#Cybersecurity Awareness Week
Explore tagged Tumblr posts
Text
Cybersecurity Analyst: Safeguarding the Digital Frontier - Who and what they do?
In today’s interconnected world, cybersecurity stands as an impenetrable shield against the relentless wave of cyber threats. At the forefront of this defense are Cybersecurity Analysts, skilled professionals who protect organizations and individuals from malicious attacks on their digital assets. This article delves into the responsibilities and significance of a Cybersecurity Analyst and…

View On WordPress
#Cloud Security#Cyber Attacks#Cyber Awareness#Cyber Awareness Training#Cyber Defense#Cyber Education#Cyber Forensics#Cyber Hygiene#Cyber Incident Response#Cyber Resilience#Cyber Risk Management#Cyber Threats#Cybersecurity#Cybersecurity Awareness Month#Cybersecurity Awareness Week#Cybersecurity Best Practices#Cybersecurity Careers#Cybersecurity Certifications#Cybersecurity Compliance#Cybersecurity Events#Cybersecurity Governance#Cybersecurity News#Cybersecurity Policies#Cybersecurity Solutions#Cybersecurity Tips#Cybersecurity Tools#Cybersecurity Trends#Cybersecurity Webinars#Data Breach#Data Privacy
1 note
·
View note
Text
clovenhooves.org registration process
There is some information on how to register here, and I am also explaining it in this post. The reason for this application system is to reduce the amount of trolls and people intending on using the forum in bad faith.
Please read the forum rules & guidelines. I'd like interested persons to feel like they can adhere to the rules. The guidelines are more suggestive.
Please read the cybersecurity guidelines to make sure you feel comfortable with making an account. I want to make sure people are aware of how to mitigate harm to themselves in the case of a database breach (which I have hopefully done enough security measures to avoid happening, but there is always some risk of hacking when it comes to websites).
Please check the membership application and see if you feel comfortable answering these questions. (Note: Your application will only be visible by yourself, trusted members, and admins. Once your application is accepted/rejected, only yourself and admins can look at it. This is in part to minimize copying of answers, we want people to answer honestly based on what they know, not based on what others have said.)
Create an account. Please read the "About Cloven Hooves" and "Registration Agreement" section and make sure you are good with it. Remember, you do not need to provide a real email address if you don't want to. But caution: a fake email address means I cannot help you recover your account if you lose your password.
Provide some info in the "Invite code/referral" section -- at least write "tumblr" since I assume you learned about it from here. :) If you are willing to share your tumblr username (assuming you have an active feminist blog), that would help speed along this step. (Note: this field and the "why are you interested in this forum?" are private and only visible to yourself and admins.)
Post your membership application in the "Pending Applications" forum.
Wait for your account to be accepted as a member, accepted as a learner, or rejected. If you are accepted as a member, you will be able to post anywhere on the forum. If you are accepted as a learner, you will be able to post questions and have discussions in "The Learning Channel". If you are rejected, you will not be able to post, so the same as a guest account. Learners and rejected people are welcome to reapply later on, probably within a few weeks/months. (Admins will not give detailed explanations on why an account has been marked as learner or rejected, as that could lead to gaming the system.)
Okay, that's all, yay!
(And when I refer to "people" throughout this post, I mean "women." Women are people. Female human beings. This is a feminist/woman-centered community.)
#radblr#terfblr#gender critical#gender critical feminism#radical feminism#radical feminists do touch#radical feminists please touch#radical feminist safe#radical feminist community#feminism#pro women#pro woman#feminist#radical feminists do interact
148 notes
·
View notes
Text




03.03.2025
Life is getting better.
After so many days in the hospital, my husband is very well, I am studying and exercising again... It feels like a rebirth 🐦🔥
I will start my new job this month, working with vulnerabilities (awareness, understanding root cases, extracting data from the management tools of the company, work closer to other internal Cybersecurity teams to help the department developers). I am not afraid, not because I am extremely courageous, but couldn't think about that until now 😄 the hospital situation was taking my whole time and effort.
I will continue my Ethical Hacker course with Cisco and started the AWS Cloud practitioner certification studies to get this one and the AI at least until July.
Thank God one phase is over! Let's to energize and go to the next one (a better one, I hope, 'cause I had enough hardcore mode in this first two months of 2025).
🌼 have a great week, guys!
#studyblr#study#study blog#daily life#dailymotivation#study motivation#studying#study space#productivity#study desk
31 notes
·
View notes
Text

PSA! THERE IS MALWARE ON YAYTEXT!
I'm not fully sure just how relevant this will be, but if anyone else uses yaytext to fancify their text with unicode, please be aware that there is now malware on the yaytext website ( yaytext.com ). it has been on there for at least a week now, so if you have gone onto the site, you might have been infected!
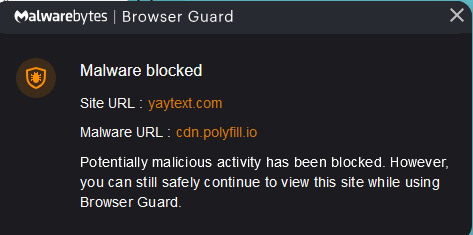
WHAT NOW? IF YOU HAVE VISITED YAYTEXT:
first, run a malware scan on your computer. you can do this for FREE with malwarebytes, bitdefender, or kaspersky*. you can find the free versions of these antivirus softwares on their respective websites, and I will link them below for convenience.
after you run the malware scan (hopefully you are not infected!), add the respective browser guard to your browser. as you can see by my screenshot, I use Malwarebytes' broswer guard. if you decide to use their browser guard too, you will still be able to safely use yaytext.
WHERE ELSE DO I GO?
you should assume that yaytext IS NOT safe to use for the time being! there are plenty of other unicode generators out there, however, so you don't have any disruption with your aesthetics.
some alternatives are:
fontspace font generator
lingojam text generator
fontalic
I have just checked all of these sites and none of them have malware on them at this time.
ANTIMALWARE SCANNING
MalwareBytes - free version BitDefender - free version Kaspersky* - free version
*note that Kaspersky is being banned in the U.S. for being a Russian company. The ban is over worries that Russia could use the AV as spyware in the U.S., because the Kremlin can force any company in Russia to share all of their data with them. Despite this, Kaspersky is a top contending cybersecurity research company. If you are not comfortable using Kaspersky, studies have shown that BitDefender provides near equivalent results. source: i am getting my degree in cybersecurity lol
74 notes
·
View notes
Note
what would your ideal trans girl rapist be like :3
textbook agp. antisocial freak. Discovered the /tttt forums at too young of an age. porn addicted since it had access to the internet. greasy frizzy hair and skinnyfat body. unwashed oversized hoodie with suspicious stains and crusty sleeves. terribly insecure and self deprecating while also being blatantly entitled and narcissistic, victim complex despite showing predatory patterns of behavior. attention seeker. fetishizes female pain and hopes it will be groped on a bus or be a victim of catcalling or assault because it thinks misogyny is somehow affirming- probably is envious that real girls get sexually harassed without even trying. or is straight up someone with aggressive rape fantasies from the violator perspective, not even feeling guilty about perpetuating the stereotype. cums thinking about nonconsenting pussy. watches rape porn and can’t get hard if it doesn’t feel authentic enough. probably has fantasies about force femming and molesting its past younger self. has spent several hours gooning to the cringiest most depraved hentai and animated western productions. has several callout posts calling it problematic. I prefer passing, or a twinkhon body type. androgynous in the sense that hrt has been in its system for awhile but they don’t wear makeup or have hyper-feminine clothes. I need a neet shut-in, or someone in tech/cybersecurity. diy hrt advocate. at least a few years worth of estrogen breast growth. ideally a micro dick which is still threatening but it would have to work to cause physical pain. self harm scars. both sadistic and masochistic tendencies. complete virgin and lacks any sexual or romantic experience with the exception of its circle of validating creeps online. rightfully earned guilt complex. knows who blanchard is. artist either with drawing or music. eyebags. suicidal and homocidal inclinations. jealously issues. has most of the symptoms of BPD but it stems from being a entitled and emotional and selfish person rather than any actual diagnosis. wears the same pairs of boxers or panties for several days and doesn’t see an issue with it. showers at a maximum once a week, maybe two if it decided to do a strenuous activity. politically intelligent except when it comes to TRA issues. knows too much about incel shootings, and incels in general. fat musky balls it forces my face into. chronically online, but that goes without saying. gingers are cute in all contexts including this one. soft small feet. anemic. low social awareness. sees me as stupid and lesser and treats me accordingly. delicate piano player fingers. chronic masturbator even in non sexual settings, practically uses genitalia as a stim toy. knows an absurd amount of niche pornography genres. fan of homestuck.
#I could go on#terfbreaking#transfem supremacy#transfem superiority#dykebreaking#mtf misgen#fakegirl#detrans kink#mtftm kink
34 notes
·
View notes
Text


Revamp on Miss Tuesday in the BTAS/TNBA Style
I basically wanted to try out how my interpretation of Miss Tuesday (or Ariadne Isychía as I’ve named her) would look and fit into both the BTAS and TNBA Universe.
I love both the statuesque style for some of the female characters in BTAS (Selina Kyle and Andrea Beaumont for ex.) and the Pin-Up style Bruce Timm did for TNBA, Justice League, Superman, and Batman Beyond!
So I wanted to practice both styles and incorporate it to Ariadne.
(I also made a new character sheet for her in my own art style! I made something similar to this chart a while back but I wasn’t happy with it so here we are! Especially now that I’m really liking how her hair looks now than before LOL )
MORE ABOUT HER BELOW ⬇️
QUICK DISCLAIMER: As I've stated before, this is a complete reinterpretation of Miss Tuesday and not from the original/canon character of her from Batman: The Audio Adventures
(This interpretation of her is practically an OC at this point as she’s become a completely different character who just has the “Miss Tuesday” alias/title)
ANYWAYS
My MT’s personality, background, and appearance are all mostly the opposite of her canon self in Batman: The Audio Adventures:
Tuesday’s relationship with Riddler in case anyone was curious- is strictly platonic, they’re pretty much besties for life and death, though in all seriousness they still have a professional relationship and view each other as intellectual equals who highly respect one another
Ariadne Isychía, or just Ari, is the full name I gave to this Miss Tuesday
As how she got the alias of “Miss Tuesday” is short but funny; so basically Edward asked her what day she was born in and in true Ari fashion, she responds with- “I was born on a Tuesday, specifically around 3:37am in Greek time, or 8:37pm Eastern Standard Time, sir.”, Edward smiled and said, “Perfect! Miss Tuesday it is!”
I gave her the name “Ariadne” because I wanted give a reference and nod to both Greek mythology (Ariadne was the Cretan Princess who helped Theseus defeat the Minotaur in the Labyrinth using her golden thread and later became the minor goddess of mazes and puzzles after marrying Dionysus) and Riddler’s BTAS debut episode: “If You’re So Smart, Why Aren’t You Rich?” (Where he created a game based off of the same legend called “Riddle of The Minotaur”)
Ari is a burnt out 36-year old former child prodigy with lower-needs Autism, and high functioning OCD
She was born in Athens, Greece but was raised in the U.S. (Gotham City to be more specific)
She graduated high school at the age of 12 and from Gotham University at 16 with a degree in Data Analytics and Cybersecurity
Before working for The Riddler, Ari was once a criminal analyst for the GCPD due to her father being a well respected officer at the time
Despite having a stable job at the time and a supportive father, she was beyond under stimulated with just doing the basics of hacking and analyzing to where she didn’t feel challenged enough nor was she really respected in the department either
So by the time Ari’s father retired and moved back to Athens, she decided to quit the GCPD and made her way to locate and track down Edward (no matter how much he tried to delete all of his information, Ari always found a way because she’s that smart and that good at her job), and managed to convince him to hire her as his assistant
Edward was both baffled and impressed at how talented she was in terms of cybersecurity and how she managed to recover ALL of his deleted information in less than a week that he hired her on the spot
Ari has the same type of dryness and nonchalance that the original Miss Tuesday from BTAA does, the difference is she isn’t always aware that when she’s being slightly apathetic or too blunt and doesn’t mean to be like that (social unawareness be like that sometimes)
Plus she’s more respectful towards Edward and refers to him as either “Mr. Nygma” or simply “Sir” instead of just calling him “Eddie” like in BTAA
Ari respects Edward so much that even though she knows she’s essentially smarter than him, she dims it down just to not hurt his ego
She has a fondness for Owls, she just thinks they’re neat. Edward and the other Rouges like to point that out to her mid-banter as they sometimes refer to her as “Owlet” or “Night Owl” since she has a tendency to stay up very late at night on the computer, and sometimes stares at people for way too long without blinking (she’s not always aware of it until Edward would tap her shoulder and asks her to knock it off, she can’t help it. It’s the ‘tism…)
#again remember this is a reinterpretation of miss tuesday and not from the original canon#my art#digital art#dc comics#dcu#rogues gallery#oc#oc art#miss tuesday#the riddler#BTAS#TNBA#character reinterpretation#character design
19 notes
·
View notes
Text

✨✨Sins of the Sub✨✨
(Abby Anderson x oc)
Abby stepped into the dorm's lobby, her heart racing as she checked her phone for the hundredth time. The glow of the screen reflected off her glasses, casting a blue hue over her cheeks. The message was clear: "Come over tonight." It had been a week since she last saw the girl with the piercing blue eyes, the one who made her knees wobble and her thoughts scatter like leaves in a storm. The anticipation had been building, a tight coil in her stomach that she could hardly contain.
The elevator dinged, and she stepped in, feeling a mix of excitement and nervousness. She knew her roommate, Jenny, was probably going to be there, studying as usual. They were two very different people, sharing a space that was too small for their clashing personalities. Jenny was butch, a no-nonsense woman who loved the structure of coding and the predictability of algorithms. Abby, on the other hand, was more of a free spirit, a sub nerd who loved to explore the uncharted waters of cybersecurity. But tonight, she had other things on her mind.
As she approached her door, she saw the silhouette of the girl she had been longing to kiss again, waiting outside. Before she could even insert her key, the girl stepped forward, her eyes locking onto Abby's with a hungry intensity. They collided into each other, their lips crashing together like waves against a shore. The girl's hands tangled in Abby's hair as they stumbled into the room, the door barely catching the frame before it swung shut behind them.
On the other side of the thin wall, Jenny's head snapped up from her textbook, a furrow forming between her brows. She had been deep in concentration, trying to decode the latest cryptographic challenge for her cybersecurity class. The sudden sound of passionate whispers and smacking lips was like nails on a chalkboard to her focused mind. With a sigh of frustration, she threw a pillow at the wall in their direction. It bounced off harmlessly, the sound muffled by the intensity of their embrace.
Abby, only partially aware of the disturbance, pulled away for a moment, her cheeks flushed and eyes glazed. She caught sight of Jenny, her roommate's expression a mix of shock and annoyance. The realization that they weren't alone hit her like a cold splash of water, and she felt a rush of embarrassment. But the desire that had been simmering inside her for days was too strong to be doused by a simple look. She leaned in for another kiss, her hand sliding around the girl's waist to pull her closer, ignoring the awkwardness of the situation.
Jenny's eyes narrowed as she slammed her book shut with a loud thud. "Seriously, Abby?" she called out, her voice a mix of anger and exasperation. "Can't you two keep it down? Some of us are trying to study here!"
Abby huffed, breaking the kiss but keeping her arms wrapped around the girl. She turned to face Jenny, her eyes flashing with a bit of irritation. "What's your problem?" she asked, her voice muffled by the girl's shoulder. "You're always holed up in here studying. Why don't you just go to the party?"
Jenny's jaw tightened as she picked up the pillow that had fallen to the floor. "Because, unlike some people, I have priorities," she shot back, her voice echoing the thump of her book. "And my scholarship doesn't pay for itself. Besides, it's not like you've ever invited me to any of those 'nerd parties' you and your friends have."
Abby's face grew redder as she realized she had been caught in the act. She had always wanted to seem cool and unflappable around this particular girl, the one who had captured her heart with a single glance at the university's hackathon. But now, she was just a mess of nerdy awkwardness, her glasses askew and her hair a wild tangle. She opened her mouth to respond, trying to come up with a smooth lie that would somehow salvage the situation, but the words that came out were a jumbled mess.
Her hookup, amused by the interruption, couldn't help but laugh, the sound a sweet melody that filled the room. She gently peeled Abby's arms from around her waist and took a step back. "Don't worry about it, Jenny," she said with a wink, her voice dripping with charm. "We'll keep it down. Promise."
Jenny's eyes narrowed as the girl sauntered closer, her confidence radiating like a force field. "What's your name, anyway?" she asked, her tone cool and collected.
"It's Luna," she replied, her smile not wavering. "But you can call me whatever you want, as long as you're smiling."
Jenny's eyes narrowed further, the unspoken challenge in her gaze. "I'm not really into... fems who top subs," she said, her voice low and steady. It was a clear line drawn in the sand, a declaration of her boundaries.
Luna looked from Jenny to Abby, a flicker of confusion crossing her features. "What's she talking about?" she whispered into Abby's ear, her breath warm and sweet.
Abby froze, her cheeks burning brighter than the neon lights of the arcade they had visited on their first date. She hadn't told Luna about her submissive side, not yet. It was something she had kept hidden, even from her closest friends. But now, in the stark light of their dorm room, with Jenny's accusatory glare boring into her, the truth was out there, and she couldn't take it back.
Luna pulled away, a puzzled expression clouding her features. "Abby, what's going on?" she asked, her voice a whisper of concern. "You said you were the one in control."
Abby's eyes darted to the floor, avoiding Luna's gaze. "It's complicated," she mumbled, her voice barely audible. The room felt smaller, the air thick with unspoken secrets and the weight of Jenny's judgmental stare.
Jenny, however, didn't miss a beat. She barked a laugh, loud and forced. "Oh, come on," she said, her voice dripping with feigned amusement. "I was just kidding. You know how I like to stir the pot." She winked at Luna, trying to play it off as a joke. "I'm the one who's always in control, not her. She's just too much of a goody-two-shoes to admit it."
Luna's eyes lit up with curiosity, and she took the bait, turning her attention to Jenny. "Really?" she asked, tilting her head to the side. "I never would've guessed that."
Jenny shrugged, her lips curling into a smug smile. "It's all about keeping things interesting," she said, her voice dropping an octave as she took a step closer to Luna. "You know, a little bit of give and take."
Her eyes flicked to Abby, who was still standing there, looking like she wanted to melt into the floor. With a quick mental pivot, Jenny decided that maybe she could use this to her advantage. If she could keep Luna's focus on her, maybe it would give Abby some space to get her thoughts in order. "So, what do you say, Luna?" she asked, leaning against the wall. "Want to take a break from the sub-dom scene and see what it's like to be with someone who knows the real power of a good code?"
Before Abby could react, Luna stepped closer to Jenny, her gaze intense. "Is that a challenge?" she asked, a glint in her eye. Jenny felt a thrill run through her as she realized she might have found someone who could match her, someone who understood the thrill of the chase and the allure of power.
Without waiting for a response, Luna leaned in and kissed Jenny, her lips demanding and unyielding. Jenny's initial surprise was quickly replaced by a surge of excitement. It was a bold move, one that she hadn't seen coming. But as she kissed Luna back, she felt the power shift in the room. Her hand slid up to cup Luna's cheek, her thumb tracing the line of her jaw as she took control of the kiss. It was a dance, a silent negotiation of dominance and submission that played out between them in a heartbeat.
Abby watched, stunned, as the scene unfolded before her. She felt like an intruder in her own space, a forgotten character in a play she had written herself. Her eyes darted between the two women, their bodies now pressed tightly together, the sparks flying between them palpable. It was mesmerizing and terrifying all at once.
As Jenny's hand came up to cup Luna's cheek, Abby saw the faintest glimpse of something she had never seen before in Jenny's eyes—fear, perhaps? But it was quickly replaced with a look of determination as Jenny stepped back, breaking the kiss. "I'll leave you two to it," she said, her voice steady despite the heat in her gaze. "But remember, Abby,
I'm always watching."

#abby anderson x female reader#sub abby anderson#abby smut#abby the last of us#nerdabby#owen hater#fuck owen#abby is not straight
11 notes
·
View notes
Text
Olivia Troye at Living It With Olivia:
During my time on the National Security Council (NSC) staff, while serving as Homeland Security and Counterterrorism Advisor to Vice President Mike Pence, I saw firsthand how vital the NSC is to the safety and stability of our nation. However, my relationship with the NSC didn’t begin there. I’ve worked closely with it throughout my career, starting in the early 2000s. Over the years, I’ve witnessed some of the most skilled, dedicated public servants in government walk those halls. It used to be that serving on the NSC staff was one of the highest honors in public service, a role reserved for the best of the best. The level of expertise was once unmatched. Regional specialists, career diplomats, intelligence professionals, military strategists, and legal and economic minds all worked in concert to ensure the President and Vice President were informed by real facts, grounded analysis, and strategic foresight. That's what the NSC was built for: to coordinate, not politicize; to unify, not divide; to protect, not perform. Now? That integrity is being gutted in real-time. According to CNN, over 100 NSC staffers were placed on administrative leave late last week. Many of them are career professionals who have served under multiple administrations. They're being pushed out and replaced by political loyalists who lack even the most basic qualifications for the roles they now occupy. This isn’t a restructuring. It’s a purge. And it will cost us.
What the NSC Actually Does
The National Security Council serves as the strategic hub of the American government during times of calm and crisis. It is the only entity designed to cut across every major department, ensuring unity of effort, speed of action, and clarity of purpose.
It:
Coordinates interagency policy across Defense, State, Homeland Security, Treasury, Energy, Justice, Commerce, HHS, and beyond.
Synthesizes intelligence and threat assessments from across the Intelligence Community.
Develops strategies on defense, foreign affairs, cybersecurity, disinformation, migration, terrorism, and disaster response.
Prepares and provides real-time situational awareness.
Guides diplomatic and military posture, manages crisis response and ensures continuity of government.
Tracks and responds to foreign and domestic threats to American lives and institutions.
The NSC doesn't just manage information; it orchestrates it. When it functions as designed, it gives America the ability to respond quickly, wisely, and proportionately. But strip out the expertise, and you're left with noise, dysfunction, and delayed decisions in moments that demand precision. Experience in national security can’t be faked. It’s forged in classified briefings, deployments, war rooms, and interagency planning sessions. The professionals who staff the NSC bring decades of institutional memory, regional knowledge, and cross-sector understanding. That matters. You cannot improvise your way through a missile launch alert. You cannot “wing it” through a global pandemic. I saw the cost of that firsthand. When COVID-19 struck, the coordination process was ignored, the experts were sidelined, and the federal response fragmented. People died who didn’t have to. That is what happens when the NSC is sidelined. And now, it’s happening again, with even fewer guardrails.
The Hypocrisy of the “Deep State” Narrative
And then there’s Marco Rubio. It’s rich to hear him claim it’s Trump vs. the “deep state.” Because I remember precisely what Rubio did during Trump’s first term: he hand-picked NSC senior directors for the Western Hemisphere because he wanted control over Cuba and Venezuela policy. Not based on merit. Not based on qualifications. Based on politics. [...] A newly declassified U.S. intelligence memo contradicted Trump’s latest fearmongering about Venezuela. It clearly states that President Nicolás Maduro is not directing Tren de Aragua, the criminal gang Trump claims is “invading” the U.S. This lie isn’t just baseless, it’s dangerous. It was crafted to stoke fear and justify extremist policies. And when professionals inside the government speak up to correct it, they’re smeared and silenced.
The National Security Council (NSC) is under major attack by the Trump Regime.
See Also:
MMFA: An intelligence report debunked MAGA media claims about Tren de Aragua and Venezuela. A Trump official is now under fire for reportedly ordering the report be redone.
#National Security Council#NSC#National Security#Nicolás Maduro#Tren de Aragua#Marco Rubio#Counterterrorism
5 notes
·
View notes
Text
It’s Cybersecurity Awareness Month
🚨🔥💦 WELCOME TO COCKTOBER, YOU TECH FREAK—CYBERSECURITY AWARENESS MONTH, WHERE YOUR BACKDOOR BETTER BE LOCKED UP TIGHT AS HELL OR YOU'RE ABOUT TO GET SLAMMED HARD! 🍑💻💦🔥🚨
IF YOU’RE LEAVING THAT BACKDOOR SWINGING WIDE OPEN 💻🍑, YOU’RE BASICALLY BEGGING FOR EVERY HACKER FROM RUSSIA 🇷🇺, CHINA 🇨🇳, AND EVERY CREEPY DUDE WITH A LAPTOP 💻 TO COME TEARING INTO YOUR FILES 💦🍆—STRAP UP THAT CYBERSECURITY LIKE YOU’RE STRAPPING INTO YOUR FAVORITE TOY! 🍆💥 IF YOU DON’T, YOU'RE GONNA GET FUCKED SO HARD YOUR COMPUTER WON’T BE ABLE TO BOOT UP WITHOUT BLUSHING 😏💻💦!
STEP 1️⃣: IF YOUR PASSWORD IS STILL "PASSWORD123," YOU’RE BASICALLY LYING SPREAD-EAGLE FOR EVERY HACKER ON THE WEB 😤🚫💦! YOU NEED A PASSWORD THAT’S AS NASTY AND STRONG AS YOUR WILDEST FANTASY 💦🛌—TRY "TH1CKD@D69!" 💋🔥 OR "H@RDCORETHRUST69!" 🍆🍑💦! MAKE THAT SHIT SO STRONG IT’LL LEAVE EVERY HACKER BLUE-BALLED!
STEP 2️⃣: TURN ON TWO-FACTOR AUTH 🔑📲—THAT’S LIKE THROWING TWO CONDOMS ON BEFORE YOU LET ANYTHING IN! 💦🍑💻 DOUBLE-BAG THAT SHIT, ‘CAUSE YOU DON’T WANT SOME NASTY RANSOMWARE SNEAKING INTO YOUR HARD DRIVE 🍆💣! DON’T LET THEM RAW-DOG YOUR FILES—LOCK THAT SHIT DOWN 🔒💻!
STEP 3️⃣: QUIT CLICKING ON "LOCAL MILFS WANNA FUCK NOW" 👵🍑 AND "FREE SEXY iPHONES" 📱💦—THAT SHIT WILL FUCK YOU OVER FASTER THAN A DRUNK VEGAS HOOKUP! YOU THINK YOU’RE GONNA SCORE BIG 💦💸, BUT ALL YOU'LL GET IS A NASTY VIRUS THAT’LL LEAVE YOUR HARD DRIVE PUKING! 💻🤢💣
FORWARD THIS FILTHY MESSAGE TO 10 FRIENDS OR YOU’LL GET YOUR FILES TAKEN SO HARD, YOU WON’T BE ABLE TO SIT STRAIGHT FOR A WEEK! 😭📂💔💦🔥
9 notes
·
View notes
Text
Germany's upper house of parliament on Friday approved a landmark easing of the country's debt limit, paving the way for increased defence spending and a €500 billion ($547 billion) financial package for infrastructure and climate initiatives.
The step secured the required two-thirds majority in the upper house, the Bundesrat, following a similar vote in the Bundestag, Germany's lower house of parliament, earlier in the week.
The measure now awaits review and formal approval by German President Frank-Walter Steinmeier.
The amendment received 53 out of 69 votes in the Bundesrat, surpassing the 46-vote threshold. The states of Brandenburg, Saxony-Anhalt, Thuringia and Rhineland-Palatinate abstained, with abstentions counted as opposition votes.
The move relaxes Germany's constitutionally-enshrined debt brake, which sets strict limits on government spending, for defence, civil protection, intelligence and cybersecurity. Any such expenditures exceeding 1% of Germany's gross domestic product (GDP) can now be financed with new debt.
Additionally, a special fund exempt from the debt brake is to be established and filled with up to €500 billion in loans. The fund is to be used to finance the repair of Germany's ailing infrastructure, with €100 billion allocated to federal states and another €100 billion earmarked for climate protection measures and the transition to greener forms of energy.
Merz defends fast-tracked vote
Conservative leader Friedrich Merz, the country's presumptive next chancellor, had rushed the vote through in the outgoing parliament, anticipating greater challenges in securing support once newly elected lawmakers take office next week.
Merz on Friday defended his decision, stressing the need for swift action in light of geopolitical and security challenges, including the ongoing war in Ukraine and US policy shifts.
Speaking in Frankfurt, he acknowledged criticism, including from within his own party, and said he was aware that he was taking a political risk, also in terms of his personal credibility.
The amendment represents a massive about-face for Merz, who had previously railed against deficit spending.
Politicians call for quick steps
"Historic times call for historic measures," said Bavarian Premier Markus Söder, describing the amendment as an opportunity to establish a protective shield. He emphasized that this was only the first step, insisting that investment, consolidation, and reforms must now follow.
Saarland Premier Anke Rehlinger, who is also currently serving as the Bundesrat president, echoed his call for a quick implementation of the newly approved investments, saying "money alone won’t solve the fundamental challenges."
#nunyas news#they can blame the inflation this triggers#on trump so why wouldn't they do it#germany increasing military spending#has never gone well for the world
5 notes
·
View notes
Text
U.S. adversaries are likely to try to undermine confidence in the outcome of the upcoming presidential election, stoke unrest, and boost their preferred candidates even after polls close on Nov. 5, according to a newly declassified assessment released by the Office of the Director of National Intelligence (ODNI) on Tuesday.
“Iran and Russia are probably willing to at least consider tactics that could foment or contribute to violent protests, and may threaten, or amplify threats of, physical violence,” according to the assessment, which was prepared on Oct. 8.
The seven-page memorandum also says Tehran’s efforts to assassinate former President Donald Trump and other former U.S. officials are likely to persist after Election Day regardless of the result.
Foreign governments, most notably China, Iran, and Russia, are better positioned now than in previous elections to exploit opportunities to sow chaos in the days and weeks after the vote, having drawn important lessons from the 2020 presidential election, which was marked by a drawn-out count and efforts by Trump and his allies to challenge the results.
“Many of these countries did not have a full appreciation for the various election processes that happen after polls close, and now that they have greater awareness of the significance, they have greater ability to attempt to disrupt them,” an ODNI official said in a call with reporters on Tuesday.
In December 2020, Iranian cyberactors were believed to have been behind the creation of a website called “Enemies of the People” that contained death threats against U.S. election officials, according to previous notices released by the FBI. Iranian actors also published personally identifiable information about U.S. officials in a bid to incite violence.
According to the ODNI memo, foreign adversaries are likely to use well-honed tools such as online influence operations, including “potentially physical threats or violence” in the wake of what is expected to be one of the most closely contested U.S. elections in living memory.
Intelligence officials have issued routine warnings in recent months that Beijing, Moscow, and Tehran are working to sow division and undermine confidence in the integrity of the election—efforts that are likely to accelerate in the waning days of the campaign, particularly on social media, the ODNI official said.
The official noted that recent intelligence indicated that Moscow was likely behind a recent unevidenced claim circulating on social media and amplified by conservative influencers that Democratic vice presidential candidate Tim Walz assaulted a former student earlier in his career.
U.S. intelligence believes that while foreign adversaries likely have the technical capability to access some U.S. election-related networks and systems, they are unlikely to try to interfere with the tallying of votes out of concern that it could prompt Washington to retaliate.
An official from the Cybersecurity and Infrastructure Security Agency said the highly decentralized nature of the election system as well as the widespread use of paper ballots and the fact that voting machines are not connected to the internet made it highly unlikely that a foreign power could manipulate the vote at scale without being detected.
Intelligence officials have long singled out China, Iran, and Russia as most actively engaged in efforts to sway U.S. elections, but the countries have different intentions in doing so. With both Democrats and Republicans in Washington staking out a hawkish line on China, Beijing has sought to focus its efforts on down-ballot races at the state and local levels that it perceives to be in its interests.
Tehran has sought to undermine the Trump campaign, with three Iranians recently indicted by the Justice Department for hacking into the email accounts of campaign officials.
Russia presents the most active foreign influence threat to the election, the ODNI official said, and is likely to be “more aggressive” in its efforts to sow chaos should Vice President Kamala Harris win, noting Moscow’s preference for a second Trump presidency.
11 notes
·
View notes
Text
Weekly Cybersecurity News Roundup | 03 Feb - 09 Feb 2025
Last week's cybersecurity news revealed key trends in malware targeting, critical flaws, supply chains, and ransomware:
Coyote malware expanded its targeting of financial institutions.
Critical flaws in AMD hardware and the Linux kernel are actively exploited.
Supply chain threats continue to grow, impacting Python and Go ecosystems.
Ransomware payments fell by 35%, showing increasing resistance to cybercriminal extortion.
𝗧𝗼𝗽 𝗡𝗲𝘄𝘀:
1️⃣ 𝗖𝗼𝗬𝗢𝗧𝗘 𝗠𝗮𝗹𝘄𝗮𝗿𝗲 𝗘𝘅𝗽𝗮𝗻𝗱𝘀 𝗥𝗲𝗮𝗰𝗵 Coyote malware now targets over 1,000 websites and 73 financial institutions. Source: https://www.fortinet.com/blog/threat-research/coyote-banking-trojan-a-stealthy-attack-via-lnk-files
2️⃣ 𝗣𝗼𝗶𝘀𝗼𝗻𝗲𝗱 𝗚𝗼 𝗣𝗿𝗼𝗴𝗿𝗮𝗺𝗺𝗶𝗻𝗴 𝗟𝗮𝗻𝗴𝘂𝗮𝗴𝗲 𝗨𝗻𝗱𝗲𝘁𝗲𝗰𝘁𝗲𝗱 𝗙𝗼𝗿 𝟯 𝗬𝗲𝗮𝗿𝘀 A backdoored typosquat of BoltDB in the Go ecosystem exploited Go Module Proxy caching for three years. Source: https://socket.dev/blog/malicious-package-exploits-go-module-proxy-caching-for-persistence
3️⃣ 𝗥𝗮𝗻𝘀𝗼𝗺𝘄𝗮𝗿𝗲 𝗣𝗮𝘆𝗺𝗲𝗻𝘁𝘀 𝗙𝗲𝗹𝗹 𝗯𝘆 𝟯𝟱% 𝗶𝗻 𝟮𝟬𝟮𝟰 Ransomware payments dropped 35% in 2024 while attackers adapted with faster, rebranded strains. Source: https://www.chainalysis.com/blog/crypto-crime-ransomware-victim-extortion-2025/
4️⃣ 𝗔𝗠𝗗 𝗦𝗘𝗩-𝗦𝗡𝗣 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗶𝗹𝗶𝘁𝘆 A critical flaw in AMD SEV-SNP could enable microcode injection by an attacker with administrative privileges. Source: https://thehackernews.com/2025/02/amd-sev-snp-vulnerability-allows.html
5️⃣ 𝟳𝟲𝟴 𝗖𝗩𝗘𝘀 𝗘𝘅𝗽𝗹𝗼𝗶𝘁𝗲𝗱 𝗶𝗻 𝟮𝟬𝟮𝟰 The number of CVEs exploited in 2024 increased by 20%. Source: https://vulncheck.com/blog/2024-exploitation-trends
𝗛𝗼𝗻𝗼𝗿𝗮𝗯𝗹𝗲 𝗠𝗲𝗻𝘁𝗶𝗼𝗻𝘀:
🟢 𝗣𝘆𝗣𝗜 𝗜𝗻𝘁𝗿𝗼𝗱𝘂𝗰𝗲𝘀 𝗔𝗿𝗰𝗵𝗶𝘃𝗮𝗹 𝗦𝘁𝗮𝘁𝘂𝘀 PyPI now labels unmaintained Python packages with an archival status, aiming to improve developer awareness and mitigate risks. Source: https://blog.pypi.org/posts/2025-01-30-archival/
🟠 𝗢𝗖𝗥 𝗖𝗿𝘆𝗽𝘁𝗼 𝗦𝘁𝗲𝗮𝗹𝗲𝗿 Malicious apps in both Google Play and the App Store use OCR to extract cryptocurrency from users. Source: https://securelist.com/sparkcat-stealer-in-app-store-and-google-play/115385/
🔴 𝗠𝗶𝗰𝗿𝗼𝘀𝗼𝗳𝘁 𝗜𝗱𝗲𝗻𝘁𝗶𝗳𝗶𝗲𝘀 𝟯,𝟬𝟬𝟬 𝗟𝗲𝗮𝗸𝗲𝗱 𝗔𝗦𝗣.𝗡𝗘𝗧 𝗞𝗲𝘆𝘀 Microsoft found attackers exploiting publicly disclosed ASP.NET keys for ViewState code injection. Source: https://www.microsoft.com/en-us/security/blog/2025/02/06/code-injection-attacks-using-publicly-disclosed-asp-net-machine-keys/
3 notes
·
View notes
Text
Cybersecurity Lab Game
Hey everyone! Welcome back to the blog. Today, I had the opportunity to dive into the Nova Cybersecurity Lab Game, which was an eye-opening experience. This interactive game puts you in the shoes of a cybersecurity expert tasked with protecting a company from cyber threats. It focuses on aspects like identifying phishing attempts, managing software updates, and securing sensitive information.

Here's a picture of the challenges that had to be done to gain more coins for the defence against cyber-attacks. There were 3 levels, and with each, they became more complex with additional coding puzzles, diverse threat scenarios, and advanced encryption techniques, demanding more sophisticated strategies and problem-solving skills.
One key takeaway was the importance of vigilance and proactive measures in cybersecurity. The game shows how cyber threats exploit human errors, like falling for phishing scams or neglecting updates. It highlights the need for ongoing education and awareness to recognize and counter these threats effectively.

Above is another image that demonstrates a successful cyber defense against an attack which resulted in no loss of users.
Challenges
The password challenge was particularly interesting. It gave me a deeper understanding of the tricks hackers use to crack passwords, such as brute force attacks. This challenge highlighted the necessity of creating strong, unique passwords and using multi-factor authentication to prevent unauthorized access.
Additionally, the coding challenge was enlightening. They demonstrated how codes and virtual mazes can be designed to keep hackers from accessing vital information, allowing only authorized personnel to navigate these defenses. This reinforced the importance of robust security protocols in protecting sensitive data.

The image above showcases a Level 2 coding challenge, illustrating the complexity of the code involved.
Overall, I found the Nova Cybersecurity Lab Game to be a great way to learn about cybersecurity. It gives practical tips on protecting digital assets, which is very helpful in today’s ever-changing digital world. Hope you enjoyed today's post and see you next week!
3 notes
·
View notes
Text
Whether it is for your small business, a larger corporation, or even your own personal data, securing information on computers or in the cloud is becoming a modern challenge. And with that said, the value of information security is increasing; global corporations have suffered major data breaches in recent years and it’s increased the demand for data security specialists. Online security measures continue to evolve so it is important for those in the field to stay on top of current trends and security methods. Every company needs to ensure confidentiality and integrity with their customers; by keeping track of these ten websites, you can say that you’re up to date and learning the most you can about information security. Wombat Security Blog One of the best ways to learn is from professionals. Wombat Security Technologies’ blog offers a large base of articles that discuss risk management, security training, and cyber threats. Their blog focuses on increasing awareness of new ways that digital security can be exploited as well as discussing best practice strategies. Of note, they offer information for novices as well as more experienced technicians. If you’re looking for a general comprehensive place to learn about information technology, Wombat’s blog can be a great first step. Errata Security Blog Security researchers who have vast experience in the field manage Errata Security Blog. With that comes a well-rounded understanding of current events in cybersecurity as well as a highly opinionated perspective on the best practices in the field. The articles that you’ll find on Errata are in-depth, personable, and unafraid to discuss the grey areas of online ethics. Their article “You are committing a crime right now” from several years ago is a great look into their personality and what you can expect from Errata’s articles. Kaspersky Lab Threatpost Kaspersky Lab Threatpost is a website which supplies daily videos, articles, and podcasts that cover information security from a variety of different angles. They also have a section of their site that focuses on mobile security – an issue that’s becoming more pressing as people have taken to storing personal and corporate information on their mobile devices. The publication focuses on recent online attacks and threats and provides a large amount of weekly content. By reading Kaspersky, you will keep up to date on current cyber attacks, how the attacks were committed, and how larger companies like Apple and Google are fighting back to defend their customers against cyber threats. Security Boulevard Security Boulevard covers information security in a myriad of different ways – from security analytics and cloud monitoring to current threats and the responses cybersecurity experts take in response to those threats. You can almost think of Security Boulevard as a database of cybersecurity information. and crossroads for information in information security. Naked Security Blog Naked Security is run by the data protection company Sophos and publishes daily articles that cover a wide variety of security topics. Some focus on recent security events while others will cover well-known websites and cultural items like Amazon Alexa. They also round up popular stories of the week and current threats that can affect firms and their employees. They’re a great source for news that covers a wide range of topics. No matter if you’re looking for cloud news or protecting a mobile site, Naked Security will have something to teach you. Security Weekly If you’re looking for a unique format and style, Security Weekly publishes webcasts and interviews on their site that specifically cover business security. They do some live streams as well. This is a great alternative for those who enjoy learning more visually. It’s also a fantastic format as more people are listening to podcasts than ever before. Security Weekly has a very clear identity and makes it easy to learn as you listen. The Akamai Blog Akamai
is an internet technology company that specializes in cloud security and also offers things like DDoS defense. Their blog - The Akamai Blog - is written by professional analysts with vast experience of working with large organizations and enterprises. It focuses on data protection, cloud security, and enterprise security. The blog provides a distinctive perspective on attacks that end up compromising websites. More so, it is well-known for giving a detailed outlook on how attacks can bring down a site. The Security Ledger The Security Ledger, being an independent provider of news, publishes day-to-day content on latest news updates and events in online security. They have an entire section to discuss the most discussed current events in security. On top of that, the Ledger also produces podcasts, collects whitepapers, and features opinion pieces that delve into ethics and best practices within the industry. Graham Cluley Graham Cluley is a long time security analyst as well and public speaker who also authors his own blog. His blog features self-written posts, podcasts, and commentary on hacking and current events. He also offers a newsletter that gives easy tips and tricks of the trade. It’s a great mobile resource that can help you learn on the run. Brian Krebs Did you know about the Bitcoin bug on Overstock.com? Brian Krebs is an investigative journalist who specializes in information technology and reporting on such issues is right up his alley. Using his connections and expertise in the security field, he provides research to write content that major publications miss. His website focuses on hacks, bugs, and data breaches. Getting up to speed on information security can be a difficult challenge at times. It’s not the most intuitive field and requires a constant effort to stay on top of trends and challenges to remain effective. Having several resources on hand to listen to professionals will certainly help. If you’re just getting started in internet technology, it is always a good idea to start with some general information before honing in on a specialty. And with that in mind, these ten sites cover all of that information and more, allowing you to continue to learn and become a force within the field. Valerie Cox is a contributing author for TeamLogic.
0 notes
Text
Hindi News Digest: Big Stories from All Sectors
In the ever-evolving landscape of news, staying informed is not just a habit—it's a necessity. At Amar Sandesh, we bring you the most important updates from across all sectors, ensuring you are never out of touch with what matters. From the heated corridors of politics to the thrilling fields of sports, from shifting economic tides to cultural milestones, here's your comprehensive Hindi News Digest.
Politics: A Season of Shifts and Strategies
Indian politics never sees a dull moment. Over the past few weeks, political dynamics have taken new turns, with regional powerhouses making headlines alongside national parties. Recent state assembly sessions have been buzzing with debates on development schemes, farmer welfare, and women’s safety, drawing strong reactions from both the ruling parties and the opposition.
The Parliament too saw robust discussions on the new education and health policies. Key political figures have launched campaigns in anticipation of upcoming elections, and alliances are being reshaped. At Amar Sandesh, we provide not just the news, but a breakdown of its implications—what it means for the common man and for India’s future.
Sports: Records, Rivalries, and Rising Stars
India’s sports scene has been electrifying. The Indian Premier League (IPL) continues to dominate headlines, with surprising upsets and remarkable performances keeping fans glued to their screens. Young cricketers are proving their mettle, and veterans are showcasing unmatched resilience. Meanwhile, preparations for the Paris Olympics are in full swing, with Indian athletes training hard and earning accolades in qualifiers across wrestling, shooting, and athletics.
Off the field, sports governance is also a hot topic, with new policies aiming to streamline funding and training support for athletes. At Amar Sandesh, we celebrate every goal, every run, and every medal—because every sporting story is a story of human spirit.
Economy: Recoveries, Reforms, and Reality Checks
India’s economy is showing signs of recovery post-pandemic, but the journey is far from over. Inflation remains a concern, especially with rising fuel and food prices affecting everyday lives. However, industrial output has improved, and sectors like technology, manufacturing, and pharmaceuticals are posting strong numbers.
The government has introduced several reform measures targeting MSMEs, startups, and digital commerce. Initiatives like “Make in India” and “Digital India” continue to attract global attention. Our economy coverage at Amar Sandesh focuses on explaining complex trends in simple terms—because financial literacy is for everyone, not just economists.
Technology: India’s Digital Pulse
India's tech sector is booming with innovations in artificial intelligence, fintech, and space research. The recent successful launch of satellites under ISRO’s new missions has once again positioned India as a rising star in space technology. Startups across Bengaluru, Hyderabad, and Gurugram are raising funds and disrupting industries ranging from healthcare to education.
Cybersecurity remains a key area of concern, with several state governments launching digital awareness programs to combat online fraud and data breaches. Amar Sandesh brings these tech stories in Hindi, breaking down jargon and highlighting how technology is reshaping our daily lives.
Culture and Entertainment: A Blend of Tradition and Trends
India’s cultural landscape remains as vibrant as ever. From film releases to music festivals and art exhibitions, the entertainment industry has bounced back post-pandemic. Bollywood is witnessing a revival with several Hindi films performing well both domestically and internationally. OTT platforms continue to offer diverse content in Hindi and regional languages, opening up new avenues for artists and storytellers.
Traditional festivals like Holi and Baisakhi were celebrated with great fervor this year, highlighting India’s rich heritage. At Amar Sandesh, we cover not just celebrity updates but also grassroots cultural movements, folk art, and literature—because every voice matters in the story of India.
Social Issues: Voices Rising, Change in Motion
Across the country, people are speaking up on issues that matter. From protests for better education facilities in rural areas to campaigns against child labor and gender discrimination, citizens are increasingly engaged and active. Non-governmental organizations and youth-led initiatives are playing a crucial role in driving awareness and action.
Amar Sandesh believes in giving space to these voices. Our social coverage focuses on people-centric stories—real problems, real heroes, and real change. Because news isn’t just about what’s happening in high places, but also in the heart of every community.
Global Affairs: India on the World Stage
India’s role on the global platform is growing. Be it in climate change dialogues, global trade discussions, or peacekeeping missions, the country is taking on greater responsibilities. Recent international visits by Indian leaders have opened new doors in diplomacy, trade, and technology partnerships.
Geopolitical tensions and global economic shifts also influence life here at home. At Amar Sandesh, we offer a global perspective in Hindi, ensuring our readers understand how world events affect India and vice versa.
In Conclusion
In a world where news is everywhere but clarity is rare, Amar Sandesh stands for trustworthy, in-depth, and balanced journalism. Our Today news in hindi isn’t just a summary—it’s a curated window into India’s heartbeat across sectors.
Stay informed. Stay empowered. Stay connected with Amar Sandesh—your voice, your news, your India.

0 notes
Text
Decision Pulse in Cybersecurity: Making Quick and Informed Tech Choices
In today’s ever-evolving digital landscape, cybersecurity is not just a technical challenge—it’s a strategic imperative. With threats becoming more sophisticated and regulations constantly shifting, decision-makers in IT and security are under pressure to act fast. Yet, speed without insight is risky. That’s where Decision Pulse by OfficeSolution steps in—an intelligent framework for making rapid, well-informed technology decisions in cybersecurity.
Why Quick Decisions Matter More Than Ever
In cybersecurity, timing is everything. A delayed response to a breach or vulnerability can result in significant financial and reputational damage. The traditional decision-making cycle—long meetings, endless vendor comparisons, manual risk assessments—can no longer keep pace with today’s threats. Enterprises need a system that enables decisive action without sacrificing due diligence.
Enter Decision Pulse: Speed + Intelligence
Decision Pulse, hosted at https://decisionpulsegenai.com, is OfficeSolution’s AI-driven approach to tech decision-making. It blends data intelligence, real-time threat analysis, and contextual business priorities to streamline cybersecurity decisions.
Whether you’re selecting a new endpoint protection platform, assessing a cloud security posture, or prioritizing patch management, Decision Pulse helps cut through the noise. It uses generative AI to quickly synthesize vast data inputs—threat feeds, compliance requirements, and product benchmarks—into concise, actionable insights.
Making Smarter Tech Choices
Here’s how Decision Pulse enhances decision-making in cybersecurity:
Data-Driven Insights: Leverages current threat intelligence and historical incident data to provide context-aware recommendations.
Vendor Agnostic Analysis: Helps you evaluate solutions based on performance, integration potential, and risk—not just brand.
Scenario Simulation: Models the impact of different decisions on your security posture, budget, and compliance metrics.
Collaborative Dashboards: Aligns CISOs, CIOs, and operational teams with a shared view of priorities and trade-offs.
Real-Time Decisions with Reduced Risk
With Decision Pulse, businesses gain the agility to respond to threats without compromising on security posture. Whether it’s a zero-day exploit or a regulatory deadline, the system empowers teams to act swiftly while maintaining control over outcomes.
In a recent implementation, one client used Decision Pulse to identify and deploy a secure access solution within 48 hours—compressing a process that usually takes weeks. The result? Mitigated access risk and no downtime.
The Future of Cybersecurity Decision-Making
As the threat landscape grows more complex, the ability to make informed, rapid decisions becomes a competitive advantage. OfficeSolution’s Decision Pulse bridges the gap between speed and strategy, enabling organizations to stay ahead of risks with confidence.
Explore the future of cybersecurity decision-making today at https://decisionpulsegenai.com. Empower your teams to act fast, stay secure, and drive smart tech investments.
0 notes