#Digital Devices
Photo
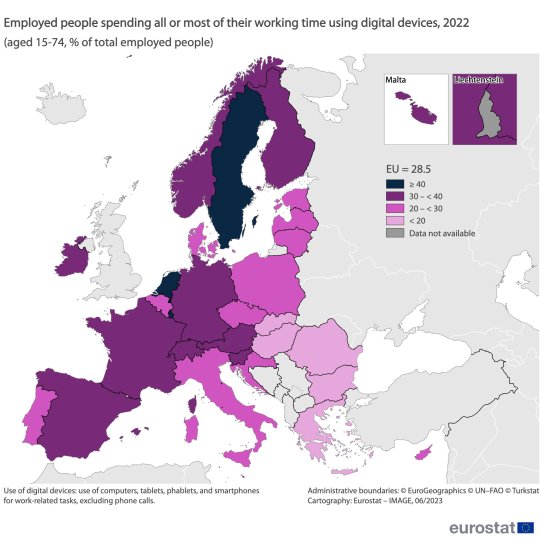
In the EU, highest rates for people aged 15-74 using digital devices for the entirety or most of their working time were in: Luxembourg (47% of employed people) The Netherlands & Sweden (41%)
Lowest: Romania, Bulgaria & Greece (all 12%)
by EU_Eurostat
83 notes
·
View notes
Text
Replacing physical buttons and controls with touchscreens also means removing accessibility features. Physical buttons can be textured or have Braille and can be located by touch and don't need to be pressed with a bare finger. Touchscreens usually require precise taps and hand-eye coordination for the same task.
Many point-of-sale machines now are essentially just a smartphone with a card reader attached and the interface. The control layout can change at a moment's notice and there are no physical boundaries between buttons. With a keypad-style machine, the buttons are always in the same place and can be located by touch, especially since the middle button has a raised ridge on it.
Buttons can also be located by touch without activating them, which enables a "locate then press" style of interaction which is not possible on touchscreens, where even light touches will register as presses and the buttons must be located visually rather than by touch.
When elevator or door controls are replaced by touch screens, will existing accessibility features be preserved, or will some people no longer be able to use those controls?
Who is allowed to control the physical world, and who is making that decision?
#i get why this is happening; it's way cheaper to buy an off-the-shelf touch kiosk or tablet and run your ui on a web server#rather than integrating with custom hardware and physical inputs#but that should not just removing accessibility features#and I know that digital devices can help a lot with accessibility: e.g. screen readers#but I wouldn't rely on any of those being installed on someone else's device
47K notes
·
View notes
Text
Discover the Latest Electronics Gadgets for Every Need
Discover a world of innovation with our collection of electronics gadgets. From cutting-edge smartphones to stylish watches and captivating home decor, explore a range of tech-forward products designed to elevate your lifestyle.
#Electronics#Gadgets#Tech#Innovation#Consumer Electronics#Smart Devices#Wearable Technology#Electronic Accessories#Cutting-edge Gadgets#Digital Devices
0 notes
Text
How digital tools are heading off alcohol-related health problems - Technology Org
New Post has been published on https://thedigitalinsider.com/how-digital-tools-are-heading-off-alcohol-related-health-problems-technology-org/
How digital tools are heading off alcohol-related health problems - Technology Org
Brian Suffoletto, MD, associate professor of emergency medicine, views interactions with patients in the Emergency Department as valuable opportunities to identify specific risks and then facilitate positive behavior changes post-ED discharge using digital devices.
He has spent more than 10 years developing digital behavioral interventions for various medical risks, from young adult binge drinking to distracted driving.
In this Q&A, we asked Suffoletto about his work and research into digital tools that can both recognize and address the negative impact alcohol use can have on a person’s health.
Many of your studies explore how digital devices can detect and reduce adolescent intoxication and binge drinking. Why did you choose to focus on this area?
Two of my close friends died in an alcohol-related car accident when I was in college. I also worked for many years in an inner-city hospital in Pittsburgh with a large referral base of young adults from various colleges, so I saw a lot of alcohol-related injuries and conditions in the emergency department.
Emergency medicine physicians have traditionally used a method called Screening, Brief Intervention and Referral to Treatment (SBIRT) that employs motivational interviewing techniques to try to persuade individuals to reduce their drinking.
But we rarely have the time or setting to effectively address the impact of alcohol use on a patient’s health. In addition, emergency department patients are often distracted, in pain or even intoxicated, so receptivity to those messages is low.
I started exploring using digital technology, including text messaging to reach people in small but repeated ways to influence health behaviors over time. With this approach, I was no longer constrained by the limitations of the hospital walls. I could, instead, identify emergency department patients at risk, then communicate with them afterward to try to influence their everyday decisions.
Can you describe recent machine modeling you and collaborators from the University of Toronto employed to predict intoxication based on measurable changes in voice?
Fluent speech depends on the rapid and precise coordination of more than 100 muscles orchestrated by high-level sensory, cognitive, and motor processes. So, you can evaluate a person’s voice on things like phonation (breathy, guttural, or creaky voice), pitch, loudness, rate, and other variables.
This study focused on frequency-based voice features – how loud a voice is — as these are particularly good at demonstrating levels of intoxication. We used tongue twisters because they act as a stress test, revealing even subtle disruptions in this intricate coordination system. Then, based on those measurable changes in voice, we built a model that predicted alcohol intoxication with an accuracy of 98%.
Tell us about the text message interventions to reduce alcohol consumption.
The best time to intervene is often prior to the behavior but soon enough to be contextually relevant. For instance, as someone starts drinking, a reminder of their consumption limits can be impactful. However, once a person is significantly intoxicated, these interventions are less effective. So, in one study we use collected voice data to identify the best time to intervene and then develop text messaging tools to help reduce risky drinking.
What advantages do digital devices offer in spurring behavioral change?
The reality is that we don’t always have someone to steer us away from bad life decisions and behaviors.
However, we are almost constantly tied to digital devices, primarily cell phones but also new wearables, so it seems natural to use these technologies to reach people.
There are two components to interventions — frequency and intensity. The whole idea behind just-in-time interventions is that we can identify periods of risk or opportunities for certain behavior, then use digital devices to nudge a person in the direction of healthy behavior at optimal moments.
It seems there is no magic formula for content in those digital nudges; it’s actually less about content and more about timing that can assist someone in self-monitoring. By being brief and focusing on short-term goals, we enable people to use their own intrinsic motivation, which is much more effective than lecturing.
You used smartphone accelerometer sensors to detect alcohol intoxication by analyzing an individual’s gait. How effective is a smartphone at detecting intoxication?
I’ve led several research projects to detect alcohol consumption remotely through digital biomarkers, analyzing GPS-tracked mobility, texting speed and errors, and gait patterns. In one gait analysis study, we had participants walk 20 steps with smartphones placed on their backs to record accelerometer data.
Then they drank enough alcohol to reach a breath alcohol concentration of .20% and repeated the same walk over subsequent hours, while we measured gait changes using the accelerometer data. We could accurately identify a breath alcohol concentration of greater than .08% more than 92% of the time.
How has this work evolved over time?
Using technology to influence behaviors is a double-edged sword. On one hand, an individual can influence a lot of people at once, and automated systems can have broad geographic reach. On the other hand, people’s expectations for how technology should look, and function are rapidly changing because of large language models and the advancements in chatbot technology.
It’s harder to retain the attention of the average individual through electronic mediums than it was 10 years ago, and new messaging modalities constantly pop up. However, text messaging use has remained constant over time and presents many opportunities to change health behaviors and hopefully help patients after they leave the emergency department.
Source: Stanford University
You can offer your link to a page which is relevant to the topic of this post.
#alcohol#amp#Analysis#approach#Behavior#biomarkers#cell#change#chatbot#college#colleges#data#devices#digital devices#Digital technology#direction#double#drinking#electronic#employed#Featured life sciences news#Features#gait#gait analysis#geographic#GPS#hand#Health#Health & medicine news#how
0 notes
Text
Digital leisure reading does little to improve reading comprehension for students - Study
For years, research showed that print reading, whether for leisure or school, improved developing readers’ ability to comprehend text. However, the explosive use of digital reading devices, constant access to these devices, and new types of reading materials have introduced new reading habits. Now, a new comprehensive review of research on digital leisure reading habits finds a virtually…

View On WordPress
0 notes
Text
The Secrets of Fingerprint Scanner Failures

Fingerprint scanners are like the locks on your digital devices, and your fingerprint is the key. They were introduced a long time ago, back in the late 19th century. It is the best way to keep your phone, computer, or even some doors safe.
But sometimes, these fingerprint scanners do not work. But sometimes it was a failure. We don’t always know why. It could be because your finger is wet, or there is dust on the scanner, or maybe your finger is not in the right position.
So, the mystery of fingerprint scanner failures is all about understanding why they sometimes do not work and finding ways to make them work better. It is like solving a little puzzle to keep your digital information safe.
Read More About: https://watchurday.com/the-secrets-of-fingerprint-scanner-failures/
#fingerprint scanner#fingerprint lock#fingerprintlock#fingerprint sensor market#technology#digital devices
1 note
·
View note
Text
Digital Age Stress: The Impact of Social Media & How to Fight It
In an era where nearly 80% of the global population owns a smartphone, many of us are more connected to our digital screens than we are to our own surroundings. Isn’t it ironic? The very tools designed to bring us closer, to broaden our horizons, are becoming silent culprits of our mounting stress.
Each time you reach for that sleek, gleaming device, do you ever stop to think—am I doing this out…

View On WordPress
#Adaptive strategies#Balance#Blue light#Breathing exercises#Call to action#Communication skills#Comparison trap#Coping mechanisms#Coping skills#Coping strategies#Coping techniques#Counteract stress#Curating digital space#Digital awareness#Digital detox#Digital devices#Digital environment#Digital era#Digital habits#Digital impact#Digital overconsumption#Digital platforms#Digital stress#Digital well-being#Dopamine-driven design#Educating#Educators#Emotional resilience#Emotional well-being#Ever-evolving nature
1 note
·
View note
Text
like father, like son 🦆
characters by @cassandraclare 🫶
#cassandra clare#artists on tumblr#shadowhunters#digital artist#tsc#illustration#cartoon#the shadowhunter chronicles#drawing#tlh#chain of thorns#chain of gold#chain of iron#the infernal devices#the last hours#clockwork angel#clockwork princess#will herondale#william herondale#james herondale#herondales#ducks#illustrator#funny#cassie clare#fanart
1K notes
·
View notes
Text

I found my one and only gomens fanart from 2019 so it had to be redone. Naturally.
#i didn’t draw the gals (azi & crawli) because I couldn’t draw meeeennnnn#anyway#here we are#i haven’t improved as much as I’d like because I don’t draw as much as I should#but it is what it is#am I Right fellas#good omens anathema#anathema device#good omens#good omens season one#good omens s1#redraw#art#artwork#my art#fanart#digital art#drawing
7K notes
·
View notes
Text
The Addition of Smart Devices.

One of the most prevailing parenting problems is technology. Children can get hooked with these digital devices for hours without blinking their eyes. This can surely trouble the parents. Whenever you try to take away the devices, they get angry and uncontrollable.
If you want to control it, it is better to get your kids to indulge in other activities as well. Get them interested in outdoor games, board games where you also participate.
Digital detox for teens; new research on mental health and social media; …
0 notes
Text
Evolution of SASE Architecture
You may have heard of different architecture principles within the context of security for networks generally and SASE specifically. The most common software architecture principles utilized by the industry in the SASE context include:
Single-pass Architecture
One-proxy Architecture
Run-to-completion Architecture
Scale-out architecture
Single-pass parallel processing Architecture
Create your security functions using the built-in
Cloud-nativeve Architecture
Isolation Architecture
API first Architecture
Slicing (E2E segmentation) Architecture
A lot of these design principles aren't new. Single-pass, One-proxy, Single-pass-parallel-processing, and Run-to-completion architectural principles have been popular since UTM (Unified Threat Management) days in the early 2000s, though they are known by different names before.
The primary purpose of these design principles is to create
Increased throughput through efficient use of resources.
Lower end-to-end latency
Lower jitter
Higher elastic (Scale-out) as well as Resiliency in the case attacks like DDoS threats to security companies
New security functions are introduced more quickly (Agility)
Integration of multiple security vendor functions, without introducing inefficiencies (Integration of the most effective technology)
Adoptability (Run anyplace)
Single-pane-of-glass
Evolution
One of the great things about the field of network security is the fact that it is ever-changing. It is constantly incorporating newer technology and deployment principles in each new version of its products. It also provides security against attackers with their advanced techniques.
However, the market for security in networks is typically dispersed. There are a variety of security companies that offer various security features. This is great for innovation, and should be encouraged and will continue. It is important to note that one vendor might not be able to perform every aspect of security.
As you will see If each vendor has an entire stack of security functions, there would be huge inefficiencies and that means huge costs. Furthermore, it may create delays, which could be an issue for certain applications. This is why it is essential to understand the more modern architectural concepts and practices. Software architecture should be designed so that it eliminates inefficiencies, but allows integration of different technology vendors for the highest security.
Before Convergence
Figure 1 as well Figure 2 represent two examples of examples of security in networks prior to SASE. Figure 1 illustrates Secure Internet Access, and Figure 2 illustrates an instance for Secure Private Access. Be aware that the sequence of security functions shown in these images is undetermined, and the order of execution is usually dependent on the deployment.
Secure Internet Access is traditionally obtained by using various security solutions as shown in Figure 1. This is because it's the Enterprise that purchases these security features, and places them in a chain of services. Because certain security functions require the proxying of links, it is known as chaining. It process is sometimes referred to as Proxy Chaining in the Industry.
Because each security system is independent and is available from multiple vendors, the functions are common across all solutions. Commonly, the functionality is traffic policing at ingress, shaping traffic at the exit point, traffic filtering to make sure that only the relevant traffic is sent to the proxies TCP termination of the client connection, a new TCP connection towards destination SSL/TLS interception (which also requires an on-demand certificate generator that emulates the certificate of destination) which comprises TLS encryption, decryption and TLS encryption as well as the authentication of proxy servers (Kerberos, the NTLM protocol, OIDC), HTTP 1.1/2.0 decoding. This is a common feature in every box/virtual appliance, by an estimate, consumes 50% of the computing power used by security solutions.
Secure Application Access is also done in a similar fashion by linking the security solution that is discrete, as illustrated in Figure 2. The common functions are the same for different security options. It's similar to the basic functionality of security products that are used to create Secure Internet Access. Some differences are the termination of SSL/TLS, instead of interception, and authenticating users using traditional methods, not proxy authentication.
The cost of common functions within security solutions can be as high than 50% of solution. The latency resulting from this type of architecture could increase by just a few milliseconds due in the use of chaining functions.
Another challenge that is faced by Enterprises using both virtual and physical appliances is scaling. The scaling issue was initially solved through the use of larger appliances or by assigning greater memory and CPU power to the security solutions based on VM. This is known as scale-up. In the case of demand constant in volume, it's logical for companies to invest for larger hardware and software. However, if the volume is high, Enterprises don't like to find money spent. Imagine a scenario where two days per year, traffic is more. What is the reason why Enterprises prefer to pay for these spikes throughout the year? That was the reason for the next step, when security companies began to provide the scaling of architecture with cloud-based services. This is similar to the rationale behind IaaS for IaaS in the Cloud applications. In the scale-out architecture that includes more instances of security software are created automatically when they detect the increased traffic or in response to DDoS attack , and brought down as demand drops. Image 3 illustrates the scale-out architecture.
It is clear that the ability to scale out is needed. But, it requires an load balancer for every security solution. The load balancer will be required to distribute the load across different instances of the security solutions. Multiple load balancer traversals demand more resources and can also increase the latency from end to end of traffic sessions.
The next evolution of the security architectures for network security addresses issues of
The need for more compute resources
Higher latency
With
One proxy architecture
Single pass architecture
Single-pass architecture and one-proxy architectural (Converged Architecture)
As illustrated in the figure below, each security function is combined with proxy and other commonly used functions coming into the picture just once. Each security function is executed one at a in a run-to completion fashion. In the end, this architecture uses up compute resources quickly. Since all functions are run within the same context of user space memory copies are omitted. Additionally, a single user space process architecture can reduce operating system context switching dramatically. A single proxy can manage multiple sessions simultaneously by using multi-threading, with each thread processing a portion of sessions, thus utilizing multi-core CPUs to the fullest extent. Multi-threading also permits certain security functions to be performed in parallel, instead of sequentially for a particular traffic session, thus reducing the speed and latency. This type of architecture is known as Single Pass Parallel Processing.'
To deal with unanticipated load and to address DDoS scenarios, an auto-scale-out architecture is implemented by utilizing a load balancer that is that is in the way of load balancing sessions.
In this design the proxy exposes an interface API. All security functions are connected to this API. Proxy invokes the relevant security functions in the course of traffic session processing. The security functions cannot implement through SASE Solution developers. SASE solution developers collaborate with technology providers by connecting technology supplier engines and feeds to the proxy servers. This way, customers of SASE service providers enjoy the all the benefits of technology suppliers - high performance SASE with the best security solutions.
However, certain technology providers may not offer Engine to users in SDK form to develop security functions in the proxy. It could be because they offer it as a cloud-based service. DLP is a prime example of how several technology providers offer it as a cloud-based service. In some instances it could be the case it is the SASE solution provider might not wish to incorporate certain security features within the user space context of proxy , for reasons such as memory restrictions and license compatibility and to avoid creating a weak user space and so on.
Unified Architecture & Bring Your Own Security Functions
The next step in the SASE structure is illustrated below. Three key points are as shown in Figure 6 below.
The support for security features using ICAP (Internet Content adaptation Protocol): Enterprises may use or want to make use of security services provided by other suppliers. ICAP specifications from IETF define how proxies are able to connect to external content adaption services, such as security services. In allowing external security services, SASE solution providers enable enterprise owners to choose from a variety of security solutions.
Make your own secure features: According to the IBM security report titled "Cost of a Data Breach Report 2022" organizations have an average of 277 days to discover and prevent a breach of data. Although SASE offers a very effective policy management, it may be that some data breaches control requires the use of programming rules. The organizations that are able to analyze the breach are in the best position to create these programs. Based upon SASE suppliers or other security solutions, the vendors could delay their product releases as they require the entire life cycle of software development. To prevent these delays and re-use the existing technology, new SASE architectures offer a means to allow Enterprises security teams to create programsmatic rules on their own and then deploy these rules. Because they won't cause instability for your proxy SASE designs provide WASM runtimes that allow the creation of programmatic rules in WASM modules. Because WASM runtime is a Sandbox, any issues that arise with WASM modules won't cause the hosting user space as well as other security function plugins to malfunction or fail.
Uniform proxy A single proxy that works for the two functions of Secure Internet Access as well as Secure Application Access will help reduce the amount of memory required. Engines and feeds for certain security features, like Anti-Malware and DLP can be memory-hogging. Setting up two proxy servers for an Enterprise site, therefore, can be expensive. Additionally, having one proxy that can support three modes (forward reverse, reverse as well as transparent) is a good development technique from a efficiency perspective too.
DIGITAL DEVICES LTD
Long before Apple set an average consumers mindset to replacing their handheld gadgets in two years, Digital Devices Ltd believed in Moore's law that computing will double every two years. With our heritage from the days of IBM Personal Computer XT, our founders have gone through the technology advancements of the 1990s and 2000s realizing that technology is an instrumental part of any business's success. With such a fast pace industry, an IT department can never be equipped with the tools and training needed to maintain their competitive edge. Hence, Digital Devices has put together a team of engineers and vendor partners to keep up with the latest industry trends and recommend clients on various solutions and options available to them. From forming close relationships with networking and storage vendors like Juniper, SolarWinds and VMWare to high-performance computing by HPE or AWS Cloud solutions, Digital Devices Limited offers the latest technology solutions to fit the ever-growing needs of the industry.
Our experts can guide you through the specifications and build cost efficiencies while providing high end, state-of-the-art customer services. We research and analyses market and its current demand and supply chain by offering wide range of bulk supplies of products like AKG C414 XLII, Shireen Cables DC-1021, Shireen Cables DC-2021, Dell p2419h monitor, Dell U2419H, Dell P2719H, Dell P2219H, Lenovo 62A9GAT1UK, LG 65UH5F-H and Complete IT Infrastructure products and services.
0 notes
Text
The Law Bytes Podcast, Episode 133: Michael Nesbitt on How the Senate Pushed Back Against a Government Bill on Searching Digital Devices at the Border
The Law Bytes Podcast, Episode 133: Michael Nesbitt on How the Senate Pushed Back Against a Government Bill on Searching Digital Devices at the Border
It isn’t every day that a Senate committee examines legislation and makes notable changes against the wishes of the government. But that’s what happened last month as a Senate committee reviewed Bill S-7, which raised significant privacy concerns regarding the legal standard for searches of digital devices at the border. A chorus of opposition sparked by Senator Paula Simons led to changes in the…

View On WordPress
0 notes
Text
Digital addiction | How to detox
Digital addiction | How to detox
Every morning, 12-year-old Amrita (name changed), lets her 592 friends on Facebook know what she did the day before. And there is plenty for this Delhi schoolgirl to post. “I wake up at 4.30 am and study till 8 am,” she says. Breaks between online classes are spent doing quick high-intensity workouts. Post school, there are guitar tutorials online, and homework to finish. Recently, Amrita…

View On WordPress
0 notes
Text

[Quiet Room]
Lyric comic to stop me going insane (its not working)
angstangstangst
lyrics are from the song Quiet Room by Yoh Kamiyama, specifically the rachie cover
#art#fanart#digital art#the amazing digital circus#amazing digital circus#the digital circus#tadc#tadc pomni#tadc ragatha#tadc fanart#buttonblossom#ragatha x pomni#pomni x ragatha#ragapom#jesterdoll#digital yuri#i have one framing device for scenes in this fuckinnnn stuff idk words#hallways are just good ok#buttercatrho art
975 notes
·
View notes
Text
Digital technologies can support healthy ageing and healthcare services for the elderly.

Looking at technology as a process, we will describe what digital, physical, legal, economic, and social structures make-up the environment where we need accessible design. The digital equivalent of architectural standards for ramps, walls, and steps, are technical standards, involving both software and hardware choices. Finally, a process being shaped by physical and virtual structures involves trade-offs, with inevitable social, economic, and technical consequences. These trade-offs are codified into patents, copyright, and consumer protection laws, and these in turn are shaped by the values of our societies.
#visual impairment#hearing impairment#digital devices#World Telecommunication and Information Society Day#World Health Organization (WHO)#17may#Digital Technologies for Older persons#disability
0 notes
Text

hi !! hello !! omg hello in there !!!!
#gamble the queue#art#my art#digital art#artists on tumblr#drawing#fan art#fanart#rain world#slugcat#rw rivulet#rain world rivulet#rivulet slugcat#hpw do i tag for. character has hand on device screen and is pressumably talking to viewer
214 notes
·
View notes