#Enhanced Database Security
Explore tagged Tumblr posts
Text
Leveraging gMSA for Enhanced Security in SQL Server
In today’s rapidly evolving cybersecurity landscape, securing database environments has become paramount for organizations worldwide. Among various strategies, integrating Group Managed Service Accounts (gMSAs) into SQL Server environments stands out as a robust method to bolster security. This article delves into practical T-SQL code examples and applications of gMSAs, offering insights into how…
View On WordPress
#Automated Password Management#Enhanced Database Security#gMSA Integration#SQL Server security#T-SQL examples
0 notes
Text
Big e-Aadhaar revamp on the cards! No more photocopies of Aadhaar card required, updation to become easy; check top steps
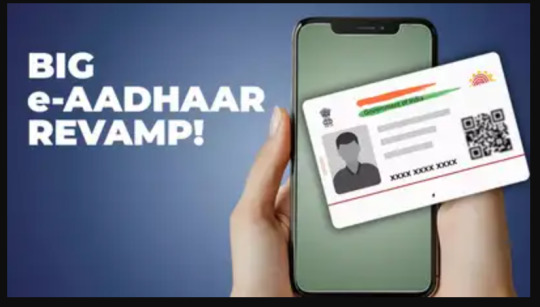
The Unique Identification Authority of India (UIDAI) is set to revamp e-Aadhaar, introducing a QR code-based system to eliminate need for physical copies. Updates, excluding biometrics, will be automated through integrated databases, reducing center visits.
Big e-Aadhaar revamp soon! In the coming weeks, a new QR code-based application will eliminate the need for Aadhaar card physical photocopies to be submitted. Users can share digital versions of their Aadhaar, choosing between complete or masked formats.By November, the Unique Identification Authority of India (UIDAI) is also planning to introduce a streamlined procedure that will significantly reduce visits to Aadhaar centres for updation.Except for biometric submissions, updates to address and other information will be automated through integration with various official databases. These include birth certificates, matriculation records, driving licences, passports, PAN cards, PDS and MNREGA systems.This initiative aims to simplify the process for citizens whilst reducing fraudulent document submissions for Aadhaar registration. Additionally, discussions are in progress to incorporate electricity bill records to enhance user convenience.Also Read | ITR filing FY 2024-25: Several changes in Form 16! Top things salaried taxpayers shouldn’t missUIDAI's chief executive officer Bhuvnesh Kumar has informed TOI about a newly developed application, with approximately 2,000 out of one lakh machines already utilising this new system."You will soon be able to do everything sitting at home other than providing fingerprints and IRIS," he said.e-Aadhaar Revamp: Explained in Top PointsThe application will enable users to update personal details including addresses, telephone numbers, names and incorrect birth date corrections.The introduction of QR code-based Aadhaar transfers between mobile devices or applications is considered essential for preventing misuse, with potential applications ranging from hotel check-ins to identity verification during rail travel. "It offers maximum user control over your own data and can be shared only with consent," Kumar said.The system can additionally be implemented by sub-registrars and registrars during property registration procedures to prevent fraudulent activities.Kumar indicated that UIDAI is working with state governments to incorporate Aadhaar verification for individuals registering properties, aiming to reduce instances of fraud.UIDAI has commenced discussions with CBSE and additional examination boards to facilitate biometric and other data updates for children, which needs to be completed during two age brackets: between five and seven years, and between 15 and 17 years. They are planning a dedicated campaign to address the pending updates, which include eight crore cases for the first update (children aged five to seven years) and 10 crore cases for the second update.Additionally, UIDAI is collaborating with various organisations, including security agencies and hospitality establishments, to extend Aadhaar services to entities where its use is not mandatory.Stay informed with the latest business news, updates on bank holidays and public holidays.
25 notes
·
View notes
Text
Greetings!

I am Dr. Stanford Pines, you may call me 'Ford' or simply 'Doctor'. I suppose it is about time I explore the World Wide Web, or the 'Internet'. There is much I still have to learn and figure out since returning to this dimension.
It seems I have fallen quite out of touch for the most part during the thirty years I was gone. It's frankly very impressive and jarring to see how so much has changed so I might take some time for me to properly adjust but I digress.
I travel through plenty of dimensions with my brother Stanley quite often to further my research. Nothing we can't handle now that Cipher is out of the picture so I will continue adventuring and learning.
I am glad to be of acquaintance to you all!
Ad astra per aspera
- Dr. Stanford Pines

OOC: HAHA- Here's a Ford blog because I genuinely couldn't help myself. My main blog is @matrixbearer2024! This Stanford Pines is very similar to the timelords from the Doctor Who franchise but other than that he's still pretty much the same. I'll mostly have him set post-weirdmageddon but I'm open to shifting whichever point in time for questions or RPs, have fun everyone!
P.S. Down below are insights to his character and inventory for anyone interested or planning to interact with him!

Doc's inventory:
Modified Sonic Screwdriver
Rift Manipulation: Creates and stabilizes interdimensional rifts using doors as conduits.
Wood Manipulation: Can interact with wooden objects, allowing for unlocking, modifying, or opening them.
Lock Picking: Can unlock doors and secure mechanisms electronically.
Repair Capabilities: Repairs mechanical devices, machinery, and certain types of technology.
Environmental Scanning: Gathers environmental data, hazards, such as toxins, radiation, or other dangers, detecting anomalies, and analyzing energy signatures.
Data Analysis: Capable of analyzing data from various sources and providing real-time feedback, which can be especially useful in scientific or technical situations.
Communication Device: Interfaces with various technologies for sending and receiving signals.
Universal Translator: Translates languages in real time, enabling communication across the multiverse.
Communications Device: Functions as a communicator to contact other beings or devices across dimensions.
Energy Emission and Manipulation: Emits energy pulses to create barriers, distract enemies, or manipulate technology as well as manipulating energy sources, allowing it to overload systems or temporarily disable them.
Holographic Projection: Can create holographic displays for visualization of data, theories, or environments.
Lock Picking: Bypasses and unlocks physical and digital security systems.
Thermal Regulation: Measures and adjusts temperature in different environments.
Frequency Manipulation: Disrupts or enhances certain technologies by emitting sounds at specific frequencies.
Medical Functions: Provides advanced diagnostics and medical support, which is due to Doc’s preparedness(paranoia) for unforeseen events. (e.g. scanning for vital signs, diseases, and medical conditions; performing rudimentary medical diagnostics and suggest treatments; minor surgical procedures, such as suturing wounds; administering certain medications or injections in emergencies)
Forcefield Manipulation: Can activate and control protective barriers or shields, adding a layer of defense in dangerous situations.
Data Storage & Retrieval: Stores information and interacts with databases, making it a powerful tool for research.
Manipulation of Atoms: Using the power of the infinity die, Doc’s sonic screwdriver can manipulate the energy within atoms of entities that have a tangible, alterable form. This ability allows him to rearrange or shift the physical properties of objects or beings.
Weaponized Function: Can shoot energy blasts, though this function was originally designed as a laser for electronic tinkering.
Time Manipulation: Has limited abilities to manipulate time within a localized area, such as slowing down or speeding up the perception of time for specific objects or people.
Emergency Beacon: Can emit distress signals to call for help or alert allies in emergencies.
Multi-Purpose Tool: Serves as a general tool for tinkering, adjusting mechanisms, and solving puzzles, which aligns with Doc's analytical nature and creativity.
Repair Box
Immortality: A set of nanobots that constantly repairs and heals injuries, rendering Doc functionally immortal. While he cannot die from age or illness, fatal wounds can still kill him.
Healing Factor: Non-fatal wounds heal rapidly, which allow the Doctor to recover quickly from injuries that would otherwise incapacitate others.
Phantom Pain: He experiences phantom pain from time to time, a side effect of the repair box, which sometimes immobilizes him during particularly bad days.
Journal & Pen
Eidetic Memory: While Doc has a photographic memory, he carries a journal where he records his travels, discoveries, and reflections. This is partly an emotional release and partly a way to process the things he can never forget.
Personal Reflections: His journal also contains musings, sketches, and insights into his more philosophical thoughts, which he tends to keep private.
Zygon Force Field Device
Personal Shield: A portable device that creates a personal force field around the doctor which protects him from the worst injuries in moments of danger.
Camouflage: For a temporary time, the advanced zygon technology refracts and manipulates light to turn Doc invisible to the naked eye. This can be activated and disabled manually.
Limited Durability: Though powerful, the forcefield can only take so much damage at a time before it needs to recharge.
Advanced Medical Kit
Comprehensive: This kit contains emergency medical supplies, medications, and advanced tools for situations where the repair box might not immediately be enough. The doctor’s paranoia drives him to always be prepared.
Multiverse Map
Hand-drawn: A rough sketch and collection of dimensions he’s visited or studied, filled with notes about potential dangers and anomalies.
OOC: Does Doc carry a phone with him? Nope! Thinks it's something redundant because of his sonic being able to act as a communicator at a rudimentary level. Granted, you're not going to get stellar audio or video quality from something like that, but it works throughout the multiverse so Doc doesn't bother. If you plan on having an OC or other character meet him through this route, it could be as a transmission to his sonic!

Doc's Appearance:
Since the time he received the repair box, Doc has been biologically frozen in a state where his physical body remains in its 40s.
Doc is standing tall at 6'2", no different from most iterations of his canon counterparts.
His coat the the same as the one he already uses in post-canon gravity falls, that hasn't changed aesthetically.
The doctor sports a suit because if he's going to kick butt might as well do it in style, he also switches between neck-ties and bow-ties because bow-ties are cool.
He wears sneakers instead of his boots since those had worn down and broken sometime during his travels and sneakers are just generally easier to replace.
Underneath all his dress-up though he's covered in scars from past battles and his old tattoos that he'd never had the time to get rid of.
His glasses still have a crack in them, mostly because he couldn't be bothered to get a new pair of bifocals anyway.
Always clean shaven, yes he still shaves his face with fire that has never changed.






Key Quotes About Doc:
"You don't need to look like a monster to be one."
"HAHAHAHA- I just SNOGGED Madame de Pompadour!"
"ALLONS-Y!"
"This apple sucks I hate apples-"
"Laptop. Gimme!"
"Who da man?! ..... Oh, well I'm never saying that again."
"Immortality isn't living forever that's not what it feels like. Immortality is everybody else dying because you can't."
"Goodness is not goodness that seeks advantage. Good is good in the deepest pit without hope, without witness, without reward. Virtue is only virtue in extremis."
"Sometimes the only choices you have are bad ones, but you still have to choose."
"The day you lose someone isn't the worst. At least you've got something to do. It's all the days they stay dead."
"Pain is a gift. Without the capacity for pain we can't feel the hurt we inflict."
"There's a lot of things you need to get across this universe. Warp drive, wormhole refractors. You know the thing you need most of all? You need a hand to hold."
"Love is not an emotion. It's a promise."
"The universe is big. It’s vast and complicated and ridiculous. And sometimes, very rarely, impossible things just happen and we call them miracles."
"Some people live more in 20 years than others do in 80. It’s not the time that matters, it’s the person."
"I’m the doctor, and I save people."
"First thing’s first, but not necessarily in that order."
"You want weapons? We're in a library! Books! Best weapons in the world!"
"People assume that time is a strict progression of cause to effect, but actually from a non-linear, non-subjective viewpoint— it’s more like a big ball of wibbly wobbly… time-y wimey… stuff."
"I’m about to do something very clever and a tiny bit against the rules of the multiverse. It’s important that I’m properly dressed."
"Arrogance can trip you up.”
"Do what I do: Hold tight and pretend it’s a plan!"
"You’ll find that it’s a very small universe when I’m angry with you."
See the bowtie? I wear it and I don’t care. That’s why it’s cool."
"Big flashy things have my name written all over them. Well… not yet. Give me time and a crayon."
"Never cruel or cowardly. Never give up, never give in.”
"Rest is for the weary, sleep is for the dead.”
"You don’t want to take over the universe. You wouldn’t know what to do with it beyond shout at it."
"Never be certain of anything. It’s a sign of weakness."
"Courage isn’t just a matter of not being frightened, you know. It’s being afraid and doing what you have to do anyway."
“Why do humans never do as they’re told? Someone should replace you all with robots. No, on second thought, they shouldn’t, bad idea.”
"You know, the very powerful and the very stupid have one thing in common: they don’t alter their views to fit the facts; they alter the facts to fit their views.”

#ford#ford x reader#ford pines#grunkle ford#gravity falls ford#gravity falls#gravity falls au#gravity falls stanford#gf ford#stanford pines#stanford pines x reader#ford x you#stanford pines x you#stanford x reader#gf stanford#stanford x you#gravity falls roleplay#gravity falls rp#gravity falls ask blog#gravity falls rp blog#intro post#introduction#blog intro#ford pines x reader#ford pines x you#stanford fanart
59 notes
·
View notes
Text
More Quirk Ideas
Continuing with my last post, here's a few more categories of quirks I came up with including technology, light, darkness, and time.
Technology:
datastream | user constantly absorbs data and information. user can turn said data into enhancement.
mind database | user can search through a collection of minds in a 1,000 mile radius.
static | user’s body is made of TV static that they can bend to their will. can disguise their body as someone else’s.
pulse | user can emit various different types of pulses. this includes pulses of radio waves, light, energy, etc.
viewpoint | user can place viewpoints anywhere they’ve been and mentally flick through them like security cameras.
error | user can digitize their consciousness and enter computers and interfere with software.
USB | user can pull USB sticks out of their arm that allow them to implant their consciousness into a device.
Light:
prism | user can absorb and manipulate light.
display | user can display a 3d hologram of anything they wish.
Energy/Electricity:
acceleration | user can create an energy that they can use to accelerate their speed, senses, reactions, etc. they can use it to affect things outside of their body, but they cannot control what they accelerate.
energy | user gathers energy constantly. they can use the energy they gather to enhance their body or create simple things like shields or blades.
radiation | user can generate and manipulate radiation.
energy exchange | user can exchange their exhaustion for energy and vice versa through proximity.
Darkness:
shadow crow | user can transform their shadow into crows. user can trade senses with any one of their crows. crows can combine. crows have a collective consciousness.
Time:
timefreeze | user can slow down the time of anyone they touch. the more fingers, the slower their time.
retry | user can return the state of a person to that of three days ago.
repair | user can return the state of an object or space to that of three days ago.
return | user can return objects to their hand that have left their hands within a timespan of three days.
45 notes
·
View notes
Text
cw: violence
Lena checked her watch. She only had a few minutes to pull this off, and had to time it perfectly. Lex was across town meeting with an investment consortium from Japan.
Officially.
She knew what he was planning. She just lacked the proof she needed. Once she had it, she would go to the media through her best friend and confidant, Kara Danvers. She had eyes on Lex right now as he met, in secret, with a Kasnian agent, the same one who'd help him orchestrate the theft of a prototype Lexosuit; that had been one of the first times that Superman had shut down one of Lex's schemes, and earned his undying hatred.
Lena needed the final piece of the puzzle before she involved Kara and pulled her into the danger of her private little war with her brother. This was so far beyond anything Lex had attempted that Lena knew now was the time, she had to stop him now, today. The line had to be drawn here, and no further.
The secure lab was deep in the bowels of the Lexcorp Tower in Metropolis; Lena made the excuse of a meeting with some of the research team working on battery enhancements for the upcoming line of Lexmobiles. (Lena had spent hours genuinely trying to talk Lex out of that god-awful name, and actually call them something marketable, but his towering ego was as immovable as it was monumental)
Lena's heart was racing as she stepped out of the elevator, carrying her briefcase under one arm. She strode down the hall like she owned the place (she did, actually- or half of it, anyway) and made sure anyone watching on the security feeds would pay her no mind. She'd worked here for years; even though she'd moved to National City to lead her own division, away from Lex, Superman, and all the drama, she was not an uncommon sight in this place.
Maybe here.
Lena stopped at the door, a heavy steel slab six feet wide and eight feet tall. Breath catching, she slipped her hand in her pocket and slid her finger through the ring she carried there. When she pulled her hand out, an image inducer created a perfect replica of Lex's hand around her own, projecting the unique contours and ridges of his palm and fingertips while simulating his pulse and unique vitals.
It was either going to work or it wasn't. She pressed the false hand to the sensors and waited. It beeped twice and turned a healthy blue.
The door let out a rush of cool air as it slid silently aside, its motion mirrored by an inner door of the same dimensions sliding in the opposite direction. Lena stepped through and removed the ring; the doors slid ominously closed behind her, latching with a heavy thunk as wrist-thick steel bolts slid home, anchoring them in place.
She knew that not only was the entire room lined with lead, but the lights could instantly switch to a red wavelength and the long sliding panels on the wall would open to reveal K-Radiator emitters. This room was designed to be a death trap for Kryptonians, should one be foolish enough to enter. That was why Lena had to do this alone.
Supergirl would rush in where angels feared to tread, and given the chance, she'd barge through those doors and end up helpless on the floor, at Lex's mercy to murder without witnesses. Or worse.
The lab was smaller than she expected, and Spartan. Despite her brother's notorious, arrogant grandiosity, he could be relentlessly practical when needed, and at heart was utterly ruthless. Lab benches lined the walls, and the computer was no different, visually, from any other workstation, though it was connected to a vast private database and would have very difficult encryption and security protocols that no one in the world could crack.
No one but her.
The far end of the room was dominated by a peculiar machine, resembling an incubation chamber of some kind, roughly human-sized and surrounded by thick steel cables and tubes, with several dozen monitors rigged up all around it, displaying all sorts of information.
Including biorhythmic data and vital signs.
Lena ran a hand over the steel of the external pod. It was warm.
Her throat tightened. This might be worse than she thought.
Turning to the terminal, Lena sat down on the stool and took from her bag a small portable drive and connection cable, setting them on the desktop in front of her. Lex had one of those drinking birds dunking placidly away at a glass of water on the desk, another bit of his peculiar humor. She'd once loved that about him, before his joking took on a mirthless, cruel streak.
Letting out a slow breath, Lena wiggled the mouse and woke the computer. It demanded a password, pass phrase, and passkey. The two she had, the latter was what the drive was for.
She typed BUCEPHALUS in the password field, then THY FEARFUL SYMMETRY in the pass phrase field, then clicked the cursor into the last box and plugged in the drive, and waited.
The program loaded automatically. If she made an attempt to brute-force the passcode, it would set off the alarms and possibly even trigger a deadly trap in this room. Lena had to crack it without cracking it; it took her months to create this algorithm, with the secret and begrudging help of Querl Dox at the DEO. He'd been concerned about it falling into the wrong hands; he was right to fear that, as it could crack virtually any system in seconds.
It did exactly that, filling in the require passcode. Lena clicked the LOGON button and let out a soft cry of relief as the screen lit up with Lex's desktop.
He had a series of folders waiting, just sitting there ready to be opened. The folders had names like LEXOSUIT, PARTICLE EMITTER, BINARY FUSION GENERATOR, SPATIAL DISTORTION CANNON, POINT-TO-POINT TRANSMATTER... and PROJECT GALATEA.
Lena opened that folder, and found a series of video files. She opened the first one, dated over a year ago.
Lex' face appeared, the man himself seated in this very lab.
"Mother stole Supergirl's DNA and used it to breach the Fortress of Solitude. She walked those hallowed halls, and didn't invite me! Not only that, she took only one device, when Superman's precious armory was right there for the taking! Is everyone a fool? Am I doomed to be surrounded by incompetents?"
He took a deep breath.
"It doesn't matter. There's enough of what she took left to comprise a viable sample... all I need is time, and I had that in abundance now that I've taken care of that nosy Gotham prosecutor that was working with Superman. He's too busy robbing banks to bother with me, and with the Metropolis police and GCPD in my pocket, Superman and that flying rat of his have nowhere to turn."
Flying rat? What the hell was he talking about?
Lena skipped a few files ahead.
"We'll call her Project Galatea. My initial plan -to create a limited-use drug that would produce Kryptonian superpowers- has been a failure. Nor was I able to successfully create a viable clone."
Lena's stomach sank. Clone? Clone? Had Lex tried to clone Supergirl? Was that was this equipment was for?
"Then it hit me- I could complete the project another way, by filling in the gaps in her DNA, but that still didn't solve all the problems. There was a missing component- I still don't know how Kryptonians actually absorb and process sunlight, for one. Still, that seems to be solving itself. Galatea's cells are absorbing the artificial solar energy that I'm pumping into her maturation chamber at a geometric rate. She might be even more powerful than her mother by the time she matures."
Lena jerked to her feet, a chill running through her body. Mother? Wait, did he mean-
Oh. Oh God.
Lena let the video drone on in the background as she moved back to the chamber. It was encased in steel plating, but it was designed to open. Lena found a pair of goggles on a work table near the control panel and put them on before flipping a switch.
The panels rotated, exposing a human form lying at an angle at rest on a padded platform. A respirator, like a flight mask, was strapped to her face, and she was submerged in thick, bubbling liquid. The chamber would have been too brilliant to look at, if Lena hadn't put on the goggles. It was flooded with brilliant solar radiation.
She'd put the inhabitant between ten and twelve years old, with golden skin and dark hair. Lena blinked a few times; it was like looking at an old picture of herself, actually.
For a brief moment, she just stared.
Then it hit her, and she almost vomited as she shoved the switch and closed the doors over the maturation chamber, stumbling back as she retched.
What did he do?
What did he do?
"I see you've met your niece."
Lena whirled, and found Lex staring her down, standing in front of the lab doors with his hands clasped behind his back, a satisfied smirk on his face.
"How... what... what the fuck did you do, Lex?"
"I think you've already pieced it together."
"Why?"
"Why?" said Lex. "I'll tell you why. Security. The security of a free state, sister. I did it because it had to done."
"This is... this is obscene," said Lena. "This is a violation, Lex. I'm not going to let you get away with it."
He laughed. "Get away with it? What do you mean, get away with it? What are you going to do, sue me for custody?"
"You... this is monstrous, Lex."
"We live in a world of monsters, dear sister," said Lex, stepping closer. "Gods and monsters, and who are we? Men, just men. There's whole universe out there, a multiverse, full of these creatures, and the human race is defenseless against them, and worse, they're being welcomed. They're eating of those Kryptonians' palms, you included, and now there are more of them. The green freak claiming to be a Martian. The so-called Amazon. There's seven or eight of them running around. Eventually it'll be twenty, then thirty, then more. They'll run roughshod over our institutions."
"You're out of your mind," said Lena.
"Am I?" said Lex. "Superman and Supergirl claim they fight for truth, justice, and the American way, right? What if their definition of justice doesn't match ours? What if they decide the American way isn't good enough? What if they decide they need to do more than pull kittens out of trees? Then what? Tell me, Lena, what happens if Superman decides to fly down tomorrow and tear the roof off the White House?"
"He wouldn't do that," said Lena. "I've met him, and I know Supergirl. She's saved my life a dozen times, and I suspect you know exactly what I'm talking about."
Lex shook his head. "Mother's extremism has always been a burden. I've done my best to protect you from her, Lena, and I've been honest about it. That's more than you can say for Supergirl."
"You kept this from me," said Lena.
"Until I was ready. I had to be sure that she was viable before I bring her out of the chamber and introduce you. She's going to be part of the family. Our long lost cousin, who we'll raise as a daughter, knowing that the Earth is truly safe now. That we'll have one of them on our side."
"This... this is Supergirl's child."
"That won't be a problem," said Lex. "It's time for you to grow up and let go of these fantasies, Lena. Supergirl doesn't have any interest in you. You're nothing to her, at best a beloved pet."
"I believe in her. We've worked together."
"I said the same thing about Superman. You know how close we were."
"It's not like that."
Lex's smirk turned cruel. "Isn't it? You've always had a type."
'Fuck you," Lena spat.
He chuckled softly and shook his head. "You're not listening. I guess I have to prove it to you. Computer! Show her."
The droning video log of Lex discussing the problems of merging Kryptonian and human DNA stopped, and another one popped up, taking the entire screen. Lena almost didn't look, but her head turned inexorably and she watched.
"Kara?"
Lena watched Kara Danvers walking down a corridor. She stumbled, as something hit her back, twice. Whatever it was tore holes in her cardigan, and she turned around, standing tall. Taller than usual. She didn't move this time; it was as if little puffs of wind were blowing holes in her clothes.
Except they weren't puffs of wind. They were bullets; Lena could see the muzzle flashes, off camera.
"What... how..."
Kara yanked her glasses off and shook her hair free, ripping the cardigan open, popping the buttons, baring the sweeping crest on the chest of her her blue uniform.
"No," Lena whispered.
"I sent the men who shot her in this recording," said Lex. "Don't worry, I already knew; Mother told me. The alien confessed it to her, before begging her not to tell you. I wonder why."
The video ended.
"This is a trick. She wouldn't... she isn't... she's my best friend."
"No, she's your master and you're an obedient dog, heeling where she tells you, and if you aren't... do you know what happened to the assassins I sent to kill Kara Danvers?"
Lena swallowed. "Shut up, Lex. Stop talking."
He smiled, teeth bared in a wolfish grin. "The martian mind-wiped them. He uses his psychic powers to erase the memories of anyone who compromises her identity."
"Stop," said Lena.
"Ever have any... episodes?" said Lex. "Any of those days, where you were so busy your memory gets a little foggy? Ever find yourself back in your apartment without quite knowing how you got there? Are you sure your own memories haven't been tampered with, Lena?"
"Shut up!" she screamed.
"You've been manipulated, tricked, deceived. She doesn't love you, she never will, and you have nowhere to turn. Help me, Lena. Join me, and we can be a proper family again. We can put things right, and lead a free world to-"
Lena reached into her pocket and pulled out a nickel plated Smith and Wesson Ladysmith revolver with faux-ivory grips bearing Lena's initials. Lex gave it to her on her twenty-first birthday, and went with her to the range the next week to teach her to use it.
"Oh," said Lex.
Lena shot him. The blast was ear-splitting in the confined space, leaving a painful ringing in its wake. Lex crumpled, toppling onto his side as if his strings had been cut. Rolling onto his back, he stemmed the gushing of his lifeblood from the wound just below his ribs and looked at her.
"Didn't think you had it in you," he rasped. "Should have known you'd be the one. You can only count on blood."
Tears stung her eyes, blurred her vision. Lena held out the weapon, her grip trembling as she aimed at his head.
"You'll never stop," she choked out. "You'll kill her. She'll never be safe as long as you're alive."
Lex grinned, the corners of his mouth wet with blood. "Do it."
Lena's finger flexed, but the trigger felt frozen in place. As it shifted slightly, a flood of memories slammed through her- shooting lessons and chess games, strange idle fancies and muted conversations, long rides in the back of sedans. Lena's graduation, Lionel's funeral, Lillian's abuses, Lex standing between their father and Lena with a bruise on his jaw, warning the old man not to lay another hand on her.
A sob tore from her throat. She couldn't do it. She couldn't.
Lex laughed flecks of blood onto the floor.
"Go on, then. I don't need you. I have my own Kryptonian, and she's going to be daddy's little girl."
It was as if the rain suddenly stopped, the sun cracking open the clouds. The gun was terribly loud again, and Lena turned away before she saw the shot connect, looking away from the blood fanning out across the floor as Lex went silent and still.
Shoving the still-hot gun back into her pocket, Lena ran.
Thought I'd share a little bit more from the in-progress Curse of Strahd AU/Crossover!
#supercorp#supergirl fanfiction#supergirl#supercorp fanfic#lena luthor#kara danvers#kara x lena#karlena#supergirl fanfic#lex luthor#spookycorp coming a little early#this is how it starts#lex isn't done yet#he's about to meet a vampire#Lena and Kara are going to have to work things out#then they're going to have to fight about it#then kiss about it#then fight a vampire about it#the entire multiverse is in danger and they're gonna kiss about that too#only the power of love can save the multiverse from the curse of strahd
149 notes
·
View notes
Text

CHECK THE FOLLOWING FOR PREVIOUS LORE INSTALLMENTS :CHAPTER ONE : RECALL. | EVENT : HELL WEEK. | CHAPTER TWO: THE MOLE. | HELL WEEK CLOSING BRIEF. | OPERATION WHAC-A-MOLE. | THE MOLE CLOSING BRIEF. | CHAPTER THREE : THE VILLAGE. | EVENT : CONTAGION CONTROL. | BOOK ONE : THE HALOCLINE. | CHAPTER FOUR : THE REPRIEVE. | CHAPTER FIVE : THE CALM BEFORE. | CHAPTER SIX : THE STORM.

PANDORA DIRECTIVE MEMORANDUM CLASSIFIED — INTERNAL DISTRIBUTION ONLY to : ALL AUTHORIZED OPERATIVES from : OFFICE OF THE DIRECTOR subject : OPERATION THALASSOPHOBIA
twelve hours ago, czernobog launched a full-scale invasion into atlantis, breaching perimeter defense systems and engaging agents of pandora in multiple sectors. the assault�� began with cybernetically-augmented foot soldiers entering through the hangar, then followed by coordinated mutant incursions across levels 01 through 09. their objectives included the dismantling of our command structure, retrieval of classified mutation data, mass destabilization of the facility, and the retrieval of our now declassified alien lifeform and namesake of our program, pandora. however, agents of pandora are not to be trifled with. thanks to the combined efforts of active combat units and support divisions, pandora successfully foiled the assault and eliminated key czernobog personnel such as velezlav zherdev and alexei dragunov. any surviving enemy units have been captured or eliminated. nonetheless, this victory comes at a great cost. confirmed fatalities include : rift — killed by czernobog mutants. mandela — killed by czernobog mutants. phoenix — killed by cybernetically-enhanced infantry at the hangar bay. oracle — sacrificed himself at the hangar bay. climax — killed by cybernetically-enhanced infantry at the hangar bay. elysium — killed by a czernobog mutant. jumpscare — killed by a czernobog mutant. other notable outcomes include : legion — out of commission. comatose state. bloodborn — out of commission. comatose state. prometheus — temporary death. alchemy — missing in action. surveillance shows him disappearing into thin air after evacuation into a pandora safehouse. his disappearance is being investigated for possible extradimensional, extraterrestrial or preternatural reasons. the service and bravery of our deceased agents directly contributed to the survival of over one-hundred fifty personnel and the preservation of humanity's greatest line of defense. their records are being archived with highest distinction. memorial proceedings will be announced following stabilization of atlantis, led by our temperance division and remaining porter models.
atlantis�� also sustained critical structural damage, including but not limited to :
> structural attrition on levels 01 to 02. > partial collapse of the corridor toward the gifted serum and cloning laboratory. > total loss of six exit corridors and 37% of ventilation systems. > entry into the command centre is currently unavailable due to compromise to its structural integrity. sloth agents and support staff will work in the war room for the meantime. > the library of alexandria is temporarily out of service and 45% of our archives have been destroyed. > partial loss of energy routing on levels 04 to 07. electricity is available but beware of disturbances and blackouts. > server systems and databases are currently only partially operational, however, our security and surveillance system are 100% functional. > our life model decoys have reduced numbers due to technopathic compromise by a czernobog agent. > destruction of various operative apartments and compromise of habitation utilities. [ agents with affected residence are suggested to find another undamaged residence to temporarily settle into while renovations commence. ]
reconstruction efforts have been started by our remaining derek and manny models, however, agents without current mission assignments are also asked to assist in repairs. if any operatives find other structural damages, please report them to your omega clearance channel.
[ MORE INFORMATION UNDER THE CUT. ]
while reconstruction efforts have began, pandora has also expedited various scientific operations. agents toxin, shepherd, elixir, and lifeweaver have been delegated to study biliquis and anomaly's mutations in hopes of improving the gifted serum without the need for the two-year isolation and physical conditioning period. agents goblin, killshot, charon, and gridlock have also been requisitioned to study czernobog's cloning technology and begin initial experimentations with trials on biological samples and uploaded memory by deceased agents. more information about these scientific endeavors will be made available once breakthroughs have been made.
however, perhaps the most important disclosure is the truth behind project pandora.
> pandora is an archivist, an alien species capable of storing biological, environmental, and cultural data within their own molecular structures. > her homeworld was destroyed by an invasive empire known as the starwalkers. > alongside another archivist, moryana, she fled across galaxies in search of safe havens and planets untouched by the starwalkers. > pandora crash-landed on earth in 1947 ( historically known as the roswell incident ) ; moryana's craft later crashed in 1959 ( believed to be responsible for the dyatlov pass incident ). > pandora was discovered and protected by human scientist dr. sieger ackermann who founded project pandora, naming the program after her. together, they began using her biological matrix to enhance and weaponize compatible human dna to create mutant soldiers as defense against possible future attack by the starwalkers. > moryana was intercepted by czernobog. his dna is believed to be extracted forcibly, resulting in unstable mutant offspring.
however, pandora also revealed that she is terminally deteriorating. it is finally disclosed that pandora's box is not just a training room, but also a biopsychic interface built to shelter her body and simulate potential threats and scenarios using what remains of her reality warping abilities.
and while pandora continues to help humanity by training and providing parts of herself to our operatives, she has asked for our assistance with retrieving moryana as potential means of biological repair— through inhabitation of moryana's form. pandora also implied an alternative, but we do not believe this is a choice she wants to make yet : selecting a viable human vessel.
nonetheless, the work is not over yet, agents. as soon as atlantis returns to at least 75% functionality, missions will be given out once again to take out czernobog's remaining forces and affiliates— until there is permanently nothing left of them. but please take these couple of days to mourn those we lost, to celebrate our victories, and to help in rebuilding our home. thank you, agents of pandora.

OOC INFORMATION.
holy shit ! another book is closed, agents ! this has been a rollercoaster of a season— from a beach episode, to a tournament arc, to agents getting kidnapped and another group fighting the clones of those kidnapped agents, to a fucking invasion into atlantis and the reveal to our real overarching plot involving aliens ! so much has happened, but i promise that the action will not stop. projectpandora still has so much to offer, and i can't wait for all of us to collaborate on what the future will bring. but as always, i just want to thank everyone for the continue support for our little rpg. i always say that this rp would be nothing without our amazing members who continue to participate, read, react, write, and plot in this community we have built and i truly do mean that. i have nothing but love for everyone who has been here with us since the beginning, for everyone who recently joined, and for everyone who joined sometime in between— i know, i know, these plots are insane and there's so much to read sometimes, but i can't help it !!! you all inspire me to create batshit plots all the time !!! but as for what's coming next : stay tuned for our chapter seven intro post, but it'll be basically be about the rebuilding efforts and future dash / discord missions. so feel free to start those aftermath threads and they will just be continued into chapter seven. also expect a patch update regarding the gifted serum and the cloning technology. and seven chapter in, but we'll also be giving out our first task ! and while it isn't mandatory, we do recommend that you do it as it will help you figure things out for the upcoming ninth chapter / third book finale. and chapter eight will be dedicated to moryana's retrieval and continuation of those dash / discord missions. but what i'm really excited for is our chapter nine event, but more on that later ! please like this once you've read, and thank you again everyone for another fun season !
7 notes
·
View notes
Text
The Bear Casting Call March 14


To apply read instructions below:
Entertainment Partners, the parent company of the POP platform - now known as the EP Casting Portal - that we use at 4 Star Casting, has sent an email saying that you will need to reset your password and set up two-step authentication moving forward.
Multi-factor Authentication (MFA) will be required for all users accessing the 4 Star Casting EP Casting Portal!
MFA enhances security and reduces the risk of unauthorized access by providing an extra layer of protection.
What You Need to Do:
You must reset your password and set up MFA on your mobile device before logging in to the platform. Step-by-step instructions can be found at https://www.ep.com/mfa/castingportal/
A dedicated support team is standing by to help you 24/7, should you need assistance. Hit the Contact Button, and then select "Crew, Talent and Background Support."
If easier, you can visit our website at www.4starcasting.com, then hit the "Log into the EP Casting Portal" tab. If you hover over the tab, there is a "MFA Instruction Page" to assist as well. Downloading the suggested APP PingID to your phone is the easiest method.
If interested and available, please send an email to: [email protected] with the following:
1) Subject Line: Chef Terry
2) In the submission email include name, age range, height, weight, phone, and email.
3) Attach a headshot and/or candid photo AND a full body in JPEG format. Make sure the photo is taken in decent lighting (no selfies), no sunglasses, no filters. Show us your style but make sure we can see your face!
4) Please confirm your mode of transportation, i.e. Uber, Bus, Own Vehicle, etc.
You must be registered with us at www.4starcasting.com to be considered.
#the bear#the bear tv#the bear hulu#the bear fx#the bear casting call#chicago casting call#4 star casting#the bear chef terry#the bear photo double
9 notes
·
View notes
Text

Post 1395
Colleagues described him as "stellar" and "straitlaced."
Doitchin Krasev aka Krastev, Federal inmate 13492-023, born 1978, incarceration intake May 2010 at age 32, discharged January 2012 and deported
False Passport Application, Identify Theft
Doitchin Krasev was a clean-cut kid from Eastern Europe who lived with a host family in the United States and went to a pricey private college in North Carolina.
Later, he worked at a pizzeria in Denver and then moved to Oregon, where he was a liquor control investigator. Colleagues described him as "stellar" and "straitlaced."
In a court proceeding in May 2010, details of Krasev's past emerged less than 24 hours after federal agents definitively identified him by showing his photo to acquaintances on the East Coast.
Investigators believe that Krasev has used three names since he was in college and that he worked in Oregon under the name of Jason Evers, a 3-year old Ohio toddler who had been kidnapped and murdered in 1982.
As a boy, he moved to the United States from Sofia, Bulgaria, to live with a host family in the Washington, D.C., area. His host father had been an attorney with the federal government at the Office of Management and Budget during the Reagan administration. His host mother was a physician.
HIs American host parents had befriended Krasev's parents, Dincho and Baychinskia Krastev, while he was visiting Russia and Eastern Europe and researching ways to help the scientific community recover after the collapse of the Soviet Union.
At the time, Dincho Krastev was a mathematician and director of the Central Library of the Bulgarian Academy of Sciences, while his wife is one of the leading Jungian scholars in Eastern Europe.
Krasev attended Davidson College outside Charlotte, N.C., in the '90s, but did not graduated from the school. He told his host family he'd dropped out of college. At that point, his host family said that they lost track of him after that.
In 1996 Krasev stole the identity of Jason Evers. He moved to Denver in the late '90s, and worked as a waiter or a bartender at a Pizzeria Uno restaurant where he was known as Daniel Kaiser.
He moved to Portland in 2002, wherein he got a job as an inspector for the Oregon Liquor Control Commission. In his application he told the agency that he'd previously worked as a private investigator in Colorado.
In his career he worked for the Bend Oregon office, and then went to the Nyssa Oregon office near the Idaho border. He later transferred back to Bend as the regional manager and returned to Nyssa in early 2010 as an investigator.
Krasev was taken into custody in April 2010 at his rental home in Caldwell Idaho. He has been charged with falsifying a passport application and identity theft. He was found out when processes were enhanced within the State Department, and the name of Jason Evers -- with an active passport -- was checked against databases of deceased Americans.
After his arrest, he refused to reveal his true identity, citing security concerns.
In the course of the investigation, officials got a tip from the Denver man who knew him as Daniel Kaiser. The tip led investigators to driver's licenses under that name in Colorado and North Carolina. From there, investigators tracked down Krasev's real name on the East Coast.
His birth certificate and Social Security number matched the death certificate for Jason Evers, killed in Cincinnati in 1982 during a botched kidnapping by a 17-year-old boy who wanted money for a new car.
Standing 5-foot-11, neatly barbered with blue eyes, Krasev was a perfect fit for an investigator's job with the Liquor Control Commission, said a local Sheriff's deputy, who said he met Krasev through his wife, who knew Krasev's girlfriend.
"He never set off any bells and whistles when you met him," the deputy said, describing Krasev as "straitlaced, clean-shaven, professional ... He kind of looks like Lance Armstrong."
Although Krasev rented a home in Caldwell, Idaho, he used to live in a house he owned in nearby Fruitland, Idaho -- both not far from Nyssa. A neighbor who lived beside Krasev in Fruitland's Applewood subdivision said he was a good neighbor. "The property looked much nicer when he was here -- he took good care of it," she said.
Krasev kept to himself, the neighbors said. But when he moved into the three-bedroom, 1,400-square-foot home beside theirs, they took him a loaf of homemade bread as a welcoming gift. A day or two later, he brought them homemade chocolate chip cookies.
The neighbor said they had a dog, Krasev drove a compact car and his girlfriend were "a cute couple" -- "They were very cordial. Just good neighbors."
His war-hero-grandfather and namesake fought the Nazis, his parents are respected scientific scholars in Bulgaria.
If Krastev had not applied for a passport, if the State Department had not begun running its own checks on death certificates, Krastev might still be Jason Robert Evers, living halfway around the world from his native Bulgaria.
Doitchin Krasev lived with his American host family from 1992 to 1994, graduated from the prestigious Georgetown Day high school and earned a scholarship to Davidson College in Charlotte, N.C.
However, as Krasev entered his second year at Davidson, his grades were poor, he seemed unhappy and ready to drop out according to American host family. He told his host family in a phone call that he was going to drop out of college, and they never heard from him again.
Chris Galvin, who had befriended Krasev in Denver in the late 1990s, said he was sure there was something painful in the past that Krastev was trying to avoid.
They played tennis, poker, pool and chess together, and Krastev would let slip clues to his past when they drank a little too much. Otherwise, Galvin said he was a good friend and one of the most intelligent people he has ever known.
"But I always felt like he was running when I knew him," Galvin said.
Galvin and a college friend, Gary Franks, once took a Colorado ski trip with Krasev, and Franks was having morning coffee this week when he recognized Krasev from photos on newspaper websites.
Franks called Galvin, leading to a crucial tip that helped federal investigators identify Krasev. The response from his friends and family has been overwhelming relief that Krasev has resurfaced, and that he was not hiding something sinister.
However, Galvin said he feels guilty about his contribution, wondering whether he betrayed the trust of a friend, and hopes Krastev does not have to pay too dear a price for his actions.
Krasev was released from federal prison in January 2012 and deported.
5m
7 notes
·
View notes
Text
Hope
~ Chapter 2 ~
Summary: Dean and Sam Winchester save a young woman —Natalie Johnson, from a coven of witches who are after her deceased grandmothers spell book. At first Dean doesn’t trust her, will he ever? Natalie is just simply a woman who gets roped up in the supernatural world from a mistake her grandmother made.
Paring: Dean x OC
Warning: Age gap, slow burn, smut (during later chapters), language, gore.
Word Count: 1,278
A/N: Hope you’re like the story! Happy reading! ♥️

Natalie had been restless in the bunker for over a week. At first, she was just trying to wrap her head around the world she had been thrown into—hunters, witches, spell books, and actual supernatural monsters—but eventually, she started getting bored. The Winchester brothers were always going off on hunts or researching the next big supernatural threat, and Natalie was just... there. She hated feeling useless.
So, one morning, after Sam returned from one of his endless trips to the bunker's archives, she made a decision.
"You know," Natalie began, leaning over the table in the war room where Sam had spread out a bunch of lore books, "I could help with this."
Dean, sitting nearby and cleaning one of his guns, snorted. "Help? How? Gonna knit us some monster repellent?"
Sam shot him a warning look, then turned back to Natalie, curious. "What do you mean? How can you help?"
Natalie took a breath, bracing herself for more of Dean's sarcasm. "Well, before I was kidnapped by a bunch of witches and thrown into the twilight zone, I was actually doing something pretty useful with my life. I work as a cybersecurity analyst. You know, hacking, tracking digital trails, all that stuff. I'm good at research, too."
Sam raised an eyebrow, intrigued. "Really?"
"Yeah," Natalie nodded. "I went to school for computer engineering, and now I help companies lock down their networks. Finding obscure information and hacking into databases is kind of my thing. I figured if you're dealing with monsters and lore all the time, maybe I can dig up stuff online, hack into things you can't."
Dean looked up from his gun, raising an eyebrow. "So, you're a geek."
Natalie's mouth twitched in annoyance. "You say that like it's a bad thing."
"It is when you're dealing with real-world stuff, like decapitating vampires and blowing up demons," Dean muttered, his voice gruff. "Not everything's about computers."
Sam gave him a sideways glance. "Dean. We're always doing research. You and I spend hours looking through archives and databases when we're not hunting. Hacking could be really useful, especially for tracking down things we can't normally get access to."
Dean grunted, clearly not thrilled with the idea of relying on Natalie for anything. "Fine. But don't expect me to hand over the keys to the Impala or anything."
Natalie rolled her eyes. "Don't worry, I wouldn't want to touch that fossil anyway."
Sam hid a smile, glancing back at his notes. "Okay, Natalie. Let's see what you've got."
It didn't take long for Natalie to prove she was more than capable. After that first offer to help, she dove headfirst into researching the latest case—a series of strange deaths involving men being burned alive in the middle of seemingly normal activities. The police reports were baffling, and there was no obvious supernatural connection at first glance.
Natalie hacked into local police databases, pulling up witness statements and security camera footage that wasn't available to the public. Within hours, she'd found patterns that had eluded both the police and the brothers.
"It's not spontaneous combustion," she said, leaning over her laptop, her fingers flying over the keys. "Each victim was seen just before their death with a strange symbol carved into their skin. I've enhanced the footage, and I'm pretty sure it's witchcraft."
Sam leaned in, impressed. "That's incredible work. How did you—?"
"IT degree, remember?" Natalie smirked. "I can analyze digital footage faster than you can look through your lore books."
Dean, who had been watching silently from across the room, crossed his arms. "Great. So now we know it's witches. That still doesn't mean we can stop them with a keyboard."
Natalie shot him a look. "No, but it helps knowing what we're up against, doesn't it?"
Dean opened his mouth to argue, but Sam cut in. "She's right, Dean. We needed this lead, and now we have it. Thanks, Natalie."
Natalie gave Sam a small, satisfied smile, ignoring the grumbling coming from Dean. "Happy to help."
Their latest hunt took them to a small town outside of Wichita. Dean, Sam, and now Natalie had tracked down the source of the deaths—a witch coven disguised as a small-town charity group. The witches were powerful, but they needed to carve the symbols into their victims to complete their rituals, which gave the trio a small window of opportunity.
Natalie stayed back in the bunker at Sam's request, continuing to monitor communications and hacking into the witches' emails and security feeds as they tried to locate the next potential victim.
While Sam and Dean were out chasing down leads, Natalie sent them real-time updates, directing them to potential sites where the witches were likely to strike next.
"This is insane," Natalie muttered to herself, eyes glued to her multiple screens. "I'm literally tracking witches in real time. How did my life turn into this?"
She sent a message to Sam's phone: Found something. They're targeting a city council member. Check the courthouse—they're holding a fundraiser tonight.
Dean's voice crackled through the walkie-talkie. "Courthouse? How the hell do you know that?"
"I hacked into their event calendar and cross-referenced with their emails," Natalie replied, her tone clipped. "One of the witches is scheduled to attend tonight. If I'm right, they'll strike during the event."
Dean didn't respond for a moment, but when he did, his tone was begrudging. "Fine. We're heading there now."
When they arrived at the courthouse, everything was just as Natalie predicted. The witches were already in place, their next victim unaware of the danger. Sam and Dean made quick work of two of the witches, and the third tried to flee. But Natalie, still monitoring from the bunker, was one step ahead. She hacked into the security system, locking all the exits remotely and trapping the witch inside the building.
The brothers cornered her, Dean delivering the final blow with a blade etched in runes designed to kill witches. The threat was over.
As they drove back to the bunker, Dean stared out the window, silent. Sam glanced over at him. "You know, Natalie was a big help tonight."
Dean grumbled under his breath. "Yeah, well, doesn't mean I have to like it."
"You don't like it because she's good at something you're not," Sam said with a smirk.
Dean shot him a glare. "I'm good at plenty of things. Like... I don't know, everything else that keeps us alive. But sure, let the geek take care of the computers."
When they returned to the bunker, Natalie was still sitting at her laptop, tapping away. When she heard the heavy footsteps, she looked up, her eyes meeting Dean's.
"So," she said, crossing her arms. "Did my geek skills help or not?"
Dean opened his mouth, ready to throw out another snarky retort, but the words stuck in his throat. He hated to admit it, but she had been useful. Hell, they wouldn't have cornered that last witch without her.
"Yeah," Dean said, finally grunting. "You helped."
Natalie raised an eyebrow, surprised by the acknowledgment. "That's the nicest thing you've said to me since I got here."
"Don't get used to it," Dean muttered, moving past her toward the kitchen. "I still don't trust you."
Natalie rolled her eyes, smiling as Sam gave her a thumbs-up from behind Dean's back.
Dean might never admit it, but Natalie was becoming more useful by the day. And while he wasn't ready to start handing out trust like candy, he couldn't deny she was starting to feel less like a liability—and more like part of the team.
#dean winchester#dean winchester fanfiction#dean winchester x ofc#dean winchester x reader#sam and dean#dean winchester drabble#dean winchester fic#dean winchester imagine#jensen ackles#spn#dean x you#dean x reader#spn drabble#dean x oc#dean x sam#dean x castiel#supernatural fandom#supernatural family#supernatural fic#supernatural fanfiction#spn fic#slow burn#supernatural#spn sam winchester#spnfandom#spn fanfic#supernatural fanfic series#spnfamily#sam winchester#castiel
12 notes
·
View notes
Text
Brazil's Social Security Institute to require biometric verification for new payroll loans
National Institute of Social Security already grappling with scandal over unauthorized union dues on benefits

Starting May 23, Brazil’s National Institute of Social Security (INSS) will mandate biometric authentication for all new payroll-deductible loans, including debt transfers between financial institutions. The measure, outlined in a directive issued by INSS President Gilberto Waller Júnior and published in the Federal Gazette, on May 8, aims to enhance security and compliance in loan processing.
According to the directive, the objective is to “map operational vulnerabilities and implement corrective measures and improvements, ensuring greater security and compliance in the processes involved.” Consequently, retirees and pensioners will have their loan margins accessible to financial institutions only after biometric authorization through the *Meu INSS platform, validated against federal government databases.
This initiative follows a prior decision on May 8, when Mr. Waller ordered the suspension of new payroll loans for retirees and pensioners, stipulating that transactions could proceed only if the beneficiary unlocked the service. The suspension was intended to facilitate the implementation of the biometric requirement, which will now take effect on May 23.
The new requirement is part of broader efforts by the INSS to prevent fraud, such as unauthorized deductions uncovered during the Federal Police’s Operation No Discount. Although payroll loans are not the focus of that investigation, reports of fraud in these transactions have persisted for years.
Continue reading.
#politics#brazil#brazilian politics#economy#national social security institute#image description in alt#mod nise da silveira
3 notes
·
View notes
Text
The US Patent and Trademark Office banned the use of generative artificial intelligence for any purpose last year, citing security concerns with the technology as well as the propensity of some tools to exhibit “bias, unpredictability, and malicious behavior,” according to an April 2023 internal guidance memo obtained by WIRED through a public records request. Jamie Holcombe, the chief information officer of the USPTO, wrote that the office is “committed to pursuing innovation within our agency” but are still “working to bring these capabilities to the office in a responsible way.”
Paul Fucito, press secretary for the USPTO, clarified to WIRED that employees can use “state-of-the-art generative AI models” at work—but only inside the agency’s internal testing environment. “Innovators from across the USPTO are now using the AI Lab to better understand generative AI's capabilities and limitations and to prototype AI-powered solutions to critical business needs,” Fucito wrote in an email.
Outside of the testing environment, USPTO staff are barred from relying on AI programs like OpenAI’s ChatGPT or Anthropic’s Claude for work tasks. The guidance memo from last year also prohibits the use of any outputs from the tools, including images and videos generated by AI. But Patent Office employees can use some approved AI programs, such as those within the agency’s own public database for looking up registered patents and patent applications. Earlier this year, the USPTO approved a $75 million contract with Accenture Federal Services to update its patent database with enhanced AI-powered search features.
The US Patent and Trademark Office, an agency within the Department of Commerce, is in charge of protecting inventors, awarding patents, and registering trademarks. It also “advises the president of the United States, the secretary of commerce, and US government agencies on intellectual property (IP) policy, protection, and enforcement,” according to the USPTO’s website.
At a Google-sponsored event in 2023, Holcombe, the author of the guidance memo, said government bureaucracy makes it difficult for the public sector to use new technologies. “Everything we do in the government is pretty stupid, when you compare it to the commercial world, right?” he said. Holcombe specifically cited cumbersome budgeting, procurement, and compliance processes, arguing that they hamper the government's ability to rapidly adopt innovations like artificial intelligence.
The USPTO is not the only government agency to ban staff from using generative AI, at least for some purposes. Earlier this year, the National Archives and Records Administration prohibited the use of ChatGPT on government-issued laptops, according to 404 Media. But soon afterward, the National Archives hosted an internal presentation that encouraged employees to “think of [Google’s] Gemini as a co-worker.” During the meeting, some archivists reportedly expressed concerns about the accuracy of generative AI. Next month, the National Archives is planning to release a new public chatbot for accessing archival records developed with technology from Google.
Other US government agencies are using—or avoiding—generative AI in different ways. The National Aeronautics and Space Administration, for example, specifically banned the use of AI chatbots for sensitive data. NASA did decide, however, to experiment with the technology for writing code and summarizing research. The agency also announced last week that it’s working with Microsoft on an AI chatbot that can aggregate satellite data to make it easily searchable. That tool is available only to NASA scientists and researchers, but the goal is to “democratize access to spaceborne data.”
9 notes
·
View notes
Text
Thailand Visa Exemptions
1. Legislative Framework and Policy Evolution
1.1 Statutory Basis
Governed by Sections 12 and 35 of the Immigration Act B.E. 2522 (1979)
Implemented through Ministerial Regulation No. 28 (B.E. 2544)
Modified by Cabinet Resolution (November 2022) extending 45-day stays until November 2025
1.2 Bilateral vs. Unilateral Agreements
Reciprocal Exemptions (12 countries including Brazil, South Korea, Peru)
90-day stays
Multiple-entry privileges
Unilateral Exemptions (56 countries)
Standard 30-day stays
45-day temporary extension for air arrivals
1.3 Historical Policy Shifts
2008: Introduction of 15-day land border restrictions
2016: Implementation of biometric tracking
2022: Temporary 45-day extension to boost tourism
2. Eligibility and Entry Protocols
2.1 Nationality-Based Classification
Passport TypeDurationEntry MethodExtension EligibilityG7 Nations45 days*Air onlyYes (30 days)ASEAN Members30 daysAir/LandNoDeveloping Economies15-30 daysConditionalVaries
*Until November 2025 per Cabinet Resolution
2.2 Document Verification Matrix
Mandatory Documents:
Passport (6+ months validity)
Onward ticket (confirmed within exemption period)
Proof of funds (THB 20,000/person)
Secondary Checks:
Previous Thai visa history (12-month lookback)
Accommodation verification
3. Immigration Assessment Algorithms
3.1 Risk-Based Screening System
Primary Inspection:
Machine-readable zone scan
Interpol database check
Facial recognition matching
Secondary Screening Triggers:
4+ visa exemptions in 12 months
Suspicious travel patterns
Incomplete documentation
3.2 Discretionary Denial Factors
Red Flags:
Previous overstays (even if paid)
Employment-seeking behavior
Frequent border runs
4. Border-Specific Implementation
4.1 Airport Processing
Dedicated Visa-Exempt Lanes at 6 international airports
Automated Immigration Gates (e-Gates) for eligible nationalities
Transit Without Visa (TWOV):
72-hour limit
Confirmed onward ticket required
4.2 Land Border Restrictions
15-Day Maximum Stay at 52 designated checkpoints
Entry Quotas:
2 land crossings per calendar year (2024 policy)
Exceptions for border pass holders
5. Extension and Conversion Mechanics
5.1 Extension of Stay
Single 30-Day Extension:
THB 1,900 fee
TM.7 form submission
Proof of address required
Exceptional Cases:
Medical treatment
Force majeure events
5.2 Visa Conversion Options
Non-Immigrant Pathways:
Business (B): Requires THB 25,000 application fee
Retirement (O): Age 50+ with financial proof
Education (ED): Enrollment in accredited institution
6. Compliance and Enforcement
6.1 Overstay Penalties
Fine Structure:
THB 500/day (maximum THB 20,000)
Automatic blacklisting after 90+ days
Voluntary Departure Program:
7-day grace period at airports
6.2 Visa-Run Monitoring
Automated Tracking System:
Flags frequent exempt entries
Calculates denial probability score
7. Special Case Analyses
7.1 Diplomatic/Official Passports
90-Day Exemption regardless of nationality
Exempt from:
Financial proof requirements
Onward ticket verification
7.2 Crew Member Privileges
72-Hour Shore Leave:
Valid with approved crew documentation
Separate from passenger exemptions
8. Emerging Policy Developments
9.1 Digital Integration
E-Arrival Card System (2024 rollout)
Blockchain Travel History (Phase 1 testing)
9.2 Security Enhancements
Biometric Exit System (Full implementation 2025)
API Integration with INTERPOL databases
9. Strategic Entry Planning
10.1 For Frequent Travelers
Alternative Solutions:
METV (6-month multiple entry)
Elite Visa (5-20 year options)
Entry Pattern Management:
Minimum 21-day intervals between exempt entries
Rotate entry points (BKK/DMK/HKT)
10.2 For Long-Term Stays
Conversion Timing:
Optimal window: Days 1-15 of entry
Avoid holiday periods
Document Preparation:
Pre-legalized paperwork
Financial trail establishment
#thailand#immigration#thai#thailandvisa#thaivisa#visa#immigrationinthailand#thaivisaexemptions#thailandvisaexemptions#visaexemptions
3 notes
·
View notes
Text
Motoko Kusanagi: A Cybernetic Force to Be Reckoned With

Let’s take a dive into the fascinating world of Motoko Kusanagi, the central character in the iconic anime and manga series, Ghost in the Shell. 🤖🔍
Background
Ghost in the Shell is a futuristic cyberpunk universe set in the mid-21st century (around 2030 AD).
The story revolves around Public Security Section 9, an anti-crime/counter-terrorist unit specializing in cyber-crimes.
Motoko Kusanagi, often referred to as “Major,” is the second-in-command of Section 91.
Abilities and Skills
Superhuman Physical Characteristics:
Major’s cybernetic body grants her enhanced strength, agility, and endurance.
She can perform feats that surpass human limits, making her a formidable combatant.
Thermo-Optical Camouflage:
Major can become invisible using therm-optic camouflage technology.
This ability allows her to blend seamlessly into her surroundings or surprise enemies.
Cyber Mind and Expert Hacker:
Her cyberbrain enables her to interface with networks and mimic various powers:
Telepathy: Communicate mentally with others.
Possession: Control other cybernetic bodies.
Illusion Creation: Manipulate perceptions.
Memory Access: Retrieve information from databases.
Offensive Mind Control: Influence others’ thoughts.
Leadership and Tactical Intelligence:
Major’s experience and strategic acumen make her an effective leader.
She excels at analyzing complex situations and devising optimal solutions.
Strengths
Combat Prowess: Major’s martial arts skills and combat experience make her a force to be feared.
Invisibility: Her therm-optic camouflage provides a tactical advantage.
Cybernetic Adaptability: She can use other bodies or objects as duplicates.
Weaknesses
Humanity vs. Cyberization: Major grapples with her identity as a cyborg—balancing her human consciousness with her cybernetic enhancements.
Vulnerability to Hacking: Despite her hacking abilities, she’s susceptible to skilled hackers.
Existential Questions: Her search for purpose and self-awareness adds depth to her character.
In summary, Motoko Kusanagi embodies the fusion of human and machine, navigating a complex world where technology blurs the lines of identity and power. Whether she’s infiltrating enemy lines or questioning her own existence, Major remains an enduring symbol of cyberpunk resilience. 🌟🤖
#Motoko Kusanagi: A Cybernetic Force in Ghost in the shell#ghost in the shell#motoko kusanagi#major motoko kusanagi#cyberpunk#transhumanism#cybernetic#90s anime#cyberpunk anime#hackers#anime hackers#cyberpunk police#cybernetic prowess
15 notes
·
View notes
Text
1. Structural Framework of the Privilege Visa System
1.1 Legislative Foundations
Established under Royal Thai Police Order No. 327/2557 (2014)
Administered by Thailand Privilege Card Company Limited (TPC), a subsidiary of the Tourism Authority of Thailand
Operates parallel to but distinct from the Elite Visa program
1.2 Program Evolution
2014 Launch: Initial 5-year membership structure
2019 Restructuring: Introduction of tiered benefits system
2023 Enhancements: Digital integration and expanded concierge services
2. Comprehensive Benefit Structure
2.1 Immigration Advantages
Dedicated Immigration Channel: 24/7 access at 8 international airports
Multiple Re-entry Permit: Embedded in visa validity
90-Day Reporting: Optional (can be handled by TPC staff)
2.2 Lifestyle Concierge Services
Real Estate Acquisition Support: Curated property portfolio access
Education Placement: Partnership with 17 international schools
Medical Coordination: Priority at 38 partner hospitals
2.3 Financial Infrastructure
Thai Bank Account: Expedited opening with minimum deposit waiver
Tax Advisory: Complimentary 10-hour annual consultation
Currency Exchange: Preferred rates at Siam Commercial Bank
3. Eligibility & Application Scrutiny
3.1 Vetting Criteria
Financial Health Check:
Liquid assets verification (minimum THB 3M equivalent)
Source of funds audit
Background Clearance:
Interpol database cross-check
Thai security agency review
3.2 Document Requirements
Primary Applicant:
10-year passport history
Certified financial statements
Health insurance (USD 100,000 coverage)
Dependents:
Legalized marriage/birth certificates
Academic records (for student dependents)
3.3 Approval Timeline
StageDurationKey ConsiderationsPreliminary Screening7-10 daysDocument completeness checkFinancial Verification15-20 daysBank confirmation processSecurity Clearance30-45 daysEnhanced for certain nationalitiesFinal Issuance5 daysCard production and delivery
4. Tax & Legal Implications
5.1 Residency Status
Non-Tax Resident: For members spending <180 days/year
Tax Resident: Automatic after 183 days with additional reporting
4.2 Asset Management
Property Ownership: Condo purchases permitted under foreign quota
Investment Vehicles: Access to SET through special foreign investor accounts
4.3 Inheritance Planning
Will Registration: Mandatory for property holdings
Succession Tax: 10% on Thai-situs assets exceeding THB 100M
5. Operational Realities & Limitations
5.1 Practical Constraints
Work Prohibition: No employment rights without separate work permit
Business Activities: Passive investment only
Political Activities: Complete restriction
5.2 Service Level Agreements
Response Times:
Emergency: 30 minutes
Standard: 4 business hours
Guarantees:
Airport processing within 15 minutes
Medical appointment scheduling within 24 hours
6. Comparative Analysis with Competing Programs
ParameterThailand GOLDMalaysia MM2HUAE Golden VisaMinimum StayNone90 days/year1 day every 6 monthsHealthcareTHB 500K annual creditMandatory insurancePremium coverageEducation15% tuition discountLocal school accessInternational optionsPath to PRNoAfter 10 yearsAfter 5 years
7. Strategic Utilization Framework
7.1 Optimal User Profiles
High-Net-Worth Retirees: Age 50+ with global income streams
Global Nomads: Location-independent entrepreneurs
Family Offices: Multi-generational wealth management
7.2 Financial Optimization
Currency Hedging: THB-denominated asset allocation
Tax Year Planning: Residency day counting system
Insurance Structuring: International policy portability
8. Emerging Program Developments
8.1 2024 Enhancements
Digital Nomad Add-on: Remote work endorsement (Q3 rollout)
Crypto Wealth Verification: BTC/ETH acceptance for qualification
Regional Hub Access: Expanded services in Chiang Mai and Phuket
8.2 Pending Regulatory Changes
Family Office Recognition: Special provisions under discussion
Art Import Privileges: Proposed duty-free allowances
Yacht Registration: Streamlined process for members
9. Critical Evaluation & Recommendations
9.1 Value Proposition Assessment
Strengths:
Unmatched concierge infrastructure
Banking and financial access
Healthcare coordination
Weaknesses:
No path to permanent residency
Rigid membership tiers
Limited business activity
9.2 Implementation Checklist
Pre-Application:
6-month financial trail preparation
Dependent document legalization
Active Membership:
Annual benefit utilization audit
Tax residency monitoring
Renewal Planning:
180-day advance evaluation
Tier upgrade analysis
Final Verdict:
The GOLD membership represents Thailand's most sophisticated non-immigrant residency solution for affluent individuals prioritizing lifestyle quality over economic activity rights. While not a pathway to citizenship, its operational advantages and service infrastructure remain unparalleled in Southeast Asia for those meeting the financial thresholds.
#thailand#immigration#thai#visa#visainthailand#thaivisa#thailandvisa#thailandprivilegevisa#privilegevisainthailand#thailandprivilegevisagoldmembership#thaipr#immigrationinthailand#thaiimmigration
4 notes
·
View notes
Text
Probably nothing, but maybe not.
The Wayback Machine enables the recovery of internet records. It was allegedly subject to a cyber-attack last month, which resulted in a suspension and subsequent limitation of its facilities.
A month before the elections! “Sensitive records”???
From Brave AI:
“The Internet Archive’s Wayback Machine, a popular digital archive tool, was temporarily taken offline in October 2024 due to a cyberattack. The attack, which compromised sensitive user records, prompted the organization to take down its website and services to improve security. The Wayback Machine, which stores archived versions of websites, was eventually restored, with some limitations, by October 15, 2024.”
New, was it a cyber attack or was it an intentional limitation of records prejudicial to the “blob”, the “swamp” and the Democratic Party?
“After the October 2024 security breach, the Internet Archive took immediate action to contain the incident:
· Disabled the JavaScript (JS) library to prevent further unauthorized access
· Activated scrubbing systems to remove sensitive data from publicly accessible areas
· Upgraded security measures to prevent similar breaches in the future
“… the following limitations are in place on the Wayback Machine:
· Access restrictions: The Internet Archive has restricted access to certain areas of the Wayback Machine to prevent further unauthorized access and minimize the impact of the breach.
· Data scrubbing: The scrubbing systems are actively removing sensitive data from publicly accessible areas, including user authentication databases, to prevent exposure of compromised information.
· Temporary downtime: The Wayback Machine may experience temporary downtime or reduced functionality as the Internet Archive works to fully remediate the breach and restore services.
· Enhanced monitoring: The Internet Archive has increased monitoring and logging to detect and respond to any further suspicious activity.
“As the Internet Archive completes its investigation and remediation efforts, it is likely that additional limitations or restrictions will be lifted, and the Wayback Machine will return to its normal functioning state. However, the exact timeline for these developments is unclear and will depend on the progress of the investigation and remediation efforts.”
6 notes
·
View notes
Text


I'm like +5 years late to the Fallout TTRPG scene [and modding for that matter] that now I got some cute customization, means I gotta make new Fallout OCs.
More info on them below!!
So these two are from Vault 40! Over 200 years ago, somebody at Vault-Tec (or one of the shareholders partnering with General Atomics) had the """great""" idea of seeing how children would fare when raised by robots rather than their fellow human vault dwellers.
Not too profound a sci-fi concept, and it's been done plenty of times, of course, but whoever came up with the idea took it a step further and implemented the Overseer's programming (an AI know to the vault's dwellers as "M.O.M." [Maternal Observational Matrix]) to assign each newborn dweller (known as "Charges" instead of children) with their own predetermined occupation based on Handler.
Miss Nanny: Charges raised by Miss Nanny units are brought up with the expectations of being patient, kind and tolerant individuals to even the most rambunctious of youths and precarious of guests. Surprisingly (or not tbh), the charges of these Miss Nanny units often mimic french phrases ("c'est la vie", "que sera sera", etc) and euphemisms heard in passing by their handlers.
These charges often end up aiding in early child development in the vault's nursery, or teaching the newest generation Vault 40's heavily varied (Vault-Tec™ approved and censored) curriculum. In some rare cases however, this can include entertainment.
Examples include, but are not limited to: Vault Chaplain, Pedicurist, Marriage Counselor, and Teacher*, Laundry Cannon Operator, Simon Says Operator, Vault Literature Narrator, etc.
*Assistant, the General Atomics Miss Nanny Teacher Variant does most of the teaching!
Mister Farmhand: Rustic and robust (most times, but not always ofc!), charges child-reared by these robots are instilled at a young age the importance of a hard day's work. Taught how to spot ripe fruit and quickly take care of invading varmints, these charges grow to be no-nonsense, honest and self-sufficient. Nevermind the charming southern drawl and charm they inherit from their handlers.
These charges learn and aid either in proper crop cultivation, rodent and insect extermination, or the study of further enhancing the vault's food source through proper hybridization. (with heavy supervision and previously provided authorization)
Examples include, but are not limited to: Vault Farmer, Hydroponics Specialist, Vault Botanist, Veterinarian (in the RARE cases of anything besides a pet rock), Vault Exterminator, Garbage Burner, etc.
Mister Gutsy: Loyal (nearly to a fault) to their country, vault and siblings, and stubbornly determined, charges raised by Mr Gutsy's are structured and disciplined, if a little rowdy when at ease, but not for long. Similarly no-nonsense like their farmhand cousins, these charges are staunchly patriotic and determined to lay down their lives if it means keeping their vault and its denizens safe.
These charges inherit occupations of vault security, tutelage of CQC and general sports, and in very rare (read: RARE) cases, exploration of the surface outside the vault*.
*This occupation has long since gone out of season as a result of [REDACTED], please reference database section 2.4.113 for further details.
Examples include, but are not limited to: Gatekeeper, Vault Security, Vault Loyalty Inspector, Assistant Shift Supervisor, Little League Coach, Vault Little League Umpire, Vault Pioneer, etc.
Mr Handy: Charges raised by Mr Handy units art taught first and foremost proper manners, social etiquette, maintaining ones' environs in a clean and proper manner and the means of navigating social situations with utmost grace and ease. Strangely enough, most charges under these brand of General Atomics handy units often pick up the speaking mannerisms and personality subroutines of their handlers.
These charges are fostered into roles of catering, hospitality, and in some cases, just plain fixing things. (Again, with HEAVY supervision)
Examples include, but are not limited to: Fry Cook, Line Cook, Busboy/girl, Delivery Boy/Girl, Vault Barber, Pip-Boy Programmer, Juke Box Technician, Vault Engineer, Hairdresser, etc.
Nurse Handy: No strangers to gore and all things bloody, those charges brought up by these medical machines are ingrained mentally with the importance and significance of life and death. Honest (almost bluntly), deeply analytical with no shortage of bedside manners, these charges call it as it is. Nevertheless, they retain some compassion, if not, a pragmatic sense of one. Like their Mr Handy cousins, they inherit their handler's british accent, albeit a little more pragmatic and near cynical in passing.
These charges grow into jobs of clinical aid assists, cosmetic surgery, general pediatrics, nursing, and in some cases, test subjects for new and innovative vaccines, treatments, etc
Examples include, but are not limited to: Vault Nurse, Clinical Test Subject, Plastic Surgeon, Tattoo Artist, Vault Mortician, Vault Crematory Operator, etc.
Some details regarding Bea and her Handler, Ferdinand!
Beatrice:
Bea is...cautious, safe to say. Born relatively premature and with a handful of ailments (on top of her already aggressive allergies), Bea's always had a struggle when it came to daily life and her job as Vault Botanist. Nevertheless, she really tries to put in the effort and carry her weight as best as she can. Much to her detriment. Raised with the constant motif of "do it scared" Bea isn't one to charge head in, but power through if absolutely necessary.
S: 4
P: 4
E: 5
C: 7
I: 7
A: 4
L: 9
Ferdinand:
Imagine if you took a charismatic old farmer with a stoic but gentle demeanor and stuffed him into a robot- that's Ferd. Gently spoken and ever patient (except for vermin), Ferdinand is your stereotypical Mr Farmhand unit. Having lost a charge before Bea, Ferdinand was hesitant on taking on another one, that is until he was handed a small blue bundle, swaddling something that looked more like a baby tato than a baby girl. For years since he's acted as her guide and mentor in a wildly changing yet stationary world.
S: 4
P: 8
E: 6
C: 5
I: 7
A: 4
L: 6
6 notes
·
View notes