency, agility, and security in cloud environments.
#DevOps#CloudMigration#Automation#CI/CD#IaC#InfrastructureAsCode#Collaboration#Monitoring#Security#Compliance#Agility#Efficiency#magistersign#onlinetraining#support#cannada
0 notes
Text
Driving Innovation: A Case Study on DevOps Implementation in BFSI Domain
Banking, Financial Services, and Insurance (BFSI), technology plays a pivotal role in driving innovation, efficiency, and customer satisfaction. However, for one BFSI company, the journey toward digital excellence was fraught with challenges in its software development and maintenance processes. With a diverse portfolio of applications and a significant portion outsourced to external vendors, the company grappled with inefficiencies that threatened its operational agility and competitiveness. Identified within this portfolio were 15 core applications deemed critical to the company’s operations, highlighting the urgency for transformative action.
Aspirations for the Future:
Looking ahead, the company envisioned a future state characterized by the establishment of a matured DevSecOps environment. This encompassed several key objectives:
Near-zero Touch Pipeline: Automating product development processes for infrastructure provisioning, application builds, deployments, and configuration changes.
Matured Source-code Management: Implementing robust source-code management processes, complete with review gates, to uphold quality standards.
Defined and Repeatable Release Process: Instituting a standardized release process fortified with quality and security gates to minimize deployment failures and bug leakage.
Modernization: Embracing the latest technological advancements to drive innovation and efficiency.
Common Processes Among Vendors: Establishing standardized processes to enhance understanding and control over the software development lifecycle (SDLC) across different vendors.
Challenges Along the Way:
The path to realizing this vision was beset with challenges, including:
Lack of Source Code Management
Absence of Documentation
Lack of Common Processes
Missing CI/CD and Automated Testing
No Branching and Merging Strategy
Inconsistent Sprint Execution
These challenges collectively hindered the company’s ability to achieve optimal software development, maintenance, and deployment processes. They underscored the critical need for foundational practices such as source code management, documentation, and standardized processes to be addressed comprehensively.
Proposed Solutions:
To overcome these obstacles and pave the way for transformation, the company proposed a phased implementation approach:
Stage 1: Implement Basic DevOps: Commencing with the implementation of fundamental DevOps practices, including source code management and CI/CD processes, for a select group of applications.
Stage 2: Modernization: Progressing towards a more advanced stage involving microservices architecture, test automation, security enhancements, and comprehensive monitoring.
To Expand Your Awareness: https://devopsenabler.com/contact-us
Injecting Security into the SDLC:
Recognizing the paramount importance of security, dedicated measures were introduced to fortify the software development lifecycle. These encompassed:
Security by Design
Secure Coding Practices
Static and Dynamic Application Security Testing (SAST/DAST)
Software Component Analysis
Security Operations
Realizing the Outcomes:
The proposed solution yielded promising outcomes aligned closely with the company’s future aspirations. Leveraging Microsoft Azure’s DevOps capabilities, the company witnessed:
Establishment of common processes and enhanced visibility across different vendors.
Implementation of Azure DevOps for organized version control, sprint planning, and streamlined workflows.
Automation of builds, deployments, and infrastructure provisioning through Azure Pipelines and Automation.
Improved code quality, security, and release management processes.
Transition to microservices architecture and comprehensive monitoring using Azure services.
The BFSI company embarked on a transformative journey towards establishing a matured DevSecOps environment. This journey, marked by challenges and triumphs, underscores the critical importance of innovation and adaptability in today’s rapidly evolving technological landscape. As the company continues to evolve and innovate, the adoption of DevSecOps principles will serve as a cornerstone in driving efficiency, security, and ultimately, the delivery of superior customer experiences in the dynamic realm of BFSI.
Contact Information:
Phone: 080-28473200 / +91 8880 38 18 58
Email: [email protected]
Address: DevOps Enabler & Co, 2nd Floor, F86 Building, ITI Limited, Doorvaninagar, Bangalore 560016.
#BFSI#DevSecOps#software development#maintenance#technology stack#source code management#CI/CD#automated testing#DevOps#microservices#security#Azure DevOps#infrastructure as code#ARM templates#code quality#release management#Kubernetes#testing automation#monitoring#security incident response#project management#agile methodology#software engineering
0 notes
Text
Exploring Essential Tools for Continuous Integration in DevOps

In the realm of DevOps, continuous integration (CI) plays a pivotal role in streamlining software development processes. Discover the essential tools that empower teams to automate builds, run tests efficiently, and integrate code seamlessly. From popular CI/CD platforms like Jenkins and GitLab CI to robust testing frameworks like Selenium and JUnit, this comprehensive guide dives deep into the tools that drive continuous integration in DevOps workflows.
Are you navigating the complexities of DevOps testing? Dive into our comprehensive guide on testing in DevOps, where we explore the critical role of continuous integration in ensuring software quality and reliability. Discover the latest tools and best practices that empower teams to automate testing, streamline workflows, and achieve faster, more reliable releases.
#devops#continuousintegration#ci#cd#softwaredevelopment#automation#testing#jenkins#gitlabci#selenium#junit#devopstesting#softwarequality#workflowautomation#releasemanagement#development#technology#innovation
0 notes
Text
Automate Home Lab Server Updates with GitLab CI CD
Automate Home Lab Server Updates with GitLab CI CD @vexpert #vmwarecommunities #devops #gitlab #linuxupdates #ubuntuupdates #automation #cicdpipeline #virtualization #homelab #homeserver #selfhosted #selfhosting #vhtforumsupdates #learneveryday
I recently wrote a blog post about replacing traditional Windows scheduled tasks with a CI/CD pipeline and the automation it provides. There are so many advantages to running something like Gitlab in your home lab to centralize your automation and help with bringing one-off scripts into source control with Git. I wanted to share with you guys a cool project I have been working on to bring my…

View On WordPress
0 notes
Text

Dive into the world of DevOps and CI/CD methodologies, uncovering the secrets behind swift and reliable software releases. Explore strategies for speed and dependability in this enlightening exploration of modern software development.
#devops#ci/cd#software development#releasemanagement#agile#automation#continuousintegration#deploymentpipeline#SoftwareReliability#devops strategies
0 notes
Text
5 Best Vulnerability Assessment Scanning Tools (May 2024)
New Post has been published on https://thedigitalinsider.com/5-best-vulnerability-assessment-scanning-tools-may-2024/
5 Best Vulnerability Assessment Scanning Tools (May 2024)
Proactively identifying and addressing vulnerabilities is crucial to protecting an organization’s digital assets. Vulnerability assessment scanning tools play a vital role in this process by automating the discovery and prioritization of security weaknesses across networks, systems, and applications. These tools help organizations stay one step ahead of potential threats by providing comprehensive visibility into their attack surface and enabling timely remediation of vulnerabilities.
In this article, we will explore some of the best vulnerability assessment scanning tools available, each offering unique features and capabilities to strengthen your cybersecurity posture.
[embedded content]
Tenable, a leading provider of cybersecurity solutions, offers Nessus, one of the most widely deployed vulnerability assessment scanners in the industry. With over 20 years of continuous development and improvement, Nessus has become a trusted tool for organizations of all sizes, known for its comprehensive scanning capabilities and flexibility.
Nessus leverages an extensive database of over 130,000 plugins to identify a wide range of security issues, including software vulnerabilities, misconfigurations, and compliance violations. This vast library of plugins, coupled with Nessus’s six-sigma accuracy, ensures that the scanner maintains a remarkably low false positive rate. Nessus’s flexible deployment options allow for scanning IT, cloud, mobile, IoT, and OT assets, providing comprehensive visibility across the attack surface. Whether deployed on-premises, in the cloud, or on a laptop for portable scanning, Nessus adapts to the unique needs of each organization.
Key features of Tenable Nessus include:
Comprehensive vulnerability scanning with over 130,000 plugins, covering a wide range of operating systems, devices, and applications
Six-sigma accuracy, ensuring a low false positive rate and reliable scan results
Flexible deployment options, including on-premises, cloud, or laptop, to accommodate various organizational requirements
Automated prioritization using the Vulnerability Priority Rating (VPR), which highlights the most critical issues for immediate remediation
Seamless integration with patch management, SIEM, and ticketing systems, enabling efficient vulnerability management workflows
Customizable reporting and dashboards for effective communication of vulnerability data to stakeholders
Invicti, formerly known as Netsparker, is an automated web application security scanner designed to help organizations continuously scan and secure their web applications and APIs. With a focus on accuracy and efficiency, Invicti enables security teams to scale their testing efforts while minimizing false positives, ensuring that resources are directed towards addressing genuine security risks.
One of Invicti’s standout features is its Proof-Based Scanning technology, which automatically verifies the exploitability of identified vulnerabilities. By safely exploiting vulnerabilities in a controlled manner, Invicti provides definitive proof of their existence, such as demonstrating the ability to retrieve a database name through SQL injection. This approach eliminates the need for manual verification, saving valuable time and effort for security teams.
Key features of Invicti include:
Comprehensive discovery and scanning of web assets, including modern web technologies like AJAX, RESTful services, and single-page applications
Support for scanning web applications, APIs (REST, SOAP, GraphQL), and web services, ensuring thorough coverage of the attack surface
Accurate vulnerability detection with Proof-Based Scanning technology, minimizing false positives and providing concrete evidence of exploitable issues
Automated verification and prioritization of vulnerabilities based on their risk level, enabling focus on the most critical issues
Integration with issue trackers, CI/CD pipelines, and collaboration tools, facilitating efficient remediation and collaboration between security and development teams
Detailed reporting for both technical and executive audiences, including actionable remediation guidance and compliance reports (PCI DSS, HIPAA, OWASP Top 10)
Nmap (Network Mapper) is a powerful open-source tool that has become an industry standard for network discovery and security auditing. With its versatility and extensive feature set, Nmap enables organizations to gain deep insights into their network infrastructure, identify potential vulnerabilities, and assess the overall security posture of their systems.
One of Nmap’s core strengths lies in its ability to perform comprehensive host discovery and port scanning. By leveraging various techniques, such as ICMP echo requests, TCP SYN scanning, and UDP probing, Nmap can efficiently identify active hosts and open ports on target systems. This information is crucial for understanding the attack surface and identifying potential entry points for attackers.
Key features of Nmap include:
Flexible host discovery options, including ICMP echo requests, TCP SYN/ACK scanning, and ARP scanning, to identify active hosts on a network
Comprehensive port scanning capabilities, supporting various scan types (TCP SYN, TCP connect, UDP, etc.) to determine open ports and associated services
Service and version detection, employing a vast database of over 1,000 well-known services to identify running applications and their versions
Advanced OS fingerprinting, analyzing the unique characteristics of network responses to determine the operating system and hardware details of target systems
Scriptable automation through the Nmap Scripting Engine (NSE), enabling customized scanning tasks and vulnerability detection using a wide range of pre-written scripts
Detailed output formats, including XML, grepable text, and normal text, facilitating integration with other tools and easy parsing of scan results
StackHawk is a modern dynamic application security testing (DAST) tool designed to seamlessly integrate into the software development lifecycle (SDLC). With a strong focus on developer enablement and automation, StackHawk empowers engineering teams to identify and remediate vulnerabilities early in the development process, promoting a shift-left approach to application security.
One of StackHawk’s key differentiators is its deep integration with CI/CD pipelines and developer workflows. By providing a simple configuration file and supporting popular CI/CD platforms like GitHub Actions, GitLab, Jenkins, and CircleCI, StackHawk enables automated security scanning as part of the regular build and deployment process. This integration allows developers to receive timely feedback on security issues and address them promptly.
Key features of StackHawk include:
Comprehensive scanning for OWASP Top 10 vulnerabilities, such as SQL Injection, Cross-Site Scripting (XSS), and more, ensuring coverage of critical security risks
Support for scanning REST APIs, GraphQL, and SOAP web services, enabling thorough testing of modern application architectures
Intelligent crawling and discovery of application endpoints, ensuring broad coverage of the attack surface
Seamless integration with popular CI/CD tools and source control platforms, enabling fully automated security testing in the development pipeline
Developer-friendly reports with detailed reproduction steps, including cURL commands, to facilitate efficient vulnerability remediation
Customizable scan configuration through a simple YAML file, allowing fine-grained control over scanning behavior and test parameters
Wiz is a cloud-native security platform that revolutionizes the way organizations secure their multi-cloud environments. With its agentless deployment and unified approach, Wiz provides comprehensive visibility and prioritized risk insights across the entire cloud stack, encompassing IaaS, PaaS, and SaaS services.
One of Wiz’s standout capabilities is its ability to analyze the full cloud stack and build a graph of all cloud resources and their relationships. By leveraging this Wiz Security Graph, the platform can identify complex attack paths and prioritize the most critical risks based on their potential impact. This contextual prioritization helps security teams focus on the issues that matter most, reducing alert fatigue and increasing remediation efficiency.
Key features of Wiz include:
Agentless deployment, connecting to cloud environments via APIs and providing rapid time-to-value without the need for agent installation
Comprehensive visibility across AWS, Azure, GCP, and Kubernetes, covering virtual machines, containers, serverless functions, and cloud services
Vulnerability assessment that spans the entire cloud estate, detecting OS and software flaws, misconfigurations, exposed secrets, IAM issues, and more
Prioritization of risks based on the Vulnerability Priority Rating (VPR), considering factors like severity, exploitability, and business impact
Contextual risk insights derived from the Wiz Security Graph, highlighting toxic combinations of risks that create attack paths
Integration with CI/CD tools, ticketing systems, and collaboration platforms to enable seamless remediation workflows and collaboration between security and development teams
Essential Components of a Cybersecurity Strategy
Vulnerability assessment scanning tools are essential components of a robust cybersecurity strategy, enabling organizations to proactively identify and mitigate vulnerabilities across their IT infrastructure. The tools featured in this article represent some of the best solutions available, each offering unique capabilities and benefits.
By leveraging these tools, organizations can gain comprehensive visibility into their attack surface, prioritize vulnerabilities based on risk, and integrate security seamlessly into their development workflows. As cyber threats continue to evolve, incorporating effective vulnerability assessment scanning tools into your security arsenal is crucial for staying ahead of potential breaches and maintaining a strong security posture.
#000#2024#agent#APIs#Application Security#applications#approach#Article#assessment#assets#Attack surface#attackers#automation#AWS#azure#Behavior#Best Of#Business#CI/CD#Cloud#Cloud-Native#Collaboration#collaboration tools#communication#compliance#comprehensive#concrete#Containers#continuous#continuous development
0 notes
Text
In the ever-evolving IT industry, where innovation is the heartbeat of progress, businesses are continually seeking avenues to enhance efficiency, reduce bottlenecks, and accelerate their development processes. One such groundbreaking methodology that has emerged as a beacon of transformative change is DevOps automation. As we embark on this journey of exploration, we will unravel the profound significance of DevOps automation in modern workflows, deciphering how it has become a linchpin for organizations striving to stay ahead in the dynamic landscape of IT.
The drumbeat of progress in technology is relentless, and organizations are under constant pressure to deliver solutions faster, more reliably, and with fewer errors. This is where DevOps automation takes center stage, orchestrating a symphony of streamlined operations, collaboration, and accelerated development cycles.
The term "DevOps" itself is a fusion of "Development" and "Operations," representing a cultural shift and a set of practices that aim to bring together previously siloed teams. At its core, DevOps seeks to break down the traditional barriers between development and operations, fostering a collaborative environment where teams work seamlessly towards common goals.
Read the full article here!
#devops#ci/cd#software engineering#software development#sdlc#technology#tech#automation#information technology
0 notes
Text
Release Management: Best Practices for Seamless Deployments
Unlock the secrets of seamless software releases with our in-depth guide on release management best practices - from version control to CI/CD, ensuring success in every deployment. #ReleaseManagement #SoftwareDeployment #CI_CD #AgileDevelopment
In the fast-paced and ever-evolving world of software development, embracing the power of efficient release management becomes paramount. It is the key that unlocks the doors to delivering exceptional, high-quality products on schedule, leaving a lasting impression on users. Release management encompasses a profound orchestration, entailing meticulous planning, seamless coordination, and diligent…

View On WordPress
#agile methodologies#agile practices#Ansible#automated testing#best practices#CI/CD#communication and collaboration#continuous deployment#continuous integration#deployment strategy#DevOps#documentation#environment management#feedback loop#Git#IaC#Infrastructure as code#monitoring metrics#post-release evaluation#Release management#rollback plan#software deployment#software development#software engineering#Terraform#version control
1 note
·
View note
Text
CI/CD practices have revolutionized the software development process by automating key aspects of building, testing, and deploying software, resulting in faster development cycles
#Devops#Devops Process#Automation Tool#Devops Practice#Software Development Practice#Software Development Lifecycle#Software Development Best Practice#Continuous Deployment#Continuous Integration#CI CD#CI CD Pipeline#CI CD Tools#Continuous Delivery
0 notes
Text

Yes, an IT support technician can transition into a DevOps engineer role with the right skills and training. While IT support technicians troubleshoot technical issues for users, DevOps engineers focus on automating processes and managing infrastructure through code. To make the transition, technicians need to learn about software development, CI/CD pipelines, configuration management, containerization, and cloud technologies. Gaining hands-on experience, pursuing certifications, and further education can help facilitate this career shift. With dedication and learning, an IT support technician can successfully become a DevOps engineer.
#ITsupport#DevOps#careertransition#automation#CI/CD#configurationmanagement#containerization#cloudtechnologies#skillsdevelopment#certifications#education#magistersign#support#onlinetraining
0 notes