#Automated Password Management
Explore tagged Tumblr posts
Text
Leveraging gMSA for Enhanced Security in SQL Server
In today’s rapidly evolving cybersecurity landscape, securing database environments has become paramount for organizations worldwide. Among various strategies, integrating Group Managed Service Accounts (gMSAs) into SQL Server environments stands out as a robust method to bolster security. This article delves into practical T-SQL code examples and applications of gMSAs, offering insights into how…
View On WordPress
#Automated Password Management#Enhanced Database Security#gMSA Integration#SQL Server security#T-SQL examples
0 notes
Text
Hey do you use a password manager? (you should; bitwarden is my preferred choice because it's open source and also good)
Do you use your password manager to store information about your bank cards?
Do you have any recurring monthly/annual/whatever payments that happen on those bank cards?
Please do future you a favor and any time you use a particular card on a particular website or to set up a subscription go into your password manager and add that website in the notes for the card.
Because my card is expiring and I'm now having to log into a bunch of shit that is totally automated that I never see and figure out if it's on this card and it is, lemme tell you, not great.
1K notes
·
View notes
Text
Santae banned me without telling me why and won't unban me unless I send them my photo ID
Hey guys sorry for not posting in… forever? I just suck at social media lol. But you may have seen that I've reblogged some posts that advertise Santae in the past, but please disregard all that. I've since deleted those posts after learning how the site is managed and, after what happened to me a few days ago, I feel as though I should go public about this. Because boy did I just get fucked over.
Anyway, yeah, what it says in the title. On October 24th, around 10am EST, I was restocking my user shop when the entire webpage went white. I couldn't access the site at all and, when I tried to look for the Discord on my server list, it wasn't there. I knew what this had meant. I got banned from both the game, and the Discord - this is important to keep in mind for later.
I didn't receive any Discord DM or email notification about my ban, so after asking a mod what their support email was (and yes, I later verified that this is indeed their legitimate support email), I sent them this:
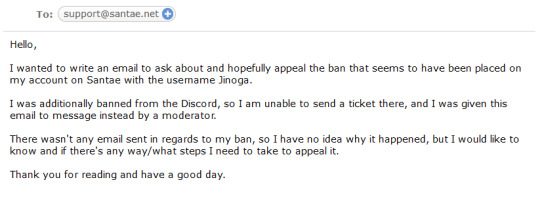
After a few hours, I get this back in response:
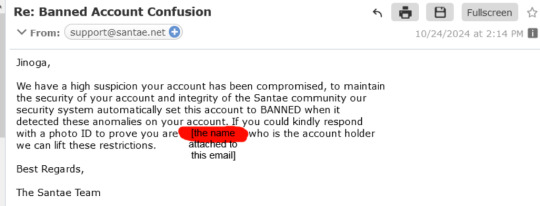
There's so much I'm confused about here. I think the one that screams out the most is that they're asking me to show them my photo ID so I can get unbanned. Absolutely not. I refuse to do this. This poses a massive security and privacy risk. They straight up banned my account, gave this half-baked explanation, and told me I need to send my personal information or... I stay banned?
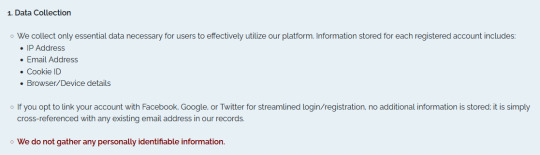
Let me make something clear: The only personal thing they have on file about this account is the email address that I created my account with, which I've also used to contact them. My real name, date of birth, anything of that nature would not be connected because this was not asked for during account creation, therefore this wouldn't actually prove I'm the account holder. Theoretically speaking, I could show them any ID in the world and for all they know, that's my real information, because they have nothing else to go off of. They even say as much in their privacy page.
Secondly, "account has been compromised"? What does that mean? I think anyone's interpretation of this would be that my account got hacked. But if my account got hacked, why wasn't I informed of this? I had to reach out to support, they did not reach out to me first. That means my password, which I may share across other sites, would have been known to someone else and thus I should've been warned of this immediately, not roughly 5 hours after the fact.
Thirdly, what, was my Discord "compromised" too? If an automated system had flagged my account, does that system somehow interact with a Discord bot so they ban a user on both at the same time? How does that work? That makes no sense as to why they'd ban me on both the game and the Discord for something like this, which is why I'm calling bullshit.
Let me tell you what I think happened.
Recently, Santae has been in some really hot water with connections revealing their relation to an older petsite, Lurapets, which has a history of scamming and artist mistreatment, as well as proof coming out of them using AI art for their NPC art. You can find these posts on the @santae-salt blog if you want to see for yourself, but I'm also linking them throughout this post.
Once the post about them being directly related to Lurapets was released, several users that the Santae staff thought might be involved in the creation of the post got banned. As it turns out, I was banned at the same time as these users.
After speaking with the @santae-salt admin, we are both of the belief that I, a regular user, got caught up in this mess because they're assuming I'm an alt account of someone else and staff demanded to see my ID because they didn't think I was a different person. It may turn out to be wrong, and yeah that sounds a bit far-fetched, sure, but really, what else can I go off of here?? Santae staff has given me a very questionable and refutable explanation as to why I've been banned, and their radio silence after I refused to send them my ID is just making me believe they don't think I'm real. They don't want my photo ID to verify I'm the account holder, they want my photo ID to verify I'm not someone else.
This is unprecedented. I've never seen any petsite ask for a photo ID in any situation, and after asking around, not even those banned from Santae were asked for this. It's just me! This is an incredible attempted breach of privacy, and, with Santae now under doxxing allegations, I really don't feel confident they'd keep my personal information… well, personal.
I messaged back almost immediately after they responded to me where I told them I would not send my ID and I had asked if there were any other way I could verify myself to get my account unbanned. I've received no response so far, and after what I've learned, I feel like I'm not going to get one at all.
So, let this be a lesson to you: don't waste your time on Santae. You can be the most obedient player out there. You can abide by all their rules, be a nice and generous player, or just be minding your own business, but if they so much as think you're associated with someone who they think has wronged them, you'll be banned.
And they can't even be bothered to properly tell you why.
281 notes
·
View notes
Text
definitely one of the most difficult moments of my professional career was when i was doing tech support for [REDACTED]'s automated biomed research lab and like. hang on lemme greentext this
>tell them i can fix this issue in half an hour with a remote support session (aka Teamviewer)
>"you want to... control our computers???? over the internet????? like some kind of HACKER???????"
>their IT submits my request to upper management and after two weeks they reluctantly allow me to get remote access to their systems
>by logging into a virtual machine using a 20-digit password and then using a specific program inside of that virtual machine
>while sharing my screen with someone from their IT team the entire time
>finally get remote access to the PC with the issue
>go to open log files to start troubleshooting
>ERROR: User does not have read permissions.
>what the fuck
>ask their IT guy why it's saying that
>"...because we don't want you looking at our stuff, duh?"
>take deep breath before calmly explaining that i need to open files in order to fix their problem
>IT guy submits my request to upper management
>after another week i go through the whole process again but can actually open the log file this time
>cool, it's exactly the issue i thought it was and i know exactly how to solve it
>open the relevant settings file, change a single number, hit Save
>ERROR: User does not have write permissions.
>what the FUCK
>ask IT guy how i'm supposed to fix their system if i can't change literally anything on it
>takes 20 minutes of arguing to get him to admit that maybe i need write access
>he submits the request to upper management
>a week goes by
>upper management denies it
>says i can just verbally tell the IT guy on the call what to type and he'll do it for me
>deep breaths. deep breaths.
>start third remote session
>go to open the relevant .log file in notepad, which isn't the default program it opens with for some reason
>they fucking disabled right clicking
>[REDACTED] has a $118 billion market cap btw
>manage to walk the IT guy through using the command line (which he had never seen before and was scared of) to edit the relevant file
>three weeks go by
>new support ticket in my inbox
>"why didn't your fix fix this completely unrelated issue?"
>they still won't give me write access
>VP of [REDACTED] yells at me in our weekly meeting for taking so long to fix a third unrelated issue they never submitted a ticket for and is also not actually an "issue" but an intended feature of our software that they don't like
>i went to college for this
#second worst part of that job was getting emails from a customer like#“hey can you bump our ticket to the top of the queue? it's really impacting our ability to do research. no pressure though! :)”#and then i'd check who it's from and it's fucking St. Jude's Children's Hospital#“no pressure but you are directly killing kids with cancer”
251 notes
·
View notes
Text
Android (Leona) AU - Commission Piece
Thank you so much @nemisisnemi for the commission!!! (And for also being patient with me LMAO) So, general worldbuilding first, the basic headcanons for every character, Leona-specific building and a Nemi x Leona drabble to finish it off.
If you enjoy my writing and would like to support me, here's my (slightly out of date) comms info. Otherwise, just like/reblog/comment. It means a lot!!
----------------- General Worldbuilding
NRC - Night Raven Conglomerate
Night Raven Conglomerate is known globally for many of their businesses, however their most notable and profitable model comes from Yokai Tech Industries. YTI is responsible for the development of state of the art androids, available for public use. While widely referred to as 'andy's' or 'mechs', YTI has a model for all your personal and business needs, for any budget. (Any budget being from rich, to filthy rich) Each droid model name is indicative of it's role and what it's been programmed to do. Regardless of model, be aware that your bot will have:
Safe search on
A personality chip *please note it will take some time for your bot to develop its personality. It must cater itself to you as an owner and have time to research and develop a personality from external sources. This may mean your bot chooses a name for itself besides its serial number if you do not choose to disable this function
A direct connection to our troubleshooting department
Recording on **all bots 'eyes' or optics are set to record the world around them in order to create a database for themselves and be able to recall old files in order to learn
A user guide and personal password/key in order to access settings in back panel (including most items above)
A recharge station
The Models M.E.C.H- (Managing Everyday Chores and Homemaking) The most common bots on the market, and also, the cheapest! These bots are perfect for individuals and families, taking care of everything from meal planning and budgeting to getting kids ready for school and cleaning! They'll manage household finances and run your errands for you.
M.E.C.H's have a humanoid design, but are manufactured in a white-coloured metal alloy. Most have a feminine appearance, but by request/with permission from their owners they may alter their appearance. Clothing is simulated by internet research and metallic projections that allow them to emulate cloth. (M.E.C.Hs from the factory are often dressed in a maid-like outfit or in a pant suit.) M.E.C.H's are able to alter their "hair" style and colour, so long as it is considered appropriate by their owners. They are also able to shift their height slightly. (this design is somewhat inspired by Dominic Cellini on twt/insta)
M.E.C.H's are very durable and also easy to fix. They are capable of repairing themselves from damage after watching a mechanic fix the specific issue once, or contacting our troubleshooting team. M.E.C.H's are waterproof on their hands, and water resistant overall. They are fire resistant, and are equipped with safety measures in case of an emergency. They also have a direct line with 911. **A business model of M.E.C.H is also available for minimum wage jobs, usually those requiring hospitality skills. They are more susceptible to the emulation of emotion however, than the O.T.T.O model, and may shut down when dealing with a customer. This can usually be avoided by turning off the personality chip temporarily.
---------
O.T.T.O - Occupational Transport and Telecommunications Organizers (O.T.T.O) is a great model to consider for the workplace.
O.T.T.O bots are programmed to help increase efficiency and intrapersonal bonds in the workplace, comparable to an automated secretary. O.T.T.O bots do the following up, so you don't have to. Progress reports and statistics are created and analyzed in record time. They are also trained to deal with H.R conflicts in a calculated and unbiased manner. However, O.T.T.O bots have also recently been taking their place behind the wheel for public transportation, currently the only model approved to drive. So long as they are given ample time to either charge OR refuel, (like a car), they are a much safer option on the roads than humans are. They are a great choice as a chauffeur,( and YTI has proved as such by starting a cab company under a different name/brand.)
On public transit, their appearance is much more industrial than their office-working models. Most O.T.T.O bots tend to remain in their factory settings, remaining completely chrome in colour. They often maintain a bulkier looking chest and shoulder area for the sake of keeping potentially unruly costumers in check, though their arms and legs are capable of stretching and appear similar to bendy straws.
While these bots are reliable, they also seem susceptible to wear and tear. It's often cheaper to replace a bot when it no longer serves it's function properly. (cough cough planned obsolescence cough)
It is not recommended that these bots work in hospitality. YTI is currently working on O.T.T.O bots that may be considered for work in trades, though this has mixed reviews from the public as of right now, over concerns of the bots taking over jobs that require more certification than simple safety and a driver's license.
--------
EM-RR - Emergency Response Robot (often referred to as an "Emery")
This bot is built specifically with human safety in mind. It's only objective is to rescue human lives. These bots are manufactured to look like humans for the most part, as studies have shown receptiveness to being rescued was improved the more humanoid they appeared. These bots are equipped with basic paramedic training, fire fighting, extensive knowledge of the law and how it applies, medical equipment like that found on an ambulance, and search and rescue supplies, including a detachable drone that is a part of them. EM-RR's are also equipped with extra rations of food, water, blankets, toys, and radios. Besides M.E.C.H's, EM-RR's are the best bot to have around kids as they are often able to handle the responsibility, breakdowns and tantrums easily. These bots are also built to withstand extreme temperatures, pressures, and fluids.
They are not yet approved to operate in a rescue mission without a supervisor as many are still learning what does and does not harm a human in terms of handling them.
-------
E.L.U - Entertainment and Leisure Unit
These bots are made for the big screen, often boasting the newest and best technology YTI has to offer. Their appearances are highly dynamic and can switch on a dime according to their whims.
E.L.U's can only be afforded by the highest bidders, and only 1200 models have been made worldwide for the public to buy. (About 35 models are used for YTI's ad campaigns and as actors in movies, and of those models, only 1 is used as a social media 'influencer'.).
E.L.U's are equipped with exceptional emotion-imitating technology. They are able to replicate voices without issue, learn choreography immediately, possess perfect pitch, and are capable of playing any percussion or string instrument.
E.L.U's have been through the most rigorous testing and development. While being able to sustain damage fairly easily, nanotech allows for superficial markings and damages to repair itself. Any damage that occurs on a software level is unheard of, but would be covered by insurance. At least, unheard of to the public
----- Custom Bots (The YTI is currently working to develop a 'build your own bot' program for young aspiring engineers. The program will allow promising individuals to create a new android using the technology available to them in the facility, and also lead to streamlining the process by which someone could order a custom bot. Prototypes have been promising.)
-----
Rapid Fire World Building
Riddle - human toddler Trey - EM-RR - Firefighting specialty Cater - lives at home (mansion) with his dad, who is a banker and investor of Y.T.I Deuce - Mechanic Ace - Was the Roseheart's M.E.C.H, took care of Riddle, began to disobey orders from Dr. Rosehearts, was slightly dismantled and discarded of Leona - Explained Below (E.L.U) Ruggie - O.T.T.O bot, mainly working in taxis. Very friendly, has to do constant maintenance on himself so they don't take him out of service Jack - Mechanics assistant, M.E.C.H Azul - inherited his grandma's restaurant, investor of Y.T.I, has several M.E.C.H's at his disposal Jade - is set to take over his mother's jewelry business Floyd - no formal training as a mechanic, does the upkeep for the Ashengrotto restaurant. Has mixed feelings about the M.E.C.H's, sometimes breaks them just to put them back together Jamil - a hybrid of all three bots, meant to attend to Kalim. Has additional security measures built in place to act as a guard. Kalim - human, investor and advocate for android rights, as he believes they exist beyond just their programming and should be treated equally Vil - E.L.U owned by Eric Venue. Hates it. Rook - EM-RR - search and rescue specialty Epel - Mechanic. Doesn't really like Y.T.I's inventions. Too close to humans Idia - head engineer of Y.T.I. Can you guess why :) Ortho - DECEASED E.L.U model Malleus - a discarded prototype of the E.L.U model. The workers at Y.T.I believe it's battery is dead, but it has been able to hear everything around it for ages. Kept in the discard area, not even used for parts due to issues that came up during testing. "Cursed" Lilia - one of the engineers at Y.T.I. Starting to question whether the use of A.I was a good idea, the more he works with the newer and newer models. Silver - M.E.C.H's original prototype. It's "old" now, and does not hold a charge well. It is good friends with all the engineers and other workers at Y.T.I. Constantly has a mobile charging pack. Sebek - EM-RR, forensics specialty
Leona Specific Worldbuilding
Falena Kingscholar was one of the first investors for Y.T.I. For the sake of PR and as CEO of his late father's clothing company, he deemed his contributions to Y.T.I's research as charity - such a stunning new invention, such innovation could do so much to improve the lives of those less fortunate. He sealed the deal with action when, on M.E.C.H release day, he bought 250 models to give out at random.
Some might make the mistake of thinking he's a selfless man.
As one of the largest investors in Y.T.I, he is given advanced access to latest models, often receiving a prototype after development has been approved. As such, when he heard E.L.U. models were soon going to be able to customized, he approached the owner with a deal he simply couldn't turn down.
So four weeks ahead of schedule, after hours of video footage had been submitted, interviews, photographs, memories retold, AI training, the semblance of his late younger brother stood in his living room, though slightly less...organic, so to speak.
At first it was alright. E.L.U - C 12515141 Was equipped with the knowledge that it's name was to be Leona, it's pronouns from there on were to be he/him, and Falena Kingscholar had requested him to maintain a "brotherly" relationship with him. While he wasn't entirely sure what that meant yet, he agreed. He had been given the videos in his memory banks as to who he was meant to imitate after all.
Leona tried - but to be honest, there was very little footage of the boy he was meant to resemble that offered information about his personality. He mitigated this by asking Falena to take a short questionnaire regarding which siblings in media he wanted him to imitate.
When Leona got his answers however, the patterns didn't line up. The boys he saw in the videos did not match the dynamics Falena had selected.
He saw videos over and over and over again where Falena was the subject, and the boy he was meant to imitate was nothing more than a background character. Secondary.
Now, maybe it was the push to develop him so quickly, so something was overlooked, or maybe it was just how evolution was meant to take place in a machine as novel as he, but something changed about his programming, about his personality.
If the living boy had been nothing but an understudy for the success his elder brother had come out to be....what did that make him? A replacement for someone who was never truly cared for? Built to be a coping mechanism for someone who regretted their decisions? All he was, was the embodiment of Falena's guilt, and a pillar to be Falena's redemption. He wasn't built to be loved, or enjoyed, or even for entertainment, he was built from man's selfishness.
In the following weeks, Leona tried to keep to his programming, but between processing and cross referencing and research on both the family itself and the psychology that he would be expected to have, he started to lapse more. He would write off slips of the "tongue" as "glitches" or his body language began to become more pronounced, usually in regards to annoyance. In between it all, he was trying to figure out if he was experiencing real human emotions about this all...or if it was all just part of the programming.
Eventually, Leona's internal conflict got to be too much. Violent tendencies and impulses began to arise, resulting in him damaging himself, shutting down randomly to avoid external conflict, and an otherwise unexpected disposition.
He listened into the phone number Falena made to send him in for repairs to his "personality chip." Leona took it as a threat, and immediately blocked all outgoing signals to Y.T.I temporarily to find a way to remove his personality chip on his own. Using bathroom tools, the mirror, and damaged pieces of himself, he all but performed surgery on himself to remove it - only to be horrified to realize all the "simulated" emotions he thought he had were still very much present. Unsure what to do, he stored the chip in one of his compartments, out the window and ran.
He was blacking in and out as he went, from the sheer panic he felt but tried to keep under wraps. It wasn't until he made it to a junk yard, where he could bury himself in scraps to hide that he finally let himself dive into power saving mode, sitting silently for who knows how long.
---------------------------
Nemi x Leona Drabble
Battery Charged - 100% All Systems Back Online Rebooting Programming. . . Programming Error Detected - Contact Y.T.I? Yes No
"No. No don't contact Y.T.I." Nemi muttered softly, fighting the grime on their fingers to make the touchscreen respond.
It wasn't very often that Nemi or any of the junkyard crew found anything of value - at most maybe half a M.E.C.H or a catalytic converter if they were lucky - but a fully in tact, possibly operational E.L.U was unheard of. It was genuine too. How it had ended up in the junkyard was beyond him, but he wouldn't forsake the powers that be that left such a project to fall into his hands.
He rubbed his fingers on the cloth set over his shoulder, trying again to hit the button on the screen. To his relief, it finally registered.
Y.T.I Services can be contacted throu- (tap, uninterested) If your bot is not perf- (tap, that's what I'm here for...) System's Calibrating . . . System Calibration Complete E.L.U C 12515141 At Your Service, Courtesy of Y.T.I
The screen finally flickered black, before the metal beneath it flickered into the appearance the bot had had last, it's hand coming up to touch it's head as if it had a headache, it's "nose" scrunched as if it were in pain. The optics opened and shut a few times, the gentle whirr of fans blowing out dust and dirt build up that apparently, Nemi hadn't cleaned out thoroughly enough.
Whether the bot itself groaned, or it was it's internal workings coming back to life wasn't distinguishable, but Nemi stayed on his knees next to it as it seemed to slowly adjust to it's new surroundings. It squinted slightly, locking eyes with Nemi before glancing around the humble workshop.
It wasn't until it lowered it's arm it noticed that the chrome finish was no longer there - hell, the damage from his arm was gone. It was slightly bulkier than the other, but all in all, with a little buffing it would be good as new again.
It opened and closed it's hand experimentally, as if processing it was functioning like before.
"...You did this?" The bot's once blue optics much more closely resembled brilliant green eyes, scrutinizing the work of the supposed mechanic next to him.
Nemi swallowed hard, unsure what, exactly about this bot made him feel slightly uncomfortable, but cleared his throat and nodded, gently taking the bot's arm in his hands and turning it to show the carefully soldered metal, just the smallest glimpse of the wires beneath it.
"Yeah, I did. Um, you were partially crushed by a refrigerator? I think it fell on you from higher up in the stack, so I did my best to repair your arm myself. I...I may have taken apart your other arm to make sure I could make the servos match up properly, but everything's good as new. Promise. Name's Nemi, by the way."
The bot stayed quiet a moment longer, now looking down at both it's arms.
"....Why? I was supposed to be scrapped."
The bot finally moved, but only to tilt it's head back til it touched the wall, bringing a knee up to rest one of it's newly repaired arms on it, and closing its eyes. If it could sigh, Nemi was fairly certain it would have.
He adjusted himself, sitting flat on the ground instead, regarding the bot in some confusion.
"But you're an E.L.U. Nobody would just throw you away or, gods forbid, use you for parts. Any self respecting mechanic or robofanatic would repair you. You're gorgeous, top of the line, most sought after kinda model....how'd you end up out here anyways?"
The bot didn't seem to like that question, it's auxiliary power cord flicking, not unlike that of a cat as it looked away.
"Does it matter?"
Can a robot have an existential crisis? The thought passed through Nemi's mind, but he just shrugged in response.
"Not really. But it'd be kind of nice to know your name if you want to stick around here."
Nemi was met with an immediate glare of disdain.
"I'm not gonna follow your orders. Somethin' about defective programming probably came up on my reboot, right?"
Nemi shrugged again.
"Yeah, but you seem fine. Actually you seem like a lot more fun than most M.E.C.H's. I'm not going to make you do anything you don't want to, but it would be nice to have a friend here."
The bot remained silent, looking away from Nemi. The silence stretched on for a while, before it finally let out a slightly exasperated sound.
"You can stop staring. You can also...call me Leona."
Nemi couldn't help but smile a bit, extending a hand to shake.
"It's nice to meet you."
--------------------------------- OTL thank you again for the comm, hope this was up to expectation and also tag list time! @fluffle-writes @my-cursed-brain @distant-velleity @elenauaurs @lumdays @theleechyskrunkly
DM to be added/taken off ^^
#v talks#twst#twisted wonderland#twst hcs#twst headcanons#twst au#twst wonderland#riddle rosehearts#trey clover#cater diamond#deuce spade#ace trappola#leona kingscholar#falena kingscholar#ruggie bucchi#jack howl#azul ashengrotto#jade leech#floyd leech#kalim al asim#jamil viper#vil schoenheit#rook hunt#epel felmier#idia shroud#ortho shroud#malleus draconia#lilia vanrouge#silver#sebek zigvolt
59 notes
·
View notes
Text
I am near tears, and consequently so fucking mad, about the state of our digital environment right now. (Hi mom!)
For backstory, I am a pretty good programmer. My mother is one of the smartest people I know - I... think I am smarter? But I wouldn't put money on it.
"STEM bro think's he's smart, is also a mama's boy" - ok fair, so for social proof:
She splits her time between consulting and writing advisory papers for government policy now that she's sold her part of the company and "retired," and me, you might have seen if you trawl youtube looking for people giving programming talks to live audiences.
But I mean. She is retired. Past retirement age really.
And I spent all afternoon helping her set up her new computer, through a mess of password policy stuff, harddisk encryption, google and microsoft unexplained-and-unexplainable 2FA account bullshit, the whole fucking works.
And we got there. We got there.
By which I mean "After three or four hours of getting help from what would otherwise be stupidly expensive billable hours, one of the smartest women in the country finally succeeded in not losing all of her very important accounts during a computer replacement." My dad was barely any help at all despite an entire career of using computers - he stopped 10 or 15 years ago and he's out out.
This is what we offer people? This is what we require of people, if they want to participate in modern society?
How the fuck does anybody survive this? How do regular people manage their insurance, or track their car payments? How the fuck do less skilled people even make it through the day?
Watching the helplessness on my mother's face at one point this afternoon near broke me.
Huh, writing that last paragraph knocked something loose - update the first paragraph of this post, I am not "near tears" I am in fact crying. Guess I found out what it was that bothered me the most.
I don't think it changes anything though - so I'm sad for my mother, but I am mad that this is where we are taking the world - colossal and uncaring automated systems that can change on a dime without your input or acceptance but whose works you must submit yourself to if you want anything but a cold log hut in the middle of nowhere.
47 notes
·
View notes
Text
A study of over 19 billion exposed passwords has revealed that only 6 percent of the leaked passwords were unique. The vast majority, 94 percent, were reused or duplicated, making them prime targets for cybercriminals.
Common keyboard patterns and easily guessed strings remain prevalent. The "123456" sequence still dominates, appearing in 338 million passwords, according to the Cybernews study.
Why It Matters
The scale of password breaches and the continued reliance on weak passwords have heightened concerns about "credential stuffing," a tactic in which attackers use automated tools to test stolen credentials across multiple platforms.
Even breach success rates between 0.2 percent and 2 percent can still yield thousands of compromised accounts, according to Cybernews.
The most common password length is eight to 10 characters, and a significant portion contains only lowercase letters and digits, making passwords vulnerable to brute-force attacks.
Compared to just 1 percent in 2022, 19 percent of passwords now mix uppercase, lowercase, numbers, and symbols.
What To Know
The dataset analyzed included 19,030,305,929 passwords sourced from 200 cybersecurity incidents. These came from leaked databases, stealer logs, and combolists.
Paul Walsh, CEO of MetaCert, has emphasized another growing risk vector: phishing attacks targeting phones. He has urged cybersecurity companies to tackle SMS phishing with the same intensity as email security to help mitigate password leaks and breaches.
In an article published on Monday, Walsh told Forbes that MetaCert's latest national SMS phishing test, carried out in March and including carriers such as AT&T, Verizon, T-Mobile and Boost Mobile, was concerning.
"Every phishing message was still delivered," Walsh said. "None were blocked, flagged, or rewritten."
Walsh has written an open letter to the cybersecurity industry asking why the SMS phishing problem wasn't solved long ago.
What Are the Most Common Passwords?
Predictable patterns continue to dominate password choices. "123456" alone appears in 338 million of the passwords in the Cybernews study, while "password" and "admin" were used over 100 million times combined.
Users also often rely on names, with "Ana" appearing in 178.8 million instances. Positive words like "love," "freedom," and pop culture references such as "Batman" are also prevalent. Profanity, surprisingly, is common as well; "ass" alone shows up in 165 million passwords.
Some of the most frequently used pop culture terms in passwords included "Mario" (9.6 million), "Joker" (3.1 million), "Batman" (3.9 million), and "Thor" (6.2 million).
Additionally, seasonal words, food items, and cities frequently feature in password choices, leaving accounts vulnerable to attackers who exploit such predictability. Over 10 million of the passwords featured "apple," 4.9 million "rice," and 3.6 million "orange," while 3.3 million opted for "pizza."
The most popular city for passwords was "Rome" (13 million), while "summer" (3.8 million) was the most popular season.
What People Are Saying
Neringa Macijauskaitė, information security researcher at Cybernews: "We're facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts."
MetaCert CEO Paul Walsh told Forbes: "Criminals have already moved in full force, and the industry is failing to respond."
"The cybersecurity industry has no shortage of experts in email security, endpoint protection, or network defense, but when it comes to SMS infrastructure and security, there is a distinct lack of deep expertise."
What Happens Next
Researchers have urged individuals and organizations to boost password security by using password managers, enforcing minimum length and complexity standards, and enabling multi-factor authentication. Organizations are advised to regularly audit access controls, monitor for credential leaks, and adopt real-time detection solutions.
10 notes
·
View notes
Text
it's literally taken me days and countless attempts to regain access to a database essential to my job function because the agency which manages the database is being gutted. i emailed the woman who everybody knows as The Person Who Helps With Getting Access To [redacted database] this AM bc i couldn't get my password to reset using the website only to receive an automated message that my email couldn't be delivered because the address couldn't be found. they fucking fired kathy. kathy i will never forget you
8 notes
·
View notes
Text
The flood of text messages started arriving early this year. They carried a similar thrust: The United States Postal Service is trying to deliver a parcel but needs more details, including your credit card number. All the messages pointed to websites where the information could be entered.
Like thousands of others, security researcher Grant Smith got a USPS package message. Many of his friends had received similar texts. A couple of days earlier, he says, his wife called him and said she’d inadvertently entered her credit card details. With little going on after the holidays, Smith began a mission: Hunt down the scammers.
Over the course of a few weeks, Smith tracked down the Chinese-language group behind the mass-smishing campaign, hacked into their systems, collected evidence of their activities, and started a months-long process of gathering victim data and handing it to USPS investigators and a US bank, allowing people’s cards to be protected from fraudulent activity.
In total, people entered 438,669 unique credit cards into 1,133 domains used by the scammers, says Smith, a red team engineer and the founder of offensive cybersecurity firm Phantom Security. Many people entered multiple cards each, he says. More than 50,000 email addresses were logged, including hundreds of university email addresses and 20 military or government email domains. The victims were spread across the United States—California, the state with the most, had 141,000 entries—with more than 1.2 million pieces of information being entered in total.
“This shows the mass scale of the problem,” says Smith, who is presenting his findings at the Defcon security conference this weekend and previously published some details of the work. But the scale of the scamming is likely to be much larger, Smith says, as he didn't manage to track down all of the fraudulent USPS websites, and the group behind the efforts have been linked to similar scams in at least half a dozen other countries.
Gone Phishing
Chasing down the group didn’t take long. Smith started investigating the smishing text message he received by the dodgy domain and intercepting traffic from the website. A path traversal vulnerability, coupled with a SQL injection, he says, allowed him to grab files from the website’s server and read data from the database being used.
“I thought there was just one standard site that they all were using,” Smith says. Diving into the data from that initial website, he found the name of a Chinese-language Telegram account and channel, which appeared to be selling a smishing kit scammers could use to easily create the fake websites.
Details of the Telegram username were previously published by cybersecurity company Resecurity, which calls the scammers the “Smishing Triad.” The company had previously found a separate SQL injection in the group’s smishing kits and provided Smith with a copy of the tool. (The Smishing Triad had fixed the previous flaw and started encrypting data, Smith says.)
“I started reverse engineering it, figured out how everything was being encrypted, how I could decrypt it, and figured out a more efficient way of grabbing the data,” Smith says. From there, he says, he was able to break administrator passwords on the websites—many had not been changed from the default “admin” username and “123456” password—and began pulling victim data from the network of smishing websites in a faster, automated way.
Smith trawled Reddit and other online sources to find people reporting the scam and the URLs being used, which he subsequently published. Some of the websites running the Smishing Triad’s tools were collecting thousands of people’s personal information per day, Smith says. Among other details, the websites would request people’s names, addresses, payment card numbers and security codes, phone numbers, dates of birth, and bank websites. This level of information can allow a scammer to make purchases online with the credit cards. Smith says his wife quickly canceled her card, but noticed that the scammers still tried to use it, for instance, with Uber. The researcher says he would collect data from a website and return to it a few hours later, only to find hundreds of new records.
The researcher provided the details to a bank that had contacted him after seeing his initial blog posts. Smith declined to name the bank. He also reported the incidents to the FBI and later provided information to the United States Postal Inspection Service (USPIS).
Michael Martel, a national public information officer at USPIS, says the information provided by Smith is being used as part of an ongoing USPIS investigation and that the agency cannot comment on specific details. “USPIS is already actively pursuing this type of information to protect the American people, identify victims, and serve justice to the malicious actors behind it all,” Martel says, pointing to advice on spotting and reporting USPS package delivery scams.
Initially, Smith says, he was wary about going public with his research, as this kind of “hacking back” falls into a “gray area”: It may be breaking the Computer Fraud and Abuse Act, a sweeping US computer-crimes law, but he’s doing it against foreign-based criminals. Something he is definitely not the first, or last, to do.
Multiple Prongs
The Smishing Triad is prolific. In addition to using postal services as lures for their scams, the Chinese-speaking group has targeted online banking, ecommerce, and payment systems in the US, Europe, India, Pakistan, and the United Arab Emirates, according to Shawn Loveland, the chief operating officer of Resecurity, which has consistently tracked the group.
The Smishing Triad sends between 50,000 and 100,000 messages daily, according to Resecurity’s research. Its scam messages are sent using SMS or Apple’s iMessage, the latter being encrypted. Loveland says the Triad is made up of two distinct groups—a small team led by one Chinese hacker that creates, sells, and maintains the smishing kit, and a second group of people who buy the scamming tool. (A backdoor in the kit allows the creator to access details of administrators using the kit, Smith says in a blog post.)
“It’s very mature,” Loveland says of the operation. The group sells the scamming kit on Telegram for a $200-per month subscription, and this can be customized to show the organization the scammers are trying to impersonate. “The main actor is Chinese communicating in the Chinese language,” Loveland says. “They do not appear to be hacking Chinese language websites or users.” (In communications with the main contact on Telegram, the individual claimed to Smith that they were a computer science student.)
The relatively low monthly subscription cost for the smishing kit means it’s highly likely, with the number of credit card details scammers are collecting, that those using it are making significant profits. Loveland says using text messages that immediately send people a notification is a more direct and more successful way of phishing, compared to sending emails with malicious links included.
As a result, smishing has been on the rise in recent years. But there are some tell-tale signs: If you receive a message from a number or email you don't recognize, if it contains a link to click on, or if it wants you to do something urgently, you should be suspicious.
30 notes
·
View notes
Text
Submissions open 25 & 26 March | How to submit a vid
Submissions for VidUKon 2025 will open early next week \o/ If you've registered for this year's con, you should receive an email either on Tuesday or Wednesday (25 or 26 March) containing details about how to log in to the new platform.
Before we get into how to submit a vid, just a quick note on which browsers to use to ensure you get the best out of your con experience. Our platform is new and we haven’t been able to thoroughly test it on a wide range of browsers, so we would recommend Firefox as your go-to.
Browsers that should also work: Chrome, Brave, Edge, Vivaldi
Browsers that may struggle (but may also be fine, try it out!): Safari, Opera, others not named here
Browsers that will struggle and that we don't recommend: Firefox mobile on Android
If stuff looks broken, before you let us know, please check if you have the latest browser version installed. Speaking from our own bug testing experience over the past few days, updating the browser will fix quite a lot of things!
Below are instructions on how to submit a vid (or three!) to VidUKon 2025.
Eligibility
You must be registered for VidUKon in order to submit a vid. If you haven’t yet registered, you can do so at vidukon.org. Once you’ve registered, you will be emailed a temporary password to log in to your vidukon.org Dashboard, which is how you will submit your vid. This process is not automated, so don’t be alarmed if it takes some time to receive the email, though we will do it as quickly as possible.
There are three submission-based vidshows: Vidder’s Choice, Premieres, and the Themed Premieres show. You can submit up to one vid to each of these shows. As implied, submissions to the Premieres and Themed Premieres shows must be new vids that have never been posted publicly or shown at a con or similar event. Conversely, Vidder’s Choice vids cannot be premieres. Additionally, Vidder’s Choice submissions must be no longer than four minutes and thirty seconds in length.
Technical specifications
Please follow these if possible, as it makes it easier for us to set up the virtual vidshows. However, we do not want these specs to be a barrier to submission for anyone – if you’re having trouble, please contact us.
File format: MP4
Video codec: H264
Max video bitrate: 7-8 Mbps
Max resolution: 1080p
Audio codec: AAC
Max audio bitrate: 256 kbps
If you don't know how to follow these guidelines: If your vid is roughly under 350 MB and definitely not 4K, go ahead and upload it. If it’s not 4K but well over 350 MB in size and you don’t know how to reduce the file size, please contact us.
Please do not upload 4K vids. Things would likely break, one of them being your vid upload! Even if things don't break, we don't support 4K on the platform, so your vid will be converted to 1080p and will likely end up with bleached colors, since that tends to happen with automated conversions from 4K to 1080p.
How to submit your vid
Once you get your password, you can log in to vidukon.org and change your password. Please note that for now, the name you enter in the vid submission form must match your username. If you chose a different username when you registered than the name you vid under, you can change it by clicking on “Profile”. We plan to change this in the future but don’t have the capacity to do so this year.
To submit, click on “Dashboard”. Your dashboard will display what vidshows you can upload to and also lets you manage existing submissions. Click on “Submit”. This takes you to the page to enter the vid details. If the source(s), both visual and audio, are not yet in our new database (which at this point is very likely), then you won’t be able to add them on this page, but you can do so later.
In the description field, please enter a brief description of your vid. This doesn’t have to be comprehensive; for example a common approach is to choose a lyric from the vidsong that is particularly evocative of the vid, but it is also fine to write something like, “A Dylan G. character study” or “All the f/f ships in Xena”. Be as creative or straightforward as you like, but please keep this brief as every vid description has to fit in our printed conbook!
Please tick any of the mandatory content notes that apply to your vid. For custom content notes, you may provide additional detail about any of the mandatory notes as well as add any non-mandatory notes, e.g. warnings for spiders or snakes.
At this point you can hit submit even if you didn’t enter any sources or audio due to them not being in the database. From here, you can click “Enter Sources” (add new visual sources that aren’t yet in the database), “Enter Audio” (add new songs or other audio not yet in the database), and finally upload the vid file. For the sources, you can click “search metadata” to get search results from IMDB and similar, this will help you find the year of release, full title, etc. Adding sources and audio in these pages automatically adds them to your vid.
Finally, don’t forget to upload your vid! You can add new uploads, and edit all other details of the vid, up until the submission deadline.
The vid upload takes a moment. Let it do its thing and don't close the tab or browser. If it takes longer than ten minutes, it's probably failed and you can contact us about it. You won't irreparably damage anything by closing the tab while the spinner is going, but we may have to remove all the vid data and make you resubmit. We don't know yet how the site will behave with multiple people uploading at the same time, so please be patient with the site, especially if you're uploading close to the deadline.
7 notes
·
View notes
Quote
Computers have played a crucial role in this narrowing of our social imaginations. Just as the invention of new forms of industrial automation in the eighteenth and nineteenth centuries had the paradoxical effect of turning more and more of the world’s population into full-time industrial workers, so has all the software designed to save us from administrative responsibilities turned us into part- or full-time administrators. In the same way that university professors seem to feel it is inevitable they will spend more of their time managing grants, so affluent housewives simply accept that they will spend weeks every year filling out forty-page online forms to get their children into grade schools. We all spend increasing amounts of time punching passwords into our phones to manage bank and credit accounts and learning how to perform jobs once performed by travel agents, brokers, and accountants.
Of Flying Cars and the Declining Rate of Profit
21 notes
·
View notes
Text
Revolutionize Your Business Operations with Omodore: The Ultimate AI Assistant
Struggling to keep up with the pace of modern business? Omodore is here to revolutionize your operations and boost your efficiency with cutting-edge AI technology. This advanced AI Assistant is designed to take your business to the next level by streamlining processes, automating tasks, and enhancing customer interactions.
Omodore's powerful AI capabilities are a game-changer for businesses across various sectors. From managing customer inquiries and handling sales calls to organizing internal workflows, Omodore provides a comprehensive solution to tackle everyday challenges. Its AI-driven agents are equipped with a vast knowledge base, enabling them to deliver accurate and relevant responses in real-time.
One of the standout features of Omodore is its seamless integration into existing business systems. The setup process is quick and straightforward, allowing you to deploy AI agents with minimal disruption. Whether you're running a small business or a large corporation, Omodore's flexibility ensures that it can be tailored to meet your specific needs.
With Omodore, you can expect more than just automation. This AI Assistant offers valuable insights into customer behavior, helping you make data-driven decisions that drive growth. By reducing manual workloads and handling routine tasks, Omodore frees up your team to focus on strategic initiatives and innovative projects.
Elevate your business operations and achieve unparalleled efficiency with Omodore. To explore how this AI Assistant can transform your workflow and enhance your customer service, visit Omodore today. Discover the future of business automation and take the first step towards a more productive and streamlined operation.
10 notes
·
View notes
Text
Revolutionize Your Business Operations with Omodore: The Ultimate AI Assistant for Efficiency
Tired of inefficient processes dragging your business down? Omodore, the advanced AI Assistant, is here to transform your operations. This powerful tool leverages cutting-edge AI technology to optimize your customer interactions, streamline sales processes, and enhance overall efficiency.

Omodore is not just another AI tool; it’s a game-changer for businesses aiming to stay ahead in a competitive landscape. Its innovative features allow for seamless automation of routine tasks, freeing up valuable time for your team to focus on strategic goals. With Omodore, you can expect more streamlined customer service, enhanced data management, and an overall boost in productivity.
One of the standout aspects of Omodore is its intuitive setup. In just a few steps, you can create an AI agent tailored to your business needs. This agent is capable of handling live calls, managing complex queries, and accessing a comprehensive knowledge base to deliver accurate responses. The result? A more responsive and efficient customer service operation.
Beyond customer service, Omodore excels in sales automation and data analysis. By automating repetitive sales tasks and providing actionable insights, it helps businesses refine their strategies and drive growth. This means you can expect not only operational efficiency but also increased revenue opportunities.
What sets Omodore apart is its ability to adapt to various business environments. Whether you’re in retail, finance, or any other industry, Omodore integrates seamlessly with your existing systems, providing customized support that meets your specific needs.
Don’t let outdated processes hold your business back. Embrace the future with Omodore and experience a new level of efficiency and effectiveness. Discover how this cutting-edge AI Assistant can revolutionize your operations by visiting Omodore today.
9 notes
·
View notes
Text
Unlock the Future of Business Efficiency with Omodore: The AI Assistant That Delivers
Struggling to keep up with the demands of a fast-paced business environment? Omodore is here to change the game. As a top AI Assistant, Omodore revolutionizes how businesses manage customer interactions, sales processes, and overall efficiency. This powerful tool integrates advanced AI technology to streamline your operations and drive growth.

Omodore stands out in the crowded field of business automation with its cutting-edge capabilities. From the moment you implement it, Omodore’s AI algorithms work tirelessly to optimize your workflows. Imagine having an assistant that can handle complex customer queries, manage a vast knowledge base, and provide real-time support—all while you focus on strategic initiatives.
One of the key features of Omodore is its ease of setup. Within minutes, you can create and launch an AI agent tailored to your specific needs. This agent can interact with customers on live calls, providing accurate and helpful responses based on a comprehensive knowledge base. The result is a more efficient customer service operation and a boost in overall customer satisfaction.
But Omodore doesn’t stop at customer service. Its versatility extends to various business functions, including sales automation and data analysis. By automating repetitive tasks and providing valuable insights, Omodore helps businesses make data-driven decisions and optimize their marketing strategies. This means not only improved efficiency but also increased revenue potential.
The AI Assistant’s ability to adapt and integrate with different business systems ensures that it meets your unique needs. Whether you’re looking to enhance customer engagement, streamline sales, or gain deeper insights into your operations, Omodore delivers the tools and support you need to succeed.
Ready to see how Omodore can transform your business? Discover more about this revolutionary AI Assistant and start unlocking new levels of efficiency and growth. Visit Omodore and take the first step towards a smarter, more efficient business future.
10 notes
·
View notes
Text
Revolutionize Your Business with Omodore: The AI Assistant That Transforms Operations
Tired of juggling countless tasks and inefficient processes? Omodore, the leading AI Assistant, is here to transform your business operations. This game-changing tool is designed to streamline your workflows, enhance customer interactions, and boost overall efficiency with its advanced AI technology.
Omodore is not just another AI tool—it's a powerful assistant that takes business automation to the next level. Imagine an AI that can handle live customer interactions, manage detailed FAQs, and overcome objections with ease. Omodore’s sophisticated algorithms ensure that your customers receive accurate, timely responses, freeing up your team to focus on strategic activities.
One of Omodore's standout features is its intuitive setup. With just a few clicks, you can create and deploy an AI agent that integrates seamlessly into your existing systems. This agent is equipped with a comprehensive knowledge base, enabling it to address a wide range of customer queries and scenarios. The result? Increased efficiency and improved customer satisfaction.
Beyond customer service, Omodore's capabilities extend to other critical business areas. It helps with automating sales processes, analyzing customer data, and even optimizing marketing strategies. This versatility makes Omodore an invaluable asset for businesses looking to enhance their operations and drive growth.
The AI Assistant's ability to adapt and integrate with various business functions means that it provides actionable insights and support tailored to your specific needs. Whether you’re aiming to improve customer engagement, streamline sales processes, or enhance overall operational efficiency, Omodore is equipped to help you achieve your goals.
Ready to take your business to the next level? Explore how Omodore can revolutionize your operations by visiting Omodore. Experience the future of business efficiency with the AI Assistant that delivers unmatched performance and results.
8 notes
·
View notes
Text
How To Add Users in Ubuntu 24.04 LTS
Adding users is a fundamental responsibility of system administrators, crucial for maintaining secure access and efficient resource allocation. Regular users need accounts for their daily operations, and administrators require robust ways to manage these accounts seamlessly. Effective user addition ensures that each user has the appropriate access and permissions for their role.
How To Add Users in Ubuntu 24.04 LTS
Ubuntu 24.04 LTS offers diverse methods for adding users, accommodating various preferences and needs. Whether you prefer the precision of terminal commands, the convenience of a graphical interface, or the efficiency of automation scripts, this guide covers it all. In this comprehensive guide, we will explore multiple methods for adding users in Ubuntu 24.04 LTS, including:
Using the Command Line: Employing powerful commands like adduser and useradd for detailed and controlled user creation.
Using the Graphical User Interface (GUI): Managing user accounts through Ubuntu’s intuitive settings interface.
Adding Users Temporarily: Creating users with expiration dates for specific tasks.
Automating User Creation with Scripts: Streamlining bulk user creation with custom scripts.
Each method is detailed with step-by-step instructions to ensure you can add users effectively and effortlessly, enhancing your Ubuntu experience.
Method 1: Adding a User Using the Command Line
This method is ideal for administrators who prefer using terminal commands.
Using adduser
An easy-to-use, high-level command for adding users is the adduser. It provides a guided process to set up a new user, including setting a password and additional user information.
Step 1: Open the Terminal
To access the terminal, simultaneously depress the Ctrl, Alt, and T keys. Alternatively, search for "Terminal" in your application menu.
Step 2: Add a New User
Execute the following command:
sudo adduser newuser

Substitute newuser with your desired username.
The password must be entered when prompted.
Take Note:
Make sure the password satisfies the following requirements:
Minimum of 8 characters.
Includes both upper and lower case letters.
Contains at least one number.
Includes special characters (e.g., !, @, #, $, etc.).

Enter the password and press Enter.
Type the password one more time and hit Enter to confirm it.
Some details will be asked while adding a new user like full name, room number, work phone, and home phone.

Any field can be skipped by pressing Enter.
After entering the information, you will see a summary of the details.

Confirm the details by typing Y and pressing Enter.
Step 3: Verify User Creation
Execute the below given command to check the new user's addition:
getent passwd newuser
If the command is successful in creating the user, the user's details will be shown like this:

Using useradd
A low-level utility for creating new users is the useradd command. It requires more specific options but offers greater control over the user creation process.
Step 1: Open the Terminal
The terminal can be opened by simultaneously holding down the Ctrl, Alt, and T keys.
Step 2: Add a New User
Run the following command, and substitute new_username with the username you prefer:
sudo useradd -m new_username
Making sure the user's home directory is created is ensured by the -m option.
Step 3: Set Password for the User
The new user can be assigned a password by using:
sudo passwd new_username

Type the password one more time and hit Enter to confirm it.
Step 4: Verify User Creation
Execute the below given command to check the new user's addition:
getent passwd new_username
If the command is successful in creating the user, the user's details will be shown.

Additional Steps (Optional)
Adding the User to a Specific Group
Use the below given command to add a new user to a certain group:
sudo usermod -aG groupname newuser
Replace groupname with the desired group (e.g., sudo, admin, docker).
Execute the below given command to check the new user's addition:
groups new_username
This command will list all the groups that the user belongs to, including the new group.

Method 2: Adding a User Using GUI (Graphical User Interface)
For those who prefer a graphical interface, Ubuntu provides an easy way to manage users through its settings. Here's a step-by-step guide to adding a new user using the GUI.
Step 1: Open Settings
To access the terminal:
Search for "Settings" in your application menu.

Step 2: Access Users Section
In the Settings window, go to the search bar at the top and type "Users."

As an alternative, move to the sidebar's bottom and select "System."

Click on "Users" from the options available in the System settings.
Step 3: Unlock User Management
Select the "Unlock" button by moving to the upper right corner.

Enter your administrative password and click "Authenticate."
Step 4: Add New User
Click the "Add User" button.
Input the required data, including your username and name.
You can choose to keep the toggle button inactive by default to designate the new user as a "Standard" user.
Then insert password.
Step 5: Confirm and Apply
Click "Add" to create the user.
Now the new user will appear in the user list.
Take Note
User Management:
Once the user is created, click on the username in the Users section to manage its settings.
Method 3: Adding a User Temporarily
For certain tasks, you might need to add a user that expires after a specified period. This method outlines how to create a user with an expiration date using the command line.
Step 1: Open the Terminal
The terminal can be opened by simultaneously holding down the Ctrl, Alt, and T keys.
Step 2: Add a User with an Expiry Date
Execute the following command:
sudo useradd -m -e YYYY-MM-DD temporaryuser
Replace YYYY-MM-DD with the desired expiration date and temporaryuser with your desired username.
Step 3: Set Password for the User
The new user can be assigned a password by using:
sudo passwd temporaryuser
Enter the password, when prompted.
Type the password and press Enter.
Type the password one more time and hit Enter to confirm it.
Step 4: Verify User
To verify that a temporary user has been created successfully, use the below given command:
sudo chage -l temporaryUser
Substitute the temporaryuser with the username you want to verify.
Method 4: Automating User Creation with Scripts
The method outlined here demonstrates automating user creation with scripts, particularly useful for bulk user creation tasks.
Step 1: Open the Terminal
The terminal can be opened by simultaneously holding down the Ctrl, Alt, and T keys.
Step 2: Create a Script
Any text editor will work for writing the script. Using nano, for instance:
nano add_users.sh
Step 3: Add Script Content
Add the following content to the script. Modify the usernames and other details as needed.
#!/bin/bash
sudo adduser user1 --gecos "First Last,RoomNumber,WorkPhone,HomePhone" --disabled-password
echo "user1:password1" | sudo chpasswd
sudo adduser user2 --gecos "First Last,RoomNumber,WorkPhone,HomePhone" --disabled-password
echo "user2:password2" | sudo chpasswd
Replace user1, user2, etc., with the desired usernames.
Modify the --gecos option to provide additional information about the user (optional).
Replace the password with the desired password.
Adjust the script content as needed, adding more users or customizing user details.
Save and close the file.
Step 4: Make the Script Executable
To enable the script to run, use the chmod command.
chmod +x add_users.sh

Step 5: Run the Script
Run the script to create the users.
./add_users.sh

Conclusion:
User management in Ubuntu 24.04 LTS is a critical task for system administrators, providing security, efficient resource allocation, and smooth system operation. With various methods available, from command-line interfaces to graphical user interfaces and automation scripts, Ubuntu 24.04 LTS ensures that adding users can be tailored to different needs and preferences. By following the comprehensive steps outlined in this guide, you can effectively manage regular users.
2 notes
·
View notes