#Difference between System Software and Utility Software
Explore tagged Tumblr posts
Text
So, in the midst of... you know, everything, life at the library goes on and I wanted to talk about the difference between Libby and Hoopla.
For those not in the know, Libby and Hoopla are both apps/software that libraries can use to offer digital items to our patrons. Libby does ebooks (including graphic novels) and audiobooks.

Hoopla does ebooks, audiobooks, digital comics (weekly issues, not just trades or graphic novels), movies, TV shows, and music.

A little while back, my library system had to cut down on the number of Hoopla items patrons can check out per month. This caused a little bit of a stir - people like Hoopla! And they should! It's really cool! But the reason we had to cut back there and not with Libby was because the ways we pay for Libby and Hoopla are different.
Libby uses a pay-per-license model. This means that when we buy an ebook or audiobook on Libby, it's like we're buying one copy of a physical item. Except, because publishers are vultures, it's often much more expensive than buying one copy of the physical book - unless it's an audiobook, in which case buying the CDs might very well be more expensive than buying the digital license on Libby. That's why you might have to wait on a list for a Libby title that's really popular: we only have licenses for so many "copies". These licenses can be in perpetuity (i.e. you pay once and you can use that copy forever) or, more commonly, for a limited length of time like a year. Once that time is up, we decide whether to pay for the license for each copy again.
Hoopla uses a pay-per-circulation model. There's no waiting: once you, the patron, decide you'd like to check something out, you can do so immediately and we pay Hoopla a smaller amount of money to essentially "rent" the license from them. Cool, right?
Except that the pay-per-circ model adds up. If we have access to a brand new or popular title on Libby and Hoopla, and the Libby copy has a long waiting list, patrons might hop over to Hoopla to check it out immediately. If enough people do this, we might end up paying more overall for the Hoopla item on a per-circulation basis than we did for the license on the Libby item. That's why libraries typically limit the number of Hoopla checkouts patrons can use per month: because otherwise, we can't predict the amount we'll be paying Hoopla in the same way we can predict the amount we'll pay Libby.
Let me be clear: If a library offers a digital service and it would be helpful to you, please use it. Don't deny yourself a service you need or would enjoy in some misguided attempt to save your library some cash. We want to offer digital services, not least because ebooks and audiobooks have accessibility features that print books often don't. If your library has Libby and Hoopla and you get utility out of both, use both!
That said, if you're upset with the lower number of checkouts on Hoopla or the limited number of titles or copies available to you on Libby, you know who you should talk to? Your elected officials. Local, state, and federal. Because those folks are the ones who decide how much money we get, and what we can spend it on.
Don't go to them angry, either, because then we'll get scolded for not using the funds they "gave" us appropriately. (If you're a frequent library user, you might be shocked at how anti-library many local government officials already are.) Write your officials an email, call them, or show up at a board meeting and say you like the services the library offers, but you'd love it if we had enough money to buy more books on Libby or offer more checkouts on Hoopla. Tell them directly that this is how you would like your tax dollars to be spent.
If anybody has questions about how Hoopla or Libby work, I'm happy to answer them! Just wanted to make sure we had a baseline understanding.
#books & libraries#librarians of tumblr#bookblr#booklr#reading#public libraries#librarians#hoopla#libby
184 notes
·
View notes
Text
What is the kernel of an operating system ?
You can think of the kernel as the core component of an operating system, just like the CPU is the core component of a computer. The kernel of an operating system, such as the Linux kernel, is responsible for managing system resources ( such as the CPU, memory, and devices ) . The kernel of an operating system is not a physical entity that can be seen. It is a computer program that resides in memory.
Key points to understand the relationship between the kernel and the OS:
The kernel acts as the intermediary between the hardware and the software layers of the system. It provides a layer of abstraction that allows software applications to interact with the hardware without needing to understand the low-level details of the hardware
The kernel controls and manages system resources such as the CPU, memory, devices, and file systems. It ensures that these resources are allocated and utilized efficiently by different processes and applications running on the system.
The kernel handles tasks like process scheduling, memory management, device drivers, file system access, and handling interrupts from hardware devices.
The kernel can be extended through the use of loadable kernel modules (LKM). LKMs allow for the addition of new functionality or device drivers without modifying the kernel itself.
#linux#arch linux#ubuntu#debian#code#codeblr#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code#Youtube
225 notes
·
View notes
Text
So I've been thinking about when will the new mainline (this includes a potential remake) Fire Emblem game will be released.
So it's been confirmed that the Switch 2 is releasing this year. While the exact date when it'll come out is unknown, there's going to be a Switch 2 Direct on April 2nd. With this in mind, I'm predicting that the Switch 2 will come out either in October or November.
Now to what this post is about. FE has historically released the next mainline game within a 1-3 and a half year timeframe. That means there's most likely going to be an announcement for a new mainline game this year. If so, the game is most likely going to release some time between mid 2026 to late 2026. BUT, there's a chance that the new game will release in early 2027 for 2 reasons.
(This is all just speculation, so take what I'm about to say with a grain of salt).
One: There were leaks in early 2022 claiming that Engage was actually finished in 2021. While some of things the leaker claimed about the game turned out to be true (it being not being a remake, the protagonist having blue and red hair, and the concept of the Emblems), there is one thing the leaker was wrong about. They claimed that Koei Tecmo and their subsidiary studio Gust also worked on Engage. No where in the game's credits mentions Koei Tecmo, nor in any interview with the developers claimed their involvement. From what I could find, only Intelligent Systems worked on Engage. So the validity of the claim that Engage was finished in 2021 can be called into question. What I'm trying to say that there's a chance Engage was still being worked on during 2021 and 2022. Also, logically speaking, why would they just sit on an already finished game for roughly 2 years? This means, unless some other studio was working on FE18 while Engage was being developed, InSyst was putting most of their attention towards Engage. There is a chance that InSyst was also working on the next game alongside Engage, but I have a feeling that InSyst was much more focused on Engage's development.
Two: The whole controversy with Unity. Basically in 2023 Unity announced a change in how developers would be charged when using Unity and developers who use Unity are mad. Here's quote from this article that basically explains what the change would be and why developers are mad:
"Instead of charging developers a set monthly rate based on the number of users utilizing the software, it would implement a pay-per-download scheme that charged developers every time their game was downloaded. That meant instead of paying a flat, predictable rate to Unity, payouts could fluctuate, resulting in potentially higher fees. This news caused a massive uproar in the game development community with developers voicing their frustration on social media. Developers argued that the pricing model was implemented without adequate warning, forcing them to either pay the new fees that can’t be adequately budgeted for or make a costly and time-consuming switch to new software. They also claimed the per-download model could be exploited by malicious actors to run up fees on developers they don’t like."
Why am I mentioning Unity? This is because Engage is the first game to use a non in house made engine for FE, meaning that there is a chance InSyst will continue to use Unity for future FE games. The problem is because of the aforementioned Unity's new method of charging developers. While the same article did state that Unity has now since revoked this change, it still probably affected the development of FE18. This is because it took a full year for Unity to revoke the change meaning that there is a chance that InSyst changed to different engine, causing a delay in the progress of the game being made.
Now this part isn't that relevant to my speculation on when FE18 will come but I just wanted mention this: While the Switch 2 is going to be backwards compatible with Switch 1 games, there's still a chance the new mainline Fire Emblem game is going to be Switch 2 exclusive. This is all dependent on when FE18 is coming out. Also if Nintendo is going to treat the Switch 2 like a true next gen console and phase out making game for the Switch 1 into the Switch 2's lifespan, or if they're going to treat it like DSI and New 3DS situation and only have a few games exclusive to the Switch 2 while still making games for the Switch 1.
Anyways, this has been on my mind for a couple of days and just wanted to share my thoughts on the matter.
#hope my ramblings are *somewhat* understandable#also I wrote this instead of doing my poetry hw lol#garn’s bs#long post#<- just in case
12 notes
·
View notes
Note
Out of curiosity (and of course please do not feel like you have to answer this)
How do you keep your story organized?
I use Miro Board to help me lay down my plot and timelines, but I’m always curious what other tools writers use to outline, organize and such for their writing.
Id love to also just create a post and have writers and artists add to it over time as a source of knowledge and help….but I’m not sure how to start it honestly.
i love this questions and for me it's SCRIVENER, baby, SCRIVENER
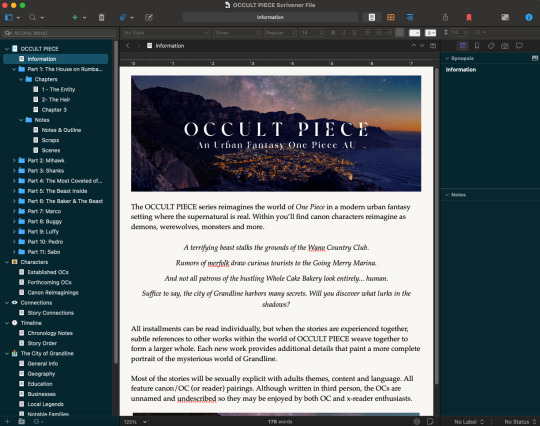
i'm using OCCULT PIECE as an example because it's a massive project and Scrivener absolutely helped me bring it to life (it finally corralled my brain into something manageable LMAO)
not sure how familiar you are with this software, but it combines a word processor with a file organization system so i can flip between documents within a work super quickly...keeps all my notes, drafts, and other docs at my fingertips
the column on the left shows the docs and folders i've set up to keep this massive AU project organized...i have folders for each story, with subfolders that have notes and chapters for each work, and then i have separate folders for worldbuilding notes, character notes, connections between stories, and similar...i expanded a bunch of the folders so you can see what's in 'em if you want a closer look
Scrivener also has a corkboard view so you can see your story elements all laid out, and you can move them around as you see fit, which makes rearranging scenes (should you choose to put separate scenes into their own text docs) very easy
i like this software for its utility but also because you pay for it once and then can transfer the license to different computers when/if you change to a new one, and you can get it pretty cheap using discount codes that come up pretty frequently (usually they're a NaNoWriMo prize)
i have never used Miro and IDK how it compares! will have to check it out and seeeeee
as for the post people can add to, do you mean like a Tumblr post with reblogs, or like a shareable document people can circulate and add to at will? would this be for a large collaborative story or universe or just general information? sounds cool either way! love it when a community comes together...
22 notes
·
View notes
Text
Leveraging XML Data Interface for IPTV EPG
This blog explores the significance of optimizing the XML Data Interface and XMLTV schedule EPG for IPTV. It emphasizes the importance of EPG in IPTV, preparation steps, installation, configuration, file updates, customization, error handling, and advanced tips.
The focus is on enhancing user experience, content delivery, and securing IPTV setups. The comprehensive guide aims to empower IPTV providers and tech enthusiasts to leverage the full potential of XMLTV and EPG technologies.
1. Overview of the Context:
The context focuses on the significance of optimizing the XML Data Interface and leveraging the latest XMLTV schedule EPG (Electronic Program Guide) for IPTV (Internet Protocol Television) providers. L&E Solutions emphasizes the importance of enhancing user experience and content delivery by effectively managing and distributing EPG information.
This guide delves into detailed steps on installing and configuring XMLTV to work with IPTV, automating XMLTV file updates, customizing EPG data, resolving common errors, and deploying advanced tips and tricks to maximize the utility of the system.
2. Key Themes and Details:
The Importance of EPG in IPTV: The EPG plays a vital role in enhancing viewer experience by providing a comprehensive overview of available content and facilitating easy navigation through channels and programs. It allows users to plan their viewing by showing detailed schedules of upcoming shows, episode descriptions, and broadcasting times.
Preparation: Gathering Necessary Resources: The article highlights the importance of gathering required software and hardware, such as XMLTV software, EPG management tools, reliable computer, internet connection, and additional utilities to ensure smooth setup and operation of XMLTV for IPTV.
Installing XMLTV: Detailed step-by-step instructions are provided for installing XMLTV on different operating systems, including Windows, Mac OS X, and Linux (Debian-based systems), ensuring efficient management and utilization of TV listings for IPTV setups.
Configuring XMLTV to Work with IPTV: The article emphasizes the correct configuration of M3U links and EPG URLs to seamlessly integrate XMLTV with IPTV systems, providing accurate and timely broadcasting information.
3. Customization and Automation:
Automating XMLTV File Updates: The importance of automating XMLTV file updates for maintaining an updated EPG is highlighted, with detailed instructions on using cron jobs and scheduled tasks.
Customizing Your EPG Data: The article explores advanced XMLTV configuration options and leveraging third-party services for enhanced EPG data to improve the viewer's experience.
Handling and Resolving Errors: Common issues related to XMLTV and IPTV systems are discussed, along with their solutions, and methods for debugging XMLTV output are outlined.
Advanced Tips and Tricks: The article provides advanced tips and tricks for optimizing EPG performance and securing IPTV setups, such as leveraging caching mechanisms, utilizing efficient data parsing tools, and securing authentication methods.
The conclusion emphasizes the pivotal enhancement of IPTV services through the synergy between the XML Data Interface and XMLTV Guide EPG, offering a robust framework for delivering engaging and easily accessible content. It also encourages continual enrichment of knowledge and utilization of innovative tools to stay at the forefront of IPTV technology.
3. Language and Structure:
The article is written in English and follows a structured approach, providing detailed explanations, step-by-step instructions, and actionable insights to guide IPTV providers, developers, and tech enthusiasts in leveraging the full potential of XMLTV and EPG technologies.
The conclusion emphasizes the pivotal role of the XML Data Interface and XMLTV Guide EPG in enhancing IPTV services to find more information and innovative tools. It serves as a call to action for IPTV providers, developers, and enthusiasts to explore the sophisticated capabilities of XMLTV and EPG technologies for delivering unparalleled content viewing experiences.
youtube
7 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
There are just two cables linking the remote Arctic archipelago of Svalbard with mainland Norway, providing almost all the data from polar-orbiting satellites to the rest of the world. And two years ago, they nearly stopped working.
Norwegian police images released in late May show the catastrophic damage done to one of the Svalbard fiber optic cables: the plastic casing slashed open, the cable exposed, and wires unfurled like a faulty electrical cord.
The unsolved January 2022 incident, which cut data flow from the SvalSat satellites and limited air traffic to the archipelago, is serving as a cautionary tale about what can happen when undersea cables—which underpin most of the global communications network—are cut. Yemen’s Iran-backed Houthi rebels did just that earlier this year when they targeted a key bottleneck between Asia, Africa, and Europe—after threatening to do so in response to Israel’s war against Hamas in Gaza.
The threat is not just limited to one or two areas. NATO officials believe that Russia has a decadeslong program to map out European undersea infrastructure as part of an effort to prepare the battlefield for a possible conflict with the 32-nation alliance.
“We know the potential is there to do damage if they would want to,” said a senior NATO official, speaking with Foreign Policy on condition of anonymity based on ground rules for interacting with journalists set by the alliance. “Part of Russian war planning is knowing where the critical infrastructure of your enemy is.”
It doesn’t take a huge effort by the Russians to get the information that they need to cause harm. Most of the pipelines are run by utility companies, and much of the data on where the cables run is in the public domain because of licensing requirements.
In response, NATO now has an undersea infrastructure coordination group that brings together military and civilian officials and has the power to convene top representatives from the private sector, based out of the alliance’s Maritime Command in the London suburb of Northwood.
“The question is connecting all the dots and creating a network,” the senior NATO official said of the information and intelligence exchange.
The ambitious effort is an attempt to use computing power to protect the vast undersea cable network that undergirds much of the global economy. Since it’s nearly impossible to patrol undersea all the time without an unrealistic number of submarines—especially across the Atlantic Ocean—the alliance has to rely on computers. Drawing on data from software interfaces and the cable and pipeline operators themselves, NATO allies are working together with the private sector to create a massive alert system for the thousands of miles of undersea infrastructure in Northern Europe, relying on sensors from the cables as well as acoustic sensors attached to wind turbines, which can be used to detect irregularities.
“NATO processes, I think, are sort of in a very early phase,” said Audun Halvorsen, the director of the emergency department for the Norwegian Shipowners’ Association (and formerly the country’s deputy foreign minister). “They are basically trying to map out the landscape when it comes to jurisdictions, when it comes to authorities involved. You are facing a huge range of different regulatory regimes for the industry around the undersea basin.”
The strategy of cutting undersea cables is almost as old as modern warfare. (The first trans-Atlantic cables had been laid a few decades earlier, in 1866.) Britain began cutting German undersea cables at the outset of World War I to sabotage communications—and the Germans happily returned the favor. When submarine telephone cables began being laid in the 1950s, during the early days of the Cold War, Soviet trawlers damaged underwater cables near the Newfoundland coast. The U.S. Navy alone owns more than 40,000 nautical miles of active cables on the seafloor.
But with fiber optic cables becoming the ubiquitous plumbing that underpins global communications and trade in the internet age, the vulnerability in the seabed is growing. Norway’s undersea pipeline network provides about 40 percent of Europe’s natural gas supply, with pipelines crisscrossing the North Sea to the United Kingdom and the rest of the continent along with about 500 underwater communication cables that carry roughly 97 percent of the world’s internet traffic—some of them extending all the way across the Atlantic Ocean. That’s as much as $10 trillion in financial transactions every day.
“It is less kinetic and more a way for the Russians to show the West that ‘we know you guys are quite challenged in securing that infrastructure,’” said Sebastian Bruns, a naval expert at the Center for Maritime Strategy and Security at the Institute for Security Policy at Kiel University in Germany. “They would be tackling the very seams of what ties our societies together.”
About 100 of those cables break globally every year—most by accident—and it’s basically impossible to protect all of that infrastructure, other than by adding even more redundant data cables or ensuring that more liquified natural gas tankers are waiting out at sea, providing another source of gas if there’s a break.
The concern for that infrastructure has led to the NATO effort, which began after the September 2022 attacks on the Nord Stream 1 and 2 pipelines that transport natural gas from Russia to Germany. Even though much of the data about where the cables are located is public, the sensor data that could determine whether a linkage is in danger of being cut is stovepiped far under the national level—meaning that it’s kept within the companies themselves. The United States alone has 85 licensed undersea telecommunications landing stations. And while many pipeline owners have taken into account the risk of corrosion and possible accidents, factoring for sabotage is less common.
Some experts believe that smaller groups of countries can move faster than NATO to protect the cables. In April, Norway and five other countries bordering the North Sea—Belgium, Denmark, the Netherlands, Germany, and the United Kingdom—agreed to share operational information to protect undersea cables and pipelines against sabotage. And the Council of the Baltic States recently met in Finland to condemn Russia’s hybrid tactics—incidents of sabotage that fall beneath the level of declared war, including threats to undersea cables.
Already, Russia is lashing out at Nordic countries through other means. Since Finland joined NATO in April 2023, Russia has been sending waves of forced migrants to their 830-mile-long shared border—nearly half of the entire boundary between Russia and the alliance—forcing Helsinki to shut down all of its crossings. Russia has proposed redrawing borders in the Baltic Sea, hit Sweden with cyberattacks, and even removed buoys on the Narva River that Estonia put in place to mark their maritime frontier.
“All of our economy under the sea is under threat,” Vice-Adm. Didier Maleterre, the deputy commander of the NATO maritime command, said in April.
The threat is heightened by a Russian submarine program that has resurged since the 2022 invasion of Ukraine, operating from the Kola Peninsula. But problems can also be caused by unintended anchor drag from commercial ships. The Hong Kong-flagged and Chinese-operated NewNew Polar Bear, suspected of damaging the Balticconnector gas pipeline between Finland and Estonia in October 2023, sailed away along the Northern Sea route with protection from a Russian icebreaker.
In the face of all the other challenges—shrinking navies, a resurgence in piracy, the Red Sea attacks—that undersea flank is exposed.
And officials say that Russia’s use of criminal and civilian networks—which are also deployed to create influence networks in mainland Europe—makes all of these tactics, including the sabotage of undersea pipelines, extremely difficult to pin on the Kremlin. The Russian surveys of the Baltic seabed, for instance, are carried out by ships with an ostensibly scientific purpose.
“We are still tied into this military-versus-civilian division of labor, whereas the Russians are much smarter using civilian vessels for military purposes,” said Bruns, the naval expert. “We are yet to find a solution for that.”
Scientists still understand relatively little about the form of the seafloor. So artificial intelligence is also being used to map it, providing another potential method to spot would-be Russian cable snappers. Some NATO countries and operators are even thinking about burying their pipelines in the seafloor, especially in the Baltic Sea, where the average depth is just under 200 feet. It’s already standard practice near most European coastlines, since it helps protect against bottom trawlers and ship anchors.
After the Balticconnector pipeline incident last fall, Norway began to do an inventory of its own undersea infrastructure, starting with oil and gas before branching out to map parts of the electrical grid and communications cables that ran underwater. Authorities were able to search nearly 5,600 miles of oil and gas pipelines.
“We searched everything,” said Gen. Eirik Kristoffersen, Norway’s chief of defense. “When we found something, we used our military experts to look [at], ‘what is this? Is this something that has been placed there? Is this something from World War II? Is it something that the fishermen dropped?’”
The ability to conduct such an extensive search stems from the infrastructure of the private sector. Norway’s energy industry already has preparedness mechanisms in place to help protect and repair undersea infrastructure for pipelines and electric cables, Halvorsen said, which is coordinated by Norwegian operator Equinor. It’s a model that Halvorsen believes has promise for communication cables, too. But across most of NATO, that capability is limited.
“There is basically zero capability in government hands to survey, repair, maintain, [or] replace any of this infrastructure,” Halvorsen said. “All that capability and capacity is for the civilian industry. So to protect this kind of underwater infrastructure, you need to have some kind of functioning interface between the government side … and the industry.”
6 notes
·
View notes
Text
Mastering Physics: Not-So-Basic Tips to Ace Your Physics Notes and Get an A+
Introduction: Are you struggling to grasp those complex physics concepts and looking for a way to elevate your note-taking game? Fear not! In this comprehensive guide, we'll unveil advanced strategies to revolutionize your approach to physics notes, ensuring you not only understand the material but also excel in your exams. Say goodbye to mundane note-taking techniques and welcome a new era of effective studying.
Understand the Fundamentals: Before diving into advanced note-taking techniques, it's crucial to have a solid understanding of the fundamental concepts. Spend ample time reviewing your textbooks, lectures, and supplementary materials to ensure you grasp the basics thoroughly. Without a strong foundation, advanced note-taking strategies may not yield optimal results.
Utilize Concept Mapping: Concept mapping is a powerful visual tool that can help you organize and connect complex ideas in physics. Rather than jotting down linear notes, create interconnected diagrams that illustrate the relationships between different concepts. This method not only enhances comprehension but also aids in long-term retention.
Incorporate Visual Aids: Physics is inherently visual, so why limit yourself to text-based notes? Integrate diagrams, graphs, and illustrations into your notes to complement written explanations. Visual aids not only enhance understanding but also make your notes more engaging and memorable.
Embrace Analog and Digital Tools: Gone are the days of traditional pen-and-paper note-taking. Embrace the versatility of digital tools such as tablets and styluses, which allow for dynamic note-taking experiences. Whether you prefer handwritten notes or digital annotations, find a method that suits your learning style and workflow.
Practice Active Recall: Passive reading of notes is often ineffective for deep learning. Instead, actively engage with the material through techniques like self-quizzing and summarization. Challenge yourself to recall key concepts from memory and reinforce your understanding through regular practice.
Leverage Anki or Spaced Repetition: Anki and other spaced repetition software are invaluable tools for mastering physics concepts. Create digital flashcards with key equations, definitions, and problem-solving techniques, and review them regularly using spaced repetition algorithms. This approach optimizes memory retention and ensures you're always prepared for exams.
Seek Clarification and Collaboration: Don't hesitate to seek clarification from your instructors or peers if you encounter challenging concepts. Engage in collaborative study sessions where you can discuss complex topics, work through problems together, and gain fresh insights. Explaining concepts to others is a powerful way to solidify your own understanding.
Stay Organized and Consistent: Consistency is key when it comes to effective note-taking. Establish a structured note-taking system that works for you, whether it's chronological, topical, or a combination of both. Keep your notes organized and easily accessible, allowing for seamless review and reference when needed.
Conclusion: By incorporating these not-so-basic physics note-making tips into your study routine, you'll be well-equipped to tackle even the most challenging concepts with confidence. Remember, mastering physics is not just about memorization—it's about understanding the underlying principles and applying them effectively. With dedication, practice, and the right strategies, you'll be on your way to earning that coveted A+ in physics. Happy studying!
#physics#study space#studyinspo#studyspo#studygram#studyblr#study with me#study tips#study notes#science
8 notes
·
View notes
Note
How do you cope with package management? I mostly use python where it's literally just a single command. It took me over an hour to work out in c++
I'm going to be really honest and say the language package/build pipeline ecosystem is the single worst thing about C++. Memory safety isn't that big of a deal in well managed projects that utilize modern C++, pointer arithmetic ain't that hard once you take your time to actually understanding but the fucking mess that is the bizarre scene of package managers, build system setups and different ways of handling that in-between different codebases that rely on eachother? Nightmarish, unsolvable, literally not possible to workaround (see https://xkcd.com/927/).
What I'd recommend - look around at different repos for software you use and look how they structure their codebases, what buildsystems they use and see how it works for you! There isn't one-size-fits-all answer, unfortunately.
The way I program my own lil side projects, I use mainly CMake + CPM.cmake (a lil script that allows me to download github repos into my own source tree at a specific version and configure them for building) and make HEAVY use of CMake Presets.
As for what I'd recommend for you to try as a good starting point would be meson. It's great at getting you into a working program pretty fast and without much boilerplate.
Best of luck. There's a world of performant OOP goodness waiting.
3 notes
·
View notes
Text


### Officers of Crimson Dawn's Fleets: Commanding the Shadows
#### Overview
The officers of Crimson Dawn's fleets are a diverse group of strategically minded individuals who play crucial roles in commanding ships, overseeing operations, and executing the organization's objectives across the galaxy. These officers range from experienced military veterans to skilled tacticians, each bringing unique strengths and expertise to Crimson Dawn’s naval operations.
### Types of Crimson Dawn Fleet Officers
1. Fleet Commanders:
- Fleet commanders are responsible for overseeing entire fleets of ships, making critical strategic decisions during battles and campaigns. They coordinate multiple vessels, ensuring that operations are executed efficiently while adapting to evolving battlefield scenarios.
- These officers are often seasoned veterans with extensive experience in naval warfare and leadership, adept at inspiring their crews during combat and maintaining order amidst chaos.
2. Ship Captains:
- Each ship within the Crimson Dawn fleet is commanded by a ship captain who manages daily operations, crew morale, and tactical maneuvers during engagements. Captains must be skilled at both leading their crew and executing the larger strategic plan set forth by their superiors.
- Often displaying a flair for combat and quick decision-making, these captains ensure their ships are battle-ready and can execute missions ranging from piracy to military assaults with precision.
3. Tactical Officers:
- Tactical officers specialize in developing and implementing strategies for fleet engagements. They analyze enemy movements, assess threats, and recommend tactical maneuvers to exploit weaknesses in opposing forces.
- Skilled in advanced warfare tactics and technology, tactical officers work closely with fleet commanders and ship captains to coordinate responses during battle, ensuring a calculated approach in every engagement.
4. Operations Specialists:
- Operations specialists handle the logistics and operational capabilities of the fleet. They are responsible for coordinating supplies, managing crew assignments, and ensuring that all necessary resources are available for missions.
- Their expertise is vital for maintaining the efficiency and readiness of ships, allowing for smooth operations during long engagements and logistical challenges encountered during fleet maneuvers.
5. Communications Officers:
- Communication officers manage all forms of communication within the fleet and between ships and command. They are essential for relaying strategic orders, coordinating movements, and maintaining situational awareness during engagements.
- In a fast-paced combat environment, these officers must work swiftly to transmit and receive information while working to protect their communications from potential enemy interception.
### Training and Skills
1. Military Training:
- Officers in Crimson Dawn’s fleets undergo rigorous military training, which encompasses both theoretical and practical aspects of space warfare. This training prepares them for a variety of combat scenarios, ranging from ship-to-ship engagements to ground support operations.
- Officers are schooled in the use of various starships, weapons systems, and tactics, ensuring adaptability in different combat situations.
2. Leadership Development:
- Strong emphasis is placed on leadership skills, with officers being trained to motivate and manage their crews effectively. Training often includes scenarios that test their decision-making, crisis management, and communication abilities.
- Future leaders are often identified for their potential, and mentorship programs within Crimson Dawn further foster the growth of upcoming officers.
3. Technological Proficiency:
- Given that Crimson Dawn operates advanced technology, officers receive training in weapons systems, starship systems, and combat strategy software. This proficiency enables them to utilize their fleet’s technological advantages effectively and respond to threats in real-time.
- They learn to adapt to the fast-evolving tech landscape, constantly updating their skills with the latest innovations in warfare and tactical equipment.
### Conclusion
The officers serving in Crimson Dawn's fleets represent a formidable cadre of military minds, dedicated to advancing the organization's dark ambitions throughout the galaxy. From fleet commanders to communications officers, each plays a vital role in ensuring the effectiveness and efficiency of Crimson Dawn’s naval power.
As conflicts unfold and the stakes rise, these officers’ strategic decisions, leadership skills, and combat proficiency will be critical in shaping the trajectory of battles, solidifying Crimson Dawn's position as a dominant force capable of wielding power in the shadows of the galaxy. Through their relentless pursuits, they continue to enhance Crimson Dawn's reputation and capability, furthering the organization’s quest for control and supremacy.

#star wars#star wars fanfiction#darth maul#savage opress#feral opress#sith#the clone wars#crimson dawn#the shadow collective#star wars what if#my fanfiction#check out my fanfic#crime syndicate
4 notes
·
View notes
Text
Transform Your School with India’s First Moodle Integrated System – CuteBrains!

In the rapidly evolving world of education, having the right tools can make all the difference. CuteBrains, India’s first school management system integrated with Moodle, is revolutionizing the way schools operate by merging the best of administrative efficiency and innovative learning. Designed to cater to the unique needs of Indian schools, CuteBrains offers a comprehensive solution that not only streamlines administrative tasks but also enhances the learning experience for students and teachers alike.
Why CuteBrains?
CuteBrains sets itself apart by being the first in India to integrate Moodle, the globally recognized learning management system (LMS), directly into school management. This powerful combination ensures that schools have a robust platform that handles both academic and administrative needs seamlessly. Here’s how CuteBrains is transforming schools across the country:
1. Seamless Administration and Academic Integration
CuteBrains integrates Moodle’s extensive learning tools directly into the school management system, allowing for a unified platform where administrative tasks and academic activities work hand in hand. Teachers can manage subjects, assignments, and grading within the same platform used for attendance, fee management, and student records. This integration eliminates the need for multiple software solutions, simplifying the workflow for teachers and administrators.
2. Enhanced Learning Experience
The Moodle integration in CuteBrains brings a wealth of interactive learning tools to the classroom. Teachers can easily create and share study materials, assignments, quizzes, and more, all within a digital environment that students find engaging and intuitive. The platform supports blended learning, online classes, and even virtual discussions, making education accessible anytime, anywhere. By incorporating these advanced tools, CuteBrains empowers teachers to deliver personalized and effective learning experiences.
3. Administrative Processes
For school administrators, CuteBrains offers a host of features that reduce the daily workload. The platform automates attendance, fee collection, timetable management, and transport tracking, allowing staff to focus on more strategic tasks. The integration with Moodle means that data flows seamlessly between administrative and academic sections, providing a complete overview of each student’s performance, attendance, and progress.
4. Simplified Communication
Communication between teachers, students, and parents is made easy with CuteBrains. Announcements, grades, attendance reports, and important updates can be shared instantly through the platform, keeping everyone informed and engaged. The integrated messaging system allows for direct communication, reducing delays and enhancing collaboration.
5. Advanced Analytics and Reporting
CuteBrains equips schools with powerful analytics tools that provide insights into student performance, attendance trends, and administrative efficiency. These data-driven insights help educators identify areas that need attention and enable administrators to make informed decisions that enhance school operations. The integration with Moodle ensures that academic data is always up-to-date and easily accessible.
6. Secure and User-Friendly Interface
Security and user experience are at the heart of CuteBrains. The platform is designed to be intuitive, ensuring that all users—from administrators to students—can navigate and utilize the features with ease. Data security measures ensure that all information is protected, giving schools peace of mind.
7. Tailored for Schools
CuteBrains understands the unique challenges faced by educational institutions. With customizable features, the platform adapts to the specific needs of each school, whether it’s managing handling complex fee structures, or aligning with national educational standards.
Conclusion
CuteBrains is not just a school management system; it’s a complete solution that integrates the best of administrative management with innovative learning. As India’s first Moodle-integrated system, it offers schools a unique opportunity to modernize their operations, enhance the educational experience, and stay ahead in the digital age. Transform your school with CuteBrains today and discover the future of education management!
6 notes
·
View notes
Text
Enterprise Resource Management: Essential Software Testing Services

Enterprise Resource Management (ERM) software is the backbone of modern business operations, ensuring that all aspects of an organization work in harmony. To maximize the effectiveness of ERM software, thorough software testing services are essential. Here's how to approach it:
1. Importance of Software Testing in ERM
Software testing ensures that all ERM modules function correctly, avoiding disruptions in critical business processes.
2. Key Areas to Focus On
Functionality Testing: Validate that each module performs its intended function.
Performance Testing: Ensure the system can handle expected loads without lag.
Security Testing: Protect sensitive business data from potential breaches.
Integration Testing: Confirm that the ERM integrates smoothly with other enterprise systems.
3. Common Challenges
Software testing in ERM can be complex due to the interdependencies between different modules. It's crucial to adopt a comprehensive testing strategy that covers all bases.
4. Tools and Technologies
Utilize advanced testing tools like Selenium, JIRA, and LoadRunner to automate testing processes and improve accuracy.
5. Best Practices
Regularly update test cases to reflect changes in the software.
Involve end-users in the testing process to gather practical feedback.
Conduct both manual and automated tests for thorough coverage.
6. Case Studies
Successful ERM implementations highlight the role of rigorous testing in preventing system failures and enhancing overall performance.
7. Final Thoughts
Implementing robust software testing services in your ERM project ensures smooth operations and long-term success. Ensure that your ERM software not only meets current business needs but is also scalable for future growth.
2 notes
·
View notes
Text
College Tools Education
Master Time Management
One of the first steps toward increased productivity is effective time management. Renowned publications like Harvard Business Review emphasize that time management is more about big-picture strategic planning rather than just everyday life hacks. It starts with setting clear priorities and understanding the difference between urgent and important tasks.
Here's how to get started:
Begin each week by mapping out major assignments, exams, and other obligations.
Utilize digital calendars and task management tools to keep everything organized.
Avoid multitasking as it can reduce the quality of your work and lead to burnout.
Develop a Study Routine
Studying efficiently is paramount for students who aim to grasp complex economic models and business strategies. Customizing a study plan that fits your learning style can significantly increase your retention and understanding.
Try these tips:
Dedicate specific times of the day to study when you're least likely to be interrupted.
Break down study material into manageable sections to avoid overwhelm.
Use active learning techniques such as teaching concepts to a peer or creating your own exam questions.
Utilize Multiple Choice Question Solvers
For exams, particularly those involving multiple-choice questions, students can benefit from technological advancements such as AI-powered multiple choice questions solvers. These tools can provide practice quizzes and instant feedback, which is essential for mastering the material.
Consider these benefits:
Immediate results help to quickly identify areas where more review is needed.
They resemble real exam formats, aiding in practice under timed conditions.
Some solvers can even offer detailed explanations for answers, enhancing your learning curve.
Enhance Productivity with Tech Tools
In the age of remote learning and digital tools, harnessing technology is vital for staying ahead. Many apps and software are designed to help with note-taking, project management, and collaboration. Our very own College Tools has a range of features that seamlessly integrate with your workflow in any Learning Management System.
Focus on tools that:
Allow for efficient note-taking and information organization.
Enable project collaboration in real-time with peers or instructors.
Offer customization to tailor the functionalities according to your productivity needs.
Balance Work and Leisure
As much as productivity is about working efficiently, it's also about resting effectively. Business and economics students should not underestimate the power of proper rest and leisure activities in maintaining a healthy work-life balance.
Here's how you can achieve balance:
Schedule breaks and leisure activities just as you would academic tasks.
Engage in activities that are completely unrelated to your studies to give your mind a break.
Practice regular self-care routines to ensure you're mentally and physically well.
Strategies from Industry Leaders
Emulating the productivity tactics of successful business leaders can also be enlightening. Outlets such as Forbes detail various approaches taken by industry professionals which can be adapted to your student life.
Key takeaways include:
Strict prioritization to allocate your best hours to the most critical tasks.
Delegation skills, which in a student context, means seeking help when you're overwhelmed, perhaps in the form of a study group.
Continuous learning and improvement, as productivity is a skill that can always be developed further.
Effective Use of Breaks
According to Lifehack, short breaks can play a significant role in maintaining productivity over long study sessions. Students should take regular breaks to stay focused and rested.
To make the most of your breaks:
Step away from your study area to ensure a change of environment.
Use techniques such as the Pomodoro Technique to structure time periods of focused study and rest.
Engage in activities that are rejuvenating, whether it's a quick walk outside or a brief meditation session.
The journey to becoming highly productive is a personal one, and what works for one student may not be as effective for another. It's important to try different strategies, measure your progress, and tweak your approach accordingly. Whether it's streamlining your study habits or harnessing the potential of digital tools, every small step towards increased productivity paves the path for success in the dynamic fields of business and economics.
2 notes
·
View notes
Text
Game Spotlight #4: Bulk Slash (1997)

Acquired Stardust’s first spotlight on a Sega Saturn game! Come join Ash as she takes a look at a game that never made it outside of Japan with 1997′s Bulk Slash!
The Sega Saturn has long been a fascinating subject to me, its rise and fall perhaps the culmination of a whirlwind of internal company politics and a rapidly changing landscape of both hardware and software. The attitude among gamers well into the 6th generation of consoles was as though its failure was a foregone conclusion not through any nuanced variety of factors, but because “duh, the Saturn sucked!”, the sort of take that time and hindsight allows to fester into a comfortable, easily repeatable opinion that you’ve heard enough people say that you too assume must be true.
But I’m happy to report that in my time experiencing a variety of titles on the Saturn in an attempt to satiate my longstanding curiosity, the Saturn doesn’t suck! In fact, the Saturn has been something that has consistently delivered games that surpassed my expectations. Daytona USA brought home a legendary racing title with a soundtrack as infamous as it is glorious (I’m personally of the opinion that Takenobu Mitsuyoshi is a genius and his involvement in anything always makes me happy), Capcom’s legendary run of fighting games was captured almost in its entirety on the Saturn, having ports of Street Fighter 2, the entire run of the Street Fighter Alpha series as well as Darkstalkers and what was at that time the entire selection of crossover games with Marvel, all of which looked significantly better than their Playstation port counterparts. SNK brought its own excellent array of arcade fighting game ports to home consoles in multiple King of Fighters releases alongside The Last Blade.
All of this is to say that the Saturn had something of a reputation as a system dominated by high quality arcade ports, which at the time was a significant thing to be able to say about a home console. It’s a talking point that has settled into that comfortable space of easily repeatable factoid that may or may not be true, but in this case it is. The Sega Saturn was indeed home to high quality arcade ports, but something that’s lost in that conversation is just how many interesting, experimental and high quality titles don’t fit the mold of ‘taking something you played in the arcade and bringing it home’ - the Saturn-exclusive games. One such example is 1997′s Bulk Slash, developed by a little-known company called CAProductions in partnership with since-defunct publisher Hudson. It was only the developer’s fourth game, and their first try at the emerging world of 3D games, a world in which conventional wisdom is that the Saturn struggled with.

Bulk Slash is something of a mix of Macross and Zeta Gundam, stylistically. An action game with a mech that transforms into a jet, featuring a story about military factions causing trouble of the genocidal variety to avenge alleged oppression. Switching freely between mech and jet forms, the main character Cress pilots his conspicuously Gundam-like mech in a campaign to defeat the Gardona military which has managed to wrap up his childhood friend Riizen into its ranks through political events prior to the start of the game. Playing out across seven stages each with different goals and a boss fight to close out the mission, the player can collect various score-boosting items as well as health recovery items and weapon upgrades not unlike Contra or Metal Slug. Bulk Slash controls remarkably well for a game featuring both a humanoid combatant in its mech running around shooting and throwing grenades as well as a jet, all while not utilizing a secondary right thumbstick for camera controls, which are instead relegated to shoulder buttons on the controller. The action is fairly fast paced with an impressive frame rate, only slowing down in instances of large chained explosions going off in certain circumstances. Just as well, the graphics and art style are quite good (almost reminiscent of the rise of the recent ‘2DHD’ art style), and the soundtrack very fitting for its time though not especially memorable.
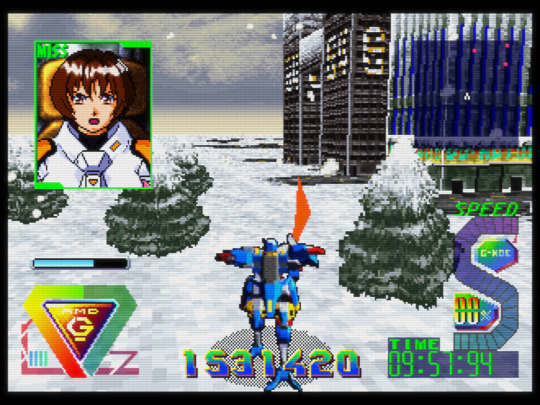
Layered into the fairly standard (albeit impressive) action gameplay is the ‘M.I.S.S’ mechanic (which stands for ‘Manageable Intelligent Support System’), a collection of 7 NPCs which must be located in each of Bulk Slash’s 7 stages serving as navigators for Cress, giving direction on the location of targets and bosses. Each of these NPCs are girls of various design, occupation and personality, including one who throws lots of English phrases into her otherwise Japanese speech which is very entertaining. Bulk Slash’s M.I.S.S system is more than meets the eye however, adding light dating sim mechanics into the game, with all 7 girls having their own endings and CG art unlocked depending on the player’s score upon defeat of the game’s final boss. It’s a small thing but really goes a long way in providing an experience that’s just varied and customizable enough. Having only 7 missions, the game is not especially long and only saves after successful runs through it after defeating the final boss, which itself has a boss gauntlet before it that can be a little rough while you’re still getting used to the game but if you put time into the game you’ll soon be able to defeat them without taking too much (or even any) damage, assisted by the fact that each of them seems to have timings for which you can score a critical hit, either dealing heavy damage or sometimes even outright destroying them in one blow.

Bulk Slash, as previously mentioned, was never released outside of Japan but the game is relatively simple to navigate and understand, being communicated very well visually. There was also a recent English translation patch which is a little hit or miss translation and localization-wise, but otherwise should assist people who don’t speak Japanese in understanding the story and character interactions, which is surprisingly good (and surprisingly dark at times) and a clear love letter to Universal Century Gundam.
Bulk Slash was the second Saturn game I ever played (after the all-time classic Daytona USA, for those wondering), and I’m glad it was such an early stop in the tour of the Saturn library because it shows off a lot of the strengths of the platform as well as bucking some of the usual talking points about the system, such as not doing 3D very well. It also layers in some of Japan’s big gaming trends at the time, such as dating sim elements most that most prominently and recently (at the time anyway) helped make Sakura Taisen a big hit on the platform just a year earlier. It’s a shame Bulk Slash never saw release outside of Japan as it would probably have done fairly well and be fondly remembered, and it’s definitely the sort of game that feels as though it would be pretty popular were it to have been an indie game releasing today.
A gem hidden among the stones, Bulk Slash is undoubtedly stardust.
--Ash
#Gaming#Video Games#Retro Gaming#Retro Games#Mech#Mecha#Sega#Saturn#Sega Saturn#Bulk Slash#Game Recommendations#Acquired Stardust#Ash#Gundam#CAProductions#Hudson#Hudson soft#Game Spotlights
13 notes
·
View notes
Text
What distinguishes an unmanaged (self-managed) VPS from a managed one And how can I figure out which suits me the best?
When looking at web hosting options, it is essential to have a solid understanding of the distinction between managed virtual private servers (VPS) and unmanaged VPS. Those who are looking for an experience that is simple to use will find that managed virtual private servers (VPS) provide convenience in server setup, maintenance, and support. On the other hand, unmanaged virtual private servers (VPS) provide you with complete control over the server, allowing you to customize and administer it in any way you see fit.

This type of VPS is best for people or enterprises who value flexibility and cost-effectiveness. In this post, we will discuss the important differences that will assist you in selecting the virtual private server (VPS) solution that is best suited to meet your individual requirements.
VPS: What is it?
First, let's get a grasp on what virtual private server hosting (VPS) is and how it operates before we move on to analyzing the distinctions between managed and unmanaged VPS hosting. Virtual private server hosting (VPS hosting) is a method of delivering hosting services in which a single physical server is partitioned into several virtual servers. The processing power (CPU), memory (RAM), and storage space utilized by each virtual server are distinct from those utilized by any other machine.
In spite of the fact that these virtual servers are established on a single physical system, they conduct their operations independently of one another. As a result of the shared underlying hardware, each user is provided with their very own dedicated virtual server, which is analogous to having a dedicated physical server but at a lesser cost. Each user's data and applications are kept separate and secure, exactly as if they were running on their own physical server because the servers are geographically separated from one another. This ensures that the servers are isolated from one another.
What exactly is a managed virtual private server?
As the name suggests, managed virtual private servers (VPS) mean that you do not have to worry about the responsibilities that are associated with the server, such as administering and maintaining your server. Your web hosting provider will be responsible for monitoring and managing all of the server's functionality. In spite of the fact that you are familiar with the technical features of the server and how to manage it, outsourcing the management of the server to your web hosting provider will alleviate the stress of carrying out all of the procedures.
The specialists who work for your web hosting provider take full responsibility for the resources on your server. They also keep a constant watch on your server to identify any potential issues, and they are responsible for implementing any necessary updates and upgrades. In particular, for users who do not have a lot of time to devote to duties that are related to the server.
The Benefits of Using a Managed Virtual Private Server-
Managed VPS hosting, also known as virtual private server hosting, provides a multitude of advantages, particularly for customers who are more concerned with the development of their applications or businesses than with the management of server infrastructure. Below are the primary benefits that come with using this service:
Firewalls, virus scanning, intrusion detection, and frequent security upgrades are some of the robust security features that managed virtual private server (VPS) software providers implement. Data is protected and cyber dangers are avoided as a result of this.
By delegating server management to a dependable web hosting provider, customers are able to concentrate solely on the operations of their businesses or the creation of applications without having to worry about the infrastructure of their servers, security concerns, or other problems.
The hosting service offers users round-the-clock technical help during their membership. This involves the installation of servers, their maintenance, and the diagnosis and resolution of technical problems in a timely manner.
Managed virtual private server (VPS) plans typically include data restoration and periodic backup services in the event that problems arise. Data recovery is made simple and expedient by the supplier, who is responsible for maintaining backups and setups.
The activities associated with server management are handled by the web hosting provider. These responsibilities include the configuration of hardware and software, the updating and patching of operating systems, the monitoring of performance, and the carrying out of frequent backups. Users will have less of a load as a result, and the server will continue to function in a stable manner.
Through the use of this service, users are able to gain access to the knowledge and experience of server management specialists. The availability of technicians allows for the provision of recommendations and the enhancement of server performance.
In general, managed virtual private server services provide higher levels of stability and constant uptime. In order to reduce the amount of time of the outage, providers utilize redundant infrastructure and monitoring technologies.
Managed virtual private server hosting is, in a nutshell, the best option for people and enterprises who require a high level of security, simplicity of management, and reliability. It provides a full solution for hosting websites and applications with little fees associated with the technical side of things and maximum peace of mind throughout the process.
What is the Unmanaged Virtual Private Server?
Your hosting provider will investigate a physical server and its availability when you use an unmanaged virtual private server (VPS). This means that you are responsible for managing and maintaining the server, as well as managing and maintaining the server itself. Choosing unmanaged virtual private server hosting necessitates either possessing the necessary technical expertise or employing a group of professionals to administer your server.
The use of an unmanaged virtual private server (VPS) is preferable for a well-established organization, regardless of how technically proficient you may be. The development of your company will be the primary focus of your attention if you are a startup. Your server management needs to be handled by a team and a full-time position in order to be successful.
The Benefits of Using an Unmanaged Virtual Private Server-
There are a lot of advantages to using unmanaged VPS (Virtual Private Server) hosting, particularly for users who are technically capable of managing their own server environment. The primary advantages are as follows:
Users are equipped with complete control, which enables them to install, configure, and optimize the server in accordance with their own requirements.
This presents users with the opportunity to increase their skills in managing and operating servers.
There is no dependence on third-party vendors for tasks such as software upgrades, and it may be tailored to meet personalized requirements.
Unmanaged virtual private servers (VPS) are typically more affordable than managed VPS because they do not include administration services, software upgrades, or technical support.
Security measures are under the authority of the users, who are responsible for ensuring their own safety.
The server can be customized in any way that the user desires, including the operating system, control panel, and software.
However, unmanaged virtual private servers are best suited for someone who possesses technical expertise or someone who can assist in managing the server. If this is not the case, a managed virtual private server (VPS) service, albeit being more expensive, can be a preferable option.
Which of These Options Should You Pick?
You are now aware that Managed Virtual Private Servers (VPS) and Unmanaged VPS each have their own set of advantages at their disposal. It is recommended that you go with unmanaged hosting if you are a professional in the field of technology, have experience maintaining servers, and have the ability to devote sufficient time to operating a server. If, on the other hand, you are a novice or a startup that has to concentrate on expanding your business, then managing a virtual private server (VPS) can be a laborious task.
The technical assistance that you receive with managed virtual private servers helps you save crucial hours. This enables you to concentrate on your primary goals, which may include managing your staff, making income, establishing relationships with customers, and other similar activities. Conversely, if you are concerned about the costs and have a good understanding of the server and how it is administered, then an unmanaged virtual private server (VPS) will be a better option for you.
Conclusion-
Users believe that it is dependable and risk-free to obtain a managed virtual private server (VPS) from a hosting provider, despite the fact that managed VPS is somewhat more expensive than self-managed VPS. This is because the price of managed VPS has decreased over time. It is also better to choose managed hosting if the procedure of setting up the server is going to have an impact on your company and take a significant amount of time.
Another aspect that should be taken into consideration is safety. It is not a bad idea to go with an unmanaged virtual private server (VPS) if you are willing to assume full responsibility for the safety of your server and be sure that it will be protected from the dangers that are there on the internet.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
A Comprehensive Guide to Power Systems Protection for Engineers
Introduction:
Power systems protection is a critical aspect of electrical engineering that focuses on safeguarding electrical equipment, personnel, and the power grid from faults, failures, and abnormal operating conditions. This comprehensive guide aims to provide engineers with valuable insights into key principles, techniques, and best practices in power systems protection.
1. Understanding System Operation and Fault Types:
Before delving into protection strategies, it is essential to have a solid understanding of how power systems operates and the various types of faults that can occur. This includes studying system components, such as generators, transformers, transmission lines, circuit breakers, relays, and protective devices. Familiarity with fault types like short circuits, open circuits, ground faults, and transient overvoltages is crucial as a foundation.
2. Principles of Protection Coordination:
Effective power systems protection requires proper coordination among protective devices. Engineers must understand the concept of selectivity to ensure that only the device closest to a fault operates, minimizing disruption to the rest of the system. Proper coordination involves selecting appropriate current settings, time delays, and coordination curves for relays and circuit breakers.
3. Relay Device Fundamentals:
Relays are an integral part of power systems protection, serving as the first line of defense against electrical faults. Engineers should have a thorough knowledge of different relay types, including overcurrent relays, differential relays, distance relays, and directional relays. Understanding their operating principles, features, and limitations aids in choosing the most suitable relays for specific applications.
4. Protective Device Coordination:
Coordinating protective devices within a system is critical to maintaining stability and preventing cascading failures during faults. Engineers must carefully analyze and design protection schemes that consider factors such as fault impedance, fault currents, relay response characteristics, and coordination margins. Advanced techniques like time grading and impedance grading can be employed to achieve optimal coordination.
5. Fault Analysis and System Modeling:
Performing fault analysis and system modeling helps engineers gain insights into power flow, fault currents, voltage profiles, and system stability. Engineers must be proficient in using software tools like ETAP, PSCAD, and DSA Tools to accurately simulate fault scenarios and assess the performance of protection schemes. Detailed knowledge of system modeling techniques enables engineers to make informed decisions regarding relay settings and coordination.
6. Communication-Based Protection:
With the increasing complexity of modern power systems, communication-based protection plays a crucial role in maintaining reliability. Knowledge of communication protocols such as IEC 61850, GOOSE (Generic Object-Oriented Substation Event), and SCADA (Supervisory Control and Data Acquisition) systems is essential for engineers to design and implement advanced protection solutions that utilize real-time data exchange between substations and control centers.
7. Integration of Automation and Control Systems:
Incorporating automation and control systems into power systems protection enhances operational efficiency and reduces response time during faults. Engineers need to understand concepts like remote terminal units (RTUs), programmable logic controllers (PLCs), and human-machine interfaces (HMIs). Familiarity with protocols like Modbus, DNP3 (Distributed Network Protocol), and OPC (OLE for Process Control) enables seamless integration of protection systems with wider control infrastructure.
8. Commissioning, Testing, and Maintenance:
Implementing effective protection strategies requires thorough commissioning, testing, and maintenance procedures. Engineers should be well-versed in practices like primary injection testing, secondary injection testing, relay calibration, fault simulation, and periodic inspections. Adhering to manufacturer guidelines, industry standards, and safety protocols ensures equipment reliability and optimal performance.
9. Access to Resources and Industry Awareness:
Staying connected with organizations like the IEEE (Institute of Electrical and Electronics Engineers) and IET (Institution of Engineering and Technology) is crucial for access to valuable resources. Engineers should actively seek research papers, technical articles, conferences, and networking opportunities. Staying informed about relay technology advancements from prominent manufacturers aids in adopting the latest protection techniques.
10. Software Applications for Enhanced Protection:
Utilizing software applications is vital in power systems protection. Advanced tools like ETAP, PSCAD, and DSA Tools aid in relay coordination analysis, fault simulation, and system modeling. Acquiring proficiency in these common industry software packages enables engineers to design and optimize protection schemes effectively.
11. Compliance with Local National Codes:
Adhering to local national codes and regulations is paramount in power systems protection. Understanding and implementing specific electrical codes and standards relevant to the country of operation is crucial. Compliance ensures safe and reliable system design, installation, and operation aligned with legal requirements and best practices.
Conclusion:
By encompassing the principles, techniques, and best practices discussed in this guide, engineers pursuing careers in power systems protection can develop a strong foundation. Continuous learning, staying updated on industry advancements, and compliance with local national codes will ensure engineers can design, implement, and maintain robust and reliable protection schemes for the power grid and its critical assets.
The Author Biography: Qusi Alqarqaz
Qusi Alqarqaz is an experienced professional in power system protection, specializing in sharing knowledge and guiding young engineers. With a career spanning utility and oil and gas industries in Texas, New Mexico, and Qatar, he has amassed extensive industry experience.
Collaborating with leading manufacturers such as SEL, ABB, Siemens, Schneider, among others, Qusi has gained proficiency in a range of protective relays. He actively pursues continuing education, completing professional development courses with software providers including ETAP and Milsoft, enabling him to utilize advanced tools for power system analysis and protection design.
Qusi's dedication to staying up-to-date with industry advancements led him to pursue additional training. He completed professional development courses at Wisconsin University, equipping him with specialized knowledge crucial for working with high-voltage power systems. He also studied power generation extensively at Strathclyde University in the UK.
Qusi actively shares his knowledge through collaborating on large-scale projects and providing training sessions for professionals. Through his posts, he aims to offer guidance and mentorship for young engineers in power system protection. His practical advice and personal experiences will empower the next generation of experts in this field.
Contact the Author:
Qusi actively shares his knowledge through collaborating on large-scale projects and providing training sessions for professionals.
Qusi Alqarqaz
9 notes
·
View notes