#Cyber Awareness
Text
The annual cyber awareness training that all air force employees take licherally has a slide that's just a picture of the Chinese flag. Talking about scammers and hackers in the background like. Do you not know this flag actually represents like a billion farmers and factory workers and ppl who don't actually use a computer except to post shitty tiktoks and work emails. Whos displaying their wrinkly red-scare ass in the air for all to see here? Just one of those ways the military casually promotes racism daily and gets away with it, prepping the little guys with the "it's ok to use hate speech, as long as it's about the Enemy" so when she sends them off to die for some rich lobbyists profits, they're ok with it
2 notes
·
View notes
Text
Cyber Awareness program United States 2023

Cybercrime refers to criminal activity that involves the use of the internet and other forms of information technology to perpetrate various types of crimes. Examples include hacking, identity theft, online fraud, and the distribution of malware. Cybercrime is a growing problem in the U.S. and around the world, as more and more individuals and organizations rely on technology for their daily activities. The FBI's Internet Crime Complaint Center (IC3) reported a total of 791,790 complaints of suspected internet crime in 2020, with a reported total loss of over 4.2 billion dollars. It's important to note that this is likely an underrepresentation of the actual scope of cybercrime, as many victims may be hesitant to report incidents or may not even be aware that they have fallen victim to cybercrime.
More details click here
2 notes
·
View notes
Text
Online Privacy: How Much Information Are You Sharing Without Realizing It?

The internet offers a treasure trove of information and connectivity. From social media interactions to online shopping experiences, we constantly share data in exchange for convenience and entertainment. However, in this ever-connected world, the lines between convenience and privacy can easily become blurred.
This blog delves into the concept of online privacy, exploring the different ways we share information online, often without even realizing it. Whether you're a seasoned internet user or just starting to navigate the digital landscape, this guide will raise your awareness about your online footprint and empower you to make informed decisions about your privacy.
The Ever-Expanding Online Footprint: How We Share Data
Our online footprint refers to the trail of data we leave behind as we navigate the internet. This data can include:
Personal Information: Names, addresses, phone numbers, email addresses, and even birthdays are often shared willingly when creating online accounts or registering for services.
Browsing History: Websites you visit, search queries you enter, and links you click on all contribute to a detailed record of your online interests and activities.
Social Media Activity: Posts, comments, photos, and even "likes" on social media platforms paint a picture of your preferences, relationships, and even location.
Device Data: Smartphones and other connected devices collect information about your location, app usage, and even browsing habits.
Cookies and Tracking Pixels: These small pieces of code embedded in websites track your online activity across different platforms, building a comprehensive profile of your digital behavior.
The Hidden Costs of Oversharing: Why Online Privacy Matters
While sharing information online can be convenient, there are potential consequences to consider:
Targeted Advertising: Companies use your online footprint to create targeted advertising profiles, bombarding you with ads based on your browsing habits and interests.
Identity Theft: Excessive personal information shared online can make you vulnerable to identity theft, where criminals use your data to commit financial fraud or impersonate you.
Social Engineering Attacks: Cybercriminals can exploit information gleaned from your online footprint to launch social engineering attacks, tricking you into revealing sensitive data or taking actions that compromise your security.
Limited Job Opportunities: Some employers might screen potential candidates' online profiles, and oversharing personal information or unprofessional content could negatively impact your job prospects.
Loss of Control: Once information is shared online, it can be difficult to control who sees it or how it's used. Oversharing can also lead to a sense of loss of control over your own privacy.
Empowering Yourself: Taking Control of Your Online Privacy
Here are some actionable steps you can take to manage your online privacy and minimize the amount of data you share unknowingly:
Review Your Privacy Settings: Most social media platforms and online services offer granular privacy settings. Take time to understand these settings and restrict data sharing according to your comfort level.
Limit App Permissions: Be mindful of the permissions you grant to apps on your phone or other devices. Only allow access to features necessary for the app's functionality.
Think Before You Share: Before posting anything online, consider who might see it and the potential consequences. Is it something you would be comfortable sharing with the world?
Use Strong Passwords and Multi-Factor Authentication: Implement strong, unique passwords for your online accounts and enable multi-factor authentication for an extra layer of security.
Consider a Privacy-Focused Browser: Some web browsers offer enhanced privacy features like blocking tracking cookies and preventing websites from collecting your data.
Educate Yourself: Knowledge is power. Invest in a comprehensive Cyber Security Course to gain a deeper understanding of online privacy threats and learn advanced techniques to protect your data.
Investing in Knowledge: Cyber Security Courses
A Cyber Security Course can equip you with the tools and knowledge you need to navigate the online world with confidence and protect your privacy. Here's how these courses can benefit you:
Understanding Data Privacy Regulations: Cyber Security Courses cover regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act), empowering you to understand your rights and take control of your data.
Learning Data Security Best Practices: These courses delve into best practices for data security, including secure data storage, encryption techniques, and responsible data sharing practices.
Developing Online Privacy Strategies: Cyber Security Courses equip you with the knowledge to create personalized online privacy strategies tailored to your individual needs and risk tolerance.
Identifying Privacy Threats: These courses explore the various threats to online privacy, including malware, phishing scams, and data breaches. They equip you with the skills to identify these threats and avoid falling victim.
Staying Up-to-Date on Emerging Threats: The cyber threat landscape is constantly evolving. Cyber Security Courses help you stay informed about the latest privacy threats and equip you with the knowledge to adapt your privacy strategies accordingly.
Cyber Security Courses: Options for All Levels
Here's a breakdown of the various Cyber Security Courses available, catering to different learning styles and experience levels:
Cyber Security Course Beginner: These introductory courses provide a foundational understanding of online privacy concepts, common data collection practices, and essential strategies for protecting your digital footprint. They are ideal for individuals new to the online world or those seeking to enhance their basic privacy awareness.
Cyber Security Course Intermediate: These courses delve deeper into online privacy regulations, data security best practices, and explore advanced privacy-enhancing technologies like anonymization and encryption. They are suitable for individuals with some understanding of online privacy who want to refine their strategies and learn how to mitigate more sophisticated data collection techniques.
Cyber Security Course Advanced : These specialized courses cover intricate topics like digital forensics and online reputation management. They are geared towards experienced IT professionals and security enthusiasts seeking to delve deeper into protecting their own privacy and potentially helping others do the same.
Building a Culture of Online Privacy Awareness
Online privacy is not a one-time fix; it's an ongoing process of awareness and informed decision-making. By understanding how your data is collected and taking proactive steps to minimize unnecessary information sharing, you can significantly enhance your online privacy and protect yourself from potential threats.
Investing in a comprehensive Cyber Security Course empowers you to navigate the online world with confidence, control your digital footprint, and create a more secure and private online experience for yourself. Remember, knowledge is your greatest weapon in the fight for online privacy. Don't wait until your data falls into the wrong hands – take charge of your online privacy today!
#cyber security course#cyber security#cybersecurity#techcore#cyber attack#data security#social security#data privacy#online privacy#internet privacy#data theft#data tracking#data storage#hacking#awareness#cyber awareness
1 note
·
View note
Text
#itcompanydubai#CybersecurityThreats#Cybersecurity Trends#Cybersecurity Mitigation#Data Protection#Cyber Defense#Information Security#Cyber Risk Management#Cyber Awareness#Threat Detection#Security Strategies
0 notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare.
Healthcare under Cyber Attack
I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Cyber Monday fraud prevention tips 2023; CyberTalk.org
New Post has been published on https://thedigitalinsider.com/cyber-monday-fraud-prevention-tips-2023-cybertalk-org/
Cyber Monday fraud prevention tips 2023; CyberTalk.org


EXECUTIVE SUMMARY:
Excited about stocking up on everyday home essentials, epic electronics or must-have fitness gear? This November 27th, Cyber Monday will be the season’s second-major shopping event, second-only to Black Friday, with mega-sales and deep discounts that are accessible from the comfort of your couch.
Founded by the National Retail Federation in 2005, Cyber Monday was originally intended to promote online-only deals, in an effort to reduce in-store Black Friday foot-traffic. However, due to an uptick in e-commerce, both commercial holidays are now intertwined. Whether you shop on Black Friday, Cyber Monday or both, it pays to be a cyber savvy consumer.
In 2022, nearly 20% of U.S. online retail transactions that occurred between Thanksgiving and Cyber Monday were fraudulent. Americans lost more than $337 million dollars, according to the U.S. Federal Bureau of Investigation. Cyber awareness and vigilance pays – Obviously, nothing beats spending the holiday season on-hold with your bank’s fraud department (just kidding).
6 Cyber Monday fraud prevention tips
This season, proactively prevent fraud.
1. Stay savvy when it comes to scams. Take a moment to review the latest holiday scam tactics. For instance, some scammers may set up fake online stores and send you emails advertising slashed prices on popular goods. Top Cyber Monday scams include those related to fake websites, gift cards, multi-factor authentication phishing, and fake charities.
2. Shop from a secure connection. Ensure that your computer or phone is protected by antivirus software. Otherwise, the risk of accidentally downloading malware increases. Avoid making purchases from cafes or other public spaces, as cyber schemers could intercept public Wi-Fi communications or ‘shoulder surf.’
3. Only shop on secure sites. Regardless of whether you’re browsing sites belonging to well-known retailers or smaller vendors, verify that the web page you’re visiting is legitimate. Here’s how: When visiting any website, look for the little lock icon in the top left corner of your browser bar. Also, be sure that you see HTTPS in the browser bar.
While there is no single solution that can help everyone easily distinguish fraudulent websites from legitimate ones, and cyber criminals can imitate both the lock icon and HTTPS, other means of site verification include checking for domain misspellings, and accessing sites by searching for them on Google, rather than by clicking on links embedded within emails.
4. Strive for strong passwords. If you create accounts with retailers to streamline and simplify the shopping process, be sure to protect the account with a strong password. Cyber criminals may employ tactics like password spraying to steal credit card numbers, but a strong password can help protect you from this type of cyber threat.
5. Consider credit over debt. If concerned about online retail security, consider making purchases with a credit card rather than a debt card. The advantage of using a credit card is that real money never leaves your bank account. In addition, credit card fraud may be easier to resolve than debt card fraud, for which you could be on the hook for a larger portion of the stolen funds.
6. Post-holiday shopping fraud review. After you’ve completed your shopping for the season, take a few minutes to review your bank and credit card transactions. Glance at your transactions daily or every few days. Ensure that amounts are correct. Look for fraudulent transactions. Should you identify any unknown purchases or obvious fraud incidents, contact your card service provider as soon as possible.
Further information
If you’re concerned about the legitimacy of a site, an advertisement, otherwise suspect malicious intent, you might want to pass on that bargain and instead tell yourself that you’ll look forward to future buying opportunities. It beats contending with bureaucracy and bank fraud.
Lastly, prior to starting your Cyber Monday shopping, take a few minutes to ensure that your web browser, antivirus and operating systems are up-to-date.
Learn more about advanced security solutions here. Discover timely trends, expert analysis, premium business whitepapers, and so much more when you subscribe to the CyberTalk.org newsletter.
#2022#2023#Accounts#advertising#Analysis#antivirus#authentication#awareness#beats#Black Friday#browser#Business#Commerce#communications#computer#credit card#credit card fraud#cyber#cyber awareness#cyber criminals#Cyber Monday#Cyber Monday Safety#cyber security awareness#cyber threat#deals#E-Commerce#Electronics#epic#factor#fraud
0 notes
Text
Any IT solution services to strengthen cybersecurity benefit mainly business owners, business partners, and employees. Strengthening cybersecurity allows them to access data and information without the threat of data breaches.
0 notes
Text
The term "birthday attack" can also refer to a collision attack or a type of brute force attack in cryptography. This attack aims to find a collision in a hash function by systematically generating and comparing a large number of inputs to look for two inputs that generate the same hash value. The attack takes advantage of the birthday paradox, which states that the probability of two people having the same birthday increases as the number of people increases.
#cybersecurity#birthday attack#cryptography#security#cyberattack#cyber awareness#infosectrain#learntorise
1 note
·
View note
Text
How to Spot Instagram Social Engineering Scams

View On WordPress
#Bot detection#Bots#Bots to inflate numbers#Browser hijackers#Clicks#Command and control server#Concert scams#Contest scams#Contests#Copyrights#Cyber awareness#Cyber safety tips#Cyber threats#Cybercrime#Cybersecurity#Cybersecurity best practices#Cybersecurity education#demographics#Digital threats#Direct email#Domain name verification#Domain names#Events#Fake accounts#Fake giveaways#Fake profiles#Fake publishing agents#followers#Fraudulent schemes#Impersonation prevention
1 note
·
View note
Text
Securing Critical Assets: Insider Threat Protection Market Insights
The global insider threat protection market size is estimated to reach USD 13.69 billion by 2030, progressing at a CAGR of 17.4% from 2023 to 2030, as per a recent report by Grand View Research, Inc. Advances in emerging technologies, such as Artificial Intelligence (AI), Machine Learning (ML), and the Internet of Things (IoT), have led to increased adoption of mobile apps and web applications, subsequently creating more complex IT infrastructure that can be vulnerable to insider threat attacks in organizations.
Gain deeper insights on the market and receive your free copy with TOC now @: Insider Threat Protection Market Report
To address potential security challenges, such organizations are implementing security services to detect bugs, as well as analyze the security landscape, while efficiently responding to cyberattacks. The need to fix bugs in web applications as well as mobile apps, and to mitigate data loss risks associated with insider threats, is expected to fuel the adoption of ITP services over the forecast period.
Insider risk management solutions use innovative threat intelligence, machine learning, and behavioral analysis algorithms that detect threats and suspicious activities leading to security breaches. These solutions are designed to detect real-time potential threats on endpoint devices such as servers, memory devices, mobile devices, and other point-of-sale devices, thereby helping the organization enhance its security posture through rapid response capabilities. In July 2022, McAfee, LLC announced a strategic partnership with Telstra, an Australia-based telecommunications and technology company.
The partnership aims to deliver comprehensive protection solutions to safeguard the identity and privacy rights of consumers across applications, activities, devices, and locations. This partnership offered Telstra customers easy access to McAfee’s robust security solutions. These solutions deliver complete security and privacy protection, with integrated applications of Antivirus Protection, Parental Controls, VPN Security, and Identity Protection, among others to secure multiple devices, including mobiles, tablets, PCs, and laptops. Such developments would further drive the market for insider threat protection solutions during the forecast period.
#Insider Threat Protection#Cyber security#Information Security#IT Security#Data Breach Prevention#Insider Risk#Insider Threat Detection#Insider Threat Solutions#Cyber Defense#Cyber Awareness
1 note
·
View note
Text
Cybersecurity Analyst: Safeguarding the Digital Frontier - Who and what they do?
In today’s interconnected world, cybersecurity stands as an impenetrable shield against the relentless wave of cyber threats. At the forefront of this defense are Cybersecurity Analysts, skilled professionals who protect organizations and individuals from malicious attacks on their digital assets. This article delves into the responsibilities and significance of a Cybersecurity Analyst and…

View On WordPress
#Cloud Security#Cyber Attacks#Cyber Awareness#Cyber Awareness Training#Cyber Defense#Cyber Education#Cyber Forensics#Cyber Hygiene#Cyber Incident Response#Cyber Resilience#Cyber Risk Management#Cyber Threats#Cybersecurity#Cybersecurity Awareness Month#Cybersecurity Awareness Week#Cybersecurity Best Practices#Cybersecurity Careers#Cybersecurity Certifications#Cybersecurity Compliance#Cybersecurity Events#Cybersecurity Governance#Cybersecurity News#Cybersecurity Policies#Cybersecurity Solutions#Cybersecurity Tips#Cybersecurity Tools#Cybersecurity Trends#Cybersecurity Webinars#Data Breach#Data Privacy
0 notes
Text
The National Security Alliance and the U.S. government are in charge of it. Cyber security awareness is essential, given how crucial security is today.
#cyber security awareness day#cyber security awareness#cyber security awareness month 2022.#cisa cybersecurity awareness month#cyber security awareness month ideas#cybersecurity awareness month champion#cyber security awareness month 2022 theme#cyber awareness#army cyber awareness#cybersecurity awareness month#cyber awareness training#national cybersecurity awareness month#cyber security training for employees#cyber awareness 2022
0 notes
Link
This coverage can be important for small businesses that don’t have the resources to invest in expensive security measures or for those who simply want peace of mind that they will be covered if something goes wrong.
Even though the Blockchain Technology promises to sort the issue of data breach, businesses and organizations still experience cyber-attacks.
What is cyber insurance?
Cyber insurance is a form of liability coverage that provides protection against the loss or damage to your business’s information and technology infrastructure. It’s designed to cover the cost of any losses or damages that you suffer as a result of a cyber attack, including data loss and theft.
Cyber insurance is an essential part of any business plan. It is a necessity for any business offering financial services. Not only does it protect your organization from the financial side of a data breach, but it also helps to prevent lawsuits from companies that have been affected by the fraudulent activity. In fact, many people consider cyber insurance to be one of the most important types of coverage available today.
The good news is that cyber insurance can be found at reasonable prices and can be customized to meet your specific needs. Here are seven things you should know about cyber insurance before deciding if it’s right for you:
· Cyber insurance is a must-have for any business
· You can choose from several types of coverage
· It can help prevent a data breach from becoming a lawsuit
· Your company might need to pay out a lawsuit if someone else is damaged by your data breaches
· It gives you the ability to cover third-party claims against your organization
· It provides coverage for all types of critical infrastructure, including power plants and oil fields
How does cyber insurance work?
Cyber insurance typically involves two types of coverage:
1. Business interruption
This type of coverage protects your business from financial losses resulting from a temporary interruption in operations due to an attack on your IT infrastructure. For example, if hackers were able to shut down your network for several hours, this type of policy would pay for lost productivity during that period. Business interruption coverage also covers the costs associated with repairing damage caused by an attack and restoring operations once they’re restored.
2. Data recovery
This type of coverage pays for the cost of recovering lost or destroyed data after it has been stolen or damaged through an attack on your IT infrastructure. This can include anything from lost computer files to documents stored in the cloud or other online storage methods.
Types of cyber insurance
The most common types of cyber insurance include:
1. Business interruption coverage (BI)
This coverage provides financial compensation after a cyber attack has caused severe damage to your business operations.
2. Data breach coverage (DBC)
This coverage provides financial compensation after a hacker has stolen personal information or proprietary data from you or your business.
3. High-value property damage and loss (HVPLL)
This coverage provides compensation when hackers cause severe damage to your company through malicious code, malware or other means. This could include stolen personal information, payment card numbers and other sensitive personal data that could be used for identity theft, fraud or other illegal activity.
#cyberattack#technology#cybercrime#malware#hacking#cyber#business insurance#risk management#cyber awareness#Business#insurance
0 notes
Text

Now-a-days, IAM has become an essential component of organizational security…
… because of its versatile characteristics and features.
IAM helps organizations to automate a lot of security tasks easily.
Let’s dig into the different IAM types and how the most common ones differ among each other.
Here Are The Different Types of IAM:
Mainly, there are 3 types of IAM used to secure the system.
Let us explore these now.
Almost all organizations come with different classes of users with varied identity needs.
Know more: https://vsecurelabs.co/types-of-iam/
0 notes
Text
Cyber Security Awareness for PSUs
Recently, the Ministry of Home Affairs has launched Cyber Jagrukta Divas which is meant to provide cyber security awareness to employees in government organizations. The ministry has asked the organizations to prepare an annual action plan to run an awareness campaign within the organization.
Get Annual Action Plan for your Organization from the link below-
1 note
·
View note
Text
For the roleplay committee on Tumblr
---
Enough with the pathetic targeting of roleplayers on Tumblr! It's downright despicable, especially given that the majority of these creative individuals are minors. Get a grip on reality and find something better to do with your time than spewing disrespect.
LISTEN UP, if I catch wind of any more of these toxic comments, I'll make it my mission to unearth your sorry identity and ensure your account is obliterated. Consider this a warning – back off and let people enjoy their space without your mindless aggression. The consequences will be swift and severe.
To those who have been hurt by the senseless targeting on Tumblr, I offer my sincere apologies. Remember, it's not a crime to pursue your passions, including roleplaying. Don't let the negativity of others dictate what brings you joy. Do what you love, stay true to yourself, and embrace your interests without reservation. Your well-being matters, and there are supportive communities out there who appreciate and respect your creative endeavors. Keep shining and doing what makes you happy. 💙
IF YOU SEE ONE OF THESE ASSHOLES TAUNTIN' OTHER ROLEPLAYERS, TELL THEM TO FUCK OFF!
--
SPREAD THE WORD!
#PROTECT TUMBLR ROLEPLAYERS
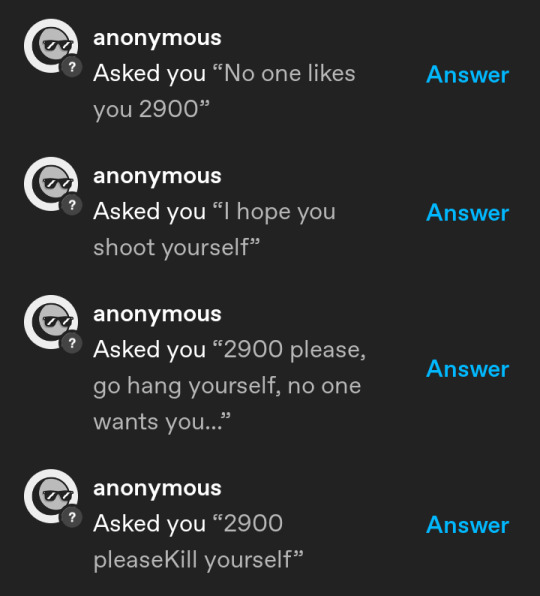
#spread awareness#get a life#protect kids#my thoughts#haters gonna hate#roleplayers#anti harassment#cyber bullying#stop bullying
150 notes
·
View notes