#Password Recovery and Security
Explore tagged Tumblr posts
Text
✅ SEO for WordPress
#IT Consultancy#Web and App Development#AdSense#SEO#Graphic Design#Password Recovery and Security#Online Marketing#Corporate Services
0 notes
Text
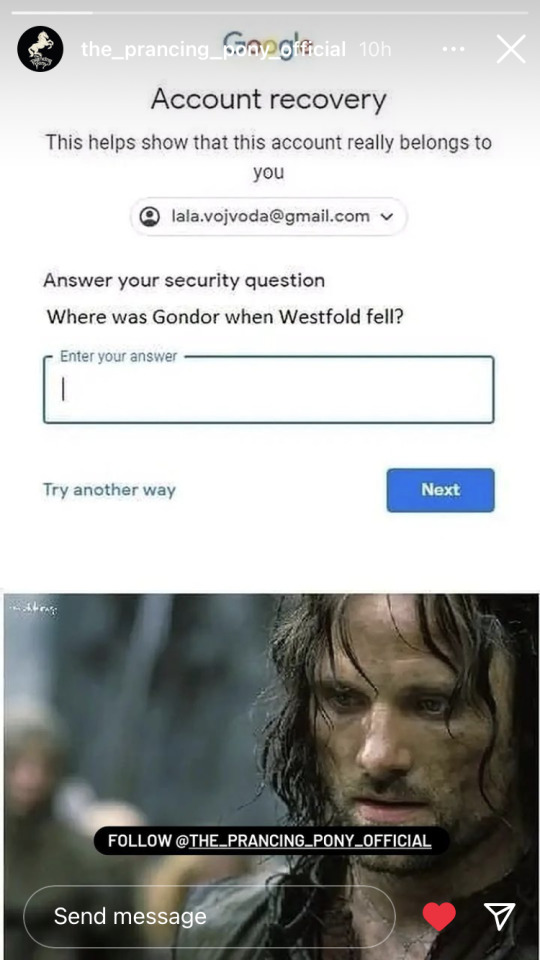
#lord of the rings#rings of power#aragorn#the two towers#jrr tolkien#tolkien#silmarillion#gondor#rohan#king theoden#viggo mortensen#meme#lotr#lotr memes#google#cyber security#password#gmail#account recovery#funny#lol#haha
41 notes
·
View notes
Text
7 Secrets ChatGPT Pour Automatiser et Optimiser Votre Entreprise
Cette vidéo vous dévoile les meilleures stratégies pour webinar: secrets to a hack-proof joomla revealed – astuces et stratégies pour réussir en ligne !. À ne pas manquer ! Description détaillée de 7 Secrets ChatGPT Pour Automatiser et Optimiser Votre Entreprise Découvrez les meilleures pratiques pour améliorer la conception de vos emails marketing et augmenter votre taux d’ouverture et de…

View On WordPress
#Joomla#joomla security#distaster recovery#password generation#siteground#hosting#webinar#hébergement web#performance#SEO#marketing#business
0 notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
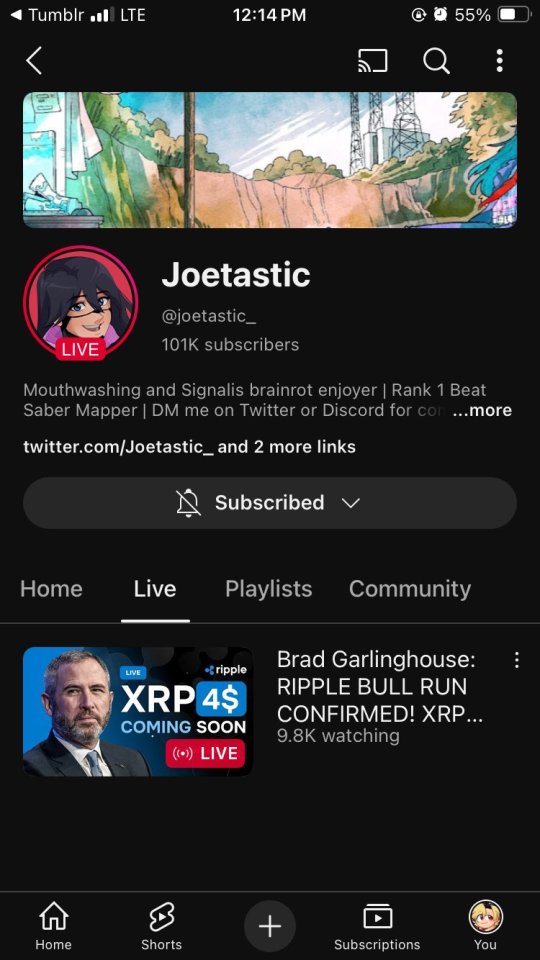
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
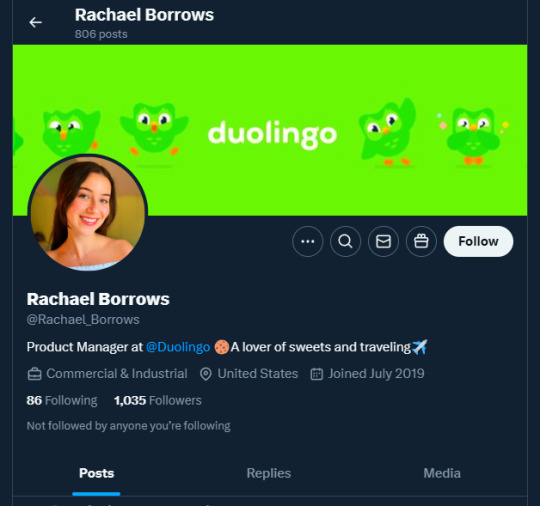
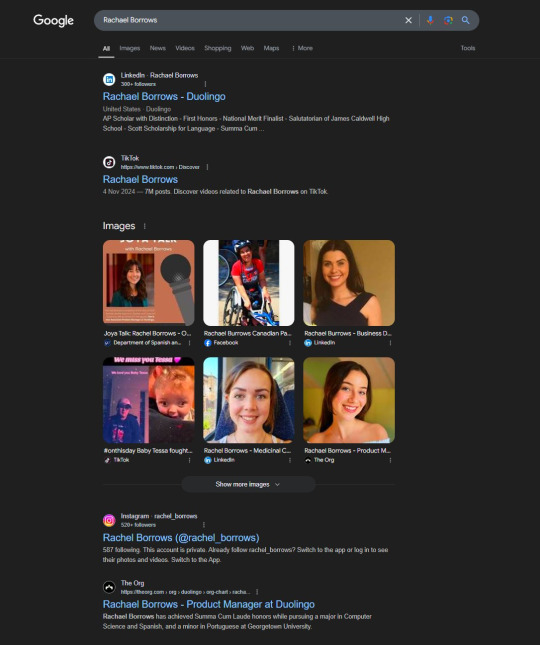
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
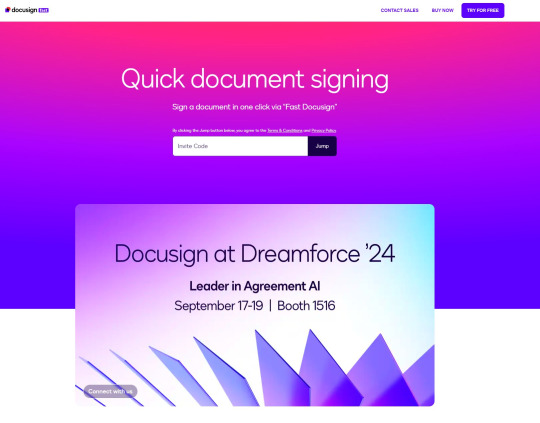
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
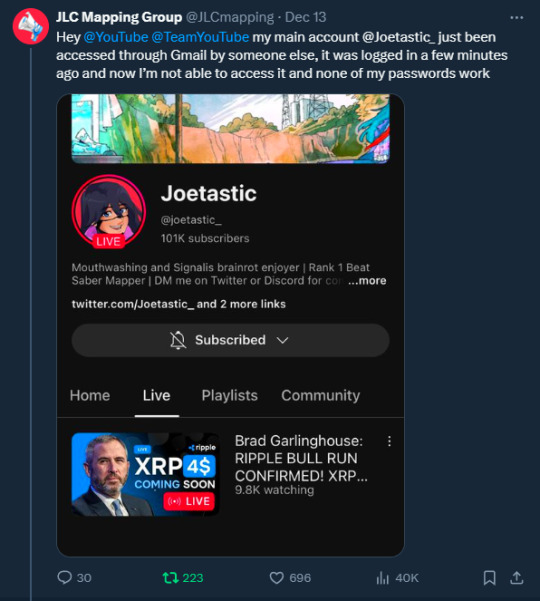
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
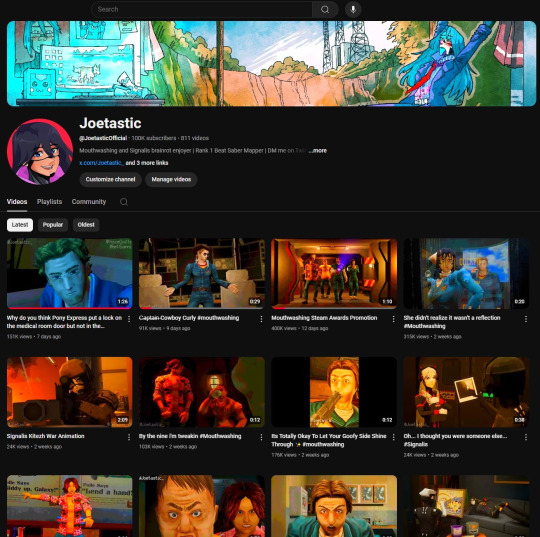
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
Inactive Gmail Accounts Deletion Next Month December 2023 - Secure Steps to Keep Your Google Account Active
Introduction: As we navigate the vast digital landscape, keeping our online accounts secure and active is crucial. Google has recently announced an upcoming cleanup initiative that targets inactive Gmail accounts. Scheduled for deletion next month, this proactive measure aims to enhance security and manage data storage efficiently. In this blog post, we’ll guide you through the steps to ensure…

View On WordPress
#Account Access#Account Activity#Account Maintenance#Account Notifications#Account Recovery#Cleanup#Cybersecurity#Data Storage#Deletion#Digital Cleanup#Gmail#Google Account#Google Services#Inactive Accounts#Online Privacy#Online Security#Password Security#Security Measures#Third-Party Apps#Two-Factor Authentication
0 notes
Text
#ccount recovery#Facebook#FB account#account access#account security#account verification#password reset#account authentication#social media#login issues#account recovery without code
0 notes
Note
I'm not the most security savvy but two-factor authentication makes me deeply suspicious. Is it actually more secure or is it just annoying? Especially the ones that send a code to your phone that pops up in your notifications.
It is genuinely, massively, TREMENDOUSLY more secure to use 2FA/MFA than to not use it.
One of our clients is currently under attack by a group that appears to be using credential stuffing; they are making educated guesses about the accounts they're trying to lot into based on common factors showing up in the credentials in years of pastes and breaches and leaks. Like, let's say it's a professional arborist's guild and their domain is arborist.tree and they've had three hundred members who have had their credentials compromised in the last ten years and the people looking at all the passwords associated with arborist.tree noticed that the words "arboreal" and "conifer" and "leaf" and "branch" show up over and over and over again in the passwords for the members of the professional arborist's guild.
So they can make an educated guess for how to log in to accounts belonging to the tree-loving tree lover's club, combine that with the list of legitimate emails, and go to town.
And they are in fact going to town. We're getting between 1000 and 4000 login attempts per hour. It's been happening for a couple weeks.
And every single one of those attempts is failing - in spite of some pretty poor password practices that believe me, I have been doing some talking about - as a result of having MFA enforced for the entire group. They all use an app that is synced to their individual accounts with a mobile device, except that sometimes you have trouble getting a code when you're up in a tree so some of them have physical MFA tokens.
People try to sign into my tumblr sometimes. To those people I say: lol, good luck, I couldn't guess my own password with a gun to my head. But if I *did* have some password that was, like "tiny-bastard-is#1" they would also need access to my email address because I've got MFA set up on tumblr. And to THAT I say: lol, good luck, it's complex passwords and MFA all the way down.
Of the types of MFA that most people will run across, the most secure to least secure hierarchy goes physical token>app based one-time-passwords>tie between email and SMS. Email and SMS are less preferred because email is relatively easy to capture and open in transit and cellphone SIMs can be cloned to capture your text messages. But if you are using email or SMS for your authentication you are still miles and miles and miles ahead of people who are not using any kind of authentication.
MFA is, in fact, so effective that I only advise people to turn it on if they are 100% sure that they will be able to access the account if they lose access to the device that had the authenticator on it. You usually can do this by saving a collection of recovery codes someplace safe (I recommend doing this in the secure notes section of your password manager on the entry for the site in question - if this is not a feature that your password manager has, I recommend that you get a better password manager, and the password manager I recommend is bitwarden).
A couple weeks ago I needed to get into a work account that I had created in 2019. In 2022, my boss had completely taken me off of managing that service and had his own account, so I deleted it from my authenticator. Then in 2024 my boss sold the business but didn't provide MFA for a ton of the accounts we've got. I was able to get back into my account because five years earlier I had taken a photo of the ten security codes from the company and saved them in a folder on my desktop called "work recovery codes." If you are going to use MFA, it is VITALLY IMPORTANT that you save recovery codes for the accounts you're authenticating someplace that you'll be able to find them, because MFA is so secure that the biggest problem with it is locking people out of their accounts.
In any kind of business context, I think MFA should be mandatory. No question.
For personal accounts, I think you should be pointed and cautious where you apply it, and always leave yourself another way in. There are SO MANY stories about people having their phones wiped or stolen or destroyed and losing MFA with the device because they didn't have a backup of the app or hadn't properly transferred it to a new device.
But it's also important to note that MFA is not a "fix all security forever" thing - I've talked about session hijacking here and the way you most often see MFA defeated is by tricking someone into logging in to a portal that gives them access to your cookies. This is usually done by phishing and sending someone a link to a fake portal.
That is YET ANOTHER reason that you should be using a good password manager that allows you to set the base domain for the password you're using so that you can be sure you're not logging in to a faked portal. If your password manager doesn't have that feature (setting the domain where you can log in to the base domain) then I recommend that you get a better password manager (get bitwarden.)
In 2020 my terrible boss wanted me to write him a book about tech that he could have run off at a vanity press and could give to prospect customers as a business card. That was a terrible idea, but I worked on the book anyway and started writing it as a book about security for nontechnical people. I started out with a very simple statement:
If every one of our customers did what we recommend in the first four chapters of this book (make good backups, use a password manager and complex unique passwords, enable MFA, and learn how to avoid phishing), we would go out of business, because supporting problems that come from those four things is about 90-95% of our work.
So yes, absolutely, please use MFA. BUT! Save your recovery codes.
828 notes
·
View notes
Note
Okay cell phone carrier customers, for the last time: If someone gets into your wireless account and orders a shit ton of devices, there's a REALLY FUCKING GOOD CHANCE that you TOLD THEM WHAT THE PASSWORD WAS or gave them access to your account when they tapped the "i forgot my password" button. You did that. You. The security systems are set up and they do work properly, but for some reason when you get a phonecall from someone with a heavy accent who can't even say the company name correctly YOU literally gave them access to your account. So sure, threaten to sue the company all you want. Go ahead. Waste your money and time in court. "You've lost yourself a valuable customer!" Bitch this company is a multi-trillion dollar company, you do not matter at all. Leave. But the point is, don't scream at customer service that your phone carriers security sucks when YOU LITERALLY GAVE OUT YOUR PASSWORD And the "I forgot my password" recovery text thing? Yeah, yeah; that has this EXACT PHRASE "[company name] will NEVER ask you for this code, and if someone does then they are not from [company name]." Like once or twice, sure. But the amount of customers that ignore this is in the thousands what the actual fuck. READING COMPREHENSION GUYS. IT'S IMPORTANT.
Posted by admin Rodney.
164 notes
·
View notes
Text
On season 5 of my jwcc rewatch and I'm at the part where Daniel's trying to get the password from the kids and I'm just like. Daniel. My man. Do you not have a forgot password feature on your super important business computer?? Did you not link your account to an email or phone number?? No dual-factor authentication or password recovery feature?? Like if Brooklynn didn't get into your system someone else would have you don't even have the most basic form of cyber security 😭😭
#this is SO funny to me you guys#a whole business tycoon that cant reset his password X'''D#jwcc#camp cretaceous#jwcc spoilers#camp cretaceous spoilers#<- those tags are just cause i saw posts from someone watching for the first time :)
50 notes
·
View notes
Text
CrowdStrike'd and BitLocker'd
With yesterday's CrowdStrike outage. I'm sure a number of you are probably wondering "what does BitLocker have to do with any of this?" Well, it all has to do with an added layer of security many organizations use to keep data from being stolen if a computers ends up in the hands of an "unauthorized user."
To start, let me briefly explain what the CrowdStrike driver issue did and what the fix for it is.
After the update was automatically installed to computers running the CrowdStrike Falcon Sensor, a faulty driver file caused the Windows kernel on those computers to crash and display a Blue Screen of Death. How Windows typically handles a crash like this is to create a crash log file, then perform a reboot. Since this driver would launch shortly after Windows finished booting, it would cause the operating system to crash and reboot again. When two crashes have occurred in sequence, Windows will automatically boot into Recovery Mode. Hence why we say several pictures of the Recovery Mode screen across social media yesterday.

Unfortunately, this update was automatically pushed out to around 8.5 million computers across several organizations, causing widespread chaos within the matter of a few hours. And the fix for this issue had to be performed by physically accessing each computer, which required those of us working in I.T. to have to run around several facilities, locate each affected computer, and apply the fix one by one.
The short and simple of the fix is either one of two options. You can either use the Recovery Mode that Windows was already booted into to navigate to Start-Up Setting, and launch Safe Mode. Once Windows boots into Safe Mode, the technician can navigate to C:\Windows\System32\Drivers\CrowdStrike, and delete the file C00000291-*.sys. After that the computer can be rebooted as normal, and the crashing will stop.
Or the technician can open System Restore from Recovery Mode. And, assuming there is a recovery point, restore the computer back to a good known working state.
Now, this may all seem simple enough. So why were so many organizations having trouble running this fix? That all has to do with BitLocker. As an added security measure, many organizations use BitLocker on their computers to perform a full hard disk encryption. This is done so that if a computer ends up being lost or stolen, and ends up in the hands of an "unauthorized user" they will not be able to access any of the data stored on the computer without a password to log into the computer, or the computer's BitLocker recovery key.
This presented a problem when trying to restore all of these affected computers, because when either trying to launch Safe Mode or System Restore, the user would be prompted for the BitLocker recovery key.
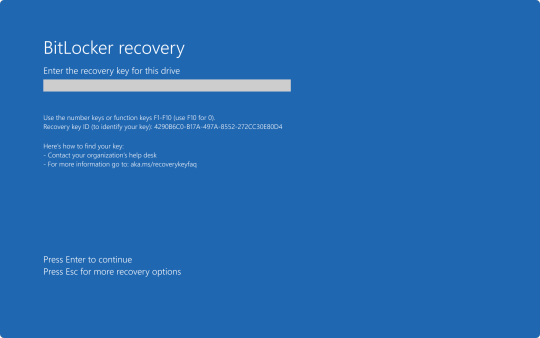
In my organization's case, we found we could save time by providing our end user the steps to perform one of the two fixes on their own to save time. But the problem we still continue to run into is the need for these BitLocker recovery keys. In my case, I've been fielding several calls where I've had end users walking from one computer to another while I provide them with the key as they walk through reverting back to a previous restore point.
Again, a pretty long story, but hopefully that can provide some context as to what's been happening over the past 48 hours.
30 notes
·
View notes
Text
Send one-time login code to your phone? Set up 2-factor authentication today? Send a code to your e-mail now? You were logged out for security reasons, please wait to log back in. Confirm your recovery phone number now? Enter e-mail to recover username?We've automatically logged you out due to inactivity. Your new password can't be the same as your old password. Please enter your phone number so we can confirm your identity. Update your password today? Your password must contain a symbol. Send a one-time code to log in? Refreshing the page. For security reasons, we've logged you out after 5 minutes. Your user ID was requested, was this you? Security alert, you logged in to your account from a computer, please confirm.
#enshittification#guess who filed their tax return today & found out that i didnt have any federal tax withheld last year so I guess i owe. Thanks boss.
5 notes
·
View notes
Text
found out today that google is full of sh!t PLS PROTECT YOURSELVES
my account got hacked, the hacker changed all my recovery details and now has access to my google drive files, my emails, any photos in google photos, and also the login info to so many websites that use google and there is NO way to get anything back or at least delete the acct.
You would think that google, as a company offering to store and handle so much info and FILES in particular and also passwords and login infos for other websites would have some kind of support for this but no they don't even have a single customer service phone number or any way of recovering anything. I searched around online for solutions but the internet is FILLED with THOUSANDS of ppl with the same concern for YEARS who lost their files, lost their connected youtube accts with thousands of subscribers. I lost access to my yahoo acct too but they had a customer service phone number (paid) but at least they verified my identity and helped me to get access back and secured my account. PSA: DO NOT RELY ON GOOGLE TO SAVE ANYTHING FOR YOU. BACK UP YOUR OWN STUFF ELSEWHERE. If anything goes wrong there is literally 0 recourse - google offers absolutely 0 support:

My only wish now is to be able to at least delete the account so they don't have access to all my info anymore but there is literally no place to go for that so I just have to be okay knowing some evil people indefinitely have 10+ years worth of my private info (emails, files, photos)
PLS learn from my mistake and use this opportunity unentangle yourself from google. They literally. have no recourse if anything goes wrong. It's not like it's impossible: Yahoo literally asked me for my state ID and location to give me access back to my account.
#Ugh I hope whoever did this I pray something horrible happens to them.#I hope they get exactly what they deserve no less#i hope they lose every cent of money they got doing this stupid shit#google#fraud#💭.txt
7 notes
·
View notes
Text
I'm half convinced that the reason Apple's password recovery is so fucking difficult and long-winded is to make people snap and create new accounts and re-buy shit they already bought on their old accounts. Tell me I'm wrong. There's no reason you should need two weeks to do security for a password reset when you got confirmation codes from both my phone number and my email address. Jfc.
#you can tell I'm pissed because I'm using punctuation#anyway this isnt the first time ive had to do this and the first time it didnt even work properly. i wanted to kms#the system speaks#apple#capitalism
12 notes
·
View notes
Text
Essential Cybersecurity Measures for Organizational Network Protection

In today's interconnected world, a robust cybersecurity strategy is no longer a luxury, but a necessity for organizations of all sizes. A strong defense against ever-evolving cyber threats is paramount to protecting sensitive data, maintaining business continuity, and preserving reputation. This blog explores critical cybersecurity organizational network protection measures.
Understanding the Threat Landscape
Before diving into protective measures, it's crucial to understand the threats organizations face. These include:
Malware: Viruses, ransomware, and spyware designed to damage or steal data.
Phishing: Deceptive emails or messages tricking individuals into revealing sensitive information.
Denial-of-Service (DoS) Attacks: Overwhelming networks with traffic, disrupting services.
Insider Threats: Malicious or accidental actions by employees or other insiders.
Data Breaches: Unauthorized access and exfiltration of sensitive data.
Essential Cybersecurity Measures
A layered approach is key to effective network protection. Here are some crucial measures:
Firewall Implementation: Firewalls act as a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predefined rules. Regularly updating firewall rules is critical.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and even automatically blocking malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential to detect and remove malicious software. Regular updates are crucial.
Strong Password Policies and Multi-Factor Authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if a password is compromised.
Regular Security Audits and Vulnerability Assessments: Regularly assessing your network for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all employees is vital. This training should cover topics like phishing awareness, password security, and safe browsing practices.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs.
Regular Backups and Disaster Recovery Planning: Regularly backing up critical data and having a disaster recovery plan in place ensures that you can recover from a cyberattack or other disaster.
Network Segmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Incident Response Plan: Having a well-defined incident response plan in place allows you to react quickly and effectively to a security incident, minimizing damage and downtime.
Building a Cybersecurity Culture
Effective cybersecurity is not just about technology; it's also about people and processes. Building a strong cybersecurity culture within your organization is crucial. This involves:
Leadership Buy-in: Securing support from top management is essential for allocating resources and prioritizing cybersecurity.
Open Communication: Encouraging employees to report suspicious activity without fear of reprisal.
Continuous Improvement: Regularly reviewing and updating your cybersecurity policies and procedures to stay ahead of evolving threats.
Xaltius Academy's Cybersecurity Course: Your Partner in Network Protection
Navigating the complex world of cybersecurity can be challenging. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the knowledge and skills needed to protect your organization's network. Our expert instructors and hands-on labs will prepare you to effectively implement and manage these critical security measures. Invest in your cybersecurity future and safeguard your organization's valuable assets.
Conclusion
Protecting your organization's network requires a proactive and multi-faceted approach. By implementing these essential cybersecurity measures and fostering a strong security culture, you can significantly reduce your risk of falling victim to cyberattacks and safeguard your organization's future.
2 notes
·
View notes
Text
Rant incoming
WHY IS TECHNOLOGY SUPPORT SO GODDAMM DIFFICULT I SWEAR TO GOD.
So. I want to play minecraft online. I don't really use my Microsoft account often but I figure it should be fine. I get signed up for PS Plus, I pay my £6.99, and now I just have to link my Microsoft.
I do the link. I submit the code, then the email, then the password...then the code again then the email then the password and so on so forth until the link expires.
I make a new Microsoft account, as suggested, and it actually seems to be getting somewhere. Until the game is like "Oh you have to sign into the account linked with your game. Yknow, Jyan, which we can remember the name of but not your freaking details".
So I try that. Get in a loop again because it's that outlook email. I sign into Gmail outlook, everything looks fine. I have a string of very recent emails from Amazon about a refund so I know my email *works* at least.
But log in still won't work. So I look on the Microsoft question thing for answers and someone has had the loop issue. There's a link about account recovery. I'm desperate, I mean what the hell nothing else is working, so I use that link. They ask for an alternative email to send me a confirmation where they explain that I did not give them enough details and, as a really really kind courtesy (BECAUSE THATS HOW THEY PHRASED THIS, LIKE IT WAS A COURTESY) they've locked me out of my account :). Yay :). Because they take security reallllly seriously. Except they haven't Because I can still access my emails on the Gmail app but still can't do anything else.
By the way, did you know once you link a Microsoft account to a ps4 account you can NEVER UNLINK AND RELINK A NEW ONE?! Why. What do you GAIN Microsoft. Oh also because ps plus is a paid service they really hate you using it on other accounts of the same ps4 device or really any online features on any account other than the main one. Because what.
So clearly my issue is too complicated for online articles. I've tried and got no where, in any case worse. Let's try reddit - SYKE ALL THE BOTS RUINED REDDIT AND I CANT ACCESS ANY TECH SUPPORT GROUPS TO ASK QUESTIONS MYSELF UNLESS I GET SO MUCH KARMA. GREAT.
So. Microsoft tech support. Please be a good - OH OF COURSE ITS NOT
To summarise this amazinggggg service
1 - CAN'T FIND A RELIABLE NUMBER BECAUSE OF THE SCAMS
1.5 - Google AI summarise RECOMMENDED ME A SCAM NUMBER AS THE OFFICIAL ONE
2 - I can't find anywhere where I can submit a text complaint.
3 - All the search bars just take me to pre written articles as if I haven't read enougj
4 - THEY THEN OFFER ME A PAIDDDDD SERVICE TO "GET FIRST IN LINE FOR GPT TO SOLVE MY ISSUE"
What. The actual. Fuck.
I just want to talk to a human who knows something PLEASE. No none of the articles have helped. No I don't want AI to tell me, it has PROVEN its USELESSNESS. I just wanna talk yo a freaking human, preferably over the phone, who can tell me what to do or initiate some stiff themself because clearly the design has self imploded and IM JUST SO FREAKING FRUSTRATED IM SAT HERE WITH £7 OF A WORTHLESS SUBSCRIPTION AND NO RELIABLE TECH SUPPORT TO FIX IT ALL BECAUSE EMAIL BROKE BUT NOT REALLY.
And that doesn't even BEGIN to worry about whether I'm gonna be able to get my money back on this completely useless service.
So I'm turning to Tumblr. What's tumblrs tech support like??? I don't know, maybe there's a genius out there SOMEWHERE. Because clearly I can't use reddit, thanks barrier to entry :/ and I can't just ring up a human who can actually listen to my words with the nuances that don't fit into the fucking booklet.
If anyone knows anything that could help, please leave your wisdom here I'm frustrated and desperate and don't wanna lose £7 on something I can't even use.
3 notes
·
View notes
Text
0 notes