#RainbowTable
Explore tagged Tumblr posts
Text

Rainbowtive
Reclaimed from an end0 term
Flag is meant to be redesigned if desired
An alter who holds trauma related to being a rainbow baby.
(This Blog was created to repost terms for the convenience and comfort of others. If you remake a reclaimed flag please tag me.)
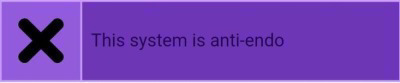
#anti endo#endo dni#complex dissociative disorder#did alter#did community#did osdd#did system#dissociative identity disorder#other specified dissociative disorder#did flag
14 notes
·
View notes
Text
🌈 Rainbowtized one of my guitar leads
Light Switch by Adysen | Brooke A McKinney
#adysen#artist#seattle#photography#brookeamckinney#adysenmusic#music#musician#fashion#hatisland#pride month#lgbt#lgbtq#gay#gaypride
2 notes
·
View notes
Note
Questions for the mun | 7. What do you do when you're bored?

I either take a nap, listen to music, or try to do something which I'm creating. There's not much of us on this platform, and drafts come in a few for me since currently I've only got muse for original characters and Chrome. And there are more active versions of the muses I picked as well, but that's more my fault than anything.
I have an account on WorldAnvil. It is a site dedicated to making campaigns for tabletop rpg's mostly, but it's also a place I like to use for world-building. I hang out there sometimes now. I would say there's a lot more to it than ToyHouse which centers around organizing your characters. There are other sites that I looked at that are similar and less expensive than WorldAnvil's paid plans, but I'm happy where I am.
If you caught me years ago when I was in my 20s I would be talking your ear off about my Zodiac Senshi.
My account is here. I do have some worlds I'm building, but I haven't published their stories yet. My worlds are set to private, just in case. I do have to warn you, that one of them is not Tumblr-safe. It's a magnus opus like O.ne Piece is to Oda. My debut comic is getting ignored at the moment... ;;; but I haven't renamed it. It is a magical girl, and no it is not inspired by R.WBY. I get that a lot since the main character is a girl that uses a scythe...
I do have a magical girl setting for my Zodiac girls, but I'm trying to think more of an original setting. There is already a Zodiac magical girls thing from D.ark H.orse...? It's more Sentai (power rangers) I feel, and reminds me of my magical girl series I started in elementary called Rainbowteers...

2 notes
·
View notes
Text
gravity rainbowt becsülettel végigolvastam, és világos volt, hogy ez jó, de nekem nem lett jó. nem fért bele a fejembe és kész. lehet, ha közösségileg olvasom, beszélgetve róla, úgy jobb
szemben az ulysessel, amin el lehet szörfözni, nem ő jön belém, hanem én megyek belé, és áramlik, visz, csobog, hallgatom, mint egy zenét (nem tűnik úgy, hogy nyelv- vagy fordításfüggő, legföljebb az ikonikusan megmaradt mondatok nincsenek benne, de maga a szöveg ilyen természetű, nekem)
ezekért a könyvekért + amire még gyakran gondolok, hogy az irodalom (meg minden művészet) számunkra gyakorlatilag végtelen
David Foster Wallace: Végtelen tréfa
Régen nem írtam arról, hogy miket olvastam, pedig tök sok jó könyvet olvastam mostanában.
A Végtelen tréfát itt a tumblin ajánlotta valaki, azzal, hogy ha szeretem Jonathan Franzen regényeit, akkor ezt is szeretni fogom. Itt jegyezném meg, hogy Wallace stílusa kicsit se hasonlít Franzenére, viszont tényleg szerettem és kár lett volna kihagyni, így köszi az ajánlást.
Oké talán annyiban hasonlít Franzenre, hogy hosszú, amerikai, van benne versenysport és nagyjából kortárs regény, de ezt leszámítva nagyon más a vibe-ja és Franzen sokkal olvashatóbb és sokkal kevésbé él vissza az olvasó türelmével. Ettől még jó volt a Végtelen tréfa, csak egy meglepő élmény.
Ha valamihez hasonlítanom kell, akkor az jut eszembe, mint amikor A nyomorultakat olvastam Victor Hugo-tól és a cselekményt megszakította egy többszáz oldalas leírás egy zárdáról amit egyébként szintén élveztem. Ez a könyv pont ilyen csak zárda helyett bentlakásos teniszakadémia van meg átmeneti ház leszokóban lévő drogosoknak. Ja és a bentlakásos intézetek leírásán kívül nincs sok cselekmény, hanem ez a cselekmény, illetve van még valami abszurd rejtvényfejtős scifi, ami engem teljesen elszállt visuel novelekre emlékeztetett. Egyébként ha még valamihez kéne hasonlítanom a Végtelen tréfát akkor az az Umineko when they cry visuel novel. Tudom, hogy a Végtelen tréfában nincsenek nagy mellű anime lányok, viszont ugyanúgy van benne monoton részekbe csomagolt mély mondanivaló és hirtelen műfaj és stílusváltás, mint az Uminekoban, és ugyanúgy nyúlik, mint a rétestészta. A szinte megfejthetetlen rejtvények, amikre részben rájövök, részben a reddit segítségét kérem is stimmelnek.
De ezek mellett a Végtelen tréfa még scifi is méghozzá meglepően jó, mármint a 90-es években Wallace csomó mindent megjósolt a streamingszolgáltatóktól kezdve, a videóchateleséig és az ahhoz kapcsolódó problémákig. De a regénynek mégse ez volt az igazán erős része, hanem a felépülő drogosokról szóló részek, amikhez nagyon tudtam érzelmileg kapcsolódni, hiába nem vagyok függő, mert nagyon plasztikusan írja le a változás és a lelki fejlődés egyszerre csodálatos és ijesztő voltát.
A teniszező gyerekek szála is tetszett, egyrészt mindig érdekelt a versenysport zárt világa, másrészt ez is komolyabb dolgokról szól és nem csak az itt is felbukkannó drogfüggőségről, hanem olyasmikről, hogy az e a jobb, ha van egy kijelölt célunk, aminek mindent alárendelünk, vagy az ha önmagunknak kell megtalálnunk az értelmet. Illetve a főszereplő Hal viszonya az érzelmeihez is egy baromira fontos téma, hogy kezdetben mennyire nem tud kapcsolódni a saját érzelmeihez, később pedig amikor elkezd tényleg érezni az egyszerre szabadítja fel és nyomorítja meg.
Szóval igazából jó könyv volt ez és igaza lehet a redditnek abban hogy első olvasásra senki se fogja fel az összes rétegét, de asszem most pár évig nem akarom újraolvasni.
27 notes
·
View notes
Photo

Add whimsy and color to your table top with new items from nJoyArt on Society6! #linkinbio #njoyart #brightdecor #whimsicaldecor #dormdecor #homedecor #rainbowdecor #rainbowtable https://www.instagram.com/p/B4CvaTin7DM/?igshid=16wommn16kpa0
1 note
·
View note
Text
Why do I always get hacked?
There are two big reasons why people get hacked.
Flaws in software and flaws in human behavior. While there's not much you can do about coding vulnerabilities, you can change your own behavior and bad habits. For More- Hacker sy kesy bachen A variety of software programs are now available that make hacking easier, however, if you want to know how it is done, you will need to have basic knowledge of programming.
0 notes
Text
Should you be worried about your passwords getting hacked?

Most IT security specialists define passwords as "the keys to our Digital Home": that's a pretty good metaphore, especially considering that our "digital home" is getting bigger as the time passes (and the technology advances). In the latest few decades we learned how to protect our precious devices (computers and, most recently, mobile devices) to prevent unauthorized access to them and their data... But, with the advent of the Internet and Internet of Things, the house became an infinite amount of different rooms: from online banking to food delivery services, from cloud-based repositories to remotely accessible Virtual Private Networks, we were literaly stormed by those "keys". At the same time, since technology runs faster than our ability to assimilate it, most internet users - as well as business companies - still use passwords in a totally insecure way today: to continue with our initial metaphore, nobody would leave the key on the door, or feel comfortable using the same key to open multiple doors, or use a weak lock & key combination, right? However, when using passwords, most of us often do just that. In the initial part of this post we'll try to summarize the most common mistakes that people do in choosing a password; then we'll briefly review the most common ways used by hackers to stole passwords; last but not least, we'll share some suggestions and best practices to secure our passwords and improve our account's security.
Common Password Mistakes
The typical password mistakes can be split into three main categories: choosing a weak password, using the same password among different web sites, and insecurely storing passwords. In the following sections we'll deal with each one of them. Choosing a weak Password A weak password, as the name implies, is a password too easy to guess or to discover using automated hacking techniques (brute-force, rainbow tables, and so on). Those who thinks that this is issue is a thing of the past because nowadays the majority of IT users have been educated enough to avoid choosing trivial passwords should check the SplashData's Most Used (and Worst) Password of 2017 infographics, which could easily change their mind. Here a list of the top 10: - 123456 (proudly keeping the first place since 2013) - password - 12345678 - qwerty - 12345 - 123456789 - letmein - 1234567 - football - iloveyou Luckily enough, such situation has been mitigated by enforcing a password security policy that is already adopted by most websites - and that is mandatory for all online services that deal with money or personal data, at least in most countries. Such policies not only require a minimum length and the presence of different character types (uppercase and lowercase letters, numbers, special characters) to make them harder to guess, but also force the users to periodically change them (often every 90 or 180 days). However, choosing a weak password is still critical for those devices where such policies are not enforced yet - such as most IoT devices. Using the same Password In addition to using passwords objectively too weak, users (and company officers) often also make the mistake of using the same password for different web sites or services. The so-called "password reuse" is probably the most serious mistake we can make nowadays: if a hacker manages to hack into a website's servers (this is happened for Yahoo, LinkedIn, Sony, and countless "minor" websites) and steal the users passwords, it will definitely try to use those retrieved passwords to gain access to other services. The only thing we can do to stop such common hacking practice is to ensure that each and every account that we have has its own password. A great example of such bad practice was given during the LinkedIn data breach (2012), through which Mark Zuckerberg's LinkedIn, Twitter and Pinterest accounts were all hacked because he used the same password for all of them. Such verification process can be automated using dedicated tools, such as Shard - a open-source command line tool that was developed to allow users to test whether a password they use for a site is used to access some of the more popular services, including Facebook. LinkedIn, Reddit, Twitter or Instagram. Insecurely storing Passwords The need to use strong passwords and a different password for each website or service inevitably brings another big requirement: the need to have a "secure" mechanism for storing these passwords, since human memory won't definitely be able to keep up. And this is where the most serious security problems often occur, not only for home users yet also for most companies. Who among us has never seen those dreadful MS Excel files (or text files!) containing a huge list of passwords? And the worst thing is that those unsecure repositories are often shared among different users (family members, co-workers, and so on), meaning that they aren't protected even with the basic user authentication mechanism provided by the OS.
How passwords are hacked
The techniques used by hackers for discovering our passwords are more than one, sometimes really trivial: as we can easily see by looking at the list below, most of them leverage or exploit the bad practices that we've talked about early on. - Social Engineering: e.g. Phishing, Password Sniffing. In practice, it is we who allow ourselves to be deceived by social engineering techniques and give passwords to those who ask for them through for example messages, emails, fake sites that disguise a well-known site. - Guessing passwords: Using personal information such as name, date of birth or pet names. When this happens, sometimes the "hacker" happens to be kind of close to the "victim": a friend, neighbor, co-worker or someone that knows enough info to perform such guesses. However, thanks to the modern approach to social networks, everyone might easily know a lot of stuff about anyone else. - Brute Force Attack: Automatically testing a large number of passwords until the right one is found. There are special programs to do this (a widely used one, John the Ripper, is open source, meaning that anyone can use it). Brute-force attacks are quite expensive to pull off, which requires time and computing power, but can easily achieve the result if the password is weak enough. - Intercepting a password, for example while it is being transmitted over a network. The bad habit of communicating passwords via email is frequent: there are even sites that, as soon as we register, send us a polite welcome message containing username and password displayed "in clear". Too bad that email is not a safe tool. - Shoulder surfing: a social engineering variant. It basically means "observing someone from behind" (i.e. "shoulder") while typing the password. - Using a KeyLogger. Keyloggers are malware programs that record everything typed on the keyboard, then transmit this data to the hacker who installed the keylogger. There are also hardware-based keyloggers that require direct access to the victim's computer. - Passwords stored in an insecure way, like handwritten on a piece of paper, or saved on a word file (see above). - By compromising a database containing a large number of user passwords, then using this information to attack other systems where users have reused the same passwords ("credential stuffing"). How to secure our Password Securing our passwords in order to avoid most - if not all - of the hacking attemps listed above is not impossible and is a goal that can be achieved by anyone. In a nushell, all we need to do is to apply two best practices: - Write strong and unique Password - Securely store your Passwords Both of them are equally important and must be followed for each and every password, without exceptions. How to write a strong Password A strong password is characterized by the following elements: length and character types used. - Regarding the length, it is strongly recommended to use at least 12 characters. - As for the character types, just let the math guide you: we have 10 numeric types (0-9), 52 letter types (26 lowercase + 26 uppercase), and more or less 33 special character types easy to type because they're directly accessible from a typical keyboard (such as #, &, %, ?, ^, and so on). To summarize all that, in total we have 95 character types available: with that in mind, we can say that a good password should have at least one character coming from each one of these types, because by increasing the types of characters, the number of possible combinations grows exponentially, thus making harder (and time-consuming) to "brute-force" the resulting password. How to store your Passwords As we aready said early on, using a different password for each website or service means that we can't rely to our memory to remember them all: at the same time, using insecure data stores such as MS Excel files or text files is definitely not an option. The best way to tackle (and fix) this problem is to use a Password Manager tool: a dedicated software that acts as a vault where you can securely store all your passwords, as well as your usernames and/or credential info, with the big advantage of having them in a single place. This basically means that you'll only need to remember the password required to access it, which is often very strong and can be further protected by other authentication factors (fingerprint, SMS, OTP, mobile tokens, and so on). The most advanced Password Managers also provide a good level of integration with the Operating System and browsers, meaning that they can even “automatically” (yet securely) fill in your credentials whenever you log in to a site (or an app) using your desktop or mobile device. IMPORTANT: Password Manager apps shouldn't be confused in any way with the "password storage" features offered by most modern browsers, such as Google Chrome, Mozilla Firefox, and MS Edge, that prompts you to store your credentials and fill out the forms for you, unless they are part of a bigger product that grants the fundamental features that a good Password Manager needs to have: centralized and distribuited repository, access from multiple devices, data encryption of the whole vault, 2-factor authentication support, and so on.
Conclusion
That's it, at least for now: we hope that this post will help most users and companies to increase their online security by securely choosing and storing their password. Read the full article
1 note
·
View note
Photo

Moon prism power ✨🌙✨ . . . #sailormoonvibes #prism #prismphotography #prettythings #instapretty #latergram #rainbowtable #colorfultable #random (at Silver Lake, Los Angeles)
#sailormoonvibes#prism#prismphotography#prettythings#instapretty#latergram#rainbowtable#colorfultable#random
1 note
·
View note
Text


Two commissions for two very lovely peeps 🧡 Characters belong to them (KindridFox/ RainbowT)
402 notes
·
View notes
Photo

Ok ok ok, I couldn’t stand it. 🌈🤣 #colorized #rainbowtized #ihavethisthingwithrainbows (at The Woodlands, Texas) https://www.instagram.com/p/CM2eKySAy4T/?igshid=15d3f3x7799nx
0 notes
Photo

#Rainbowt parts . . . . . . . . #3dprint #3dprinter #3dprinting #manufacturing #tinkercad #tinkering #autodesk #fusion360 #openscad #robotics #robotic #arduino #arduinoproject #fablab #maker #making #makersgonnamake #engineering #electronics #hitec #rover #explorer #mechatronics https://www.instagram.com/p/CAmn0dnqQXT/?igshid=7sdoa9o387gs
#rainbowt#3dprint#3dprinter#3dprinting#manufacturing#tinkercad#tinkering#autodesk#fusion360#openscad#robotics#robotic#arduino#arduinoproject#fablab#maker#making#makersgonnamake#engineering#electronics#hitec#rover#explorer#mechatronics
0 notes
Photo

keep life colorful
#hoarding#pyrexlove#pyrex#vintage#vintageglass#collection#keeplifecolorful#rainbow#rainbowtize#roygbiv
2 notes
·
View notes
Photo

Password rules. Often they are a pain, sometimes it’s worse. Like this example from a large company. Only 6-10 characters? Why limit to 10? Is there a database column width limitation? Are they storing the password somehow, hopefully at least encrypted? With only 10 characters, that leave open a brute force attack since you know the password length. Most places hash passwords, which gives a constant length hash value regardless of the password length. If they are hashing, this is still not good as rainbow tables for popular SHA-1 and MD5 hashes of up to 10 characters are easily available. And why can’t passwords have < and >?Those characters are common in HTML and XML, so is there a clear-text password problem with using those characters? Is my password easily recoverable if their user data gets breached? Makes me wonder. If you store passwords, use a good hashing algorithm. Salt the passwords. Don’t arbitrarily keep me from using certain characters. And don’t keep me from using a long password! . #techtuesday #password #passwords #passwordcracking #rainbowtables #md5 #sha1 #security #passwordbreach #securitybreach #technology #shortpassword https://www.instagram.com/p/Bs8aKSanU2r/?utm_source=ig_tumblr_share&igshid=wsej3uv2ylzs
#techtuesday#password#passwords#passwordcracking#rainbowtables#md5#sha1#security#passwordbreach#securitybreach#technology#shortpassword
0 notes
Text
Can hackers mess with your Internet?
By using a technique called DNS
(Domain Name Server) hijacking, hackers can breach the security of your home Wi‑Fi and potentially cause you a great deal of harm. For More- How to protect from hacker They can redirect your traffic to a website run by them, causing you to unwittingly give your credit card number or Facebook login credentials to a criminal.
0 notes
Photo

The time I got Rainbowitis. 😂☺️ I was rainbowtizing everything!😂😂😂
#artjournal#creativejournal#visualjournal#quotes#staedtler#staedtlerpens#art#rainbow#rainbowitis#rainbowtized
1 note
·
View note


